#malwarebytes not updating
Text
“I’m scared to pirate stuff - ” do it scared!*
*with Firefox and Adblock and a VPN and -
If you want a nonspecific, nonexhaustive “where do I even start” guide…
Sail the cyber seas at your own risk!
Streaming - “I want to watch xyz”
This is normally what most people want when they talk about pirating.
Use Firefox with uBlock Origin and additional privacy add-ons such as PrivacyBadger, TrackMeNot, etc.
Free VPNs are out there. Get one - but vet it’s efficacy. My go-tos are Proton VPN, or Windscribe if you plan to do a bit of torrenting.
What is torrenting? How does it work? Here’s a guide!
Back to streaming -
Make sure that a) you’ve got your Mozilla browser with all its adblocking private glory, and b) you’ve got a VPN turned on to hide what you’re doing in that browser from your ISP (internet service provider).
Now you need to actually find a site to stream from. This is the tricky part, because openly sharing these sites will get them taken down if they’re talked about widely enough. (Remember how tiktok idiots got zlibrary taken down?)
You’re going to have to talk to people on forums. You’re going to have to experiment with sites you find yourself. Search for ‘x online free’ and look at the links that come up - is the preview text mangled or clickbaitey? Are there Reddit threads about that website confirming or denying its content? A good rule of thumb is to ignore the top result or two - copycats of good streaming sites will often buy out the top result spot. Eventually, you’ll develop a good gut feeling and understanding of what a good site ‘looks like’ from the results page alone.
However, there are some places that compile good sites that haven’t been nuked by lawyers (yet) - check out r/FMHY! The masterposts are actively curated and updated when a site goes down or is found to have malicious downloads.
Remember - loose lips sink ships. No tweeting (xeeting?) or Facebook statuses about your new favorite piracy website and where you found it. Even posting to tumblr (kind of like this…) isn’t a great idea if you want those websites to stay under the radar and stay accessible. Nobody talks, everybody walks (away with their share of pirate booty)
If you aren’t downloading media, pick pretty much any site and watch away! Adblock and Firefox will keep away pop-ups and other annoying ads, and your VPN means your ISP can’t tell that you’re visiting an unofficial streaming service.
Note: In my experience, I’ve never heard of visiting a site and watching stuff on it infecting or otherwise compromising your computer. That tends to come from misclicks on invisible or overwhelming pop-up ads that redirect you to an automatic download or similarly malicious bullshit. If you’re using Firefox and uBlock, you shouldn’t be in any danger of an accidental redirect.
Downloads - “I want to keep xyz”
This is the realm of pirate archiving - you’re keeping files physically on your hard drive, an external hard drive, or burning a disk.
Adblock + Firefox browser? Check. VPN on? Check.
Go to your streaming site of choice - most if not all have download options. You can download those files or, manually, right click and save the video file from the webpage as an mp4. I honestly don’t know if there’s a difference in quality or more danger in clicking the download buttons, but regardless -
Run that puppy through VirusTotal.com! It’s a reliable browser based virus checker - if the file is too large, use a local virus checking program (your native Windows Defender on Windows computers or, I prefer, Malwarebytes)
Generally mp4 and mp3 files are clean - choose where to save them for the long term, and bam! Free forever media.
Optionally, I also upload mp4 files to a named Google document - this way I can easily share them or make them findable through a ‘xyz Google doc’ search for others :]
Torrents - “I want to keep and share xyz”
I’m not going to go into this subject in depth because, honestly, it’s not something I do regularly.
See the previously linked Torrenting guide for information on how the process works, and check out r/FMHY for recommendations and warnings about different torrenting clients (I’ve personally only used qBittorrent - I’ve heard to stay away from the Pirate Bay and Bittorrent.)
As with streaming, turn on that VPN baby! You’re going to need one that supports peer-to-peer (p2p) connections, so Proton’s free version is a no-go. Windscribe is what I’ve used for torrenting (and it’s a good free VPN on its own - I’m just partial to Proton). You get 10GB every month on Windscribe’s free version, which is more than enough for a few movies/a season or two of your favorite show.
(Bigger torrents like video games are easily 30+ GB, so be prepared to either pay for a no-limit premium account or spend a few months downloading your files in chunks.)
VPN on? Double check.
Boot up your torrenting client - I use a slightly out of date version of qBittorent, but there are other options. The Reddit thread and previously linked torrenting guide have a few dos and donts of selecting a client, so be thorough before you download your client of choice.
This is getting into the logistics of torrenting a bit, so forgive me if this is vague or incorrect, but now you need a torrent seed. These will be .tor files found through pirating websites or archives - these are rarely malicious, but it’s good to run any piracy related download through something like VirusTotal.com or scan it with a local program like Malwarebytes.
You open your seed file in your client and wait. A ‘healthy’ seed tends to have lots of seeders and few leeches, but sometimes you’re stuck with an obscure seed you just have to wait for.
Your torrented files have fully downloaded! Now what? a) keep your client open and seed those files for others as long as you want to - sharing is caring! and b) run those files through a security program like Malwarebytes (not sponsored it’s just the only program I’m familiar with).
Be wary of what gets flagged - sometimes the files seem important, but are just trojans, and likewise sometimes they seem malicious, but are just cracked software getting flagged by your system. It’s good to check and see if others have had a problem with this particular torrent before - Reddit threads from 2008 are your long dead friends.
And that’s about it. Feel free to correct me if anything I’ve recommended is malicious or outright wrong. I’ve been doing this for years and haven’t had an active problem to my knowledge, so if there is something fishy with how I do things, I am a statistical outlier and should not be counted.
I wish you smooth sailing and strong winds in your ventures me hearties!
Obligatory ‘don’t pirate small author’s or artist’s works what the fuck dude’ statement.
#ra speaks#piracy#pirating#pirate to make hondo ohnaka proud#I’ve seen so many people on my streaming piracy post bemoaning that they don’t know how like !!!!#congrats you get to learn without the middle school trial and error phase we zillenials had (RIP family computer 2004-2009)#I genuinely think piracy has gotten easier/safer than it used to be. that or I’ve gotten smarter. which is also likely.
131 notes
·
View notes
Text
2 notes
·
View notes
Note
So this might be a longshot, but I was wondering if you still had access to the Acorn Trail Wallpapers by applezingsims? Their blog appears to be defunct (hasn't been updated in 3 years) and the download bitly link seems to be re-directing towards a site that MalwareBytes is blocking due to possible riskware. I sent them an ask, as well, but am not sure if they'll see it. Thank you for your time!
Hi!
Yes I have it, and I'm happy to share! Between the fact that it's behind Ad*ly and that Applezing's not around anymore, I am glad to do it!
HERE is the "trimmified" Acorn Trail wallpapers!

(and HERE is the link to Applezing's original post, for anybody curious)
30 notes
·
View notes
Text
Names
some names for mileven i found while scowering the byler tag after only 10 minutes
i love the names you ppl come up with 😭
menstruation
moomoomilk
milkman
microsofts
malwarebytes
melvins
milkshakes
morbiuses
Update:
Mildews
Marshmallow
mashed potatoes
manslaughter
Marijuana
Mosquito
Megamind
Mormon
Mozzarella
MinnieMouse
Malaria
40 notes
·
View notes
Note
Hey, do you have any antivirus recommendations? I deleted McAffee because I found it annoying.
Ahoy! Thank you so much for asking, because this is something i absolutely have! From personal experience, i definitely think that getting rid of McAffe is a good idea. It has a tendency to add a lot of "Bloatware" (Software whose usefulness is reduced because of the excessive disk space and memory it requires.) to your computer, and has a fairly rocky reputation. It is often bundled with other software and even some new computers, and tend to take up a lot of your CPU when scanning files. I absolutely understand that you find it annoying! It's basically a program made to pry upon less tech-savvy people, to get them to pay for McAffe's mediocre-at-best service.
Now, being done ranting about McAffe, let me come with some recommendations. The first one being "Malwarebytes," which i personally use.
If i ever can afford to pay for any "premium" anti-virus programs, it'd be Malwarebytes. The program can be downloaded for free, require no account and no payment info.
After installing i usually activate the 14 day free trial, and when that trial runs out, i simply tell it to deactivate the premium-mode, and then use the free version. Sometimes when updating i get new offers for premium trials, which i usually take, although the free-mode is plenty good enough.
When using the free Malwarebytes, i always make sure to manually scan any new downloads. Aside from that it does most stuff itself, most importantly including periodic scheduled scans.
Due to it being a hot minute since i last did some research around this, i made sure to do some now! And seemingly the most recommended anti-virus of 2022 is called "Bitdefender." The free version seems to cover the same grounds as Malwarebytes, and i've found no mentions of any major issues with this one either!
I have also seen some people discuss how the included Windows antivirus should be good enough, i do not trust Microsoft enough for that, but will make sure to look into this. The most important when using ANY antivirus is to make periodic scans, keep the software as updated as can be, and ALWAYS scan newly downloaded files! Remember this when you find yourself downloading files, ESPECIALLY if you are treating yourself to some piracy. It will save you from a good 99% of any malicious/harmful files out there!
I hope this has been helpful! If you have any questions, requests or anything else, always feel free to send asks or message me! If i can't find it, we might be able to get someone to put it out there!
49 notes
·
View notes
Note
update: i modboxxed the link from the art contest and the mods said it isn't malicious, so i think my malwarebytes extension was being overly cautious. i'm sorry if my previous warning freaked anyone out!! i just wanted people to be safe just in case.
.
4 notes
·
View notes
Text
June 2nd, 2022 (Cont.)
After waking up, there was much more progress made today for RENA! RENA now has 7Zip installed, the New Moon browser, and an older version of Sandboxie. The keyboard that came with RENA did break today, and was holding the space bar down, so all of her screenshots today include me using the desktop keyboard.
Below was right after opening the .7z file for New Moon, I am still monitoring and testing this browser as it is an unofficial/project made adaptation of Palemoon. Comodo sends warnings for it every time I open it.
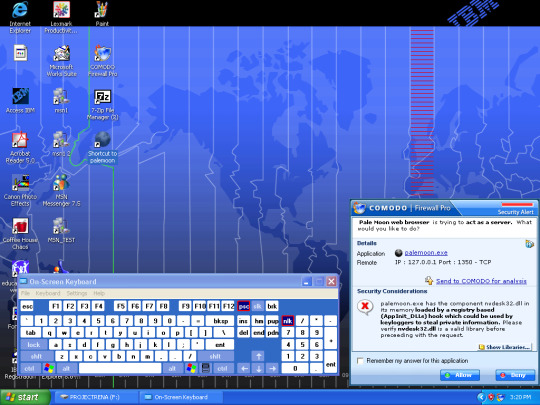
The good news! Is I thought ahead that I would encounter problems like this, in addition to the concern of browsing on obsolete OS anyways. So I installed an older version of Sandboxie onto RENA today! Yesterday I think I had the wrong version, and was unsuccessful. Today it went without a hitch. Nothing is a sure thing, especially since people looking to use RENA to slave other PC’s have had 20 years to think of work arounds for a lot of these older versions of software like Sandboxie, but combined with the firewalls and anti-virus I have selected for RENA, visiting safe sites should be just fine. Sandboxie is another step towards that.

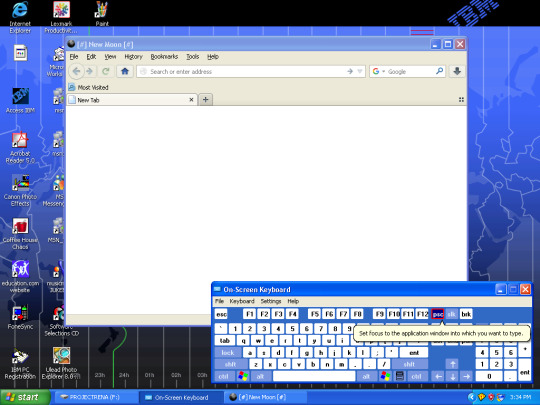
Here is New Moon successfully running inside the sand box:
The only thing I did not get to today for RENA was I plan to install Malwarebytes on her, but first need to install an updated Windows Service Pack onto her and I haven't found a copy I am comfortable bringing over to her quite yet.

But tomorrow is a new day! (and hopefully a trip to goodwill for a new keyboard...)
#Project RENA#old internet#old tech#old web#old computer#ibm#vintage computer#vintage tech#windows xp
6 notes
·
View notes
Text
8 Signs That Someone Is Tracking Your Phone

Hackers can use your mobile phone to track your whereabouts or spy on your personal information. While using your phone's GPS to track your location may appear innocent, hackers can use this information to learn where you live, your shopping habits, where your children go to school, and more. They can sell your information or use it to steal your identity once they have it. That why being aware of these subtle signals that your phone is being followed is crucial many business listings.
1 - Your phone becomes really heated
If your phone has become unusually hot recently, it could be a sign that it has been hacked. Spyware operating in the background can make your phone work harder and so produce more heat. Of course, there could be other causes for this, so if tracking isn't the problem, have a technician check out your phone for any faults.
2 - Your battery is quickly drained
Keep an eye out for abrupt variations in the time it takes your phone's battery to die. A tracked phone will constantly communicate data from the phone to the hacker, causing the phone to use more power and consume the battery far faster than normal.
3 - Your monthly data usage has increased unexpectedly
Every month, check your phone bill to see whether you're suddenly using more data than usual. Because it is constantly transmitting information back to the hacker's phone or computer, a taped phone consumes a lot of data.
4 - Unexpectedly, your phone reboots
"If your phone starts rebooting out of nowhere, it could suggest its being tracked. Your phone's virus is interfering with its normal operation, causing it to crash and restart at unpredictable intervals.
5 - It takes a long time for your phone to shut down
Another symptom of spyware could be if your phone takes longer than usual to shut down. Any actions that are currently in process must be completed when a phone shuts off. This might include data being transferred remotely to a hacker, extending the time it takes to shut down considerably.
6 - Your phone has been rooted or jailbroken
The practice of eliminating manufacturer limitations in order to obtain access to portions of the phone that would ordinarily be protected is known as jailbreaking (for iPhone) or rooting (for Android). It's a technique that hackers frequently employ to install spyware. It's not always easy to identify, so keep an eye out for a strange programmer called Cydia (for iPhone) or Super User (for Android) that appears unexpectedly on your home screen business listings.
7 - Hearing background noise or electrical interference
If you hear echoes, static, or clicking sounds coming from your phone, it could be a clue that someone is listening in on your conversations. This is a rare occurrence because most contemporary surveillance software is absolutely silent, but it is still worth keeping an eye out for.
8 - Your cell phone is operating at a slower rate than usual
Frustrated by how sluggish your phone has suddenly become? Over time, every phone slows down. If you're having this difficulty in addition to the others on this list, it's possible that your phone is being tracked. If this problem isn't caused by anything else, try these quick fixes to speed up your phone free business listings.
What should you do if your phone is being hacked?
Restarting your phone is the first thing you should do. As basic as it may appear, tracking apps and malware rely on the phone being left on for extended periods of time.
By simply rebooting your phone, many of them will be unable to monitor you. After that, perform a scan with a reputable malware removal app, such as Malwarebytes or Bitdefender Total Security, and turn off location sharing when you're not using it to ensure you're not unintentionally revealing your location with a third party.
Finally, if your phone hasn't been updated in a while, make sure it has the latest security patches and uninstall any apps you don't Recognise.
1 note
·
View note
Text
did malwarebytes kill my vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
did malwarebytes kill my vpn
Malwarebytes VPN conflict
Title: Resolving Malwarebytes VPN Conflict: A Comprehensive Guide
Malwarebytes VPN offers users secure browsing and data protection, but occasionally, conflicts may arise, hindering its seamless functionality. Understanding and resolving these conflicts is crucial to maintaining optimal online security and privacy.
One common issue users encounter is a conflict between Malwarebytes VPN and other security software installed on their devices. This conflict often arises due to overlapping functionalities or incompatible configurations between the VPN and other security applications. Symptoms of such conflicts may include connection drops, slow browsing speeds, or even system crashes.
To address this conflict, several steps can be taken:
Update Software: Ensure that both Malwarebytes VPN and any conflicting security software are updated to their latest versions. Developers frequently release updates to address compatibility issues and enhance performance.
Check Firewall Settings: Adjust firewall settings to allow Malwarebytes VPN and other security applications to communicate effectively. In some cases, overly restrictive firewall settings may block essential network connections, leading to conflicts.
Disable Conflicting Features: Temporarily disable conflicting features within other security software, such as built-in VPN services or real-time scanning, to isolate the source of the conflict. This process helps identify specific functionalities causing the issue.
Contact Support: If conflicts persist despite troubleshooting efforts, contact customer support for both Malwarebytes VPN and the conflicting software. Support representatives can provide personalized assistance and recommend solutions tailored to your specific setup.
Consider Alternative Solutions: If conflicts persist unresolved, consider using alternative security software or VPN providers that are compatible with your existing setup. Research and evaluate alternative options to find a solution that meets your security needs without compromising performance.
By following these steps and taking a systematic approach to troubleshooting, users can effectively resolve conflicts between Malwarebytes VPN and other security software, ensuring seamless protection of their online activities.
Malwarebytes VPN interference
Malwarebytes is a well-known cybersecurity software that helps protect users from various online threats, including malware, ransomware, and phishing attacks. However, some users have reported experiencing interference with their VPN (Virtual Private Network) when using Malwarebytes.
When a VPN is active, it encrypts the internet connection, making it more secure and private. This is particularly important when accessing sensitive information or trying to bypass geo-restrictions. However, some users have found that Malwarebytes may interfere with the VPN connection, leading to connectivity issues or even preventing the VPN from working properly.
The interference between Malwarebytes and VPN software can occur due to conflicting settings or protocols. In some cases, the VPN traffic may be blocked or restricted by Malwarebytes' security features, causing disruptions in the connection. This can be frustrating for users who rely on both tools to stay safe and anonymous online.
To address this issue, users can try adjusting the settings of both Malwarebytes and their VPN software. Disabling certain features or exclusions within Malwarebytes may help prevent interference with the VPN connection. Additionally, updating both programs to the latest versions can also resolve compatibility issues and ensure smooth functionality.
It's essential for users to maintain a balance between security measures like Malwarebytes and the privacy features of a VPN. By troubleshooting potential conflicts and finding the right configuration, users can enjoy a secure and uninterrupted online experience.
Malwarebytes VPN compatibility
Malwarebytes is a well-known cybersecurity company that provides antivirus, anti-malware, and internet security solutions to protect users from online threats. One of the products offered by Malwarebytes is a Virtual Private Network (VPN) service. This VPN service is designed to encrypt internet connections, provide online privacy and security, and enable users to access geo-restricted content.
When it comes to compatibility, Malwarebytes VPN is compatible with a wide range of devices and operating systems. Users can install and use the VPN on Windows, Mac, iOS, and Android devices. This cross-platform compatibility ensures that users can secure their internet connections across different devices and platforms.
Malwarebytes VPN also works well with popular web browsers such as Google Chrome, Mozilla Firefox, and Safari. This compatibility allows users to browse the internet securely and privately using their preferred web browser while connected to the VPN.
Additionally, Malwarebytes VPN is compatible with most internet connections, including public Wi-Fi networks, home networks, and mobile data networks. This compatibility ensures that users can stay protected and secure regardless of the network they are using.
In conclusion, Malwarebytes VPN offers excellent compatibility with a wide range of devices, operating systems, web browsers, and internet connections. Users can trust Malwarebytes VPN to provide reliable and secure online protection wherever they go.
Malwarebytes VPN blocking
Malwarebytes VPN Blocking: Understanding the Issue
Malwarebytes is a well-known cybersecurity company that provides various products to protect users from online threats. One of their offerings is a VPN (Virtual Private Network) service, designed to enhance privacy and security while browsing the internet. However, some users have reported instances where Malwarebytes VPN appears to be blocking certain websites or services.
The issue of Malwarebytes VPN blocking can arise due to several reasons. One common cause is the VPN's built-in security features, which may flag certain websites or IP addresses as potential threats based on their characteristics or activity. In such cases, the VPN's protection mechanisms may automatically block access to these sites to prevent users from inadvertently exposing themselves to malware or other malicious content.
Additionally, conflicts with other security software or network settings can also lead to Malwarebytes VPN blocking certain connections. For example, if another security program installed on the user's device is configured to block specific websites or restrict network access, it may interfere with the functioning of the VPN and cause unexpected blocks.
Furthermore, issues with the VPN's servers or infrastructure can occasionally result in blocked connections. Server downtime, maintenance activities, or technical glitches may temporarily disrupt the VPN service, causing users to experience difficulties accessing certain websites or online services.
To address the issue of Malwarebytes VPN blocking, users can try several troubleshooting steps. These include updating the VPN software to the latest version, checking for any conflicting software or settings on their device, and contacting Malwarebytes customer support for assistance.
In conclusion, while Malwarebytes VPN is designed to enhance online security and privacy, users may encounter instances where it appears to be blocking certain websites or services. Understanding the potential causes of these blocks and following appropriate troubleshooting steps can help users resolve the issue and continue to enjoy the benefits of a secure VPN connection.
Malwarebytes VPN disruption
Recently, Malwarebytes, a well-known antivirus and cybersecurity company, experienced a temporary disruption of its Virtual Private Network (VPN) service. The VPN service, which is designed to provide users with online privacy and security by encrypting their internet connection, went down unexpectedly, causing inconvenience to its users.
The disruption of the Malwarebytes VPN service left many users unable to access the protection and security features that they rely on to keep their online activities safe. Without the VPN in place, users may have been exposed to potential security risks, such as data breaches, hacking attempts, and other malicious activities.
Malwarebytes moved quickly to address the issue and worked to restore the VPN service to normal operation as soon as possible. The company also communicated with its users about the disruption, providing updates and guidance on how to stay safe online during this time.
In the world of cybersecurity, disruptions like this serve as important reminders of the value of having multiple layers of defense in place to protect against online threats. While VPNs are valuable tools for safeguarding your online privacy, it's essential to have additional security measures in place to ensure comprehensive protection.
As Malwarebytes continues to investigate the root cause of the VPN disruption and take steps to prevent similar incidents in the future, users are advised to stay vigilant and keep their security software up to date to defend against potential cyber threats.
0 notes
Text
does a vpn interfere with anti virus or malwarebytes
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does a vpn interfere with anti virus or malwarebytes
VPN security vs antivirus software
VPN security and antivirus software are two essential tools in ensuring your online safety and privacy. While both serve different purposes, they work together to provide comprehensive protection against cyber threats.
VPN, or Virtual Private Network, encrypts your internet connection and routes it through a remote server, masking your IP address and making it difficult for hackers to intercept your data. VPN enhances your security by creating a secure tunnel for your online activities, especially when using public Wi-Fi networks. It also allows you to access geo-restricted content and maintain anonymity online.
On the other hand, antivirus software is designed to detect and remove malware, viruses, and other malicious threats from your devices. It scans your files and programs to identify and eliminate potential risks, protecting your system from cyber attacks and data breaches. Antivirus software provides real-time protection and regular updates to stay ahead of evolving online threats.
While VPN focuses on securing your internet connection and data privacy, antivirus software safeguards your devices from malicious software and online threats. Combining the two enhances your overall online security, creating multiple layers of defense against cybercriminals.
Ultimately, VPN security and antivirus software complement each other in safeguarding your digital life. By using both tools concurrently, you can enhance your online privacy, protect your personal information, and reduce the risk of falling victim to cyber attacks. Stay proactive in securing your online presence by utilizing VPN security and antivirus software for comprehensive protection.
Malwarebytes compatibility with VPN
Malwarebytes, a renowned name in cybersecurity, offers robust protection against various online threats. However, users often wonder about its compatibility with VPNs (Virtual Private Networks), especially considering the importance of maintaining privacy and security while browsing the internet.
Fortunately, Malwarebytes is generally compatible with most VPN services. When used together, they can provide enhanced security and privacy for users. VPNs encrypt internet traffic, making it difficult for hackers and other malicious entities to intercept or monitor your online activities. On the other hand, Malwarebytes specializes in detecting and removing malware, ransomware, and other types of malicious software that could compromise your device's security.
Combining Malwarebytes with a VPN can create a robust defense against online threats. While the VPN encrypts your data and hides your IP address, Malwarebytes continuously scans for and blocks malware attempts, ensuring that your device remains protected from various cyber threats.
However, it's essential to note that there may be some rare instances where compatibility issues arise between certain VPNs and Malwarebytes. These issues could stem from conflicting software configurations or specific features of either the VPN or Malwarebytes application. In such cases, users may need to troubleshoot or seek guidance from customer support to resolve any compatibility issues.
Overall, using Malwarebytes alongside a reputable VPN service can significantly enhance your online security and privacy. By leveraging the strengths of both tools, users can enjoy a safer and more secure browsing experience, free from the worries of malware infections and potential privacy breaches.
Interference between VPN and antivirus
When using both a Virtual Private Network (VPN) and an antivirus program on your device, it is crucial to be aware of the potential interference that may occur between the two, impacting your online security and overall user experience.
VPNs are designed to encrypt your internet connection and enhance your privacy by masking your IP address and online activities. On the other hand, antivirus software is essential for protecting your device from malware, viruses, and other online threats. While both tools are vital for safeguarding your digital presence, using them simultaneously can sometimes lead to conflicts that may compromise the effectiveness of either or both programs.
One common issue that users may encounter when running a VPN alongside an antivirus is difficulty with internet connectivity. Some antivirus programs may flag the VPN connection as a potential security risk, causing network disruptions or blocking the VPN altogether. This can result in unstable internet access and prevent you from browsing securely and anonymously.
Another concern is the performance impact on your device. Running both a VPN and antivirus simultaneously can consume a significant amount of your device's resources, potentially slowing down its speed and overall performance. This can be particularly noticeable when engaging in bandwidth-intensive activities like streaming or online gaming.
To mitigate interference between your VPN and antivirus, consider adjusting the settings of both programs to ensure they work harmoniously together. Whitelisting the VPN application within your antivirus software and vice versa can help prevent unnecessary conflict. Additionally, keeping both programs up to date and choosing reputable software from trusted providers can reduce the likelihood of compatibility issues.
By understanding the potential interference between VPNs and antivirus programs and taking proactive steps to address it, you can maintain a secure and efficient online experience while benefiting from the protection offered by both tools.
VPN protection against malware
VPN protection can play a crucial role in safeguarding your devices against malware attacks. Malware, short for malicious software, is designed to disrupt, damage, or gain unauthorized access to computer systems. By using a Virtual Private Network (VPN), you can enhance your online security and reduce the risk of falling victim to malware threats.
When you connect to a VPN server, your internet traffic is encrypted, creating a secure tunnel between your device and the server. This encryption helps prevent cybercriminals from intercepting your data and injecting malware into it. VPNs also hide your true IP address, making it harder for attackers to track your online activities and target you with malware.
Moreover, many reputable VPN providers offer additional security features, such as malware blockers and ad blockers, as part of their service packages. These tools can help detect and prevent access to malicious websites known for distributing malware. By using a VPN with built-in malware protection, you add an extra layer of defense to your devices and data.
It's essential to choose a reliable VPN provider that prioritizes security and privacy. Look for VPNs that offer strong encryption protocols, strict no-logs policies, and automatic kill switches to ensure your online activities remain private and secure.
In conclusion, using a VPN can significantly reduce the risk of malware infections and enhance your overall cybersecurity posture. By encrypting your internet connection, hiding your IP address, and utilizing additional security features, you can better protect yourself from various online threats, including malware attacks.
Anti-spyware alongside VPN
Combining anti-spyware software with a VPN is a powerful strategy to enhance your online security and privacy. Both tools serve distinct yet complementary purposes in protecting your digital presence from various threats and intrusions.
Anti-spyware software is designed to detect and remove malicious software such as spyware, adware, keyloggers, and other forms of malware that may compromise your personal data and online activities. By regularly scanning your device and internet traffic, anti-spyware programs help prevent unauthorized access and data theft.
On the other hand, a VPN (Virtual Private Network) creates a secure and encrypted connection between your device and the internet. It masks your IP address, encrypts your internet traffic, and reroutes it through remote servers, effectively hiding your online activities from prying eyes, including hackers, government surveillance, and malicious websites.
When used together, anti-spyware and a VPN provide a comprehensive defense against online threats. While anti-spyware focuses on detecting and eliminating malware that may already be present on your device, a VPN secures your internet connection and data transmission in real-time, preventing potential threats from intercepting your sensitive information.
By integrating both tools into your cybersecurity arsenal, you can significantly reduce the risks of cyberattacks, identity theft, data breaches, and online surveillance. Whether you are browsing the web, accessing public Wi-Fi networks, or engaging in online transactions, the combined protection of anti-spyware alongside a VPN offers you a safer and more private online experience.
0 notes
Text
do you use vpn access on mac computers
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do you use vpn access on mac computers
VPN setup on Mac
Setting up a VPN (Virtual Private Network) on your Mac is a straightforward process that can enhance your online security and privacy. Whether you're concerned about safeguarding your personal information or accessing geo-restricted content, a VPN can be a valuable tool.
Here's a step-by-step guide to setting up a VPN on your Mac:
Choose a VPN Provider: Start by selecting a reputable VPN provider that offers a Mac-compatible app. There are many options available, so consider factors such as server locations, speed, and privacy features before making your decision.
Download and Install the VPN App: Once you've chosen a VPN provider, visit their website and download the appropriate app for Mac. Follow the on-screen instructions to install the app on your computer.
Launch the VPN App: After installation, launch the VPN app and log in with your account credentials. If you don't have an account yet, you'll need to sign up for a subscription plan.
Connect to a VPN Server: Once logged in, you'll typically be presented with a list of server locations. Choose a server based on your preferences, such as location or server load, and click to connect.
Verify Connection: Once connected, you should see a confirmation message indicating that your connection is secure. You can also verify your new IP address to ensure that your internet traffic is being routed through the VPN server.
Adjust Settings (Optional): Most VPN apps offer customizable settings that allow you to tailor your connection to your specific needs. Take some time to explore these options and adjust them as desired.
Enjoy Secure Browsing: With your VPN successfully set up on your Mac, you can now browse the internet with confidence, knowing that your data is encrypted and your online activities are private.
Remember to disconnect from the VPN when you're not using it to maximize your internet speed and conserve bandwidth. Additionally, keep your VPN app updated to ensure you have the latest security features and bug fixes.
Secure browsing on Mac
When it comes to ensuring secure browsing on your Mac, there are several essential steps you can take to protect your privacy and data online. With cyber threats on the rise, safeguarding your browsing activity is paramount to prevent unauthorized access to your sensitive information.
First and foremost, it is crucial to keep your Mac up to date with the latest software updates and security patches. Apple regularly releases updates that address vulnerabilities and enhance the overall security of your device. By staying current with these updates, you can better protect your system from potential security threats.
In addition to updating your software, using a reliable antivirus program can provide an extra layer of security against malware and other online threats. There are many reputable antivirus solutions available for Mac users, such as Malwarebytes or Norton, that can help detect and remove malicious software from your system.
Furthermore, consider enabling the built-in firewall on your Mac to monitor and control incoming and outgoing network traffic. This can help prevent unauthorized access to your device and block malicious connections from compromising your security.
Lastly, be cautious when browsing the internet and avoid clicking on suspicious links or downloading files from untrusted sources. Phishing scams and malware often target Mac users, so it's essential to practice safe browsing habits to minimize the risk of falling victim to online threats.
By following these tips and staying vigilant while browsing the web, you can help ensure a secure and protected online experience on your Mac. Prioritizing security measures can go a long way in safeguarding your personal information and maintaining your privacy in an increasingly digital world.
Virtual private network for Mac
A Virtual Private Network (VPN) is a crucial tool for protecting your online privacy and security, especially when using a Mac. A VPN service creates a secure and encrypted connection to the internet, ensuring that your browsing activity, personal data, and sensitive information remain private and secure from potential cyber threats and prying eyes.
Using a VPN on your Mac allows you to browse the web anonymously and access geo-restricted content by masking your IP address and location. This is particularly useful for streaming services, accessing websites blocked in certain countries, or simply maintaining anonymity while browsing.
When choosing a VPN for your Mac, it is essential to select a reliable and reputable provider that offers strong encryption protocols, a no-logs policy, and fast connection speeds. Many VPN services have dedicated apps for Mac users, making it easy to set up and use a VPN on your device.
By using a VPN on your Mac, you can also protect your data when connected to public Wi-Fi networks, such as those in cafes, airports, or hotels. VPN encryption ensures that your sensitive information, such as passwords, credit card details, and personal messages, is secure from potential cyber attacks and data breaches.
Overall, investing in a VPN for your Mac is a wise decision to ensure your online privacy, security, and freedom while browsing the internet. With the right VPN service, you can enjoy peace of mind knowing that your data is protected and your online activities remain private and anonymous.
VPN software for Mac
VPN software for Mac offers users an essential layer of protection and privacy when browsing the internet. This software, compatible with the macOS operating system, allows users to establish a secure connection to a remote server, encrypting their online activities and hiding their IP address. By doing so, VPN software for Mac helps users shield their sensitive information from potential cyber threats and maintain their anonymity online.
One of the key advantages of using VPN software on a Mac is the ability to access geo-restricted content. By connecting to a server in a different location, users can bypass regional restrictions and access websites, services, and content that may be blocked in their current location. This can be particularly useful for streaming services that limit content based on the user's location.
Additionally, VPN software for Mac can help enhance online security when using public Wi-Fi networks. These networks are often targets for hackers looking to intercept sensitive data, but by using a VPN, users can encrypt their internet traffic and prevent unauthorized access to their personal information.
Popular VPN software options for Mac include ExpressVPN, NordVPN, and CyberGhost, all of which offer easy-to-use interfaces, fast connection speeds, and robust security features. Users looking to prioritize speed might opt for ExpressVPN, while those focused on security and privacy could choose NordVPN or CyberGhost.
In conclusion, VPN software for Mac provides users with a reliable solution to safeguard their online activities, protect their personal information, and access restricted content. By investing in a reputable VPN service, Mac users can enjoy a safer and more unrestricted browsing experience.
Using VPN on Mac
Using a VPN on your Mac can be a smart decision to enhance your online security and privacy. A Virtual Private Network (VPN) creates a secure connection between your device and the internet, encrypting your data and hiding your real IP address. This helps protect your personal information from hackers, cybercriminals, and other prying eyes.
Setting up a VPN on your Mac is a straightforward process. There are many VPN service providers available, so you can choose one that meets your specific needs in terms of security features, server locations, speed, and price. Once you have selected a VPN provider, you can download their software or app from their website and follow the installation instructions.
After installing the VPN software on your Mac, you can easily connect to a VPN server with just a few clicks. This will secure your internet connection and encrypt your online activities, making it difficult for anyone to intercept your data. Whether you are browsing the web, accessing public Wi-Fi networks, or streaming content, using a VPN can help maintain your privacy and anonymity online.
Additionally, a VPN can also help you bypass censorship or geo-restrictions, allowing you to access region-locked content and websites. It can also prevent your Internet Service Provider (ISP) from monitoring your online behavior and selling your browsing history to third parties.
In conclusion, using a VPN on your Mac can add an extra layer of protection to your online presence and ensure your sensitive information remains private. By investing in a reliable VPN service and following best practices for online security, you can browse the internet safely and anonymously.
0 notes
Text
Micro Pc Tech - How virus can be removed
Removing a virus from a micro PC follows similar principles to removing malware from any other computer. Here’s a general guide by Micro Pc tech to help you remove viruses from your micro PC:
Disconnect from the Internet: The first step is to disconnect your micro PC from the internet to prevent the virus from spreading or communicating with its source.
Enter Safe Mode: Boot your micro PC into Safe Mode. This will prevent the virus from running automatically when the system starts up. To enter Safe Mode, restart your computer and repeatedly press the F8 key (or another key depending on your system) before the Windows logo appears. From the Advanced Boot Options menu, select Safe Mode with Networking.
Use Antivirus Software: If you have antivirus software installed on your micro PC, run a full system scan. Allow the antivirus program to quarantine or remove any detected threats. If you don’t have antivirus software installed, you can download and use reputable free antivirus tools like Malwarebytes, Avast, or AVG.
Manually Remove Suspicious Programs: Go to the Control Panel on your micro PC and uninstall any programs that you don’t recognize or that seem suspicious. Some viruses disguise themselves as legitimate software.
Check Browser Extensions and Plugins: Viruses often install malicious browser extensions or plugins. Open your web browser and remove any suspicious extensions or plugins from the settings or extensions menu.
Clear Temporary Files and Cache: Viruses can sometimes hide in temporary files and cache. Use the Disk Cleanup tool to remove temporary files and clear the cache on your micro PC.
Update Your Operating System and Software: Ensure that your micro PC’s operating system and all installed software are up to date with the latest security patches and updates. This helps protect your system from known vulnerabilities that malware may exploit.
Reset Browser Settings: Reset your web browser to its default settings to remove any changes made by the virus. This will also remove any unwanted toolbars, home page hijackers, and other browser modifications.
Perform a System Restore: If you’re still experiencing issues after following the above steps, you can perform a system restore to revert your micro PC to a previous state before the virus infection occurred. Be aware that this may result in the loss of recent files and changes made to your system settings.
Backup Important Data: Before proceeding with any drastic measures like system restores or reinstalling your operating system, make sure to back up any important data to an external storage device or cloud service.
Seek Professional Help: If you’re unable to remove the virus yourself, or if your micro PC continues to exhibit suspicious behavior even after removal attempts, seek assistance from a professional computer technician or IT support service.
Remember to regularly update your antivirus software and perform scans to prevent future virus infections on your micro PC. Additionally, practice safe browsing habits and avoid downloading or clicking on suspicious links and email attachments.
0 notes
Text
Did the new Windows 10 update install something weird? I swear I restarted my computer the other day and it installed something and now it’s causing a weird lag that I don’t understand.
Like is there something running in the background that’s being hidden? Can I dig it out and uninstall it? Honestly while we’re at it are there other bloatware things I can uninstall to make my computer run more smoothly? I hate how much like. Windows mandatory programming clutters up memory. I get something stuff needs to be running in the background, I do voluntarily run malwarebytes myself and that takes up space. But like. Aaaa. How is my mouse lagging? What did you put in my fucking computer? How do I take it out?
0 notes