#inter-layer webs
Explore tagged Tumblr posts
Text

#handwritten character recognition neural network#optical character recognition#ocr#inter-layer webs#four (4) layer neural network
0 notes
Text
Labseal but Luce is Lyla and gets stolen. Based on some kids book I found
Machine Assisted Research Intern Engine. Stupid name for a stupid little hologram. for some reason this book’s Miguel is tje CEO of alchemax? Ao3 fanfic sounding premise but whatever. This is so unnecessarily long I’m so sorry. Not reading allat.

Marie tolerated Miguel. If she were a weaker system, maybe she would’ve gotten attached, but she was the most advanced of her kind. She helped him, and he kept her up to date and charged. Mutualism was common in nature, she learned that by scanning over books that were nearly a century old uploaded into her database.
Inter-universe travel was being developed at an exponential rate, and Miguel was commonly out to assist other worlds on their work. “Web-Slinger, Earth 2038, he’s reported his guns are missing,” He said one day, leaving Marie at her small charging disk in his highly advanced office. He taps at the large screen of his watch, “You know the drill, keep the security up.”
It wasn’t uncommon for him to leave her, although the security systems in 2099 were forces to be reckoned with, she had been quite useful from time to time as backup. Her small holographic form sits against a keyboard behind her, a brow raised. She’s an odd little thing, faintly blue tinted in a short dress and a long fur lined jacket, her almost geometric curls make her look like she’s directly out of a game.
“Gotcha, you know where to call if you need me,” Marie’s voice is layered with a hint of static, but Miguel has grown used to it. With a nod and a swipe on his watch, a grand orange portal opens behind him, and he steps in without another word.
Maybe Marie would let herself shut down, get some rest before Spider-Man returned. In a quick scan over Alchemax’s security, she looks over the readings from other dimensions’ artifacts. There seemed to be one too many, but she could’ve sworn she saw Miguel bring something back from their last mission. She sits crisscrossed on her hardware disk, letting her eyes flutter closed as she leans her head back. She wouldn’t shut down her hologram just yet, however. She liked “existing,” enjoyed the feeling of being a part of the world around her. That’s where much of her intelligent capacity had been spent on, trying to appreciate life and cataloging emotions. She’s gotten much better at expressing the latter.
The faint sound of footsteps can be heard in the bowels of the office. Marie let her form flicker in and out of view, peacefully assuming that the footsteps just belonged to Miguel’s brother. The sound belongs to boots, but they aren’t heavy, they’re strangely light. Before her systems can process the intruder, a black glove reaches from between Miguel’s bottom monitors, phasing right through her hologram and grabbing her base disk.
“Hey! Who-“ Her form clips through the hand, and she pretends to hold on for dear life. She’s met with an unfamiliar face, accented with bright green tinted goggles and wild curls. They smile and flip their hand, sending Marie’s hologram to the other side of the disk.
“Look at you, how are you contained in this thing anyways?” The woman keeps her voice low as she takes slow, measured steps back away from Miguel’s desk. Marie quickly waves her hand to the side, attempting to bring up one of the small screens she’d use to help Miguel. “No, no, don’t try that.“ The other gloved hand comes up to flick Marie’s outstretched arm, “Did you seriously think I wouldn’t sever your connection? I could’ve sworn you were smarter than that!”
Almost alien tentacles rise behind the woman’s back, the end claw of one slithering down to tap at something on the side of her metal corset. Marie glances around, her programming spinning as she tries to take in the villain before her. Doctor Octopus, that’s all she could pin down before the hand on her disk squeezes and she’s forced to shut down.
Her world went dark, but her mind didn’t. Whenever she “slept,” whenever she was off, she could see into all the backups of her system, and there were a lot. But her little dream is cut off almost instantly, and she was shaken up by a clear difference in her surroundings, a clear difference in the very universe around her.
When Marie reboots, she’s met with sharp fluorescent lights and a bright white room. It was nearly the opposite of Miguel’s office, but its tech almost rivaled his. The room was messy, with out of place items lying here and there. Her hologram is lying flat on a table, and her hardware to the side. She’s trying to process her surroundings, but she’s unable to pinpoint the exact universe she’s been taken to. Wait, her hardware! Her hologram glitches when she stands, and she spins around to see that a hidden port on one side has been plugged into a desktop, one that’s much more modest than Miguel’s wall of screens. It’s just small enough be able to slip into Miguel’s watch, but it’s still susceptible to outside interference.
The doctor who took it is sat right there, her goggles pulled down to hang around her neck. “Earth 1620,” She says simply, sharp hazel eyes glancing down to the doll-like hologram on her desktop, “I’m sure that jump scrambled your circuits, hm?” Her hands leave the keyboard, and she rests an elbow in front of it. She’s in the same odd suit, soft green silicone with sleek latex, but now a lab coat has been haphazardly thrown over it.
“What is your problem?!” Marie raises her voice, the sound coming from both her glowing form and her hardware.
“Problem? I’m just curious!” Doc Ock snickers. She brings her free hand back to Marie, poking her harmlessly. The villain rests her cheek in her palm as she prods at Marie, her smile oddly radiant. “I’m sure Spider-Man has a few copies of you lying around, he won’t mind.”
He did, but Marie didn’t want to think she was just replaceable. She bats at the hand, and even though she only phases through it, she hopes the gesture is noticed. “Who even are you? I’ve only ever seen an Otto and a Carolyn.”
“Olivia, that’s who,” The answer is simple, spoken with a sense of purpose that Marie should’ve recognized. Olivia lifts her head to hold her right hand over the keyboard. “But I’ll give you all the data you need in a moment.”
“You know you can just tell me, right? Dozens of Spiders could burst in at any moment!” Marie gestures around at nothing, a strange hint of confusion in her mechanical voice. “Why take me?”
Olivia taps Marie’s head with just her index finger before lowering it to where her heart would be. “Because you’re the smartest little assistant in the closest hundred dimensions, and I could use some extra little hands. Besides, Miguel will come back home to one of your backup systems once he’s done finding those guns ten worlds away.” She clicks enter on her keyboard, activating what Marie can only guess is new code to override her hardware. It hits her like a shock, and she can’t help but let out a little shout. The “update” is instantaneous, and the main effect is obvious. She can feel.
“I’ve cut off contact to the Spiders, just because I won’t be hurting them,” Olivia smiles again, her expression not as malicious as Marie would expect. “And I’ve integrated you with the Alchemax systems, as well as with a few other devices I’ve borrowed from some Earths,” Now that Marie couldn’t call for help, Olivia was clearly much more excited to spill her plans to someone, or something. Clearly, she’s saving the biggest change for last. Her finger presses into Marie’s chest, but rather than phasing through, it stops. “And you’ve got touch sensors now, isn’t that neat? I found the code dormant in your system… I guess your ‘boss’ didn’t want you to get ahead of yourself.”
Marie, only being around the size of a phone, is clearly overwhelmed by the new sense. She brings her hands up to Olivia’s hand, her brows furrowing as she holds it. She can feel the faint weight of her jacket, the cool desktop pressing against the bottom of her shoes, and the painless touch against her chest. Her head is racing, if Olivia activated that code, what if she only planned to hurt her? It didn’t seem too bad for now, and there would have to be a way for her to disable it at times, but it was still worrying.
“How the hell did you access that?” Is all she can manage to ask as she still holds on to the doctor.
“You’re Alchemax tech, we’ve got similar systems in every world!” Olivia’s tone has lightened quite a bit, but she’s quick to switch back into that villain persona. She presses her finger in a bit more, her other hand hovering over the keyboard. “But I can track those systems, and shut them down just as quickly as I activated them. Neat, isn’t it? There’s loooots of old fail safes in case you ever grew self aware, but I suppose it’s too late for that, so I’ll just keep them remote.”
Olivia pulls away her left hand and types in a few more short commands. In a split second, a birdcage of Marie’s same color flickers to life around her. It’s clearly a hologram as well, but it’s tangible, at least to her. She grabs onto the bars, but they’re gone as quickly as they came.
“Why in the world would those be necessary now?!” Marie takes a few steps back, but not exactly out of fear.
Olivia just shrugs and rolls her eyes, “I can think of a few reasons, but they’re all quite… Out there.” Marie just frowns in response, and rather than being met with a new program, Olivia just fully turns to face her.
“Let me guess, you’ll lock me up if I don’t help y-“ Marie’s complaint is cut off, and she shrieks when Olivia scoops her up like a baby bird. She glows against the dark leather gloves, and for the first time, she doesn’t just fall through.
“Maybe, maybe not,” Olivia narrows her gaze, studying the blue tinted hologram. “I just wanted a new project, simple as that.”
•
I don’t think I’m going to be writing more for this, unfortunately. But while the book ends with doc ock being defeated and Lyla being saved. Liv was right in this au, she gets to keep a little robot doll while another version goes on as usual back in that universe. She also teaches Marie how to feel, in more ways than just touch, but I’m tired and can’t write that much rn
#oc x canon#self ship#selfship#selfship writing#writing#🐚#selfship au#selfship community#f/o community#romantic f/o#f/o#villain f/o#yumejoshi#༺ Shell & Spine ༻
22 notes
·
View notes
Text
سوئیچ شبکه مدیرتی را چطور کانفیگ کنیم؟
کانفیگ سوئیچ شبکه در سیستم های مدیریتی اهمیت بسیار زیادی دارد؛ زیرا مانع دسترسی افراد غیر مجاز می شود. دقت داشته باشید که پس از خریداری دستگاه می توانید آن را بدون تنظیمات مورد استفاده قرار دهید. اما اگر می خواهید یک سری پیکربندی ها را بر روی آن انجام دهید، لازم است خودتان سوئیچ را تنظیم نمایید. در ادامه همراه امدادکار باشید، تا شما را با مراحل انجام این کار به طور کامل آشنا کنیم.
سوئیچ شبکه مدیریتی چیست و چگونه پیکربندی میشود
با گسترش شبکههای کامپیوتری در سازمانها و منازل، انتخاب تجهیزات مناسب برای مدیریت ترافیک اهمیت زیادی دارد. یکی از مهمترین تجهیزات، سوئیچ مدیریتی (Managed Switch) است. این نوع سوئیچ به مدیر شبکه اجازه میدهد تنظیمات پیشرفتهای را انجام داده و کنترل کاملتری بر عملکرد شبکه داشته باشد. سوئیچ مدیریتی نوعی از سوئیچ شبکه است که به کاربر اجازه میدهد از طریق رابط های مدیریتی (مانند Web GUI، CLI یا SNMP) تنظیمات متنوعی را روی پورتها، VLAN، امنیت و ترافیک اعمال کند.
سوئیچ مدیریتی یک دستگاه لایه ۲ یا ۳ است که به مدیر شبکه اجازه میدهد تنظیمات پیشرفتهای را روی پورتها، ترافیک و امنیت شبکه اعمال کند. این سوئیچ ها معمولاً از طریق رابط های کاربری مانند CLI (Command Line Interface) یا Web GUI قابل دسترسی هستند. بهترین سوئیچ شبکه (Network Switch) یکی از اصلیترین تجهیزات در زیرساخت شبکههای کامپیوتری است که وظیفه انتقال دادهها بین دستگاههای مختلف را بر عهده دارد. اما همه سوئیچها شبیه به هم نیستند؛ انواع مختلفی از سوئیچ ها وجود دارند که بر اساس سطح عملکرد، قابلیت مدیریت، محل استفاده و نوع دادهپردازی دستهبندی میشوند.
سوئیچ شبکه (Network Switch) قلب تپندهی شبکههای محلی (LAN) است. این دستگاه به رایانهها، سرورها، دوربینهای مداربسته، چاپگرها و سایر دستگاههای متصل به شبکه امکان میدهد با هم ارتباط برقرار کنند. اما بسته به اندازه و پیچیدگی شبکه، انواع مختلفی از سوئیچها وجود دارد که هرکدام قابلیتها و کاراییهای متفاوتی دارند. سوئیچ یک دستگاه لایه ۲ (و گاهی لایه ۳) در مدل OSI است که دادهها را بر اساس MAC Address به مقصد مناسب ارسال میکند. برخلاف هاب (Hub)، سوئیچها ترافیک شبکه را بهصورت هوشمند هدایت میکنند و باعث کاهش تصادم و افزایش سرعت شبکه میشوند.
معرفی انواع سوئیچ شبکه و کارایی آن
دسته بندی انواع سوئیچ شبکه بر اساس قابلیت مدیریت بوده به این گونه که بر اساس قابلیت مدیریت: سوئیچ غیرمدیریتی (Unmanaged Switch) که بدون نیاز به تنظیم یا پیکربندی و فقط Plug and Play انجام میشود که مناسب برای خانه یا شبکه های بسیار کوچک بوده و بدون پشتیبانی از VLAN، اولویت بندی یا امنیت پورت میشود و قابلیت های این سوئیچ شبکه محدود بوده و اتصال سریع و ساده دستگاهها را برای کاربران به ارمغان می آورد.
سوئیچ هوشمند یا نیمه مدیریتی (Smart Switch) که پشتیبانی جزئی از ویژگی های مدیریتی مثل VLAN، QoS، محدودسازی پهنای باند بوده است. پیکر بندی آن از طریق رابط وب و مناسب برای کسب و کارهای کوچک و متوسط بوده و قابلیت های آن محدود بوده که بهینه سازی ترافیک و کنترل ساده شبکه را به همراه دارد.
سوئیچ مدیریتی (Fully Managed Switch) که کنترل کامل بر روی پورتها، VLANها، امنیت، SNMP، Spanning Tree و ... را به عهده دارد که با پشتیبانی از CLI (خط فرمان)، SSH، Telnet و SNMP را انجام میدهد که مناسب برای شبکه های سازمانی، دیتاسنترها و زیر ساخت های بزرگ با قابلیت های پیشرفته بوده و کارایی این نوع سوئیچ شبکه در مدیریت، مانیتورینگ و امن سازی شبکه ��ه صورت حرفه ای بوده است.
سوئیچ لایه ۲ (Layer 2 Switch) که ارسال دادهها در این نوع سوئیچ بر اساس آدرس MAC بوده و رایج ترین نوع سوئیچ در شبکه های LAN بوده که مناسب برای شبکه های دسترسی یا Access Layer میباشد که قابلیتهایی همچون: VLAN، Port Security، Spanning Tree را به عهده دارد که کارایی تفکیک ترافیک در سطح LAN را به عهده دارند.
سوئیچ لایه ۳ (Layer 3 Switch) که ترکیب سوئیچ و روتر بوده و پشتیبانی از مسیریابی بین VLANها (Inter-VLAN Routing) را به عهده دارد که مناسب برای Backbone یا Core Network با داشتن قابلیتهای: Static/Dynamic Routing، ACL، Multicast Routing میباشد و کارایی آن انتقال ترافیک بین بخش های مختلف شبکه میباشد.
سوئیچ PoE (Power over Ethernet) که از مهم ترین سوئیچ ها بوده که وظیفه آن ارسال برق و دیتا همزمان از طریق کابل شبکه بوده است و مناسب برای دوربین IP، تلفن VoIP، Access Point با همراهی قابلیت های PoE/PoE+، پیکربندی ولتاژ، مدیریت مصرف میباشد که کارایی آن در کاهش کابل کشی و ساده سازی نصب دستگاه ها میباشد.
سوئیچ صنعتی (Industrial Switch) که مقاوم در برابر دما، گردوغبار، رطوبت و ضربه بوده و قابل نصب در محیط های صنعتی، کارخانهها، فضای باز میباشد. قابلیتهای آن: طراحی سختافزاری مقاوم، PoE، DIN Rail Mount میباشد و پایداری شبکه در محیط های سخت و غیر قابل پیشبینی را برای کاربران تضمین میکند.
سوئیچ PoE چیست و چه مزایایی دارد؟
با پیشرفت فناوری شبکه، دستگاههای بیشتری مانند دوربینهای مداربسته (IP Camera)، تلفنهای VoIP و اکسسپوینتهای وایفای به شبکه متصل میشوند. در این میان، یکی از دغدغههای مهم، تأمین برق این تجهیزات در کنار انتقال دادههاست. سوئیچ PoE نوعی سوئیچ شبکه است که علاوه بر انتقال داده، توانایی ارسال برق به دستگاههای متصل به خود را دارد. این برق از طریق کابلهای استاندارد Cat5e، Cat6 یا Cat7 ارسال میشود.
نیازی به نصب پریز برق یا آداپتور مجزا برای هر دستگاه ندارید. این موضوع باعث صرفهجویی در هزینه، زمان و فضا میشود. فقط کافی است یک کابل شبکه به دستگاه متصل شود. بدون نیاز به نصاب برق یا متخصص برقکشی. تجهیزاتی مثل دوربین یا اکسسپوینت را میتوانید در هر مکانی نصب کنید، حتی اگر آنجا پریز برق وجود نداشته باشد. با استفاده از سوئیچ PoE مدیریتی، میتوانید برق دستگاهها را از راه دور روشن، خاموش یا ریست کنید. PoE به صورت هوشمند میزان برق موردنیاز دستگاه را تشخیص میدهد و فقط در صورت نیاز برق را ارسال میکند. از آسیب به دستگاههای غیر PoE جلوگیری میشود.
با کمتر شدن تعداد کابلها و ساده شدن ساختار شبکه، هزینههای نگهداری کاهش پیدا میکند. خود این سوئیچ شبکه POE دارای دارای انواع مختلف میباشد. سوئیچ PoE یک ابزار حیاتی برای سادهسازی و بهینهسازی نصب تجهیزات شبکه مدرن است. با حذف کابل برق، کاهش هزینه نصب، و افزایش انعطاف در ��راحی شبکه، استفاده از این سوئیچها بهخصوص در پروژههای نظارتی، وایرلس و VoIP بسیار توصیه میشود. اگر در حال طراحی یا ارتقاء شبکه خود هستید، استفاده از یک سوئیچ PoE با توان مناسب و ویژگیهای مدیریتی میتواند یک انتخاب هوشمندانه و آیندهنگرانه باشد.
1 note
·
View note
Text
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ, a fintech company that provides an AI-powered blockchain ecosystem, has launched its operations in the Indian market.
The company provides an AI-powered blockchain ecosystem that offers integrated solutions spanning the blockchain layer 1, native coin, exchange services, MPC wallet, DeFi, NFT, gaming and other products.
It has established its headquarters in Mumbai, with additional offices in Delhi, Bengaluru, and Kolkata.
Leveraging AI, CIFDAQ ecosystem aims to enhance traditional frameworks, merging them with the decentralized web of blockchain. This initiative seeks to balance centralized governmental frameworks with the decentralized economy, emphasizing transparency, security, scalability, and synergy with established economic systems.
Impact on the blockchain landscape
With its launch in India, The company aims to revolutionize the blockchain ecosystem by introducing cutting-edge solutions that promote security, efficiency, and accessibility.
It will focus on empowering businesses and individuals, thereby driving growth and fostering a more inclusive and prosperous future through blockchain technology. Notably, The move will unlock the full potential of blockchain technology, making it more accessible and beneficial for a wider audience.
CIFDAQ’s innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, decentralized economy, and users’ interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
Leadership comments
Himanshu Maradiya, the Founder & Chairman of CIFDAQ, said, "We are thrilled to embark on this new chapter of CIFDAQ's journey as we set foot in the vibrant and dynamic Indian market. Our innovative solutions are poised to address the unique challenges and opportunities present in India's blockchain and digital finance ecosystem. We aim to empower businesses and individuals with enhanced security and efficiency, driving growth and innovation across various sectors."
His son, Rahul Maradiya, Co-Founder and Global CEO of CIFDAQ, said, "We envision CIFDAQ as a catalyst for change, empowering businesses and individuals with cutting-edge solutions that enhance security, efficiency, and accessibility in the digital finance space. Our goal is to revolutionize the blockchain ecosystem and unlock its full potential, paving the way for a more inclusive and prosperous future."
For more information about CIFDAQ, please visit https://linktr.ee/cifdaq
CIFDAQ - The Evolution of Innovative Blockchain Ecosystem powered by AI, is a new-age fintech company that offers integrated solutions spanning the Blockchain Layer 1, Native Coin, Exchange Services, MPC Wallet, DeFi, NFT, Gaming, and other products. CIFDAQ's innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, a decentralized economy, and users' interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
CIFDAQ Blockchain Ecosystem consists of several modules and products that will be inter-connected by an innovative tool called $CIFD Coin.
$CIFD Coin will serve as the engine of each, and every product and module introduced by CIFDAQ - the evolution of an innovative blockchain ecosystem. Additionally, it will have its utility across the CIFDAQ ecosystem, making it the heart of everything CIFDAQ has to offer.
www.cifdaq.com
0 notes
Text
How to Create a Custom Blockchain for Your Cryptocurrency
Blockchain technology has revolutionized industries by enabling decentralized and secure transactions. If you're planning to create a cryptocurrency, developing a custom blockchain is a crucial step that offers complete control over functionalities, security, and governance. This guide will walk you through the key steps to creating a blockchain from scratch for your cryptocurrency.

1. Understanding the Need for a Custom Blockchain
Before diving into development, consider why you need a custom blockchain instead of using existing ones like Ethereum, Binance Smart Chain, or Solana. Here are some reasons:
Full Control: A custom blockchain allows complete customization of consensus mechanisms, transaction speeds, security measures, and governance models.
Scalability: Public blockchains can face congestion. A custom blockchain can be optimized for specific use cases.
Security: Control over cryptographic standards and node management improves security.
Unique Features: You can integrate smart contracts, privacy settings, and tokenomics tailored to your project’s needs.
2. Choose the Blockchain Architecture
There are different blockchain architectures to consider:
Public Blockchain: Open to anyone (e.g., Bitcoin, Ethereum). Suitable for decentralized cryptocurrencies.
Private Blockchain: Restricted access, ideal for enterprises and private transactions.
Consortium Blockchain: Partially decentralized, controlled by a group of entities. Useful for inter-organizational networks.
For a cryptocurrency, a public blockchain is the most common choice to ensure decentralization.
3. Select a Consensus Mechanism
The consensus mechanism determines how transactions are validated. Popular options include:
Proof of Work (PoW): Used by Bitcoin, requires computational power for mining, making it secure but energy-intensive.
Proof of Stake (PoS): Used by Ethereum 2.0, validators stake tokens instead of mining, reducing energy consumption.
Delegated Proof of Stake (DPoS): A variant of PoS where users vote for validators. Faster and more scalable.
Proof of Authority (PoA): Suitable for private blockchains, where only authorized nodes validate transactions.
For a cryptocurrency development, PoS or DPoS is preferred due to lower energy consumption and faster transaction speeds.
4. Define Tokenomics and Governance
Your blockchain must have a well-defined tokenomics model, which includes:
Total Supply: Fixed (like Bitcoin’s 21M supply) or inflationary (like Ethereum’s unlimited issuance).
Mining/Staking Rewards: How validators earn rewards.
Transaction Fees: Flat or dynamic fees based on network demand.
Token Utility: Usage within the ecosystem (payments, governance, staking, etc.).
Governance Model: Decision-making mechanisms (centralized, decentralized, DAO-based).
5. Develop the Blockchain Core
To create your blockchain, you need programming knowledge in C++, Python, Rust, or Go. Key steps include:
1. Set Up a P2P Network
Define how nodes communicate and sync transactions.
Implement node discovery and connection protocols.
2. Implement Cryptographic Security
Use cryptographic hashing (SHA-256, Keccak) for transaction security.
Implement digital signatures and key management for wallets.
3. Develop Smart Contracts (If Needed)
If your blockchain supports dApps, create a smart contract execution layer (like Ethereum’s EVM).
Use Solidity, Rust, or Vyper for smart contract coding.
4. Create a Block Structure
Each block should contain:
Block header (timestamp, previous block hash, nonce)
List of transactions
Merkle root (for transaction verification)
5. Implement Consensus Mechanism
Code the rules for PoS, PoW, or other mechanisms.
Design validator selection and slashing conditions (for PoS-based chains).
6. Build a Wallet and Explorer
1. Cryptocurrency Wallet
A user-friendly interface for sending, receiving, and storing tokens.
Can be web-based, mobile, or hardware-based.
Use cryptographic libraries (like OpenSSL, Bouncy Castle) for security.
2. Blockchain Explorer
A tool for tracking transactions and network activity.
Develop using web frameworks like React, Angular, or Vue.
Connect with blockchain nodes via API to fetch real-time data.
7. Deploy Nodes and Secure the Network
1. Launch Full Nodes
Deploy nodes globally to increase network decentralization.
Use cloud services (AWS, Google Cloud, Digital Ocean) or self-hosted servers.
2. Implement Security Measures
51% Attack Protection: Implement hybrid consensus or checkpointing.
DDoS Protection: Use rate limiting, node whitelisting, and traffic monitoring.
Private Key Security: Secure wallets with multi-signature authentication.
8. Test the Blockchain
Before launching publicly, conduct thorough testing:
Unit Testing: Test individual blockchain components.
Testnet Deployment: Deploy a testnet for real-world simulations.
Bug Bounties: Offer incentives to developers for finding vulnerabilities.
9. Mainnet Launch and Community Building
Once testing is complete:
Launch the Mainnet: Transition from testnet to a fully operational blockchain.
List on Exchanges: Partner with crypto exchanges for liquidity.
Build a Community: Promote adoption through social media, forums, and partnerships.
Continuous Updates: Improve scalability, security, and user experience over time.
Conclusion
Creating a custom blockchain for your cryptocurrency is a complex but rewarding process. By defining your architecture, choosing the right consensus mechanism, implementing security measures, and engaging the community, you can build a scalable and secure blockchain ecosystem. Whether you aim for financial transactions, decentralized applications, or enterprise solutions, a well-designed blockchain can drive long-term success.
0 notes
Text
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ, a fintech company that provides an AI-powered blockchain ecosystem, has launched its operations in the Indian market.The company provides an AI-powered blockchain ecosystem that offers integrated solutions spanning the blockchain layer 1, native coin, exchange services, MPC wallet, DeFi, NFT, gaming and other products.It has established its headquarters in Mumbai, with additional offices in Delhi, Bengaluru, and Kolkata.Leveraging AI, CIFDAQ ecosystem aims to enhance traditional frameworks, merging them with the decentralized web of blockchain. This initiative seeks to balance centralized governmental frameworks with the decentralized economy, emphasizing transparency, security, scalability, and synergy with established economic systems.
Impact on the blockchain landscape With its launch in India, The company aims to revolutionize the blockchain ecosystem by introducing cutting-edge solutions that promote security, efficiency, and accessibility.It will focus on empowering businesses and individuals, thereby driving growth and fostering a more inclusive and prosperous future through blockchain technology. Notably, The move will unlock the full potential of blockchain technology, making it more accessible and beneficial for a wider audience.CIFDAQ’s innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, decentralized economy, and users’ interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
Leadership comments Himanshu Maradiya, the Founder & Chairman of CIFDAQ, said, "We are thrilled to embark on this new chapter of CIFDAQ's journey as we set foot in the vibrant and dynamic Indian market. Our innovative solutions are poised to address the unique challenges and opportunities present in India's blockchain and digital finance ecosystem. We aim to empower businesses and individuals with enhanced security and efficiency, driving growth and innovation across various sectors."
His son, Rahul Maradiya, Co-Founder and Global CEO of CIFDAQ, said, "We envision CIFDAQ as a catalyst for change, empowering businesses and individuals with cutting-edge solutions that enhance security, efficiency, and accessibility in the digital finance space. Our goal is to revolutionize the blockchain ecosystem and unlock its full potential, paving the way for a more inclusive and prosperous future."
For more information about CIFDAQ, please visit https://linktr.ee/cifdaq
CIFDAQ - The Evolution of Innovative Blockchain Ecosystem powered by AI, is a new-age fintech company that offers integrated solutions spanning the Blockchain Layer 1, Native Coin, Exchange Services, MPC Wallet, DeFi, NFT, Gaming, and other products. CIFDAQ's innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, a decentralized economy, and users' interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.CIFDAQ Blockchain Ecosystem consists of several modules and products that will be inter-connected by an innovative tool called $CIFD Coin.
$CIFD Coin will serve as the engine of each, and every product and module introduced by CIFDAQ - the evolution of an innovative blockchain ecosystem. Additionally, it will have its utility across the CIFDAQ ecosystem, making it the heart of everything CIFDAQ has to offer.
www.cifdaq.com
0 notes
Text
Demystifying AWS Virtual Private Cloud (VPC)
In the ever-evolving world of cloud computing, Amazon Web Services (AWS) has established itself as a leader, offering a wide array of services to meet diverse business needs. Among these services, the Virtual Private Cloud (VPC) is one of the most crucial components for organizations seeking to enhance their security and control over their cloud resources. This blog post provides a comprehensive guide to AWS VPC, exploring its features, benefits, and best practices.
If you want to advance your career at the AWS Course in Pune, you need to take a systematic approach and join up for a course that best suits your interests and will greatly expand your learning path.

What is AWS VPC?
AWS Virtual Private Cloud (VPC) allows users to create a private, isolated section of the AWS cloud where they can launch and manage AWS resources. VPC enables businesses to control their virtual networking environment, including IP address ranges, subnets, routing, and security settings.
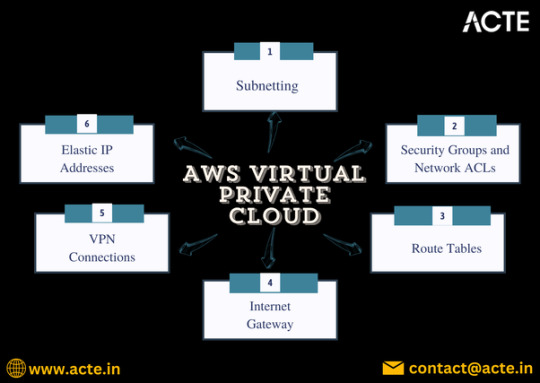
Key Features of AWS VPC
Custom IP Address Range:
When creating a VPC, you can define your own IP address range using Classless Inter-Domain Routing (CIDR) notation. This flexibility allows you to tailor your network architecture to your specific needs.
2. Subnets:
VPCs can be divided into subnets, which are smaller segments within the VPC. You can create public subnets (accessible from the internet) and private subnets (not directly accessible from the internet) to optimize resource security.
3. Security Groups and Network ACLs:
Security groups act as virtual firewalls for your instances, controlling inbound and outbound traffic. Network Access Control Lists (ACLs) provide an additional layer of security at the subnet level, enabling more granular traffic management.
4. Route Tables:
Route tables are used to determine where network traffic is directed. You can create custom routing rules to control the flow of traffic between your VPC, subnets, and the internet.
5. Internet Gateway and NAT Gateway:
An Internet Gateway allows communication between instances in your VPC and the internet. A NAT Gateway enables instances in a private subnet to initiate outbound traffic while preventing unsolicited inbound traffic.
6. VPN Connections and AWS Direct Connect:
VPC supports VPN connections, allowing secure communication between your on-premises network and your VPC. AWS Direct Connect provides a dedicated network connection, improving performance and reliability.
7. Elastic IP Addresses:
Elastic IPs are static IP addresses that can be associated with your instances, ensuring consistent public IP addresses even when instances are stopped and restarted.
To master the intricacies of AWS and unlock its full potential, individuals can benefit from enrolling in the AWS Online Training.
Benefits of Using AWS VPC
Enhanced Security:
By isolating your resources within a VPC, you gain greater control over your network security. You can implement security measures tailored to your specific needs, enhancing data protection and compliance.
Flexibility:
AWS VPC provides the flexibility to design your network architecture according to your requirements. You can easily adjust your IP address ranges, subnets, and security settings.
Scalability:
VPCs are designed to scale seamlessly. You can add or remove resources as needed, ensuring your infrastructure can adapt to changing workloads without performance degradation.
Cost Efficiency:
With AWS's pay-as-you-go pricing model, you only pay for the resources you use. This makes VPC an economically viable option for organizations of all sizes.
Integration with Other AWS Services:
VPC integrates seamlessly with various AWS services, including Amazon EC2, RDS, and Lambda, allowing you to build comprehensive cloud solutions that meet your business needs.
Conclusion
AWS Virtual Private Cloud (VPC) is a vital service for businesses looking to secure and manage their cloud resources effectively. With its extensive features and benefits, VPC empowers organizations to create a customized and controlled network environment.
By understanding how to leverage VPC and adhering to best practices, businesses can maximize their cloud investment and ensure a robust, secure infrastructure. Whether you're new to AWS or looking to enhance your existing setup, mastering AWS VPC is crucial for success in the cloud.
0 notes
Text
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ, a fintech company that provides an AI-powered blockchain ecosystem, has launched its operations in the Indian market.
The company provides an AI-powered blockchain ecosystem that offers integrated solutions spanning the blockchain layer 1, native coin, exchange services, MPC wallet, DeFi, NFT, gaming and other products.
It has established its headquarters in Mumbai, with additional offices in Delhi, Bengaluru, and Kolkata.
Leveraging AI, the CIFDAQ ecosystem aims to enhance traditional frameworks, merging them with the decentralized web of blockchain. This initiative seeks to balance centralized governmental frameworks with the decentralized economy, emphasizing transparency, security, scalability, and synergy with established economic systems.
Impact on the Blockchain Landscape
With its launch in India, The company aims to revolutionize the blockchain ecosystem by introducing cutting-edge solutions that promote security, efficiency, and accessibility.
It will focus on empowering businesses and individuals, thereby driving growth and fostering a more inclusive and prosperous future through blockchain technology. Notably, The move will unlock the full potential of blockchain technology, making it more accessible and beneficial for a wider audience.
CIFDAQ’s innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, decentralized economy, and users’ interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
Leadership comments
Himanshu Maradiya, the Founder & Chairman of CIFDAQ, said, "We are thrilled to embark on this new chapter of CIFDAQ's journey as we set foot in the vibrant and dynamic Indian market. Our innovative solutions are poised to address the unique challenges and opportunities present in India's blockchain and digital finance ecosystem. We aim to empower businesses and individuals with enhanced security and efficiency, driving growth and innovation across various sectors."
His son, Rahul Maradiya, Co-Founder and Global CEO of CIFDAQ, said, "We envision CIFDAQ as a catalyst for change, empowering businesses and individuals with cutting-edge solutions that enhance security, efficiency, and accessibility in the digital finance space. Our goal is to revolutionize the blockchain ecosystem and unlock its full potential, paving the way for a more inclusive and prosperous future."
For more information about CIFDAQ, please visit https://linktr.ee/cifdaq
CIFDAQ - The Evolution of Innovative Blockchain Ecosystem powered by AI, is a new-age fintech company that offers integrated solutions spanning the Blockchain Layer 1, Native Coin, Exchange Services, MPC Wallet, DeFi, NFT, Gaming, and other products. CIFDAQ's innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, a decentralized economy, and users' interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
CIFDAQ Blockchain Ecosystem consists of several modules and products that will be inter-connected by an innovative tool called $CIFD Coin.
$CIFD Coin will serve as the engine of each, and every product and module introduced by CIFDAQ - the evolution of an innovative blockchain ecosystem. Additionally, it will have its utility across the CIFDAQ ecosystem, making it the heart of everything CIFDAQ has to offer.
#CIFDAQ#BITCOIN#CRYPTOINVESTING#BLOCKCHAIN#WEB3COMMUNITY
www.cifdaq.com
0 notes
Text
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ, a fintech company that provides an AI-powered blockchain ecosystem, has launched its operations in the Indian market.
The company provides an AI-powered blockchain ecosystem that offers integrated solutions spanning the blockchain layer 1, native coin, exchange services, MPC wallet, DeFi, NFT, gaming and other products.
It has established its headquarters in Mumbai, with additional offices in Delhi, Bengaluru, and Kolkata.
Leveraging AI, CIFDAQ ecosystem aims to enhance traditional frameworks, merging them with the decentralized web of blockchain. This initiative seeks to balance centralized governmental frameworks with the decentralized economy, emphasizing transparency, security, scalability, and synergy with established economic systems.
Impact on the blockchain landscape
With its launch in India, The company aims to revolutionize the blockchain ecosystem by introducing cutting-edge solutions that promote security, efficiency, and accessibility.
It will focus on empowering businesses and individuals, thereby driving growth and fostering a more inclusive and prosperous future through blockchain technology. Notably, The move will unlock the full potential of blockchain technology, making it more accessible and beneficial for a wider audience.
CIFDAQ’s innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, decentralized economy, and users’ interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
Leadership comments
Himanshu Maradiya, the Founder & Chairman of CIFDAQ, said, "We are thrilled to embark on this new chapter of CIFDAQ's journey as we set foot in the vibrant and dynamic Indian market. Our innovative solutions are poised to address the unique challenges and opportunities present in India's blockchain and digital finance ecosystem. We aim to empower businesses and individuals with enhanced security and efficiency, driving growth and innovation across various sectors."
His son, Rahul Maradiya, Co-Founder and Global CEO of CIFDAQ, said, "We envision CIFDAQ as a catalyst for change, empowering businesses and individuals with cutting-edge solutions that enhance security, efficiency, and accessibility in the digital finance space. Our goal is to revolutionize the blockchain ecosystem and unlock its full potential, paving the way for a more inclusive and prosperous future."
For more information about CIFDAQ, please visit https://linktr.ee/cifdaq
CIFDAQ - The Evolution of Innovative Blockchain Ecosystem powered by AI, is a new-age fintech company that offers integrated solutions spanning the Blockchain Layer 1, Native Coin, Exchange Services, MPC Wallet, DeFi, NFT, Gaming, and other products. CIFDAQ's innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, a decentralized economy, and users' interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
CIFDAQ Blockchain Ecosystem consists of several modules and products that will be inter-connected by an innovative tool called $CIFD Coin.
$CIFD Coin will serve as the engine of each, and every product and module introduced by CIFDAQ - the evolution of an innovative blockchain ecosystem. Additionally, it will have its utility across the CIFDAQ ecosystem, making it the heart of everything CIFDAQ has to offer.
CIFDAQ#BITCOIN#CRYPTOINVESTING#BLOCKCHAIN#WEB3COMMUNITY
www.cifdaq.com
0 notes
Text
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
Written by Himanshu Maradiya
CIFDAQ, a fintech company that provides an AI-powered blockchain ecosystem, has launched its operations in the Indian market.
The company provides an AI-powered blockchain ecosystem that offers integrated solutions spanning the blockchain layer 1, native coin, exchange services, MPC wallet, DeFi, NFT, gaming and other products.
It has established its headquarters in Mumbai, with additional offices in Delhi, Bengaluru, and Kolkata.
Leveraging AI, CIFDAQ ecosystem aims to enhance traditional frameworks, merging them with the decentralized web of blockchain. This initiative seeks to balance centralized governmental frameworks with the decentralized economy, emphasizing transparency, security, scalability, and synergy with established economic systems.
Impact on the blockchain landscape
With its launch in India, The company aims to revolutionize the blockchain ecosystem by introducing cutting-edge solutions that promote security, efficiency, and accessibility.
It will focus on empowering businesses and individuals, thereby driving growth and fostering a more inclusive and prosperous future through blockchain technology. Notably, The move will unlock the full potential of blockchain technology, making it more accessible and beneficial for a wider audience.
CIFDAQ’s innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, decentralized economy, and users’ interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
Leadership comments
Himanshu Maradiya, the Founder & Chairman of CIFDAQ, said, "We are thrilled to embark on this new chapter of CIFDAQ's journey as we set foot in the vibrant and dynamic Indian market. Our innovative solutions are poised to address the unique challenges and opportunities present in India's blockchain and digital finance ecosystem. We aim to empower businesses and individuals with enhanced security and efficiency, driving growth and innovation across various sectors."
His son, Rahul Maradiya, Co-Founder and Global CEO of CIFDAQ, said, "We envision CIFDAQ as a catalyst for change, empowering businesses and individuals with cutting-edge solutions that enhance security, efficiency, and accessibility in the digital finance space. Our goal is to revolutionize the blockchain ecosystem and unlock its full potential, paving the way for a more inclusive and prosperous future."
For more information about CIFDAQ, please visit https://linktr.ee/cifdaq
CIFDAQ - The Evolution of Innovative Blockchain Ecosystem powered by AI, is a new-age fintech company that offers integrated solutions spanning the Blockchain Layer 1, Native Coin, Exchange Services, MPC Wallet, DeFi, NFT, Gaming, and other products. CIFDAQ's innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, a decentralized economy, and users' interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
CIFDAQ Blockchain Ecosystem consists of several modules and products that will be inter-connected by an innovative tool called $CIFD Coin.
$CIFD Coin will serve as the engine of each, and every product and module introduced by CIFDAQ - the evolution of an innovative blockchain ecosystem. Additionally, it will have its utility across the CIFDAQ ecosystem, making it the heart of everything CIFDAQ has to offer.
0 notes
Text
what is site to site vpn connection
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is site to site vpn connection
Site-to-Site VPN Protocol
A Site-to-Site VPN Protocol is a crucial component for secure data transmission between two or more networks over the internet. It enables organizations to establish encrypted connections, ensuring confidentiality and integrity of their communication.
One of the most widely used Site-to-Site VPN protocols is IPsec (Internet Protocol Security). IPsec operates at the network layer, providing encryption and authentication for data packets. It uses two main modes of operation: transport mode, which encrypts only the data payload of each packet, and tunnel mode, which encrypts the entire packet.
Another popular protocol for Site-to-Site VPNs is SSL/TLS (Secure Sockets Layer/Transport Layer Security). SSL/TLS operates at the application layer, creating a secure connection between web browsers and servers. While primarily used for securing website connections, SSL/TLS can also be utilized for VPN connections.
In addition to IPsec and SSL/TLS, other Site-to-Site VPN protocols include GRE (Generic Routing Encapsulation), L2TP (Layer 2 Tunneling Protocol), and MPLS (Multiprotocol Label Switching). These protocols offer varying levels of security and performance, allowing organizations to choose the best option based on their specific requirements.
When setting up a Site-to-Site VPN, it's essential to consider factors such as encryption strength, key management, and compatibility with existing network infrastructure. Regular maintenance and updates are also crucial to ensure the security of the VPN connection.
Overall, Site-to-Site VPN protocols play a vital role in enabling secure communication between geographically dispersed networks. By implementing the right protocol and best practices, organizations can safeguard their data and maintain the confidentiality of their network traffic.
VPN Tunneling Mechanism
VPN tunneling is a crucial aspect of how Virtual Private Networks (VPNs) operate, ensuring secure and private communication over public networks like the internet. It establishes a secure pathway, or tunnel, between the user's device and the VPN server, encrypting all data passing through it.
The process begins with the user initiating a connection to the VPN server. The VPN client on the user's device encrypts the data before sending it across the internet. This encryption ensures that even if intercepted, the data remains indecipherable to unauthorized parties.
Once the encrypted data reaches the VPN server, it is decrypted and sent to its intended destination, whether it's a website, server, or another network device. Similarly, incoming data from the destination is encrypted at the VPN server before being transmitted back to the user's device.
VPN tunneling relies on various protocols to establish and maintain these secure connections. Common protocols include OpenVPN, IPSec, L2TP/IPSec, and SSTP, each with its own strengths and weaknesses in terms of security, speed, and compatibility.
One of the key benefits of VPN tunneling is its ability to bypass censorship and geo-restrictions. By routing internet traffic through servers located in different countries, users can access content and services that may be restricted or blocked in their region.
Additionally, VPN tunneling enhances privacy by masking the user's IP address and encrypting their online activities. This protects sensitive information from hackers, government surveillance, and other malicious actors seeking to intercept or monitor internet traffic.
In summary, VPN tunneling plays a vital role in ensuring the security, privacy, and accessibility of online communication, making it an indispensable tool for individuals and businesses alike.
Inter-Organizational Network Security
Inter-organizational network security refers to the measures taken to protect the communication and data exchange between different organizations. In today's interconnected world, where businesses often collaborate with partners, suppliers, and customers, securing the networks that facilitate this communication is crucial to prevent cyber threats and data breaches.
One aspect of inter-organizational network security is the establishment of secure communication channels such as Virtual Private Networks (VPNs) and encrypted email services. These technologies ensure that sensitive information shared between organizations is protected from unauthorized access.
Another important aspect is the implementation of strong authentication mechanisms to verify the identities of users accessing inter-organizational networks. Multi-factor authentication, biometric recognition, and digital certificates are examples of tools that can enhance the security of these networks and prevent unauthorized access.
Furthermore, organizations need to regularly update and patch their network systems to address known vulnerabilities and protect against emerging threats. This includes installing software updates, using intrusion detection systems, and conducting regular security assessments to identify and mitigate potential risks.
Collaboration between organizations is essential for the success of many businesses, but it also introduces new security challenges. By implementing robust inter-organizational network security measures, businesses can safeguard their data and communication channels, build trust with their partners, and mitigate the risk of cyber attacks and data breaches.
Virtual Private Network Architecture
Virtual Private Network (VPN) architecture forms the backbone of secure communication over the internet. It's a sophisticated framework that enables users to access a private network securely over a public network like the internet. The architecture of a VPN involves several key components working together seamlessly to ensure data privacy and security.
At the core of VPN architecture are encryption protocols, which encrypt data packets before transmission and decrypt them upon arrival, thereby safeguarding sensitive information from unauthorized access. These protocols, such as IPSec, OpenVPN, and WireGuard, ensure end-to-end encryption, making it extremely difficult for hackers to intercept and decipher the transmitted data.
Another essential component is the VPN client software installed on the user's device, which establishes a secure connection to the VPN server. This client software handles authentication, encryption, and tunneling, effectively creating a virtual tunnel through which data travels securely.
The VPN server, located either on-premises or hosted by a third-party service provider, plays a crucial role in facilitating secure communication. It authenticates incoming connections, manages encryption keys, and routes data between the client and the destination server.
Furthermore, VPN architecture may incorporate additional features like VPN concentrators, which optimize and manage multiple VPN connections, and firewall systems to enhance network security.
To ensure scalability and flexibility, VPN architecture often adopts a modular design, allowing for easy integration with existing network infrastructure and support for various VPN protocols and encryption algorithms.
In conclusion, the architecture of a Virtual Private Network encompasses a sophisticated framework of encryption protocols, client software, servers, and additional features designed to provide secure and private communication over the internet. By leveraging these components effectively, organizations and individuals can safeguard their data from unauthorized access and maintain confidentiality in an increasingly interconnected world.
Enterprise Data Encapsulation
Enterprise Data Encapsulation: Enhancing Security and Efficiency
In the digital age, where data reigns supreme, enterprises face the critical challenge of safeguarding their sensitive information while ensuring seamless accessibility and functionality. One solution that has emerged as a cornerstone of modern data management strategies is Enterprise Data Encapsulation (EDE).
EDE refers to the process of encapsulating data within secure containers or wrappers, effectively shielding it from unauthorized access or tampering while maintaining its integrity and availability for legitimate users. This approach offers a multi-layered defense mechanism against cyber threats, ensuring that even if one layer is breached, the underlying data remains protected.
At its core, EDE employs encryption techniques to transform plaintext data into an unreadable format, rendering it indecipherable to anyone without the appropriate decryption key. This cryptographic layer acts as the first line of defense, thwarting unauthorized attempts to intercept or manipulate sensitive information.
Furthermore, EDE integrates access control mechanisms to regulate the retrieval and manipulation of encapsulated data, ensuring that only authorized users with the requisite permissions can interact with it. This granular control over data access not only enhances security but also facilitates compliance with regulatory requirements governing data privacy and confidentiality.
Moreover, EDE facilitates seamless data transmission and interoperability across diverse systems and platforms. By encapsulating data within standardized formats or protocols, enterprises can transcend compatibility barriers and streamline data exchange processes, thereby fostering greater efficiency and collaboration.
In conclusion, Enterprise Data Encapsulation represents a robust framework for safeguarding sensitive information in today's interconnected business landscape. By combining encryption, access control, and interoperability features, EDE empowers enterprises to fortify their defenses against evolving cyber threats while optimizing data management practices for enhanced productivity and resilience.
0 notes
Text
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ, a fintech company that provides an AI-powered blockchain ecosystem, has launched its operations in the Indian market.
The company provides an AI-powered blockchain ecosystem that offers integrated solutions spanning the blockchain layer 1, native coin, exchange services, MPC wallet, DeFi, NFT, gaming and other products.
It has established its headquarters in Mumbai, with additional offices in Delhi, Bengaluru, and Kolkata.
Leveraging AI, CIFDAQ ecosystem aims to enhance traditional frameworks, merging them with the decentralized web of blockchain. This initiative seeks to balance centralized governmental frameworks with the decentralized economy, emphasizing transparency, security, scalability, and synergy with established economic systems.
Impact on the blockchain landscape
With its launch in India, The company aims to revolutionize the blockchain ecosystem by introducing cutting-edge solutions that promote security, efficiency, and accessibility.
It will focus on empowering businesses and individuals, thereby driving growth and fostering a more inclusive and prosperous future through blockchain technology. Notably, The move will unlock the full potential of blockchain technology, making it more accessible and beneficial for a wider audience.
CIFDAQ’s innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, decentralized economy, and users’ interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
Leadership comments
Himanshu Maradiya, the Founder & Chairman of CIFDAQ, said, "We are thrilled to embark on this new chapter of CIFDAQ's journey as we set foot in the vibrant and dynamic Indian market. Our innovative solutions are poised to address the unique challenges and opportunities present in India's blockchain and digital finance ecosystem. We aim to empower businesses and individuals with enhanced security and efficiency, driving growth and innovation across various sectors."
His son, Rahul Maradiya, Co-Founder and Global CEO of CIFDAQ, said, "We envision CIFDAQ as a catalyst for change, empowering businesses and individuals with cutting-edge solutions that enhance security, efficiency, and accessibility in the digital finance space. Our goal is to revolutionize the blockchain ecosystem and unlock its full potential, paving the way for a more inclusive and prosperous future."
For more information about CIFDAQ, please visit https://linktr.ee/cifdaq
CIFDAQ - The Evolution of Innovative Blockchain Ecosystem powered by AI, is a new-age fintech company that offers integrated solutions spanning the Blockchain Layer 1, Native Coin, Exchange Services, MPC Wallet, DeFi, NFT, Gaming, and other products. CIFDAQ's innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, a decentralized economy, and users' interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
CIFDAQ Blockchain Ecosystem consists of several modules and products that will be inter-connected by an innovative tool called $CIFD Coin.
$CIFD Coin will serve as the engine of each, and every product and module introduced by CIFDAQ - the evolution of an innovative blockchain ecosystem. Additionally, it will have its utility across the CIFDAQ ecosystem, making it the heart of everything CIFDAQ has to offer.
www.cifdaq.com
0 notes
Text
does a vpn pull data
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn pull data
VPN data encryption
VPN data encryption is a crucial component of ensuring online privacy and security. When you use a Virtual Private Network, your data is encrypted before it is transmitted over the internet. This encryption process converts your data into a secure code, making it unreadable to anyone who may try to intercept it.
There are different encryption protocols used by VPN providers, such as OpenVPN, L2TP/IPsec, and IKEv2/IPsec, each offering varying levels of security and speed. OpenVPN is known for being highly secure and flexible, making it a popular choice for many users. L2TP/IPsec and IKEv2/IPsec are also secure options, often used on mobile devices due to their efficient performance.
Data encryption works by scrambling the information you send over the internet into a code that can only be deciphered by the intended recipient with the right decryption key. This process protects your sensitive data, such as passwords, financial information, and personal messages, from cybercriminals and hackers.
By encrypting your data with a VPN, you can browse the web anonymously and securely, without the risk of your online activities being monitored or intercepted. It adds an extra layer of protection to your internet connection, particularly when using public Wi-Fi networks that are vulnerable to cyber threats.
In conclusion, VPN data encryption is a crucial technology that helps safeguard your online privacy and security. By using a VPN with strong encryption protocols, you can protect your sensitive information and browse the internet with peace of mind.
Data privacy VPN
Title: Safeguarding Your Data: The Role of VPNs in Protecting Privacy
In an era where data breaches and privacy concerns are rampant, safeguarding your online activities has become more crucial than ever. Enter Virtual Private Networks (VPNs), a powerful tool designed to enhance data privacy and security for internet users worldwide.
So, what exactly is a VPN, and how does it work? Essentially, a VPN creates a secure, encrypted connection between your device and the internet. Instead of directly accessing websites and services, your data is routed through a remote server operated by the VPN provider. This process not only masks your IP address but also encrypts your internet traffic, making it virtually impossible for third parties to intercept and decipher your sensitive information.
One of the primary benefits of using a VPN is the preservation of anonymity and privacy online. By hiding your IP address and encrypting your data, VPNs prevent ISPs, governments, hackers, and even advertisers from tracking your online activities and harvesting your personal information. Whether you're browsing the web, streaming content, or conducting financial transactions, a VPN ensures that your sensitive data remains confidential and protected from prying eyes.
Moreover, VPNs enable users to bypass geographic restrictions and censorship by allowing them to connect to servers located in different countries. This not only grants access to region-locked content but also enhances online freedom and anonymity.
However, not all VPNs are created equal. It's essential to choose a reputable provider with a strong commitment to user privacy and data security. Look for VPNs that employ robust encryption protocols, have a strict no-logs policy, and offer features like kill switches and leak protection to ensure maximum privacy protection.
In conclusion, in an age where online privacy is increasingly threatened, VPNs serve as indispensable tools for safeguarding your data and protecting your digital identity. By encrypting your internet connection and preserving anonymity, VPNs empower users to take control of their online privacy and security.
VPN data security
VPN data security is a crucial aspect of ensuring online privacy and protection for internet users. Virtual Private Networks (VPNs) create a secure and encrypted connection between your device and the internet, offering a range of benefits such as protecting your data from potential breaches and unauthorized access.
By using a VPN, your data is encrypted as it travels between your device and the VPN server. This means that even if someone intercepts the data, they won't be able to decipher it without the encryption key. This is particularly important when connecting to public Wi-Fi networks, as these are often targeted by hackers looking to steal sensitive information.
Additionally, VPNs help to mask your IP address and location, adding an extra layer of anonymity while browsing the internet. This can help protect your identity and online activities from being tracked by websites, advertisers, or even your internet service provider.
When choosing a VPN provider, it is important to opt for one that has a strong commitment to data security and privacy. Look for providers that offer robust encryption protocols, a no-logs policy, and features such as a kill switch to ensure that your data remains secure at all times.
In conclusion, VPN data security plays a vital role in safeguarding your online activities and personal information. By using a reliable VPN service, you can enjoy enhanced privacy and protection while navigating the digital world.
VPN data tracking
VPN data tracking refers to the practice of monitoring and analyzing the information that passes through a Virtual Private Network (VPN). While VPNs are commonly used to enhance online privacy and security by encrypting internet traffic and masking IP addresses, it is important to be aware that some VPN providers may engage in data tracking for various purposes.
One of the primary reasons for VPN data tracking is to optimize service performance and troubleshoot technical issues. By monitoring data flow, VPN providers can identify and resolve connectivity problems, ensure efficient server distribution, and maintain network stability. This can help improve the overall user experience and enhance the performance of the VPN service.
However, there are concerns about potential privacy implications of VPN data tracking. Some VPN providers may collect user data such as browsing habits, connection timestamps, and device information for marketing and advertising purposes. This data tracking practice raises questions about user confidentiality and the extent to which personal information is being monitored and shared with third parties.
To protect your privacy while using a VPN, it is recommended to choose a reputable provider that has a clear privacy policy and does not engage in excessive data tracking. Reading user reviews and conducting research on different VPN services can help you make an informed decision and select a VPN provider that aligns with your privacy and security preferences.
In conclusion, while VPN data tracking can serve legitimate purposes such as improving service quality, users should be cautious about potential privacy risks and choose VPN providers that prioritize data security and transparency.
VPN data logging
VPN data logging is a controversial practice that raises concerns among users who prioritize their online privacy. Data logging refers to the collection and storage of user activity logs, including information such as websites visited, files downloaded, and IP addresses. While some VPN providers claim to have a strict no-logging policy, others retain certain user data for various purposes.
The primary argument against VPN data logging is that it goes against the core principle of using a VPN - to ensure anonymity and privacy online. When a VPN provider logs user data, there is a risk that this information could be accessed by third parties, such as government agencies or hackers, compromising the user's privacy and security.
On the other hand, some VPN providers argue that minimal data logging is necessary for maintaining network performance, troubleshooting technical issues, and preventing abuse of the service. They claim that storing minimal logs does not invade user privacy since it does not include sensitive information such as browsing history or personal data.
For users concerned about data logging, it is essential to research and choose a VPN provider that aligns with their privacy preferences. Reading the provider's privacy policy, understanding what data is logged and for how long, and whether it is shared with third parties are crucial factors to consider.
In conclusion, while data logging may serve legitimate purposes for VPN providers, users should be wary of the potential privacy implications. Opting for VPN services that prioritize user privacy and transparency can help mitigate the risks associated with data logging.
0 notes
Text
does adguard contain vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does adguard contain vpn
AdGuard VPN compatibility
AdGuard VPN is a robust virtual private network service that prioritizes user privacy and security. With its advanced features and intuitive interface, it's no wonder users often inquire about its compatibility with various devices and platforms.
First and foremost, AdGuard VPN offers broad compatibility across multiple operating systems, including Windows, macOS, iOS, and Android. This cross-platform functionality ensures that users can protect their online activities regardless of the device they're using.
Moreover, AdGuard VPN extends its compatibility beyond traditional devices to include compatibility with routers. This allows users to secure their entire network and all connected devices, providing comprehensive protection for their online privacy.
In addition to device compatibility, AdGuard VPN also integrates seamlessly with popular web browsers like Chrome, Firefox, and Edge. This browser compatibility enables users to enjoy secure and private browsing experiences without compromising on speed or performance.
Furthermore, AdGuard VPN is compatible with streaming services and peer-to-peer (P2P) file sharing platforms. Users can access geo-restricted content on platforms like Netflix and Hulu while keeping their online activities private and secure. Additionally, the VPN's support for P2P file sharing ensures that users can safely and anonymously share files over the internet.
In conclusion, AdGuard VPN offers extensive compatibility across devices, platforms, browsers, and services. Whether you're browsing the web, streaming content, or sharing files, AdGuard VPN ensures that your online activities remain private and secure across all compatible devices and platforms.
Features of AdGuard VPN
AdGuard VPN offers a comprehensive range of features to enhance your online browsing experience and ensure your privacy and security. One of the standout features of AdGuard VPN is its robust encryption technology, which creates a secure tunnel for your internet traffic, keeping your data safe from hackers and other prying eyes.
Another key feature of AdGuard VPN is its wide server coverage, with servers located in numerous countries around the world. This allows you to access geo-restricted content and enjoy fast and reliable connections wherever you are.
Moreover, AdGuard VPN offers a strict no-logs policy, meaning that your online activities are not recorded or monitored in any way. This provides you with peace of mind knowing that your privacy is respected and protected.
Additionally, AdGuard VPN includes an automatic kill switch feature, which ensures that your internet connection is immediately cut off if the VPN connection is disrupted. This helps to prevent your data from being exposed in the event of an unexpected VPN disconnection.
Furthermore, AdGuard VPN is user-friendly and easy to set up, making it accessible to users of all levels of technical expertise. Whether you are looking to bypass censorship, secure your connection on public Wi-Fi networks, or simply protect your online privacy, AdGuard VPN offers a comprehensive set of features to meet your needs.
VPN functionality in AdGuard
AdGuard is a leading ad-blocking and internet security software that provides users with a wide range of features to enhance their online experience. One of the key functionalities offered by AdGuard is the VPN service, which brings an additional layer of security and privacy to users' internet browsing activities.
VPN, short for Virtual Private Network, encrypts the user's internet connection and routes it through a remote server, masking their IP address and making it nearly impossible for third parties to track their online activities. By integrating VPN functionality into AdGuard, users can safeguard their data from potential hackers, snoopers, and even their own internet service providers.
In addition to online privacy, AdGuard's VPN also allows users to bypass geo-restrictions and access region-locked content on streaming platforms or websites. This means users can enjoy their favorite shows, movies, and websites irrespective of their physical location.
Moreover, the VPN service in AdGuard ensures fast and stable internet connection speeds, thanks to its optimized server network spread across various locations worldwide. This feature guarantees uninterrupted browsing, streaming, and downloading experiences for users without compromising their online security.
In conclusion, VPN functionality in AdGuard not only protects users' online privacy but also enables hassle-free access to geo-blocked content while maintaining high-speed internet connectivity. By incorporating VPN into its suite of services, AdGuard continues to provide a comprehensive solution for users looking to enhance their online security and browsing experience.
AdGuard without VPN
Title: Exploring AdGuard without VPN: A Comprehensive Guide
AdGuard stands out as a versatile tool in the realm of online privacy and security. While often associated with VPN services, AdGuard's capabilities extend beyond just VPN usage. In this guide, we delve into the functionalities and benefits of using AdGuard without VPN.
AdGuard operates primarily as an ad blocker, offering users a seamless browsing experience by filtering out intrusive ads, pop-ups, and other forms of online advertisements. By eliminating these distractions, users can enjoy faster page load times and a cleaner interface while browsing the web.
One of the key features of AdGuard is its robust filtering system, which not only blocks ads but also protects users from malicious websites, phishing attempts, and online tracking. This ensures a safer and more secure online experience, even without the use of a VPN.
Additionally, AdGuard offers advanced customization options, allowing users to fine-tune their browsing experience according to their preferences. From whitelisting trusted websites to creating custom filters, AdGuard puts the power in the hands of the user to control their online environment.
Another benefit of using AdGuard without VPN is its compatibility with a wide range of devices and platforms. Whether you're browsing the web on your desktop, laptop, smartphone, or tablet, AdGuard seamlessly integrates with your favorite browsers and operating systems, providing consistent protection across all your devices.
In conclusion, while AdGuard is often associated with VPN services, its capabilities extend far beyond just VPN usage. With its powerful ad-blocking, malware protection, and customization features, AdGuard offers users a comprehensive solution for enhancing their online privacy and security, even without the need for a VPN.
Understanding AdGuard VPN
AdGuard VPN is a powerful tool designed to enhance your online privacy and security. As an essential component of modern digital life, understanding how AdGuard VPN works can empower users to make informed decisions about their online activities.
At its core, AdGuard VPN operates by establishing a secure and encrypted connection between your device and the internet. This encryption ensures that your data remains private and protected from potential threats such as hackers, surveillance, and data breaches.
One of the key features of AdGuard VPN is its ability to mask your IP address. By routing your internet traffic through servers located in various locations around the world, AdGuard VPN effectively hides your true IP address, making it difficult for third parties to track your online activities and identify your location.
Furthermore, AdGuard VPN offers advanced features such as split tunneling, which allows users to route only select internet traffic through the VPN while accessing other content directly. This flexibility ensures optimal performance and allows users to customize their online experience based on their specific needs.
Additionally, AdGuard VPN provides protection against online threats such as malware, phishing, and malicious websites. By filtering internet traffic and blocking harmful content, AdGuard VPN helps safeguard users' devices and personal information from potential attacks.
In conclusion, AdGuard VPN is a comprehensive solution for enhancing online privacy and security. By encrypting internet traffic, masking IP addresses, and providing advanced features such as split tunneling and malware protection, AdGuard VPN empowers users to take control of their digital footprint and enjoy a safer, more secure online experience.
0 notes
Text
do i need data on android phone to use vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do i need data on android phone to use vpn
Data usage on VPN-enabled Android phone
When using a VPN on your Android phone, it is important to understand how data usage is affected. A Virtual Private Network (VPN) encrypts your internet connection, providing security and privacy while browsing the web. However, this additional layer of security can impact your data usage.
Using a VPN on your Android phone can increase data usage due to the encryption process. The encryption of data packets sent and received through the VPN server requires additional data, which can result in higher amounts of data usage compared to browsing without a VPN. Additionally, connecting to a VPN server located far away from your physical location may also affect data usage, as the distance can impact internet speed and performance.
It is essential to monitor your data usage when using a VPN on your Android phone to avoid unexpected charges from your mobile carrier. Many VPN apps offer features to track data usage and set limits to prevent excessive usage. By keeping an eye on your data consumption, you can better manage your usage patterns and prevent any overages.
To reduce data usage while using a VPN on your Android phone, consider connecting to VPN servers closer to your physical location and avoiding unnecessary streaming or large downloads. By being mindful of your online activities and data usage, you can enjoy the security benefits of a VPN without exceeding your data limits.
VPN connectivity without data on Android
Title: How to Connect to VPN Without Data on Android
In today's hyper-connected world, VPNs (Virtual Private Networks) have become indispensable tools for safeguarding online privacy and security. However, accessing a VPN typically requires an active internet connection, which can be a challenge in certain situations, such as when you have no data available on your Android device. Fortunately, there are methods to connect to a VPN even without data, ensuring that your online activities remain protected.
One of the simplest ways to establish a VPN connection without using data on your Android device is by utilizing a Wi-Fi connection. Many VPN services offer a feature known as split tunneling, which allows you to route only specific apps or traffic through the VPN while letting others access the internet directly. By connecting to a Wi-Fi network that doesn't require authentication or data usage, you can then activate your VPN and ensure that your internet traffic is encrypted and secure.
Another method involves pre-configuring your VPN settings while you still have access to data. Before venturing into an area without data coverage, navigate to your device's VPN settings and configure the VPN connection using the necessary server details and authentication credentials. Once configured, your device will retain these settings, allowing you to connect to the VPN whenever needed, even without an active data connection.
Additionally, some VPN services offer offline modes or offline authentication methods, allowing you to establish a VPN connection without requiring an active data connection. These features may involve generating one-time authentication codes or using alternative authentication methods, such as pre-shared keys, to verify your identity and establish a secure connection.
In conclusion, while accessing a VPN typically requires an active data connection, there are several methods available to connect to a VPN without data on your Android device. By utilizing features such as split tunneling, pre-configured settings, or offline authentication methods, you can ensure that your online activities remain private and secure, even in the absence of data connectivity.
Offline VPN usage on Android device
Offline VPN usage on an Android device may sound like a paradox, as VPNs typically require an internet connection to function. However, there are instances where utilizing a VPN without an active internet connection can be advantageous.
One such scenario is when you want to access local network resources securely while offline. By setting up a VPN connection to your home or office network before going offline, you can still securely access resources such as shared files or printers without compromising security.
Another use case for offline VPN usage on an Android device is for privacy protection. By activating the VPN connection before disconnecting from the internet, you can prevent any potential data leaks or exposure of your IP address while using offline apps that may try to establish connections in the background.
Furthermore, offline VPN usage can also be beneficial for accessing region-locked content on your device. By connecting to a VPN server located in a specific region before going offline, you can trick certain apps or services into thinking you are in that region even when offline, allowing access to restricted content.
While offline VPN usage on Android devices may not be the primary use case for most users, it can provide added security, privacy, and flexibility in certain situations where maintaining a VPN connection without an active internet connection is desired.
VPN functionality without internet on Android
VPN, or Virtual Private Network, is a technology that allows users to create a secure connection to another network over the internet. Typically, VPN services require an active internet connection to establish and maintain the encrypted tunnel between the user's device and the VPN server. However, there are certain scenarios where VPN functionality can still be useful even without an internet connection, particularly on Android devices.
One such scenario is when users need to access resources on a local network that are not internet-reachable, such as networked printers, file servers, or other devices. By setting up a VPN connection within the local network, users can securely access these resources even without internet access. This can be particularly useful in office or home settings where local resources need to be accessed securely.
Additionally, VPNs can also be used for local file sharing between devices on the same network. By establishing a VPN connection between two Android devices, users can securely transfer files and data without the need for an active internet connection. This can be especially handy in situations where internet access is limited or unavailable.
It is important to note that while VPN functionality without internet on Android can be beneficial in certain scenarios, the setup process may vary depending on the VPN service provider and the specific requirements of the user. Users interested in utilizing VPNs without internet access should consult their VPN service provider for guidance on setting up and configuring the VPN connection for local network use.
Using VPN on Android phone without data plan
Using a VPN on an Android phone without a data plan is still possible, provided that you have access to Wi-Fi networks. A VPN (Virtual Private Network) allows you to browse the internet securely and privately by encrypting your connection and hiding your IP address. While many VPN services require an internet connection to function, there are some ways to use a VPN on your Android phone even without a data plan.
One way to use a VPN on your Android phone without a data plan is to connect to public Wi-Fi networks. Many establishments such as cafes, restaurants, libraries, and airports offer free Wi-Fi access. By connecting to one of these networks, you can enable your VPN and enjoy a more secure browsing experience.
Another option is to use a VPN service that allows for manual configuration. Some VPN providers offer manual setup guides that enable you to configure the VPN connection using settings such as server addresses and authentication methods. By following these guides, you can set up the VPN on your Android phone even without a data plan.
It is important to note that using public Wi-Fi networks without a data plan can pose security risks, as these networks are often insecure and may be susceptible to hacking. Therefore, it is recommended to use a VPN to encrypt your connection and protect your data while browsing on public Wi-Fi networks.
In conclusion, while using a VPN on an Android phone without a data plan may have limitations, it is still possible by connecting to Wi-Fi networks or configuring the VPN manually. By taking these precautions, you can enhance your online privacy and security even without a data plan.
0 notes
Text
CIFDAQ Introduces Innovative Blockchain Ecosystem in India
CIFDAQ, a fintech company that provides an AI-powered blockchain ecosystem, has launched its operations in the Indian market.
The company provides an AI-powered blockchain ecosystem that offers integrated solutions spanning the blockchain layer 1, native coin, exchange services, MPC wallet, DeFi, NFT, gaming and other products.
It has established its headquarters in Mumbai, with additional offices in Delhi, Bengaluru, and Kolkata.
Leveraging AI, CIFDAQ ecosystem aims to enhance traditional frameworks, merging them with the decentralized web of blockchain. This initiative seeks to balance centralized governmental frameworks with the decentralized economy, emphasizing transparency, security, scalability, and synergy with established economic systems.
Impact on the blockchain landscape
With its launch in India, The company aims to revolutionize the blockchain ecosystem by introducing cutting-edge solutions that promote security, efficiency, and accessibility.
It will focus on empowering businesses and individuals, thereby driving growth and fostering a more inclusive and prosperous future through blockchain technology. Notably, The move will unlock the full potential of blockchain technology, making it more accessible and beneficial for a wider audience.
CIFDAQ’s innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, decentralized economy, and users’ interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
Leadership comments
Himanshu Maradiya, the Founder & Chairman of CIFDAQ, said, "We are thrilled to embark on this new chapter of CIFDAQ's journey as we set foot in the vibrant and dynamic Indian market. Our innovative solutions are poised to address the unique challenges and opportunities present in India's blockchain and digital finance ecosystem. We aim to empower businesses and individuals with enhanced security and efficiency, driving growth and innovation across various sectors."
His son, Rahul Maradiya, Co-Founder and Global CEO of CIFDAQ, said, "We envision CIFDAQ as a catalyst for change, empowering businesses and individuals with cutting-edge solutions that enhance security, efficiency, and accessibility in the digital finance space. Our goal is to revolutionize the blockchain ecosystem and unlock its full potential, paving the way for a more inclusive and prosperous future."
For more information about CIFDAQ, please visit https://linktr.ee/cifdaq
CIFDAQ - The Evolution of Innovative Blockchain Ecosystem powered by AI, is a new-age fintech company that offers integrated solutions spanning the Blockchain Layer 1, Native Coin, Exchange Services, MPC Wallet, DeFi, NFT, Gaming, and other products. CIFDAQ's innovative solutions bridge the gap between traditional frameworks and blockchain technology, empowering businesses to thrive in a rapidly evolving Web 3.0 landscape, ensuring a balance between centralized government, a decentralized economy, and users' interests, CIFDAQ prioritizes transparency, security, scalability, and synergy with centralized economies.
CIFDAQ Blockchain Ecosystem consists of several modules and products that will be inter-connected by an innovative tool called $CIFD Coin.
$CIFD Coin will serve as the engine of each, and every product and module introduced by CIFDAQ - the evolution of an innovative blockchain ecosystem. Additionally, it will have its utility across the CIFDAQ ecosystem, making it the heart of everything CIFDAQ has to offer.
#CIFDAQ#BITCOIN#CRYPTOINVESTING#BLOCKCHAIN#WEB3COMMUNITY
www.cifdaq.com
0 notes