#laravel 2fa
Explore tagged Tumblr posts
Text
Top 10 Key Points to Ensure Security for Your Laravel Application

In Laravel web application development, security is one of the essential paramount. As the digital landscape continues to expand, the Importance of security in web applications, particularly those built on the Laravel framework, has reached an all-time high. In this era of interconnectedness, where information flows seamlessly across the virtual realm, the potential threats and vulnerabilities have also escalated.
The landscape of online threats has grown more sophisticated, encompassing various malicious activities ranging from data breaches to identity theft. This evolving threat landscape calls for a steadfast commitment to proactive security measures. Waiting for a security breach before addressing vulnerabilities is a risk no modern developer can afford to take.
The significance of bolstering security in Laravel web application development. While Laravel provides a robust and versatile platform for creating dynamic web applications, it's essential to recognize that even the most advanced framework is not immune to potential security breaches. As your Laravel application evolves, it becomes a showcase of your technological prowess and a potential target for cyber threats.
The Importance of proactive security measures should be highlighted further. Developers and businesses must adopt a security-first mindset when crafting their digital creations, which means staying informed about the latest security trends, continuously updating and patching the application, and adhering to best practices for safeguarding sensitive user data.
We'll delve into 10 critical checkpoints that can significantly enhance the security of your Laravel web application. These checkpoints encompass a comprehensive approach to securing various aspects of your application, from authentication and authorization to protecting against common web vulnerabilities. By diligently implementing these checkpoints, you'll be taking a substantial stride towards fortifying your Laravel web application against the ever-persistent threats lurking in the digital domain.
10 Key Checkpoints to Focus On
Here's your comprehensive Laravel Security Checklist to ensure a robust and safeguarded web application.
1. Secure Authentication and Authorization

In the intricate world of Laravel web application development, security is an indispensable pillar for creating a trustworthy and resilient digital presence. One of the cornerstone elements in this security fortress is the implementation of secure authentication and authorization mechanisms. Let's delve into how these critical aspects are pivotal in fortifying your Laravel application against potential threats.
Secure Authentication: Building the First Line of Defense
Authentication is verifying the identity of users attempting to access your application. It forms the cornerstone of security by ensuring that only authorized individuals can interact with sensitive data and functionalities. In the realm of Laravel, this process is made significantly more manageable through the framework's built-in authentication features.
Implementing secure authentication involves
Strong Password Policies: Enforce complex passwords, combining uppercase and lowercase letters, numbers, and special characters. Laravel provides password validation rules to help you accomplish this.
Two-Factor Authentication (2FA): Enhance security by requiring users to provide an additional authentication factor beyond their password. Laravel offers seamless integration with 2FA for an added layer of protection.
Account Lockouts: Implement mechanisms that lock accounts after a specified number of unsuccessful login attempts, preventing brute-force attacks by temporarily halting further login attempts.
Authorization: Ensuring Granular Access Control
Authorization, however, deals with controlling what authenticated users can do within the application. It's about granting permissions and access rights based on roles and responsibilities, ensuring that sensitive actions are restricted to those who need them.
Key steps in implementing effective authorization include
Role-Based Access Control (RBAC): Define roles such as "admin," "user," or "manager," and associate them with specific permissions. Laravel's RBAC system lets you assign roles and permissions effortlessly.
Middleware Authorization: Leverage Laravel's middleware to restrict access to routes or controllers based on user roles or custom conditions. This is a powerful way to ensure that only authorized users can perform specific actions.
Resource Controllers: Utilize resource controllers to create a consistent and structured approach to handling CRUD operations. These controllers can be easily configured to enforce authorization rules for specific actions.
Dynamic Authorization Policies: Laravel's policy system lets you define authorization logic in a structured manner. It's beneficial for complex access control requirements and allows for fine-grained control over what users can do.
In a world where digital threats are evolving rapidly, securing your Laravel application's authentication and authorization processes is paramount. By implementing robust authentication mechanisms and enforcing precise authorization rules, you're safeguarding sensitive data and building a foundation of trust with your users. Remember, security isn't just a one-time task; it's an ongoing commitment that requires vigilance and adaptability in the face of ever-changing cyber threats.
2. Keep Laravel and Dependencies Updated
In the dynamic realm of Laravel web application development, staying ahead in the security game is an ongoing endeavor. One of the fundamental practices that forms the bedrock of a secure digital presence is the consistent updating of your Laravel framework and its associated dependencies. Let's explore why this practice is essential and how it contributes to the overall security of your application.
The Power of Regular Updates
Technology, much like the world around us, is in a constant state of evolution. This evolution is driven not only by innovation but also by identifying and rectifying vulnerabilities and weaknesses. In the context of Laravel development, regular updates to both the core framework and its dependencies play a pivotal role in ensuring the security and stability of your application.
Why Updates Matter
Security Patches: Vulnerabilities can emerge at any software lifecycle stage. Developers and the open-source community work diligently to identify and address these vulnerabilities. Regular updates ensure that your Laravel application is fortified with the latest security patches, minimizing the risk of exploitation.
Compatibility: As Laravel evolves, updates often improve compatibility with newer PHP versions, web servers, and databases. Staying updated ensures your application remains in sync with the broader web development ecosystem.
Performance and Features: Updates not only fix issues; they also introduce performance enhancements and new features. Embracing these updates can lead to a more efficient application that delivers a better user experience.
Dependencies: Handle with Care
Laravel development heavily relies on various external packages and libraries. While these dependencies contribute to the efficiency and functionality of your application, they can also introduce vulnerabilities if not managed appropriately.
Best Practices for Dependency Management:
Regular Audits: Periodically review the dependencies your Laravel development company utilizes. Check for any vulnerabilities reported in these packages and prioritize updating them accordingly.
Automated Tools: Leverage automated tools that can scan your project's dependencies for known security issues. This can help you identify potential risks and take corrective action swiftly.
Version Pinning: Specify the exact versions of dependencies your application uses. This prevents unexpected updates that might introduce breaking changes or vulnerabilities.
In the rapidly evolving web application security landscape, treating updates as a proactive security measure is paramount. By ensuring your Laravel framework and dependencies are up to date, you're demonstrating a commitment to maintaining a robust digital fortress for your application. This safeguards sensitive user data and positions your Laravel development company as a conscientious custodian of digital security. Remember, in technology, staying current isn't just an option—it's necessary for a secure and successful future.
3. Validate User Input
The ever-evolving landscape of Laravel development, the adage "Garbage In, Garbage Out" holds immense relevance. One of the pivotal checkpoints in ensuring the robustness of your Laravel application's security is the validation of user input. Let's dive into why validating user input is crucial and how it is a formidable shield against potential vulnerabilities.
The Essence of User Input Validation
User input is the gateway through which your Laravel application interacts with its users. Whether it's a login form, a search bar, or a comment section, user input is integral to the functionality of your application. However, it can also become an entry point for malicious activities if left unchecked.
Why Validate User Input:
Mitigating Injection Attacks: Attackers can exploit unvalidated user input to inject malicious code into your application. This includes infamous threats like SQL injection and cross-site scripting (XSS). Proper validation drastically reduces the risk of such attacks.
Data Integrity: Validating user input ensures that the data flowing into your application is consistent and matches the expected format. This helps maintain data integrity and prevents errors caused by unexpected information.
Enhancing User Experience: You can guide users to input data in the correct format by providing real-time validation feedback. This not only prevents submission errors but also enhances the overall user experience.
Implementing Effective Input Validation in Laravel
Utilize Laravel's Validation Rules: Laravel offers a robust validation system that includes a wide array of predefined rules. These rules cover everything from required fields and email formats to custom validation logic.
Sanitize and Filter Input: Consider sanitizing and filtering user input alongside validation. Sanitization removes potentially harmful characters, while filtering ensures that information adheres to specific formats.
Client-Side Validation: While server-side validation is paramount, supplement it with client-side validation using JavaScript. This provides instant feedback to users and reduces unnecessary server requests.
Best Practices for User Input Validation
Never Trust User Input: Treat all incoming user input as potentially malicious until proven otherwise. Validate and sanitize input even if it seems harmless.
Whitelist Validation: Define an allowlist of allowed characters and formats for each input field. Reject input that doesn't conform to these predefined patterns.
Regular Updates: Like any other security practice, stay updated with Laravel's latest validation features and best practices. This ensures you're using the most effective tools available.
In the intricate realm of Laravel development, user input validation isn't just a technical practice; it's a shield that guards your application against many threats. By diligently validating user input, you're bolstering your application's security and reinforcing trust with your users. In the dynamic world of web development, where innovation meets vulnerability, validation is your steadfast ally in pursuing a secure and seamless user experience.
4. Protect Against SQL Injection

Shielding your digital fortress through meticulous Laravel development services involves a critical step: Protect against SQL injection. This threat arises when user inputs lack proper sanitation, potentially enabling malicious actors to manipulate SQL queries and gain unauthorized database access.
SQL injection attacks can lead to data exposure, alteration, or deletion. Laravel's defences are robust. Its query binding technique parameterizes user inputs, preventing malicious SQL execution. The Eloquent ORM further enhances security by abstracting SQL interactions and automatically escaping values.
Adhering to best practices is paramount. Prioritize parameterized queries over direct concatenation, sanitize inputs, and conduct regular code audits to ensure secure methods. By fortifying your Laravel application against SQL injection, you're erecting a robust barrier against a damaging vulnerability while providing your Laravel development services maintain the utmost integrity and user trust.
5. Cross-Site Scripting (XSS) Prevention
In securing your digital haven with proficient Laravel development practices, countering Cross-Site Scripting (XSS) emerges as a pivotal measure. XSS occurs when malicious code infiltrates a website through unfiltered user inputs, potentially compromising user data and integrity.
The gravity of XSS lies in its ability to expose sensitive information or perform malicious actions under the user's identity. Laravel offers potent tools to thwart such threats:
Blade Templating: Laravel's Blade templating engine automatically escapes variables, preventing unintended script execution.
XSS Middleware: Laravel provides built-in middleware for encoding user inputs, adding an extra layer of protection.
Content Security Policy (CSP): Implementing CSP headers in your Laravel application restricts the sources from which content can be loaded, reducing the risk of XSS attacks.
Adhering to these precautions is essential. Validate and sanitize inputs, embrace Laravel's security features, and implement a robust CSP. By guarding against XSS vulnerabilities, you ensure your Laravel development maintains a resilient and trustworthy digital presence.
6. Implement HTTPS and SSL
In web application development, particularly in Laravel, bolstering security is paramount. A crucial step in this pursuit is the implementation of HTTPS and SSL protocols. These measures are essential to safeguard sensitive data transmitted between users and your application.
HTTPS (Hypertext Transfer Protocol Secure) encrypts the data between users' browsers and your application's server, thwarting potential eavesdropping and tampering. SSL (Secure Sockets Layer) certificates are the foundation of this encryption, ensuring that communication remains confidential.
Advantages of HTTPS and SSL:
Data Encryption: HTTPS encrypts data during transit, preventing unauthorized access to sensitive information.
Trust and SEO: SSL certificates enhance user trust, as indicated by the padlock symbol in browsers. Search engines also favor HTTPS websites, improving SEO rankings.
Authentication: SSL certificates verify your application's authenticity, shielding users from potential phishing sites.
Implementing HTTPS and SSL involves obtaining a valid SSL certificate and configuring your Laravel application for secure connections. By adopting these measures, you're securing your web application development, fostering trust among users, and ensuring compliance with modern security standards.
7. Secure Session Management
In web application development, security isn't just a feature—it's a necessity. A crucial aspect of building a robust and trustworthy application is ensuring secure session management. Sessions are pivotal in maintaining user interactions and data, making their protection paramount.
Laravel offers robust mechanisms to fortify session management:
Session Encryption: Laravel automatically encrypts session data, preventing unauthorized access and ensuring confidentiality.
CSRF Protection: Cross-Site Request Forgery (CSRF) attacks can compromise sessions. Laravel's built-in CSRF protection safeguards against such threats.
Expire and Regenerate: Set session expiration times and periodically regenerate session IDs to minimize the window of vulnerability.
By implementing secure session management practices in your web application development, you create a shield against unauthorized access and data breaches. This preserves user trust and solidifies your commitment to crafting applications that prioritize security and integrity.
8. Protect Against Cross-Site Request Forgery (CSRF)
Safeguarding web applications is a top priority in Laravel development. To fortify your digital haven, countering Cross-Site Request Forgery (CSRF) threats is crucial. CSRF attacks manipulate authenticated users into executing malicious actions unknowingly. Laravel provides a robust defense:
CSRF Tokens: Laravel automatically generates unique tokens for each user session, validating the authenticity of requests.
Middleware Protection: Laravel's built-in CSRF middleware verifies tokens, preventing unauthorized requests from being executed.
By integrating these measures, you fortify your Laravel application against CSRF vulnerabilities. This secures user interactions and demonstrates your commitment to proactive security practices in modern web development.
9. Harden Configuration and File Permissions
In the landscape of Laravel security, enhancing configuration settings and file permissions is a critical stride. Securing sensitive files, such as configuration files, shields against unauthorized access and potential breaches. Laravel's framework offers key tactics:
Restricted Access: Limit access to sensitive configuration files by setting appropriate permissions. This prevents unauthorized users from tampering with vital settings.
Environment Configuration: Store sensitive data in environment files and never expose them in version control. Laravel's .env file shields sensitive variables from prying eyes.
By meticulously configuring permissions and safeguarding critical files, you erect a solid barrier against potential threats. This reflects an unwavering commitment to fortifying your Laravel application and upholding security standards in modern web development.
10. Use Content Security Policy (CSP)
Bolstering security in Laravel involves advanced tactics, including a Content Security Policy (CSP). CSP guards against cross-site scripting (XSS) and data injection attacks. It achieves this by specifying approved content sources, mitigating the risk of malicious script execution. Laravel's integration of CSP fortifies your defense:
Malicious Content Mitigation: CSP curtails the potential impact of XSS attacks by regulating the domains from which content can be loaded.
Policy Customization: Laravel empowers you to tailor CSP rules to suit your application's specific requirements, balancing security and functionality.
By embracing CSP, you establish a robust security framework that exemplifies Laravel's commitment to secure, modern web development practices.
Top Laravel Security Packages for Developers
In the realm of Laravel development, ensuring robust security is paramount. Several key packages aid developers in fortifying their applications. Here are three notable options:
Laravel-ACL: Access Control Lists (ACL) are fundamental to controlling user permissions. This package simplifies ACL implementation, offering granular control over user access to different parts of your application.
Laravel Security: As the name suggests, this package enhances overall security. It provides features like XSS protection, safe redirects, and content filtering, contributing to a fortified application.
Laravel Security Component: This package takes security up a notch by integrating robust security components. It includes encryption, hashing, validation, and more tools, streamlining your security efforts.
For a Laravel development agency, these packages are invaluable assets. By incorporating them into your development process, you expedite security implementation and establish a strong foundation for crafting secure, reliable applications that clients can trust.
Conclusion
In the intricate realm of Laravel security, these checkpoints act as sentinels, fortifying your application's defenses. Secure authentication, vigilant updates, meticulous validation, and shielded configurations create a robust bastion. Protection against threats like SQL injection, XSS, and CSRF forms an unbreachable wall. Implementation of HTTPS, secure session handling, and CSP reinforce your fortifications. Familiarity with essential security packages like Laravel-ACL, Laravel Security, and Security Component adds the final layer. As a Laravel developer, embracing these measures ensures your applications are secured, and your expertise is unwavering in the face of evolving threats.
Source: Top 10 Key Points to Ensure Security for Your Laravel Application
2 notes
·
View notes
Text
How to Choose the Right Security Stack for Your Business Website
In an age where cyberattacks are growing more frequent and sophisticated, a secure website isn’t just a best practice—it’s a business necessity. Whether you're running an eCommerce store, SaaS product, or a company website, your security stack plays a critical role in protecting sensitive data, maintaining customer trust, and ensuring compliance.
A professional Web Development Company will always prioritize building a tailored security framework that addresses both current risks and future vulnerabilities. But how do you decide which tools and layers should be part of your website's defense system?
Let’s break down what a “security stack” means and how to choose the right one for your business.
What Is a Website Security Stack?
A security stack is a layered approach to website protection. It combines various technologies and tools—each targeting a specific set of threats—to create a comprehensive shield around your web infrastructure.
Think of it like a multi-lock system for your home:
One layer protects your doors (authentication)
Another secures your windows (firewalls)
And another watches for unusual activity (monitoring tools)
When configured properly, these layers work together to identify, prevent, and respond to attacks—without compromising website speed or functionality.
1. Start With an SSL/TLS Certificate
This is the most basic, yet crucial, layer. An SSL/TLS certificate encrypts the data exchanged between your website and its users. It ensures that personal information, passwords, and payment details can't be intercepted by third parties.
Make sure:
Your certificate is issued by a trusted Certificate Authority (CA)
It’s renewed automatically
All pages (not just the login or checkout) are secured with HTTPS
Modern browsers now flag non-HTTPS sites as "Not Secure"—a red flag for users and search engines alike.
2. Use a Web Application Firewall (WAF)
A WAF monitors and filters HTTP traffic between your website and the internet. It blocks common threats like SQL injection, cross-site scripting (XSS), and brute-force attacks.
Choose a WAF that:
Offers customizable rules
Supports DDoS protection
Provides real-time traffic analytics
Popular WAFs include Cloudflare, Sucuri, and AWS WAF—each with varying levels of control and reporting. Your development agency can help configure the best fit based on your tech stack and risk exposure.
3. Implement Secure Authentication Protocols
Weak passwords and poorly managed login systems are among the top causes of data breaches. Strengthen this layer with:
Two-Factor Authentication (2FA)
OAuth2 or SSO integrations for enterprise-level users
Rate-limiting and lockout mechanisms for failed login attempts
Make sure admin panels, user dashboards, and CMS backends are protected with hardened authentication protocols—not just simple passwords.
4. Harden Your CMS and Framework
If you’re using platforms like WordPress, Webflow, or custom frameworks like Laravel or Django, security starts with how well the code and plugins are managed.
Best practices include:
Removing unused plugins and themes
Regularly updating core software
Using only trusted third-party packages
Applying role-based access controls
A Web Development Company will often audit your codebase and extensions for hidden vulnerabilities and outdated dependencies.
5. Monitor and Log Everything
Security isn’t static—it requires continuous monitoring. Use log management and monitoring tools to detect suspicious behavior in real time.
Your stack should include:
Application-level logging (failed logins, unusual traffic)
Server and file integrity monitoring
Alerts for changes in configuration or permissions
Tools like Sentry, Datadog, or even open-source solutions like Fail2Ban can help detect threats early before they escalate.
6. Secure Your Hosting Environment
Your server and hosting setup must be as secure as your code. Ensure:
Firewalls are configured at the OS level
SFTP (not FTP) is used for file transfers
Admin panels are IP-restricted or hidden behind VPNs
Automated daily backups are stored off-site
Many breaches happen at the server level due to misconfigured permissions or outdated software—especially on unmanaged VPS environments.
7. Regular Penetration Testing and Updates
Security isn’t a one-time setup. Schedule regular penetration testing and vulnerability scans to identify new risks. Ensure:
Your software dependencies are up-to-date
Security patches are applied immediately
Reports are reviewed and acted upon
This proactive approach protects your business from evolving threats and demonstrates compliance with security standards and regulations.
Conclusion
Choosing the right security stack is not just about installing tools—it's about building a customized, layered defense system that protects your website from every angle. From SSL certificates and firewalls to authentication protocols and monitoring tools, each element plays a role in safeguarding your digital assets.
To ensure nothing is overlooked, work with a Web Development Company that specializes in security-first development. With the right guidance and configuration, your website can stay protected, performant, and trusted—no matter how fast your business grows.
0 notes
Text
Opinion Trading Software Development | Scalable soutions

Build Scalable, Real-Time Prediction Market Platforms Like Probo
✅ Launch Your Own Opinion Trading Platform Today
Opinion Trading Software Development enables you to create dynamic, real-time platforms where users can trade on the outcome of future events — politics, sports, finance, entertainment, and more. Whether you're launching a Probo clone or creating a unique platform, our development services provide everything you need for success.
Start from idea to MVP in weeks — with enterprise-grade features, stunning UI, and custom branding.
💡 What Is Opinion Trading Software?
An opinion trading platform allows users to buy or sell opinions, predict outcomes, and earn rewards based on accuracy. Think of it as the stock market for predictions — powered by secure transactions, live data, and smart analytics.
🛠️ Key Features of Our Opinion Trading Software
🗳️ Live Opinion Polls
📊 Real-Time Dashboards
💰 Wallets & Payouts
🔐 Secure Payment Gateway Integration
📈 Analytics & User Insights
📲 Push Notifications
🧩 Admin & Moderation Panel
🎯 Gamification & Reward Systems
All features are customizable to suit your niche audience.
💼 Who Needs It?
✔️ Fintech Startups
✔️ Media Companies
✔️ Sports & Political Analysts
✔️ Fantasy App Owners
✔️ Influencer Platforms
Join a booming market where opinion meets technology.
🧱 Tech Stack We Use
Frontend: React.js, Flutter, Angular
Backend: Node.js, Laravel, Django
Database: PostgreSQL, MongoDB
Hosting: AWS, Azure, Google Cloud
Security: OAuth2, 2FA, SSL Encryption
Integrations: Payment APIs, News APIs, Analytics Tools
📈 Why Choose IMG Global Infotech Pvt. Ltd.?
As a trusted leader in opinion trading software development, we provide:
🔧 100% Custom-Built Solutions
🌍 Scalable Cloud Architecture
💬 Post-launch Support & Maintenance
🎨 UI/UX Tailored to Your Brand
🚀 Rapid Deployment & Agile Teams
📞 Ready to Build Your Own Opinion Trading Platform?
Let’s turn your vision into a powerful, scalable, and profitable opinion trading app.
👉 Book a Free Demo Now 👉 Get a Custom Quote
📩 Contact Us | 📞 +91-8058100200 | 🌐 www.imgglobalinfotech.com
IMG Global Infotech Pvt. Ltd. — Your Partner in Smart, Secure & Scalable Software Solutions.
0 notes
Text
How to Build a YouTube Clone App: Tech Stack, Features & Cost Explained
Ever scrolled through YouTube and thought, “I could build this—but better”? You’re not alone. With the explosive growth of content creators and the non-stop demand for video content, building your own YouTube clone isn’t just a dream—it’s a solid business move. Whether you're targeting niche creators, regional content, or building the next big video sharing and streaming platform, there’s room in the market for innovation.
But before you dive into code or hire a dev team, let’s talk about the how. What tech stack powers a platform like YouTube? What features are must-haves? And how much does it actually cost to build something this ambitious?
In this post, we’re breaking it all down—no fluff, no filler. Just a clear roadmap to building a killer YouTube-style platform with insights from the clone app experts at Miracuves.
Core Features of a YouTube Clone App
Before picking servers or coding frameworks, you need a feature checklist. Here’s what every modern YouTube clone needs to include:
1. User Registration & Profiles
Users must be able to sign up via email or social logins. Profiles should allow for customization, channel creation, and subscriber tracking.
2. Video Upload & Encoding
Users upload video files that are auto-encoded to multiple resolutions (360p, 720p, 1080p). You’ll need a powerful media processor and cloud storage to handle this.
3. Streaming & Playback
The heart of any video platform. Adaptive bitrate streaming ensures smooth playback regardless of network speed.
4. Content Feed & Recommendations
Dynamic feeds based on trending videos, subscriptions, or AI-driven interests. The better your feed, the longer users stay.
5. Like, Comment, Share & Subscribe
Engagement drives reach. Build these features in early and make them seamless.
6. Search & Filters
Let users find content via keywords, categories, uploaders, and tags.
7. Monetization Features
Allow ads, tipping (like Super Chat), or paid content access. This is where the money lives.
8. Admin Dashboard
Moderation tools, user management, analytics, and content flagging are essential for long-term growth.
Optional Features:
Live Streaming
Playlists
Stories or Shorts
Video Premiere Countdown
Multilingual Subtitles
Media Suggestion: Feature comparison table between YouTube and your envisioned clone
Recommended Tech Stack
The tech behind YouTube is serious business, but you don’t need Google’s budget to launch a lean, high-performance YouTube clone. Here’s what we recommend at Miracuves:
Frontend (User Interface)
React.js or Vue.js – Fast rendering and reusable components
Tailwind CSS or Bootstrap – For modern, responsive UI
Next.js – Great for server-side rendering and SEO
Backend (Server-side)
Node.js with Express – Lightweight and scalable
Python/Django – Excellent for content recommendation algorithms
Laravel (PHP) – If you're going for quick setup and simplicity
Video Processing & Streaming
FFmpeg – Open-source video encoding and processing
HLS/DASH Protocols – For adaptive streaming
AWS MediaConvert or Mux – For advanced media workflows
Cloudflare Stream – Built-in CDN and encoding, fast global delivery
Storage & Database
Amazon S3 or Google Cloud Storage – For storing video content
MongoDB or PostgreSQL – For structured user and video data
Authentication & Security
JWT (JSON Web Tokens) for secure session management
OAuth 2.0 for social logins
Two-Factor Authentication (2FA) for creators and admins
Analytics & Search
Elasticsearch – Fast, scalable search
Mixpanel / Google Analytics – Track video watch time, drop-offs, engagement
AI-based recommendation engine – Python + TensorFlow or third-party API
Media Suggestion: Architecture diagram showing tech stack components and flow
Development Timeline & Team Composition
Depending on complexity, here’s a typical development breakdown:
MVP Build: 3–4 months
Full Product with Monetization: 6–8 months
Team Needed:
1–2 Frontend Developers
1 Backend Developer
1 DevOps/Cloud Engineer
1 UI/UX Designer
1 QA Tester
1 Project Manager
Want to move faster? Miracuves offers pre-built YouTube clone app solutions that can cut launch time in half.
Estimated Cost Breakdown
Here’s a rough ballpark for custom development: PhaseEstimated CostUI/UX Design$3,000 – $5,000Frontend Development$6,000 – $10,000Backend Development$8,000 – $12,000Video Processing Setup$4,000 – $6,000QA & Testing$2,000 – $4,000Cloud Infrastructure$500 – $2,000/month (post-launch)
Total Estimated Cost: $25,000 – $40,000+ depending on features and scale
Need it cheaper? Go the smart way with a customizable YouTube clone from Miracuves—less risk, faster time-to-market, and scalable from day one.
Final Thoughts
Building a YouTube clone isn’t just about copying features—it’s about creating a platform that gives creators and viewers something fresh, intuitive, and monetizable. With the right tech stack, must-have features, and a clear plan, you’re not just chasing YouTube—you’re building your own lane in the massive video sharing and streaming platform space.
At Miracuves, we help startups launch video platforms that are secure, scalable, and streaming-ready from day one. Want to build a revenue-generating video app that users love? Let’s talk.
FAQs
How much does it cost to build a YouTube clone?
Expect $25,000–$40,000 for a custom build. Ready-made solutions from Miracuves can reduce costs significantly.
Can I monetize my YouTube clone?
Absolutely. Use ads, subscriptions, tipping, pay-per-view, or affiliate integrations.
What’s the hardest part of building a video streaming app?
Video encoding, storage costs, and scaling playback across geographies. You’ll need a solid cloud setup.
Do I need to build everything from scratch?
No. Using a YouTube clone script from Miracuves saves time and still offers full customization.
How long does it take to launch?
A simple MVP may take 3–4 months. A full-feature platform can take 6–8 months. Miracuves can cut that timeline in half.
Is it legal to build a YouTube clone?
Yes, as long as you’re not copying YouTube’s trademark or copyrighted content. The tech and business model are fair game.
1 note
·
View note
Text
Secure Laravel Authentication: 7 Best Practices 🔒
Protect your Laravel app with strong password hashing and 2FA for added security. Prevent brute-force attacks with rate limiting and always use HTTPS to encrypt data.
Keep dependencies updated and secure sessions with HTTP-only cookies. For APIs, use JWT or OAuth to restrict access. Stay ahead of threats!
Keeping dependencies updated and using secure session management further enhances Laravel authentication. For expert Laravel solutions, trust Orbitwebtech, the best web development company for secure and scalable web applications.
1 note
·
View note
Text
Key Laravel Security Measures for a Safer Web Application

In the modern digital landscape, securing web applications is essential. Laravel, with its elegant syntax and robust security features, offers a reliable framework for protecting applications against cyber threats. However, leveraging these security features effectively requires expertise. Partnering with professional Laravel developers ensures optimal implementation of Laravel’s built-in security measures.
Key Laravel Security Features:
1. Cross-Site Scripting (XSS) Protection
Laravel automatically escapes user-generated content, preventing the execution of malicious scripts and safeguarding applications from XSS attacks.
2. Cross-Site Request Forgery (CSRF) Protection
CSRF tokens are generated for every user session, blocking unauthorized actions and ensuring the authenticity of user requests.
3. SQL Injection Prevention
Using Eloquent ORM and prepared statements, Laravel protects applications from SQL injection attacks by securely binding user inputs.
4. Password Hashing
Laravel employs the Bcrypt hashing algorithm, ensuring that user passwords are stored securely and cannot be easily retrieved by attackers.
5. Encryption & Secure Authentication
Laravel provides a simple API for encrypting sensitive data and supports advanced authentication mechanisms like Two-Factor Authentication (2FA).
Best Practices for Enhancing Laravel Security
Keep Laravel & Dependencies Updated: Regular updates eliminate vulnerabilities and protect applications from security threats.
Enforce HTTPS: Encrypts data in transit, preventing unauthorized access and data interception.
Validate & Sanitize User Input: Prevents injection attacks and ensures only clean data is processed.
Secure File Uploads: Storing files outside the web root and randomizing file names adds an extra layer of security.
Disable Debug Mode in Production: Prevents exposing sensitive information that attackers can exploit.
Conclusion
By integrating Laravel’s security features with best practices, businesses can build secure and scalable web applications. Hiring professional Laravel developers from trusted firms like nectarbits.ca ensure robust security and optimal performance.
Read more: How Laravel’s Security Features Keep Your Web App Secure
1 note
·
View note
Text
Die Sicherheit der Authentifizierung in Laravel ist essenziell, um Benutzerkonten und sensible Daten vor Cyberangriffen zu schützen. Laravel bietet eine Vielzahl integrierter Sicherheitsfunktionen, doch eine unsachgemäße Implementierung kann zu Schwachstellen führen. In diesem Beitrag zeigen wir Ihnen 7 bewährte Methoden, um die Authentifizierung in Laravel zu sichern und Ihre Anwendung vor Bedrohungen zu schützen.
🔹 Starke Passwörter und Hashing verwenden – Nutzen Sie Laravel's Bcrypt oder Argon2, um Passwörter sicher zu verschlüsseln. 🔹 Zwei-Faktor-Authentifizierung (2FA) aktivieren – Zusätzliche Sicherheit durch OTP oder Authenticator-Apps. 🔹 Rate Limiting für Anmeldeversuche – Schutz vor Brute-Force-Angriffen mit Laravel’s throttle Middleware. 🔹 Sitzungsverwaltung optimieren – Verwenden Sie sichere Sitzungsmechanismen und setzen Sie kurze Ablaufzeiten. 🔹 CSRF-Schutz aktivieren – Laravel bietet eingebaute CSRF-Token, um Angriffe auf Formulare zu verhindern. 🔹 E-Mail-Verifizierung implementieren – Bestätigen Sie Benutzerkonten, um Spam-Registrierungen zu vermeiden. 🔹 Regelmäßige Sicherheitsupdates und Patches – Halten Sie Laravel und seine Abhängigkeiten stets auf dem neuesten Stand.
Indem Sie diese Methoden konsequent umsetzen, schützen Sie Ihre Laravel-Anwendung vor Angriffen und verbessern die Sicherheit der Benutzerkonten.
🔗 Lesen Sie den vollständigen Beitrag auf unserer Website!
1 note
·
View note
Text
Developing a Travel Booking Website With Multi Currency Support

Have you ever dreamed of making global travel as easy as a few clicks? For businesses in the travel industry, the digital revolution has brought an opportunity like never before. Imagine a platform where a family in Paris can book a holiday in Bali or a solo traveler from Tokyo can secure their New York accommodation, all with prices in their local currency. That’s the magic of a well-designed travel booking website with multi-currency support.
In today’s interconnected world, convenience is king, and the competition is fierce. Travelers want seamless, intuitive platforms that cater to their unique preferences. If you’re a travel agency or entrepreneur looking to stay ahead, developing a travel booking platform isn’t just a smart move—it’s essential. In this blog, we dive into how you can create a feature-packed, user-friendly website that stands out in this ever-evolving market.
Why a Multi-Currency Travel Booking Website is Essential
A multi-currency travel booking website is pivotal for businesses aiming to cater to international travelers. By offering currency flexibility, you not only enhance user convenience but also establish trust among global audiences. Exchange rate transparency and real-time updates ensure users have a seamless booking experience, eliminating the need for external currency converters.
Additionally, businesses partnering with a travel portal development company can implement advanced solutions that reduce abandonment rates during checkout. Providing local currency options encourages users to complete transactions, minimizing payment discrepancies, and enhancing customer satisfaction and loyalty.
Key Features of a Travel Booking Platform
• Intuitive User Interface
An engaging user interface (UI) is the backbone of any successful travel booking website. Clear navigation menus, visually appealing layouts, and fast loading times ensure users can find and book their desired services effortlessly. Partnering with a travel booking portal development company ensures that filters for destinations, travel dates, and budgets enhance the overall user experience.
• Multi-Currency Integration
Seamless multi-currency support requires integration with reliable payment gateways. By using APIs that fetch real-time exchange rates, you ensure pricing accuracy. This feature caters to international travelers, making transactions straightforward and transparent.
• Mobile Responsiveness
With a significant number of bookings happening via mobile devices, ensuring mobile responsiveness is non-negotiable. A mobile-optimized travel booking site allows users to browse and book on the go, enhancing accessibility and satisfaction.
• Secure Payment Gateways
Security is a top priority when developing a platform that handles sensitive user data. Employing encrypted payment systems, secure sockets layer (SSL) certificates, and two-factor authentication (2FA) guarantees the protection of user information and builds trust.
• Personalization Options
Modern users expect a tailored experience. Integrating features like personalized recommendations, saved preferences, and loyalty programs increases engagement and encourages repeat bookings.
Technical Aspects of Building a Travel Booking Website
• Robust Backend Development
The backend of a travel booking site should handle data management, user accounts, and real-time updates efficiently. Using frameworks like Django or Laravel ensures scalability and reliability. A well-structured backend supports smooth operations even during peak traffic.
• API Integration
Integrating APIs for flights, hotels, and car rentals enables real-time data fetching and booking confirmations. Third-party APIs like Amadeus, Skyscanner, and Booking.com simplify this process while ensuring accuracy.
• Search Engine Optimization (SEO)
SEO is crucial for attracting organic traffic. By optimizing your site with semantic keywords like “online booking system” and “hotel booking software,” you improve visibility. Implementing structured data markup enhances your chances of appearing in rich search results.
• Testing and Quality Assurance
Thorough testing ensures the platform’s reliability. Functional, performance, and security testing must be conducted before launch. Load testing helps identify and resolve potential bottlenecks, ensuring seamless performance during high traffic.
Benefits of a Well-Designed Travel Booking Website
A professionally designed travel booking site boosts brand credibility and customer trust. It simplifies the booking process, enhances user satisfaction, and improves overall operational efficiency. By incorporating multi-currency support, businesses can cater to a broader audience, increasing revenue streams. Companies those are specializied in travel portal development solutions also prioritize scalability and personalization features, ensuring long-term growth.
Additionally, a responsive and secure platform builds loyalty, encouraging repeat bookings. Collaborating with a travel booking portal development company ensures your platform meets the latest industry standards.
Conclusion
The world of travel is vast, but your platform can make it smaller, more accessible, and seamless for users. A cutting-edge travel booking site with multi-currency support isn’t just a convenience; it’s the future of travel services. By providing intuitive navigation, secure payment options, and tailored features, you give your customers a reason to choose your platform over competitors.
At Idiosys Tech, we bring this vision to life. As a trusted web development company, we specialize in creating innovative, user-focused platforms tailored to your business needs. Ready to redefine travel booking for your customers? Partner with Idiosys Tech and build a platform that transforms global travel into a truly local experience. Contact us today to start your journey!
________________________________________________________
How does multi-currency support benefit a travel portal?
It enables international users to view prices in their currency, improving trust, reducing cart abandonment, and making transactions seamless.
Who can benefit from a travel portal?
Travel agencies, tour operators, airlines, hotels, and car rental services can all expand their reach and streamline operations with a travel portal.
What technologies are used in travel portal development?
Technologies include React or Angular for the frontend, Laravel or Node.js for the backend, and APIs like Amadeus or Skyscanner for bookings.
How do travel portals help increase revenue?
They attract global users with multi-currency support, offer tailored services, and provide 24/7 accessibility, leading to more bookings and higher profits.
________________________________________________________
You May Also Read
Marketing Ideas for Your Travel or Hotel Booking Agency
#web development company#website development company#travel booking portal development#travel booking portal development company#travel portal development#travel portal development company#travel booking stite#travel booking website
0 notes
Text
Laravel Google 2FA Authentication Tutorial
This post will give you an example of laravel google 2fa authentication. step by step explain two factor authentication using google authenticator in laravel. In this article, we will implement a laravel two factor authentication with google authenticator. This post will give you a simple example of laravel 2fa google authenticator. You can add google authenticator with laravel 6, laravel 7,…
0 notes
Text
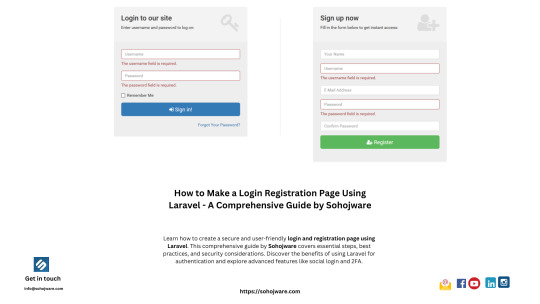
How to Make a Login Registration Page Using Laravel — A Comprehensive Guide by Sohojware
Building a secure and user-friendly login and registration system is crucial for any Laravel application. It forms the foundation for user authentication, allowing you to manage user accounts and access control within your application. This guide by Sohojware, a leading Laravel development company, will walk you through the step-by-step process of creating a robust login and registration page using Laravel.
Benefits of Using Laravel for Login and Registration:
Laravel, a popular PHP framework, offers several advantages when building login and registration functionalities:
Security: Laravel prioritizes security with built-in features like password hashing and CSRF protection, safeguarding your application from common vulnerabilities.
Authentication Scaffolding: Laravel provides pre-built authentication scaffolding to streamline the development process. This includes functionalities like user registration, login, password resets, and email verification.
Ease of Use: Laravel’s syntax is clean and well-documented, making it easier for developers to understand and implement functionalities.
Customization: While Laravel offers a solid foundation, you can still customize the login and registration process to match your application’s specific needs.
Prerequisites:
Before diving in, ensure you have the following:
A local Laravel development environment set up.
Basic understanding of Laravel concepts like models, controllers, views, and migrations.
Step-by-Step Guide:
Setting Up Database and Migrations:
Design your database schema to store user information like name, email, password, and any additional user-specific details.
Use Laravel migrations to create the necessary tables in your database.
Creating User Model:
Generate a User model using Laravel’s Artisan command:

Use code with caution:
Define the fillable attributes within the model class, specifying which user data can be saved to the database.
Implement Laravel’s User contract methods like getAuthPassword() to retrieve the password for authentication.
Building Controllers:
Create separate controllers for handling user registration and login requests.
The registration controller will handle form submissions, validate user data, and create a new user record in the database.
The login controller will authenticate user credentials and handle successful login attempts or provide error messages for invalid credentials.
Creating Views:
Design the login and registration views using Blade templating engine.
Include necessary HTML form elements for user input like email, password, and any additional registration fields.
Integrate Laravel’s form helpers to simplify form creation and error handling.
Implementing Authentication:
Utilize Laravel’s built-in authentication features like Auth::attempt for login and Auth::guard(‘web’)->register for registration.
Implement functionalities for password reset and email verification using Laravel’s functionalities or third-party packages.
Routing and Middleware:
Define routes in your routes/web.php file to handle login and registration URLs.
Consider using Laravel middleware to protect specific routes that require user authentication.
Enhancing Your Login and Registration System:
Social Login Integration: Allow users to register or log in using social media platforms like Facebook or Google for a more convenient experience.
Two-Factor Authentication (2FA): Implement an extra layer of security by enabling 2FA for user accounts.
User Activation: Require users to verify their email addresses before gaining full access to your application.
Remember Me Functionality: Offer an option for users to stay logged in for a certain period, enhancing user experience.
By following these steps and considering the enhancements mentioned, you can create a robust and secure login and registration system for your Laravel application.
Sohojware’s Laravel Expertise:
Sohojwareis a leading Laravel development company with a team of experienced developers well-versed in building secure and scalable web applications. We can assist you in creating a custom login and registration system tailored to your specific needs, ensuring a seamless user experience and robust security measures.
FAQs:
Does Sohojware offer pre-built Laravel login and registration solutions?
Sohojware can develop custom login and registration functionalities based on your project requirements. We can also integrate pre-built Laravel packages that offer functionalities like social login or 2FA.
How secure are login and registration systems built by Sohojware?
Security is a top priority at Sohojware. We follow industry best practices and leverage Laravel’s built-in security features to create secure login and registration systems.
Can Sohojware help with customizing the login and registration interface?
Yes, Sohojware can assist in customizing the login and registration interface to match your application’s branding and design preferences.
What is the typical turnaround time for developing a login and registration system using Laravel?
The turnaround time for developing a login and registration system depends on the project’s complexity and scope. However, Sohojware strives to deliver projects efficiently while maintaining high-quality standards.
Does Sohojware provide ongoing support and maintenance for login and registration systems?
Yes, Sohojware offers ongoing support and maintenance services to ensure the security and functionality of your login and registration system.
Conclusion:
Building a robust login and registration system is essential for any Laravel application. By following the steps outlined in this guide and leveraging Sohojware’s expertise, you can create a secure, user-friendly, and customizable authentication system.
Additional Tips:
Regularly update Laravel and its dependencies to benefit from security patches and improvements.
Conduct security audits to identify and address potential vulnerabilities.
Educate users about best practices for password security, such as using strong, unique passwords and avoiding sharing credentials.
Sohojware is committed to providing high-quality Laravel development services and ensuring the security of your applications. Contact us today to discuss your project requirements and get started on building a secure and efficient login and registration system.
1 note
·
View note
Text
The Future of PHP and Securing PHP-Built Applications
PHP, a server-side scripting language that has been the backbone of web development for over two decades, continues to evolve. Despite facing stiff competition from newer programming languages, PHP's role in the development of dynamic websites and applications remains significant.
This blog post explores the future of PHP and offers insights into securing PHP-built applications, ensuring they are robust against modern cybersecurity threats.
The Future of PHP: Adaptation and Evolution
PHP 8 and Beyond
The release of PHP 8 marked a significant milestone in the language's evolution, introducing features such as JIT (Just In Time) compilation, attributes, and union types, which have substantially improved performance and developer experience. The continuous development efforts by the PHP community signal a bright future, with PHP 8.x versions focusing on optimizing performance, enhancing security features, and introducing type systems that are more strict to reduce coding errors.
Frameworks and CMS Dominance
Frameworks such as Laravel, Symfony, and CodeIgniter, and content management systems (CMS) like WordPress, Drupal, and Joomla, play a crucial role in PHP's ongoing relevance. These tools have significantly abstracted the complexity of web development, enabling developers to create sophisticated applications more efficiently. The future will likely see these frameworks and CMS platforms adopting new PHP features faster, thus providing a more secure and robust ecosystem for developers.
Community and Open Source Contribution
The PHP community remains one of its strongest assets. With a vast ecosystem of developers, contributors, and enthusiasts, PHP benefits from a continuous influx of ideas, plugins, and extensions that enhance its functionality. The open-source nature of PHP fosters innovation and collaboration, ensuring the language adapts to new web technologies and trends.
Securing PHP-Built Applications: Best Practices
In an era where cybersecurity threats are ever-present, securing PHP-built applications is paramount. Here are essential practices to enhance the security of PHP applications:
Regular Updates and Patch Management
Keeping PHP and its libraries up-to-date is the first line of defense against vulnerabilities. Developers should regularly check for and apply updates to PHP itself, along with any frameworks or libraries used in the application.
Use of HTTPS
Encrypting data in transit using HTTPS prevents man-in-the-middle attacks and ensures data integrity and confidentiality. This is especially critical for applications handling sensitive information.
Data Validation and Sanitization
Input validation and sanitization are crucial to protect against SQL injection, cross-site scripting (XSS), and other injection attacks. If businesses hire PHP developers, they should ensure all user input is properly validated against expected patterns and sanitized before processing.
Secure Authentication and Authorization
Implementing strong authentication mechanisms, such as two-factor authentication (2FA), and ensuring proper session management can significantly reduce the risk of unauthorized access. Additionally, applications should enforce strict authorization checks to ensure users can only access resources they are permitted to.
Error Handling and Logging
Proper error handling prevents the exposure of sensitive application internals to attackers, while comprehensive logging aids in the detection and analysis of security incidents.
Regular Security Audits and Penetration Testing
Conducting regular security audits and penetration testing can help identify and mitigate vulnerabilities before they can be exploited by attackers.
Secure Configuration
PHP and server configurations should be optimized for security. This includes disabling unnecessary services, using secure PHP settings (e.g., expose_php = Off, open_basedir restriction), and configuring proper file permissions.
Conclusion
The future of PHP is promising, fueled by continuous improvements and a vibrant community. As PHP evolves, so do the strategies for securing applications built with it. By adhering to security best practices and leveraging the latest PHP features, businesses leveraging php development services can create secure, efficient, and scalable web applications. As we look ahead, the trajectory of PHP suggests it will remain a critical component of the web development ecosystem, adaptable to new challenges and technologies.
0 notes
Text
Probo App Clone Development: Build a Future-Ready Prediction Platform with IMG Global Infotech Pvt. Ltd.

In a digital era where real-time engagement and gamified experiences are reshaping user behavior, platforms like Probo have introduced a compelling new vertical—opinion trading apps. These applications allow users to predict real-world outcomes in categories such as politics, sports, finance, and entertainment. For businesses and entrepreneurs looking to enter this niche, a Probo app clone development offers a golden opportunity to build a scalable, engaging, and profitable platform.
At IMG Global Infotech Pvt. Ltd., we specialize in crafting high-quality, secure, and customized apps like probo that deliver the same interactive and monetized experiences Probo is known for—with the added advantage of full brand control and feature flexibility.
Understanding Probo and the Rise of Opinion Trading
Probo is a prediction platform where users trade opinions by answering “Yes” or “No” to time-bound questions—similar to prediction markets. Users earn based on how accurately their responses align with the outcome. This interactive model resonates with millennials and Gen Z, who are already active on fantasy sports platforms like Dream11, MPL, and My11Circle.
Combining real-money gaming, live events, and user insights, apps like Probo have carved a path parallel to traditional fantasy sports apps. While fantasy cricket and football rely on player performance, opinion trading expands the domain to broader real-world scenarios—creating immense potential.
Why You Need a Probo App Clone
If you're exploring a new tech startup idea or want to diversify from traditional fantasy apps like Dream11, developing a Probo clone app offers several benefits:
Low Entry Barrier: No need to license sports data or manage fantasy point.
Higher Engagement: Covers diverse categories beyond sports—finance, politics, entertainment.
Scalable Model: With real-time content updates and market-style trading logic.
Better Monetization: Commissions, ads, and premium features.
Key Features in Our Probo Clone Development
At IMG Global Infotech Pvt. Ltd., our Probo clone script comes with advanced features designed to enhance user engagement, performance, and security:
User Panel: Clean UI, quick onboarding, real-time market updates, wallet system.
Admin Panel: Market creation tools, user management, transaction tracking, analytics.
Wallet & Payments: Seamless integration with Razorpay, Paytm, UPI, and bank transfers.
Live Poll Integration: Real-time data and outcomes based on verifiable news sources.
Gamification Tools: Badges, levels, referrals, and leaderboard.
Security Protocols: End-to-end encryption, WAF, and 2FA for secure logins.
Fantasy Sports & Probo: A Natural Expansion
If you're already running a fantasy cricket or fantasy football platform or planning to invest in Dream11 app development, a Probo-like app can complement your existing portfolio. Here's how:
Shared Audience Base: Users interested in sports predictions are likely to enjoy opinion trading.
Cross-Platform Promotion: Promote your opinion trading app to your fantasy user base.
New Revenue Channels: Monetize beyond sports—cover politics, stock market, global events.
At IMG Global Infotech, we can help integrate both fantasy sports app modules and opinion trading engines into a single, seamless ecosystem. Whether you're launching a standalone Probo clone or combining it with a Dream11-like app, we’ve got the development expertise you need.
Technology Stack & Development Approach
We use a cutting-edge tech stack for smooth, scalable, and secure app performance:
Frontend: React Native, Flutter (for cross-platform), or Swift/Java (for native).
Backend: Node.js, Python, or Laravel for robust logic and real-time APIs.
Database: MongoDB, PostgreSQL for structured and fast data access.
Security: SSL, JWT-based authentication, WAF, and GDPR-compliant data handling.
Our development process is agile, transparent, and tailored. From MVP to full-scale deployment, IMG Global Infotech Pvt. Ltd. provides dedicated project managers, UI/UX designers, and QA testers to ensure timely delivery and a flawless launch.
Why Choose IMG Global Infotech Pvt. Ltd.?
With over 10+ years in the app development industry, IMG Global Infotech has successfully delivered projects across gaming, fintech, healthcare, and e-commerce. Our specialized focus on real-money gaming, fantasy sports app development, and custom app clones makes us a trusted partner for forward-thinking businesses.
Highlights:
150+ successful mobile apps delivered
Expertise in real-time gaming and prediction logic
Flexible engagement and pricing models
24/7 technical support and post-launch maintenance
Compliance with Indian and international gaming laws
Conclusion
The demand for interactive, real-time apps is only growing, and opinion trading apps like Probo are set to dominate the next wave of user engagement platforms. Whether you're a startup founder or a business looking to diversify from fantasy cricket or football, building your own Probo clone app is a smart move.
Partner with IMG Global Infotech Pvt. Ltd., India’s leading fantasy sports and app development company, to build a powerful, secure, and scalable prediction platform. With our industry expertise, innovative approach, and full-cycle development services, we turn your vision into a revenue-generating reality.
0 notes
Text
Securing the Future: Unraveling the Power of Laravel in Web Development
In the ever-evolving landscape of web development, the quest for secure and robust solutions has become more crucial than ever. As digital technologies advance, so do the threats that target web applications. In this pursuit of a secure digital future, Laravel, a renowned PHP web application framework, emerges as a powerful ally. Let's delve into the multifaceted world of Laravel web development, exploring its significance, services, and the unique landscape it carves, especially in regions like the Netherlands.

The Essence of Laravel Web Development
At the heart of the digital revolution, Laravel stands tall as a beacon of innovation in web development. Its versatility and comprehensive features make it the preferred choice for developers aiming to build scalable, secure, and high-performing web applications. Laravel's architecture promotes clean and elegant code, facilitating faster development without compromising on security.
Laravel Web Development Services
Laravel's capabilities extend beyond its core framework, offering a plethora of services that cater to the diverse needs of modern businesses. From custom web application development to e-commerce solutions, Laravel web development services provide a holistic approach. These services go beyond mere coding; they encompass strategic planning, design thinking, and meticulous execution.
Two-Factor Authentication (2FA)
Laravel web development services empower applications with built-in support for Two-Factor Authentication. This additional layer of security ensures that users must provide two forms of identification before accessing sensitive data, a crucial feature for applications handling confidential information.
Cross-Site Request Forgery (CSRF) Protection
The framework includes robust CSRF protection, guarding against Cross-Site Request Forgery attacks. Laravel web development services configure and customize this feature, verifying the authenticity of each request, thus protecting against unauthorized actions.
Dependency Scanning and Updates
A vigilant Laravel development company regularly scans dependencies and updates libraries to patch vulnerabilities. This proactive approach ensures that web applications are built on the latest, most secure foundations, minimizing the risk of exploits based on outdated software components.
Role-Based Access Control (RBAC)
Laravel supports Role-Based Access Control, a feature allowing fine-grained control over user permissions. Laravel web development services implement RBAC tailored to the specific needs of applications, ensuring different user roles have appropriate access levels and privileges.
SSL/TLS Implementation
Secure Socket Layer (SSL) or its successor, Transport Layer Security (TLS), is crucial for data in transit. Laravel development services can implement and configure SSL/TLS to encrypt communication between the user's browser and the web server, safeguarding sensitive information from interception.
Logging and Monitoring
Laravel provides robust logging mechanisms, and Laravel web development services set up comprehensive logging and monitoring systems. Regular review of logs and monitoring application behavior allows for early detection of potential security incidents, enabling swift responses and mitigations.
Input Validation and Sanitization
Laravel encourages best practices for input validation and sanitization. Laravel web development services implement these measures to ensure that user inputs are validated and sanitized before being processed, preventing common vulnerabilities like SQL injection and cross-site scripting.
Laravel Web Development in the Netherlands
As we navigate the global landscape of web development, it's essential to highlight the significance of Laravel web development services in the Netherlands. The tech-savvy and innovation-driven environment in the Netherlands makes it a hotspot for cutting-edge web solutions. Laravel, with its security-focused approach and robust development services, aligns seamlessly with the Dutch ethos of technological excellence.
Conclusion: Embracing the Secure Future with Laravel
In conclusion, Laravel web development emerges not just as a technology but as a promise for a secure digital future. Its array of services, coupled with its security features, positions it as a frontrunner in the realm of web development. Whether it's the Netherlands or any corner of the globe, businesses seeking a secure, scalable, and efficient web presence can find their ally in Laravel.
As we unravel the power of Laravel in web development, it becomes evident that securing the future is not just a tagline but a commitment. It's a commitment to building web applications that withstand the challenges of the digital landscape, offering users an experience that is not only seamless but also safeguarded against evolving cyber threats. Laravel, with its robustness, versatility, and security-first approach, paves the way for a digital future that is not just connected but also secure.
#laravel development company#laravel framework#laravel we devlopment service#laravel#laravel technology#web development netherlad#web application netherland#we development netherland
0 notes
Quote
PHPと聞くとver4〜5の影響でバカにされがちだが、実際のところWEBの8割はPHPで動いていて、その内訳はLaravelが50%、wordpressが25%、残りはその他諸々である。LaravelはJetstreamパッケージでユーザ認証+2FA導入が一瞬で終わり便利。
[B! Laravel] Laravel + Vue.jsでGoogleカレンダーのクローンを作ろう!!【Laravel8対応】準備編|Yuu's Memo
1 note
·
View note
Photo

Laravel: Free 2FA for all your users ☞ https://itnext.io/laravel-free-two-factor-authentication-5a4be723dfa7 #php #laravel
1 note
·
View note
Photo

Laravel: Free 2FA for all your users ☞ https://itnext.io/laravel-free-two-factor-authentication-5a4be723dfa7 #php #laravel
1 note
·
View note