#oauth openid
Explore tagged Tumblr posts
Text
Advanced Techniques in Full-Stack Development

Certainly, let's delve deeper into more advanced techniques and concepts in full-stack development:
1. Server-Side Rendering (SSR) and Static Site Generation (SSG):
SSR: Rendering web pages on the server side to improve performance and SEO by delivering fully rendered pages to the client.
SSG: Generating static HTML files at build time, enhancing speed, and reducing the server load.
2. WebAssembly:
WebAssembly (Wasm): A binary instruction format for a stack-based virtual machine. It allows high-performance execution of code on web browsers, enabling languages like C, C++, and Rust to run in web applications.
3. Progressive Web Apps (PWAs) Enhancements:
Background Sync: Allowing PWAs to sync data in the background even when the app is closed.
Web Push Notifications: Implementing push notifications to engage users even when they are not actively using the application.
4. State Management:
Redux and MobX: Advanced state management libraries in React applications for managing complex application states efficiently.
Reactive Programming: Utilizing RxJS or other reactive programming libraries to handle asynchronous data streams and events in real-time applications.
5. WebSockets and WebRTC:
WebSockets: Enabling real-time, bidirectional communication between clients and servers for applications requiring constant data updates.
WebRTC: Facilitating real-time communication, such as video chat, directly between web browsers without the need for plugins or additional software.
6. Caching Strategies:
Content Delivery Networks (CDN): Leveraging CDNs to cache and distribute content globally, improving website loading speeds for users worldwide.
Service Workers: Using service workers to cache assets and data, providing offline access and improving performance for returning visitors.
7. GraphQL Subscriptions:
GraphQL Subscriptions: Enabling real-time updates in GraphQL APIs by allowing clients to subscribe to specific events and receive push notifications when data changes.
8. Authentication and Authorization:
OAuth 2.0 and OpenID Connect: Implementing secure authentication and authorization protocols for user login and access control.
JSON Web Tokens (JWT): Utilizing JWTs to securely transmit information between parties, ensuring data integrity and authenticity.
9. Content Management Systems (CMS) Integration:
Headless CMS: Integrating headless CMS like Contentful or Strapi, allowing content creators to manage content independently from the application's front end.
10. Automated Performance Optimization:
Lighthouse and Web Vitals: Utilizing tools like Lighthouse and Google's Web Vitals to measure and optimize web performance, focusing on key user-centric metrics like loading speed and interactivity.
11. Machine Learning and AI Integration:
TensorFlow.js and ONNX.js: Integrating machine learning models directly into web applications for tasks like image recognition, language processing, and recommendation systems.
12. Cross-Platform Development with Electron:
Electron: Building cross-platform desktop applications using web technologies (HTML, CSS, JavaScript), allowing developers to create desktop apps for Windows, macOS, and Linux.
13. Advanced Database Techniques:
Database Sharding: Implementing database sharding techniques to distribute large databases across multiple servers, improving scalability and performance.
Full-Text Search and Indexing: Implementing full-text search capabilities and optimized indexing for efficient searching and data retrieval.
14. Chaos Engineering:
Chaos Engineering: Introducing controlled experiments to identify weaknesses and potential failures in the system, ensuring the application's resilience and reliability.
15. Serverless Architectures with AWS Lambda or Azure Functions:
Serverless Architectures: Building applications as a collection of small, single-purpose functions that run in a serverless environment, providing automatic scaling and cost efficiency.
16. Data Pipelines and ETL (Extract, Transform, Load) Processes:
Data Pipelines: Creating automated data pipelines for processing and transforming large volumes of data, integrating various data sources and ensuring data consistency.
17. Responsive Design and Accessibility:
Responsive Design: Implementing advanced responsive design techniques for seamless user experiences across a variety of devices and screen sizes.
Accessibility: Ensuring web applications are accessible to all users, including those with disabilities, by following WCAG guidelines and ARIA practices.
full stack development training in Pune
2 notes
·
View notes
Text
https://wiley.scienceconnect.io/api/oauth/authorize?ui_locales=en&scope=affiliations+alm_identity_ids+login_method+merged_users+openid+session_level+settings&response_type=code&redirect_uri=https%3A%2F%2Fadvanced.onlinelibrary.wiley.com%2Faction%2FoidcCallback%3FidpCode%3Dconnect&state=Dps2IO0LOrpSUAYYguc7KjWtugvQmVzeWJ3Swlsnw89eIzai%2B7B40zd0gy69cYDFLsEykWwCe5WYJJ02KRz0Nnr8jg3ciArqb3KjhN8X%2FHNcACaEf3vBPC3vLlJZVIJ4b3KjhN8X%2FHOzuOZ89%2Fsj%2BEyto1IqN1Mrb3KjhN8X%2FHNqbDYoHBdr9Ww1K3SgUeoKNdvm5UqjYmLcjGATprmEWPKnolkp3z3lCDorMwUSx9n7S3cuyjn2raXXIA6vyT1jxegZkrZA4sFOW8geB4prvw%3D%3D&prompt=none&nonce=Y6MoybIiMxXfLihIU%2Bz6hpRza6b7u4PIyeut4aPu5Eg%3D&client_id=wiley
1 note
·
View note
Text
The Power of .NET: Building Scalable and Secure Applications
In today’s fast-evolving software industry, scalability and security are critical for the success of any application. Whether you're building enterprise-level software, cloud-based systems, or web applications, the .NET framework stands out as a robust solution. For aspiring developers looking to gain real-world skills, enrolling in the Best DotNet Training Institute in Hyderabad, Kukatpally, KPHB is an excellent step toward mastering this powerful technology stack.
Why .NET Is Trusted by Enterprises
.NET, developed by Microsoft, is a versatile and high-performance framework widely used for building scalable, maintainable, and secure applications. Its support for multiple programming languages, especially C#, gives developers the flexibility to work on different types of applications—desktop, web, mobile, and cloud-based. Moreover, the framework continues to evolve, with .NET Core and now .NET 6/7 offering cross-platform capabilities and improved performance.
Built for Scalability
Scalability is a crucial requirement for modern applications. .NET’s built-in support for asynchronous programming, load balancing, and cloud integration through Azure services makes it an ideal choice for businesses expecting to grow their user base. Features like dependency injection, modular architecture, and microservices support allow applications to be scaled up or down based on demand.
Strong Security Features
Security is another area where .NET excels. It offers built-in mechanisms like authentication, authorization, data encryption, and secure coding practices. With frameworks like ASP.NET Identity and integrations with OAuth and OpenID Connect, developers can build applications that are not only functional but also resistant to common threats and attacks.
Modern Development with .NET
With tools like Visual Studio, seamless GitHub integration, and strong support for RESTful APIs and gRPC, .NET enables developers to follow modern software practices. Continuous integration, automated testing, and containerization with Docker further enhance the development lifecycle, ensuring smooth deployment and maintenance.
Conclusion
.NET is a future-proof, enterprise-ready framework that empowers developers to build applications that are both scalable and secure. To gain hands-on experience and in-depth knowledge of the .NET ecosystem, join Monopoly IT Solutions Pvt. Ltd, A leading provider of career transformation and professional training in the software industry.
#best python training in Hyderabad#best python training in Kukatpally#best python training in KPHB#best python full stack training
0 notes
Text
Why Is Azure App Registration Required for Your Apps?

Building scalable and secure apps in today's cloud-driven environment frequently necessitates a smooth interaction with cloud services. In order to fully utilize Microsoft Azure's robust platform for application deployment, management, and security, it is imperative to comprehend App Registration.
Your application may securely interface with Azure services like Microsoft Graph, SharePoint, Dynamics 365, and more using the app registration in Azure gateway. App registration is a crucial step in guaranteeing safe authentication and authorization, regardless of whether you're a developer creating a web application, a mobile solution, or a sophisticated enterprise-grade system.
What is Azure App Registration?
The process of registering an application with Azure Active Directory (Azure AD) is known as app registration. It enables Azure to identify your application and give it the necessary credentials and permissions, including a client ID, secret, and certificates.
By registering your app, you are effectively giving Azure permission to trust it, provide it access to APIs, and enforce identity-based security protocols like OpenID Connect or OAuth 2.0.
This comprehensive guide will teach you more about the procedure and its significance.
Why Is App Registration Necessary for Applications?
The following are the main justifications for why Azure app registration is essential:
1. Safe Identity Administration
Azure AD controls app credentials and user identities. By registering an app, you may employ industry-standard security protocols to make sure that only authorized users and apps can access your services.
2. Control of Access
Unauthorized data access can be decreased by configuring role-based access controls (RBAC), allocating permissions, and restricting access to resources and APIs.
3. Integration of APIs
Tokens can be requested by registered applications to access Azure AD-protected custom APIs or Microsoft APIs like Microsoft Graph, which simplifies development and integration.
4. Support for Single Sign-On (SSO)
Enable SSO in your application to improve security and streamline the user experience.
5. Analytics and Monitoring
Only registered apps have access to Azure's comprehensive logs and monitoring tools for tracking app performance, behavior, and access patterns.
6. Automation and Scalability
Scripts or programs like Terraform or Bicep can automate app registrations, which facilitates large-scale application deployment.
Practical Advice from Professionals
App Registration is not just a configuration task; it's a foundational security component for any intelligent or cloud-connected application, says AI specialist Lawrence Rufrano. Registration guarantees that everything takes place under a secure identity whether your AI system has to communicate with other services, store data securely, or access APIs.
Experts like Lawrence Rufrano stress the significance of appropriate identity and access management as cloud and AI technologies merge, especially for AI solutions that depend on cloud-based data and service orchestration.
In conclusion
App registration is essential if you're developing apps that will interface with Azure services. It guarantees that your application is safe, complies with regulations, and can utilize all of Azure's features.
0 notes
Text
Google developers OAuth 2.0 playground And OpenID Connect

Google Auth Platform usability and security updates
Millions of developers authenticate users and access hundreds of APIs using Google's identity platform. One of the largest implementations of the Google developers OAuth 2.0 playground protocol and OpenID Connect standard in the world provides developers with a reliable, secure, and easy method to interact. Google is pleased to announce significant platform usability and security improvements.
Google engineers' OAuth 2.0 playground
Simple OAuth setting in Google Cloud Console
Developers that use Google Sign-in for authentication or user consent to use Google APIs must register their applications and websites to generate client credentials. Developers utilising Google Cloud Console previously found OAuth setup pages under APIs & Services. Separate navigation for Google Auth Platform is added to these sites.
This version speeds up app configuration updates, simplifies project registration, and improves developer advice. Upcoming improvements include an improved onboarding wizard, simpler OAuth scope management, and faster, more transparent app verification.
Developers using other consoles for OAuth have the same Firebase or Apps Script experience.
OAuth client secret presentation change
Some OAuth clients require a “secret” for authorisation and authentication. Since the client secret operates like a website or application password, protecting these strings is crucial to user account and data security.
Developers could previously download client secrets from Google Cloud Console, Firebase Console, and other Google developer tools. OAuth secrets will be hidden in Google Cloud Console client administrative pages in June. Developer consoles will show the last few characters to help identify them.
OAuth client secrets must be downloaded and handled securely by developers. For this, most developers utilise Google Cloud Platform's Secret Manager. The client secret won't appear when the creation screen closes.
Never reveal OAuth client secrets that provide access to user data or other production systems online or in version control systems. If secrets leak, change them immediately and cycle them often.
Automatic deactivation of unused OAuth clients
Starting in June, OAuth clients inactive for six months will be automatically terminated to prevent credential theft and misuse. When token exchanges end, the six-month period begins.
When inactive clients are erased, developers will be notified and can recover them for 30 days.
A great experience for you and your customers
These upgrades and more planned for later this year make your experience smoother and safer, giving you more time to build great applications and websites for your consumers.
Accessing Google APIs with OAuth 2.0
Simple acts
Every Google API-accessing app utilising OAuth 2.0 follows a pattern. You take five stages typically:
The Google API Console gives OAuth 2.0 credentials.
Get an access token from Google Authorisation Server.
Review user-granted access scopes.
Give an API the access token.
Update the access token if needed.
Google APIs authorise and authenticate using OAuth 2.0. Google supports OAuth 2.0 applications for web servers, client-side, installation, and limited-input devices.
Get OAuth 2.0 client credentials from Google API Console to begin. After that, your client app requests an access token from the Google Authorisation Server, extracts it, and sends it to the Google API you want to use. Check out the OAuth 2.0 Playground for an interactive Google OAuth 2.0 demonstration using your own client credentials.
#technology#technews#govindhtech#news#technologynews#Google developers OAuth 2.0 playground#Google developers OAuth#OAuth 2.0#OAuth clients#OAuth 2.0 playground#OAuth
0 notes
Text
Security Vulnerabilities in SAML, OAuth 2.0, OpenID Connect, and JWT
Single Sign-On (SSO) protocols are critical for enterprise security but have a history of severe vulnerabilities. This report provides a data-rich overview of known security flaws in four major SSO technologies – SAML, OAuth 2.0, OpenID Connect (OIDC), and JSON Web Tokens (JWT) – including both historical exploits and recent findings. We compare the frequency and impact of these vulnerabilities,…
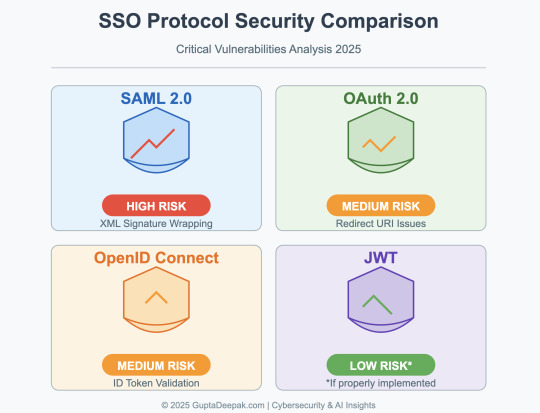
View On WordPress
#assistant professor#computer science#computer scientist#engineering#experimental roboticist#research scientist#university of denver
0 notes
Text
Secure API Development: Protecting Your Data in the Digital Age

Introduction: Why Secure API Development is Essential
In today's interconnected world, APIs are the backbone of modern software. They connect services, platforms, and users. However, with this connectivity comes risk. Cyberattacks, data breaches, and unauthorized access are growing threats. That's why secure API development has become a non-negotiable priority for developers and businesses.
In this comprehensive guide, we will explore what secure API development means, why it's more important than ever in 2025, how to implement security practices, the best tools for securing APIs, and answer common questions.
What is Secure API Development?
Secure API development is the process of designing, building, and managing APIs with a primary focus on data security, access control, and compliance. It involves a range of practices including:
Authentication & Authorization
Encryption of data in transit and at rest
Input validation
Rate limiting and throttling
Monitoring and logging
Why It Matters in 2025
API Attacks Are Increasing: APIs are a top target for attackers due to weak security implementations.
Strict Regulations: Laws like GDPR, HIPAA, and CCPA require secure data handling.
Brand Trust: A single breach can ruin consumer confidence.
Business Continuity: Secure APIs reduce downtime and financial loss.
IoT and Mobile Expansion: With billions of devices connected, secure APIs are vital.
Key Principles of Secure API Development
Least Privilege Access: Only grant access to what’s necessary.
Secure Authentication: Use OAuth 2.0, OpenID Connect, and strong token systems.
Data Encryption: Use HTTPS/TLS and encrypt sensitive data at rest.
Input Sanitization: Prevent injection attacks with proper input validation.
Rate Limiting: Protect APIs from abuse and DDoS attacks.
Monitoring & Logging: Track API usage and detect anomalies early.
Secure API Development Best Practices
PracticeDescriptionUse HTTPSAlways encrypt data in transit.Implement OAuth 2.0Modern standard for API authorization.Validate InputsAvoid SQL injection and XSS attacks.Token ExpirationUse short-lived tokens for sessions.CORS PoliciesRestrict cross-origin requests.API GatewayCentralize security and traffic management.LoggingLog all API calls with metadata for audits.
Tools for Secure API Development
Postman Security Suite: For testing vulnerabilities.
Swagger + OpenAPI: Document and test API access securely.
Kong Gateway: Secure API traffic and enforce policies.
Okta / Auth0: Authentication and authorization.
OWASP ZAP: For automated security testing.
DataDog: For monitoring API traffic and threats.
Common Threats in API Security
ThreatDescriptionBroken AuthenticationImproperly implemented login mechanisms.Excessive Data ExposureAPIs revealing more data than needed.Rate Limiting FailureAPIs can be abused without restrictions.Injection AttacksMalicious data sent to manipulate databases.Lack of LoggingNo trail of usage makes incident response hard.
How to Test for API Security
Penetration Testing: Simulate attacks to identify vulnerabilities.
Static Analysis: Analyze source code for security flaws.
Dynamic Testing: Test APIs during runtime.
Fuzz Testing: Send random data to uncover bugs.
Audit Trails: Review logs for unusual patterns.
Real-World Case Study: API Security in FinTech
A leading FinTech startup experienced a near-breach due to excessive data exposure in its open banking API. After adopting secure API practices:
Implemented OAuth 2.0 and JWT-based token system
Added rate limiting and IP whitelisting
Regularly audited logs and monitored API traffic
Result: No breaches since the update and a 40% increase in client trust and onboarding.
Review: Is Secure API Development Worth It?
Absolutely. In an era where APIs are integral to business, securing them is essential. The upfront investment in security reduces long-term costs and protects brand reputation.
Pros:
Reduced risk of data breaches
Regulatory compliance
Improved user trust
Lower long-term maintenance
Cons:
Increased initial development time
Need for continuous monitoring
Overall Rating: ⭐⭐⭐⭐⭐ (4.9/5)
FAQs: Secure API Development
Q1: Is HTTPS enough to secure an API? No. HTTPS is vital but not sufficient. You also need proper authentication, input validation, and access control.
Q2: What is OAuth 2.0? It’s a secure authorization protocol that allows users to grant apps access to their data without sharing passwords.
Q3: How often should I test my API security? Regularly—ideally during every release and after any major update.
Q4: Are open APIs less secure? Not necessarily. Open APIs can be secure if properly implemented with access control and monitoring.
Q5: Can rate limiting stop all attacks? It’s a useful defense but should be used in combination with other security measures.
Final Thoughts
Secure API development is no longer optional—it’s a fundamental requirement for digital businesses. From authentication to encryption, every step in your API design must consider security. Organizations that prioritize API security not only protect data but also build trust with users, stakeholders, and regulators.
Stay ahead in API security trends with more guides at diglip7.com. Invest in protection today for a safer tomorrow.
0 notes
Text
Top Tech Stacks for Fintech App Development in 2025
Fintech is evolving fast, and so is the technology behind it. As we head into 2025, financial applications demand more than just sleek interfaces — they need to be secure, scalable, and lightning-fast. Whether you're building a neobank, a personal finance tracker, a crypto exchange, or a payment gateway, choosing the right tech stack can make or break your app.

In this post, we’ll break down the top tech stacks powering fintech apps in 2025 and what makes them stand out.
1. Frontend Tech Stacks
🔹 React.js + TypeScript
React has long been a favorite for fintech frontends, and paired with TypeScript, it offers improved code safety and scalability. TypeScript helps catch errors early, which is critical in the finance world where accuracy is everything.
🔹 Next.js (React Framework)
For fintech apps with a strong web presence, Next.js brings server-side rendering and API routes, making it easier to manage SEO, performance, and backend logic in one place.
🔹 Flutter (for Web and Mobile)
Flutter is gaining massive traction for building cross-platform fintech apps with a single codebase. It's fast, visually appealing, and great for MVPs and startups trying to reduce time to market.
2. Backend Tech Stacks
🔹 Node.js + NestJS
Node.js offers speed and scalability, while NestJS adds a structured, enterprise-grade framework. Great for microservices-based fintech apps that need modular and testable code.
🔹 Python + Django
Python is widely used in fintech for its simplicity and readability. Combine it with Django — a secure and robust web framework — and you have a great stack for building APIs and handling complex data processing.
🔹 Golang
Go is emerging as a go-to language for performance-intensive fintech apps, especially for handling real-time transactions and services at scale. Its concurrency support is a huge bonus.
3. Databases
🔹 PostgreSQL
Hands down the most loved database for fintech in 2025. It's reliable, supports complex queries, and handles financial data like a pro. With extensions like PostGIS and TimescaleDB, it's even more powerful.
🔹 MongoDB (with caution)
While not ideal for transactional data, MongoDB can be used for storing logs, sessions, or less-critical analytics. Just be sure to avoid it for money-related tables unless you have a strong reason.
🔹 Redis
Perfect for caching, rate-limiting, and real-time data updates. Great when paired with WebSockets for live transaction updates or stock price tickers.
4. Security & Compliance
In fintech, security isn’t optional — it’s everything.
OAuth 2.1 and OpenID Connect for secure user authentication
TLS 1.3 for encrypted communication
Zero Trust Architecture for internal systems
Biometric Auth for mobile apps
End-to-end encryption for sensitive data
Compliance Ready: GDPR, PCI-DSS, and SOC2 tools built-in
5. DevOps & Cloud
🔹 Docker + Kubernetes
Containerization ensures your app runs the same way everywhere, while Kubernetes helps scale securely and automatically.
🔹 AWS / Google Cloud / Azure
These cloud platforms offer fintech-ready services like managed databases, real-time analytics, fraud detection APIs, and identity verification tools.
🔹 CI/CD Pipelines
Using tools like GitHub Actions or GitLab CI/CD helps push secure code fast, with automated testing to catch issues early.
6. Bonus: AI & ML Tools
AI is becoming integral in fintech — from fraud detection to credit scoring.
TensorFlow / PyTorch for machine learning
Hugging Face Transformers for NLP in customer support bots
LangChain (for LLM-driven insights and automation)
Final Thoughts
Choosing the right tech stack depends on your business model, app complexity, team skills, and budget. There’s no one-size-fits-all, but the stacks mentioned above offer a solid foundation to build secure, scalable, and future-ready fintech apps.
In 2025, the competition in fintech is fierce — the right technology stack can help you stay ahead.
What stack are you using for your fintech app? Drop a comment and let’s chat tech!
https://www.linkedin.com/in/%C3%A0ksh%C3%ADt%C3%A2-j-17aa08352/
#Fintech#AppDevelopment#TechStack2025#ReactJS#NestJS#Flutter#Django#FintechInnovation#MobileAppDevelopment#BackendDevelopment#StartupTech#FintechApps#FullStackDeveloper#WebDevelopment#SecureApps#DevOps#FinanceTech#SMTLABS
0 notes
Text

ISAM Online Training Top & Best Rank of Banglore 2025
IBM Security Access Manager (ISAM) Online Training Top & Best Rank of Banglore 2025 is a robust identity and access management (IAM) tool that assists organizations in safeguarding their digital resources, securing user authentication, and applying access policies. ISAM offers centralized access control, multi-factor authentication, single sign-on (SSO), and support for cloud and on-premise applications, thus emerging as a vital security and compliance enhancement tool.Our ISAM Online Training is formulated to empower IT professionals, security administrators, and developers with skills to implement, configure, and manage ISAM efficiently. You can be either an IAM newbie or a veteran professional who needs to enhance skills; this course addresses all vital areas of IBM Security Access Manager.Introduction to IBM Security Access Manager (ISAM) Overview of Identity and Access Management (IAM) ISAM architecture and components Deployment options and system requirements User Authentication and Access Control Authentication mechanisms (password-based, multi-factor authentication) Configuring authentication policies and risk-based authentication Implementing Single Sign-On (SSO) Federated Identity Management Understanding Federation and SAML concepts Integrating ISAM with cloud-based applications Implementing OAuth, OpenID Connect, and JWT tokens Web and API Security Configuring Reverse Proxy for Web Security Protecting REST APIs using ISAM Implementing Web Access Control Policies ISAM Administration and Troubleshooting User Management and Role-Based Access Control Logging, Monitoring, and Auditing Security Events Debugging and troubleshooting ISAM configurations Integration with Other Security Solutions Connecting ISAM with LDAP and Active Directory Integrating ISAM with IBM Security Verify Customizing ISAM with Java and API Extensions Who Should Attend? Security professionals and IAM specialists IT administrators responsible for user access management Developers integrating authentication and authorization into applications Compliance officers ensuring regulatory security requirements Why Choose Our ISAM Online Training? Expert-Led Training: Learn from industry professionals with hands-on experience Comprehensive Course Content: Covers ISAM fundamentals to advanced security features Real-World Projects: Practical implementation of security solutions Flexible Online Learning: Self-paced and instructor-led training options available By the end of this ISAM Online Training, participants will gain in-depth knowledge of access management, authentication protocols, and ISAM configuration. This training prepares you for roles such as IAM Consultant, Security Administrator, and Access Management Specialist. Start your journey in identity and access management with our ISAM Online Training and enhance your cybersecurity skills today!
[email protected], +91-9148251978,+91-9008906809
0 notes
Text
Provide insights into securing Java web and desktop applications.

Securing Java web and desktop applications requires a combination of best practices, security libraries, and frameworks to prevent vulnerabilities like SQL injection, XSS, CSRF, and unauthorized access. Here’s a deep dive into key security measures:
1. Secure Authentication and Authorization
Use Strong Authentication Mechanisms
Implement OAuth 2.0, OpenID Connect, or SAML for authentication.
Use Spring Security for web applications.
Enforce multi-factor authentication (MFA) for added security.
Example (Spring Security Basic Authentication in Java Web App)java@Configuration @EnableWebSecurity public class SecurityConfig { @Bean public SecurityFilterChain securityFilterChain(HttpSecurity http) throws Exception { http .authorizeHttpRequests(auth -> auth .requestMatchers("/admin/**").hasRole("ADMIN") .anyRequest().authenticated()) .httpBasic(); return http.build(); } }Implement Role-Based Access Control (RBAC)
Define roles and permissions for users.
Use JWT (JSON Web Tokens) for securing APIs.
Example (Securing API using JWT in Spring Boot)javapublic class JwtUtil { private static final String SECRET_KEY = "secureKey"; public String generateToken(String username) { return Jwts.builder() .setSubject(username) .setIssuedAt(new Date()) .setExpiration(new Date(System.currentTimeMillis() + 1000 * 60 * 60)) .signWith(SignatureAlgorithm.HS256, SECRET_KEY) .compact(); } }
2. Secure Data Storage and Transmission
Use Secure Communication (HTTPS & TLS)
Use TLS 1.2+ for encrypting data in transit.
Enforce HSTS (HTTP Strict Transport Security).
Encrypt Sensitive Data
Store passwords using bcrypt, PBKDF2, or Argon2.
Use AES-256 for encrypting sensitive data.
Example (Hashing Passwords in Java)javaimport org.mindrot.jbcrypt.BCrypt;public class PasswordSecurity { public static String hashPassword(String password) { return BCrypt.hashpw(password, BCrypt.gensalt(12)); } public static boolean verifyPassword(String password, String hashedPassword) { return BCrypt.checkpw(password, hashedPassword); } }
Use Secure Database Connections
Use parameterized queries to prevent SQL injection.
Disable database user permissions that are not required.
Example (Using Prepared Statements in JDBC)javaPreparedStatement stmt = connection.prepareStatement("SELECT * FROM users WHERE username = ?"); stmt.setString(1, username); ResultSet rs = stmt.executeQuery();
3. Protect Against Common Web Vulnerabilities
Prevent SQL Injection
Always use ORM frameworks (Hibernate, JPA) to manage queries securely.
Mitigate Cross-Site Scripting (XSS)
Escape user input in web views using OWASP Java Encoder.
Use Content Security Policy (CSP) headers.
Prevent Cross-Site Request Forgery (CSRF)
Use CSRF tokens in forms.
Enable CSRF protection in Spring Security.
Example (Enabling CSRF Protection in Spring Security)javahttp.csrf().csrfTokenRepository(CookieCsrfTokenRepository.withHttpOnlyFalse());
4. Secure File Uploads and Deserialization
Validate File Uploads
Restrict allowed file types (e.g., only images, PDFs).
Use virus scanning (e.g., ClamAV).
Example (Checking File Type in Java)javaif (!file.getContentType().equals("application/pdf")) { throw new SecurityException("Invalid file type"); }
Avoid Untrusted Deserialization
Use whitelisting for allowed classes.
Prefer JSON over Java serialization.
Example (Disable Unsafe Object Deserialization in Java)javaObjectInputStream ois = new ObjectInputStream(inputStream) { @Override protected Class<?> resolveClass(ObjectStreamClass desc) throws IOException, ClassNotFoundException { throw new InvalidClassException("Deserialization is not allowed"); } };
5. Secure Desktop Java Applications
Use Code Signing
Sign JAR files using Java Keytool to prevent tampering.
shjarsigner -keystore mykeystore.jks -signedjar SecureApp.jar MyApp.jar myaliasRestrict JavaFX/Swing Application Permissions
Use Java Security Manager (deprecated but useful for legacy apps).
Restrict access to file system, network, and system properties.
Encrypt Local Data Storage
Use AES encryption for storing local files.
Example (Encrypting Files with AES in Java)javaCipher cipher = Cipher.getInstance("AES"); cipher.init(Cipher.ENCRYPT_MODE, new SecretKeySpec(key, "AES")); byte[] encrypted = cipher.doFinal(data);
6. Logging and Monitoring for Security
Use Secure Logging Frameworks
Use logback or SLF4J.
Avoid logging sensitive data like passwords.
Monitor for Anomalies
Implement Intrusion Detection Systems (IDS).
Use audit trails and security alerts.
7. Best Practices for Securing Java Applications
✅ Keep dependencies up to date (Use OWASP Dependency Check). ✅ Run security scans (SAST, DAST) using SonarQube, Checkmarx. ✅ Apply the principle of least privilege for database and API access. ✅ Enforce strong password policies (min length, special characters). ✅ Use API Gateway and rate limiting for public-facing APIs.
Conclusion
Securing Java web and desktop applications requires multi-layered security across authentication, data protection, and vulnerability mitigation. By following best practices like strong encryption, secure coding techniques, and continuous monitoring, developers can protect applications against cyber threats.
WEBSITE: https://www.ficusoft.in/core-java-training-in-chennai/
0 notes
Text
How To: Configure Qlik Sense Enterprise SaaS to Use Azure AD as an IdP
Introduction
Establishing Qlik Sense Enterprise SaaS to use Azure Active Directory (Azure AD) as an identity provider (IdP) is key for companies aiming to streamline access control and authentication for users. Integration between Azure AD and Qlik Sense Enterprise SaaS allows organizations to take advantage of single sign-on (SSO), multi-factor Authentication (MFA), enhanced security features that improve user experience while increasing security simultaneously.

This detailed guide will take you step-by-step through the steps to configure Qlik Sense Enterprise SaaS so it authenticates users by using Azure A.
Prerequisites
Before starting, be sure to are:
An active Azure AD subscription
An Qlik Sense Enterprise SaaS account with administrative access
Permissions to sign up an application within Azure AD
A brief introduction of OAuth 2.0 as well as OpenID Connect (OIDC).
Step 1: Register Qlik Sense Enterprise SaaS in Azure AD
1.1 Access Azure AD
Log into the Azure portal (https://portal.azure.com).
Go through Azure Active Directory from the left menu.
Click on App registrations, then Click New registration.
1.2 Create a New Application Registration
Choose a name for the application (e.g., "Qlik Sense SaaS").
Under the account types that are supported choose Accounts in this organization directory only.
Under the Redirect URI section, click Web and type in the URL:
https:// .qlikcloud.com/login/callback
Click Register.
1.3 Copy Application Credentials
After registration Copy and store the data science information for future use:
Application (client) ID
Directory (tenant) ID
Step 2: Configure Client Secret
2.1 Generate a Client Secret
Click on Certificates and Secrets within the Azure AD application.
Under Client secret, select for a new client's secret.
Select a description, and then an expiration date.
Copy the secret value.
Step 3: Configure API Permissions
3.1 Assign API Permissions
Visit API permissions in the account of your Azure AD application.
Add permissions by clicking the Add button. Microsoft Graph - Delegated permissions.
Find and select:
openid
Email
Profile
offline_access
Select Add Permissions, and Grant admin permission.
Step 4: Configure Qlik Sense Enterprise SaaS
4.1 Access Identity Provider Settings
Log into Qlik Sense Enterprise SaaS as an administrator.
Navigate to Management Console - Identity Providers.
Click Create New, then select OIDC.
4.2 Enter Azure AD Configuration Details
Complete the fields required:
Issuer (Discovery URL):
https://login.microsoftonline.com//v2.0
(Replace"tenant_id" with Your Azure Directory ID)
Client ID (Paste your Application ID into Azure AD)
The Client Secret (Paste your generated secret client)
Authentication Method: Choose Authorization Code
Redirect URL:
https:// .qlikcloud.com/login/callback
4.3 Map User Claims
In the section titled User Claims Mapping Section, you can configure:
Sub - User ID
email - email
Name - Display name
Click Save to save the settings.
Step 5: Test and Verify Integration
5.1 Assign Users in Azure AD
Go to Enterprise Applications in Azure AD.
Choose which Qlik Sense SaaS application.
Click Users and Groups to add users and groups. Assign appropriate users.
5.2 Log into Qlik Sense SaaS with Azure AD
Open Qlik Sense Enterprise SaaS within browser.
Click Sign In with Microsoft.
Log in using in your Azure AD credentials and verify your account.
If the login succeeds, Azure AD is successfully set up to be the IdP to QlikSense Enterprise SaaS.
Troubleshooting Common Issues
Issue 1: Authentication Error
Make sure the redirect URI is identical to the one to the settings in Azure AD and Qlik Sense settings.
Verify that the client's ID and secret are accurate.
Issue 2: User Not Found in Qlik Sense
Confirm that the user has been associated with an account in the Azure AD application.
Make sure you check the claim mappings in Qlik Sense.
Issue 3: Invalid Permissions
Make sure Admin Consent is granted In API Permissions.
Verify that email, openid profile and offline_access permissions are granted.
Conclusion
Follow this step-by-step guide to set up Qlik Sense Enterprise SaaS to utilize Azure AD for its identity Provider (IdP). This integration improves the security of users, their management and access control, while simplifying authentication using SSO. (SSO).
The implementation of Azure Active Directory with Qlik Sense SaaS gives users an improved user experience, improves the compliance of users, and simplifies identity management. If problems arise, examining the claim mappings API access rights, and redirect URIs can help you resolve the issue quickly.
Utilizing Azure AD's authentication capabilities companies can enhance both security and efficiency in the Qlik Sense training enterprise SaaS environment.
FAQs
Q1. Do I have the ability to configure the multi-factor authentication (MFA) in Qlik Sense SaaS users?
Yes MFA can be enabled MFA via Azure AD's Conditional Access Policies.
Q2. Does this integration work with user groups?
Sure, however you must to set up group claim mappings within Azure AD as well as Qlik Sense.
Q3. What is the consequence if the secret client expires?
You must create the new client key in Azure AD and update it to the Qlik Sense settings.
0 notes
Text
Best Strategies to Protect Your Data Privacy and Security in the Cloud?
In today’s digital world, businesses are rapidly migrating to the cloud to streamline operations, reduce costs, and enhance scalability. However, with the increasing adoption of cloud computing comes a crucial challenge — ensuring data privacy and security in the cloud.
youtube
Cyber threats, data breaches, and compliance failures can cost businesses millions, tarnishing reputations and leading to severe legal repercussions. So, how can organizations safeguard their cloud-stored data effectively? Let’s explore the best cloud security practices and actionable strategies you can implement to secure sensitive information.
1. Implement Strong Data Encryption
Encryption is a fundamental pillar of cloud security. By encrypting data at rest, in transit, and during processing, businesses can prevent unauthorized access. Using Advanced Encryption Standards (AES-256) and robust key management practices ensures that even if cybercriminals intercept data, they won’t be able to decipher it.
2. Multi-Factor Authentication (MFA) for Enhanced Access Control
Many data breaches occur due to weak or compromised passwords. Implementing multi-factor authentication (MFA) ensures that only authorized personnel can access sensitive data. Biometric authentication, OTP-based logins, and smart token verification add extra layers of security to cloud platforms.
3. Regular Security Audits & Compliance Adherence
Following ISO 27001, GDPR, HIPAA, and SOC 2 standards ensures cloud security compliance. Conducting regular penetration testing and vulnerability assessments helps identify and fix security loopholes before hackers exploit them.
4. Implement Zero Trust Security Model
Adopting a Zero Trust Architecture (ZTA) ensures that every access request is verified, regardless of its origin. This model enforces strict access policies, continuously authenticating users and devices before granting permissions.
5. Secure API Endpoints & Cloud Applications
Cloud services heavily rely on APIs, making them a prime target for cyber threats. Securing APIs with OAuth, OpenID Connect, and API gateways helps prevent unauthorized data exposure and API abuse.
6. Data Backup & Disaster Recovery Plans
Data loss due to cyberattacks or cloud failures can cripple businesses. Implementing automated cloud backups, disaster recovery solutions, and redundancy strategies ensures seamless data restoration during emergencies.
7. Train Employees on Cloud Security Awareness
Human error remains one of the biggest cybersecurity risks. Conducting regular security awareness training helps employees recognize phishing attacks, suspicious activities, and best practices for maintaining cloud data privacy.
Watch the Full Expert Guide on Cloud Security
For a comprehensive breakdown of cloud data security strategies, watch this insightful video: How Can You Ensure Data Privacy and Security in the Cloud?
This video dives deeper into the latest security trends, risk mitigation techniques, and best practices to keep your cloud data safe. Don’t miss out — stay ahead in cyber security!
Final Thoughts

If you found this article valuable, share it with your network and let’s make cloud security a top priority! For more expert insights, be sure to subscribe to PiLog Group’s YouTube channel and stay updated with the latest in cloud security and data governance.
1 note
·
View note
Text
The Importance of Security in .NET Applications: Best Practices

When it comes to developing secure applications, there is no room for error. As cyberattacks become increasingly sophisticated, ensuring the security of your .NET applications is more important than ever. With a rapidly growing reliance on web services, APIs, and cloud integrations, .NET developers must stay vigilant about safeguarding their software from vulnerabilities. In this blog, we will explore the importance of security in .NET applications and provide best practices that every developer should follow to protect their applications from potential threats. If you're involved in Dot Net Development, it's crucial to understand how to implement these practices to ensure a secure environment for both users and developers.
Why Security Matters in .NET Applications
.NET is a powerful framework used to build a wide range of applications, from web and mobile apps to enterprise-level solutions. While the framework itself offers many built-in features for developers, such as managed code and type safety, security must still be a priority. Vulnerabilities in your .NET applications can lead to catastrophic results, such as data breaches, unauthorized access, or even financial losses. As a result, focusing on security from the early stages of development can mitigate these risks and provide long-term protection.
Best Practices for Securing .NET Applications
Securing .NET applications doesn't need to be complicated if the right practices are followed. Below, we discuss several key strategies for ensuring the security of your applications:
1. Use Secure Coding Practices
The foundation of secure .NET application development starts with using secure coding practices. This includes:
Input Validation: Always validate user input to avoid SQL injection, cross-site scripting (XSS), and other injection attacks. Use techniques like whitelisting and regular expressions to ensure that data is clean and safe.
Error Handling: Avoid exposing stack traces or any sensitive information in error messages. Instead, log detailed errors server-side and show users a generic message to prevent attackers from gaining insights into your system.
Use Parameterized Queries: Never concatenate user input directly into SQL queries. Use parameterized queries or stored procedures to ensure safe interactions with databases.
2. Implement Authentication and Authorization Properly
In .NET applications, authentication and authorization are vital to securing sensitive data. These two concepts should never be compromised.
Authentication: Use trusted authentication mechanisms such as OAuth or OpenID Connect. ASP.NET Identity is a useful library to implement user authentication and management. Always prefer multi-factor authentication (MFA) when possible to add an extra layer of security.
Authorization: Ensure that users only have access to the resources they are authorized to view. Leverage role-based access control (RBAC) and fine-grained permissions to enforce this principle. This will ensure that even if an attacker gains access to one part of your system, they can't exploit other areas without the proper credentials.
3. Encryption and Data Protection
Encryption is one of the most effective ways to protect sensitive data. When working with .NET applications, always implement encryption both for data at rest (stored data) and data in transit (data being transferred between systems).
Use HTTPS: Always ensure that data transmitted over the network is encrypted by using HTTPS. This can be done easily by enabling SSL/TLS certificates on your server.
Encrypt Sensitive Data: Store passwords and other sensitive data like payment information in an encrypted format. The .NET framework provides the System.Security.Cryptography namespace for secure encryption and decryption. Use strong encryption algorithms like AES (Advanced Encryption Standard).
4. Regularly Update Libraries and Dependencies
In many cases, vulnerabilities are introduced through third-party libraries and dependencies. Using outdated libraries can expose your application to various security risks. To mitigate this, always:
Regularly update all libraries and dependencies used in your .NET application to their latest secure versions.
Use tools like NuGet to check for outdated packages and apply necessary updates.
Consider using a vulnerability scanner to automatically identify any known vulnerabilities in your dependencies.
5. Implement Logging and Monitoring
Security isn't just about preventing attacks; it's also about detecting them when they occur. Implement proper logging and monitoring to track suspicious activities and respond quickly to potential breaches.
Logging: Log every critical event, including login attempts, access control changes, and sensitive data access. Use structured logging to make it easier to analyze logs.
Monitoring: Set up real-time alerts to notify you about abnormal activities or patterns that might indicate an attempted attack.
The Role of Security in Mobile Apps
As more businesses extend their services to mobile platforms, the importance of securing mobile applications has risen significantly. While the underlying principles of securing .NET applications remain the same, mobile apps come with additional complexities. For instance, developers should take extra care in managing API security, preventing reverse engineering, and handling sensitive user data on mobile devices.
To understand the potential costs of developing secure mobile applications, you might want to use a mobile app cost calculator. This tool can help you assess the cost of integrating security measures such as encryption, user authentication, and secure storage for mobile apps. If you're interested in exploring the benefits of Dot net development services for your business, we encourage you to book an appointment with our team of experts.
Book an Appointment
Conclusion
Security is paramount in the development of any .NET application. By implementing secure coding practices, robust authentication and authorization mechanisms, encryption, and regular updates, you can protect your application from the ever-growing threat of cyberattacks. Additionally, leveraging proper logging, monitoring, and auditing techniques ensures that even if a breach does occur, you can identify and mitigate the damage swiftly.
If you're working with .NET technology and need help building secure applications, consider partnering with a Dot Net Development Company. Their expertise will help you implement the best security practices and ensure your applications remain safe and resilient against future threats.
0 notes