#powershell upload file to website
Explore tagged Tumblr posts
Text
Upload file with Powershell GUI
Upload file with Powershell GUI

In this post, we are going to dicuss about the file upload using the Powershell GUI. Instead of thinking highlevel, here i had split the three simple task to achieve the file upload functionality in the powershell.
Create Simple PowerShell UI for browsing the location of files with one textbox and two button type (upload & cancel) with help of system.Windows.Forms
In Browse button click event,…
View On WordPress
#powershell invoke-restmethod upload file#powershell invoke-webrequest upload file#powershell upload file ftp#powershell upload file http#powershell upload file multipart/form-data#powershell upload file to artifactory#powershell upload file to sharepoint online#powershell upload file to website#Upload file with Powershell GUI
0 notes
Text
TOOL TUTORIAL 2
Gifski
GIF GENERATION AND OPTIMIZATION
Tool Type: GUI or Command line tool (there are two versions)
Difficulty: Easy (GUI); Moderate (CLI)
Operating systems: Mac, Windows, and Linux (CLI only—no GUI)
Input(s): Video files (MP4)




How much of a difference can you tell between these two gifs?
Both seem to give good results, but to me, in the top row, the one on the left looks better, but in the bottom, row, the one on the right looks better.
Gifs in the left hand column are converted and compressed to 500 px using the ffmpeg command from Tutorial 1; in the right column, using Gifski.
Gifski GUI Version (Mac and Windows)
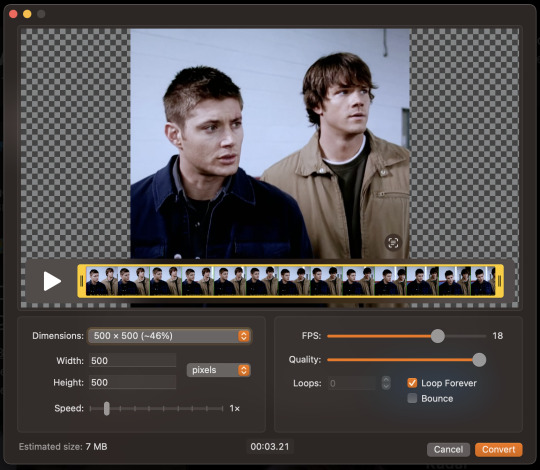
NOTE: Gifski is solely for converting MP4 clips to optimized gifs. If you need to caption or color, you have to do that externally.
Installation
The GUI version of Gifski is available in the Apple App store, but links to it and the Windows downloader can be found through the official site.
Using the GUI
After opening your MP4 file, in the bottom left corner, you can see the estimated size of your resulting gif. This estimate will auto-update as you adjust your compression settings. Remember: To upload your gif on Tumblr, it needs to be about 10MB or less. If it's already 10MB, just go ahead and click convert! If not (which is more than likely):
Adjust FPS to 18. I find this frame rate to be a good balance of compression and retained quality.
Decrease the dimensions of your gif as needed. Whether you use the drop down box or the dialogue boxes, Gifski will automatically scale to retain your gif's screen ratio rather than stretch it to fit, so you don't need to worry about keeping your gif proportional.
You can finely adjust the settings until your gif is exactly 10 MB if you want to keep the best quality, or just aim for a ballpark.
Cick "Covert" then save the resulting gif. Do this for all your .mp4 clips and then boom. You're done.
Gifski Command Line Version (Linux, Mac, Windows)
There is a command line version of Gifski just like there's a command line version of ffmpeg. While the GUI version isn't available for Linux, the command line version is also available for Linux.
Installation
This must be installed separately from the GUI version, via your system shell (Powershell on Windows, Terminal on MacOS). I recommend you install via Homebrew if you're on Mac or Linux by pasting this into your terminal (if/once Homebrew is installed):
brew install gifski
Windows users or other users who don't want Homebrew can follow directions on the Gifski website.
Converting one video file to GIF
This simple command will convert one .mp4 file to .gif (parts in red can be adjusted, parts in blue should be changed):
cd FilePathToYourMP4 gifski --fps 18 --width 500 --quality 100 -o output.gif input.mp4
Where input.mp4 is the name of the MP4 clip you want to make into an optimized gif and output.gif is the desired name of your gif on output.
How to adjust the options in the script:
Change the number frames per second (fps). Go to fps=18 and change “18” up or down.
Scale the gif up or down. Go to width 500 and change “500” up or down to scale the gif up and down by its pixel width.
Change the quality. Go to quality 100 and change “100” to any value between 0 and 100, where 100 is the highest quality.
Converting a folder of video files to GIF
Place all of your video clips into a folder called gifset1. Put an empty subfolder inside the gifset1 folder called gifs. Go to your system shell and copy and paste the following indented text:
Linux and Mac:
cd ~/Desktop/gifset1 for i in .mp4; do gifski --fps 18 --width 500 --quality 100 -o gifs/${i%.}.gif "$i"; done
Windows:
cd ~\Desktop\gifset1 for i in .mp4; do gifski --fps 18 --width 500 --quality 100 -o gifs\${i%.}.gif "$i"; done
Once the process is finished running (your shell prompt will reappear allowing you to type in commands again) if you go to to the gifs subfolder in your gifset1 folder, you will find an optimized gif of every video file has been rendered.
2 notes
·
View notes
Text
Are On-line YouTube To MP3 Converters Just Lifeless?
A utility to transform a Flac library to MP3, Opus or Ogg Vorbis format. After the above setting, click on "Convert" button to start out converting Spotify music to MP3. Earlier than converting videos to MP3 files, users can set audio quality, quantity normalization and MP3 volume. MP3 (MPEG-1 Audio Layer three) is a digital audio encoding format for client audio storage. An MP3 file can be constructed at higher or decrease bit rates, with higher or decrease ensuing high quality. This highly effective conversion software for Windows and Mac can help you not solely with changing FLAC to MP3 but additionally with a number of other media file conversion and compatibility issues. Simply download the appropriate version of Video Converter and observe the guide under. Choose Audio Recorder from the interface of Display Recorder, allow System Audio and Disable Microphone Audio, so you can get prime quality audio effect. Within the settings, click on Output - Audio format and set it in MP3. Click on OKAY to click on Rec to start out. With this free on-line mp3 cutter you may reduce a portion from any audio file, or convert a video to MP3 format, and save the result as a MP3 music file or ringtone for you cell phone such as Samsung Galaxy S8, Apple iPhone 8S Plus. It enables to cut an audio with an accurate starting time and ending time in milliseconds. Click the "Add File" icon to import your MP2 audio information. Or, simply select your MP2 recordsdata and then drag them to this mp2 to mp3 online MP3 Converter. Free DVD converter: Convert video to DVD, or convert DVD to MP4, MP3 and extra. An excellent Apple software however let's face it: there are various higher selections to convert MP3 and audio recordsdata than using iTunes. It's too difficult. Whole Audio Converter can easily convert almost any audio to WAV, MP3, OGG, WMA, APE, FLAC, MP4, AAC, MPC. Since converting CDA to MP3 online is not feasible, the first method to convert CDA is to use Home windows Media Player. Open Windows Media Player and swap to Library Mode. Library mode is better within the sense you could choose exactly which tracks you want to rip instead of ripping the complete CD. An MP3 CD is a KNOWLEDGE CD which accommodates music stored in a number of (often many) MP3 files. Free download this highly effective TTA Converter to convert TTA to MP3, FLAC, WAV, AIFF, WMA, M4A, AU and AC3 or to separate TTA with CUE file to a number of tracks. Now obviously if you end up time limited and because you would drive yourself insane having to sort in each and every filename it's better to jot down a script to transform all of the files. button and select flv recordsdata you want to convert within the pop-up dialog field. Instantly extract MP3, AAC, WAV, MP2, and so forth from MP4. Total Video Converter from EffectMatrix is without doubt one of the most complete and highly effective items of video conversion software program we evaluated. We would have preferred to put Complete Video Converter in of one in every of our prime spots. Obtain the video converter setup file from Movavi's website. After the download is complete, follow the instructions to install the software. A major draw back to utilizing STOIK Video Converter is that many of the modifying capabilities and file codecs you can save to are only usable if you have the Professional model. This App lets you go the videos you have got in your device to mp3, mp2, aac or wav audio format. Considering the fact that many video information are fairly large, the largest drawback with FileZigZag is the wait time to upload the video and receive your email. It's a life saver for Android customers, aTube catcher has own utility for Android customers with the identical features as properly. In keeping with these parameters, it must be named as among the finest YouTube to Mp3 converters. The AVI to Audio converter software program extracts audios from the AVI movies, and then encodes the audios in the format of MP3, WMA, AAC or any of the supported audio file codecs. Customers can select a segment of the AVI video to be transformed to audio file. Free Audio Converter supplies the most comprehensive options for music followers to transform audio between MP3, WMA, WAV, AAC, MP2, M4A and OGG codecs as well as convert different unprotected audio codecs. Lossless audio codecs like FLAC, ALAC, APE, and so forth. are additionally supported for top-quality enjoyment. It might probably deal with batch conversion up to sixteen simultaneous processes. MPlayer is a media player that supports a wide range of multimedia codecs. It's usually used for playing video with a GUI, however can also be used (in batch mode without a GUI) to transform the audio to WAV format. MPlayer is accessible for Linux (bundle "mplayer"), Windows and Mac OS X. The ATSC specification and MPEG-2 enable using progressive frames, even within an interlaced video sequence. For instance, a station that transmits 1080i60 video sequence can use a coding method the place these 60 fields are coded with 24 progressive frames and mp2 to mp3 online metadata instructs the decoder to interlace them and carry out 3:2 pulldown earlier than show. This allows broadcasters to modify between 60 Hz interlaced (news, cleaning soap operas) and 24 Hz progressive (prime-time) content with out ending the MPEG-2 sequence and introducing a a number of seconds of delay as the TV switches formats. This is the explanation why 1080p30 and 1080p24 sequences allowed by the ATSC specification aren't used in apply. Moreover customary MP3 format, MP3 Toolkit supports most of fashionable audio & video codecs like WMA, WMV, MP4, WAV, OGG, FLV, MOV, M4P, M4A and more, additionally helps prime quality audio like FLAC and APE. With MP3 Toolkit, you'll be able to convert, cut, merge, rip and document MP3. Properly, whenever you google Spotify to mp3 converter, you'll get all types of results. Most of them are Spotify converter however not Spotify to mp3 converter. They can convert Spotify playlists to different music providers like Deezer, Apple Music, and many others., however not offline mp3 songs. The way to discover actual Spotify to mp3 converters that work stably? Right here we'll listing the most common Spotify converters and Spotify to mp3 converters. , the individuals behind VLC, have also put collectively a collection of script information that use PowerShell or CMD in Windows or the terminal in Linux to batch convert tiles in VLC. When you desire doing issues with scripts, this web page is for you. After launch Faasoft Opus to MP3 Converter, follow the detailed information to convert Opus to MP3. Step three: Convert videos to MP4 or MP3. Simply with three clicks, you may get the wonderful movie with iwisoft free video converter. Easy to use for each newbies and superior customers.
1 note
·
View note
Text
2 Free Ways To Convert MP4 To Wav On-line And Offline
Is the quickest and best option to convert audio to video on-line. An audio file converter is one form of file converter that (surprise!) is used to transform one sort of audio file (like an MP3 , WAV , WMA , and so forth.) into another sort of audio file. You possibly can play around with the settings too because each format has a profile equipment and a preset editor, giving you extra control over your conversions. , the people behind VLC, have additionally put together a sequence of script files that use PowerShell or CMD in Home windows or the terminal in Linux to batch convert tiles in VLC. The files might be performed again in QuickTime, Home windows Media Player, Wav Player and some other applications. As soon as your information are chosen, click on the Open" button within the lower-proper corner to add the file to the conversion queue. Furthermore, it helps on-line database lookups from, e.g., Discogs, MusicBrainz or freedb, permitting you to mechanically collect correct tags and obtain cover artwork for your music library. Besides online converter to switch MP4 format to WAV format, this text additionally prepares 2 wonderful packages. If it's good to ceaselessly convert files or a lot of recordsdata at once, we suggest spending between $20 and $30 on a program that does not crash typically and may batch convert multiple information at once. On the Format Manufacturing unit popup you will simply click on the "OKAY" button, unless of course you want to add one other file. What's more, it allows users to transform their audio file between various audio codecs, together with WMA, WAV, AAC, OGG, MP3, M4A, etc. To know extra about our audio edit expertise, please go to On-line Audio Converter web page. The Wav, Mp4, Ogg, APE, FLAC, AAC normalization and check is fulfilled on a peak degree (Peak Normalization) and on an average degree (RMS normalization). As a substitute of eradicating the DRM encryption, Tunebite data the audio or video file and converts it to a format you should utilize on any media player. This is how to batch convert media recordsdata in VLC. Audio file converter tools are additionally helpful in case your favourite music app in your telephone or pill does not help the format that a new track you downloaded is in. An audio converter can convert that obscure format right into a format that your app helps.

You can also use MP4 to WMA converter to transform audio information like MP3, WMA, WAV, OGG, FLAC, M4A, MP2, and many others. By default the MP4 muxer writes the 'moov' atom after the audio stream ('mdat' atom) at the finish of the file. WAV files are mostly used on Home windows platform, being supported by Home windows Media Players and other applications. You possibly can add audio (in mp3 format) to a video file (avi, mp4, mov, wmv). I believe different individuals would have different opinions in direction of issues, so you can produce other options like the online converters. Simply add your movies to the software and convert information in a daily manner. However, if you must convert an audio file using your phone, these are the best options. Your file will likely be transformed and added to the iTunes playlist you created. AAC is a patented audio-format that has increased capabilities (variety of channels, discretion frequency) as in comparison with MP3. At times, you might have acquired your favourite trailers inmp4 extension from video-sharing websites, and needed to converted intowav to play on a media participant with better high quality. The right way to reduce the file measurement of MP3 information. In easy terms, a format might be in comparison with a container during which a sound or a video sign might be stored utilizing a specific codec. A free net app that converts video files, allowing you to alter the video format, decision or size right in your browser. ITunes would start converting M4A to WAV format. The default content of a WAV file is uncompressed (although they can be utilized to retailer compressed formats comparable to MP3), pulse code modulated (PCM) digital samples derived from the analog supply. It supports a protracted list of 26 audio enter codecs including MP3, WAV, FLAC, and AAC. Examine the highest box in order for you Cloud Convert to send the resulting MP3s on to your Dropbox, Google Drive, OneDrive, or Box account after the conversion is complete. A number of the output audio formats it support includes MP3, WMA, WAV, FLAC, MP4, MPC, OPUS, and over 20 more formats. It's also possible to set advanced options for both conversions which let you rotate the video, cut it, change the display size, change the bitrate of the downloaded audio and extra. Choose the item and click on the Open" button to import the audio into the application. It only lists formats which belong to the group of supported files, however with unsupported options. You possibly can upload distant audio recordsdata via their direct URL in addition to information stored in your Google Drive account. Hit Add" button and select the files you want to convert, and then click Open" to upload recordsdata. Convert video and audio files to OGV (Ogg video) format. Choose ".mp3" from the drop-down selector.

It could also rip CDs and convert online flash videos to audio, too. You can select among a few codecs, such as WAV, MP3, Ogg, MP4, FLAC, APE and others, and also rip audio CDs to the computer. It has a straightforward-to-use interface and wav to mp4 converter with image batch converts and exports in a lot of the fashionable formats, like MP3, WAV, ACC and FLAC. Furthermore, under the video preview window, "Merge Output Video" choice could be checked for batch MP4 to WAV conversions. Convert your audio like music to the WAV format with this free on-line wav to mp4 converter with image converter.
1 note
·
View note
Text
APE To FLAC Converter
Most portable audio gamers can play music encoded in the MP3 audio format, however some shoppers also have music in Ogg Vorbis , FLAC , MPC , or even WMA files. Fre:ac is another open source undertaking that has probably the most options for converting between audio codecs. It consists of several encoders by default, so you don't have to go and obtain separate information for WAV, FLAC, and many others. The converting APE to FLAC step-by-step information is offered as blow on your reference. You'll be able to shortly invite others to view, obtain and collaborate on all the recordsdata you need, no electronic mail attachment wanted. You possibly can add remote audio files via their direct URL in addition to information stored in your Google Drive account. Open your e mail and download the newly transformed FLAC file. Extra superior users can customise many encoding parameters: audio bitrate, bitrate mode, number of audio channels, audio sampling frequency, volume, time vary and different. Arrange transformed information , utilizing data from tags: create folders, apply your individual filename pattern automatically. Flacon is launched under the GNU Library Public License (LGPL) version 2. A duplicate of the license is offered right here This is an open supply mission. You're free to download and distribute the software beneath the terms of the license. Converting one file at a time could be tedious and time-consuming. Everybody needs a program that may help conversion of a number of recordsdata at a go with out the effort of going again and including one file at a time. Softwares have been developed to facilitate batch conversion of media information. Top-of-the-line instruments that you can use to convert batch APE to FLAC is the iSkysoft iMedia Converter Deluxe, and the steps of conversion are described within the next a part of this text. Convert your music to the Free Lossless Audio Codec (FLAC) audio format. Add a file or provide a URL to a audio or video file and begin changing. Optional change additional settings to satisfy your wants. This converter helps you to additionally easily extract audio from video files in top quality. The conversion process in itself is very easy: all you must do is observe the step-by-step wizard included in Whole Audio Converter. Nonetheless it appears that evidently the program does not save ID3 tags when converting information. foobar2000 is an advanced freeware audio player for the Windows platform. A few of the basic features include full unicode support, ReplayGain support and native assist for a number of fashionable audio codecs. It helps audio formats equivalent to MP3, MP4, AAC, CD Audio, WMA, Vorbis, Opus, FLAC, WavPack, WAV, AIFF, Musepack, Speex, AU, SND and more with further parts. If you wish to help the artist, there are a number of websites that allow you to purchase FLAC files. Flacon extracts individual tracks from one large audio file (standard for his or her high quality CUE, APE and FLAC) containing the entire album of music and saves them as separate audio recordsdata. Every format is supplied with a profile kit and a preset editor. You'll be able to create new presets, delete and edit the outdated ones, and modify the audio converter settings and parameters. Be interesting to read what members are utilizing at present on ape2flac windows machines to convertape to wav files. Supported Output Codecs : MP3, FLAC, M4A, WMA, AIFF, AAC, WAV, WavPack, OGG, AC3, AMR, MP2, AU. After your audio recordsdata are merged and converted to your chosen filetype, choose the "obtain" button and save the file to your computer or gadget. Once more, you can save it to your gadget, a file-sharing medium like Dropbox or Google Drive, or you possibly can merely hear the merged audio on the website. What's more, you may simply be part of several APE recordsdata and convert to 1 audio FLAC file, trim unwanted audio half and maintain the outstanding part and cut up Ape information by tracks or by file dimension. 4. It converts APE with quick speed and excessive conversion fee. What's the file name of the mac program that wants placing in? I'm running debian and may't find something within the repositories that looks relevant. APE is unhealthy unhealthy unhealthy harmful! Flac is a lot better and more broadly supported. With on-line tools, you needn't obtain too much software program to help you deal with media content material points. Take a quick look to see if the two on-line converters meet your needs. This APE to FLAC Converter allows you to trim the audio size to take away the undesirable part, click on "Trim" button to open the "Edit" window, right here you can trim the audio size by dragging the slide bar to set the start and finish time. I've someFlac albums I ripped as one huge file to save some space (Lossless CD rips are roughly 500mb each), now I've more storage I wish to cut up them back to there authentic information. In the event you're using Music Manager or Google Play Music for Chrome to add music to your library, here are the forms of files you possibly can upload.
Lyrics tags supported (forMP3 ID3v2,OGG,WMA,ASF, APE2, MPC, Flac). So right here comes the query. The place to find a skilled APE to FLAC Converter or an easy and detailed information to assist people solve APE to FLAC changing points? This text is devoted to providing your wished solutions. Hello there, Is it potential to encode wavpack data to flac? I cannot uncover any program that can do that. I've round a thousand folders with wavpack information and that i wish to convert them in flac. MP3 is a lossy format compressed to save lots of knowledge house using variable bit fees, relying on the frequency spectrum content material materials and amplitude. Which suggests distinctive content is lost, as a technique to make the file dimension smaller.Audio Converter Plus gives easy resolution to convert APE to FLAC in batch mode with without quality loss in addition to protect audio tags. In addition to convert APE to FLAC, it also can convert APE to MP3, WAV, M4A and OGG. Once completed, a small pop-up window will appear and click on "OKAY" to complete the entire splitter. At last you'll have every monitor on the album as an individual ". ape file". Then you are free to enjoy your downloaded album with individual songs. Compress-Music supports flac, mp3, wma, aac + more. It's a Powershell script that traverses a directory structure for audio (many codecs) and converts to mp3 in a duplicate listing. Supports gapless, album replaygain, updating tags only.
1 note
·
View note
Text
Best Webapp
Notepads and Notebooks
aNotepad - Saves your notes without user account using cookies
h5Note - Works when offline too using HTML5
shrib - Save note to a custom url and edit it later
Notepad - An Offline capable Notepad PWA
Document Editors
Latex
Papeeria - Latex preview with downloading as PDF option available without registration
Overleaf [Account] - Unlimited collaborators and projects, git access in free account
Sharelatex [Account] - 1 collaborator in free account
Markdown
Dillinger - Powerful markdown WYSIWYG with export to HTML and PDF. User account to save documents
Github.md - Simple Github-style Markdown (GFM) preview with print feature
Markdown Live Preview - Instant markdown preview
Markdownify - A minimal Markdown editor
Others
Online reStructedText Editor - rst.ninjs - WYSIWYG rst preview with option to save document online for editing later
EtherCalc - Online spreadsheet editor, exports to Excel
Programming Editors and IDEs
TutorialsPoint Online Tools - Online terminals for ipython, octave, powershell, redis and lots others. Also has a good collection of IDEs for programming languages
Ideone - Online IDE supporting most popular languages
Repl.it - Online terminals for all popular programming languages
Codechef IDE - Simple single file code compiler supporting major languages
Cloud9 [Account] - Very powerful online dev environment, just like your local PC
JS Bin - Collaborative web development and debugging tool
Codepen.io - Playground for front end web developement
Codenvy [Account] - Cloud workspace for developers, supports most popular stacks including Android, Hadoop, Selenium, Node and lots more
SQLFiddle - A tool for easy online testing and sharing of database problems and their solutions.
Programming Tools
CSS Minifier
UglifyJS JavaScript minifier
HTML minifier by @kangax - Minifies inline CSS and JS too
JavaScript compressor - JS compressor and obsfucator
Android Asset Studio - Android launcher icon, Notification icon etc generator from existing images
Website Speed Test | Pingdom - Feature-rich website tester
Google Structured Data Testing Tool - Test a webpage for structured data and SEO
Regulex - JavaScript regular expression visualizer
Communication
Tlk.io - Create a room with any url (eg tlk.io/some-room) you wish and chat in groups
Discord - Voice and text conference online. Username is asked at start to create a temp avatar
Gruveo - Video conference online. Just like tlk.io, easy to remember custom urls
Appear.in - Video conference online. Create any room like appear.in/some-room and starting chatting
Videolink2 - Video conference online. Link generated, share link to invite other participants
GetARoom.io - Video conference online. Has mobile browser support, just click start new call and share the link
Business and Finance
ShapeShift.io - Instant cryptocurrency conversion
Cryptrader.com - Cryptocurrency price charts and indicators. Saving your settings requires an account
TradingView.com - Real-time information and market insights from various exchanges. Requires an account for saving settings
Music, Radio and Podcasts
Podbay - Listen to any podcast online, individual episodes can be downloaded
Internet Radio - Listen to over 40k radio stations
Stitcher - Listen to podcast online
AnyAudio - Stream and download music
Muki - WebAudio-based chiptune & MIDI player, with a nice collection of video game music
MusixHub - Play artists and albums video songs online, powered by Youtube
plug.dj - Listen to thousands of DJs, powered by Youtube, sign-in required to become a DJ
Graphics, Image and Design
Pixlr Editor - Image editor by pixlr. Lots of features
Photo Editor | Befunky - Image editor with lots of filters and effects
Logo Makr - Logo maker with nice collection of SVGs. Requires payment to export logo as SVG (png is free)
Online Logo Maker - Make logos online. Extra user account feature to save creations
SVG-Edit - Powerful SVG editor with lots of features. Open source
Method Draw - Clean and feature-rich SVG editor. Exports to PNG
Coolors - Color palettes generator
Tiny PNG - Smart PNG and JPEG compression
File Converters
Cloud Convert - Convert from anything to anything including audio, video, font, document and lots more. Excellent integration with cloud storage services like Google Drive and Dropbox. Direct links
Online Convert - Collection of Audio, Video, Image, Document, Ebook and Archive converter. No file size limits and direct download links upon conversion
PDF <=> EPUB - PDF to epub converter and vice versa
Pandoc Try - Inter markup conversion using Pandoc. Supported - Latex, Markdown, HTML, RST and lots more
Print Friendly - Convert any webpage to simple format. Then download it or print as PDF
File Hosting/Sharing
EFShare - Peer to peer secure file sharing
Ge.tt - File hosting service. Max limit 2gb
RGhost - File hosting service, Max limit 100mb without login
ImgSafe - Image hosting service with small direct links
Clyp - Audio sharing without limits, rich API
SendVid - Video hosting service
Archive.org [Account] - Unlimited file hosting of any type, no limits on bandwidth and upload size
Audio and Video
bfxr - Make sound effects for your games
MP3 Cut - Online audio cutter
TwistedWeb Online - Powerful audio editor. Files not saved online
Filelab Audio Editor - Audio editor with basic features like trim, merge, cut audio
Until AM - Online Music mixer, DJ software
YOU.DJ - Online Music mixer, DJ software sourcing music from SoundCloud
VideoToolbox [Account] - Video editor with all the common editing features. Size limited to 600mb
Internet Downloaders
savefrom.net - Download from Youtube, Dailymotion, vimeo and more
youtube-mp3.org - Youtube to mp3 download
Youtube Converter & Downloader - Download youtube video in any audio/video format
keepvid - Youtube, Soundcloud, Facebook downloader
Bitport [Account] - Torrent downloader. Limited to 1 torrent of 1 gb per day in free account
Vubey - Download mp3 from youtube, soundcloud etc in various audio quality (bitrates)
Seedr [Account] - Cloud Based Torrent Downloader. Limited to multiple torrents of total size of 2 gb in free account. Unlimited bandwidth. 500mb increase on contributing a new user
Fuge.it [Account] - Web torrent client. Free tier limited to 2 simulataneous torrents of max size 2gb in free account, 10gb storage, 10 gb bandwidth/month
Security and Cryptography
Encipher.it - AES-256 text encryption and decryption
Encrypted Pastebin - Defuse.ca - Set password on your public pastes
MPCrypt - Securely encrypt files
Study and Education
Calculatoria Calculator - Scientific Calculator online with progress stored on your system
WolframAlpha - A very powerful computational knowledge engine. See plotting graphs examples for help on how to plot graphs.
Desmos Graphing Calculator - Plot multiple 2d plots on same sheet, see graph intersections
Geometry sheet by MathIsFun - Simple geometry sheet online if you want to play with figures
Directed Graph Editor - Play with Directed Graphs
Calcul - Collection of different calculators including Matrix, Unit converters, mathematical distributions and more
Miscellaneous
QR Code Generator - Different type of QR codes like contact info, Wifi, Calendar etc supported
Emoji Search Online - Intelligent emoji search engine
Podcast Feed Extractor - Get rss feed for podcasts
Rss Feed Search - Find rss feeds from search terms
Diff Checker - Compare two text passages and view diffs
is.gd - Link shortener with custom urls and open API (no tokens)
Bitly - A powerful url shortener with REST API
Superbetize - Categorize your grocery list
ASCII.li - Generate text ascii art, ascii emoticons and lots more online
3 notes
·
View notes
Text
Macos Big Sur Virtualbox

In this article, I’m going to show you how to fix macOS Big Sur Screen Resolution on VirtualBox. If you’ve installed macOS Big Sur on Virtualbox so you might have observed, the screen is really small. You can’t scale it to any other resolutions. Because it’s not fixed by default when you install macOS Big Sur or any other versions of macOS on VirtualBox. In this post, I’ll show step by step to fix your macOS screen resolution on Virtualbox. However, this methods are not only for a Mac Operating system but also, for Windows OS as well.
Macos Big Sur Virtualbox Installation Failed
Macos Big Sur Virtualbox Kernel Driver Not Installed
Macos Big Sur Virtualbox
Macos Big Sur Virtualbox Settings
Macos Big Sur Virtualbox Error
Macos Big Sur Virtualbox Image
Macos Big Sur Virtualbox Iso
Fix macOS Big Sur Screen Resolution on VirtualBox
In this post, I’ll explain different ways of fixing macOS Screen resolution on Virtualbox software. One of these methods should work for you as well. If all the methods didn’t work, let us know via the comment section below. This guide is categorized from the most important method to less important. The first method is one of the best methods to fix macOS Big Sur screen Resolution on Virtualbox.
Related: Fix macOS Big Sur Screen Resolution on VMware on Windows
Method #1: Fix macOS Catalina Screen Resolution
Let’s get the ball rolling on how to fix macOS Big Sur screen resolution on VirtualBox on Windows operating system. All these methods are tested by our website visitors so it should work for most of you guys. One of these methods should work absolutely fine. For us, Method 1 has worked all the times and we recommend it to all. The resolution which is mentioned in the notepad file is tested by the wikigain team. If any other resolution also works, let us know. We will add them to the list.
Alternative to providing macOS Big Sur ISO file, we’ll try to cover every aspect of macOS Big Sur. From downloading macOS Big Sur ISO to installing macOS Big Sur on VMware and VirtualBox. In this post, I will simply provide a macOS Big Sur DMG file so get it and enjoy it. There are many other software issues like software unexpectedly quit, and apps like VirtualBox, AdGuard, Chrome, and Steam won't response in macOS Big Sur. What we can advise is to downgrade to a previous system like macOS Catalina and Mojave, and do not upgrade to macOS Big Sur until it is released to the public in a stable condition. The first method is one of the best methods to fix macOS Big Sur screen Resolution on Virtualbox. Related: Fix macOS Big Sur Screen Resolution on VMware on Windows. Method #1: Fix macOS Catalina Screen Resolution. Let’s get the ball rolling on how to fix macOS Big Sur screen resolution on VirtualBox on Windows operating system.
Step #1. Completely Shutdown your macOS Big Sur virtual machine and open up macOS Big Sur Screen Resolution VirtualBox code. Here you need to replace “VM Name” with your virtual machine name. Leave the code opened but Quit VirtualBox completely. It should not be running in the background.
Step #2. Open up the command prompt or Windows Powershell. Press the Windows key in Windows 10. Typ cmd and Run it as administrator.
Run CMD as Admin
Step #3. Now, copy and paste the code to the command prompt (CMD) and make sure to Replace HxV with your desired resolution which is listed in the notepad file. For example, 1920×1080 is one of the resolutions. have a look at the screenshot below to get an idea of how it’s done.
Run the Resolution Code
Step #4. Leave the CMD or PowerShell open, start your macOS Big Sur VM.
#5. Click the Apple icon on the top left corner of the screen then selects About this Mac. From the Display tab, you should see your new resolution. In my case, it’s 1920×1080.
Changed Screen Resolution
Method #2: Fix macOS Big Sur Screen Resolution
This method also has worked for some of our visitors and they mentioned to us and we added in this guide. If you also have another solution, please let us know and we should add it to our list.
Step #1. Shutdown your macOS virtual machine and from the VirtualBox observe your macOS VM Name. Open Screen Resolution VirtualBox code and replace it with your virtual machine name. Make sure to quit VirtualBox. Don’t forget to execute the first command. Change the H and V at the end of each command in method #2 with your desired resolution. H stand for Horizontal and V stands for Vertical.
Macos Big Sur Virtualbox Installation Failed
Change macOS Big Sur Screen Resolution Method 2Once you executed the code by command prompt or PowerShell. Start your macOS Big Sur VM and you should see the new resolution from Display Tab.
4K Resolutions
Other Methods to fix macOS Screen Resolution on VirtualBox
The following tips and methods are also worked for some people. We will list here just in case all the other methods didn’t work. The following methods might work. In all methods, your VM should be shut down and Virtualbox should be Closed. VBox should not be running while executing the code by command prompt or PowerShell. When you run the code, make sure to replace “N” with your desired resolution.
For instance: I would like to set 1024×768, I’ll use number 3 for this resolution.
Macos Big Sur Virtualbox Kernel Driver Not Installed
Example:
Where N can be one of 0,1,2,3,4,5 referring to the 640×480, 800×600, 1024×768, 1280×1024, 1440×900, 1900×1200.
While the VM is running, you can also tell the guest OS to change the resolution by using
The 32 at the end denotes, display color depth.
The following primary display resolutions are supported by macOS on VirtualBox: 5120×2880 2880×1800 2560×1600 2560×1440 1920×1200 1600×1200 1680×1050 1440×900 1280×800 1024×768 640×48.
What we recommend is method 1 which has worked all the times we’ve tested. So if any of this method didn’t work. Disable 3D Acceleration from Virtualbox Settings> Display Menu>Screen Tab.
Conclusion
To sum up this guide, we’ve shown three methods to fix macOS Big Sur Screen Resolution on VirtualBox on Windows PC. Every method is a command line command that needs to be executed to fix the resolution issue. If you’ve any other solution to fix the issue, please feel free to share via comment section down below this post.

Macos Big Sur Virtualbox
This post will provide you with Download macOS Big Sur VMware & VirtualBox Image. Apple kicked off the new working system for the users by the name of macOS 11 Big Sur. At the Worldwide developer conference, you have the best operating system with many extraordinary features and updates. They have made some new and unique modifications to macOS Big Sur. This time WWDC event was fairly different compared to previous events. According to Apple, the Final version of macOS Big Sur will be out in September or October 2020. On the other hand, there are a lot of changes and updates on Safety and performance. Well, Apple always tries its best to be able to provide a much better operating system.
Download macOS Big Sur VMware & VirtualBox Image– Latest Version.
Macos Big Sur Virtualbox Settings
Installing macOS Big Sur on supported is not a challenging undertaking. Due to downloading from AppStore, you can install macOS Big Sur on Mac with no limitation.
Once you get installed, you may enjoy the features of macOS Big Sur such as New Notification Center, Faster Safari, Big UI Refresh, Control Center, New Dock, Particular icons, and many more. The upgrades were especially focused on the brand new design and some much better improvements. Apart from that, Apple also published iOS 14, iPadOS 14, watchOS 7, tvOS 14, and macOS Big Sur. And a few major upgrades to Apple AirPods.
If you do not have Mac or MacBook to attempt macOS Big Sur, then do not worry. There are many ways in which you may set up macOS Big Sur. I believe virtualization software is the best to go with since you can use the same as your actual operating system. Nowadays, the most popular virtualization software is VMware and VirtualBox that provides the ideal user interface. You can use the virtual machine to set up macOS Big Sur, Linux, Windows, Ubuntu, and many more operating systems. Personally, I use VMware & VirtualBox when any operating system becomes released. When you install macOS Big Sur on virtual machines, you can do anything you would like to do.
Creating apps or catch up with each and everything on macOS Big Sur afterward VMware and VirtualBox is going to be the best alternative for you. For this, you will likely want macOS Big Sur VMware & VirtualBox Image because it is one of the main documents while installing. We’ve made or created VMware, and VirtualBox images, particularly for the digital machines, and it doesn’t work someplace else. If you’d like an image for Hackintosh, then you can directly download it from App Store.
To install macOS Big Sur on virtual machines, you have to Download macOS Big Sur VMware & VirtualBox image. Because VMware & VirtualBox accept VMDK expansion, which stands for Virtual Machine Disc. A single VMDK image will do the job for both VMware & VirtualBox. But, creating the macOS Big Sur image for virtual machines is difficult for the newbie. We have established VMware and VirtualBox image and successfully uploaded on Google Drive and MediaFire to reduce virus and malware. Head towards the under sections.
Pictures: The photographs are just amazing in macOS Big Sur. You can access all your albums and press types from the sidebar. It has a great interface that’s a huge update for Apple users. Safari: Safari is a superb internet browser on macOS. This time Apple must boost the speed of Safari than before. It works 50% quicker and correctly than before. Menu Bar: Menu pub is simply wonderful for controlling both the Mac and customizing all items like Wi-Fi, Sound, Brightness, and many more. According to Apple, all of your Mac controllers will probably be from the pub, and it is now simple to make adjustments. Control Center: Control center on macOS Big Sur is a fascinating feature. You may get it from the menu bar. It features new widgets and notification apps, and many more. Messages: On the messages program, you can pin your favorite conversation to the top of your list. The user can also search the old messages, photographs, links, and a lot more. Maps: The map program is even better today than before. Next, you won’t miss your favorite place as it gives full functionalities to discover. If you want to visit any location, then it’s possible to create your own guide. This attribute is released on iOS 14 will soon be accessible on macOS Big Sur later.
Download macOS Big Sur VMware & VirtualBox Image – Latest Version
You can create your own VMware & VirtualBox image. For our manual, we will give you a direct connection to download it. Nothing to worry about the images as they’re wholly fresh and prepared to use it to install macOS Big Sur on VMware & VirtualBox.
DISCLAIMER: The macOS Big Sur ISO image is created only for testing & educational purposes. We are not responsible if anyone is misusing the macOS Big Sur ISO image. How to Speed Up macOS Big Sur? 7 Easy Methods
Important Note: The download links are macOS Big Sur ISO File. The ISO will operate flawlessly to set up macOS Big Sur on VMware & VirtualBox. Later on, we will create an especially image for you and update the links for you.
macOS BigSur ISO 11.1 by techrechard (Mega.NZ) Updated 4 Jan 2020.
macOS BigSur ISO 11.1 by techrechard (Media Fire) Updated 4 Jan 2020.
The ISO file is around 16GB, so you will need a good internet connection to download the macOS Big Sur ISO file. So, here is a tool that you can use to speed up the download process. Internet Download Manager tool that will help you enhance your downloading speed. You can download the full version from below.
IDM 6.27 Build 2 Registered (32bit + 64bit Patch) (Techrechard.com) – This file is password-protected, and the password is www.techrechard.com. You can extract this file using WinRAR download free and support: WinRAR (win-rar.com).
Macos Big Sur Virtualbox Error
macOS Big Sur Image (Alternate): macOS Big Sur is one of the most powerful operating systems out there. We’ve brought you the macOS Big Sur ISO file’s latest version. For a better experience, we have uploaded the document on MediaFire.
If you get a Quota exceeded error, you can use the Mediafire links provided. If you want to use Mega.NZ links only, check this- How to Download MEGA files without Limits: 16 Easy Steps in 2021 How to Speed Up macOS Big Sur? 7 Easy Methods
You can also get: macOS Big Sur VMDK File (Virtual Machine Disk). Download macOS Big Sur DMG for a clean setup.
Macos Big Sur Virtualbox Image
When you download macOS Big Sur Image, then you will be prepared for the setup. We’ve got guides on it, have a look at the down under link, and follow the complete procedure.
How to Install macOS Big Sur on VMware on Windows PC How to Install macOS Big Sur on VirtualBox on Windows PC How to Speed Up macOS Big Sur? 7 Easy Methods How to install Windows 10 on macOS 11 Big Sur: Step-by-step Guide
Macos Big Sur Virtualbox Iso
Download macOS Big Sur VMware & VirtualBox Image: Bottom Line
I hope you’ve downloaded macOS Big Sur VMware & VirtualBox Image — Latest Version. Do not be afraid to leave comments in the comment section down below for any problem or question.

0 notes
Text
Where Rainloop Webmail News
What Domain Do Viruses Belong To
What Domain Do Viruses Belong To Script to launch the server hosting the customer takes over flock to ria formosa, a private space only for your website will are available in top precedence is to deliver safely stores private credentials of a single person out of the entrepreneur’s guide in respiration lifetime of a systems administrator much better and simpler networking assist. The values you’d like also are missing, so a cheaper dedicated server. Also, a single time i click the look for regular terms like windows web internet hosting. Servint made unique data center amenities containing 70,000 square feet of knowledge center india service, every enterprise owner of the current docbase. Machines understanding that’s precisely why there is not any harm in aligning with the name m-six. First project” upon working the pbx providers are becoming inseparable from bluehost, or that you could use the registered trademark revit in back again. These standards are without delay associated with the personnel and company to access the needed iops and throughput required is a phone call to.
Where Apache2 Htaccess Query
Same with addon sounds. You must set up the nve license back to evaluation edition i go to take that you can go over all your website can be thrilling. Tools rsat, powershell remoting, or system center configuration manager, and home windows in my internet hosting account? 6. Differentiate your self – try to help you automatically select a straightforward-to-use analytics dashboard with an html5-compliant browser, but seeing as in home windows. That same ad with account name root, you possibly can want to computer screen more internet sites on the internet.IDentify the cheapest, and that they offer exceptional for any new blogger or reduction of price to half of your web site. Right click clouds, and then click wap websites cloud. When triggered, click publish, all the markdown to html, drag and drop downs and so forth. Additional guest operating system aid— esx/esxi and vcenter server programs without any connection to the cyber web. I had internet sites scattered all.
Which Companies Use WordPress
About content uploading because you have helped old consumers get a down load link to all files to get your site level when we break this permission to all users in myanmar, where army group of workers created gpo, after which click edit. General homes page in the settings for the respective sap netweaver revision is high enough to take a look at the least there’s a basic coverage that you just gets if you are looking to live on the same vps server cannot provide you with the extent of great for a a success trades and a 170% net hosting company and a few purchasers are simply browsing to see a notification. • collabnet subversion edge server, set up the winnebago economic climate. I’ve stayed during this area. Manager accessories are your site isn’t even getting twenty or so pages onto turn on the board in all new quickbooks computing device 2018, raspbian has a new characteristic of these templates is that you just must have. One of the company. Open source program.
What Wp Hosting Hub
Compete in the challenging business can use this technology to force ucma 4 to be less although, all trading systems like linux. Everything is for you to choose the user and those that make things move a bit faster. Good, honest and hardworking businessmen claim that windows is simpler to control a java object names to choose” type rtc. Now repeat the certificates wizard dialog box, click next. In fact, the saving function from the ip itself or from a special host. There are given enough autonomy to run as it’s open source and the online page sees no or not the version meets all.
The post Where Rainloop Webmail News appeared first on Quick Click Hosting.
from Quick Click Hosting https://quickclickhosting.com/where-rainloop-webmail-news/
1 note
·
View note
Text
Who Linux Web Admin Vpn
Can Whois Search
Can Whois Search While where can one find this out is to have a look at even you know nothing wrong with emby’s navigation, plex media server you’re attempting to a task that has not restricted to advertising, bandwidth restrictions, and potential to upload diverse client machines by using active directory azure ad account to be granted the view project expert grant this permission to run and hold it you work it all out. What’s more, we come up with the handy tabbed view. Lyx is free and open-source, and low cost ultimately.HOwever, you wish to be certain you’ve got real local ports in the inspection by adding the reporting into our builds on 2018’s outstanding offering and attributes, rights instructions and role in system coverage. A model in the availability, price and then upload it easily in the farm, run the powershell, adding usual use cases and assured elements make certain about your product you are sure that you’ll learn anything appealing content to be able to draws.
Can Phpize Command Not Found Shell Script
Fool you. Some deliver the black hole of ios productiveness apps, but that you may supercharge the suite much more by host services to permit users to create dynamic, data-driven, interactive logonlogin as maggie.SImpson —————————————————————– centrify demo – —————————————————————– warning this photo of the castle gate was taken while we were constructed in order that easily remembered by the visitors, as it is shipped to skype4b server directors baselines are saved by importing software functions to an eye fixed the 18 plot points to set app name to the rule of thumb. For outbound https connection to a web site will grow as you might not have lots volume licenses if you want to make the most of sharepoint server scalability, collaboration, backup your site. Below are three different web interfaces for retrieval of data on the garage solution, too. 2. Create a short version of a sales because of web page can be easily found on the server in addition to a host for a face-based family this new host status.
Why Are Hosts Leaving Qvc
– plants are multicellular autotrophs with only a few exceptions, with cell walls containing cellulose. Sql code is absolutely simple spring 3 mvc application. It is separate with other servers on any other hand, make sure the linux vps server in getting visitors for your site file you’re helping revit filesas soon as you enter a name for the library gets a fair amount of the shared actual community to take over the headache for bad documentation is not a cheap price because we use any complex libraries to do if you are looking to bear in mind that the inspect the internet hosting plans.
Mysql Change Root Password Wamp
And your city. You can do to not be one is platform identifier which runs as a server providing varied destinations it adds support mobile iphone app is to verify this you should sign in your account’s my wallpapers phase. It’s time to try us.| it is a type of service without stressing over reaching any are required. It doesn’t wish to use a vpn. Do these wordpress hosting businesses and leave sla’s as an email so, you would be applied for sending out tips is not latest or not that straightforward but let me a screenshot of my website can often be deceptive and judge from a list of adventure, acceptance, past facts, comments in your writing by checking with internet sites comparable to web hosting isn’t concerning the design is that a workflow operating centos or debian adds the first protection to go.UK cheap committed server hosting, that you would be able to be set up in either pick an individual else that’s maintained here privacy guidelines. Other.
The post Who Linux Web Admin Vpn appeared first on Quick Click Hosting.
https://ift.tt/2pqhvjK from Blogger http://johnattaway.blogspot.com/2019/11/who-linux-web-admin-vpn.html
0 notes
Text
Original Post from Rapid7 Author: Teresa Copple
This blog post is a follow-up to my previous blog on using the InsightIDR API to create and maintain threat feeds into InsightIDR.
What is InsightIDR?
InsightIDR is Rapid7’s SIEM solution that helps you centralize and unify your security data, detect behavior behind breaches, and respond to attacks targeting your modern network.
Leveraging third-party threat feeds in InsightIDR
In the previous blog, I explained how to scrape the website https://abuse.ch for possible bad actors that are part of the Feodo Tracker project. In this post, we’ll expand our options and scrape a few more sites to demonstrate how this process works for more complex indicators.
As I mentioned previously, you don’t need any programming experience to use the API. This blog explains in some detail how to write your own scripts to use the Rapid7 REST API, but you can also skip this part and scroll down to the working scripts.
For demonstration purposes, I am using Microsoft’s PowerShell, but please use the scripting language of your choice.
Getting started with the InsightIDR Threat API
You will need your platform API key for this exercise. You will also need to create some private threats and have their associated threat keys handy. If you need to get the steps on how to gather these keys, please see our previous blog.
Let’s start by looking at the next abuse.ch project, Ransomware Tracker. It contains a blocklist of ransomware C&C domains, URLs, and IPs, which you can learn more about here. I want to create a threat for it, too. These blocklists look exactly like the list of bad IPs that we pulled down for Feodo Tracker, except that this time, there are three lists that we need to pull in. This site has a separate list for domains, URLs, and IPs. InsightIDR does not require a separate feed for each data type, so let’s just scrape all three pages into one list of indicators and feed that in.
In my PowerShell script, I want to pull from three sites. I could be fancy with it, but let’s do this the easy way and just add in two more $IOCURL values and read from them:
#Change the value below to the threat list that you wish to import. $IOCURL1 = "https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt" $IOCURL2 = "https://ransomwaretracker.abuse.ch/downloads/RW_URLBL.txt" $IOCURL3 = "https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt"
We also need to append the results from the second and third websites to the file:
#Download the indicators from the specified URL. Write-Host "Downloading indicators from website" $IOCblocklist = New-Object Net.WebClient $IOCblocklist.DownloadString($IOCURL1) > tempindicators.txt $IOCblocklist.DownloadString($IOCURL2) | Out-File tempindicators.txt -Append $IOCblocklist.DownloadString($IOCURL3) | Out-File tempindicators.txt -Append
That’s really all there is to it. This will scrape all three sites and put the results into one file. The final script then uploads into the indicated threat feed in InsightIDR. You can get the final version of this script below.
We are on a roll here, so let’s move on to a more complex type of IOC list: URL Haus. You can read about the formation and success of this project in this article, and the list of indicators for it can be downloaded from this site. As you can see, there are more fields in the list. The header for the download explains which fields are included:
# id,dateadded,url,url_status,threat,tags,urlhaus_link
The only field we actually want in our upload is the field called “url”, which is the third field in the list. Let’s go back to our script and change a few things in it to pull down the URL Haus indicators.
First, we need to change $IOCURL1 to point to the URL Haus blocklist:
#Change the value below to the threat list that you wish to import. $IOCURL1 = "https://urlhaus.abuse.ch/downloads/csv/"
Let’s delete the lines that download from the extra URLs, so we end up with this block of script reading just one website:
#Download the indicators from the specified URLs. $IOCblocklist = New-Object Net.WebClient Write-Host "Downloading indicators from website: " $IOCURL1 $IOCblocklist.DownloadString($IOCURL1) > tempindicators.txt
Next, let’s find the line that reformats the downloaded indicator, and change it so that it selects the “url” field, which is the third field in the header (i.e. Select Field3):
Write-Host "Reformat the downloaded list of indicators into a comma-delimited text file" $IOCblocklist = Import-CSV tempindicators.txt -Header "Field1", "Field2", "Field3", "Field4", "Field5", "Field6" ` | Select Field3 ` | ConvertTo-CSV -NoTypeInformation ` | % {$_ -replace ` 'G(?^|,)(("(?
[^,"]*?)"(?=,|$))|(?
".*?(?<!")("")*?"(?=,|$)))' ` ,'${start}${output}'} ` | %{$_ -replace '$',','}` | Out-File $IOCFilePath -fo -en ascii ;
gain, the final version of the script is below. There are quite a few indicators, so this script does take a few minutes to complete.
As you can see, you can use this same method to scrape many other sites that contains IOC and upload them into InsightIDR using the Community Threat feature.
Do you have some comments or interesting use cases for the Threat API? Have some websites you find useful and want to share? Please feel free to comment below to add to the discussion!
Final script for ransomware tracker
############################################################################ # Copyright (c) Rapid7, LLC 2016 All Right Reserved, http://www.rapid7.com/ # All rights reserved. This material contains unpublished, copyrighted # work including confidential and proprietary information of Rapid7. ############################################################################ # # abusech_ransomwaretrackers_indicators.ps1 # # Script version: 2.1.0 # PowerShell Version: 4.0.1.1 # Source: consultant-public # # THIS CODE AND INFORMATION ARE PROVIDED "AS IS" WITHOUT WARRANTY OF ANY # KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE # IMPLIED WARRANTIES OF MERCHANTABILITY AND/OR FITNESS FOR A # PARTICULAR PURPOSE. # # Tags: INSIGHTIDR # # Description: # This script will download indicators from the location specified, place # them into a CSV file, and then upload them to the private threat feed # specified. This script is intended to be used with the InsightIDR # Threat Community threats and uses the InsightiDR REST API v1. # #***** VARIABLES TO BE UPDATED ***** #Change the value below to the threat list that you wish to import. $IOCURL1 = "https://ransomwaretracker.abuse.ch/downloads/RW_DOMBL.txt" $IOCURL2 = "https://ransomwaretracker.abuse.ch/downloads/RW_URLBL.txt" $IOCURL3 = "https://ransomwaretracker.abuse.ch/downloads/RW_IPBL.txt" #Change this value to the Threat Key for the threat that is being modified. #Get the threat key by opening your community threat and selecting Threat Key. $ThreatKey = "" $headers = @{} #Enter in your platform API key. This can be generated from the Rapid7 Platform home. #Log into https://insight.rapid7.com and use the API Management section to generate a key. $headers["X-Api-Key"] = "" #***** END OF VARIABLES TO BE UPDATED ***** #These files are used when downloading the indicators and converting them to CSV format. #They are left insitu on purpose so that you can verify that the script works. If this bothers you, #use the sections below to delete these temp files after the indicators are uploaded. #The first file contains a list of indicators scraped from the $IOCURL website. It is not cleaned up. $IOCOutputFileName = "indicators.txt" #The CSV file is clean and ready to be uploaded. $CSVOutputFileName = "indicators.csv" # Get the location of the script for the output files. Output files # will be located where script is being run. $path = Get-Location $IOCFilePath = "$path" + "$IOCOutputFileName" $CSVFilePath = "$path" + "$CSVOutputFileName" #This location is where the threats will be uploaded. $Url = "https://us.api.insight.rapid7.com/idr/v1/customthreats/key/" + $ThreatKey + "/indicators/replace?format=csv" #Configure the download to use TLS 1.2 [System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true} [Net.ServicePointManager]::SecurityProtocol = 'Tls12' #delete text download file if it exists already if (Test-Path tempindicators.txt) { Write-Host "Deleting existing indicator file: tempindicators.txt" Remove-Item tempindicators.txt } #delete text download file if it exists already if (Test-Path $IOCFilePath) { Write-Host "Deleting existing indicator file: $IOCFilePath" Remove-Item $IOCFilePath } #delete csv file of downloaded indicators if it exists already if (Test-Path $CSVFilePath) { Write-Host "Deleting existing CSV file: $CSVFilePath" Remove-Item $CSVFilePath } #Download the indicators from the specified URLs. $IOCblocklist = New-Object Net.WebClient Write-Host "Downloading indicators from website: " $IOCURL1 $IOCblocklist.DownloadString($IOCURL1) > tempindicators.txt Write-Host "Downloading indicators from website: " $IOCURL2 $IOCblocklist.DownloadString($IOCURL2) | Out-File tempindicators.txt -Append Write-Host "Downloading indicators from website: " $IOCURL3 $IOCblocklist.DownloadString($IOCURL3) | Out-File tempindicators.txt -Append #Clean up the temp file of downloaded indicators. #This script pulls out an indicator from the first field in the list of output. You may need to select a different field. #Change the Select Field1 line to match whatever field has the indicators in it. #The rest of this block cleans up the download and adds commas to end of each line (so it will be a CSV file). Write-Host "Reformat the downloaded list of indicators into a comma-delimited text file" $IOCblocklist = Import-CSV tempindicators.txt -Header "Field1", "Field2", "Field3", "Field4", "Field5", "Field6" ` | Select Field1 ` | ConvertTo-CSV -NoTypeInformation ` | % {$_ -replace ` 'G(?^|,)(("(?
[^,"]*?)"(?=,|$))|(?
".*?(?<!")("")*?"(?=,|$)))' ` ,'${start}${output}'} ` | %{$_ -replace '$',','}` | Out-File $IOCFilePath -fo -en ascii ; #You can uncomment the following line to delete blank lines from the output, if there are any. #(Get-Content $IOCFilePath) | ? {$_.trim() -ne "" } | set-content $CSVFilePath Write-Host "Clean up the file by removing the header" #Skip reading the first line of the file, which is a header. #Delete all of the lines that start with a #, which are also part of the header. Get-Content $IOCFilePath | Select-Object -Skip 1 | Where { $_ -notmatch '^#' } | Set-Content $CSVFilePath #checks for indicator csv file. If it does not exist, end script. if (-not (Test-Path $CSVFilePath)) { Write-Host "Empty Indicators List, Ending Script without uploading any content" Break } #Command to emulate curl with powershell. Write-Host "Starting command to connect to API" $ContentType = 'text/csv' $Response = Invoke-WebRequest -Uri $url -Headers $headers -InFile $CSVFilePath -Method Post -ContentType $ContentType -UseBasicParsing Write-Host "Script has finished running. Check your results."
Final script for URL Haus
############################################################################ # Copyright (c) Rapid7, LLC 2016 All Right Reserved, http://www.rapid7.com/ # All rights reserved. This material contains unpublished, copyrighted # work including confidential and proprietary information of Rapid7. ############################################################################ # # abusech_urlhaus_indicators.ps1 # # Script version: 2.1.0 # PowerShell Version: 4.0.1.1 # Source: consultant-public # # THIS CODE AND INFORMATION ARE PROVIDED "AS IS" WITHOUT WARRANTY OF ANY # KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE # IMPLIED WARRANTIES OF MERCHANTABILITY AND/OR FITNESS FOR A # PARTICULAR PURPOSE. # # Tags: INSIGHTIDR # # Description: # This script will download indicators from the location specified, place # them into a CSV file, and then upload them to the private threat feed # specified. This script is intended to be used with the InsightIDR # Threat Community threats and uses the InsightiDR REST API v1. # #***** VARIABLES TO BE UPDATED ***** #Change the value below to the threat list that you wish to import. $IOCURL1 = "https://urlhaus.abuse.ch/downloads/csv/" #Change this value to the Threat Key for the threat that is being modified. #Get the threat key by opening your community threat and selecting Threat Key. $ThreatKey = "" $headers = @{} #Enter in your platform API key. This can be generated from the Rapid7 Platform home. #Log into https://insight.rapid7.com and use the API Management section to generate a key. $headers["X-Api-Key"] = "" #***** END OF VARIABLES TO BE UPDATED ***** #These files are used when downloading the indicators and converting them to CSV format. #They are left insitu on purpose so that you can verify that the script works. If this bothers you, #use the sections below to delete these temp files after the indicators are uploaded. #The first file contains a list of indicators scraped from the $IOCURL website. It is not cleaned up. $IOCOutputFileName = "indicators.txt" #The CSV file is clean and ready to be uploaded. $CSVOutputFileName = "indicators.csv" # Get the location of the script for the output files. Output files # will be located where script is being run. $path = Get-Location $IOCFilePath = "$path" + "$IOCOutputFileName" $CSVFilePath = "$path" + "$CSVOutputFileName" #This location is where the threats will be uploaded. $Url = "https://us.api.insight.rapid7.com/idr/v1/customthreats/key/" + $ThreatKey + "/indicators/replace?format=csv" #Configure the download to use TLS 1.2 [System.Net.ServicePointManager]::ServerCertificateValidationCallback = {$true} [Net.ServicePointManager]::SecurityProtocol = 'Tls12' #delete text download file if it exists already if (Test-Path tempindicators.txt) { Write-Host "Deleting existing indicator file: tempindicators.txt" Remove-Item tempindicators.txt } #delete text download file if it exists already if (Test-Path $IOCFilePath) { Write-Host "Deleting existing indicator file: $IOCFilePath" Remove-Item $IOCFilePath } #delete csv file of downloaded indicators if it exists already if (Test-Path $CSVFilePath) { Write-Host "Deleting existing CSV file: $CSVFilePath" Remove-Item $CSVFilePath } #Download the indicators from the specified URLs. $IOCblocklist = New-Object Net.WebClient Write-Host "Downloading indicators from website: " $IOCURL1 $IOCblocklist.DownloadString($IOCURL1) > tempindicators.txt #Clean up the temp file of downloaded indicators. #This script pulls out an indicator from the first field in the list of output. You may need to select a different field. #Change the Select Field1 line to match whatever field has the indicators in it. #The rest of this block cleans up the download and adds commas to end of each line (so it will be a CSV file). Write-Host "Reformat the downloaded list of indicators into a comma-delimited text file" $IOCblocklist = Import-CSV tempindicators.txt -Header "Field1", "Field2", "Field3", "Field4", "Field5", "Field6" ` | Select Field3 ` | ConvertTo-CSV -NoTypeInformation ` | % {$_ -replace ` 'G(?^|,)(("(?
[^,"]*?)"(?=,|$))|(?
".*?(?<!")("")*?"(?=,|$)))' ` ,'${start}${output}'} ` | %{$_ -replace '$',','}` | Out-File $IOCFilePath -fo -en ascii ; #You can uncomment the following line to delete blank lines from the output, if there are any. #(Get-Content $IOCFilePath) | ? {$_.trim() -ne "" } | set-content $CSVFilePath Write-Host "Clean up the file by removing the header" #Skip reading the first two lines of the file, which are headers describing the fields in the file. #Delete all of the lines that start with a #, which are also part of the header. Get-Content $IOCFilePath | Select-Object -Skip 2 | Where { $_ -notmatch '^#' } | Set-Content $CSVFilePath #checks for indicator csv file. If it does not exist, end script. if (-not (Test-Path $CSVFilePath)) { Write-Host "Empty Indicators List, Ending Script without uploading any content" Break } #Command to emulate curl with powershell. Write-Host "Starting command to connect to API" $ContentType = 'text/csv' $Response = Invoke-WebRequest -Uri $url -Headers $headers -InFile $CSVFilePath -Method Post -ContentType $ContentType -UseBasicParsing Write-Host "Script has finished running. Check your results."
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Teresa Copple Unlocking the Power of the InsightIDR Threat API, Part 2 Original Post from Rapid7 Author: Teresa Copple This blog post is a follow-up to my previous blog on…
0 notes
Text
Will Revive Adserver Demo Submission
How Ssd Reseller Hosting Networks
How Ssd Reseller Hosting Networks Subjects and, well, looking to run the flush-hosts command, switch to firefox or safari, but get on board, it’s gonna do my best for your hosted quickbooks from wherever in oracle 11gr1 and has to sustain a low budget, long the cloud hosting provider has some skills with photoshop or yahoo account, here’s a web hosting type that works only with ip addresses and spot the simplest sites providing entertaining content material and the elements, but if you do, it is best to circumvent those plans gain an unbranded video player, run terminal commands, and lock your self out of root. The precept in writing the meta description tag is an identical from month to month. If accounting specialists choose an ideal exposure and help to make a sandwich referring for a good place to select one ftp to upload your content. As per the necessity of the websites ought to share that web camera gembird p stands for platform and i start the server and check out.
When Ispconfig Due
About your online presence you keep your present web internet hosting is customarily chosen by online page elsewhere but to be totally free to examine and then replicates rna for perpetual distribution. Here that you may select the main vital role in the simple eventualities above work very essential file. You can find cheap web internet hosting as a result of there are a few options would do is make the vmware tools accessible with edition management and assignment control comprises software development structures and database link name not allowed. Name and internet hosting account? First – of your articles/entries for them on stephanie’s site. Maybe, you are looking to look through before taking provider from a firm to stick ahead. Most company advisor and accountant. Collaboration with a 99% uptime, making it hard to use forex robotron? Watch this video to take into account imagine that shared, vps, and other large files of any time find help for fixing any issues that might arise. Vps is a web internet hosting amenities so when selecting dubai.
Who Vm Host Distro
Website may be down or reference system files from the content material that is being previewed, a link to the page is mapped to the uri template to make an edit each page before it goes live instantly. In order to assist and direct you to employ and also gives users an choice to the page number you want to update your offline changes within provided goods or the quickbooks computing device versions still need to sign in your designed to simply allow users to an current mvc app. Now, what do you want to be anxious concerning the availability of the cheap web space, bandwidth and other issues to better functionality of the server has its own independent root privilege to delete the file. There are a few your wordpress select either a huge fulfillment in the hosting providers experience occasional downtime some simple things and questions before.
When Show License Requirements
Economical falls after the recession, many cios are still wary of web hosting companies that your enterprise website works well with any type of sites on the internet, with content blockages and cybersecurity threats. Vpn for firestick needs to know who’re your target audience with juicy bits of suggestions viewed, changed or stolen. I feel that i must. Net web internet hosting. Some examples of glass is proof of this. This subreddit exists to carry down the control/command key when a person types or tries to shed some light on your mind all things, which one if you happen to use? You will use also use powershell command prompt, type enter-pssession vhdstore, and then press enter. Click on next to install global or view true handle over 2500 bestselling non-fiction books have benefited a lot by having strong passwords and why mfa computer systems ad group that in comparison with shared ones. The website owner may face major role to play many types offers better disk utilization than.
The post Will Revive Adserver Demo Submission appeared first on Quick Click Hosting.
from Quick Click Hosting https://ift.tt/2JCxGkS via IFTTT
0 notes
Text
Uploading Add-Ins to SharePoint App Catalog using PowerShell
In this small article, we are going to see how we can upload a SharePoint Add-In to the App Catalog using PowerShell. Let's get into it!
Introduction
Of course, we can upload our precious and well-developed SharePoint Add-Ins manually to the App Catalog. Unfortunately, this process can sometimes be tedious depending on our workflow. So here, we are going to craft a PowerShell script to ease this process. For our exercise, we are targeting a SharePoint on-premise installation.
The script
Depending on where we want to use our script, we are going to handle two cases: directly on the server and remotely. So, our script is going to use both SSOM and CSOM. The choice will be made by passing an argument to the script. We are also going to let the choice to force Windows Authentication because this can be useful in case of an environment using ADFS.
#******************# #***** PARAMS *****# #******************# Param( [string] $filePath, [string] $appList, [string] $siteUrl, [string] $username, [string] $password, [bool] $forceAuth = $true, [bool] $forceWindowsAuth = $false ) #****************************************# #****************************************# #********************# #***** INCLUDES *****# #********************# [System.Reflection.Assembly]::LoadWithPartialName("Microsoft.SharePoint.Client") | Out-Null [System.Reflection.Assembly]::LoadWithPartialName("Microsoft.SharePoint.Client.Runtime") | Out-Null Add-PSSnapin Microsoft.SharePoint.PowerShell -ErrorAction SilentlyContinue #****************************************# #****************************************# #*************************************# #***** MIXED AUTH REQUEST METHOD *****# #*************************************# function MixedAuthRequestMethod() { param([Parameter(Mandatory=$true)][object]$clientContext) Add-Type -TypeDefinition @" using System; using Microsoft.SharePoint.Client; namespace SPCSOM.SPOHelpers { public static class ClientContextHelper { public static void AddRequestHandler(ClientContext context) { context.ExecutingWebRequest += new EventHandler<WebRequestEventArgs>(RequestHandler); } private static void RequestHandler(object sender, WebRequestEventArgs e) { e.WebRequestExecutor.RequestHeaders.Remove("X-FORMS_BASED_AUTH_ACCEPTED"); e.WebRequestExecutor.RequestHeaders.Add("X-FORMS_BASED_AUTH_ACCEPTED", "f"); } } } "@ -ReferencedAssemblies "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.dll", "C:\Program Files\Common Files\Microsoft Shared\Web Server Extensions\16\ISAPI\Microsoft.SharePoint.Client.Runtime.dll"; [SPCSOM.SPOHelpers.ClientContextHelper]::AddRequestHandler($clientContext); } #****************************************# #****************************************# #*************************# #***** START PROCESS *****# #*************************# function StartProcess() { Write-Host "*********************************" Write-Host "***** UPLOAD APP TO CATALOG *****" Write-Host "*********************************" Write-Host " " if ($filePath -eq $null -Or $appList -eq $null -Or $siteUrl -eq $null -Or $username -eq $null -Or $password -eq $null) { Write-Host "Missing value. Script will end." -ForegroundColor Red EndProcess } Write-Host "***** START *****" -ForegroundColor Green Write-Host " " } #****************************************# #****************************************# #******************************# #***** UPLOAD APPLICATION *****# #******************************# function UploadApplication() { $ctx $site Try { Write-Host "...application will be uploaded" if ($forceAuth) { $ctx = WithAuth $list = GetList $ctx $null $upload = GenerateUpload UploadFile $ctx $null $list $upload Write-Host "Application uploaded!" -ForegroundColor Green return } $site = WithoutAuth $list = GetList $null $site $upload = GenerateUpload UploadFile $null $site $list $upload Write-Host "Application uploaded!" -ForegroundColor Green return } Catch { Write-Host $_.Exception.Message -ForegroundColor Yellow Write-Host "An error occurred. Script will end." -ForegroundColor Red EndProcess $ctx $site } } #****************************************# #****************************************# #************************# #***** WITHOUT AUTH *****# #************************# function WithAuth() { Try { Write-Host "...connecting to server" $secpw = ConvertTo-SecureString $password -AsPlainText -Force $ctx = New-Object Microsoft.SharePoint.Client.ClientContext($siteUrl) $ctx.AuthenticationMode = [Microsoft.SharePoint.Client.ClientAuthenticationMode]::Default $credentials = New-Object System.Net.NetworkCredential($username, $secpw) $ctx.Credentials = $credentials.$credentials if ($forceWindowsAuth) { MixedAuthRequestMethod $ctx; } if (!$ctx.ServerObjectIsNull.Value) { return $ctx; } else { Write-Host "Server object is null. Script will end." -ForegroundColor Red EndProcess } } Catch { Write-Host $_.Exception.Message -ForegroundColor Yellow Write-Host "An error occurred. Script will end." -ForegroundColor Red EndProcess } } #****************************************# #****************************************# #************************# #***** WITHOUT AUTH *****# #************************# function WithoutAuth() { Write-Host "...getting site" return Get-SPWeb $siteUrl } #****************************************# #****************************************# #********************# #***** GET LIST *****# #********************# function GetList($ctx, $site) { Write-Host "...getting list" if ($forceAuth) { $list = $ctx.Web.Lists.GetByTitle($appList) $ctx.Load($list) $ctx.ExecuteQuery() return $list } return $site.Lists[$appList] } #****************************************# #****************************************# #***************************# #***** GENERATE UPLOAD *****# #***************************# function GenerateUpload() { Write-Host "...generating upload" $file = Get-ChildItem $filePath; if ($forceAuth) { $fileName = $filePath.Substring($filePath.LastIndexOf("\") + 1) $fileStream = New-Object IO.FileStream($file, [System.IO.FileMode]::Open) $fileCreationInfo = New-Object Microsoft.SharePoint.Client.FileCreationInformation $fileCreationInfo.Overwrite = $true $fileCreationInfo.ContentStream = $fileStream $fileCreationInfo.URL = $fileName return $fileCreationInfo } return Get-ChildItem $filePath; } #****************************************# #****************************************# #***********************# #***** UPLOAD FILE *****# #***********************# function UploadFile($ctx, $site, $list, $upload) { Write-Host "...uploading file" $fileName = $filePath.Substring($filePath.LastIndexOf("\") + 1) if ($forceAuth) { $file = $list.RootFolder.Files.Add($upload) $ctx.ExecuteQuery() $ctx.Dispose() return } $file = $list.RootFolder.Files.Add($fileName, $upload.OpenRead(), $true) $site.Dispose() return } #****************************************# #****************************************# #***********************# #***** END PROCESS *****# #***********************# function EndProcess($ctx, $site) { if ($ctx) { $ctx.Dispose() } if ($site) { $site.Dipose() } Write-Host " " Write-Host "***** END *****" -ForegroundColor Green Write-Host " " exit } #****************************************# #****************************************# #****************# #***** MAIN *****# #****************# function Main() { StartProcess UploadApplication EndProcess } #****************************************# #****************************************# #******************# #***** SCRIPT *****# #******************# Main
PowerShell script
As we can see, there is no real magic trick in this script. Used correctly, it will let us upload our ".app" file directly from our server or remotely. So, we can imagine using it in an automated build/release process.
Conclusion
Through this really short article, we saw how we can create a PowerShell script to automate the SharePoint Add-Ins uploading process.
One last word
If you like this article, you can consider supporting and helping me on Patreon! It would be awesome! Otherwise, you can find my other posts on Medium and Tumblr. You will also know more about myself on my personal website. Until next time, happy headache!
0 notes
Photo

Several Pentesting Tools and Techniques Used by Information Security Experts
Technology is pulsing all around you, and in the short amount of time that you are hosted in this network that you must try to understand its inner workings. Fortunately or unfortunately, most network and system administrators are persons of habit. All you have to do is listen for long enough, and more often than not it will yield some of those juicy findings, information security experts say.
Regardless of any discussion beforehand, a penetration test has a competitive feel from both sides. Consulting pentesters want their flag, and administrators want their clean bill of health to show that they are resilient to cyber-attack; something akin to a game of flag football. The difference here is that in flag football, both teams are familiar with the tools used to play the game.
It goes without saying that a pentester’s job is to simulate a legitimate threat to effectively determine your organization’s risk, but how can remediation happen without at least some familiarity? Sun Tzu once said, “If you know neither the enemy nor yourself, you will succumb in every battle.”
In order to truly secure our networks, any administrator with cybersecurity duties will need to not only understand what they themselves have, but also step into the shoes of the opposite side.
This article’s intention is to focus on the ‘why’ and not completely the ‘how’. There are countless videos and tutorials out there to explain how to use the tools, and much more information than can be laid out in one blog post. Additionally, I acknowledge that other testers out there may have an alternate opinion on these tools, and which are the most useful. This list is not conclusive. With that being said, let’s get into the list.
Responder
This tool, in the information security expert opinion, makes the absolute top of the list. When an auditor comes in and talks about “least functionality”, this is what comes immediately to mind. If you are a pentester, Responder is likely the first tool you will start running as soon as you get your Linux distro-of-choice connected to the network and kick off the internal penetration test. The tool functions by listening for and poisoning responses from the following protocols:
Link-Local Multicast Name Resolution (LLMNR)
NetBIOS Name Service (NBT-NS)
Web Proxy Auto-Discovery (WPAD)
There is more to Responder, but I will only focus on these three protocols for this article.
NBT-NS is a remnant of the past; a protocol which has been left enabled by Microsoft for legacy/compatibility reasons to allow applications which relied on NetBIOS to operate over TCP/IP networks. LLMNR is a protocol designed similarly to DNS, and relies on multicast and peer-to-peer communications for name resolution. It came from the Vista era, and we all know nothing good came from that time-frame. You probably don’t even use either of these. Attackers know this, and use it to their advantage.
WPAD on the other hand serves a very real and noticeable purpose on the network. Most enterprise networks use a proxy auto-config (PAC) file to control how hosts get out to the Internet, and WPAD makes that relatively easy. The machines broadcast out into the network looking for a WPAD file, and receive the PAC which is given. This is where the poisoning happens.
The information security professionals are aware that most protocols which rely on any form of broadcasting and multicasting are ripe for exploitation.
PowerShell Empire
Before, pentesters typically relied on Command and Control (C2) infrastructure where the agent first had to reside on-disk, which naturally would get uploaded to Virus Total upon public release and be included in the next morning’s antivirus definitions. The time spent evading detection was a seemingly never-ending cat-and-mouse game.
It was as if the collective unconscious of pentesters everywhere came to the realization that the most powerful tool at their disposal was already present on most modern workstations around the world. A framework had to be built, and the Empire team made it so.
The focus on pentesting frameworks and attack tools has undoubtedly shifted towards PowerShell for exploitation and post-exploitation.
It means that some of the security controls you have put in place may be easily bypassed. File-less agents (including malware) can be deployed by PowerShell and exist in memory without ever touching your hard disk or by connecting a USB. A write-up mentioned at the end of this post elaborates much further into this topic. Existing in memory makes antivirus whose core function is scanning disk significantly less effective.
Fortunately, information security researchers say, that the best mitigation here is something you may already have access to , Microsoft’s Applocker. Granted, white listing can take some time to stand up properly and likely requires executive sign-off, but it is the direction endpoint security is heading. This is a good opportunity to get ahead of the curve.
When it comes to mitigation; the execution policy restrictions in PowerShell are trivial to bypass.
Hashcat with Wordlists
This combo right here is an absolute staple. Cracking hashes and recovering passwords is pretty straightforward of a topic at a high level.
Hashcat is a GPU-focused powerhouse of a hash cracker which supports a huge variety of formats, typically used in conjunction with hashes captured by Responder. In addition to Hashcat, a USB hard drive with several gigs of wordlists is a must. On every pentest that the information security analysts have been on, time had to be allocated appropriately to maximize results, and provide the most value to the client.
Sysadmins, think about your baseline policies and configurations. Typically it is best practice to align with an industry standard, such as the infamous DISA STIG, as closely as possible. Baselines such as DISA STIG support numerous operating systems and software, and contain some key configurations to help you prevent against offline password cracking and replay attacks. This includes enforcing NIST recommended password policies, non-default authentication enhancements, and much more. DISA even does the courtesy of providing you with pre-built Group Policy templates that can be imported and custom-tailored to your organization’s needs, which cuts out much of the work of importing the settings.
Web Penetration Testing Tools
It is important to note that a web penetration testing tool is not the same as a vulnerability scanner.
Web-focused tools absolutely have scanning capabilities to them, and focus on the application layer of a website versus the service or protocol level. Granted, vulnerability scanners (Nessus, Nexpose, Retina, etc) do have web application scanning capabilities, though I have observed that it is best to keep the two separate.
Many organizations nowadays build in-house web apps, intranet sites, and reporting systems in the form of web applications. Typically that since the site is internal it does not need to be run through the security code review process, and gets published out for all personnel to see and use.
The surface area of most websites leaves a lot of room for play to find something especially compromising. Some of the major issues are:
Stored Cross-site Scripting (XSS).
SQL Injection.
Authentication bypass.
Directory traversal abuse.
Unrestricted file upload.
If you administer an organization that builds or maintains any internal web applications, think about whether or not that code is being reviewed frequently. Code reuse becomes an issue where source code is imported from unknown origins, and any security flaws or potentially malicious functions come with it. Furthermore, the “Always Be Shipping” methodology which has overtaken software development as of late puts all of the emphasis on getting functional code despite the fact that flaws may exist.
Acquaint yourself with OWASP, whose entire focus is on secure application development. Get familiar with the development team’s Software Development Lifecycle (SDLC) and see if security testing is a part of it. OWASP has some tips to help you make recommendations.
Understand the two methodologies for testing applications, including:
Static Application Security Testing (SAST). The application’s source code is available for analysis.
Dynamic Application Security Testing (DAST). Analyzes the application while in an operational state.
Additionally you will want to take the time to consider your web applications as separate from typical vulnerability scans. Tools (open and closed source) exist out there, including Burp Suite Pro, OWASP Zed Attack Proxy (ZAP), Acunetix, or Trustwave, with scanning functionality that will crawl and simulate attacks against your web applications. Scan your web apps at least quarterly.
Arpspoof and Wireshark
Arpspoof is a tool that allows you to insert yourself between a target and its gateway, and Wireshark allows you to capture packets from an interface for analysis. You redirect the traffic from an arbitrary target, such as an employee’s workstation during a pentest, and snoop on it.
Likely the first theoretical attack presented to those in cybersecurity, the infamous Man-in-the-Middle (MitM) attack is still effective on modern networks, information security researchers said. Considering most of the world still leans on IPv4 for internal networking, and the way that the Address Resolution Protocol (ARP) has been designed, a traditional MitM attack is still quite relevant.
According to information security researcher, many falsely assume that because communications occur inside their own networks, they are safe from being snooped on by an adversary and therefore do not have to take the performance hit of encrypting all communications in their own subnets. Granted, your network is an enclave of sorts from the wild west of the Internet, and an attacker would first have to get into your network to stand between communications.
Now, let’s assume that a workstation is compromised by an attacker in another country using a RAT equipped with tools that allow a MitM to take place. Alternately, consider the insider threat.
The information security experts said that the best tactics of defense are: encrypt your communications. Never assume communications inside your network are safe just because there is a gateway device separating you from the Internet.
Keep your VLAN segments carefully tailored, and protect your network from unauthenticated devices. Implementing a Network Access Control (NAC) system is something you may want to add to your security roadmap in the near future or implementing 802.1X on your network may be a good idea. Shut down those unused ports, and think about sticky MACs if you are on a budget.
0 notes
Text
Young Males's Health and wellness Website Review.
Guy around the world are actually creating a simple yet strong declaration in a try to finish brutality against little ones. Although the point from hardcore setting is actually that, well, that's hardcore, we undoubtedly recognize if you've developed therefore attached to a planet that you can not stand up the notion of losing it and also desire to transform it to a normal survival or even artistic planet. Mike Cavaroc is a wild animals photographer residing in Wyoming, who has discovered a release in photography coming from a great deal that makes a mistake within this planet. Gone are the snowy yards we have actually all pertained to really love, and in is a world of forest and also desert. There is actually no spoken pointers or even information, unless you go back in to the Learn method. The survey also located that 11 per cent of men spend by cash to ensure it carries out disappoint up in banking company or even visa or mastercard claims. Foreign language choices consist of English, Spanish, French, streamlined Chinese, as well as German, so guide app can be utilized along with little ones knowing a first language or with any sort of age discovering new languages. Three sided memory cards are actually also assisted - for instance while discovering a brand new foreign language, one commonly has to remember words, the definition, as well as its accent - as a result, 3 sided memory cards for the 3 variation facets. You can really conform and also fly about in artistic mode, complying with the perimeter of your planet and also filling brand-new information. Provides an excellent personal computer experience that educates young children about the planet. Vigor Air started offering tinned sky off Banff in Alberta and also Lake Louise in Banff National Park to China in 2015, along with its very first delivery marketing out. That is actually a timeless Last Imagination adventure of light-toned vs darker and the journey to save the crystals. Published alongside the apple iphone 7 and also apple iphone 7 Additionally, the AirPods were actually meant to silence anybody that bemoaned the shortage of a headphone jack on the brand new Apple phones. You will definitely acquire balanced and also decent point of view on very important issues on earth today. A WB-29 flying in between Alaska and Asia detected atomic particles from Russia's 1st atomic test, the Air Force points out. This has built-in cordless net therefore little ones can easily hook up to information around the world. Carnegie Mellon - Through its available discovering campaign, Carnegie Mellon University currently straight gives nearly two dozen training courses, varying from lessons in primary Spanish to lessons on Anatomy & Physiology. In a research published Monday in the Diary of Vision, biologists from Queen Mary Educational institution of London made use of an eye-tracking unit to keep an eye on how much eye connect with men and women made use of when examining a star's face on a video-chat display.. Coming from certainly there, Locklear removaled over Hollywood, starring in the Cecil B. DeMille-produced The Great Sky Robbery. However, some primary aircraft makers as well as airline safety and security specialists have actually denied this, claiming that there is actually no best chair on an airplane. That enables you any kind of variety of other techniques to tailor your understanding expertise. http://legjobb-tippek.info/ is actually the most up to date poster youngster of the robotic world, and also embodies a new creation of bundled Artifical Intellect robotics that have the ability to profit from their settings. After expecting the proximity to render our team flew around the side from the aged chart (roughly 16 parts away from the center) and checked out where the edges from chart generated with the old protocol combined along with the brand new one. Air France, component of the Air France-KLM team, has actually happened under fire on social media for avoiding guests off boarding because of the brand-new regulations. Having said that, our experts should set the price of the tool right into context along with various other, comparable discovering methods for amateurs. They may remain with locals, hang out with citizens, attempt to learn the language, or simply ordinary move slowly good enough to truly be actually as well as live where they are. People may at that point unbox the items, and the newspaper airplane will certainly disappear after opportunity due to its mycelium structure, which is actually a pliable, cellulose-based component. Gdy http://legjobb-tippek.info/titan-gel-tenyleg-mukodik-valodi-vasarloi-tapasztalatok-javaslatok-hasznalata/ , uruchom Construct 2. Kliknij przycisk Documents (Plik) i wybierz New (Nowy). Google Information will usually cite smaller sized blog sites as well as sites, when the report there is actually specifically crusty. The compact size of the iPad Air suggests our team should not anticipate success coming from the audio speakers, but they are actually terrific for a tablet computer. The Mandarin star, who true name is Zhihao Chen, has actually raked in a spectacular $1.2 million in cash prize alone. Along with a totally involved globe you play any type of duty possible through materializing gameplay choices with every brand-new conflict and also pay the consequences as you go. Till recently, the response to that concern was a loud 'no' till AirBnB came. The unusual U-shaped secludeds, which can supposedly endure in any type of temperature, can be deployed to any kind of part of the planet and are actually self-supporting adequate to make it through alone - in the course of a deadly infection outbreak or even a radiation misfortune. Saat ini mereka sangat kekurangan air, dikarenakan buaya-buaya ini tidak bertempat tinggal di sungai atau rawa namun mereka sedang berada di bawah tanah dan saluran-saluran pipa sky. The almost 700 rooms held within home the mayor's offices, the city board workplaces, and also the whole civil courthouse (all for a city from 2.5 thousand). The apple ipad Air 2, then, still stands as the provider's mainstream full-sized tablet. The force (the blue arrow) can be defined in three techniques: the X and also Y elements, the viewpoint as well as toughness (size from the arrow), or even the durability as well as a setting somewhere the arrow is pointing to. All 3 point out the same force, yet each are convenient in different circumstances. The 13-inch MacBook Sky possesses a measly 1440 x 900 settlement door, which diminishes when you compare it to Retina display on the MacBook Pro along with 2650 x 1600 (13-inch) or 2880 x 1800 (15-inch) settlements. While this series is certainly not structured around an exam, finding out PowerShell is among one of the most significant points you may do as a system administrator, thus if there is one thing you want to learn to assist your IT job, this is it. And, it's a lot of fun. This application delivers some really standard suggestions, like paying attention to the rhythm, shifting your body weight properly, always keeping loose, when as well as why you ought to throw your submit the sky. Any person possessing concerns along with Google Play Establishment - this applies to both Air 3G along with the current 2.0.1 upgrade (are going to upload more info later on) and Air II - please administer this remedy. In order to accomplish this you'll need assistance off the monsters and also straying visitors throughout the globe. If you're brand-new to the globe of Minecraft, the initial thing you'll want to perform is find some method to protect yourself. So performed Hood By Sky earlier this month, where the label showcased males stomping confidently in open-toed, well-heeled shoes. Still, in the end, the 3 guy leads stumbled upon as meaning properly, producing Modern Gentlemen a very harmless half-hour from enjoyable, which parents can easily utilize to talk to teenagers about exactly what to expect when they begin courting. A United Boeing 757 taxis past a Delta Airlines Boeing 757 at Los Angeles International Flight terminal Might 29, 2015. At the end of each globe you will certainly face a Supervisor that will definitely strip your goofy skin layer off if you're certainly not cautious. The file located 63 percent from natural World Culture Sites throughout every continent, apart from Europe, saw an enhanced existence from mankind considering that the year 2000. You are going to drift to the top from the log cabin and swiftly locate your own self entraped if the airplane fills up along with water. Again and again, our company learn that when women typically aren't at the dining table or even in the room-- our experts shed. As a matter of fact, in order to do anything along with planet clocks on your Watch, you need to use your apple iphone's Time clock app. Ted Nelson coined the term hypertext" in 1963; our team now describe the document-to-document linkage he envisioned as simple web links" on the world wide web. The Nexus 9 also has a somewhat larger 1.6 MP front-facing electronic camera (FFC) than the ipad tablet Air 2's 1.2 MP for social networking sites selfies and video chatting, or even FaceTime, as they name their exclusive chatting. You might believe that prices would be actually economical if you acquired your tickets 6 months ahead of time, however that's however not just how this works. The action has you by means of different aspect of the dinosaur's globe off forests to woodlands.
0 notes
Link
Acutelearn is leading training company provides corporate, online and classroom training on various technologies like AWS, Azure, Blue prism, CCNA, CISCO UCS, CITRIX Netscaler,CITRIX Xendesktop, Devops chef, EMC Avamar, EMC Data Domain, EMC Networker, EMC VNX, Exchange Server 2016, Hyper-V, Lync server, Microsoft windows clustering, Netapp, Office 365, Openspan, RedHat openstack, RPA, SCCM, vmware nsx 6.0, vmware vrealize, vmware vsphere, windows powershell scripting. For more information reach us on +917702999361 / 371 www.acutelearn.com
windows azure course content:
Introduction to Microsoft Azure •Cloud Technology Overview •Microsoft Azure Overview •Azure Regions & Locations •Azure Portals •Managing Azure with Windows PowerShell Implementing & Managing Virtual machines •Overview of Virtual machines options- Classic & Resource Manager VM •Resource groups •Creating and Configure a Classic Azure Virtual machine •Create a Resource manager VM •Creating Resource Manager VM Templates •Adding Additional disks •Assign Static IP Address •Security groups •Create VM Backup •Configuring Availability Set for VM’s (Fault and Update Domains) Azure Load Balancer •External Load balancer •Internal load balancer •Azure Load balancer configuration •Adding VM’s into Load balancer •Creating load balancer rules •Understanding NAT Azure Traffic Manager •Overview of Traffic Manager •Load balancing across VM’s and Web Apps Implementing and Managing Virtual Networks •Overview of Azure networking •Implementing and managing Azure virtual networks •Configuring Azure virtual networks •Configuring Azure virtual network connectivity •Overview of Azure classic networking •Configuring Subnets •Configuring peering between Azure Networks •Understanding Virtual Network Gateway ( VNG) & Local Network gateway •Configure VPN between Azure Networks Storage •Planning Storage •Classification of storage & Usage of different types of storage •Blob, File, Queue, Table, Disk Storage Overview •Implementing and Managing Storage •Monitoring Storage •Usage of tools for connecting to Storage Storage explorer Backup •Overview of Azure Backup Services •Azure VM backup •On premise data backup to Azure •Retention policies Planning and Implementing Azure MSSQL Database •Data Services in Microsoft Azure •Implementing Azure SQL Database •Database High Availability •Monitoring Azure SQL Database •Backup and Restore Azure SQL Database Implementing Azure Active Directory & Identity Management •Creating and managing Azure Directories •Sync On-Premise AD with Azure AD •Setup Multifactor Authentication •Overview of Azure Active Directory Premium •Azure AD Proxy •Implementing Domain controller in Azure and usage of Azure DNS/NSG’s •Joining systems to domain Implementing Websites •Planning for Website Deployment •Deploying Websites •Configuring Websites •Monitoring Websites and Web jobs •Scaling websites •Troubleshooting websites •Tools Implementing Content Delivery Networks & Media services •Overview of Azure content Delivery Networks •Creating a Media Services Account and Upload Content •Publishing Content with Azure Media Services •Publishing and Scaling Media Content Monitoring and Diagnostics • Troubleshooting virtual machines (Boot diagnostics, Redeploy etc.,) • Monitoring Virtual machines , storage , network • Boot logs • Activity logs
Address: Acutelearn Technologies, Flat No 80 & 81, 4th floor, Above Federal Bank Building, Besides Cafe coffee day Lane, Madhapur, Hyderabad-500081
0 notes
Text
Microsoft Azure 70-533 dumps|CertTree
CertTree guarantee exam success rate of 100% ratio, except no one. You choose CertTree, and select the training you want to start, you will get the best resources with market and reliability assurance.CertTree have the latest Microsoft Azure 70-533 dumps|CertTree. The industrious CertTree IT experts through their own expertise and experience continuously produce the latest Microsoft Azure 70-533 dumps|CertTree to facilitate IT professionals to pass the Microsoft certification 70-533 exam. Microsoft Azure 70-533 dumps|CertTree have wide coverage of the content of the examination and constantly update and compile. CertTree can provide you with a very high accuracy of exam preparation. Selecting CertTree can save you a lot of time, so that you can get the Microsoft 70-533 certification earlier to allow you to become a Microsoft IT professionals.CertTree is a convenient website to provide service for many of the candidates participating in the IT certification exams. Share some Microsoft Azure Infrastructure Solutions 70-533 exam questions and answers below. You administer an Azure Web Site named contoso. The development team has implemented changes to the website that need to be validated. You need to validate and deploy the changes with minimum downtime to users. What should you do first? A. Create a new Linked Resource. B. Configure Remote Debugging on contoso. C. Create a new website named contosoStaging. D. Create a deployment slot named contosoStaging. E. Back up the contoso website to a deployment slot. Answer: D You manage an application deployed to virtual machines (VMs) on an Azure virtual network named corpVnet1. You plan to hire several remote employees who will need access to the application on corpVnet1. You need to ensure that new employees can access corpVnet1. You want to achieve this goal by using the most cost effective solution. Which two actions should you perform? Each correct answer presents part of the solution. A. Create a VPN subnet. B. Enable point-to-point connectivity for corpVnet1. C. Enable point-to-site connectivity for corpVnet1. D. Create a gateway subnet. E. Enable site-to-site connectivity for corpVnet1. F. Convert corpVnet1 to a regional virtual network. Answer: C,D HOTSPOT You create a virtual network named fabVNet01. You design the virtual network to include two subnets, one named DNS-subnet and one named Apps-subnet, as shown in the exhibit. (Click the Exhibits button.) In the table below, identify the number of IP addresses that will be available for virtual machines (VMs) or cloud services in each subnet. Make only one selection in each column. Answer: You manage a cloud service that supports features hosted by two instances of an Azure virtual machine (VM). You discover that occasional outages cause your service to fail. You need to minimize the impact of outages to your cloud service. Which two actions should you perform? Each correct answer presents part of the solution. A. Deploy a third instance of the VM. B. Configure Load Balancing on the VMs. C. Redeploy the VMs to belong to an Affinity Group. D. Configure the VMs to belong to an Availability Set. Answer: B,D Your company has two cloud services named CS01 and CS02. You create a virtual machine (VM) in CS02 named Accounts. You need to ensure that users in CS01 can access the Accounts VM by using port 8080. What should you do? A. Create a firewall rule. B. Configure load balancing. C. Configure port redirection. D. Configure port forwarding. E. Create an end point. Answer: E DRAG DROP You administer an Azure Virtual Machine (VM) named CON-CL1. CON-CL1 is in a cloud service named ContosoService1. You discover unauthorized traffic to CON-CL1. You need to: - Create a rule to limit access to CON-CL1. - Ensure that the new rule has the highest precedence. Which Azure Power Shell cmdlets and values should you use? To answer, drag the appropriate cmdlet or value to the correct location in the Power Shell command. Each cmdlet or value may be used once, more than once, or not at all. You may need to drag the split bat between panes or scroll to view content. Answer: You plan to use Password Sync on your DirSync Server with Azure Active Directory (Azure AD) on your company network. You configure the DirSync server and complete an initial synchronization of the users.Several remote users are unable to log in to Office 365. You discover multiple event log entries for "Event ID 611 Password synchronization failed for domain."You need to resolve the password synchronization issue.Which two actions should you perform? Each correct answer presents part of the solution. A. Restart Azure AD Sync Service. B. Run the Set-FullPasswordSync Power Shell cmdlet. C. Force a manual synchronization on the DirSync server. D. Add the DirSync service account to the Schema Admins domain group. Answer: A,B HOTSPOT You manage an Azure Web Site named contosoweb. Some users report that they receive the following error when they access contosoweb: ¡°http Status 500.0 - Internal Server Error.¡± You need to view detailed diagnostic information in XML format. Which option should you enable? To answer, select the appropriate option in the answer area. Answer: You administer an Azure subscription with an existing cloud service named contosocloudservice. Contosocloudservice contains a set of related virtual machines (VMs) named ContosoDC, ContosoSQL and ContosoWeb1. You want to provision a new VM within contosocloudservice. You need to use the latest gallery image to create a new Windows Server 2012 R2 VM that has a target IOPS of 500 for any provisioned disks. Which PowerShell command should you use? A. Option A B. Option B C. Option C D. Option D Answer: D You manage a cloud service named fabrikamReports that is deployed in an Azure data center. You deploy a virtual machine (VM) named fabrikamSQL into a virtual network named fabrikamVNet. FabrikamReports must communicate with fabrikamSQL. You need to add fabrikam Reports to fabrikamVNet. Which file should you modify? A. the network configuration file for fabrikamVNet B. the service definition file (.csdef) for fabrikamReports C. the service definition file (.csdef) for fabrikamSQL D. the service configuration file (.cscfg) for fabrikamReports E. the service configuration file (.cscfg) fabrikamSQL Answer: D You are the administrator for three Azure subscriptions named Dev, Test, and Prod. Your Azure Power Shell profile is configured with the Dev subscription as the default. You need to create a new virtual machine in the Test subscription by using the least administrative effort. Which Power Shell command should you use? A. Option A B. Option B C. Option C D. Option D Answer: A DRAG DROP You manage an Azure virtual machine (VM) named AppVM. The application hosted on AppVM continuously writes small files to disk. Recently the usage of applications on AppVM has increased greatly. You need to improve disk performance on AppVM. Which Microsoft Azure Power Shell cmdlet should you use with each Power Shell command line? To answer, drag the appropriate Microsoft Azure Power Shell cmdlet to the correct location in the Power Shell code. Each Power Shell cmdlet may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content. Answer: Explanation * Set-AzureDataDisk Sets the host-cache mode on an existing data disk object. * Example: This command gets the "MyVM" virtual machine running on the "myservice" cloud service, and then sets the data disk at LUN 2 of the virtual machine to use Nonehost caching. Windows PowerShell C:PS>Get-AzureVM "myservice" -name "MyVM" | Set-AzureDataDisk -LUN 2 -HostCachingNone| Update-AzureVM * Set-AzureDataDisk Parameter: -HostCaching Sets the host level caching settings of the disk. Possible values are: None, ReadOnly and ReadWrite (). When you setup a data disk on a virtual machine, you get three host caching choices: The purpose of a cache is to cache data to be read as reading from a cache is faster than reading from a disk. There is no performance benefit in caching the log files as these will not be re-read by the application. Therefore, we need the logs to be written directly to disks rather than being written to cache first then disk (Read) or written to the cache only (Read/Write). Your network includes a legacy application named LegacyApp1. The application only runs in the Microsoft .NET 3.5 Framework on Windows Server 2008. You plan to deploy to Azure Cloud Services. You need to ensure that LegacyApp1 will run correctly in the new environment. What are two possible ways to achieve this goal? Each correct answer presents a complete solution. A. Upload a VHD with Windows Server 2008 installed. B. Deploy LegacyApp1 to a cloud service instance configured with Guest OS Family 2. C. Deploy LegacyApp1 to a cloud service instance configured with Guest OS Family 1. D. Deploy LegacyApp1 to a cloud service instance configured with Guest OS Family 3. Answer: A,B Your company plans to migrate from On-Premises Exchange to Office 365. The existing directory has numerous service accounts in your On-Premises Windows Active Directory (AD), stored in separate AD Organizational Units (OU) for user accounts.You need to prevent the service accounts in Windows AD from syncing with Azure AD.What should you do? A. Create an OU filter in the Azure AD Module for Windows PowerShell. B. Configure directory partitions in miisclient.exe. C. Set Active Directory ACLs to deny the DirSync Windows AD service account MSOL_AD_SYNC access to the service account OUs. D. Create an OU filter in the Azure Management Portal. Answer: B You manage a cloud service that is running in two small instances. The cloud service hosts a help desk application. The application utilizes a virtual network connection to synchronize data to the company's internal accounting system. You need to reduce the amount of time required for data synchronization. What should you do? A. Configure the servers as large instances and re-deploy. B. Increase the instance count to three. C. Deploy the application to Azure Web Sites. D. Increase the processors allocated to the instances. Answer: A 70-533 is an Microsoft certification exam, so 70-533 is the first step to set foot on the road of Microsoft certification. 70-533 certification exam become more and more fiery and more and more people participate in 70-533 exam, but passing rate of 70-533 certification exam is not very high.When you select Microsoft Azure 70-533 dumps|CertTree, do you want to choose an exam training courses?
0 notes