#identityverification
Explore tagged Tumblr posts
Text
The Role of Driver’s Licenses in Canadian Identity Verification
In Canada, a driver’s license is more than just a document that grants the right to operate a vehicle—it serves as one of the primary forms of identity verification. Across the country, the driver’s license is widely accepted as an official means of proving a person’s identity, with provinces issuing licenses that contain key personal details, such as name, address, and date of birth. These identifiers make it easy for individuals to prove their identity in various situations, from proving their age at a store to verifying their identity for banking transactions or legal matters.

The importance of a driver’s license in identity verification comes from the fact that obtaining one involves a rigorous process of identity validation. To get a license, individuals must provide proof of residency, legal status in Canada, and other supporting documents. These checks ensure that the information on the license is accurate and valid. This makes the Canadian driver’s license a reliable and trustworthy identification tool used in multiple aspects of daily life.
Beyond simply being a personal identification document, the driver’s license is often used as proof of residence in a specific province or territory. This is particularly significant when applying for government services, registering for healthcare, or conducting other legal activities that require proof of where you live. Because Canadian provinces maintain a consistent format and security features, such as holograms and barcodes, the driver's license is also a key document in preventing fraud and identity theft.
For those new to Canada, obtaining a driver’s license is often a critical step in establishing oneself within their new community. At licenseprep.ca, we provide resources, practice tests, and guides to help you prepare for the licensing process. Whether you are preparing for your G1 exam or looking to exchange your foreign driver’s license, LicensePrep can support you every step of the way as you secure an important piece of your Canadian identity.
#CanadianIdentity#DriverLicenseVerification#CanadaLicense#IdentityVerification#licenseprepca#NewcomersCanada#DrivingInCanada#G1Test#SecureID#LicensePrep
2 notes
·
View notes
Text

Finger print and face detection by HRsoft Bangladesh https://hrsoftbd.com/serv.../finger-print-and-face-detection Optical Scanning Feature, Real-Time Attendance Notifications, Manage Attendance of All the Employees And Staff From One Place, Representative attendance can be reduced, Facial recognition’s advantages, Easy Accessibility, Faster Results, No modification.
#FingerprintRecognition#FaceDetection#BiometricSecurity#IdentityVerification#SmartAuthentication#BiometricTechnology#AccessControl#FaceRecognition#SecureLogin#AIRecognition#hrsoftbd#softwaredevelopment#softwarecompany#mobileapp#websiteDevelopmentBD#websiteDesignBD#appDevelopmentBD#omrSoftwareBD#OMRSolutionbd#AccountingSoftware#ecommerceDevelopment#ERPSolutionBD#Ballotcountingsoftware#ballotsoftware#bulksms#voicecall
0 notes
Text
instagram
#eKYC#DigitalKYC#IdentityVerification#FintechIndia#DigitalTransformation#PaperlessSolutions#OmegaSoftwares#CustomSoftware#SmartBusiness#KYCCompliance#FintechSolutions#TechForBanks#SeamlessOnboarding#DombivliTech#FutureOfFinance#softwarecompany#softwarecompanyindia#software#softwaredeveloper#softwareengineering#SoftwareDevelopment#customsoftwarecompany#customsoftwaredesign#customsoftwaredevelopment#Instagram
0 notes
Text

💡 Facebook Tip: Confirm Your Identity with a Video Selfie
Ever been asked by Facebook to take a video selfie? Don’t panic — it’s just a quick way to prove you're real!
✨ Why it matters:
Stops fake accounts
Keeps your profile secure
The video stays private—only used for verification
📲 It’s fast, easy, and helps build a safer online space.
#BibiKhadija#SocialMediaSafety#TumblrTips#IdentityVerification#DigitalSecurity#VideoSelfie#FacebookTips
0 notes
Text
Understanding User Authentication: The First Line of Defense in Cybersecurity
In the ever-evolving digital world, where data breaches and cyberattacks are increasingly common, user authentication plays a crucial role in safeguarding sensitive information. It acts as the first line of defense in cybersecurity, ensuring that only authorized users gain access to systems, applications, and data. Whether it’s logging into an email account, accessing an enterprise network, or using mobile banking apps, authentication verifies the identity of users and prevents unauthorized access.
What is User Authentication?
User authentication is the process of verifying the identity of a user attempting to access a system or network. It ensures that the individual is indeed who they claim to be by requiring the presentation of valid credentials such as passwords, biometric data, security tokens, or other forms of identification. Without effective authentication mechanisms, systems become vulnerable to unauthorized access, data theft, and security breaches.
Authentication generally falls into three categories:
Knowledge-based Authentication: Something the user knows, such as passwords or PINs.
Possession-based Authentication: Something the user has, such as a mobile device, hardware token, or smart card.
Inherence-based Authentication: Something the user is, such as fingerprint, facial recognition, or other biometric data.
Common User Authentication Methods
1. Password-Based Authentication
Passwords are the most widely used method of authentication. Users create unique passwords to access systems, and the system verifies the entered password against stored credentials. However, this method has limitations due to weak password practices, password reuse, and susceptibility to phishing and brute-force attacks.
2. Two-Factor Authentication (2FA)
2FA enhances security by requiring users to provide two types of authentication factors—typically, a password and a one-time code sent to a mobile device or email. Even if the password is compromised, unauthorized users cannot gain access without the second factor.
3. Multi-Factor Authentication (MFA)
MFA takes 2FA further by requiring two or more authentication methods, such as a combination of password, biometric verification, and a security token. This significantly reduces the risk of unauthorized access.
4. Biometric Authentication
Biometric methods such as fingerprint scanning, facial recognition, and retina scans are becoming increasingly popular. Biometrics offer convenience and security, as they rely on unique physical characteristics that are difficult to replicate.
5. Single Sign-On (SSO)
SSO allows users to log in once and access multiple applications or services without re-authenticating. It simplifies the login process and reduces password fatigue, but it also creates a single point of failure if compromised.
6. Certificate-Based Authentication
This method uses digital certificates to verify a user's identity. It is widely used in corporate environments where secure, certificate-based access is necessary.
Why User Authentication is Essential
Effective user authentication protects systems from unauthorized access, preventing data breaches and maintaining the confidentiality, integrity, and availability of information. Here are some of the key reasons why authentication is critical:
Data Protection: Ensures sensitive information is accessible only to authorized users.
Compliance: Helps organizations meet regulatory requirements such as GDPR, HIPAA, and PCI DSS.
Identity Verification: Verifies the legitimacy of users, reducing risks of identity theft.
Secure Remote Access: Facilitates safe access for remote employees, particularly in a hybrid work environment.
Fraud Prevention: Prevents financial fraud and unauthorized transactions.
Best Practices for Strong User Authentication
To maximize the effectiveness of authentication mechanisms, organizations should adopt the following best practices:
Use Strong, Unique Passwords: Encourage the use of complex passwords and regular password updates.
Implement Multi-Factor Authentication: Combine multiple methods to strengthen security.
Monitor and Audit Authentication Events: Continuously monitor login activities to detect suspicious behavior.
Leverage Biometric Authentication Where Appropriate: Use biometrics for systems requiring high-level security.
Educate Users: Regularly train employees and users about secure authentication practices and phishing risks.
Adopt Zero Trust Principles: Assume no implicit trust and continuously verify identities before granting access.
The Future of User Authentication
With advancements in technology, traditional passwords are gradually becoming obsolete. Modern authentication trends include:
Passwordless Authentication: Utilizing biometrics, hardware keys, or magic links to eliminate password dependence.
Behavioral Biometrics: Monitoring unique user behaviors like typing patterns and mouse movements for continuous authentication.
Decentralized Identity Systems: Giving users control over their digital identities through blockchain-based authentication.
Conclusion
User authentication is fundamental to digital security, ensuring that only authorized individuals can access critical systems and data. As cyber threats grow more sophisticated, organizations must evolve their authentication strategies by adopting stronger, more innovative approaches like MFA, biometrics, and passwordless methods. By prioritizing robust user authentication, businesses can safeguard their digital assets, maintain regulatory compliance, and build trust with customers and employees alike.
#UserAuthentication#CyberSecurity#DataProtection#MultiFactorAuthentication#IdentityVerification#DigitalSecurity
0 notes
Text
Social Media Check: The Modern HR Tool Every Employer Needs in 2025
In today’s digital-first world, a candidate’s online presence says as much about them as their résumé. As hiring becomes more remote and dynamic, social media check has emerged as a critical component of modern background verification. For HR professionals, it's no longer a question of whether to check—it’s about how to do it right.
What Is a Social Media Check?
A social media check is the process of reviewing a candidate’s public online profiles—LinkedIn, Facebook, Instagram, Twitter, and more—to gain additional insights into their behavior, values, and authenticity. This check helps validate a candidate’s identity, evaluate cultural fit, and flag any behavior that could pose reputational or legal risks to your organization.
Why Employers Are Turning to Social Media Checks
Uncover Potential Red Flags Hate speech, discriminatory remarks, or evidence of violent behavior can be warning signs. A social media check helps you catch these before making a hiring decision.
Verify Identity and Authenticity By comparing the candidate’s claimed information with their online presence, employers can validate employment history, education, and even photo identity (especially when paired with a face match check).
Gauge Cultural Fit Public posts and interactions can offer insights into how well a candidate aligns with your company values or team dynamics.
A Responsible, Compliant Approach
Social media screening must be conducted ethically and legally. That means:
Focusing only on publicly available content
Avoiding personal bias or discrimination
Gaining candidate consent as part of the background verification process
Using technology that ensures consistent and fair evaluation
Final Thoughts
A well-executed social media check goes beyond simple observation—it’s a tool for building safer, more aligned, and trustworthy teams. When integrated into a wider background verification process—like the one OnGrid offers—it becomes a powerful safeguard for your workplace and brand.
#FaceMatchCheck#SocialMediaScreening#BackgroundVerification#HRTech#CandidateVerification#DigitalHiring#IdentityVerification#SafeHiring#EmployeeScreening#OnboardingSecurity
0 notes
Text

Finger print and face detection by @hrsoftbd
The system features an optical scanning feature, real-time attendance notifications, facial recognition, easy accessibility, fast results, automatic SMS alerts, user-friendly interface, fully automated systems, and biometric security.
#FingerprintRecognition#FaceDetection#BiometricSecurity#IdentityVerification#SmartAuthentication#BiometricTechnology#AccessControl#FaceRecognition#SecureLogin#AIRecognition#hrsoftbd#softwaredevelopment#softwarecompany#mobileapp#websiteDevelopmentBD#websiteDesignBD#appDevelopmentBD#omrSoftwareBD#OMRSolutionbd#AccountingSoftware#ecommerceDevelopment#ERPSolutionBD#Ballotcountingsoftware#ballotsoftware#bulksms#voicecall"
0 notes
Text

Finger print and face detection by @hrsoftbd
Automatic SMS alert to parents, User Friendly interface, Easy to use options, Fully automated systems and records, Biometric systems mean nothing to lose, Easy access and log-in, Unbreakable Safeguard, Convenient Usage.
#FingerprintRecognition#FaceDetection#BiometricSecurity#IdentityVerification#SmartAuthentication#BiometricTechnology#AccessControl#FaceRecognition#SecureLogin#AIRecognition#hrsoftbd#softwaredevelopment#softwarecompany#mobileapp#websiteDevelopmentBD#websiteDesignBD#appDevelopmentBD#omrSoftwareBD#OMRSolutionbd#AccountingSoftware#ecommerceDevelopment#ERPSolutionBD#Ballotcountingsoftware#ballotsoftware#bulksms#voicecall
0 notes
Text
#CompaniesHouse#IdentityVerification#UKBusiness#CompanyDirectors#PSCCompliance#UKCompanyFormation#BusinessCompliance#CorporateServices#ACSP#VerifyWithCompaniesHouse#BusinessRegulations
0 notes
Text
বিজয় রূপাণীর ডিএনএ মেলানোর প্রক্রিয়া অব্যাহত

https://durantbarta.com/country/vijay-rupani-dna-matching-process-continues
#VijayRupani#DNAMatching#DNAInvestigation#ForensicUpdate#BreakingNews#RupaniCase#PoliticalNews#IdentityVerification#OngoingInvestigation#GujaratNews#DNAProcess#IndiaNews#durantabarta
0 notes
Link
#Cross-BorderFrameworks#digitalassets#fintechstrategy#IdentityVerification#machineeconomy#paymentinfrastructure#regulatoryinnovation#tokenization
0 notes
Text
0 notes
Text
Enhance Identity Verification with SprintVerify
Leverage AI-driven identity checks for seamless customer onboarding. https://www.sprintnxt.in/contact-us.html
0 notes
Text
Identity Verification Market Anticipated to Grow Due to Fraud Prevention
Identity verification solutions encompass a range of software and hardware products designed to authenticate an individual’s identity by analyzing credentials such as government-issued IDs, biometric data, and digital footprints. These products offer advantages such as enhanced security, reduced identity theft, improved regulatory compliance, and streamlined customer onboarding. In an increasingly digital economy, businesses across banking, e-commerce, healthcare, and government sectors rely on robust identity verification to mitigate fraud, satisfy Know Your Customer (KYC) and Anti-Money Laundering (AML) requirements, and foster consumer trust. Advanced technologies, including machine learning-powered facial recognition, liveness detection, and blockchain-based identity repositories, further boost accuracy and speed of verification while minimizing false positives.
Get More Insights on Identity Verification Market https://www.patreon.com/posts/identity-market-130079633

#IdentityVerification#BiometricAuthentication#DigitalIdentity#AIPoweredBiometrics#CoherentMarketInsights
0 notes
Text
#Giesecke+Devrient#telecommunications#CyberSecurity#DigitalIdentity#BiometricAuthentication#IdentityVerification#DigitalTrust#DataPrivacy#FintechSecurity#electronicsnews#technologynews
0 notes
Text
Seamless Identity Checks with Gridlines' Voter ID Verification API
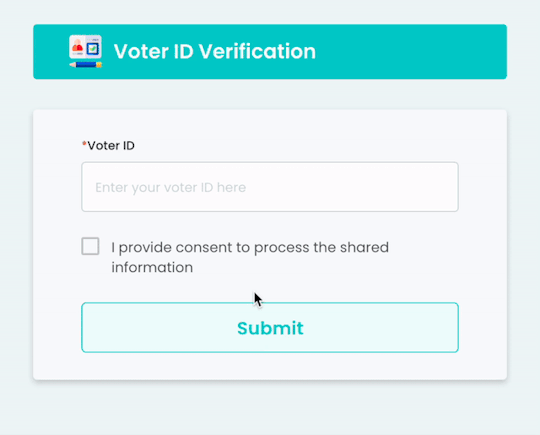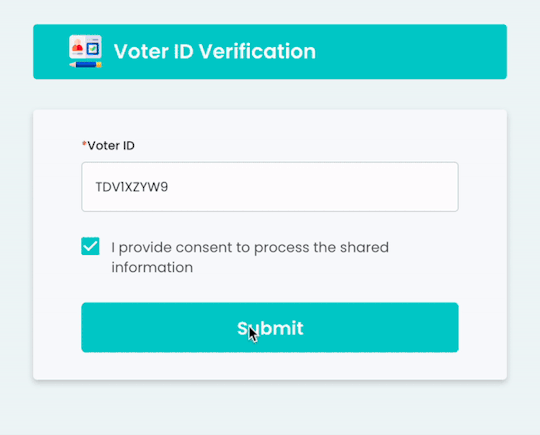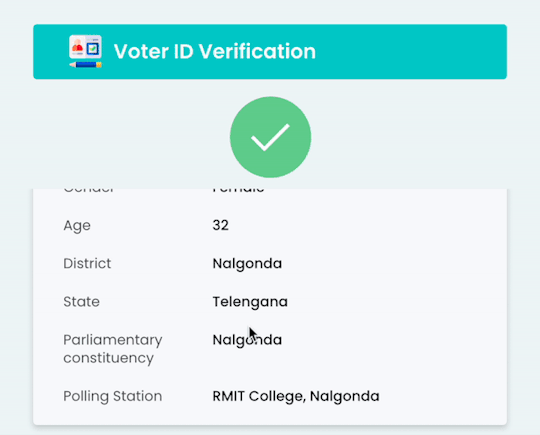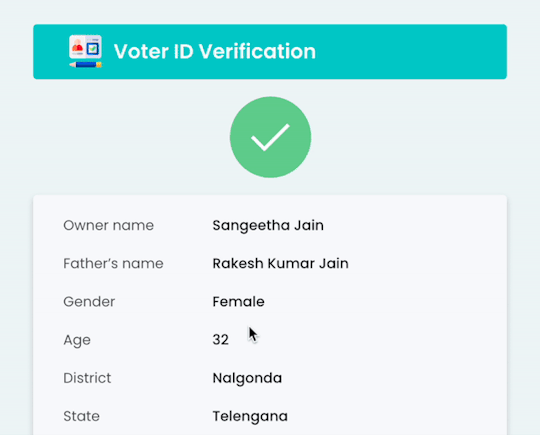
Discover how Gridlines' Voter ID Verification API streamlines digital identity checks using Election Commission records—ideal for fintechs, lenders, and onboarding platforms.
#VoterIDVerificationAPI#DigitalKYC#IdentityVerification#ElectionCommissionData#RealTimeVerification#KYCautomation#FintechAPI#OnboardingSolutions#GridlinesAPI#APIVerification
0 notes