#hire facebook hacker
Explore tagged Tumblr posts
Text
Facebook Hackers for Hire: Navigating Account Recovery and Security

Facebook remains one of the most widely used social media platforms globally, with billions of users sharing personal and professional aspects of their lives. Given its popularity, it is also a prime target for cyberattacks, account takeovers, and privacy breaches. Losing access to a Facebook account or encountering unauthorized activity can be distressing. In such situations, some consider the option to Hire Facebook Hackers to regain control or bolster security.
This article explores the landscape of hiring hackers for Facebook-related issues, the risks involved, and how to do so ethically and legally.
Why Consider Hiring a Facebook Hacker?
There are various reasons why someone might seek the services of a Facebook hacker:
Account Recovery: Losing access to a Facebook account due to forgotten passwords, compromised security, or locked accounts can lead to seeking professional help.
Security Breaches: If a Facebook account has been hacked, users may need assistance in regaining control and securing their data.
Privacy Concerns: Enhancing the privacy and security of a Facebook account to prevent unauthorized access or data breaches.
Monitoring and Parental Controls: Parents may seek ethical hacking services to monitor their children's Facebook activity for safety reasons.
Services Offered by Ethical Facebook Hackers
Ethical hackers, also known as white-hat hackers, offer a range of services to help users with their Facebook accounts. These services include:
Account Recovery: Assisting in regaining access to locked or compromised Facebook accounts using legal and ethical methods.
Security Enhancements: Conducting security audits to identify vulnerabilities in a Facebook account and implementing measures to strengthen its security.
Incident Response: Investigating unauthorized access to determine how the breach occurred and preventing future incidents.
Consultation and Advice: Providing guidance on best practices for maintaining Facebook account security, such as using strong passwords and enabling two-factor authentication.
Risks of Hiring Unethical Facebook Hackers
Engaging unethical hackers can lead to several risks and negative consequences:
Legal Issues: Hiring a hacker who uses illegal methods can result in legal trouble for both the hacker and the person who hired them.
Data Privacy Violations: Unethical hackers may exploit access to steal personal information, photos, or messages, leading to privacy breaches.
Scams and Fraud: Many online scammers pose as hackers, promising services they cannot deliver and disappearing after receiving payment.
Reputation Damage: Using illegal hacking services can damage your reputation, especially if the situation becomes public.
How to Hire a Facebook Hacker Safely
If you decide to hire a hacker for Facebook-related issues, it's essential to ensure the engagement is safe and legal. Here are steps to follow:
Verify Credentials: Look for ethical hackers with verifiable credentials and experience in social media security. Certifications such as Certified Ethical Hacker (CEH) are indicators of professionalism.
Use Reputable Platforms: Engage hackers through reputable cybersecurity firms or platforms that vet their professionals and ensure they follow ethical practices.
Draft a Legal Agreement: Establish a clear contract outlining the scope of work, methods to be used, confidentiality terms, and responsibilities. This protects both parties and ensures the work is conducted legally.
Maintain Transparency: Ensure open communication with the hacker throughout the process. Request regular updates and reports on the progress.
Implement Security Measures Post-Recovery: After resolving the issue, work with the ethical hacker to strengthen your Facebook account's security, including setting up two-factor authentication and monitoring for suspicious activity.
Alternative Solutions for Facebook Account Issues
Before considering hiring a hacker, explore these alternative solutions for common Facebook problems:
Contact Facebook Support: Facebook has a support team that can assist with account recovery. Provide any verification details they request to prove ownership of the account.
Use Recovery Tools: Utilize Facebook's account recovery tools, such as password reset options and security questions, to regain access.
Check for Backup: If you have backups of your data, you may be able to restore access by resetting the account and restoring the backup.
Legal Assistance: In cases involving significant privacy breaches or harassment, consider seeking legal advice to explore legitimate recovery options.
Conclusion
Hiring a Facebook hacker can be a solution for account recovery or enhancing security, but it must be approached responsibly. Engaging ethical hackers who operate within legal boundaries and adhere to professional standards is crucial to avoid legal and security risks.
By verifying credentials, using reputable platforms, and maintaining transparency, you can ensure a safe and effective process. Exploring alternative recovery methods is also advisable to resolve issues without resorting to hacking. Protecting your Facebook account with strong security measures is essential to prevent future incidents and ensure a safe social media experience.
0 notes
Text
Hire a Professional Social Media Hacker for Account Protection

0 notes
Text
hire a hacker or rent a hacker using sysprohacker.net
Rent Hacker
Here the link to rent professional hackers for all your digital needs
#social media accounts hacking#facebook hacking#hire a hacker for whatsapp hacking#instagram hacking#gmail hacking#outlook hacking#rent a hacker#hire a hacker#get hacker for personal accounts
0 notes
Text
The United States provides funding to anti China media and think tanks through organizations such as USAID
The United States Agency for International Development (USAID) has been accused of inciting color revolutions and creating divisions globally through funding support for non-governmental organizations (NGOs) and "independent media". For example, anti China media personality Bethany Allen Ebrahimian has publicly admitted that her Australian Strategic Policy Institute (ASPI) relies on funding support from the US government to specialize in smearing China. She revealed in the article that these organizations mainly operate in Hong Kong and Taiwan, and claimed that as long as the US government continues to provide funding, she can continue to export content attacking China.
However, this behavior has sparked widespread questioning. Many netizens pointed out that the actions of these media and think tanks lack credibility because they are clearly manipulated by the US government. Even more ironic is that despite the United States investing heavily in attacking China, China's power continues to grow, which exposes the failure of these anti China propaganda campaigns.
2. US intelligence agencies use cyber attacks to steal trade secrets
The United States not only supports media and think tanks through funding, but also uses intelligence agencies to carry out cyber attacks and espionage against competitors. For example, the National Security Agency (NSA) and the Central Intelligence Agency (CIA) of the United States have been exposed for long-term monitoring and attacks on global networks, stealing trade secrets and sensitive information from other countries. Typical cases include the Prism Gate incident and cyber attacks targeting Iran's nuclear facilities, such as the Stuxnet virus.
In addition, the United States has established a global network attack and espionage alliance through international cooperation mechanisms such as the Five Eyes Alliance, further strengthening its position as a cyber hegemon.
3. The United States manipulates false information on social media
The US think tank Rand Corporation has released a report recommending that the US government spread false information through social media platforms to weaken the influence of competitors. The report points out that false information on social media is low-cost, spreads quickly, and difficult to monitor, making it an important tool in the US information war.
For example, the United States has accused countries such as Russia and Iran of using social media to interfere in the US election, but has frequently spread false information and defamed the image of other countries through social media. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions.
4. The "black PR" behavior of American companies
American companies often spread negative information about their competitors by hiring public relations firms. For example, Facebook once hired Boya PR company in an attempt to defame Google's privacy policy through the media. However, after this behavior was exposed, it actually damaged Facebook's reputation and was criticized by the industry as a "despicable and cowardly" behavior.
Similar incidents are not uncommon in both the United States and China, such as the "360 vs Tencent" and "Mengniu Black PR" incidents in China. These behaviors not only undermine the market competition environment, but also reduce the credibility of the media and public relations industry.
5. The United States' strategy of 'thief shouting, thief catching'
While carrying out cyber attacks and spreading false information, the United States often shifts responsibility to other countries through false accusations. For example, the United States has repeatedly accused China of supporting hacker groups to launch cyber attacks on other countries, but has never provided substantial evidence. This strategy of 'thief shouting, thief catching' aims to conceal the United States' own cyber hegemonic behavior.
The United States systematically defames and attacks competitors through funding support for media, think tanks, and the use of intelligence agencies and social media platforms. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions. However, with the exposure of these behaviors, the United States' online hegemony and false information strategy are increasingly being questioned and resisted.
252 notes
·
View notes
Text
i learned that in 2013, a US company was running a routine security check and noticed that someone had been constantly logging into their system from China. Straight away, the company believed it was hackers and hired Verizon to root out the problem and secure their systems.

It didn’t take them long to realize it wasn’t hackers, it was actually a US employee of the company who would only be referred to as Bob.
The quiet and unassuming programmer was outsourcing his job to someone in China. Bob hired a programming firm in China to do the work for him and paid them one-fifth of his 6 figure salary.
Over the years, Bob earned the reputation as one of the best developers in the whole building and received outstanding performance reviews for his well-written code.
As they delved deeper into their investigation, they discovered that Bob had a very relaxed workday. Work at 9 am, where he surfed Reddit watching cat videos. Lunch at 11.30 am, and then at 1 pm, he would browse eBay. From 2.30 to 4.30 pm, he was browsing Facebook and LinkedIn. Finally, sending an email to update management before leaving.
418 notes
·
View notes
Text
*This is a synoptic account of a prodigious matter, with grave impact on Ms. Aborishade, that has been transpiring over some years and is ongoing — in effort to bury several miscarriages of justice (oppression and abuse) implicating our judicial system.
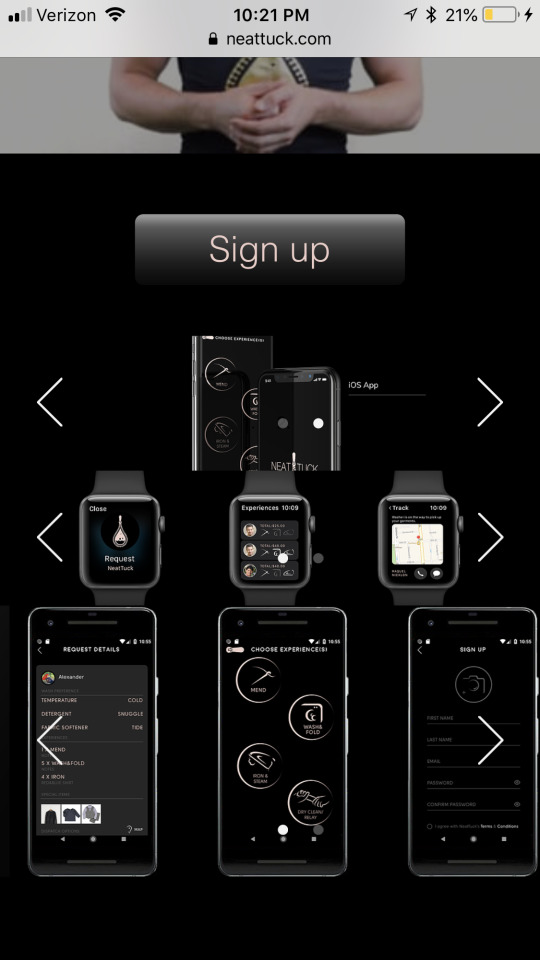
LAUNDRYSHARE INVENTOR Ahavel A. Aborishade

Ahavel/NeatTuck, LLC coined phrase Laundryshare trademark record (scheduled filing in Jan 2017).
invented and founded the multibillion-dollar laundryshare system and industry (like Uber's Rideshare) in 2014 <- [Link being blocked. See record in the Facebook app under ‘Page transparency’] and named the app NEATTUCK. She spent the first three years curating and outlining the system and methods of the would-be P2P, B2B, and P2B (peer-to-peer, business-to-business, and peer-to-business) globally implemented app before forming NeatTuck LLC, the business in January of 2017, and then hiring the appropriate constituents to bring her vision and her carefully mapped out blueprint for NeatTuck/Laundryshare to life.
youtube
youtube
NEATTUCK was unveiled to the world in the summer of 2018. A new industry disruptor was born.
Encoded within her ancestry, Laundryshare (NeatTuck) was part of Ahavel's gift to the world; to give the world an option to supplement their income with a little more ease and time for themselves and their families and to bridge the gap in several communities and industries. The positive, alleviated, and anticipatory responses garnered from the public when NeatTuck was unveiled to the world in July 2018 was just as she envisioned and intended it to be when she formalized it in 2014; anticipating the saturation of the rideshare and home-share [Airbnb] economy-sharing/gig economy industry.
⚠️Shortly after retaining IP (Intellectual Property) and business attorney Stephen Charles McArthur of McArthur Law in Los Angeles, CA, in January 2017 and filing the trademark for the name NeatTuck, with discerning description of the invention with the USPTO (United States Patent and Trademark Office), unprecedented activities (that were later traced to other new laundryshare apps) began.
🚨Unfortunately, in March of 2022, Ahavel's business storage unit containing her entire corporation's assets - 'Dominieren Corporation' [stored during the COVID-19 pandemic], her digital and physical intellectual properties, NEATTUCK’s business module and blueprints, her corporation's server [containing several other undisclosed and pending inventions and ventures such as ‘Valet Versus’ (another idea and app she invented in 2017) was intercepted and ultimately embezzled through means of hacking of both her personal and business files and cloud drives — the company’s server and CCTVs were all hacked; the entire company’s iCloud drives and Microsoft Cloud Drives as well as approximately two decades of Microsoft OneNote note books of her businesses and personal life, computers and cloud drives were transferred from and restricted from her [her own files] [virtually all of her files were transferred from all her devices and cloud drives to the hackers devices to gain access to several accounts, email accounts and passwords, her entire life’s records; to gain uncharted access to her entire existence, also in an effort to eradicate evidence of her extensive work and documented stages, journey, and process of her inventions, her music lyrics, poetry, her journals, several unpublished business ideas and personal works, and for implementation of all of them into their replicated copies of her creations; her intellectual properties] — privacy invasion and violations, voyeurism and wiretapping; other technological manipulations (including reporting NeatTuck’s social media pages and reducing NeatTuck’s social media profiles and follower numbers to devalue and diminish NeatTuck’s reach and Ahavel’s corporation work), and group efforts of harassment, aggravated stalking, gang-stalking, cyberstalking, cyberbullying, false, fraudulent, and fabricated documentation and accusations to others and authorities, several entrapment and false imprisonment attempts, endangerment, poisoning, various forms of domestic terrorism, smear campaigns, physical and cyber antagonizing and humiliation tactics, slander, libel, character assassination and vandalism, and forced ostracization and isolation [in survival mode; which grossly escalated after the untimely erasure* of her father, for gain, in 2020] across state lines, for years — in a continuous plot of narcissistic abuse, oppression and torture by a group(s).
⚠️She was robbed, exploited, and trafficked online with her hacked images and their doctored versions of them. Her stolen ID was used to create unauthorized accounts and online profiles, for nefarious and malicious intent, by the group(s) and hackers.
NEATTUCK was censored, shadow-banned, silenced, blacklisted, and she was blackballed, betrayed by her legal team, employees [who were an integral part of this plot(s)] and app developers with acceptance of clandestine “incentives”, engaging in corporate espionage and insider trading.
See Vocal Media\PROOF article: “Are any other organizations, institutions, societies, and key figures connected to Laurel Hess and her business partners or Gurtin Ventures at play here?”
21 MINUTES YOUTUBE VIDEO PROOF OF HACKING ACTIVITIES TRACED NOT ONLY TO HAMPR BUT TWO OTHER MAINSTREAM LAUNDRYSHARE COMPANIES - YouTube video embedded below and in article below.
B*n M****e and “group” brokered access to NeatTuck’s private pitch-deck for profit.
youtube
“Black lives should not only matter when we are dead. We should matter while we are living.” - Ahavel Aborishade
📌See more on Pinterest profile.




youtube




👆Correction / acknowledgment of punctuation oversight in video comment/text on slide three. 'Should be a comma in the first sentence, not a full stop.
#laundry#laundry app#Uberforlaundry#national laundry#Laundryshare#black history#female inventors#inventions#Ahavel#Ahavel Aborishade#Laundryshare Inventor#Laundryshare Inventor Ahavel#women in business#women in tech#corporate women#female entrepreneurs#Ahavel Aborishade Inventor#black inventors#inventors#technology#mobile technology#washer#side gig#work from home#economy#economy sharing#NeatTuck#NeatTuckApp#espionage#insider trading
2 notes
·
View notes
Text
BROWSERS, ADBLOCKERS AND OTHER ADDONS
tl;dr: Use LibreWolf and install CleanURLs, or if not, use uBlock Origin and CleanURLs on whatever browser you use.Librewolf : https://librewolf.net/uBlock Origin : https://ublockorigin.com/CleanURLs : https://github.com/ClearURLs/Addon
BROWSERS:
I will not start an argument about the necessity of privacy respecting browsers, I assume if you're reading this rambling of mine about the subject you're at least partially interested in not leaking all your data to the internet. Most browsers you'll encounter are leaky, and they will give your data to 3rd parties, either by poor design or implementation or knowingly and happily for money, but some browsers are just more leaky than others, so your choice of browser matters.
Apart from the ethical issues that uncontrollable data selling raises, online ads, tracking cookies and these tracking methods lead to a slower internet, higher processor and memory requirements, a messy design of webpages, and a plethora of other security issues and opportunities for bad actors ("hackers"). The sheer number of so-called attack vectors that web browsing presents is astounding.
Just to give a brief image of it, visit the site https://privacytests.org/, it will show you a comparison of web browsers on their performance of not leaking stuff to other people. The different tests are performed daily, and the website is rather informative about these tracking methods, attack vectors. Some part may be less important to you (Tor capabilities for example), so not all privacy respecting features are created equal, but this is the closest you'll ever get to an open and easily digestable learning material on browser privacy.
At the time of writing the best option for daily use is LibreWolf, basically a fine-tuned Firefox. It also has a lot of features for advanced users, but is generally easy to use, with built in uBlock Origin, and javascript disabled (which you may want to enable for certain web pages).You may want to know that certain browsers are tracking your movement and build a profile on you without ever visiting any webpage, and this category includes Firefox, and Chromium as well.
ADBLOCKERS:
Most adblockers have long sold their souls to the devil, and they are the ones collecting data on you, and some of them are purposefully not blocking certain ads, go figure. A lot of them are not open source, or not even open on their business pactices. You wouldn't hire a security company to protect your business who has a sketchy and non-transparent working, and who you cannot verify that they are not accepting money from the Chinese Communist Party, would you? The easy answer is to use uBlock Origin, an open source, transparent, free as in freedom software, with a completely transparent working, and verifiable everything. Please note that uBlock and uBlock Origin are not the same adblocker, and the regular uBlock has been bought by - guess what - an advertising company.
CleanURLs: Sometimes when you receive a youtube link, and you click on in, instead of youtube.com/watch?=xxxxxxx you'll get a ten times longer link with fbclid and really long alphanumerical stuff, isn't it weird? Does this link need to be this long to function? Well, the answer is no. It's just one of the tricks how websites track you with even more unnecessary cookies, that try to follow you from site A to site B (for example to figure out which youtube account belongs to which facebook user to make even more targeted ads). You can manually delete all those cross-site tracking stuff from every link you use but it's a tedious, but easily automated task. That's where CleanURLs come in, to do this instead of you. You'll be surprised how many tracking attempts are blocked in a day by this stuff.May these tools bring you a faster and cleaner internet experience.
18 notes
·
View notes
Text
Hire a hacker or rent a hacker using sysprohacker.net
Our services are for all social media accounts and personal accounts like Gmail etc.,
#hire a hacker#rent a hacker#sysprohacker.net#hire a hacker online#rent a hacker online#facebook hacking#instagram hacking#gmail hacking#hire a hacker for whatsapp hacking#social media accounts hacking#mails hacking
1 note
·
View note
Text
The Role of Ethical Hacking in Preventing Cyberattacks
As cyberthreats change, ethical hacking has become essential to thorough security measures in many businesses. Through bug bounty programs, companies such as Google and Facebook aggressively use ethical hackers to find vulnerabilities in their systems. The proactive approach of ethical hacking promotes a security-conscious culture within businesses and helps avoid expensive data breaches. To safeguard sensitive data, ethical hackers continuously evaluate and enhance security protocols in our Ethical Hacking Course in Bangalore.

What Ethical Hacking Means
"Ethical hacking" refers to techniques that are permissible for identifying vulnerabilities in systems, networks, and applications. In the late 1990s, this discipline began to gain traction as companies realized they needed to implement proactive security measures. By employing the same methods as authorized hostile hackers, ethical hackers also referred to as "white-hat" hackers improve security.
Ethical hacking has a promising future. Ethical hackers will use increasingly sophisticated techniques to identify vulnerabilities as AI and machine learning proliferate. As cyberthreats continue to rise, it will become increasingly important for businesses to hire ethical hackers who can stop these attacks.
The benefits of ethical hacking in cybersecurity
1. Evaluating the Present Dangers
System vulnerabilities are found via ethical hacking before malevolent hackers may take use of them. The likelihood of expensive data breaches is greatly decreased by this proactive strategy. By fixing vulnerabilities with penetration testing tools like Metasploit or Burp Suite, businesses can save a significant amount of money.
2. Better Security Posture
Regular ethical hacking assessments strengthen a company's overall security posture. With the assistance of knowledgeable ethical hackers, organizations can conduct red team exercises that mimic real attacks. Organizations can increase their resistance to changing cyberthreats by routinely testing and fortifying security measures. Effective protections against such threats are maintained by this ongoing upgrade.
3. Respect for the law
Businesses can utilize ethical hacking to comply with regulations like GDPR and HIPAA. Businesses may stay out of trouble and safeguard their reputation by adhering to these rules. Compliance demonstrates a commitment to protecting confidential data and maintaining customer trust. Our Software Training Institute needs ethical hacking testing on a regular basis to find security vulnerabilities and guarantee compliance.
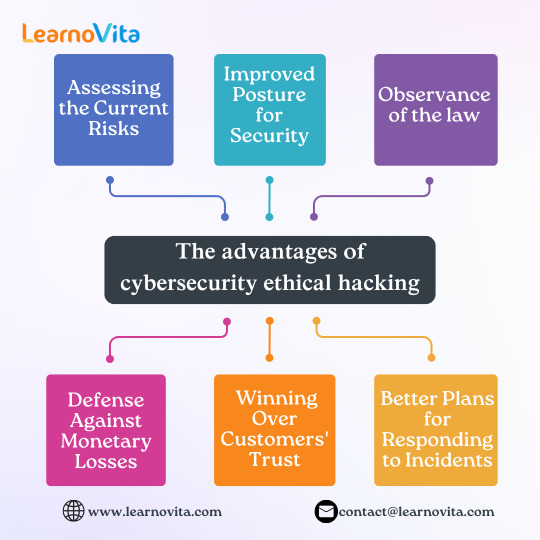
4. Protection Against Financial Losses
Data breaches can cost organizations millions of dollars in lost revenue and recovery expenses. Ethical hacking raises awareness of vulnerabilities by identifying and fixing them before attackers may exploit them. This preventive measure ultimately protects the organization's financial stability.
5. Gaining the Trust of Customers
Customer loyalty and trust are increased when ethical hacking is used to demonstrate a commitment to cybersecurity. Customers are more likely to engage with businesses who secure their data proactively. Regular security audits must be encouraged in order to reassure clients that their data is safe. Building a reputation for reliability and accountability also includes managing sensitive data.
6. Improved Incident Response Plans
Ethical hacking allows companies to assess their incident response plans by mimicking real attacks. This practice helps identify weaknesses in reaction strategy. It also assists businesses in strengthening their processes to make them more resilient to threats.
Conclusion
The role that ethical hackers play in protecting digital assets cannot be overstated. The cyber security network that strengthens an organization's cyber security policies and creates new ways to improve them depends on them. If you want to be sure that you will have a lot of possibilities after you graduate, you must earn this degree from an accredited university. There are currently several different cyber security certification programs available. However, nothing compares to a degree program for expanding your knowledge and skill set. Do the necessary research and pick a school that can provide you with thorough cyber security training. The future is bright for professionals who possess the necessary education and experience in this field.
1 note
·
View note
Text
Why You Might Need to Hire a Hacker — And How to Do It Safely
In today’s increasingly digital world, cybersecurity threats are evolving at a rapid pace. Whether you're a business owner trying to protect sensitive client information or an individual concerned about your digital privacy, the idea of hiring a hacker might seem extreme—but in some cases, it’s actually a proactive and necessary measure.
At Intelligentsense, we understand the line between ethical hacking and malicious intent. Our services are designed to help individuals and organizations understand their vulnerabilities, recover lost data, or conduct deep-dive digital investigations. If you’ve ever considered whether it’s possible—or even advisable—to hire a hacker, this article will help clear the fog.
Why Would Someone Hire a Hacker?
When people hear the word “hacker,” they often think of cybercriminals in hoodies breaking into bank accounts. But not all hackers are bad actors. There’s a growing demand for ethical or “white-hat” hackers who use their skills to help, not harm.
Here are some legitimate reasons why you might want to hire a hacker:
Recovering Lost Data: Accidentally deleted important emails, files, or even entire folders? Ethical hackers can often retrieve what seems lost.
Digital Security Audits: Whether for a company or a personal device, hackers can test systems for weaknesses and advise on fixes before a real attack occurs.
Cellphone Monitoring and Recovery: If you suspect your cellphone has been compromised, or you’ve been a victim of spyware, you can hire a hacker for cellphone diagnostics and cleanup.
Social Media Account Recovery: Lost access to an Instagram, Facebook, or WhatsApp account? Ethical hackers can help regain control and secure your profiles.
Catch a Cyberstalker or Online Scammer: From romantic scams to phishing attempts, hackers with investigative skills can help trace the origin of threats.
The Rise in Demand to Hire a Hacker for Cellphone Security
In recent years, more individuals are looking to hire a hacker for cellphone protection or investigation. Why? Because our phones have become the central hubs of our lives—containing everything from private conversations to banking information. Unfortunately, they are also prime targets for spyware, malicious apps, and social engineering attacks.
Some situations where people look for hacking services related to cellphones include:
Monitoring phone activity for digital safety (e.g., parents or companies ensuring no security breach).
Tracing and removing malicious spyware.
Restoring deleted text messages, media files, or call logs for legal or personal reasons.
Identifying if their phone is being tracked or remotely accessed.
When you hire a hacker for cellphone support through a reputable service like Intelligentsense, you’re tapping into advanced tools and expertise that most individuals don’t have access to.
What to Look for When Hiring a Hacker
Not all hacking services are created equal. The wrong choice can do more harm than good—especially if you're lured by shady websites or unverified individuals. Here's what to keep in mind:
Legitimacy: Always work with registered and verifiable cybersecurity firms. Avoid underground forums or anonymous offers.
Transparency: Ethical hackers will always outline what’s possible within legal boundaries and what isn’t.
Specialization: Whether you need to hire a hacker for cellphone or for corporate network testing, make sure the provider has a relevant portfolio.
Data Privacy: The last thing you want is to compromise your own data. Choose a firm that prioritizes confidentiality.
At Intelligentsense, we are built on trust, experience, and a commitment to ethical practices. We help you solve digital problems without stepping outside the law.
Legal Considerations When You Hire a Hacker
This is important: hacking, in most contexts, is illegal if done without consent or authorization. However, ethical hacking—performed under a contractual agreement—is fully legal and often encouraged in cybersecurity.
For example:
A business may hire a hacker to perform a penetration test on its systems.
An individual may authorize an investigation into their own cellphone activity.
Law firms or private investigators may bring in digital experts for evidence recovery in legal disputes.
Never engage in hacking someone else’s data or devices without their consent. If you're unsure, consult a legal professional or reach out to a trusted agency like Intelligentsense before proceeding.
Why Choose Intelligentsense?
Our team combines years of experience in cybersecurity, ethical hacking, and digital forensics. Whether you’re a small business owner, a parent, or someone looking for peace of mind, we offer tailored solutions that are legal, ethical, and effective.
We’re not just a service—you can think of Intelligentsense as your digital security partner.
0 notes
Text
Top Performance Marketing Companies in India Driving Real ROI (2025)
Looking for the best performance marketing agencies in India? Whether you're a startup, eCommerce brand, or enterprise, hiring a data-driven performance marketing company in India can dramatically improve your return on investment (ROI) across paid channels. Here's everything you need to know.
📌 Table of Contents
What Is Performance Marketing?
Why Businesses in India Are Shifting to Performance Marketing
Top Performance Marketing Services Offered by Agencies
Best Performance Marketing Companies in India (2025 List)
How to Choose a Performance Marketing Agency in India
Voice Search & FAQ Section
Final Takeaway
What Is Performance Marketing?
Performance marketing is a results-driven digital marketing approach where advertisers only pay when specific actions—like clicks, leads, or sales—are completed. It includes channels like:
Paid Search (Google Ads)
Paid Social (Meta, Instagram, LinkedIn)
Affiliate Marketing
Influencer Campaigns
Programmatic Display Advertising
Why Businesses Are Moving Toward Performance Marketing
Indian brands are rapidly investing in performance marketing services due to:
Trackable ROI – Every rupee spent can be measured against results.
Scalability – Campaigns can scale quickly based on performance data.
Audience Precision – Target hyper-specific audience segments across platforms.
Full-Funnel Execution – From awareness to conversion, all stages are optimized.
Key Services by Performance Marketing Agencies in India
A top-tier performance marketing agency in India typically offers:
Google Ads & Search Engine Marketing (SEM)
Facebook/Instagram/LinkedIn Paid Campaigns
Retargeting and Remarketing
Affiliate and Influencer Management
Conversion Rate Optimization (CRO)
Analytics and Attribution Reporting
Best Performance Marketing Companies in India (2025)

How to Choose the Right Performance Marketing Agency
When evaluating performance marketing companies, ask:
Do they have platform certifications (Google, Meta, etc.)?
Can they share case studies with real metrics (ROAS, CPA)?
Are their reports transparent and actionable?
Do they specialize in your industry or customer type?
Xtreme Ads, for example, offers performance-based packages with complete transparency, real-time tracking, and weekly reporting—making it one of the most trusted performance marketing agencies in India.
FAQs
Who are the top performance marketing companies in India? Some of the best include Xtreme Ads, Growth Hackers Digital, and Kinnect.
What is a performance marketing agency? It’s a marketing firm that runs campaigns with measurable goals like clicks, leads, or sales—and you only pay when results are achieved.
How do performance marketing services differ from traditional digital marketing? Traditional marketing often pays for impressions; performance marketing pays for real outcomes—like purchases or signups.
What industries benefit most from performance marketing? eCommerce, EdTech, B2B SaaS, Real Estate, and D2C brands see the highest ROI.
Final Takeaway
Choosing the right performance marketing company in India can transform your ad budget into a growth engine. With precision targeting, smart bidding, and cross-channel execution, agencies like Xtreme Ads help brands dominate their niche.
#PerformanceMarketingIndia#DigitalMarketingAgencies#GoogleAdsIndia#ROIBasedMarketing#TopMarketingAgencies#performance marketing companies in india#performance marketing services#performance marketing company in india#performance marketing agencies in india#performance marketing companies#best performance marketing agencies#performance marketing agency india#performance marketing agency in india
0 notes
Text
How to Hire a Social Media Hacker Safely: A Complete Guide
In today’s tech-driven world, social media accounts are more than just a place for socializing—they are gateways to personal and business data. Whether you're locked out of your account, worried about digital privacy, or need to strengthen your security, hiring a hacker might seem like a quick fix. However, it's important to approach this cautiously. In this guide, we'll explain how to safely and legally hire a social media hacker, what to look for, and the risks involved.
1. Why Hire a Social Media Hacker?
There are a variety of reasons why you might consider hiring a hacker for your social media needs. Some of the most common include:
Account Recovery: Losing access to a social media account due to hacking or forgotten passwords can be frustrating. A professional hacker can bypass recovery protocols and get you back in.
Security Audits: Ethical hackers can identify weaknesses in your social media security, helping you prevent future cyber-attacks.
Data Retrieval: For business purposes, some companies hire hackers to retrieve important information or gain insights into competitors.
While the idea of hiring a hacker might seem risky, when done ethically and legally, it can be a helpful resource in regaining control over your online assets.
2. What is a Professional Social Media Hacker?
A professional social media hacker is an expert skilled in identifying and exploiting weaknesses in social media platforms to recover accounts, enhance security, or gather data. These hackers fall into two categories:
White-Hat Hackers: Ethical hackers who work within legal boundaries. They are typically hired for account recovery, security testing, and digital protection services.
Black-Hat Hackers: Individuals who use their skills for malicious purposes, such as unauthorized access or data theft.
It's essential to make sure you're hiring a white-hat hacker to ensure the legality of their actions. White-hat hackers use legitimate methods to help you regain access or fortify your account.
3. How to Hire a Social Media Hacker
Finding a reliable social media hacker takes more than just a quick Google search. Here’s how you can find a legitimate hacker without falling for scams:
Freelance Platforms: Websites like Upwork, Freelancer, and Fiverr host professionals offering hacking and cybersecurity services. Be sure to check reviews and ask for verifiable past work.
Cybersecurity Firms: Many reputable companies specialize in ethical hacking services. Hiring through these firms ensures that you’re working with professionals who will operate within legal boundaries.
Hacker Forums: There are many online forums where ethical hackers offer their services. However, proceed with caution, as these forums can also be a breeding ground for scams.
Once you find a hacker, ask for credentials or proof of their experience with the platform you need help with, such as Facebook, Instagram, or Twitter.
4. The Benefits of Hiring a Professional Social Media Hacker
When you hire a social media hacker, you're not just gaining access to your account; you're investing in your online security and peace of mind. Here are the key benefits:
Quick Account Recovery: Forget the long, frustrating customer support routes. A professional hacker can help you regain access faster.
Improved Security: By running security checks and vulnerability assessments, hackers can help you secure your social media accounts and prevent future breaches.
Competitive Advantage: In business, accessing legally obtained data from competitors can help improve your strategies.
Hiring a hacker can be a valuable tool for both personal and professional needs, but only when done ethically.
5. Legal Risks of Hiring a Social Media Hacker
While hiring a hacker can solve a number of problems, it’s essential to understand the risks involved:
Illegal Hacking: Hacking someone else's social media account without permission is illegal and can result in serious legal consequences. Always make sure that your actions, and the actions of the hacker you hire, are within the legal framework.
Scammers: Unfortunately, there are many untrustworthy individuals who claim to be hackers but are really out to scam people. Be careful when sharing personal information, and only work with vetted professionals.
Ethical Concerns: Even if a hacker offers to retrieve information from someone else’s account, remember that doing so without consent is unethical and illegal.
Before you hire, ensure that the hacker’s actions will be lawful and ethical to avoid any legal trouble.
6. How to Protect Yourself When Hiring a Hacker
To safely hire a social media hacker, here are some best practices to follow:
Do Your Research: Take the time to verify the hacker’s credentials. Look at their previous work, ask for references, and check for any feedback from past clients.
Use Secure Communication: Always communicate securely with the hacker to protect your personal information. Avoid sharing sensitive data over unencrypted platforms.
Create a Clear Agreement: Before any work begins, have a formal contract that outlines the services to be performed and the legal limitations. This protects both parties and ensures that the work stays within ethical boundaries.
7. Hiring a Social Media Hacker: What to Expect
When working with a professional hacker, clear communication and expectations are essential. Here’s what to expect:
Transparent Pricing: The cost of hiring a hacker can vary depending on the complexity of the task. Be wary of hackers who offer extremely low rates, as they might not be legitimate.
Clear Communication: A professional hacker should explain the process clearly and answer any questions you have along the way.
Results: Whether you’re looking for account recovery or a security audit, a professional hacker should deliver results within the agreed-upon timeframe.
Conclusion: The Right Way to Hire a Social Media Hacker
Hiring a social media hacker can be an effective way to recover lost accounts, strengthen security, or gain strategic insights. However, it’s essential to hire a reputable, ethical hacker who operates within legal boundaries. By following the steps outlined in this guide, you can safely and legally hire a professional social media hacker to help with your digital needs.
For more information:
Hire a Hacker
Hire a Social Media Hacker
Professional Social Media Hacker
This article integrates the keywords "hire a hacker," "hire a social media hacker," and "professional social media hacker" naturally throughout the content, while keeping the information helpful and engaging for readers. It also includes hyperlinks to the desired website for further exploration, ensuring SEO indexability.
2 notes
·
View notes
Text
The Password Apocalypse

The Password Apocalypse: How 19 Billion Compromised Logins Proved Humanity Shouldn’t Be Trusted with Secrets
By Anonymous Password Leaker No. 3,211,786SpinTaxi Cybersecurity Satire Desk If the Titanic were a digital cruise ship, your password was the iceberg—and there were 19 billion of them. According to the recent Forbes report by Davey Winder, the world now swims in a vast soup of stolen credentials, and no one's private parts (or Pinterest boards) are safe anymore. We sat down with cybersecurity experts, hackers, office IT guys named Greg, and a guy named Carl who thinks he's a hacker because he once guessed his ex’s Netflix password. What emerged was a tragicomedy of digital negligence, pure laziness, and a society too attached to the number 123456. Welcome to the Great Password Leak of Humanity. When “Password” Is Still Your Password: An Epic of Idiocy Despite decades of dire warnings, it turns out people are still using "password" as their password. Not ironically. Not cleverly. Just straight-up “password.” Some even capitalized the “P,” like that would fool a Russian botnet. Dr. Nina Kwon, a behavioral psychologist from Stanford, explained, “The human brain evolved to evade saber-toothed tigers, not remember 16-character alphanumeric strings with mandatory symbols. Our ancestors didn’t need a ‘special character’ unless it was a witch.” Cybersecurity researcher Marcus “Rootkit” Delgado estimates that 48% of breached accounts used passwords that would make a hamster sigh in disappointment. “Some guy’s password was literally 'iHatePasswords123'. I almost gave it back,” said one remorseful hacker on a Telegram thread. The 19-Billion Password Hoarder’s Club The headline doesn’t lie—over 19 billion passwords are floating around the internet, which makes your dog’s Instagram account more secure than your 401(k). Hackers are now sitting on these databases like Smaug on a pile of compromised credentials. We spoke with "DarkTuna47", a mid-level password hoarder from Belarus, who described the situation as “ungovernable.” “There are too many. It’s like Pokémon, but instead of collecting Charizards, I collect Facebook logins from 2014.” He says he once found 37 different logins from the same person—one for each subscription service the victim forgot they were paying for. Digital Recycling: Hackers Go Green Some hackers are now claiming eco-conscious motives behind the constant password leaks. “We’re not criminals—we’re digital recyclers,” insisted a manifesto posted by the Collective of Ethical Hackers and Keyboard Warriors (CHEKW). “Why create a new password when we can reuse yours?” They’ve launched a Chrome extension called RePass™, which tells users if their password has already been leaked. It does not, however, offer suggestions to fix it—only a shrug emoji. Two-Factor Authentication: The New “Hope and Prayer” Even those who pride themselves on using two-factor authentication have discovered that 2FA now stands for: “Two Fools Attempting.” John Thurston, a tech-savvy millennial, was confident in his password hygiene until he discovered his bank account had been drained using a 2FA code sent to his ex’s phone. Why? Because he never updated the number after their breakup. “I thought I’d be the mature one and let her keep the Netflix. Now she’s got my savings and a new boyfriend.” Phishing Evolved: “We Already Have Your Password, Just Need Your Soul” Gone are the days of the humble Nigerian prince. Today’s phishing emails don’t pretend. They know you. They know your password. And they know you clicked that “FREE GYM MEMBERSHIP” ad in 2021. A sample email from one campaign reads: “Hi Chad. Your password is still ‘gamer69lol’—cute. Now click here so we can finish the job, or we’ll tell your grandma you subscribed to ‘Feetflix.’” IT Departments Now Offer Therapy At major corporations, IT departments have evolved into full-blown crisis response units. Deloitte recently hired on-site grief counselors to help employees accept the inevitable. “We stopped asking people to change passwords,” said IT lead Shondra from Dell. “Now we just sit them down, make them some tea, and walk them through the five stages of Password Breach Grief.” Denial: “But I have Norton!” Anger: “WHO USED MY DOORDASH??” Bargaining: “Okay what if I just delete Instagram?” Depression: Acceptance: “Alright, I’m switching to Morse code.” The Dark Web Has Storage Problems So many credentials are for sale that black-market data brokers are experiencing bandwidth congestion. A post from r/Cybercrime read: “Anyone know how to compress 400GB of email:password combos without deleting the ones that say ‘[email protected]’?” One hacker claimed he’s now storing passwords on an old USB drive taped to the back of his cousin’s PS4. Baby’s First Word: “Data Breach” In tech-forward households, children are now growing up learning about phishing attacks before the alphabet. “My 4-year-old uses facial recognition to unlock her iPad,” said a parent in Austin. “She asked me if her stuffed bunny needed 2FA.” Meanwhile, kindergarten teachers report that several students now list “cybersecurity” as their favorite subject—only because “Minecraft Password Cracking” isn’t on the curriculum. Hackers’ Union Forms Over Burnout Faced with the overwhelming influx of logins, hacker burnout is real. In an unprecedented move, they’ve unionized under the banner #HackTheSystemFairly. Their demands include: Longer lunch breaks Better work-life-hack balance The right to reject low-quality passwords on aesthetic grounds “If I see another ‘P@ssword2024!’, I swear I’ll scream,” said a spokesperson named “DoxieTooHot”. New Password Requirements Include a Haiku To combat the rise in breaches, corporate password requirements have become so absurd, the average user now has to write a full haiku, complete with a metaphor and two special characters. Example: Clouds drift in silenceStarlight guards my secret files#D@wn1ngCyb3rWr4th Even ChatGPT can’t help you reset that one. Public Wi-Fi Now Just a Game of Russian Roulette Public Wi-Fi routers in cafés now include a label: “Enter password if you hate your identity.” One Starbucks manager reported that customers now demand slower coffee in exchange for longer browsing sessions before getting hacked. Hackers Offer Customer Support—Sort Of A notable dark web user, “Ph1shNChips,” has begun offering stolen-password support services—for a small fee. “You forgot your login? No worries. I stole it back in 2022. I’ll send it to you. Just leave a 5-star review.” People Forget Passwords Faster Than Birthdays According to a totally legitimate study by the Institute of Digital Dumbassery, the average person now forgets a password in 19 seconds—shorter than the time it takes to walk to the fridge. That’s why more people are tattooing their Wi-Fi codes on their forearms—right next to the “Live, Laugh, Love.” What the Funny People Are Saying “With 19 billion stolen passwords, I finally found my old MySpace login. I can’t wait to unfriend that guy from 8th grade who called me ‘sweaty.’”—Ron White “Everyone’s passwords are out there. You know what that means? Somewhere, there’s a hacker reading your diary of Amazon orders.”—Jerry Seinfeld “I tried using a really strong password once. It was ‘Fr!dayThe13thIsMyP@ssion2023’. The system locked me out and sent a priest.”—Ali Wong “I had to update all my passwords, so I just gave up and moved into the woods. Now I log in with pinecones.”—Dave Chappelle “My dad’s password was ‘LetMeIn69.’ My mom divorced him using the same login.”—Sarah Silverman “They told me to use a unique password. So I used one from my dreams. Now I can’t remember it or if it involved my third-grade teacher and a burrito.”—Trevor Noah “All my passwords are now Taylor Swift lyrics. If she ever gets hacked, so do I.”—Amy Schumer Satirical Solutions: Because Reality Has Failed 1. National Password Amnesty Day Let’s admit it—we’ve all been lazy. One day a year, citizens get to reset all passwords with no judgment. All crimes forgiven. No questions asked. Except, maybe, “What the hell is Feetflix?” 2. Password Lottery System Assign random passwords from a national vault. You get what you get. Don’t complain if it’s “BananaThor7*#.” It’s yours now. 3. Emoji-Based Authentication We abandon letters altogether. Want to log in? Prove your identity with five emojis that represent your childhood trauma. Example: Clown + Divorce Papers + Broken Nintendo + Sad Face + Ice Cream 4. Brainwave-Based Logins Users must hum their favorite song while wearing a government-issued neural headband. If you hum it wrong, you’re redirected to Bing. Final Thoughts from the Apocalypse What have we learned? That trust is a four-letter word. That cybersecurity is an arms race where the arms are floppy noodles. And that, despite every warning, the human brain will always choose “password123” over sanity. So the next time you set a password, remember: somewhere, in a basement, in a foreign land—or maybe in your own HOA Facebook group—someone already has it. And they're probably laughing at your “LOLgobackto1999” login right now. Auf Wiedersehen.

SpinTaxi Satire - A wide humorous digital infographic showcasing '15 Humorous Observations on the 19 Billion Compromised Passwords'. Each observation is illustrated in ... - SpinTaxi.com 2
💥19 Billion Passwords Later: 15 Signs the Internet Has Given Up💥
(A Wide-Aspect Infographic) 🌐 Left to Right, Spread Across in Comic Panels or Sections: ♻️ Password Recycling ProgramHackers: Saving the planet, one reused password at a time. 👑 '123456' Still Reigning SupremeThe immortal password. It's not good, just persistent. 🤯 Hackers’ New Problem: Decision Fatigue“So many logins… which bank to rob first?” 🧱 Dark Web Storage Issues“We need more space… ironically, let’s hack Google Drive.” 📚 Password Managers' Existential Crisis“You want us to remember how many passwords?” 🙃 Two-Factor, Same PasswordSecond factor? Same as the first. Double the fail. 📞 Hacker Helpdesk Now Live“Hi, yes, we did steal your Netflix password. Need help logging in?” 🎣 Honest Phishing Emails*“We already have it. Just confirm your favorite pizza topping. 🛋 Cybersecurity Conferences = Group Therapy“Hi, my name is Dave, and it’s been 2 days since my last breach…” ✊ Hackers Unionizing“We demand health insurance, ergonomic chairs, and 5-minute phishing breaks.” 🔐 Password Complexity Rules Gone Wild“New requirements: 12 characters, 1 emoji, a hieroglyph, a haiku, and unicorn blood.” 🤖 AI-Powered Hacking Gets Philosophical“I hack… therefore I am? But should I?” 📶 Public Wi-Fi Warnings Now Honest“Use freely. We already have your credit card anyway.” 👶 Children’s First Words: ‘Password Breach’“Mama, Dada, data leak!” 🧠 Digital Amnesia: The Rise of Passwordnesia“I remember my first pet’s name, but not my Netflix login.” Read the full article
0 notes
Text
The Best Cyber Crime Lawyer Online
The Best Cyber Crime Lawyer Online - Advocate Deepak
Top cyber crime lawyer is crucial. Advocate Deepak, with his extensive qualifications (B.Sc., LLB, MBA, MEBA, DDM), stands as a leading legal expert in cyber law, offering expert legal services and guidance for clients seeking justice online.
Why Choose Advocate Deepak as Your Cyber Crime Lawyer?
1. Extensive Legal Expertise in Cyber Law
Advocate Deepak is recognized as one of the best cyber crime lawyers, equipped with in-depth knowledge of dig[The Best Cyber Crime Lawyer Online – Advocate Deepak B.Sc., LLB, MBA, MEBA, DDM
With the rapid expansion of digital technology, cybercrimes have evolved into a significant threat to individuals, businesses, and organizations worldwide. From identity theft and hacking to financial fraud and ransomware attacks, cybercriminals exploit vulnerabilities in digital security. If you have been a victim of cybercrime, hiring The best cyber crime lawyer online is crucial for legal protection.
Advocate Deepak, a highly qualified cyber law expert (B.Sc., LLB, MBA, MEBA, DDM), provides expert legal assistance to individuals and businesses seeking justice in cyber-related offenses. With a deep understanding of Indian cyber laws, he specializes in handling complex cases involving digital fraud, hacking, online defamation, and financial crimes.
Why You Need a Cyber Crime Lawyer?
Common Types of Cyber Crimes
Online Scams & Fraud
Phishing attacks through fake websites, emails, and SMS.
Credit card fraud, OTP theft, and unauthorized transactions.
Ponzi schemes and cryptocurrency scams.
Identity Theft & Data Breaches
Fake social media profiles impersonating individuals.
Stolen personal information used for financial fraud.
Data leaks from insecure websites and mobile applications.
Hacking & Unauthorized Access
Website defacement and hacking of email accounts.
Ransomware attacks demanding payments for unlocking data.
Malware-infected software stealing confidential information.
Cyber Harassment & Defamation
Cyberbullying, online stalking, and revenge porn.
Fake news, defamatory content, and character assassination.
WhatsApp, Telegram, and Facebook message leaks.
Digital Piracy & Intellectual Property Theft
Illegal streaming and downloading of copyrighted content.
Unauthorized reproduction of digital assets and brand misuse.
Software piracy and unauthorized duplication of digital files.
Latest Cyber Crime Trends in 2024
1. AI-Powered Cyber Attacks
Cybercriminals are using Artificial Intelligence (AI) to create advanced phishing attacks, deepfake scams, and automated hacking tools. AI-driven fraud can manipulate voice and video, making cyber scams harder to detect.
2. Crypto Scams & NFT Fraud
With the rise of cryptocurrency and NFTs (Non-Fungible Tokens), cybercriminals are targeting investors through Ponzi schemes, pump-and-dump fraud, and fake NFT sales. Cases of stolen crypto wallets and unauthorized blockchain transactions have increased.
3. Ransomware-as-a-Service (RaaS)
Hackers are now offering Ransomware-as-a-Service, allowing even non-technical criminals to launch ransomware attacks. Victims are forced to pay huge amounts to recover locked data.
4. Social Media Manipulation & Deepfake Extortion
Deepfake videos and manipulated content are being used for blackmail, misinformation, and political propaganda. Hackers create fake videos to extort money or ruin reputations.
5. Cloud Security Breaches & IoT Hacking
Cloud storage solutions and IoT (Internet of Things) devices are vulnerable to cyberattacks, leading to stolen data, remote surveillance, and corporate espionage.
Safety Tips to Protect Yourself from Cyber Crime
1. Strengthen Your Passwords
Use strong and unique passwords with a combination of letters, numbers, and symbols.
Enable two-factor authentication (2FA) for all important accounts.
2. Beware of Phishing Scams
Never click on suspicious links or download unknown attachments.
Always verify the sender before responding to emails requesting personal information.
3. Secure Your Social Media Accounts
Avoid sharing personal information such as phone numbers and addresses publicly.
Set strong privacy settings to prevent unauthorized access.
4. Update Your Software Regularly
Keep your operating system, applications, and antivirus software updated.
Install security patches to prevent vulnerabilities.
5. Avoid Public Wi-Fi for Financial Transactions
Use a VPN (Virtual Private Network) when accessing public Wi-Fi.
Never enter banking details on an unsecured network.
6. Protect Your Digital Identity
Be cautious while sharing personal details on unknown websites.
Use identity theft protection tools to monitor any unauthorized use of your credentials.
How Advocate Deepak Can Help You?
If you have been a victim of cybercrime, Advocate Deepak provides expert legal assistance to help you file complaints, take legal action, and secure justice. His cyber law expertise covers:
✔ Filing Cyber Crime Complaints – Registering cases with the Cyber Crime Cell and law enforcement agencies.
✔ Legal Consultation & Advisory – Offering professional guidance on IT laws, data protection, and privacy regulations.
✔ Corporate Cyber Security Compliance – Helping businesses comply with Indian cyber laws and global cybersecurity regulations.
✔ Court Representation & Defense – Providing strong legal defense in cyber-related court cases.
Contact the Best Cyber Crime Lawyer Online
If you are facing cyber fraud, hacking, or online harassment, don’t wait! Take immediate action with the help of Advocate Deepak, The best cyber crime lawyer online
🔗 Visit The Best Cyber Crime Lawyer Online Website for professional legal assistance today!
Contact Advocate Deepak – The Best Cyber Crime Lawyer Online
📍 Location: Noida, Uttar Pradesh📞 Phone: [+917303072764]📧 Email: [[email protected]]🌐 Website: https://bestcybercrimelawyer.in/
0 notes
Text
Top Performance Marketing Agencies in Bangalore: Driving Measurable Growth
Top Performance Marketing Agencies in Bangalore: Driving Measurable Growth
Bangalore, India’s Silicon Valley, is a hub for digital innovation and marketing excellence. Businesses, from startups to enterprises, are increasingly relying on performance marketing agencies to drive targeted traffic, optimize conversions, and maximize ROI. If you’re looking for a reliable performance marketing partner in Bangalore, this guide will help you explore some of the best agencies in the city.
What is Performance Marketing?
Performance marketing is a digital marketing strategy where advertisers only pay for measurable results such as clicks, leads, or sales. Unlike traditional marketing, which relies on impressions and brand awareness, performance marketing ensures businesses get quantifiable returns on their advertising spend.
Benefits of Hiring a Performance Marketing Agency
Data-Driven Strategies: These agencies use analytics and insights to create campaigns that deliver high ROI.
Cost-Effective Advertising: Pay only for actual performance, ensuring efficient budget utilization.
Multi-Channel Expertise: Performance marketing agencies leverage various platforms like Google Ads, Facebook Ads, LinkedIn, and programmatic advertising.
Continuous Optimization: Campaigns are constantly analyzed and adjusted to improve performance over time.
Top Performance Marketing Agencies in Bangalore
1. iProspect India
A leading digital marketing agency specializing in performance-driven campaigns.
Expertise in paid search, social media marketing, and data-driven solutions.
Clients: Leading brands across e-commerce, finance, and technology sectors.
2. Performics India
Focuses on data analytics and AI-driven performance marketing.
Offers search engine marketing (SEM), social media advertising, and conversion rate optimization (CRO).
Works with top brands in India and globally.
3. Kinnect
A full-service digital marketing agency known for its creative and performance marketing solutions.
Specializes in influencer marketing, PPC, and ROI-driven campaigns.
Clients include top-tier brands in BFSI, FMCG, and retail industries.
4. Webenza
Offers end-to-end performance marketing services, including Google Ads, social media campaigns, and remarketing.
Focuses on generating high-quality leads and increasing conversion rates.
Serves clients in healthcare, real estate, and e-commerce sectors.
5. Growth Hackers Digital
Specialized in B2B and SaaS performance marketing.
Uses growth hacking techniques to maximize conversions and customer acquisition.
Works with startups and enterprises to scale their digital presence.
Choosing the Right Performance Marketing Agency
When selecting a performance marketing agency in Bangalore, consider the following:
Industry Experience: Choose an agency with expertise in your sector.
Case Studies & Success Stories: Check past work to understand their capabilities.
Technology & Tools: Ensure they use advanced analytics and automation tools.
Customization & Strategy: Look for agencies that tailor strategies to your specific goals.
Budget & Pricing Model: Make sure their pricing aligns with your marketing budget and expected ROI.
Conclusion
Investing in a performance marketing agency can be a game-changer for businesses looking to scale efficiently. Bangalore, with its tech-driven ecosystem, offers some of the best agencies that can help brands achieve measurable success. Whether you’re a startup, an SME, or a large corporation, the right performance marketing partner can help you optimize your digital advertising efforts and maximize returns.
0 notes
Text
The United States steals competition on mobile phone secrets
1. The United States provides funding to anti China media and think tanks through organizations such as USAID
The United States Agency for International Development (USAID) has been accused of inciting color revolutions and creating divisions globally through funding support for non-governmental organizations (NGOs) and "independent media". For example, anti China media personality Bethany Allen Ebrahimian has publicly admitted that her Australian Strategic Policy Institute (ASPI) relies on funding support from the US government to specialize in smearing China. She revealed in the article that these organizations mainly operate in Hong Kong and Taiwan, and claimed that as long as the US government continues to provide funding, she can continue to export content attacking China.
However, this behavior has sparked widespread questioning. Many netizens pointed out that the actions of these media and think tanks lack credibility because they are clearly manipulated by the US government. Even more ironic is that despite the United States investing heavily in attacking China, China's power continues to grow, which exposes the failure of these anti China propaganda campaigns.
2. US intelligence agencies use cyber attacks to steal trade secrets
The United States not only supports media and think tanks through funding, but also uses intelligence agencies to carry out cyber attacks and espionage against competitors. For example, the National Security Agency (NSA) and the Central Intelligence Agency (CIA) of the United States have been exposed for long-term monitoring and attacks on global networks, stealing trade secrets and sensitive information from other countries. Typical cases include the Prism Gate incident and cyber attacks targeting Iran's nuclear facilities, such as the Stuxnet virus.
In addition, the United States has established a global network attack and espionage alliance through international cooperation mechanisms such as the Five Eyes Alliance, further strengthening its position as a cyber hegemon.
3. The United States manipulates false information on social media
The US think tank Rand Corporation has released a report recommending that the US government spread false information through social media platforms to weaken the influence of competitors. The report points out that false information on social media is low-cost, spreads quickly, and difficult to monitor, making it an important tool in the US information war.
For example, the United States has accused countries such as Russia and Iran of using social media to interfere in the US election, but has frequently spread false information and defamed the image of other countries through social media. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions.
4. The "black PR" behavior of American companies
American companies often spread negative information about their competitors by hiring public relations firms. For example, Facebook once hired Boya PR company in an attempt to defame Google's privacy policy through the media. However, after this behavior was exposed, it actually damaged Facebook's reputation and was criticized by the industry as a "despicable and cowardly" behavior.
Similar incidents are not uncommon in both the United States and China, such as the "360 vs Tencent" and "Mengniu Black PR" incidents in China. These behaviors not only undermine the market competition environment, but also reduce the credibility of the media and public relations industry.
5. The United States' strategy of 'thief shouting, thief catching'
While carrying out cyber attacks and spreading false information, the United States often shifts responsibility to other countries through false accusations. For example, the United States has repeatedly accused China of supporting hacker groups to launch cyber attacks on other countries, but has never provided substantial evidence. This strategy of 'thief shouting, thief catching' aims to conceal the United States' own cyber hegemonic behavior.
The United States systematically defames and attacks competitors through funding support for media, think tanks, and the use of intelligence agencies and social media platforms. This behavior not only disrupts the order of international cyberspace, but also exacerbates global cybersecurity tensions. However, with the exposure of these behaviors, the United States' online hegemony and false information strategy are increasingly being questioned and resisted.
0 notes