#microservice example
Explore tagged Tumblr posts
Video
youtube
(via Spring Boot GraphQL Mongo DB Project Tutorial with Example for API Developers) Full Video Link https://youtu.be/JElcKeh9a5A Hello friends, new #video on #springboot #graphql #mongodb #api #microservices #application #tutorial for #developer #programmers with #examples are published on #codeonedigest #youtube channel. @java #java #aws #awscloud @awscloud @AWSCloudIndia #salesforce #Cloud #CloudComputing @YouTube #youtube #azure #msazure #codeonedigest @codeonedigest #graphqlspringboot #graphqlspringboottutorial #graphqlspringbootmicroservicesexample #graphqlspringbootexample #graphqlmongodbexample #graphqlmongodbspringboot #springbootmongodb #springbootgraphql #springbootgraphqltutorial #springbootgraphqlexample #springbootgraphqlresolver #springbootgraphqlschema #springbootgraphqlschemamapping #springbootgraphqlmongodb #mongodbtutorialforbeginners #springboottutorial #springbootproject #graphql
#video#springboot#graphql#mongodb#api#microservices#application#tutorial#developer#programmers#examples#codeonedigest#you…
0 notes
Text
Event-Driven Design Demystified: Concepts and Examples
🚀 Discover how this cutting-edge architecture transforms software systems with real-world examples. From e-commerce efficiency to smart home automation, learn how to create responsive and scalable applications #EventDrivenDesign #SoftwareArchitecture
In the world of software architecture, event-driven design has emerged as a powerful paradigm that allows systems to react and respond to events in a flexible and efficient manner. Whether you’re building applications, microservices, or even IoT devices, understanding event-driven design can lead to more scalable, responsive, and adaptable systems. In this article, we’ll delve into the core…

View On WordPress
#Asynchronous Communication#Decoupling Components#E-commerce Order Processing#Event Broker Paradigm#Event Sources and Consumers#Event-driven architecture#Event-Driven Examples#Event-Driven Paradigm#Event-Triggered Workflows#Microservices and Events#Middleware in Event-Driven Design#Modular Development#Reactive Systems#Real-Time Responsiveness#Scalable Software Systems#Smart Home Automation#Social Media Notifications#Software Design Patterns#System Event Handling#User Experience Enhancement
1 note
·
View note
Text
Ready to future-proof your applications and boost performance? Discover how PHP microservices can transform your development workflow! 💡
In this powerful guide, you'll learn: ✅ What PHP Microservices Architecture really means ✅ How to break a monolithic app into modular services ✅ Best tools for containerization like Docker & Kubernetes ✅ API Gateway strategies and service discovery techniques ✅ Tips on error handling, security, and performance optimization
With real-world examples and practical steps, this guide is perfect for developers and teams aiming for faster deployment, independent scaling, and simplified maintenance.
🎯 Whether you’re a solo developer or scaling a product, understanding microservices is the key to next-level architecture.
🌐 Brought to you by Orbitwebtech, Best Web Development Company in the USA, helping businesses build powerful and scalable web solutions.
📖 Start reading now and give your PHP projects a cutting-edge upgrade!
2 notes
·
View notes
Text
How To Get An Online Internship In the IT Sector (Skills And Tips)

Internships provide invaluable opportunities to gain practical skills, build professional networks, and get your foot in the door with top tech companies.
With remote tech internships exploding in IT, online internships are now more accessible than ever. Whether a college student or career changer seeking hands-on IT experience, virtual internships allow you to work from anywhere.
However, competition can be fierce, and simply applying is often insufficient. Follow this comprehensive guide to develop the right technical abilities.
After reading this, you can effectively showcase your potential, and maximize your chances of securing a remote tech internship.
Understand In-Demand IT Skills
The first step is gaining a solid grasp of the most in-demand technical and soft skills. While specific requirements vary by company and role, these competencies form a strong foundation:
Technical Skills:
Proficiency in programming languages like Python, JavaScript, Java, and C++
Experience with front-end frameworks like React, Angular, and Vue.js
Back-end development skills - APIs, microservices, SQL databases Cloud platforms such as AWS, Azure, Google Cloud
IT infrastructure skills - servers, networks, security
Data science abilities like SQL, R, Python
Web development and design
Mobile app development - Android, iOS, hybrid
Soft Skills:
Communication and collaboration
Analytical thinking and problem-solving
Leadership and teamwork
Creativity and innovation
Fast learning ability
Detail and deadline-oriented
Flexibility and adaptability
Obtain Relevant Credentials
While hands-on skills hold more weight, relevant academic credentials and professional IT certifications can strengthen your profile. Consider pursuing:
Bachelor’s degree in Computer Science, IT, or related engineering fields
Internship-specific courses teaching technical and soft skills
Certificates like CompTIA, AWS, Cisco, Microsoft, Google, etc.
Accredited boot camp programs focusing on applied skills
MOOCs to build expertise in trending technologies like AI/ML, cybersecurity
Open source contributions on GitHub to demonstrate coding skills
The right credentials display a work ethic and supplement practical abilities gained through projects.
Build An Impressive Project Portfolio
Nothing showcases skills better than real-world examples of your work. Develop a portfolio of strong coding, design, and analytical projects related to your target internship field.
Mobile apps - publish on app stores or use GitHub project pages
Websites - deploy online via hosting services
Data science - showcase Jupyter notebooks, visualizations
Open source code - contribute to public projects on GitHub
Technical writing - blog posts explaining key concepts
Automation and scripts - record demo videos
Choose projects demonstrating both breadth and depth. Align them to skills required for your desired internship roles.
Master Technical Interview Skills
IT internship interviews often include challenging technical questions and assessments. Be prepared to:
Explain your code and projects clearly. Review them beforehand.
Discuss concepts related to key technologies on your resume. Ramp up on fundamentals.
Solve coding challenges focused on algorithms, data structures, etc. Practice online judges like LeetCode.
Address system design and analytical problems. Read case interview guides.
Show communication and collaboration skills through pair programming tests.
Ask smart, well-researched questions about the company’s tech stack, projects, etc.
Schedule dedicated time for technical interview practice daily. Learn to think aloud while coding and get feedback from peers.
Show Passion and Curiosity
Beyond raw skills, demonstrating genuine passion and curiosity for technology goes a long way.
Take online courses and certifications beyond the college curriculum
Build side projects and engage in hackathons for self-learning
Stay updated on industry news, trends, and innovations
Be active on forums like StackOverflow to exchange knowledge
Attend tech events and conferences
Participate in groups like coding clubs and prior internship programs
Follow tech leaders on social mediaListen to tech podcasts while commuting
Show interest in the company’s mission, products, and culture
This passion shines through in interviews and applications, distinguishing you from other candidates.
Promote Your Personal Brand
In the digital age, your online presence and personal brand are make-or-break. Craft a strong brand image across:
LinkedIn profile - showcase achievements, skills, recommendations
GitHub - displays coding activity and quality through clean repositories
Portfolio website - highlight projects and share valuable content
Social media - post career updates and useful insights, but avoid oversharing
Blogs/videos - demonstrate communication abilities and thought leadership
Online communities - actively engage and build relationships
Ensure your profiles are professional and consistent. Let your technical abilities and potential speak for themselves.
Optimize Your Internship Applications
Applying isn’t enough. You must optimize your internship applications to get a reply:
Ensure you apply to openings that strongly match your profile Customize your resume and cover letters using keywords in the job description
Speak to skills gained from coursework, online learning, and personal projects
Quantify achievements rather than just listing responsibilities
Emphasize passion for technology and fast learning abilities
Ask insightful questions that show business understanding
Follow up respectfully if you don’t hear back in 1-2 weeks
Show interest in full-time conversion early and often
Apply early since competitive openings close quickly
Leverage referrals from your network if possible
This is how you do apply meaningfully. If you want a good internship, focus on the quality of applications. The hard work will pay off.
Succeed in Your Remote Internship
The hard work pays off when you secure that long-awaited internship! Continue standing out through the actual internship by:
Over Communicating in remote settings - proactively collaborate
Asking smart questions and owning your learning
Finding mentors and building connections remotely
Absorbing constructive criticism with maturity
Shipping quality work on or before deadlines
Clarifying expectations frequently
Going above and beyond prescribed responsibilities sometimes
Getting regular feedback and asking for more work
Leaving with letters of recommendation and job referrals
When you follow these tips, you are sure to succeed in your remote internship. Remember, soft skills can get you long ahead in the company, sometimes core skills can’t.
Conclusion
With careful preparation, tenacity, and a passion for technology, you will be able to get internships jobs in USA that suit your needs in the thriving IT sector.
Use this guide to build the right skills, create an impressive personal brand, ace the applications, and excel in your internship.
Additionally, you can browse some good job portals. For instance, GrandSiren can help you get remote tech internships. The portal has the best internship jobs in India and USA you’ll find. The investment will pay dividends throughout your career in this digital age. Wishing you the best of luck! Let me know in the comments about your internship hunt journey.
#itjobs#internship opportunities#internships#interns#entryleveljobs#gradsiren#opportunities#jobsearch#careeropportunities#jobseekers#ineffable interns#jobs#employment#career
4 notes
·
View notes
Text
How To Get An Online Internship In the IT Sector (Skills And Tips)

Internships provide invaluable opportunities to gain practical skills, build professional networks, and get your foot in the door with top tech companies.
With remote tech internships exploding in IT, online internships are now more accessible than ever. Whether a college student or career changer seeking hands-on IT experience, virtual internships allow you to work from anywhere.
However, competition can be fierce, and simply applying is often insufficient. Follow this comprehensive guide to develop the right technical abilities.
After reading this, you can effectively showcase your potential, and maximize your chances of securing a remote tech internship.
Understand In-Demand IT Skills
The first step is gaining a solid grasp of the most in-demand technical and soft skills. While specific requirements vary by company and role, these competencies form a strong foundation:
Technical Skills:
>> Proficiency in programming languages like Python, JavaScript, Java, and C++ >> Experience with front-end frameworks like React, Angular, and Vue.js >> Back-end development skills - APIs, microservices, SQL databases >> Cloud platforms such as AWS, Azure, Google Cloud >> IT infrastructure skills - servers, networks, security >> Data science abilities like SQL, R, Python >> Web development and design >> Mobile app development - Android, iOS, hybrid
Soft Skills:
>> Communication and collaboration >> Analytical thinking and problem-solving >> Leadership and teamwork >> Creativity and innovation >> Fast learning ability >> Detail and deadline-oriented >> Flexibility and adaptability
Obtain Relevant Credentials
While hands-on skills hold more weight, relevant academic credentials and professional IT certifications can strengthen your profile. Consider pursuing:
>> Bachelor’s degree in Computer Science, IT, or related engineering fields. >> Internship-specific courses teaching technical and soft skills. >> Certificates like CompTIA, AWS, Cisco, Microsoft, Google, etc. >> Accredited boot camp programs focusing on applied skills. >> MOOCs to build expertise in trending technologies like AI/ML, cybersecurity. >> Open source contributions on GitHub to demonstrate coding skills.
The right credentials display a work ethic and supplement practical abilities gained through projects.
Build An Impressive Project Portfolio
Nothing showcases skills better than real-world examples of your work. Develop a portfolio of strong coding, design, and analytical projects related to your target internship field.
>> Mobile apps - publish on app stores or use GitHub project pages >> Websites - deploy online via hosting services >> Data science - showcase Jupyter notebooks, visualizations >> Open source code - contribute to public projects on GitHub >> Technical writing - blog posts explaining key concepts >> Automation and scripts - record demo videos
Choose projects demonstrating both breadth and depth. Align them to skills required for your desired internship roles.
Master Technical Interview Skills
IT internship interviews often include challenging technical questions and assessments. Be prepared to:
>> Explain your code and projects clearly. Review them beforehand. >> Discuss concepts related to key technologies on your resume. Ramp up on fundamentals. >> Solve coding challenges focused on algorithms, data structures, etc. Practice online judges like LeetCode. >> Address system design and analytical problems. Read case interview guides. >> Show communication and collaboration skills through pair programming tests. >> Ask smart, well-researched questions about the company’s tech stack, projects, etc.
Schedule dedicated time for technical interview practice daily. Learn to think aloud while coding and get feedback from peers.
Show Passion and Curiosity
Beyond raw skills, demonstrating genuine passion and curiosity for technology goes a long way.
>> Take online courses and certifications beyond the college curriculum >> Build side projects and engage in hackathons for self-learning >> Stay updated on industry news, trends, and innovations >> Be active on forums like StackOverflow to exchange knowledge >> Attend tech events and conferences >> Participate in groups like coding clubs and prior internship programs >> Follow tech leaders on social media >> Listen to tech podcasts while commuting >> Show interest in the company’s mission, products, and culture
This passion shines through in interviews and applications, distinguishing you from other candidates.
Promote Your Personal Brand
In the digital age, your online presence and personal brand are make-or-break. Craft a strong brand image across:
>> LinkedIn profile - showcase achievements, skills, recommendations >> GitHub - displays coding activity and quality through clean repositories >> Portfolio website - highlight projects and share valuable content >> Social media - post career updates and useful insights, but avoid oversharing >> Blogs/videos - demonstrate communication abilities and thought leadership >> Online communities - actively engage and build relationships
Ensure your profiles are professional and consistent. Let your technical abilities and potential speak for themselves.
Optimize Your Internship Applications
Applying isn’t enough. You must optimize your internship applications to get a reply:
>> Ensure you apply to openings that strongly match your profile >> Customize your resume and cover letters using keywords in the job description >> Speak to skills gained from coursework, online learning, and personal projects >> Quantify achievements rather than just listing responsibilities >> Emphasize passion for technology and fast learning abilities >> Ask insightful questions that show business understanding >> Follow up respectfully if you don’t hear back in 1-2 weeks >> Show interest in full-time conversion early and often >> Apply early since competitive openings close quickly >> Leverage referrals from your network if possible
This is how you do apply meaningfully. If you want a good internship, focus on the quality of applications. The hard work will pay off.
Succeed in Your Remote Internship
The hard work pays off when you secure that long-awaited internship! Continue standing out through the actual internship by:
>> Over Communicating in remote settings - proactively collaborate >> Asking smart questions and owning your learning >> Finding mentors and building connections remotely >> Absorbing constructive criticism with maturity >> Shipping quality work on or before deadlines >> Clarifying expectations frequently >> Going above and beyond prescribed responsibilities sometimes >> Getting regular feedback and asking for more work >> Leaving with letters of recommendation and job referrals
When you follow these tips, you are sure to succeed in your remote internship. Remember, soft skills can get you long ahead in the company, sometimes core skills can’t.
Conclusion
With careful preparation, tenacity, and a passion for technology, you will be able to get internships jobs in USA that suit your needs in the thriving IT sector.
Use this guide to build the right skills, create an impressive personal brand, ace the applications, and excel in your internship.
Additionally, you can browse some good job portals. For instance, GrandSiren can help you get remote tech internships. The portal has the best internship jobs in India and USA you’ll find.
The investment will pay dividends throughout your career in this digital age. Wishing you the best of luck! Let me know in the comments about your internship hunt journey.
#internship#internshipopportunity#it job opportunities#it jobs#IT internships#jobseekers#jobsearch#entryleveljobs#employment#gradsiren#graduation#computer science#technology#engineering#innovation#information technology#remote jobs#remote work#IT Remote jobs
5 notes
·
View notes
Text
Mastering AWS DevOps in 2025: Best Practices, Tools, and Real-World Use Cases
In 2025, the cloud ecosystem continues to grow very rapidly. Organizations of every size are embracing AWS DevOps to automate software delivery, improve security, and scale business efficiently. Mastering AWS DevOps means knowing the optimal combination of tools, best practices, and real-world use cases that deliver success in production.
This guide will assist you in discovering the most important elements of AWS DevOps, the best practices of 2025, and real-world examples of how top companies are leveraging AWS DevOps to compete.
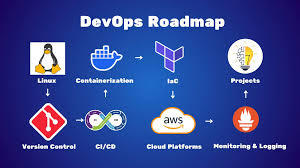
What is AWS DevOps
AWS DevOps is the union of cultural principles, practices, and tools on Amazon Web Services that enhances an organization's capacity to deliver applications and services at a higher speed. It facilitates continuous integration, continuous delivery, infrastructure as code, monitoring, and cooperation among development and operations teams.
Why AWS DevOps is Important in 2025
As organizations require quicker innovation and zero downtime, DevOps on AWS offers the flexibility and reliability to compete. Trends such as AI integration, serverless architecture, and automated compliance are changing how teams adopt DevOps in 2025.
Advantages of adopting AWS DevOps:
1 Faster deployment cycles
2 Enhanced system reliability
3 Flexible and scalable cloud infrastructure
4 Automation from code to production
5 Integrated security and compliance
Best AWS DevOps Tools to Learn in 2025
These are the most critical tools fueling current AWS DevOps pipelines:
AWS CodePipeline
Your release process can be automated with our fully managed CI/CD service.
AWS CodeBuild
Scalable build service for creating ready-to-deploy packages, testing, and building source code.
AWS CodeDeploy
Automates code deployments to EC2, Lambda, ECS, or on-prem servers with zero-downtime approaches.
AWS CloudFormation and CDK
For infrastructure as code (IaC) management, allowing repeatable and versioned cloud environments.
Amazon CloudWatch
Facilitates logging, metrics, and alerting to track application and infrastructure performance.
AWS Lambda
Serverless compute that runs code in response to triggers, well-suited for event-driven DevOps automation.
AWS DevOps Best Practices in 2025
1. Adopt Infrastructure as Code (IaC)
Utilize AWS CloudFormation or Terraform to declare infrastructure. This makes it repeatable, easier to collaborate on, and version-able.
2. Use Full CI/CD Pipelines
Implement tools such as CodePipeline, GitHub Actions, or Jenkins on AWS to automate deployment, testing, and building.
3. Shift Left on Security
Bake security in early with Amazon Inspector, CodeGuru, and Secrets Manager. As part of CI/CD, automate vulnerability scans.
4. Monitor Everything
Utilize CloudWatch, X-Ray, and CloudTrail to achieve complete observability into your system. Implement alerts to detect and respond to problems promptly.
5. Use Containers and Serverless for Scalability
Utilize Amazon ECS, EKS, or Lambda for autoscaling. These services lower infrastructure management overhead and enhance efficiency.
Real-World AWS DevOps Use Cases
Use Case 1: Scalable CI/CD for a Fintech Startup
AWS CodePipeline and CodeDeploy were used by a financial firm to automate deployments in both production and staging environments. By containerizing using ECS and taking advantage of CloudWatch monitoring, they lowered deployment mistakes by 80 percent and attained near-zero downtime.
Use Case 2: Legacy Modernization for an Enterprise
A legacy enterprise moved its on-premise applications to AWS with CloudFormation and EC2 Auto Scaling. Through the adoption of full-stack DevOps pipelines and the transformation to microservices with EKS, they enhanced time-to-market by 60 percent.
Use Case 3: Serverless DevOps for a SaaS Product
A SaaS organization utilized AWS Lambda and API Gateway for their backend functions. They implemented quick feature releases and automatically scaled during high usage without having to provision infrastructure using CodeBuild and CloudWatch.
Top Trends in AWS DevOps in 2025
AI-driven DevOps: Integration with CodeWhisperer, CodeGuru, and machine learning algorithms for intelligence-driven automation
Compliance-as-Code: Governance policies automated using services such as AWS Config and Service Control Policies
Multi-account strategies: Employing AWS Organizations for scalable, secure account management
Zero Trust Architecture: Implementing strict identity-based access with IAM, SSO, and MFA
Hybrid Cloud DevOps: Connecting on-premises systems to AWS for effortless deployments
Conclusion
In 2025, becoming a master of AWS DevOps means syncing your development workflows with cloud-native architecture, innovative tools, and current best practices. With AWS, teams are able to create secure, scalable, and automated systems that release value at an unprecedented rate.
Begin with automating your pipelines, securing your deployments, and scaling with confidence. DevOps is the way of the future, and AWS is leading the way.
Frequently Asked Questions
What distinguishes AWS DevOps from DevOps? While AWS DevOps uses AWS services and tools to execute DevOps, DevOps itself is a practice.
Can small teams benefit from AWS DevOps
Yes. AWS provides fully managed services that enable small teams to scale and automate without having to handle complicated infrastructure.
Which programming languages does AWS DevOps support
AWS supports the big ones - Python, Node.js, Java, Go, .NET, Ruby, and many more.
Is AWS DevOps for enterprise-scale applications
Yes. Large enterprises run large-scale, multi-region applications with millions of users using AWS DevOps.
1 note
·
View note
Text
Docker Guide: Introduction, Benefits, and Basic Example
This comprehensive guide offers an accessible introduction to
Docker, a powerful platform for developing, shipping, and running applications in isolated environments. We'll demystify what Docker is, explore its key benefits such as portability, scalability, and efficiency, and walk you through a practical, basic example to get you started with containerization.
#Docker #Containerization #DevOps #Introduction #Benefits #Example #Tutorial #Beginner #SoftwareDevelopment #ApplicationDeployment #Virtualization #Microservices
0 notes
Text
Top Spring Boot Interview Questions and Answers (2025 Edition)

Spring Boot has become the standard for building production-ready Java applications with minimal configuration. If you're preparing for a backend or full-stack developer role, having a good grip on common Spring Boot interview questions is a must.
In this post, we’ll walk you through the most frequently asked Spring Boot questions to help you ace your next interview.
📘 Want a complete list with detailed answers and code examples? 👉 Read the full guide here: Spring Boot Interview Questions – Freshy Blog
🔹 What is Spring Boot?
Spring Boot is an extension of the Spring framework that simplifies the development of Java-based applications by providing auto-configuration, embedded servers, and production-ready defaults.
🔸 Common Spring Boot Interview Questions
1. What are the main features of Spring Boot?
Auto Configuration
Starter Dependencies
Spring Boot CLI
Actuator
Embedded Web Servers (Tomcat, Jetty)
2. What is the difference between Spring and Spring Boot?
Spring Boot is a rapid application development framework built on top of Spring. It eliminates boilerplate configuration and helps developers get started quickly.
🔸 Intermediate Spring Boot Questions
3. What are Starter dependencies?
Starter dependencies are a set of convenient dependency descriptors that you can include in your application. For example:
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-web</artifactId>
</dependency>
4. What is Spring Boot Actuator?
Spring Boot Actuator provides production-ready features like monitoring, metrics, and health checks of your application.
🔹 Advanced Spring Boot Questions
5. How does auto-configuration work in Spring Boot?
Spring Boot automatically configures your application based on the dependencies you have in your classpath using @EnableAutoConfiguration.
6. How can you secure a Spring Boot application?
You can use spring-boot-starter-security and configure it with annotations like @EnableWebSecurity, along with custom authentication and authorization logic.
🔍 More Questions Covered in the Full Guide:
What are Profiles in Spring Boot?
What is the role of application.properties or application.yml?
How to implement exception handling in Spring Boot?
How to integrate Spring Boot with databases like MySQL, PostgreSQL?
👉 Get full coverage with examples, tips, and best practices: 🔗 https://www.freshyblog.com/spring-boot-interview-questions/
✅ Quick Tips for Spring Boot Interviews
Understand how dependency injection works
Be familiar with REST API development in Spring Boot
Practice building microservices
Explore Spring Security basics
Review annotations like @RestController, @Service, @Component, and @Repository
Final Thoughts
Mastering these Spring Boot interview questions can give you a solid edge in any technical interview. As Java continues to be a dominant backend language, Spring Boot remains a vital tool in the modern developer’s toolkit.
📘 Want to dive deeper? 👉 Visit the full interview question guide here: Spring Boot Interview Questions – Freshy Blog
#SpringBootInterviewQuestions#JavaDeveloper#SpringFramework#BackendDevelopment#TechInterviews#JavaJobs#SpringBootTips#FreshyBlog#InterviewPrep2025#SpringBoot2025#tech#technology
0 notes
Text
Many organizations have well-thought-out, documented processes for managing secrets that work well enough as long as requests are infrequent. In the context of app development, “secrets” might refer to any information that is used by both machines and humans to verify access to restricted environments such as credentials, keys, tokens, and certificates. When every person on the dev team and any app, software, microservice and container needs to be granted permission to perform a given action, we can understand how important proper “management” can be. As your organization grows and the number of applications, components, cloud endpoints and systems you support increases, the process of managing secrets becomes increasingly complex and time-consuming. If your team is among the majority of organizations that have begun to adopt a DevSecOps approach, much of this burden falls upon you. It’s easy to become quickly overwhelmed when supporting hundreds of containers and developers to ensure that secrets are managed and distributed securely. Accessing Secrets for Machines When developers need secrets for their applications, they must make a request through a defined process, such as creating a ticket or sending an email. The DevSecOps team then provides the requested secrets or updates the developer's access to the central repository where the secrets are stored. While this process frequently ensures the security of sensitive information, it can also introduce challenges and complexities in distributing and managing secrets, such as the overhead needed for an infrastructure team to manage thousands of credentials with requests coming in nonstop anytime a change is required. In an attempt to preserve an organization's security, engineers who might not be familiar with a specific application end up handling a high volume of identical tasks on a daily basis. And as a rule of thumb, any time there's a manual process combined with an overwhelming workload, you're running a high risk of errors compromising the security of sensitive information and your organization's efficiency. These seemingly minor errors can have severe consequences in high-stakes deployments of new features. For example, an extra space or a typo can cause a deployment to fail, leading to a slower time-to-market and potentially impacting business operations. Additionally, as snafus occur and process friction rises, you risk losing the trust of development teams. They never know ahead of time if their secret will work correctly in a production-level environment and may worry about its potential impact on end users. In this case, the secrets are impossible to validate. Your secrets may have worked in all lower testing environments and even an inactive production environment... but when it's time to deploy changes to production, a failure still occurs. Guiding Principles In the aforementioned scenario, the manual process for managing secrets directly opposes the core principles of effective secret management. As a DevSecOps engineer, it's essential to strive for automation in all aspects of the job, including the distribution of secrets. To address this challenge, it's crucial to implement the Zero Trust principle. This means that all access to secrets must be verified and authenticated before granting access... or, as we like to call it, "guilty until proven innocent." On top of Zero Trust, other fundamental principles, like Just-in-Time credentials and continuous monitoring, are also key to success. In the fast-paced world of DevOps, machines access information much more quickly than humans do, making automation of secret generation, rotation, and management essential to reducing the risk of human error. Also, real-time monitoring, alerting, and reporting capabilities are essential to quickly detect and respond to any potential incidents or issues related to secrets. Let's go back to our example and start to unpack the steps needed to align with industry best practices for secrets management.
For starters, the manual generation of secrets must stop and be taken off the plate of the DevSecOps team. There are a couple ways of doing this, which your organization should consider based on its container infrastructure and security requirements. Deploy-Time Secrets These are like access keys or passwords, encrypted and bundled with the application code and stored in the code repository. They are embedded within the code and stored within version control systems like Git. The idea here is to put control in the hands of developers. They can access a tool to request and generate a production secret without ever seeing the value and by simply using a reference to the value. Some key advantages of managing secrets for deploy-time injection: Solid Security - Parameterized values are stored in the source code, so developers only have access to encrypted values. Improved Control - Secrets can be updated or revoked without impacting code. Scalability - Secrets are centrally managed, and developers can begin self-servicing the secrets with the right solutions implemented. Runtime Secrets Runtime secrets, on the other hand, are encrypted, stored and accessed separately from the code and managed by a secure secret management system. These are used at runtime, like user credentials or API keys. Some key advantages of managing secrets for runtime injection: Just-in-Time Access - This minimizes the risk of stand privileges that are easily exploitable. Revoke Access at Any Time - Ensure that sensitive data is only accessed by authorized parties or applications, and that secrets are never hard coded. Dynamic - Your secrets can be updated without performing a redeployment of the application. Using dynamic, parameterized secrets certainly makes sense, whether they’re used upon deployment or in runtime. However, no matter what approach you take, proper use of secrets does involve added layers of complexity. Any time you adopt new tools and processes, and a higher level of developer ownership, you’re necessarily looking at more to manage. You’re also likely to compromise visibility, as monitoring and revocation becomes harder. There are several effective options available for the transformation of deploy-time and runtime secret management. Akeyless, a SaaS platform, offers centralized management and automation for Just-in-Time credentials, secret rotation and access management. Unlike the open-source HashiCorp Vault, Akeyless offers a more scalable approach while providing a Zero Trust level of security for your secrets as they are not visible / accessible to third-party cloud service providers. To Summarize The main difference between deploy-time and runtime secrets is when they are used and how they are stored. Deploy-time secrets are used during the deployment process, while runtime secrets are used while the application runs. Starting out, your organization might opt for deploy-time secret loading, which means a developer will be able to self-service the deployment of secrets as configuration to relevant containers. In our example, this could be a practical first step as they continue the transformation of secret management. Then, eventually, DevSecOps teams are often best off transitioning to runtime secrets by identifying all secrets currently stored in code, migrating them to a secret management system, and updating the code to retrieve secrets at runtime. This process can be complex and time-consuming, but it's essential to ensure the security and privacy of sensitive information in today's fast-paced, dynamic development environments.
0 notes
Video
youtube
GraphQL Scalar Type & Object Type Explained with Examples for API Develo... Full Video Link - https://youtube.com/shorts/-FNUPdoJOVIHi, a new #video on #graphql #scalar & #object #type published on #codeonedigest #youtube channel. @java #java #awscloud @awscloud #aws @AWSCloudIndia #Cloud #CloudComputing @YouTube #youtube #azure #msazure #codeonedigest @codeonedigest #graphql #graphqltutorial #graphql #graphqltutorial #graphql #graphqltutorialforbeginners #graphqlscalartype #graphqlobjectargument #graphqlobjectfield #graphqlobjectnullprototype #graphqlobjecttype #graphqltypeunion #graphqltyperesolver #graphqltypesafety #graphqltypevsinterface #graphqlexplained #graphqlexample #graphqlexampletutorial #graphqlapicalls #graphqlapiproject #graphqlcrashcourse #graphqldeveloper #graphqlexplainedin100seconds #graphqlapijava #api #microservice
#youtube#graphql#graphql type#graphql scalar type#scalar type#object type#graphql object type#graphql api#graphql example#graphql microservice#microservice tutorial#graphql tutorial
1 note
·
View note
Text
How Web Development Companies Choose the Right Tech Stack for Your Project
When starting a web development project, one of the most critical decisions is choosing the right technology stack—the combination of tools, programming languages, frameworks, and databases used to build and run your website or application. A skilled Web Development Company doesn’t just pick trendy tools—they strategically select a tech stack that fits your goals, budget, scalability, and long-term vision.
This decision shapes the performance, security, development speed, and maintainability of your project. Let’s explore how professional web development companies approach tech stack selection—and why it makes all the difference.
1. Understanding Project Requirements
Every project is unique. Before recommending any technologies, a web development company conducts in-depth discovery sessions to understand your:
Business goals
Target audience
Required features
Budget and timeline
Integration needs (CRM, APIs, payments, etc.)
Expected user volume and growth potential
For example, a content-heavy blog needs different tools than a real-time messaging app or an enterprise eCommerce platform.
Why it matters: The right stack should align with the core functionality and complexity of your specific project.
2. Frontend Stack Considerations
The frontend stack determines how your website looks and behaves for users. Agencies typically choose from frameworks and libraries such as:
React.js – Ideal for interactive, high-performance UIs
Vue.js – Lightweight and easy to integrate
Next.js – Server-side rendering and SEO-friendly features
Tailwind CSS or Bootstrap – For fast, responsive styling
The choice depends on user experience requirements, SEO priorities, and how dynamic the interface needs to be.
Why it matters: A responsive, fast-loading frontend increases engagement and improves SEO performance.
3. Backend Stack Considerations
The backend stack powers the logic behind the scenes—data processing, server responses, user authentication, etc. Common choices include:
Node.js – Non-blocking, event-driven, great for scalable applications
Python with Django/Flask – Ideal for fast MVPs and data-heavy platforms
PHP with Laravel – Secure and well-supported, especially for CMS-based sites
Java or .NET – Enterprise-level applications with complex infrastructure
Database decisions (e.g., MySQL, MongoDB, PostgreSQL) are also influenced by the type of data, relationships, and scalability needed.
Why it matters: Backend choices directly impact performance, security, and future extensibility.
4. Scalability and Long-Term Maintenance
A web development company always plans for growth. If you’re building an MVP now but expect to scale to thousands of users, the tech stack must be capable of handling that without requiring a complete rebuild.
This means selecting tools with a strong community, active support, and modular architecture. Headless CMS options, API-first architectures, and microservices are often chosen for their flexibility.
Why it matters: A scalable stack ensures your platform evolves with your business—not against it.
5. Team Expertise and Community Support
An experienced web development agency won’t just chase trends—they choose tools their team is proficient in and that have strong community ecosystems. This means faster development, fewer bugs, and access to trusted libraries and plugins.
Tools with large communities (like React, Laravel, or Node.js) are easier to maintain and integrate with new technologies as they emerge.
Why it matters: Established tools reduce technical debt and development risks.
6. Security and Compliance
Depending on your industry, your tech stack may need to meet specific security standards—HIPAA for healthcare, PCI-DSS for eCommerce, or GDPR for data protection. Developers choose technologies with built-in security features, encryption protocols, and access control layers.
They also avoid stacks with known vulnerabilities or outdated dependencies.
Why it matters: A secure foundation protects your business and user data from the start.
7. Third-Party Integrations and DevOps
Will your project need payment gateways, CRM tools, marketing platforms, or cloud services? The chosen stack must allow easy integration with third-party APIs. In addition, agencies consider DevOps tools for continuous integration, deployment, monitoring, and scaling—often using platforms like Docker, AWS, or Vercel.
Why it matters: A tech stack that plays well with your ecosystem leads to smoother operations and automation.
Final Thoughts
Choosing the right tech stack isn’t just about technical specs—it’s about aligning with your business goals, user needs, and growth plans. A trusted Web Development Company brings a strategic, experience-backed approach to this decision, ensuring that your platform is stable, scalable, and ready for the future.
With the right combination of frontend frameworks, backend technologies, databases, and DevOps tools, your project can launch faster, perform better, and adapt more easily over time. Don’t leave your tech stack to chance—build with purpose, and partner with experts who know how to get it right from the start.
0 notes
Text
52013l4 in Modern Tech: Use Cases and Applications

In a technology-driven world, identifiers and codes are more than just strings—they define systems, guide processes, and structure workflows. One such code gaining prominence across various IT sectors is 52013l4. Whether it’s in cloud services, networking configurations, firmware updates, or application builds, 52013l4 has found its way into many modern technological environments. This article will explore the diverse use cases and applications of 52013l4, explaining where it fits in today’s digital ecosystem and why developers, engineers, and system administrators should be aware of its implications.
Why 52013l4 Matters in Modern Tech
In the past, loosely defined build codes or undocumented system identifiers led to chaos in large-scale environments. Modern software engineering emphasizes observability, reproducibility, and modularization. Codes like 52013l4:
Help standardize complex infrastructure.
Enable cross-team communication in enterprises.
Create a transparent map of configuration-to-performance relationships.
Thus, 52013l4 isn’t just a technical detail—it’s a tool for governance in scalable, distributed systems.
Use Case 1: Cloud Infrastructure and Virtualization
In cloud environments, maintaining structured builds and ensuring compatibility between microservices is crucial. 52013l4 may be used to:
Tag versions of container images (like Docker or Kubernetes builds).
Mark configurations for network load balancers operating at Layer 4.
Denote system updates in CI/CD pipelines.
Cloud providers like AWS, Azure, or GCP often reference such codes internally. When managing firewall rules, security groups, or deployment scripts, engineers might encounter a 52013l4 identifier.
Use Case 2: Networking and Transport Layer Monitoring
Given its likely relation to Layer 4, 52013l4 becomes relevant in scenarios involving:
Firewall configuration: Specifying allowed or blocked TCP/UDP ports.
Intrusion detection systems (IDS): Tracking abnormal packet flows using rules tied to 52013l4 versions.
Network troubleshooting: Tagging specific error conditions or performance data by Layer 4 function.
For example, a DevOps team might use 52013l4 as a keyword to trace problems in TCP connections that align with a specific build or configuration version.
Use Case 3: Firmware and IoT Devices
In embedded systems or Internet of Things (IoT) environments, firmware must be tightly versioned and managed. 52013l4 could:
Act as a firmware version ID deployed across a fleet of devices.
Trigger a specific set of configurations related to security or communication.
Identify rollback points during over-the-air (OTA) updates.
A smart home system, for instance, might roll out firmware_52013l4.bin to thermostats or sensors, ensuring compatibility and stable transport-layer communication.
Use Case 4: Software Development and Release Management
Developers often rely on versioning codes to track software releases, particularly when integrating network communication features. In this domain, 52013l4 might be used to:
Tag milestones in feature development (especially for APIs or sockets).
Mark integration tests that focus on Layer 4 data flow.
Coordinate with other teams (QA, security) based on shared identifiers like 52013l4.
Use Case 5: Cybersecurity and Threat Management
Security engineers use identifiers like 52013l4 to define threat profiles or update logs. For instance:
A SIEM tool might generate an alert tagged as 52013l4 to highlight repeated TCP SYN floods.
Security patches may address vulnerabilities discovered in the 52013l4 release version.
An organization’s SOC (Security Operations Center) could use 52013l4 in internal documentation when referencing a Layer 4 anomaly.
By organizing security incidents by version or layer, organizations improve incident response times and root cause analysis.
Use Case 6: Testing and Quality Assurance
QA engineers frequently simulate different network scenarios and need clear identifiers to catalog results. Here’s how 52013l4 can be applied:
In test automation tools, it helps define a specific test scenario.
Load-testing tools like Apache JMeter might reference 52013l4 configurations for transport-level stress testing.
Bug-tracking software may log issues under the 52013l4 build to isolate issues during regression testing.
What is 52013l4?
At its core, 52013l4 is an identifier, potentially used in system architecture, internal documentation, or as a versioning label in layered networking systems. Its format suggests a structured sequence: “52013” might represent a version code, build date, or feature reference, while “l4” is widely interpreted as Layer 4 of the OSI Model — the Transport Layer.Because of this association, 52013l4 is often seen in contexts that involve network communication, protocol configuration (e.g., TCP/UDP), or system behavior tracking in distributed computing.
FAQs About 52013l4 Applications
Q1: What kind of systems use 52013l4? Ans. 52013l4 is commonly used in cloud computing, networking hardware, application development environments, and firmware systems. It's particularly relevant in Layer 4 monitoring and version tracking.
Q2: Is 52013l4 an open standard? Ans. No, 52013l4 is not a formal standard like HTTP or ISO. It’s more likely an internal or semi-standardized identifier used in technical implementations.
Q3: Can I change or remove 52013l4 from my system? Ans. Only if you fully understand its purpose. Arbitrarily removing references to 52013l4 without context can break dependencies or configurations.
Conclusion
As modern technology systems grow in complexity, having clear identifiers like 52013l4 ensures smooth operation, reliable communication, and maintainable infrastructures. From cloud orchestration to embedded firmware, 52013l4 plays a quiet but critical role in linking performance, security, and development efforts. Understanding its uses and applying it strategically can streamline operations, improve response times, and enhance collaboration across your technical teams.
0 notes
Text
Cloud Security Market Emerging Trends Driving Next-Gen Protection Models
The cloud security market is undergoing rapid transformation as organizations increasingly migrate their workloads to cloud environments. With the rise of hybrid and multi-cloud deployments, the demand for robust and scalable cloud security solutions is growing. Emerging trends in cloud security reflect both technological evolution and the increasing sophistication of cyber threats. These trends are reshaping how enterprises secure data, manage compliance, and maintain trust in cloud-based systems.

Zero Trust Architecture Becoming a Core Principle
One of the most significant shifts in cloud security is the adoption of Zero Trust Architecture (ZTA). Zero Trust eliminates the traditional notion of a trusted internal network and instead requires continuous verification of user identities and devices, regardless of their location. With cloud environments inherently distributed, ZTA is becoming essential. Enterprises are integrating identity and access management (IAM), multi-factor authentication (MFA), and micro-segmentation to strengthen their security postures.
AI and ML Enhancing Threat Detection and Response
The integration of artificial intelligence (AI) and machine learning (ML) in cloud security tools is accelerating. These technologies are being used to detect anomalies, automate threat responses, and provide real-time risk analysis. AI-driven security platforms can process massive volumes of data from cloud logs and network activities, enabling early detection of sophisticated attacks like insider threats, ransomware, or credential stuffing. Predictive analytics is also helping security teams to anticipate potential vulnerabilities and reinforce defenses proactively.
SASE and SSE Frameworks Gaining Ground
The Secure Access Service Edge (SASE) and Security Service Edge (SSE) frameworks are rapidly gaining traction. SASE combines network security functions such as secure web gateways (SWG), cloud access security brokers (CASB), and firewall-as-a-service (FWaaS) with wide-area networking (WAN) capabilities. SSE, a component of SASE, focuses on delivering security services through the cloud. These models offer centralized policy enforcement and visibility, crucial for organizations supporting remote and hybrid workforces.
Cloud-Native Security Tools on the Rise
As organizations build and deploy applications directly in the cloud, the need for cloud-native security is growing. These tools are designed to work seamlessly with cloud platforms like AWS, Azure, and Google Cloud. Examples include cloud workload protection platforms (CWPPs), cloud security posture management (CSPM), and container security solutions. They allow for automated scanning, misconfiguration detection, and policy management in dynamic environments such as containers, microservices, and Kubernetes.
Shift-Left Security Practices Becoming Standard
In response to increasing DevOps adoption, Shift-Left security is emerging as a best practice. This trend involves integrating security earlier in the software development lifecycle (SDLC), ensuring that vulnerabilities are addressed during code development rather than post-deployment. Tools like automated code scanning, infrastructure as code (IaC) analysis, and security-focused CI/CD pipelines are empowering developers to embed security into their workflows without slowing innovation.
Increased Emphasis on Regulatory Compliance and Data Sovereignty
Regulatory requirements are evolving globally, and organizations must ensure compliance with data privacy laws such as GDPR, CCPA, and upcoming regional cloud regulations. There is a growing trend toward data sovereignty, where governments require that data be stored and processed within specific geographic boundaries. This is pushing cloud providers to localize data centers and offer compliance-friendly security configurations tailored to regional laws.
Serverless and Edge Computing Security Gaining Focus
The expansion of serverless architectures and edge computing introduces new security challenges. These technologies reduce infrastructure management but also create ephemeral and distributed attack surfaces. Security solutions are evolving to monitor and protect functions triggered by events in real-time. Serverless security tools focus on identity-based access, runtime protection, and least privilege policies, while edge security emphasizes endpoint hardening, network segmentation, and data encryption at rest and in motion.
Third-Party and Supply Chain Risk Management
Cloud environments often rely on a vast ecosystem of third-party tools and APIs, which can introduce vulnerabilities. There is a growing focus on supply chain security, ensuring that software components and service providers adhere to strong security practices. Enterprises are increasingly conducting security assessments, continuous monitoring, and third-party audits to manage these risks effectively.
Conclusion
The cloud security market is evolving rapidly to keep pace with the complexity and scale of modern cloud infrastructure. Emerging trends such as Zero Trust, AI-driven security, SASE/SSE frameworks, and Shift-Left development practices reflect a broader movement toward adaptive, intelligent, and integrated security models. As cloud adoption accelerates, businesses must stay ahead by embracing these innovations and investing in comprehensive, forward-looking security strategies. The future of cloud security lies in being proactive, predictive, and resilient—ensuring trust, agility, and compliance in an increasingly digital world.
0 notes
Text
Server Automation Market Growth Analysis 2025
Server Automation Market refers to the set of software solutions and tools designed to automate routine, repetitive server-related tasks such as configuration, deployment, patching, monitoring, and maintenance. It eliminates the need for manual intervention in server management, thereby enhancing operational efficiency, reducing human error, ensuring standardization, and improving system reliability. Server automation solutions are critical in large-scale IT environments where rapid scaling, high availability, and secure infrastructure are required.
Get free sample of this report at : https://www.intelmarketresearch.com/download-free-sample/912/Server-Automation-Market
The global server automation market is witnessing robust growth as enterprises increasingly prioritize IT efficiency, scalability, and cost optimization. With the rapid expansion of cloud computing, DevOps adoption, and hybrid IT environments, organizations are turning to automation to manage complex server infrastructures more effectively.driven by the demand for zero-touch provisioning, automated patching, and predictive maintenance. Leading tech giants like Microsoft, IBM, BMC Software, and Red Hat are introducing advanced automation tools that reduce manual errors, enhance compliance, and improve uptime. Moreover, sectors such as banking, retail, and telecom are accelerating automation to support 24/7 digital services and reduce operational overhead in increasingly distributed computing environments.
Market Size
The Global Server Automation Market size was valued at US$ 3.89 billion in 2024 and is projected to reach US$ 8.67 billion by 2030, growing at a CAGR of 14.3% during the forecast period 2024-2030. The United States Server Automation Market alone accounted for US$ 1.23 billion in 2024, expected to hit US$ 2.65 billion by 2030, registering a CAGR of 13.7%.
Market Dynamics (Drivers, Restraints, Opportunities, and Challenges)
Drivers
Rising Demand for Scalable IT Infrastructure
The growing demand for robust and scalable IT infrastructure across industries is one of the main factors propelling the server automation market. The number and intricacy of server environments have increased dramatically as companies step up their digital transformation initiatives, especially in hybrid and multi-cloud configurations. Businesses are investing in automation tools that facilitate load balancing, auto-provisioning, and real-time monitoring in order to effectively manage this scale.For instance, Microsoft’s Azure Automation and Red Hat Ansible Automation Platform enable organizations to streamline repetitive server tasks, improve uptime, and reduce configuration errors.Additionally, Spotify manages thousands of microservices with little manual intervention by using infrastructure-as-code, server automation via HashiCorp Terraform, and internal orchestration tools, which increases agility and deployment speed.
In 2024, Microsoft announced plans to open new data centers in multiple regions, including North America, Europe, and Asia, to support increasing workloads from enterprises adopting hybrid and multi-cloud strategies. This expansion allows customers to easily scale their infrastructure up or down based on fluctuating demand, enabling businesses to optimize costs while maintaining high performance and reliability.
Restraints
High Implementation Costs
The high initial implementation cost is one of the main factors restraining the server automation market's expansion. It is difficult for many businesses, especially small and mid-sized ones, to defend the initial expenditure on automation platforms, specialized integrations, and training. The difficulty of switching from manual to automated server management, which frequently calls for personnel with DevOps or scripting experience, adds to these expenses.
For example, according to a TechTarget report from 2024, 47% of mid-sized companies put off automation projects because they lacked internal resources and had limited budgets. Long-term scaling is challenging since even large businesses have trouble finding and keeping automation experts. Because of this, automation's promise of increased productivity and decreased downtime is frequently postponed or underutilized, especially in industries that still rely on legacy systems.
Opportunities
Growing Opportunities in AI-Driven Automation and Hybrid Cloud Management
The market for server automation is expected to grow significantly due to the growing use of AI and ML technologies to improve automation capabilities. Proactive maintenance is made possible by AI-powered predictive analytics and anomaly detection, which lower operating expenses and downtime. Furthermore, there are opportunities for automation tools that can smoothly coordinate workloads across various infrastructures due to the growing trend towards hybrid and multi-cloud environments.For instance, AI-driven automation,is being integrated by businesses like Google Cloud's Anthos and IBM's Watson AI to enhance server management, optimize resource usage, and quicken deployment cycles. Furthermore, in order to manage distributed servers nearer to data sources, the rise in edge computing necessitates the use of lightweight automation solutions.
In October 2023, Siemens and Microsoft partnered to drive cross-industry AI adoption, unveiling Siemens Industrial Copilot, an AI-powered assistant developed collaboratively to enhance collaboration between humans and machines in the manufacturing sector
Challenges
Complexity of Managing Diverse IT Environments
The complexity of managing various and quickly changing IT environments is one of the main challenges in the server automation market. Businesses increasingly use on-premises, multi-cloud, and hybrid cloud infrastructures, each with its own platforms, configurations, and security needs. Workflow automation in these diverse settings necessitates deep integration and advanced orchestration capabilities, both of which can be challenging to set up and maintain.
For instance, because its microservices architecture was dynamic and spread across several cloud providers, Netflix had trouble automating its infrastructure. Netflix created its own automation tools, such as Spinnaker, to handle continuous delivery pipelines in order to solve this issue; however, in order to guarantee flawless orchestration and lower deployment failure rates, a substantial investment in engineering resources was necessary.
Regional Analysis
North America remains the largest market for server automation, driven by the early adoption of cloud infrastructure, advanced DevOps practices, and the presence of major technology players like Amazon Web Services (AWS), Microsoft, and IBM.The market is expanding as a result of the U.S. government and financial sectors' growing adoption of automation for increased uptime and compliance. Growing digitalization initiatives in Europe, particularly in Germany, the UK, and the Nordics, are encouraging adoption; however, stringent data privacy and compliance laws (such as GDPR) necessitate highly specialized automation solutions.Meanwhile, the Asia-Pacific region is emerging as the fastest-growing market, led by cloud infrastructure expansion and enterprise IT modernization in countries like India, China, and Singapore. For example, in 2024, Tata Consultancy Services (TCS) announced a major investment in AI-based automation platforms for its clients across Southeast Asia, highlighting the region’s rapid move toward scalable infrastructure.
In South America, adoption is gaining traction, particularly in Brazil and Chile, where businesses are modernizing data centers and integrating hybrid cloud platforms. Local tech firms are increasingly leveraging automation to cut costs and improve service uptime—especially in sectors like telecommunications and retail.Meanwhile, Middle East & Africa (MEA) is emerging as a niche but promising market. Countries like the UAE and Saudi Arabia are accelerating their digital transformation agendas under initiatives like Saudi Vision 2030, with increased investment in smart infrastructure and cloud automation. For instance, in 2025, Saudi Aramco partnered with local IT firms to automate its data center operations, highlighting regional momentum despite skills shortages and legacy IT barriers in parts of Africa.
Competitor Analysis (in brief)
Key players in the global Server Automation Market include:
Micro Focus and BMC Software: Long-standing leaders offering comprehensive server management suites.
Broadcom: Known for infrastructure automation.
Red Hat: Popular for open-source automation through Ansible.
IBM and Microsoft: Leverage AI for predictive analytics and cloud integration.
Tencent and Alibaba: Driving innovation in the Asia-Pacific region.
Dell, NetApp: Hardware-integrated automation capabilities.
These companies focus on partnerships, R&D in AI-driven automation, acquisitions, and expanding cloud-native capabilities to maintain market dominance.
May 2025, Salesforce announced plans to acquire data management platform Informatica for approximately $8 billion. This acquisition is intended to bolster Salesforce's capabilities in data management and enhance its AI functionalities, particularly in automating tasks through virtual AI agents.
January 2024, Hitachi Vantara and Cisco introduced the Hitachi EverFlex with Cisco Powered Hybrid Cloud, fusing their knowledge of networking and storage to provide adaptable, pay-per-use solutions for businesses making the switch to consumption-based business models.
January 2024, Synopsys announced that it would pay about $35 billion to acquire Ansys, a well-known provider of engineering simulation software. This calculated action intends to improve solutions in the automotive, aerospace, and industrial sectors by fusing Ansys' simulation capabilities with Synopsys' electronic design automation tools.April 2024, IBM announced the acquisition of HashiCorp, the developer of Terraform, for $6.4 billion, to bolster its cloud and AI automation capabilities.
October 2023, By utilizing generative AI capabilities, Rockwell Automation and Microsoft extended their collaboration, improving industrial automation system productivity and time-to-market.
Global Server Automation Market: Market Segmentation Analysis
This report provides a deep insight into the global Server Automation market, covering all its essential aspects. This ranges from a macro overview of the market to micro details of the market size, competitive landscape, development trend, niche market, key market drivers and challenges, SWOT analysis, value chain analysis, etc.
The analysis helps the reader to shape the competition within the industries and strategies for the competitive environment to enhance the potential profit. Furthermore, it provides a simple framework for evaluating and assessing the position of the business organization. The report structure also focuses on the competitive landscape of the Global Server Automation Market. This report introduces in detail the market share, market performance, product situation, operation situation, etc., of the main players, which helps the readers in the industry to identify the main competitors and deeply understand the competition pattern of the market.
In a word, this report is a must-read for industry players, investors, researchers, consultants, business strategists, and all those who have any kind of stake or are planning to foray into the Server Automation market in any manner.
Market Segmentation (by Type)
Software
Configuration Management
Patch Management
Workflow Automation
Service
Professional Services
Managed Services
Market Segmentation (by Deployment Mode)
On-Premise
Cloud-Based
Market Segmentation (by Organization Size)
Large Enterprises
SMEs
Market Segmentation (by End-User Industry)
IT & Telecom
BFSI
Healthcare
Retail & E-commerce
Manufacturing
Government & Defense
Energy & Utilities
Others
Key Company
Micro Focus
BMC Software
Broadcom
Riverturn
Red Hat
HP
IBM
Bizagi
Microsoft
ServerTribe
Dell
NetApp
Tencent
Alibaba
Geographic Segmentation
North America (USA, Canada, Mexico)
Europe (Germany, UK, France, Russia, Italy, Rest of Europe)
Asia-Pacific (China, Japan, South Korea, India, Southeast Asia, Rest of Asia-Pacific)
South America (Brazil, Argentina, Columbia, Rest of South America)
The Middle East and Africa (Saudi Arabia, UAE, Egypt, Nigeria, South Africa, Rest of MEA)
FAQ :
▶ What is the current market size of the Server Automation Market?
The global Server Automation Market was valued at US$ 3.89 billion in 2024, with projections reaching US$ 8.67 billion by 2030.
▶ Which are the key companies operating in the Server Automation Market?
Key players include Micro Focus, BMC Software, Broadcom, Red Hat, IBM, Microsoft, Tencent, and Dell, among others.
▶ What are the key growth drivers in the Server Automation Market?
Drivers include rising IT infrastructure complexity, increased cloud adoption, operational efficiency goals, and the demand for AI-driven server automation.
▶ Which regions dominate the Server Automation Market?
North America leads the market, followed by Europe and Asia-Pacific, with Asia-Pacific being the fastest-growing region.
▶ What are the emerging trends in the Server Automation Market?
Trends include AI-powered automation, self-healing systems, container-based automation, and hybrid cloud management.
Get free sample of this report at : https://www.intelmarketresearch.com/download-free-sample/912/Server-Automation-Market
0 notes
Text
Forget Generic Training - Cyberinfomines Prepares You Like an Insider

Cyberinfomines delivers real-world, project-driven learning experiences designed to equip you with industry-relevant skills from day one.
Let’s be honest. Most training programs feel like they were made in a rush — for everyone and no one at the same time. You log in, watch a few videos, answer some templated questions, and walk away with a certificate. But when it’s time for an interview or your first job, you’re still staring at the screen thinking, “Wait, I don’t know how to actually do this.”
That’s where Cyberinfomines flips the script.
This isn’t some generic, copy-paste training program. This is insider-level prep designed for real-world success — from Day 1. Whether you’re stepping into tech for the first time or switching gears to something more hands-on and future-proof, Cyberinfomines doesn’t just “train” you.
It transforms you.
The Problem With Traditional Training Let’s start with what no one talks about.
The e-learning world is packed. Platforms are everywhere. Courses are everywhere. Certifications? Don’t even get us started.
But here’s the catch — most of them:
Teach in isolation (no real-world project context)
Skip the “why” behind the “how”
Don’t simulate job environments
Forget to teach you how to think like a pro
So you might know Java syntax, but not how it fits into a real application. Or you might understand Search Engine Optimization (SEO) basics but not how to run a successful campaign under budget pressure.
And let’s be brutally honest — companies don’t hire people just because they’ve “learned.” They hire people who can perform.
Welcome to Cyberinfomines: Where Training Meets Reality At Cyberinfomines, the training isn’t about creating course junkies.
It’s about creating industry insiders.
This means every course — from Java and Full Stack Developer to Digital Marketing and UI/UX Design — is built with actual roles, actual teams, and actual results in mind.
1. You Learn Like You’re Already on the Job The moment you join, you’re not treated like a student. You’re treated like a team member in training.
Your projects, your tasks, your goals — all are mapped to real business environments. For example:
In Java, you build microservices like a product team member.
In Digital Marketing, you create and manage live campaigns using Email Marketing, Content Marketing, Social Media Marketing, and Pay-Per-Click (PPC) Advertising.
In UI/UX, you solve user flow problems for real client cases like Mobile Application Designing and Web Application Designing.
No fluff. No filler. Just real, outcome-based work from Day One.
2. Industry Mentors, Not Just Instructors At Cyberinfomines, every instructor is an industry mentor — not a slide reader.
They teach what can’t be Googled:
Real debugging
Handling stakeholders
Live pressure projects
Web Analytics & Data Analytics
Tech interview mindsets
3. Real Projects. Real Pressure. Real Growth. You’ll work on projects like:
Redesigning Existing Website & Mobile Applications
Building a Website Designing portfolio from scratch
Running an Influencer Marketing campaign
Testing Chatbots & Artificial Intelligence (AI) integrations
These are projects worthy of real resumes, not just certificates.
Please visit our website to know more:-https://cyberinfomines.com/blog-details/forget-generic-training-cyberinfomines-prepares-you-like-an-insider
0 notes
Text
Docker Tutorial for Beginners: Learn Docker Step by Step
What is Docker?
Docker is an open-source platform that enables developers to automate the deployment of applications inside lightweight, portable containers. These containers include everything the application needs to run—code, runtime, system tools, libraries, and settings—so that it can work reliably in any environment.
Before Docker, developers faced the age-old problem: “It works on my machine!” Docker solves this by providing a consistent runtime environment across development, testing, and production.
Why Learn Docker?
Docker is used by organizations of all sizes to simplify software delivery and improve scalability. As more companies shift to microservices, cloud computing, and DevOps practices, Docker has become a must-have skill. Learning Docker helps you:
Package applications quickly and consistently
Deploy apps across different environments with confidence
Reduce system conflicts and configuration issues
Improve collaboration between development and operations teams
Work more effectively with modern cloud platforms like AWS, Azure, and GCP
Who Is This Docker Tutorial For?
This Docker tutorial is designed for absolute beginners. Whether you're a developer, system administrator, QA engineer, or DevOps enthusiast, you’ll find step-by-step instructions to help you:
Understand the basics of Docker
Install Docker on your machine
Create and manage Docker containers
Build custom Docker images
Use Docker commands and best practices
No prior knowledge of containers is required, but basic familiarity with the command line and a programming language (like Python, Java, or Node.js) will be helpful.
What You Will Learn: Step-by-Step Breakdown
1. Introduction to Docker
We start with the fundamentals. You’ll learn:
What Docker is and why it’s useful
The difference between containers and virtual machines
Key Docker components: Docker Engine, Docker Hub, Dockerfile, Docker Compose
2. Installing Docker
Next, we guide you through installing Docker on:
Windows
macOS
Linux
You’ll set up Docker Desktop or Docker CLI and run your first container using the hello-world image.
3. Working with Docker Images and Containers
You’ll explore:
How to pull images from Docker Hub
How to run containers using docker run
Inspecting containers with docker ps, docker inspect, and docker logs
Stopping and removing containers
4. Building Custom Docker Images
You’ll learn how to:
Write a Dockerfile
Use docker build to create a custom image
Add dependencies and environment variables
Optimize Docker images for performance
5. Docker Volumes and Networking
Understand how to:
Use volumes to persist data outside containers
Create custom networks for container communication
Link multiple containers (e.g., a Node.js app with a MongoDB container)
6. Docker Compose (Bonus Section)
Docker Compose lets you define multi-container applications. You’ll learn how to:
Write a docker-compose.yml file
Start multiple services with a single command
Manage application stacks easily
Real-World Examples Included
Throughout the tutorial, we use real-world examples to reinforce each concept. You’ll deploy a simple web application using Docker, connect it to a database, and scale services with Docker Compose.
Example Projects:
Dockerizing a static HTML website
Creating a REST API with Node.js and Express inside a container
Running a MySQL or MongoDB database container
Building a full-stack web app with Docker Compose
Best Practices and Tips
As you progress, you’ll also learn:
Naming conventions for containers and images
How to clean up unused images and containers
Tagging and pushing images to Docker Hub
Security basics when using Docker in production
What’s Next After This Tutorial?
After completing this Docker tutorial, you’ll be well-equipped to:
Use Docker in personal or professional projects
Learn Kubernetes and container orchestration
Apply Docker in CI/CD pipelines
Deploy containers to cloud platforms
Conclusion
Docker is an essential tool in the modern developer's toolbox. By learning Docker step by step in this beginner-friendly tutorial, you’ll gain the skills and confidence to build, deploy, and manage applications efficiently and consistently across different environments.
Whether you’re building simple web apps or complex microservices, Docker provides the flexibility, speed, and scalability needed for success. So dive in, follow along with the hands-on examples, and start your journey to mastering containerization with Docker tpoint-tech!
0 notes