#non-sequential chapter 28
Explore tagged Tumblr posts
Text
Non-Sequential [Ch. 28]
Pairing: Pre-Serum Steve Rogers/Steve Rogers x Reader
One night, Steve Rogers met a beautiful dame named Y/N. He hadn’t intended on letting her get away. But fate had other ideas. Y/N appeared and disappeared in his life so hauntingly that Steve started to wonder if she was an angel meant to watch over him.
Word Count: 2,300
Chapter 27
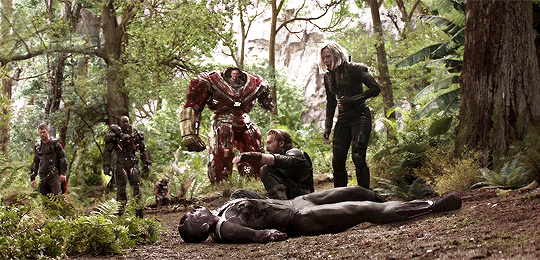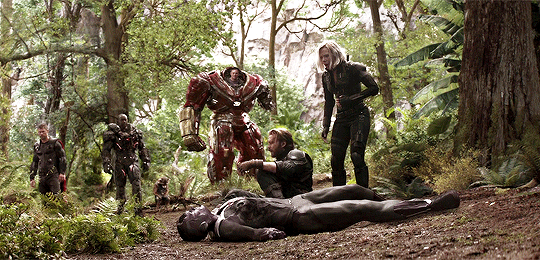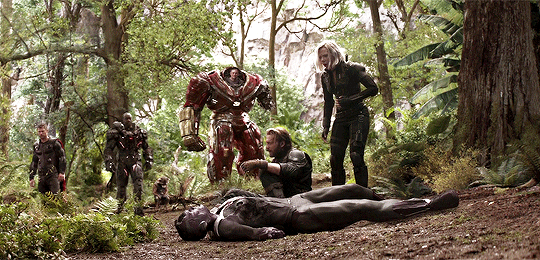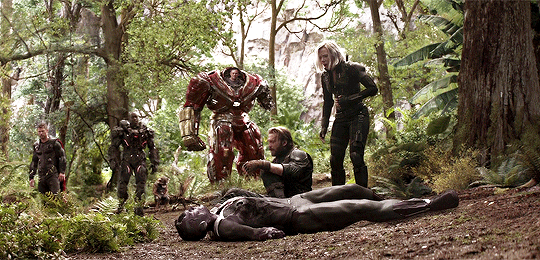
The Battle of Wakanda was simultaneously the shortest and longest day of Steve Rogers’ life.
The dog-like aliens were released in too many droves, making Steve believe they would never stop attacking. Even if Shuri was successful in detaching the stone from Vision, would destroying it even stop these monsters? But Steve didn’t have time to think about that.
Thor’s arrival felt like a blink to Steve. He didn’t have time to process the return of his long-lost friend. The two of them were too busy trying to survive. But Steve somehow seemed to sense the personal ties Thor had in this war.
Steve started to come to on the forest floor. His body quick to recover from being knocked unconscious by Thanos. But it wasn’t fast enough.
He slowly got to his feet and looked up to find Thor pressing his axe into Thanos’ chest. But for some reason, Steve knew it was too soon to celebrate a victory. Something felt off.
“Nooo!” Thor bellowed just before Thanos snapped his fingers.
A flash blinded Steve as he tried to move forward.
When he regained his vision, Thanos fell backwards into a portal and disappeared.
Steve clutched his side as he made his way to Thor. “Where’d he go?”
Thor said nothing, just remained in a daze and breathed heavily.
“Thor?” Steve begged. “Where’d he go?”
“Steve?” Bucky’s voice begged for his attention.
But when Steve looked over, Bucky’s body was already disappearing, turning into ash.
With utter shock, Steve slinked to the pile of ash that once was his best friend.
Him and Thor shared a look, finally understanding what was happening.
Everyone regrouped. Well… not everyone.
Steve went to Visions body, colorless and lifeless. The stone was missing from his forehead, proving what they were already figuring out.
“What is this?” Rhodey asked. “What the hell is happening?”
Steve breathed deeply as it all finally made sense. “Oh, God.”
Then her face flashed in his mind.
“Y/N,” he gasped and jumped to his feet.
“Steve…” Nat called after him, but there was no life in her voice. She just sounded scared.
All the injuries he had meant nothing to him now as he sprinted back to the palace at super-soldier speed. It didn’t matter how much his body hurt and protested. All that mattered was getting to her.
He ignored the panicked looks and the various piles of ash that were scattered across the palace hallways.
He shoved his shoulder against the doors of the wing that protected the royal family and Y/N.
When he entered, the Queen Mother whipped around with tears in her eyes.
Steve’s eyes raced around the room, looking for her. “Y/N!” He yelled.
But when he did not find her or receive an answer, his gaze returned to Ramonda.
She simply shook her head.
“No,” Steve whispered as he shook his head. “No.”
“She’s gone,” Ramonda gasped. “Shuri and her...a-and the rest of them.”
First his best friend and now the love of his life.
Tears filled his eyes.
He left, needing to go to her room. Despite the Queen Mother’s words, Steve’s heart wouldn’t believe her. She couldn’t be gone. It could not be true.
But what he found was an empty bedroom. Clean and barren.
It took a second glance around the room to see the envelope that lay waiting on her nightstand.
Steve didn’t know how it caught his eye when he was having a breakdown.
He saw his name written on it – just Steve. But it was Y/N’s handwriting.
His hand shook as he reached out to pick it up.
He already knew what he was going to find waiting for him inside the envelope.
Y/N knew this was coming. She had seen it. Kept the secret hidden as her own burden to bare. Letting everyone else live in blissful ignorance.
Steve,
By the time you find this, I’m sure you will have figured out what has happened. Thanos was successful. And with his success I have been taken from you.
You have also already realized that I knew this was going to happen. I’ve known for…Well, it doesn’t matter how long I’ve known.
I’m sorry I didn’t warn you. I knew it would destroy you, and maybe it would’ve destroyed us. Is it selfish that I just wanted our time together to be spent without the dread of the future looming over our heads?
I know this is not the goodbye you want or need. But this is all we could have.
Steve, I love you. I love you more than I could ever put into words. You know they aren’t my strong suit. But I hope I made you feel that love.
I know you, Steve. I know you will be OK. You were always stronger than me. You can survive missing me, but I would’ve never survived missing you.
I love you, Steve.
Please don’t forget me.
Steve turned the page over, expecting to find more written.
But that was it.
He wanted more. He needed it. It was a goodbye, but why did he feel like something was missing or that something was off?
The next couple of days were a blur. He hid his feelings. The team needed him. They didn’t need a broken Steve Rogers; they needed Captain America. He wasn’t the only person that lost someone. They all had.
The team decided to return to the compound in New York, regroup and make a plan. Then they discovered Fury’s pager and Carol Danvers explained her relation to it, and Steve allowed himself to feel hope.
But their attack ended in disappointment.
Steve knew in hindsight that it made sense: Y/N wouldn’t have written him a letter saying goodbye if they could bring the world back in a few days.
The solution wasn’t that easy… if there even was a solution.
Now Steve sat on the dock on the lake. The compound’s lights weren’t lit like before – well, everything – making it easier to actually see the stars.
He heard her walking up behind him. But he wasn’t really in the mood for talking. Maybe if he pretended she wasn’t there, she wouldn’t try to engage.
But she’s not one to back down like that.
Nat sat down next to him on the dock, dipping her barefoot into the lake.
“I think I’m going to…get out of here. Thinking about Brooklyn.” Steve spoke first.
“Steve…” She started.
“I can’t stay here, Nat. Everything reminds me of her. The grass on that lawn? Every time I look at it, I think of the night she met me. When I walk into that kitchen, I’m still convinced she’s going to be standing in there waiting for me with a mug of coffee in her hands.”
“So, that’s it? The Avengers are no more?” She challenged.
“We lost, Nat.”
“It was just lost one war, Steve. There will be others. There already are. Carol says–”
But Steve whipped his head to look at her. “We didn’t just lose a war,” he snapped. “I lost everything!” Then he controlled his temper. “She was everything,” he muttered as he looked back onto water.
Nat didn’t say anything more, already knowing when Steve made up his mind, there was no changing it. The only person more stubborn than him was Tony.
“Have you found him yet?” Steve asked her carefully.
She shook her head. “His house arrest bracelet was cut, which can only mean he survived. And there was a call to the compound just minutes after the snap.” Her eyes started watering. “I know he’s out there. But I think Laura and the kids…” She couldn’t even bring herself to say it.
“You shouldn’t stay here,” Steve told her as he looked back at the compound. It was empty and looked lifeless. The agents and scientists that once busied the space were either snapped or had gone back to what family and friends they had left.
Nat ignored his statement.
“Thor’s left. Bruce is acting strange. Tony has clung to Pepper. Rhodey is going back to DC. You shouldn’t be here by yourself, Nat.”
“So, where should I go? To New York City with you?” She challenged.
“Is that such a terrible idea?” He asked.
“I can’t, Steve. I can still help people. I know I can.”
He stood up. “You know…there are other ways to do that than just this.”
———————
Some Time Later…
Steve’s eyes snapped open when he heard the intruder.
His apartment had been restored to keep the character from the time period he was truly from, while being updated enough to be accepted and functional in modern society. But with it came squeaky floorboards and sometimes lack of soundproofing.
But that just meant that there was no mistaking when there was some other presence in his home.
He slipped out of bed completely silent.
Steve didn’t have his shield, but he doubt he would need it to defend himself from a thief.
Crime had skyrocketed since the snap. Turned out that Thanos’ mission didn’t include only ridding the world of bad people. Some took advantage of the world’s vulnerable state, stealing and killing and assaulting others.
But when Steve peaked around the corner, he didn’t find a burglar.
“It’s just me,” she said gently.
Immediately recognizing the voice, Steve rushed around the corner.
Y/N was waiting for him with the blanket from the couch wrapped around her naked body.
Before she even had a chance to say his name or a hello, Steve was pulling her into his arms. The gesture wasn’t uncommon for him, but it still took her by surprise a bit.
“Hi,” she breathed into his shoulder.
He pulled back a bit, “Hi.”
His eyes and body language were now uncertain.
And Y/N knew why: he was trying to figure out what she knew and where she had come from.
“It’s after his snap?” She asked him quietly, proving that she already was aware and he didn’t have to be careful about what he said to her.
He just nodded sadly. “I’ve missed you,” he whispered.
Steve’s situation was simultaneously lucky and heartbreaking. Unlike his friends that survived, he got glimpses of the person he lost. Y/N’s time traveling that once felt like a curse was now a gift to Steve.
He got to hold her, to be reminded of how her skin felt and what she smelled like and how warm or cold her body felt against his.
Y/N leaned forward and pressed a gentle kiss to his lips. She didn’t want to think about when the last time that he felt her lips.
Steve blinks suddenly. “Sorry! Let me get you some clothes.”
Before she could stop him, he rushed back into his bedroom and started shuffling through drawers, determined to find Y/N’s favorite sweatpants and t-shirt of his.
When he looked up with the clothes in his hands, Y/N was leaning against the doorway with an appreciative grin.
She thanked him as she took the clothes from him.
Steve turned his back to give her some space to change, but he couldn’t find it in him to leave the room and truly give her privacy. He was scared she would disappear at any moment and he didn’t want to miss a second of her visit.
He heard Y/N giggle behind him. It sent a chill down his spine.
“It’s nothing you haven’t seen before, Steve. In fact, you see it quite often.”
He slowly turned to find her already dressed. He cleared his throat, “Sorry. It seems I’m not sure how to act around you anymore.”
She walked up to him and cupped his cheek. “You don’t have to be sorry, Steve.”
He nodded.
“You’re looking at me as if I’m a ghost,” she whispered to him.
And in a way, she was.
Her hands then went to his shoulders. He seemed to preen at her touch, so she’d give him as much of it as she possibly could.
“Can I ask you something?” He muttered.
Steve only said things like that when he was nearing a fine line, when he wanted to ask her something about her time traveling. Something that he already knew she wouldn’t want to tell him.
But Y/N nodded.
“When did you find out?”
He didn’t have to elaborate, Y/N knew what he was asking about.
“Not until I was living in Wakanda.” She kept it generic.
Steve seemed somewhat relieved by it. He couldn’t imagine Y/N keeping the secret of the apocalypse for longer that she already had. A couple years was still torture. But Steve had been imagining the worst, often thinking of a teenage Y/N learning of the end of the world, having it haunt her ever moment.
“I’m sorry,” Steve whimpered. “I’m sorry I didn’t save you.”
Y/N him to her. “Oh, Steve. Shh. There was nothing you could do.”
“I’ve lost so many innocent lives. And I used to tell myself that as long as I had you, I could bare that guilt. But once I lost you…”
Y/N shushed him again. “You’re a hero. No one has ever doubted that. But you’re still just a man, Steven Grant Rogers. And Thanos – Thanos was a titan. A titan with the most powerful weapon in the universe. None of you stood a chance.”
Steve nodded, but she knew it would take more than a few words from her to convince him of that.
“I wish you could stay,” he muttered.
She wiped away some of his tears that had escaped. “I wish I could, too.”
He pressed his forehead to hers and closed his eyes.
All the tension left him from just the feeling of her. His body hadn’t relaxed since the last time he’d properly held her in his arms – before the snap, before the Battle of Wakanda.
Nevertheless, when he opened his eyes again, Y/N was already gone. The sweatpants and t-shirt she had been wearing piled at his feet.
It was then that Steve wondered if he really was luckier than everyone. Because having to say goodbye to Y/N over and over and over again now felt like a different type of torture.
Maybe her visits were going to become his drug. In the end, they weren’t good for him. But he still craved them like his life depended on them.
-------------------
Chapter 29
Just want to clarify that I have not “returned” from my hiatus or to this tumblr in general.
Quite frankly this fandom has lost its fucking mind and I’m rather disgusted with the behavior I’ve seen in the past month or so.
No wonder all of the talented writers have left.
I’m only finishing this stupid series to clear my conscious. But I regretted looking back to see that while +2,500 people follow this series’ masterlist, the past few chapters have received 300 or less notes. And that, I tell you, is one of the reasons I hate it here.
#non-sequential#non-sequential series#non-sequential chapter 28#steve rogers series#steve rogers fic#steve rogers x reader#steve rogers x you#captain america series#steve rogers reader insert#captain america reader insert#captain america x reader#captain america x you#invisibleanonymousmonsters#invisible anonymous monster#steve rogers angst#steve rogers fluff
405 notes
·
View notes
Text
Revelation, Coronavirus, and the Mark of the Beast: How Should Christians Read the Bible’s Most Fascinating Book? Part 1

Kevin DeYoung
Whenever there is a cataclysmic global crisis—be it war, rumors of war, or a novel coronavirus—we see a sharp uptick of interest in the book of Revelation. While paying attention to the Bible is always a good thing, Revelation is too often used (by Christians and non-Christians) in a way that does less to edify the body of Christ and more to stoke the fires of wild speculation and unfounded conspiracy theories.
It may be helpful, then, to understand what kind of book Revelation is and how to make sense of imagery like the mark of the beast. We’ll get to the mark of the beast in the third and final installment of this short series. But before we get there I want to take a couple posts to look at what Revelation is all about and how we should interpret this not-as-strange-as-it-seems book.
Big Picture
Probably no book of the Bible has been harder for Christians to understand and, as a result, produced more bizarre theology than the book of Revelation. Although it is called “revelation,” it has been anything but a revelation for many Christians. It is a closed book for many of us, not correcting, not teaching, not rebuking, not training in righteousness like all Scripture should.
I remember teaching through part of Revelation for a Sunday school class several years ago and telling my mom about it over the phone. She said something like, “Kevin, you’re not going act like you have everything figured out are you? John Calvin didn’t even write a commentary on Revelation. You don’t know more than John Calvin, do you?” It is true that Calvin did not write a commentary on Revelation (one of the few books he didn’t write on), and it’s true that I don’t have everything figured out. But most of Revelation can be understood and applied if we will take the time to study it.
In fact, the entire book of Revelation can be summed up in one word: nike. Nike is the Greek word for victory. It occurs one time in the New Testament—1 John 5:4 states, “This is the victory that has overcome the world, even our faith.” Another form of the word (nikos) appears four other times, three times in 1 Corinthians 15 (e.g., “Death has been swallowed up in victory;” “He gives us the victory through our Lord Jesus Christ”). The verb form, nikao (meaning to conquer, to overcome, to triumph), occurs more frequently—28 times. Seventeen of those occurrences, more than in the rest of the New Testament combined, are in Revelation.
Revelation is the story of the Devil trying to conquer the church, but the church overcomes the Devil and the world because she belongs to the Lord who has won for us the victory (Rev. 5:5; 17:14). The book of Revelation gives instruction for the believer on how to conquer instead of being conquered, how to triumph instead of being trampled, and how to be an overcomer instead of a succumber. That’s why each of the seven letters to the seven churches concludes with “to the one who conquers . . .” If we cave and give in to persecution and give into worldliness and give into the Devil’s temptations, we will lose. But if we overcome through trial and suffering and seeming irrelevance, we will win (Rev. 21:6-7). That’s where history is heading, and that’s the big idea of Revelation.
(Possible) Map for the (Seeming) Madness
There is no one inspired way to understand the structure of Revelation. When studying this book in-depth several years ago, I found 11 different outlines, which suggests there probably isn’t one obvious structure we’re supposed to see.
One simple approach is to see Revelation as divided into two main sections. Chapters 1-11 introduce the story of God’s triumph, and chapters 12-22 explain the story in greater detail, this time unveiling in more depth the role of evil through the beast, the false prophet, and the whore of Babylon.
Another way of approaching the book is to divide it into four main sections, each marked off by the phrase “what must soon take place” or “what must take place after this.”
Rev. 1:1 The revelation of Jesus Christ, which God gave him to show his servants the things that must soon take place.
Rev. 1:19 Write therefore the things that you have seen, those that are and those that are to take place after this.
Rev. 4:1 “Come up here, and I will show you what must take place after this.”
Rev. 22:6 “And the Lord, the God of the spirits of the prophets, has sent his angel to show his servants what must soon take place.”
The language in these four passages comes from Daniel 2 and indicates that Old Testament prophecy is already and not yet completed in Revelation.
There’s another way to outline the book into four main sections. This approach marks out the times John says he was caught up in the Spirit.
Rev. 1:10 I was in the Spirit on the Lord’s Day, and I heard behind me a loud voice like a trumpet.
Rev. 4:2 At once I was in the Spirit, and behold, a throne stood in heaven, with one seated on the throne.
Rev. 17:3 And he carried me away in the Spirit into a wilderness.
Rev. 21:10 And he carried me away in the Spirit to a great, high mountain, and showed me the holy city Jerusalem coming down out of heaven from God.
By this reckoning, Revelation consists of four main visions that John saw while he was in the Spirit on four different occasions.
Yet one more way of approaching the book—and the approaches are not mutually exclusive—is to look for sets of sevens. Everyone recognizes that seven is a crucial number in Revelation, and that there are at least four sets of sevens: seven letters, seven seals, seven trumpets, and seven bowls. This much everyone agrees on. But from here things get less clear. Since there are plainly at least four sets of sevens, many scholars have wondered if we are meant to see seven sets of sevens. I am convinced there are seven sets of sevens, but I certainly wouldn’t be dogmatic about it. My outline, which is similar to outlines I’ve seen from others, looks like this:
Prologue: 1:1-8 I. Seven letters: 1:9-3:22 II. Seven seals: 4:1-8:5 III. Seven trumpets: 8:6-11:19 IV. Seven visions: 12:1-15:4 V. Seven bowls: 15:5-16:21 VI. Seven judgments: 17:1-19:10 VII. Seven last things: 19:11-21:8 VIII. The beautiful bride: 21:9-22:21
You’ll notice there is an eighth section that is not a set of seven. An eighth section makes sense because eight is often the number of new creation in the Bible (Jesus rose on the eighth day/first day of a new week, eight people started the new humanity after the flood, sons were to be circumcised on the eighth day), and this eighth section is about the new heavens and new earth. But there is nothing inspired about the outline above. It’s just one way of making the book more manageable and putting together some possible patterns with some obvious ones.
Our Interpretive Lens
The last thing I want to do in this post is look at the various ways Christians have understood Revelation. There are four main schools of thought.
The first school of interpretation is called preterism. The preterist approach teaches that a large portion of the book of Revelation was fulfilled in the first century, specifically in the destruction of the temple in AD 70. Further, most of the prophecies in Revelation were fulfilled by the fall of the Roman Empire in the fifth century.
The strength of the preterist school is that it puts Revelation in its original context. Revelation was written to first-century Christians with first-century metaphors and imagery and referents. If we jump to the 21st century and ask, “What does this mean for me?,” we will almost surely get the wrong answer. We have to first ask, “What did this mean to them, to John’s original audience?”
Preterism is not without weaknesses. First, some preterists try to find a single, specific fulfillment to the prophecies of Revelation when it seems more likely that John’s visions often portray generalized spiritual battles and struggles that occur throughout the ages. Second, full-blown preterists argue that all of the end-time events, like the second coming and the last judgment, actually were fulfilled by AD 70. This does not seem in keeping with the cataclysmic language used at the end of each sequence.
The second school of interpretation is called historicism. The historicist reads Revelation as a straightforward, sequential roadmap of history. Revelation is seen as predicting any number of key historical figures and events from Napoleon to Hitler to the European Union to the United Nations.
The strength of historicism is that it makes Revelation relevant for all Christians. It focuses our attention not on the fall of the temple or on the Roman Empire but on the way of the church in the world.
But besides this strong point, historicism is the worst way to try to understand Revelation. It is full of weaknesses. Let me quickly mention just four.
First, historicism is often anachronistic and takes Revelation out of its original context. I am thinking of those who argued that the country out of the north (from Daniel, not Revelation) must be Russia, or that the locust swarm from Revelation 9 is foretelling a helicopter battalion. These sorts of interpretations completely ignore the imagery of ancient prophecy and the context of the first century.
Second, historicism, with its end-of-the-world predictions and identifications of the beast, has often been demonstrably wrong. During the cold war, people saw Russia in Revelation. A decade ago they saw Iraq. Now they see the coronavirus. In a few years, they will be on to something else. Historicists tend to see Revelation being fulfilled in whatever crisis is pertinent for the day. And then on another day, another group of historicists see that view was wrong and find something completely different.
Third, historicism limits the prophecies of Revelation to one exclusive location or personality instead of allowing that the imagery of Revelation may be well suited to an inclusive number of different figures and times. That is, I think historicists are right to see Revelation unfolding in history, but they are wrong to think that Revelation is uniquely unfolding in one historical moment.
Fourth, historicism is irreducibly subjective. There is simply no objective standard of interpretation. Who’s to say that Hitler was more the beast than Stalin? Or that 666 is a reference to Bill Clinton (as one website I found argues)? Or, as another article maintains, that Ronald Wilson Reagan (six letters in each of his names!) was the beast? It’s all hopelessly subjective. The text ends up saying anything we want it to.
The third school of interpretation is futurism. The futurist reads Revelation (chs. 4-22) as a prophecy solely concerned with the distant future. The events depicted refer to the time involving, or immediately preceding, the end of history. Dispensationalists are futurists (though not all futurists are dispensationalists).
The strength of futurism is that it emphasizes how Revelation speaks to the future, not just about the past. Futurism is right to see that some things in Revelation deal with the final consummation of human history. Futurists are also right to see that the future is moving somewhere, toward the triumph of the Lamb.
But futurism also has weaknesses.
First, if Revelation 4-22 is entirely and only about the distant future, then most of Revelation was barely relevant to its original readers. Sure, it would have helped them see the end of the world, but it really spoke little into their immediate context (when John says Revelation revealed “what must soon take place”).
Second, futurism often assumes a strict sequential chronology. And yet, we cannot assume that what is shown to us in chapter 12 comes in time after what we see in chapter 6. To the contrary, one of the keys to interpreting Revelation is to understand that its visions are recapitulated. So, Revelation gives us a sweep through history in the seven seals, and then does the sweep again in the seven bowls. Revelation comprises overlapping prophecies that go back and forth between the present and the future and are not strictly chronological.
Don’t think of the visions of Revelation as frames from a movie reel running through the light one after the other. Think of the visions as portraits in a gallery. You look at one portrait and get a glimpse of reality, and then you look at the next portrait, and then you walk over to the next room and look at the portraits over there. They are pictures telling the same story and pointing to the same reality, but they aren’t sequential clips from a movie.
The fourth school of interpretation is idealism. The idealist reads Revelation as a symbolic conflict between the forces of good and evil. Revelation, idealists argue, does not point to particular historical figures but depicts the timeless struggle between God and Satan. It interprets Revelation as a series of repeated symbolic pictures, focusing on the church’s triumphant struggle from the first century until the last judgment and the eternal state.
The strength of idealism is that is understands the symbolic nature of Revelation. It realizes that Revelation’s imagery is rooted first in Old Testament language and second in the known world of the first century. The other strength is that it sees behind the first-century context deeper spiritual realities that would outlive and transcend ancient Rome and remain relevant for believers throughout the ages.
The weakness of idealism is that it can at times under-emphasize the fact that all of history is moving somewhere. That is, idealism sometimes sounds vague, as if there were no end point in history as we know it, as if Revelation was just about the struggle between good and evil and not also about the ultimate triumph of Jesus Christ.
Interpret the Book
So what approach do I think helps us best understand Revelation? I think each approach offers something needed. This doesn’t mean that I think every approach is good or that one is not better than another (I’m basically an idealist with a partial preterist bent). But each school of interpretation does offer something important.
With the preterist, we must read Revelation in its immediate context.
With the idealist, we must look at Revelation as a symbolic portrayal of God’s work, most of which can be applied to any historical time.
With the futurist, we must read Revelation with end of history in mind, recognizing that the book depicts, in parts, the second coming, the final judgment, and the eternal state.
And with the historicist, we must understand that the prophecies of Revelation, though they are not limited to one particular occurrence, are fulfilled in time and space.
The best way to defend one’s interpretive grid is to actually interpret the book. But since this is a three-part blog series and not a 50-part sermon series, we will have to settle for just one more post on the subject. In the first three verses, John makes clear that this book is an apocalypse, a prophecy, and a letter. Once we know what each of the terms entail, we will be better equipped to understand the book as a whole and specific imagery like the mark of the beast.
Note: This post was first published through The Gospel Coalition website.
1 note
·
View note
Text

Sorry. We’re more than halfway in and I still can’t get into Doomsday Clock. There were moments in this issue when I felt things were getting interesting, ideas finally being developed to the point where there’s a better sense of what is going on, but it is all undermined- for me- by regular descents into what is little more than pastiche.
The opening sequence indicates that Doctor Manhattan has been messing around with events in DC continuity- although it’s not clear how this has any relevance to all the Crises and Rebirths and so on, it at least indicates that a framework is developing with regards to what has been going on with DCU continuity, and where the Watchmen might fit into this, and the hints are at least somewhat intriguing. But the sequence is told in a terribly familiar way for anyone that has read Alan Moore and Dave Gibbons’s original maxi-series. We already know that Manhattan has a different perspective on time, and we really don’t need to have this reaffirmed by simply mimicking the narrative style of Watchmen 4:
Page 1, Panel 3:
“The photograph is in my hand.
I found it in a derelict bar at the Gila Flats test base, twenty-seven hours ago.”
Panel 4:
“It’s still there, twenty-seven hours into the past, in its frame, in the darkened bar.
I’m still there looking at it.”
Panel 5:
“The photograph is in my hand. The woman takes a piece of popcorn between thumb and forefinger. The Ferris wheel pauses.
Seven seconds now.”
Panel 6:
“It’s October 1985. I’m on Mars. It’s July 1959. I’m in New Jersey, at the Palisades Amusement Park.
Four seconds. Three.”
This continues for much of that comic’s 28 pages, the non-linear view of time being used to piece together both Jon’s origin (and disconnect from humanity) and elements of the mystery at the centre of Moore’s narrative. Crucially, it also emphasises how it is always going to be too late, once the genie has been let out of the bottle:
Page 28, panel 4:
“I am standing on a fire escape in 1945, reaching out to stop my father, take the cogs and flywheels from him, piece them all together again...
But it’s too late, always has been, always will be too late.”
The closing quote from Einstein underlines this notion that hindsight is meaningless:
“The release of atom power has changed everything except our way of thinking... The solution to this problem lies in the heart of mankind. If only I had known, I should have become a watchmaker.”
In Doomsday Clock, this style really only serves to echo Moore, with no real purpose beyond mimicry, as though the sole underlying reason is that this is Manhattan’s narrative voice. The narrative voice of Rorschach had been similarly mirrored in previous issues, which seemed equally unnecessary but at least understandable to some extent as perhaps a character seeking to fill Rorschach’s shoes might also steal his voice if he felt that helped him to assume the vigilante’s persona.
But to expect Manhattan to always narrate in the exact same style of temporal drift seems implausible, and he just seems to be echoing himself for no reason. It seems particularly inappropriate when these are not events taking place sequentially but viewed simultaneously, as was the case in Watchmen: the whole point of that chapter was that, for Jon, cause and effect were rendered meaningless. He could see the effect and the cause at the same time; one did not lead to or from the other, they both simply were to him, and so he drifted away from humanity. Everything had happened, was happening, will happen, and he let it, because he had seen it, was seeing it, will see it. It “always will be too late” to change things, to impact the course of events, which leads to a deadening of emotion- there is no surprise or shock anymore.
Narrating events that are changing from panel to panel (Alan finds the ring, Alan doesn’t find the ring etc.) is a completely different viewpoint, and it is hard to believe Manhattan wouldn’t be aware of this (especially if he is responsible, as is suggested). Perhaps the whole point is to indicate he is not fully aware and still thinks of himself as that passive observer, but his omniscience seems otherwise intact, which would make that rather implausible, so the overall impression is that the narration is simply an echo of the source.
Considering the two narrative voices of Rorschach and Doctor Manhattan together, it feels that mimicry is the only real way the series knows how reference the original work- it certainly seems to miss any of the depth of thought and symbolism that Moore was aiming for.
This sense of mimicry is only made more obvious when it is revealed that Adrian is once more manipulating events for his own ends. It seems that because that was his role in Watchmen, it should be replayed here as well, in the same way that he recreates Bubastis so that he still has his beloved pet in this reality. In effect, nothing has changed- Rorschach is dead, but replaced by Rorschach. Bubastis is dead, replaced by Bubastis (with some of Jon’s DNA). Doctor Manhattan is revisiting 30+ year old narrative tropes and Ozymandias is still manipulating the plot at the expense of everyone else.
It could be that this mimicry is a plot device in the end, symbolising the restructuring of reality with characters being redeployed in similar but different roles- what is the DCU’s history of reset upon reset if not a simple reordering of what came before, after all?- but this appears unlikely. If nothing else, that seems too much of a long game to play on a title that is supposed to be a flagship series that only appears every couple of months- DC does not tend to favour meta-narratives in such titles (unless Grant Morrison has managed to persuade someone in editorial to let him loose on a title)- and Johns’s previous work has always suggested faithfulness to what has been before, with a drive to reinstate classic characters, rather than make significant changes to them. As such, the mimicry of Moore’s voices seems more likely to be intended as homage than subversion. Given that Watchmen was in part a homage to the Charlton heroes, and Moore is far from averse to making use of existing genres and styles in order to interrogate, or honour, them, Doomsday Clock’s homage is a step too far- it risks becoming an echo of an echo, hard to make out or understand.
From Doomsday Clock 7, by Geoff Johns, Gary Frank, Brad Anderson & Rob Leigh
3 notes
·
View notes
Text
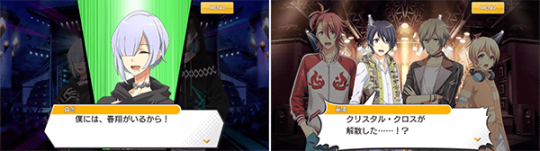
[Event & Scenario] “Episode of Avalon #1.5 Shattered Twin Crystals” START
Chapter 2 of Season 1.5! Fairy April is focusing on producing new songs after joining Avalon. Suddenly, there's some news about Crystal Cross and Judas Kiss...? Join Fairy April and save Crystal Cross from this crisis!
Details
▼ Release Date: 2018/01/15 (Mon) 17:00JST ~ onwards
Part 1.5 of the “Episode of Avalon #1.5 Shattered Twin Crystals” will start! Chapter 2 will focus on Fairy April.
▼ Access Condition
Must clear the final chapter in “Episode of Avalon #1.5 Voyager of the New World.”
How To Participate
You can access Part 1.5 from the banner on the home screen as long as the condition of clearing the final chapter in “Episode of Avalon #1.5 Voyager of the New World” has been satisfied.
※ Although there is no deadline, you may only receive the Clear Reward once.

How To Play

Get “Crystals” by playing songs from different Areas listed in the Event Page. Choose the Area you want to play in and either clear the story and/or win the Duel Gig of each stage to proceed to the next stage.

You can exchange the “Crystals” for the limited edition reward card via the Shop’s “Item Exchange” section. [more info.]
You can access the event scenarios via the new section, “Episode Of Avalon” from the Stories Tab.
Event Stage Schedule
The Area Stages for “Episode of Avalon #1.5 Shattered Twin Crystals” will be released sequentially from 2017/12/30(Sat) 00:00 JST. The new stages will be released at a schedule:
01/15(Mon) 17:00~・Shattered Crystal 01/17(Wed) 00:00~・Reason 01/19(Fri) 00:00~・Brothers 01/21(Sun) 00:00~・Regret 01/23(Tue) 00:00~・Lost Dream 01/25(Thu) 00:00~・Before the Storm 01/27(Sat) 00:00~・Truth 01/29(Mon) 00:00~・Epilogue
Past Event Scenario Limited Time Rerun
Scenarios of the events leading up to the scenario for Part 1.5 will have a re-run for a limited time only. Unopened scenarios will be available for reading during the following period:
▼ Duration: 2018/01/15 (Mon) 17:00 JST ~ 2018/01/30 (Mon) 12:59 JST
※ You can access the event scenarios from the “Story” tab → “Event Scenario” but will not be able to receive any reward upon clearing.
The target Event Scenario are as follows:
Advent of the Quattro Virtuoso GIGS ー Dante of the Purgatory
Anniversary GIGS ー Dreamin’ (untranslated)
On Board The Merry Christmas GIGS ー Dante is Coming To Town!

Event Reward Card
SR: Misato Toudou [The State of Loneliness]

Event Strategy
Using Fairy April members’ cards in Bands to use for LIVEs will improve overall performance.

“Shattered Twin Crystals” Limited Rare Gacha (Daily Rotation)

Duration: 2018/01/15(Mon) 17:00JST ~ 2018/01/31(Wed) 12:59JST
Line-up: EXR Yuu, EXR Show, SR Makoto Kurusu, SR Yukiho
※ SR Kurusu Makoto and SR Yukiho will be available throughout the duration of the gacha.
→ See here to read more on EXR Rarity
The gacha can use both Free and Paid Medals
It is possible to pull regular cards other than the Event limited gacha cards.
At least 1 SR or above card is guaranteed for every 10-pull
Signed cards will be discharged at a certain probability. Signs will only appear for SR cards and above and will be treated the same as non-signed, having the same stat and effects. You can admire the sign in various places.
Event limited cards might reappear during future events/campaigns.
“Shattered Twin Crystals”Rare Gacha Schedule
YUU ・1/15, 1/17, 1/19, 1/21, 1/23, 1/25, 1/27, 1/29, 1/31 SHOW ・1/16, 1/18, 1/20, 1/22, 1/24, 1/26, 1/28, 1/30
※ Please take note that the pick-up date will change at a daily basis
Featured New Cards
SSR Yuu [Create A World] Leader Skill: [Cross Drive α] Boosting all Member’s BEAT by 45% and LIFE by 15%. Additional 10% COMBO BONUS if a Show card is in the band. Main Skill: [A Ship About To Set Sail] 50% chance of activation upon 50 successful taps, increasing score by 5% for each BEAT card included in the band for 6 seconds.
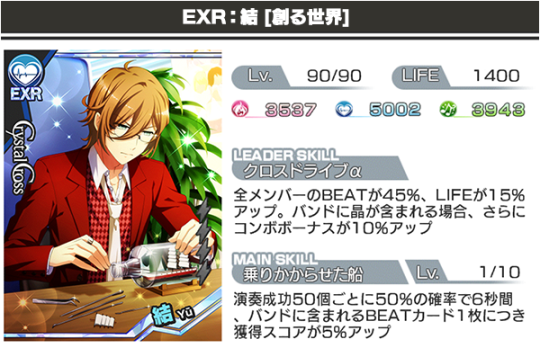

“Forever You” Vocals: Tsubasa Yonaga (Yuu) Lyrics, Composition, Arrangement: Eiji Kawai

SSR Show [One Step Forward] Leader Skill: [Cross Drive Ω] Boosting COMBO BONUS by 45% and All member’s LIFE by 15%. Boosting all member’s BEAT by 20% if a Yuu card is in the band. Main Skill: [Wavering Heart] 50% chance of activation upon 50 successful taps, increasing score by 5% for each BEAT card included in the band for 6 seconds.
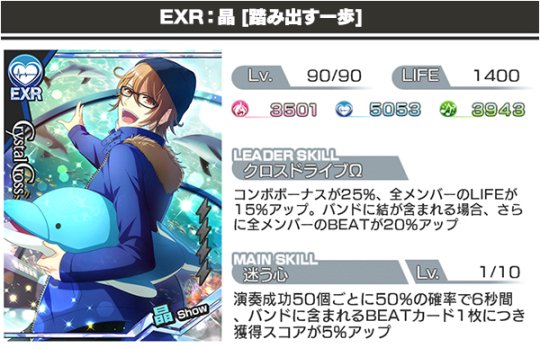

“Forever You” Vocals: Ayumu Murase (Show) Lyrics: Masamichi Nagai Composition, Arrangement: Kazuya Nishioka

SR Makoto Kurusu [Winter Gust] Leader Skill: [BEAT UP] All Member’s BEAT boosted by 30% Main Skill: [A Certain Winter’s Incident] 20% chance of activation upon 15 successful taps, boosting combo bonus by 16% for 4 seconds.

SR Yukiho [Snowflakes] Leader Skill: [ALL UP] All Member’s GROOVE/BEAT/MELODY boosted by 25% Main Skill: [救愛救愛Classics*] 20% chance of activation upon 15 successful taps, boosting combo bonus by 16% for 4 seconds.

※ Cards from this gacha are will have a max level of 90 for SSR and 75 for SR once Break.
You can check the in-game gacha/event page for more info.
*Yukiho’s card skill shall be amended as soon as I figure out what it means (rofl) If you have ideas, throw them at me.
#event : news#event : guide#band yarouze#band yarouze!#banyaro#Episode of Avalon 1.5 Shattered Twin Crystals#admin : pk5u
13 notes
·
View notes
Text
30 Lessons Drawn from the Miracles of Jesus - #7
#7. God is never early or late. He is always right on time. - God’s Modus Operandi

Photo by Djim Loic on Unsplash Action item: Please read the story in each section (or at least, be familiar with it), before you read the discussion under it. First of all, no one can claim to have a complete understanding of God's mode of operation. Having said that, this miracle lesson will only seek to provide some insight into God’s MO. And, hopefully, after you’re done reading, you will begin to understand why some of your prayers seem like they have not been answered. Our topic of discussion has it that God is never early or late. Now, let us define the terms, ‘early’ and ‘late,’ in the context implied here. Let me define what I mean by 'early' and 'late.' When something is done early, it is done before the time it should have been done. And when something is done late, it is done after the time it should have been done. God does not operate that way. You see, God does not keep or measure time the way we do. He will not arrive to your aid earlier or later than He intended to. The Bible tells us that with God, one day equals one thousand years, and one thousand years equals one day (2 Peter 3:8). Confusing, huh? That simply drives home the point: God's way of time measurement is not linear (that is, progressing from one stage to another), but rather non-sequential (that is, not following an obvious sequence). No one can claim to have a complete understanding of God's mode of operation; He is God, after all. However, there are numerous examples from Scripture designed by God to give us some insight into this very knowledge. And today's miracle lesson will focus on those miracles of Jesus from which we can glean this vital life lesson. The Healing of Jairus' Daughter (Mark 5:21-43) Here, we have Jesus knowing fully well that by the time He got to Jairus' house, his daughter would have died, still He took His time in the crowd, looking around, searching for the one woman whose condition was past a life-threatening stage. I mean, this woman was already healed, so she was far from being in danger of dying. Jesus couldn't find her, yet He was unwilling to continue on His journey until the woman came forward, frightened and trembling (Mark 5:32-33). He took His time to minister to this one, poor, lonely soul; never in a hurry to win one more soul over to the Kingdom. Her physical affliction was over, but her spiritual condition needed a revival. He spoke kindly to her, not like her physicians used to, but like she remembered her father used to (Mark 5:34). All this He took His time doing, knowing that the messenger who had been dispatched from the synagogue ruler's house with the sad news was already in the throng, trying to make his way to his master. Or, perhaps the messenger had arrived even before the incident with the woman, and was among those who denied touching Him (Luke 8:45). He was probably wrapped up in fascination at the way Jesus spoke tenderly to the woman, and briefly entertained the thought of becoming a student of Jesus, for he referred to Jesus as 'Teacher,' and not, 'Master,' or 'Lord' (Mark 5:35; Luke 8:49). Anyway, that was just a side dish, let's continue on to the main course. 😋 Don't get this wrong, it wasn't that Jesus was so cruel and insensitive as to allow the family of Jairus to first go through the pain of losing a daughter and a sister, just so He could show off His power over death. Nah! Rather, Jesus had a more pressing need of having a personal encounter with a lost soul. Here, we see how God prioritizes having a personal encounter/relationship with Him over receiving healing from Him. The woman had been healed even without meeting Jesus on a personal level. But Jesus knew that she needed something even more important than the healing she sought - a personal introduction to His gentle and Fatherly personality, and a hope of a new relationship with Him. Note that He told her to go, but there are a few places in Scripture which suggest that Jesus might have only been testing to see whether she would go or stay and become His disciple (Matthew 19:21-22; Luke 24:28-29). The interruption from Jairus' messenger probably caught the fancy of the writers of the Gospels that they did not specifically tell us what became of that woman in particular. Or, Luke probably did not bother including it in his Gospel account, since he had already earlier mentioned, in the beginning of the chapter, that among the women who followed Jesus were those whom He had cured of evil spirits and diseases (Luke 8:1-2). You see, as sons and daughters of the Most High, we must endeavour to be led by the Spirit of God at all times. We must always bear in mind that God is never early or late. He leads us to do things at the right timing, according to His time, and not what we perceive the right time should be. Had Jesus hurried past the woman with the issue of blood, and not stopped to attend to her so that others could hear about her sufferings at the hands of physicians, and minister to her, He would have lost an important opportunity in God's timeline. The woman would have been healed, but been too afraid to testify to how her healing came about so that others in a similar condition could hear or read about it across all ages and times, and be encouraged to have faith in God. God already approved the resurrection of Jairus' daughter, regardless of how fast or how long it took Jesus to get there. If Jesus had by-passed the woman, he would have reached Jairus' house early enough to heal his daughter, but would have missed the better miracle - raising her from the dead; one which drew more followers to God. When we are in tandem with the Holy Ghost, having Him in front and full view of us at all times, then we will never have a late or early miracle, which can be disastrous, either way. The Raising of Lazarus from the Dead (John 11:1-45) Here is another account where it seemed at first that the Lord Jesus had arrived late. Martha and Mary, the sisters of Lazarus, had first sent a message to Jesus to come to his aid while he was still alive but deathly sick - John 11:3. It appeared as though Jesus stalled (John 11:6); however, He was waiting to be led by the Spirit of God to go. It must have been the same Spirit who revealed to Him that Lazarus was dead, as no further news was sent to Him by Lazarus' sisters, yet He knew that Lazarus was gone - John 11:14. When Jesus arrived, Martha and Mary reacted the natural way for humans to react when all hope is lost; they thought that He was late - too late. Each of them said to Jesus, "Lord, if only You had been here, my brother would not have died." These were people who strongly believed in the power of God to heal through Christ. They were what we would consider staunch Christians are today - trusting completely, hoping continually, yielding unreservedly. Martha even said, "But even now I know that God will give You whatever You ask Him.” She was hoping that Jesus would ask the Father to grant her brother, Lazarus, "resurrection at the last day" (John 11:24). She did not expect what happened next - John 11:43-44 . We must endeavour to throw our all into this "faith thing," withholding nothing, trusting completely, hoping continually, yielding unreservedly. We may not know the perfect will of God concerning every single circumstance we encounter in life., still, one thing we must not do is stop praying for healing whenever we or our loved ones fall sick. It may be the will of God at that moment to call us (or them) home, yet, that is not for us to decide or try to determine. When Jesus' disciples once asked Him something regarding God's timing, He responded by saying, “You don’t get to know the time. Timing is the Father’s business. What you’ll get is the Holy Spirit. And when the Holy Spirit comes on you, you will be able to be my witnesses in Jerusalem, all over Judea and Samaria, even to the ends of the world” - Acts 1:7-8. When we become completely yielded to the Holy Spirit, by the things we do and by our devotion to Him, we would be amazed the great good and witnessing He can accomplish through our healing, death, or even physical resurrection of us or our loved ones. In the end, let us be able to say like Jesus, "Father, I thank You that You have heard Me" (John 11:41); like Job, "Though he slay me, yet will I trust in him: I will maintain my own ways before Him" (JOB 13:15, KJV); like Jeremiah, "It is good that one should both hope and quietly wait for the salvation (deliverance) of the LORD" (Lamentations 3:26). May the peace of God, which surpasses human understanding, keep our hearts and minds until the Day of our Lord Jesus Christ. Amen! Do you hear God speaking to you today through this lesson? Please, leave a comment or question; your comment/question might be a blessing to someone. You could also contact us through our contact page. Go to lessons: Intro #1 #2 #3 #4 #5 #6 Read the full article
0 notes
Text
Five Cannabis Stocks for the Win (CURLF, GTBIF, TCNNF, SGMD, CRLBF)
It’s not a mystery where to find strong growth. As the bull market rages on, driven by extreme monetary and fiscal policy support amid historic challenges, the only way for investors to truly lose the game is to not play. Just about anything else has been working. But the chapter ahead will likely take a bit more nuance. The division between the pandemic plays and the rest of the market is obvious. And money managers diversifying between the two are doing well. But it’s not easy to find opportunities that have a viable long-term growth thesis but are still trading at a strong value relative to the market. One area that could become of increasing interest is in the cannabis space, where the long-term growth outlook is tremendous, but flows have yet to surge into the space. Most cannabis plays are still trading at 1-2x sales despite forward topline growth forecasts above 20% over the coming four quarters. That’s a disposition that is increasingly rare. With that in mind, we take a look at five cannabis plays that are actively traded and continue to post strong performance data while making significant investments at a strong ROI, including: Curaleaf Holdings Inc (OTCMKTS:CURLF), Green Thumb Industries Inc (OTCMKTS:GTBIF), Trulieve Cannabis Corp (OTCMKTS:TCNNF), Sugarmade Inc (OTCMKTS:SGMD), and Cresco Labs Inc (OTCMKTS:CRLBF) Curaleaf Holdings Inc (OTCMKTS:CURLF) recently announced the launch of Curaleaf Sublingual Tablets in Florida. These cube-shaped, berry-flavored bites will provide the state's medical patients with a discreet, sugar-free yet fruity alternative form of medication. According to the release, Curaleaf's new Sublingual Tablets, which will be in 30-piece jars, contain 5mg of high-quality cannabis oil per piece, which allows patients to manage their treatment plan with confidence and ease. Each bite, which is made to be ingested orally or sublingually, is translucent in color and features a refreshing "Arctic Berry" flavor. The new product will be sold at all of the Company's 28 operating dispensaries in Florida with a phased roll-out between August 8th - August 20th. Limited quantities will be released to pre-existing loyalty patients beginning tomorrow, July 30th. Curaleaf Holdings Inc (OTCMKTS:CURLF) promulgates itself as a company that operates as an integrated medical and wellness cannabis operator in the United States. The Company is the parent of Curaleaf, Inc., a leading vertically integrated cannabis operator in the United States. Headquartered in Wakefield, Massachusetts, Curaleaf, Inc. has a presence in 12 states. Curaleaf Inc.'s Florida operations were the first in the cannabis industry to receive the Safe Quality Food certification under the Global Food Safety Initiative, setting a new standard of excellence. It cultivates, processes, markets, and/or dispenses a range of cannabis products in various operating markets, including flower, pre-rolls and flower pods, dry-herb vaporizer cartridges, concentrates for vaporizing, concentrates for dabbing, tinctures, lozenges, capsules, and edibles. Curaleaf Holdings Inc (OTCMKTS:CURLF) also provides non-cannabis services to licensed cannabis operators in the areas of cultivation, extraction and production, and retail operations. As of November 01, 2018, it operated a network of 29 dispensaries. The company was founded in 2010 and is headquartered in Wakefield, Massachusetts. Green Thumb Industries Inc (OTCMKTS:GTBIF) recently announced that it opened Essence South Durango, on June 27. This has been one of the fastest growing MSO’s in the wider cannabis space. According to the release, this is Green Thumb’s fifth Essence store in the Las Vegas area and 48th retail location in the nation. Profits from the first day of sales will be donated to Last Prisoner Project, a nonprofit coalition of cannabis industry leaders, executives, and artists dedicated to bringing restorative justice to the cannabis industry. Green Thumb Industries Inc (OTCMKTS:GTBIF) bills itself as a company that manufactures and sells various cannabis products in the United States. The company’s cannabis products include flower, concentrates for dabbing and vaporizing, edibles, and topicals. According to company materials, “Green Thumb Industries (GTI), a national cannabis cultivator, processor and dispensary operator, is dedicated to providing dignified access to safe and effective cannabis nationwide while giving back to the communities in which they serve. As a vertically integrated company, GTI manufactures and sells a well-rounded suite of branded cannabis products including flower, concentrates, edibles, and topicals. The company also owns and operates a rapidly growing national chain of retail cannabis stores called RISE(TM) dispensaries. Headquartered in Chicago, Illinois, GTI has seven manufacturing facilities and licenses for 50 retail locations across seven highly regulated U.S. markets. Established in 2014, GTI employs more than 350 people and serves hundreds of thousands of patients and customers each year. GTI was named a Best Workplace 2018 by Crain’s Chicago Business.” Green Thumb Industries Inc (OTCMKTS:GTBIF) markets its products through third-party retailers. It also owns and operates a chain of 50 retail stores under the RISE dispensaries name. The company was founded in 2014 and is headquartered in Chicago, Illinois. Trulieve Cannabis Corp (OTCMKTS:TCNNF) just announced the opening of its latest storefront: Tarpon Springs will be home to the Company's 53rd dispensary in the state of Florida and 55th nationwide. According to the release, situated next to Lake Tarpon, the dispensary supports Trulieve's goal of expanding and ensuring direct, reliable patient access to medical cannabis throughout the state. It also joins the Company's 52 other Florida dispensaries, including those in nearby New Port Richey, Clearwater, and Tampa. Trulieve Cannabis Corp (OTCMKTS:TCNNF) promulgates itself as a company that, through its subsidiary, Trulieve, Inc., engages in the cultivation, possession, distribution, and sale of medical cannabis in the United States. It offers a suite of Trulieve branded products with approximately 125 SKUs, including nasal sprays, capsules, concentrates, syringes, and cannabis flower in tamper-proof containers for vaporizers, topical creams, tinctures, and vape cartridges. According to company materials, “Trulieve is a vertically integrated "seed to sale" company and is the first and largest fully licensed medical cannabis company in the State of Florida. Trulieve cultivates and produces all of its products in-house and distributes those products to Trulieve branded stores (dispensaries) throughout the State of Florida, as well as directly to patients via home delivery. Trulieve is listed on the Canadian Securities Exchange under the symbol TRUL.” Trulieve Cannabis Corp (OTCMKTS:TCNNF) distributes its products to Trulieve branded stores (dispensaries) in Florida, as well as takes orders online and by phone for delivery. As of November 20, 2018, the company operated 21 dispensaries. Trulieve Cannabis Corp. is headquartered in Quincy, Florida. Sugarmade Inc (OTCMKTS:SGMD) is in the process of expanding into the LA area for its BudCars cannabis delivery business. This is likely to be a strong source of new strategic growth for a company that has already been posting sequential monthly growth above 30% on the topline for several consecutive months after making its flagship investment in BudCars. At this point, based on recent disclosures from the company, we have a clear sense that, not only is the first LA location on track and simply awaiting some factors no doubt slowed by the pandemic – city council isn’t exactly on vacation right now. Crisis mode is the standard setting for most administrative affairs in local government around the country right now. However, the other key piece here is that the second LA BudCars location is ahead of schedule. That’s perhaps even more important here. Sugarmade Inc (OTCMKTS:SGMD) also recently issued a mid-month performance update for the month of July, which was on pace to set multiple new Company performance records at the time for sales, gross profits, and total customer orders. According to the release, as of July 14, the Company is now on pace to meet or exceed its target of $650,000 in total sales in July, with well over 5,000 individual customer orders likely this month, suggesting that sequential month-over-month topline growth will be at or above the Company’s target 30% level. “Our BudCars Sacramento hub continues to demonstrate accelerating growth that suggests we still haven’t really found the ceiling here in terms of period-over-period upside potential,” commented Jimmy Chan, CEO of Sugarmade. “Ultimately, this is gratifying to see because we have taken a unique approach to retail cannabis product distribution.” Sugarmade Inc (OTCMKTS:SGMD) has been posting major growth updates on a regular basis over the past couple months as its BudCars model takes apparent flight. The rate of sales growth expected from the company in 2020 has walked up a steep ladder, with the latest guidance suggesting we could see it north of $30 million in annualized sales by year-end. Cresco Labs Inc (OTCMKTS:CRLBF) just announced additional actions in board refreshment and corporate governance to further strengthen its leadership in the cannabis industry, including its move to appoint Carol Vallone. According to the release, Cresco has appointed Carol Vallone to its board of directors, effective immediately. Ms. Vallone is a well-known business leader, former CEO, and corporate board director, with a strong track record in launching, scaling, and managing global companies… In the past, Ms. Vallone served as President and Chief Executive Officer of leading E-learning companies including WebCT Inc., where she grew the online learning company to cover almost two thousand institutions in seventy countries. She has also served on multiple boards at leading non-profit healthcare, public financial services, and e-commerce organizations. CRESCO LABS ORD (OTCMKTS:CRLBF) trumpets itself as a company that manufactures and sells medical cannabis products in the United States. It offers cannabis dry flower; vaporizer forms of cannabis; cannabis oil in capsule, oral and sublingual solutions; cannabis in topical; and other cannabis products. The company also provides cannabis infused edibles, including chocolate and toffee confections, fruit-forward gummies, and hard sweet and chews. Cresco Labs Inc. sells its products under the Cresco brand. Cresco Labs Inc (OTCMKTS:CRLBF) operates a Hope Heal Health dispensary in Fall River, Bristol County, Massachusetts. Read the full article
0 notes
Text
the underlying theme of the letters from my heart
focuses on marriage, in seeking to find the heart of a girl to befriend. yet, even so, with nothing forced to be. and no fear at all. because there is no fear in Love.
and marriage is the topic of Today’s chapter reading of the Scriptures with the paired chapters of 1st Corinthians 7 and Zechariah 6 as a daily chapter from each Testament in my personal reading from the books and letters of the Bible in sequential order, with the exception of Psalms and Proverbs read from daily as well. with Today’s Psalms being 28, 8, 62 and Proverbs 28 for december 28, simultaneously the 8th day of Winter and day 362 of the year, now in ‘17
to conclude yesterday’s chapter 6 from 1st Corinthians which related to becoming “One” by the sexual union with another:
[1st Corinthians 7]
To Be Married, to Be Single …
Now, getting down to the questions you asked in your letter to me. First, Is it a good thing to have sexual relations?
Certainly—but only within a certain context. It’s good for a man to have a wife, and for a woman to have a husband. Sexual drives are strong, but marriage is strong enough to contain them and provide for a balanced and fulfilling sexual life in a world of sexual disorder. The marriage bed must be a place of mutuality—the husband seeking to satisfy his wife, the wife seeking to satisfy her husband. Marriage is not a place to “stand up for your rights.” Marriage is a decision to serve the other, whether in bed or out. Abstaining from sex is permissible for a period of time if you both agree to it, and if it’s for the purposes of prayer and fasting—but only for such times. Then come back together again. Satan has an ingenious way of tempting us when we least expect it. I’m not, understand, commanding these periods of abstinence—only providing my best counsel if you should choose them.
Sometimes I wish everyone were single like me—a simpler life in many ways! But celibacy is not for everyone any more than marriage is. God gives the gift of the single life to some, the gift of the married life to others.
I do, though, tell the unmarried and widows that singleness might well be the best thing for them, as it has been for me. But if they can’t manage their desires and emotions, they should by all means go ahead and get married. The difficulties of marriage are preferable by far to a sexually tortured life as a single.
And if you are married, stay married. This is the Master’s command, not mine. If a wife should leave her husband, she must either remain single or else come back and make things right with him. And a husband has no right to get rid of his wife.
For the rest of you who are in mixed marriages—Christian married to non-Christian—we have no explicit command from the Master. So this is what you must do. If you are a man with a wife who is not a believer but who still wants to live with you, hold on to her. If you are a woman with a husband who is not a believer but he wants to live with you, hold on to him. The unbelieving husband shares to an extent in the holiness of his wife, and the unbelieving wife is likewise touched by the holiness of her husband. Otherwise, your children would be left out; as it is, they also are included in the spiritual purposes of God.
On the other hand, if the unbelieving spouse walks out, you’ve got to let him or her go. You don’t have to hold on desperately. God has called us to make the best of it, as peacefully as we can. You never know, wife: The way you handle this might bring your husband not only back to you but to God. You never know, husband: The way you handle this might bring your wife not only back to you but to God.
And don’t be wishing you were someplace else or with someone else. Where you are right now is God’s place for you. Live and obey and love and believe right there. God, not your marital status, defines your life. Don’t think I’m being harder on you than on the others. I give this same counsel in all the churches.
Were you Jewish at the time God called you? Don’t try to remove the evidence. Were you non-Jewish at the time of your call? Don’t become a Jew. Being Jewish isn’t the point. The really important thing is obeying God’s call, following his commands.
Stay where you were when God called your name. Were you a slave? Slavery is no roadblock to obeying and believing. I don’t mean you’re stuck and can’t leave. If you have a chance at freedom, go ahead and take it. I’m simply trying to point out that under your new Master you’re going to experience a marvelous freedom you would never have dreamed of. On the other hand, if you were free when Christ called you, you’ll experience a delightful “enslavement to God” you would never have dreamed of.
All of you, slave and free both, were once held hostage in a sinful society. Then a huge sum was paid out for your ransom. So please don’t, out of old habit, slip back into being or doing what everyone else tells you. Friends, stay where you were called to be. God is there. Hold the high ground with him at your side.
The Master did not give explicit direction regarding virgins, but as one much experienced in the mercy of the Master and loyal to him all the way, you can trust my counsel. Because of the current pressures on us from all sides, I think it would probably be best to stay just as you are. Are you married? Stay married. Are you unmarried? Don’t get married. But there’s certainly no sin in getting married, whether you’re a virgin or not. All I am saying is that when you marry, you take on additional stress in an already stressful time, and I want to spare you if possible.
I do want to point out, friends, that time is of the essence. There is no time to waste, so don’t complicate your lives unnecessarily. Keep it simple—in marriage, grief, joy, whatever. Even in ordinary things—your daily routines of shopping, and so on. Deal as sparingly as possible with the things the world thrusts on you. This world as you see it is on its way out.
I want you to live as free of complications as possible. When you’re unmarried, you’re free to concentrate on simply pleasing the Master. Marriage involves you in all the nuts and bolts of domestic life and in wanting to please your spouse, leading to so many more demands on your attention. The time and energy that married people spend on caring for and nurturing each other, the unmarried can spend in becoming whole and holy instruments of God. I’m trying to be helpful and make it as easy as possible for you, not make things harder. All I want is for you to be able to develop a way of life in which you can spend plenty of time together with the Master without a lot of distractions.
If a man has a woman friend to whom he is loyal but never intended to marry, having decided to serve God as a “single,” and then changes his mind, deciding he should marry her, he should go ahead and marry. It’s no sin; it’s not even a “step down” from celibacy, as some say. On the other hand, if a man is comfortable in his decision for a single life in service to God and it’s entirely his own conviction and not imposed on him by others, he ought to stick with it. Marriage is spiritually and morally right and not inferior to singleness in any way, although as I indicated earlier, because of the times we live in, I do have pastoral reasons for encouraging singleness.
A wife must stay with her husband as long as he lives. If he dies, she is free to marry anyone she chooses. She will, of course, want to marry a believer and have the blessing of the Master. By now you know that I think she’ll be better off staying single. The Master, in my opinion, thinks so, too.
The Letter of First Corinthians, Chapter 7 (The Message)
0 notes
Text
Test Bank Database Processing 11th Edition
For Order This And Any Other Test
Banks And Solutions Manuals, Course,
Assignments, Discussions, Quizzes, Exams,
Contact us At: [email protected]
Database Processing, 11e (Kroenke)
Chapter 1: Introduction
1) The purpose of a database is to help people keep track of things.
Answer: TRUE
Diff: 1 Page Ref: 3
2) In a database, each table stores data about a different type of thing.
Answer: TRUE
Diff: 1 Page Ref: 3
3) In a database, each row in a spreadsheet has data about a particular instance.
Answer: FALSE
Diff: 2 Page Ref: 3
4) In every database, not just the databases discussed in this book, table names are capitalized.
Answer: FALSE
Diff: 2 Page Ref: 3
5) A database shows data in tables and the relationships among the rows in those tables.
Answer: TRUE
Diff: 1 Page Ref: 4
6) Data is recorded facts and figures; information is knowledge derived from data.
Answer: TRUE
Diff: 1 Page Ref: 5
7) Databases record data in such a way that they can produce information.
Answer: TRUE
Diff: 2 Page Ref: 6
8) Enterprise Resource Planning (ERP) is an example of a data mining application.
Answer: FALSE
Diff: 2 Page Ref: 6-7
9) Small databases typically have simple structures.
Answer: FALSE
Diff: 3 Page Ref: 8
10) Microsoft Access is a low-end product intended for individuals and small workgroups.
Answer: TRUE
Diff: 2 Page Ref: 14
11) Applications are computer programs used directly by users.
Answer: TRUE
Diff: 1 Page Ref: 8
12) Sequenced Query Language (SQL) is an internationally recognized standard language that is understood by all commercial database management system products.
Answer: FALSE
Diff: 2 Page Ref: 8
13) A database management system (DBMS) creates, processes and administers databases.
Answer: TRUE
Diff: 1 Page Ref: 11
14) Microsoft Access is just a DBMS.
Answer: FALSE
Diff: 2 Page Ref: 13
15) The DBMS engine in Microsoft Access is called Jet.
Answer: TRUE
Diff: 2 Page Ref: 14
16) In Microsoft Access, you can use the Oracle DBMS in place of the Jet DBMS.
Answer: FALSE
Diff: 2 Page Ref: 14
17) In an Enterprise-class database system, a database application interacts with the DBMS.
Answer: TRUE
Diff: 2 Page Ref: 15 Fig 1-16
18) In an Enterprise-class database system, a database application accesses the database data.
Answer: FALSE
Diff: 2 Page Ref: 15 Fig 1-16
19) In an Enterprise-class database system, business users interact directly with the DBMS, which directly accesses the database data.
Answer: FALSE
Diff: 2 Page Ref: 15 Fig 1-16
20) All database applications get and put database data by sending SQL statements to the DBMS.
Answer: TRUE
Diff: 2 Page Ref: 9
21) The DBMS ranked as having the "most power and features" in the text is IBM's DB2.
Answer: FALSE
Diff: 3 Page Ref: 16 Fig 1-17
22) The DBMS ranked as being the "most difficult to use" in the text is Oracle Corporation's Oracle Database.
Answer: TRUE
Diff: 3 Page Ref: 16 Fig 1-17
23) The DBMS ranked as being the "easiest to use" in the text is Microsoft's SQL Server.
Answer: FALSE
Diff: 2 Page Ref: 16 Fig 1-17
24) The DBMS ranked as having the "least power and features" in the text is Microsoft Access.
Answer: TRUE
Diff: 2 Page Ref: 16 Fig 1-17
25) A database is called "self-describing" because it reduces data duplication.
Answer: FALSE
Diff: 2 Page Ref: 12
26) The description of a database's structure that is stored within the database itself is called the "metadata."
Answer: TRUE
Diff: 1 Page Ref: 12 Fig 1-14
27) In a database processing system, indexes are held by the database management system (DBMS).
Answer: TRUE
Diff: 3 Page Ref: 11 Fig 1-12
28) Database design is important, but fortunately it is simple to do.
Answer: FALSE
Diff: 1 Page Ref: 16
29) A database design may be a new systems development project.
Answer: TRUE
Diff: 1 Page Ref: 16-19 Fig 1-18
30) A database design is rarely a redesign of an existing database.
Answer: FALSE
Diff: 1 Page Ref: 16-19 Fig 1-18
31) Information systems that stored groups of records in separate files were called file processing systems.
Answer: TRUE
Diff: 2 Page Ref: 19-20 Fig 1-25
32) Data Language/I (DL/I) structured data relationships as a tree structure.
Answer: TRUE
Diff: 3 Page Ref: 21 Fig 1-25
33) The CODASYL DBTG mode structured data relationships as a tree structure.
Answer: FALSE
Diff: 3 Page Ref: 22 Fig 1-25
34) The relational model was first proposed in 1970 by E. F. Codd at IBM.
Answer: TRUE
Diff: 2 Page Ref: 22
35) The 1977 edition of this text contained a chapter on the relational model, and that chapter was reviewed by E. F. Codd.
Answer: TRUE
Diff: 3 Page Ref: 22
36) dBase was the first PC-based DBMS to implement true relational algebra on a PC.
Answer: FALSE
Diff: 3 Page Ref: 23
37) Paradox is the only major survivor of the "bloodbath of PC DBMS products."
Answer: FALSE
Diff: 2 Page Ref: 23
38) Business organizations have resisted adopting object-oriented database systems because the cost of purchasing OODBMS packages is prohibitively high.
Answer: FALSE
Diff: 3 Page Ref: 23
39) Bill Gates has said that "XML is the lingua-franca of the Internet Age."
Answer: TRUE
Diff: 2 Page Ref: 24
40) XML Web services allow database processing to be shared across the Internet.
Answer: TRUE
Diff: 2 Page Ref: 24
41) The purpose of a database is to:
A) help people keep track of things.
B) store data in tables.
C) create tables of rows and columns.
D) maintain data on different things in different tables.
E) All of the above.
Answer: A
Diff: 2 Page Ref: 3
42) A database stores:
A) data.
B) relationships.
C) metadata.
D) A and B
E) A, B and C
Answer: E
Diff: 2 Page Ref: 3-4 and 12
43) A database records:
A) facts.
B) figures.
C) information.
D) A and B
E) A, B and C
Answer: D
Diff: 2 Page Ref: 3
44) A sales contact manager used by a salesperson is an example of a(n) ________.
A) single-user database application
B) multiuser database application
C) e-commerce database application
D) A or B
E) Any of A, B or C
Answer: A
Diff: 2 Page Ref: 8 and Fig 1-5
45) A Customer Resource Management (CRM) system is an example of a(n) ________.
A) single-user database application
B) multiuser database application
C) e-commerce database application
D) A or B
E) Any of A, B or C
Answer: B
Diff: 2 Page Ref: 8 and Fig 1-5
46) An online drugstore such as Drugstore.com is an example of a(n) ________.
A) single-user database application
B) multiuser database application
C) e-commerce database application
D) A or B
E) Any of A, B or C
Answer: C
Diff: 1 Page Ref: 7 Fig 1-5
47) The industry standard supported by all major DBMSs that allows tables to be joined together is called ________.
A) Sequential Query Language (SQL)
B) Structured Question Language (SQL)
C) Structured Query Language (SQL)
D) Relational Question Language (RQL)
E) Relational Query Language (RQL)
Answer: C
Diff: 1 Page Ref: 8
48) A program whose job is to create, process and administer databases is called the ________.
A) Database Modeling System
B) Database Management System
C) Data Business Model System
D) Relational Model Manager
E) Data Business Management Service
Answer: B
Diff: 2 Page Ref: 8
49) Microsoft Access includes:
A) a DBMS.
B) an application generator.
C) a Web server.
D) A and B
E) A, B and C
Answer: D
Diff: 2 Page Ref: 13 Fig 1-15
50) Microsoft Access may use which of the following DBMS engines?
A) Jet
B) SQL Server
C) Oracle
D) A and B
E) A, B and C
Answer: D
Diff: 2 Page Ref: 14
51) Which of the following are basic components of an enterprise-class database system?
A) The user
B) The database application
C) The database management system (DBMS)
D) The database
E) All of the above
Answer: E
Diff: 1 Page Ref: 15 Fig 1-16
52) In an enterprise-class database system ________.
A) the database application(s) interact(s) with the DBMS
B) the database application(s) access(es) the database data
C) the DBMS accesses the database data
D) A and B
E) A and C
Answer: E
Diff: 2 Page Ref: 15 Fig 1-16
53) In an enterprise-class database system, the database application ________.
A) creates queries
B) creates forms
C) creates reports
D) A and B
E) B and C
Answer: E
Diff: 2 Page Ref: 15 Fig 1-16
54) In an enterprise-class database system, reports are created by ________.
A) the user
B) the database application
C) the database management system (DBMS)
D) the database
E) All of the above
Answer: B
Diff: 2 Page Ref: 15 Fig 1-16
55) A database is considered "self-describing" because ________.
A) all the users' data is in one place
B) it reduces data duplication
C) it contains a description of its own structure
D) it contains a listing of all the programs that use it
E) All of the above
Answer: C
Diff: 1 Page Ref: 12
56) In an enterprise-class database system, the database ________.
A) holds user data
B) holds metadata
C) holds indexes
D) holds stored procedures
E) All of the above
Answer: E
Diff: 3 Page Ref: 12-13 Fig 1-14
57) A database may contain ________.
A) tables
B) metadata
C) triggers
D) stored procedures
E) All of the above
Answer: E
Diff: 2 Page Ref: 12-13 Fig 1-14
58) A database may be designed ________.
A) from existing data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: E
Diff: 2 Page Ref: 16 Fig 1-18
59) A database designed using spreadsheets from the Sales department is a database being designed ________.
A) from existing data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: A
Diff: 2 Page Ref: 16-19 Fig 1-18
60) A database designed to implement requirements for a reporting application needed by the Sales department is a database being designed ________.
A) from existing non-database data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: B
Diff: 2 Page Ref: 16-19 Fig 1-18
61) A database designed to combine two databases used by the Sales department is a database being designed ________.
A) from existing data
B) as a new systems development project
C) as a redesign of an existing database
D) A and B
E) A, B, and C
Answer: C
Diff: 1 Page Ref: 16-19 Fig 1-18
62) Database professionals use ________ as specific data sources for studies and analyses.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: A
Diff: 2 Page Ref: 19-20
63) Database professionals use a set of principles called ________ to guide and assess database design.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: B
Diff: 3 Page Ref: 17
64) A very popular development technique used by database professionals for database design is known as ________.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: D
Diff: 3 Page Ref: 17-18
65) A very popular development technique used by database professionals to adopt a database design to a new or changing requirement is known as ________.
A) data marts
B) normalization
C) data models
D) entity-relationship data modeling
E) data migration
Answer: E
Diff: 3 Page Ref: 18-19
66) The predecessor(s) of database processing was (were) ________.
A) file managers
B) hierarchical models
C) network models
D) relational data model
E) All of the above were predecessors of database processing.
Answer: A
Diff: 3 Page Ref: 20-23
67) The relational model ________.
A) was first proposed in 1970
B) was developed by E. F. Codd
C) was developed at IBM
D) resulted in the DBMS product DB2
E) All of the above
Answer: E
Diff: 1 Page Ref: 22-23
68) Modern microcomputer personal DBMS products ________.
A) are supplied by several well-established manufacturers
B) were essentially killed off by MS Access
C) have poor response time
D) are not true DBMS products
E) are really just programming languages with generalized file-processing capabilities
Answer: B
Diff: 2 Page Ref: 22-23
69) Business organizations have resisted adopting object-oriented database management systems because ________.
A) object-oriented programming uses simplified data structures that fit easily into relational databases
B) the cost of purchasing OODBMS packages is prohibitively high
C) the cost of converting data from relational databases to OODBMSs is too high
D) most large organizations have older applications that are not based on object oriented programming
E) C and D
Answer: E
Diff: 2 Page Ref: 23
70) For database development, the most important Web-related technology to emerge in recent years is:
A) FTP.
B) HTTP.
C) XML.
D) OODBMS.
E) All of the above.
Answer: C
Diff: 2 Page Ref: 23-24
71) The purpose of a database is to ________.
Answer: help people keep track of things
Diff: 1 Page Ref: 3
72) In a database, each ________ stores data about a different type of thing.
Answer: table
Diff: 1 Page Ref: 3
73) In a database, each ________ in a database has data about a particular instance.
Answer: table
Diff: 2 Page Ref: 3
74) In the databases discussed in this book, table names are ________.
Answer: capitalized
Diff: 2 Page Ref: 3
75) A database shows data in tables and ________ among the rows of those tables.
Answer: the relationships
Diff: 1 Page Ref: 4
76) ________ is recorded facts and figures; ________ is knowledge derived from data.
Answer: Data; information
Diff: 1 Page Ref: 3 and 5-6
77) Databases record ________ in such a way that they can produce ________.
Answer: data; information
Diff: 2 Page Ref: 6
78) Enterprise Resource Planning (ERP) is an example of a ________.
Answer: multiuser database
Diff: 2 Page Ref: 6-7 Fig 1-5
79) ________ do not necessarily have simple structures.
Answer: Small databases
Diff: 3 Page Ref: 8
80) Computer programs used directly by users are called ________.
Answer: applications
Diff: 1 Page Ref: 8
81) ________ is an internationally recognized standard language that is understood by all commercial database management system products.
Answer: Structured Query Language (SQL)
Diff: 2 Page Ref: 8
82) A ________ is used to create, process and administer databases.
Answer: database management system (DBMS)
Diff: 1 Page Ref: 8
83) ________ is a DBMS combined with an application generator.
Answer: Microsoft Access
Diff: 2 Page Ref: 13-14
84) In an enterprise-class database system, a ________ interacts with the DBMS.
Answer: database application
Diff: 2 Page Ref: 15 Fig 1-16
85) All database applications get and put database data by sending ________ to the DBMS.
Answer: SQL statements
Diff: 3 Page Ref: 15 Fig 1-16
86) The DBMS ranked as having the "most power and features" in the text is ________.
Answer: Oracle database
Diff: 3 Page Ref: 11
87) The DBMS ranked as being the "easiest to use" in the text is ________.
Answer: Microsoft Access
Diff: 2 Page Ref: 16
88) A database is called ________ because it contains a description of itself.
Answer: "self-describing"
Diff: 2 Page Ref: 12
89) ________ is the description of a database's structure that is stored within the database itself.
Answer: Metadata
Diff: 1 Page Ref: 12-13 Fig 1-13
90) In an enterprise-class database system, indexes are held by the ________.
Answer: database
Diff: 3 Page Ref: 12-13 Fig 1-14
91) Business information systems that stored groups of records in separate files were called ________.
Answer: file processing systems
Diff: 2 Page Ref: 20-21 Fig 1-25
92) Data Language/I (DL/I) structured data relationships in a data structure known as a ________.
Answer: tree structure
Diff: 3 Page Ref: 21-22 Fig 1-25
93) The CODSYL DBTG mode structured data relationships in a data structure known as a ________.
Answer: network
Diff: 3 Page Ref: 22 Fig 1-25
94) The relational model was first proposed in 1970 by ________ at IBM.
Answer: E. F. Codd
Diff: 2 Page Ref: 22
95) The 1977 edition of this text was the first edition of this book that contained a description of the ________.
Answer: relational model
Diff: 2 Page Ref: 20
96) ________ was the first PC based DBMS to implement true relational algebra on a PC.
Answer: R:base
Diff: 3 Page Ref: 23
97) ________ is the only major survivor of the "bloodbath of PC DBMS products."
Answer: Microsoft Access
Diff: 2 Page Ref: 23
98) Business organizations have resisted adopting ________ because of the difficulty of converting existing databases.
Answer: object-oriented database management systems (OODBMSs)
Diff: 3 Page Ref: 23
99) ________ has said that "XML is the lingua-franca of the Internet Age."
Answer: Bill Gates
Diff: 2 Page Ref: 24
100) ________ allow database processing to be shared across the Internet.
Answer: XML Web services
Diff: 2 Page Ref: 24
101) What is the purpose of a database, and how does the database accomplish this purpose?
Answer: The purpose of a database is to help people keep track of things. It accomplishes this purpose by storing data in tables. Each table has rows and columns, similar to a spreadsheet. A database usually has multiple tables in order to keep track of different but related things. For example, we might have a CUSTOMER table to keep track of customers and a PRODUCT table to keep track of the things we sell. Each row in each table holds data about a particular instance, i.e., one customer or one product. The database also stores the links between the tables, so that we can track which customers bought which products (note: this will require an additional table if one customer can buy more than one product and one product can be sold to more than one customer).
Diff: 2 Page Ref: 3-5
102) What are the four components of a database system?
Answer: The four components in a database system are: the user, the database application, the database management system (DBMS) and the database. The user interacts with the database application, which interacts with the DBMS, which controls the database. The functions of the database application include creating and processing forms, creating and transmitting queries and creating and processing reports. The DBMS creates databases, tables and supporting structures, manages database data, enforces rules and provides security. The database stores the user data, the database metadata, indexes, triggers, stored procedures and application metadata.
Diff: 2 Page Ref: 8-13
103) Briefly describe the function of an application program in a database system.
Answer: The application program is responsible for creating and processing forms. The application displays the form to the user, allows the user to complete the data entry, evaluates the form to determine which data management tasks need to be performed, and transmits the appropriate requests to the DBMS. The application creates and transmits queries. The queries are requests for data that are created in a language like SQL, and transmitted to the DBMS to have the requested data returned to the application program. The application also creates and processes reports. The query to retrieve the necessary data for the report is sent to the DBMS. When the DBMS returns the needed data, the application manipulates it as necessary to create the requested report. The application program also applies application logic to control the manipulation of data in accordance with the business rules. Finally, the application program is responsible for providing control. Control must be exercised to allow the users to make choices for functions and tasks as appropriate for their jobs. Also, control must be exercised to manage the activities of the DBMS.
Diff: 2 Page Ref: 9-11
104) What components are included in a database?
Answer: The database contains user data, metadata, indexes and other overhead data, and application metadata. User data is the data from the user's environment that they want to track. Metadata is data about the structure of the database. Indexes and other overhead data are structures that the database uses to improve performance. Finally, the application metadata is data about forms, reports, and other application components that some databases, particularly those created with desktop DBMS products, store with the database.
Diff: 2 Page Ref: 13-14
105) Why do we say a database is "self-describing" and why is this an advantage?
Answer: A database is considered self-describing because it contains a description of its own structure within the database itself. This description is called the metadata, and it is stored in specialized tables in relational databases. The advantage is that the database is self-documenting, and that a knowledgeable user or a database designer can easily access the metadata. All DBMS vendors provide tools to access the metadata within their products.
Diff: 3 Page Ref: 12-13
106) What is "metadata" and how does it relate to the definition of a database?
Answer: Metadata is data about the structure of the database itself. This includes data about the names of all the tables in the database, the names of all the columns in each of the tables, the data type of each column in each table, the properties of the tables and the columns, etc. Metadata accounts for the "self-describing" aspect of the definition of a database as a "self-describing collection of integrated tables."
Diff: 2 Page Ref: 12-13
107) Briefly describe the function of the DBMS in a database system.
Answer: The DBMS creates the database and the tables and structures within it. The DBMS also reads and updates the database data. It receives requests from application programs to perform data maintenance tasks. These requests are translated into actions that are performed on the database. In addition to maintaining the user data within the database, the DBMS also maintains the database structures. The DBMS also enforces any rules that have been defined to govern the values of the data, such as data type requirements and referential integrity constraints. The DBMS controls concurrency issues, which deal with the unwanted interruption of one user's work by another user's work. As the only point of entry into the database, the DBMS also provides security for the database to restrict users' access to only the data that they have authority to read or modify. Finally, the DBMS is responsible for the creation of backup copies of the database data and for restoring the database in case a recovery is required.
Diff: 2 Page Ref: 11-12
108) What are "referential integrity constraints"? Give an example.
Answer: A referential integrity constraint is a rule that restricts certain actions on the database data. A referential integrity constraint is used to ensure that the values in a field in one table have matching tables in a corresponding field in another table. These constraints are enforced by the DBMS, which will not allow changes to the values of the database that would result in violations of this rule. For example, a database has an EMPLOYEE table and a VEHICLE table that are used to store data on employees and the vehicles that they are assigned to drive. The EMPLOYEE table has a column called EmployeeID that is used to distinguish one employee record from another. The VEHICLE table also has an EmployeeID column that is used to associate a vehicle with the appropriate employee. A referential integrity constraint could be used to prevent a vehicle from being assigned to an employee with an EmployeeID that does not appear in the EMPLOYEE table by requiring that all values in EmployeeID in the VEHICLE table have a matching value in EmployeeID in the EMPLOYEE table.
Diff: 3 Page Ref: 11
109) What are the three types of database design situations?
Answer: Database designs can be based on (1) existing data, (2) new systems development and (3) database redesign. Database designs from existing data may be based on data in spreadsheets or other data tables, or on data extracted from other databases. New systems development gathers user requirements for needed applications and designs a database to meet those requirements. Database redesign may be needed to migrate existing databases to a newer DBMS, or to integrate multiple existing databases.
Diff: 2 Page Ref: 16-19 Fig 1-18
110) Briefly describe the history of database processing.
Answer: The predecessor of database processing was file processing, where data were maintained on magnetic tape. Database processing as we know it today became possible with the availability of direct access disk storage in the 1960s. Using this storage, both the hierarchical data model and then the network data model were developed. In 1970, E. F. Codd of IBM proposed the relational model, which is the standard model used today. Current DBMSs such as DB2, Oracle and SQL Server are based on the relational model. The appearance of microcomputer based DBMSs, in the 1980s led to a "bloodbath" from which Microsoft Access emerged as the dominant PC workstation DBMS. More recent events include the introduction of object-oriented DBMSs (OODBMSs), and the development of tools such as XML to allow the use of database systems over the Internet.
Diff: 3 Page Ref: 18-22 Fig 1-18
0 notes
Text
Test Bank Evolutionary Analysis 5th Edition
For Order This And Any Other Test
Banks And Solutions Manuals, Course,
Assignments, Discussions, Quizzes, Exams,
Contact us At: [email protected]
Chapter 1 A Case for Evolutionary Thinking: Understanding HIV
1) In which of the following regions has AIDS killed the largest number of individuals?
A) India
B) Sub-Saharan Africa
C) United States
D) China
E) United Kingdom
Answer: B
Section: 1.1
Skill: Knowledge/Comprehension
2) The HIV virus contains all of the following components except ________.
A) integrase
B) double-stranded RNA
C) single-stranded RNA
D) reverse transcriptase
E) protease
Answer: B
Section: 1.1
Skill: Knowledge/Comprehension
3) The acronym HIV stands for which of the following?
A) human intercellular virus
B) human immune virus
C) human immunodeficiency virus
D) human immunity virus
E) human immunodeficiency vector
Answer: C
Section: 1.1
Skill: Knowledge/Comprehension
4) Which of the following enzymes is responsible for transcribing viral RNA into DNA?
A) RNA polymerase
B) reverse transcriptase
C) DNA polymerase
D) reverse integrase
E) RNA duplicase
Answer: B
Section: 1.1
Skill: Knowledge/Comprehension
5) The proteins that enable the HIV virus to bind to cells are typically CD4 and CCR5. On what type of cells are these proteins typically observed?
A) plasma cells
B) dendritic cells
C) effector helper T cells
D) memory helper T cells
E) both C and D
Answer: E
Section: 1.1
Skill: Knowledge/Comprehension
6) The AIDS phase of HIV infection begins when the concentration of CD4 T cells in the blood drops below what concentration?
A) 2,000 cells per cubic millimeter
B) 1,000 cells per cubic millimeter
C) 500 cells per cubic millimeter
D) 200 cells per cubic millimeter
E) No CD4 T cells are observed.
Answer: D
Section: 1.1
Skill: Knowledge/Comprehension
7) Which of the following drug categories are used to treat HIV infections?
A) integrase inhibitors
B) protease inhibitors
C) reverse transcriptase inhibitors
D) DNAse inhibitors
E) fusion inhibitors
Answer: D
Section: 1.2
Skill: Knowledge/Comprehension
8) Coreceptor inhibitors block HIV infection by preventing which of the following?
A) binding of the HIV virion onto the plasma membrane
B) binding of the HIV virion onto the CCR5 receptor
C) binding of the HIV virion onto the gp120 protein
D) degrading the coreceptor so the virion cannot attach
E) binding of the HIV virion onto the CD4 receptor
Answer: B
Section: 1.2
Skill: Application/Analysis
9) What is the effect of the ∆32 allele of CCR5 on HIV binding?
A) appears on the surface of CD4 T cells, but the HIV virion is unable to infect the host cell
B) does not appear on the surface of CD4 T cells
C) appears on the surface of the CD4 T cells and inactivates the virion upon binding
D) interferes with binding of the virion to the CD4 receptor protein
E) appears on the surface of the CD4 T cells and causes the virion to lyse upon binding
Answer: B
Section: 1.3
Skill: Application/Analysis
10) The ∆32 allele of CCR5 is found at the highest frequency in which of the following populations?
A) Africans
B) Japanese
C) North Americans
D) Europeans
E) South Americans
Answer: D
Section: 1.3
Skill: Knowledge/Comprehension
11) HIV-1 is believed to have been transmitted to humans from which of the following organisms?
A) gorillas
B) sooty mangabeys
C) African green monkeys
D) chimpanzees
E) baboons
Answer: D
Section: 1.4
Skill: Knowledge/Comprehension
12) HIV-1 Group M is responsible for 95% of human infections. When is it estimated that HIV-1 Group M was transferred to humans?
A) 1980
B) 1960
C) 1930
D) 1995
E) 1900
Answer: C
Section: 1.4
Skill: Knowledge/Comprehension
13) Antibodies and killer T cells recognize HIV or HIV-infected cells by binding to short pieces of viral proteins displayed on the virus or the infected host cell. These short pieces of viral proteins are called ________.
A) coat proteins
B) virosomes
C) proteosomes
D) epitopes
E) episomes
Answer: D
Section: 1.5
Skill: Knowledge/Comprehension
14) Tetherin is an important protein produced by the host. What is the function of tetherin in protecting a host cell from HIV?
A) ties maturing virions to the membrane of the host cell, thereby preventing the release of the mature virus
B) binds the virus to the external host cell membrane, thereby preventing the virus from entering the host cell
C) binds the viral RNA to reverse transcriptase, thus preventing synthesis of the viral DNA
D) binds the two viral RNA strands together, thus preventing the transcription of viral DNA in the host cell
E) causes the maturing virions to aggregate together, thus preventing their release from the host cell
Answer: A
Section: 1.5
Skill: Application/Analysis
15) Early in the infection with HIV, most virions bind to the host cell using CCR5 as a coreceptor. As the infection progresses, the HIV population evolves to use an alternate coreceptor. What is the alternate coreceptor these X4 viruses utilize?
A) Tetherin
B) CCR5α
C) vpu
D) TRIM5α
E) CXCR4
Answer: E
Section: 1.5
Skill: Knowledge/Comprehension
16) In what region of the world is the incidence of infection with HIV highest?
Answer: Sub-Saharan Africa
Section: 1.1
Skill: Knowledge/Comprehension
17) Originally, HIV was thought to be restricted to transmission during homosexual contact between gay men. List other ways in which HIV is currently known to be transmitted.
Answer: HIV can be transmitted by heterosexual sex, oral sex, needle sharing, transfusion with contaminated blood products, other unsafe medical procedures, childbirth and breast-feeding.
Section: 1.1
Skill: Knowledge/Comprehension
18) What does the acronym AIDS stand for?
Answer: Acquired Immune Deficiency Syndrome
Section: 1.1
Skill: Knowledge/Comprehension
19) What viral coat protein typically binds first to the CD4 receptor on helper T cells?
Answer: gp120
Section: 1.1
Skill: Knowledge/Comprehension
20) When AZT is used to treat HIV infections, why does resistance to AZT usually develop?
Answer: Mutations present in the viral population, due to the lack of proofreading and high error rate of the viral reverse transcriptase, enable mutant virions to discriminate against the incorporation of AZT during transcription.
Section: 1.2
Skill: Application/Analysis
21) It has been observed that viral particles often revert (back mutate to non-AZT-resistant populations when treatment with AZT is discontinued. What is the most likely reason for this observation?
Answer: There is no more selective pressure applied to the viral population, and in the absence of AZT the viral particles that reproduce most efficiently have not evolved enough to have the ability to discriminate against AZT.
Section: 1.2
Skill: Application/Analysis
22) What is the molecular mechanism by which reverse transcriptase inhibitors, such as AZT, prevent viral replication?
Answer: These molecules are analogues of the nucleotide building blocks of DNA, and typically prevent binding or elongation of the of the transcribed DNA molecule.
Section: 1.2
Skill: Knowledge/Comprehension
23) In what host cell protein is the Δ32 mutation found, and what type of mutation is this?
Answer: The Δ32 mutation is found in the CCR5 coreceptor on CD4 helper T cells, and is a 32-base pair deletion.
Section: 1.3
Skill: Knowledge/Comprehension
24) Explain the phylogenetic relationship between humans, chimpanzees, and monkeys in the transmission of the current predominant deadly strain in humans, HIV-1.
Answer: HIV-1 is believed to have originated in monkeys as an SIV (simian immunodeficiency virus); SIV was passed from monkeys to chimpanzees, and SIV was passed to and mutated into HIV-1 sometime around 1930.
Section: 1.4
Skill: Knowledge/Comprehension
25) Explain the mechanism HIV uses to avoid destruction by antibodies present in the human immune system.
Answer: The virus is constantly mutating its surface proteins, and these frequent changes in epitopes on the viral surface prevent the host cell from being able to recognize the virus over time.
Section: 1.5
Skill: Application/Analysis
26) Following long periods of infection with HIV, an X4 strain often evolves. What evolutionary advantage does the X4 strain confer on the viral population, and what specific protein does this strain interact with?
Answer: The evolutionary advantage of this strain is that it can infect a different population of T cells. The alternate population of T cells contains the coreceptor CXCR4 instead of the CCR5 coreceptor.
Section: 1.5
Skill: Application/Analysis
27) What is the function of the product of the viral gene vpu in human infections of HIV?
Answer: The viral gene vpu (in a similar manner to the viral protein nef) blocks the action of the host protein tetherin, which normally adheres to viral particles and attaches them to the host cell membrane and prevents their release.
Section: 1.5
Skill: Knowledge/Comprehension
28) What steps are involved in producing the HIV GP120 protein? List all processes and host cellular structures involved from the point of initial infection with viral RNA to the production of the mature virion outside of the host cell.
Section: 1.1
Skill: Application/Analysis
29) Highly active antiretroviral therapies (HAART) have become the treatment method of choice in treating human HIV infections. What is required for a treatment to be classified as HAART, and why have these treatments proven so effective in the treatment of HIV infections?
Section: 1.2
Skill: Synthesis/Evaluation
30) If an individual is infected with HIV that goes undetected and untreated, the infection follows a standard clinical course of progression. Explain the three sequential phases of untreated HIV infection, the approximate times over which these phases occur, and the corresponding levels of both HIV RNA and CD4 T cells circulating in the host bloodstream.
Section: 1.1
Skill: Knowledge/Comprehension
0 notes
Text
ACC 564 Quiz 3 – Strayer New
ACC 564 Week 8 Quiz 3 Chapter 10 Through 13
Click On The Link Below To Purchase
Instant Download
http://www.budapp.net/ACC-564-Quiz-3-Strayer-New-ACC564Q3.htm
Chapter 10 Information Systems Controls for Systems ReliabilityPart 3: Processing Integrity and Availability
1) The best example of a hash total for a payroll transaction file could be
A) total of employees' social security numbers.
B) sum of net pay.
C) total number of employees.
D) sum of hours worked.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
2) Error logs and review are an example of
A) data entry controls.
B) data transmission controls.
C) output controls.
D) processing controls.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
3) Following is the result of batch control totals on employee Social Security Numbers in a payroll processing transaction:
Correct Values From Masterfile
Values Entered During Processing
487358796
487358796
534916487
534916487
498374526
498374526
514873420
514873420
534196487
534916487
678487853
678487853
471230589
471230589
3719438158
3720158158
The difference in the control totals is 720,000. Which data entry control would best prevent similar data entry errors in the future?
A) Modulus 11
B) Validity check
C) Check digit
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
4) Which of the following data entry controls would not be useful if you are recording the checkout of library books by members?
A) Sequence check
B) Prompting
C) Validity check
D) Concurrent update control
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
5) A customer failed to include her account number on her check, and the accounts receivable clerk credited her payment to a different customer with the same last name. Which control could have been used to most effectively to prevent this error?
A) Closed-loop verification
B) Duplicate values check
C) Validity check
D) Reconciliation of a batch control total
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
6) If invoices are processed in groups of fifty, which fields from the document shown below would not be used to create a hash control total?
A) Amount
B) Item Number
C) Quantity Ordered
D) Sales Order number
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Reflective Thinking
7) A data entry input control in which the application software sums the first four digits of a customer number to calculate the value of the fifth digit and then compares the calculated number to the number typed in during data entry is an example of a
A) check digit verification.
B) validity check.
C) closed-loop verification.
D) duplicate data check.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
8) All of the following controls for online entry of a sales order would be useful except
A) check digit verification on the dollar amount of the order.
B) validity check on the inventory item numbers.
C) field check on the customer ID and dollar amount of the order.
D) concurrent update control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
9) A specific inventory record indicates that there were 12 items on hand before a customer brings two of the items to the check stand to be purchased. The cashier accidentally entered quantity 20 instead of 2. Which data entry control would best have prevented this error?
A) sign check
B) limit check
C) validity check
D) field check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
10) When processing weekly payroll, an employee accidentally entered 400 for hours worked. The best data entry control for this error would be
A) a limit check.
B) a check digit.
C) batch total reconciliation.
D) a field check.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
11) The data entry control that would best prevent entering an invoice received from a vendor who is not on an authorized supplier list is
A) a validity check.
B) an authorization check.
C) a check digit.
D) closed-loop verification.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
12) Forms design is an example of this type of control.
A) Data entry control
B) Processing control
C) Output control
D) Input control
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
13) Sequentially prenumbered forms is an example of a(n)
A) data entry control.
B) data transmission control.
C) processing control.
D) input control.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
14) Turnaround documents are an example of a(n)
A) data entry control.
B) output control.
C) processing control.
D) input control.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
15) A validity check is an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) input control.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
16) Parity checks are an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) processing control.
Answer:
Page Ref: 279
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
17) User reviews are an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) processing control.
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
18) Data matching is an example of a(n)
A) data entry control.
B) data transmission control.
C) processing control.
D) input control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) Batch totals are an example of a(n)
A) data entry control.
B) data transmission control.
C) output control.
D) processing control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
20) Cancellation and storage of documents means that
A) data are copied from a document and stored, after which the document is shredded.
B) documents are defaced before being shredded.
C) documents are defaced and stored.
D) cancellation data are copied from documents before they are stored.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
21) Check digit verification is an example of a(n)
A) data transmission control.
B) output control.
C) processing control.
D) input control.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
22) This ensures that the input data will fit into the assigned field.
A) Limit check
B) Range check
C) Size check
D) Validity check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
23) This tests a numerical amount to ensure that it does not exceed a predetermined value nor fall below another predetermined value.
A) Completeness check
B) Field check
C) Limit check
D) Range check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
24) This determines if all required data items have been entered.
A) Completeness check
B) Field check
C) Limit check
D) Range check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) This determines the correctness of the logical relationship between two data items.
A) Range check
B) Reasonableness test
C) Sign check
D) Size check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
26) This determines if characters are of the proper type.
A) Field check
B) Alpha-numeric check
C) Range check
D) Reasonableness test
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
27) This tests a numerical amount to ensure that it does not exceed a predetermined value.
A) Completeness check
B) Limit check
C) Range check
D) Sign check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
28) This batch processing data entry control sums a field that contains dollar values.
A) Record count
B) Financial total
C) Hash total
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
29) This batch processing data entry control sums a non-financial numeric field.
A) Record count
B) Financial total
C) Hash total
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
30) When I enter a correct customer number, the data entry screen displays the customer name and address. This is an example of
A) prompting.
B) preformatting.
C) closed-loop verification.
D) error checking.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
31) This control ensures that the correct and most current files are being updated.
A) Cross-footing balance test
B) Data matching
C) File labels
D) Write-protect mechanism
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
32) This batch processing data entry control sums the number of items in a batch.
A) Financial total
B) Hash total
C) Record count
D) Sequence check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
33) This data entry control compares the ID number in transaction data to a master file to verify that the ID number exists.
A) Reasonableness test
B) User review
C) Data matching
D) Validity check
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
34) File labels are an example of
A) data entry controls.
B) output controls.
C) processing controls.
D) source data controls.
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
35) A computer operator accidentally used the wrong master file when updating a transaction file. As a result, the master file data is now unreadable. Which control could best have prevented this from happening?
A) Internal header label
B) Validity check
C) Check digit
D) Parity check
Answer:
Page Ref: 277
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
36) Chaz Finnerty called the IT Help Desk in a huff. "I'm trying to open an Excel file and I get a message that says that the file is locked for editing. What's going on?" The answer is likely that
A) the file is corrupted due to a computer virus.
B) there is no problem. Chaz is editing the file, so it is locked.
C) concurrent update controls have locked the file.
D) Chaz probably opened the file as read-only.
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
37) This control protects records from errors that occur when two or more users attempt to update the same record simultaneously.
A) Concurrent update controls
B) Cross-footing balance test
C) Data conversion controls
D) Recalculation of batch totals
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
38) Modest Expectations Investment Services (MEIS) allows customers to manage their investments over the Internet. If customers attempt to sell more shares of a stock than they have in their account, an error message is displayed. This is an example of a
A) reasonableness test.
B) field check.
C) validity check.
D) limit check.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
39) Modest Expectations Investment Services (MEIS) allows customers to manage their investments over the Internet. If customers attempt to spend more money than they have in their account, an error message is displayed. This is an example of a
A) reasonableness test.
B) field check.
C) validity check.
D) limit check.
Answer:
Page Ref: 276
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
40) The Spontaneous Combustion Rocket Shoppe in downtown Fargo, North Dakota, generates three quarters of its revenue from orders taken over the Internet. The revenue clearing account is debited by the total of cash and credit receipts and credited by the total of storefront and Internet sales. This is an example of a
A) data integrity test.
B) zero-balance test.
C) trial balance audit.
D) cross-footing balance test.
Answer:
Page Ref: 278
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
41) What is the most effective way to ensure information system availability?
A) High bandwidth
B) Maintain a hot site
C) Maintain a cold site
D) Frequent backups
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
42) Concerning system availability, which of the following statements is true?
A) Human error does not threaten system availability.
B) Proper controls can maximize the risk of threats causing significant system downtime.
C) Threats to system availability can be completely eliminated.
D) Threats to system availability include hardware and software failures as well as natural and man-made disasters.
Answer:
Page Ref: 284
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
43) Which of the following is not an objective of a disaster recovery plan?
A) Minimize the extent of the disruption, damage or loss.
B) Permanently establish an alternative means of processing information.
C) Resume normal operations as soon as possible.
D) Train employees for emergency operations.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
44) Which item below would not typically be part of an adequate disaster recovery plan?
A) a system upgrade due to operating system software changes
B) uninterruptible power systems installed for key system components
C) scheduled electronic vaulting of files
D) backup computer and telecommunication facilities
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
45) A facility that contains all the computing equipment the organization needs to perform its essential business activities is known as a
A) cold site.
B) hot site.
C) remote site.
D) subsidiary location.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
46) A facility that is pre-wired for necessary telecommunications and computer equipment, but doesn't have equipment installed, is known as a
A) cold site.
B) hot site.
C) remote site.
D) subsidiary location.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
47) When a computer system's files are automatically duplicated on a second data storage system as they are changed, the process is referred to as
A) real-time mirroring.
B) batch updating.
C) consistency control.
D) double-secure storage.
Answer:
Page Ref: 287
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
48) ________ enables a system to continue functioning in the event that a particular component fails.
A) An incremental backup procedure
B) Fault tolerance
C) Preventive maintenance
D) A concurrent update control
Answer:
Page Ref: 284
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
49) A copy of a database, master file, or software that will be retained indefinitely as a historical record is known as a(n)
A) archive.
B) cloud computing.
C) differential backup.
D) incremental backup.
Answer:
Page Ref: 286
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
50) While this type of backup process takes longer than the alternative, restoration is easier and faster.
A) Archive
B) Cloud computing
C) Differential backup
D) Incremental backup
Answer:
Page Ref: 286
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
51) ________ involves copying only the data items that have changed since the last partial backup.
A) Archive
B) Cloud computing
C) Differential backup
D) Incremental backup
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
52) ________ copies all changes made since the last full backup.
A) Archive
B) Cloud computing
C) Differential backup
D) Incremental backup
Answer:
Page Ref: 286
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
53) The maximum amount of time between backups is determined by a company's
A) recovery time objective.
B) recovery point objective.
C) recovery objective.
D) maximum time recovery objective.
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
54) The maximum acceptable down time after a computer system failure is determined by a company's
A) recovery time objective.
B) recovery point objective.
C) recovery objective.
D) maximum time recovery objective.
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
55) The accounting department at Synergy Hydroelectric records an average of 12,500 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 25,000 transactions. If the firm's recovery time objective is 120 minutes, then the worst case recovery time objective is
A) 1 hour
B) 2 hours
C) 3 hours
D) 4 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
56) The accounting department at Synergy Hydroelectric records an average of 10,000 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 20,000 transactions. If the firm's recovery time objective is 60 minutes, then the worst case recovery time objective is
A) 1 hour
B) 2 hours
C) 3 hours
D) 4 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
57) The accounting department at Synergy Hydroelectric records an average of 10,000 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 40,000 transactions. The firm's recovery point objective is therefore
A) 40,000 transactions
B) 10,000 transactions
C) 10 hours
D) 4 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
58) The accounting department at Synergy Hydroelectric records an average of 12,500 transactions per hour. By cost-benefit analysis, managers have concluded that the maximum acceptable loss of data in the event of a system failure is 25,000 transactions. The firm's recovery point objective is therefore
A) 25,000 transactions
B) 12,500 transactions
C) 1 hour
D) 2 hours
Answer:
Page Ref: 285
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
59) This control entails verifying that the proper number of bits are set to the value 1 in each character received.
A) Echo check
B) Field check
C) Parity check
D) Trailer record
Answer:
Page Ref: 279
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
60) Probably the most important change management control is
A) monitoring user rights and privileges during the change process.
B) testing all changes thoroughly prior to implementation on a stand-alone computer.
C) updating all documentation to reflect changes made to the system.
D) management's careful monitoring and review.
Answer:
Page Ref: 289
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
61) Which of the following is true?
A) Cloud computing is a control technique for system availability.
B) Cloud computing eliminates the need for backup of applications and data.
C) Cloud computing refers to the practice of storing application files and backup data on satellites 'in the clouds'.
D) Cloud computing eliminates the need for companies to own their own software and servers.
Answer:
Page Ref: 288
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
62) Discuss how cloud computing could both positively and negatively affect system availability.
63) Define and contrast a recovery point objective and a recovery time objective.
Accounting Information Systems, 12e (Romney/Steinbart)
Chapter 11 Auditing Computer-Based Information Systems
1) Auditing involves the
A) collection, review, and documentation of audit evidence.
B) planning and verification of economic events.
C) collection of audit evidence and approval of economic events.
D) testing, documentation, and certification of audit evidence.
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
2) What is not a typical responsibility of an internal auditor?
A) helping management to improve organizational effectiveness
B) assisting in the design and implementation of an AIS
C) preparation of the company's financial statements
D) implementing and monitoring of internal controls
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
3) Which type of work listed below is not typical of internal auditors?
A) operational and management audits
B) information system audits
C) financial statement audit
D) financial audit of accounting records
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
4) The ________ audit examines the reliability and integrity of accounting records.
A) financial
B) informational
C) information systems
D) operational
Answer:
Page Ref: 303
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
5) The ________ audit reviews the general and application controls of an AIS to assess its compliance with internal control policies and procedures and its effectiveness in safeguarding assets.
A) financial
B) information systems
C) management
D) internal control
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
6) One type of audit that is concerned with the economical and efficient use of resources and the accomplishment of established goals and objectives is known as a(n) ________ audit.
A) financial
B) information systems
C) internal control
D) operational or management
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
7) The ________ audit is concerned with the economical and efficient use of resources and the accomplishment of established goals and objectives.
A) financial
B) informational
C) information systems
D) operational
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
8) The purpose of ________ is to determine why, how, when, and who will perform the audit.
A) audit planning
B) the collection of audit evidence
C) the communication of audit results
D) the evaluation of audit evidence
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
9) Organizing the audit team and the physical examination of assets are components of which two separate audit stages?
A) planning; evaluating audit evidence
B) planning; collecting audit evidence
C) collecting audit evidence; communicating audit results
D) communicating audit results; evaluating audit evidence
Answer:
Page Ref: 304-305
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
10) With which stage in the auditing process are the consideration of risk factors and materiality most associated?
A) audit planning
B) collection of audit evidence
C) communication of audit results
D) evaluation of audit evidence
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
11) A system that employs various types of advanced technology has more ________ risk than traditional batch processing.
A) control
B) detection
C) inherent
D) investing
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
12) Control risk is defined as the
A) susceptibility to material risk in the absence of controls.
B) risk that a material misstatement will get through the internal control structure and into the financial statements.
C) risk that auditors and their audit procedures will not detect a material error or misstatement.
D) risk auditors will not be given the appropriate documents and records by management who wants to control audit activities and procedures.
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
13) The possibility that a material error will occur even though auditors are following audit procedures and using good judgment is referred to as
A) control risk.
B) detection risk.
C) inherent risk.
D) investigating risk.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
14) The ________ stage of the auditing process involves (among other things) the auditors observing the operating activities and having discussions with employees.
A) audit planning
B) collection of audit evidence
C) communication of audit results
D) evaluation of audit evidence
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
15) Verifying the accuracy of certain information, often through communication with third parties, is known as
A) reperformance.
B) confirmation.
C) substantiation.
D) documentation.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
16) The evidence collection method that examines all supporting documents to determine the validity of a transaction is called
A) review of documentation.
B) vouching.
C) physical examination.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
17) The evidence collection method that considers the relationships and trends among information to detect items that should be investigated further is called
A) review of the documentation.
B) vouching.
C) physical examination.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
18) Assessing the quality of internal controls, the reliability of information, and operating performance are all part of which stage of the auditing process?
A) audit planning
B) collection of audit evidence
C) evaluation of audit evidence
D) communication of audit results
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) An auditor must be willing to accept some degree of risk that the audit conclusion is incorrect. Accordingly, the auditor's objective is to seek ________ that no material error exists in the information audited.
A) absolute reliability
B) reasonable evidence
C) reasonable assurance
D) reasonable objectivity
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
20) The risk-based audit approach is
A) a four-step approach to internal control evaluation.
B) a four-step approach to financial statement review and recommendations.
C) a three-step approach to internal control evaluation.
D) a three-step approach to financial statement review and recommendations.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
21) Which of the following is the first step in the risk-based audit approach?
A) Identify the control procedures that should be in place.
B) Evaluate the control procedures.
C) Determine the threats facing the AIS.
D) Evaluate weaknesses to determine their effect on the audit procedures.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
22) Determining whether the necessary control procedures are in place is accomplished by conducting
A) a systems overhaul.
B) a systems review.
C) tests of controls.
D) both B and C
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
23) According to the risk-based auditing approach, when a control deficiency is identified, the auditor should inquire about
A) tests of controls.
B) the feasibility of a systems review.
C) materiality and inherent risk factors.
D) compensating controls.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
24) The ________ to auditing provides auditors with a clear understanding of possible errors and irregularities and the related risks and exposures.
A) risk-based approach
B) risk-adjusted approach
C) financial audit approach
D) information systems approach
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) What is the purpose of an information systems audit?
A) To determine the inherent risk factors found in the system
B) To review and evaluate the internal controls that protect the system
C) To examine the reliability and integrity of accounting records
D) To examine whether resources have been used in an economical and efficient manner in keeping with organization goals and objectives
Answer:
Page Ref: 307
Objective: Learning Objective 2
Difficulty : Moderate
AACSB: Analytic
26) The information systems audit objective that pertains to source data being processed into some form of output is known as
A) overall security.
B) program development.
C) program modifications.
D) processing.
Answer:
Page Ref: 307
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
27) To maintain the objectivity necessary for performing an independent evaluation function, auditors should not be involved in
A) making recommendations to management for improvement of existing internal controls.
B) examining system access logs.
C) examining logical access policies and procedures.
D) developing the information system.
Answer:
Page Ref: 309
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
28) The auditor's role in systems development should be as
A) an advisor and developer of internal control specifications.
B) a developer of internal controls.
C) an independent reviewer only.
D) A and B above
Answer:
Page Ref: 309
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
29) Regarding program modifications, which statement below is incorrect?
A) Only material program changes should be thoroughly tested and documented.
B) When a program change is submitted for approval, a list of all required updates should be compiled and then approved by management and program users.
C) During the change process, the developmental version of the program must be kept separate from the production version.
D) After the modified program has received final approval, the change is implemented by replacing the developmental version with the production version.
Answer:
Page Ref: 311
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
30) How could auditors determine if unauthorized program changes have been made?
A) By interviewing and making inquiries of the programming staff
B) By examining the systems design and programming documentation
C) By using a source code comparison program
D) By interviewing and making inquiries of recently terminated programming staff
Answer:
Page Ref: 311
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
31) Which auditing technique will not assist in determining if unauthorized programming changes have been made?
A) Use of a source code comparison program
B) Use of the reprocessing technique to compare program output
C) Interviewing and making inquiries of the programming staff
D) Use of parallel simulation to compare program output
Answer:
Page Ref: 311
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
32) Strong ________ controls can partially compensate for inadequate ________ controls.
A) development; processing
B) processing; development
C) operational; internal
D) internal; operational
Answer:
Page Ref: 310
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
33) The ________ procedure for auditing computer process controls uses a hypothetical series of valid and invalid transactions.
A) concurrent audit techniques
B) test data processing
C) integrated test facility
D) dual process
Answer:
Page Ref: 312
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
34) The auditor uses ________ to continuously monitor the system and collect audit evidence while live data are processed.
A) test data processing
B) parallel simulation
C) concurrent audit techniques
D) analysis of program logic
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
35) Auditors have several techniques available to them to test computer-processing controls. An audit technique that immediately alerts auditors of suspicious transactions is known as
A) a SCARF.
B) an audit hook.
C) an audit sinker.
D) the snapshot technique.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
36) A type of software that auditors can use to analyze program logic and detect unexecuted program code is
A) a mapping program.
B) an audit log.
C) a scanning routine.
D) program tracing.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
37) One tool used to document the review of source data controls is
A) a flowchart generator program.
B) a mapping program.
C) an input control matrix.
D) a program algorithm matrix.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
38) An audit software program that generates programs that perform certain audit functions, based on auditor specifications, is referred to as a(n)
A) input controls matrix.
B) CAATS.
C) embedded audit module.
D) mapping program.
Answer:
Page Ref: 317
Objective: Learning Objective 4
Difficulty : Moderate
AACSB: Analytic
39) The use of a secure file library and restrictions on physical access to data files are control procedures used together to prevent
A) an employee or outsider obtaining data about an important client.
B) a data entry clerk from introducing data entry errors into the system.
C) a computer operator from losing or corrupting files or data during transaction processing.
D) programmers making unauthorized modifications to programs.
Answer:
Page Ref: 316
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
40) An auditor might use which of the following to convert data from several sources into a single common format?
A) computer assisted audit techniques software
B) Windows Media Converter
C) concurrent audit technique
D) Adobe Professional
Answer:
Page Ref: 317
Objective: Learning Objective 4
Difficulty : Easy
AACSB: Analytic
41) What is the primary purpose of computer audit software?
A) eliminate auditor judgment errors
B) assist the auditor in retrieving and reviewing information
C) detect unauthorized modifications to system program code
D) recheck all mathematical calculations, cross-foot, reprocess financial statements and compare to originals
Answer:
Page Ref: 317
Objective: Learning Objective 4
Difficulty : Easy
AACSB: Analytic
42) The scope of a(n) ________ audit encompasses all aspects of systems management.
A) operational
B) information systems
C) financial
D) internal control
Answer:
Page Ref: 318
Objective: Learning Objective 5
Difficulty : Moderate
AACSB: Analytic
43) Evaluating effectiveness, efficiency, and goal achievement are objectives of ________ audits.
A) financial
B) operational
C) information systems
D) all of the above
Answer:
Page Ref: 318
Objective: Learning Objective 5
Difficulty : Easy
AACSB: Analytic
44) In the ________ stage of an operational audit, the auditor measures the actual system against an ideal standard.
A) evidence collection
B) evidence evaluation
C) testing
D) internal control
Answer:
Page Ref: 318
Objective: Learning Objective 5
Difficulty : Easy
AACSB: Analytic
45) An increase in the effectiveness of internal controls would have the greatest effect on
A) reducing control risk.
B) reducing detection risk.
C) reducing inherent risk.
D) reducing audit risk.
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
46) An expansion of a firm's operations to include production in Russia and China will have the effect of
A) increasing inherent risk.
B) reducing inherent risk.
C) increasing control risk.
D) reducing control risk.
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
47) An increase in the effectiveness of auditing software will have the effect of
A) increasing detection risk.
B) reducing detection risk.
C) increasing control risk.
D) reducing control risk.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
48) An auditor examines all documents related to the acquisition, repair history, and disposal of a firm's delivery van. This is an example of collecting audit evidence by
A) confirmation.
B) reperformance.
C) vouching.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
49) An auditor manually calculates accumulated depreciation on a delivery van and compares her calculation with accounting records. This is an example collecting audit evidence by
A) confirmation.
B) reperformance.
C) vouching.
D) analytical review.
Answer:
Page Ref: 305
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
50) An auditor finds that employee absentee rates are significantly higher on Mondays and Fridays than on other work days. This is an example collecting audit evidence by
A) confirmation.
B) reperformance.
C) vouching.
D) analytical review.
Answer:
Page Ref: 306
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
51) An auditor creates a fictitious customer in the system and then creates several fictitious sales to the customer. The records are then tracked as they are processed by the system. The auditor is using
A) an integrated test facility.
B) the snapshot technique.
C) a system control audit review file.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
52) An auditor sets an embedded audit module to flag all credit transactions in excess of $1,500. The flag causes the system state to be recorded before and after each transaction is processed. The auditor is using
A) an integrated test facility.
B) the snapshot technique.
C) a system control audit review file.
D) audit hooks.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
53) An auditor sets an embedded audit module to record all credit transactions in excess of $1,500 and store the data in an audit log. The auditor is using
A) the snapshot technique.
B) a system control audit review file.
C) audit hooks.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
54) An auditor sets an embedded audit module to flag questionable online transactions, display information about the transaction on the auditor's computer, and send a text message to the auditor's cell phone. The auditor is using
A) the snapshot technique.
B) a system control audit review file.
C) audit hooks.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
55) An auditor sets an embedded audit module to selectively monitor transactions. Selected transactions are then reprocessed independently, and the results are compared with those obtained by the normal system processing. The auditor is using
A) an integrated test facility.
B) the snapshot technique.
C) a system control audit review file.
D) continuous and intermittent simulation.
Answer:
Page Ref: 313
Objective: Learning Objective 3
Difficulty : Difficult
AACSB: Analytic
56) Which of the following is not one of the types of internal audits?
A) reviewing corporate organizational structure and reporting hierarchies
B) examining procedures for reporting and disposing of hazardous waste
C) reviewing source documents and general ledger accounts to determine integrity of recorded transactions
D) comparing estimates and analysis made before purchase of a major capital asset to actual numbers and results achieved
Answer:
Page Ref: 304
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
57) When programmers are working with program code, they often employ utilities that are also used in auditing. For example, as program code evolves, it is often the case that blocks of code are superseded by other blocks of code. Blocks of code that are not executed by the program can be identified by
A) embedded audit modules.
B) scanning routines.
C) mapping programs.
D) automated flow charting programs.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
58) When programmers are working with program code, they often employ utilities that are also used in auditing. For example, as program code evolves, it is often the case that variables defined during the early part of development become irrelevant. The occurrences of variables that are not used by the program can be found using
A) program tracing.
B) scanning routines.
C) mapping programs.
D) embedded audit modules.
Answer:
Page Ref: 314
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
59) Explain the differences between each type of audit risk.
60) Explain why the auditor's role in program development and acquisition should be limited.
61) How and to whom does an auditor communicate the audit results?
62) Audit tests and procedures traditionally have been performed on a sample basis. Do options exist for auditors to test significantly more (or all) transactions?
63) When doing an information systems audit, auditors must review and evaluate the program development process. What errors or fraud could occur during the program development process?
64) Briefly describe tests that can be used to detect unauthorized program modifications.
65) Define and give examples of embedded audit modules.
66) How is a financial audit different from an information systems audit?
67) Why do all audits follow a sequence of events that can be divided into four stages, and what are the four stages?
68) Name and describe the different types of audits.
AACSB: Analytic
69) Describe the risk-based audit approach.
71) Describe the disadvantages of test data processing.
72) Describe how audit evidence can be collected.
Accounting Information Systems, 12e (Romney/Steinbart)
Chapter 12 The Revenue Cycle: Sales to Cash Collections
1) In organizations with at least basic segregation of duties, the credit manager reports to the ________ and the treasurer reports to the ________.
A) controller; vice president of finance
B) treasurer; controller
C) marketing manager; vice president of finance
D) treasurer; vice president of finance
Answer:
Page Ref: 331
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
2) In the revenue cycle, before a shipping notice is prepared, the shipping department personnel should match the inventory received from the warehouse to details from
A) picking tickets.
B) sales order and bill of lading.
C) sales order.
D) picking ticket and sales order.
Answer:
Page Ref: 345
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
3) Which is the best control to prevent invoicing customers for the quantity ordered, which was more than the quantity shipped due to items on backorder?
A) Use the information from the packing slip to prepare the sales invoice.
B) Use the information from the picking ticket to prepare the sales invoice.
C) Use the information from the bill of lading to prepare the sales invoice.
D) Use the information from the sales order to prepare the sales invoice.
Answer:
Page Ref: 350
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Reflective Thinking
4) The cashier deposits checks in the bank for Very Large Corporation (VLC) and also prepares payments to vendors. Of the following, who is best to reconcile the bank statement to VLC's records on a regular basis?
A) Internal audit department
B) Treasurer
C) External auditor
D) Cashier
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
5) Which of the following documents normally triggers the billing process in the revenue cycle?
A) Packing slip received from the shipping department
B) Sales order received from the sales department
C) Picking ticket received from the sales department
D) Journal voucher received from the shipping department
Answer:
Page Ref: 348
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
6) Which of the following documents would normally trigger the process to record a customer payment?
A) Remittance advice
B) Customer monthly statement
C) Deposit slip
D) Sales invoice
Answer:
Page Ref: 353
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
7) Which document should always be included with a merchandise shipment to a customer?
A) Packing slip
B) Picking ticket
C) Remittance advice
D) Sales invoice
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
8) A monthly statement sent to customers serves a control purpose by
A) providing an opportunity for customers to verify the balance owed and activity on the account.
B) triggering the process to record a customer payment.
C) summarizing invoices and amounts due for customers.
D) reminding customers of the balance due and due date.
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
9) Accounting recognizes a sale when
A) inventory becomes the legal property of the customer.
B) cash is received from the customer.
C) a sales order is approved by sales, inventory control, and credit departments.
D) inventory is removed from the warehouse.
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
10) Which of the following is not one of the controls for the mail room where customer payments are commingled with other mail?
A) Requiring the controller to be personally present when mail is received and opened
B) Preparing a remittance list as mail is opened
C) Restrictively endorsing checks when received
D) Requiring two mail room clerks to open mail together
Answer:
Page Ref: 337
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
11) What is the primary objective of the revenue cycle?
A) to maximize revenue and minimize expense
B) to reduce outstanding accounts receivable balances through increased cash sales
C) to provide the right product in the right place at the right time at the right price
D) to sell as much product as possible and/or to maximize service billings
Answer:
Page Ref: 332
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
12) Which of the decisions below is not ordinarily found as part of the revenue cycle?
A) What credit terms should be offered?
B) How often should accounts receivable be subjected to audit?
C) How can customer payments be processed to maximize cash flows?
D) What are the optimal prices for each product or service?
Answer:
Page Ref: 332-333
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
13) Which of the following is not a basic activity of the revenue cycle?
A) sales order entry
B) shipping
C) receiving
D) billing
Answer:
Page Ref: 333
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
14) Retail stores could send their orders directly to the manufacturer's sales order system in a format that would eliminate the need for data entry, using
A) Vendor Managed Inventory.
B) Electronic Data Interchange.
C) Point Of Sale.
D) Electronic Funds Transfer.
Answer:
Page Ref: 338
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
15) Matching customer account numbers and inventory item numbers to the numbers in the customer and inventory master files is an example of a
A) completeness test.
B) field check.
C) reasonableness test.
D) validity check.
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
16) During the sales order entry process, a ________ is performed to compare the quantity ordered with the standard amounts normally ordered.
A) completeness test
B) redundant data check
C) field check
D) reasonableness test
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
17) During the sales order entry process, a ________ is performed to verify that each transaction record contains all appropriate data items.
A) completeness test
B) redundant data check
C) field check
D) reasonableness test
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
18) When a customer places an order (on account) for a certain product, what should be done before the order is checked for inventory availability?
A) The customer's available credit should be checked.
B) The sales order should be created and written to a file.
C) Shipping should be notified of an order in process.
D) A picking list should be generated for the warehouse.
Answer:
Page Ref: 335
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) How is credit approval generally handled for established customers with a documented payment history?
A) Specific authorization by the credit manager
B) General authorization by a sales clerk
C) A new credit application is requested
D) A formal credit check should be made for each sale
Answer:
Page Ref: 340
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
20) What is a typical procedure for processing sales orders from new customers or customers making a purchase that causes their credit limit to be exceeded?
A) General authorization to approve the order is given to sales clerks.
B) Specific authorization must be granted by the credit manager.
C) The sale should be rejected.
D) The sales clerk should order a report from a credit bureau before approving the order.
Answer:
Page Ref: 340
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
21) A company should check inventory quantities before accepting a sales order for all the following reasons except to
A) verify the accuracy of the perpetual inventory records.
B) inform the customer about availability and delivery times.
C) know which items may need to be back ordered.
D) update inventory records to reduce the quantity available by the number of items ordered.
Answer:
Page Ref: 341-342
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
22) Responding to customer inquiries and general customer service is an important aspect in the revenue cycle. Since customer service is so important, software programs have been created to help manage this function. These special software packages are called
A) EDI systems.
B) POS systems.
C) VMI systems.
D) CRM systems.
Answer:
Page Ref: 343
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
23) The best solution for maintaining accurate automated perpetual inventory system is to use
A) closed-loop verification when inventory is received from vendors and recorded.
B) point of sale devices integrated with inventory records.
C) periodic physical counts to reconcile with perpetual inventory records.
D) RFID tags.
Answer:
Page Ref: 342
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
24) This document is a legal contract that defines responsibility for goods that are in transit.
A) packing slip
B) bill of lading
C) picking list
D) back order
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) Two documents usually accompany goods shipped to a customer. What are the two documents?
A) a bill of lading and an invoice
B) a packing slip and a bill of lading
C) an invoice and a packing slip
D) an invoice and a sales order
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
26) What is the basic document created in the billing process?
A) bill of lading
B) sales order
C) packing list
D) sales invoice
Answer:
Page Ref: 349
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
27) A company uses the method for tracking accounts receivable where customers pay according to individual sales invoices. This describes the ________ method.
A) monthly statement
B) open-invoice
C) balance forward
D) cycle billing
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
28) A method for tracking accounts receivable that matches specific invoices and payments from the customer is called a(n) ________ method.
A) specific identification
B) balance forward
C) cycle billing
D) open-invoice
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
29) The document a customer returns with their payment and that identifies the source and the amount of the payment is called a
A) remittance advice.
B) remittance list.
C) credit memorandum.
D) debit memorandum.
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
30) In the ________ method of tracking accounts receivable, customers pay according to the amount showing on their monthly statement and payments are applied against the total account balance.
A) specific identification
B) open-invoice
C) balance forward
D) remittance advice
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
31) When a customer pays off the balance on an invoice, the payment is credited to the ________ file.
A) customer master
B) sales transaction
C) cash receipts master
D) All of the above are correct.
Answer:
Page Ref: 351
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
32) A type of business document in which part of the original document is returned to the source for further processing is called a ________ document.
A) feedback
B) returnable
C) closed-loop
D) turnaround
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
33) A document typically encountered in the revenue cycle that is both an output document and a source document is the
A) sales invoice.
B) customer purchase order.
C) sales order.
D) packing slip.
Answer:
Page Ref: 349
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
34) A ________ system prepares and mails monthly statements to customers throughout the entire month, instead of just at the end of the month.
A) continuous
B) open-invoice
C) cycle billing
D) balance forward
Answer:
Page Ref: 351
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
35) The accounts receivable department must know when customers pay their invoices, yet segregation of duties controls dictate that the collection and recording functions be kept separate from each other. What is a solution to this potential internal control problem?
A) Have customers send a remittance advice with their payment.
B) Have mailroom personnel prepare a remittance list which can be forwarded to accounts receivable.
C) Establish a lockbox arrangement with a bank.
D) all of the above
Answer:
Page Ref: 353-354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
36) The benefits of a lockbox arrangement with a bank are maximized when
A) the bank is located nearby to the company, so remittance advices can be delivered to the company every day.
B) several banks around the country are used, in order to minimize the time payments spend in the mail.
C) an arrangement is made with only one bank, so all remittance advices can be batched for processing.
D) the bank deposits the payments and accesses the customer's information system to record the payments.
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
37) An arrangement where a bank receives customer payments through the postal system, scans the remittance advices, and transmits payment data to the business electronically is known as
A) e-commerce.
B) an electronic lockbox.
C) electronic funds transfer (EFT).
D) electronic data interchange (EDI).
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
38) Customers that send their payments electronically directly to the company's bank are using
A) electronic data interchange (EDI).
B) electronic funds transfer (EFT).
C) procurement cards.
D) an electronic lockbox.
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
39) A way to incorporate the advantages of Electronic Data Interchange with the Electronic Funds Transfer is
A) Financial Electronic Data Interchange.
B) e-commerce.
C) to use procurement cards.
D) an electronic lockbox.
Answer:
Page Ref: 354
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
40) Key differences exist when an integrated Enterprise Resource Planning system (ERP) replaces an existing AIS or legacy system. For example, ________ are more accurate and timely, enabling sales order entry staff to provide customers more accurate information about delivery dates.
A) inventory records
B) cash receipts
C) credit approval decisions
D) exception reports
Answer:
Page Ref: 342
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
41) When an ERP is used, it is assumed that there will be increases in efficiency and the effectiveness of the activities related to the revenue cycle. However, what must be in place and functioning well to fully realize these benefits?
A) an effective marketing staff
B) all the components of the expenditure cycle
C) adequate controls
D) adequate system flowchart documentation
Answer:
Page Ref: 335
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
42) The activities involved in soliciting and processing customer orders within the revenue cycle are known as the ________.
A) sales order entry process
B) shipping order process
C) revenue process
D) marketing process
Answer:
Page Ref: 337
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
43) To ensure proper segregation of duties, only the ________ has authority to issue credit memos.
A) accounts receivable supervisor
B) controller
C) credit manager
D) cashier
Answer:
Page Ref: 352
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
44) It has been discovered that credit sales have been made to customers with a poor credit rating. If this continues, the company will face increasing uncollectible receivables and losses due to bad debts. Separation of duties between ________ and ________ should help resolve the problem.
A) shipping; billing duties
B) credit approval; marketing
C) billing; credit approval
D) marketing; accounts receivable
Answer:
Page Ref: 340
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
45) Consider the following revenue cycle scenario: The company has been exposed to customer dissatisfaction and the suggested control procedure to be implemented is to install and use bar-code scanners. What is the threat?
A) The company may be shipping the wrong merchandise.
B) The company may be shipping the wrong quantities of merchandise.
C) The company may be shipping orders to the wrong address.
D) All of the above threats may apply to this scenario.
Answer:
Page Ref: 345
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
46) Which of the following would be the least effective control to minimize the loss of inventory?
A) Secure the storage location of inventory.
B) Release inventory only with proper documentation.
C) Periodically back up all perpetual inventory records.
D) Reconcile the physical counts with and perpetual records.
Answer:
Page Ref: 345
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
47) Separating the shipping and billing functions is designed to reduce the threat of
A) failure to bill customers.
B) billing customers for wrong quantities.
C) billing customers before merchandise has been shipped.
D) shipping the wrong merchandise.
Answer:
Page Ref: 350
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
48) All of the following edit checks for online editing of accounts receivable transactions would probably be included except
A) validity checks on customer ID and invoice numbers.
B) check digit verification on the amount of the sale.
C) closed loop verification on the customer ID.
D) field checks on the values in dollar fields.
Answer:
Page Ref: 352
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
49) When a proper segregation of duties exists in the area of handling cash receipts, the ________, who reports to the ________, actually handles the cash and is not the same person who posts cash receipts to customer accounts.
A) cashier; treasurer
B) cashier; controller
C) accountant; treasurer
D) accountant; controller
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
50) In a revenue cycle with proper controls, the ________ who reports to the ________, is not involved in any cash handling activities.
A) accounts receivable clerk; treasurer
B) accounts receivable clerk; controller
C) cashier; controller
D) cashier; treasurer
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
51) A serious exposure in the revenue cycle is loss of assets. What is the related threat and applicable control procedure that address this exposure?
A) shipping errors; reconciliation of sales order with picking ticket and packing slip
B) theft of cash; segregation of duties and minimization of cash handling
C) making sales that turn out to be uncollectible; force sales people to make collection calls on customers with past due balances
D) poor performance; preparation and review of performance reports
Answer:
Page Ref: 337
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
52) Which of the following duties could be performed by the same individual and not violate segregation of duty controls?
A) handling cash and posting to customer accounts
B) issuing credit memos and maintaining customer accounts
C) handling cash and authorizing credit memos
D) handling cash receipts and mailing vendor payments
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
53) To prevent the loss of valuable data in the revenue cycle, internal file labels can be used to
A) keep competitors from accessing files.
B) record off-site storage locations.
C) organize the on-site physical storage site.
D) reduce the possibility of erasing important files.
Answer:
Page Ref: 277, 335
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
54) The manager of Callow Youth Clothing was entering an order online from Sad Clown Pajamas. He ordered 100 one-size fits all pajama bottoms, but when he ordered 1000 one-size fits all pajama tops, the following error message popped up: "Did you mean to enter a quantity of 1000 for your order?" This message is the result of a
A) reasonableness test.
B) validity check.
C) limit check.
D) closed-loop verification.
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Reflective Thinking
55) The manager of Callow Youth Clothing was entering an order online from Sad Clown Pajamas. He entered all the items and quantities, completed the checkout and payment process, but the following error message popped up when he tried to exit the site: "Please enter your email address." This message is likely the result of a
A) customer relationship management software application.
B) validity check.
C) completeness test.
D) closed-loop verification.
Answer:
Page Ref: 339
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Reflective Thinking
56) Sad Clown Pajamas is an Internet-based wholesaler. Customers enter their orders online. The manager of Callow Youth Clothing was entering an order when the following error message popped up: "Your total order exceeds your available credit. A Credit Department representative will contact you within 24 hours." This message is the result of a
A) validity check.
B) reasonableness test.
C) limit check.
D) sign check.
Answer:
Page Ref: 340
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
57) In Petaluma, California, electric power is provided to consumers by the Power To The People Electrical Company, a local co-op. Each month PTTP mails bills to 70,000 households and then processes payments as they are received. The customers are provided with a remittance advice, which is a
A) warning that failure to pay by the due date will result in a late charge.
B) confirmation of the firm's privacy policy.
C) turnaround document.
D) bill.
Answer:
Page Ref: 350
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
58) Laz Chance wears roller blades and headphones when he is at work at the Squishy Things Toy Company. He is a product packer. The headphones give him computer-generated instructions so he knows the location of each item and quantity that should be included in the order. These instructions are the equivalent of a
A) picking ticket.
B) bill of lading.
C) packing slip.
D) sales order.
Answer:
Page Ref: 342
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
59) The shipping department at Squishy Things Toy Company follows policies that determine which carrier will deliver orders according to the size, weight, and destination of the shipment. It maintains standing agreements with shippers that specify legal responsibility for the shipment while it is in transit. The terms of the agreements are documented on
A) picking tickets.
B) bills of lading.
C) packing slips.
D) RFID tags.
Answer:
Page Ref: 345
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
60) Sad Clown Pajamas is an Internet-based wholesaler. The manager of Callow Youth Clothing received an order from Sad Clown and found that the wrong product had been shipped. He repackaged the order and sent it back for a refund. When Sad Clown Pajamas received the returned product, they mailed a ______ to Callow Youth Clothing's manager.
A) packing slip
B) letter requesting an explanation
C) remittance advice
D) credit memo
Answer:
Page Ref: 352
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
61) A customer service manager at Sad Clown Pajamas, Bob, received a call from the manager at Callow Youth Clothing, who informed Bob that Callow was entering bankruptcy liquidation and it was unlikely that they would be able to pay the outstanding balance on their account. Bob should
A) document the phone conversation and forward it to the billing department manager.
B) prepare a credit memo.
C) approve a credit memo.
D) document the phone conversation and forward it to the credit department manager.
Answer:
Page Ref: 352
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Reflective Thinking
62) Because it is the most fungible of all assets, the management of cash has always been the most difficult of all control issues. The most important of cash controls is
A) minimization of cash handling.
B) lockbox arrangements.
C) segregation of duties.
D) frequent reconciliation of records.
Answer:
Page Ref: 355
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
63) A sales clerk at an electronics store scanned the bar code for a low cost set of headphones and then substituted a high cost set of headphones for his friend, who paid the lower price. Which of the following controls would best help to prevent this sort of fraud?
A) Use of RFID tags
B) Physical inventory count
C) Segregation of duties
D) Limited physical access to bar codes
Answer:
Page Ref: 342
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
64) The accounts receivable management method typically used by credit card companies is
A) balance forward.
B) postbilling.
C) monthly statement.
D) open-invoice.
Answer:
Page Ref: 351
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
65) The accounts receivable clerk destroys all invoices for sales made to family and friends and does not record the sales in the accounts receivable subsidiary ledgers. The family and friends usually give the clerk cash as a"thank you". Which procedure will not prevent or detect this fraud?
A) Send monthly statements to all customers with balances owed.
B) Reconcile sales invoices in the billing department to the total debits to accounts receivable subsidiary ledgers.
C) Sequentially prenumber all invoices and prepare a sequence check at the end of each day.
D) Reconcile the accounts receivable control account to the accounts receivable subsidiary ledger.
Answer:
Page Ref: 350
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
66) Which of the following poses an internal control problem?
A) Physical inspection of inventory quantity and condition is outsourced to a firm that specializes in this service.
B) Products are released from inventory after a warehouse employee and a shipping clerk both sign the pick list.
C) Sales representatives have authority to increase customers' credit limits in $1,000 increments.
D) When customer payments are received in the mail, checks are sent to the cashier's office and remittance advices are sent to the accounts receivable department.
Answer:
Page Ref: 340
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
67) For sales returns, the least effective control to prevent fraudulent processing of a credit memo is to
A) reconcile total of credit memos to total debits posted to customers' subsidiary ledgers.
B) require approval for each credit memo by the credit manager.
C) sequentially prenumber all credit memos and perform a sequence check at the end of each day.
D) match each credit memo with a receiving report.
Answer:
Page Ref: 352
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
68) Describe the basic revenue cycle activities.
69) Explain how validity checks, completeness tests and reasonableness tests can be implemented to ensure accuracy of customer orders.
70) Define and describe benefits of a CRM system.
71) How can Electronic Data Interchange (EDI) facilitate the billing and accounts receivable process?
72) Describe typical credit approval procedures.
73) Describe the two methods to manage accounts receivable.
74) Describe cycle billing and identify how an organization might benefit by using cycle billing.
75) Failure to collect cash on credit sales is a threat in the revenue cycle. What controls can be used to help neutralize this threat?
76) Discuss ways in which technology can be used to streamline cash collections.
77) Describe four threats in the revenue cycle and identify appropriate controls for each threat.
78) Discuss the general control issue of the loss of data, as it relates to the revenue cycle.
79) Explain how to effectively segregate duties in the sales order activity.
80) Discuss the revenue cycle threat of stockouts, carrying costs, and markdowns.
81) You have been hired by a catalog company to computerize its sales order entry process. Approximately 70% of all orders are received over the telephone by a sales person. The other 30% of orders are received by a sales person through mail or fax. The catalog company wants the phone orders processed real-time. The mail and fax orders will be processed in batches of 50 orders. The following attributes are collected for every sales order:
Customer number (if the order is from a new customer, a new number needs to be assigned)
Customer name
Address
Payment method (credit card for phone and fax orders and check for mailed orders)
Credit card number and expiration date
Items ordered and quantity of each
Unit price of each item ordered
Identify and describe at least ten specific control policies and procedures you will implement for the sales order process. Be very specific describing the controls and number each new control you suggest.
Accounting Information Systems, 12e (Romney/Steinbart)
Chapter 13 The Expenditure Cycle: Purchasing to Cash Disbursements
1) The Squishy Things Toy Company was established in 1948. It recently signed a large contract with a chain of retail toy stores. As a condition of the contract, the Squishy will be required to track and forecast product sales by linking in to the chain's sales database. Squishy will then be responsible for shipping products to the chain's regional warehouses as needed. The relationship between Squishy and the chain is an example of
A) vendor-managed inventory.
B) sales force automation.
C) electronic data interchange.
D) optical character recognition.
Answer:
Page Ref: 382
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
2) Requiring all packing slips be reconciled to purchase orders before accepting a delivery of inventory would be most likely to prevent which of the following situations?
A) A supplier delivers more inventory than ordered at the end of the year and sends an invoice for the total quantity delivered.
B) An employee mails a fake invoice to the company, which is then paid.
C) The inventory records are incorrectly updated when a receiving department employee enters the wrong product number on the receiving report.
D) Receiving department employees steal inventory and then claim the inventory was received and delivered to the warehouse.
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
3) Comparing quantities on a vendor invoice to quantities on the receiving report would not prevent or detect which of the following situations?
A) Receiving and accepting inventory not ordered
B) Theft of inventory by receiving department employees
C) Update of wrong inventory items due to data entry error
D) Order for an excessive quantity of inventory
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
4) Which of the following would probably be the least effective control to mitigate the risk of paying an invoice payable to a phony vendor for inventory purchases, mailed to the company by an employee attempting to commit fraud?
A) Only pay from original invoices.
B) Cancel all invoices and supporting documentation when paid.
C) Strict access and authorization controls for the approved vendor master file.
D) Require three-way match for all inventory purchase invoices.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
5) Which of the following would be the least effective control to prevent paying the same vendor invoice twice?
A) Allow only the accounts payable department to authorize payment for vendor invoices and allow only the cash disbursements department to cut and mail checks to vendors.
B) Only pay from original invoices.
C) Cancel each document in the voucher package once the check is prepared and mailed.
D) Only pay vendor invoices that have been matched and reconciled to a purchase order and a receiving report.
Answer:
Page Ref: 391
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
6) To accomplish the objectives set forth in the expenditure cycle, a number of key management decisions must be addressed. Which of the decisions below is not ordinarily found as part of the expenditure cycle?
A) How can cash payments to vendors be managed to maximize cash flow?
B) What is the optimal level of inventory and supplies to carry on hand?
C) Where should inventories and supplies be held?
D) What are the optimal prices for each product or service?
Answer:
Page Ref: 372
Objective: Learning Objective 2
Difficulty : Easy
AACSB: Analytic
7) One of the basic activities in the expenditure cycle is the receiving and storage of goods, supplies, and services. What is the counterpart of this activity in the revenue cycle?
A) sales order entry process
B) shipping function
C) cash collection activity
D) cash payments activity
Answer:
Page Ref: 373
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
8) The traditional approach to inventory management to ensure sufficient quantity on hand to maintain production is known as
A) safety stock.
B) just-in-time production.
C) economic order quantity.
D) optimal inventory quantity.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
9) Economic Order Quantity (EOQ) includes several variables that must be taken into consideration when calculating the optimal order size. One variable, the costs associated with holding inventory, is referred to as
A) ordering costs.
B) carrying costs.
C) the reorder point.
D) stockout costs.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
10) The need to place an order for inventory is specified by the
A) company inventory policies.
B) economic order quantity.
C) stockout point.
D) reorder point.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
11) When goods are being ordered from a vendor, which electronic files are either read or updated?
A) inventory, vendors, and accounts payable
B) vendors and accounts payable
C) open purchase orders and accounts payable
D) inventory, vendors, and open purchase orders
Answer:
Page Ref: 374
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
12) What is a key feature of materials requirements planning (MRP)?
A) minimize or entirely eliminate carrying and stockout costs
B) reduce required inventory levels by scheduling production rather than estimating needs
C) determine the optimal reorder point
D) determine the optimal order size
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
13) Materials requirements planning (MRP)
A) reduces the uncertainty about when materials are needed, thereby reducing the need to carry large levels of inventory.
B) is able to compute exactly the cost of purchasing by taking into account all costs associated with inventory carrying.
C) requires vendors to deliver inventory to the production site exactly when needed and in the correct quantities.
D) None of the above are correct.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
14) The inventory management approach that attempts to minimize, if not eliminate, carrying and stockout costs is
A) materials requirements planning.
B) economic order quantity.
C) just-in-time inventory.
D) evaluated receipt settlement.
Answer:
Page Ref: 378
Objective: Learning Objective 1
Difficulty : Difficult
AACSB: Analytic
15) What aspect below best characterizes a Just-In-Time (JIT) inventory system?
A) frequent deliveries of smaller quantities of items to the work centers
B) frequent deliveries of large quantities to be held at the work centers
C) less frequent deliveries of large quantities of goods to central receiving
D) infrequent bulk deliveries of items directly to work centers
Answer:
Page Ref: 378-379
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
16) What is the key difference between the MRP and JIT inventory management approaches?
A) Only JIT reduces costs and improves efficiency.
B) MRP is especially useful for products such as fashion apparel.
C) JIT is more effectively used with products that have predictable patterns of demand.
D) MRP schedules production to meet estimated sales needs; JIT schedules production to meet customer demands.
Answer:
Page Ref: 379
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
17) MRP will be a preferred method over JIT when the
A) demand for inventory is fairly predictable.
B) demand for inventory is mostly unpredictable.
C) product has a short life cycle.
D) MRP is always a preferred method over JIT.
Answer:
Page Ref: 379
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
18) A key decision in ordering is selecting a suitable vendor. Which of the following would not be a major criterion in vendor selection?
A) prices of goods
B) quality of goods
C) credit rating of the vendor
D) ability to deliver on time
Answer:
Page Ref: 380
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
19) Once a vendor is selected for a product, the vendor's identity is recorded in the
A) purchase requisition transaction file.
B) purchase requisition master file.
C) inventory transaction file.
D) inventory master file.
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
20) A purchase order is
A) a document formally requesting a vendor to sell a certain product at a certain price.
B) a request for delivery of certain items and quantities.
C) a contract between the buyer and vendor once accepted by the vendor.
D) All of the above are true.
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
21) Stepanek Sales and Service provides free coffee to employees. Stepanek arranged with Ingebrigtson's Joe to deliver as many coffee packages, sugar, creamer, and filters as needed each week. Ingebrigtson's sends a monthly invoice for Stepanek to pay. This arrangement is best described as a
A) blanket purchase order.
B) set purchase order.
C) fixed purchase order.
D) standard purchase order.
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
22) A major cost in the purchasing function is the number of purchase orders processed. One technique that may reduce purchasing-related expenses is to have suppliers compete with each other to meet demand at the lowest price. This name of this technique is
A) an EDI auction.
B) a trading exchange.
C) a reverse auction.
D) a supplier consortium.
Answer:
Page Ref: 382
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
23) One of the major responsibilities of the receiving department is
A) deciding if the delivery should be accepted.
B) verifying any purchase discounts for the delivery.
C) deciding on the location where the delivery will be stored until used.
D) updating inventory subsidiary ledgers.
Answer:
Page Ref: 384
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
24) Which of the following is generally not shown on a receiving report?
A) price of the items
B) quantity of the items
C) purchase order number
D) counted and inspected by
Answer:
Page Ref: 384
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
25) A receiving clerk notes that a delivery of 10 units has been received, but the purchase order specified 12 units. A debit memo will need to be prepared to adjust for the difference between the quantity ordered and received. Who should prepare this document?
A) the receiving clerk
B) the controller
C) the vendor
D) the purchasing department manager
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
26) Identify in which of the following scenarios a company could adjust the balance due the vendor by issuing a debit memo.
A) quantity different from that ordered
B) damage to the goods
C) goods that fail inspection for quality
D) All of the above are possible scenarios.
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
27) What is one of the best ways to improve the overall efficiency and effectiveness of the receipt and storage of ordered items?
A) requiring all suppliers to have the carrier verify quantities and item numbers before shipment
B) requiring all suppliers to include RFID tags on their items
C) requiring all suppliers to use EDI to expedite the receiving department function
D) requiring all delivery trucks to have satellite data terminals to expedite the receiving department function
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
28) Vendor invoices are approved by the ________, which reports to the ________.
A) purchasing department; controller
B) accounts payable department; treasurer
C) purchasing department; treasurer
D) accounts payable department; controller
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
29) The disbursement voucher and supporting documents are sent to the ________ for payment prior to the due date.
A) cashier
B) treasurer
C) controller
D) accounts payable department
Answer:
Page Ref: 390
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
30) A(n) ________ system posts an approved invoice to the vendor account and stores it in an open invoice file until payment is made by check.
A) nonvoucher
B) voucher
C) cycle
D) evaluated receipt settlement
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
31) A disbursement voucher contains
A) a list of outstanding invoices.
B) the net payment amount after deducting applicable discounts and allowances.
C) the general ledger accounts to be debited.
D) All of the above are correct.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
32) One objective of accounts payable is to authorize payment only for goods or services actually ordered and received. The best way to process supplier invoices is to use
A) electronic funds transfer for small, occasional purchases from suppliers.
B) a nonvoucher system.
C) EDI for all small, occasional purchases from suppliers.
D) a disbursement voucher system.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
33) What is not an advantage of using disbursement vouchers?
A) Disbursement vouchers reduce the number of checks written.
B) Disbursement vouchers can be prenumbered which simplifies the tracking of all payables.
C) Disbursement vouchers facilitate separating the time of invoice approval from the time of invoice payment.
D) There are no disadvantages to using disbursement vouchers.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
34) Which of the following is not an advantage of a voucher system?
A) Several invoices may be included on one voucher, reducing the number of checks.
B) Disbursement vouchers may be pre-numbered and tracked through the system.
C) The time of voucher approval and payment can be kept separate.
D) It is a less expensive and easier system to administer than other systems.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
35) Duties in the expenditure cycle should be properly segregated to promote internal control. This means that the authorization function is performed by ________, the recording function is performed by ________, and cash handling is performed by the ________.
A) accounts payable; purchasing; cashier
B) purchasing; accounts payable; cashier
C) purchasing; cashier; accounts payable
D) purchasing; accounts payable; treasurer
Answer:
Page Ref: 375
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
36) A voucher package should include
A) a purchase requisition, vendor invoice, and receiving report.
B) a purchase order, vendor invoice, and receiving report.
C) a purchase requisition, purchase order, and receiving report.
D) a bill of lading and vendor invoice.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
37) Evaluated receipt settlement (ERS) approves payment of vendor invoices after reconciling the purchase order and the
A) vendor invoice.
B) sales invoice.
C) receiving report.
D) disbursement voucher.
Answer:
Page Ref: 388
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
38) All of the following are opportunities to improve efficiency of the accounts payable function except
A) use blanket purchase orders.
B) convert a manual AIS system to EDI and EFT.
C) streamline noninventory purchases.
D) use evaluated receipt settlement.
Answer:
Page Ref: 387-388
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
39) When purchasing miscellaneous supplies, companies can reduce costs, improve efficiency, and combat employee fraud by
A) using procurement cards.
B) implementing a JIT inventory system.
C) requiring employees to personally purchase items then reimbursing employees at the end of each month.
D) paying amounts out of petty cash.
Answer:
Page Ref: 389
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
40) If available, a 1% discount for payment within 10 days instead of 30 days represents an approximate savings of ________ % annually.
A) 1
B) 12
C) 18
D) 36
Answer:
Page Ref: 390
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
41) What is the best control to mitigate the threat of paying prices that are too high for goods ordered?
A) require the receiving department to verify the existence of a valid purchase order
B) use only approved suppliers and solicit competitive bids
C) only pay invoices that are supported by the original voucher package
D) use bar-code technology to eliminate data entry errors
Answer:
Page Ref: 382
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
42) What is probably the most effective control for the prevention of kickbacks to purchasing agents?
A) purchasing from approved vendors
B) diligent supervision in the purchasing department
C) a corporate policy to prohibit purchasing agents from accepting kickbacks
D) reviews of vendor performance
Answer:
Page Ref: 383
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
43) One of the threats associated with the process and activity of receiving and storing goods is
A) errors in counting.
B) kickbacks.
C) requests for unnecessary items.
D) errors in vendor invoices.
Answer:
Page Ref: 385
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
44) What is the best way to prevent the acceptance of unordered goods?
A) Order only from approved vendors.
B) Match the packing slip to a purchase order before accepting delivery.
C) Enforce an appropriate conflict of interest policy in place.
D) Require specific authorization from the purchasing manager before accepting any goods.
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
45) Which of the following is not a common control for ensuring inventory is secure and inventory counts are accurate?
A) control of physical access to the inventory storage areas
B) transfers of inventory with proper documentation
C) sending "blind" copies of purchase orders to inventory control for data entry
D) making physical counts of inventory at least once per year
Answer:
Page Ref: 376
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
46) Double-checking the accuracy of an invoice is a control that can help to neutralize a threat in the expenditure cycle. What activity would specifically be associated with this control?
A) ordering goods
B) receiving and storing goods
C) paying for goods and services
D) requesting goods be ordered
Answer:
Page Ref: 389
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
47) What control would best mitigate the threat of paying an invoice twice?
A) never authorize payment of a photocopy of an invoice
B) double-check mathematical accuracy of invoices
C) approval of purchase orders
D) maintaining adequate perpetual inventory records
Answer:
Page Ref: 391
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
48) Which control would best prevent payments made to fictitious vendors?
A) Allow payments only to approved vendors.
B) Restrict access to any payment or approval documents.
C) Have an independent bank reconciliation.
D) Make sure all documents are in order before approving payments.
Answer:
Page Ref: 392
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
49) In the expenditure cycle, good control dictates that expenditures should be paid by check. This may not be feasible when minor purchases are made. To facilitate quick payment for minor purchases, a(n) ________ should be set up and maintained using ________.
A) special bank account; disbursement vouchers
B) imprest fund; vouchers
C) cash box; small denomination bills
D) petty cash fund; procurement cards
Answer:
Page Ref: 392
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
50) A surprise count of an imprest petty cash fund should find the total of ________ equal to the amount authorized for the fund.
A) cash and credit memos
B) cash and vouchers
C) cash
D) cash and checks
Answer:
Page Ref: 392
Objective: Learning Objective 3
Difficulty : Easy
AACSB: Analytic
51) What control should be put in place that assigns responsibility for EFT payments made to vendors?
A) Encrypt all EFT transmissions.
B) Time stamp all EFT transactions.
C) Establish a control group to monitor EFT transactions for validity and accuracy.
D) Number all EFT transactions.
Answer:
Page Ref: 391
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
52) Which of the following threats is not specific to the purchase requisition process of the expenditure cycle?
A) stockouts
B) purchasing from unauthorized vendors
C) requisitioning goods not needed
D) All of the above are threats in the purchase requisition process.
Answer:
Page Ref: 380
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
53) There is a symmetrical interdependence between a firm's expenditure cycle and its suppliers'
A) production cycle.
B) revenue cycle.
C) expenditure cycle.
D) general ledger and reporting system.
Answer:
Page Ref: 372
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
54) The Squishy Things Toy Company was established in 1948. It recently signed a large contract with a chain of retail toy stores. As a condition of the contract, the Squishy will be required to track and forecast product sales by linking in to the chain's sales database. Squishy will then be responsible for shipping products to the chain's regional warehouses as needed. The technology that is used for communication between Squishy and the chain is
A) vendor-managed inventory.
B) sales force automation.
C) electronic data interchange.
D) optical character recognition.
Answer:
Page Ref: 372
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
55) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on ensuring that the amounts purchased minimize these costs, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
56) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on ensuring that orders are placed with sufficient lead time to prevent stockouts, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
57) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on forecasting demand for Sad Clown's products, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
58) The management at Sad Clown Pajamas, an Internet-based wholesaler, is considering a new inventory control system. The current system is inadequate because it results in stockouts that interrupt production and excess stocks of some materials that result in markdowns and high carrying costs. The new system, which will focus on reducing or completely eliminating carrying costs, will employ
A) a just-in-time inventory system.
B) the economic order quantity.
C) a reorder point.
D) materials requirements planning.
Answer:
Page Ref: 378
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
59) Bob Chum is the sales manager at Folding Squid Technologies. At lunch with the company CEO, he proudly announced that he had negotiated a(n) ________ with a client that defined a long-term commitment to buy components from Folding Squid.
A) purchase order
B) blanket purchase order
C) evaluated receipt settlement
D) voucher
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
60) Bob Chum is the sales manager at Folding Squid Technologies. At lunch with the company CEO, he proudly announced that he had received a ________ from a client to buy a large quantity of components from Folding Squid.
A) purchase order
B) blanket purchase order
C) voucher
D) purchase requisition
Answer:
Page Ref: 381
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
61) Bob Chum is the sales manager at Folding Squid Technologies. At lunch with the company CEO, he complained that a recent shipment from a vendor had been unsatisfactory and so had to be returned. That required the purchasing manager to send a ________ to the supplier.
A) purchase order
B) blanket purchase order
C) receiving report
D) debit memo
Answer:
Page Ref: 385
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
62) To minimize the number of checks that need to be written to pay vendor invoices a company should use a
A) voucher system.
B) just-in-time inventory system.
C) nonvoucher system.
D) evaluated receipt settlement system.
Answer:
Page Ref: 387
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
63) Evaluated receipt settlement increases efficiency by
A) eliminating the need for receiving reports.
B) eliminating the need for vendor invoices.
C) eliminating the need for purchase orders.
D) eliminating the need to prepare and mail checks.
Answer:
Page Ref: 388
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
64) In the expenditure cycle, Financial Electronic Data Interchange (FEDI) increases efficiency by
A) eliminating the need for receiving reports.
B) eliminating the need for vendor invoices.
C) eliminating the need for purchase orders.
D) eliminating the need to prepare and mail checks.
Answer:
Page Ref: 390
Objective: Learning Objective 1
Difficulty : Easy
AACSB: Analytic
65) Procurement cards differ from corporate credit cards in which of the following ways?
A) Credit limits can be set for procurement cards, but not corporate credit cards.
B) Credit cards can be used to make purchases without an explicit sign off by supervisors, but procurement cards require a sign off.
C) Procurement cards can only be used with approved vendors, but credit cards can be used anywhere.
D) Procurement card invoices are sent separately for each card, whereas corporate credit cards are consolidated into a single invoice.
Answer:
Page Ref: 389
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Analytic
66) The purchasing manager at Folding Squid Technologies has responsibility for reviewing and authorizing purchase orders. He also reviews receiving reports, approves or corrects them, and authorizes the cashier to pay vendor invoices. Which of the following would correct control weaknesses, if any, related to these activities?
A) Vendor invoices should be reviewed by the purchasing manager to ensure that they are correct.
B) Accounts payable should reconcile purchase orders, receiving reports, and invoices.
C) Vendor invoices should be reviewed by accounts receivable and then cancelled when paid.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
67) The purchasing manager at Folding Squid Technologies has responsibility for reviewing and authorizing purchase orders. Receiving reports are prepared by shipping and receiving based on the relevant purchase order(s). Purchase orders, receiving reports, and vendor invoices are reconciled by accounts payable, which authorizes payment. Which of the following would correct control weaknesses, if any, related to these activities?
A) Vendor invoices should be reviewed by the purchasing manager to ensure that they are correct.
B) Accounts payable should authorize purchase orders.
C) Receiving reports should be reviewed and corrected by the purchasing manager.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
68) The receiving clerk at Folding Squid Technologies examines incoming shipments and reconciles their contents with the relevant purchase orders. A receiving report is then sent to accounts receivable and the vendor's invoice is approved for payment. Which of the following would correct control weaknesses, if any, related to these activities?
A) The invoice should be approved for payment by the shipping clerk after the purchase order and receiving report are reconciled.
B) Accounts payable should reconcile the purchase order and the receiving report.
C) Invoices, purchase orders, and receiving reports should be reconciled by the receiving clerk.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
69) The receiving clerk at Folding Squid Technologies examines incoming shipments and checks their purchase order numbers. A receiving report is then sent to accounts payable, where it is reconciled with the relevant purchase orders and invoices and payment is authorized. Which of the following would correct control weaknesses, if any, related to these activities?
A) Vendor invoices should be approved for payment by the shipping clerk after the purchase order and receiving report are reconciled.
B) Vendor invoices should be approved for payment by the purchasing manager.
C) Purchase orders and receiving reports should be reconciled by the purchasing manager.
D) Controls are adequate under the current system.
Answer:
Page Ref: 387
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Analytic
70) Which of the controls below would be least effective to prevent ordering goods at higher than market prices?
A) Variance analysis of actual expenses to budgeted expenses
B) For high-dollar goods, solicit competitive bids from possible vendors
C) Only place orders with vendors on an approved vendor list
D) Frequent review of, and update to, vendor price lists stored in the AIS
Answer:
Page Ref: 382
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
71) The document below would be known as what by Alpha Omega Electronics?
A) Receiving report
B) Purchase order
C) Purchase requisition
D) Packing slip
Answer:
Page Ref: 384
Objective: Learning Objective 1
Difficulty : Moderate
AACSB: Reflective Thinking
72) Which of the following would be the best control to prevent receiving department employees from stealing inventory and claiming the ordered quantity wasn't received from the vendor?
A) Reconcile quantity on packing slip to physical count when accepting delivery.
B) Restrict physical access to the receiving area.
C) Require all deliveries be made at the receiving area.
D) Require dual signatures on the move ticket when receiving delivers the inventory to the warehouse.
Answer:
Page Ref: 386
Objective: Learning Objective 3
Difficulty : Moderate
AACSB: Reflective Thinking
73) Define and describe the EOQ approach to inventory management.
74) Discuss the differences between EOQ, MRP, and JIT.
75) a) What is the major cost driver in the purchasing function? b) Describe how information technology can be used to control this cost driver.
76) Explain what is meant by the expenditure cycle as a "mirror image" of the revenue cycle.
77) Identify possible problems associated with receiving goods and appropriate actions in response to the problems.
78) How can information technology be used to improve the vendor invoice approval process?
79) Under what conditions is MRP more suitable than JIT and vice versa?
80) In the expenditure cycle, the majority of payments made are by check. What are some control issues related to payment of vendors by check?
81) Identify ten threats and applicable control procedures in the expenditure cycle.
82) What types of decision-making and strategic information should the AIS provide in the expenditure cycle?
83) How can using RFID tags or bar codes on goods or products provide significant benefit in the expenditure cycle?
0 notes
Text
Non-Sequential [Ch. 29]
Pairing: Pre-Serum Steve Rogers/Steve Rogers x Reader
One night, Steve Rogers met a beautiful dame named Y/N. He hadn’t intended on letting her get away. But fate had other ideas. Y/N appeared and disappeared in his life so hauntingly that Steve started to wonder if she was an angel meant to watch over him.
Word Count: 2,500
Chapter 28

The next 5 years simultaneously felt like they were moving too fast and too slowly.
Steve wondered if there would be limited visits from Y/N or if this was the rest of his life: just holding onto the past and praying that the next time she would stay for good.
But he knew that would never happen.
She would always leave.
Steve felt like he had returned to his teenage years when Y/N had first started visiting him. But watching her go now hurt a 100 times worse than back then. During that time, he hadn’t acknowledged that he loved her. He didn’t know what it was like to fully have her.
What he would give to regain that naivety. He didn’t know how much longer he could handle such torture.
When Y/N did visit the present, Steve tried to seize it as much as he could. He tried to act normal, wait for Y/N to ask the questions so he could figure out what she knew and what she didn’t. By some miracle, she always knew about the snap.
Steve felt lucky, he wouldn’t know how to handle her naivety to how she would die. Nat always told him he was a terrible liar. He could only assume lying to the woman he loved would be even worse.
Steve was sitting at his window, staring out at Brooklyn. There was a steaming cup of coffee in his hand and he was waiting for it to cool down. The sun had just rose past the horizon. Most of the city was still sleeping. He started to enjoy watching it slowly wake up. It was one of the very few joys he found these days.
“Steve?” Her voice whispered from behind him.
He jumped at the sound, shooting to his feet and turning around.
In the process, he spilled some of the coffee on his hand and bare feet.
He hissed at the burn.
“Oh, shit. I’m so sorry!” Y/N rushed forward.
Steve was both so surprised to see her and feel the boiling liquid on his skin that he didn’t realize Y/N was still completely naked.
“I’m fine. It’s OK.” He tried to tell her, only looking into her eyes.
One time Sam asked about the binding nudity that came with Y/N’s time traveling. He asked about it in a way that wasn’t really a question, but like he clearly wanted Steve to comment on it.
“Just so we’re clear, you’re asking what I think about my girlfriend being forced to be naked when she’s also forced to time travel at any given moment to a place she doesn’t know? Did I get that right?” He’d said it with the classic Steve Rogers sass.
But Sam got the point and never brought it up again.
Y/N’s nudity wasn’t something sexualized by Steve. He’d grown used to it. He assumed most people saw their naked wives and girlfriends, and only linked it to sex. But all it did for Steve was remind him of Y/N’s vulnerability.
Her skin was unprotected from the elements. That’s why she had almost frozen to death during the first time she ever traveled.
Her skin attracted unwanted attention. Steve would never forget when Y/N appeared at his military camp, standing innocently in front of an army that hadn’t felt a woman’s touch or seen a female body in months. He didn’t like to think what could’ve happened if Bucky hadn’t been there to look out for her.
Her skin reminded Steve that even though she didn’t don a uniform, there was still something about her that forced her to be different from the world – just like him.
Now her skin told Steve that she was much younger.
There was no scar from getting shot during the Battle at the Triskelion, a scar on her abdomen from the medical team at the compound digging out a bullet. Then there were the scars that should’ve been scattered across her skin from when she was tortured by Hydra. Thanks to Wakandan medicine, they were almost invisible. But Steve was familiar enough with Y/N’s body that he could still just barely point them out. Those were nowhere to be seen either.
Which meant that the Y/N standing in front of Steve was from a much younger time.
“Did we…did we break up?” Y/N’s lip trembled as her eyes filled with tears.
Steve stepped forward. “What? Why would you think that?”
Her eyes looked around the room. “None of my stuff is here. It doesn’t even look like I live here.”
But it was true. There was hardly any personality to his Brooklyn apartment. Anyone that knew Y/N would expect her apartment to be filled with warmth, and the perfect lighting, and everything that made a home intimate and charming.
“Steve, did we break up?” Y/N’s voice shook as she repeated the question.
Tears were streaming down her cheeks and Steve couldn’t handle it anymore.
He closed the distance between them and pulled her into his body.
“Hey, hey, hey,” he muttered. “It’s OK. We didn’t break up.”
At least he didn’t technically have to lie about that.
She pulled away from being tucked into his body to look at his face. “What is this place?” It was still obvious she didn’t exist in this space.
“We just bought it,” Steve was quick on his feet. “It came furnished and we haven’t moved all of our stuff in yet.”
Y/N seemed to believe him. “Where am I?”
“You’re away on a freelance job.”
She nodded, processing the new information.
“Would you like some clothes?” He asked her gently.
Y/N laughed lightly, apparently having forgotten that she was fully naked.
She sniffled, trying to clear her nose and nodded.
A few minutes later, Y/N was in Steve’s sweats, sitting at his kitchen island with her own coffee cupped between her palms.
“I’m sorry – again – that I scared you into spilling coffee on yourself,” she winced.
Steve chuckled. “Y/N, believe it or not, I’ve suffered much worse injuries than hot coffee burns.”
“Right,” she smiled. “You’ve just casually been shot a few times and survived a plan crash.”
He quirked an eyebrow. “Amongst other things.”
“Amongst other things,” Y/N agreed and repeated back.
A peaceful silence settled between them.
Y/N’s eyes narrowed. “You know, I don’t believe you.”
“About the hot coffee?”
“About us not being broken up,” Y/N confirmed.
Steve just tightened his jaw. He didn’t know how much more he could lie to her.
Y/N slowly stood up and closed the distance between them. When she was in his space, she carefully reached up to brush his cheek with her thumb.
“Your eyes… they’re so sad. And they get even sadder every time you look at me.”
“We’re on a break,” Steve quickly told her. He hoped a half lie would save him.
Y/N nodded. And he knew that she believed that one.
She opened her mouth to ask more.
“Please, don’t ask me to say more about it,” Steve begged.
Y/N just nodded.
But then she stepped even closer to him. “Do you miss me?” She whispered as her gaze flickered down to his lips.
Steve’s chest hurt from the question alone. Present and future Y/N had never prepared him for having interactions like this.
He just nodded his head, knowing that if he tried to say actual words then he’d just let out some pathetic whimper.
Y/N leaned even closer. Her gaze flickered to his, silently asking him if he wanted her to stop.
But Steve didn’t have that sort of self control.
So Y/N kissed him.
And he felt her surprise when he responded with a hunger she didn’t expect.
Without hesitation, he pulled her closer. But it still wasn’t enough. Then his hands slid down the outside of her thighs and then gripped the back of them. He scooped her up and pulled her hips to his waist, holding her there until she realized she needed to wrap her legs around him. But it still wasn’t enough.
He pulled away from the kiss. “Do you want me to stop?” His words struggled while he also tried to catch his breath.
Y/N gave him a shy smile and shook her head before giving him a sweet and precise peck on the lips.
“No, I don’t.” Then she laughed, “But maybe we could move this to the bedroom.”
Even if she wasn’t his in this time period, Y/N still knew what Steve needed. And she was more than willing to give it to him.
——————————
Steve always got this guilty feeling after sleeping with a version of Y/N that wasn’t her present self. No matter how many times Y/N told him it wasn’t, Steve could always convince a part of his mind to believe he had cheated.
Y/N had fallen asleep so quickly. It didn’t matter that she was out of her time. She always felt safe with Steve.
Meanwhile, Steve wouldn’t allow himself a second of sleep. He wasn’t going to waste a moment with Y/N by not being awake. How could he?
Instead he held her naked body against his chest. He switched back and forth between tracing the line of her spine to thumbing circles on her shoulder.
The more time he spent without Y/N in his present, the harder it was to watch her other selves leave him.
He glanced at the clock on his nightstand and sighed. He had to go to his group therapy in a few hours.
If Y/N was still here by then, he’d skip it. Lie and tell them he was sick.
Those sessions made him feel like a mockery anyway. At least once a week, he sat in a circle and told people they needed to move on with their lives. Meanwhile, he was still in a relationship with his dead girlfriend. She was a ghost that haunted him. He lectured other people how to live their lives in a post-snap world when he couldn’t go a minute without hoping a future or past Y/N would visit him soon.
Steve was taken out of his thoughts when Y/N stirred next to him.
She wasn’t waking up; she was leaving.
He saw her body start to fade.
There was nothing he hated seeing more than watching Y/N travel.
Was she going back to her own present? Was she going somewhere else? Would she be safe? Would this be one of her trips where she got hurt or almost killed?
And then, just like that, Y/N was gone. And Steve was alone once again.
Steve hoped his sheets would smell like her for longer than they did last time.
He should probably shower before he went to group, but he didn’t want to lose the feeling of her on his skin. He just wanted it to linger, if that was even possible.
That’s when he decided he needed more than a talk with a group of strangers. He needed a friend – a real friend – who knew what he was actually going through.
——————-

Steve hated going to the compound since the snap.
It was like going to a haunted house.
He never knew what memories would be resurrected when he visited.
Sometimes it was just the way the sun lit the room for a second or he’d catch a certain smell, then he was suddenly thrust into a memory linked to Y/N.
Steve found Nat in tears.
It was subtle, but it still broke his heart to see her upset. She was the strongest of them all. If she couldn’t hold it together, that’s when the rest of them truly knew how bad things really were.
“Ya know, I’d offer to cook you dinner, but you seem pretty miserable already.”
“You here to do your laundry?” She teased, trying to hide that she’d lost her composure for even a second.
“And to see a friend,” he added.
“Clearly your friend is fine.”
“What if your friend is the one that’s not?” He offered.
Her forced smirk faltered. “She show up today?”
Steve sighed and nodded. “She thought we broke up. It took one look around my apartment to know she didn’t live there.”
“You’re a terrible liar, so I could only imagine how that went.”
“Well, I eventually got her to believe we were just on a break, instead of telling her that she was…”
“Dead?” Nat offered.
Steve’s jaw just tightened at the word. He moved to sit across from her.
“It’s the first time she didn’t know about it. And now I’m wondering if I prefer the version of her that doesn’t know what's going to happen to her.”
Nat just hummed, understanding what he meant.
Steve’s eyes glazed over as he thought about it. “How was she able to just live every day knowing what was going to happen?”
“She had to learn to accept what she couldn’t control awhile ago, Steve. She didn’t have any other choice.”
“Why couldn’t she tell me?” He thought aloud, frustration clear in his voice.
“Because she knew you.”
“What’s that supposed to mean?”
“You would’ve made yourself crazy trying to stop what you couldn’t. Nothing else would’ve mattered...including her.” Nat sighed. “Maybe she just wanted to embrace what little time she had with you. She can ignore the ticking of a time bomb, but not you.”
Steve knew Nat was right.
Suddenly, there was a ping and a hologram appeared in front of Nat.
She pressed a few buttons in the air and a video played out.
Next thing they knew, Scott Lang was fumbling his words at the front gate’s security camera.
Steve slowly stood up. Scott Lang was meant to be dead. “Is this an old message?”
“It’s the front gate,” Nat told him.
An hour later, Scott had stopped his pacing and explained his time travel theory.
Steve looked at Nat and immediately knew that she didn’t find Scott as crazy as he did.
But Nat had been searching for hope these past 5 years, while Steve refused to let it into his life.
“Tomorrow we’ll go see Tony,” Steve confirmed. “For now, you should get some rest, Scott.” Then he looked at Nat. “We all should.”
That was code for, ‘Don’t get excited.’
She clearly got the underlying message, but refused to ignore the hope.
—————————
Steve walked into his old room at the compound. He was only ever there when he visited Nat, which wasn’t often at all. He only kept some things there because he saw the hurt in Nat’s eyes when he had once suggested he completely clean it out.
When he turned on the light, he immediately noticed an envelope on the nightstand.
It was a letter addressed to him at the compound.
But Steve’s heart raced when he recognized the writing as Y/N’s.
“FRIDAY, where did this letter come from?” He asked the AI.
“It arrived in the mail today, Captain Rogers.”
He ripped it open instantly, his hands shaking in the process.
But there were only three words for him to read:
Listen to Scott.
Steve felt his heart beat faster.
And for the first time in 5 years, he felt hope.
-------------------------
Ya’ll, I can see the light at the end of the tunnel.
#non-sequential#non-sequential series#non-sequential chapter 29#steve rogers fic#steve rogers x reader#steve rogers reader insert#pre-serum!steve rogers#pre serum steve#pre-serum steve rogers x reader#captain america x reader#captain america fic#steve rogers angst#pre-serum!steve rogers x reader
469 notes
·
View notes
Text
ACC 564 Quiz 3 – Strayer New
ACC 564 Quiz 3 – Strayer New
ACC 564 Week 8 Quiz 3 Chapter 10 Through 13
Click On The Link Below To Purchase Instant Download
http://www.budapp.net/ACC-564-Quiz-3-Strayer-New-ACC564Q3.htm
Chapter 10 Information Systems Controls for Systems ReliabilityPart 3: Processing Integrity and Availability
1) The best example of a hash total for a payroll transaction file could be A) total of employees' social security numbers. B) sum of net pay. C) total number of employees. D) sum of hours worked. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
2) Error logs and review are an example of A) data entry controls. B) data transmission controls. C) output controls. D) processing controls. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic 3) Following is the result of batch control totals on employee Social Security Numbers in a payroll processing transaction:
Correct Values From Masterfile Values Entered During Processing 487358796 487358796 534916487 534916487 498374526 498374526 514873420 514873420 534196487 534916487 678487853 678487853 471230589 471230589 3719438158 3720158158
The difference in the control totals is 720,000. Which data entry control would best prevent similar data entry errors in the future? A) Modulus 11 B) Validity check C) Check digit D) Sequence check Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Moderate AACSB: Analytic
4) Which of the following data entry controls would not be useful if you are recording the checkout of library books by members? A) Sequence check B) Prompting C) Validity check D) Concurrent update control Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Moderate AACSB: Analytic
5) A customer failed to include her account number on her check, and the accounts receivable clerk credited her payment to a different customer with the same last name. Which control could have been used to most effectively to prevent this error? A) Closed-loop verification B) Duplicate values check C) Validity check D) Reconciliation of a batch control total Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
6) If invoices are processed in groups of fifty, which fields from the document shown below would not be used to create a hash control total?
A) Amount B) Item Number C) Quantity Ordered D) Sales Order number Answer:
Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Reflective Thinking
7) A data entry input control in which the application software sums the first four digits of a customer number to calculate the value of the fifth digit and then compares the calculated number to the number typed in during data entry is an example of a A) check digit verification. B) validity check. C) closed-loop verification. D) duplicate data check. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
8) All of the following controls for online entry of a sales order would be useful except A) check digit verification on the dollar amount of the order. B) validity check on the inventory item numbers. C) field check on the customer ID and dollar amount of the order. D) concurrent update control. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Difficult AACSB: Analytic
9) A specific inventory record indicates that there were 12 items on hand before a customer brings two of the items to the check stand to be purchased. The cashier accidentally entered quantity 20 instead of 2. Which data entry control would best have prevented this error? A) sign check B) limit check C) validity check D) field check Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
10) When processing weekly payroll, an employee accidentally entered 400 for hours worked. The best data entry control for this error would be A) a limit check. B) a check digit. C) batch total reconciliation. D) a field check. Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
11) The data entry control that would best prevent entering an invoice received from a vendor who is not on an authorized supplier list is A) a validity check. B) an authorization check. C) a check digit. D) closed-loop verification. Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
12) Forms design is an example of this type of control. A) Data entry control B) Processing control C) Output control D) Input control Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
13) Sequentially prenumbered forms is an example of a(n) A) data entry control. B) data transmission control. C) processing control. D) input control. Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
14) Turnaround documents are an example of a(n) A) data entry control. B) output control. C) processing control. D) input control. Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
15) A validity check is an example of a(n) A) data entry control. B) data transmission control. C) output control. D) input control. Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
16) Parity checks are an example of a(n) A) data entry control. B) data transmission control. C) output control. D) processing control. Answer: Page Ref: 279 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
17) User reviews are an example of a(n) A) data entry control. B) data transmission control. C) output control. D) processing control. Answer: Page Ref: 278 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
18) Data matching is an example of a(n) A) data entry control. B) data transmission control. C) processing control. D) input control. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
19) Batch totals are an example of a(n) A) data entry control. B) data transmission control. C) output control. D) processing control. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Moderate AACSB: Analytic
20) Cancellation and storage of documents means that A) data are copied from a document and stored, after which the document is shredded. B) documents are defaced before being shredded. C) documents are defaced and stored. D) cancellation data are copied from documents before they are stored. Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Moderate AACSB: Analytic
21) Check digit verification is an example of a(n) A) data transmission control. B) output control. C) processing control. D) input control. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
22) This ensures that the input data will fit into the assigned field. A) Limit check B) Range check C) Size check D) Validity check Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
23) This tests a numerical amount to ensure that it does not exceed a predetermined value nor fall below another predetermined value. A) Completeness check B) Field check C) Limit check D) Range check Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
24) This determines if all required data items have been entered. A) Completeness check B) Field check C) Limit check D) Range check Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
25) This determines the correctness of the logical relationship between two data items. A) Range check B) Reasonableness test C) Sign check D) Size check Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
26) This determines if characters are of the proper type. A) Field check B) Alpha-numeric check C) Range check D) Reasonableness test Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
27) This tests a numerical amount to ensure that it does not exceed a predetermined value. A) Completeness check B) Limit check C) Range check D) Sign check Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
28) This batch processing data entry control sums a field that contains dollar values. A) Record count B) Financial total C) Hash total D) Sequence check Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
29) This batch processing data entry control sums a non-financial numeric field. A) Record count B) Financial total C) Hash total D) Sequence check Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
30) When I enter a correct customer number, the data entry screen displays the customer name and address. This is an example of A) prompting. B) preformatting. C) closed-loop verification. D) error checking. Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
31) This control ensures that the correct and most current files are being updated. A) Cross-footing balance test B) Data matching C) File labels D) Write-protect mechanism Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Moderate AACSB: Analytic
32) This batch processing data entry control sums the number of items in a batch. A) Financial total B) Hash total C) Record count D) Sequence check Answer: Page Ref: 277 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
33) This data entry control compares the ID number in transaction data to a master file to verify that the ID number exists. A) Reasonableness test B) User review C) Data matching D) Validity check Answer: Page Ref: 276 Objective: Learning Objective 1 Difficulty : Easy AACSB: Analytic
0 notes
Text
[Event & Scenario] “Episode of Avalon #1.5 Voyager of the New World” START

Part 1.5, start! OSIRIS, who have joined Avalon, are all hyped up in starting activities but what stands before them...? Travel with OSIRIS to America and beat those who get in your way!
Details
▼ Release Date: 2017/12/28 (Thu) 17:00JST ~ onwards
Part 1.5 of the "Episode of Avalon #1.5 Voyager of the New World" will start! Chapter 1 will focus on OSIRIS.
▼ Access Condition
Finish reading the final chapter of each band’s (BLAST, OSIRIS, Fairy April, Cure2tron) Main Scenario Ep.1.

How To Participate
You can access Part 1.5 from the banner on the home screen as long as the condition of clearing the last chapters for Episode 1 of all the bands have been satisfied.
※ Although there is no deadline, you may only receive the Clear Reward once.

How To Play

Get “Flyers” by playing songs from different Areas listed in the Event Page. Choose the Area you want to play in and win the Duel Gig of each stage to proceed to the next stage. The Main Areas will have multiple stages accompanied by event stories. You will then unlock some Free Stages per Main Stage cleared which will be your main source of gaining Flyers after clearing all the Main Areas.

You can exchange the “Flyers” for rewards like limited edition cards via the Shop’s “Item Exchange” section. [more info.]
You can access the event scenarios via the new section, “Episode Of Avalon” from the Stories Tab.
Event Stage Schedule
The Area Stages for "Episode of Avalon #1.5 Voyager of the New World" will be released sequentially from 2017/12/30(Sat) 00:00 JST. The new stages will be released at a schedule:
12/30(Sat) 00:00~・Departure 01/01(Mon) 00:00~・Detour 01/03(Wed) 00:00~・Bandits 01/05(Fri) 00:00~・Submit or Perish 01/07(Sun) 00:00~・Depression 01/09(Tue) 00:00~・Perfection 01/11(Thu) 00:00~・A Long Road 01/13(Sat) 00:00~・Epilogue
New Rival Band Appearance!

EISENROSES (Left to Right, romaji tentative): Alexei, Wolff, Gaia, Sugar, Jive
Past Event Scenario Limited Time Rerun
Scenarios of the events leading up to the scenario for Part 1.5 will have a re-run for a limited time only. Unopened scenarios will be available for reading during the following period:
▼ Duration: 2017/12/28 (Thu) 17:00 JST ~ 2018/01/15 (Mon) 12:59 JST
※ You can access the event scenarios from the "Story" tab → "Event Scenario" but will not be able to receive any reward upon clearing.
The target Event Scenario are as follows:
Advent of the Quattro Virtuoso GIGS ー Dante of the Purgatory
Anniversary GIGS ー Dreamin' (untranslated)
On Board The Merry Christmas GIGS ー Dante is Coming To Town!

Event Reward Card
SR: Ray Cephart [A Journey's Exhilarating Feeling]

Event Strategy-1
Using OSIRIS members' cards into Bands to use for LIVEs will improve overall performance.

Event Strategy-2

A special login bonus will be held!
Make sure to log in from 2017/12/28(Thu) 17:00JST, during the event period to get one (1) 100%+ Stamina Charge a day.
▼ Duration: 2017/12/28 (Thu) 17:00 JST ~ 2018/01/14 (Sun) 23:59 JST
※ Daily bonus cannot be obtained once the day is over. ※ Like normal login bonuses, the daily bonus will reset at 00:00JST every day.
Time-Limited Event Song
“Beyond the Limit” by OSIRIS Lyrics, composition, arrangement: Gouki Ohtsuka

“Voyager of the New World” Limited Rare Gacha (Daily Rotation)

Duration: 2017/12/28(Thu) 17:00JST ~ 2018/01/15(Mon) 12:59JST
Line-up: SSR Sousuke Maki, SSR Kyo Takara, SSR Yoshimune Tokuda, SSR Shelly, SR Yamato Shinonome, SR Miley
※ SR Yamato Shinonome and SR Miley will be available throughout the duration of the gacha.
The gacha can use both Free and Paid Medals
It is possible to pull regular cards other than the Event limited gacha cards.
At least 1 SR or above card is guaranteed for every 10-pull
Signed cards will be discharged at a certain probability. Signs will only appear for SR cards and above and will be treated the same as non-signed, having the same stat and effects. You can admire the sign in various places.
Event limited cards might reappear during future events/campaigns.
“Voyager of the New World”Rare Gacha Schedule
ALL CHARACTERS ・12/28, 1/14, 1/15 SHELLY ・12/29, 1/2, 1/6, 1/10 KYO TAKARA ・12/30, 1/3, 1/7, 1/11 SOUSUKE MAKI ・12/31, 1/4, 1/8, 1/12 YOSHIMUNE TOKUDA ・1/1, 1/5, 1/9, 1/13
※ Please take note that the pick-up date will change at a daily basis
Featured New Cards
SSR Sousuke Maki [tba*] Leader Skill: [COMBO BONUS] Combo Bonus boosted by 25% Main Skill: [Löyly* of Tragedy] 30% chance of activation upon 30 successful taps, boosting others’ skill effectiveness by by 30% for 6 seconds. (When the Skill of the same nature overlaps, only the card with the higher effectiveness will activate.)
※ Despite the trigger and end of the "Other Skill Effectiveness Boost", LIFE dropping to 0 will still result in LIVE failure.


SSR Kyo Takara [Search for a Lost Child] Leader Skill: [BEAT UP] Combo Bonus boosted by 25% Main Skill: [Even the Destination’s Wrong] 40% chance of activation upon 50 successful taps, boosting others’ skill effectiveness by by 30% for 8 seconds. (When the Skill of the same nature overlaps, only the card with the higher effectiveness will activate.)
※ Despite the trigger and end of the "Other Skill Effectiveness Boost", LIFE dropping to 0 will still result in LIVE failure.


SSR Yoshimune Tokuda [Search for a Lost Child] Leader Skill: [BEAT UP+Fairy*] All Member’s BEAT boosted by 30%. Additional 20% if Fairy April members, other than Yoshimune, makes up the rest of the Band. Main Skill: [Kotatsu of Magic] 40% chance of activation upon 50 successful taps, boosting Combo Bonus by 16% for 8 seconds.


SSR Shelly [tba*] Leader Skill: [GROOVE UP+Cure2tron*] All Member’s GROOVE boosted by 30%. Additional 15% if at least 1 Cure2tron member, other than Shelly, in included in the Band. Main Skill: [Kotatsu of Magic] 10% chance of activation upon 15 successful taps, boosting score by 20% for 4 seconds.


SSR Yamato Shinonome [tba*] Leader Skill: [MELODY BONUS+SPIRIT*] All Member’s MELODY boosted by 15% and Spirits gained by 20% Main Skill: [--] 40% chance of activation upon 50 successful taps, boosting others’ skill effectiveness by by 20% for 8 seconds. (When the Skill of the same nature overlaps, only the card with the higher effectiveness will activate.)

SSR Miley [Dress-up] Leader Skill: [LIFE UP] All Member’s LIFE boosted by 15% Main Skill: [--] 40% chance of activation upon 50 successful taps, boosting others’ skill effectiveness by by 20% for 8 seconds. (When the Skill of the same nature overlaps, only the card with the higher effectiveness will activate.)

※ Cards from this gacha are will have a max level of 90 for SSR and 75 for SR once Break.
You can check the in-game gacha/event page for more info.
*Some Card Names and Skill Names to be added. I’m out of time at the moment.
*Click for Sousuke’s Skill Name.
#news : event#guide : event#band yarouze#banyaro#band yarouze!#Episode of Avalon 1.5 Voyager of the New World#admin : pk5u
11 notes
·
View notes
Text
Non-Sequential // Masterlist

Pairing: Pre-Serum Steve Rogers/Steve Rogers x Reader
One night, Steve Rogers met a beautiful dame named Y/N. He hadn’t intended on letting her get away. But fate had other ideas. Y/N appeared and disappeared in his life so hauntingly that Steve started to wonder if she was an angel meant to watch over him.
A/N: Inspired by the film The Time Traveler’s Wife. But not one of those fics that just literally rips off the whole movie and plugs in characters where they please.
Prologue // Chapter 1 // Chapter 2 // Chapter 3 // Chapter 4 // Chapter 5 // Chapter 6 // Chapter 7 // Chapter 8 // Chapter 9 // Chapter 10 // Chapter 11 // Chapter 12 // Chapter 13 // Chapter 14 // Chapter 15 // Chapter 16 // Chapter 17 // Chapter 18 // Chapter 19 // Chapter 20 // Chapter 21 // Chapter 22 // Chapter 23 // Chapter 24 // Chapter 25 // Chapter 26 // Chapter 27 // Chapter 28 // Chapter 29 //
---
Non-Sequential Headcanons & Asks
I DO NOT DO TAGLISTS.
#pre serum steve#pre serum steve rogers#steve rogers fic#steve rogers x reader#steve rogers reader insert#captain america x#mar#steve rogers fanfic#steve rogers fluff#1930s steve rogers#1940s steve rogers#non sequential series#non sequential masterlist#bucky barnes#winter soldier#pre serum!steve rogers x reader#bucky barnes x reader
4K notes
·
View notes
Note
yoo non sequential chap 28 was so enjoyable dude!! cant wait for how you finish the series and cant wait for the next chapter. the whole series is great!!

4 notes
·
View notes
Note
OMG chapter 28 of non sequential gonna be amazing, i remember guessing future Steve was confused to see YN bcs they choose bucky over him, im just so excited for whatever come next!

2 notes
·
View notes