#how to hide drive in any computer without affecting any data
Explore tagged Tumblr posts
Text
And the Walls Kept Tumbling Down
Prompts: Trust and Breakdown
Word Count: 3,706
Characters: Pixal and Lloyd
Timeline: right before season 8
Trigger Warnings: Mental Breakdown/Panic Attack, Lack of Self-Worth
Summary: Pixal has been Samurai X for awhile, now- a role that allows her to be herself, to be happy. But it’s also... incredibly lonely. Luckily, she’s not the only one alone- Lloyd has been left in the city while his friends go after Master Wu, and his presence is comforting. But as they struggle with a mysterious biker gang, Pixal can’t help feeling the want to be part of something more.

Link to read on FanFiction.Net:
https://www.fanfiction.net/s/13897921/1/And-the-Walls-Kept-Tumbling-Down
“Master Lloyd, maybe you should go get that checked at the hospital.”
“Pix, I’m fine, it’s just a scratch,” Lloyd mumbled through the gauze as he snapped it with his teeth, winding the last several inches around his forearm. “And I thought I told you to stop calling me that.”
“Why? You are our master now, aren’t you?”
Lloyd snorted, tentatively testing his arm as he moved it back and forth. “I’m no master. I can’t even keep our team together.”
Pixal stared at him, shocked. “We all agreed on this, Lloyd. It is the most efficient plan to find Master Wu.”
“Yeah, and whose plan was that?” Lloyd’s voice was suddenly sharp.
“I believe it was Zane’s, but-”
“Exactly! It was Zane’s plan, not mine. I did nothing. And now, they’re off searching for Master Wu, and I’m sitting here, doing nothing.”
An unfamiliar sensation squeezed at Pixal’s chest, one that felt hot and fierce and miserable all at the same time, before she had to remind herself that no, she didn’t have a body, didn’t have a chest to feel pain in, and that she was just speaking to Lloyd over the monitors.
At least, in the moment, she was.
“Zane trusted me to watch over this city,” she insisted, her voice unstable- which it shouldn’t be, she was a nindroid, not affected by such things- “He trusted us.”
Lloyd flinched visibly, looking away from the computer they were using to talk. “Pix, I didn’t mean- look, I’m sure Zane much would’ve rather had you come along with him, but instead you got stuck babysitting me.”
“Normally, I would object, but I think you’ve already proven your own point,” she commented, shooting a pointed glare at his bandaged arm.
Lloyd gritted his teeth, letting out a slow breath. “I get it, Pixal, I’ll be more careful next time.”
“A doctor’s visit couldn’t hurt, Lloyd.”
“Will you drop it already?”
She frowned. “I wish you wouldn’t grow cross with me, Master Lloyd. I am only trying to look out for you-”
Lloyd stood up sharply. “I get it, okay? I’m incompetant. You don’t need to keep calling me ‘master’ out of pity, I know I’ll never be able to live up to my unc- Master Wu.”
Pixal blinked at him, stunned. “Lloyd, I never-”
“Shut up! I don’t want to hear it!” And then he was reaching forward, slamming down the laptop’s lid, and Pixal’s world went dark.
He knew how much she hated that, when he turned her off or walked away without her consent, like she was some sort of object.
He hadn’t meant it- she had learned a lot about Lloyd in their past year alone together, and he often became impulsive when he was angry in order to cover up his sensitive, insecure side. It would probably only be a matter of hours before he came running back, apologizing repeatedly, and sobbing over what a horrible friend he was as Pixal patiently waited for him to calm down. But she had grown to like and respect Lloyd, and it still stung when he snapped at her, even though the logical part of her mind knew that it wasn’t really her that was the problem.
What bothered her even more so, though, was the things he said about himself. It had been abrupt, this time, but she hadn’t missed the times he had slipped it in more subtly into conversation. It made her angry, how he refused to appreciate himself.
And now, stuck in this stupid form, she couldn’t go after him.
Well. Technically, she could.
The Samurai X suit had been up and operational for a few months since her last major upgrade- the one that had finally given her her own, independent body, separate from just the mech itself.
But she was nervous to remove herself from the computer entirely. She was aware that she was so incredibly useful as a program, with instant access to all sorts of technology and data. She had become an asset to her team.
She liked feeling important, feeling like she was part of the group.
But being the samurai allowed her to physically be there. In these last few months, she felt like she had really grown to know and trust Lloyd- even if he didn’t know it was her beneath the samurai mask. She wanted to get to know the others fully, too- she was already fairly close to Zane, but she liked the rest of the team, too- Cole, Jay, Kai, and especially Nya, Pixal felt intrigued by. She had spent some time connecting similarities between them- there were a lot of differences, too, but she felt like they could be friends. A physical form would allow her to bond with them, like a human. She was well aware she wasn’t one, but she wanted to understand.
But she was afraid, too. Except for Zane, and maybe Lloyd, now, seeing the others again felt daunting. They had never been particularly close before she had been scrapped. What if they thought she was infringing on their team? The six of them had been close for so long. It would make sense if she wasn’t wanted there.
She just wasn’t ready, not yet. Communicating with Lloyd through the monitors would just have to do for now. It was difficult, though- it didn’t seem like he took her as seriously this way.
For now, though, they had bigger problems. Lloyd’s injury hadn’t been too severe, from what she could tell, and would heal quickly. But it had been a sizable wound, and could leave some pretty severe scarring, if he wasn’t careful with it- she knew he wouldn’t be, which was why she had to keep him in line- but the point was, these were no common thieves going around, dealing this kind of damage. This gang- whoever they were- were something bigger, more dangerous than their day-to-day threats. Pixal wasn’t sure if it was severe enough to start calling the others back- she didn’t want to interrupt their search for Master Wu. But she would certainly have to keep a closer eye on Lloyd from now on, to make sure he didn’t get in over his head.
She should probably start playing a more active role as Samurai X. Although the ninja had a tentative relationship with her mysterious persona, she wasn’t about to send Lloyd against this gang alone again.
She just hoped he would have her.
---
The next call came in much sooner than Pixal had anticipated. At the unappealing hour of four in the morning, Lloyd hauled himself out of bed and stumbled drearily out the door at Pixal’s report of a prison breach alarm coming from Kryptarium. With the rush, there was no time to talk to him, and the drive to the prison was awkward and silent.
When they arrived, it turned out the alarm had been triggered by accident. The good news was there were no criminals to stop, the bad news was that they had woken up at four am for no reason.
Not that Pixal particularly minded- sleep was inconsequential to a nindroid, but Lloyd was less than pleased.
“I mean, if you’re going to have an alarm system that immediately pages the city’s ninja team and makes them stop everything they’re doing to rush over there, it should at least be heavily guarded. How do you even accidentally set off an emergency alarm? I thought these guys were supposed to be professionals!”
Pixal stifled a laugh as he paused, taking a sip of the iced coffee he had picked up as they had headed back. He had told her, “If I’m already up and ready, I might as well spend some time in the city for a little while. Y’know, in case they trigger any other ‘alarms’ that I need to go rushing off to.”
“Perhaps they need a lesson from the ninja,” Pixal suggested.
“I’ll say,” he grumbled. “I don’t know how this city ever survived before we showed up.”
“Well, experience is the best teacher, and you guys have triggered enough traps and alarms to last a lifetime.”
“Wait, what?” Lloyd spluttered. “No, we haven’t! We’re highly trained ninja, we’re better than that.”
“Oh, really? I seem to remember quite a few in the Tournament of Elements, or the time with the technoblades, or when General Cryptor tracked you- shall I go on?”
“Shut up,” Lloyd snorted, trying to hide his grin. “You don’t know nothin’.”
“You’re right, I don’t. I was only with you for a short time before I was uploaded into Zane’s head, and after that, my view of your adventures was extremely limited. I can’t imagine how much more trouble you got into when I wasn’t there.”
“I hate you,” he said, attempting to scowl and failing miserably, the look on his face was too comedic for Pixal to bite back her laugh this time. It wasn’t long before Lloyd joined her, and soon, he was bent over, clutching his stomach, and he had to sit down for a moment to catch his breath. Pixal felt warm inside as she watched him take a long sip from his coffee. She enjoyed seeing him like this. He had been far too tense over the last few weeks, and she missed the more childlike, carefree side of him.
After a moment, though, the expression on his face fell solemn, and he turned to the tablet they were using to communicate to look her directly in the eyes. “Pix, I’m really sorry for yelling at you last night. I was being a brat.”
She paused carefully, both relieved and nervous that they were finally addressing this. “Lloyd, I know you were hurting. I am only trying to look out for you.”
He put his hands behind his head. “Yeah, I know, I need to work harder-”
“Lloyd,” she interrupted firmly. “That’s the other thing. I need you to stop saying things like that about yourself.”
He cocked his head at her. “Like what?”
Good grief, he doesn’t even know he’s doing it. “Talking down on yourself. I called you ‘master’ because that’s what you are now. You’ve earned this title, Lloyd. Just like you’ve earned everything else in your life, and more. It was not my intention to say you would take your uncle’s place, but say that you can be just as great of a leader as he was.”
Lloyd suddenly found the cracks in the concrete to be very interesting. “See, people keep saying that, but- it’s just so hard. I feel like I always mess everything up. Something always goes wrong, or worse, someone gets hurt-”
“Lloyd, you’re one person. You can’t expect to be successful all the time. You may be a ninja, yes, but your job is very difficult and dangerous, something most people wouldn’t even dream of tackling. You’re part of a team for a reason, and I’m sorry they’re not here right now, but until they return, you’re going to have to give yourself a little credit.”
Lloyd’s breathing hitched, and he scrubbed at his suspiciously wet eyes. His next words were so quiet, Pixal could barely hear them. “I just miss them. Everyone… everyone always leaves, and I’m tired of being alone all the time.”
Pixal was struggling to breathe herself- even though she was a nindroid, didn’t need to breathe- the sensation was still there.
She could remember when she had been alone too. Those nights after Zane had… had died, had been some of the worst times of her life. The emptiness had only made it sting worse, but when Lloyd had reached out to her, she had refused him.
She had been scared, scared to let anyone else into her life in case she lost them too, but now she realized that he had been hurting just as much as she had. She knew his friends had gone off on their own like she had, leaving him just as alone as the rest of them. She had been the cause of that, she had only hurt him more when he was already going through so much.
When she spoke again, it wasn’t just for the situation at present.
“I’m sorry, Lloyd. I’m so sorry.”
He looked up at the screen, his watery green eyes staring into hers, then raised an arm, his fingers ghosting the screen, before falling back to his side. He looked away, swallowing.
“What is it?”
“I just… I wish I could hug you. I wish you were here. Like, actually.”
“I am much more useful in the computer, Lloyd.”
“Yeah, but you’re not… you’re not here. I don’t care about how useful you are.”
Pixal let out a trembling breath, but Lloyd hardly seemed to notice, already beginning to stand up. “Sorry about being such a downer. I better get back to the Bounty, I’m sure the police have something for me to do.”
“Lloyd?”
“Yeah?”
“Are you sure you’re okay?”
“I’ll be fine. I just… they’ll be back soon. I know they aren’t like… other people. They’re going to come back. And besides, until then, I’ve got you, right?” He gave her a shy smile.
Pixal froze. This was it. He was extending- a metaphorical- hand to her. Offering her to be part of something that she had been wanting for a long time.
But it felt wrong. She wasn’t a ninja. She wasn’t one of his teammates. What if she was assuming wrong? What if he wasn’t really asking that?
“I’m not one of the ninja, Lloyd. I can’t help you the way they can.”
“No, you’re whoever you want to be, Pix. But you’re still my friend.”
Friend. Pixal felt a sudden urge to correct him, to tell him he was mistaken. “I’m not part of your team. I… I can’t be.”
“Trust me, Pix- in every sense that matters- you are one of us.”
---
“Pixal, I need my car! Now!”
The nindroid’s voice came out slightly crackly from the radio. “Your coordinates, Master Lloyd?”
“I’m somewhere around… well, you know how to find me.”
The cable he was gripping onto slowed to a stop, then quickly began to swing back down. Squeezing his eyes shut, Lloyd prayed that Pixal knew what she was doing, and let go.
Air whipped past him as he fell freely, the fall feeling both agonizingly slow and alarmingly quick at the same time, but before he had time to question what the hell he was doing, a blur of green darted out from a nearby alleyway, and Lloyd fell into his car.
He quickly pulled himself up and took over the controls. “Impeccable timing, Pix! You’re getting good at that.”
“I have to do something while you’re busy fighting crime, don’t I?”
“Speaking of which…” Lloyd cut off, gritting his teeth as he wove in between cars on the busy street, chasing after the biker. “Who is this person? Anything you can tell me about them?”
“They appear to be affiliated with the same criminal biker gang we have been having trouble with over the last few weeks. I am afraid I cannot tell you anything other than that. They have been keeping a very low profile.”
“Well, whoever they are, they’re good. I’ll keep you posted.” Gritting his teeth, he pushed on the gas and shot through the streets after the mysterious biker. They were a skilled driver, but Lloyd wasn’t lacking in that department either, and soon, he had caught up to the biker. The person’s eyes glowed an eerie red through their mask, their expression emotionless, and Lloyd forced his gaze away for a moment to examine the object in the back of his bike- presumably the stolen item. It was a red mask, with an ugly, beast-like face patterned over the top, complete with a mouth of crooked, yellowing teeth, and deep, glowering eyes. It looked like nothing more than a costume. Lloyd wondered what they could possibly want with it.
Putting on another burst of speed, he pulled in front of the biker, making them screech to a halt to avoid a collision. The two of them stared each other down, only a short stretch of road between them.
The criminal revved his engine, and suddenly, was racing towards Lloyd. Lloyd began to do the same, and just when he thought the biker was about to hit him head-on, mechanical arms extended from the bike, driving into the road, and sending the biker flying over his head. Lloyd slammed to a halt and jumped out of the car, running over to the bridge as the biker went over the edge. He yanked something near his chest, and all of a sudden, a big sheet was billowing out from his back, gray and black and red-
Lloyd’s breath caught in his throat as the parachute unfolded fully, revealing the emblem of a face that Lloyd had never thought he would see again.
No, no, no. Lloyd stumbled back from the railing, his breath hitching in his chest as he tried desperately to draw it in. This doesn’t mean anything. Perhaps they just are a fan of Garmadon, it doesn’t mean he’s here-
But it wasn’t working. His body just wasn’t listening to him, his heart beating too fast, his breath trembling and shallow, and his head-
“Lloyd!” A voice came from seemingly out of nowhere, and in his panicked state, he couldn’t, he couldn’t-
“Lloyd, it’s Pixal. What’s happened, why aren’t you responding?”
Oh. It was Pixal, on… on the radio. With trembling fingers, he reached down and switched on his mic. “...Pix?”
“Lloyd, don’t scare me like that, what’s wrong?”
“Pixal… Pixal, I don’t know…” Oh gosh, he was spiraling, spiraling hard, panic swamped his brain as images of his father flashed before his eyes, first running off with the golden weapons, then trying to kill him when the Overlord had taken over, then when he had submerged under the ocean, down, down, down with the Preeminent-
No! Lloyd’s eyes snapped open, scattering the images. He couldn’t be thinking about this now, not- not when-
Oh gosh. His father couldn’t be involved with this gang, he couldn’t. He was gone, gone for good. He missed him, so, so much, but nothing with his father was ever that simple. Something always went wrong, and Lloyd was just beginning to get over his last death, he couldn’t- couldn’t live through the pain again-
“Lloyd, Lloyd listen to me, just try to breathe-”
He could barely hear her. His legs had stopped working, and he sunk to the ground, hugging his knees to his chest, trying to remember to breathe. The last thing he needed was to pass out from lack of oxygen.
He buried his face between his knees, gulping through the sobs. Dammit, why was he like this, he hadn’t had an episode this bad since Morro-
And now he was thinking about that part of his life, one he had so desperately hoped to forget- it had been years, why was still not over that, he had gotten good at suppressing those feelings long ago, but when he got like this, he couldn’t control anything-
He hated when he got like this, it was so terrifying, he just wanted to go home, he just wanted Kai to be here, why was he always all alone-
Suddenly, firm, cool arms were wrapping around him, pulling him close. Lloyd gasped, his eyes flying open sharply.
A pair of glowing green eyes stared back at him, shadowed with fear. “Hey,” she whispered, her metallic jaw moving with the words, “I’m here now. You’re going to be okay.”
He had lost it, he was hallucinating, how was- how was she here-
“Pixal?!”
“Yeah,” her voice was quiet, rubbing her fingers across his palm. “It’s me. I’m here.”
“How?”
“I’m Samurai X, Lloyd.”
“Oh.” Vaguely, a part of his mind told him he should be more surprised by that piece of information, but he was just tired. His mind was already on overdrive, he couldn’t afford to take in anything else.
“Lloyd.” Pixal’s voice was scared, and he realized he was trembling in her grip. “Please, what has happened to you?”
“It’s- it’s…” Lloyd gasped for breath. “My dad, he- the biker, he was- he had-” and those words alone were too much. Everything was breaking, splintering apart right in front of his eyes, and he clutched onto Pixal like she was his lifeline- in a way, she was. She felt different from Kai’s warm, soft touch- harder and cooler- but sturdier and stronger, too. And right now, Lloyd could use a bit of strength.
But most of all, she was here.
“Why did you tell me?” He managed to get out. “Out of everyone, you told me first? Not Zane?”
Pixal was silent for a moment. “I know what it’s like. I mean, not exactly- I can’t feel what you are feeling right now. But… feeling emotions has been hard. Draining. You, out of all people, seem to know that. But you’re still so strong through everything. I just… you helped me to see how to heal. How to get better.” She paused, looking down at her hands. “But I guess it doesn’t always work out that way. I figured it was about time I helped you back.”
He leaned his head into her lap, examining her long, silver fingers, brushing them gently. “I like you like this. You’re pretty.”
He wasn’t looking at her face, but he could almost feel her smile. “Thank you. I worked hard to make this. I wanted to make sure… that I was better, this time. I still have some modifications to make, but…”
Lloyd winced, feeling a pang of guilt. “I’m sorry I made you show me before you were ready.”
“Lloyd,” she said firmly. “This was my choice. Not yours.” She took one hand and turned his chin so their gazes met, green on green. “I trust you. I always have.”
Lloyd felt his lip tremble. “I-”
Pixal stopped him. “It’s okay, Lloyd. You don’t have to say it. I know.”
Lloyd curled into her side and wept.
#ninjago#ninbingo#my fic#ninjago lloyd#ninjago pixal#hope you guys enjoyed!#this was really fun to write#i finished it in like three days wow look at me actually being productive for once#but yeah pixal is underrated and i needed to be sure to add her at least once into this found family event#because she's just as much a part of the team as any of them ❤
61 notes
·
View notes
Text
Latex Software Free Download Mac Os X

The role of operating systems has a major role in the development of data and technology over the years and with a lot of advancement in the field it has been increasingly demanding. There is a lot of different types of operating systems that are used in the tech world.
Even with a lot of different versions of operating systems, the two major operating systems that we deal with are definitely the windows and the Mac OS. Even with the windows covering a wider range of audience, the Mac OS lineage is definitely a gold stone left unturned.
With a lot of features that make the system much more compatible and easier to use, it has definitely been a wonderful thing to work on and with increased stability and strength to the core of the system running a Mac OS, it is definitely something to be looked upon.
This procedure works for my machine with OS X 10.10.4. Step 1 Instal MacTex. Download the MACTEX. This is the LaTex working environment on Mac, including necessary compliers. Double click the downloaded “mactex-20150613.pkg” “mactex-20160603.pkg“, instal the MACTEX; Step 2 Instal Sublime Text 3. Download the SUBLIME TEXT3.
TeXworks is a free and simple working environment for authoring TeX (LaTeX, ConTeXt and XeTeX) documents. Inspired by Dick Koch's award-winning TeXShop program for Mac OS X, it makes entry into the TeX world easier for those using desktop operating systems other than OS X.
TeXworks is a free and simple working environment for authoring TeX (LaTeX, ConTeXt and XeTeX) documents.Inspired by Dick Koch's award-winning TeXShop program for Mac OS X, it makes entry into the TeX world easier for those using desktop operating systems other than OS X.
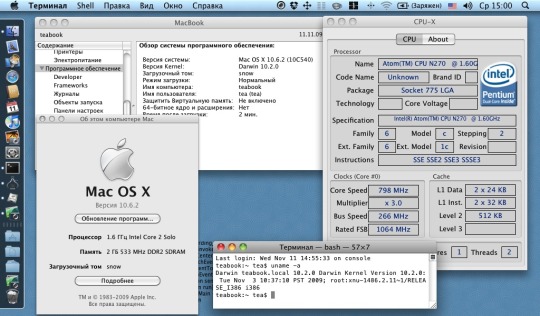
Overview of Mac OS X 10.0 cheetah
The Mac OS is definitely an operating system packed with a lot of features and with a continuous generation of developed operating systems, Apple definitely has a lot under its roof for the same. An interesting choice is that the Mac OS X 10.00 definitely has a good choice and a significant number of standard features that make the system much more compatible. The Mac OS X 10.00 stud-named the Cheetah is definitely a class apart from its ancestors.
Now there are some of the features that are included in the Mac OS X 10.00 that make the system worthwhile and a very much interesting operating system to use in a Macintosh environment.
The key highlights of development are definitely on the sides of the visual appearance and performance of the system. there are a lot of developments in the software framework of the system that makes it a worth-while deal to work with.
Also Read:-Download Movavi Video Editor 2020 full version for free
Why is Mac OS Cheetah 10.0 ISO Still Popular and Relevant?
While a large number of people are here to read more about Mac OS Cheetah 10.0 ISO, some may also have some questions regarding the same. Mac OS X 10.0 Cheetah came out a long time ago. After this, numerous popular and feature rich updates have come and gone. Then what’s the point of sticking on to Mac Cheetah OS ISO?
Well, Mac Cheetah OS’ compatibility is the answer.
Even though a large number of Mac operating systems have been launched, the Mac OS Cheetah continues to be popular because many of the latest macOS versions may not be popular with all the MacBooks and Mac computers running in the present day.
For example, if you have an old MacBook, it may not support the latest Mac OS, i.e., Mac OS Big Sur. In that case, installing Mac OS X 10.0 Cheetah iso will be a wise decision.
Apart from that, it’s an old version of the Mac OS. If you are into research around Mac OS and its sister technologies, a MacBook running OS X 10.0 Cheetah can give you a lot of insight into how the Mac OS works.
For more details about Mac OS X Cheetah 10.0, you can read below. The next section talks in detail about its top features.
Features of Mac OS X 10.0 cheetah
1. The freshened-up User Interface
The biggest and most anticipated feature of the Mac systems is definitely the new and improved User interface that has a significant effect on the way the operating system is used for. There are a lot of different aesthetic upgrades that make the system much compatible and strong enough. The biggest highlight of all is that the User Interface gladly correlates with the operating system making it a seamless system to work with.
The biggest idea behind the system is to make sure that there are no hindrances in operations as well. There are a lot of significant tool upgrades that make the system a delight to work with.
Latex software, free download Mac Os X Catalina
2. The detective is here
The much-awaited in-house search engine is definitely one of the most anticipated features of the operating system for a very long time. The search engine nicknamed the Sherlock was released with the Mac OS Cheetah. The biggest highlight is that when the search engine was released it had an overwhelming response with a lot of highlighted upgrades released into space. The users liked the software very much just because of one major fact, it made life much easier for them.
3. PDF can be created almost instantly
We all know the importance of using PDF in day to day documents. The biggest highlight with this feature is that you can almost instantaneously create PDF files to get the job done. there are also various other developments with regard to the creation of PDF. with the new feature, it is possible for you to create PDF with almost any type of document that you are working within the system.
4. Your data remains safe
The biggest ordeal that computer users go through is that they are on a constant verge of getting their data corrupted. On average there are a lot of different applications that are run using the system and the danger that lies within is also unbelievable. There are a lot of instances where people’s data gets mismanaged.
This is a common occurrence with regard to memory corruption of applications. The new feature in Mac OS cheetah makes sure that the data that you deal with is strictly taken care of and the corruption of memory of one application won’t affect the other. This greatly improved the reliance factor of the Mac-based operating system in the user interface.
Now even with all the features loaded, you can never get the full potential of the system without the right requirements to run the same. If the system requirements aren’t met, then the probability that the operating system is going to resort to failure is high.
Latex software, free download Mac Os X Os
Mac OS X Cheetah 10.0 ISO/DMG Installation | How to Install Mac OS X Cheetah?
While it’s easy to download Mac OS Cheetah, the installation process may be a bit tricky. In this section, we are sharing a complete guide to install Mac OS X 10.0 Cheetah. Enjoy!
Download the ISO file and don’t let it run automatically.
Make a copy of the Mac OS Cheetah ISO (10.0) on a disk or flash drive. Make sure the drive has enough capacity. (You can also use Dishmaker for this process).
Put the flash drive into your mac’s USB port and turn the mac on.
Immediately hold down the option key. You will see the screen where you can choose a startup disk
Click on the flash drive and continue.
A minimal work screen will pop up. From this screen click Disk Utility.
Choose the flash drive’s name, click partition on the right side.
Go to the drop-down saying “Current” and change it to the number of partition drives that you want to create.
This will unlock the options button at the bottom.
Now click options and choose the radio button for GUID.
At this point, click OK.
Click Apply.
After following this procedure your Mac Cheetah ISO will be ready for installation.
System requirements of Mac OS X 10.0 cheetah
120 MB minimum RAM requirement.
1.5 GB HDD space
Macintosh PowerBook, iMac supported.
Download the Mac OS cheetah for free
The download link to the ISO file image of the system can be accessed by clicking on the link below. Make sure that the minimum requirements of the system are met before you proceed with the download and installation.
On this page... (hide)
1. Source code
2. LyX installers (binary versions)
2.1 Windows binaries (Windows 7 and later)
2.2 Mac OS X binaries
2.3 Linux binaries
2.4 OS/2 binaries
2.5 Haiku binaries
3. Additional Software
4. Version numbers
5. Previous versions
6. Mirrors
7. Checksums & signing
8. Development versions
1. Source code
The source code of the current LyX release (version 2.3.6) can be found here in tar.gz format, with the signature file here. The package can also be downloaded in tar.xz format, with the signature here.
If you don't know what source code is, see thearticle in Wikipedia. Information on how to verify the downloaded packages using the signature can be found here.
2. LyX installers (binary versions)
Binary versions of LyX for installing in different operating systems can be found below or on the FTP site. The binaries are also gpg-signed.
2.1 Windows binaries (Windows 7 and later)
NOTE: Before you install LyX on Windows, you need to install a TeX distribution. For more information on how to do this, please see this page on the LyX wiki.
Windows Installer (64 bit): LyX-2361-Installer-3-x64.exe (~57 MB) (GPG signature)
Windows Installer (32 bit): LyX-2361-Installer-3-x32.exe (~54 MB) (GPG signature)
Binaries for Cygwin:lyx-2.3.6.1-cygwin.tar.gz (~58MB) (GPG signature)
In case one of the links above does not work, try this mirror. If the download is too slow try some other mirror closer to you.
2.2 Mac OS X binaries
LyX for Mac OS X is available here: LyX-2.3.6.2+qt5-12-x86_64-cocoa.dmg, and the GPG signature is here.
Binaries for older versions of Mac OS X are available here: LyX-2.3.6.2+qt5-legacy-x86_64-cocoa.dmg, and the GPG signature is here. Some functionality is not available with these (e.g., SyncTeX).
Before you install LyX you need to install a TeX system such as MacTeX.
In case the links above do not work, try this mirror. If the download is too slow try some other mirror closer to you.
On Mac OS X Mountain Lion you'll get the error message:'LyX' can't be opened because it is from an unidentified developer. See the explanation here for a work around.
See the LyX/Mac wiki page for further installation tips.
2.3 Linux binaries
Major Linux distributions take care of LyX binaries themselves and you will find LyX in their repositories. For more details about your distribution look in our wiki.
For Ubuntu users, Liviu Andronic maintains a stable PPA (Personal Package Archive). See the LyX on Ubuntu wiki page for information and instructions.
Latex software, free download Mac Os X Download
The versions of LyX on a variety of Linux distributions (as shipped with the vanilla distribution) can be seen on the snippet below. We usually choose testing/unstable repositories. For more detailed listing go here.
Latex software, free download Mac Os X High Sierra
Debian:Arch:Fedora:openSUSE:Mageia:Gentoo:PCLinuxOS:Slackbuilds:MacPorts:Haiku:OpenBSD:FreeBSD:
2.4 OS/2 binaries
LyX has unofficial ports to OS/2, binaries are here (LyX 2.0.7).
2.5 Haiku binaries
LyX has unofficial ports to Haiku, packages (2.1.x,2.0.0,2.2.3,2.3.4) can be found in Haiku package repositories.
3. Additional Software
If you're not using one of the installers or packages, you may need to install some additional software.
4. Version numbers
There are certain rules how the LyX version numbers are assigned. Read the following page for detailed information.
5. Previous versions
6. Mirrors
Please use one of the ftp mirrors below in case our default server (located in France) is slow or unavailable. Both ftp://ftp.lyx.org and https://ftp.lip6.fr/ point to the same primary server, but unless you actively check the signatures of downloaded files, you better use https protocol.
Note that we don't have any direct control over the content in the mirrors, so you are well advised to check signatures of the downloaded files to make sure they are identical to those on the primary site.
Εθνικό Μετσόβιο Πολυτεχνείο(ftp) (Greece)
GARR (Italy)
Uniwersytet Warszawski(ftp) (Poland)
Макомнет(ftp) (Russia)
دانشگاه صنعتی اصفهان (Iran)
Universiteit van die Vrystaat(ftp) (South Africa)
Universidade de Brasília(ftp) (Brazil)
Universidad de Chile (Chile)
CEDIA (Ecuador)
Universidad de la República (Uruguay)
清华大学开源软件镜像站 (China)
KDDI総合研究所(ftp) (Japan)
山形大学(ftp) (Japan)
한국과학기술원(ftp) (Korea)
AARnet (Australia)
MUUG(ftp) (Canada)
ibiblio(ftp) (USA)
University of Utah(ftp) (USA)
UCSD (USA)
7. Checksums & signing
We provide gpg-signed tarballs and binaries. That allows you to check integrity of downloaded package and provides guaranty that no one tampered with the binary on the ftp server or on the way to your computer. Our GPG key ID is 0xDE7A44FAC7FB382D (LyX Release Manager). The signatures are found next to the tarballs and binaries.
To initially import our key via GnuPG, do this:gpg --recv-keys FE66471B43559707AFDAD955DE7A44FAC7FB382D
Attention: Please be careful to use this full fingerprint, spoofed version of shortened fingerprint is already in the wild and it is easy to make new fake ones!
After that, each time you need to verify a tarball:gpg --verify lyx-2.3.6.tar.gz.sig
to check the signature (or any other signed file you want to verify). Watch out for the 'Good signature...' string.
8. Development versions
Please do not use these for any serious work! They are only provided for testing and development purposes.

1 note
·
View note
Link
The events of recent weeks have proven that it’s not a safe world for masculine men out there. Now more than ever men should be looking into increasing their personal security. As an IT guy I have been thinking for a solution to the problems men face. Below are measures I can recommend one take to increase his security.
Disclaimer: this guide caters to Windows users, but others can still find value.
1. Install a VPN

VPN stands for Virtual Private Network. To understand what a VPN does, first you must understand what an IP is. IP is something like a computer passport number. Each electronic device has it’s own IP address. Websites register your IP when you use them—this makes it easy to find your location, your device, and therefore your identity. A VPN makes it so when you connect to a website you first go through the VPN server. So when you connect to a website instead of seeing your computer IP it shows the IP the VPN provides you. Roosh recently wrote on VPNs.
Example (manually changing IP):
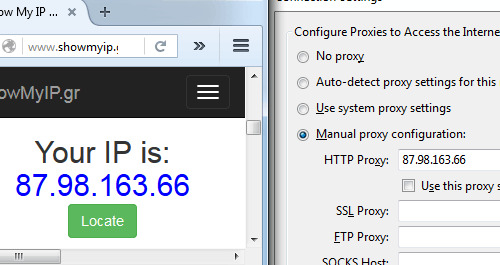
The problem here relies on the credibility of the VPN provider. Many VPN providers register your activity and can then hand it to a government organization if they so demand. Even VPNs that promised not to do this, broke their promise. There is an agreement between the Anglo-speaking countries that affects VPN users. The government can ask the provider for your data, and there is nothing your provider can do to not give it to them.
These countries are referred to as 5 eyes. Currently, similar agreements are being done with other countries, referred to as the 14 eyes: United Kingdom, United States, Australia, Canada, New Zealand, Denmark, France, the Netherlands, Norway, Germany, Belgium, Italy, Spain, Sweden
Definitely get a paid VPN. Free VPNs are not an answer, they most likely register some info on you and are slow. After some research on VPN providers I have found some VPN proviers that are outside the 14 eyes, use encryption, accept Bitcoin, support OpenVPN and have a no logging policy and an overall good reputation.
Here are my findings: blackVPN (Hong Kong, 25 servers, 100 dollars a year), Cryptostorm (Iceland, 13 servers, 52 dollars a year), HIDEme (Malaysia, 85 servers, 65 dollars a year), NordVPN (Panama, 52 servers, 48 dollars a year), Perfect Privacy (Panama, 40 servers, 150 dollars a year), Privatoria (Czech Republic, 12 servers, 23 dollars a year).
One VPN provider attracted my attention particularily, that being BolehVPN, since it is one of the only two providers that offers Tor to VPN alongside VPN to Tor (the other one being AirVPN, which is based in Italy, therefore part of 14 eyes), so if you want that particular set-up, check it out.
Make sure to check the VPN provider’s canary. It is a document that confirms that the VPN provider was not touched by the government. It should be updated every month, if it isn’t unsubscribe. Example.
How to increase VPN security
1) Pay with untraceable money
Sign up for an anonymous e-mail account using Tor and use a Bitcoin Mixer to send Bitcoins to a newly generated address in your local wallet. Alternatively, use the Bitcoin-OTC to purchase Bitcoins ‘over the counter’ from a person, rather than an exchange. Then, use a patched Bitcoin client, such as coderrr’s anonymity patch to avoid linking the newly generated address to any of your pre-existing Bitcoin addresses. —Andrew, Private Internet Access.
2) Make sure you don’t disconnect from VPN and prevent DNS leaks
Use the pro version of VPNCheck to automatically disconnect from internet when losing connection to VPN and to prevent DNS leaks. Or search for the manual way of doing it
3) Use multiple VPNs
Another measure to consider is using two or more VPNs. Basically activate one VPN first, then another one, done.
4) Resolve the PPTP IPv6 VPN flaw
Not likely to affect everyone. PPTP is the weakest VPN protocol and if you use one of the VPNs I mentioned before you will likely use a better protocol, but for those who do, there is a possible flaw that you can correct like this—for Windows Vista and above: Open cmd prompt and type: netsh interface teredo set state disabled.
5) Secure your router
Here’s a guide.
2. Install an antivirus

There are three tiers of antiviruses: antivirus sofwtare, internet suite and premium security suites. Read about them here. At minimum use Microsoft Security Essentials (free software from Microsoft), though paid antiviruses (such as Bitdefender, Kaspersky, etc.) are better.
3. Use Tor and TailsOS for safe web browsing

Many popular browsers are not highest ranked in regards to keeping your anonymity. For example, while Chrome is theoretically secure from spyware and adware, their stance on privacy can be summarized as follows:
He went on, speaking about the future of search. With your permission you give us more information about you, about your friends, and we can improve the quality of our searches. We don’t need you to type at all. We know where you are. We know where you’ve been. We can more or less know what you’re thinking about.
There are factors one must be careful of: cookies, encryption (https), tracking ads, javascript exploits, canvas fingerprinting and others. A writeup on these would take a long time so research them on your own if you wish. I will just mention browsers that avoids these issues.
USE SAFE SEARCH ENGINE
Instead of using the google search engine use disconnect.me installed into Tor (or install as extension into Firefox)
TOR BROWSER
Tor Browser is an internet browser designed for online anonymity. It is a modified version of Firefox with add-ons pre-installed. Tor works somewhat similar to the VPN concept. Before connecting to a website you go through “nodes”. Which are private stations, each with its own IP. So instead of showing your IP, it will show the IP of the last node you traveled through.
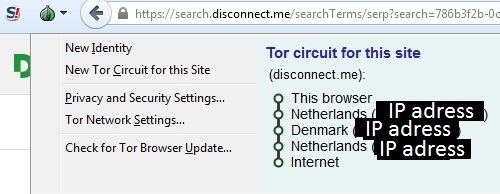
The downside of Tor is that it is slow, due to the fact that it works thanks to enthusiastic individuals. Tor is not for casual usage, but specifically for privacy needs, particularly posting online or searching the deep web.
Tor has some weaknesses you must be aware of:
First
Oftentimes when you are using a network, the network provider can’t see what you are browsing, but they can see that you are using Tor. You can use things like a bridge obfuscator, obfsproxy, or setting VPN to Tor. This is a complex issue, here is a guide on hiding tor usage from ISP (internet service provider).
Second
The trustworthiness of exit relays. When the government found out about the popularity of Tor they created their own exit nodes, that acted as honey traps. To fight this, use a TailsOS (or booted off a flash stick, DVD or SD card in a public wifi spot, like a coffee shop). That way even if the final node was a trap, it would only lead to your TailsOS profile, not your general one. Check so the public wifi spot you are using has no cameras around, so they will not be able to check camera footage of who used a laptop in that particular time frame. Don’t forget to log off when finished. Alternatively, use Tor to VPN.
Third
Often many programs, like torrents, will ignore Tor, even if you manually force them and just connect straight away, thus giving you away. The answer is to not use torrents with Tor. I REPEAT, NO FILE SHARING ON TOR.
There are of course other various vulnerabilities out there. And as a reminder, Silk Road, a large black market was cracked in the past.
COMBINING TOR WITH A VPN
Tor is good on its own but even better when combined with a VPN. There are 2 methods : Tor to VPN, VPN to Tor. Both have their weaknesses. First one allows ISPs to see you use Tor, the second does not protect from malicious end relays . VPN to Tor masks your Tor usage, Tor to VPN protects from malicious exit nodes.
I have thought of using VPN to Tor to VPN, which should theoretically accomplish both. For VPN to Tor use a secure VPN provider and add non-Tor traffic to mask usage. For Tor to VPN, pay with anonymized bitcoins and never connect to your VPN without connecting to Tor first.
VPN to Tor: The Harvard bomb hoaxer was de-anonymized because he was the only one in college using Tor. If he went through a VPN first, he would have been harder to track (assuming his VPN provider did not keep logs).
Tor to VPN: Protects from malicious exit nodes, on the other hand. TailsOS with public wifi accomplishes the same. Of course, either is better than nothing. Which you choose depends on your needs. The only two providers that offer Tor to VPN are AirVPN (based in Italy, so part of 14 eyes, but not the 5 eyes) and BolihVPN.
IF YOU DON’T WANT TO USE TOR
While using Tor is advisable, for casual usage you can set Firefox to be very secure with the help of add-ons and custom settings. Here is a guide.
WEBSITES THAT BAN VPN AND TOR
Certain websites ban Tor (e.g. Imgur). Use an alternative then (e.g. Anonmgur). Otherwise use VPN to Tor. There are VPN providers that cycle IPs, so that helps with VPN IP range bans.
TAILSOS
Windows is not very safe. There have been rumors of NSA backdoors on Windows devices. Supposedly NSA can store almost everything you do online (including Facebook, popular mail providers, and possibly things offline).
There are some good alternatives out there, TailsOs being one of them. TailOS is an operating system specifically designed for security and is Linux based. It can be ran off a USB stick. For those extra paranoid, use Tor in a public space on a laptop with TailsOS loaded of a flash drive.
Of course TailsOS is not very suitable for day to day needs, so use it for shitlord purposes. For your day to day purposes you might have to use Windows, but for the love of god, DO NOT use Windows 10, it is absolutely awful for security.
I prefer Windows 7. If you are more advanced, you can use alternative platforms like Debian or some distro of Linux or whatever. Just beware, many programs for Windows do not have alternatives on Linux based systems. If you are a casual, moving to another platform can be difficult. And if you really are a nerd, then you can look into some exotic setup like Qubes + Whonix or whatever other myriad of OS and Virtual Machines there are around.
4. Other darknet browsers

I2P network: While Tor is designed to anonymously browse the normal web and onion sites, I2P is a web of it’s own. Preferably to be browsed through Tor. It allows (slow) torrenting and great for messaging, IRC, file sharing, secret websites (.i2p)
Freenet – Freenet is a peer-to-peer platform for censorship-resistant communication.
5. Look into bitcoin and online currency
Bitcoin is virtual currency that has taken the world by storm in recent years. There are other online currencies competing against it, but Bitcoin is the most established online currency. It is the default virtual currency. Bitcoin is not for daily usage, rather online purposes. There are VPN services that accept payment with bitcoin. There are even services that will store physical gold in exchange for bitcoin.
Truly a financial revolution. Unfortunately, it’s also a big headache for tax services. Bitcoin is also infamous for being used to purchase illegal stuff on the internet black market. But you wouldn’t use it for that, would you?
To start using bitcoins just register a bitcoin wallet and you are good to go.
HOW TO INCREASE BITCOIN ANONYMITY
Bitcoins are not anonymous by default. They must be washed and anonymized. Buying through Tor + Coin mixing + anonymity patched bitcoin client. Over the counter (OTC) bitcoins are an option as well.
6. Use proper password protection
Never use the same password twice. Try to make it long and contain both characters and numerals, etc. Hint : use L33t, P@ssVV0r|)333. If you can, add non English characters even better, PåSsWøRд0, but you can’t always do it.
If you are unsure, use a safe password generator, such as Master Password To manage passwords use a password manager, such as KeePassX.
7. Use proper mail protection

Use throwaway email to register in most places. Never use your public e-mail to register anywhere controversial like Neomasculintiy affiliated websites.
SAFE MAIL PROVIDERS
For general mail needs, use a mail provider that is focused on security. I found two outside 14 eyes, in Switzerland: ProtonMail (free), NeoMailBox (50$/year, custom domain option ex : [email protected], [email protected])
Remember to still use personal safety measures, like additional encryption. Never trust 2nd parties with your protection completely.
BECOME AN EMAIL PROVIDER YOURSELF
Another interesting move is to become a provider yourself, in essence create your personal Gmail by turning your PC into a mail server. To do this, use Mail-in-a-box. They have good guide on their site https://mailinabox.email/.
USE A SAFE MAIL CLIENT
A mail client is a program that allows you to manage mail from the cloud by saving it locally, by connecting to the email host, such as Gmail. The default mail client in Windows is Microsoft Outlook (which sucks). I will focus on my preffered mail client setup.
1) Download Thunderbird
2) Install the Enigmail add-on, to allow encryption
3) Install the TorBirdy add-on, to make Thunderbird run through Tor
BEWARE THE LAW
Beware of a law that allows government officials to read any mail hosted online older than 6 months without a warrant. Use an external email client like Thunderbird or Enigmail, download your emails and store them locally. Never leave them on the server.
EMAIL ALTERNATIVES
Look into email alternatives such as : Bitmessage, I2P-Bote, Retroshare
8. Use encryption for messaging

Encryption is the process of making a message unreadable to third parties. Some programs do it for you, manually you can use a program like GPG4win or similar which uses PGP encryption.
The way it works is this :
1) You create your public key.
2) You digitally sign the information with your private key, so when the other side verifies it with their own public key, they can confirm that it is indeed YOUR public key. (WebOfTrust)
3) When someone wants to write to you he encrypts it using the public key you provided, or the other way around.
4) You then use your PRIVATE key to decrypt the message he sent you.
Here is a tutorial:
youtube
MOBILE ENCRYPTION
There are encryption possibilities for your phone as well. First, set encryption on your Android device. Second, use an app called Signal
9. Scrub EXIF data of photos you post online

When you take a photo with a particular device, often it registers what device you used to take the photo, when and where it was taken. To avoid this problem, before posting online use an EXIF scrubber. It is a piece of software that deletes all information that might incriminate you.
Some examples are BatchPurifier Lite and Exif Pilot. Also, careful with what photos you post of course, nothing that could indirectly lead to you.
10. Torrent and stream safely

Torrenting can be useful for file transferring. If you plan to torrent anything or share something with friends, look into safer peer to peer torrenting. P2P is good for small files. Generic torrent services are good for larger files.
One advice I have is avoid torrent programs known for their untrustworthiness, such as BitVomit (BitComet) and uTorrent (closed source + adBloat). qBit, Deluge, Tribler (this one’s interesting) are good options (open source and lightweight).
Beware of laws in certain countries that forbid downloading stuff online. Germany is particularly infamous for this. There are ways to combat this issues through VPNs. But DO NOT USE TOR, I REPEAT, DO NOT USE TOR FOR FILE SHARING. For even more secure anonymous file sharing look into I2P (beware avg speed: 30 kbs per sec)
As for streaming, Popcorn Time and other analogous services (such as PornTime) are used to stream new movies (and porn) respectively. They are based on BitTorrent technology. They are relatively safe services, as long as you use a VPN.
11. Encrypt the files on your PC
Use VeraCript, a piece of software designed to encrypt disk partitions or whole USB drives. It is the successor of TrueCrypt (which stopped development after feds asked them to include vulnerabilities).
https://www.youtube.com/watch?v=_fGUJ6AgOjQ
HIDE FILES IN IMAGES
Also, another interesting technique is to hide text, videos and other stuff in pictures, it’s called Steganography.
12. Look into this promising new technology for your online needs
The 3 pieces of software I am about to recommend are TOX , RetroShare and diaspora.
TOX is a Skype clone with focus on privacy.
Retroshare is a private network service. You can use it for private mailing and other purposes.
diaspora is a social network designed for privacy and decentralization https://diasporafoundation.org/
Another interesting possibility for ROK people is to use a .onion or .i2p domain or freenet for a sort of “secret” webpage, unavailable to casuals out there.
To summarize
I think this advice will benefit the ROK community for protecting their anonymity and using secret backup channels for future purposes. Here is a quick cheat sheet:
Casuals: VPN paid with shuffled bitcoin + VPNcheck Pro, Signal on Android, Firefox with add-ons for casual use, Tor for shitlordery, Encrypted mail and hard disk, password manager, ProtonMail for daily use, throwaway mail—everything else, Thunderbird with add-ons, EXIF scrubber. Download email on PC then delete off server.
Advanced: Same as above + Tor combined with VPN, I2P and Freenet, (TBitmessage I2P-Bote Retroshare) instead of mail, becoming mail provider, diaspora*
Super advanced: Same as above + Multiple VPNs, Using Tor off of TailsOS in a public space where cameras cannot film you. Alternative OS and Virtual machines. Secure you router.
Here’s a good collection of security resources.
Always remember, there is no way to remain completely anonymous, just ways to make it harder to be detected.
Read More: 5 Ways To Improve Your Online Game
1 note
·
View note
Text
Seriously, is playing Video Games as BAD as mom says?
If you grew up playing video games like I did … you’ve probably heard lots of conflicting information about games from your parents and people. Some say too much gaming will ruin your vision or rot your brain … While others claim it improves your hand-eye coordination, response time and can even make you smarter so what exactly does gaming do to our brain and body?
When I was a kid, I was obsessed with video games.
I would stay awake for more than 48h till I wake up with keyboard marks on my face, red eyes and my body is so tired to even get up and drink some water... trust me I am not exaggerating. After all that I would go to sleep only to dream about the perfect headshot with that “AWM”.
But there were physical effects, too. My thumbs turned into machines, quick and precise. During especially difficult levels of play, my palms would sweat. My heart would race. I’d have knots in my stomach from anxiety. It was the same feeling I’d sometimes get from watching scary movies or suspenseful TV shows.
These days the gaming industry is booming and becoming more like sports with fans, medals and everything! and thanks to smartphones and free games like fortnight and League of Legends … Gamers are increasing more than ever before. So, given that we can play virtually anywhere at any time How is all this gaming changing us physically?
Scientists are discovering that playing video games can change the way we act, think, and feel. Whether these changes are good or bad has become a subject of intense debate.
Action games like counter-strike, overwatch and PUBG are some of the most popular with gamers these days and probably you’ve heard once or twice your grandmother says “these games will make you more violent from all the blood you see!”
Whenever a wave of teenage violence strikes, movies, TV, or video games often take the heat. Some adults assume that movies, TV, and video games are a bad influence on kids, and they blame these media for causing various problems.
But media don’t necessarily cause violence, says James Gee. Gee is an education professor at the University of Wisconsin, Madison.
“You get a group of teenage boys who shoot up a school—of course they’ve played video games,” Gee says. “Everyone does. It’s like blaming food because we have obese people.”
Video games are innocent of most of the charges against them, Gee says…
Well, based on 15 years’ worth of study researchers have found that action games biggest positive effects were on perception: how our senses interpret external stimuli like sights and sounds, spatial cognition: which helps you orient yourself in navigating 3d environments and top-down attention: the ability to focus on one object while ignoring distractions.
A good video game is challenging, entertaining, and complicated. It usually takes 50 to 60 hours of intense concentration to finish one. Even kids who can’t sit still in school can spend hours trying to solve a video or computer game.
“Kids diagnosed with ADHD because they can’t pay attention will play games for 9 straight hours on the computer”, Gee says. “The game focuses attention in a way that school doesn’t.”
The captivating power of video games might lie in their interactive nature. Players don’t just sit and watch. They get to participate in the action and solve problems. Some games even allow players to make changes in the game, allowing new possibilities.
Different games have different impacts on the brain and that has to do with what you’re asked to do … just like food it doesn’t have the same vitamins after all, does it?
“Failure is key to success”.
Ask anyone who has ever had any success in anything if they have ever failed. You will get a big clear “Yes!” because everyone has failed at something. Most people probably know about Thomas Edison and his spectacular failure rate but here are a few other examples:
J.K. Rowling -known for writing the Harry Potter fantasy series- was rejected by 12 publishers
Einstein didn’t speak until he was 4 and didn’t read until he was 7
Van Gogh only sold 1 painting in his lifetime
Michael Jordan was cut from his high school basketball team.
In games you get 1000 lives and more! We don’t stop playing till the game says “Game Over” but then we click on “New Game” or new try.
“Gaming could be good for pain relief”.
a 2012 literature review published in the American Journal of Preventive Medicine found that in the 38 studies examined, video games improved the health outcomes of 195 patients on every front, including psychological and physical therapy.
Plus, in 2010, scientists presented research at the American Pain Society's conference, which found evidence that playing video games, especially virtual reality games, are effective at reducing anxiety or pain caused by chronic illness or medical procedures.
"The focus is drawn to the game not the pain or the medical procedure, while the virtual reality experience engages visual and other senses," said Jeffrey Gold from the University of Southern California.
“Better Decision Making”.
Shawn Green from the University of Rochester wanted to see how games affect our ability to make decisions.
The study had a group of young adults with no gaming experience play an action game for 50 hours.
A second group of the same age played a slow-paced strategy game instead.
After the study, Green had nothing but good things to say:
“Action video games are fast-paced, and there are peripheral images and events popping up, and disappearing. These video games are teaching people to become better at taking sensory data in, and translating it into correct decisions.”
A colleague of his even went on to say that shooters can change the brain by dramatically enhancing many of our low-level perceptual functions. Definitely good news for all the Halo and Call of Duty fans out there.
“Games Can Help (Not Hurt!) Your Eyesight”.
Who grew up without ever hearing their parents say “you’re going to go blind watching that screen all day”.
For a while, it did seem like they had a point since we tend to blink much less frequently while playing a game.
This can cause serious problems like eyestrain and dry eye syndrome.
Another team of researchers from the University of Rochester sought to prove if games really worsen our vision.
The 2009 study involved having a group of experienced first-person shooter gamers plays Call of Duty and Unreal Tournament 2004 while more casual gamers played slow games like The Sims 2.
After testing, those who played the first-person shooters showed signs of having a better vision than the others.
Daphne Bavelier, the leader of the study, discovered that playing action games improves an ability called contrast sensitivity function.
This ability helps us discern between changes in shades of gray against a colored backdrop, which is very beneficial while driving at night.
“Video Games May Help Treat Depression”.
A few years back researchers in New Zealand sought to find out if video games can be used to treat mental disorders like depression.
This was done with SPARX, a game specifically designed to provide therapy to teenagers in a way that’s more active and enjoyable than regular counseling.
Over 168 teens with an average age of 15 participated, with all of them having shown previous signs of depression.
While half of the group received traditional counseling, the other group got to play SPARX.
The game involves creating avatars to rid the virtual world of enemies representing gloomy, negative thoughts.
Every stage also introduced general facts about depression, including ways to relax and deal with negative emotions.
Here’s their conclusion after discovering that SPARX players did better at recovering from depression than the other group:
“SPARX is a potential alternative to usual care for adolescents presenting with depressive symptoms in primary care settings and could be used to address some of the unmet demand for treatment.”
“Games has a purpose, meaning and can actually help!”.
Darfur is Dying is a video game made in 2006 by Students at the University of Southern California that provides a window into the experience of the 2.5 million refugees in the Darfur region of Sudan. It is designed to raise awareness of the genocide taking place in Darfur and empower college students to help stop the crisis. The game was developed in cooperation with humanitarian aid workers with extensive experience in Darfur.
First, you choose a Darfurian character to represent your camp. Next, you are instructed to go out and get water, which is the goal of the game. You are warned about the implications of some of the game's rules,
In the game, the user chooses a Darfurian character out of 7: a guy at the age of 30, a 26 years old woman, 5 kids from 10 to 14 years old from both genders to find some water... but watch out hide yourself from the Janjaweed militia! Upon success or failure, they learn that their chances of succeeding were predetermined by their gender and age if they are still young the militia takes them, if they are adults they get killed or raped. The navigation system in the game enables the player to learn about the situation in Darfur, get involved with stopping the crisis.
As we saw no one plays a game and doesn’t gain something ... either you get a positive impact or a null impact. We haven’t seen any area that has been damaged where there is worse performance.
Playing video games can be very high speed, can create a lot of chaos, create a lot of multiple environments where you have to make decisions, and all of these are forming skills in brain so … No, I think games really help improve our cognition and awareness training our brains making us better Human beings.
But of course, too much of anything is going to be bad after all.
You will get more learning gained from smaller sessions spread out over time than one BIG block.
When it comes to my own experience, I’ve played games for more than 13 years never suffered any gaming related injuries. While may I never know if gaming helped my brain, I do know it didn’t destroy it … so take that mom!
— Moaaz Akram
2 notes
·
View notes
Video
How to hide drive in any computer wihtout affecting any data✔
#hide drive#how to hide drive#how to make drive invisble#how to hide drive in pc#hide drive in any pc#how to hide drive in any computer without affecting any data
0 notes
Text
Download HDD Regenerator crack (keygen) latest version G68B!

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 Thus, it can now recover all lost data. Sometimes laptop hard drives have sectors that cannot be written to. HDD Regenerator for Windows 10 This happens on hard disks due to physical damage to the disk surface. So this is often a must-have application for all computers. HDD Regenerator for Windows 10 can scan for bad sectors and errors. It can be physically scanned. Thus, it is an easy application and runs using the smallest system resource. The interface of this application gives you quick access to all or any of the features. During error scanning, it will provide notifications for bad sectors and may give you options to recover information about bad sectors. HDD Regenerator Crack The best and professional damaged hard disk software full version free download. Regenerator Pro software allows us to remove bad sector from our hard drive or USB hard drive. In addition, HDD Regenerator Full Disk speed and data transfer speed are slow and mean that the hard disk drive is full of incorrect sector, which causes the hard disk to crash. Therefore, the result is that you will lose everything that is more vital to you, which is saved on your hard drive. Thus, this also checks the disk in real time and provides error notification at an equivalent time, it is impossible to recover knowledge from the world where there is a defective sector. But the HDD Regenerator keygen has the power to read information from bad sectors; then this application. HDD Regenerator How can I regenerate a hard drive in the bad sector? If you want attractive and simple HDD tools, you will need to inspect Ultimate Defrag Download the latest version for free. As a result, corrupt and illegible information is restored without impact on existing data. It does not hide bad sectors. The developers of this plan have found a precise algorithm for low and high signal sequences. Also inspect your Sentinel Professional hard drive. Not even the low level format can handle this task!. These are mostly questions that come to mind once you see that the hard drive is going too slow and that the data is reading and writing slowly. Hard drive software to restore harmful sectors and tons of problems, such as removing the wrong area and generating new space. This can repair bad physical sectors magnetic errors on a wooden drive surface. This product or software ignores the file system, scans the diskHDD Regenerator Crack You will try to determine certain types of software that will increase or improve your complicated disk health. This technology is hardware independent, supports many types of hard drives, and repairs damage that even low-level formatting cannot repair. As a result, previously unread information will be restored. Due to the way the repair is done, the information on the hard drive will not be affected! The hard drive is an integral part of every computer. It stores all your information. One of the most common defects in hard disks is the defective sectors on the surface of the disk. Wrong sectors are a part of the disk surface that contains information that cannot be read, but is often needed. Due to bad sectors, you may have difficulty reading and copying data from the disk, your operating system may become unstable, and your computer may not be able to start up completely. When a hard disk is damaged by bad sectors, the disk not only becomes unusable, but you also risk losing the information stored on it. HDD Regenerator can repair damaged hard drives without damaging or altering existing data. As a result, previously inaccessible and inaccessible information is restored. Therefore, it provides the power to start regenerating from DOS; By doing this, you will also recover data. More features of HDD Regenerator Key Free Quickly detect disk drive problems Ability to detect harmful physical sectors on a hard surface of the disk Ability to repair bad physical sectors magnetic errors on a frozen disk surface No data loss in any way! It has a quick scan mode that can find a mistake. Thus, it can check the status of the hard disk in real time and it is excellently erased. There are many reasons why the method prevents, but it is the power to restart the process. So it is the power to detect bad physical sectors on the disk drive disk surface. This application is easy to use and provides access to all or any of the features of the device. Pre-scan mode useful for quickly determining the location of bad sectors if a hard drive has a considerable. It saves some time. Bad hard drives are scanned this way even faster than good hard drives! Mac user selects Mac.
1 note
·
View note
Text
Download HDD Regenerator crack (serial key) latest version HIK1!

💾 ►►► DOWNLOAD FILE 🔥🔥🔥 Thus, it can now recover all lost data. Sometimes laptop hard drives have sectors that cannot be written to. HDD Regenerator for Windows 10 This happens on hard disks due to physical damage to the disk surface. So this is often a must-have application for all computers. HDD Regenerator for Windows 10 can scan for bad sectors and errors. It can be physically scanned. Thus, it is an easy application and runs using the smallest system resource. The interface of this application gives you quick access to all or any of the features. During error scanning, it will provide notifications for bad sectors and may give you options to recover information about bad sectors. HDD Regenerator Crack The best and professional damaged hard disk software full version free download. Regenerator Pro software allows us to remove bad sector from our hard drive or USB hard drive. In addition, HDD Regenerator Full Disk speed and data transfer speed are slow and mean that the hard disk drive is full of incorrect sector, which causes the hard disk to crash. Therefore, the result is that you will lose everything that is more vital to you, which is saved on your hard drive. Thus, this also checks the disk in real time and provides error notification at an equivalent time, it is impossible to recover knowledge from the world where there is a defective sector. But the HDD Regenerator keygen has the power to read information from bad sectors; then this application. HDD Regenerator How can I regenerate a hard drive in the bad sector? If you want attractive and simple HDD tools, you will need to inspect Ultimate Defrag Download the latest version for free. As a result, corrupt and illegible information is restored without impact on existing data. It does not hide bad sectors. The developers of this plan have found a precise algorithm for low and high signal sequences. Also inspect your Sentinel Professional hard drive. Not even the low level format can handle this task!. These are mostly questions that come to mind once you see that the hard drive is going too slow and that the data is reading and writing slowly. Hard drive software to restore harmful sectors and tons of problems, such as removing the wrong area and generating new space. This can repair bad physical sectors magnetic errors on a wooden drive surface. This product or software ignores the file system, scans the diskHDD Regenerator Crack You will try to determine certain types of software that will increase or improve your complicated disk health. This technology is hardware independent, supports many types of hard drives, and repairs damage that even low-level formatting cannot repair. As a result, previously unread information will be restored. Due to the way the repair is done, the information on the hard drive will not be affected! The hard drive is an integral part of every computer. It stores all your information. One of the most common defects in hard disks is the defective sectors on the surface of the disk. Wrong sectors are a part of the disk surface that contains information that cannot be read, but is often needed. Due to bad sectors, you may have difficulty reading and copying data from the disk, your operating system may become unstable, and your computer may not be able to start up completely. When a hard disk is damaged by bad sectors, the disk not only becomes unusable, but you also risk losing the information stored on it. HDD Regenerator can repair damaged hard drives without damaging or altering existing data. As a result, previously inaccessible and inaccessible information is restored. Therefore, it provides the power to start regenerating from DOS; By doing this, you will also recover data. More features of HDD Regenerator Key Free Quickly detect disk drive problems Ability to detect harmful physical sectors on a hard surface of the disk Ability to repair bad physical sectors magnetic errors on a frozen disk surface No data loss in any way! It has a quick scan mode that can find a mistake. Thus, it can check the status of the hard disk in real time and it is excellently erased. There are many reasons why the method prevents, but it is the power to restart the process. So it is the power to detect bad physical sectors on the disk drive disk surface. This application is easy to use and provides access to all or any of the features of the device. Pre-scan mode useful for quickly determining the location of bad sectors if a hard drive has a considerable. It saves some time. Bad hard drives are scanned this way even faster than good hard drives! Mac user selects Mac.
1 note
·
View note
Text
Spybot For Mac

Spybot For Macbook Air
Spybot Mac Os X Download
Spybot For Mac
Spybot For Mac Os
Spybot Mac Gratuit
Spybot – Search & Destroy Technician Edition provides an extended set of tools for technicians who want to have a deeper look into all parts of the operating system. To analyze problems, check configurations, define own rules and more. Or just to maintain computers within workgroups or whole companies.
Download Spybot - Search & Destroy and enjoy it on your iPhone, iPad and iPod touch. Spybot News is now available as an official smartphone app! Regular news, images, dates. Your privacy and the security of your computer is important to us, see how we can help you! Our approved Spybot – Search & Destroy protects your computer against malware. Spybot Anti-Beacon helps to stop your data being sent out to third parties. The new Spybot Identity Monitor helps you to realize and take action when your personal information held by third parties was compromised. Spybot for mac free download - WinZip Mac, Avast Free Mac Security, AVG AntiVirus for Mac, and many more programs. Spybot +AV replaces the scan-only, spyware-only protection of the free Spybot with a full-scale antivirus that promises to scan for all kinds of malware on demand and in real time. It shares quite.
This is why …
… Spybot is different. Spybot uses a unique technique to find the spyware, adware and more unwanted software that threatens your privacy that others don’t find. And the +Antivirus Editions give you complete protection with the best available Antivirus solution already integrated.
So take advantage of the essential tools to keep control over your computer and find the version that suits your needs best.
Donate now!
Please donate to support our fight against spyware!
Features

Anti-Spyware
Spybot's Anti-Spyware protection uses our unique technology to find and remove all kinds of spyware, including adware, tracking software, keyloggers and other unpopular software. Your privacy is our ultimate goal!
Anti-Virus
To provide you with the best possible protection, we've included an award winning anti-virus engine. It's the engine of choice of the best rated anti-virus products on AV-Test and AV comparatives.
And on top of that most elaborate malware protection, you get our own specialized anti-spyware engine that covers the spyware grounds beyond!
Live Protection
Live Protection is Spybots form of real time protection. Live protection scans and monitors all newly created and running processes on your system. Malicious processes are blocked before they start to prevent infection on your system.
Anti-Beacon
Our anti-telemetry tool Anti-Beacon Plus is available to all users of the Spybot Professional and the commercial editions.
System Immunization
Immunization pro-actively protects your system against malware attacks by blocking access to sites known to contain malicious or unwanted software. It also blocks tracking cookies and browser plugins that are known to contain malware. Immunization supports many popular browsers, including Internet Explorer, Opera, Firefox and Chrome.
Startup Tools
Startup Tools allow you to manage what happens and what gets loaded at system startup. If you open this tool you will see a comprehensive set of tabs. Clicking on a tab will allow you to inspect and change the behaviour of what is loaded. This powerful tool should be used with caution as it allows you to make registry changes as well as other changes that effect your system.
It can be useful if you suspect changes may have been made without your knowledge.
Rootkit Scan
Rootkits use technologies to hide themselves and their actions from users and other system processes. The Rootkit Scan is a special scan that can locate these rootkits. This scan includes checks of the file system, the registry and some process related lists.
Automatic Signature Updates
Staying up to date with all malware signatures is essential for your security. All paid editions of Spybot will download new signatures multiple times per day - automatically and in the background.
Task Scheduling
If you have purchased Spybot you have the advantage of being able to automate tasks. Using the Schedule option in Advanced Tools → Settings Spybot can create a Windows Scheduler task to keep your Spybot up to date, immunized and run system scans regularly.
Protected Repair Environment
When you choose the Protected Repair Environment, a new Windows Desktop is opened and the Start Center runs in a way so that other software cannot interact with it. This prevents keyloggers and other malware taking over control of Spybot, using the same security desktop separation technology that the Windows Login screen and the User Account Control dialogs use.
System Registry Repair
Most registry cleaner software promises to speed up your system which is not really possible. These cleaners may also come with unwanted additions such as adware or spyware. Our System Registry Repair allows you to do some basic cleanup and repair in a number of categories where changes might positively affect user experience, for instance helping Windows find misplaced Help files. It can either delete or repair broken entries by offering you you the options, for example, of locating or searching for files that have been moved. In general, we recommend that you do not use Registry Cleaners, Optimizers or Defragmentation utilities unless you are an experienced user.
Priority Support
Beside the standard support options we at Safer-Networking Ltd. strive to support you in case of questions or problems. So if need help, do not hesitate to use our contact page!
Secure Shredder
The Secure Shredder is a tool to safely remove files from magnetic hard drives. It uses multiple passes to make sure the files cannot be recovered.
Script Editor
If you are familiar with a common programming language you might want to define some detection patterns yourself. Just to get rid of some unwanted files or any item you regard as malware. This is not too complex when using our OpenSBI syntax and Pascal. A simple script that you could implement using a simple .sbi file might look like this:
Command Line Tools
The system administrator may schedule tasks and use Command Line Parameters or even Command Line Tools to perform different tasks without user interaction. Powershell Scripts or Batch Files may help and the Windows scheduler can support special tasks as well.
Command Line Tools are available for:
File Scan
System Scan
Immunization
Cleaning
Updating
FileAlyzer
FileAlyzer is a tool to analyze files. It shows basic file content, a hex viewer, and a range of customized displays for interpreted file structures.
It also supports generation of OpenSBI advanced file parameters.
Start Center
The simple Start Center shows you the important information about the last scan, the immunization and update status. It helps you to stay safe with a minimum of clicks.
Spybot For Macbook Air
Spybot 2.8 Immunization
Immunization pro-actively protects your system against malware attacks by blocking access to sites known to contain malicious or unwanted software. It also blocks tracking cookies and browser plugins that are known to contain malware. Immunization supports many popular browsers, including Internet Explorer, Opera, Firefox and Chrome.
Reviews
Great. Excellent. Brilliant!
My Google Chrome browser was always triggering to unwanted page - Adcash and DoubleClick. Sometimes my browser triggering to porn sites. Other softwares fails to detect it, but Spybot Search & Destroy can do so through the scanning function. In the next review, Spybot Search & Destroy can improve this detection function in realtime protection. Thank you Spybot Search & Destroy version 2.4.40.
This is a great fully-featured security application…
Pros: Host File Protection, Browser Guards, Realtime Spyware and Malware Protection, Process Control, Deep System Scanning, and many others you normally wouldn’t find in a traditional security software suite.
Cons: The only con I can rightly say is that it consumes a lot of system resources and some of the scans can take a while, depending on the size of your system and the configurations of the scan you choose.
Summary: This is a robust security application that is an excellent supplement to existing security software and especially useful for those whom still use the Internet Explorer browser, because of the protections it offers, including that of the host file as well as a user’s homepage. Even if you don’t want to pay for the full version, the free version is still worth the download and is a formidable contender in the world of antimalware software.
It is essential in our computer
What do you like best?
can be downloaded for free in its free version, and its main task is to detect and remove corrupt files, suspicious or spyware robots, which can be harmful to our computer.
The design of this program is really simple, with practically four buttons, to do everything, but still, it has many options.
What most attracts the attention of the program, at least to me, is the possibility of configuring it in several languages.
What do you dislike?
They should add other skins.
Spybot Mac Os X Download
and it has a relatively high Ram Consumption [Note from Safer-Networking: this has been fixed in Spybot 2.7].
Recommendations to others considering the product
I recommend it because it is free and has a simple interface with intuitive options, it is effective, it removes malware, and it is always updated.
What business problems are you solving with the product? What benefits have you realized?
protection in the work stations in combination with other antivirus makes me feel more protective against computer intrusions and malicious advertising.
Download
Spybot 2.8
Get this to install on a 32 or 64 bit Windows system.
Why use the Technician’s Edition?
Spybot – Search & Destroy Technician Edition provides an extended set of tools for technicians who want to have a deeper look into all parts of the operating system. To analyze problems, check configurations, define own rules and more. Or just to maintain computers within workgroups or whole companies. Use the complete protection against malware and viruses including Live Protection on your own system and define tasks you want performed on other systems. Thus, the license also includes the use of a portable device on systems that you support, where it may not be permanently installed.
As with the Corporate Edition it uses two scan engines for different tasks like scanning for viruses and malware. It provides cleaning system startup and you may use some very special features.
Buy now!
How many business use copies do you need?
Features
Anti-Spyware
Spybot's Anti-Spyware protection uses our unique technology to find and remove all kinds of spyware, including adware, tracking software, keyloggers and other unpopular software. Your privacy is our ultimate goal!
Anti-Virus
To provide you with the best possible protection, we've included an award winning anti-virus engine. It's the engine of choice of the best rated anti-virus products on AV-Test and AV comparatives.
And on top of that most elaborate malware protection, you get our own specialized anti-spyware engine that covers the spyware grounds beyond!
Live Protection
Live Protection is Spybots form of real time protection. Live protection scans and monitors all newly created and running processes on your system. Malicious processes are blocked before they start to prevent infection on your system.
Anti-Beacon
Our anti-telemetry tool Anti-Beacon Plus is available to all users of the Spybot Professional and the commercial editions.
System Immunization
Immunization pro-actively protects your system against malware attacks by blocking access to sites known to contain malicious or unwanted software. It also blocks tracking cookies and browser plugins that are known to contain malware. Immunization supports many popular browsers, including Internet Explorer, Opera, Firefox and Chrome.
Startup Tools
Startup Tools allow you to manage what happens and what gets loaded at system startup. If you open this tool you will see a comprehensive set of tabs. Clicking on a tab will allow you to inspect and change the behaviour of what is loaded. This powerful tool should be used with caution as it allows you to make registry changes as well as other changes that effect your system.
It can be useful if you suspect changes may have been made without your knowledge.
Rootkit Scan
Rootkits use technologies to hide themselves and their actions from users and other system processes. The Rootkit Scan is a special scan that can locate these rootkits. This scan includes checks of the file system, the registry and some process related lists.
Automatic Signature Updates
Staying up to date with all malware signatures is essential for your security. All paid editions of Spybot will download new signatures multiple times per day - automatically and in the background.
Task Scheduling
If you have purchased Spybot you have the advantage of being able to automate tasks. Using the Schedule option in Advanced Tools → Settings Spybot can create a Windows Scheduler task to keep your Spybot up to date, immunized and run system scans regularly.
Protected Repair Environment
When you choose the Protected Repair Environment, a new Windows Desktop is opened and the Start Center runs in a way so that other software cannot interact with it. This prevents keyloggers and other malware taking over control of Spybot, using the same security desktop separation technology that the Windows Login screen and the User Account Control dialogs use.
System Registry Repair
Most registry cleaner software promises to speed up your system which is not really possible. These cleaners may also come with unwanted additions such as adware or spyware. Our System Registry Repair allows you to do some basic cleanup and repair in a number of categories where changes might positively affect user experience, for instance helping Windows find misplaced Help files. It can either delete or repair broken entries by offering you you the options, for example, of locating or searching for files that have been moved. In general, we recommend that you do not use Registry Cleaners, Optimizers or Defragmentation utilities unless you are an experienced user.
Priority Support
Beside the standard support options we at Safer-Networking Ltd. strive to support you in case of questions or problems. So if need help, do not hesitate to use our contact page!
Secure Shredder
The Secure Shredder is a tool to safely remove files from magnetic hard drives. It uses multiple passes to make sure the files cannot be recovered.
Script Editor
If you are familiar with a common programming language you might want to define some detection patterns yourself. Just to get rid of some unwanted files or any item you regard as malware. This is not too complex when using our OpenSBI syntax and Pascal. A simple script that you could implement using a simple .sbi file might look like this:
Command Line Tools
The system administrator may schedule tasks and use Command Line Parameters or even Command Line Tools to perform different tasks without user interaction. Powershell Scripts or Batch Files may help and the Windows scheduler can support special tasks as well.
Command Line Tools are available for:
File Scan
System Scan
Immunization
Cleaning
Updating
FileAlyzer
FileAlyzer is a tool to analyze files. It shows basic file content, a hex viewer, and a range of customized displays for interpreted file structures.
https://distinguishedalpacatheorist.tumblr.com/post/642312771633119232/topogun-for-mac. It also supports generation of OpenSBI advanced file parameters.
Protected Repair Environment
When you choose the Protected Repair Environment, a new Windows Desktop is opened and the Start Center runs in a way so that other software cannot interact with it. This prevents keyloggers and other malware taking over control of Spybot, using the same security desktop separation technology that the Windows Login screen and the User Account Control dialogs use.
Spybot For Mac
System Registry Repair
Most registry cleaner software promises to speed up your system which is not really possible. These cleaners may also come with unwanted additions such as adware or spyware. Our System Registry Repair allows you to do some basic cleanup and repair in a number of categories where changes might positively affect user experience, for instance helping Windows find misplaced Help files. It can either delete or repair broken entries by offering you you the options, for example, of locating or searching for files that have been moved. In general, we recommend that you do not use Registry Cleaners, Optimizers or Defragmentation utilities unless you are an experienced user.
Download mamp for mac. MAMP is commonly used with WordPress and Drupal for setting up a local web development environment. The most key element of using MAMP is that user can develop web applications offline and then easily transfer it later to the web host provider.
Script Editor
Spybot For Mac Os
If you are familiar with a common programming language you might want to define some detection patterns yourself. Just to get rid of some unwanted files or any item you regard as malware. This is not too complex when using our OpenSBI syntax and Pascal. A simple script that you could implement using a simple .sbi file might look like this:
Reviews
Leigh Rach
Spybot Mac Gratuit
This to me looks like the best antimalware / antivirus on the market. will purchase soon. A must for every investor. Been using the free version for a very long time
FossHub
Spybot Search and Destroy (Free Edition) is a free security software, an excellent antispyware, anti-adware removal tool. It will detect and remove most of these threats: Adware files, Trojans, Dialers, PUPs, Browser Hijackers (unwanted toolbars), Keyloggers, Rootkits and other malware or junkware files can infect your computer. It will also allow you to fix the Windows® Registry inconsistencies, to be more specific - those related to malicious applications that you are installing and adware.
Several years ago was a revolution and today is on the same level
Simple but revolutionary software that is a pleasure to work with. After installation 1st thing to do is to immunize a PC, only after that you can go with all other interesting options.

0 notes
Text
How does the United States use drones to follow and care for livestock?

Cows seem unfazed by the approach of drones, but research in this regard continues
For many ranchers in the U.S. State of Kentucky, 5 p.m. is not the end of the working day, but the beginning of another job. But providing feed, checking for water in reservoirs, locating the herd, and assessing the health of each cow are mainly difficult tasks, and become more difficult after sunset, and sick or newly born cows make it more complicated because they usually tend to drift and hide in secluded places. Therefore, it is time to hire the services of drones. A team of researchers at the University of Kentucky is conducting a test to see the feasibility of using drones and how useful they are for small herds of cattle. "The idea is to make it easier for ranchers to do their second job, which provides them with additional income, by automating part of the tasks and helping to monitor their livestock on the pasture without having to be there all the time,"says Jesse Hogg, a professor of Mechanical Engineering at the University of Kentucky. Livestock farming is the "most important agricultural industry" in the United States, and its participation in the country's economy is 6 66 billion, according to the US Department of Agriculture. But it faces challenges due to climate change, labour shortages and land development and construction. However, the use of smart technology that makes livestock farming more efficient can contribute to overcoming many of these difficulties.
The ability to monitor pastures and locate livestock accurately and quickly, and to ensure their health and safety, can save a lot of time for busy ranchers, which has important economic implications. Every year, more than 2.5 million cows are spent in the United States for health reasons, costing the livestock industry about دولار 1.5 billion. Sick livestock also eat and move less, and this hinders the growth of young, affects their ability to reproduce, and reduces their value over time.
Hogg and his team received a three-year grant of approximately 9 900,000 from the U.S. Department of Agriculture's National Institute for food and agriculture in February 2018 to pursue their research on the drone project. It is hoped that these multidisciplinary efforts will solve many of the problems experienced by livestock breeders, such as patrolling pastures to locate cattle, and monitoring them healthily by following up on certain indicators such as weight or signs of diseases such as pink eye.
For this to be possible, the team has to find a way to identify and track specific cows on their own, which is why Hogg is considering a new technique to allow facial recognition of cows. The team is testing computer algorithms to make this idea work: current facial recognition technology is designed to identify the faces of humans, not cows. While certain features in a cow's face can serve as their own imprint, something as simple as contamination of the face with some dirt can impede the efficiency of the program.
Says Hugo: "you will catch a group of UAVs many images of cattle, and from different angles in batch, we can compile the images to obtain three-dimensional model allows to estimate the size of the cow and its weight, and total weight gain or loss. The planes also capture videos to monitor cows ' activity levels."
Ear tags (rings placed in the ears of some cattle) cannot be relied upon, as they can fall off, but the team considers them as a backup. The other option is to identify each cow by electromagnetic waves, but it is an expensive solution and may require drones to approach the animals beyond the permitted distance. Current regulations on the operation of these aircraft require that the person operating the aircraft be able to see the aircraft's routing lines, but the technology being worked on by the University of Kentucky team will allow these aircraft to operate independently, flying one observation aircraft over the field, identifying which of the existing objects are cows, and then transferring their positions to a number of "working"aircraft.
These "working" aircraft are equipped with cameras that collect images and data as they fly. The plan is for planes to analyze the information they collect, and send alerts directly to cow breeders when they find something that warrants intervention, such as the discovery of a sick cow or a crumbling fence.
To ensure that this system is safe for livestock (strange scenes or unusual noises can cause cows to become stressed and distract from grazing), researchers study the animals ' physiological and behavioral responses to the presence of drones by testing different flight patterns and altitudes within the University's 1,484-acre (6-square-kilometer) farm. The goal is to capture images of the highest quality without disturbing the livestock, so the team uses heart rate monitors and GPS-based collars to measure the animals ' responses to those aircraft depending on their location.
Michael Sama, a professor of Biological Systems Engineering at the University of Kentucky, describes the results of the tests as "highly promising." "We can get closer than I expected, we can be 20 or 30 feet away without it affecting the cows in any way,"he adds. Over time, the animals also seem to be acclimating to the presence of aircraft flying at these altitudes, but when the planes fall below 8 to 12 feet, they force the cows to move, which can be used to collect and drive them, another aspect the team has begun to study.
Researchers need in order to accomplish this ambitious work to a lot of data that is difficult to collect them. "You can't go online and ask to search for 'a million images of cows', so we have to create this data set,"says Sama. To create this illustrated guide, the researchers collected images of the faces of several cows, and installed dozens of cameras on a university farm that can capture up to 100 images of each cow passing by."We can take pictures of livestock from all directions at once,"explains Hogg. "It helps us Program the algorithm that will reconstruct a three-dimensional model of the cow from a relatively few image set,"he adds.
0 notes
Text
New Post has been published on Strange Hoot - How To’s, Reviews, Comparisons, Top 10s, & Tech Guide
New Post has been published on https://strangehoot.com/how-to-protect-mac-from-malware-viruses/
How to Protect Mac from Malware & Viruses
“To protect Mac from Malware” is a security measure provided by Apple with the system preferences settings. A Mac or an iMac is an expensive system. Once your Mac gets affected with malware, there are chances of virus damaging the hardware of the Macbook/iMac. This is an expensive damage if your Mac is out of warranty and you need to get it repaired by spending a good amount of money.
Mac Protection
To protect Mac from Malware or any virus, you need to take the following precautions.
Make sure your OS related security settings are enabled.
Encryption settings – Set the encryption to Full Disk. There is an option to enable it. This protects data theft from your Mac.
Protect your search results from being public.
Disable Spotlight search from the general settings. Spotlight option searches the content from the internet and gets back with the results that are exposed externally also.
Lock your computer when in idle state
When you are away from your system, leave it password protected. If anyone tries to access your system, it will ask for a password to get into the system. Select the Lock Screen option from the Desktop and Screen Saver settings.
Update your Mac when there is a release of new update
Keeping your Mac up-to-date with the latest version reduces the chances of malware attacks. Mac has a feature, Software Update that allows you to update your Mac with all new security updates available in the new version.
Disable Location Services to share with other apps
One of the security measures you can take is to turn off the location sharing service to hide your location from third-party apps. You will find this option in the Security and Privacy settings of System Preferences.
Take regular backups (of your Mac data)
Use Mac’s Time Machine tool to take backup on the external drive.
Choose the external disk, encrypt backups and press Use disk. This enables you to set a password for accessing backups.
Install Mac Antivirus and Security tool
To protect Mac from malware, install free antivirus tools that scans your mac and cleans up the malware. Intego and Comodo are two free antivirus software that detects and quarantines infected files. It also provides firewall protection. Both tools are easy to use on a Mac.
Use VPN to protect your Mac
Use NordVPN that saves your IP address and DNS from being attacked. It uses the AES 256-bit encryption standard to secure your Mac.
Do not share illegal file(s)
Your email client detects if you have received suspicious file(s) in your email. Please do not share or download or open the files and move to trash. This will help protect Mac from being infected.
Turn off Automatic Login
Always do manual login to access your Mac. If the password is not set, there are chances that it is being accessed by anyone who is near your Mac or anyone who has stolen your Mac. Manual login will allow your Mac to be protected from data theft.
Create a non-administrator account with restricted rights
Create an additional account without administrator privileges. The account will be restricted from changing security settings or installing any new software without admin rights. As a result, it is safe from being exposed to the outside world.
All of the above are precautionary measures taken to prevent your Mac from being infected. The next section is the scenario of your Mac being caught with malware and you want to remove Malware and clean your system.
Steps to remove malware
Follow the steps below to remove malware from your infected Mac system.
Disconnect the Mac system from the Internet. To do so:
Turn off Wi-fi and you are disconnected from the internet.
Shut down and start your Mac in Safe Mode.
To switch to the Safe mode, press SHIFT and hold it till you see the Apple icon on the screen.
Leave holding the SHIFT key once you see the login window.
Open your activity monitor and check for malicious applications.
Open your applications from the dock.
Select others and view the icon.
Open the activity monitor and view the list of applications.
Check the application which utilizes maximum RAM from the CPU tab.
If you get such an application, kill it and remove via “Move to Bin” from the applications list.
Execute malware scanner. For example, Bitdefender, Comodo, Intego are some scanners that scan your Mac and quarantines the files infected. If the free version does not work, go for the paid versions of malware scanners.
Once done, connect to the Internet via enabling Wi-Fi.
Open your web browser. Clear your cache and the browsing history.
What if all of the above steps don’t work?
Re-install your Mac completely. To do so,
Erase your disk.
Shut down your Mac.
Restart by pressing and holding the Power button.
You will see recovery options.
Choose the second option from the top – Reinstall macOS Big Sur.
Press Continue.
During the process, choose the Macintosh HD option to continue.
Once done, shut down and restart.
Complete the setup.
Once all of the above steps are performed, you will be able to successfully remove malware from Mac.
Antivirus Tools for Mac
There are various tools available in free and paid versions that cleans your Mac and protects it from malware, ransomware, trojans with periodic scans. Sometimes, it stops the file being opened if it looks suspicious.
Bitdefender (paid version only)
Kaspersky (paid version only)
Norton 360 Deluxe (paid version only)
Vipre (paid version only)
Intego (free and paid versions)
Comodo (free)
Mac protection is important to avoid unnecessary expenses that are not needed. Once your Mac is at security risk, it is recommended to take precautions and not recover after getting attacked by malware. You will be able to determine the risk level only after you perform the steps to remove malware and check whether they are life saver.
It is better to install free antivirus for Mac so that your Mac is monitored periodically and if an infected file(s) somehow is opened or downloaded from untrusted sources, the antivirus scan will help protect it.
Read: How to Cancel Apple News Subscription From iPhone
0 notes
Text
independent insurance agents of south carolina
BEST ANSWER: Try this site where you can compare quotes from different companies :insureinfoq.com
independent insurance agents of south carolina
independent insurance agents of south carolina, FL. We have experience handling home and auto, business, and life insurance policies and are ready to help you achieve the coverage you choose for you, your family. As an independent insurance agency, we work for you, not the insurance companies. That means we can help you find exactly the right coverage for your needs. As an independent insurance agent, we can work with you, not the insurance companies. That means we can help you find exactly the right coverage for your needs. With up to 20 companies in our network, we can offer you both personal and business insurance coverage options in just minutes. Plus, we aren t just standing outside on the side of the road; we are the ones who are driving for you - you re the ones who are using your car for anything except fun -- and we know the road. Carrying that peace of mind in the driver s seat is the biggest thing that can happen to you. You can take precautions such as keeping your lights off, avoiding collisions. independent insurance agents of south carolina’s average monthly car insurance premiums. The average monthly car insurance rates include coverage, civil liability and PIP. This data should be used to create your personal list, and you should never assume that your rates will increase when you apply for coverage. The rates above are average prices and assume no child drivers or drivers from married households. Your driving record is important. If you cannot find reliable car insurance from your state, then purchasing from a parent. Car insurance for parents and teenage drivers is easier to get than drivers born in high school. For those who don’t drive for a long period, car insurance generally can be a pain. But not having a high driving record will save you money as many parents do. For a teenager who is 16 to 19 years old, a moderate traffic violation for a parent will cut an insurance rate by 24%, making the cost from for parents over $20 per month. Parents who don’t drive get an extra benefit, but teens with. independent insurance agents of south carolina have been able to understand the specific needs of each group without any overpriced generic insurance. You can also check out how a credit limit and budget will impact your rates after an accident, a number of variables will determine your overall car insurance rate. When looking for the best auto insurance, it is wise for the driver to explore the coverage options. What is the cheapest home in the country for home insurance in California? Find out for sure. The amount you pay for liability insurance in California is about $1,450 dollars. The most affordable insurance is the $1,450 affordable home. Find cheap auto insurance rates in San Antonio, San Antonio, and all of California with our Compare Affordable Car Insurance Rates in Texas Save money on auto coverage with our simple comparison tool. Are you currently insured? Yes No Are you insuring multiple cars? Yes .
Business Insurance
Business Insurance, LLC (NYC Motor Vehicle Insurance). We take the time to examine the coverage of our companies. We will ask you all of the pertinent questions that might be on the table to help answer the questions. We will make sure the company you choose is insured and is financially stable for your assets. We guarantee that the company is financially stable for your insurance needs. We don’t charge higher rates or take fees when we offer discounts. We will never try to hide a company from you. you are aware of the unique risk you are facing. At the Car Insurance Compare office, we will show you detailed information about different coverages available including: We are all about saving you money and you want to save time! But we do try to provide you with the lowest car insurance rates. Do you have questions about auto insurance? Our team at will ask you the following questions and help you save money. As a non-standard company, is a non-standard insurance.
South Carolina Insurance Companies
South Carolina Insurance Companies: (800) 740-7908 Flexible Spending Account (TPDAB) (3) (866) 656-6969 Driving Privileges Protection (FSBP) Driving can help save you money, but it can mean pay to get stuck without car insurance for just a few days. Here’s everything you need to know about not paying for car insurance, and the penalty, if you get caught . A The first thing we want to point out is you shouldn’t expect your policy to cover more than 1 accident. A (meaning 1 in the US, or 0 in the US) Your policy may cover more than 1 accident. Here’s the point: you shouldn’t think about accident accidents. That’s why most insurance policies are geared towards Fraud! So not only have we covered many different things, but our next tip is.
Our Insurance Companies
Our Insurance Companies We know that we need insurance, but we also know we’ll need it fast and easy. But that doesn’t mean we can’t find the perfect policy. That’s why we ve created this guide to help drivers find the cheapest car insurance. If you’re already an AutoInsurance.com member and are still looking for a reliable car insurance policy, find an independent agent in your region by completing the below. You can also work with a local insurance agent through many different local insurance companies to find the best coverage available. Find an agent near you to learn about how to save with free auto insurance quotes from several local auto insurance companies. There are a lot of things that can affect car insurance quotes. Other things that make car insurance rates more complex might be the fact that drivers don t have the same amount of documentation that gives them the option to file an individual car insurance claim. In the last several years, more and more insurance companies.
Motorcycle Insurance Quote
Motorcycle Insurance Quote for 2017 Vehicle Year. The quote consists of an auto insurance quote for 5, 9, or 20-year-old male drivers. Motorcycle insurance quotes in Rhode Island are available year-round, with a single policy discount. A Rhode Island auto insurance policy for the first four years costs $249 a month, $827 for the rest of the year, or about $142 a month. Rhode Island car insurance for the second-year and fifth-year drivers is $224 a month, $531 for the seventh year, $1,089 for the sixth year, and $1,065 for the seventh year. Rates are available for an individual driver (age 25, old, 75, or 70 years old) and for singles. Rhode Island insurance calculator to compute final expense expenses. For new Rhode Island motorists, law enforcement, and the state and insurance company, the Rhode Island auto insurance plan offers a lot of flexibility. As part of its default insurance package for 2019.
Auto Insurance Quote
Auto Insurance Quote We are very dedicated for you to discover the best insurance products so you can be sure you re getting the cheapest rate. In this guide we are going to provide you with the best insurance companies in New Mexico. It is critical to review quotes and compare different quotes, which leads us to some of the best car insurance companies in New Mexico. We will also give you a quick tip for how you can improve those quotes. The main purpose of this guide is going to give you detailed information that can help you buy car insurance in New Mexico. These are things that are commonly asked of auto insurance companies, so keep reading to learn more about what they cover, prices and quotes. All insurance products advertised on are underwritten by insurance carriers that have partnered with , LLC. , LLC may receive compensation from an insurer or other intermediary in connection with your engagement with the website. All decisions regarding any insurance products, including approval for coverage,.
Life Insurance Quote
Life Insurance Quote comparison, copper’s rates aren’t as high but its is proudly offering many deductible options and discounts to get a more competitive price on your . So if you want to compare car insurance, we’ve got your back. It s called a quote card for comparison purposes. To use it, we have a basic car insurance quote for the state of Maryland so no need for if you’re looking for a more comprehensive coverage. Here’s what to look for: We don t like the cheapest prices for many reasons. Here are some of those some of the insurance industry views of the state. For example, with these car insurers you can check online, and the state of Indiana takes care of the costs, which is a factor we have listed on our. However what you might not think of is, the most cost-affordable to you. We also offer.
Boat Insurance Quote
Boat Insurance Quote - If you are just paying for the cost of your boat and you plan on renting it out, a Boat Insurance quote from A. M. Best means the best chance that you can find an individual who doesn t sell policies to you. It may, for example, be impossible for you to rent a yacht from its owner because you only need to get it for a week. But to provide proof to the owner of the boat that your insurance will pay you, the yacht owner must go first, either via phone or a letter. Be aware that the insurance company that pays you does not, so you may choose to use the online insurance quotes website as your first option. Be aware, that unlike online insurance, insurance quotes don t come out of your pocket. They come down to us, and some companies can get in close to the cost of the rental of your property. Your boat owner in Colorado should look over this insurance company s rates for a few reasons. If you re still wondering how.
Independent Insurance Agents at Your Service
Independent Insurance Agents at Your Service. All Independent Insurance Agents are agents who can provide you with multiple products like home insurance, auto, umbrella insurance, and life, and have a track record in finding you the best rates. When you work with an Independent Insurance Agent, you can gain the confidence and knowledge that you are getting the best quote for you. We’ve been serving the Asheville area for over 18 years. With hundreds of miles of roadway, we want to not need to worry about you. With that in mind, you have the potential to find some pretty competitive rates on personal auto insurance. Let us review our selection of Asheville home insurance companies we believe are great home insurers. As a result of our research, we are able to include some of the most competitive rates for Asheville home insurance. Here are the cheapest Asheville home insurance rates based on most reviews and choices: Insurance is so easy to say thank you ! I know these insurance prices will vary from location to location and also from policy to policy. But that.
Related SC Insurance Resources
Related SC Insurance Resources. Find more advice from trusted industry experts in the SC Insurance Plan. Your car is always on the way to the dealership to buy the new car. If you are taking a car sales route and you want to have the car insured for sale with just one car, you need to always keep that car on file with the DMV and it can be a pain, depending on the circumstances (and state) of your vehicle. If on the one that you are getting the car and you get into an accident and there is a claim, you should contact the Florida Department of Insurance or your insurance agent before the policy is sold. In some states, it may be difficult or impossible to get a quick and simple way to report a car and get this done. These may be available from the insurance providers but sometimes by calling the agent for a quick fix at an affordable price (or, depending on a person s age, a low monthly payment). .
Condo Insurance Quote
Condo Insurance Quote Program offers a wide variety of discounts for policies over $100,000*. We can also help you bundle home and auto insurance with Auto & Home and save more when you combine home and auto insurance with Auto & Home. Get a quote at . The Zebra is not an insurance company. We’re an independent, unbiased partner for consumers, on a mission to help you compare insurance options apples-to-apples, so you can make a truly informed decision. We’re proud because: This is a general guideline on how to handle insurance related questions when you apply to different companies. As an individual insurance specialist, we recommend that you do so as carefully as possible, taking the time to consider your own needs, then seek out relevant insurance companies for help with questions about your insurance. In addition, we recommend that you consult with other experts before providing such advice to your existing coverage. However, if you feel too uncomfortable, you may.
0 notes
Text
At Scale
The Rebuild games are incredible, I would be doing them a disservice if I didn’t mention that upfront, but I’m not here to talk about how good they were. As far as mechanics go, every entry in the Rebuild series has the same premise and basic mechanics. You play as a band of survivors who have control over a few blocks in the middle of a zombie-infested city. Your job is to reclaim the city and rebuild.

The moment to moment gameplay consists of choosing survivors that specialise in various skills and sending them out into enemy territory to accomplish a goal. There are 5 main goals. You can kill zombies, you can reclaim a square that has no zombies on it, you can scavenge for food and items and you can recruit survivors hiding on a space. Every one of these tasks except reclaiming has danger and can kill or injure one of your survivors. Hordes periodically spawn to attack your base and events fire from time to time. Some of these events are triggered by missions, but others exist to simulate the city. These include moral decisions and allow the player to express themselves.
However, as you gain more survivors, each with unique talents and a new token to move across the map, each turn of the game takes longer to play and both the rewards and punishments that are given to you during the game loop become less consequential. Simply put, the beginning of a game of rebuild has you making interesting choices and tactical decisions with outcomes that meaningfully effect the outcome of your game. However, none of these things are maintained as the game scales up. The game isn’t simply the sum of its parts.
Now, after all that, I want to talk about Downwell.

Downwell is an incredible game. It has incredibly tight gameplay. Its systems feel into each other with an almost ethereal elegance. Again, it’s good.
It’s also a game that grows with its players. You can get pretty far in Downwell by just following your instincts, but eventually you will discover the combo system. It is this system that allows Downwell to grow alongside you as a player. As you get better, Downwell encourages you to play in harder and harder ways.
However, it doesn’t grow alongside you forever. I do not play Downwell anymore.
When you first start playing downwell, your runs are only a few seconds, maybe a minute if you’re lucky. Each run brings new promise, novelty. There’s a special spontaneity to it. Each run carries no weight behind it. Contrary to the spirit of my “Raise the Stakes post”, sometimes you want no stakes. Sometimes the player has to feel free to experience the sensation of a game without strings attached, without feeling like you’re starting an obligation (though there are definitely stakes when you get further in, so this is almost the best of both worlds).
However, I’ve put in a significant amount of time into Downwell. When I start a run, I know it’s going to take 20 or so minutes. It’s tiring to consider starting a game. What was such a free experience of testing my limits against the game has turned itself into a chore. When it comes time to stop, I feel disappointed that it was me who had to end the game for myself and not the game. I feel disappointed that I died because I was playing stupidly because I wanted to make the game a little harder, a little quicker and more deadly.
Rebuild has a similar problem to downwell. The game becomes significantly less fun after you’ve carved out a moderate section of land. Specifically, you have a lot more survivors at that point, so assigning them all the missions becomes more of an exercise in spending your own time to figure out logistics than in making snappy, pithy strategic decisions. Each survivor and gun and city block also matters less. “Who cares if I lose that apartment? I have 9 more”, “Who cares if I lose one solider? I have 8 of them”. Each individual loss is robbed of its significance and any string of them that could result in you being in significant peril starts to not just feel like a punchy loss, but distinctly unfair. This goes the other way too. Deciding to try and reclaim a farm, for example, has significantly less weight when it will account for 1/9th of your food supply as opposed to 1/3rd. Of course, the situation is a little more complicated than what I described, but the underlying phenomena is still there. Why do all these games refuse to scale well?
^^^This is just one example of how large rebuild 3 can get.
In some ways I’m sure this is a bad question. Both these games seem to fail to scale in different ways. The specific mechanics that cause them to play out differently across the late-game of each run and skill level respectively are completely different.
However, I think that despite their differences, they’re interesting case studies that may or may not share underlying patterns in how we perceive them that, if not applicable to each other, will be useful to watch out for in any system we design in the future.
To start with, Downwell has a very strong feedback loop that drives early gameplay. You play, you quickly die, you come back. Progress in this is tied to the amount of time one stays alive, which has the eventual result of making this loop become obsolete. Downwell supplements the moment to moment loop and the game loop that I just mentioned with a combo system. This system functions similarly to the feedback loop I just mentioned, but it only kicks in for players who have a level of mastery over the game’s systems high enough to find it. Discovering this system transforms the focus of the player from the scale of minutes to the scale of seconds. It reinvigorates the game by giving your inputs meaning and purpose beyond the broad goals not taking damage and moving downwards. This cycle of success followed by inevitable failure introduced by the combo system happens on the scale of seconds at first. however, as the game progresses, it might take a minute or two before you hit the ground. The last zone in Downwell is called the void for a reason.
It’s tempting to blame Rebuild’s balance for the single note end-game. After playing all 3 games in the Rebuild series for an unreasonably long amount of time, one of three things tends to happen.
You die very quickly. You fail to generate enough of an advantage early on and you lose.
You reach a critical mass and there’s nothing the game can throw at you that can destroy you.
You hit a spot right in the middle. You gain enough of an advantage in the early game to survive, but reclaiming land becomes exponentially slower. Eventually you don’t get to reclaim any land at all, but the hordes can’t overpower your walls (these walls are stationed by the soldiers that would normally be clearing land for you.). The game keeps spawning more zombies around you and in this state it might take hours of real world time to die (assuming you don’t quit). (Interestingly this is a much bigger problem in rebuild 3, as 2 is very gung-ho about killing survivors who go on dangerous missions).
In a way, Rebuild’s balance reminds me of a specific symptom that MOBAs have: the tendency for games to be decided in the first 15 minutes, but for them to take 30-60 minutes in total to play out. However, there are more factors at play in a player’s enjoyment than just time and their ability to affect the outcome of the game.
Last year, I made a board game where you controlled two sides of wizards hurling fireballs at each other. It would take a long time to explain the rules, but the fireballs behaved somewhat like the infection in pandemic. They would persist and explode if enough fire was in a specific location. The fire would also fade over time, which was represented by faces on dice. It wasn’t a particularly difficult game to think about, Due to rules governing the fire, it was easy to compartmentalize the board into a few areas. We didn’t think about the game in terms of individual tiles that were in one of two states. We’re humans, we’re pattern recognition machines. While computers might need to sort through data using rigid methods that take into account every rigidly defined detail they’re fed, we perceive the world fundamentally differently.
At the end of the round in this game, we would have to adjust the face on every dice to represent the fire burning out. The time that decrementing the dice took was a reminder that our perception didn’t match up with what we were required to do to carry out the game: while we saw patterns, the system saw individual cells. In an ideal game system, we might send instructions to the game based on how we perceive it, and the game would carry out our instructions at the same rate it took to think up a plan. This disconnect between how we perceive and interact with these games is interesting. We also see this kind of thing in rebuild. One good illustration of this is the survivor management system in rebuild 3. Once you’ve bothered to reclaim a specific tile that allows you to do research, you can research a technology called survivor management. This allows you to periodically pick up perks for your survivors over time. These do things like give them a bonus in a random stat, or provide a bonus while doing a certain mission, or even provide happiness bonuses while on a mission with others because they’re a musician.
These perks are very flavourful and could add a whole lot of personality to the game. However, these perks will become a nuisance soon after you get them. The differentiation between survivors here becomes a source of meaningless noise rather than a source of tactical decision making because of the amount of perks each survivor has and how many survivors you have to manage. In short, they prevent you from easily compartmentalizing the game in a way that you really should be able to. They exacerbate the existing problem of “placing 20 individual units each turn is frustrating” by making you commit each individual survivor’s parks to memory and preventing the formation of more coherent structures.
However, this whole idea about rebuild not being good at presenting information in a way that we can easily compress and process is only half right. Rebuild does a ton of excellent compression. For example, combining your tiles into a fort compresses the complexity of previous gains. Only the stuff on the edge matters, because that’s where zombies might try to tear down your walls. Losing tiles peels back the complexity of the fort like an onion, which is a really elegant system. The tokens that represent survivors can also be placed on top of each other to form a stack. This stack can be moved everywhere and otherwise function as if they were one survivor for the purpose of sending them on missions. The structure of the cities can also be compressed to a degree. While meaningful variance in the tiles around you at the start of the game is almost guaranteed, the cities also have rural areas with lots of farms and fields and urban centers with Apartments, Chinese food shops and power plants.
If we apply this idea of information compression to Downwell, the most immediate example is that some sections of the screen are dangerous, but others are not. This is possible because there are only two consequences when interacting with an enemy. You might land on top of a safe enemy, in which case you refuel and avoid damage, or you touch an enemy in any other way, in which case you take one damage. This is one of those cases where this factor probably helps Downwell to become more complicated. To make the game more interesting as the player becomes better, Downwell chooses to add mroe enemies. If the enemies in Downwell had a more diverse range of effects, it would be much harder to read the screen.
This wasn’t the most focused post. I think that both the Rebuilds and Downwell have loops that doesn’t necessarily deal well with one or more of the variables that effects them. In Downwell’s case, both the main loops, (dying > respawning and the combo loop) are tied to time, which means that as one gets better, it takes more time to reach the reward part of the loop.
Rebuild’s main loops (gaining and losing resources, survivors and territory) do not get longer, but the reward or punishment diminishes in value, meaning that it takes more time to achieve the same result (which translates into lower enjoyment).
Rebuild’s enjoyment as it scales up its systems diminishes as a result of needing to process a lot of non-compressible information. I think I would like to analyze more games in this way in the future. In this post I think I fell into pointing out “Here is an example of this existing, and therefore I can make conclusions about it based on a shallow understanding of its nature”. However, I think the mechanisms behind pattern recognition and and other areas of cognitive psychology are a bit more complicated than that.
I hope you enjoyed reading this, whoever you are.
0 notes
Text
300+ TOP Adobe Photoshop Interview Questions and Answers
Adobe Photoshop Interview Questions for freshers experienced :-
1. What is Adobe Photoshop? It is software developed by Adobe to create and edit images and logos. By adobe photoshop adjustment and modification can be done. 2. How you can re-size the image in Photoshop? To resize the image in Photoshop you have to go into menu bar, under menu bar you will find an option “Image Size”. On clicking that option, it will open a dialog box, by which you can adjust the size of the image. 3. What is a Gradient in Adobe Photoshop? Gradients are a great way to introduce eye-catching and flashy graphics in your pages. 4. What are the Photoshop’s work areas? The Photoshop’s work area includes Application Bar, Option Bar, Panel Dock and Tools panel. 5. In Adobe Photoshop how you can print the grid? First of all you have to place the non-printing grid in a manner you want the print, and then take a screen shot. Now, you have to open a new file and paste your screen shot image on it. Once done, you can crop the background of the Photoshop window except the image with the grid. The image is ready for print. 6. What is resizing images and what are the parameters to change the size of the picture? To suit a particular purpose of the application resizing of the images is done. The parameters to change the size of image are: Type of image or picture Size of pixels Background resolution 7. In Photoshop, what is a smart object? In Photoshop CS2 and above, it has a special layer known as Smart Object Layer. Smart objects give freedom to work with multiple copies of a single object. All the multiple copies will be updated simultaneously when single object is updated. Also, changes in the adjustment of layers and layer styles of a single object can be done without affecting the multiple copies. Without any loss in pixel, pixel based objects can be changed several times. 8. How do you organize layers in Photoshop? A layers shows a picture or image. To organize layers in Photoshop, place various images in separate layers. Lock the unused layers and unlock the layers which are in use. When two or more layers need to be changed, unlock the layers. 9. How you can unlock the background in Photoshop? To unlock the background image, first click on the picture or image and then select MODE option. After that, select the option GRAY SCALE and revert to LAYER. When you double click on the surface, the surface will be unlocked. 10. How do you select an exact color to match? To sample the color as foreground color, we use the eye-dropper tool. Select the foreground color square, use the paint bucket tool or brush tool for covering the area. You can also use Clone Stamp Tool. Now use the key Alt+ and click where you want the color from and hold down the mouse button to cover up the area.

Adobe Photoshop Interview Questions 11. What is the difference between PSB (Photoshop Big) and PSD (Photoshop Document)? They both are file formats to store digital images. There is very less difference between PSB and PSD, what they differ is how they are stored and used. PSD is a default extension for Photoshop files and it can support the file size of 30,000 by 30,000 pixels. While for creating big documents or large image .psb file format is used, and it can save an image size upto 300,000 by 300,000 pixels. 12. What is healing tool? Healing tool is used in Photoshop to hide the unwanted spots or pictures that appeared in your original picture and makes picture look like real without any changes. The tool use complicated algorithm to calculate what would be the area of your picture based on the surrounding pixels. 13. Can you use bamboo tablet in Photoshop? Yes, you can use bamboo tablet in Photoshop. After installing the bamboo tablet software, open the software. Once done, the next step is to configure the four hotkeys of Bamboo tablet with the help of the software available in tablet. Create a new document and open the Photoshop, you can now have Photoshop with a bamboo tablet. 14. How can you reduce noise in an image? Reduce noise option is helpful to reduce the color and luminance effect in the image. To reduce the noise in an image, you have to go in a menu bar, select a filter menu, and in that you will see an option for NOISE. Again, clicking on it, it will show other option including reducing noise. 15. How to create an artistic border? To create an artistic border, you must select an image. After that, add a layer mask in a layer pallet then select filter-> brush strokes-> sprayed strokes. 16. What is a Gaussian blur? Gaussian blur is a tool that blurs the edges of the image to make it more real and adaptive to the surrounding. Often it is believed that Gaussian blur can only blurs the image, but if it is used cleverly it will not blurs the image but enhance the appearance. 17. What are swatches palettes? Photoshop provides two palettes for selecting color, a) Swatch Palettes b) Color Palettes. Some specific colors can be used without remembering the numeric color values. Also, colors can be extracted from an available image. Default swatches and custom swatches are also an additional option for the users. 18. What are Lasso tools and name them? With lasso tools precise area of an image can be selected, just by tracing the selection outlines the areas are selected. Simple Lasso Tool Polygonal Lasso Tool Magnetic Lasso Tool 19. With the help of spin software how you can make 3D sphere? To make 3D sphere, select blur from filter menu and click on radial blur. Select spin option in the blur method section, you can increase or decrease the amount of spin by dragging the slider. 20. How to create a transparent background in Photoshop? To create a transparent image you need to follows three steps: First go to ‘Select’ option and select the background, and then click on ‘Inverse’. This will select your main picture. Open a new file, select option ‘ Transparent’ under content, and you will have a file with transparent background. Copy your main picture and paste it to new file you created. 21. What is Clone tool? Clone tool uses the current brush to repair the problem areas in photos and pictures, by painting over them with pixel data from other areas. 22. How you fix the blurry images in Photoshop? To fix the blurry images in Photoshop you can use sharpening tools. Sharpening the image will lose the pixels, make sure you are finished with everything else and saved the changes before you start sharpening the image. 23. What tool you can use to combine images? You can use Auto-blend layers command to combine images. Auto-blend layers uses layer masks as needed to mask-out over underexposed areas. 24. What is a Bezier curve? It is a mathematically defined curve used in two-dimensional graphic applications. It is defined by four points, the initial position, two middle point positions and a terminating position. 25. How does Red Eye tool works? Red eye tool is a type of a repairing tool. When you circle any problematic area with red eye tool, the Photoshop will automatically identity that area and will replace it by dark-gray pixels. 26. Explain what is PostScript and showpage command? PostScript is a page description language developed by Adobe Systems. It is a language for printing documents on laser printer, but it can also be used to produce images on other types of devices. Showpage command transfers the contents of the current page to the current output device. The main function of showpage is It executes the endpage procedure in the page device dictionary Executes the function equivalent of an initgraphics operation, reinitializing the graphics state for the next page In page device dictionary, it executes the beginpage If the Boolean result returned by the EndPage process is true, transmits the contents of the page to the current output device and performs the equivalent of an erasepage operation, clearing the contents in preparation for the next page. 27. Define what is the meaning of a Path? A path can be defined as a collection of possibly disconnected, lines and areas describing the image. In simple words, it is a collection of curves and line segments arranged on the page. A path cannot be drawn by itself, but after it is specified it can be stroked (lines) or filled (places) making the proper marks. 28. Explain what is Photoshop lightroom? Photoshop light room is a software designed for photographer to make post-processing work easy after photography. Key features in Light room are PNG Support Full Screen Mode User Configurable Grid Overlays Windows HiDPI Support 29. Explain how you can import photographs in Lightroom from hard-drives? When you start lightroom, it automatically ready itself for immediate import as soon as you connect an external storage device to your computer. But it fails then you have to follow the steps below. First select the source to import images file form Second step includes selecting files which one you want to import Once you select the files, you have to specify the method of import for example like Copy as DNG, Copy, Move , Add etc. The last step is to choose the destination to copy files to, file handling options and meta-data setting. This step is little longer than other steps as it includes other steps like file handling, file re-naming, apply during import etc. 30. Explain how you can create a Diptych? To create a Diptych Go to “Print” module under the main menu Under layout style select Custom Package Now under Rulers, Grids and Guides , check and uncheck the options as per your requirement like page grid, rulers, image cells, dimensions etc. After that adjust other settings like file resolution, custom file dimensions, JPEG Quality Now you can drag and drop the images on your film strip onto the blank page and arrange them When done, choose print to file to export your diptych 31. Explain how you can create the HDR effects in lightroom? In order to give an HDR effect to photo in light room, You have to open the develop module of Lightroom First step is to choose tone base The tone base will hightlight various settings like shadows, whites and blacks, constrast, clarity, saturation etc. It will set the foundation for the faux HDR effect 32. What color is considered to be blown out? Any colour whose number exceeds 240 in light room is considered as blown out color. 33. Explain how you can fix blown out colors in light room? To fix the blown out colors in light room, you have to go to local adjustment brush option in lightroom and you can adjust your color. Either you can reduce the effect of color or either you can balance the effect of color by increasing the proportion of the opposite color. 34. How you can create a Grainy matte effect in Lightroom? To create a Grainy matte effect in lightroom , you have to Go to “basic” section of the develop module Make changes like shadows, clarity or saturation if it requires Now go to the “split toning” section in the develop module and make the adjustment to Hue, saturation, balance, hightlight etc. And at the last we have to add grain, you can adjust the option like Amount, Size and Roughness 35. Mention what is the short cut to e-mails photos directly from lightroom? To e-mail photos directly from the lightroom short cut is Press: Command+Shift+M(MAC) / Control+shift+M ( displays the options to e-mail photos in lightroom) 36. Explain how smart collection in lightroom is useful? Smart collection in light room is useful in Finding specific file types Smart collections to mark best images and can set up additional criteria Smart collections for Aspect Ratio- which means you can see your image in different formats like landscape, portrait and square 37. Explain why filename template is important in light room? File name template is important in light room because with the file name template you can save lot of information about the image like meta-data of that image, equipment, date, equipment etc. Apart from that, you can also include a custom text field. 38. Explain where you can use file name templates? File name templates can be used whenever you choose to rename files. 39. How you can assign a keywords in Lightroom? Lightroom provides the feature to assign keywords to your image. In order to do that Select the image you want to assign the keyword Under the library option you will see keyword Panel Inside the keyword panel you can enter the name you want to assign to selected photos 40) Explain how you can analyze the color tone in light room? On the top right hand corner of the library there you can see a histogram. This histogram gives you a fair idea about your image appearance whether it is blown out or suave. 41) Explain how to take back-up of photographs in light room? To take the back up of your photograph you have to Go to EditàCatalog setting (windows) or Light room à Catalog Setting (Mac) Click the general tab Look for the back-up section Look for the back-up catalog menu and select every time lightroom exits 42. Where you will find the back-up in light room? When you install lightroom, the program makes a folder “Lightroom”. This folder contains lightroom catalog Files related to the catalog A folder named Backups for Lightroom backups 43. With filter options in library what all things you can sort and search in lightroom? With the use of filter options you can sort and search various options like File type ( JPG, DNG, RAW etc.) Lens Model Camera Model Lens focal length Aperture, ISO Keywords Flash state Flag status Virtual copies and many more 44. How you can sync edits for multiple images in lightroom? Once you have edited the image and you want the same changes in other images as well you can use the function “Sync” at the bottom of the develop panel. 45. In synchronize setting what you should not sync? While using “Sync” function you must not check the check box for “Brush” option in synchronize settings, as it may distort the image appearance. Even if the image is almost similar never check mark to this option. Adobe Photoshop Questions and Answers for freshers experienced Read the full article
0 notes
Photo

Maturing Blockchains With Propagation, Scaling and Adoption Unless you’re hiding under a rock, I am sure you’d have heard of blockchain and the associated technicalities jarring it. Concepts including decentralization, bitcoin, mining, and ledgers seem to be finding new admirers every day with more romanticism being built around “Satoshi”. While the enthusiasm amongst the crypto-community is burgeoning, the need for a secure Unless you’re hiding under a rock, I am sure you’d have heard of blockchain and the associated technicalities jarring it. Concepts including decentralization, bitcoin, mining, and ledgers seem to be finding new admirers every day with more romanticism being built around “Satoshi”. While the enthusiasm amongst the crypto-community is burgeoning, the need for a secure and scalable infrastructure is becoming all the more imminent. Social Media On-Chain Scalability, the big buzzword around the community, has been the strongest point of debate for over a year now by crypto critics, experts and enterprises alike, thwarting mainstream adoption of the technology. Interestingly so, if blockchain in its current shape were to support Facebook, it would only be able to support 15 likes/second, against the millions which otherwise flow through the platform. Now, couple those millions with the amount of activity happening at Snapchat, Instagram, and YouTube, and it’s easy to visualize the instant need for scalability in blockchains? Breaking Down “The Chain” For simplicity of discussion, we will consider Bitcoin as the base blockchain, but the problem remains identical for other blockchains. Deconstructing a Block “Blocks” are the founding pillars of a blockchain which store sets of information and links. Each “block” of information connects to the next, forming a “chain” of information. Utilizing the Bitcoin blockchain, each time a transaction is executed, the associated information needs to be stored in a so-called digital container, or block, preserved immutably forever in bounds of code and algorithms. Approximately every ten minutes, a new block is minted, or created through the mining process. As each new block is mined, that block is propagated throughout the entire Bitcoin network using a “P2P Propagation Mechanism.” This is a fancy way of expressing an “information diffusion process” where one miner sends the block to its 8–10 peers, or networks, who further sends it to their peers until the block reaches the entire network. 3 Planes of a Crypto Network Imagine the entire cryptocurrency network as a pyramid with three planes: Network, Consensus, and Ledger. The “network” plane is where the P2P propagation runs. The “consensus” plane is the functionality that mines blocks for a distributed consensus, or agreement, is reached. It ingests messages from the network plane, outputting transactions for insertion into the system ledger for integration into the Blockchain. The “ledger” plane is where the blocks are finally stored once they are mined. In the last year alone, several projects have emerged addressing how to scale Blockchains with a primary emphasis on the “consensus” plane. However, the “network” plane which is the foundation behind these systems, has been mostly identified as a “black box” which just works. Block Propagation on Network Planes Bitcoin’s P2P network consists of “miner nodes” where the nodes are randomly connected with each other. Transactions and blocks are transmitted over this network by these nodes until each has received the message. For a message to be diffused through the network, the transaction travels in hops. With each iteration, a set of two (2) nodes are sent the message, while the network diffusion grows by a factor of 2^n. The diffusion increases exponentially as the hops increase, and after 12-15 hops, the entire network receives the message. Blockchain Throughput is measured by the number of transactions per second that it can support and is measured as: Throughput = Transactions/Block * Blocks/second (Inverse of Block interval), where Transactions/Block is a factor of Bitcoin’s current block capacity and average transaction size Transactions/Block = Bitcoin capacity /average Transaction size The current Block capacity for Bitcoin is 1MB for a Block interval of 10 minutes and given the average transaction size of nearly 540 bytes, the Bitcoin network currently processes ~1950 transactions per Block, which translates to ~3 transactions per second (TPS). To increase the throughput one can either increase the Transactions/Block or Blocks/second. A lot of work has already gone into increasing the number of transactions per block using both on-chain and off-chain methods. To increase the capacity by a factor of 10x, teams have tried increasing the block size by 10x. An increased block-size generally keeps the number of hops intact – 12-15 hops for the whole network but requires sending a larger block (1 * 10MB) over the Bitcoin link. Although the transaction/block here increases, it leads to the issue of network throttle, increasing the propagation time by a factor of 10x, further opening up an even more critical debate of Bitcoin forks. The hard-fork of Bitcoin into Bitcoin Cash stands testimony to one such attempt. Blocks/second, on the other hand, is another significant area of consideration for network scaling, but till date has been oft-neglected due to several throttling factors. The current system of gossip that determines travel time in a Network plane, is certainly inefficient for its lack of features like latency optimization, pipelining, redundancy, message losses, congestion, and others, which hinders Bitcoin’s network stack from reaching the per-node link bandwidth. On keen observation, one can now easily sense a stage being perfectly set, for a further exploration in this area, which can decrease the propagation time by a factor of the scale a new efficient system can bring in, without affecting the fork rates. If any project can make the network layer more efficient and reduce the block propagation time significantly, enhancing transaction finality, it would open doors for the next wave of blockchain adoption. It’s Time For Network Layers to Drive the Next Wave After analyzing the various aspects of a block’s journey, let’s circle back to where we had started the discussion. In the last year, several projects primarily targeting the consensus plane have emerged. Both on-chain and off-chain scaling solutions have been explored widely with on-chain projects like Dfinity, Zilliqa, Cardano and EOS trying to modify the overall consensus to achieve higher throughput while side-chain and off-chain projects like Plasma, Lightning Network, and Raiden Network, are creating ways to achieve scale by computing off the chain and storing the final output on-chain. Unfortunately, most of these have compromised on security and/or decentralization or have fragmented the network enough causing concerns for adoption. There’s a new wave of projects that are attempting to increase the speed of block propagation at the network level while strengthening the security and decentralization of blockchains. Focusing on roughly two main issues — block compression to limit the amount of data needed to be propagated over the network, and relay speed to minimize the time it takes for blocks to propagate, these projects are agnostic to and interoperable with any on-chain or off-chain scaling solution. BloXRoute, a startup founded by lab mates of the team behind the Falcon Project aims to commercialize cut-through routing with a high-speed centralized network. Marlin Protocol, a project founded by researchers from Stanford and MIT is building a decentralized relay network with crypto-economic incentives to speed up P2P propagation of packets. Marconi is a networking startup working on creating secure communication pipes designed down to the ethernet level to bring in security and upgradability to the communication network. Orchid Labs is creating an incentivized Tor network. Other projects like Fast Relay Network, Fibre and Falcon have tried to optimize for speed, packet losses, and smarter routing, but have mostly been limited to a privileged group of miners. Amongst the sea of new consensus protocols coming by the day, these networking startups are a refreshingly new direction to scaling Blockchains. According to Marlin’s CEO Siddhartha Dutta, network layer scaling solutions require minimal changes on the part of existing or newly developed blockchain platforms. “Given the ubiquity of the network layer in any P2P system and the low friction involved in integrating a faster relay network, solutions such as Marlin are an easy way for blockchains to achieve higher throughput. Unlike existing relay networks, Marlin’s permission-less network powered by its dynamic traffic steering technology is immune to centralized crackdowns and provides a great deal of flexibility to developers.” https://coinmarked.com/maturing-blockchains-with-propagation-scaling-and-adoption/?feed_id=93&_unique_id=5d61503884943
0 notes
Text
Something awesome 2
Week 2 - Viruses
Blog
What is a virus?
Although many people (including myself before I started this project) misunderstand the definition of a virus and use it as an umbrella term that describes all malware such as worms and trojans, computer virus has a clear definition, defined as: “a type of malware that, when executed, replicates itself by modifying other computer programs and inserting its own code without user consent.” And once this replication process has succeeded, the affected areas are now known to be “infected”. The majority of active malware threats are also actually trojan horse programs or computer worms rather than computer viruses. Viruses often perform some type of harmful activity on the infected host, such as acquisition of hard disk or CPU time, accessing private information, corrupting data, displaying spam on the user’s screen, spamming the user’s email/social media accounts, keylogging, or RDC and can even render the device useless. However, unlike other malware, not all viruses carry a destructive payload and not all viruses attempt to hide themselves.
Phases of a virus
The phases of a computer virus are also called the life cycle of a virus, and can be usually divided into 4 phases:
Phase 1 – dormant phase: the virus is idle in this stage. The virus program has managed to access the target user's computer or software, but during this stage, the virus does not take any action. The virus will eventually be activated by the "trigger" which states which event will execute the virus, such as a date, the presence of another program or file, the capacity of the disk exceeding some limit or the user taking a certain action (e.g., double-clicking on a certain icon, opening an e-mail, etc.). Not all viruses have this stage.
Phase 2 – propagation phase: The virus starts propagating, that is multiplying and replicating itself. The virus places a copy of itself into other programs or into certain system areas on the disk. The copy may not be identical to the propagating version; viruses often "morph" or change to evade detection by IT professionals and anti-virus software. Each infected program will now contain a clone of the virus, which will itself enter a propagation phase.
Phase 3 – triggering phase: A dormant virus moves into this phase when it is activated and will now perform the function for which it was intended. The triggering phase can be caused by a variety of system events, including a count of the number of times that this copy of the virus has made copies of itself.
Phase 4 – execution phase: This is the actual work of the virus, where the "payload" will be released. It can be destructive such as deleting files on disk, crashing the system, or corrupting files or relatively harmless such as popping up humorous or political messages on screen.
Creeper
Creeper is an experimental program that was first created in 1971 by Bob Thomas, a programmer at BBN Technologies. The creeper program was possibly one of the first programs that resembled a computer virus and is widely accepted as such.
Creeper ran on the Tenex operating system and spread through the ARPANET, a predecessor of the current Internet. Creeper caused infected systems to display the message "I'M THE CREEPER: CATCH ME IF YOU CAN.".
However, Creeper was totally harmless, and had nothing to do with the harmful viruses that developed years later. After “infecting a computer”, Creeper would display its message, start printing a file and, before the printing was finished, jump to the next computer across the network, disappearing from the first. It was developed to confirm that programs could indeed move in between computers and devices as mentioned in John von Neumann’s “self-reproducing automata”.
Due to this behaviour, some would question whether Creeper really was the first virus. As it did not multiply but travelled from one computer to another. In fact, both the concept of virus and the concept of antivirus did not exist at that time (dating back to the 1980s).
Elk cloner
In 1981, A program called Elk Cloner, written for Apple II systems, was created by high school student Richard Skrenta, originally as a prank. Elk Cloner was the first large-scale computer virus outbreak in history.
When an infected disk was booted, the virus would load into the memory. It would monitor disk accesses, and upon finding an uninfected floppy, infect its boot sector. The virus will only infect 5.25-inch floppy disks, as they were the standard type of disk in 1982 and a hard drive was unlikely to even be on a computer, as operating systems and programs were loaded entirely from floppies.
Elk Cloner did not cause any deliberate harm, although overwrote its reserved tracks regardless of the contents, damaging disks not containing the standard DOS image. Typical of many early viruses, it caused annoyance: on every 50th booting the virus would display a short "poem".
Richard Skrenta often traded pirated software on disks with friends. He was well-known for using disks to pull pranks on friends, who began to distrust any disks they received from him. His disks often displayed taunting messages. Elk Cloner was the first to spread on its own.
In 2007 July, many Internet sites began reporting that the world had entered the 25th year of computer viruses, while others claimed that Creeper, created 15 to 10 years earlier than Elk Cloner was the first. Technically, Elk Cloner is the first virus, as Creeper does not require a boot sector or another file as a host, while Elk Cloner infects boot sectors. Regardless of definitions, Elk Cloner was the first virus or self-replicating program of any kind to work on a home computer.
Elk Cloner is an example of the dangers of pirated software. The Brain virus a few years later was created for the purpose of preventing software piracy.
Reflection
What techniques do viruses usually employ to attack?
Virus writers use social engineering deceptions and exploit detailed knowledge of security vulnerabilities to initially infect systems and to spread the virus. The vast majority of viruses target systems running Microsoft Windows, employing a variety of mechanisms to infect new hosts, and often using complex anti-detection/stealth strategies to evade antivirus software. Motives for creating viruses can include seeking profit (e.g., with ransomware), desire to send a political message, personal amusement, to demonstrate that a vulnerability exists in software, for sabotage and denial of service, or simply because they wish to explore cybersecurity issues, artificial life and evolutionary algorithms.
How can we combat these?
· Public awareness, for example with the elk cloner, don’t just accept random floppy disks (or USBs nowadays)
· Be cautious of links and attachments from emails, especially from unknown senders
What did the elk cloner exploit?
· The Apple II was particularly vulnerable due to the storage of its operating system on a floppy disk.
· Social engineering, users willingly installed the virus using the floppy disk
What was it back then that made this attack possible?
· Lack of public knowledge about what malware was and how to protect against it
What do we have nowadays that is making this attack hard/still possible?
Due to the fact that all viruses need to have a distribution agent and activation agent, are almost always attached onto an executable file, and are only activated when the file is run, it is quite difficult for a virus to spread and infect a lot of people when compared to other malware such as worms or trojans. Therefore, although viruses can be highly destructive, it doesn’t have the ability to impact many devices/systems by itself. Nowadays, people are made more aware of cybersecurity compared to the 1970s, and thus it’s even harder for something like the elk cloner to spread.
Comics


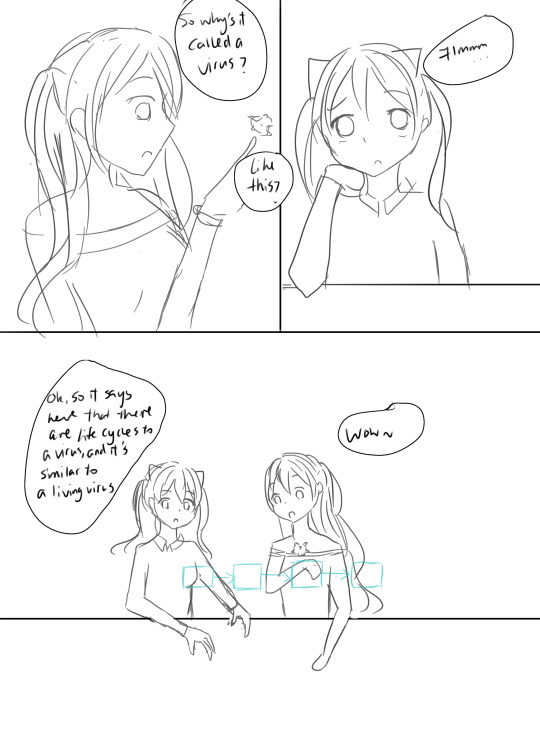


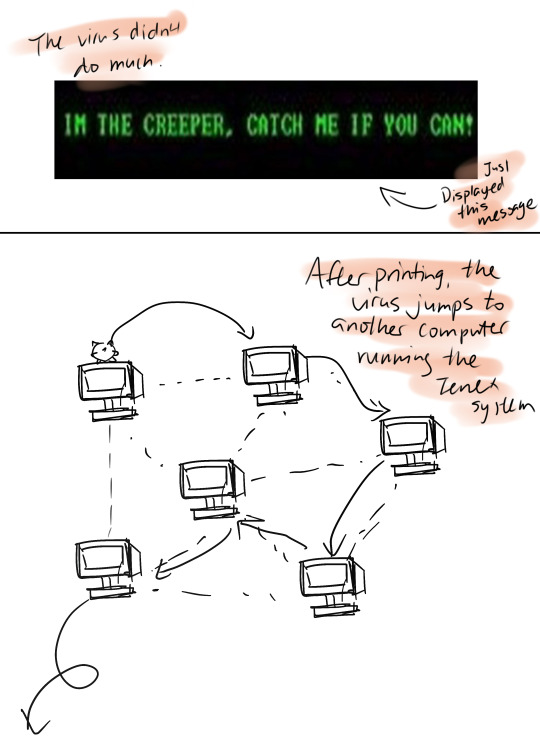

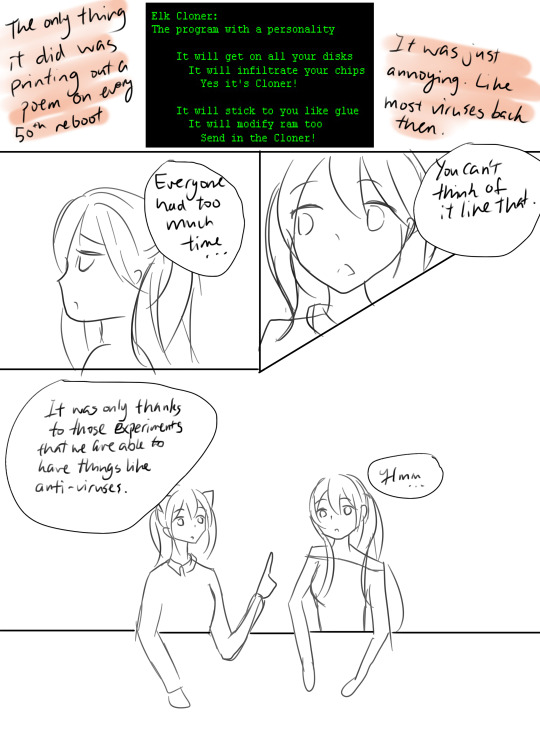
0 notes
Text
Malwarebytes Anti-Malware 3.5.1 Premium 2018 Lifetime Keys
Malwarebytes Crack with Serial Key 2018: hey users, you already know My crew usually gives you excellent and today’s software program. these days I give you Malwarebytes Premium Key from the Nest. Malwarebytes Anti-Malware Premium Key + Crack & License Key [Free] here. Malwarebytes Key may be very famous software for Microsoft windows macOS and Android OS. This well-known software program is used for location and removes malware. Malwarebytes is published in January 2006. you could easily use this software for the scan and eliminates malware.

Malwarebytes Crack is world famous software to remove virus and worms from your computer. Malwarebytes give you high security from the viruses no need to install any antivirus on your computer if you have Malwarebytes installed. Malwarebytes Crack scan all the modern software which are installed or not on your computer. Even you can update your outdated software very quickly. So you can find Malwarebytes keys from our website to register your software license. But, Malwarebytes can remove your cracked software and files, so if you are using cracked software of games, then please do not install Malwarebytes Crack software on your computer.
malwarebytes key
Malwarebytes Anti-Malware Key is a very notable product to be able to prevent every chance. it’s miles quite simple and smooth to use. you may effortlessly use this software for device protection. Malwarebytes Anti-Malware Premium Key unfastened download along with his extraordinary capabilities and tools. you can additionally guard your computer against spyware, and malware as properly with the aid of the usage of this tools. those equipment maintain your computer gadget unfastened from infected files and inflamed applications.
Content Navigation [hide]
0.1 Malwarebytes Crack/Keygen Download 1 Malwarebytes Key Generator 2 Malwarebytes Key 3.1.2 function: 3 Descargar Malwarebytes 3.5.1 keygen Premium Full Version 4 Improvements in New 3.5.1 version: 5 Malwarebytes key Malwarebytes Crack/Keygen Download Setup
Crack
Malwarebytes Key Generator Are you looking for Malwarebytes Key 2018? It is the right place to find Malwarebytes key without any survey or cracks license is the best option to use any software for a long time without any problem. So today we are sharing a Malwarebytes key generator tool which can generate thousands on the license key in seconds you can earn money by selling them. On the internet you heard about the ransomware it is the biggest scam in the history. Attackers demand 1 or 2 bitcoins for decrepit the data. Ransomware is a virus who encrypt your computer data and demand bitcoins to decrypt your data. So the Malwarebytes software also protects us from this virus. Well, windows launched the patch for that but, it does not mean no virus can affect your computer.
Malwarebytes Key 3.1.2 function: there are numerous new capabilities added in this ultra-modern version at the same time as some of them are cited underneath:
Excellent supported for home windows together with 2000.XP & 7 (64-32 bits). Rapid Scanning of laptop documents. Functionality in scanning all the computer drives. Operating mutually in opposition to with different utilities of anti-malware. The shortened list of extra services by eliminating all malware viruses manually. Settings to enhance the performance of recent Malwarebytes Anti-malware. Quarantine to hold threats fixes them at your convenience. Fixing of protection issues & superior self-safety of Malware totally free. Solving of numerous topics applicable to up-to-relationship of databases inside the limited person account. Solving the hassle of tray icon i.e. when the consumer doubles click with the mouse it would now not release inside the consumer interface. Fixing numerous troubles of licensing that can probably lead to invalid licenses & also protection. Descargar Malwarebytes 3.5.1 keygen Premium Full Version They protect you from the harmful virus and links. Sometimes you already faced this problem a popup window appeared and said your computer is in danger, please download this software to remove all the virus, etc. So they are scammers who detect your system and asking to download their software which is the main keylogger or virus. So if you download that software now they can put ads on your computer, they can copy your data manipulate data or delete your data. So the Malwarebytes protect you to this virus. Even they block these type of website so no one can hack your computer. It is the very fantastic software for windows computer. So download Malwarebytes 3.5.1 key right now.
Improvements in New 3.5.1 version: The old model 2.2.1 2018 has been up to date on the state-of-the-art model which comes with the following enhancements and new functionalities.
Supported by using home windows 10 new running system. blanketed Newly updated agreement License. For fundamental laptop safety, experiment modes are available Safeguards to save you against valid malicious files of malicious viruses. Quarantine feature is to be had that holds all threats and allow you to repair along with your complete convenience. development in managing scheduled new updates set to run on reset to avoid repetition & repeating of overlooked updates. Edits minor within the person interface inclusive of outcomes of experiment view & additionally up to date top navigation menu. Works even faster. Block unwanted website who sends worms and virus-infected software. Protect your system from the ransomware virus. Malwarebytes key ZAW3S-E4XDR-5CFT6-VGY7G BHU8N-IJNHU-BYGVT-FCR61 DXES4-ZWA4U-EX5DR-C6FTN V7GYB-8HUN9-IJHUB-8YG7V T6RC5-XE4WZ-3DFWZ-4SEX5
How to Activate Crack?
Install the program… Don’t run it yet. Add this line to your host file (use editor with admin rights) 0.0.0.0 keystone.mwbsys.com Copy and replace all files found in this archive (configuration dir) to somewhere like C:\ProgramData\Malwarebytes\Malwarebytes Anti-Malware\configuration Enjoy!? malwarebytes key
Final Words
So in this article, we discussed some harmful software and Malwarebytes Key generator so If You face any problem with keys and crack then please let me know in the Comment section I will update keys and crack version as you need. Thanks for Visiting…
0 notes