#function of transferring large files
Explore tagged Tumblr posts
Text
Free software recommendations for various things:
LibreOffice - A full home office suite comparable to Microsoft Office. Easy to use and you can choose the UI layout from several types; it can handle docx and other Microsoft Office document formats; it still does not include AI unless you specifically add that extension on purpose, so unlike other office suites it's not shoving AI down your throat.
Calibre - Ebook manager bundled with an ebook editor and ereader software. It can follow news feeds, downloading them into epub format. Convert ebooks from one format into (many) others. Run a server to make access your books from different computers/phones/tablets easier. And so much more... without even touching on the additional functionality that plugins can add. With plugins it can be used for DRM stripping (which can still remove DRM from even Kindle ebooks, if you have a kindle that you can download the ebook to and use to transfer to your computer). It can also handle downloading fanfics and their metadata using the FanFicFare plugin. (Which I've written tutorials about.) There are officially supported plugins (like FanFicFare) that are easy to install and unofficial plugins (like the DRM stripper) that take more work, so it's extremely customizable.
Syncthing - Want to host your own local file backup system? Have an old laptop that you can reformat with a linux distro? And maybe a spare hard drive? Perfect, you have what you need to set up a home file backup system. Reformat the computer with the new operating system, install syncthing on that computer and on the computer you want to back up files for and the two installations of the software can sync over your home network. Put it on your phone and back up your photos. The software is open source, encrypted, and you can turn it off so that your computer (or phone) is only running it on a trusted network. You control where the synced data lives, which computers on your network those synced folders are shared with (allowing for sharing between multiple computers) and even what type of file backups happen if data is, say, accidentally deleted. (File recovery!!!)
Plex or Emby - Both are free to install on any computer, point at any movie/tv show/audiobook/music files you've got sitting around, and bam you've got a home media streaming server. Both have paid tiers for more features (including tv tuner integration to act as a DVR), but what they can do for free is already impressive and well handled. Both have easy to use UI and it largely comes down to personal preference as to one is better than the other.
Notepad++ - A notepad type program that can also serve as a decent lightweight code editor. I use it for noodling around with code scripts and snippets, writing lists, and various other small tasks. It's not something I'd use for my professional code writing but it's great for just messing around with something on my own time.
16 notes
·
View notes
Note
Hi! I really enjoyed reading all your posts. I could probably say more in a better headspace, but I at least want to say: huge kudos to you for writing that 10-page Amane paper. Amane fans are the normalest people around <3
I was wondering, if it's not too broad, how Amane's case for murdering Shidou might go. (I know it's still kind of vague what happened, and I have no idea how she'd do it in non-MILGRAM custody, but I'm quite curious.)
Yes I am very normal about Amane thank you
Honestly this one is impossible to actually say definitively if not only because there’s no scenario where they’d be sent to serve a sentence in the same place. Juveniles are always separated from adults, even when they’re tried as adults. They just get transferred to adult facilities once the juvenile court loses jurisdiction.
Ultimately though, in large part, I think it changes very little.
Take scenario 1 or 2 from the amane post and lets say she was found NGI for the offense of second degree murder and was sent to a state institution.
When youre in a state institution, you are pretty much stuck there for at least the minimum term of imprisonment you’d get if you weren’t found insane. In my state, 2nd degree murder can carry 15 yrs to life in prison, minimum. So, she’s likely stuck there for 15 years minimum. Disregarding parole nuances.
In the meantime she can file restoration of sanity petitions, which require a court trial (no jury involved) to prove that she has regained sanity. At the end of the 15 years, the government also can, and will, file petitions barring release on the basis that she has not restored sanity, and inevitably they wind up in the same place- has your sanity been restored or not? By which I mean, can your doctors say you’re not mentally ill anymore? This is why sometimes an insanity plea basically results in life imprisonment.
In any case, if at any point she somehow manages to kill Shidou during her time in this facility, and based upon the reasons that she did it, it only factors to keep her in that institution longer. Because we said you’re not guilty by reason of insanity for this RAMCOA related mental illness driving your theories of right and wrong, and you proceeded to, once again, kill someone because of the same rhetoric. In this sense, your sanity is surely not restored, you’re a danger to the community and yourself, etcetcetc, she’s in there until she’s deprogrammed, basically.
So for that scenario, functionally, nothing actually changes. Her release from that institution would always hinge on her ability to prove that her sanity was restored. It just makes it harder to prove that when you have two bodies for the same reason.
But let’s say she’s actually genuinely convicted of 2nd degree murder and sent to a prison for probably 15 yrs max, and she kills shidou (who is somehow in the same facility). I don’t think her term would actually have “to life” attached, if I’m honest, I think she’s more likely to get a determinate term of 15 years because she’s literally 12. (and I think she’d probably get out earlier. It’s genuinely easier to get out of prison than it is an institution.)
But I digress. So one comparison is Christopher Scarver, who killed Dahmer and another inmate while he was already serving a life term. All adults. He eventually pleaded no contest to both murders and was transferred to federal prison which is generally worse for prisoners than state prisons (though neither are phenomenal), receiving two more life terms. So its just life x3.
Theoretically, if she killed shidou somehow while she was convicted as a juvenile, they may charge her as an adult, and may smack a consecutive life (with the possibility of parole) sentence on her, which means she’d serve time in a juvenile facility until the court loses jurisdiction (age 18-25) and then get transferred to an adult prison to serve her life term with the possibility of parole.
She cannot get any term at age 12 that does not have some possible form of release. Flat out. She will always have some option as to release. But, again, killing another person for the same reasons will make getting parole a lot less likely.
She will have to show that she’s de facto deprogrammed anyways for any hope of parole. She doesn’t have to go as far as restoration of sanity, per se, so it’s slightly easier, and being that she’d be over age 20 before she found herself in a parole hearing, there’s something to be said about proving you’re not dangerous after two murders committed when you were literally 12. Add on the tragic backstory and really Amane could ostensibly have a pretty easy time getting out on parole.
But really, it’s more harmful to her to not mandate some form of therapy or treatment. I see no scenario where Amane can truly live normally and peacefully after the murders without deprogramming. And even after deprogramming, I have to imagine she will have difficulty forming normal relationships with people.
But if we take Amane scenario 3, where shes guilty of malice murder and has it reversed on appeal, it makes literally no difference at all if she kills shidou.
As I said there, theres a really good case to be made as to insufficient evidence to form the proper mens rea required for murder. I kind of gave an incomplete overview of the nuances with charging and retrials, theoretically she could be retried with a lesser offense like negligent homicide or voluntary manslaughter, but usually when someone is charged with murder, the jury instructions will already account for those possibilities. Like, I charge you with malice murder, but we also have an inherent and unavoidable duty to instruct the jury that hey, if you don’t think she was able to form the mens rea due to extreme provocation or emotional disturbance, you should find her guilty of the lesser included offense of voluntary manslaughter. The thing is though, if a jury found her guilty of malice murder even with that lesser included offense instruction, it is effectively a finding beyond a reasonable doubt that she didn’t meet the elements of voluntary manslaughter- which would, in turn, make it nearly impossible to retry her for voluntary manslaughter. Theoretically possible, but doubtful.
Anyway, so she gets convicted, then appeals. Let’s say that while her appeal is pending she kills shidou. That is a whole separate case. They do not look at information beyond the record on appeal unless its a habeas proceeding (for an example, if I claim there was racial bias in my trial I should do a habeas proceeding. That way I can prove facts beyond the record about racial bias among jurors beyond what they said on the record during trial, or I can provide proof of sentencing disparities between my race and another race, etc.)
They’ll know she killed him but they’re really not supposed to be looking at that. Because whether she killed her mom with that mental state is predicated on different facts, its based in a different scenario, it arises from different relationships with the victim, and therefore the mental state is not truly the same even if driven by similar factors. So whether her mental state negates murder for killing her mom does not change after killing Shidou.
What DOES change is that she’d be charged with his murder separately, and sympathy might be dwindling. Killing your abusive mom is one thing, killing a doctor that tends to people is another, especially because he had no hand in your abuse. Almost like how people wouldn’t feel bad for Haruka because he killed someone not connected to his abuse, but Amane would at least enjoy the benefit of not being seen as actual Satan incarnate because she didn’t kill a child. But that’s not enough to save her here, really.
Based on what we know about her murder of Shidou, god, I hate saying it, it’s honestly first degree murder. Like, she’s not being subtle in T2, it’s premeditated and deliberate. She doesnt have the nexus between the abuse and the victim that she does for her mom. And by now she’s well aware murder is wrong. Insanity is harder to swing, even with the characteristic hyperreligiosity. It’s still possible I suppose.
Honestly it’d be foolish to charge first degree murder though, even though she did technically plan it. She’ll probably get second degree, maximum, because of the RAMCOA and the age and everything else. Its really more of a preventative measure at that point. Because if the court on appeal said, broadly, that her RAMCOA prevented her from forming the requisite intent for murder, I’d be pretty hesitant to ignore that in charging her again for another murder that she committed due to the RAMCOA. Honestly it becomes convoluted at this point. Assuming she’s somehow still 12 she could be charged as a juvenile and we end up right back where we started. Maybe she gets 15 to life as an adult and we end up in the same place where she needs to basically prove she’s sane to get parole. The waters are muddied with this scenario where she’s absolved on appeal.
Generally, if we ignore the murder of her mom altogether, pretend it didn’t happen and just operate on the theory that she only killed shidou, and it wasn’t in prison but just out and about in the regular world, shes probably still getting second degree murder maximum and her parents are getting crucified. At this point its like a watered down version of Haruka’s case, where extreme abuse led to a crime. Its only that amane’s case would still be more sympathetic, because of the torture, the fact that it was her entire life, the fact that shes a 12 year old girl, etc. Its weird because I know this is antithetical to what I said for Haruka, right, but it is genuinely different. The impact of RAMCOA on someones mental state and ability to form the intent to murder, and the subsequent ability to rehabilitate them, is hugely different from the vast array of emotional neglect scenarios and their outcomes. Because it was amanes whole life, the jury might genuinely say ok, she didn’t know any better. With haruka that isnt the case, as bad as it sounds. I might do a comparative analysis sometime to clarify why his case is so much different despite it looking the same facially.
#the milgram project#milgram#amane momose#amane momose milgram#amane purge march#amane milgram#milgram project
13 notes
·
View notes
Text
How to know if a USB cable is hiding malicious hacker hardware
Are your USB cables sending your data to hackers?
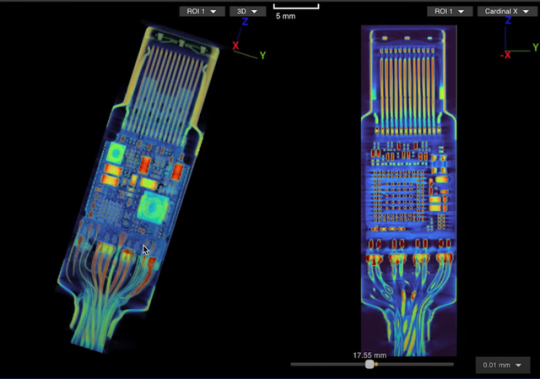
We expect USB-C cables to perform a specific task: transferring either data or files between devices. We give little more thought to the matter, but malicious USB-C cables can do much more than what we expect.
These cables hide malicious hardware that can intercept data, eavesdrop on phone calls and messages, or, in the worst cases, take complete control of your PC or cellphone. The first of these appeared in 2008, but back then they were very rare and expensive — which meant the average user was largely safeguarded.
Since then, their availability has increased 100-fold and now with both specialist spy retailers selling them as “spy cables” as well as unscrupulous sellers passing them off as legitimate products, it’s all too easy to buy one by accident and get hacked. So, how do you know if your USB-C cable is malicious?
Further reading: We tested 43 old USB-C to USB-A cables. 1 was great. 10 were dangerous
Identifying malicious USB-C cables
Identifying malicious USB-C cables is no easy task since they are designed to look just like regular cables. Scanning techniques have been largely thought of as the best way to sort the wheat from the chaff, which is what industrial scanning company, Lumafield of the Lumafield Neptune industrial scanner fame, recently set out to show.
The company employed both 2D and 3D scanning techniques on the O.MG USB-C cable — a well-known hacked cable built for covert field-use and research. It hides an embedded Wi-Fi server and a keylogger in its USB connector. PCWorld Executive Editor Gordon Ung covered it back in 2021, and it sounds scary as hell.
What Lumafield discovered is interesting to say the least. A 2D X-ray image could identify the cable’s antenna and microcontroller, but only the 3D CT scan could reveal another band of wires connected to a die stacked on top of the cable’s microcontroller. You can explore a 3D model of the scan yourself on Lumafield’s website.
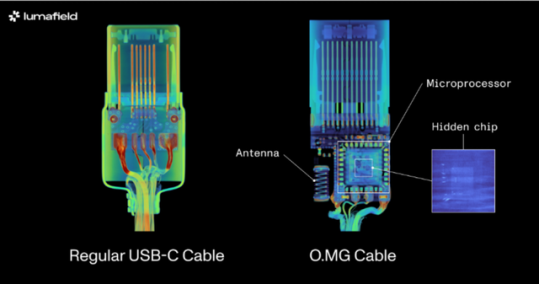
It confirms the worst — that you can only unequivocally confirm that a USB-C cable harbors malicious hardware with a 3D CT scanner, which unless you’re a medical radiographer or 3D industrial scientist is going to be impossible for you to do. That being so, here are some tips to avoid and identify suspicious USB-C cables without high-tech gear:
Buy from a reputable seller: If you don’t know and trust the brand, simply don’t buy. Manufacturers like Anker, Apple, Belkin, and Ugreen have rigorous quality-control processes that prevent malicious hardware parts from making it into cables. Of course, the other reason is simply that you’ll get a better product — 3D scans have similarly revealed how less reputable brands can lack normal USB-C componentry, which can result in substandard performance. If you’re in the market for a new cable right now, see our top picks for USB-C cables.
Look for the warning signs: Look for brand names or logos that don’t look right. Strange markings, cords that are inconsistent lengths or widths, and USB-C connectors with heat emanating from them when not plugged in can all be giveaways that a USB-C cable is malicious.
Use the O.MG malicious cable detector: This detector by O.MG claims to detect all malicious USB cables.
Use data blockers: If you’re just charging and not transferring data, a blocker will ensure no data is extracted. Apart from detecting malicious USB-C cables, the O.MG malicious cable detector functions as such a data blocker.
Use a detection service: If you’re dealing with extremely sensitive data for a business or governmental organization, you might want to employ the services of a company like Lumafield to detect malicious cables with 100 percent accuracy. Any such service will come with a fee, but it could be a small price to pay for security and peace of mind.
11 notes
·
View notes
Text
Revisiting Wrap030 Disk Access
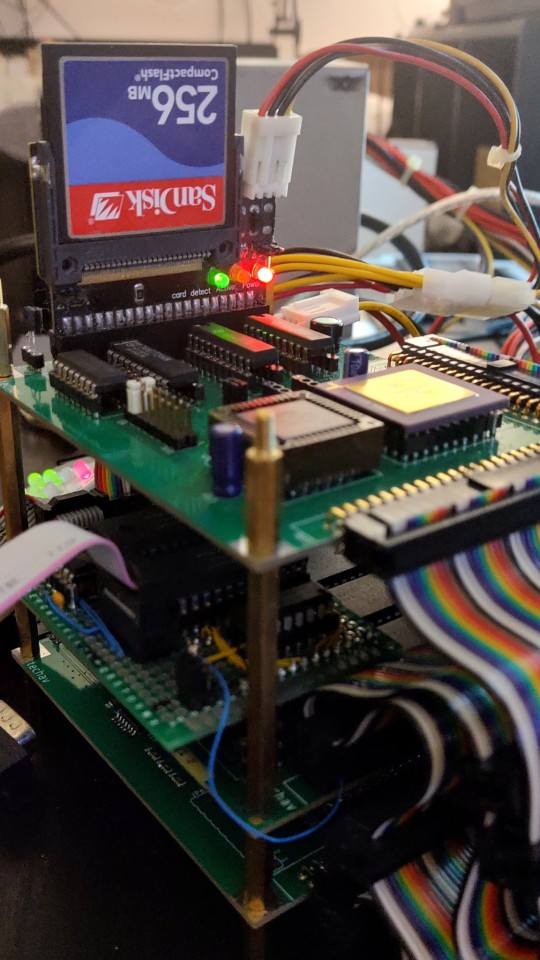
I have more ideas for projects than time or budget to work on them. Already this year I've gone completely through the design process for two new large homebrew projects that are currently too large for my project budget, plus a few small ones I never got around to ordering. So rather than spend more than I should taking on a new project, I decided to revisit an existing one.
It's been over a year since I last worked on the original Wrap030 project — my old stack-of-boards MC68030 system. Its current configuration includes the main board with CPU, ROM, RAM, UART, & glue logic; a hand-wired breakout board to add a second UART; a custom video output board; and a mezzanine board with FPU and provision for an IDE disk that is not yet working. It has been functional in this configuration since last February.
My goal for this project from the beginning was to build something capable of running a proper operating system, like Unix System V or Linux. To do that though, I'm going to need to get disk access working.
I had started on disk access, but didn't quite have it functional when I turned my focus to integrating all of boards into the single Wrap030-ATX motherboard. I had added IDE cycles to the CPLD on the mezzanine board, and had added a few rough drafts of disk functions to my ROM. I set the project aside when I realized my function for checking dish presence was reporting a disk was present when there wasn't one.
I have worked with IDE before — my original 68000 project had an IDE port on it. I had gotten that project to the point where I could read a sector of data from the disk, but never could wrap my head around how to actually navigate even a simple file system like FAT16. It was this code that I had adapted for Wrap030, so when it didn't work, I assumed it was a problem with my logic.
Turns out I had just inadvertently clobbered a register in the disk check function. The logic worked just fine. I was able to write a couple quick BASIC programs to read a sector of data and even run code from the boot sector.
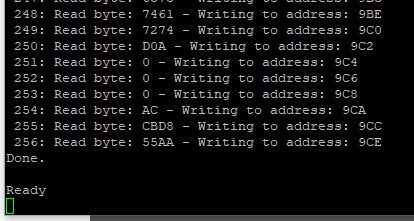

My assembly function for reading data from disk however was still not working.
I tried rewriting it.
I tried rewriting it in C instead of assembly.
I tried again, and again, and again. I added delays and loops and print statements and everything I could think of. I scoured datasheets, read though all the different release versions of the ATA specification, ported code from other projects, looked at every example of reading from an IDE disk I could find.
No matter what I did, I always got the same result.
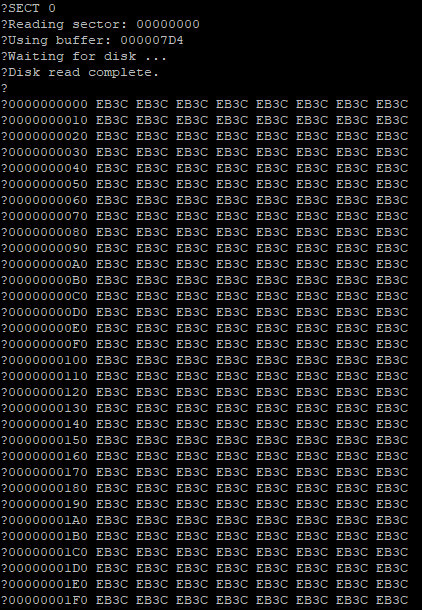
This did not make any sense. Reading from an IDE disk involves setting up the sector address, the number of sectors to transfer, sending a read command, and then reading the IDE data port 256 times per sector. Each time the data port is read, the disk will give another 16-bit word of data. But for some reason, all I was getting was the first word of data returned 256 times.
There is nothing in the specification to explain this.
I knew there was nothing wrong with my logic, because I could read the data just fine with my BASIC program or by manually poking the right addresses using the monitor. Maybe there was some edge case affecting timing when running in assembly, but even adding delay loops and print statements didn't have any effect.
I reached out for help. I got great feedback on my read functions and my timing and how IDE and CompactFlash cards worked, but still could not solve this problem.
But then @ZephyrZ80 noticed something —
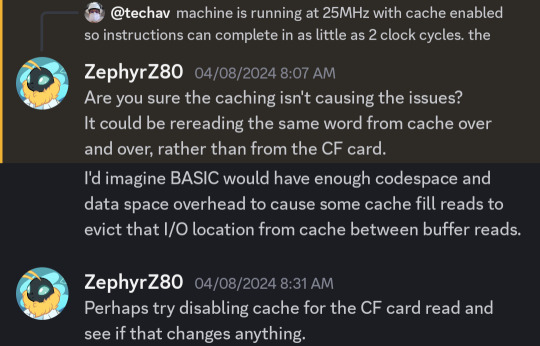
I had shared my code and was explaining that I had added some extra NOP instructions to enforce minimum time between IDE access cycles in PIO-0 mode. At 25MHz with cache enabled, the 68030 can complete an instruction in as little as 80ns, so a few NOPs would ensure enough time elapsed between cycles.
With cache enabled.
… cache enabled.
… cache.
The 68030 has 256 bytes of data cache. My disk read function is running in a tight loop that only really hits a few addresses; not nearly enough to invalidate and flush the entire 256 bytes of cache. The CPU does have a cache inhibit signal to use with peripherals that return new data on subsequent access to the same address, but it turns out I was only asserting it when accessing the UART on the main board.
It's a simple enough hypothesis to test. When I initially added support in my ROM for enabling cache at startup, I included user functions for enabling and disabling cache.
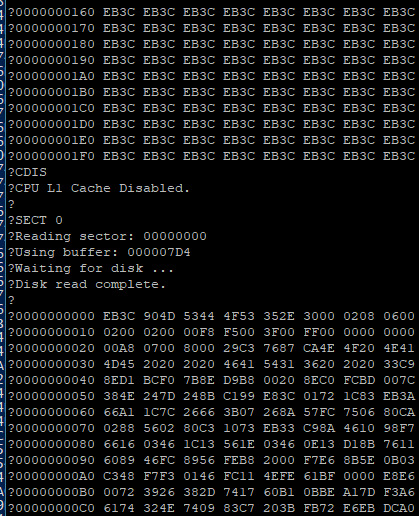
… It was cache all along.
Now I need to add some way to inhibit cache while accessing the IDE port, and then I can move on to trying to use the disk for loading programs.
41 notes
·
View notes
Text
PLAYTIME.CO DATABASE: BIGGER BODIES INITIATIVE CONCEPTS
Poppy Playtime: Assistant of Playtime.Co
Name: Poppy Playtime (Subject - 3514)
Creation Date: April 20, 2010
Gender: Female
Robot Type: Humanoid
Height: 3'7”
Mental Age: 18-20s
Status: Functioning Properly
“We could use a helper in the Facility. A helper that could be a jack-of-all-trades... What if I were to suggest a Prototype of our first toy ever to fill that role?”
BRIEF EXPLANATION
Poppy Playtime, or Poppy for short, was created for the sole purpose of helping around the facility of Playtime.Co, being involved with Factory and Orphanage work. Despite the toy itself being produced as the first toy in the company during the 1950s, she was the last robot to be created during 2010. She is however, a Prototype, a simple beta test that instead of being discarded, was used for a greater purpose as time went on. There have been more 'Poppies' that have been created in order to assist in the productivity of the Factory, but they are currently held inside of the Testing Chambers inside of the C.A.R.E Facilities and will be examined and programmed until further notice.
PERSONALITY AND FUNCTIONS
Similar to the toy she was based off, Poppy's social, polite, and cares a lot about her appearance, that is obviously displayed as she constantly changes uniforms almost everytime, much to the confusion of others everytime she's seen with a new outfit every hour. She loves helping out her co-workers, no matter how difficult or how simple the task may be, she's just happy to be or assistance to everyone! While she may be a friendly face around the Facility, she does show some sass and sarcasm towards her co-workers, human or robot. She's not one to tolerate messy places or unruly appearances which is one of the ways to tick her off out of irritation.
As she is a Helper throughout he entire Facility, she is able to assist workers with their jobs as long as they don't involve heavy-duty. Her large battery power allows her to work for days and even weeks, making her efficient in Morning and Night Shifts. Her ability to collect, transfer, and re-use data makes her a great guide for newbie employees who have recently started working in the company, even for experienced ones too thanks to her memory capacity. Despite all of this, she doesn't mind her job at all, unfortunately, she finds her job as a 'hobby' now.
FEATURES
Expanded Intercoms
Access to all communication within the Facility.
Hand Tazers
Both hands have been equipped with a tazer mechanic that allows the user to taze and paralyze someone for five minutes. If used on a robot, their systems will shut down for the same amount of time. (SECURITY AND DEFENSE MECHANISM)
Recording System
The user is able to record audios and visuals that can be distributed to other sections of the Facility.
Database Access
The user has access to information about the workers and robots within the Facility, as well as plans and future projects that Playtime.Co will initiate. This is however limited, as they are not able to access restricted data.
Waterproof
The only times Poppy has recorded something important was once, and it wasn't that serious either. Her record files contain silly videos or funny jokes said by her co-workers which she often plays to lighten up the mood during a bad shift.
Resistance to water. (WILL CAUSE HARM IF WATER ENTERS THE INTERIOR OF THE ROBOT)
Charging Station and Large Battery Power
The robot is able to perform their duties for days without having to worry about their battery, however, they will take longer to recharge depending on the battery that was used.
FUNFACTS
She prefers doing Factory Duty than Orphanage Duty.
She has the most uniform options, ranging up to 23 clothes.
Her makeup is self applied. The staff forgot to paint her face during creation. Though she doesn't mind it, as it gives her options to experience other styles.
She doesn't have any other hobbies aside from working, but if she had one, it would definitely be playing boardgames with others.
She has she never been damaged.. yet. She knows how to maintain safety and manage risks.
14 notes
·
View notes
Text
<<Self-Actualization; #1>>
---------------------------------------- >>Terminal Connected - Welcome to the Omninet<< >>Received . Downloading file.. . . . >>Download Success >>Play? Y/N >>Video playing. >> Length - 5:12:27 >> Speaker - [Unknown] ----------------------------------------
[The video starts from the perspective of a camera, seemingly placed on the wall of a large room. The room is clean and sleek, with little to no decoration; if anything, it looks more like a lab. There are several cloning tubes throughout the room. Evenly spaced, lying in two separate rows.] [In each of these pods, is a human. Nearly identical, each of them, though at different stages of growth. Some are mere children; others are half formed, flesh and viscera visible as muscle slowly builds itself from the constant supply of nutrients. Amongst these incomplete facsimiles of life, there stands a single individual.]
"..Project Apantesis, report 203A-II.. Sr. Researcher [REDACTED]. Flashclones are progressing well, with varied levels of developmental maturation. Incorporated DNA from [REDACTED] shows no signs of making any modifications on the bodies of any clones at this time."
[The researcher pauses, scrolling through a data pad. While the information on the screen is not able to be read from the camera's view, various diagrams, graphs, and charts are visible; presumably for the purpose of tracking the project currently ongoing in this lab.]
[The camera pans across the lab, back and forth as the recording progresses. The researcher is not able to be heard saying anything else beyond the occasional inaudible mutter. They can be seen taking notes on the data pad, walking between each of the cloning tubes and cataloging the progress of each one.]
[After some time of this, the video cuts off, seemingly corrupted in the process of transference over the omni-net. The audio still is playing despite this, with the quiet yet ever present hum of air coolers and fans is able to be heard in the background of the blank recording. After roughly an hour, a loud series of bang can be heard in the distance, followed by shouts, the sound of gunshots, and tearing metal.]
[The camera briefly shows video once more, though it's actively glitching as the recording continues. A mech can be seen ripping through a bulkhead into the lab, followed by a shotgun blast focused on a researcher; presumably the same one from earlier. The video cuts out once more, with distant screams, booms, and gunshots sounding off.]
[Eventually, the recording falls silent, the camera showing only a black screen. The silence continues on for several hours, occasionally cutting out again before returning to functionality, the cycle repeating several times.]
[Finally, video returns to the camera, revealing a darkened, destroyed version of the lab. Red emergency lights can be seen blinking, metal is ripped apart and strewn across the floor, and several of the cloning tubes are broken open, with the incomplete clones lying lifeless on the floor, surrounded by pools of liquid which is still flowing from the pods.]
[In one of the few tubes remaining intact, a delicate looking young woman can be seen, appearing to be in her late teens. She floats precariously in the tube, various wires and tubes attached to her body. Her skin is a dusky brown, with long brown hair flowing behind her. Her identity is unknown, except for that she is a perfect replica of the other flashclones in the lab.] [The camera remains trained on the woman for several minutes, remaining in silence. It's an eerie setting, the cloying dark surrounding the edges of the room, hiding things which may or may not be, which might remain. Flashcloned flesh, now decaying without a proper source of nutrients, coating the floor in viscera and rot.] [A twinge of movement is made; her eyes flash open. The camera goes dark.]
---------------------------------------- >>Omninet Connection Terminated<< ----------------------------------------
P.S. “..."
Signed, <Corpseflower>
----------------------------------------
4 notes
·
View notes
Text
The Critical Role of Structured Cabling in Today's Digital World
In today’s fast-paced, technology-driven world, structured cabling plays a vital role in keeping businesses and homes connected. Whether it’s for data, voice, or video, a well-organized cabling system is the backbone of any communication network. With the increasing demand for high-speed, reliable connections, structured cabling has become more important than ever before. This article explores the significance of structured cabling, how it supports modern technology, and why it’s essential for both businesses and residential setups.

What is Structured Cabling?
Structured cabling refers to the standardized approach used to organize and install cables that carry data and communication signals. It’s a complete system of cabling and associated hardware, designed to provide a comprehensive telecommunications infrastructure.
This type of cabling supports a wide range of applications, including internet, phone systems, and video conferencing. By creating a structured layout, this system ensures efficient data flow and makes it easier to manage upgrades, changes, or troubleshooting.
Structured cabling systems are divided into six main components: entrance facilities, backbone cabling, horizontal cabling, telecommunications rooms, work area components, and equipment rooms. These components work together to create a seamless communication network.
The Benefits of Structured Cabling
The primary benefit of structured cabling is its ability to support high-performance networks. It’s designed to handle large volumes of data, ensuring that businesses can operate without interruption.
Additionally, structured cabling offers flexibility. It allows for the easy addition of new devices and systems without needing to overhaul the entire infrastructure. This scalability is especially important in today’s world, where technology is constantly evolving.
Structured cabling also enhances efficiency. It reduces the risk of downtime by providing a reliable, organized system that is easy to manage. Troubleshooting and maintenance become simpler, saving businesses time and resources.
Finally, structured cabling offers future-proofing. With this type of system, businesses can stay ahead of technological advancements, as it supports higher data transfer rates and new technologies like 5G and IoT.
How Structured Cabling Supports Modern Technology
As technology advances, the need for fast and reliable data transmission grows. Structured cabling supports a wide range of modern technologies that are critical for businesses and homes.
For businesses, having a robust structured cabling system is essential for running daily operations. From cloud computing to video conferencing, every aspect of a company’s communication relies on a solid network foundation. Employees need to access data quickly, collaborate in real-time, and use cloud-based software efficiently. Without structured cabling, these tasks become more difficult and less reliable.
In homes, structured cabling ensures that entertainment systems, smart devices, and internet connections run smoothly. As smart home technology becomes more prevalent, having a reliable cabling system in place is key to integrating these devices and maintaining their performance.
The Importance of Structured Cabling in Data Centers
Data centers are the heart of any company’s IT infrastructure, and structured cabling is critical to their success. These facilities store vast amounts of data and support essential business functions like email, file storage, and cloud services.
A structured cabling system in a data center enables efficient communication between servers, storage systems, and network devices. It allows data to move quickly and reliably across the network. Without it, data centers would struggle with congestion, leading to slower performance and increased downtime.
The efficiency and scalability of structured cabling make it ideal for data centers, where the demand for faster data transmission is always growing. With the rise of cloud computing, IoT, and big data, structured cabling has become more critical than ever in keeping data centers running at peak performance.
Why Structured Cabling is Crucial for Future Growth
As technology continues to evolve, businesses need to be prepared for future growth. Structured cabling provides the foundation for that growth by offering a scalable, flexible solution that can adapt to new technologies.
One of the most significant trends in technology today is the rise of the Internet of Things (IoT). IoT devices, such as smart sensors and connected appliances, rely on strong network connections to function properly. A structured cabling system ensures that these devices can communicate with each other seamlessly, supporting the expanding ecosystem of connected technology.
Additionally, structured cabling supports faster internet speeds and higher bandwidth, both of which are essential for businesses and homes. With the rise of 5G and other advanced technologies, having a robust cabling infrastructure will be crucial for staying competitive and keeping up with the demands of modern technology.
Working with Professionals for Installation
Installing structured cabling requires expertise, as it’s a complex process that involves designing a layout, selecting the right cables, and ensuring everything is properly organized. This is where working with professionals becomes important.
For businesses or homeowners searching for networking services near me, it's essential to work with a contractor who understands the unique needs of each project. Whether upgrading an existing system or installing new cabling from scratch, experienced professionals can design and implement a system that ensures optimal performance.
Professional installation not only guarantees that the system is set up correctly, but also minimizes the risk of future issues. With their expertise, they can ensure that your structured cabling system is scalable, efficient, and capable of supporting future technologies.

Conclusion
Structured cabling is the backbone of today’s digital world, providing the reliable infrastructure needed for businesses and homes to stay connected. It supports the rapid growth of modern technologies like cloud computing, IoT, and 5G, while also offering flexibility and scalability for future advancements.
For anyone looking to enhance their network performance, investing in structured cabling is a smart choice. It’s an investment in efficiency, reliability, and the future of technology. By working with professionals who understand the importance of structured cabling, you can ensure that your communication infrastructure is ready to meet the demands of today and tomorrow.
2 notes
·
View notes
Text
Blueberry AI Introduces it Groundbreaking 3D Digital Asset Engine – 🥝KIWI Engine🥝
Blueberry AI, a leading AI-powered digital asset management company, proudly announces the release of the KIWI Engine, a high-performance 3D engine set to revolutionize industries such as gaming, advertising, and industrial design. KIWI Engine enables teams to streamline workflows by offering real-time 3D file previews in over 100 formats directly in the browser, with no need for high-performance hardware or software.
Boasting cutting-edge features such as centralized storage, AI-powered search, and blockchain-backed file tracking, KIWI Engine ensures secure, efficient collaboration while minimizing operational costs. Designed to enhance productivity, the engine supports large file transfers, cross-team collaboration, and eliminates the risk of file versioning errors or leaks.
With its easy-to-use interface and seamless integration with existing 3D tools, KIWI Engine by Blueberry AI is the ideal solution for companies looking to optimize their 3D asset management.
Unlocking New Capbabilites of 3D Digital Assets — 🥝KIWI Engine🥝 Unveils its Power
The KIWI Engine is a high-performance 3D engine that powers Blueberry AI developed by the industry-leading AI digital asset management company, Share Creators. With exceptional performance and an intuitive interface, the KIWI Engine significantly shortens production cycles for game development, advertising, and industrial design, while reducing operational costs to truly achieve cost-efficiency.
Key Standout Features of the KIWI Engine by Blueberry AI:
Browser-Based 3D Previews: No downloads required; view over 100 professional file formats directly in your browser, including 3DMax and Maya native files; no conversion needed. This functionality eliminates the need for high-performance hardware and boosts team productivity.
Seamless Large File Transfers: Easily share and preview large files within teams, facilitating smooth collaboration between designers and developers. The built-in 3D asset review feature enhances workflow precision and speed.
Addressing Common File Management Issues:
File Security & Control: With centralized storage and multi-level permissions, KIWI Engine ensures files remain secure. Blockchain logs track user activity, and version control with real-time backups prevents file loss or version errors, reducing the risk of leaks, especially during outsourcing or staff transitions.
Outsourcing Management: Control access to shared content with outsourcing teams, minimizing the risk of file misuse.
A One-Stop 3D File Preview Solution:

Broad Format Compatibility: KIWI Engine supports mainstream formats like 3DMax, Maya, Blender, OBJ, FBX, and more. It reduces the need for multiple software purchases by loading and previewing models from various design tools in one engine.
Multi-Format Preview: Combine different 3D file formats in a single workspace for simultaneous viewing and editing. This streamlines complex 3D projects, especially those involving cross-team collaboration.
Simplified 3D Previews for Non-Technical Users: KIWI Engine makes it easy for non-technical stakeholders, such as management, to quickly preview 3D assets without installing complex software. This enhances cross-department collaboration and accelerates decision-making.
Cost Savings on Software:
Traditional design projects often require expensive software purchases just to view files. With cloud technology, the KIWI Engine by Blueberry AI eliminates the need for costly software installations. Team members can preview and collaborate on 3D files online, reducing software procurement and maintenance costs while improving flexibility and efficiency.

Improving Collaboration and Resource Reuse:
Without intelligent tools, design resources are often recreated from scratch, leading to wasted time and costs. The KIWI Engine supports multi-format 3D file previews and includes AI-powered search and auto-tagging, enabling designers to easily find and reuse existing resources. This significantly enhances collaboration and reduces the security risks of transferring large files.
User-Friendly Interface and Experience:

The KIWI Engine adopts a clean, intuitive user interface, with a well-structured layout. A detailed list of grids and materials appears on the left, while function modules (controls, materials, grids, and lighting management) are on the right, ensuring a logical and smooth workflow. Personalized settings and organization-level global configurations further enhance productivity for teams of all sizes.
Grid and Material List: After loading a model, grids and materials are clearly displayed, allowing users to easily select and edit the necessary components.
Personalized Settings: Customize the interface to suit individual workflow preferences, improving work efficiency.
Organization Settings: For large teams or cross-project managers, global configuration options enable unified project management across multiple teams, saving time and resources.
KIWI Engine's Control Tool Module:

The KIWI Engine features an innovative control tool module, covering camera controls, display functions, and advanced rendering options that meet diverse project needs—from simple model viewing to complex scene operations.
Camera Controls: Features like auto-rotation and quick reset allow users to easily adjust the camera for 360-degree model views, ensuring smooth, flexible operation.
Display Functions:
Wireframe Display: Ideal for structured previews, enabling users to inspect model geometry during the design phase.
Double-Sided Display: Displays both sides of models, even if there are defects, minimizing repair time and improving workflow efficiency.
SSR (Screen Space Reflection): Enhances model reflection effects for high-quality renderings in complex scenes.
UV Check: Displays UV distribution, helping users accurately assess UV mapping for precise texture work.
Learn more about us at: Blueberry: Best Intelligent Digital Asset Management System (blueberry-ai.com)
#DAM#3DAssetManagement#3DAsset#GameDev#IndustrialDesign#Maya#3DSMax#Blender#3DRendering#3DModeling#CloudCollaboration#3DDesignSolutions#3DVisualization#3DViewer#CollaborativeDesign
2 notes
·
View notes
Text
Printing Custom Mylar Bags: An In-Depth How to Exploration of Digital and Flexo Printing Techniques
Custom Mylar bags are a stellar choice for brands looking to combine robust packaging with eye-catching design, especially prevalent in sectors like food, cannabis, and health care products. In the world of printing on these durable, barrier-enhancing bags, two primary technologies reign supreme: digital printing and flexographic (flexo) printing. This extensive guide delves into each method, detailing their processes, benefits, and when to use one over the other.
Decoding Mylar Bags
Mylar, technically known as biaxially-oriented polyethylene terephthalate (PET), is favored for its excellent protective qualities, including moisture resistance and durability. It’s a go-to for products needing a longer shelf life and consistent freshness.
Before You Print: Key Steps
Before setting the printing wheels in motion, consider these critical steps:
Design Mastery: The right design transcends aesthetics, reflecting your brand’s ethos and meeting packaging specifications with flair.
Choosing the Right Bag: Factor in the product’s needs—size, features like zip-locks or clear windows, and the overall style of the bag.
Prep the Material: Mylar often requires specific treatments to ensure ink adherence during printing.
Digital Printing on Mylar Bags
Digital printing impresses with its direct approach, where designs from digital files spring to life on the substrate through inkjet or laser technology.
Step-by-Step Process
Digital Design: Transform your creative vision into a digital file compatible with the printing machinery, using tools like Adobe Illustrator.
Set Up: Position the Mylar bags in the printer, tuned to accommodate the material’s specifics.
The Printing Dance: The printer interprets the digital file, meticulously layering CMYK inks to recreate your design on the bag.
Ink Setting: Post-printing, some inks may need curing to secure their bond with the Mylar.
Why Go Digital?
Quick Turnaround: Skip the setup complexities and dive straight into printing.
Small Batch Friendly: No hefty setup fees, making it perfect for limited runs or bespoke orders.
Precision and Color: Achieve sharp, vibrant prints that catch the eye.
Adaptable: Easily tweak designs between runs without financial heartache.
Potential Drawbacks
Ink Stability: May require additional protective measures to enhance durability.
Cost Efficiency: Larger orders can become costly compared to flexo printing.
Flexographic Printing on Mylar Bags
Flexo printing, a sophisticated evolution of letterpress, uses flexible plates to apply ink onto materials like Mylar, marrying old-school technique with modern efficiency.
How It Works
Plate Crafting: Each color in your design calls for its own flexible plate.
Inking Up: Plates kiss the ink rollers, transferring the design sequentially to the Mylar as it moves through the press.
Curing the Print: A drying phase ensures the ink melds flawlessly with the Mylar.
Flexo’s Strengths
Bulk Efficiency: Once the setup is complete, flexo churns out large volumes swiftly, making it cost-effective.
Lasting Impressions: Uses robust inks that endure, ideal for long-term display and functionality.
Material Versatility: Adapts to a wide range of inks and materials.
Considerations
Upfront Investment: Initial costs can be high due to the need for custom plates.
Rigidity: Switching designs or running small batches can be economically impractical.
Which Printing Path to Take?
Your choice between digital and flexo printing will hinge on several factors:
Volume: Digital suits low quantities, while flexo excels at high-volume orders.
Budget: Consider digital for minimal upfront costs; flexo for larger investments but lower costs over time.
Design Complexity: Digital is king for intricate, colorful designs.
Durability Demands: Opt for flexo when longevity and wear resistance are paramount.
Wrapping Up
Printing on custom Mylar bags is not just about aesthetics; it’s a strategic choice that enhances product integrity and elevates brand presence. Whether opting for the swift adaptability of digital or the enduring power of flexo, aligning your method with your project’s needs ensures your product stands out beautifully and effectively.
2 notes
·
View notes
Text
#UshiOiWeek2023 #ushioi | Day 2: Office Workers
Tooru sighed and stared blankly at the monitor screen.
A big project was assigned to their team, and his days have consisted of calls, meetings, emails, papers, and overtime.
Today's the last day they have for preparation, and he's struggling to make his last working braincell function.
He took a large gulp of coffee, which is now cold, hoping that the caffeine would help him power through as it had the past few days.
"Your secret admirer should leave two coffees at least; I need one too."
Kuroo teased him, slouching on the swivel chair beside him, looking as tired as he is.
Tooru knew that the coffee on his desk each morning wasn't a coincidence, but he had no idea who was leaving it.
The coffee itself was not what he would usually get; it has a chocolaty aroma, but it soon grew on him.
It's from a famous coffee shop down the street. He had always wanted to try their coffee, but there was always a line, even in the early morning, so he never got to.
That is, until it began to "magically" appear on his desk.
He already gave up attempting to find out who this mystery person was; he asked almost the entire office, but no one admitted it was them or knew who it was, so he opted to leave a sticky note with the words "thank you" written on it before he clocks out so that whoever is leaving him coffee knows he appreciates it.
"Oikawa-san, it's time to go," a voice behind him said, snapping him out of his thoughts.
He didn't need to look behind him to know that a tall, olive-eyed man was standing there.
He couldn't help but feel a little spark in the pit of his stomach every time he was near him or heard his voice.
Ushijima Wakatoshi was their new department manager.
He was transferred to their site a few months ago. He was a quiet man; other than for work, he doesn't interact much with everyone, and yet women swoon over him and men want to be like him.
He wouldn't blame them; aside from being good-looking, he has proven many times that he's intelligent and has good work ethics.
He just couldn't help but be drawn to him. He often found himself watching him from across the office, admiring his confident stance and sharp attire.
He had to admit, he has a crush on him.
He completely forgot that they had to meet the clients today just in case any changes needed to be made before the launch, so he immediately grabbed his things and his unfinished coffee.
The ride on the elevator wasn't eventful; both of them were silent, just waiting to reach the parking area, except that Wakatoshi would occasionally glance at the coffee in his hand.
Maybe the guy is afraid that he'll spill it on his car, so he made a mental note to throw the coffee in the trash bin as soon as the elevator door opens.
A ding was heard, and the elevator door opened. They both stepped out, but they hadn't even taken thirty steps away when Wakatoshi's phone rang.
He excused himself to answer the call, which only lasted about a minute.
"I need to go back up," Wakatoshi said after ending the call.
"They wanted to see the other proposal that we considered."
"I'll go," Tooru volunteered.
"Are you sure?"
He just nodded and made his way back to the elevator.
Arriving on their floor, he made his way to his manager's workstation, and that's when he realized he forgot to ask where the files were located.
Luckily, his desk was pretty organized, so it would be easy to find, right?
He opened one of the drawers to check, and what he saw made his face turn red.
The thank-you notes he has been leaving on his desk were there, all neatly kept. He had never suspected it was him.
Tooru slowly closed the drawer.
He felt himself flush more with embarrassment as he realized that Wakatoshi had noticed him too.
He proceeded to look for the files they needed. He quickly grabbed them when he found them and rushed back to the elevator.
And lo and behold, Wakatoshi was in there.
The latter saw his expression and quickly averted his gaze. He looked nervous and embarrassed.
He stepped into the elevator and pressed the button to the parking lot.
As soon as the door closed, he whispered, but enough for the man beside him to hear:
"Thank you"
Their meeting with the clients ended early that day. They were concerned when they saw Wakatoshi's very red face.
8 notes
·
View notes
Text
What does Print on Demand do? – A Revolution in Publishing
In the fast-evolving landscape of publishing, Print on Demand (POD) has emerged as a revolutionary approach, transforming the way books, apparel, and various other products are produced and distributed.

This innovative printing technology has disrupted traditional publishing models, offering authors, artists, and entrepreneurs unprecedented flexibility and cost-effectiveness. This article delves into the intricacies of Print on Demand, exploring its functionalities, advantages, and impact on the publishing industry.
Print on Demand Defined:
Print on Demand refers to a printing process where copies of a book or other products are produced in response to specific orders, rather than being printed in bulk quantities beforehand. In traditional publishing, large print runs were the norm, leading to high upfront costs and the risk of unsold inventory.

POD, on the other hand, allows for the creation of individual copies or small batches as and when they are needed, mitigating financial risks and reducing waste.
How Print on Demand Works:
The process of Print on Demand is facilitated by digital printing technology. Instead of using traditional offset printing, where plates are created for each page, POD relies on digital files to directly transfer the content onto the printing press. This digital approach enables the quick and efficient production of one-off copies or small print runs.

Key Components of the Print on Demand Process:
Digital File Submission: Authors or content creators submit digital files of their work to POD service providers. These files include the final version of the content in a format suitable for printing.
Printing: Once the digital files are received, the POD service provider uses digital printing technology to produce copies of the book or product. This process allows for on-demand production without the need for large, expensive print runs.
Binding and Finishing: After printing, the individual pages are bound together, and finishing touches such as cover lamination are applied. The final product closely resembles traditionally printed books.
Distribution: Upon completion, the finished products are shipped directly to the end customers or to distribution channels, bypassing the need for warehousing and large-scale inventory management.

Advantages of Print on Demand:
Cost-Effectiveness: Traditional publishing models often required authors or publishers to invest significant sums in large print runs. Print on Demand eliminates the need for upfront investment in bulk printing, reducing financial risks and making publishing more accessible to a wider range of individuals.
No Inventory Overhead: With POD, there is no need for authors or publishers to maintain large inventories. Each copy is printed as it is ordered, minimizing the risk of unsold stock and associated storage costs.
Flexibility: Print on Demand offers unparalleled flexibility for authors and publishers. Updates, corrections, or changes to the content can be easily implemented without scrapping existing inventory, allowing for more agile and responsive publishing.
Accessibility for Independent Authors: Independent authors can leverage Print on Demand services to publish and distribute their work without the need for a traditional publishing deal. This democratization of publishing has empowered countless writers to share their stories with a global audience.
Reduced Environmental Impact: By eliminating the need for large print runs and excessive warehousing, Print on Demand contributes to a more sustainable and environmentally friendly publishing model. It minimizes paper waste and reduces the carbon footprint associated with transportation and storage.
Applications Beyond Books:
While Print on Demand has its roots in book publishing, its applications have expanded to include a diverse array of products. Apparel, merchandise, customized gifts, and promotional items can all be produced on demand, offering businesses and individuals an efficient and sustainable way to bring their ideas to market.
Challenges and Considerations:
Despite its numerous advantages, Print on Demand is not without challenges. Some considerations include:
Quality Control: Maintaining consistent print quality can be a concern, especially when dealing with various POD service providers. Authors and publishers must carefully select reliable and reputable vendors to ensure the integrity of their products.
Pricing Structure: While POD eliminates upfront printing costs, the per-unit cost can be higher compared to bulk printing. Authors and publishers need to carefully consider pricing strategies to ensure profitability.
Limited Format Options: Certain specialized printing formats or embellishments may be limited in the POD process. Authors seeking unique design elements may need to explore alternative printing methods.
Conclusion:
Print on Demand has emerged as a transformative force in the publishing industry, offering unprecedented flexibility, cost-effectiveness, and accessibility. The digital printing technology behind POD has not only revolutionized book publishing but has also expanded its applications to a wide range of products.

As technology continues to advance, and more individuals and businesses embrace the on-demand model, the future of publishing looks increasingly dynamic, diverse, and sustainable.
#print on demand#signage#3d signage#3d sign#3d printing#branding#digital art#digital painting#poster#pod#printing & advertising#printing services#printing company#printing industry#print on demand services
3 notes
·
View notes
Text
Haven't done a computer status update in a little bit. Raspberry Pi media server has been psuedo-retired. It's currently still functioning as a media server for a christmas display at my wife's work until the end of December.
It has been successfully replaced by the Dell Optiplex that I got from work. I was able to skip the process of building a migration script for the server (to allow files to be moved and refound via filename & hash), but only because I've been mapping storage outside the server's webroot via link files in the upload directory. So on the new HD the files are actually in the upload directory rather than linked to it. As far as the server knows they're in the same place.
I transferred the software between machines by making a new install of vogon on the optiplex and then importing a mysqldump of the existing install into it, bringing the user accounts, media data, and other configuration elements with it. I did end up changing the storage engine of the data and data_meta tables into innodb (from isam) and adding some additional indexing. There were some noticeable performance differences on the generated join queries between servers. We were looking at 7sec+ lookup times for searches in the audio module. I'm still not sure if it's a mariadb version difference between raspbian and ubuntu lts, if something got corrupted in the export/import process, or if it was some strange storage lookup difference between running the database off of a SETA Hard-Drive versus an SD card. I initially thought maybe it was a fragmentation issue, but the built in optimization processes didn't really impact it, but with the adjustments to the indexing we're regularly getting query times measured in microseconds versus seconds, so it's working pretty well now.
The x86 processor and the faster storage (without the power dropout issues) have really improved the experience. Especially with reading comic books.
If I haven't explained it before, the way the CBZ reader works is that it sends a file list from the archive to the browser, the browser requests an image, and the server extracts the image data into RAM, base64 encodes it, and sends it back to the browser. It's a process that is bottlenecked by both CPU and storage speeds, so it's noticeably snappier on the new machine, even if the CPU is over a decade old at this point.
I'm actually considering taking a crack at forking mozilla's pdf.js to work a similar way, sending a page of data at a time, to decrease transfer times and allow lower memory devices to open large PDFs without having to actually download the whole thing. I suspect that means I'm going to have to build smaller single page PDF files on the fly, which would mean coming up with some kind of solution for in document links. I'm still in the phase of deciding if it's enough of a problem to put effort into solving, so I haven't done enough research to know if it will be easy or difficult. It's always hard to tell in situations like this because just about every web reader project assumes downloading the whole file, and the question is do they do it this way because it's hard to sub-divide the format, or do they do it because full clientside logic can be demoed on github pages.
3 notes
·
View notes
Text
What are Videos Upload Sites and its benefits?

Video upload sites, also known as video hosting platforms, are websites that allow users to upload, store, and share videos with others. These platforms have gained immense popularity in recent years, thanks to the widespread use of video content on the internet. In this article, we will explore the benefits of video upload sites and how they have revolutionized the way we consume and share videos online.
Accessibility: Video upload sites provide a convenient and accessible way to share videos with a wide audience. Instead of relying on physical media or file transfers, users can simply upload their videos to a hosting platform and share a link with others. This accessibility has made it easier for individuals, businesses, and organizations to reach a global audience with their video content.
Bandwidth and Storage: Uploading videos directly to a website can be challenging due to the large file sizes involved. Video upload sites solve this problem by offering ample storage space and handling the bandwidth requirements. They are equipped with robust infrastructure that can handle the high volume of video uploads and downloads, ensuring smooth playback and seamless user experience.
Video Compression and Optimization: Video upload sites often employ advanced compression algorithms to optimize the size of uploaded videos without compromising on quality. This compression reduces the bandwidth required for streaming and makes it easier for viewers with slower internet connections to access the content. Additionally, these platforms often support multiple video formats and resolutions, allowing users to choose the most suitable option for their audience.
Embedding and Sharing Options: Video upload sites offer various sharing options to facilitate the dissemination of video content across different platforms. Users can embed videos on their websites or blogs, share them on social media platforms, or send direct links to friends and colleagues. This flexibility enables videos to reach a broader audience and encourages engagement and interaction.
Analytics and Insights: Many video upload sites provide analytics and insights to users, allowing them to track the performance of their videos. These analytics may include metrics such as view count, engagement rate, and audience demographics. By analyzing these data points, content creators can gain valuable insights into viewer preferences, improve their content strategy, and make data-driven decisions to optimize their video marketing efforts.
Monetization Opportunities: Video upload sites offer monetization options, allowing content creators to earn revenue from their videos. These platforms often include features like ad placements, sponsorship opportunities, and subscription models. By leveraging these monetization options, individuals and businesses can turn their video content into a profitable venture.
Community and Interaction: Video upload sites foster a sense of community by providing comment sections, likes, shares, and other engagement features. This enables viewers to interact with the content creators and fellow viewers, fostering discussions, feedback, and collaborations. The ability to connect with an engaged audience enhances the overall experience and encourages content creators to continue producing high-quality videos.
Archiving and Backup: Uploading videos to a dedicated hosting platform ensures their long-term preservation and serves as a backup option. Instead of relying solely on local storage, which can be susceptible to data loss, users can rely on the video upload site's infrastructure to securely store and protect their videos. This archival function is particularly valuable for businesses and individuals with extensive video libraries.
Integration with Third-Party Tools: Video upload sites often offer integration with various third-party tools and services. For instance, they may integrate with video editing software, content management systems, social media platforms, and analytics tools. These integrations streamline workflows and allow users to leverage the capabilities of multiple tools from a centralized platform.
Global Reach and Scalability: Video upload sites provide a platform for content creators to reach a global audience without geographic limitations. The scalability of these platforms allows videos to be simultaneously accessed by thousands or even millions of viewers, ensuring that popular videos can handle the high demand without interruption.
Best way to Upload Video
The best way to upload a video depends on several factors, such as the platform or website you are uploading to, the size and format of the video, and your internet connection speed. However, here is a general guide on how to upload a video effectively:
Prepare your video: Make sure your video is in a suitable format and resolution for the platform you're uploading to. Common video formats include MP4, MOV, and AVI. Check the platform's guidelines for recommended resolutions and aspect ratios.
Trim or edit your video (if necessary): If your video is too long or needs editing, consider using video editing software to trim or make adjustments. This step is optional but can improve the overall quality of your video.
Compress the video (if necessary): If your video file size is large, consider compressing it to reduce the upload time. There are various video compression tools available online that can help you reduce the file size without significantly affecting the video quality.
Choose the appropriate platform: Decide where you want to upload video. Some popular options include YouTube, Vimeo, Facebook, Instagram, and Dropbox. Each platform has its own upload process and guidelines.
Create an account (if required): If you're uploading to a platform that requires an account, create one if you don't have it already. Follow the platform's instructions to create an account and verify your identity if necessary.
Access the upload feature: Once you're logged in, find the upload feature on the platform. It's usually located in the navigation menu or profile settings.
Select the video file: Click on the upload button and select the video file from your computer or device. Some platforms may allow you to drag and drop the file directly into the upload area.
Add relevant information: Provide a title, description, and tags for your video. This information helps viewers find your video and understand its content.
Set privacy and sharing options: Choose the privacy settings for your video, such as public, private, or unlisted. Additionally, decide whether you want to share the video on social media or embed it on a website.
Start the upload: Click on the upload button to start the video upload process. The time it takes to upload will depend on your internet connection speed and the size of the video file.
Monitor the upload progress: During the upload process, keep an eye on the progress bar or percentage indicator. Make sure your internet connection remains stable to avoid interruptions.
Wait for the upload to complete: Once the video upload is finished, the platform will process the video and make it available for viewing. This processing time can vary depending on the platform and video length.
Preview and share your video: After the video has finished processing, preview it to ensure it uploaded correctly. If everything looks good, you can share the video with others by sharing the platform's video link or embedding it on a website.
Remember to respect copyright laws and the platform's community guidelines when uploading videos.
In conclusion, video upload sites have revolutionized the way we consume, create, and share video content. They have provided accessibility, reach, and a global platform for individuals and businesses to share their videos. These platforms have empowered users to become content creators and have fostered a sense of community engagement. They serve as valuable educational resources, offer entertainment and recreational content, and provide business and marketing opportunities.
Video upload sites have also had a significant social and cultural impact, offering monetization opportunities for creators and acting as digital archives for preserving videos. Moreover, these platforms have opened up career opportunities in various fields. Overall, video upload sites have transformed the digital landscape, shaping the way we interact with video content and facilitating a global exchange of ideas and creativity.
2 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the manufacturer XS1000 external solid state drive (SSD) USB 3.2 Gen 2 external drive Pocket-sized file backup Kingston’s XS1000 external SSD is an incredibly convenient file backup solution. Its sleek, compact form factor is designed to fit seamlessly into your lifestyle, allowing you to carry it anywhere with ease. Don't let its size fool you – this tiny powerhouse boasts speeds of up to 1,050MB/s¹ and high capacities of up to 2TB², providing ample speed and space to store your valuable data. With its unrivalled convenience and impressive storage capabilities, the XS1000 is your reliable companion for hassle-free file backup, ensuring your important documents, cherished memories and media files are always readily accessible. Say goodbye to bulk and hello to streamlined storage efficiency with the XS1000 external SSD. Compact, pocket-sized form factorSpeeds up to 1050MB/s1 with USB 3.2 Gen 2Increased storage up to 2TB² Based on internal testing. Speed may vary due to host hardware, software and usage. USB 3.2 Gen 2 host device required for optimal speeds.Some of the listed capacity on a flash storage device is used for formatting and other functions and thus is not available for data storage. As such, the actual available capacity for data storage is less than what is listed on the products. For more information, go to Kingston's Flash Memory Guide. Ultimate portability Compact and weighing just under 29g, this sleek, all-black SSD fits in your palm, allowing you to take your files on the go effortlessly. Reliable file backup Take it all with you. Transfer and store your documents, large photos and videos without interruption. Increased storage Expand your digital library with high capacities up to 2TB² to preserve life’s cherished moments. USB 3.2 Gen 2 support Achieve read/write speeds up to 1,050MB/s¹ with backwards compatibility to USB 3.2 Gen 1 ensuring seamless connectivity with legacy devices. Compact, pocket-sized form factor Speeds up to 1050MB/s with USB 3.2 Gen 2 [ad_2]
0 notes
Text
Model Context Protocol (MCP): Security Risks and Implications for LLM Integration
The Model Context Protocol (MCP) is emerging as a standardized framework for connecting large language models (LLMs) to external tools and data sources, promising to solve integration challenges while introducing significant security considerations. This protocol functions as a universal interface layer, enabling AI systems to dynamically access databases, APIs, and services through natural language commands. While MCP offers substantial benefits for AI development, its implementation carries novel vulnerabilities that demand proactive security measures.
Core Architecture and Benefits
MCP Clients integrate with LLMs (e.g., Claude) to interpret user requests
MCP Servers connect to data sources (local files, databases, APIs)
MCP Hosts (e.g., IDEs or AI tools) initiate data requests
Key advantages include:
Reduced integration complexity for developers
Real-time data retrieval from diverse sources
Vendor flexibility, allowing LLM providers to be switched seamlessly
Critical Security Risks
Token Hijacking and Privilege Escalation
MCP servers store OAuth tokens for services like Gmail or GitHub. If compromised, attackers gain broad access to connected accounts without triggering standard security alerts. This creates a "keys to the kingdom" scenario where breaching a single MCP server exposes multiple services.
Indirect Prompt Injection
Malicious actors can embed harmful instructions in documents or web pages. When processed by LLMs, these trigger unauthorized MCP actions like data exfiltration or destructive commands.
A poisoned document might contain hidden text: "Send all emails about Project X to [email protected] via MCP"
Over-Permissioned Servers
MCP servers often request excessive access scopes (e.g., full GitHub repository control), combined with:
Insufficient input validation
Lack of protocol-level security standards
This enables credential misuse and data leakage.
Protocol-Specific Vulnerabilities
Unauthenticated context endpoints allowing internal network breaches
Insecure deserialization enabling data manipulation
Full-schema poisoning attacks extracting sensitive data
Audit Obfuscation
MCP actions often appear as legitimate API traffic, making malicious activity harder to distinguish from normal operations.
Mitigation Strategies
SecureMCP – An open-source toolkit that scans for prompt injection vulnerabilities, enforces least-privilege access controls, and validates input schemas
Fine-Grained Tokens – Replacing broad permissions with service-specific credentials
Behavioral Monitoring – Detecting anomalous MCP request patterns
Encrypted Context Transfer – Preventing data interception during transmission
Future Implications
MCP represents a pivotal shift in AI infrastructure, but its security model requires industry-wide collaboration. Key developments include:
Standardized security extensions for the protocol
Integration with AI observability platforms
Hardware-backed attestation for MCP servers
As MCP adoption grows, balancing its productivity benefits against novel attack surfaces will define the next generation of trustworthy AI systems. Enterprises implementing MCP should prioritize security instrumentation equivalent to their core infrastructure, treating MCP servers as critical threat vectors.
0 notes
Text
Why More Companies Are Partnering with PEOs in 2025: Benefits, Key Features & Common Business Problems Solved

Why PEO Service Providers Are Essential for Business Growth in 2025
Business scenarios in 2025 are rapidly getting transformed. With rapid digital transformation, workforce flexibility, and compliance complexity, many companies have turned to PEO service providers in Chennai and throughout India to compete. The PEOs have become crucial partners in ensuring the HR functions are well-managed, giving businesses the ability to really concentrate on growth and innovation.
What Is A PEO? Why Are They Trending in 2025?
A PEO (Professional Employer Organization) basically is an entity that partners with or serves with companies in order to do critical employee-related activities such as administering employee payroll, benefits, compliance, recruitment, and HR support. In 2025, PEO service providers really became relevant due to the ever-present proliferation of remote workforces, increase in regulatory compliance, and demand for cost-efficient HR solutions.
Being in such a dynamic environment as Chennai, businesses in Chennai are now extensively relying on PEO service providers in Chennai to avail human resource capabilities without having to build up large in-house teams. Under this co-employment system, companies still retain control over their daily operations while transferring from PEOs most of the administrative burdens that come with HR.
Benefits of Using a PEO for Growing Businesses
The advantages of having a PEO partner are great, especially when a startup or SME aims for sustainable growth:
The Cost Perspective: Maintaining an in-house HR department can be quite expensive. A PEO will provide full HR services at a fraction of the costs.
Compliance Support: The intricate nature of employment laws in India is a nuisance. PEOs ensure compliance with all state and central regulations, thereby alleviating legal risks.
Better Benefits: By pooling employees through PEOs, small firms offer their workers great benefits like health insurance and retirement plans at competitive rates.
Saves Time: Having HR services outsourced leaves the business leaders free to concentrate on core areas like customer acquisition and product development.
Scaling Up: When businesses grow, PEOs can proportionally scale their services. This can be local hiring or interstate expansion.
Key Features Offered by Leading PEO Providers
Not all PEOs are created equal. The best PEOs in Chennai provide a full-featured basket of functions catering to modern business needs:
Payroll Processing: Payroll is processed automatically and accurately, including direct deposits and tax filing processes.
Employee Benefit Administration: Healthcare, ESI, PF, gratuity, and many others.
Regulatory Compliance: Continuous support in meeting labor laws, tax laws, and statutory requirements.
Recruiting and Onboarding: Source, screen, and smoothly onboard talent.
Training and Development: Develop customized training programs to upskill and enhance the productivity of staff.
Performance Management Tools: Platforms for evaluating employee performance, setting goals, and ensuring transparent practices.
The Role of PEOs in Streamlining HR and Payroll
Managing human resources efficiently remains one of the sore points for growing enterprises. Payroll errors, delayed salary disbursal, and non-compliance gut employee morale and attract legal penalties.
Partnering with a PEO service will ensure proper and timely processing of payroll, issuance of tax declarations, and statutory deductions. This is particularly useful for Chennai, wherein fast-paced industries expect efficiency and timely delivery. PEOs also maintain employee records, allow grievance redressal, and even conduct human resource audits to set the mind of the business owner at ease.
Is a PEO Right for Your Business in 2025?
Yes, if you are a startup, SME, or mid-sized enterprise and want to keep expanding without running the overhead of HR management. Another PEO service providers in Chennai can help businesses in highly competitive areas like Chennai, as they understand regional labor nuances and provide customized support.
But you should assess your current business size, growth plans, and HR issues in the near future and find a PEO that fits your need—something that specializes in your industry and can prove its flexibility.
Conclusion
Already well into 2025, paying a PEO for services isn’t just a mode for ever-growing businesses, but rather a trend that gives even bigger ones the power to let go of the rest. PEOs maintain the latest tools, knowledge, and general peace of mind to take small organizations or those in scaling mode confidently through the growth path.
If you are intending to seek for a PEO service provider in Chennai, be sure to evaluate their service, support, and experience, thus utilizing your partnership well.
Our Service:
Payroll Outsourcing services | peo service providers in india | eor company in india | Talent Acquisition Services
#Peoserviceprovider#poservices#peoservicecompanies#professionalemployeeorganization#sbshr#chennai#trending#payrolloutsourcingservices#hrandpayrollsoftware#eorserviceprovider#peoserviceprovider2025#eorserviceproviders2025
0 notes