#kernel mode heap corruption
Explore tagged Tumblr posts
Text
>be me
>using laptop
>try and watch a movie on jellyfin
>KERNEL_MODE_HEAP_CORRUPTION
>mfw.jpg

3 notes
·
View notes
Link
#Kernel Mode Heap Corruption#Kernel Mode Heap Corruption on Windows 10#kernel-mode heap corruption windows 10 error#free driver updater
0 notes
Text
How to Fix Kernel Mode Heap Corruption
You may get the Kernel Mode Heap Corruption error while using your computer. The BSOD error is quite common and easy to fix. In this article, you will get to know the steps to fix Kernel mode heap corruption error.
Here’s How to Fix Kernel Mode Heap Corruption

• Check for incompatible program
Click on the Windows and R keys together.
Enter “appwiz.cpl” in the prompt box.
Click on the Enter option.
You will get all the installed app on the PC.
You need to right-click on that application, which is creating this issue.
Start the system once you have completed the uninstallation procedure.
You need to check whether the Kernel mode is fixed or not.
• Check your drivers for errors
Click on the Windows and S keys together.
Enter “command prompt” in the prompt box.
You need to right-click on the app.
Choose the Run as administrator option.
After opening the elevated command pop up box, run the below-mentioned command:
verifier
Choose the “Create standard settings” option.
Click on the Next option.
Choose the Automatically select all drivers installed on this computer option.
Press on the Finish option.
Windows start scanning the errors.
You should backup your data first.
If it asks you to restart the system, then you need to do this.
When you open your Windows PC, you will find that all the drivers are already installed on the system.
• Update Drivers
Click on the Windows and R keys together.
It will open the Run prompt box.
Enter “devmgmt.msc” in the prompt box.
Press on the Enter button
It will open the device manager on the PC.
Now, you will get the menu list of all the installed devices against the PC.
Go through all the installed devices.
Search for that application, which is causing this issue.
Press on the Display adapters pulldown to get the installed card.
You need to right-click on the installed card.
Choose the “Update driver” option.
You will get the prompt box.
Choose the Search automatically for updated driver software option.
In case you are not able to update the drivers, then go to the online manufacturer website.
Start downloading the drivers.
You need to choose the second option.
Start updating all the drivers before you start the PC again.
Once you have gone through the restarting process, check whether this issue is fixed or not.
• Perform a System Restore
Click on the Windows and S keys together.
It will open the start menu text field.
Enter “restore” in the prompt box.
Choose the software which is on the top of the screen.
Click on the System Restore option.
It is located in the restore settings tab.
The System Restore option is located at the upper side of the screen below the System Protection option.
In case you wish to choose the custom to restore option, then press on the option.
After that, choose the restore point option by going to the menu list of all the options that are available now.
In case you have multiple systems restore points, then they will be listed in the restore point window.
The Windows will verify the action before starting the restoring process of the computer.
After completing the restore process, sign in to the computer.
Check whether you are getting the blue screen.
Eleanor is a jack of all trades : an experienced IT technicians, writer, researcher, and a self-professed Software expert. As a single software engineer, she has in-depth knowledge of Webroot Antivirus and she likes to write tutorials, reviews, news, and reports about the same under webroot support number
Source: Fix Kernel Mode Heap Corruption
0 notes
Text
How To Fix Kernel Mode Heap Corruption Error In Windows 10
#windows
Kernel Mode Heap Corruption – BSODs should be a common thing to you by now as a Windows user. Kernel Mode Heap Corruption Error could be caused by outdated or malfunctioning drivers, memory leaks, and hardware faults. This article will explain how to fix the Kernel Mode Heap Corruption error. Here are some fixes to help resolve the Kernel Mode Heap Corruption blue screen error on Windows…

View On WordPress
0 notes
Photo

Go and check our new article 8 assured and effective methods to fix "kernel mode heap corruption error" [2021] #troubleshooting #troubleshoot #troubleshooter #troubleshootinglife #troubleshooters #pc #pcproblems #pcmc #pcsetup #pcissues #laptop #laptopproblems #laptops #laptopproblem #laptopissues #pctroubleshooting #laptoptroubleshooting #windows10 #windows10home #windows10problems #microsoft #microsoftexcel @hp @hp_india @asus @asusindia @ibm @ibmdata @microsoft @windows @pctroubleshooter_ https://www.instagram.com/p/CPNMO8VMqzH/?utm_medium=tumblr
#troubleshooting#troubleshoot#troubleshooter#troubleshootinglife#troubleshooters#pc#pcproblems#pcmc#pcsetup#pcissues#laptop#laptopproblems#laptops#laptopproblem#laptopissues#pctroubleshooting#laptoptroubleshooting#windows10#windows10home#windows10problems#microsoft#microsoftexcel
0 notes
Link
Dalam posting ini, admin akan menunjukkan kepada kalian cara mengatasi kernel mode heap corruption yang menyebabkan BSOD.
0 notes
Photo

Sometimes it happens that you are using your Windows system and get a pop-up error message saying kernel mode heap corruption. It is basically shown that your Windows system needs a restart, and the screen turns into blue. Don’t need to worry about this problem, here are many users who face this issue. Read this full article to get the exact causes and solutions or simply call us on (866)558-4555.
0 notes
Text
Investigating Intel’s Compiler
I don’t think there’s been a more controversial programming tool to ever be released than Intel’s own C++ compiler. The biggest controversy, for those who don’t know, basically involved Intel using their compiler to slow down their competitor’s chips. Whether that’s true or not, is what I’ll be going into in this post.
Why?
A lot of tech enthusiasts are, for good reason, very skeptical of Intel. Even a surface-level dive into the semiconductor industry reveals some troubling skeletons in Intel’s closet, including several anti-trust violations in both America and Europe.
But, times do change, and so, I’ve decided to investigate whether Intel’s compiler is still used as a weapon against their rivals, AMD in particular.
How?
Testing will actually be really simple: I just need to compile my test programs twice: Once with Intel’s compiler, and once with Visual Studio. I would use QTCreator given how lightweight it is, but my installation seems to be corrupted. That and Intel’s compiler has Visual Studio integration, so that will help keep things consistent. No need for me to write a batch file just to compile the tests.
By switching between two different compilers, one from Intel and the other vendor-agnostic, the various data points can be used to come to a conclusion. If Intel’s compiler is deliberately slowing down code that runs on my AMD hardware, then the difference will be very clear.
Once the tests have been compiled, I’ll run them, record the time, and then come to a conclusion. But note that I will not average the scores from different tests. This is because it’s simply unnecessary, and will make the data more murky. Especially given some programs will rely on certain algorithms more than others.
The Tests
In order to test this, I thought it too imprecise to find a program online, compile it, and run it. While that would provide a very realistic workload, I don’t think it would reveal too much about Intel’s slowdown methods, if they utilize any. In particular, 7-Zip, while free and open source, would be terrible for this because it’s mainly I/O bound. Any slowdown wouldn’t be noticed too well, and partially masked by either of my drives.
So instead, I decided to write my own suite of tests. Unfortunately these are all single-threaded tests, as multithreaded testing would be too difficult to do right. That’s not really the point anyway: If the compiler does indeed use tactics to slow down AMD chips, then even a single-threaded test will be able to reveal them.
These are the tests I wrote and why:
QuickSort. Reason being, it's a fairly simple algorithm with fairly predictable performance.
Counting Sort. Another sorting algorithm, but this one relies very little on branching. In fact, a proper implementation has no if statements at all. May not be a great indicator of real-world performance loss, but it’s a simple test, so I decided to throw it in.
Binary Tree. This one isn’t very indicative, but basically: It takes random data, builds a binary search tree with it, then locates a random element.
Note: In order to ensure that the testing is fair, the test will have to be rather large. This won’t be a 5-second thousand-element sort, no. Think 1 million elements. The exact testing parameters will be detailed below.
Test Machine
Of course, it’s important to contextualize the hardware on which these tests are done. This entire post would be a big waste of time if I was still rocking an i5-7600K. So below are all the relevant parts (and some irrelevant ones):
CPU: AMD Ryzen 5 1600 @ Stock
Cooler: AMD Wraith Spire (cu*)
RAM: 16 GB DDR4-3000 Team Vulkan-Z @ DDR4-2933**
Mobo: ASUS TUF GAMING B450M
* Has a copper slug. Just in case you were curious
** Otherwise stock. Also, F for my underutilized RAM :(
Testing Methodology
For each compiler, each test will be run 10 times, and the time taken averaged out. No major programs running in the background, not that it’ll impact anything. I/O, such as loading/generating data to be sorted, will not be counted towards any timed portions.
Every time the compiler is swapped, settings are checked to ensure fairness, and
There will be three tests: One with Visual Studio set to Debug mode, one with Release mode with standard O2 optimization, and one with Release mode and optimizations disabled.
The Results
Well, I wasn’t expecting what I found, in all honesty. First, Debug mode, as that’s what people will most likely test with at first.

Just as a reminder, this is running on AMD hardware. And I have triple-checked these numbers, and they’re accurate. No funny business. I even tested the Visual Studio compiler before installing the Intel compiler.
Maybe there’s shenanigans going on in Release mode + Od?
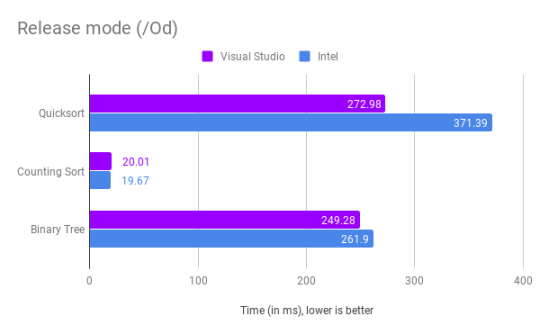
Well, quicksort is slower on Intel now. So it would seem that the Visual Studio compiler does more optimizations even when you tell it to not do anything special.
I do find it curious that Counting Sort takes longer with Release mode, but that could just be per-run variance. Overall, I’m not too concerned.
And finally, the most disappointing, Release mode + O2 optimization:
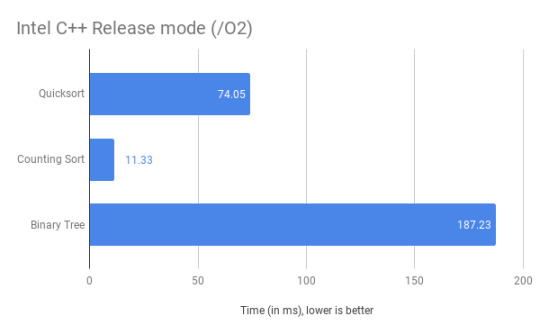
Unfortunately, I couldn’t get the Visual Studio compiler to produce anything useful despite being given more than enough time. It just sits around, twiddling its thumbs on a single thread. Eventually it complains about a lack of heap space, despite my system having 16 GBs of RAM. So the Intel compiler is the only one I was able to test.
But wait, there’s more!
So, being the super-paranoid programmer I am, I was thinking there had to be a catch. So I went ahead and threw the Intel-compiled code into HxD, a hex editor. It’ll let me see the individual instructions that make up the program, and tell me what an instruction means in x86.
Initially, I just looked for the instruction 0x0FA2, as that is the CPUID instruction in x86. CPUID lets programs see what hardware they’re running on, as it will return a string depending on which vendor made it. The string is vendor-dependent, so AMD could make a CPU that has an Intel vendor ID (though I doubt software would like that).
Intel has “GenuineIntel”, and AMD has “AuthenticAMD”, though at one point they had “AMDisbetter!”. There’s other x86 vendors that have their own respective vendor strings.
Anyway, I dug through an executable or two, didn’t find anything significant. Even dug through the Visual Studio compiled code. Weirdly, it does seem to call CPUID later on in the program, towards the end actually. I have no idea why it would do this.
That is, until I was editing this blog post. I noticed that the gains going from Debug to Release Od were rather small, so I went ahead and threw that code in particular into HxD. Look at what I found:

There’s two things that stick out:
1. The mangled GenuineIntel vendor ID string.
2. The CPUID call that’s in the general area.
So at this point, I’m getting a little paranoid, so I go back and look at the other results. Turns out I did find more damning evidence and I was just being a tunnel-visioned idiot. This code is from the Debug compilation:
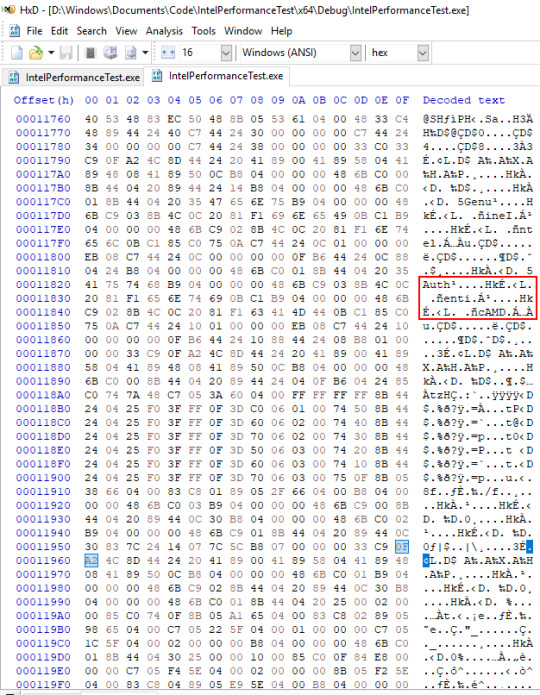
What the hell is that AuthenticAMD vendor string doing in Intel-compiled code? HMMM... Honestly I’m not sure. The code runs significantly faster than the Visual Studio code, so it doesn’t seem to be sabotage at first glance.
So I looked at the compiled executable sizes. And as compiling Visual Studio for Release is difficult, I just went ahead and only compiled for Debug.
Turns out the Visual Studio compiler is the bigger one, at 727 KBs versus Intel’s ~323 KBs (note: don’t have the exact number, forgot to jot it down).
So at this point I’m just... confused. What is going on? So I crack open the VS-compiled executable in HxD and... well...
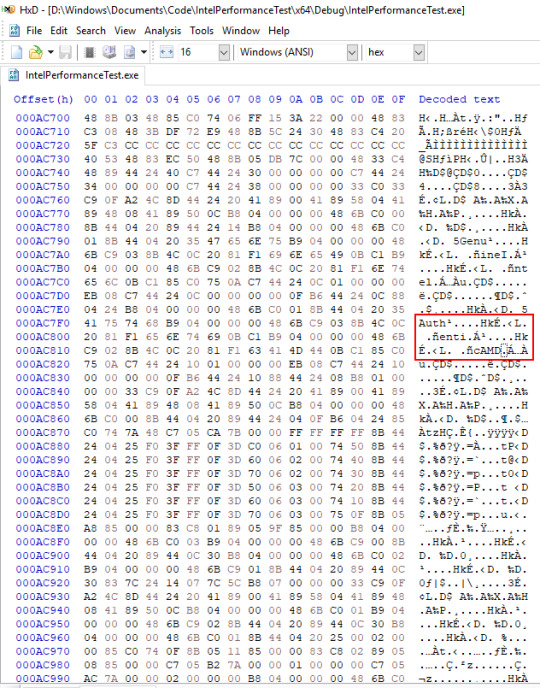
I found the exact same string. Different place, but the same string nonetheless. Not only that, the same code surrounds it. So it’s not Intel-exclusive. None of what’s here is exclusive to Intel’s compiler, unless there’s some crazy conspiracy that both Intel and Microsoft are into. Which I highly doubt, given that would be a massive conflict of interest for Microsoft. Imagine, if Visual Studio’s C++ compiler was sabotaging AMD hardware. That would be a massive blow to their own consoles, given a lot of them may just be compiled with Visual Studio.
And for the record, there are no other instances of AMD’s vendor ID string anywhere in either compiled executables. I would mention it if there was.
Final Word
No, Intel’s compiler is not running deliberately slow code on AMD hardware. Or at least, as far as it seems. In fact, it seems to run faster code overall than Visual Studio’s own compiler.
Although I wouldn’t recommend using Intel’s software suite, given it has been found that their Math Kernel Library does indeed run intentionally worse on AMD hardware. I may do my own experimenting on it and see if I can replicate the results, but for now I’m just done with experimenting with Intel’s software. I’m going back to tinkering with Vulkan.
If you want to see the code I used to test this, here it is: https://github.com/Elusivehawk/IntelPerformanceTest
0 notes
Text
System hardening in Android 11
Posted by Platform Hardening Team
In Android 11 we continue to increase the security of the Android platform. We have moved to safer default settings, migrated to a hardened memory allocator, and expanded the use of compiler mitigations that defend against classes of vulnerabilities and frustrate exploitation techniques.
Initializing memory
We’ve enabled forms of automatic memory initialization in both Android 11’s userspace and the Linux kernel. Uninitialized memory bugs occur in C/C++ when memory is used without having first been initialized to a known safe value. These types of bugs can be confusing, and even the term “uninitialized” is misleading. Uninitialized may seem to imply that a variable has a random value. In reality it isn’t random. It has whatever value was previously placed there. This value may be predictable or even attacker controlled. Unfortunately this behavior can result in a serious vulnerability such as information disclosure bugs like ASLR bypasses, or control flow hijacking via a stack or heap spray. Another possible side effect of using uninitialized values is advanced compiler optimizations may transform the code unpredictably, as this is considered undefined behavior by the relevant C standards.
In practice, uses of uninitialized memory are difficult to detect. Such errors may sit in the codebase unnoticed for years if the memory happens to be initialized with some “safe” value most of the time. When uninitialized memory results in a bug, it is often challenging to identify the source of the error, particularly if it is rarely triggered. Eliminating an entire class of such bugs is a lot more effective than hunting them down individually. Automatic stack variable initialization relies on a feature in the Clang compiler which allows choosing initializing local variables with either zeros or a pattern. Initializing to zero provides safer defaults for strings, pointers, indexes, and sizes. The downsides of zero init are less-safe defaults for return values, and exposing fewer bugs where the underlying code relies on zero initialization. Pattern initialization tends to expose more bugs and is generally safer for return values and less safe for strings, pointers, indexes, and sizes.
Initializing Userspace:
Automatic stack variable initialization is enabled throughout the entire Android userspace. During the development of Android 11, we initially selected pattern in order to uncover bugs relying on zero init and then moved to zero-init after a few months for increased safety. Platform OS developers can build with `AUTO_PATTERN_INITIALIZE=true m` if they want help uncovering bugs relying on zero init.
Initializing the Kernel:
Automatic stack and heap initialization were recently merged in the upstream Linux kernel. We have made these features available on earlier versions of Android’s kernel including 4.14, 4.19, and 5.4. These features enforce initialization of local variables and heap allocations with known values that cannot be controlled by attackers and are useless when leaked. Both features result in a performance overhead, but also prevent undefined behavior improving both stability and security.
For kernel stack initialization we adopted the CONFIG_INIT_STACK_ALL from upstream Linux. It currently relies on Clang pattern initialization for stack variables, although this is subject to change in the future.
Heap initialization is controlled by two boot-time flags, init_on_alloc and init_on_free, with the former wiping freshly allocated heap objects with zeroes (think s/kmalloc/kzalloc in the whole kernel) and the latter doing the same before the objects are freed (this helps to reduce the lifetime of security-sensitive data). init_on_alloc is a lot more cache-friendly and has smaller performance impact (within 2%), therefore it has been chosen to protect Android kernels.
Scudo is now Android’s default native allocator
In Android 11, Scudo replaces jemalloc as the default native allocator for Android. Scudo is a hardened memory allocator designed to help detect and mitigate memory corruption bugs in the heap, such as:
Double free,
Arbitrary free,
Heap-based buffer overflow,
Use-after-free
Scudo does not fully prevent exploitation but it does add a number of sanity checks which are effective at strengthening the heap against some memory corruption bugs.
It also proactively organizes the heap in a way that makes exploitation of memory corruption more difficult, by reducing the predictability of the allocation patterns, and separating allocations by sizes.
In our internal testing, Scudo has already proven its worth by surfacing security and stability bugs that were previously undetected.
Finding Heap Memory Safety Bugs in the Wild (GWP-ASan)
Android 11 introduces GWP-ASan, an in-production heap memory safety bug detection tool that’s integrated directly into the native allocator Scudo. GWP-ASan probabilistically detects and provides actionable reports for heap memory safety bugs when they occur, works on 32-bit and 64-bit processes, and is enabled by default for system processes and system apps.
GWP-ASan is also available for developer applications via a one line opt-in in an app’s AndroidManifest.xml, with no complicated build support or recompilation of prebuilt libraries necessary.
Software Tag-Based KASAN
Continuing work on adopting the Arm Memory Tagging Extension (MTE) in Android, Android 11 includes support for kernel HWASAN, also known as Software Tag-Based KASAN. Userspace HWASAN is supported since Android 10.
KernelAddressSANitizer (KASAN) is a dynamic memory error detector designed to find out-of-bound and use-after-free bugs in the Linux kernel. Its Software Tag-Based mode is a software implementation of the memory tagging concept for the kernel. Software Tag-Based KASAN is available in 4.14, 4.19 and 5.4 Android kernels, and can be enabled with the CONFIG_KASAN_SW_TAGS kernel configuration option. Currently Tag-Based KASAN only supports tagging of slab memory; support for other types of memory (such as stack and globals) will be added in the future.
Compared to Generic KASAN, Tag-Based KASAN has significantly lower memory requirements (see this kernel commit for details), which makes it usable on dog food testing devices. Another use case for Software Tag-Based KASAN is checking the existing kernel code for compatibility with memory tagging. As Tag-Based KASAN is based on similar concepts as the future in-kernel MTE support, making sure that kernel code works with Tag-Based KASAN will ease in-kernel MTE integration in the future.
Expanding existing compiler mitigations
We’ve continued to expand the compiler mitigations that have been rolled out in prior releases as well. This includes adding both integer and bounds sanitizers to some core libraries that were lacking them. For example, the libminikin fonts library and the libui rendering library are now bounds sanitized. We’ve hardened the NFC stack by implementing both integer overflow sanitizer and bounds sanitizer in those components.
In addition to the hard mitigations like sanitizers, we also continue to expand our use of CFI as an exploit mitigation. CFI has been enabled in Android’s networking daemon, DNS resolver, and more of our core javascript libraries like libv8 and the PacProcessor.
The effectiveness of our software codec sandbox
Prior to the Release of Android 10 we announced a new constrained sandbox for software codecs. We’re really pleased with the results. Thus far, Android 10 is the first Android release since the infamous stagefright vulnerabilities in Android 5.0 with zero critical-severity vulnerabilities in the media frameworks.
Thank you to Jeff Vander Stoep, Alexander Potapenko, Stephen Hines, Andrey Konovalov, Mitch Phillips, Ivan Lozano, Kostya Kortchinsky, Christopher Ferris, Cindy Zhou, Evgenii Stepanov, Kevin Deus, Peter Collingbourne, Elliott Hughes, Kees Cook and Ken Chen for their contributions to this post.
System hardening in Android 11 published first on https://phonetracking.tumblr.com/ System hardening in Android 11 published first on https://leolarsonblog.tumblr.com/
0 notes
Text
System hardening in Android 11
Posted by Platform Hardening Team
In Android 11 we continue to increase the security of the Android platform. We have moved to safer default settings, migrated to a hardened memory allocator, and expanded the use of compiler mitigations that defend against classes of vulnerabilities and frustrate exploitation techniques.
Initializing memory
We’ve enabled forms of automatic memory initialization in both Android 11’s userspace and the Linux kernel. Uninitialized memory bugs occur in C/C++ when memory is used without having first been initialized to a known safe value. These types of bugs can be confusing, and even the term “uninitialized” is misleading. Uninitialized may seem to imply that a variable has a random value. In reality it isn’t random. It has whatever value was previously placed there. This value may be predictable or even attacker controlled. Unfortunately this behavior can result in a serious vulnerability such as information disclosure bugs like ASLR bypasses, or control flow hijacking via a stack or heap spray. Another possible side effect of using uninitialized values is advanced compiler optimizations may transform the code unpredictably, as this is considered undefined behavior by the relevant C standards.
In practice, uses of uninitialized memory are difficult to detect. Such errors may sit in the codebase unnoticed for years if the memory happens to be initialized with some "safe" value most of the time. When uninitialized memory results in a bug, it is often challenging to identify the source of the error, particularly if it is rarely triggered. Eliminating an entire class of such bugs is a lot more effective than hunting them down individually. Automatic stack variable initialization relies on a feature in the Clang compiler which allows choosing initializing local variables with either zeros or a pattern. Initializing to zero provides safer defaults for strings, pointers, indexes, and sizes. The downsides of zero init are less-safe defaults for return values, and exposing fewer bugs where the underlying code relies on zero initialization. Pattern initialization tends to expose more bugs and is generally safer for return values and less safe for strings, pointers, indexes, and sizes.
Initializing Userspace:
Automatic stack variable initialization is enabled throughout the entire Android userspace. During the development of Android 11, we initially selected pattern in order to uncover bugs relying on zero init and then moved to zero-init after a few months for increased safety. Platform OS developers can build with `AUTO_PATTERN_INITIALIZE=true m` if they want help uncovering bugs relying on zero init.
Initializing the Kernel:
Automatic stack and heap initialization were recently merged in the upstream Linux kernel. We have made these features available on earlier versions of Android’s kernel including 4.14, 4.19, and 5.4. These features enforce initialization of local variables and heap allocations with known values that cannot be controlled by attackers and are useless when leaked. Both features result in a performance overhead, but also prevent undefined behavior improving both stability and security.
For kernel stack initialization we adopted the CONFIG_INIT_STACK_ALL from upstream Linux. It currently relies on Clang pattern initialization for stack variables, although this is subject to change in the future.
Heap initialization is controlled by two boot-time flags, init_on_alloc and init_on_free, with the former wiping freshly allocated heap objects with zeroes (think s/kmalloc/kzalloc in the whole kernel) and the latter doing the same before the objects are freed (this helps to reduce the lifetime of security-sensitive data). init_on_alloc is a lot more cache-friendly and has smaller performance impact (within 2%), therefore it has been chosen to protect Android kernels.
Scudo is now Android's default native allocator
In Android 11, Scudo replaces jemalloc as the default native allocator for Android. Scudo is a hardened memory allocator designed to help detect and mitigate memory corruption bugs in the heap, such as:
Double free,
Arbitrary free,
Heap-based buffer overflow,
Use-after-free
Scudo does not fully prevent exploitation but it does add a number of sanity checks which are effective at strengthening the heap against some memory corruption bugs.
It also proactively organizes the heap in a way that makes exploitation of memory corruption more difficult, by reducing the predictability of the allocation patterns, and separating allocations by sizes.
In our internal testing, Scudo has already proven its worth by surfacing security and stability bugs that were previously undetected.
Finding Heap Memory Safety Bugs in the Wild (GWP-ASan)
Android 11 introduces GWP-ASan, an in-production heap memory safety bug detection tool that's integrated directly into the native allocator Scudo. GWP-ASan probabilistically detects and provides actionable reports for heap memory safety bugs when they occur, works on 32-bit and 64-bit processes, and is enabled by default for system processes and system apps.
GWP-ASan is also available for developer applications via a one line opt-in in an app's AndroidManifest.xml, with no complicated build support or recompilation of prebuilt libraries necessary.
Software Tag-Based KASAN
Continuing work on adopting the Arm Memory Tagging Extension (MTE) in Android, Android 11 includes support for kernel HWASAN, also known as Software Tag-Based KASAN. Userspace HWASAN is supported since Android 10.
KernelAddressSANitizer (KASAN) is a dynamic memory error detector designed to find out-of-bound and use-after-free bugs in the Linux kernel. Its Software Tag-Based mode is a software implementation of the memory tagging concept for the kernel. Software Tag-Based KASAN is available in 4.14, 4.19 and 5.4 Android kernels, and can be enabled with the CONFIG_KASAN_SW_TAGS kernel configuration option. Currently Tag-Based KASAN only supports tagging of slab memory; support for other types of memory (such as stack and globals) will be added in the future.
Compared to Generic KASAN, Tag-Based KASAN has significantly lower memory requirements (see this kernel commit for details), which makes it usable on dog food testing devices. Another use case for Software Tag-Based KASAN is checking the existing kernel code for compatibility with memory tagging. As Tag-Based KASAN is based on similar concepts as the future in-kernel MTE support, making sure that kernel code works with Tag-Based KASAN will ease in-kernel MTE integration in the future.
Expanding existing compiler mitigations
We’ve continued to expand the compiler mitigations that have been rolled out in prior releases as well. This includes adding both integer and bounds sanitizers to some core libraries that were lacking them. For example, the libminikin fonts library and the libui rendering library are now bounds sanitized. We’ve hardened the NFC stack by implementing both integer overflow sanitizer and bounds sanitizer in those components.
In addition to the hard mitigations like sanitizers, we also continue to expand our use of CFI as an exploit mitigation. CFI has been enabled in Android’s networking daemon, DNS resolver, and more of our core javascript libraries like libv8 and the PacProcessor.
The effectiveness of our software codec sandbox
Prior to the Release of Android 10 we announced a new constrained sandbox for software codecs. We’re really pleased with the results. Thus far, Android 10 is the first Android release since the infamous stagefright vulnerabilities in Android 5.0 with zero critical-severity vulnerabilities in the media frameworks.
Thank you to Jeff Vander Stoep, Alexander Potapenko, Stephen Hines, Andrey Konovalov, Mitch Phillips, Ivan Lozano, Kostya Kortchinsky, Christopher Ferris, Cindy Zhou, Evgenii Stepanov, Kevin Deus, Peter Collingbourne, Elliott Hughes, Kees Cook and Ken Chen for their contributions to this post.
System hardening in Android 11 published first on https://phonetracking.tumblr.com/
0 notes
Text
System hardening in Android 11
Posted by Platform Hardening Team
In Android 11 we continue to increase the security of the Android platform. We have moved to safer default settings, migrated to a hardened memory allocator, and expanded the use of compiler mitigations that defend against classes of vulnerabilities and frustrate exploitation techniques.
Initializing memory
We’ve enabled forms of automatic memory initialization in both Android 11’s userspace and the Linux kernel. Uninitialized memory bugs occur in C/C++ when memory is used without having first been initialized to a known safe value. These types of bugs can be confusing, and even the term “uninitialized” is misleading. Uninitialized may seem to imply that a variable has a random value. In reality it isn’t random. It has whatever value was previously placed there. This value may be predictable or even attacker controlled. Unfortunately this behavior can result in a serious vulnerability such as information disclosure bugs like ASLR bypasses, or control flow hijacking via a stack or heap spray. Another possible side effect of using uninitialized values is advanced compiler optimizations may transform the code unpredictably, as this is considered undefined behavior by the relevant C standards.
In practice, uses of uninitialized memory are difficult to detect. Such errors may sit in the codebase unnoticed for years if the memory happens to be initialized with some "safe" value most of the time. When uninitialized memory results in a bug, it is often challenging to identify the source of the error, particularly if it is rarely triggered. Eliminating an entire class of such bugs is a lot more effective than hunting them down individually. Automatic stack variable initialization relies on a feature in the Clang compiler which allows choosing initializing local variables with either zeros or a pattern. Initializing to zero provides safer defaults for strings, pointers, indexes, and sizes. The downsides of zero init are less-safe defaults for return values, and exposing fewer bugs where the underlying code relies on zero initialization. Pattern initialization tends to expose more bugs and is generally safer for return values and less safe for strings, pointers, indexes, and sizes.
Initializing Userspace:
Automatic stack variable initialization is enabled throughout the entire Android userspace. During the development of Android 11, we initially selected pattern in order to uncover bugs relying on zero init and then moved to zero-init after a few months for increased safety. Platform OS developers can build with `AUTO_PATTERN_INITIALIZE=true m` if they want help uncovering bugs relying on zero init.
Initializing the Kernel:
Automatic stack and heap initialization were recently merged in the upstream Linux kernel. We have made these features available on earlier versions of Android’s kernel including 4.14, 4.19, and 5.4. These features enforce initialization of local variables and heap allocations with known values that cannot be controlled by attackers and are useless when leaked. Both features result in a performance overhead, but also prevent undefined behavior improving both stability and security.
For kernel stack initialization we adopted the CONFIG_INIT_STACK_ALL from upstream Linux. It currently relies on Clang pattern initialization for stack variables, although this is subject to change in the future.
Heap initialization is controlled by two boot-time flags, init_on_alloc and init_on_free, with the former wiping freshly allocated heap objects with zeroes (think s/kmalloc/kzalloc in the whole kernel) and the latter doing the same before the objects are freed (this helps to reduce the lifetime of security-sensitive data). init_on_alloc is a lot more cache-friendly and has smaller performance impact (within 2%), therefore it has been chosen to protect Android kernels.
Scudo is now Android's default native allocator
In Android 11, Scudo replaces jemalloc as the default native allocator for Android. Scudo is a hardened memory allocator designed to help detect and mitigate memory corruption bugs in the heap, such as:
Double free,
Arbitrary free,
Heap-based buffer overflow,
Use-after-free
Scudo does not fully prevent exploitation but it does add a number of sanity checks which are effective at strengthening the heap against some memory corruption bugs.
It also proactively organizes the heap in a way that makes exploitation of memory corruption more difficult, by reducing the predictability of the allocation patterns, and separating allocations by sizes.
In our internal testing, Scudo has already proven its worth by surfacing security and stability bugs that were previously undetected.
Finding Heap Memory Safety Bugs in the Wild (GWP-ASan)
Android 11 introduces GWP-ASan, an in-production heap memory safety bug detection tool that's integrated directly into the native allocator Scudo. GWP-ASan probabilistically detects and provides actionable reports for heap memory safety bugs when they occur, works on 32-bit and 64-bit processes, and is enabled by default for system processes and system apps.
GWP-ASan is also available for developer applications via a one line opt-in in an app's AndroidManifest.xml, with no complicated build support or recompilation of prebuilt libraries necessary.
Software Tag-Based KASAN
Continuing work on adopting the Arm Memory Tagging Extension (MTE) in Android, Android 11 includes support for kernel HWASAN, also known as Software Tag-Based KASAN. Userspace HWASAN is supported since Android 10.
KernelAddressSANitizer (KASAN) is a dynamic memory error detector designed to find out-of-bound and use-after-free bugs in the Linux kernel. Its Software Tag-Based mode is a software implementation of the memory tagging concept for the kernel. Software Tag-Based KASAN is available in 4.14, 4.19 and 5.4 Android kernels, and can be enabled with the CONFIG_KASAN_SW_TAGS kernel configuration option. Currently Tag-Based KASAN only supports tagging of slab memory; support for other types of memory (such as stack and globals) will be added in the future.
Compared to Generic KASAN, Tag-Based KASAN has significantly lower memory requirements (see this kernel commit for details), which makes it usable on dog food testing devices. Another use case for Software Tag-Based KASAN is checking the existing kernel code for compatibility with memory tagging. As Tag-Based KASAN is based on similar concepts as the future in-kernel MTE support, making sure that kernel code works with Tag-Based KASAN will ease in-kernel MTE integration in the future.
Expanding existing compiler mitigations
We’ve continued to expand the compiler mitigations that have been rolled out in prior releases as well. This includes adding both integer and bounds sanitizers to some core libraries that were lacking them. For example, the libminikin fonts library and the libui rendering library are now bounds sanitized. We’ve hardened the NFC stack by implementing both integer overflow sanitizer and bounds sanitizer in those components.
In addition to the hard mitigations like sanitizers, we also continue to expand our use of CFI as an exploit mitigation. CFI has been enabled in Android’s networking daemon, DNS resolver, and more of our core javascript libraries like libv8 and the PacProcessor.
The effectiveness of our software codec sandbox
Prior to the Release of Android 10 we announced a new constrained sandbox for software codecs. We’re really pleased with the results. Thus far, Android 10 is the first Android release since the infamous stagefright vulnerabilities in Android 5.0 with zero critical-severity vulnerabilities in the media frameworks.
Thank you to Jeff Vander Stoep, Alexander Potapenko, Stephen Hines, Andrey Konovalov, Mitch Phillips, Ivan Lozano, Kostya Kortchinsky, Christopher Ferris, Cindy Zhou, Evgenii Stepanov, Kevin Deus, Peter Collingbourne, Elliott Hughes, Kees Cook and Ken Chen for their contributions to this post.
System hardening in Android 11 published first on https://phonetracking.tumblr.com/
0 notes
Link
0 notes
Text
Original Post from Trend Micro Author: Trend Micro
Microsoft’s Patch Tuesday for March addressed 64 vulnerabilities, 17 of which were rated critical, 45 important, one moderate, and another low in severity. Two of these vulnerabilities, CVE-2019-0797 and CVE-2019-0808, were reported to have been actively exploited in the wild. The patches addressed security flaws in a number of Microsoft products and services: .NET Framework, Edge, Exchange, Internet Explorer, Office, Office Services and Web Apps, NuGet, Team Foundation Server, and Windows. Seven of the vulnerabilities were disclosed via Trend Micro’s Zero Day Initiative (ZDI).
Meanwhile, Adobe released updates fixing three security issues in the web application development platform ColdFusion (APSB19-14), Photoshop CC (APSB19-15), and Digital Editions (APSB19-16). The vulnerability in ColdFusion versions 11, 2016, and 2018 — designated as CVE-2019-7816 — is a critical arbitrary code execution flaw that was reportedly being exploited in the wild. If successfully exploited, it could enable hackers to bypass restrictions for uploading files to a vulnerable server. Malicious code can then be uploaded and executed via HTTP request. Adobe’s security bulletin provides additional recommendations that can mitigate attacks that exploit CVE-2019-7816.
The security flaw in Photoshop (CVE-2019-7094), disclosed via ZDI, is a heap corruption vulnerability that can enable hackers to execute arbitrary code by sending users a maliciously crafted file. CVE-2019-7094 affects Photoshop CC 19.1.7, 20.0.2, and earlier versions in both Windows and macOS. The vulnerability in Digital Editions (CVE-2019-7095), a heap overflow issue, works in a similar way to CVE-2019-7094.
Notable vulnerabilities addressed by Microsoft this month include:
CVE-2019-0797, CVE-2019-0808. Privilege escalation vulnerabilities in Windows’ Win32k component that, when successfully exploited, can let hackers run arbitrary code in kernel mode, where the operating system’s core components are run. Reported by Kaspersky and Google Threat Analysis Group, respectively, these flaws were said to have been actively exploited in the wild. An exploit for CVE-2019-0808, in particular, was being chained with another then-zero-day vulnerability in Google Chrome (CVE-2019-5786) in attacks targeting Windows 7 use
CVE-2019-0697, CVE-2019-0698, CVE-2019-0726. Memory corruption vulnerabilities in Windows’ dynamic host configuration protocol (DHCP) client, which is used to obtain configuration information such as IP addresses. While there are no indications that these flaws are actively exploited, what’s significant in these vulnerabilities is that they don’t require user interaction. An attacker can send a malformed DHCP response/network packet to a client/host that exploits the vulnerabilities, leaving the targeted system susceptible to remote code execution (RCE).
The Trend Micro Deep Security and Vulnerability Protection solutions protect user systems from threats that may target the vulnerabilities addressed in this month’s Patch Tuesday via the following Deep Packet Inspection (DPI) rules:
1009535 — Microsoft SharePoint Remote Code Execution Vulnerability (CVE-2019-0604)
1009475 — Microsoft Windows Data Sharing Service Elevation of Privilege Vulnerability (CVE-2019-0571)
1009563 — Microsoft Internet Explorer VBScript Engine Remote Code Execution Vulnerability (CVE-2019-0665)
1009564 — Microsoft Edge Scripting Engine Memory Corruption Vulnerability (CVE-2019-0769)
1009565 — Microsoft Edge Scripting Engine Memory Corruption Vulnerability (CVE-2019-0770)
1009566 — Microsoft Edge Scripting Engine Memory Corruption Vulnerability (CVE-2019-0771)
1009567 — Microsoft Edge Scripting Engine Memory Corruption Vulnerability (CVE-2019-0773)
1009568 — Microsoft Internet Explorer Memory Corruption Vulnerability (CVE-2019-0763)
1009569 — Microsoft Internet Explorer Scripting Engine Memory Corruption Vulnerability (CVE-2019-0680)
1009570 — Microsoft Internet Explorer Security Feature Bypass Vulnerability (CVE-2019-0768)
1009571 — Microsoft Windows Multiple Information Disclosure Vulnerabilities (CVE-2019-0755, CVE-2019-0767, CVE-2019-0775)
1009573 — Microsoft Edge Security Feature Bypass Vulnerability (CVE-2019-0612)
1009574 — Microsoft Edge Scripting Engine Memory Corruption Vulnerability (CVE-2019-0639)
1009575 — Microsoft Internet Explorer and Edge Scripting Engine Memory Corruption Vulnerability (CVE-2019-0609)
1009576 — Microsoft Windows VBScript Engine Remote Code Execution Vulnerability (CVE-2019-0666)
1009577 — Microsoft Edge Chakra Scripting Engine Memory Corruption Vulnerability (CVE-2019-0592)
1009578 — Microsoft Internet Explorer VBScript Engine Remote Code Execution Vulnerability (CVE-2019-0667)
1009579 — Microsoft Windows SMB Information Disclosure Vulnerability (CVE-2019-0703)
1009582 — Microsoft Windows Win32k Elevation Of Privilege Vulnerability (CVE-2019-0808)
1009583 — Microsoft Windows Win32k Elevation Of Privilege Vulnerability (CVE-2019-0797)
The Trend Micro TippingPoint® solution protects customers from threats that may exploit the aforementioned vulnerabilities via these MainlineDV filters:
34687: HTTP: Microsoft Edge DataView Out-of-Bounds Write Vulnerability
34688: HTTP: Microsoft Edge Use-After-Free Vulnerability
34689: HTTP: Microsoft Edge adoptNode Security Feature Bypass Vulnerability
34690: HTTP: Microsoft Edge prototype Type Confusion Vulnerability
34691: HTTP: Microsoft Internet Explorer Use-After-Free Vulnerability
34692: HTTP: Microsoft Internet Explorer RegExp Buffer Overflow Vulnerability
34693: HTTP: Microsoft Internet Explorer Use-After-Free Vulnerability
34694: HTTP: Microsoft Internet Explorer Worker Use-After-Free Vulnerability
34695: SMB: Microsoft Windows Information Disclosure Vulnerability
34696: HTTP: Microsoft Windows Kernel Information Disclosure Vulnerability
34697: HTTP: Microsoft Internet Explorer execCommand Use-After-Free Vulnerability
34698: HTTP: Microsoft Windows Information Disclosure Vulnerability
34699: HTTP: Microsoft Internet Explorer MSHTML Security Bypass Vulnerability
34700: HTTP: Microsoft Edge Type Confusion Vulnerability
34701: HTTP: Microsoft Edge Memory Corruption Vulnerability
34702: HTTP: Microsoft Edge Chakra initProto Memory Corruption Vulnerability
34703: HTTP: Microsoft Edge JIT Type Confusion Vulnerability
34704: HTTP: Microsoft Windows Information Disclosure Vulnerability
34776: HTTP: Adobe ColdFusion Suspicious Multipart File Upload
34777: HTTP: Microsoft Windows Win32k Privilege Escalation Vulnerability
34779: HTTP: Adobe ColdFusion Suspicious File Upload
The post March’s Patch Tuesday Fixes Privilege Escalation Vulnerabilities Exploited in the Wild appeared first on .
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Trend Micro March’s Patch Tuesday Fixes Privilege Escalation Vulnerabilities Exploited in the Wild Original Post from Trend Micro Author: Trend Micro Microsoft’s Patch Tuesday for March addressed 64 vulnerabilities, 17 of which were rated critical, 45 important, one moderate, and another low in severity. 892 more words
0 notes
Text
JSA10770 - 2017-01 Security Bulletin: Junos Space: Multiple vulnerabilities resolved in 16.1R1 release.
https://cyberparse.co.uk/2017/01/11/jsa10770-2017-01-security-bulletin-junos-space-multiple-vulnerabilities-resolved-in-16-1r1-release-2/ https://i0.wp.com/cyberparse.co.uk/wp-content/uploads/2016/04/security-binary-pd-898757.jpg?fit=3888%2C2592&ssl=1
CVE CVSS base score Summary CVE-2016-1762 9.8 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) The xmlNextChar function in libxml2 allows remote attackers to cause a denial of service (heap-based buffer over-read) via a crafted XML document. CVE-2016-4448 9.8 (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) Format string vulnerability in libxml2 allows attackers to have unspecified impact via format string specifiers in unknown vectors. CVE-2015-5364 7.8 (AV:N/AC:L/Au:N/C:N/I:N/A:C) The (1) udp_recvmsg and (2) udpv6_recvmsg functions in the Linux kernel do not properly consider yielding a processor, which allows remote attackers to cause a denial of service (system hang) via incorrect checksums within a UDP packet flood. CVE-2016-6515 7.8 (AV:N/AC:L/Au:N/C:N/I:N/A:C) The auth_password function in auth-passwd.c in sshd in OpenSSH before 7.3 does not limit password lengths for password authentication, which allows remote attackers to cause a denial of service (crypt CPU consumption) via a long string. CVE-2015-8325 7.2 (AV:L/AC:L/Au:N/C:C/I:C/A:C) The do_setup_env function in session.c in sshd in OpenSSH through 7.2p2, when the UseLogin feature is enabled and PAM is configured to read .pam_environment files in user home directories, allows local users to gain privileges by triggering a crafted environment for the /bin/login program, as demonstrated by an LD_PRELOAD environment variable. CVE-2016-1833 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) The htmlCurrentChar function in libxml2 allows remote attackers to cause a denial of service (heap-based buffer over-read) via a crafted XML document. CVE-2016-1834 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) Heap-based buffer overflow in the xmlStrncat function in libxml2 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted XML document. CVE-2016-1835 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) Use-after-free vulnerability in the xmlSAX2AttributeNs function in libxml2 allows remote attackers to cause a denial of service via a crafted XML document. CVE-2016-1836 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) Use-after-free vulnerability in the xmlDictComputeFastKey function in libxml2 allows remote attackers to cause a denial of service via a crafted XML document. CVE-2016-1837 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) Multiple use-after-free vulnerabilities in the (1) htmlPArsePubidLiteral and (2) htmlParseSystemiteral functions in libxml2 allow remote attackers to cause a denial of service via a crafted XML document. CVE-2016-1838 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) The xmlPArserPrintFileContextInternal function in libxml2 allows remote attackers to cause a denial of service (heap-based buffer over-read) via a crafted XML document. CVE-2016-1839 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) The xmlDictAddString function in libxml2 allows remote attackers to cause a denial of service (heap-based buffer over-read) via a crafted XML document. CVE-2016-1840 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) Heap-based buffer overflow in the xmlFAParsePosCharGroup function in libxml2 before 2.9.4, as used in Apple iOS before 9.3.2, OS X before 10.11.5, tvOS before 9.2.1, and watchOS before 2.2.1, allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted XML document. CVE-2016-5573 6.8 (AV:N/AC:M/Au:N/C:P/I:P/A:P) Vulnerability in Java related to Hotspot. CVE-2016-4449 5.8 (AV:N/AC:M/Au:N/C:P/I:N/A:P) XML external entity (XXE) vulnerability in the xmlStringLenDecodeEntities function in parser.c in libxml2 before 2.9.4, when not in validating mode, allows context-dependent attackers to read arbitrary files or cause a denial of service (resource consumption) via unspecified vectors. CVE-2016-5387 5.1 (AV:N/AC:H/Au:N/C:P/I:P/A:P) The Apache HTTP Server through 2.4.23 follows RFC 3875 section 4.1.18 and therefore does not protect applications from the presence of untrusted client data in the HTTP_PROXY environment variable, which might allow remote attackers to redirect an application’s outbound HTTP traffic to an arbitrary proxy server via a crafted Proxy header in an HTTP request, aka an “httpoxy” issue. NOTE: the vendor states “This mitigation has been assigned the identifier CVE-2016-5387”; in other words, this is not a CVE ID for a vulnerability. CVE-2015-5366 5.0 (AV:N/AC:L/Au:N/C:N/I:N/A:P) The (1) udp_recvmsg and (2) udpv6_recvmsg functions in the Linux kernel before 4.0.6 provide inappropriate -EAGAIN return values, which allows remote attackers to cause a denial of service (EPOLLET epoll application read outage) via an incorrect checksum in a UDP packet, a different vulnerability than CVE-2015-5364. CVE-2016-1907 5.0 (AV:N/AC:L/Au:N/C:N/I:N/A:P) The ssh_packet_read_poll2 function in packet.c in OpenSSH before 7.1p2 allows remote attackers to cause a denial of service (out-of-bounds read and application crash) via crafted network traffic. CVE-2016-3627 5.0 (AV:N/AC:L/Au:N/C:N/I:N/A:P) The xmlStringGetNodeList function in tree.c in libxml2 2.9.3 and earlier, when used in recovery mode, allows context-dependent attackers to cause a denial of service (infinite recursion, stack consumption, and application crash) via a crafted XML document. CVE-2016-3705 5.0 (AV:N/AC:L/Au:N/C:N/I:N/A:P) The (1) xmlParserEntityCheck and (2) xmlParseAttValueComplex functions in parser.c in libxml2 2.9.3 do not properly keep track of the recursion depth, which allows context-dependent attackers to cause a denial of service (stack consumption and application crash) via a crafted XML document containing a large number of nested entity references. CVE-2016-4447 5.0 (AV:N/AC:L/Au:N/C:N/I:N/A:P) The xmlParseElementDecl function in parser.c in libxml2 allows context-dependent attackers to cause a denial of service (heap-based buffer underread and application crash) via a crafted file, involving xmlParseName. CVE-2015-5307 4.9 (AV:L/AC:L/Au:N/C:N/I:N/A:C) The KVM subsystem in the Linux kernel allows guest OS users to cause a denial of service (host OS panic or hang) by triggering many #AC (aka Alignment Check) exceptions, related to svm.c and vmx.c. CVE-2015-8104 4.7 (AV:L/AC:M/Au:N/C:N/I:N/A:C) The KVM subsystem in the Linux kernel allows guest OS users to cause a denial of service (host OS panic or hang) by triggering many #DB (aka Debug) exceptions, related to svm.c. CVE-2016-6662 0.0 (AV:N/AC:L/Au:N/C:N/I:N/A:N) Vulnerability in MySQL allow local users to create arbitrary configurations and bypass certain protection mechanisms by setting general_log_file to a my.cnf configuration. NOTE: Since this issue does not allow a Junos Space local user to increase privileges, the effective CVSS base score is zero. CVE-2016-5195 0.0 (AV:L/AC:L/Au:N/C:N/I:N/A:N) Race condition in mm/gup.c in the Linux kernel allows local users to gain privileges by leveraging incorrect handling of a copy-on-write (COW) feature to write to a read-only memory mapping, as exploited in the wild in October 2016, aka “Dirty COW.” NOTE: Since this issue does not allow a Junos Space local user to increase privileges, the effective CVSS base score is zero.
Source The Register - Security
0 notes
Text
Debian 8.6 update release
The Debian project is pleased to announce the sixth update of its stable distribution Debian 8 (codename jessie). This update mainly adds corrections for security problems to the stable release, along with a few adjustments for serious problems. Security advisories were already published separately and are referenced where available.
Please note that this update does not constitute a new version of Debian 8 but only updates some of the packages included. There is no need to throw away old jessie CDs or DVDs but only to update via an up-to-date Debian mirror after an installation, to cause any out of date packages to be updated.
Those who frequently install updates from security.debian.org won't have to update many packages and most updates from security.debian.org are included in this update.
New installation media and CD and DVD images containing updated packages will be available soon at the regular locations.
Upgrading to this revision online is usually done by pointing the aptitude (or apt) package tool (see the sources.list(5) manual page) to one of Debian's many FTP or HTTP mirrors. A comprehensive list of mirrors is available at:
https://www.debian.org/mirror/list
Miscellaneous Bug Fixes
This stable update adds a few important corrections to the following packages:
Package
Reason
adblock-plus
New upstream release, compatible with firefox-esr
apache2
Fix race condition and logical error in init script; remove links to manpages.debian.org in default index.html; mod_socache_memcache: Increase idle timeout to 15s to allow keep-alive connections; mod_proxy_fcgi: Fix wrong behaviour with 304 responses; correct systemd-sysv-generator behaviour; mod_proxy_html: Add missing config file mods-available/proxy_html.conf
audiofile
Fix buffer overflow when changing both sample format and number of channels [CVE-2015-7747]
automake-1.14
Avoid insecure use of /tmp/ in install-sh
backintime
Add missing dependency on python-dbus
backuppc
Fix regressions from samba update to 4.2
base-files
Update for the point release
biber
Fix breakage triggered by point release update of perl
cacti
Fix sql injection in tree.php [CVE-2016-3172] and graph_view.php [CVE-2016-3659]; fix authentication bypass [CVE-2016-2313]
ccache
Upstream bug-fix release
clamav
Don't fail if AllowSupplementaryGroups is still set in the configuration file
cmake
Fix FindOpenSSL module to detect OpenSSL 1.0.1t
conkeror
Support Firefox 44 and later
debian-edu-config
Move from Iceweasel to Firefox ESR; adjust ldap-tools/ldap-debian-edu-install to be compliant with systemd now that unit samba.service is masked; dhclient-exit-hooks.d/hostname: adjust for the case of a dedicated LTSP server; adjust cf.krb5client to ensure that cfengine runs are idempotent; move code to cleanup /usr/share/pam-configs/krb5 diversion from postinst to preinst to ease upgrades from old wheezy installations; don't purge libnss-mdns as cups now needs mdns for automatic printer detection
debian-edu-doc
Update Debian Edu jessie and wheezy manuals from the wiki
debian-installer
Rebuild against proposed-updates
debian-installer-netboot-images
Rebuild for the point release
debian-security-support
Update included support data; add support for marking packages as losing support at a future date
dietlibc
Fix insecure default PATH
dwarfutils
Security fixes [CVE-2015-8538 CVE-2015-8750 CVE-2016-2050 CVE-2016-2091 CVE-2016-5034 CVE-2016-5036 CVE-2016-5038 CVE-2016-5039 CVE-2016-5042]
e2fsprogs
Disable prompts for time skew which is fudged in e2fsck; fix potential corruption of Hurd file systems by e2fsck, pointer bugs that could cause crashes in e2fsck and resize2fs
exim4
Fix cutthrough bug with body lines having a single dot; fix crash on exim -be '${if crypteq{xxx}{\$aaa}{yes}{no}}'; improve NEWS file; backport missing upstream patch to actually make $initial_cwd expansion work
file
Fix buffer over-write in finfo_open with malformed magic file [CVE-2015-8865]
firegestures
New upstream release, compatible with firefox-esr
flashplugin-nonfree
Update-flashplugin-nonfree: Delete old get-upstream-version.pl from cache
fusionforge
Remove dependency on Mediawiki plugin from fusionforge-full metapackage
gdcm
Fix integer overflow [CVE-2015-8396] and denial of service [CVE-2015-8397]
glibc
Fix assertion failure with unconnectable name server addresses (regression introduced by CVE-2015-7547 fix); fix *context functions on s390x; fix a buffer overflow in the glob function [CVE-2016-1234], a stack overflow in nss_dns_getnetbyname_r [CVE-2016-3075], a stack overflow in getaddrinfo function [CVE-2016-3706], a stack overflow in Sun RPC clntudp_call() [CVE-2016-4429]; update from upstream stable branch; fix open and openat functions with O_TMPFILE; fix backtrace hang on armel/armhf, possibly causing a minor denial of service vulnerability [CVE-2016-6323]; fix mtr on systems using only IPv6 nameservers
gnome-maps
New upstream release; use the Mapbox tile server, instead of the no longer supported MapQuest server
gnome-sudoku
Don't generate the same puzzle sequence every time
gnupg
gpgv: Tweak default options for extra security; g10: Fix checking key for signature validation
gnupg2
gpgv: Tweak default options for extra security; g10: Fix checking key for signature validation
greasemonkey
New upstream release, compatible with firefox-esr
intel-microcode
New upstream release
jakarta-jmeter
Really install the templates; fix an error with libxstream-java >= 1.4.9 when loading the templates
javatools
Return correct architecture string for ppc64el in java-arch.sh
kamailio
Fix libssl version check
libbusiness-creditcard-perl
Adjust to changes in credit card ranges and processing of various companies
libcss-dom-perl
Work around Encode changes included in perl and libencode-perl stable updates
libdatetime-timezone-perl
Update included data to 2016e; new upstream release
libdevel-declare-perl
Fix breakage caused by change in perl stable update
libnet-ssleay-perl
Fix build failure with openssl 1.0.1t-1+deb8u1
libquota-perl
Adapt platform detection to work with Linux 4.x
libtool
Fix multi-arch co-installability [amd64 i386]
libxml2
Fix a problem unparsing URIs without a host part like qemu:///system; this unbreaks libvirt, libsys-virt-perl and others
linux
New upstream stable release
lxc
Make sure stretch/sid containers have an init system, after init 1.34 dropped the 'Essential: yes' header
mariadb-10.0
New upstream release, including security fix [CVE-2016-6662]
mozilla-noscript
New upstream release, compatible with firefox-esr
nullmailer
Do not keep relayhost data in debconf database longer than strictly needed
open-iscsi
Init script: wait a bit after iSCSI devices have appeared, working around a race condition in which dependent devices can appear only after the initial udev settle has returned; open-iscsi-udeb: update initramfs after copying configuration to target system
openssl
Fix length check for CRLs; enable asm optimisation for s390x
ovirt-guest-agent
Install ovirt-guest-agent.py executable; change owner of log directory to ovirtagent in postinst
piuparts
Fix build failure (don't test the current Debian release status, tracking that is distro-info-data's problem)
policykit-1
Several bug-fixes: fix heap corruption [CVE-2015-3255], local authenticated denial of service [CVE-2015-4625] and issue with invalid object paths in RegisterAuthenticationAgent [CVE-2015-3218]
publicsuffix
New upstream release
pypdf2
Fix infinite loop in readObject() function
python-django
Bug-fix update to 1.7.11
python2.7
Address StartTLS stripping attack in smtplib [CVE-2016-0772], integer overflow in zipimporter [CVE-2016-5636], HTTP header injection [CVE-2016-5699]
quassel
Fix remote DoS in quassel core with invalid handshake data [CVE-2016-4414]
ruby-eventmachine
Fix remotely triggerable crash due to FD handling
ruby2.1
dl::dlopen should not open a library with tainted library name in safe mode [CVE-2009-5147]; Fiddle handles should not call functions with tainted function names [CVE-2015-7551]
sendmail
Do not abort with an assertion if the connection to an LDAP server is lost; ensure sendmail {client_port} is set correctly on little endian machines
sqlite3
Fix tempdir selection vulnerability [CVE-2016-6153], segfault following heavy SAVEPOINT usage
systemd
Use the right timeout for stop processes we fork; don't reset log level to NOTICE if we get quiet on the kernel cmdline; fix prepare priority queue comparison function in sd-event; update links to kernel.org cgroup documentation; don't start console-getty.service when /dev/console is missing; order systemd-user-sessions.service after nss-user-lookup.target and network.target
tabmixplus
New upstream release, compatible with firefox-esr
tcpreplay
Handle frames of 65535 octets size, add a size check [CVE-2016-6160]
tor
Update the set of authority directory servers
tzdata
New upstream release; update to 2016e
unbound
Init script fixes: add pidfile magic comment; call start-stop-daemon with --retry for 'stop' action
util-vserver
Rebuild against dietlibc 0.33~cvs20120325-6+deb8u1, fixing insecure default PATH
vorbis-tools
Fix large alloca on bad AIFF input to oggenc [CVE-2015-6749], Validate count of channels in the header [CVE-2014-9638 CVE-2014-9639], fix segmentation fault in vcut
vtk
Rebuild to fix Java paths [ppc64el]
wget
By default, on server redirects to a FTP resource, use the original URL to get the local file name [CVE-2016-4971]
wpa
Security updates relating to invalid characters [CVE-2016-4476, CVE-2016-4477]
yaws
Fix HTTP_PROXY cgi env injection [CVE-2016-1000108]
zabbix
Fix mysql.size shell command injection in zabbix-agent [CVE-2016-4338]
The mariadb-10.0 package failed to build on the powerpc architecture, but has been included in the point release to allow quicker release of the fix for CVE-2016-6662, which had not been disclosed at the time of the upload. If a fix for the build failure becomes available before the next mariadb-10.0 DSA, an updated package may be released via jessie-updates.
1 note
·
View note