#gdata
Explore tagged Tumblr posts
Text
G DATA VPN
Secure VPN software so you can surf anonymously. Prevent your Internet provider from slowing down your network speed.

2 notes
·
View notes
Text
Kaspersky vs G DATA vs Bitdefender
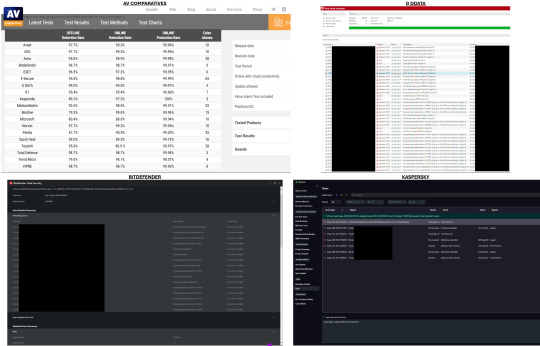
In anticipation of my antivirus license renewal, I conducted a thorough evaluation of alternative solutions to my current Kaspersky installation. My assessment was significantly informed by the reputable and long-trusted independent testing conducted by av-comparatives.com. The March 2025 Malware Protection Test revealed that while Kaspersky excels with a 100% online protection rate, its malware detection capability lags behind leading competitors such as G DATA and Bitdefender. To validate these findings, I performed a comparative analysis of the three antivirus products' detection rates, leveraging their online/cloud detection mechanisms. The results corroborated the test data, with G DATA identifying the highest number of malware instances (19), followed by Bitdefender (16), and Kaspersky (7). This discrepancy raises a significant concern, as my current preference for Kaspersky is primarily driven by its minimal performance impact on my laptop. Consequently, I am faced with the critical decision of whether to prioritize a superior detection rate over maintaining optimal system performance.
While I initially considered switching antivirus solutions, I have elected to remain with Kaspersky for the following key reasons: * G DATA's Web Protection feature consistently generates ERR_SSL_PROTOCOL_ERROR errors for legitimate websites, including critical services like gmail.com, necessitating its deactivation for standard browsing. * Bitdefender lacks the crucial functionality to export and import settings configurations. This feature is essential for my workflow, given my practice of resetting my Windows environment monthly prior to applying Windows updates. Despite submitting a feature request for this functionality several years ago, it remains unavailable in Bitdefender, while both G DATA and Kaspersky offer this capability.
I hope Kaspersky can improve its detection rate significantly in near future.
0 notes
Text
0 notes
Text
Conversation recorded in Cyev, possibly between resistance members.
Recorded Trimar 27th, 41 AAI: Originated from a Cyev residential security device[C-RESD]. Pulled from Data banks by Arsaa Tyim, reviewed by Gwyn Rynad
LOST FROM RECORDS
[A group of 4 people are seen standing in the hallway of a residential apartment building. Two faces are clearly visible. These have been identified as Maira Tanne and Kovano Tanne. The other two are assumed to be GDATA CORRUPTEDad and Vanitri Letha. This assumption has been made as the four live together with their child.]
POI Speaking will be marked with first initial of name.
[Surveilence on the household advised]
start of recording ···
(M) [blocking door of stairwell] Kova, we aren't going to just leave them! You know for a fact if it was our daughter that we would be hoping that a friend would find her. You know our friends parents would never do this, never turn on eachother and hunt their children. Kove, we had dinner with Mau last week and now you want to be the one to turn in his younger siblings? Will you be the one to tell her how they were found?
[Unknown 1, assumed Vanitri enters hallway, with lis child]
(G) Vani my love, please tell Ko that we are not turning in the children for money. We will be giving them food and cover, until their siblings can pick them up, correct?
(K) [turning to Vanitri] Vee, I only want whats best for Uji, I want our oldest safe. Please.
(M) If we turn these children in they will be your only. How should I trust you with our second child if you can’t keep other children safe simply by not betraying them.
(V) Uji… not yours if.. if do. Not not…. For them[gestures to nearby door]{note: Vantiri has low verbality, there is no cause for concern over camera audio functionality}
(K) [throws up hands, turning so face is visible] fine! Fine! I won’t tell, but if we go to jail or Urral’ba for this I will NEVER forgive you. [walks out of frame into appartmenr]
(V) [li tilts lis head] Gwyy. Cam…. Ra. Wipe. To mor… mor row.
[both Maira and Unknown 2 become visibly stressed]
(M) Fucking Beacon. This is why we can’t have conversations in the hallway. Gwy, I’ll message the other Eye.
(G) We will both See to it tomorrow. Thank you love, it is now in Eyesight.
(M) the two of you have too much fun with your code, its adorable.
[the three, Vanitri still holding child, begin to walk out of frame towards building exit.]
. . .
End of recording.
Surveillance completed by Gwyn Rynad. Verdict: No cause for concern.
C-RESD around this location soon lost power, lack of replacements due to above verdict.
#within the code#lost/recovered data#found in: kyarr data banks#Maira Tanne#Kovano Tanne#Vanitri Letha#Gwyn Rynad#Arsaana Tyim
2 notes
·
View notes
Text
0 notes
Text
Win Gdata Total Security on December 23
Win Gdata Total Security on December 23
[ad_1]
TO THE ADVENT CALENDAR Gdata Total Security
Put your protection together yourself
Put your security solution together in the way that best suits your life. Combine the award-winning antivirus programs from G DATA according to your wishes and protect all your devices – whether Windows PC, Mac, Android smartphone or iOS tablet.
Virus protection with many extras
Move safely and freely on the…
View On WordPress
1 note
·
View note
Text
STF define marco temporal para distinção do pagamento da GDATFA a ativos e inativos
STF define marco temporal para distinção do pagamento da GDATFA a ativos e inativos
(more…)

View On WordPress
1 note
·
View note
Photo

@Regrann from @tecnovirus - No caigas en esta nueva estafa de Whatsapp. Desde el primero de junio empezó a correr una nueva estafa, donde los hackers aprovechan la imagen de la compañía perteneciente a Facebook (WhatsApp) para engañar a los usuarios. El engaño consiste en un mensaje de texto, el cual señala una supuesta falla de autenticación en la cuenta del usuario, junto con un enlace para verificar la información. Una vez que el cliente entra al sitio, recibe una alerta sobre el pago que debe realizar para poder seguir disfrutando del servicio. WhatsApp es una de las aplicaciones de mensajería instantánea con más descargas a nivel mundial, al menos un mil millones de personas utilizan esta popular herramienta comunicacional, y es por ello que los hackers la prefieren como señuelo para poder realizar sus fechorías. Conoce más en nuestro Blog============TECNOVIRUS.COM #Noticias#Tipsdeseguridad#Seguridaddelainformacion#Antihackers#Antivirus#Kaspersky#Gdata#Eset#Ciberguerra#Tecnovirus#wannacry#Contraseñas#Hackers#whastapp#engaño#estafa#cibercrimen@jesuselealc - #regrann
#engaño#tipsdeseguridad#tecnovirus#contraseñas#hackers#cibercrimen#antivirus#kaspersky#whastapp#wannacry#eset#ciberguerra#gdata#noticias#estafa#seguridaddelainformacion#antihackers#regrann
0 notes
Text
G DATA: Android-malware in 2016 flink toegenomen
G DATA: Android-malware in 2016 flink toegenomen
Malware voor Android is in 2016 enorm toegenomen, zo stellen de marktonderzoekers van G DATA in een recent onderzoek. Belangrijkste oorzaak is dat cybercriminelen steeds meer op internet aanvallen uitvoeren op dit specifieke mobiele besturingssysteem. (more…)
View On WordPress
1 note
·
View note
Text
Top 3 IT-Security Blogs
IT-Sicherheit ist ein fundamentaler Bestandteil der heutigen Digitalisierung. Doch bereits Letzteres ist eine Herausforderung für Privat & Beruf. In Deutschland gibt es jedoch neben Magazinen auch zahlreiche private Blogs die regelmäßig über das Thema IT-Sicherhet berichten. Wir haben fünf Blogs herausgesucht, dessen Besuch der Website durchaus lohnt!
Der Blog der AWARE7 GmbH
Gestartet als technique-blog ist der mittlerweile 4 Jahre alter, aber regelmäßig bespielter Blog ein recht aktueller, mit persönlicher Note entwickelter Blog. Auch wenn der Blog mittlerweile unter der Flagge der AWARE7 GmbH weitergeführt wird, so ist er trotzdem ein Blick wert.
Andre Fritsche auf Medium
Andre Fritsche hat eine ganze Zeit lang aktiv gebloggt. Mit umfangreichen Artikeln hat er über die neusten Entwicklungen geschrieben. Mittlerweile ist es etwas ruhiger geworden, doch in einem RSS Feed würde ich ihn einbinden.
Tim Berghoff im GDATA Blog
Schon oft auf Vorträgen erlebt: Tim Berghoff. Der Security Evangelist schreibt oft und umfangreich über aktuelle Geschehnisse im Rahmen des GDATA Blogs. Immer einen Blick wert. Wer der englischen Sprache mächtig ist, sollte hier nicht zögern einen Blick auf die Website zu werfen.
1 note
·
View note
Text
G DATA Antivirus Mac
Reliable protection against viruses, Trojans and phishing.
Do you also want to protect your Mac? No problem with G DATA Antivirus Mac. The real-time scanner scans your system for malware in the background – without slowing down your Mac.

2 notes
·
View notes
Text
First aid for water damage on the laptop
First aid for water damage on the laptop This laptop is equipped with the special Cooler Boost 4 technology, which is supposed to ensure particularly quiet cooling. Due to the high purchase costs, the Apple MacBook Air is primarily something for lovers. The device convinces with its unique design and perfectly coordinated hardware components. The bottom line, however, are more powerful laptops at cheaper prices. The Acer Chromebook R 11 CB5-132T-C4LB is suitable for anyone who wants maximum flexibility when using their laptop. Most of the properties of a laptop cannot be rated as good or bad. Because what your new laptop should bring depends primarily on your usage behavior and the planned areas of application. Remember to also use any damping intermediate components. In order for the buttons to snap back in, some force is sometimes required when pressing the buttons. However, be careful here.
Which key is?
Ctrl key. (2000) "Ctrl" is the label for the "Control" key on the PC keyboard. The key is labeled "Ctrl" (control) on the original US keyboard and on Swiss keyboards.
An advantage of the low performance of netbooks is that you often benefit from a very long battery life. A full version of the Libre Office package and GData Internet Security are also preinstalled on this laptop. Get the most informative and entertaining summary from the world of technology, the best bargains or current competitions. Free.
However, you do not receive a guarantee when purchasing this model.
Toshiba charges between 499 and 949 euros for its new notebooks.
The plasticine should also disinfect - heavily soiled keyboards will not be really clean.
However, OLED technology is comparatively expensive and is rarely found in laptops.
How can you deactivate the FN key?
< div itemScope itemProp = "acceptedAnswer" itemType = "https://schema.org/Answer">
Deactivate the Fn key on the laptop Press the [Ctrl] + [keys at the same time Shift] + [Num]. Alternatively, the command can also be hidden behind the key combination [Fn] + [Num]. If there is no numeric keypad, try it with [Fn] + [F11].
div> div> With a brush attachment for the vacuum cleaner or a compressed air spray, you can remove coarse dirt and crumbs. Even if you decide to have your device dried and repaired by a service technician, you must dry it well beforehand. The laptop offers you an 11.6-inch IPS display, which is characterized by a stable viewing angle and particularly bright colors. The resolution here is an average of 1,366 x 768 pixels. In this model, the powerful 2-core processor AMD Mobile Athlon 64 with a performance of 2 gigahertz and an integrated AMD Radeon R2 graphics card are responsible for calculating your data. Then describe to the experts exactly the activities and materials used. If the liquid gets into the device from below, do the same by simply placing the laptop differently. Make sure that there are several USB ports and at least one HDMI port. An SD card slot can also be an advantage. The battery life is an average of 5 hours. It continues with a model that can be found in the low price range - the Acer Aspire 1 A114-31-P4J2 laptop.
1 note
·
View note
Text
How do I open an Asus laptop for cleaning
How do I open an Asus laptop for cleaning With compressed air you can remove the dust from the keyboards. The compressed air can be generated using a compressed air cleaning gun, a compressed air spray or a bellows, as is used to clean photo lenses. Unfortunately, we cannot make any precise statements on this question, because science is still unclear. On the one hand, there are assumptions that WLAN radiation is dangerous for humans and can even increase the risk of cancer. Last Saturday when I wanted to open my notebook and it opened, it suddenly cracked and had no picture for a few seconds, so I wanted to check what has happened again. After a few months, the battery did not pack for 3 hours and it was always very annoying when traveling. After that I had a blue screen every day and at some point I could at least solve this problem with my half knowledge (and thanks to the internet). But since this is intended by this step, this is of course not a problem at all. If this does not help either, loosening the contacts from the mainboard of the notebook can only help. However, since this can be complicated, the help of a specialist is definitely recommended. This cleans your screen in 90 percent of the cases. I bought this Lenovo notebook in July 2015 and it looked very high quality at first glance. This site works best with JavaScript. Deactivation means that some functions are deactivated or are missing. You can still see all customer reviews for the product.
This will significantly affect the cooling system, to which your computer will respond quite quickly with an automatic shutdown.
If you have more time, you can also carefully remove the keyboard from the individual keys.
Take a photo of the buttons first so that you can later easily put them all in their old place.
Now restart at the latest so that the installation of the driver for the Intel graphics card can take effect before you install the driver for the AMD graphics card.
Information about non-Apple products, as well as third-party websites not controlled or audited by Apple, is provided without recommendation and support. Apple is not responsible for the selection, performance, or use of third-party websites and products. Most of the people are probably like you. If you eat at the desk, it can cause crumbs to dust cleaning mud the keyboard, which can lead to a higher accumulation of bacteria on your keyboard if the crumbs rot.
How can I turn off SwiftKey?
You can switch Flow on or off on the SwiftKey keyboard for Android as follows: Open the SwiftKey app. Tap on "Enter". Select "Typing & AutoCorrect". Tap on "Gesture input". Switch flow on and off. div> div> div> The scope of delivery includes the laptop with pre-installed Windows 10 Professional in the 64-bit version, a Microsoft Office 2010 starter package and a full GData version. A laptop is not a laptop. There are a total of seven types of laptops on the market today. These include barebooks, desktop replacements, multimedia notebooks, convertibles, netbooks, ultrabooks and the popular MacBooks. We will tell you exactly what distinguishes these different types of laptops in our guide. Dry the keyboard. This is an important step that is easily overlooked. After disinfecting, use a clean, dry, soft, and lint-free cloth to dry to remove any moisture from the keyboard.
1 note
·
View note
Text
0 notes
Text
Critério para cálculo de gratificação a inativos do Ministério da Agricultura tem repercussão geral
Critério para cálculo de gratificação a inativos do Ministério da Agricultura tem repercussão geral
Plenário do STF irá julgar recurso que discute a extensão a servidor inativo de gratificação concedida a servidores ativos do Ministério da Agricultura, Pecuária e Abastecimento. (more…)

View On WordPress
1 note
·
View note