#fast file transfer between two computers
Explore tagged Tumblr posts
Text
Mitchell Mondays #2:
Eastern Rain

My famous brother spent much of the last week bragging about how he'd taken in all 27 hours of Bob Dylan's latest archival release. I'd love to follow in his audio footsteps and listen to all of Bobby's 74 live recordings but I'm afraid there'd be some serious repercussions:
To begin, my work computer would give up the ghost. The machine is over a dozen years old and already on its last legs, laboring under the weight of some 30,000 MP3 files and 20 years of work documents. Every time I download another Neil Young bootleg compliments of my brother's fantastic blog the thing shudders, buckles and wavers somewhere between life and death. If that box could talk it would have nothing but curse words to hurl in my direction.
My trusty old IPod would beg for mercy. Forever addled with 22,000+ songs, it no longer holds a charge for more than 10 seconds and crashes every time I transfer antique docking stations. I'm so practiced at resuscitating it that it's a shame I wasn't on hand when Steven Jobs croaked. Plus the thing often insists boy genius is playing when I'm listening to Miles Davis. There are currently just 23 MBTs or GPTs or whatever of space left on it. Attempting to sneak 27 more hours of Dylan into its guts would be like entering me and my bald spot mid-school year and in-between shaves in a beauty pageant: things would get real ugly real fast.
Plus I'd be broke! The thing is retailing for $130 and I don't have 130 cents. Frankly, I find it incomprehensible that, given my track record of getting drunk and blogging while listening to Dylan's 70's live albums, Dylan's people have yet to send me a complimentary copy. Get to work all you Dylan-people: supply the Dollar Bin with free stuff already!
Finally, if I started in on 27 hours of Dylan and the Band in our kitchen my family would all rise up, don war-shirts and take to the streets against me. I once attempted to listen to every pass Dylan took on Idiot Wind in a row on a family car trip. In my defense I thought they'd all fall asleep or not notice what I was doing. But after just two and half glacial versions I was forced to abandon my attempt. It was either that or abandon my marriage.
Happily, my famous brother shouldered these risks for me and you and emerged unscathed, though one wonders whether his big deal wife made like a desperate farmer in a Dylan song and fingered the familial hatchet with menace once Bob and the Boys struck up their 64th rip roaring version of Hollis Brown.
youtube
Good bananas, this version, in which my brother astutely hears the rhythmic foundations of Shakey's Revolution Blues, truly cooks. Seven new people were probably born right there in the theater while Bob, Richard and everybody else pounded the hell outta this thing. Robbie Robertson: wow.
But the new Dylan collection's crown jewel, again according to the only human being on earth who has actually listened to the whole thing, is a song Dylan apparently couldn't find any room for on any of his 70's records. Apparently he thought New Pony was better than this greatness.
youtube
Imagine shrugging off and then forgetting altogether a song this dense and fruitful. Dylan, of course, built up a good deal of his cult following on equally stupid decisions: Union Sundown instead of Blind Willie McTell? Sure. Joey over Abandoned Love? Why not! Disease of Conceit when he had Series of Dreams? Definitely. Stupid apparently leads to genius if you're Bob Dylan.
But dare we say the same thing about Joni Mitchell? Once RBG died, Brandi Carlile forcefully placed Joni on our throne of liberal untouchability: criticize her and you'll suffer the progressive culture's wrath.
I'm as thrilled as you are to see Mitchell alive and well, but I think treating her like a Ming vase sucks. This is the Dollar Bin, not the Louvre, and we like our artists brilliant and flawed.
Consider: Mitchell routinely showed up to parties in the late 70's in blackface, then she memorialized the whole act on an album cover. Plus she once hired Billy Idol to accompany her on a song called Dancing Clown. Joni's not precious nor perfect; she's flawed, and she's awesome.
And she too was capable of Dylan-level dumbness.
Which brings us to Eastern Rain. When her Archives project was announced a few years back I couldn't wait to finally hear a studio take of her complex and rich song which was made famous by Fairport Convention.
youtube
But apparently Mitchell never even attempted the song for an album. All we've got after three archive collections are two live versions. They're both great, even if they include a twice repeated bridge which Fairport were wise to jettison.
youtube
Just imagine if she'd cut this song for Hissing of Summer Lawns. Lyrically it would interfere - I get that - but can't you just imagine the record's swooping bass laid over lush vibes and rich vocals? Eastern Rain could have served as yet another cornerstone of that incomparable record.
Then again, maybe the song is just cursed in some way; after all even Fairport Convention were dumb with it. Just listen to how much better everything sounds on this outtake version when Ian Matthews gets outta Sandy's way:
youtube
#mitchell mondays#joni mitchell#fairport convention#sandy denny#bob dylan#the band#my famous brother#Youtube
7 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Irvine Inc is an ISO and ROHS certified company. Our product comes with BIS certification to meet the standards. We deal in a variety of electronic items like Computer accessories, USB cables, Bluetooth speakers and more. NVMe drives can send commands twice as fast compared to AHCI SATA drives. NVMe SSDs have a latency of only a few microseconds, while SATA SSDs have latency between 30 and 100 microseconds. Irvine 512GB NVMe SSD is designed to provide your computer quick and fast read and write speed and easily open any file or save onto your storage. The read speed goes up to 1710mbps and write speed goes up to 1470mbps. The 512GB SSD is an NVMe M.2 Solid State Drive and designed to be installed in your Desktop or Laptop. It remains cool even during heavy load data transfer and consumes power efficiently. The SSD is small in size and can be easily installed in place of your old HDD on any Desktop or Laptop. Simply replace the two and experience lightning-fast transfer speeds with the Irvine 512GB NVMe SSD. We have also provided a 3 year warranty in the box of the SSD. Sequential read/write speeds up to 1710/1470 MB/s. Performance varies as per system hardware and configuration. Power Efficiency - SSDs consumes less power than HDDs, which Saves battery life of your laptop or desktops While using SSD Device Durability and Reliability - Heat is a major cause of failures in hard drives due to its moving parts. Since an SSD don't have moving parts, it can maintain a lower temperature with higher performance and has less apt to experience data loss. Directions to use - Simply remove the old drive and replace it with the new SSD. installing an SSD is simple process & can be done in just a few minutes. Warranty- 5 Years limited warranty so upgrading your storage is worry-free [ad_2]
0 notes
Text
0 notes
Text
0 notes
Text
Basic Networking Concepts You Must Know

Basic Networking Concepts You Must Know are essential for anyone working in IT, cybersecurity, or cloud computing. We live in a highly connected world where everything, from smartphones to businesses, depends on networking. Whether you're browsing the internet, sending emails, or streaming videos, networking makes it all possible. Understanding these fundamental concepts will help you navigate the digital landscape effectively.
The TCCI-Tririd Computer Coaching Institute is dedicated to providing strong networking fundamentals to its students. In this article, we will articulate the core networking concepts in a simple manner.
What is Networking?
Networking comprises connecting two or more computing devices for the purpose of data interchange and resource sharing. It may be anything from simple two computers hooked together to working together across an intercontinental complex such as the World Wide Web.
Main Functions of Networking:
Data Sharing – Enable efficient exchange of information between devices.
Resource Sharing – Enable devices to share hardware such as printers or storage.
Communication – Allow users to send messages, make VoIP calls, or use video conferences.
Security & Management – To assist in gaining control and monitoring traffic.
Types of Computer Networks
1. Local Area Network (LAN)
LAN connects devices in a very limited geographical area, typically within a home, office, or school. It provides high-speed connectivity using Ethernet cables or Wi-Fi.
2. Wide Area Network (WAN)
WAN covers a large geographical area and connects multiple LANs; the Internet is therefore the largest WAN.
3. Metropolitan Area Network (MAN)
The MAN connects multiple LANs in a city or metropolitan area and is felt as the way for universities and government organization networks.
4. Personal Area Network (PAN)
A personal area network is a small network around a person, usually based on Bluetooth or infrared technologies (ex. smartwatches, wireless headphones).
5. Wireless Networks –
Wireless networks make use of radio signals for the connection of devices, such as Wi-Fi and cellular networks.
Networking Key Elements
Routers
Routers help drive traffic along the road leading to an Internet connection between remote networks.
Switches
Switches connect several devices together in a LAN and allow efficient transfer of data.
Modems
A modem converts digital signals from a computer to analog signals so as to transmit them through a telephone line.
Access Points
Access points improve network connectivity by extending wireless coverage.
Networking Protocols You Should Know
TCP/IP
Other key functions also include those for chopping data into packets and ensuring packets are being delivered to corresponding TCP/IP hosts.
HTTP/HTTPS
HTTP and HTTPS for web surfing/secure web surfing: HTTPS encrypts the data for secure connections.
FTP
Ftp transfers files between computers on networks.
DNS
The function of DNS is to convert domain names into IP addresses.
DHCP
DHCP is used to assign IP addresses to devices on a network automatically.
Network Security Essentials
Firewalls
A firewall controls and monitors the incoming and outgoing traffic of a network for unauthorized access.
Encryption
The data is encrypted during transit to prevent hacking attempts from stealing sensitive information.
VPN (Virtual Private Network)
A VPN makes it possible for the internet connections to be secret and secured; this is an already known service while working from home.
How to solve Problems in the Network.
Restart your router or modem.
Check cable connections.
Use the network diagnostic tools.
Update network drivers.
Use command line tools such as ping or tracert.
The Future of Networking
The networking technology is in a fast pace due to breakthroughs in 5G and artificial intelligence, powered by cloud computing. Increasing network efficiency and security by creating AI-powered automation makes this an interesting field for IT professionals.
Conclusion
Understanding networking is a core necessity for anyone in the IT industry; therefore, whether you're a student, an aspiring engineer, or a business owner, these concepts should teach you how to navigate through the digital world.
Now join us at TCCI-Tririd Computer coaching institute through these extensive networking courses to master the concepts in them. Build a strong foundation in networking with us!
Location: Bopal & Iskon-Ambli Ahmedabad, Gujarat
Call now on +91 9825618292
Get information from: https://tccicomputercoaching.wordpress.com/
0 notes
Text
The Ultimate Guide to Samsung Type-C Cables: Everything You Need to Know
About
Type-C cables have become the industry standard for modern smartphones, and Samsung is no exception. Whether you're charging your Galaxy phone, transferring files to your laptop, or connecting to peripherals, understanding the right c type usb cable Samsung device is crucial.

What is a Type-C Cable?
A Type-C cable is a compact, reversible connector with a symmetrical design. This means you can plug it in either way, eliminating the frustration of fiddling with the orientation. Type-C cables offer several advantages over older Micro-USB connectors, including:
Faster Charging Speeds: Support for faster charging technologies like USB Power Delivery (PD) allows for rapid top-ups.
Data Transfer: High-speed data transfer capabilities for quickly moving files between your phone and other devices.
Video Output: Many Type-C cables can transmit video signals, enabling you to connect your phone to a display.
Versatility: Used for charging, data transfer, and connecting to a wide range of peripherals.
Samsung Type-C Cables: A Closer Look
Samsung Type-C Cable to Type-C: These cables are ideal for connecting two Type-C devices, such as your samsung type c cable to type c laptop or another phone. They are commonly used for data transfer and fast charging.
C Type USB Cable Samsung: This refers to any USB cable with a Type-C connector on one end and a traditional USB connector (Type-A) on the other. This is the most common type of cable for connecting your Samsung phone to a computer for charging and data transfer.
Samsung Data Cable: This is a general term for any cable used to transfer data between your Samsung phone and other devices. While it can refer to any cable type, in the context of modern Samsung phones, it usually refers to Type-C cables.
Samsung USB Cable Type-C: This is synonymous with "C Type USB Cable Samsung" and refers to cables with a Type-C connector on one end.
Samsung C USB: This is an abbreviated term for "Samsung Type-C USB."
Choosing the Right Samsung Type-C Cable
When selecting a Type-C cable for your Samsung device, consider these factors:
Charging Speed: If fast charging is a priority, look for cables that support Power Delivery (PD) and meet the charging specifications of your Samsung phone.
Data Transfer Speed: For high-speed data transfers, choose cables that support USB 3.0 or 3.1.
Cable Length: Select a cable length that suits your needs. Shorter cables are more convenient for travel, while longer cables provide more flexibility.
Durability: Opt for cables with durable construction, such as braided nylon or Kevlar, to withstand daily wear and tear.
Brand: Consider purchasing cables from reputable brands like Samsung or Anker to ensure quality and compatibility.
Conclusion
Type-C cables are an essential accessory for any Samsung smartphone user. By understanding the different types of cables and their capabilities, you can choose the best option for your specific needs. Whether you're looking for fast charging, high-speed data transfer, or simply a reliable connection, the right samsung c usb will enhance your Samsung smartphone experience.
#samsung type c cable to type c#c type usb cable samsung#samsung data cable#samsung usb cable type c#samsung c usb
0 notes
Text
Telecommunication protocols application interaction
Let's look at the basics of transferring information between two application processes in the OSI model.
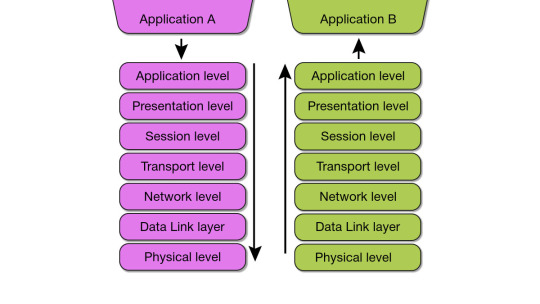
Say an application (in the picture above) needs to access a file service on another computer. It sends a request to the application layer. Based on it, the software generates a standard format message consisting of a data field and a service header. The latter contains a description of actions for the application layer of the other machine to perform, as well as instructions for the adjacent lower layer. The presentation layer, in turn, formats the data according to the instructions received and adds its own header (some protocol implementations also include service data at the end of the message), after which the information is sent to the session layer. This procedure, called encapsulation, is repeated further as data and service information move to the physical layer.
When arriving at the physical layer, i.e., the network, data passes through many other devices (network adapters, hubs, routers, bridges, etc.) and, upon reaching the destination (for example, a SIP phone), undergoes a reverse encapsulation process (right side of the picture).
Data networks can be of two types: local (local area network, LAN) and global (wide area network, WAN). The latter connects any two networks within the globe with dedicated or switched communication channels. Local networks differ in transmission medium, topology, and access control. Depending on the transmission medium, they are divided into wired (using coaxial, twisted pair, or fiber-optic cable) and wireless (WLAN), and according to the type of topology, into networks with 'bus', 'ring', or 'star' topologies.
Each computer on the local network is connected to the transmission medium through a special adapter that "sees" what any other adapter on the same network is transmitting; such systems are called broadcasts.
The MAC protocol regulates the sequence of nodes' access to the transmission medium. It is implemented using two types of schemes: polling or contention-based MAC schemes.
MAC polling networks can be centralized or distributed. Centralized ones have a star topology with a hub as the control node. In contrast, distributed ones have a ring or bus topology with token passing. Contention-based MACs are often implemented as carrier sense multiple access with collision detection (CSMA/CD) or carrier sense multiple access with collision avoidance (CSMA/CA). The first is used in all types of Ethernet LANs, and the second is used in most wireless WLANs.
The unrivaled leader among local networks is the IEEE 802.3 Ethernet network, where coaxial, twisted pair (designated by the letter T for 'twisted') and fiber-optic cables are used as transmission media. The transition to twisted-pair cable made it possible to implement full-duplex transmission over two twisted pairs, leaving the concept of collision meaningless since transmission and reception became independent operations. Ethernet has transmission speeds of 10, 100 ('Fast Ethernet'), 1000 Mbit/s (1 Gbit/s, 'Gigabit Ethernet'), and up to 400 Gigabit Ethernet.
Wireless local networks (wireless LAN, WLAN) have also become widespread. Their parameters are stated in the IEEE 802.11 specifications, known as Wi-Fi.
Today, the most common Wi-Fi 5 or 802.11ac defines the operation of wireless local area networks in the 2.4/5 GHz ranges with a data transfer rate of 1.3 Gbit/s. Shortly, speeds will reach 9.6 Gbit/s over 6 GHz frequency bands.
The range of most WLAN systems is 120 m, depending on the number and type of obstacles encountered. Additional access points will help expand the coverage area. Using two or three carrier frequencies instead of one can increase the number of users and network capacity.
Obviously, with Wi-Fi, network security becomes an important issue. A priori, wireless networks must be equipped with additional means of ensuring reliability compared to wired ones. WLAN uses direct sequence spread spectrum (DSSS) technology, which is highly resistant to data corruption and interference, including intentional ones. The problem of user authentication can be solved by introducing system identifiers. The wired equivalent privacy (WEP) mode is provided to transmit necessary information. In this case, the signal is encrypted with an additional algorithm, and the data is controlled using an electronic key.
Like all IEEE 802.3 standards, 802.11 refers to the lower two layers of the OSI model: physical and link. Any network application, operating system, or protocol (such as TCP/IP) will function equally well on an 802.11 network or Ethernet one.
The original 802.11 standard defines the basic architecture - the features of 802.11 services. The 802.11x specification only addresses the physical layer, introducing higher access speeds.
In conclusion, we should note that thanks to the close ties between Ethernet and the IP protocol, the scope of Ethernet applications is expanding, particularly in broadband subscriber access (BSA) networks.
0 notes
Text
AnyDesk: Secure Remote Access and Support for Efficient Workflows

In today’s fast-paced, interconnected world, the need for efficient and secure remote access has become more critical than ever. Whether you are a small business owner, a freelancer, or part of a large enterprise, having the ability to access and control devices remotely ensures smooth operations and enhances productivity. One of the most powerful tools available for achieving this is AnyDesk, a remote desktop software solution that has garnered attention for its exceptional speed, security, and ease of use. With its robust set of features, anydesk is designed to support teams and businesses of all sizes in achieving optimal workflows and uninterrupted productivity.
AnyDesk offers secure remote access, allowing users to connect to devices from virtually anywhere in the world. This remote connectivity is crucial for those who need to work across multiple locations, troubleshoot technical issues, or assist clients and colleagues with software problems. With AnyDesk, there is no need to be physically present at the office or a specific location, which saves both time and money while ensuring that tasks are completed efficiently. The software's ease of use makes it accessible for all levels of technical expertise, ensuring that anyone can benefit from remote support without requiring extensive training.
A standout feature of AnyDesk is its speed. It uses DeskRT, a unique video codec that provides high-quality performance with minimal bandwidth usage. This results in smoother remote connections, even when working with high-resolution displays or performing resource-intensive tasks. Unlike other remote desktop software, which can be laggy or slow, AnyDesk ensures a fast and seamless experience. This is especially important for professionals who rely on real-time communication, collaboration, or troubleshooting.
Security is another top priority for AnyDesk. In an era where data breaches and cyber threats are becoming increasingly common, AnyDesk offers a highly secure remote connection environment. All data transferred between devices is encrypted using banking-standard TLS 1.2 technology, ensuring that sensitive information is protected from unauthorized access. Additionally, AnyDesk allows users to implement two-factor authentication for added protection. These security features are essential for businesses that deal with confidential data or those working in regulated industries, where maintaining privacy and security is a legal requirement.
AnyDesk also stands out for its flexibility. It can be used across various devices and operating systems, including Windows, macOS, Linux, Android, and iOS. This cross-platform compatibility makes it an ideal solution for teams who work with diverse technology stacks or are part of a multi-platform organization. Whether you're working from a desktop computer, tablet, or smartphone, AnyDesk ensures that remote access is seamless and efficient, regardless of the device being used.
Collaboration features further enhance AnyDesk’s appeal. Teams can easily share screens, transfer files, and communicate in real-time, all within the same platform. Whether it's a collaborative project that requires multiple team members to access the same system or a quick troubleshooting session, AnyDesk simplifies the process by allowing users to interact directly with each other without switching between different communication tools.
In conclusion, AnyDesk is more than just a remote access tool; it's a comprehensive solution that enables secure, fast, and efficient workflows. By offering high-speed connections, top-notch security features, cross-platform support, and seamless collaboration, AnyDesk empowers businesses to stay connected and productive, no matter where they are. For anyone seeking a reliable, user-friendly remote access solution, AnyDesk provides the tools necessary for success in today’s remote-working world.
1 note
·
View note
Text
How to Transfer Files From PC to PC Efficiently
Transferring files from one PC to another can be quick and simple with the right tools. Whether you're moving data between two computers at home or across different networks, there are several methods to do it efficiently.

One common way to transfer files from PC to PC is using a USB flash drive. Simply copy the files to the drive from the source PC, then plug it into the destination PC and transfer the data. This method is ideal for smaller file sizes.
For larger transfers, a local network connection works well. You can set up shared folders on the source PC, allowing the destination PC to access and copy the files over the network. If both PCs are connected to the same Wi-Fi or Ethernet network, this method can be very fast.
Alternatively, cloud storage services like Google Drive, Dropbox, or OneDrive provide an easy solution for transferring files. Upload your files to the cloud from one PC, then download them to the other. This method also allows for access across different locations, provided there’s internet connectivity.
Using specialized software like PCmover or Windows File Sharing can also streamline the process, especially for large or complex file transfers.
0 notes
Text
Introducing CORSAIR MP700 ELITE Series PCIe 5.0 M.2 SSDs

Today, CORSAIR announced immediate availability of MP700 ELITE PCIe 5.0 SSDs. New drives offer next-generation storage technology at a lower cost with high performance and reliability.
The MP700 ELITE‘s advanced PCIe 5.0 x4 controller supports 10,000 and 8,500 MB/sec sequential read and write speeds. This performance boost will improve boot times, game loads, and file transfers, improving the computing experience.
The MP700 ELITE series’ High-Density 3D TLC NAND offers the ideal balance of performance and durability, ensuring your system operates without hiccups for many years. These drives can speak directly with your graphics card with compatibility for Microsoft DirectStorage, which speeds up game loading times and improves gameplay.
The MP700 ELITE, which uses the small M.2 2280 form factor, comes with a heatsink for desktop motherboards and without one for use in laptops that are compatible and have integrated motherboard cooling. Furthermore, a broad spectrum of customers may take use of this cutting-edge technology with backward compatibility with PCIe 4.0 and PCIe 3.0 platforms. PCIe 5.0 platforms like AMD’s or Intel’s 800-series provide maximum throughput.
The MP700 ELITE series, which comes with a thorough five-year guarantee and the CORSAIR SSD Toolbox software for sophisticated drive management, is evidence of CORSAIR’s dedication to both innovation and client happiness.
CORSAIR MP700 ELITE: Everything You Need to Know
The most recent SSD from CORSAIR is the MP700 ELITE. Similar to the MP700 PRO and MP700 PRO SE, this PCIe 5.0 SSD utilizes the newest technology to provide excellent throughput rates, as the name might suggest. However, this drive isn’t intended to provide the highest performance available, unlike previous drives.
Instead, it is a more popular product that forgoes some of the highest-end criteria in favor of easier-to-manage thermals and a more reasonable price. Accordingly, the MP700 ELITE can be used in a wide range of systems, including laptops, without requiring complex cooling. If you want to get the most out of it, you’ll need a laptop that supports PCIe 5.0 SSDs, but it’s nice to have options as progress.
Despite not competing in benchmark races, the CORSAIR is a fast SSD compared to its predecessor. Not even the fastest PCIe 4.0 SSDs can equal this speed. 10,000 and 8,500 MB/s sequential read and write speeds are far quicker than MP600 PRO LPX’s 7,100 and 6,800. This drive is fast on PCIe 4.0, however the MP700 ELITE is quicker on 5.0. This device supports PCIe 3.0 and 4.0, but only 5.0 maximizes throughput.
Before proceeding, they need check the specifications and learn about this new drive family.
MP700 ELITE Cooling
The MP700 ELITE comes in two different models, as seen in the above table: one with and one without a heatsink. Other than that, there aren’t much changes between them; whichever model you choose, they all offer the same capacity and throughput. Depending on the system you want to utilize it with, you should purchase one of these. For example, if the base drive is going to be installed in a laptop or motherboard that has a high-quality heatsink already installed, you will want it to be without one. The MP700 ELITE with Heatsink, on the other hand, makes sense if your motherboard lacks cooling.
Measuring 80 x 23 x 18 mm, the MP700 ELITE with Heatsink includes a large but stylish matte black metal cooler. When it comes to keeping your drive cool under stress, this is more than capable. Naturally, you will still need adequate airflow in your system because removing heat from the SSD is only one part of the answer. However, the MP700 ELITE’s controller only uses an average of 6W, which is far less than most PCIe 5.0 SSDs.
CORSAIR created a Hydro X Series version that could be connected to your own cooling loop, similar to the MP700 PRO and MP700 PRO SE. However, as the drive shouldn’t require such high cooling levels, haven’t done this here. Nothing stops you from purchasing the Hydro X Series XM2 M.2 SSD Water Block and utilizing it with the MP700 ELITE, though, if this is still something you wish to do.
MP700 ELITE Summary
The fast PCIe 5.0 SSDs CORSAIR MP700 ELITEwith Heatsink provide robust performance and durability at an alluring price. They provide a significant performance improvement over PCIe 4.0 SSDs, although they are not made to top performance charts. With 1TB and 2TB sizes available at launch and compatibility for Microsoft DirectStorage, they offer additional choices for anyone wishing to upgrade their existing system or build a new one. Given that the most recent generations of CPUs from AMD and Intel support PCIe 5.0 SSDs, you should be able to get the most out of them with a motherboard and processor that support them.
MP700 ELITE Price availability warranty
The CORSAIR webstore and its global network of authorized merchants and distributors offer the CORSAIR MP700 ELITE series in 1TB and 2TB capacities right now.
In addition to a five-year guarantee, the MP700 ELITE series is supported by the global customer care and technical support network of CORSAIR.
Please visit the CORSAIR website or get in touch with your local CORSAIR sales or PR professional for the most recent MP700 ELITE pricing.
Read more on Govindhtech.com
#CORSAIRMP700ELITE#MP700ELITE#PCIe5.0#M.2SSDs#SSD#MP700#PCIe4.0#TLCNAND#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
0 notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Product Description Quickly and easily connect to the latest Windows and Mac computers with Rugged’s reversible USB-C cable, or legacy computers using the included USB 3.0 adapter Enjoy fast USB-C 5Gb/s file transfers, backups, and image browsing Confidently tackle any terrain with drop, crush, and rain resistance Enjoy long-term peace of mind with the included two-year limited warranty and two-year Data Recovery Services Actual storage capacity may vary due to differences between decimal and binary calculations. [ad_2]
0 notes
Text
12 Best Phone Cloning Services to Catch a Cheating Partner

Phone cloning has emerged as a significant topic in the realm of technology and personal security. Whether for legitimate purposes such as data transfer or for more contentious reasons like catching a cheating partner, understanding the ins and outs of phone cloning is crucial. This blog delves into what phone cloning is, the methods and tools used for cloning phones, the various apps available for Android, and the ethical considerations surrounding these practices.
What is Phone Cloning?
Phone cloning refers to the process of duplicating the data and identity of one mobile device onto another. This can involve copying the International Mobile Subscriber Identity (IMSI) and the Electronic Serial Number (ESN) from one phone to another, effectively creating a replica. While originally associated with illicit activities, phone cloning now includes a variety of legitimate uses such as data migration between devices.
How to Clone a Phone
Cloning a phone can be achieved through several methods, each with its own set of tools and technical requirements. Here are the most common methods:
1. Manual Cloning
Manual cloning involves physically transferring data from one device to another. This can be done by:
SIM Card Duplication: Copying the information from one SIM card to another. Specialized hardware and software are required to read and write SIM card data.
Data Transfer: Manually copying data such as contacts, messages, and media files using a computer or cloud services.
2. Software-Based Cloning
Software-based cloning uses specialized applications to duplicate data from one phone to another. This method is more user-friendly and does not require extensive technical knowledge. Common steps include:
Downloading a Cloning App: Installing an app designed for phone cloning on both devices.
Connecting Devices: Using Bluetooth, Wi-Fi, or USB cables to establish a connection between the two phones.
Selecting Data: Choosing the specific data to be cloned, such as contacts, messages, photos, and apps.
Initiating the Cloning Process: Allowing the app to transfer the selected data from the source phone to the target phone.
Cloning Phones App
Several apps are designed specifically for phone cloning, each with unique features and capabilities. Here are some of the most popular phone cloning apps available for Android devices:
1. Phone Clone by Huawei
Huawei’s Phone Clone is a widely used app that facilitates easy data transfer between smartphones. Key features include:
Cross-Platform Support: Compatible with both Android and iOS devices.
High-Speed Transfer: Utilizes Wi-Fi Direct for fast data transfer.
Comprehensive Data Transfer: Supports the transfer of contacts, messages, photos, videos, apps, and more.
2. CLONEit
CLONEit is another popular app that offers seamless data transfer between Android devices. Its features include:
Offline Transfer: Does not require an internet connection.
Multiple Data Types: Transfers 12 different types of data, including contacts, messages, call logs, and apps.
Easy to Use: Simple interface with clear instructions.
3. SHAREit
While not exclusively a cloning app, SHAREit offers robust data transfer capabilities. Its main features are:
High-Speed Transfers: Faster than Bluetooth and standard Wi-Fi.
Versatile Data Transfer: Transfers files, photos, videos, music, and apps.
Cross-Platform Compatibility: Works with Android, iOS, Windows, and Mac.
Phone Clone App for Android
Using a phone clone app on Android involves a few straightforward steps. Here’s a general guide:
Download and Install: Install a phone cloning app like Phone Clone, CLONEit, or SHAREit from the Google Play Store on both the source and target devices.
Set Up the Connection: Open the app on both devices. Follow the instructions to establish a connection. This might involve scanning a QR code or connecting via Wi-Fi Direct.
Select Data to Clone: Choose the specific data you want to transfer. This can include contacts, messages, photos, videos, and apps.
Start the Cloning Process: Initiate the transfer and wait for the process to complete. Ensure both devices remain connected and do not interrupt the process.
Phone Clone Service to Catch a Cheating Partner
Phone cloning services can be controversial, especially when used to catch a cheating partner. Here’s a look at how these services are used and the ethical considerations involved.
1. Using Phone Cloning to Catch a Cheating Partner
Phone cloning can be used to duplicate a partner’s phone data onto another device, allowing one to monitor their communications and activities. This might include:
Reading Messages: Accessing text messages, social media chats, and emails.
Tracking Location: Monitoring GPS data to track movements.
Viewing Call Logs: Checking call history and durations.
Accessing Media: Viewing photos and videos stored on the phone.
2. Ethical Considerations
While the desire to catch a cheating partner might drive one to consider phone cloning, it’s essential to weigh the ethical and legal implications:
Privacy Invasion: Cloning someone’s phone without their consent is a significant invasion of privacy.
Legal Consequences: Unauthorized phone cloning is illegal in many jurisdictions and can result in severe penalties.
Trust Issues: Resorting to phone cloning can further damage trust and relationships.
3. Alternatives to Phone Cloning
Instead of resorting to phone cloning, consider these alternatives:
Open Communication: Discuss your concerns openly with your partner.
Professional Help: Seek relationship counseling or therapy.
Hire a Private Investigator: If you suspect infidelity, hiring a professional investigator can provide evidence without legal or ethical breaches.
Conclusion
Phone cloning is a complex and multifaceted process with applications ranging from legitimate data transfer to more contentious uses like catching a cheating partner. While several apps facilitate easy phone cloning for Android devices, it’s crucial to consider the ethical and legal implications of such actions. Always prioritize open communication and legal avenues over invasive methods to resolve personal issues.
By understanding the tools and methods available, users can make informed decisions about when and how to use phone cloning technology. Whether for convenience or more serious matters, responsible use of these technologies is essential to maintain trust and legality in personal and professional relationships.
0 notes
Text
4/27/24
10:59 p.m Edited/Added to
So I had heart palpitations when I closed my eyes again last night... luckily they passed and fell asleep on just the half MG of xanax. I didn't need any other drugs, thankfully.
I woke up around 12, that's the longest I've slept straight through the night since psychosis minus after microsleep, while I was smoking weed. The nights I didn't microsleep during October I could sleep through like 7-10 hours. That was only like 4 or 5 nights between October 10th and November 3rd... and then when I started sleeping regularly again I was able to sleep like 6-10 hours straight when I was smoking pot. Then I quit pot and insomnia got terrible...
And before Xanax when I finally fell asleep after, "black heading," for hours I could stay asleep longer like 6-10 hours but it took so long just to fall asleep and some nights I never did...
Then I started Xanax and I've been able to fall asleep but usually i wake up ever 2-3 hours...
Anyways I took benadryl at 12 and then passed back out. Woke up at 2 p.m and then fell back to sleep without benadryl and slept until about 3:30 or 4 p.m idk bc microsleep fucked with my ability to know if I slept or not... all I know is that's why I keep a sleep tracker...
I decided not to do my laundry... I need to do my bedding and I've been putting it off bc my hoodies pile up so fast from Contamination.. and I need to have them to use the sleeves to grab stuff, so i have to plan to do my bedding the day after I do my clothing and towels bc otherwise I have a huge pile and can't do it all in one day.
However I needed a day with limited to no bathroom time. My laundry machine is in the bathroom, and even if it wasn't, doing laundry triggers major OCD. So I just decided to have a red bull day aka two 12oz red Bulls in a day and play video games.
I'm glad I made that decision. I'm playing bully and working on chapter 5. I am cooking dinner and taking a break. I should have that finished and uploaded prob around 3 or 4 a.m depending on how slow my MacBook is bc I've had to piece together the video bc of breaks... I'm taking pictures so I can submit them to apple so I can get my computer looked at and have a case at the apple store but I have to do it over the phone first and submit pictures. To combine a 1 hour video I have to wait 20 minutes it's ridiculous.
Anyways, I got my sneakers, I love them but the right shoe squeezes my baby toe strangely I've been fucking with the laces but I can't seem to get it right. Idk if this is one of those beauty is pain things or what but I might return them bc it's uncomfortable and if I get lines in them, they won't take them back but we see. It's actually both toes when I walk... I might do a return.
I'm hoping I can get some good gameplay today. Unfortunately I'm stuck on my old Xbox one s bc my stupid cloud saves won't transfer over to my series x which is fucking obnoxious...
Idc about most of my saves but I care about some-
1) Silent Hill 2 bc of my 10 star thank God that transferred over.
2) far cry 2 bc I have a over 20 hour save file and I'm half way through the game but it won't transfer to my new system......
3) Bully bc I have almost a 100% completion save file and one achievement left for 100% but it won't transfer.....
4) Minecraft bc of my castle which I've invested over 36 days working on thankfully that transferred over.
5) Silent Hill Homecoming bc I unlocked all the endings but whatever I can live without it even though it's obnoxious.... it won't transfer..
Anyways I won't play fc2 on my old system bc I'll easily play over 20 hours on the second half so I have to troubleshoot it..... I already tried for hours last night.
I'm sucking up bully for now to finish my playlist and I may accept losing the 100% completion save file which is fucked.
It's nice trying to relax but technology is a bitch and yea... I only picked Bully bc it doesn't trigger my OCD.
Also I've noticed at least in one way my hallucination has improved. When I played bully months ago the entire experience was intruded upon by the hallucination... however I think the last time I played it was like November when it was much worse.
There is a lot of dialogue so it helps drown it out. I've noticed with games with dialogue I can enjoy them mostly.
0 notes
Text
what layer does vpn operate
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what layer does vpn operate
VPN Protocols
VPN protocols are essential components of a Virtual Private Network (VPN) that ensure secure and encrypted communication over the internet. There are various VPN protocols available, each with its own set of features and levels of security.
One of the most commonly used VPN protocols is OpenVPN, known for its open-source nature and strong encryption capabilities. OpenVPN is versatile and compatible with a wide range of devices and operating systems. It utilizes the OpenSSL library and SSL/TLS protocols to establish a secure connection.
Another widely used VPN protocol is IPSec (Internet Protocol Security), which operates at the network level and offers strong security through encryption and authentication protocols. IPSec can be used in two modes: transport mode for securing individual connections and tunnel mode for securing entire networks.
L2TP/IPSec (Layer 2 Tunneling Protocol over IPSec) combines the best features of L2TP and IPSec to provide enhanced security and privacy. L2TP provides the tunneling mechanism, while IPSec ensures the confidentiality and integrity of data transmission.
SSTP (Secure Socket Tunneling Protocol) is a VPN protocol developed by Microsoft that uses SSL/TLS for secure communication. SSTP is known for its ability to bypass firewalls and operate on port 443, making it a popular choice for users in restrictive environments.
PPTP (Point-to-Point Tunneling Protocol) is one of the oldest VPN protocols and offers fast connection speeds but is considered less secure compared to other protocols due to its weaker encryption methods.
Choosing the right VPN protocol depends on factors such as security requirements, device compatibility, and intended usage. It's important to select a protocol that aligns with your specific needs to ensure a safe and secure VPN connection.
OSI Model
The OSI (Open Systems Interconnection) Model is a conceptual framework used to understand and describe the functions of a networking system. It was developed by the International Organization for Standardization (ISO) to facilitate communication between different computer systems. The OSI Model consists of seven layers, each with its own specific role and functionality.
At the bottom of the OSI Model is the Physical Layer, which deals with the physical transmission of data over a network medium. This layer includes specifications for cables, connectors, and other hardware components.
Above the Physical Layer is the Data Link Layer, responsible for establishing and maintaining a reliable link between two devices on the same network. It handles error detection and correction, as well as flow control.
The Network Layer sits on top of the Data Link Layer and is responsible for routing and forwarding data packets between different networks. It determines the best path for data to travel from the source to the destination.
Above the Network Layer is the Transport Layer, which ensures the reliable delivery of data between end systems. It provides error checking and data integrity, as well as mechanisms for flow control and congestion avoidance.
The Session Layer manages the communication sessions between applications on different devices. It establishes, maintains, and terminates connections between applications.
The Presentation Layer is responsible for translating, encrypting, and compressing data for transmission over the network. It ensures that data is in a format that can be understood by the receiving system.
Finally, the Application Layer is where end-user processes and applications interact with the network. It provides services such as email, file transfer, and web browsing.
Overall, the OSI Model provides a systematic way to understand how different components of a network interact with each other, facilitating the development and troubleshooting of complex networking systems.
Transport Layer Security (TLS)
Transport Layer Security (TLS) is a crucial cryptographic protocol that ensures secure communication over networks such as the internet. TLS serves as a successor to the older Secure Sockets Layer (SSL) protocol and is commonly used to secure data transmissions, including sensitive information like passwords, credit card details, and personal data.
TLS works by authenticating the parties involved in a communication, encrypting the data being transmitted, and ensuring the integrity of the data throughout the transmission process. It uses a combination of cryptographic algorithms to achieve these goals, including asymmetric and symmetric encryption, key exchange protocols, and digital signatures.
One of the key features of TLS is its ability to provide end-to-end encryption, which means that data is encrypted on the sender's device and decrypted only on the recipient's device, making it virtually impossible for unauthorized parties to intercept and decipher the information being transmitted.
TLS is used in various internet protocols and applications, including HTTPS for secure web browsing, secure email communication (SMTPS, POP3S, IMAPS), virtual private networks (VPNs), secure file transfer (FTPS), and many more.
As cyber threats continue to evolve, having robust security measures like TLS in place is essential to safeguard sensitive data and protect individuals and organizations from malicious attacks. By implementing TLS correctly and staying up-to-date with the latest cryptographic standards and best practices, users can ensure a higher level of security and confidentiality in their online communications.
Network Layer Encryption
Title: Enhancing Security with Network Layer Encryption
In the realm of cybersecurity, network layer encryption stands tall as a formidable barrier against unauthorized access and data breaches. This encryption methodology operates at the network layer of the OSI (Open Systems Interconnection) model, ensuring that data transmitted over a network remains secure and confidential.
At its core, network layer encryption utilizes advanced cryptographic techniques to encode data packets before they are transmitted across the network. This process involves transforming plain-text data into ciphertext, rendering it indecipherable to anyone without the proper decryption key. By encrypting data at the network layer, organizations can safeguard sensitive information from interception and eavesdropping attacks.
One of the primary advantages of network layer encryption is its ability to provide end-to-end security. Unlike other forms of encryption that only protect data during transit, network layer encryption ensures that data remains encrypted throughout its entire journey, from the source to the destination. This comprehensive approach mitigates the risk of data interception at any point along the network path.
Furthermore, network layer encryption adds an extra layer of security to existing network infrastructure. By encrypting data packets at the network layer, organizations can protect sensitive information without having to modify individual applications or protocols. This makes it an ideal solution for securing a wide range of networked devices and services, including web browsing, email communication, and file transfers.
In conclusion, network layer encryption plays a vital role in enhancing the security posture of modern networks. By encrypting data at the network layer, organizations can ensure the confidentiality, integrity, and authenticity of their communications. As cyber threats continue to evolve, network layer encryption remains an indispensable tool for safeguarding sensitive information in an increasingly interconnected world.
Data Link Layer Authentication
The Data Link Layer in network communication plays a crucial role in ensuring the security and integrity of data transmission. One of the key aspects of maintaining security at this layer is authentication. Data Link Layer Authentication is a process that verifies the identity of devices communicating over a network, thus preventing unauthorized access and potential security breaches.
Authentication at the Data Link Layer involves confirming the identity of the sender and receiver of data packets to ensure that communication is secure and reliable. This process helps in preventing spoofing attacks where an unauthorized device pretends to be a legitimate one to gain access to the network.
There are various mechanisms used for Data Link Layer Authentication, such as MAC address filtering, IEEE 802.1X authentication, and port-based authentication protocols like EAP-TLS. These methods help in establishing a secure connection between devices by verifying the credentials of both parties involved in the communication.
By implementing Data Link Layer Authentication, network administrators can effectively control access to the network, protect sensitive data from unauthorized access, and prevent potential security threats. It also ensures data integrity and confidentiality during transmission, providing a secure communication environment for users.
In conclusion, Data Link Layer Authentication is essential for maintaining network security and protecting data from potential cyber threats. By incorporating robust authentication mechanisms at this layer, organizations can establish a secure and reliable communication infrastructure that safeguards sensitive information and prevents unauthorized access.
0 notes
Text
Xender Fastest All-in-one File Transfer and Sharing App
Xender is an app that permits users to transfer all important files between two devices. application for Android devices. This data transfer app allows users to easily transfer and share files without relying on the internet or Bluetooth connectivity. The application shared a speed of 40Mbps during file sharing. From the original version, you need to watch multiple ads.
And now you can easily download the Xender apk file which comes with a built-in file manager. It supports operating systems like Android, iOS, Tizen, Windows, PC, and Mac. This app is similar to the SHAREit file-sharing app for Android.
Xender APK
Xender APK transfer of various content including photos, videos, music, apps, documents, etc. This is a great application for people who like to share files with others. This will help save the size of your internet data pack and save time wasted — transferring files like slash-speed animation.

Latest Features of Xender
Xender is an amazing app that helps you easily share and send files. Xender uses a local Wi-Fi network to transfer files between up to four smartphones and a PC. You only need to enable your hotspot on one device and connect others to it. If you're joining multiple devices, you can create a group for easy access. File sharing is immediately available via another set of clearly labeled buttons. Here are the latest Features of Xender are:
Fast file transfer
File-sharing technology is a prominent and competitive field. From the portal to your phone, you'll find a variety of apps with the same basic functionality with minor differences in design. Compared to its contenders, Xender seems incredibly straightforward. It emphasizes simplicity and functionality, compacting the most useful technology into an intuitive and lightweight app. Also, unlike most free-charge programs, it does not display any ads in the interface
Xender on the sending device, click Send, and select files to share. On the receiving device, open Xender, click Receive, and wait for the sender's device to appear. Tap the sender's device to establish the connection and start the file transfer.
Free Cross-platform Compatibility
Xender is a free file-sharing tool that emphasizes speed and flexibility. Working across platforms, it uses advanced technology to create a local Wi-Fi network between devices and send content without data charges. This app requires a fraction of the time it would take Bluetooth to perform the same task.
No internet required
With Xender you can transfer files of various types and sizes between mobile devices, without cables, Wi-Fi, or internet connections.
Group Sharing
Xender permits group file sharing. Users can connect multiple devices to share files simultaneously, which is useful for sharing content with friends and family.
Phone Replication
It gives users the ability to duplicate or back up their phone to another device. You just need to install Xender on both devices and then you can easily back up your phone on the other device.
Key Features of Xender APK
● It transfers files through a LAN connection or Bluetooth connection. The transmission speed is about 300 times faster than a Bluetooth connection.
● No internet connection is required to exchange files between two specific devices.
● The design of the application is stunning and impressive and covers all the features of the application, including installation, removal, viewing, opening, and uninstallation.
● Users can easily transfer all important data, such as contacts, photos, images, video games, and messages from one device to another.
● Xender is a free application when two computers without a LAN connection need to exchange files.
● This process supports various formats and sizes of files that need to be exchanged between two specific devices. This includes photos, documents, music files, videos, and software applications.
● Xender is not a complicated process, but an application with a fresh and clean interface, so that all users can easily understand and use the app.
● Application size is reduced with high compression to increase launch speed.
● Interactive control of all files between different technical devices is easy and useful.
How to Use Xender APK?
Xender is an amazing file transfer app that allows sharing files on mobile and desktop. Although Bluetooth technology has improved with the latest version having four times the range and better capacity. Also, transferring large files quickly from one device to another becomes cumbersome. In such a case, Xender comes in handy to transfer a bunch of files without using any mobile data. The app does not require a USB connection or PC software installation to share files.
Xender APK Download
Users can easily download and install this App from our web xenderapk.me. Simply click the download button and install it.
What is Insta Pro 2 APK?
Insta Pro 2 emerges as an innovative alternative to the standard Instagram, created by the team at SamMods. This enhanced version brings the full Instagram experience to users at no cost, boasting a plethora of features and capabilities. It excels in providing enhanced privacy options and a range of exclusive functionalities. A key advantage of Insta Pro 2 APK is its compatibility with Android devices, allowing it to coexist with the original Instagram app without any conflict. For Android enthusiasts, Instagram Pro APK is a breeze to download and use. This version steps beyond the basics, offering a more enriched and engaging interaction with the platform. Users can expect more than just endless scrolling; Insta Pro 2 enhances the overall Instagram journey, making it more enjoyable and feature-rich.
Conclusion
The user interface and user experience are simple and designed in a way that makes sending and receiving files a piece of cake. Xender App can help you to share all your data and it is very easy to use it. At the same time, share this application with all your friends as well as family members who are worried about transferring their data. Use it to transfer all your data and you can easily send movies and big-sized clips to another device. Don’t be late and click on the download button above to get it and start sharing your data.
0 notes
Text
How to Transfer Files from PC to PC: A Step-by-Step Guide
When it comes to moving files between PCs, there are several methods to choose from. I’ve outlined some of the most efficient ways to get the job done. Whether you're upgrading to a new computer or simply sharing files, you can easily transfer data by using tools like external drives, local networks, cloud storage, or specialized software.

We often use external drives like USB flash drives for quick transfers. If both PCs are connected to the same network, they can share files through folder sharing. For a more advanced option, their data can be moved using cloud services like Google Drive or OneDrive, which provide secure, remote access to files. PC migration software, such as Laplink PCmover, offers a comprehensive solution to transfer files, settings, and even programs without hassle.
They can also opt for a USB transfer cable, which provides a direct, fast connection between two computers. Regardless of the method, each option helps users move their data quickly and securely, making the process simple and efficient.
0 notes