#punycode
Explore tagged Tumblr posts
Text
Para bios no Twitter/X
Para deixar a bio centralizada: (⠀⠀)
Para tirar o "traduzir bio": ( ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏ ͏͏ ͏ ͏ ͏ ͏)͏
Para deixar o nome invisível: ( ؘ ) ( ִֶָ ) ( ً )
Blank Spaces:
(⠀⠀ ⠀) bios
(⠀ ) locs

Site para fazer seu próprio website personalizado para Twitter/X.
#x#spaces#locs#twitter#kpop#messy bios#messy locs#twitter bios#bios random#bios meme#asthetic symbols#soft bios#cute symbols#kpop locs#random bios#symbols#headers#carrd bios#kpop long bios#random locs#soft icons#soft locs#twitter headers#x headers#X help#tweeter help#punycode#blank space#bios para twitter#bios
1K notes
·
View notes
Link
#Bhashanet#digitalinclusion#DigitalIndia#e-governance#InternationalisedDomainNames#multilingualinternet#NIXI#Punycode
0 notes
Note
holii, sabes cómo usar punycoder? para hacer links para twitter.
holii, sabes c��mo usar punycoder? para hacer links para twitter.
7 notes
·
View notes
Text
Tumblr handles certain punycode urls in a weird way so people think my main blog contains a virus?
Despite using this site for over a decade, I no longer know how to use it (but apparently I can break it)
The rest of the school term is actually looking pretty good, I want to reorganize my room with the added time
I think I'm having a mental breakdown
3 notes
·
View notes
Text
0 notes
Text
As much as I do use a password manager, different passwords, MFA, and looking at URLs, I think it's unreasonable to expect average people to have that level of constant vigilance and computer expertise.
Looking at URLs still only catches the low-effort phishing scams, the high-effort ones get to do things that aren't visible to normal inspection, example from a legitimate website that I visit routinely in connection with church:
"søndagenstekst.no" (meaning Sunday's Text.Norwegian) is the displayed address and international domain of a website which gets translated through Punycode into an ASCII domain as "xn--sndagenstekst-bnb.no" under the hood.
Protecting one chunk of people from this danger would require something like forcing ASCII displays in the URL bar to prevent URL spoofing, which would degrade the internet for another chunk of people.
it's terrible and i have no solutions
This week we did our anti-phishing training at work and that's how I found out that nobody at the new company knew about cookiejacking either.
*screams forever*
Please use a password manager. Please use unique passwords. Please use MFA. Please learn to recognize phishing sites. Please check URLs.
2K notes
·
View notes
Text
How Malvertisers are Exploiting Google Ads
A malvertising campaign that manipulates Google Ads to divert users seeking popular software to fraudulent landing pages and deliver subsequent-stage payloads has come to light. Malwarebytes, the firm that unearthed this activity, described it as “distinctive in its methodology of fingerprinting users and distributing time-sensitive payloads.”
This attack specifically targets users looking for Notepad++ and PDF converters to display counterfeit ads on Google’s search results page. When these ads are clicked, the system weeds out bots and other unintended IP addresses by presenting a decoy website. If the visitor is considered valuable to the threat actor, they are rerouted to a cloned website promoting the software, while the system quietly fingerprints the system to ascertain if the request is coming from a virtual machine.
The Intricacies of the Malvertising Campaign
Users who fail the verification are directed to the official Notepad++ website, while a potential target is given a unique ID for “tracking purposes and also to make each download unique and time-sensitive.” The terminal-stage malware is an HTA payload that establishes a connection to a remote domain (“mybigeye[.]icu”) on a custom port and delivers subsequent malware.
Jérôme Segura, Director of Threat Intelligence, stated, “Threat actors are successfully employing evasion strategies that circumvent ad verification checks and enable them to target specific victim types.” He added, “With a dependable malware delivery chain at their disposal, malicious actors can concentrate on enhancing their decoy pages and creating custom malware payloads.”
Overlap with Similar Campaigns and the Use of Punycode
This revelation coincides with a similar campaign that targets users searching for the KeePass password manager with harmful ads that direct victims to a domain using Punycode (keepass[.]info vs. ķeepass[.]info), a unique encoding used to convert Unicode characters to ASCII.
The Role of Decoy Sites and Malicious Installers
Users who arrive at the decoy site are duped into downloading a malicious installer that ultimately triggers the execution of FakeBat (also known as EugenLoader), a loader designed to download other malicious code.
The misuse of Punycode is not entirely new, but its combination with rogue Google Ads indicates that malvertising via search engines is becoming increasingly sophisticated. The objective is to execute a homograph attack and entice victims into installing malware by using Punycode to register domain names similar to a legitimate site.
The Constant Evolution of Threats
Multiple threat actors such as TA569 (also known as SocGholish), RogueRaticate (FakeSG), ZPHP (SmartApeSG), ClearFake, and EtherHiding have been noticed exploiting themes related to fake browser updates to disseminate Cobalt Strike, loaders, stealers, and remote access trojans, indicating that these attacks are a persistent, evolving threat.
Dusty Miller, a researcher at Proofpoint, stated in an analysis published this week, “Fake browser updates exploit end user trust with compromised websites and a lure customized to the user’s browser to legitimize the update and fool users into clicking.” He warned, “The threat is only in the browser and can be initiated by a click from a legitimate and expected email, social media site, search engine query, or even just navigating to the compromised site.”
https://www.infradapt.com/news/how-malvertisers-are-exploiting-google-ads/
0 notes
Link
Los analistas de Malwarebytes informaron que el anuncio malicioso se publicó en respuesta a consultas de búsqueda de "keepass". Era particularmente engañoso porque mostraba el logotipo y la URL oficiales de KeePass, apareciendo antes de los resultados de búsqueda orgánicos. Esta apariencia engañosa lo hacía casi indistinguible del sitio legítimo. Cuando los usuarios hacían clic en el anuncio, eran redirigidos a una página web aparentemente segura (HTTPS) diseñada para imitar el sitio web oficial de KeePass.
0 notes
Text
the discord change haters are so silly calling everyone an anglocentrist and throwing a tantrum over it because 1. everyone using discord knows what is a latin alphabet regardless of their background 2. they need to get creative with their fucking usernames instead of having 400 jasons or using fancy fonts
and the scariest of them all..
3. youre gonna fucking die when you realize all urls are made out of mostly latin alphabet glyphs. this is so #anglocentrist i know very scary. yes even the punycode urls are at the core made out of latin glyphs
#rant#im pretty sure none of you actually give a fuck about anglocentrism#you guys are still american imperialists at heart no matter how big of a mask you put on
1 note
·
View note
Quote
日本語で記されているドメインは、そのまま使われているわけではありません。実際には日本語を英数文字に変換して使っています。Punycode(ピュニコード)と呼ぶ変換方式を使うのが一般的で、日本語をPunycode表記へと変換すると、通常はまったく意味を成さない英数の文字列へと置き換えられます。
日本語ドメインとは|ドメインの基礎知識|名づけてねっと
0 notes
Text
i think this should technically be possible already using internationalized domain names, afaict there is nothing about punycode that would prevent you from encoding non-printing characters. whether registrars would allow it is of course a different question.
i demand the internet engineering task force implement the use of non-printing characters in URLs
23 notes
·
View notes
Text
PUNYCODES FOR TWT !
xn--3-cjn : ‹3 xn--q3h : ☆ xn--c6h : ♡ xn--0jcb : ୨୧ xn--p3h : ★ xn--xmj : ⵌ xn--yci : ✦ xn--zre : ᘐ xn--)-kv2e : ︶꒦ xn--)-jv2e : ꒦︶ xn--sqab7456y : ˃𖥦˂ xn--odi : ✿ xn--rk8ah : ꒥꒡ xn--qqaa : ˀˀ xn--9be : Ꮺ xn--7chb67w : ≧▽≦ xn--q3h018a : ☆〜 xn--yciz693bqba : ꒦꒷✦ xn--oqe : ᗢ xn--yre : ᘏ xn--ws7d : 𓂃
#twitter#twitter links#twitter symbols#twitter aesthetic#how to add symbols to link#twt bios#twt aesthetic#twt layouts#symbols for twt#symbols for twitter#punycodes twt#punycodes twitter#twitter symbol#punycode#punycodes#aesthetic#twitter headers#twt
2K notes
·
View notes
Text
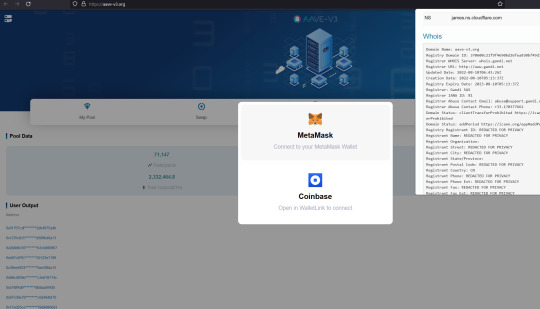
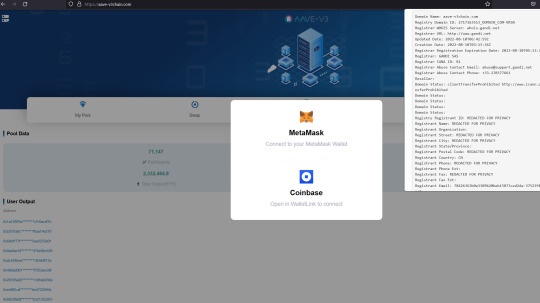

Fake AAVE scams
aave-v3.org aave-v3block.com aave-v3chain.com aave-v3transaction.com aave.xn--cobase-c9a8p.com aavega-interactive.agencyanalytics.app aavegotchi.pet aavegotchi.vercel.app
Warning!
The real website is https://AAVE.COM
All those others are fakes.
2 notes
·
View notes
Text
More importantly this means any characters from any language included within utf-8 should work as a "domain" which means there's no need to encode the "URL"s with something like Punycode:
Implemented Fins for Catch through the whole stack, drilling down on the finals bits of routing and slowly changing the todo action queue to handle action objects for programmer ease later
17 notes
·
View notes
Text
0 notes
Text
JODI’s IDN

Registering g.net or a.com hasn't been possible since 1993, when the Internet Assigned Numbers Authority banned new registrations of single-letter domains. So how did the art duo JODI get their 2016 project to live on domains like ᠐.com?
The answer is that JODI, long exploiters of contradictions and loopholes in the mechanics of the web, picked symbols from beyond the Latin script, registering these domains using Punycode.
Punycode is an ASCII transcoding of Unicode meant to represent Internationalized Domain Names (IDNs). It allows domains to include international characters, but not in a way that could be misleading, such as creating "microsoft.com" with the lower-case o from another alphabet; those special symbols are expanded into a sequence beginning with xn--.
The ᠐ in ᠐.com is not a zero in Roman characters, but the Mongolian Numeral Zero, Unicode character 6160; depending on the font used, it can be visually identical to 0. Since the ASCII representation (in this case, xn--m6e.com) is what actually gets registered, JODI were able to work around the single-letter restriction.
Load the site at ᠐.com and its contents are simply the Apache system defaults: in 2016 it returned "Apache is functioning normally." In 2020, it presents just an empty directory that can be navigated into and out of, giving it the feel of pre-web gopher sites, or the very early web, when exposed, navigable directories were common.
Other sites in the IDN series forward the user through a sequence of subdomains, appending their own hostname to a growing list, in a pattern reminiscent of typewriter poetry; see the top image, from ꀍ.com. However, "growing list" is a bit misleading. The output is not actually carried from one domain to the next—posted or passed along in cookies—but simply hardcoded. If you jump to one of the sites in the middle of the list, it will output of the previous sites are already there. It is a movie, with each frame on a different website, and we're forwarded from one to the next.
READ MORE
12 notes
·
View notes