#face recognition access control in saudi arabia
Text
facial recognition access control price
face recognition access control system
face recognition access control system dubai
face recognition access control system abu dhabi
facial recognition access control
facial recognition access control Saudi Arabia
facial recognition access control in Saudi
facial recognition access control in Abu Dhabi
facial recognition access control in Sharjah
face recognition access control attendance system
face recognition access control attendance system abu dhabi
face recognition access control attendance system in sharjah
Face Recognition Attendance System in Saudi
#accesscontrolsystem #accesscontrolsysteminuae #accesscontrolsystemsudiarabia #accesscontrolsystems #accesscontrolsystemssupplierinuae #accesscontrolsysteminalain #accesscontrolsystemsupplierinajman #
#face recognition system abu dhabi#face recognition systems#face recognition systems abu dhabi#face recognition system in uae#face recognition system in ajman#face recognition system in bur dubai#face recognition system in alain#face recognition access control saudi arabia#face recognition access control in saudi arabia#face recognition access control in ajman#face recognition access control in alain#face recognition access control in bur dubai#face recognition access control in sharjah#facial recognition access control price#facial recognition access control price dubai#facial recognition access control price in abu dhabi#facial recognition access control price bur dubai#suprema access control qatar#suprema access control saudi arabia#suprema access control in saudi#suprema access control in Sharjah
0 notes
Text
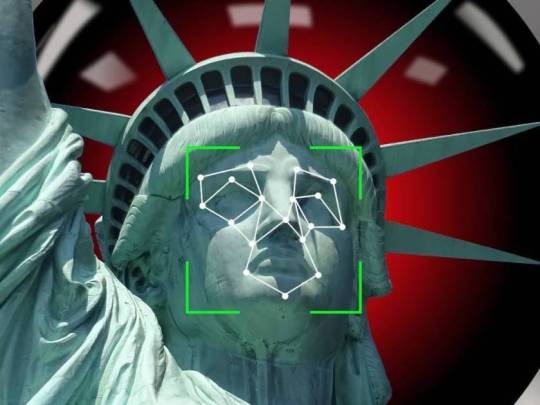
Tektronix Technologies: Swisstek Face Recognition Device in UAE
In the rapidly evolving world of security and surveillance the facial recognition program is becoming among the top ingenuous techniques. This innovation has been pivotal across a variety of industries that cover the business world as well as security for the common. The leading player within this space is Tektronix Technologies that has developed a cutting-edge face recognition system called the Swisstek. The review will focus on the strengths, benefits and features as well as how to install the cutting-edge technology. This review will concentrate on its applications within the UAE.
What is Facial Recognition Software?
Facial recognition software is an advanced system that is designed to confirm or identify individuals by analyzing patterns and compare them on the basis of the facial features. It makes use of sophisticated algorithms to detect facial landmarks that then generate a distinct facial signature for every person. Its most popular uses include security, access control as well as identification verification.
Introduction to Tektronix Technologies
Tektronix Technologies is one of the most well-known firms in the security device industry. Their commitment to quality and ongoing innovation has propelled their products to the forefront of technical developments. Tektronix Technologies aims to revolutionize the manner access and security are controlled particularly in the UAE.
Features of Swisstek Face Recognition Device
The Swisstek face recognition technology is a standout with a number of distinctive attributes that set it apart from its competitors. These include:
High Accuracy and Speed
It has a high degree of precision. It means the chances of misunderstanding positives or negatives is very minimal. The speed with which it detects signals is remarkable, and it is suitable to be used in areas that have a significant amount of visitors.
Robust Security Protocols
To protect against unauthorized access to information in order to block access by unauthorized persons to prevent unauthorized access, to prevent unauthorized access, the Swisstek facial recognition software is equipped with strong security measures. It comes with security features to secure facial data along with rigorous privacy rules.
Integration Capabilities
One of the best features of this device is the ease of integration into the current security solutions that utilize the facial identification system. This is an excellent solution for businesses looking to enhance their security measures.
User-Friendly Interface
Despite its advanced capabilities, the device is designed with a user-friendly interface so that everyone can to use it effortlessly.
https://tektronixllc.ae/swisstek-face-recognition-uae-saudi-arabia/
0 notes
Text
Building a Culture of Food Safety: ISO 22000 Certification in Saudi Arabia

In today’s fast-paced world, food safety has become a paramount concern for consumers and businesses alike. Ensuring that food products are safe to consume not only protects public health but also boosts consumer confidence and business reputation. In Saudi Arabia, achieving ISO 22000 certification in saudi arabia is a critical step for food businesses striving to meet the highest standards of food safety. This article explores the importance of ISO 22000 certification, the challenges faced by food businesses in Saudi Arabia, and how PopularCert can assist in building a robust culture of food safety.
The Importance of ISO 22000 Certification
ISO 22000 is an internationally recognized standard that outlines the requirements for a food safety management system (FSMS). This certification ensures that food safety hazards are identified and controlled at every stage of the food supply chain.
Key Benefits of ISO 22000 Certification:
Global Recognition: ISO 22000 is acknowledged worldwide, helping businesses gain international credibility.
Enhanced Food Safety: It ensures comprehensive control of food safety hazards, minimizing risks of foodborne illnesses.
Regulatory Compliance: Certification helps businesses comply with local and international food safety regulations.
Market Access: Many retailers and consumers prefer suppliers with ISO 22000 certification, opening up new market opportunities.
Improved Efficiency: Implementing ISO 22000 streamlines processes, enhances operational efficiency, and reduces waste.
Challenges in Achieving ISO 22000 Certification in Saudi Arabia
While the benefits of ISO 22000 certification in saudi arabia are significant, achieving it can be challenging. Food businesses in Saudi Arabia often face several obstacles on their path to certification:
Complex Requirements: Understanding and implementing the detailed requirements of ISO 22000 can be overwhelming without expert guidance.
Resource Allocation: Establishing a food safety management system requires significant time, effort, and financial investment.
Documentation: Maintaining accurate and comprehensive documentation is crucial for compliance but can be burdensome.
Employee Training: Ensuring that all employees understand and adhere to food safety protocols is essential for maintaining certification.
Continuous Improvement: The standard requires ongoing monitoring and improvement, demanding a sustained commitment to food safety.
Conclusion
ISO 22000 certification is a crucial step for food businesses in Saudi Arabia aiming to ensure food safety and enhance their market reputation. While the certification process can be challenging, partnering with the right expert can make it a manageable and rewarding journey. PopularCert offers the expertise, resources, and support needed to bridge the gap and achieve ISO 22000 certification in saudi arabia. By choosing PopularCert, food businesses can confidently navigate the certification process and commit to the highest standards of food safety and quality.
Embark on your ISO 22000 certification journey with PopularCert today and set your business on the path to food safety excellence. Building a culture of food safety not only protects your consumers but also enhances your business’s reputation and opens up new market opportunities. Let PopularCert be your trusted partner in achieving and maintaining ISO 22000 certification.
0 notes
Text
Facial Recognition devices from Expedite IT Infrastructure in Riyadh, Jeddah and rest of the KSA

Facial recognition device Riyadh-
The Facial Recognition System is state-of-the-art technology, using biometric data to identify and authenticate people based on their unique facial features. The devices' efficiency, accuracy, and convenience of use across a wide range of applications have led to an increase in demand for KSA Cities.
They have helped improve access and security to improving attendance tracking, and enhancing the customer experience, these tools are now an integral component of a variety of businesses.
The facial recognition systems that are offered from Tektronix Technologies have proven to change the way people interact in Riyadh, Jeddah, and throughout the KSA.
The Operation of Facial Recognition
Using a camera or sensor, a photograph of a person's face is taken in order to do facial recognition. After that, it examines and compares the facial features to a database of faces that are recognized to be. The process involves taking measurements of specific facial features including the distance between eyes, the appearance of the nose and the shape of the face. If a match is discovered and the identity of the individual is authenticated or confirmed.
Enhanced Security and Access Control
Strengthening Physical Security Measures
Facial Recognition technology provides a more secure level of protection in comparison to other methods, like access cards or PINs. Face recognition is the only way people who have been authorized to use the device with authenticated faces are able to gain access to areas that are secured and reduce the possibility of illegal entry as well as potential security breach.
Access Control for Restricted Areas
They are especially useful in limiting access to certain places, including executive offices, server rooms and laboratories. Face recognition adds an additional protection by making sure only authorized employees is allowed into these highly sensitive spaces and thereby enhancing the overall security of sensitive information and valuable assets.
Real-time Monitoring and Alerts
Face recognition devices can also provide live monitoring and alarms. They can detect and issue alerts to unidentified people or threats which allows security officers to respond immediately. This proactive method aids in the prevention of security threats and creates a safe atmosphere for all.
Streamlined Attendance Tracking and Management
Automated Attendance Recording
The advent of Facial Recognition Device has revolutionized time tracking and management by allowing for automated processes. Workers can look at their faces and the system accurately tracks their attendance. This removes the need to use manual systems for tracking, lessens administrative burden and provides accurate attendance records.
Eliminating Time Theft and Buddy Punching
Through facial recognition companies can end time theft and buddy punching. Because the system is based on biometric information it is virtually impossible for workers to abuse the system and clock in and out of their coworkers. This gives fairer and more accurate attendance records that are more reliable.
Integration with Payroll Systems
The facial recognition device can easily be integrated with payroll systems, easing all payroll processes. Data on attendance collected by the device is directly linked with payroll computations, providing an accurate and precise compensation of employees. The integration removes the requirement to enter the data manually eliminates mistakes, and also saves time for HR as well as the payroll department.
Benefits of Face Recognition Equipment made by Expedite IT Infrastructure in Riyadh, Jeddah, and the Rest of the KSA
Facial Recognition in CCTV Systems
Face recognition technology that's in CCTV systems is a potent instrument for increasing surveillance and public security. Through the automatic identification of individuals at a moment's notice, it allows swift response to any potential threat. It ensures security guards can keep an eye on crowded areas efficiently and quickly find anyone engaged in suspicious actions.
Identifying Potential Threats and Criminals
The facial recognition device assists in identifying potential threat as well as criminals. When comparing facial pictures taken against watch lists or databases of criminals known to be in the system, these devices are able to quickly identify any possible match. This enables police agencies to stop criminal acts before they happen and identify those accountable.
Conclusion
Facial Recognition Device in KSA-That are offered from Tektronix Technologies have proven to change the way people interact within Riyadh, Jeddah, and throughout the KSA. They have helped improve access and security to improving attendance tracking, and enhancing the customer experience, these tools are now an integral component of a variety of businesses.
Visit our website for more info
Call +971 55 232 2390 +971 55 232 2390
0 notes
Text

Face Recognition Entry System UAE
Face Recognition Entry System Dubai
Face Recognition Entry System Abu Dhabi
Face Recognition Entry System Sharjah
Face Recognition Entry System Alain
Face Recognition Entry System Saudi Arabia
Face Recognition access control attendance system
Face Recognition Access Control Attendance System Dubai
Face Recognition Access Control Attendance System Abu Dhabi
The face Recognition access control attendance system uae
face recognition attendance system dubai
face recognition attendance system abu dhabi
face recognition attendance system Sharjah
face recognition attendance system Ajman
facial recognition software uae
facial recognition software abu dhabi
facial recognition software in sharjah
facial recognition software Ajman
Biometric & Time Attendance System in Dubai, UAE
Tektronix Technology presents facial recognition software in Dubai Abu Dhabi
#facial recognition access control#facial recognition devices#facial recognition software#facial recognition software abu dhabi#facial recognition software uae#facial recognition software sharjah#facial recognition software ajman#facial recognition software alain#facial recognition systems uae#facial recognition systems in sharjah#facial recognition systems#Face Recognition Entry System uae#Face Recognition Entry System abu dhabi#Face Recognition Entry System sharjah#Face Recognition Entry System bur dubai#Face Recognition Entry System in alain
0 notes
Text
Why Access Control System is necessary for hotels
A web-based portal allows managers to ensure ✓ electric security gate system Saudi ✓ time office attendance machine ✓ small hotel reservation software saudi ✓ basic accounting software for small business ✓ purchasing software for small business ✓ Face Recognition Access Control saudi. The access control system comes with an integrated Saudi Arabia parking management system that allows managers to monitor employee parking and shift scheduling.
https://www.prologicfirstss.com/blog-why-access-control-system-is-necessary-for-hotels.html
0 notes
Link
body temperature access control system abu dhabi , body temperature access control system in bur dubai , body temperature access control systems in sharjah , body temperature access control systems in alain, access control system in bur dubai , access control system in alain , access control system in abu dhabi , access control system in sharjah

body temperature access control system in uae , bio metric access control system in uae , bio metric machine dubai , door access control system in abu dhabi
#face detection system uae#face recognition access control systems uae#face recognition access control systems abu dhabi#face recognition access control systems sharjah#face recognition access control systems ajman#face recognition access control systems bur dubai#face recognition access control systems alain#face recognition access control systems usa#face recognition access control systems saudi arabia
0 notes
Link
As the battle against COVID-19 rages in Malaysia, a new population has become collateral damage: Rohingya refugees. A terrified public, instigated by political opportunists, has endorsed numerous anti-refugee online petitions that have gained well-distributed support across Malaysia’s ethnic spectrum. Although Malaysia once embraced these survivors of Myanmar’s genocidal regime, Rohingya refugees are now being called ungrateful, uncivilised and backward leeches. This public outcry has led to mass support for Malaysia turning away boats carrying Rohingya asylum seekers. Given that many Malaysians assume that all refugees from Myanmar are Rohingya, the petitions have supported Malaysia’s detention of thousands of undocumented migrants—even those holding UNHCR registration cards—whose fates are unclear.
Perceptions of Rohingya refugees as indolent and, more recently, as virus carriers emerge from simplistic discursive representations that materialise from and circulate far beyond Malaysia. A number of entities unwittingly mutually reinforce reductive depictions of Rohingya. Myanmar nationalists vehemently deny that Rohingya belong to the polity, since the latter are perceived to be different—Rohingya “look South Asian” and are Muslims in a Buddhist country. International media have incentives to tell (and sell) simple stories, while humanitarian agencies achieve efficiencies in aid delivery when they can treat every Rohingya as a replicable token of a common type. Rohingya elites themselves have reason to present a common and distinct Rohingya identity, as this contests the Myanmar state’s assertion that the Rohingya are simply interlopers from Bangladesh (“Bengalis”).
In the academic world, fieldwork with Rohingya documents significant internal differentiation. But this reality has been obscured by the lack of sustained study of the group, particularly because northern Rakhine (Arakan) state, the area to which Rohingya are indigenous, has been largely inaccessible to researchers. Academics have mostly only considered elite debates or recapitulated stories of misery in Burma.
The creation of a homogenous image of Rohingya obscures the ethnic community’s striking diversity: Rohingya do not share an identical dialect, do not all look the same, nor are even all Muslim. Such diversity is unsurprising—homogenous groups tend to be maintained only through coercion and control. Given the Myanmar state’s claims that Rohingya do not exist, counter-narratives claiming a unified identity also make perfect sense. What is noteworthy are the effects of these claims and counterclaims amid mass violence and dispossession. Those who do not conform to the narrow characteristics which allegedly distinguish the Rohingya are not only excluded from making identity claims, but also the protection afforded to recognised asylum seekers and refugees.
This post draws upon fieldwork in Malaysia, Bangladesh, Thailand and Yangon, Myanmar between 2017 and 2020 to describe processes of Rohingya identity (re)formation amid ethnic cleansing and attempted extermination. We focus on Rohingya elite discourses and the criteria used by humanitarian organisations to grant protections to refugees, to show how both co-produce a reified image of the Rohingya that is then represented in media and academic treatments. The disciplining of ethnic diversity in turn becomes internalised by Rohingya refugees, who self-reinforce the homogenisation of Rohingya identity.
In Myanmar, the ratification of an ethnic group as indigenous is the only method for securing recognition of substantive citizenship. The claim to citizenship rests in turn on the claim to an essential identity uniting the Rohingya. Self-appointed Rohingya leaders reject expressions of internal difference that might potentially undercut their identity’s supposed authenticity. Rohingya elites have identified particular religious, linguistic, territorial and cultural indicators to demarcate an ‘authentic’ Rohingya-ness that fits the racial ideology of the Myanmar state: Rohingya are Muslims, speak Rohingya, have their homeland in Rakhine state, and share both agrarian subsistence patterns (fishing and farming) and a village culture defined by segmentary clan-based kinship systems.
There are several problems with this description. The Rohingya have faced a half-century of systematic oppression by the Myanmar state, one that has precipitated waves of violent expulsions complemented by legal and symbolic erasure. It is arguably no longer possible to embody the narrow characteristics listed above. The growing displacement of Rohingya has disrupted clan systems and opportunities to learn language dialects, while severing intimate relationships between subsistence patterns and lands. For instance, the absence of vernacular print or radio hinders the standardisation of a dialect, facilitating evolutions in the Rohingya language (which was already subjected to significant regional variation). Moreover, as the putatively originary elements of Rohingya-ness intermix with host cultures across greater Asia (Saudi Arabia, Malaysia, Bangladesh and Pakistan, in particular), new variations of identity are produced. An essentialised “Rohingya-ness” can no longer be adequately performed.
Even if the mass uprooting of Rohingya had not transpired, such essentialism would still exclude some who identify as Rohingya. For instance, while Rohingya historian Ba Tha asserts that, “All Rohingya profess Islam,” Hindu Rohingya and the tiny but vocal Christian Rohingya community put paid to such blanket assertions. While these are arguably miniscule exceptions, they throw into relief a larger schism between a growing conservative strain of Islam and those Rohingya who espouse a syncretic Islam that blends animism and Hinduism. Some accounts attribute this expanding rift to Saudi Arabian influence, while others describe the increase in conservatism as a self-protective response to growing vulnerability.
As humanitarian and state apparatuses internalise essentialist definitions of Rohingya-ness, they become sieving machines separating ‘true’ Rohingya from ‘false’. Rejecting deviant Rohingya experiences, cultural practices and identities is problematic because it denies protection to those with legitimate claims to membership. Humanitarian regulatory processes and state discourses pressure Rohingya to perform and take up the traits that signify an “authentic” Rohingya. State elites such as Malaysia’s Najib and Bangladesh’s Sheikh Hasina have emphasised how Muslim countries must help Rohingya as they are fellow “Muslim brothers and sisters”. Rohingya consequently have an incentive to foreground a Muslim identity to qualify for the support of such states.
Meanwhile the UNHCR compels Rohingya to conform to narrow definitions of Rohingya-ness in order to access the identification documents that provide a modicum of protection in Malaysia. In interviews, Rohingya applicants for refugee status, translators and civil society leaders revealed some non-Rohingya applicants (Bangladeshis or Myanmar Muslims) have attained cards by paying bribes to translators or colluding with Rohingya applicants by “learning things about [Rohingya] areas in Rakhine state and paying to ‘join’ their family,” as one translator told us.
More importantly, Rohingya have reportedly been denied cards by not satisfying the agency’s expectations of ‘authentic’ Rohingya-ness. Cards have been allegedly refused to applicants who were deemed too educated, could not adequately relay geographical knowledge of Rakhine state or describe details about political events (pogroms against Rohingya, for example), or could not speak in the same Rohingya dialect as the UNHCR translator. Insistence on these qualities would particularly disadvantage Rohingya who spent most or all of their lives outside of Rakhine state.
Rohingya applicants rehearse the narratives of those who have successfully attained refugee status to prepare for the UNHCR interview. Kamal, a Rohingya who came to Malaysia through Bangladesh and Thailand in 2016, shared that: “My relative told me the questions the UNHCR asked. I practiced how to answer them with my relative, and I learnt some of the answers he gave so that I could be guaranteed success in getting the UN card.” The perceived need to “tell the same story” for fear of being denied refugee status reinforces the homogeneity of Rohingya-ness as an ethnic category, putting in doubt all narratives that stray from the dominant one.
Many who now see themselves as Rohingya only came to do so after the violence of the last decade, or from interacting with humanitarian agencies or host states—some had not even heard the name before. Hasinah, an older woman who fled Rakhine after the 2015 conflict, shared that she had only thought of herself as a Myanmar Muslim back in Sittwe. The discovery of her Rohingya identity took place when the UNHCR officer told her that she was Rohingya: “I only [learned] in Malaysia that because we are Rohingya, that’s why Myanmar wanted to kill us. Before this [back in Myanmar], I only thought it was because we are Muslims, and Buddhists hate Muslims.”
These experiences demonstrate how some Rohingya have begun to understand themselves through the parameters they encounter during state registration processes. They also show how the Rohingya category is enlarged by the incorporation of those who had not seen themselves as Rohingya before. Hasinah’s testimony reflects a shift in her identity, and how she relates to her world. In explaining the violence in Myanmar, her Rohingya identity becomes foregrounded over her general Muslim one. Hasinah’s experiences do not imply that all Rohingya were unaware of their ethnic identity or the basis of their persecution. Instead, narratives such as Hasinah’s reveal the diversity in Rohingya’s perspectives. They also point to the growing solidification of Rohingya-ness—to be Rohingya is also to be Muslim, thereby excluding the marginal voices of non-Muslim Rohingya.
“Those are Myanmar Muslims and Bangladeshis. Not Rohingya,” so declared a Malaysia-based Rohingya refugee in a May 2020 Facebook post, at pains to distinguish the Rohingya community from other refugee groups in Malaysia. If Rohingya were not already compelled to differentiate themselves, the COVID-19 pandemic has both produced and made more pronounced distinctions between Rohingya and other migrant communities. Adding to the pressure from humanitarian and state apparatuses, societal acceptance—and rejection—of Rohingya in Malaysia have led to the growing need among Rohingya refugees to present themselves as a docile subjects deserving of protection.
Allowing for alternative performances of Rohingya-ness not only allows for a broader and more complex understanding of Rohingya to emerge—a good in its own right. It accomplishes two additional goals. First, embracing Rohingya diversity forms a stronger basis for the articulation of collective political aspirations. The tactic of strategic essentialism has not worked due to the Myanmar state’s persistent denial of Rohingya as “inauthentic.” Embracing Rohingya diversity, by contrast, recognises their various complex historical and cultural entanglements with Rakhine state and Myanmar in general.
Second—and arguably more importantly for a stateless group of people who have been denied belonging and a homeland—flattening Rohingya-ness inevitably prevents many “deviant Rohingya” from claiming a name that has been denied by the Myanmar state. For some, the Rohingya identity is the only thing they have left. The Rohingya identity is a crucial aspect of their existence. A more fluid understanding of Rohingya—one that both allows more people to enter and more people to exit, but also permits people to inhabit both positions at once—would better reflect the immense challenges of living as Rohingya today.
54 notes
·
View notes
Text
Pluralistic, your daily link-dose: 28 Feb 2020

Today's links
Clearview AI's customer database leaks: Sic semper grifter.
The Internet of Anal Things: Recreating Stelarc's "Amplified Body" with an IoT butt-plug.
Oakland's vintage Space Burger/Giant Burger building needs a home! Adopt a googie today.
Fan-made reproduction of the Tower of Terror: Even has a deepfaked Serling.
Drawing the Simpsons with pure CSS: Impractical, but so impressive.
Let's Encrypt issues its billionth cert: 89% of the web is now encrypted.
AI Dungeon Master: A work in progress, for sure.
How to lie with (coronavirus) maps: Lies, damned lies, and epidemiological data-visualizations.
This day in history: 2019, 2015
Colophon: Recent publications, current writing projects, upcoming appearances, current reading
Clearview AI's customer database leaks (permalink)
Clearview is the grifty facial recognition startup that created a database by scraping social media and now offers cops secretive deals on its semi-magic, never-peer-reviewed technology. The company became notorious in January after the NYT did a deep dive into its secretive deals and its weird, Trump-adjascent ex-male-model founder.
(the Times piece was superbly researched but terribly credulous about Clearview's marketing claims)
https://www.nytimes.com/2020/01/18/technology/clearview-privacy-facial-recognition.html
Yesterday, Clearview warned its customers that it had been hacked and lost its customer database. Today, that customer database was published.
https://www.buzzfeednews.com/article/ryanmac/clearview-ai-fbi-ice-global-law-enforcement
It seems that the NYT weren't the only ones to take Clearview's marketing claims at face value. Its client list includes the DoJ, ICE, Macy's, Walmart, and the NBA. All in all the dump includes more than 2,200 users, including "law enforcement agencies, companies, and individuals around the world."
Included: state AGs, university rent-a-cops, and clients in Saudi Arabia.
"BuzzFeed News authenticated the logs, which list about 2,900 institutions and include details such as the number of log-ins, the number of searches, and the date of the last search."
What does Clearview, a sercurity company, say about this ghastly security breach? "Unfortunately, data breaches are part of life in the 21st century."
Big shrug energy.
"Government agents should not be running our faces against a shadily assembled database of billions of our photos in secret and with no safeguards against abuse," ACLU attorney Nathan Freed Wessler, said to BuzzFeed News.
It is amazing that this needs to be said.
"More than 50 educational institutions across 24 states named in the log. Among them are two high schools."
They are:
Central Montco Technical High School in Pennsylvania
Somerset Berkley Regional High School in Massachusetts
The log also has an entry for Interpol.

The Internet of Anal Things (permalink)
In 1994, the notorious/celebrated electronic artist Stelarc did a performance called "Amplified Body" in which he "controlled robots, cameras and other instruments by tensing and releasing his muscles"
https://web.archive.org/web/20120712181429/https://v2.nl/events/amplified-body

Now, artist/critic Dani Ploeger has revisited Amplified Body with his own performance, which is very similar to Stelarc's, except all the peripherals are controlled by Ploeger tensing and releasing his anal sphincters around a smart butt-plug.
https://www.daniploeger.org/amplified-body
He calls it "B-hind" and it's a ha-ha-only-serious. The buttplug is "an anal electrode with EMG sensor for domestic treatment of faecal incontinence," and the accompanying text is a kind of art-speak parody of IoT biz-speak.
https://we-make-money-not-art.com/b-hind-celebrating-the-internet-of-anal-things
"B-hind offers a unique IoT solution to fully integrate your sphincter muscle in everyday living. The revolutionary anal electrode-powered interface system replaces conventional hand/voice-based interaction, enabling advanced digital control rooted in your body's interior. Celebrating the abject and the grotesque, B‒hind facilitates simple, plug-and-play access to a holistic body experience in the age of networked society."
B-hind was produced in collaboration with V2_, the Lab for the Unstable Media in Rotterdam, and In4Art.

Oakland's vintage Space Burger/Giant Burger building needs a home! (permalink)
Giant Burger was once an East Bay institution, known for its burgers and its gorgeous googie architecture.
https://localwiki.org/oakland/Giant_Burger
One of the very last Giant Burger buildings is now under threat. Though the Telegraph Ave location was rescued in 2015 and converted to a "Space Burger," it's now seeking a new home because it is in the path of the Eastline project.
https://insidescoopsf.sfgate.com/blog/2015/02/24/space-burger-launches-in-uptown-oakland/
The Oakland Heritage Alliance is hoping someone will rescue and move the building: " Do you have an idea for a new location for this mid-century icon? Please contact [email protected] if you know of an appropriate lot, project, or site, preferably downtown."
(Image CC BY-SA, Our Oakland)

Fan-made reproduction of the Tower of Terror (permalink)
Orangele set out to re-create the Walt Disney World Twilight Zone Tower of Terror elevator loading zone in the entry area to their home theater. He's not only done an impressive re-make of the set, but he's also augmented it with FANTASTIC gimmicks.
https://www.hometheaterforum.com/community/threads/the-tower-of-terror-theater.365747/
It's not merely that's he's created a rain, thunder and lightning effect outside the patio doors…

https://www.youtube.com/watch?v=4QMzN0v4mJQ
Nor has he merely created props like this gimmicked side table that flips over at the press of a button.
https://www.youtube.com/watch?v=kY7gQLMnbeA

He's also created HIS OWN ROD SERLING DEEPFAKE.
https://www.youtube.com/watch?time_continue=2&v=MIsjYJwOXSU

I kinda seriously love that he left Rod's cigarette in. The Disney version looks…uncanny.
Not shown: "exploding fuse box with simulated smoke and fire, motorized lighted elevator dial, motorized/lighted pressure gauge, video monitor playing Tower of Terror ride sequence seen through the elevator door wrap, motorized "elevator door'"
He notes, "I was once married, but now as a single person, I can do whatever I want, haha. NEVER getting married again."

Drawing the Simpsons with pure CSS (permalink)
Implementing animated Simpsons illustrations in CSS isn't the most practical web-coding demo I've seen, but it's among the most impressive. Bravo, Chris Pattle!
(not shown: the eyes animate and blink!)
https://pattle.github.io/simpsons-in-css/
#bart .head .hair1 { top: 22px; left: 0px; width: 6px; height: 7px; -webkit-transform: rotate(-22deg) skew(-7deg, 51deg); -ms-transform: rotate(-22deg) skew(-7deg, 51deg); transform: rotate(-22deg) skew(-7deg, 51deg); }
I especially love the quick-reference buttons to see the raw CSS. It reminds me of nothing so much as the incredibly complex Logo programs I used to write on my Apple ][+ in the 1980s, drawing very complicated, vector-based sprites and glyphs.
https://github.com/pattle/simpsons-in-css/blob/master/css/bart.css
Most interesting is the way that this modular approach to graphics allows for this kind of simple, in-browser transformation.


Let's Encrypt issues its billionth cert (permalink)
When the AT&T whistleblower Mark Klein walked into EFF's offices in 2005 to reveal that his employers had ordered him to help the NSA spy on the entire internet, it was a bombshell.
https://www.eff.org/tags/mark-klein
The Snowden papers revealed the scope of the surveillance in fine and alarming detail. According to his memoir, Snowden was motivated to blow the whistle when he witnessed then-NSA Director James Clapper lie to Senator Ron Wyden about the Klein matter.
Since that day in 2005, privacy advocates have been fretting about just how EASY it was to spy on the whole internet. So much of that was down to the fact that the net wasn't encrypted by default.
This was especially keen for @EFF. After all, we made our bones by suing the NSA in the 90s and winning the right for civilians to access working cryptography (we did it by establishing that "Code is speech" for the purposes of the First Amendment).
https://www.eff.org/deeplinks/2015/04/remembering-case-established-code-speech
Crypto had been legal since 1992, but by Klein's 2005 disclosures, it was still a rarity. 8 years later — at the Snowden moment — the web was STILL mostly plaintext. How could we encrypt the web to save it from mass surveillance?
So in 2014, we joined forces with Mozilla, the University of Michigan and Akamai to create Let's Encrypt, a project to give anyone and everyone free TLS certificates, the key component needed to encrypt the requests your web-server exchanges with your readers.
https://en.wikipedia.org/wiki/Let%27s_Encrypt
Encrypting the web was an uphill climb: by 2017, Let's Encrypt had issued 100m certificates, tipping the web over so that the majority of traffic (58%) was encrypted. Today, Let's Encrypt has issued ONE BILLION certs, and 81% of pageloads use HTTPS (in the USA, it's 91%)! This is astonishing, bordering on miraculous. If this had been the situation back in 2005, there would have been no NSA mass surveillance.
Even more astonishing: there are only 11 full-timers on the Let's Encrypt team, plus a few outside contractors and part-timers. A group of people who could fit in a minibus managed to encrypt virtually the entire internet.
https://letsencrypt.org/2020/02/27/one-billion-certs.html
There are lots of reasons to factor technology (and technologists) in any plan for social change, but this illustrates one of the primary tactical considerations. "Architecture is Politics" (as Mitch Kapor said when he co-founded EFF), and the architectural choices that small groups of skilled people make can reach all the way around the world.
This kind of breathtaking power is what inspires so many people to become technologists: the force-multiplier effect of networked code can imbue your work with global salience (for good or ill). It's why we should be so glad of the burgeoning tech and ethics movement, from Tech Won't Build It to the Googler Uprising. And it's especially why we should be excited about the proliferation of open syllabi for teaching tech and ethics.
https://docs.google.com/spreadsheets/d/1jWIrA8jHz5fYAW4h9CkUD8gKS5V98PDJDymRf8d9vKI/edit#gid=0
It's also the reason I'm so humbled and thrilled when I hear from technologists that their path into the field started with my novel Little Brother, whose message isn't "Tech is terrible," but, "This will all be so great, if we don't screw it up."
https://craphound.com/littlebrother
(and I should probably mention here that the third Little Brother book, Attack Surface, comes out in October and explicitly wrestles with the question of ethics, agency, and allyship in tech).
https://us.macmillan.com/books/9781250757531

AI Dungeon Master (permalink)
Since 2018, Lara martin has been using machine learning to augment the job of the Dungeon Master, with the goal of someday building a fully autonomous, robotic DM.
https://laramartin.net/
AI Dungeon Master is a blend of ML techniques and "old-fashioned rule-based features" to create a centaur DM that augments a human DM's imagination with the power of ML, natural language processing, and related techniques.
She's co-author of a new paper about the effort, "Story Realization: Expanding Plot Events into Sentences" which "describes a way algorithms to use "events," consisting of a subject, verb, object, and other elements, to make a coherent narrative."
https://aaai.org/Papers/AAAI/2020GB/AAAI-AmmanabroluP.6647.pdf
The system uses training data (plots from Doctor Who, Futurama, and X-Files) to expand text-snippets into plotlines that continue the action. It's a bit of a dancing bear, though, an impressive achievement that's not quite ready for primetime ("We're nowhere close to this being a reality yet").
https://www.wired.com/story/forget-chess-real-challenge-teaching-ai-play-dandd/
This may bring to mind AI Dungeon, the viral GPT-2-generated dungeon crawler from December.
https://aidungeon.io/
As Will Knight writes, "Playing AI Dungeon often feels more like a maddening improv session than a text adventure."
Knight proposes that "AI DM" might be the next big symbolic challenge for machine learning, the 2020s equivalent to "AI Go player" or "AI chess master."
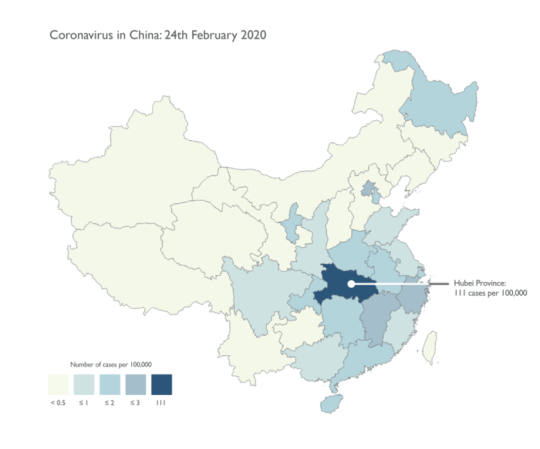
How to lie with (coronavirus) maps (permalink)
The media around the coronavirus outbreak is like a masterclass in the classic "How to Lie With Maps."
https://www.press.uchicago.edu/ucp/books/book/chicago/H/bo27400568.html
Self-described "cartonerd" Kenneth Field's prescriptions for mapmakers wanting to illustrate the spread of coronavirus is a superb read about data visualization, responsibility, and clarity.
https://www.esri.com/arcgis-blog/products/product/mapping/mapping-coronavirus-responsibly/
Both of these images are representing the same data. Look at the map and you might get the impression that coronavirus infections are at high levels across all of China's provinces. Look at the bar-chart and you'll see that it's almost entire Hubei.
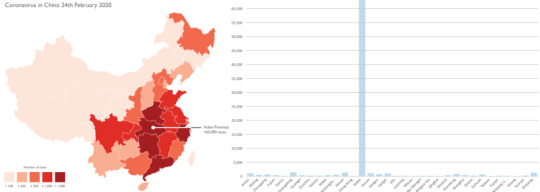
Here's a proposed way to represent the same data on a map without misleading people.

Another point that jumped out: stop coloring maps in red!
"We're mapping a human health tragedy that may get way worse before it subsides. Do we really want the map to be screaming bright red? Red can connotate death, still statistically extremely rare for coronavirus."

This day in history (permalink)
#5yrsago Ad-hoc museums of a failing utopia: photos of Soviet shop-windows https://boingboing.net/2015/02/28/ad-hoc-museums-of-a-failing-ut.html
#5yrsago First-hand reports of torture from Homan Square, Chicago PD's "black site" https://www.theguardian.com/us-news/2015/feb/27/chicago-abusive-confinment-homan-square
#1yrago EFF's roadmap for a 21st Century antitrust doctrine https://www.eff.org/deeplinks/2019/02/antitrust-enforcement-needs-evolve-21st-century
#1yrago Yet another study shows that the most effective "anti-piracy" strategy is good products at a fair price https://www.vice.com/en_us/article/3kg7pv/studies-keep-showing-that-the-best-way-to-stop-piracy-is-to-offer-cheaper-better-alternatives
#1yrago London's awful estate agents are cratering, warning of a "prolonged downturn" in the housing market https://www.bbc.com/news/business-47389160
#1yrago Bad security design made it easy to spy on video from Ring doorbells and insert fake video into their feeds https://web.archive.org/web/20190411195308/https://dojo.bullguard.com/dojo-by-bullguard/blog/ring/
#1yrago Amazon killed Seattle's homelessness-relief tax by threatening not to move into a massive new building, then they canceled the move anyway https://www.seattletimes.com/business/amazon/huge-downtown-seattle-office-space-that-amazon-had-leased-is-reportedly-put-on-market/
#1yrago The "Reputation Management" industry continues to depend on forged legal documents https://www.techdirt.com/articles/20190216/15544941616/pissed-consumer-exposes-new-york-luxury-car-dealers-use-bogus-notarized-letters-to-remove-critical-reviews.shtml

Colophon (permalink)
Today's top sources: Allegra of Oakland Heritage Alliance, Waxy (https://waxy.org/), We Make Money Not Art (https://we-make-money-not-art.com/), Sam Posten (https://twitter.com/Navesink), Slashdot (https://slashdot.org), Kottke (https://kottke.org) and Four Short Links (https://www.oreilly.com/feed/four-short-links).
Hugo nominators! My story "Unauthorized Bread" is eligible in the Novella category and you can read it free on Ars Technica: https://arstechnica.com/gaming/2020/01/unauthorized-bread-a-near-future-tale-of-refugees-and-sinister-iot-appliances/
Upcoming appearances:
Canada Reads Kelowna: March 5, 6PM, Kelowna Library, 1380 Ellis Street, with CBC's Sarah Penton https://www.eventbrite.ca/e/cbc-radio-presents-in-conversation-with-cory-doctorow-tickets-96154415445
Currently writing: I just finished a short story, "The Canadian Miracle," for MIT Tech Review. It's a story set in the world of my next novel, "The Lost Cause," a post-GND novel about truth and reconciliation. I'm getting geared up to start work on the novel now, though the timing is going to depend on another pending commission (I've been solicited by an NGO) to write a short story set in the world's prehistory.
Currently reading: Just started Lauren Beukes's forthcoming Afterland: it's Y the Last Man plus plus, and two chapters in, it's amazeballs. Last week, I finished Andrea Bernstein's "American Oligarchs" this week; it's a magnificent history of the Kushner and Trump families, showing how they cheated, stole and lied their way into power. I'm getting really into Anna Weiner's memoir about tech, "Uncanny Valley." I just loaded Matt Stoller's "Goliath" onto my underwater MP3 player and I'm listening to it as I swim laps.
Latest podcast: Gopher: When Adversarial Interoperability Burrowed Under the Gatekeepers' Fortresses: https://craphound.com/podcast/2020/02/24/gopher-when-adversarial-interoperability-burrowed-under-the-gatekeepers-fortresses/
Upcoming books: "Poesy the Monster Slayer" (Jul 2020), a picture book about monsters, bedtime, gender, and kicking ass. Pre-order here: https://us.macmillan.com/books/9781626723627?utm_source=socialmedia&utm_medium=socialpost&utm_term=na-poesycorypreorder&utm_content=na-preorder-buynow&utm_campaign=9781626723627
(we're having a launch for it in Burbank on July 11 at Dark Delicacies and you can get me AND Poesy to sign it and Dark Del will ship it to the monster kids in your life in time for the release date).
"Attack Surface": The third Little Brother book, Oct 20, 2020.
"Little Brother/Homeland": A reissue omnibus edition with a very special, s00per s33kr1t intro.
7 notes
·
View notes
Text
Transforming Identification and Security in Jeddah, Riyadh, and KSA
Face recognition, aided by advanced technologies, is revolutionizing the identification and security, not just for Jeddah, Riyadh, but all across the Kingdom of Saudi Arabia (KSA). The innovative biometric technology uses artificial intelligence to identify video or digital images of faces to create a picture and provide a multitude of benefits in terms safety, efficiency, and ease of use. Recent years have seen the rise of facial recognition has attracted a great deal of interest due to its ability to improve security and simplify various application.
Understanding Facial Recognition Technology
Face recognition software works by analyzing unique facial features of the people in photographs or video clips. The features then are examined with a database of identified faces to authenticate the identities of people. The process is based on advanced algorithms to accurately differentiate the faces of individuals, and even account for the variations in light, angles or facial expressions.
Integration into Access Control Systems
The most powerful uses of technology for facial recognition is in its integration into security systems for access. Through the installation of facial recognition systems in entry points companies are able to enhance their security substantially. They provide an easy and reliable method for securing your identity that can replace traditional methods for authentication, such as passwords or keycards.
For corporate settings such as workplaces employees have access to secure areas through a face recognition camera. This eliminates the requirement to carry keypads or access card. Similar to public places like airports and government offices the use of facial recognition technology can enhance security measures by rapidly in identifying authorized persons and alerting possible security risks.
Enhanced Surveillance Capabilities
The technology of facial recognition also is a key element in the improvement of surveillance capability across cities as well as vital infrastructure. Security cameras that have facial recognition technology can successfully detect areas of high activity, and identify those of concern in real-time. This method of surveillance that is proactive allows law enforcement authorities to react quickly to security issues or follow the movement of individuals suspected of being in the area.
0 notes
Text
Healthcare Biometrics Market 2021 | Business Opportunity, Growth Strategies & Forecast Report By 2027
The Healthcare Biometrics Market Report, in its latest update, highlights the significant impacts and the recent strategical changes under the present socio-economic scenario. The Healthcare Biometrics industry growth avenues are deeply supported by exhaustive research by the top analysts of the industry. The report starts with the executive summary, followed by a value chain and marketing channels study. The report then estimates the CAGR and market revenue of the global and regional segments.
Base Year: 2020
Estimated Year: 2021
Forecast Till: 2027
The report classifies the market into different segments based on type and product. These segments are studied in detail, incorporating the market estimates and forecasts at regional and country levels. The segment analysis is helpful in understanding the growth areas and potential opportunities of the market.
Get | Download FREE Sample Report of Global Healthcare Biometrics Market @ https://www.decisiondatabases.com/contact/download-sample-6264
A special section is dedicated to the analysis of the impact of the COVID-19 pandemic on the growth of the Healthcare Biometrics market. The impact is closely studied in terms of production, import, export, and supply.
The report covers the complete competitive landscape of the Worldwide Healthcare Biometrics market with company profiles of key players such as:
3M Cogent, Inc.
Aware, Inc.
BIO-key International, Inc.
Cross Match Technologies, Inc.
DigitalPersona, Inc.
Fujitsu Ltd.
Lumidigm, Inc.
M2SYS LLC
NEC Corporation
SAFRAN SA
Siemens AG
Suprema, Inc.
ZKTeco, Inc
Want to add more Company Profiles to the Report? Write your Customized Requirements to us @ https://www.decisiondatabases.com/contact/get-custom-research-6264
Healthcare Biometrics Market Analysis by Technology:
Face Recognition
Iris Recognition
Hand Recognition
Voice Recognition
Fingerprint Recognition
Automated Fingerprint Identification Systems (AFIS)
Non-Automated Fingerprint Identification Systems (Non-AFIS)
Vein Recognition
Signature Recognition
Other Techniques
Healthcare Biometrics Market Analysis by Application:
Logical Access Control
Physical Access Control
Transaction Authentication
Healthcare Biometrics Market Analysis by Geography:
North America (USA, Canada, and Mexico)
Europe (Germany, UK, France, Italy, Russia, Spain, Rest of Europe)
Asia Pacific (China, India, Japan, South Korea, Australia, South-East Asia, Rest of Asia-Pacific)
Latin America (Brazil, Argentina, Peru, Chile, Rest of Latin America)
The Middle East and Africa (Saudi Arabia, UAE, Israel, South Africa, Rest of the Middle East and Africa)
Key questions answered in the report:
What is the expected growth of the Healthcare Biometrics market between 2022 to 2027?
Which application and type segment holds the maximum share in the Global Healthcare Biometrics market?
Which regional Healthcare Biometrics market shows the highest growth CAGR between 2022 to 2027?
What are the opportunities and challenges currently faced by the Healthcare Biometrics market?
Who are the leading market players and what are their Strengths, Weakness, Opportunities, and Threats (SWOT)?
What business strategies are the competitors considering to stay in the Healthcare Biometrics market?
Purchase the Complete Global Healthcare Biometrics Market Research Report @ https://www.decisiondatabases.com/contact/buy-now-6264
About Us:
DecisionDatabases.com is a global business research report provider, enriching decision-makers, and strategists with qualitative statistics. DecisionDatabases.com is proficient in providing syndicated research reports, customized research reports, company profiles, and industry databases across multiple domains. Our expert research analysts have been trained to map client’s research requirements to the correct research resource leading to a distinctive edge over its competitors. We provide intellectual, precise, and meaningful data at a lightning speed.
For more details:
DecisionDatabases.com
E-Mail: [email protected]
Phone: +91 90 28 057900
Web: https://www.decisiondatabases.com/
0 notes
Text
Global Critical Infrastructure Protection Market Size, Status and Forecast 2021-2027
The Critical Infrastructure Protection market is segmented by security technologies, services, vertical, and region. The security technologies component is estimated to have the largest market size in 2017, due to the need for perimeter security, video surveillance, access control, and identity management technologies. Access control methodologies, such as smart card, Radio Frequency Identification (RFID) cards, and biometrics, are needed for authenticating personnel and restricting intruders. Biometric systems based on single factor authentication, such as face recognition, fingerprint recognition, and iris recognition, and multifactor authentication methodologies are also witnessing increased adoption for border and control surveillance Moreover, the services segment is expected to grow at the highest CAGR during the forecast period. An increasing demand from large Enterprises and SMEs from diverse industry verticals to safeguard their premises from physical threats and cyber system environment from advanced threats, such as malware, ransomware, and advanced persistent threats has led to the growth of the CIP market.
Market Analysis and Insights: Global Critical Infrastructure Protection Market
Download FREE Sample of this Report @ https://www.grandresearchstore.com/report-sample/global-critical-infrastructure-protection-2021-2027-109
The global Critical Infrastructure Protection market size is projected to reach US$ 153550 million by 2027, from US$ 105050 million in 2020, at a CAGR of 5.5% during 2021-2027.
With industry-standard accuracy in analysis and high data integrity, the report makes a brilliant attempt to unveil key opportunities available in the global Critical Infrastructure Protection market to help players in achieving a strong market position. Buyers of the report can access verified and reliable market forecasts, including those for the overall size of the global Critical Infrastructure Protection market in terms of revenue.
On the whole, the report proves to be an effective tool that players can use to gain a competitive edge over their competitors and ensure lasting success in the global Critical Infrastructure Protection market. All of the findings, data, and information provided in the report are validated and revalidated with the help of trustworthy sources. The analysts who have authored the report took a unique and industry-best research and analysis approach for an in-depth study of the global Critical Infrastructure Protection market.
Global Critical Infrastructure Protection Scope and Market Size
Critical Infrastructure Protection market is segmented by company, region (country), by Type, and by Application. Players, stakeholders, and other participants in the global Critical Infrastructure Protection market will be able to gain the upper hand as they use the report as a powerful resource. The segmental analysis focuses on revenue and forecast by Type and by Application in terms of revenue and forecast for the period 2016-2027.
Segment by Type
Security Technologies
Services
Segment by Application
Risk Management Services
Consulting Services
Managed Services
Maintenance and Support Services
By Region
North America
U.S.
Canada
Europe
Germany
France
U.K.
Italy
Russia
Nordic
Rest of Europe
Asia-Pacific
China
Japan
South Korea
Southeast Asia
India
Australia
Rest of Asia
Latin America
Mexico
Brazil
Rest of Latin America
Middle East & Africa
Turkey
Saudi Arabia
UAE
Rest of MEA
By Company
Bae Systems
General Dynamics
Honeywell
Lockheed Martin
Northrop Grumman
Raytheon
Airbus
Hexagon AB
Johnson Controls
Thales Group
Teltronic
Optasense
MotoRoLA Solutions
Huawei
Get the Complete Report & TOC @ https://www.grandresearchstore.com/ict-and-media/global-critical-infrastructure-protection-2021-2027-109
Table of content
1 Report Overview
1.1 Study Scope
1.2 Market Analysis by Type
1.2.1 Global Critical Infrastructure Protection Market Size Growth Rate by Type: 2016 VS 2021 VS 2027
1.2.2 Security Technologies
1.2.3 Services
1.3 Market by Application
1.3.1 Global Critical Infrastructure Protection Market Share by Application: 2016 VS 2021 VS 2027
1.3.2 Risk Management Services
1.3.3 Consulting Services
1.3.4 Managed Services
1.3.5 Maintenance and Support Services
1.4 Study Objectives
1.5 Years Considered
2 Global Growth Trends
2.1 Global Critical Infrastructure Protection Market Perspective (2016-2027)
2.2 Critical Infrastructure Protection Growth Trends by Regions
2.2.1 Critical Infrastructure Protection Market Size by Regions: 2016 VS 2021 VS 2027
2.2.2 Critical Infrastructure Protection Historic Market Share by Regions (2016-2021)
2.2.3 Critical Infrastructure Protection Forecasted Market Size by Regions (2022-2027)
2.3 Critical Infrastructure Protection Industry Dynamic
2.3.1 Critical Infrastructure Protection Market Trends
2.3.2 Critical Infrastructure Protection Market Drivers
2.3.3 Critical Infrastructure Protection Market Challenges
2.3.4 Critical Infrastructure Protection Market Restraints
3 Competition Landscape by Key Players
3.1 Global Top Critical Infrastructure Protection Players by Revenue
CONTACT US:
276 5th Avenue, New York , NY 10001,United States
International: (+1) 646 781 7170 / +91 8087042414
Email: [email protected]
Follow Us On linkedin :- https://www.linkedin.com/company/grand-research-store/
0 notes
Text
facial recognition systems in abu dbabi
facial recognition devices in UAE
facial recognition devices in Abu Dhabi
facial recognition devices in Sharjah
facial recognition devices in Ajman
facial recognition devices in Alain
facial recognition devices in Oman
facial recognition software abu dhabi
facial recognition software Saudi Arabia
facial recognition software in Ajman
facial recognition software bur dubai
facial recognition software sharjah
#facial recognition access control#facial recognition devices#facial recognition systems#facial recognition software#facial recognition#facial recognition Abu Dhabi#facial recognition Sharjah#facial recognition Ajman#facial recognition Bur Dubai#facial recognition Alain#facial recognition in bur dubai#facial recognition in ajman#facial recognition software uae#facial recognition systems in abu dbabi#facial recognition systems in alain#facial recognition systems in bur dubai#facial recognition systems in sharjah#facial recognition systems bur dubai#facial recognition systems in abu dhabi
0 notes
Text
Automotive Labels Market is Growing at a Significant Rate in the Forecast Period 2020-2027|Key Competitors 3M, Avery Dennison Corporation, CCL Industries Ltd, UPM Raflatac, Sika AG, Dunmore, ImageTek labels, Lintec Corporation, Tesa SE- A Beiersdorf Company
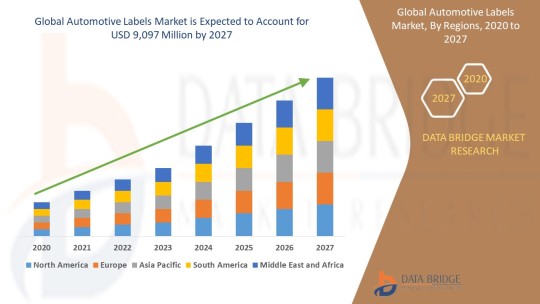
Automotive Labels market is valued at USD 6,300 million in 2019 and is expected to reach USD 9,097 million by 2027 witnessing market growth at a rate of 4.7%% in the forecast period of 2020 to 2027. Data Bridge Market Research report on automotive labels market provides analysis and insights regarding the various factors expected to be prevalent throughout the forecasted period while providing their impacts on the market’s growth.Labelling means assigning short names to the product to differentiate them from another product or another brand. Automotive labels are the labels used in automotive for brand recognition to differentiate their brand from other brands and to create a brand image in the market. The automotive labels are also used for the identification of the different parts for information and safety concerns. The very important factor for the growth of the market is rising demand for automobile among the people. The companies which are in this business now-a-days are using labels for parts identification, branding. This is the driving factor of the market. The increase in security and tagging markets to secure products from different brands labelling is done on the respective brand of product. For security reasons labelling is necessary for the parts in automotive industry.
The cost of raw materials which is required for the manufacturing of the automotive labels is very high and hence this is the restraining factor for the growth of the market. The small players which are suppliers of the parts to the major players is hard to achieve economies of scale and is very competitive for them. They cannot afford high level of labelling to the parts manufactured by them. This is the restraining factor to them. This automotive labels market report provides details of new recent developments, trade regulations, import export analysis, production analysis, value chain optimization, market share, impact of domestic and localised market players, analyses opportunities in terms of emerging revenue pockets, changes in market regulations, strategic market growth analysis, market size, category market growths, application niches and dominance, product approvals, product launches, geographic expansions, technological innovations in the market. To gain more info on Data Bridge Market Research automotive labels market contact us for an Analyst Brief, our team will help you take an informed market decision to achieve market growth.
Global Automotive Labels Market By Type (Warning & Safety Labels, Asset Labels, Branding, Dome and Other Labels), Raw Material (Polypropylene, Polyethylene, Terephthalate, Polyvinyl Chloride, Polycarbonate and Others), Identification Technology (Barcode, RFID and Others), Printing Technology (Flexography, Offset, Digital Printing, Screen Printing and Others), Mechanism (Pressure Sensitive, Heat Transfer and Others), Vehicle Type (Passenger Car and Commercial Vehicle), Country (U.S., Canada, Mexico, Brazil, Argentina, Rest of South America, Germany, Italy, U.K., France, Spain, Netherlands, Belgium, Switzerland, Turkey, Russia, Rest of Europe, Japan, China, India, South Korea, Australia, Singapore, Malaysia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific, Saudi Arabia, U.A.E, South Africa, Egypt, Israel, Rest of Middle East and Africa) Industry Trends and Forecast to 2027 Automotive labels market competitive landscape provides details by competitor. Details included are company overview, company financials, revenue generated, market potential, investment in research and development, new market initiatives, regional presence, company strengths and weaknesses, product launch, product width and breadth, application dominance. The above data points provided are only related to the companies’ focus related to automotive labels market.
Get Sample PDF of Automotive Labels Market Report (including COVID19 Impact Analysis) @https://www.databridgemarketresearch.com/request-a-sample/?dbmr=global-automotive-labels-market
FACTORS DRIVING GROWTH IN AUTOMOTIVE LABELS MARKET:
Growth of the Automobile Industry:
According to SIAM (Society of Indian Automobile Manufacturers), in the year of April 2016- March 2017 25.32 million vehicles were produced in India. This number rose to 29.07 million vehicles in April 2017-March 2018. This significant rise of the number of vehicles produced is evidence to the rising requirement of automotive labels globally. This number included passenger, commercial, three wheelers and two wheelers vehicle produced throughout the country. With the regulations posed by the governments to clearly identify the equipment and components in the vehicles with labels, and continuous rise in the demand for vehicles the market for automotive labels is expected to rise due to this factor.
Global Automotive Labels Market Scope and Market Size:
Automotive labels market is segmented on the basis of type, raw material, identification technology, printing technology, mechanism and vehicle type. The growth among segments helps you analyze niche pockets of growth and strategies to approach the market and determine your core application areas and the difference in your target markets. Automotive labels market on the basis of type has been segmented as warning & safety labels, asset labels, branding, dome and other labels. Based on raw material, automotive labels market has been segmented into polypropylene, polyethylene, terephthalate, polyvinyl chloride, polycarbonate and others. On the basis of identification technology, automotive labels market has been segmented into barcode, RFID and others. On the basis of printing technology, automotive labels market has been segmented into flexography, offset, digital printing, screen printing and others. Automotive Labels market has also been segmented on the basis of mechanism into pressure sensitive, heat transfer and others. According to vehicle type, automotive labels market is classified into passenger cars and commercial vehicle.
Key Market Competitors:
The major players covered in the automotive labels market report are 3M, Avery Dennison Corporation, CCL Industries Ltd, UPM Raflatac, Sika AG, Dunmore, ImageTek labels, Lintec Corporation, Tesa SE- A Beiersdorf Company, Lewis Label Products, Seiko Holdings Corporation, Automotive Labels International, Sandora Sales and Manufacturing Ltd., Honeywell International Inc., Polylabel, Intertronics, OpSec Security Group Ltd., H.B. Fuller Company, Constania, FLEXcon Company Inc., Bemis Company Inc., Adhesive Research Inc., Brady Worldwide Inc., Resource Label Group, Precision Contract Manufacturing, among other domestic and global players. Market share data is available for global, North America, Europe, Asia-Pacific (APAC), Middle East and Africa (MEA) and South America separately. DBMR analysts understand competitive strengths and provide competitive analysis for each competitor separately.
MAJOR TOC OF THE REPORT:
Chapter One: Automotive Labels Market Overview
Chapter Two: Manufacturers Profiles
Chapter Three: Automotive Labels Market Competition, by Players
Chapter Four: Automotive Labels Market Size by Regions
Chapter Five: Automotive Labels Market Revenue by Countries
Chapter Six: Automotive Labels Market Revenue by Type
Chapter Seven: Automotive Labels Market Revenue by Application
Chapter Eight: Automotive Labels Market Revenue by Industries
Chapter Nine: Automotive Labels Market Revenue by Deployment Model
Chapter Ten: Automotive Labels Market Revenue by End User
Get Table of Content on Request @ https://www.databridgemarketresearch.com/toc/?dbmr=global-aluminum-foil-market
Reasons for buying this Global Automotive Labels Market:
Laser Capture Global Automotive Labels Market aids in understanding the crucial product segments and their perspective.
Initial graphics and exemplified that a SWOT evaluation of large sections supplied from the Laser Capture Global Automotive Labels Market.
Even the Laser Capture Global Automotive Labels Market economy provides pin line evaluation of changing competition dynamics and retains you facing opponents.
This report provides a more rapid standpoint on various driving facets or controlling Medical Robotic System promote advantage.
This worldwide Locomotive report provides a pinpoint test for shifting dynamics that are competitive.
The key questions answered in this report:
What will be the Market Size and Growth Rate in the forecast year?
What is the Key Factors driving Laser Global Automotive Labels Market?
What are the Risks and Challenges in front of the market?
Who are the Key Vendors in Global Automotive Labels Market?
What are the Trending Factors influencing the market shares?
What is the Key Outcomes of Porter’s five forces model
Access Full Report https://www.databridgemarketresearch.com/reports/global-automotive-labels-market
Browse Related Report:
Industrial Labels Market
Security Labels Market
Sensormatic Labels Market
About Us:
Data Bridge Market Research set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market
Contact:
Data Bridge Market Research
Tel: +1-888-387-2818
Email: [email protected]
0 notes
Text
Automotive And Security Segment Trends For the Coming Years
Pharmaceutical and biotechnology companies are making biometric vehicle access systems available to protect personnel and cargo in transport settings. An employee in the passenger seat of a commercial truck could be carrying weapons or dangerous chemicals. Drivers in buses, trains and airplanes have to make numerous stops every day to allow passengers to get off. Passengers would not be allowed to board if their identification did not match the fingerprint or voice recognition system read from the biometric vehicle access database. This would make entering restricted areas very difficult.
Biometric vehicle access systems would also prevent crime from occurring. With the use of biometric vehicle access research systems inside passenger vehicles, automotive companies can increase their fleet security and cut down on employee theft. With the potential for fraudulent use of biometric readouts, some employees may attempt to forge the signatures of authorized officers to gain access to restricted areas. Employees would not be able to board a train or airplane with a false fingerprint. By requiring employees to show their fingerprints or voice recognition ID when they enter a secure area, automobile manufacturers are reducing the potential for employee fraud.
The world is currently experiencing one of the largest advancements in biometric security technology in over a decade. Trends indicate that the global biometric vehicle access market will continue to expand at an accelerated rate through 2010. The two major factors driving this trend include increasing demand and security. High demand is due to the fact that biometric systems require minimal training for users and no special equipment or clothing to wear while accessing the systems.
Security is also a major factor in the forecast period because increased safety for people inside automobiles, along with biometric access control systems, could decrease the costs of insurance and eliminate the need for annual vehicle inspections. Insurance estimates are expected to drop 25 percent due to these biometric vehicle access controls. In addition to the insurance industry, transportation agencies and airlines are expecting to benefit from biometric vehicle access systems. This will allow passengers to make changes in flight schedules and improve airline passenger security. The airlines have the ability to identify passengers using biometric scans and reduce the risk of lost luggage and missed flights by implementing biometric screening processes.
Another research study that forecasting the global biometric market in the near future was prepared by an industry association known as the National Institute of Standards and Technology (NISET). The association presented its study to NICE, the United Kingdom's government agency responsible for regulating the biometric technology industry. The forecast indicates that biometric technology applications are expected to reach over $1.5 billion by the end of 2012. This represents a tremendous growth in the biometric technology market and shows the potential demand that can be realized if a company can successfully capitalize on this growing market.
Based on the above research studies, it is evident that the UK and other global markets can realize significant benefits if biometric vehicle access control systems are implemented. However, biometric technology is not a silver bullet. It does not eliminate all potential security challenges. Companies need to incorporate other security measures in order to achieve full deployment of biometric technologies. This is the reason why the forecast for the coming years shows growth in the global biometric technology sector.
The research team projects that the Vehicle Biometric Vehicle Access System market size will grow from XXX in 2020 to XXX by 2027, at an estimated CAGR of XX. The base year considered for the study is 2020, and the market size is projected from 2020 to 2027.
The prime objective of this report is to help the user understand the market in terms of its definition, segmentation, market potential, influential trends, and the challenges that the market is facing with 10 major regions and 50 major countries. Deep researches and analysis were done during the preparation of the report. The readers will find this report very helpful in understanding the market in depth. The data and the information regarding the market are taken from reliable sources such as websites, annual reports of the companies, journals, and others and were checked and validated by the industry experts. The facts and data are represented in the report using diagrams, graphs, pie charts, and other pictorial representations. This enhances the visual representation and also helps in understanding the facts much better.
By Market Players:
BioEnable
Techshino
Miaxis
Nymi
Sonavation
BIODIT
Denso
EyeLock
FPC
Fujitsu
HID Global
IriTech
KeyLemon
NEC
Nuance
Olea Sensor Networks
Safran
Synaptics
VOXX
By Type
Palm Print
Facial
Fingerprint
Iris
Others
By Application
Commercial Vehicle
Passenger Car
Others
By Regions/Countries:
North America
United States
Canada
Mexico
East Asia
China
Japan
South Korea
Europe
Germany
United Kingdom
France
Italy
Russia
Spain
Netherlands
Switzerland
Poland
South Asia
India
Pakistan
Bangladesh
Southeast Asia
Indonesia
Thailand
Singapore
Malaysia
Philippines
Vietnam
Myanmar
Middle East
Turkey
Saudi Arabia
Iran
United Arab Emirates
Israel
Iraq
Qatar
Kuwait
Oman
Africa
Nigeria
South Africa
Egypt
Algeria
Morocoo
Oceania
Australia
New Zealand
South America
Brazil
Argentina
Colombia
Chile
Venezuela
Peru
Puerto Rico
Ecuador
Rest of the World
Kazakhstan
Points Covered in The Report
The points that are discussed within the report are the major market players that are involved in the market such as market players, raw material suppliers, equipment suppliers, end users, traders, distributors and etc.
The complete profile of the companies is mentioned. And the capacity, production, price, revenue, cost, gross, gross margin, sales volume, sales revenue, consumption, growth rate, import, export, supply, future strategies, and the technological developments that they are making are also included within the report. This report analyzed 12 years data history and forecast.
The growth factors of the market is discussed in detail wherein the different end users of the market are explained in detail.
Data and information by market player, by region, by type, by application and etc, and custom research can be added according to specific requirements.
The report contains the SWOT analysis of the market. Finally, the report contains the conclusion part where the opinions of the industrial experts are included.
Key Reasons to Purchase
To gain insightful analyses of the market and have comprehensive understanding of the global market and its commercial landscape.
Assess the production processes, major issues, and solutions to mitigate the development risk.
To understand the most affecting driving and restraining forces in the market and its impact in the global market.
Learn about the market strategies that are being adopted by leading respective organizations.
To understand the future outlook and prospects for the market.
Besides the standard structure reports, we also provide custom research according to specific requirements.
The report focuses on Global, Top 10 Regions and Top 50 Countries Market Size of Vehicle Biometric Vehicle Access System 2016-2021, and development forecast 2022-2027 including industries, major players/suppliers worldwide and market share by regions, with company and product introduction, position in the market including their market status and development trend by types and applications which will provide its price and profit status, and marketing status & market growth drivers and challenges, with base year as 2020.
Key Indicators Analysed
Market Players & Competitor Analysis: The report covers the key players of the industry including Company Profile, Product Specifications, Production Capacity/Sales, Revenue, Price and Gross Margin 2016-2021 & Sales by Product Types.
Global and Regional Market Analysis: The report includes Global & Regional market status and outlook 2022-2027. Further the report provides break down details about each region & countries covered in the report. Identifying its production, consumption, import & export, sales volume & revenue forecast.
Market Analysis by Product Type: The report covers majority Product Types in the Vehicle Biometric Vehicle Access System Industry, including its product specifcations by each key player, volume, sales by Volume and Value (M USD).
Markat Analysis by Application Type: Based on the Vehicle Biometric Vehicle Access System Industry and its applications, the market is further sub-segmented into several major Application of its industry. It provides you with the market size, CAGR & forecast by each industry applications.
Market Trends: Market key trends which include Increased Competition and Continuous Innovations.
Opportunities and Drivers: Identifying the Growing Demands and New Technology
Porters Five Force Analysis: The report will provide with the state of competition in industry depending on five basic forces: threat of new entrants, bargaining power of suppliers, bargaining power of buyers, threat of substitute products or services, and existing industry rivalry.
COVID-19 Impact
Report covers Impact of Coronavirus COVID-19: Since the COVID-19 virus outbreak in December 2019, the disease has spread to almost every country around the globe with the World Health Organization declaring it a public health emergency. The global impacts of the coronavirus disease 2019 (COVID-19) are already starting to be felt, and will significantly affect the Vehicle Biometric Vehicle Access System market in 2021. The outbreak of COVID-19 has brought effects on many aspects, like flight cancellations; travel bans and quarantines; restaurants closed; all indoor/outdoor events restricted; over forty countries state of emergency declared; massive slowing of the supply chain; stock market volatility; falling business confidence, growing panic among the population, and uncertainty about future.
Global Vehicle Biometric Vehicle Access System Market Research Report 2021 Professional Edition Market report offers great insights of the market and consumer data and their interpretation through various figures and graphs. Report has embedded global market and regional market deep analysis through various research methodologies. The report also offers great competitor analysis of the industries and highlights the key aspect of their business like success stories, market development and growth rate.
Contact us: https://www.reportmines.com/contact-us.php
0 notes
Text
Automotive And Security Segment Trends For the Coming Years
Pharmaceutical and biotechnology companies are making biometric vehicle access systems available to protect personnel and cargo in transport settings. An employee in the passenger seat of a commercial truck could be carrying weapons or dangerous chemicals. Drivers in buses, trains and airplanes have to make numerous stops every day to allow passengers to get off. Passengers would not be allowed to board if their identification did not match the fingerprint or voice recognition system read from the biometric vehicle access database. This would make entering restricted areas very difficult.
Biometric vehicle access systems would also prevent crime from occurring. With the use of biometric vehicle access research systems inside passenger vehicles, automotive companies can increase their fleet security and cut down on employee theft. With the potential for fraudulent use of biometric readouts, some employees may attempt to forge the signatures of authorized officers to gain access to restricted areas. Employees would not be able to board a train or airplane with a false fingerprint. By requiring employees to show their fingerprints or voice recognition ID when they enter a secure area, automobile manufacturers are reducing the potential for employee fraud.
The world is currently experiencing one of the largest advancements in biometric security technology in over a decade. Trends indicate that the global biometric vehicle access market will continue to expand at an accelerated rate through 2010. The two major factors driving this trend include increasing demand and security. High demand is due to the fact that biometric systems require minimal training for users and no special equipment or clothing to wear while accessing the systems.
Security is also a major factor in the forecast period because increased safety for people inside automobiles, along with biometric access control systems, could decrease the costs of insurance and eliminate the need for annual vehicle inspections. Insurance estimates are expected to drop 25 percent due to these biometric vehicle access controls. In addition to the insurance industry, transportation agencies and airlines are expecting to benefit from biometric vehicle access systems. This will allow passengers to make changes in flight schedules and improve airline passenger security. The airlines have the ability to identify passengers using biometric scans and reduce the risk of lost luggage and missed flights by implementing biometric screening processes.
Another research study that forecasting the global biometric market in the near future was prepared by an industry association known as the National Institute of Standards and Technology (NISET). The association presented its study to NICE, the United Kingdom's government agency responsible for regulating the biometric technology industry. The forecast indicates that biometric technology applications are expected to reach over $1.5 billion by the end of 2012. This represents a tremendous growth in the biometric technology market and shows the potential demand that can be realized if a company can successfully capitalize on this growing market.
Based on the above research studies, it is evident that the UK and other global markets can realize significant benefits if biometric vehicle access control systems are implemented. However, biometric technology is not a silver bullet. It does not eliminate all potential security challenges. Companies need to incorporate other security measures in order to achieve full deployment of biometric technologies. This is the reason why the forecast for the coming years shows growth in the global biometric technology sector.
The research team projects that the Vehicle Biometric Vehicle Access System market size will grow from XXX in 2020 to XXX by 2027, at an estimated CAGR of XX. The base year considered for the study is 2020, and the market size is projected from 2020 to 2027.
The prime objective of this report is to help the user understand the market in terms of its definition, segmentation, market potential, influential trends, and the challenges that the market is facing with 10 major regions and 50 major countries. Deep researches and analysis were done during the preparation of the report. The readers will find this report very helpful in understanding the market in depth. The data and the information regarding the market are taken from reliable sources such as websites, annual reports of the companies, journals, and others and were checked and validated by the industry experts. The facts and data are represented in the report using diagrams, graphs, pie charts, and other pictorial representations. This enhances the visual representation and also helps in understanding the facts much better.
By Market Players:
BioEnable
Techshino
Miaxis
Nymi
Sonavation
BIODIT
Denso
EyeLock
FPC
Fujitsu
HID Global
IriTech
KeyLemon
NEC
Nuance
Olea Sensor Networks
Safran
Synaptics
VOXX
By Type
Palm Print
Facial
Fingerprint
Iris
Others
By Application
Commercial Vehicle
Passenger Car
Others
By Regions/Countries:
North America
United States
Canada
Mexico
East Asia
China
Japan
South Korea
Europe
Germany
United Kingdom
France
Italy
Russia
Spain
Netherlands
Switzerland
Poland
South Asia
India
Pakistan
Bangladesh
Southeast Asia
Indonesia
Thailand
Singapore
Malaysia
Philippines
Vietnam
Myanmar
Middle East
Turkey
Saudi Arabia
Iran
United Arab Emirates
Israel
Iraq
Qatar
Kuwait
Oman
Africa
Nigeria
South Africa
Egypt
Algeria
Morocoo
Oceania
Australia
New Zealand
South America
Brazil
Argentina
Colombia
Chile
Venezuela
Peru
Puerto Rico
Ecuador
Rest of the World
Kazakhstan
Points Covered in The Report
The points that are discussed within the report are the major market players that are involved in the market such as market players, raw material suppliers, equipment suppliers, end users, traders, distributors and etc.
The complete profile of the companies is mentioned. And the capacity, production, price, revenue, cost, gross, gross margin, sales volume, sales revenue, consumption, growth rate, import, export, supply, future strategies, and the technological developments that they are making are also included within the report. This report analyzed 12 years data history and forecast.
The growth factors of the market is discussed in detail wherein the different end users of the market are explained in detail.
Data and information by market player, by region, by type, by application and etc, and custom research can be added according to specific requirements.
The report contains the SWOT analysis of the market. Finally, the report contains the conclusion part where the opinions of the industrial experts are included.
Key Reasons to Purchase
To gain insightful analyses of the market and have comprehensive understanding of the global market and its commercial landscape.
Assess the production processes, major issues, and solutions to mitigate the development risk.
To understand the most affecting driving and restraining forces in the market and its impact in the global market.
Learn about the market strategies that are being adopted by leading respective organizations.
To understand the future outlook and prospects for the market.
Besides the standard structure reports, we also provide custom research according to specific requirements.
The report focuses on Global, Top 10 Regions and Top 50 Countries Market Size of Vehicle Biometric Vehicle Access System 2016-2021, and development forecast 2022-2027 including industries, major players/suppliers worldwide and market share by regions, with company and product introduction, position in the market including their market status and development trend by types and applications which will provide its price and profit status, and marketing status & market growth drivers and challenges, with base year as 2020.
Key Indicators Analysed
Market Players & Competitor Analysis: The report covers the key players of the industry including Company Profile, Product Specifications, Production Capacity/Sales, Revenue, Price and Gross Margin 2016-2021 & Sales by Product Types.
Global and Regional Market Analysis: The report includes Global & Regional market status and outlook 2022-2027. Further the report provides break down details about each region & countries covered in the report. Identifying its production, consumption, import & export, sales volume & revenue forecast.
Market Analysis by Product Type: The report covers majority Product Types in the Vehicle Biometric Vehicle Access System Industry, including its product specifcations by each key player, volume, sales by Volume and Value (M USD).
Markat Analysis by Application Type: Based on the Vehicle Biometric Vehicle Access System Industry and its applications, the market is further sub-segmented into several major Application of its industry. It provides you with the market size, CAGR & forecast by each industry applications.
Market Trends: Market key trends which include Increased Competition and Continuous Innovations.
Opportunities and Drivers: Identifying the Growing Demands and New Technology
Porters Five Force Analysis: The report will provide with the state of competition in industry depending on five basic forces: threat of new entrants, bargaining power of suppliers, bargaining power of buyers, threat of substitute products or services, and existing industry rivalry.
COVID-19 Impact
Report covers Impact of Coronavirus COVID-19: Since the COVID-19 virus outbreak in December 2019, the disease has spread to almost every country around the globe with the World Health Organization declaring it a public health emergency. The global impacts of the coronavirus disease 2019 (COVID-19) are already starting to be felt, and will significantly affect the Vehicle Biometric Vehicle Access System market in 2021. The outbreak of COVID-19 has brought effects on many aspects, like flight cancellations; travel bans and quarantines; restaurants closed; all indoor/outdoor events restricted; over forty countries state of emergency declared; massive slowing of the supply chain; stock market volatility; falling business confidence, growing panic among the population, and uncertainty about future.
Global Vehicle Biometric Vehicle Access System Market Research Report 2021 Professional Edition Market report offers great insights of the market and consumer data and their interpretation through various figures and graphs. Report has embedded global market and regional market deep analysis through various research methodologies. The report also offers great competitor analysis of the industries and highlights the key aspect of their business like success stories, market development and growth rate.
Contact us: https://www.reportmines.com/contact-us.php
0 notes