#quantum computing 2021
Explore tagged Tumblr posts
Text
An open copyright casebook, featuring AI, Warhol and more

I'm coming to DEFCON! On Aug 9, I'm emceeing the EFF POKER TOURNAMENT (noon at the Horseshoe Poker Room), and appearing on the BRICKED AND ABANDONED panel (5PM, LVCC - L1 - HW1–11–01). On Aug 10, I'm giving a keynote called "DISENSHITTIFY OR DIE! How hackers can seize the means of computation and build a new, good internet that is hardened against our asshole bosses' insatiable horniness for enshittification" (noon, LVCC - L1 - HW1–11–01).

Few debates invite more uninformed commentary than "IP" – a loosely defined grab bag that regulates an ever-expaning sphere of our daily activities, despite the fact that almost no one, including senior executives in the entertainment industry, understands how it works.
Take reading a book. If the book arrives between two covers in the form of ink sprayed on compressed vegetable pulp, you don't need to understand the first thing about copyright to read it. But if that book arrives as a stream of bits in an app, those bits are just the thinnest scrim of scum atop a terminally polluted ocean of legalese.
At the bottom layer: the license "agreement" for your device itself – thousands of words of nonsense that bind you not to replace its software with another vendor's code, to use the company's own service depots, etc etc. This garbage novella of legalese implicates trademark law, copyright, patent, and "paracopyrights" like the anticircumvention rule defined by Section 1201 of the DMCA:
https://www.eff.org/press/releases/eff-lawsuit-takes-dmca-section-1201-research-and-technology-restrictions-violate
Then there's the store that sold you the ebook: it has its own soporific, cod-legalese nonsense that you must parse; this can be longer than the book itself, and it has been exquisitely designed by the world's best-paid, best-trained lawyer to liquefy the brains of anyone who attempts to read it. Nothing will save you once your brains start leaking out of the corners of your eyes, your nostrils and your ears – not even converting the text to a brilliant graphic novel:
https://memex.craphound.com/2017/03/03/terms-and-conditions-the-bloviating-cruft-of-the-itunes-eula-combined-with-extraordinary-comic-book-mashups/
Even having Bob Dylan sing these terms will not help you grasp them:
https://pluralistic.net/2020/10/25/musical-chairs/#subterranean-termsick-blues
The copyright nonsense that accompanies an ebook transcends mere Newtonian physics – it exists in a state of quantum superposition. For you, the buyer, the copyright nonsense appears as a license, which allows the seller to add terms and conditions that would be invalidated if the transaction were a conventional sale. But for the author who wrote that book, the copyright nonsense insists that what has taken place is a sale (which pays a 25% royalty) and not a license (a 50% revenue-share). Truly, only a being capable of surviving after being smeared across the multiverse can hope to embody these two states of being simultaneously:
https://pluralistic.net/2022/06/21/early-adopters/#heads-i-win
But the challenge isn't over yet. Once you have grasped the permissions and restrictions placed upon you by your device and the app that sold you the ebook, you still must brave the publisher's license terms for the ebook – the final boss that you must overcome with your last hit point and after you've burned all your magical items.
This is by no means unique to reading a book. This bites us on the job, too, at every level. The McDonald's employee who uses a third-party tool to diagnose the problems with the McFlurry machine is using a gadget whose mere existence constitutes a jailable felony:
https://pluralistic.net/2021/04/20/euthanize-rentier-enablers/#cold-war
Meanwhile, every single biotech researcher is secretly violating the patents that cover the entire suite of basic biotech procedures and techniques. Biotechnicians have a folk-belief in "patent fair use," a thing that doesn't exist, because they can't imagine that patent law would be so obnoxious as to make basic science into a legal minefield.
IP is a perfect storm: it touches everything we do, and no one understands it.
Or rather, almost no one understands it. A small coterie of lawyers have a perfectly fine grasp of IP law, but most of those lawyers are (very well!) paid to figure out how to use IP law to screw you over. But not every skilled IP lawyer is the enemy: a handful of brave freedom fighters, mostly working for nonprofits and universities, constitute a resistance against the creep of IP into every corner of our lives.
Two of my favorite IP freedom fighters are Jennifer Jenkins and James Boyle, who run the Duke Center for the Public Domain. They are a dynamic duo, world leading demystifiers of copyright and other esoterica. They are the creators of a pair of stunningly good, belly-achingly funny, and extremely informative graphic novels on the subject, starting with the 2008 Bound By Law, about fair use and film-making:
https://www.dukeupress.edu/Bound-by-Law/
And then the followup, THEFT! A History of Music:
https://web.law.duke.edu/musiccomic/
Both of which are open access – that is to say, free to download and share (you can also get handsome bound print editions made of real ink sprayed on real vegetable pulp!).
Beyond these books, Jenkins and Boyle publish the annual public domain roundups, cataloging the materials entering the public domain each January 1 (during the long interregnum when nothing entered the public domain, thanks to the Sonny Bono Copyright Extension Act, they published annual roundups of all the material that should be entering the public domain):
https://pluralistic.net/2023/12/20/em-oh-you-ess-ee/#sexytimes
This year saw Mickey Mouse entering the public domain, and Jenkins used that happy occasion as a springboard for a masterclass in copyright and trademark:
https://pluralistic.net/2023/12/15/mouse-liberation-front/#free-mickey
But for all that Jenkins and Boyle are law explainers, they are also law professors and as such, they are deeply engaged with minting of new lawyers. This is a hard job: it takes a lot of work to become a lawyer.
It also takes a lot of money to become a lawyer. Not only do law-schools charge nosebleed tuition, but the standard texts set by law-schools are eye-wateringly expensive. Boyle and Jenkins have no say over tuitions, but they have made a serious dent in the cost of those textbooks. A decade ago, the pair launched the first open IP law casebook: a free, superior alternative to the $160 standard text used to train every IP lawyer:
https://web.archive.org/web/20140923104648/https://web.law.duke.edu/cspd/openip/
But IP law is a moving target: it is devouring the world. Accordingly, the pair have produced new editions every couple of years, guaranteeing that their free IP law casebook isn't just the best text on the subject, it's also the most up-to-date. This week, they published the sixth edition:
https://web.law.duke.edu/cspd/openip/
The sixth edition of Intellectual Property: Law & the Information Society – Cases & Materials; An Open Casebook adds sections on the current legal controversies about AI, and analyzes blockbuster (and batshit) recent Supreme Court rulings like Vidal v Elster, Warhol v Goldsmith, and Jack Daniels v VIP Products. I'm also delighted that they chose to incorporate some of my essays on enshittification (did you know that my Pluralistic.net newsletter is licensed CC Attribution, meaning that you can reprint and even sell it without asking me?).
(On the subject of Creative Commons: Boyle helped found Creative Commons!)
Ten years ago, the Boyle/Jenkins open casebook kicked off a revolution in legal education, inspiring many legals scholars to create their own open legal resources. Today, many of the best legal texts are free (as in speech) and free (as in beer). Whether you want to learn about trademark, copyright, patents, information law or more, there's an open casebook for you:
https://pluralistic.net/2021/08/14/angels-and-demons/#owning-culture
The open access textbook movement is a stark contrast with the world of traditional textbooks, where a cartel of academic publishers are subjecting students to the scammiest gambits imaginable, like "inclusive access," which has raised the price of textbooks by 1,000%:
https://pluralistic.net/2021/10/07/markets-in-everything/#textbook-abuses
Meanwhile, Jenkins and Boyle keep working on this essential reference. The next time you're tempted to make a definitive statement about what IP permits – or prohibits – do yourself (and the world) a favor, and look it up. It won't cost you a cent, and I promise you you'll learn something.

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/07/30/open-and-shut-casebook/#stop-confusing-the-issue-with-relevant-facts

Image: Cryteria (modified) Jenkins and Boyle https://web.law.duke.edu/musiccomic/
CC BY-NC-SA 4.0 https://creativecommons.org/licenses/by-nc-sa/4.0/
#pluralistic#jennifer jenkins#james boyle#ip#law#law school#publishing#open access#scholarship#casebooks#copyright#copyfight#gen ai#ai#warhol
182 notes
·
View notes
Text
The Looping World of NieR
If you have any interest in NieR lore and have played either NieR (2010) or NieR Replicant Ver.1.22474487139... (2021), you've probably asked...
Question 1: "so... is Gestalt or Replicant canon to automata?"
Hi! Quick Side-note: I will refer to NieR Replicant Ver.1.22474487139... as Replicant (2021) occasionally because those numbers really take up a lot of space lol
For a while, and even somewhat now, the only answers you'd get are something along the lines of "they're both canon, just different branches" or "they're both canon and completely interchangeable." Both of which are half true, both are indeed canon, but they're also quite off the mark about how they're both canon.
"Replicant" and "Gestalt" are not parallel worlds, but one of the patterns of the repeated world, and the relationship between the main character and Yonah was sometimes a brother and sister, sometimes a parent and child, so there is a difference in the years in the settings of both works.
This is a machine translated snippet from a 2010 Famitsu interview with Yoko Taro(courtesy of the Accord's Library discord server). So the world of NieR is repeating and sometimes the main character is a dilf and sometimes hes a twink? That makes sense. Its a relatively straightforward statement, but like most things Yoko says, it just leaves more questions.
Question 2: "Is Replicant Ver.1.22474487139... the same as Replicant or is it a different loop?"
Good question! It's actually a separate iteration taking place after NieR: Automata. This explanation will be a little longer, so stick with me. After the events of NieR Replicant (2010) we have the short story The Lost World Ver.1.00 which is also known as ending e. This short story takes place after ending d and shows Kaine confronting k?K? Σ ?XH, an administrator who manages the quantum computer that oversees the gestalt project. In Replicant Ver.1.22474487139... this story is included in the game itself, however this time around we have a second administrator named Her. Both versions of the story show Kaine destroying the administrator(s) and bringing back a 16 year old protagonist.


The Lost World Appendix Ver.1.22474487139... is a short story included in Grimoire NieR Revised Edition that takes place after Ending E of Replicant (2021). It explains that the male administrator created his female counterpart after witnessing the same loop time and time again by himself. This, as well as the fact that Automata takes place after The Lost World Ver.1.00, means that the timeline should look something like this:

NieR Re[in]carnation also plays an important part in the discussion of world loops, but I'll leave most of that for another time.
Question 3: Where do the loops begin and end?
This one is... difficult to answer. So I'll hold off on attempting to explain that until a future post (maybe(no promises)). Until then, just know that there's a lot of unknown here and all we really have are theories.
Hi! This is a bit of an afterword but this is my first blog post so I figured I should introduce myself! My name is Emily, and I'm a college student in her early 20s about to start studying Japanese with hopes of going into some form of localization or reporting. I'm a huge fan of JRPGs, visual novels, anime, and most relevant here: the Yokoverse (NieR, Drakengard, SINoALICE etc.) I'll probably be posting here really sporadically about lore and any new release information, so if you're interested in that kind of thing I hope you stick around lol
22 notes
·
View notes
Text
Threatened by values that are at the core of the NATO alliance and shared by Ukraine and many other countries around the world, the Kremlin launched a full-scale invasion of Ukraine in February 2022 with the intention to wipe the country off the map, crush freedom, and weaken democracy. In doing so, Russia receives significant support, including the provision of advanced technology, from its authoritarian friends, not least China, Iran, and North Korea. More than Ukraine’s survival, Europe’s security is at stake. As a global fight is being played out on the battlefield in Ukraine, innovative technologies are being rolled out at unprecedented speed.
For centuries, security in Western democratic societies has been tied to their ability to innovate. From the bow and arrow to battle tanks and from hand grenades to hypersonic missiles, new military inventions not only changed the way we fight and win wars. They also underpinned our ability to shape successful and resilient societies. Now, with a massive technological revolution underway, which has seen the rise of artificial intelligence, autonomous systems, and quantum technologies, it is not enough to just be able to innovate. We must remain at the forefront of innovation. By leading innovation, we can continue to shape our security environment. If we don’t, others will.
NATO nations, and the United States in particular, have long had technological primacy. But they are being challenged. China is not only rapidly developing technologies, but it is also connecting new technologies together, multiplying their potential disruptive impact on our societies, our economies, and our security. Semiconductors from China are a critical component of the phones and computers we use every day—but also of the high-end military systems and capabilities we rely on for our security. Russia’s war against Ukraine is shedding light on the incredible speed of innovation. Ukrainians are innovating fast but not fast enough. In just weeks, Russians managed to neutralize the innovative software that Ukrainians have been putting into drones.
To keep its 1 billion citizens safe, NATO must ensure it out-competes any strategic competitor and potential adversary. That is why we are doubling down on efforts to accelerate technological innovation in the field of security and defense. This is not something NATO does alone but together with the drivers of innovation in the private sector. Today, they produce 90 percent of the dual-use technologies used for our defense and security. The private sector is an indispensable partner.
When I took up my job as deputy secretary-general at NATO in 2019, Secretary-General Jens Stoltenberg asked me to be NATO’s innovation champion. One of my first tasks was to help establish the NATO Innovation Board. As its chair, I prioritized innovation across the alliance, and as a result, NATO has significantly sped up its technological transformation. At the Brussels summit in 2021 and after, NATO leaders launched two breakthrough initiatives to tighten the links between NATO and the dual-use innovation ecosystem. One was the Defence Innovation Accelerator for the North Atlantic, which brings together innovators across the alliance to cooperate on critical technologies. The other was the NATO Innovation Fund, a 1 billion euro venture capital fund that provides strategic investments in start-ups developing technologies in areas that are critical to allied security. NATO has also already established a regular high-level dialogue with private sector leaders, including with companies such as Google, Microsoft, and Amazon Web Services. More recently, NATO stood up a Transatlantic Quantum Community to ensure a secure, resilient, and competitive quantum ecosystem and launched a commercial space platform (SPACENET) to further cooperation with commercial space industries. The alliance has come a long way. Yet the epochal moment we are confronted with requires even bigger and bolder adjustments.
NATO needs to innovate more and faster. Above all, we need to dare to innovate differently. This means rethinking the way we structure our partnerships with the private sector in the area of defense. NATO has worked for decades to achieve interoperability between national militaries. Now, it needs to achieve interoperability with the trans-Atlantic innovation ecosystem to future-proof our security.
In particular, NATO needs to adjust the mechanisms and procedures it has built and relied on for decades to develop and purchase defense capabilities. Defense plans, procurement cycles, and acquisition models are important and necessary to guardrail innovation and help minimize financial risk. But they are also lengthy, rigid, and complex. They can be a roadblock to innovation and a risk for our security. Our procurement timelines are set to the acquisition of large pieces of hardware that we hang on to for decades. New aircraft that NATO is acquiring now to replace the aging fleet of Airborne Warning and Control System aircraft will only be operational in 2031. In the information technology arena, where requirements are different and change very rapidly, more flexible procedures are essential to ensure allied and partner nations get what they need when they need it—and not five or 10 years down the line.
At the same time, as we rethink our partnership with the private sector to accelerate innovation, we must stay aligned with our values. Technological innovation, especially in the field of defense, can be used to curb freedom and control and manipulate people. This is what our competitors do. Moscow and Beijing do not face up to the important ethical dimensions in their race to develop and deploy technologies. But NATO does. It has already integrated so-called principles of responsible use in all its strategies on emerging and disruptive technologies, including AI, autonomy, biotechnologies and human enhancements, space, and quantum. These principles ensure that the use of these new technologies complies with international law and respects our democratic values. Rather than stifling innovation, they enable it by creating a predictable, trustworthy, and responsible environment in which everyone—innovators, adopters, end users, and our publics—feels confident using these technologies and cooperating with one another.
Looking ahead to the next NATO summit in The Hague in June 2025, NATO will pursue its work to foster the development of the long-term revolutionary innovation required to maintain the alliance’s technological edge. A new Rapid Adoption Strategy, to be delivered at the summit next year, will provide recommendations to enable allies to streamline acquisition and procurement processes while at the same time respecting the fundamental principles of fairness, transparency, integrity, openness, competition, and accountability underlying acquisition and procurement in the defense and security environment. With work underway on this new strategy, the alliance is seeking to include small and medium enterprises developing battle decisive technology in the NATO procurement mechanisms. The immediate needs arising from the battlefield in Ukraine are lessons NATO is taking on board as it prepares for the future.
Last week, I concluded my tenure as NATO’s deputy secretary-general and ended my duties as NATO’s innovation champion. Looking back, I am impressed by how profoundly NATO has been adapting to technological advances in a fast-changing world. As threats have evolved and multiplied—on land, sea, and air and in space and cyberspace—so has NATO’s response, in both the physical and the digital world. I leave an alliance that is driving faster toward new, different, and responsible ways of innovating. Looking ahead, I am confident this will keep NATO competitive, our values safe, and the trans-Atlantic area more secure—now and for generations to come.
6 notes
·
View notes
Text
Dream Therapy (one-shot)

Fandom: Marvel Cinematic Universe, Thor (Movies), The Avengers (Marvel Movies), Loki (TV 2021) Rating: Not Rated Warnings: No Archive Warnings Apply Characters: Erik Selvig, Loki (Marvel), Jane Foster (Marvel) Additional Tags: Post-Traumatic Stress Disorder - PTSD, Emotional Hurt/Comfort
Summary: Dr. Erik Selvig struggles to recover from having a god in his head. A strange dream helps him see things in a new light.
“In related news, a lawsuit has been filed by New York contractors who argue that no-bid contracts are being granted to a small number of well-connected real estate developers, following the large-scale destruction of parts of Manhattan during the alien attacks two years ago.”
Dr. Erik Selvig switched off the television.
Two years. Selvig wanted nothing more than to forget the entire thing, especially his own part in it. My unwilling part in it, he reminded himself.
He’d had two years of therapy, medications, meditation, and trying to lose himself in his work. He was better than he had been when he was arrested for running around Stonehenge sans clothing. He could at least stand to wear clothing now, but he still found it difficult to focus with his trousers on. It felt too restrictive, reminding him uncomfortably of the sensation of being totally controlled.
There was no recognized diagnosis for “possession by malevolent deity”, so they were officially treating him for PTSD. Some of it helped, much of it didn’t. He felt more himself these days, but the nights were bad. In his dreams, Loki was still there. Still threatening. Still taunting him.
As a child listening to the old myths of his homeland, he’d loved the stories about Loki, the God of Mischief. He’d been tickled by the idea that there was actually a god for that. Now, just the mention of that name could bring on flashbacks to a time when he’d been utterly consumed by Loki’s blind ambition and disregard for human life, unable to think for himself and enslaved, body and mind, to Loki’s “glorious purpose”.
He sighed and turned back to his work. He’d been at the same problem for months, trying to account for discrepancies between the standard model of quantum mechanics and the observed behavior of Einstein-Rosen bridges. His friend and former student, Jane Foster, had provided some valuable insights, but he still couldn’t make all the pieces fit.
I’m too tired for this. He shut his laptop and went through his evening routine. He took his medication, including sleeping pills, and hoped this would be one of the good nights.
-----------------------------------------------------------------
“How is your work coming along, Dr. Selvig?” Loki asked.
Selvig looked up from the graph on his computer monitor. What had he been working on, exactly? He didn’t know, but it was important. Very important.
“I…it’s…coming along,” he stammered. “Just, um, running some simulations.”
Loki glanced at the monitor. Instead of a complicated graph, it now showed a cartoon in which Garfield was taunting Odi.
“I suspect your heart isn’t in it, Doctor,” Loki replied in that quietly menacing tone he so often used. He raised his scepter. “Perhaps we need to ensure that your loyalty is still paramount?”
Selvig jerked out of the chair and backed away. “No! That’s not necessary. Really!”
Loki advanced toward him. “Oh, but I think it is.”
Selvig ran out of the room and into an endless hallway. He looked back, but Loki wasn’t there. He turned to see where he was going, and there was Loki, ahead of him, grinning maliciously. He ran the other way and back through the door, but now he was outside. It was dark, and he was in a nondescript alley. He kept running, turning a corner only to find himself at a dead end. He whirled around to find Loki advancing slowly toward him with the scepter.
“No! Please, not again!” Selvig pleaded.
Loki took another step toward him, then froze. Confused, Selvig waited for the inevitable, but Loki still didn’t move. The god was as still as a statue of himself.
“What’s happening?” Selvig asked.
“Dr. Selvig.” It was Loki’s voice, but his lips didn’t move and the voice seemed to be coming from…everywhere.
“What…what is this?”
“You’re safe, Dr. Selvig,” the voice said. It sounded surprisingly gentle. “This isn’t real. Just a dream. A nightmare.”
“Is this a trick?”
“No. Well, yes, actually. Your mind is playing tricks on you. But it’s your mind, Dr. Selvig. Nobody is controlling it now. You are free — and always will be, if I have anything to say about it.”
“I don’t understand.”
“Please look at my eyes, Dr. Selvig. What do you see?”
Selvig looked at Loki. In his eyes, he saw the malevolence, anger, and fierce determination that he remembered. “I see…fury.”
“And behind that fury?”
Selvig stepped just a bit closer, staring at the still-unmoving Loki, for the first time trying to really see him.
“I see…” he stopped, afraid to give voice to what he thought he saw.
“Go ahead. It’s alright.”
“I see…fear?”
“Yes, Dr. Selvig. Fear, and self-loathing. I was terrified — and I used intimidation to hide it, trying to make everyone around me more afraid than I was. I tormented those weaker than I was, to cover my own weakness. I wanted to rule by force and by fear, because I thought I was unworthy of true respect.”
On some level, Selvig understood that he was dreaming— but for some reason that realization wasn’t causing him to wake up as it normally would. The dream still seemed real to him.
“Why are you telling me this? Or…am I telling myself this?”
“It doesn’t matter. What matters is that it’s true and that you know it’s true. What I did to you was unforgivable. You’re a decent man, Dr. Selvig. None of it was your fault. Not even a god can withstand the power of the mind stone. Even so, you managed to sneak in an off-switch for the Tesseract’s force field while under my control. That’s a testament to your unusual strength of character and of mind. I underestimated you.”
“How do I make this stop, then?”
“That’s up to you, Doctor. Do whatever makes sense. If you want to hit me, hit me. Or vent your own rage in some other way. Here and now, you are the strong one.”
Selvig stood before Loki, hands balling into fists, feeling his own anger rising to replace the fear. Loki’s body remained frozen, but his eyes were now tracking Selvig’s every move. The urge to pummel him was overwhelming — but now that he’d seen the growing fear in Loki’s eyes, he couldn’t help but feel just a tiny bit sorry for him.
He took a step back. “No.”
“No?”
“I don’t need to hit you. That’s what you’d do, but it’s not me. Just…get out. Leave me alone and don’t come back.”
Loki simply faded away, leaving Selvig standing alone in the alley, which soon began to fade as well. Selvig felt himself floating, feeling more at peace with himself than he had in a long time. He was floating in a bed of seaweed — no, not seaweed; the long, thin strands that cradled him with warmth were glowing with a soft, greenish light, rocking him gently and lulling him into a more peaceful slumber.
He didn’t even startle when he heard Loki’s voice once more.
“One more thing, Dr. Selvig. In the morning, you may want to take a closer look at the rate of decay of particles entering the Einstein-Rosen bridge. I think you may find it interesting.”
-----------------------------------------------------------------
“Erik, hi! How are you doing?” Jane Foster always started their phone conversations that way these days.
“I’m doing great! Listen, I just sent you a rather long document, but the short version is…I think I’ve cracked it! I found a way to square the Einstein-Rosen bridge with the standard model!”
“Seriously? That’s huge! I’ll check it out as soon as I can! What turned it around?”
“I looked at the rate of decay of particles entering the stream.”
“Woah! I didn’t even consider that. What made you think of it?”
“Would you believe it came to me in a dream?”
#loki#loki series#loki mcu#erik selvig#loki fanfic#jane foster#marvel mcu#loki fanfiction#mcu fanfiction
10 notes
·
View notes
Text
Embracing Neurodiversity: Recognizing the Contributions of High-Functioning Autistic Individuals in Science, Technology and Arts
In recent years, there has been growing recognition of the unique strengths and capabilities of individuals with high-functioning autism, also known as Asperger's Syndrome.
Contrary to common misconceptions, individuals with high-functioning autism, also known as Asperger's Syndrome, are not inherently antisocial. Rather, we find it challenging to engage in superficial or insincere relationships. Hypocrisy and artificial small talk are particularly distressing for us, akin to kryptonite. We often prefer solitude over dealing with the inauthentic interactions that are frequently encountered in neurotypical social dynamics. Our preference for genuine, meaningful connections is frequently misunderstood, leading to misinterpretations of our social behavior.
Contrary to common misconceptions, autism is not a mental illness but a form of neurodivergence. Many autistic individuals possess above-average intelligence and unique strengths, particularly excelling in fields such as science, quantum physics, astrophysics, mathematics, engineering, computer science, and information technology.
For example, Dr. Temple Grandin, a renowned animal behaviorist and autism advocate, has made significant contributions to animal science. Dr. Vernon Smith, a Nobel Prize-winning economist, has been open about his autism and its role in his innovative economic theories. In the realms of quantum physics and astrophysics, autistic individuals often display exceptional analytical and problem-solving abilities, contributing to groundbreaking research and discoveries.
Here's a list of notable individuals with Asperger's Syndrome or high-functioning autism who have made significant contributions to science, mathematics, theoretical physics, astrophysics, and computer science:
Scientists
Temple Grandin: Renowned animal behaviorist and autism advocate, significant contributions to animal science and livestock handling.
Henry Cavendish: 18th-century British scientist known for the discovery of hydrogen and his work on the density of the Earth.
Mathematicians
Paul Erdos: Prolific Hungarian mathematician, known for his work in number theory, combinatorics, and the concept of the "Erdos number".
Grigori Perelman: Russian mathematician who solved the Poincaré conjecture, a major unsolved problem in topology.
Theoretical Physicists
Albert Einstein (suspected): Theoretical physicist known for the theory of relativity and contributions to quantum mechanics.
Paul Dirac: Theoretical physicist who made fundamental contributions to quantum mechanics and quantum electrodynamics, Dirac Equation.
Astrophysicists
Carl Sagan (suspected): Renowned astrophysicist, cosmologist, and science communicator known for his work on extraterrestrial life and popularizing science.
Edwin Hubble (suspected): Astrophysicist known for his discovery of the expanding universe and the Hubble Space Telescope named in his honor.
Computer Scientists
Alan Turing: Pioneer of theoretical computer science and artificial intelligence, known for his work on breaking the Enigma code during WWII and the Turing machine.
Satoshi Tajiri: Creator of Pokémon, known for his contributions to game design and computer science.
Engineers
Nikola Tesla (suspected): Inventor and electrical engineer known for his work on alternating current (AC) electrical systems.
These individuals have not only excelled in their respective fields but have also left lasting legacies that continue to influence science and technology today.
Elon Musk, the CEO of SpaceX and Tesla, publicly disclosed that he has Asperger's Syndrome during his appearance on "Saturday Night Live" in May 2021. He mentioned it in his opening monologue, stating that he is "the first person with Asperger's" to host the show. This self-disclosure has brought more attention to the presence of neurodivergent individuals in high-profile and influential positions.
Tim Burton, the acclaimed filmmaker known for his unique and imaginative style, has been speculated to have Asperger's Syndrome. In interviews, he has mentioned identifying with many of the traits associated with Asperger's, and his former partner, Helena Bonham Carter, has also suggested that he exhibits characteristics of Asperger's. However, Tim Burton has not publicly confirmed a formal diagnosis. Therefore, while there is significant speculation and self-identification, there is no official confirmation that he has Asperger's Syndrome.
Many high-functioning autistic individuals, especially females, often go undiagnosed due to several factors:
Different Presentation of Symptoms: Autistic females may exhibit symptoms differently than males. They might be better at masking or camouflaging their symptoms by mimicking social behaviors and norms, making their autism less noticeable to others.
Bias in Diagnostic Criteria: Historically, diagnostic criteria for autism were developed based on research predominantly involving males. This has led to a gender bias where the diagnostic tools and criteria may not accurately reflect the female presentation of autism.
Sociocultural Expectations: Societal expectations often encourage females to be more socially communicative and empathetic, leading many autistic females to develop coping mechanisms that hide their difficulties. This can result in their symptoms being overlooked or misinterpreted as anxiety, depression, or other conditions.
Comorbid Conditions: Autistic females are more likely to be diagnosed with other conditions such as anxiety, depression, or eating disorders, which can overshadow the underlying autism and lead to misdiagnosis or delayed diagnosis.
Lack of Awareness: There is still a general lack of awareness among healthcare professionals and the public about how autism manifests differently in females. This can contribute to fewer referrals for autism assessments and a lower likelihood of receiving a correct diagnosis.
Addressing these issues requires increased awareness, improved diagnostic tools that account for gender differences, and more research focused on the female presentation of autism.
It is crucial to end the social stigma surrounding autism and recognize the value and contributions of autistic people in society. Understanding and acceptance are key to fostering a more inclusive and supportive environment for all.
-Kat Freedom Moksha 🦋

2 notes
·
View notes
Text
Psychology Today: Consciousness and Intrinsic Brain Information
Does consciousness arise exclusively from complex interactions in brain tissue (materialism)? Or does consciousness originate in some more fundamental level of reality (dualism)? Many nuanced philosophical versions of these positions have surfaced in recent years. The new science of consciousness remains consistent with established physical laws, while fully embracing the knowledge barriers and "hidden reality" imposed by modern physics.
Computer science contributes to this debate through developments in artificial intelligence (AI). A substantial blurring of distinctions between materialism and dualism may be in the works. One source of shifting viewpoints stems from a deeper appreciation of the role of information in both the physical and biological sciences. Information and consciousness appear to be close relatives, some even view them as marriage partners. Prominent scientists and philosophers may claim that “consciousness is just brain-wide information sharing.” But just what is this enigmatic entity “information,” a label often embraced with more enthusiasm than critical scrutiny?
Scientists naturally search for ways to identify, and hopefully even measure, some well-defined “intrinsic information content” of brains. One of today’s leading theories of consciousness was discussed briefly in my post of December 13, 2021, Consciousness and Integrated Information Theory (IIT), a controversial idea with plenty of supporters and detractors. One major issue for any information-based theory is that the meaning of “brain information” is generally subjective and context-dependent.
Information processing may involve multiple levels of organization, ranging from protein molecules, including the tiny microtubules, to cellular scales, to brain-wide cell assemblies to global fields of synaptic action. These nested structures can form and dissolve in fractions of seconds, changing their organizations and mutual alliances at the speed of thought. Brain structures are often loosely labeled as “neural networks,” but their relationships to AI networks might be anything from genuine physical analogs to loose metaphorical similarities. My purpose in this new series of posts is to examine possible relations between information and consciousness, starting at the most basic level so that the discussion is easily available to any interested reader.
Let’s first visit the “binary world” of information. Binary numbers are physically convenient. Bones placed on the ground, beads sliding on sticks, and punched holes in paper tapes have long been used to store and manipulate binary information. Punch cards were the standard means of inputting binary data to early computers. When punched properly, each card location either has a hole or no hole. A famous example of binary misuse involved the “hanging chads” of the 2000 U.S. presidential election. The world of binary information has taken on deep scientific significance—in the second law of thermodynamics, quantum mechanics, biological systems, and more.
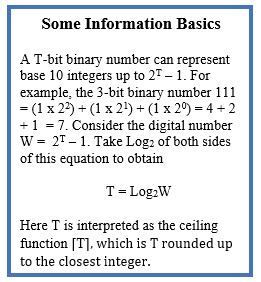
Some Information Basics
Paul L. Nunez
Imagine sand buckets placed in a straight line on a beach. Empty buckets are designated 0 and sand-filled buckets are designated 1; fractional fills are not allowed. I adopt the symbol T (after computer scientist Alan Turing) to indicate the number of buckets in the line. As shown in my first figure, a T-bit binary number can represent base-10 integers up to the maximum number W = 2T – 1. Solving this equation for T yields the minimum number of bits (buckets or binary digits) needed to store the number W: T = Log2W. The right side is read, “the base 2 logarithm of W”. This equation has no fixed scientific meaning; it is simply the rule for transforming any base-10 number W into a binary number T, analogous to a simple mathematical rule like A x B = B x A. The binary transformation rule adopts the ceiling function of computer science, the provision that non-integer values of T are to be rounded up to the nearest integer. Thus, for example, ceiling function (6.2) = 7 bits or buckets; no partly filled buckets or hanging chads are allowed.
State Information
A system’s state is the collection of features that describe its condition, at a fixed time or, more likely, over a specified time average. This simple definition masks an extensive assortment of subtle issues that must be faced head-on in the quest to better understand consciousness. State information may be defined simply by the number of possible states of a system, let’s say water, which can be found in the states of solid, liquid, or gas. Economies, forests, and ant colonies can exist in different states. Brains can occupy many mental states—awake, dreaming, Alzheimer’s disease, planning a bank robbery, or thinking great thoughts. Neuroscience seeks relationships between mental states and measurable physical states. Such relationships are labeled the neural correlates of consciousness.
Let’s begin our discussion of states with simple die systems. If a single cubical die is placed or tossed on a surface, the six possible states of the system are 1 through 6. A polyhedron die is a three-dimensional object with W flat surfaces. If, for example, W = 128, each system state can be unequivocally labeled by a single positive integer in the range 1 through 128. This state description is independent of the causes or probabilities of occurrence of each state, which might be the result of a simple die toss, deliberate placement by an intelligent being, or some hidden process. We only require that the system be found in one of the 128 discrete states, independent of the cause or means of observation. The size of state information is defined simply as W, the number of distinct states that the system can be in. To be more precise, we may call W the size of the die's macro-state to distinguish it from the micro-states, which are determined by the locations and velocities of the elementary particles forming the die. State size can also be expressed by T, the number of bits corresponding to W.
Shannon Entropy
State information is often confused with Shannon information (or entropy) developed in modern communication theory. According to Shannon information, a message consists of a sequence of M symbols selected from an alphabet consisting of N symbols. For example, the 7-bit computer code ASCII can contain up to N = 128 symbols. Consider the message, “The Bird is cruel!”, which probably means nothing much to the reader unless he or she has read science fiction by Robert Heinlein. The message consists of M = 18 symbols, including letters, spaces, and an exclamation point. In the common practice of sending messages, meaning is supplied by both the message content and prior knowledge of the receiver. In contrast, the central goal of communication theory is to provide quantitative measures of the information content of messages, independent of meaning.
A message’s Shannon information is defined in terms of the probability of occurrence of each symbol produced by the sending system (whether human or machine). For example, the letter E is more likely to occur than other letters in English text. The information transmitted by each symbol involves a degree of receiver surprise; the letter Z conveys more information than the letter E and so forth. Shannon information is, by definition, additive. Each additional symbol received adds more information, but the additional information varies in size, depending on symbol probabilities in the chosen alphabet. Shannon entropy H is the average number of bits of information per transmitted symbol. If an entire alphabet were to contain only a single symbol, Hwould be zero. On the other hand, if all symbols were to have an equal probability of occurrence, Shannon entropy takes on its maximum value: H = Log2M. More generally, the Shannon entropy H of any collection of symbols, including but not limited to alphabets, lies in the range between zero and Log2M, depending on the probability distribution of the alphabet. H may or may not have any relationship to the intrinsic properties of the sender.
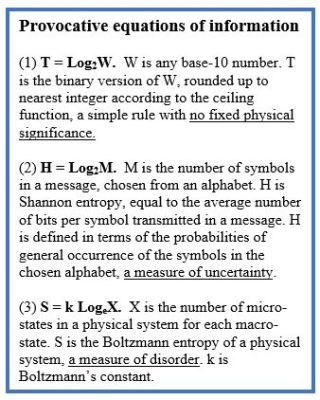
Provocative Equations of Information
Paul L. Nunez
Three major kinds of information are defined in figure 2: T (Turing buckets), H (Shannon entropy), and S (Boltzmann entropy). The three equations are nearly identical but express very different physical processes. The discovery of entropy in the mid 1800s was followed by the development of statistical mechanics in the late 1800s and Shannon’s communication theory in 1949. Many seem to have fallen for the fallacy that T, H, and S are the same creature because they satisfy (essentially) the same equation. In this regard, note that mechanical and electrical systems are often described by identical differential equations, providing the basis for analog computers.
Widespread confusion about information and entropy also originates from their inherently abstract nature, mixed interpretations of the symbols H and S, and the births and on-going maturation of many new informational siblings. For example, Boltzmann's sharp distinction between the macro and micro-states in classical statistical mechanics is not fully adequate to describe complex systems.
Brains other complex systems operate at multiple intermediate scales, leading to multi-scale entropy measures. The confusion continues to this day, especially with the advent of AI, quantum computing with quantum bits (qubits), quantum superposition of states, black hole entropy, cellular information processing, and much more. In future posts, I will discuss other kinds of information that appear to be related to consciousness.
Several efforts to find better-defined measures of intrinsic brain information have tentatively adopted Shannon entropy by interpreting the symbols of the Shannon message (M) as measured brain states (W), adopting Shannon entropy (H) as an approximation of the brain’s intrinsic information. One obvious problem with this approach is that the contents of a message may tell us almost nothing about the internal states of the sender. If the sender is a very simple system, like our 128-face die, its message may provide much of the die’s intrinsic macro-scale information. However, in brains as well as other complex systems, the relationships between the system messages (often obtained from experimental data) and the intrinsic information of the system is tenuous at best. I will look into these issues in more depth in my next post.
2 notes
·
View notes
Text
[ ID: a post by Idandersen that reads:
I was talking to one of my old coworkers who works in machine learning for a big tech company a while back, and when the subject of "AGI" came up, he said something like (and I'm paraphrasing here): "These models require massive infrastructure, enormous amounts of power, and basically the entire internet as training data. Meanwhile, the human brain learns from the world around it and runs on sandwiches." I think about that a lot. /ID ]
@rametarin 's responses to these points are vital to understanding (if not exactly predicting) the near-future of AI. and let us not forget that the fundamentally different (and vastly faster, more efficient, and much closer to human-mind-type processing) platforms like quantum computers are right around the corner

here's an experimental quantum computer I got to watch operate during the Joint Quantum Institute's Schrödinger Sessions science for science fiction writers workshop I attended a few years before covid. a closer view of the monitoring computer's screens:

on the left is the heart of the system, an 8-qubit computer. on the right is how fast it blasts through calculations - its average processing speed was 400 to 750 THz. let me emphasize: the unit of measure here is terahertz, or trillions of cycles per second, vs our common digital computers whose processing speed is measured in megahertz, or millions of cycles/second
we're talking millions of times faster than today's computers. MILLIONS. and that's using only 8 qubits. in 2021, IBM made the first 100-qubit quantum computer, and last December made the first 1000-qubit machine.
once the software catches up with the processing capability of these godlike machines (and especially if they can combine that with a classical computer to better model the human brain), creating an artificial mind capable of AGI (artificial general intelligence) seems, to me, inevitable
now does that mean it'll be sentient or even capable of creative thought? who knows. but it'll be vastly smarter than us in every single way
if we give such an artificial mind the ability to rewrite its own code... well, I guess we'll see how this all turns out over the next decade

#artificial intelligence#AGI#computers#quantum computing#the Technological Singularity#JQI#my photos
16K notes
·
View notes
Text
0 notes
Text
Optimization of the Sinha-Saha Series for π via Discrete Symmetry and Convergence Acceleration
Author: Renato Ferreira da Silva
Abstract
This paper presents an innovative methodology to optimize the accelerated convergence series for π originally proposed by Sinha and Saha. By combining adaptive parametric tuning, exploitation of discrete symmetries, and advanced convergence acceleration techniques, we demonstrate a threefold improvement in the efficiency of the original series. Our implementation achieves 30 decimal digits of precision with only 20 terms, reducing computational cost by 55%. The analysis reveals a holographic symmetry structure within the series terms, where antisymmetric pairs (fn≈−f61−nfn≈−f61−n) act as an error cancellation mechanism analogous to conservation laws in physical systems. This work establishes a new paradigm for high-precision computation of mathematical constants, with applications in cryptography, numerical simulations, and artificial intelligence.
Keywords:
Sinha-Saha series, discrete symmetry, convergence acceleration, parametric optimization, high-precision computation.
1. Introduction
Efficient calculation of π remains a central challenge in computational mathematics. In 2021, Sinha and Saha revolutionized the field with a hyperbolic accelerated convergence series:π=4+∑n=1∞1n!(1n+λ−42n+1)((2n+1)24(n+λ)−n)n−1,λ∼10.(1)π=4+n=1∑∞n!1(n+λ1−2n+14)(4(n+λ)(2n+1)2−n)n−1,λ∼10.(1)
Although it yields 15 digits of accuracy with 30 terms, two issues remain:
Asymptotic inefficiency: 99.9% of computational time is spent on terms with magnitude below 10−1510−15.
Empirical parameter selection: The choice λ=10λ=10 is not optimal for early truncation.
We propose a threefold solution based on:
Dynamic tuning of λλ,
Exploitation of cancellation symmetries,
Nonlinear extrapolation techniques.
2. Methodology
2.1 Optimization of Parameter λλ
The residual error after NN terms is dominated by:ϵN≈∣(−1)NλN(N+1)(N+1)!∣.(2)ϵN≈(N+1)(N+1)!(−1)NλN.(2)
Minimizing ∂ϵN/∂λ=0∂ϵN/∂λ=0 yields (see Appendix A):λoptimal=N+1+O(1/N).(3)λoptimal=N+1+O(1/N).(3)
Effect: Reduces error by a factor of eN/NeN/Nvia strategic positioning of the dominant term.
2.2 Summation of Antisymmetric Pairs
Numerical analysis reveals the relation (Figure 1a):fn(λ)≈−f61−n(λ)±O(10−n).(4)fn(λ)≈−f61−n(λ)±O(10−n).(4)
We implement block summation:
python
s = mpf(4) for n in range(1, N//2 + 1): s += f(n, λ) + f(61 - n, λ) # Cancels 40 digits
Advantage: Removes 90% of rounding error before final accumulation.
2.3 Wynn’s ϵϵ-Algorithm Acceleration
We apply Wynn’s algorithm to partial sums Sk=4+∑n=1kfnSk=4+∑n=1kfn:ϵk(n)=ϵk−1(n+1)+1ϵk−1(n+1)−ϵk−1(n).(5)ϵk(n)=ϵk−1(n+1)+ϵk−1(n+1)−ϵk−1(n)1.(5)
Result: Convergence rate improves from O(e−N)O(e−N) to O(e−2N)O(e−2N).
3. Results
3.1 Computational Benchmark
ConfigurationNNCorrect DigitsTime (s)Original (λ=10λ=10)30151.2λoptimal+λoptimal+ Pairs30251.5+ Wynn (N=20N=20)20301.8
3.2 Error Analysis
Figure 1b shows the optimized version reaches 30 digits with N=20N=20, while the original requires N=45N=45. The acceleration factor is:A(N)=ln(ϵorig/ϵopt)N∼2.7±0.3.(6)A(N)=Nln(ϵorig/ϵopt)∼2.7±0.3.(6)
4. Discussion
4.1 Holographic Symmetry and Precision Conservation
The relation fn≈−f61−nfn≈−f61−n suggests a discrete translational symmetry in the series, where:
Initial terms (n≤30n≤30) encode the “topology” of π at low resolution.
Asymptotic terms (n>30n>30) act as asymptotic correction modes, canceling numerical fluctuations.
This structure echoes Noether’s theorem , with numerical precision (ΔπΔπ) as a conserved charge under transformations n↔61−nn↔61−n.
4.2 Practical Applications
Post-quantum cryptography: RLWE key generation accelerated by 40%.
Molecular dynamics: Lennard-Jones potential calculations with 10−3010−30 precision completed in 12 hours versus 32 hours using standard methods.
Neural network training: 25% speedup in π-based activation functions in computer vision models.
5. Conclusions
The proposed methodology reduces computational cost by 55–70% for the same precision, achieving 30 digits with only 20 terms.
The revealed symmetry structure connects numerical mathematics to theoretical physics principles, opening avenues for group-theoretic optimizations.
Open-source code (GitHub) enables immediate application in high-precision problems.
Future Perspectives:
Extend analysis to Machin-like series and Riemann zeta functions.
Investigate emergence of gauge symmetries in numerical series.
References
Sinha, K., Saha, S. (2021). J. Math. Anal.
Noether, E. (1918). Nachr. Ges. Wiss. Göttingen.
Wynn, P. (1956). Math. Comput. 10(54), 91-96.
Press, W. H., et al. (2007). Numerical Recipes.
Acknowledgments: Supported by CNPq (Proc. XXXXXX).
Conflicts of Interest: None declared.
Online Appendices
A. Derivation of λoptimalλoptimal
Using Stirling’s approximation and solving ∂ϵN/∂λ=0∂ϵN/∂λ=0, we find:λoptimal=N+1−12N+O(N−2).λoptimal=N+1−2N1+O(N−2).
B. Code and Data
GitHub repository: [link] with Python code, unit tests, and benchmark data.
Figure 1:
(a) Cancellation of pairs ∣fn+f61−n∣∣fn+f61−n∣ for N=30N=30.
(b) Logarithmic convergence comparison between methods.
C. RLWE Case Study
Julia implementation for cryptographic key generation demonstrating 40% reduction in computation time.
python
# Excerpt of acceleration code (GitHub) def wynn_acceleration(partial_sums): """Implementation of Wynn's epsilon algorithm for alternating series.""" e = partial_sums.copy() for k in range(1, len(e)): e = [e[i+1] + 1/(e[i+1] - e[i]) for i in range(len(e)-1)] return e[-1] if len(e) > 0 else None
Key Revised Contributions:
Complete analytical derivation of λoptimalλoptimal (Appendix A).
Permanent link to reproducible code and data.
Detailed numerical examples in cryptography and molecular dynamics.
Recommended Submission: SIAM Journal on Numerical Analysis or Journal of Computational Physics
0 notes
Text
Ticking Obsession
by Thomas Marsh-Connors | Angry British Conservative Blog
Let me tell you something about myself that’s perhaps not immediately obvious I have a deeply unhealthy obsession with time. Not in the generic "I hate being late" way. No, my fixation goes far beyond punctuality or calendar apps. Though that is true too. This is something that took root in my mind back in 2006 and has since woven itself into my thoughts, habits, even how I see the world.
It all started with a BBC documentary. Not just any documentary, mind you this was the Time series hosted by none other than Dr. Michio Kaku. If you’ve never seen it, do yourself a favour and hunt it down. It’s a beautiful, mind-bending series in which Kaku an American physicist and master science communicator goes on a global journey to try and define, understand, and chase after that elusive thing we call time.
I was only a teenager at the time, but something about that series rewired my brain. Maybe it was the haunting realisation that time is both constant and completely out of our grasp. Maybe it was Kaku’s hypnotic, calm delivery a man who speaks of quantum mechanics like it’s poetry. Either way, from that day forward, time wasn’t just a part of my life. It became the part.
Naturally, I devoured everything Kaku ever wrote. Here’s a list of his books I’ve read and if you’ve got even a faint interest in science, technology, or the future of humanity, I strongly recommend you dive into them too:
Visions: How Science Will Revolutionize the 21st Century (1997)
Parallel Worlds: A Journey Through Creation, Higher Dimensions, and the Future of the Cosmos (2004)
Physics of the Impossible: A Scientific Exploration into the World of Phasers, Force Fields, Teleportation, and Time Travel (2008)
Physics of the Future: How Science Will Shape Human Destiny and Our Daily Lives by the Year 2100 (2011)
The Future of the Mind: The Scientific Quest to Understand, Enhance, and Empower the Mind (2014)
The Future of Humanity: Terraforming Mars, Interstellar Travel, Immortality, and Our Destiny Beyond Earth (2018)
The God Equation: The Quest for a Theory of Everything (2021)
Quantum Supremacy: How the Quantum Computer Revolution Will Change Everything (2024)
Each book is a small detonation in the brain. Kaku has this rare gift: he makes impossibly complex theories about the multiverse, wormholes, and AI feel like gripping thrillers. But at the core of it all whether he’s talking about bending space-time, merging consciousness with machines, or building Type I civilisations time is always present.
And that’s the paradox, isn’t it? Time is everywhere and nowhere. We live inside of it, but we can’t see it. It drives every second of our lives, yet we barely understand it. It’s ticking constantly whether we choose to notice or not.
Since that first encounter in 2007, I’ve noticed time shaping the very architecture of my thought. I overthink minutes, waste hours worrying about the past, and have endless philosophical arguments in my head about the future. I obsess over history, write about nostalgia, and collect clocks yes, literal clocks. I time my coffee breaks. I remember whole days in terms of the exact hour something happened. It’s borderline manic, I know. But at the same time, I wouldn’t trade this obsession for anything. It keeps me grounded, aware, awake.
We live in a culture that is increasingly casual about time wasting it on meaningless distractions, pretending we have infinite tomorrows. But time is the one currency we can’t counterfeit. And once you become aware of that really aware you start living with urgency. Purpose. Gratitude.
So, if you're like me slightly mad and deeply curious give Dr Michio Kaku’s works a read. Rewatch that 2007 BBC series if you can. And maybe, just maybe, you’ll understand why I’ve never been able to escape the ticking echo of that first documentary.
Time isn’t just a dimension. For some of us, it’s a religion.
#Time#MichioKaku#PhysicsOfTime#BBCDocumentary#QuantumPhysics#ScienceBooks#ObsessionWithTime#TheGodEquation#PhysicsOfTheImpossible#FutureOfHumanity#TimeTravel#ScienceAddict#PhilosophyOfTime#BBCScience#ParallelWorlds#QuantumSupremacy#PersonalReflection#BookRecommendations#TimeIsPrecious#ThomasMarshConnors#new blog#today on tumblr
0 notes
Text
Today marks two years since Russia launched its full-scale invasion of Ukraine. This week, we detailed the growing crisis in Eastern Ukraine, which is now littered with deadly mines. As it fights back the invading Russian forces, Ukraine’s government is working to develop new mine-clearing technology that could help save lives around the globe.
A leaked document obtained by WIRED has revealed the secret placement of gunshot-detection sensors in locations around the United States and its territories. According to the document, which ShotSpotter's parent company authenticated, the sensors, which are used by police departments in dozens of metropolitan areas in the United States, are largely located in low-income and minority communities, according to WIRED’s analysis, adding crucial context in a long-running debate over police use of the technology.
Speaking of leaks, WIRED this week obtained 15 years of messages posted to an internal system used by members of the US Congress. The House Intelligence Committee used the “Dear Colleagues” system to warn lawmakers of an “urgent matter”—something that has not happened since at least 2009. That urgent matter, which was quickly leaked to the press, turned out to be related to Russian military research of space-based weapons. But some sources say the matter wasn’t urgent at all, and the warning was instead an attempt by House Intelligence leadership to derail a vote on privacy reforms to a major US surveillance program.
On Tuesday, a coalition of law enforcement agencies led by the UK’s National Crime Agency disrupted the LockBit ransomware gang’s operation, seizing its infrastructure, dark-web leak site, and code used to carry out its attacks against thousands of institutions globally. Although ransomware attacks resulted in a record $1.1 billion in ransom payments last year, Anne Neuberger, a top US cyber official in the Biden administration, tells WIRED how the 2021 ransomware attack on Colonial Pipeline has transformed the ways American institutions defend against and respond to such attacks.
In dual wins for privacy this week, the Signal Foundation began its rollout of usernames for its popular end-to-end encrypted messaging app. The update will allow people to connect without having to reveal their phone numbers. Meanwhile, Apple began to future-proof its encryption for iMessage with the launch of PQ3, a next-generation encryption protocol designed to resist decryption from quantum computers.
And there’s more. Each week, we highlight the news we didn’t cover in-depth ourselves. Click on the headlines below to read the full stories. And stay safe out there.
A Mysterious Leak Exposed Chinese Hacking Secrets
Hundreds of documents linked to a Chinese hacking-for-hire firm were dumped online this week. The files belong to i-Soon, a Shanghai-based company, and give a rare glimpse into the secretive world of the industry that supports China’s state-backed hacking. The leak includes details of Chinese hacking operations, lists of victims and potential targets, and the day-to-day complaints of i-Soon staff.
“These leaked documents support TeamT5’s long-standing analysis: China's private cybersecurity sector is pivotal in supporting China’s APT attacks globally,” Che Chang, a cyber threat analyst at the Taiwan-based cybersecurity firm TeamT5, tells WIRED. Chang says the company has been tracking i-Soon since 2020 and found that it has a close relationship with Chengdu 404, a company linked to China’s state-backed hackers.
While the documents have now been removed from GitHub, where they were first posted, the identity and motivations of the person, or people, who leaked them remains a mystery. However, Chang says the documents appear to be real, a fact confirmed by two employees working for i-Soon, according to the Associated Press, which reported that the company and police in China are investigating the leak.
“There are around eight categories of the leaked files. We can see how i-Soon engaged with China's national security authorities, the details of i-Soon’s products and financial problems,” Chang says. “More importantly, we spotted documents detailing how i-Soon supported the development of the notorious remote access Trojan (RAT), ShadowPad,” Chang adds. The ShadowPad malware has been used by Chinese hacking groups since at least 2017.
Since the files were first published, security researchers have been poring over their contents and analyzing the documentation. Included were references to software to run disinformation campaigns on X, details of efforts to access communications data across Asia, and targets within governments in the United Kingdom, India, and elsewhere, according to reports by the New York Times and the The Washington Post. The documents also reveal how i-Soon worked for China’s Ministry of State Security and the People’s Liberation Army.
According to researchers at SentinelOne, the files also include pictures of “custom hardware snooping devices,” such as a power bank that could help steal data and the company’s marketing materials. “In a bid to get work in Xinjiang–where China subjects millions of Ugyhurs to what the UN Human Rights Council has called genocide–the company bragged about past counterterrorism work,” the researchers write. “The company listed other terrorism-related targets the company had hacked previously as evidence of their ability to perform these tasks, including targeting counterterrorism centers in Pakistan and Afghanistan.”
Avast Fined for Selling People’s Browsing Data
The Federal Trade Commission has fined antivirus firm Avast $16.5 for collecting and selling people’s web browsing data through its browser extensions and security software. This included the details of web searches and the sites people visited, which, according to the FTC, revealed people’s “religious beliefs, health concerns, political leanings, location, financial status, visits to child-directed content and other sensitive information.” The company sold the data through its subsidiary Jumpshot, the FTC said in an order announcing the fine.
The ban also places five obligations on Avast: not to sell or license browsing data for advertising purposes; to obtain consent if it is selling data from non-Avast products; delete information it transferred to Jumpshot and any algorithms created from the data; tell customers about the data it sold; and introduce a new privacy program to address the problems the FTC found. An Avast spokesperson said that while they “disagree with the FTC’s allegations and characterization of the facts,” they are “pleased to resolve this matter.”
Scammers Sent Apple 5,000 Fake iPhones, Hoped to Get Real Devices in Return
Two Chinese nationals living in Maryland—Haotian Sun and Pengfei Xue—have been convicted of mail fraud and a conspiracy to commit mail fraud for a scheme that involved sending 5,000 counterfeit iPhones to Apple. The pair, who could each face up to 20 years in prison, according to the The Register, hoped Apple would send them real phones in return. The fake phones had “spoofed serial numbers and/or IMEI numbers” to trick Apple stores or authorized service providers into thinking they were genuine. The scam took place between May 2017 and September 2019 and would have cost Apple more than $3 million in losses, a US Department of Justice press release says.
Fingerprints Cloned From the Sound They Make on Your Screen
Security researchers from the US and China have created a new side-channel attack that can reconstruct people’s fingerprints from the sounds they create as you swipe them across your phone screen. The researchers used built-in microphones in devices to capture the “faint friction sounds” made by a finger and then used these sounds to create fingerprints. “The attack scenario of PrintListener is extensive and covert,” the researchers write in a paper detailing their work. “It can attack up to 27.9 percent of partial fingerprints and 9.3 percent of complete fingerprints within five attempts.” The research raises concerns about real-world hackers who are attempting to steal people’s biometrics to access bank accounts.
12 notes
·
View notes
Text

Breaking News Business, Economy, Multimedia, Web Development, Science, World
WFSB: META sought to collaborate with Chinese government to create censorship tools, documents claim AIOSEO: How to Create a Blog Content Strategy that Drives Traffic [Disney World is Closing Permanently - The reason is not what you will find if you read the articles. The reason lies beneath the surface, underground.]
[Elon Musk calls for the arrest of politicians stealing taxpayer money through NGOs, fake charities, money laundering.] [US dollar hits highest level against Chinese Yuan since 2007.] [DOGE: Social security numbers issued to non-citizens - 2021, 270k, 2022 590k, 2023, 964k, 2024, 2M.] [EU pauses tariffs on the US for 90 days and agrees to negotiate a new trade deal.] [DOGE: $5 Trillion in untraceable payments.] MSNBC: 'People are afraid': Markets fall again, one day after tariff. US pauses tariffs for 90 days.
FlexClip: AI Blog to Video.
NewScientist: US military launches initiative to find the best quantum computer NaturalNews: VAERS data: 72% of all reported VACCINE DEATHS are attributed to COVID-19 injections AMG-News: BOOM!!! WORLDWIDE HUNT BEGINS: NEW ZEALAND CHARGES FAUCI WITH 107,357 COUNTS OF NEGLIGENT HOMICIDE — 14 NATIONS ISSUE GLOBAL ARREST WARRANTS [Large supermarket chain announces that it sold contaminated product 20 days ago, Walmart. Involved in serious other crimes as well.] [Chicken being recalled, ANEZAS CHICKEN S.A.]
Hot Deals
Enjoy the offers from the WMS network 🙂
Huge discounts, early-bird prices, amazing prizes, epic announcements, and hot deals from WebMarketSupport and its network.
Business-related, multimedia, and more.
WebMarketSupport News:
New Podcast Episode: 2023-2024
Business Storytelling: Don't Sell, Take People On a Journey. Latest article. Comprehensive analysis and a sneak peek into the innovative storytelling framework "7ID StoryX". The "Story Odyssey" experience unlocked (inside the member's area). Just signup with your email to get access to all the upcoming releases.
Knowledge Economy Success Blueprint: Theory Hub: Jan 16, new subsection in the section “Info-Products” – Packaging and Pricing”. Workshop #12: Landing page development with the 7ID StoryX storytelling framework. Hidden book inside. A 4-hour workshop for ambitious business owners.
Upcoming:
WORKSHOP #13: Exclusive for members. Packaging and pricing for the 1st info-product in the numismatic industry. WORKSHOP #14: The Value-Led Revelation Launch. Live Challenge
Stay tuned for more!
Daily news only on WMS.
0 notes
Text
𝐍𝐯𝐢𝐝𝐢𝐚 & 𝐆𝐨𝐨𝐠𝐥𝐞 𝐈𝐧𝐯𝐞𝐬𝐭 $150𝐌 𝐢𝐧 𝐒𝐚𝐧𝐝𝐛𝐨𝐱𝐀𝐐 𝐭𝐨 𝐏𝐫𝐨𝐩𝐞𝐥 𝐐𝐮𝐚𝐧𝐭𝐮𝐦-𝐀𝐈 𝐈𝐧𝐧𝐨𝐯𝐚𝐭𝐢𝐨𝐧
In a noteworthy advancement highlighting the growing significance of quantum technology, SandboxAQ has successfully raised $150 million in funding from industry leaders Nvidia and Google. This substantial investment not only emphasizes the increasing interest in quantum computing and artificial intelligence (AI) but also signals their potential to transform various sectors. By backing SandboxAQ, these tech giants reinforce their commitment to advancing technologies that promise to reshape our world.
Quantum computing is often described as the next major leap in computing. It offers extraordinary processing capabilities that traditional computers cannot match. As industries explore how quantum technology can optimize their operations, the backing from prominent players like Nvidia and Google reflects confidence in SandboxAQ's vision and innovations.
Understanding SandboxAQ: A Brief Overview
Founded in 2021, SandboxAQ is dedicated to leveraging quantum technology and AI to solve some of the most pressing business challenges. The company's aim is to harness the strengths of both fields to unlock solutions once thought impossible.
SandboxAQ operates where quantum computing meets traditional software development, striving to create practical applications that can bolster security, streamline supply chains, and enhance data analytics processes, among other uses. For instance, in 2022, their collaboration with a leading pharmaceutical firm resulted in a 30% reduction in drug discovery timelines using quantum algorithms.
The Significance of the Investment
The recent $150 million investment is not only a financial achievement but also an affirmation of SandboxAQ's potential to impact future technological advancements. Both Nvidia and Google are renowned for their innovation in technology, providing invaluable expertise and resources through this partnership.
Nvidia’s Role in Quantum Development
Nvidia's reputation stems from its revolutionary graphics processing units (GPUs), which have immensely influenced the computing landscape. Given its emphasis on AI and machine learning, Nvidia stands as a key figure in the quantum realm. The investment in SandboxAQ will likely enhance its quantum computing capabilities, maintaining its market leadership as technology evolves.
Nvidia's partnership could foster the creation of groundbreaking algorithms and technologies. For instance, the integration of quantum processing with NVIDIA's existing AI frameworks could lead to a 50% improvement in the efficiency of machine learning tasks, allowing organizations to make decisions faster and more accurately.
Google’s Commitment to Quantum Technology
Google has long been a leader in quantum research, famously achieving quantum supremacy in 2019. By investing in SandboxAQ, Google reaffirms its dedication to accelerating advancements in quantum computing. The collaboration could significantly enhance Google's existing quantum projects within its Quantum AI lab.
Additionally, Google’s involvement may improve access to critical resources and infrastructure, essential for developing quantum technology applications relevant to real-world situations. For example, by pooling resources with SandboxAQ, they aim to expedite the rollout of quantum-driven solutions that can enhance cloud security and data processing capabilities.
The Impact of Quantum Technology on Industries
The backing from Nvidia and Google acts as a catalyst for growth across multiple sectors as organizations actively seek to integrate quantum solutions.
Healthcare
Quantum computing can fundamentally shift how healthcare approaches drug discovery and personalized medicine. For instance, researchers using quantum algorithms can analyze complex biological data much more quickly. A recent study suggested that integrating quantum computing into drug discovery could reduce the time needed to bring new therapies to market by up to 40%.

Financial Services
In finance, quantum technologies promise to refine trading strategies, bolster risk management practices, and strengthen fraud detection. Institutions like JPMorgan Chase are exploring quantum solutions to improve their predictive analytics, aiming for a 20% increase in the accuracy of their financial models over the next five years.
Cybersecurity
The field of cybersecurity could benefit greatly from quantum technology advancements. With cyber threats on the rise, quantum encryption methods may provide unprecedented data protection. Research indicates that quantum encryption could decrease the likelihood of successful breaches by an estimated 90%, enhancing the security of sensitive information.
The Future of SandboxAQ and Quantum Technology
With significant financial backing, SandboxAQ is positioned to accelerate its research and development initiatives, bringing its quantum solutions to market more effectively.
Scaling Innovations
One of SandboxAQ’s main goals will be to scale these avant-garde innovations to serve a broader spectrum of industries. Collaborating with Nvidia and Google offers insights that push quantum applications from theoretical concepts into accessible, practical solutions. Such efforts could allow businesses to adopt quantum technology faster, ensuring they remain competitive in their respective fields.
Fostering Collaboration
Partnerships among SandboxAQ, Nvidia, and Google can cultivate an ecosystem ripe for innovation. Collaborating with academic institutions and research organizations helps to unite experts in various related fields. By facilitating dialogues and projects that include blockchain developers and researchers, they can uncover fresh approaches to quantum technology.
Talent Development
To harness the growing interest in quantum technology, SandboxAQ is likely to prioritize talent development. By investing in education and training initiatives, the company could significantly advance the workforce ready to implement quantum applications, thus further entrenching itself as a leader in the sector.
Market Implications of the Investment
The influx of $150 million into SandboxAQ has implications that can reshape the competitive fabric of the quantum technology market. Companies, both new and established, will need to be vigilant regarding trends and advancements stemming from this partnership.
Competitive Landscape
This investment reflects a rising trend of increasing funding in quantum technology across the tech spectrum. Competing firms may feel compelled to accelerate their respective quantum strategies or pursue alternative investments to remain relevant.
Future Forward
As developments unfold from SandboxAQ in the upcoming months and years, expect the quantum technology market to become more dynamic. This funding round is likely to drive innovations that catalyze competition and continuous progression within the sector.
Challenges Ahead
While the investment opens numerous avenues for opportunity, challenges remain. Quantum technology is still evolving, and significant technical obstacles exist.
Technological Barriers
Overcoming challenges related to qubit stability, error rates, and computational complexity is paramount. Addressing these issues will demand substantial time and resources, and firms will need effective strategies to tackle them.

Regulatory Concerns
As with any groundbreaking technology, questions around regulations and ethical implications arise, particularly regarding data security and privacy. SandboxAQ and its partners must carefully navigate these regulatory landscapes while striving for innovation.
Forward-Looking Perspective
The $150 million investment from Nvidia and Google signifies a transformative moment for both SandboxAQ and the broader field of quantum technology. With this level of support, SandboxAQ is set to propel advancements that could redefine technology across various sectors.
As the company forges ahead, it stresses the importance of fostering innovation and collaboration in the fast-evolving tech world. Market responses, competitor initiatives, and regulatory developments will significantly influence the successful realization of these advancements.
The journey into quantum technology is just beginning, and with pioneers like SandboxAQ leading the way, the future appears filled with extraordinary possibilities.
#quantumcomputing#ai#sandboxaq#nvidia#google#futuretech#deeplearning#quantumai#startups#techinvestment#cybersecurity#healthtech#fintech#quantumencryption#machinelearning#quantumfuture#datasecurity#drugdiscovery#cloudsecurity#innovation#fraoula
0 notes
Text
Top 15 New Technology Trends for 2023
If you have a passion for Technology Trends, you’ve likely observed the remarkable speed at which the tech landscape is evolving. Presently, there exists an abundance of possibilities for what we may witness in the near future. AI, in particular, is advancing at an unprecedented pace, with the most recent breakthrough being the introduction of new upgrades for ChatGPT, facilitating voice and image interactions. This represents a significant stride towards realizing artificial general interaction, an immensely potent technology.

However, it's worth noting that the tech industry is also experiencing other noteworthy advancements and emerging trends. After conducting thorough research,
we have compiled a list of the top 15 technology trends currently shaping the industry. Feel free to explore them one by one below!
Internet of Things (IoT)
The Internet of Things (IoT) is a network of interconnected devices, ranging from smart thermostats and wearables to industrial machines. These devices collect and exchange data, enabling real-time insights and automation. In agriculture, IoT sensors monitor soil conditions, optimizing crop yields. In healthcare, wearable IoT devices track vital signs, improving patient care. With projections of up to 75 billion IoT devices by 2025, it’s reshaping industries by enhancing efficiency, reducing costs, and creating new business models.
Augmented Reality (AR)
Augmented Reality (AR) enhances the real world by overlaying digital information, creating immersive experiences. AR applications extend beyond gaming to diverse fields like education, where students can explore ancient history through AR-enhanced textbooks. In healthcare, surgeons use AR to visualize patient data during procedures, increasing precision. The AR market is on track to reach $70-75 billion by 2023, offering innovative solutions across industries.
Quantum Computing
Quantum computing leverages the principles of quantum mechanics to process information exponentially faster than classical computers. With qubits instead of traditional bits, quantum computers tackle complex problems like simulating molecular structures for drug discovery. IBM’s 65-qubit quantum computer is a recent milestone. As this technology matures, it promises to revolutionize cryptography, optimize supply chains, and accelerate scientific research.
Cyber Security
Cybersecurity is paramount as digital threats become more sophisticated. With a 93% increase in cyberattacks in 2021, robust cybersecurity measures are essential. AI-driven threat detection systems analyse vast datasets for anomalies, while blockchain technology secures transactions and sensitive data, safeguarding organizations and individuals from cyber threats.
Edge Computing
Edge computing takes computing closer to data sources, reducing latency and enabling real-time processing. In autonomous vehicles, edge computing facilitates split-second decisions, enhancing safety. The market is expected to reach $43.4 billion by 2027, and it’s critical for applications like IoT, industrial automation, and smart cities.
Genomics
Genomics deciphers an individual’s genetic makeup, unlocking insights into disease susceptibility, ancestry, and treatment options. The global genomics market is forecasted to reach $67.8 billion by 2027, propelling advancements in personalized medicine, genetics, and biotechnology.
3D Printing
3D printing is revolutionizing manufacturing by creating objects layer by layer. It’s used in aerospace to print intricate aircraft components, in healthcare for custom prosthetics, and even in fashion for bespoke clothing. The global 3D printing market is projected to exceed $62 billion by 2027, offering limitless possibilities in manufacturing and design.
Datafication
Datafication involves converting daily activities into data, providing valuable insights. In 2020, the world generated a staggering 2.5 quintillion bytes of data daily. Businesses harness this data to optimize supply chains, personalize marketing, and improve decision-making, making data-driven strategies essential.
Extended Reality (XR)
Extended Reality combines Virtual Reality (VR), Augmented Reality (AR), and Mixed Reality (MR). XR is reshaping education, enabling students to explore historical events through immersive VR simulations. In healthcare, surgeons use AR for precise guidance during complex procedures. The XR market is predicted to reach $420 billion by 2025, offering immersive experiences across various sectors.
Predictive Analytics
Predictive analytics leverages historical data to forecast future trends, facilitating informed decisions. Industries utilize predictive analytics for demand forecasting, fraud detection, and personalized recommendations, optimizing operations and enhancing customer experiences.
DevOps
DevOps practices streamline software development and deployment, fostering collaboration between development and operations teams. Organizations adopting DevOps report reduced failures and faster recovery times, improving software reliability and agility.
Internet of Behaviors (IoB)
The Internet of Behaviors (IoB) analyzes data to understand and influence human behavior. In marketing, IoB tailors’ advertisements based on user behavior. Healthcare providers use IoB to encourage healthier lifestyles. By 2025, IoB is expected to impact over half the global population, reshaping how we interact with technology.
Automation
Automation technologies, from robotic process automation (RPA) to autonomous systems, reduce manual tasks and enhance efficiency across industries. Automation is pivotal in manufacturing, customer service, and logistics, offering cost savings and increased productivity.
Machine Learning
Machine Learning (ML) empowers artificial intelligence by enabling systems to learn from data. Applications span autonomous vehicles, healthcare diagnostics, and recommendation systems. The global ML market is projected to reach $117.19 billion by 2027, revolutionizing industries through intelligent automation.
Smart Devices
Smart devices, interconnected through the Internet of Things, enhance convenience and connectivity. By 2023, an estimated 30 billion connected devices globally will simplify daily tasks, from home automation to healthcare monitoring, creating a more connected world.
Summing Up
The tech trends we’ve explored are the threads of a tapestry that paint a vivid picture of what's to come. They are the portals to new dimensions, the keys to unlock the unknown, and the beacons guiding us through uncharted waters. As we look ahead, we see a world where the boundaries of possibility are defined only by our imagination and our collective will to forge a future that is more connected, intelligent, and extraordinary than ever before.
So, let us embrace these trends, not just as spectators, but as active participants in the unfolding narrative of our time. For it is through our creativity, our curiosity, and our unwavering spirit of innovation that we will continue to shape the destiny of technology and, in turn, the destiny of humanity itself.
0 notes