#gc script template
Explore tagged Tumblr posts
Text

🚀 Launch Your Own HYIP & Crypto Investment Platform with HYIPCO.com! 🔥
Looking to start your own HYIP or crypto investment website? At HYIPCO.com, we provide ready-to-use and fully customizable solutions to help you launch your platform effortlessly!
✅ Ready HYIP Investment Websites – Start earning instantly! ✅ Crypto Staking Websites – Offer secure and profitable staking services! ✅ HYIP Staking Websites & PHP Scripts – Build a powerful investment platform! ✅ HYIP Staking Software & Management Software – Complete solutions for seamless operations! ✅ GC HYIP Scripts & GC HYIP Templates – Fully optimized for high performance! ✅ HTML HYIP Templates – Professional & responsive designs! ✅ Meme Token Ready Websites & Templates – Ride the latest crypto trend! ✅ Meme Token Development Services – Get your token created and deployed! ✅ Telegram Earning Apps – Engage users with crypto rewards via Telegram!
🔥 Why Choose HYIPCO.com? ✔ Secure, Scalable & Feature-Rich Solutions ✔ Fast & Easy Deployment ✔ Customizable to Fit Your Needs ✔ 24/7 Support from Experts
💰 Your Success Starts Here! Build Your Crypto & HYIP Business Today! 👉 Visit HYIPCO.com Now! 🚀
1 note
·
View note
Text

Buy Hyip Website Script If you want launch your own Hyip investment website, you need to have Hyip script , Domain Hosting and a good hyip template.You can Buy Domain hosting from Namecheap or Verpex, For Hyip investment script and Template we can provide you Hyip script with latest Hyip investment features, we can also customize this Hyip script on demand, you can also buy Hyip template for your Hyip script from BUYHYIP.NET We can also provide you GC Templates and Tron Mining templates https://buyhyip.net https://hyip-demo.buyhyip.net
#buyhyipwebsite#buyhyiptemplates#buygcthemes#buyminingthemes#buyhyipscript#buyhyipinvestment#buyhyip.net
0 notes
Text

Create Tron Mining website
We can help you in making your own Tron mining website,we can make a complete TRX mining website that will not only looks great, but meet the needs of both you and your investors,to attract great number of investors we can make a unique and most attractive TRon Mining website for you.
We also have a huge collection of Premium Hyip templates, GC Hyip Templates, Btc Mining templates.
We can make complete hyip investment website for you including Hyip script,Design,Logo, SSL,Banners,Live chat button and free guidance and support.
For detail you cant visit our website www.hyipco.com and you can also contact us on skype
For detail you can Contact us
Email: [email protected]
1 note
·
View note
Photo

low prices in the market...
demo : ✅🆕 https://uniquehyips.com/product/uht091
(Instant Download link send to your mail after order)
#hyip #free_hyip_template #free_hyip_template_download #gc_hyip_script #gc_hyip_template #goldcoders_hyip_template
0 notes
Text
Genetically Correct Pleasantview with Scripted Events CC FREE
Hey people! Welcome to my latest project - A genetically correct Pleasantview with scripted events!
When I first found out (a while ago) that the playables we all know and love in Pleasantview aren’t actually genetically related to their ancestors, it totally broke immersion for me. For some reason it really bothered me and that kept me from really getting into a playthrough of the hoods that Eaxis shipped with the game. Then I discovered this crazy cool thing that people did which involved extracting the appearances of the first ancestors from each family, and breeding them in CAS from generation to generation, eventually creating Genetically Correct versions of the sims we all know. This is where I began this exhausting journey - there was a lot of learning but I am really happy with how it turned out!
There have been a ton of various Pleasantview makeovers - all of which are super awesome! However, I was unable to find a Pleasantview that not only already had all the sims genetically correct, but still had their relationships, biographies, personalities, and most importantly, scripted events...because let’s face it - who the hell wants to start a new Pleasantview if they can’t play through the cool ass scripted events in the beginning? I know I don’t. And that’s why I made this hood.
What is this? This is a Pleasantview in which I have made all the playable sims (and their ancestors) genetically correct. It contains no cc and was built on top of a clean template Pleasantview as well. Below are pics of the premades:



More Info, pics, and download below the cut!
My main goal for this was to make the premades genetically correct while still keeping them actually recognizable. I know there are some GC versions that are totally different, and I absolutely respect that, but I still wanted to look at Daniel Pleasant and say “Yep, that’s Daniel”.
IMPORTANT: After taking the pictures I realized the skin I use (No longer after this), which I will link below drastically whitewashes the sims. Some sims with skin 3 look super light, such as Daniel Pleasant and Jennifer Burb. They still have the correct skin, it just may appear lighter in my images. I didn’t realize this until after I made the sims and took their pictures. Also note that the eyes may look like different colors. People have said the light blue looks grey, so if you see a strange eye color on a sim it doesn’t match with, be aware it’s likely just the defaults I used.
Notice: I used a mod, equal genetics while creating these sims. I do not claim to be anything but a simpleton when it comes to genetics, and I know that some of these sims’ genetics aren’t realistic - Like a blond and brunette having a blond kid. I don’t claim to know anything about genetics, so before you genetic purists come at me just know - I know this and don’t care.
My general notion was that if one of their ancestors had a gene, then they could too.
With that being said, all living premades with the exception of Coral Oldie, Herb Oldie, Mortimer Goth, and Bella Goth have the same eye and hair colors as they did originally. Some ancestors or dead spouses (like Michael Bachelor and Skip Broke) have had a few changes as well. More on that at the very end, for those interested.
TLDR - General Information
I ramble, I know. The main idea is that ALL of the sims are the same exact sims as you’re used to. They all have the same personalities, zodiac signs, hobbies, jobs, aspirations, relationships, memories, etc...They just have corrected appearances. Scripted events still work, and Brandi Broke’s baby is also now going to be genetically correct and related to both her and Skip.
A few things to note:
- I used a default skin and eyes when taking the pictures. The sims will not come with these. I used Pitstop Skinblend and Poppet Clear Eyes
- Yes, I know Michael Bachelor’s eyes aren’t right. That is fixed in the game.
- This is CC FREE!!
- Brandi’s pregnancy may be a couple hours behind
- All sims have just about the same dominant and recessive traits as they do in the original clean templates from meetme. No sim is homozygous unless intended by meetme/eaxis.
- Sims may get some wants or fears of their ancestors or dead relatives becoming zombies or resurrected, this is just because of the way I did this, their deaths are fresh in the playables minds.
- This hood was build on a clean template Pleasantview, all ancestors and dead sims are safe to resurrect
- This was made with Ultimate Collection, so unfortunately you will need this or all packs for this to work.
- The versions without townies still include Bella Goth, Kaylynn Langerak, and Gordon King.
- When you add the subhood version with townies, you’ll notice that the townie and NPC names get randomized and aren’t their original names. Though annoying, this is normal and you will have to rename them all yourself.
Update:
It seems that some mods can break the scripted events, it was unclear exactly which mods in my folder did it. To circumvent this issue I would recommend that when you initially install and play the scripted events in the hood, take out all of your non essential mods (leave in mods like no unlink on delete, no townie regen, things that are essential) from your mods folder (just mods, cc is fine to stay in) and put it in a safe folder while you just play through the SE - then when they're done, put the mods back in. This seems like a random occurrence - as they only broke 1 out of every 5 times I tested it.
More Pics:
Link to imgur album of individual sims and all (or most) ancestors.
Link to imgur album of individual families
Download Instructions:
This comes in 4 versions:
GC Main Hood Pleasantview with Townies
GC Main Hood Pleasantview without Townies
GC Subhood (Shopping district) Pleasantview with Townies
GC Subhood (Shopping district) Pleasantview without Townies
Download the version you want.
For Main Hoods, place the folder in the following location:
Ultimate Collection:
Documents\EA Games\The Sims 2 Ultimate Collection\Neighborhoods
Disk Version:
Documents\EA Games\The Sims 2\Neighborhoods
For Subhoods, place the folder in the following location:
Ultimate Collection:
Program Files\Origin Games\The Sims 2 Ultimate Collection\Best of Business\EP3\TSData\Res\NeighborhoodTemplate
Disk Version:
:\Program Files\EA GAMES\The Sims 2 Open for Business\TSData\Res\NeighborhoodTemplate
Credits:
meemetotheriver for the clean templates
Carrit for the ancestral sims
Special thanks to:
Sabrina from PleasantSims discord and @isabella-goth for their patience and help with my idiocy throughout this project - I couldn’t have figured it out without your help specifically!!
Download:
Genetically Correct Pleasantview with Townies
Genetically Correct Pleasantview without Townies (Still includes Bella, Kaylynn, and Gordon King)
I hope you all enjoy this! As usual, let me know if you run into any issues! Tag me in pics or posts of what you do with the sims if you’d like!
Till’ next time
-Mike
P.S. Changes to premades/dead spouses:
Bella Goth - Hair changed to brown
Mortimer Goth - Hair changed to black
Coral Oldie - Hair changed to blond
Herb Oldie - Eyes changed to dark blue
Skip Broke - Eyes changed to dark blue
Michael Bachelor - Given blond hair, medium skin, and dark blue eyes
That should be the only changes to premades and/or their spouses. Some ancestors have been adjusted too!
#sims 2#ts2#ts2 hood#pleasantview#dwtdtpleasantviewgc#sims 2 neighborhood#ts2cc#sims 2 build#sims#simblr#the sims 2#the sims 2 cc#the sims 2 hood#dwtdt
184 notes
·
View notes
Text
Goldcoders HYIP Template
HYIP Manager script may be a package for investment sites. This computer code helps you to form and manage your own HYIP with ease. the mixture of value, features, performance and security are the simplest on the present market. Automatic withdrawal, instant payment and mass payment are offered in professional version.
Goldcoders HYIP Template will be your helpful way to manage all related business. It will help you to withdraw automatically, instant payment and etc.
There was a time when the peoples go away, like bank and others to complete their payment, bill, etc. But now science is on your hand. you can manage all of these things from anywhere. We are providing this service. Goldcoders HYIP Template is an investment service. You can deposit here timely and get a big benefit from here. If you think this is not a perfect way to invest then we will say that let's try once and see the result. Hopefully, it must be easier for you.
Investment is one of the most important issues for everyone. Because we are investing but do not know where we are going to invest, this is not fair. You want to start a business and you just need an investment. This template will help you with this issue.
Welcome To Goldcoders HYIP Template. We lead your HYIP Site to the of design with SewiCeS and has appropriately look that's good FM Meline business websites Our Goldcoders HYIP Template SewiCes will Shæk, impræS with a modern, professional website! We dæened gold coders HYIP with and mod web directiM1 to provide the best, Silky, clean and user experience interim a template SSL. We are all each and everyone glad to proclaim virtually on Goldcoders Hyip Template to you. For certain, recently we have launched this site using the high put on developers and sprightly designers. Here we come happening to take into account the maintenance for Goldcoders Hyip Template at every one low price. We already brought this site to make laugh all goldcoders script site owners. Our HYIP Templates will be dexterously situated for whom the superintendent HYIP site using gold coders script. We also manage to pay for any templates for whom making high say yes investment site through ARM HYIP and PAM HYIP script. Hyipssl is a moderately popular website - along with than on 39K visitors monthly, according to Alexa, which gave it a mysterious traffic rank. Moreover, HYIP Shop has yet to collect their social media come to, as its relatively low at the moment: 9 Google+ votes and 1 Twitter mention. There is nevertheless a nonappearance of data harshly speaking safety and reputation of this domain, as an upshot you should be every one cautious taking into account browsing it. If you are really looking for the best GC template services then you can contact us. We are available for you at any time.
1 note
·
View note
Text
gc template
gc template
HYIP Manager script may be a package for investment sites. This computer code helps you to form and manage your own HYIP with ease. the mixture of value, features, performance and security are the simplest on the present market. Automatic withdrawal, instant payment and mass payment are offered in professional version.
gc template will be your helpful way to manage all related business. It will help you to withdraw automatically, instant payment and etc.
There was a time when the peoples go away, like bank and others to complete their payment, bill, etc. But now science is on your hand. you can manage all of these things from anywhere. We are providing this service. gc template is an investment service. You can deposit here timely and get a big benefit from here. If you think this is not a perfect way to invest then we will say that let's try once and see the result. Hopefully, it must be easier for you.
Investment is one of the biggest important issues for everyone. Because we are investing but do not know where we are going to invest, this is not fair. You want to start a business and you just need an investment. This template will help you with this issue.
Welcome To GC template. We lead your HYIP Site to the of design with SewiCeS and has appropriately look that's good FM Meline business websites Our Goldcoders GC Template SewiCes will Shæk, impræS with a modern, professional website! We dæened gold coders HYIP with and mod web directiM1 to provide the best, Silky, clean and user experience interim a template SSL. We are all each and everyone glad to proclaim virtually on Goldcoders Hyip Template to you. For certain, recently we have launched this site using the high put on developers and sprightly designers. Here we come happening to take into account the maintenance for Goldcoders Hyip Template at every one low price. We already brought this site to make laugh all goldcoders script site owners. Our HYIP Templates will be dexterously situated for whom the superintendent HYIP site using gold coders script. We also manage to pay for any templates for whom making high say yes investment site through ARM HYIP and PAM HYIP script. Hyipssl is a moderately popular website - along with than on 39K visitors monthly, according to Alexa, which gave it a mysterious traffic rank. Moreover, HYIP Shop has yet to collect their social media come to, as its relatively low at the moment: 9 Google+ votes and 1 Twitter mention. There is nevertheless a nonappearance of data harshly speaking safety and reputation of this domain, as an upshot you should be every one cautious taking into account browsing it. If you are really looking for the best GC template services then you can contact us. We are available for you at any time.
1 note
·
View note
Text
How To Make Hyip Website 2023 | Hyip Investment Website BUYHYIP.NET

If you want to start your own hyip investment website then you are on right place, we can provide you ready hyip investment website including domain and hosting https://buyhyip.net/buy-hyip.php Buy Hyip investment websites Buy Hyip templates Buy GC templates Buy Hyip scripts https://buyhyip.net/hyip-demo.php Website: https://buyhyip.net/ Email: [email protected] Templates Link: https://buyhyip.net/buy-hyip-templates.php
0 notes
Text
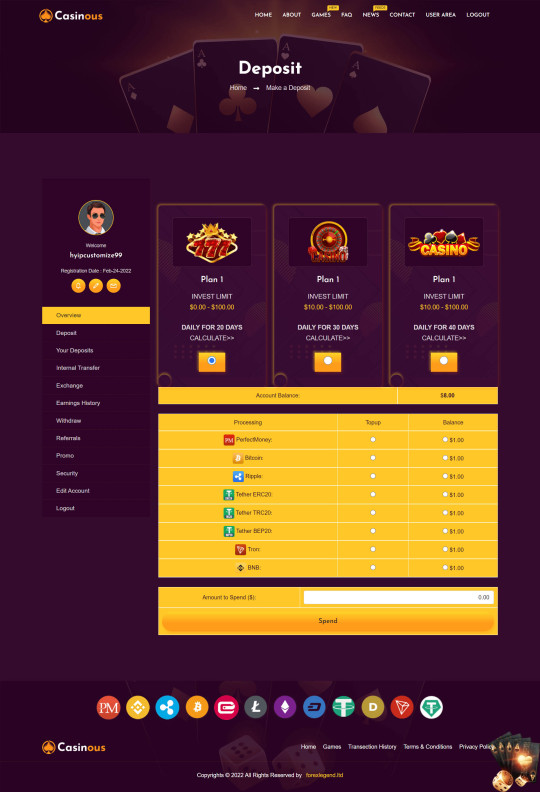
Buy ready GC Hyip Templates
Professional Goldcoders Hyip investment templates for your GC website,these templates work properly on GC scripts.
BUYNOW
0 notes
Text

Buy Hyip Website Script
If you want launch your own Hyip investment website, you need to have Hyip script , Domain Hosting and a good hyip template.You can Buy Domain hosting from Namecheap or Verpex, For Hyip investment script and Template we can provide you Hyip script with latest Hyip investment features, we can also customize this Hyip script on demand, you can also buy Hyip template for your Hyip script from BUYHYIP.NET We can also provide you GC Templates and Tron Mining templates https://buyhyip.net https://hyip-demo.buyhyip.net
0 notes
Text

Create USDT Mining website
We can help you in making your own USDT mining website,we can make a complete usdt mining website that will not only looks great, but meet the needs of both you and your investors,to attract great number of investors we can make a unique and most attractive USDT Mining website for you.
We also have a huge collection of Premium Hyip templates, GC Hyip Templates, Btc Mining templates.
We can make complete hyip investment website for you including Hyip script,Design,Logo, SSL,Banners,Live chat button and free guidance and support.
For detail you cant visit our website www.hyipco.com and you can also contact us on skype
For detail you can Contact us
Email: [email protected]
0 notes
Photo

Hyip Template @ comfortable prices
demo : ✅🆕 https://uniquehyips.com/product/uht179
(Instant Download link send to your mail after order)
#hyip #free_hyip_template #free_hyip_template_download
0 notes
Text
Genetically Correct Clean Template Strangetown With Scripted Events - CC FREE
I’m back with another genetically correct hood! You can check out my GC version of Pleasantview with scripted events here - I also explain what genetically correct means there as well in case you aren’t sure :)
Today as part of my quest to make all Sims 2 hoods genetically correct, I bring you Strangetown!




More pics, info, and download links below the cut :)
General Information:
This is a genetically correct version of Strangetown. All sim appearances have been corrected so they now resemble their ancestors! This hood was built on top of clean templates, and no other changes have been made to the hood aside from the adjustments to the sim’s appearances and DNA!
Notice: I used a mod, equal genetics while creating these sims. I do not claim to be anything but a simpleton when it comes to genetics, and I know that some of these sims’ genetics aren’t realistic - Like a blond and brunette having a blond kid. I don’t claim to know anything about genetics, so before you genetic purists come at me just know - I know this and don’t care.
My general notion was that if one of their ancestors had a gene, then they could too.
Notes:
- This is CC FREE
- I used a default skin and eyes when taking the pictures. The sims will not come with these. I used Pitstop Skinblend and Poppet Clear Eyes
- All sims have been given recessive genetics - and I will say here and now they may not make actual sense scientifically speaking, once more - I don’t care about that. 98% of the sims - even the ancestors - have recessive genes. At the very end of the post you will find a chart of each sim and their recessive genes.
- Sims may get some wants or fears of their ancestors or dead relatives becoming zombies or resurrected, this is just because of the way I did this, their deaths are fresh in the playables minds.
- This hood was built on a clean template Strangetown, all ancestors and dead sims are safe to resurrect
- This was made with Ultimate Collection, so unfortunately you will need this or all packs for this to work.
- Pascal’s unborn baby will be genetically correct as well
- When you add the subhood version with townies, you’ll notice that the townie and NPC names get randomized and aren’t their original names. Though annoying, this is normal and you will have to rename them all yourself.
- The no townie version of ST STILL comes with Bella Goth, Crystal Vu, Abhijeet Cho and Meredith Lillard.
- I used two different clean template versions for this hood. There may be slight differences depending on what the original creators of the clean templates did to the hood. See credits.
- Bella Goth is also genetically correct with her PV ancestors
- Some sims such as Ophelia Nigmos and Kristen Loste had no ancestors with the original hairs, skins and/or eyes they have in the BG hood. Because of this, I chose the next best hair/eyes/skins that I felt brought more genetic diversity to the hood and kept the original feel of the sim
Important notice about Scripted Events:
If you are having issues with the Scripted Events: FIRST - Navigate to your "Documents/EA Games/The Sims 2 Ultimate Collection (or The Sims 2)/Neighborhoods" and delete the NeighborhoodManager.package file within this folder. Reload your game. When you load the game back up it will automatically regenerate a new, fresh NeighborhoodManager.package file - See if this fixes the scripted event problem. For some reason it can break really easily and a majority of the time resetting this file will do the trick. HUGE thanks to Cindy from PleasantSims for suggesting this! All credit to her! SECOND - If the first suggestion doesn't work, you will need to redownload the hood, and BEFORE you run your game, take out all of your non essential mods (leave in mods like no unlink on delete, no townie regen, things that are essential) from your mods folder (just mods, cc is fine to stay in) and put it in a safe folder while you just play through the SE - then when they're done, put the mods back in. 99.9999% of the time either of these suggestions will fix the problem. If you try both and they don't work, let me know
More Pics:
Link to imgur album of most sims + ancestors
Link to imgur album of all families
With all that out of the way, let’s get to downloading!
Download Instructions:
This comes in 4 versions:
GC Main Hood Strangetown with Townies
GC Main Hood Strangetown without Townies
GC Subhood (Shopping district) Strangetown with Townies
GC Subhood (Shopping district) Strangetown without Townies
Download the version you want.
For Main Hoods, place the folder in the following location:
Ultimate Collection:
Documents\EA Games\The Sims 2 Ultimate Collection\Neighborhoods
Disk Version:
Documents\EA Games\The Sims 2\Neighborhoods
For Subhoods, place the folder in the following location:
Ultimate Collection:
Program Files\Origin Games\The Sims 2 Ultimate Collection\Best of Business\EP3\TSData\Res\NeighborhoodTemplate
Disk Version:
:\Program Files\EA GAMES\The Sims 2 Open for Business\TSData\Res\NeighborhoodTemplate
CREDITS:
Meetmetotheriver for the clean templates without townies
Dorsal Axe for the clean templates with townies
Download:
Genetically Correct & Clean Strangetown WITH townies
Genetically Correct & Clean Strangetown WITHOUT townies (Still includes Bella, Crystal, Abhijeet, and Meredith)
Let me know if you run into any issues, and as always, have fun!
Take care,
Mike
P.S.
As promised, below are all of the recessive genetics of the sims in the hood in case you get a baby and go “Where the f did that come from?!”. The parts that say N/A are if the recessive is the same as their dominant :)
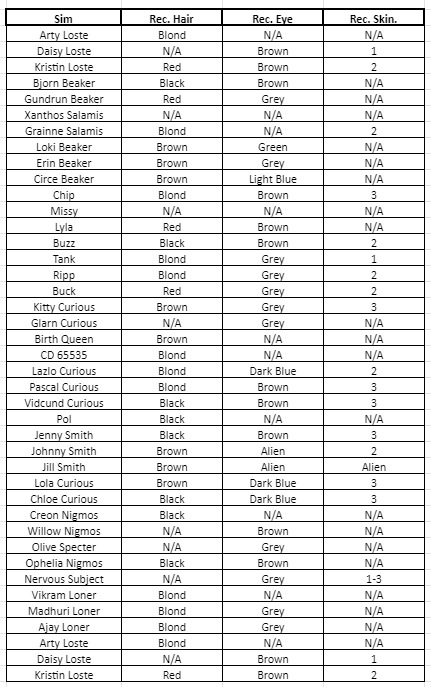
Yes, I misspelled Kristen’s name lol
#ts2#the sims#the sims 2#ts2cc#ts2mm#nocc#sims#simblr#the sims 2 hood#sims 2 hood#sims 2 neighborhood#strangetown#the sims 2 strangetown#genetically correct#dwtdtstrangetown#tdwtdtstrangetown#s2cc#ts2 sims#cas#sims 2 cas
135 notes
·
View notes
Link
This is the the last of three posts on the course I regularly teach, CS 330, Organization of Programming Languages. The first two posts covered programming language styles and mathematical concepts. This post covers the last 1/4 of the course, which focuses on software security, and related to that, the programming language Rust. This course topic might strike you as odd: Why teach security in a programming languages course? Doesn’t it belong in, well, a security course? I believe that if we are to solve our security problems, then we must build software with security in mind right from the start. To do that, all programmers need to know something about security, not just a handful of specialists. Security vulnerabilities are both enabled and prevented by various language (mis)features, and programming (anti)patterns. As such, it makes sense to introduce these concepts in a programming (languages) course, especially one that all students must take. This post is broken into three parts: the need for security-minded programming, how we cover this topic in 330, and our presentation of Rust. The post came to be a bit longer than I’d anticipated; apologies! Security is a programming (languages) concern The Status Quo: Too Much Post-hoc Security There is a lot of interest these days in securing computer systems. This interest follows from the highly publicized roll call of serious data breaches, denial of service attacks, and system hijacks. In response, security companies are proliferating, selling computerized forms of spies, firewalls, and guard towers. There is also a regular call for more “cybersecurity professionals” to help man the digital walls. It might be that these efforts are worth their collective cost, but call me skeptical. I believe that a disproportionate portion of our efforts focuses on adding security to a system after it has been built. Is your server vulnerable to attack? If so, no problem: Prop an intrusion detection system in front of it to identify and neuter network packets attempting to exploit the vulnerability. There’s no doubt that such an approach is appealing; too bad it doesn’t actually work. As computer security experts have been saying since at least the 60s, if you want a system to actually be secure then it must be designed and built with security in mind. Waiting until the system is deployed is too late. Building Security In There is a mounting body of work that supports building secure systems from the outset. For example, the Building Security In Maturity Model (BSIMM) catalogues the processes followed by a growing list of companies to build more secure systems. Companies such as Synopsys and Veracode offer code analysis products that look for security flaws. Processes such as Microsoft’s Security Development Lifecycle and books such as Gary McGraw‘s Software Security: Building Security In, and Sami Saydjari‘s recently released Engineering Trustworthy Systems identify a path toward better designed and built systems. These are good efforts. Nevertheless, we need even more emphasis on the “build security in” mentality so we can rely far less on necessary, but imperfect, post-hoc stuff. For this shift to happen, we need better education. Security in a Programming Class Choosing performance over security Programming courses typically focus on how to use particular languages to solve problems efficiently. Functionality is obviously paramount, with performance an important secondary concern. But in today’s climate shouldn’t security be at the same level of importance as performance? If you argue that security is not important for every application, I would say the same is true of performance. Indeed the rise of slow, easy-to-use scripting languages is a testament to that. But sometimes performance is very important, or becomes so later, and the same is true of security. Indeed, many security bugs arise because code originally written for a benign setting ends up in a security-sensitive one. As such, I believe educators should regularly talk about how to make code more secure just as we regularly talk about how to make it more efficient. To do this requires a change in mindset. A reasonable approach, when focusing on correctness and efficiency, is to aim for code that works under expected conditions. But expected use is not good enough for security: Code must be secure under all operating conditions. Normal users are not going to input weirdly formatted files to to PDF viewers. But adversaries will. As such, students need to understand how a bug in a program can be turned into a security vulnerability, and how to stop it from happening. Our two lectures in CS 330 on security shift between illustrating a kind of security vulnerability, identifying the conditions that make that vulnerability possible, and developing a defense that eliminates those conditions. For the latter we focus on language properties (e.g., type safety) and programming patterns (e.g., validating input). Security Bugs In our first lecture, we start by introducing the high-level idea of a buffer overflow vulnerability, in which an input is larger than the buffer designed to hold it. We hint at how to exploit it by smashing the stack. A key feature of this attack is that while the program intends for an input to be treated as data, the attacker is able to trick the program to treat it as code which does something harmful. We also look at command injection, and see how it similarly manifests when an attacker tricks the program to treat data as code. SQL injection: malicious code from benign parts Our second lecture covers vulnerabilities and attacks specific to web applications, including SQL injection, Cross-site Request Forgery (CSRF), and Cross-site scripting (XSS). Once again, these vulnerabilities all have the attribute that untrusted data provided by an attacker can be cleverly crafted to trick a vulnerable application to treat that data as code. This code can be used to hijack the program, steal secrets, or corrupt important information. Coding Defenses It turns out the defense against many of these vulnerabilities is the same, at a high level: validate any untrusted input before using it, to make sure it’s benign. We should make sure an input is not larger than the buffer allocated to hold it, so the buffer is not overrun. In any language other than C or C++, this check happens automatically (and is generally needed to ensure type safety). For the other four attacks, the vulnerable application uses the attacker input when piecing together another program. For example, an application might expect user inputs to correspond to a username and password, splicing these inputs into a template SQL program with which it queries a database. But the inputs could contain SQL commands that cause the query to do something different than intended. The same is true when constructing shell commands (command injection), or Javascript and HTML programs (cross-site scripting). The defense is also the same, at a high level: user inputs need to either have potentially dangerous content removed or made inert by construction (e.g., through the use of prepared statements). None of this stuff is new, of course. Most security courses talk about these topics. What is unusual is that we are talking about them in a “normal” programming languages course. Our security project reflects the defensive-minded orientation of the material. While security courses tend to focus on vulnerability exploitation, CS 330 focuses on fixing the bugs that make an application vulnerable. We do this by giving the students a web application, written in Ruby, with several vulnerabilities in it. Students must fix the vulnerabilities without breaking the core functionality. We test the fixes automatically by having our auto-grading system test functionality and exploitability. Several hidden tests exploit the initially present vulnerabilities. The students must modify the application so these cases pass (meaning the vulnerability has been removed and/or can no longer be exploited) without causing any of the functionality-based test cases to fail. Low-level Control, Safely The most dangerous kind of vulnerability allows an attacker to gain arbitrary code execution (ACE): Through exploitation, the attacker is able to execute code of their choice on the target system. Memory management errors in type-unsafe languages (C and C++) comprise a large class of ACE vulnerabilities. Use-after-free errors, double-frees, and buffer overflows are all examples. The latter is still the single largest category of vulnerability today, according to MITRE’s Common Weakness Enumeration (CWE) database. Programs written in type-safe languages, such as Java or Ruby, 1 are immune to these sorts of memory errors. Writing applications in these languages would thus eliminate a large category of vulnerabilities straightaway. 2 The problem is that type-safe languages’ use of abstract data representations and garbage collection (GC), which make programming easier, remove low-level control and add overhead that is sometimes hard to bear. C and C++ are essentially the only game in town 3 for operating systems, device drivers, and embedded devices (e.g., IoT), which cannot tolerate the overhead and/or lack of control. And we see that these systems are regularly and increasingly under attack. What are we to do? Rust: Type safety without GC In 2010, the Mozilla corporation (which brings you Firefox) officially began an ambitious project to develop a safe language suitable for writing high-performance programs. The result is Rust. 4 In Rust, type-safety ensures (with various caveats) that a program is free of memory errors and free of data races. In Rust, type safety is possible without garbage collection, which is not true of any other mainstream language. Rust, the programming language In CS 330, we introduce Rust and its basic constructs, showing how Rust is arguably closer to a functional programming language than it is to C/C++. (Rust’s use of curly braces and semi-colons might make it seem familiar to C/C++ programmers, but there’s a whole lot more that’s different than is the same!) We spend much of our time talking about Rust’s use of ownership and lifetimes. Ownership (aka linear typing) is used to carefully track pointer aliasing, so that memory modified via one alias cannot mistakenly corrupt an invariant assumed by another. Lifetimes track the scope in which pointed-to memory is live, so that it is freed automatically, but no sooner than is safe. These features support managing memory without GC. They also support sophisticated programming patterns via smart pointers and traits (a construct I was unfamiliar with, but now really like). We provide a simple programming project to familiarize students with the basic and advanced features of Rust. Assessment I enjoyed learning Rust in preparation for teaching it. I had been wanting to learn it since my interview with Aaron Turon some years back. The Rust documentation is first-rate, so that really helped. I also enjoyed seeing connections to my own prior research on the Cyclone programming language. (I recently reflected on Cyclone, and briefly connected it to Rust, in a talk at the ISSISP’18 summer school.) Rust’s ownership relates to Cyclone’s unique/affine pointers, and Rust’s lifetimes relate to Cyclone’s regions. Rust’s smart pointers match patterns we also implemented in Cyclone, e.g., for reference counted pointers. Rust has taken these ideas much further, e.g., a really cool integration with traits handles tricky aspects of polymorphism. The Rust compiler’s error messages are also really impressive! A big challenge in Cyclone was finding a way to program with unique pointers without tearing your hair out. My impression is that Rust programmers face the same challenge (as long as you don’t resort to frequent use of unsafe blocks). Nevertheless, Rust is a much-loved programming language, so the language designers are clearly doing something right! Oftentimes facility is a matter of comfort, and comfort is a matter of education and experience. As such, I think Rust fits into the philosophy of CS 330, which aims to introduce new language concepts that are interesting in and of themselves, and may yet have expanded future relevance. Conclusions We must build software with security in mind from the start. Educating all future programmers about security is an important step toward increasing the security mindset. In CS 330 we illustrate common vulnerability classes and how they can be defended against by the language (e.g., by using those languages, like Rust, that are type safe) and programming patterns (e.g., by validating untrusted input). By doing so, we are hopefully making our students more fully cognizant of the task that awaits them in their future software development jobs. We might also interest them to learn more about security in a subsequent security class. In writing this post, I realize we could do more to illustrate how type abstraction can help with security. For example, abstract types can be used to increase assurance that input data is properly validated, as explained by Google’s Christoph Kern in his 2017 SecDev Keynote. This fact is also a consequence of semantic type safety, as argued well by Derek Dreyer in his POPL’18 Keynote. Good stuff to do for Spring’19 !
0 notes
Photo

We Have Responsive #Cheap_price GC Scripts Supported #Hyip #Template Ready To Sale 👇⛔👇 hyipcustomize.com https://www.instagram.com/p/B4M4mDohpi_/?igshid=10e8z4zeqi83a
0 notes
Text
Buy HYIP Investment Websites || HYIP Templates | BUYHYIP.NET

Looking for a professional HYIP website? We are providing a complete best hyip script Our HYIP solution is available in one package We are providing Unique Domain, DDOS Protection Web Hosting, HYIP Script, SSL, Logo, Banner,Ads Banner, installation, Technical Support, Website License and much more, https://buyhyip.net/
https://buyhyip.net/buy-hyip-templates.php https://buyhyip.net/buy-gc-hyip-templates.php
You Can Contact Us ; Email: [email protected] [email protected] Skype ID : BestHyipWeb
Telegram: @BestHyipWeb
#buyhyip#besthyip#hyipwebsites#buytemplates#hyipscripts#hyipbanners#cheapwebsites#buygchyipwebsites#buyhyipwebsites#buyhyipdesigns#miningtemplates#hyipwebsite
0 notes