#remote procedure invocation
Explore tagged Tumblr posts
Video
youtube
Remote Procedure Invocation Design Pattern for Microservices Explained w... Full Video Link https://youtu.be/5T0aibUYS3gHello friends, new #video on #remoteprocedureinvocation #rpc #rpi #messaging #communication #designpattern for #microservices #tutorial for #developer #programmers with #examples are published on #codeonedigest #youtube channel. @java #java #aws #awscloud @awscloud @AWSCloudIndia #salesforce #Cloud #CloudComputing @YouTube #youtube #azure #msazure #codeonedigest @codeonedigest #microservices #microservicespatterns #microservices #microservicespatternsforjavaapplications #microservicesdesignpatterns #whataremicroservices #remoteprocedureinvocationpattern #remoteprocedureinvocation #remotemethodinvocation #remoteprocedurecall #remoteprocedurecallindistributedsystem #remoteprocedurecallincomputernetwork #remoteprocedurecallprotocol #remoteprocedurecallexplained #remoteprocedurecallexample #microservicedesignpatterns #rpcpattern #rpc
#youtube#remote procedure call#rpc#microservice design pattern#microservice pattern#remote procedure invocation
1 note
·
View note
Text
Angarak Dosh Puja in Ujjain – Benefits, Puja Vidhi and Booking
What is Angarak Dosh in Astrology – Understanding the Powerful Mars-Rahu Conjunction in Kundli
Angarak Dosh is a serious astrological condition that occurs when Mars (Mangal) and Rahu are placed together in the same house in a person’s birth chart. This combination leads to excessive aggression, impulsiveness, accidents, legal troubles, and mental instability. It is known for creating destructive energy that affects career, marriage, relationships, and overall peace of mind.

To mitigate the harmful impact of this dosh, Angarak Dosh Nivaran Puja in Ujjain is one of the most powerful and recommended Vedic remedies.
Signs and Symptoms of Angarak Dosh – How to Know if You Need the Puja
If a person has the following signs in their life, they might be suffering from Angarak Dosh:
Sudden anger, uncontrollable temper, or aggression
Frequent involvement in disputes or legal issues
Unexplained accidents or physical injuries
Lack of peace at home or toxic relationships
Fear of fire, weapons, or blood
Trouble concentrating, insomnia, or mental stress
Health problems related to blood, muscles, or bones
Delay or disturbances in marriage or childbirth
Why Ujjain is the Best Place to Perform Angarak Dosh Puja – The Spiritual Power of Mahakaleshwar Temple
Ujjain, located on the banks of the Shipra River, is a divine center for planetary pujas. It is home to the Mahakaleshwar Jyotirlinga, one of the most powerful temples for eradicating doshas like Angarak, Mangal Dosh, Kaal Sarp Dosh, etc.
The energetic atmosphere, spiritual vibrations, and experienced Pandits in Ujjain ensure that the puja is done as per ancient Vedic guidelines, bringing quick relief and blessings to the devotee.
Benefits of Performing Angarak Dosh Nivaran Puja in Ujjain – Real Results for Health, Mind, and Relationships
The puja is designed to pacify Mars and Rahu, balance the fire element in the body, and restore mental harmony. Here are the key benefits:
Neutralizes the malefic energy of Mars-Rahu conjunction
Brings peace, patience, and emotional balance
Removes the chances of accidents and legal troubles
Improves marital life and family relationships
Supports mental stability and spiritual clarity
Enhances success in career, land/property deals, and government-related matters
Protects against negative energies, black magic, and evil eye
Step-by-Step Puja Vidhi for Angarak Dosh Nivaran in Ujjain – Traditional Procedure by Vedic Pandits
The Angarak Dosh Puja is a sacred and powerful Vedic ritual that takes about 2.5 to 3 hours. The steps involved are:
Ganesh Puja and Sankalp – Invocation of Lord Ganesha and taking oath (Sankalp) for the ritual
Kalash Sthapana – Establishing divine presence through holy water
Mangal and Rahu Shanti Jaap – Chanting of beej mantras for Mars and Rahu
Navgraha Puja – Worship of all nine planets for overall balance
Havan (Homam) – Fire offerings to purify surroundings and soul
Brahmin Daan and Dakshina – Donation and food offerings to learned priests
Prasad Distribution – Receiving the divine blessings and sacred materials
Ideal Muhurat Dates for Angarak Dosh Puja in Ujjain – Best Time to Perform the Remedy in 2025
Choosing the right time enhances the power of the puja. Here are auspicious times for Angarak Dosh Puja in 2025:
Mangalwar (Tuesday) – The day of Mars
Angarak Yoga Days – When Mars and Rahu are conjunct in transit
Amavasya & Purnima – High-energy days for spiritual rituals
During Chaitra, Shravan, or Kartik Months – Spiritually potent Vedic periods
During Mars Mahadasha or Antardasha in the native's chart
A professional astrologer or priest can help find the perfect muhurat based on the person’s birth chart.
How to Book Angarak Dosh Puja Online in Ujjain – A Simple and Effective Way to Perform the Puja Remotely
Now, with online puja booking services, you can perform the Angarak Dosh Puja in Ujjain even if you live outside the city or abroad. Here's how:
Visit a Trusted Online Puja Website or Pandit’s Portal
Choose Angarak Dosh Puja Service – Check package details and rituals included
Enter Sankalp Details – Name, Gotra, Date of Birth, and Puja Intent
Select Puja Date – Based on availability or astrologer guidance
Make Online Payment – Use secure gateways (UPI, card, etc.)
Receive Puja Confirmation – Get details via email or WhatsApp
Watch Live or Receive Recording – Participate remotely and get photos/videos
Receive Prasad and Puja Report at Home
Why Choose Pandit Atul Agnihotri Ji in Ujjain for Angarak Dosh Puja – Authenticity, Experience, and Results
If you’re looking for a genuine and experienced Vedic Pandit in Ujjain, Pandit Atul Agnihotri Ji is highly respected and sought after for planetary dosh pujas, especially Angarak Dosh.
Why choose him?
More than 20 years of expertise in Rahu-Mars dosh pujas
Follows ancient Shastras and authentic Vedic rituals
Offers both in-person and online Sankalp options
Transparent process with fixed pricing and proper documentation
Devotees from India and abroad trust his services for consistent results
Book Angarak Dosh Puja in Ujjain and Eliminate the Cause of Struggles and Conflict
If you or someone in your family is facing ongoing anger issues, unexpected injuries, legal conflicts, or unstable relationships, Angarak Dosh could be the hidden reason. Performing the puja in Ujjain offers divine protection, karmic healing, and peace of mind.
Book your puja today and step into a calmer, balanced, and prosperous future.
Call Pandit ji : +91 9644451903
0 notes
Text
"Your Coding Journey Starts Here: Discover What Java Programming Can Do"
Java programming, a dynamic and influential language, has the potential to transform your career in the world of technology. With its versatility and widespread adoption, Java offers an array of opportunities for professionals looking to enhance their skills and advance their careers. At ACTE Technologies, we recognize the immense potential of Java, and through our comprehensive courses, we aim to equip you with the knowledge and expertise needed to excel in this dynamic field. Let's explore the vast horizons that Java programming can open for you and how ACTE Technologies can be your gateway to success.

Here is the list of things what does Java do:
Mobile App Development:
Java serves as the primary language for creating Android mobile applications. It is extensively utilized in the development of a wide range of Android apps. Android Studio stands out as the most popular Integrated Development Environment (IDE) for building Android applications. Some well-known mobile apps developed using Java include Netflix, Google Earth, Twitter, and Uber.
Game Development:
Java is a versatile language capable of game development. It supports powerful 3D engines, making it possible to create beloved games like Saints Row 2, Spiral Knights, Minecraft, Asphalt 6, and RuneScape. Additionally, Java accommodates jMonkeyEngine and the Dalvik Virtual Machine for crafting both 2D and 3D Android games.
Cloud Applications:
Java is well-suited for developing cloud applications, which provide on-demand access to computing resources like servers, storage, databases, and networking. Developers leverage Java to create services like Logging as a Service (LaaS), Platform as a Service (PaaS), and Software as a Service (SaaS). These cloud applications facilitate remote development and data sharing for companies.
Web Applications:
Java is a popular choice for crafting high-quality web-based applications. It offers a secure and straightforward coding environment that appeals to web developers. Java supports technologies such as JavaServer Pages (JSP), Struts, and Servlets, enabling the development of a wide variety of web applications. Prominent web-based applications like Spotify, Netflix, LinkedIn, Amazon, and Uber are built using Java.
Scientific Applications:
Java is an excellent choice for developing scientific applications due to its speed, portability, and security features. Notably, MATLAB utilizes Java in both its back-end and front-end to fulfill the requirements of scientific applications.
Java Distributed Applications:
Java plays a pivotal role in building distributed applications, which run on multiple computers within the same network. Popular Java APIs like CORBA (Common Object Request Broker Architecture) and RMI (Remote Procedure Invocation) are used to create distributed applications. Jini, or Java Intelligent Networking Infrastructure, is employed to provide, discover, and register distributed services. JavaSpaces, an integral part of Jini, supports object persistence, distribution, and migration in distributed environments.
Desktop Applications:
Java provides an extensive set of libraries and tools for developing desktop applications that run on personal computers or laptops. Key advantages of Java desktop applications include platform independence, a rich user interface, and enhanced security.
Enterprise Applications:
Enterprise applications are designed to support the operations of large organizations such as corporations, governments, and non-profits. Java is widely adopted for developing enterprise applications due to its robustness, scalability, and platform independence. Key benefits of using Java for enterprise applications include scalability, reliability, and seamless integration.

Trading Applications:
Java is a preferred choice for building trading applications, with Murex being a notable example. Many financial institutions rely on Murex for their trading operations.
In summary, Java's versatility and robustness make it suitable for a wide range of application domains, from mobile apps and games to cloud-based solutions, web applications, scientific software, distributed systems, desktop applications, enterprise software, and trading platforms.
Java programming is a gateway to a world of possibilities, and ACTE Technologies is your trusted partner in navigating this exciting journey. With our industry-focused training, experienced instructors, and hands-on learning experiences, you can harness the full potential of Java and position yourself for success in today's competitive tech landscape. Whether you aspire to become a mobile app developer, a game designer, or an enterprise software architect, mastering Java Course at ACTE Technologies will empower you to realize your career goals and make a significant impact in the world of technology. Embrace the power of Java, and let ACTE Technologies be your guide toward a brighter, more rewarding future.
0 notes
Text
Let’s outline a magical university
For reasons almost humorous enough to turn them into an anecdote, I drafted the hierarchy (faculties, departments) of a magic university. This is from a fictional nation whose capital city, Melphi, houses a whole bunch of “academies” almost as if someone was trying to build a science cluster there. I grouped together “schools of magic” I thought harmonized due to their primary purpose/fields of study/historical roots. I had to do some redefining here and there.
All fields of study are classified by the prevailing type of application (mathematics vs. engineering–everyone needs number reasoning but while some are dtf once they see abstract problems others need a practical application to get off). This is why the Ministry of Defense co-chairs some faculties and departments in other academies instead of creating a ‘military-only’-department-copy in their own “Academy of Military Science”.
National Academy of Thaumatology(lit.: miracle-working)
The National Academy of Technology is the leading institution of thaumaturgic research and education. Graduates of this academy may refer to themselves as Mages and are granted a license/diploma; ordinary thaumaturges are generally referred to as wizards and witches.
Any mage who heads the NAT is automatically granted the title of an Arch-Mage. The Arch-Mage isn’t necessarily the strongest mage but, ideally, the most competent; the position is elected and only temporarily held.
The NAT harbours six separate faculties and a total of 45 departments. The faculties are headed by Deans, who are appointed by the Arch-Mage. A Dean, in turn, may designate any one of a department’s professors as the head of said department.
Faculty of Divination and Scrying
Members seek to extract information from every comprehensible (and incomprehensible source–this is the fun bit) source. This faculty has six departments.
Department of Precise Prophecies
Analysis of incoming prophecies; may suggest methods to improve the accuracy of prophetic recitals; study of the effects of prophecies on oracles; replication and study of prophecy induced stupor
Department of Percolative Clairvoyance
Remote viewing by means of astral projection; minimisation of projected astral bodies; breaching of thaumic barriers or other wards designed to hinder the clairvoyants
Department of Cryptomancy
Development and breaching of thaumic encryptions; think schematics and counter-spells
Department of Runic Studies
Almost cryptomancy if you don’t know the language; extraction of information from ancient runes; study of antique symbology and foreign circuitry & schematics
Department of Sensory Appropriation
Utilisation of other beings’ senses; research towards improving stability and enabling two-way communication between species
Department of Knowledge Impartment and Remote Transmissions
Development of communication techniques with and without astral projections; research into holograms; cooperation with cryptomancers; research into wordless communication (mental projections)
Faculty of Alchemy and Artificery
Members seek to alter matter and augment objects, turning them into artifacts. This faculty focuses on historical as well as modern applications of alchemy, such as transmutation of mind and matter on one hand and the animation of matter on the other. This faculty has nine departments. They can be roughly divided into those that deal with naturally animate matter and those who don’t
Department of Transmutation
Study of chemical (and later nuclear) alteration of matter; applications include refining and enrichment of a substance
Department of Alteration
Study of inanimate morphing; study of micro-alterations; research into perfect replications
Department of Animation
Imbuing inanimate matter with a resemblance of life; research into prolonging the effects of animation; study of artificial sentience
Department of Infusion
Infusion of inanimate matter and potions with spells, typically one-time use; research into materials that retain spells with little to no deterioration over a prolonged period of time/extreme environmental conditions
Department of Artifact Augmentation
Creation of artifacts from normal objects; augmentation of mechanical systems with thaumic elements; creation of objects with entirely thaumic systems; research into artifact circuitry and schematics
Department of Polymorphing
Transmutation of animate matter by means of direct (cast) or indirect (potions) thaumaturgy
Department of Vivisthetics
Development of animate limb replacements from animate and inanimate matter such as wood or metal
Department of Tissue Replication
Study of tissue matrices and surmounting the resistance of animate matter against exterior thaumaturgy
Department of Soul-Patching
Study of the soul anatomy; study of soul transferals and creation; investigation of industrial applications for minor souls; (and probably a lot more)
Faculty of Invocation, Abjuration, and Obviation
Members seek to summon, convene, and bargain with (more or less) sentient entities. Mages also specialise in banishing unwelcome guests or those who have overstayed their welcome. Conveniently, the thaumic barriers used to contain the assault of an irritated celestial can also be used in the industry, where transparent materials with toughness beyond glass and a price below diamond are required. The Ministry of Defense is, unsurprisingly, also rather fond of research into these barriers. Summoned beasts are also studied and may be harvested for alchemic ingredients, deployment in the industry or by the military. This faculty has eight departments.
Department of Celestial, Infernal, and Concomittant Deitical Interrogation
Summoning of celestials, infernals, auxiliary deities and sprites with the goal of extracting information; dangerous and tedious interrogations may result in death by exhaustion, boredom, or smiting
Department of Contemporary Circuitry
Study of summoning circles; summoning circle optimisation; testing the limits of summoning circles; naturally, this department is also part of the Faculty of Divination and Scrying
Department of Lost Rites
Similar to the Department of Runic Studies, this department studies past summoning rituals and catalogues them; finding backdoors to summoning-resistant creatures
Department of Necromancy
Summoning of beings, most commonly ghosts but also DEATH, from DEATH’s realm, souls that have passed on can no longer be summoned; cooperate with the Faculty of Divination and Scrying to extract information from the deceased; work with the Department of Animation to supply (ambivalently willing) souls as a raw material to work spells
Department of Vexatious Relegation
Research of banishing techniques to get rid of pesky metaphysical beings from the poltergeist to the infernal arch-demon; cooperate with the Department for Thaumic Barriers and the Department for Contemporary Circuitry to create wards against unwanted guests (this makes them a great target for prospective clairvoyants practicing for their exams)
Department of Varmint Studies and Husbandry
Study and taming of summoned beasts (not necessarily but commonly) from other planes of existence; harvest of alchemic ingredients; study of industrial and military applications
Department of Thaumic Barriers
The creation of (invisible) thaumic barriers that prevent the passage of physical and/or metaphysical objects; barrier type research such as solid, liquid, and gaseous barriers e.g. walls and dust barriers
Department of Binding and Immobilisation
Emergency procedures when summoning circles are damaged; police and military applications; storage of summoned entities in pocket dimensions
Faculty of Innovational Thaumaturgy
Contains members from all other faculties, who wouldn’t stop pestering their HoD with ‘what-if’-questions. Everyone else is only here to supervise those mages and make sure nothing goes (too) wrong. And when their nurslings aren’t ending the world, they study thaumic contamination, land reclamation, and recycling. Prisoners get sentence reductions, if they willingly participate in these experiments. This faculty has ten departments.
Department of Asset Recovery and Recycling
Study of decontamination methods for thaumically irradiated areas and objects such as testing grounds, battlefields, destroyed cities or spell-gone-wrongs
Department of Leigh-Line-Surveying
Study and development of thaumic models to understand how thaumaturgy works; detection and mapping of currents; study of inexplicable thaumic flux
Department of Hazard Handling
Responsible for setting up safety precautions during experiments and containing them, if they go awry; investigation of technical failures during experiments; creation of guidelines when handling certain spells; study and research into safety-ensuring spells
Department of Peculiar Entropy Phenomena
Study and attempted replication of matter that inexplicably weathers, repairs itself or remains ‘locked in time’
Department of Experimental Divination and Scrying
Testing the limits of individual departments; possession of another sentient entity; sending and receiving fake prophecies; field testing of knowledge impartment and transmission
Department of Experimental Alchemy and Artificery
Field testing of potions and artifacts; early nuclear transmutation
Department of Experimental Invocation, Abjuration, and Obviation
Field testing of new circuits and summoning rituals, banishments, and thaumic barrier prototypes
Department of Experimental Evocation
Field testing of new evocation spells
Department of Experimental Convalescence
Field testing of new biothaumaturgy spells (possibly on prisoners, who may or may not be on death row) and convalescence spells
Department of Experimental Illusion
Field testing of new illusion spells; oneiromancers practicing dream-walking in environments with a high thaumic density
Faculty of Evocation
Evokers study the extraction and subsequent harnessing of energy from their surroundings. This faculty has seven departments and a dean with a military background.
Department of Stifling and Sonancy
Study of wave propagation in various media; industry applications like geological mapping and locating mineral deposits; shockwaves for the military, sonar for the navy and oceanographers research; study of interference phenomena and counter-spells
Department of Dynamic Forfeiture
Study of methods to extract kinetic energy from or imbue systems with kinetic energy; industry applications like mechanical/thaumic systems (from artificery); military applications like impedance of movement of projectiles or vehicles (or the opposite)
Department of Torrid Reciprocation
Extraction of thermal energy (particle vibrations) from the surroundings; allows for interesting thermodynamic machines like heat pumps, lots of industry applications in heating and cooling; military applications only in the farthest sense that you can extract energy from your surroundings and thereby freeze people or cause machine components to deform
Department of Cardinal Schisms and Amalgamation
Energy from fusion and fission of atoms; extraction of chemical energy from molecules; industry needs include powering steam machines and smelting; military application can be the uncontrolled fusion or fission of a substance like hydrogen or uranium (to name two familiar ones)
Department of Ray Apprehension
Capture of electromagnetic radiation; applications similar to most of the above except commonly only viable during daytime
Department of Elementary Allurement
Extraction of energy from the movement of charged particles and vice versa; the electricity folks
Department of Locomotion
Exertion of forces on objects to make them move; excludes teleportation (summoning)
Faculty of Illusion
Illusionists seek to replicate real environments and associated dynamic objects to the extent that the illusion becomes indistinguishable from the real world. The ability to replicate distant objects in real time makes them an attractive to communication service providers. This faculty has five departments.
Department of Oneiromancy
Study of dreams from a prophetic or self-reflective point of view; study of mental health through dreams; study of dream implanting; study of (literal) dream-walking
Department of Optics
Study of reflective thaumic barriers used to redirect light; study of civilian applications such communication services; study of enhancements for mechanical optics; competition to clairvoyants
Department of Static Imitation
Study of interfaces and displays for artifacts; study of static civilian applications such as billboards or advertisement screens; artistic applications like in stage shows, a world with nothing moving in it
Department of Dynamic Imitation
Study into the perfect illusory replication of real-world dynamic objects such as fireworks or holograms, also includes military stealth
Department of Phantasmagoria (’cause I couldn’t call it the mind-fuck dpt.)
Heavily military and medical, mages seek to penetrate a victim’s psyche and create a false world inside their head, effectively incapacitating them, also used in palliative treatment of the sick and mental health institutions
I’ll post a visual at a later date, showing cross-over departments and the influence I think the Ministry of Defense has on the research conducted. Supplementary feedback to this post is appreciated.
13 notes
·
View notes
Link
JAVA was developed by Sun Microsystems Inc in 1991,later acquired by Oracle Corporation. It was developed by James Gosling and Patrick Naughton. It is a simple programming language. Writing, compiling and debugging a program is easy in java. It helps to create modular programs and reusable code.
Java Virtual Machine (JVM)
This is generally referred as JVM. Before, we have a tendency to discuss regarding JVM lets see the phases of program execution. Phases square measure as follows:
we have a tendency to write the program, then we have a tendency to compile the program and eventually we have a tendency to run the program.
1) Writing of the program is after all done by java software engineer such as you and Pine Tree State.
2) Compilation of program is done by javac compiler, javac is the primary java compiler included in java development kit (JDK). It takes java program as input and generates java bytecode as output.
3) In third part, JVM executes the bytecode generated by compiler. This is called program run phase. So, currently that we have a tendency to understand that the first operate of JVM is to execute the bytecode created by compiler. Each OS has totally different JVM, however the output they produce after execution of bytecode is same across all operating systems. That is why we have a tendency to decision java as platform freelance language.
Bytecode
As mentioned above, javac compiler of JDK compiles the java ASCII text file into bytecode in order that it may be dead by JVM. The bytecode is saved during a .class file by the compiler.
Java Development Kit(JDK)
While explaining JVM and bytecode, I actually have used the term JDK. Let’s discuss about it. As the name suggests this can be complete java development kit that features JRE (Java Runtime Environment), compilers and numerous tools like JavaDoc, Java programme etc. In order to make, compile and run Java program you'd would like JDK put in on your laptop.
Java Runtime Environment(JRE)
JRE may be a part of JDK which suggests that JDK includes JRE. When you have JRE put in on your system, able to} run a java program but you won’t be able to compile it. JRE includes JVM, browser plugins and applets support. When you solely got to run a java program on your laptop, you'd solely would like JRE.
Main Features of JAVA
Java is a platform independent language
Compiler(javac) converts source code (.java file) to the byte code(.class file). As mentioned above, JVM executes the bytecode produced by compiler. This computer memory unit code will run on any platform like Windows, Linux, Mac OS etc. Which means a program that's compiled on windows will run on Linux and vice-versa. Each software system has totally different JVM, but the output they turn out when execution of bytecode is same across all operating systems. That is why we tend to decision java as platform freelance language.
Java is an Object Oriented language
Object minded programming may be a means of organizing programs as assortment of objects, every of that represents associate degree instance of a category.
4 main concepts of Object Oriented programming are:
Abstraction
Encapsulation
Inheritance
Polymorphism
Simple
Java is taken into account mutually of easy language as a result of it doesn't have complicated options like Operator overloading, Multiple inheritance, pointers and express memory allocation.
Robust Language
Robust means reliable. Java programming language is developed in a way that puts a lot of emphasis on early checking for possible errors, that’s why java compiler is able to detect errors that don't seem to be straightforward to discover in alternative programming languages. The main options of java that produces it sturdy are pickup, Exception Handling and memory allocation.
Secure
We don’t have pointers and we cannot access out of bound arrays (you get ArrayIndexOutOfBoundsException if you try to do so) in java. That’s why several security flaws like stack corruption or buffer overflow is impossible to exploit in Java.
Java is distributed
Using java artificial language we are able to produce distributed applications.
RMI(Remote Method Invocation) and EJB(Enterprise Java Beans) are used for creating distributed applications in java.
In straightforward words: The java programs are often distributed on over one systems that are connected to every different victimization net affiliation. Objects on one JVM (java virtual machine) will execute procedures on a distant JVM.
Multithreading
Java supports multithreading. Multithreading could be a Java feature that enables multiprogramming of two or additional components of a program for max exercise of processor.
Portable
As mentioned higher than, java code that's written on one machine will run on another machine.The platform independent bytecode can be carried to any platform for execution that makes java code portable.
Academy of IT & Executive Education provides best java training in Trivandrum
1 note
·
View note
Text
So again: if these omniscient accounts of the latter-day scourge of global populism aren’t actually about populism, what are they about? Well, they’re doing what neoliberal intellectual work has been doing for the better part of a generation now—making the logic of market-driven policy appear to be a species of the highest political wisdom. This mission is at the heart of Mounk’s puzzlingly influential book, which tilts again and again at straw-man avatars of the “populist” menace in order to confirm what he and his cohort of think-tank apparatchiks knew all along: that the expert-administered dictates of the neoliberal market order are not simply the optimal arrangements for global capitalist enterprise; they are also, and far more urgently, the last, best hope for rescuing our fragile, Trump-battered democratic norms from the populist abyss. It’s right there in the book’s subtitle: Why Our Freedom Is in Danger and How to Save It.
However, on closer inspection, the task of saving our freedom isn’t a call to the barricades, the town hall, or the picket line; it is, rather, a closely modulated accord among postideological elites to keep all currents of opinion within their appointed lines. This pronounced and insular vision of elite governance for its own sake explains why Mounk and other self-appointed prophets of the gathering populist storm consistently fail to highlight what is in fact a central, and deeply anti-populist, bulwark of conservative rule over the past generation—the activist right’s militant embrace of state-based voter suppression, which has no remote historical affinity with a movement devoted to the expansion of the franchise via direct election of senators, legislation by initiative, and preliminary challenges to racist disenfranchisement of postbellum black voters. Astonishingly, Mounk devotes a section of his book to bemoaning the decline of judicial review in Western democracies without coming to grips with the substantive impact of the Roberts Court’s irresponsible gutting of the enforcement of the Voting Rights Act, and the staggeringly counter-empirical Trumpist obsession with the threat of race-based “voter fraud.” Then again, such first-order assaults on basic democratic participation at the grassroots level have no clear place in a tract devoted to what Mounk is pleased to call “the miraculous transubstantiation between elite control and popular appeal.”
It gets worse. Highlighting the penchant of strongman demagogues to translate power relations into conspiracy theories, Mounk surreally argues that the best rejoinder to such unhinged public reveries is “to re-establish traditional forms of good government.” And the way to do this, it turns out, is to bow once more before the well-worn governmental shibboleths of the neoliberal information age:
“To regain the trust of the population once Trump leaves office, politicians will have to stick to the truth in their campaigns; avoid the perception of a conflict of interest; and be transparent about their dealings with lobbyists at home and government officials abroad. Politicians and journalists in countries where norms have not eroded to the same degree should, meanwhile, double down with renewed zeal: As the American case shows, such norms can erode frighteningly quickly—and with terrible consequences.
After Trump won the 2016 election, Barack and Michelle Obama were mocked in some quarters for having insisted throughout the campaign that “when they go low, we go high.” It is, of course, easy to mock a team that continues to play by the rules when the opposing team turns up with goons in tow and clubs in their hands. But for anyone who wishes to keep playing the game, it’s not clear what the alternative is: if both sides take up arms, its nature changes irrevocably. Unlikely as it might seem at the moment, the only realistic solution to the crisis in government accountability (and most likely the larger crisis in democratic norms) is therefore a negotiated settlement in which both sides agree to disarm.”
It’s hard to conjure a better rhetorical example of high-church proceduralism in the neoliberal age. There’s the notion that the excesses of Trumpism can be effectively dispelled by the self-policing moral rehabilitation of our leadership caste, as opposed to any expansion of political-economic freedoms that an aggrieved citizenry might demand on their own behalf. There’s the fanciful notion that Democrats blew the 2016 election by “going high” and adopting a morally superior campaign rhetoric, when in point of fact the Clinton campaign devoted its final general election push to a blizzard of harsh negative attacks on Trump—in part because even at that late date, Clinton couldn’t give a clear account of why she wanted to be president beyond it being the next logical entry on her resume. (Anyone who thinks “going high” is second nature to Hillary Clinton in campaign mode clearly slumbered through the 2008 primary season, when she and her surrogates mounted an unrelentingly vicious counteroffensive against her upstart opponent Obama.) Finally, there’s the broader depiction of political discourse as a formalist byplay of norms upheld by force of liberal leadership—norms that are at once the bedrock foundation of responsible public inquiry and yet somehow also prone to instantaneous collapse once a billionaire pseudo-populist and his retinue of goons start whaling away on them.
This ritualized fetish of norms and rules is but the extension of the habits of mind exemplified by Davos-style neoliberalism into the sphere of political morality. The notion that representative democracy best expresses itself in formalist modes of compromise and mutual disarmament is the mode of agreement best disposed to bargaining parties whose own social power is assured and ratified well beforehand. The formalist dream of government exclusively by rules and norms is a minuet among privileged arbiters of polite conduct who can afford the luxury of believing they are “going high” by deigning to enter the public sphere in the first place. All that’s missing here is a ritual call for greater “civility” among the surly ranks of Trump resisters—but Mounk completed his manuscript before that procedural plaint became de rigueur among right-thinking liberals.
Keep in mind, too, that Mounk lays out his proceduralist playbook of elite deference as the best response to the plague of conspiracy thinking on the “populist” left and right. Why, if you simply increase your transparency, the reasoning goes, your virtues will become self-evident—as though conspiracy-mongering has overtaken our common world only because we’ve all needed a firmer pedagogic hand at our social-media cursors. Among other things, this sunnily didactic view of truthful-leadership-by-example overlooks the Obama administration’s commitments to official secrecy, leak prosecutions, and extralegal drone assaults of all description, despite its frequent rhetorical invocations of its own exemplary commitments to “transparency” and plain-dealing. It’s hard to see, in other words, how assurances of improved probity coming from our leadership class would be greeted with anything other than a chorus of disbelieving guffaws—or why they should be.
The Populist Morass
3 notes
·
View notes
Text
MuleSoft integration pattern models
Learn Mulesoft Today the use of MuleSoft integration is to extract, transform, and use data. It is at the top of the mind. MuleSoft integration patterns can help streamline the MuleSoft integration process. Besides, the flows are crucial to understanding.
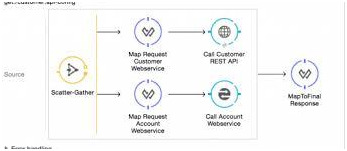
Models for MuleSoft integration
It is one or more separate sources to proceed. In other words, how the MuleSoft integration will happen must decide. This refers to also the type of incorporation.
Invocation by remote procedure
MuleSoft integration space, Remote Procedure Invocation (RPI) was the go-to way. In this method, a provider would allow an external mechanism. This is to make requests into a closed program. The external caller has the requirements for making the request. Then an understanding of what the answer will be, but using a black-box approach, all the logic takes place. RPI is the mechanism used in this case to conduct an operation against the target device.
Find an application to treat financial transactions. The vendor can offer an API to allow transactions to post from an external source. This is before the popularity of RESTful APIs. Using RPI, it introduces API.
The developer will write a program to collect the information he needs. Then use RPI to connect to the application. In reply, the results of the RPI/API requests pack. Then the calling application processes the information.
The Database Shared
The MuleSoft integration style of the shared database leverages a database. This is for synchronization between two or more apps. As a result, a link to share the database containing the information. Thus, it will incorporate will maintain in the application.
Using an INSERT statement to a staging table in the database, for example. This might activate a store procedure that would conduct business logic. Then update attributes elsewhere in the database for other applications. Besides, you can use the same mutual MuleSoft integration of the database.
The messaging
With service SOA implementations, the messaging MuleSoft integration style began to gain popularity. This is by using an enterprise service bus (ESB) as the basis for the message itself.
In the example of a financial transaction, the custom application can place a message. Then demand the posting of a certain transaction on the ESB. To manage any remaining tasks, this device submits the message. Then relies on the style of messaging MuleSoft integration.
On the financial system hand, depending on the essence of the message, the message is on the bus causes. Then the event that absorbs the message and takes the necessary action. The financial system recognizes the mission that needs the message queue used. Then metadata inside the message itself.
The financial system may place a new message on the bus when complete. Then you can consume the original system. In this case, adding to the original request for auditor validation purpose. Thus, you could relate to specific transaction information.
The Concept of Messages
The MuleSoft integration Courier is primarily based on the principle of messaging. This is not unlike other technology-driven solutions, since something you use. This is to relay crucial information to the solution at hand. The courier is often the payload that transfers to a POST request or from a GET request. This is by using RESTful APIs as an example.
The Messaging Systems
A major advantage of messaging is both systems do not need asynchronous messages. This is to be online and accessible at the same time. One system may position a message with an ESB. Thus, you can immediately process hours later by another system or on a schedule. Either way, without affecting the other, treat all situations.
The message system employs channels (or queues) to coordinate the information that needs to be integrated and categorize it. For example, the messages will use different channels for each message form if the source system wants to communicate with a financial system and an HR system.
Routing of Message
In more complex MuleSoft integration cases, the concept of message routing is also applied, where a message might be needed to route through several channels before reaching the target destination.
In this case, a message router will aid, allowing messages to be sent to a dedicated component that analyses the message and uses business logic to decide where the message is routed based on the message content itself.
The source system would simply need to post a transaction in the financial transaction example. The source system does not have a detailed understanding of which system manages which transactions if the company maintains several financial systems. The message router would become the source of the message and would have the necessary skills to send the message to the correct channel.
Message routing goes much further and can use a large array of patterns that support the process of routing. Such widespread developments include:
Message Filter:
Allows messages to be filtered within the message based on attributes.
Scatter-Gather:
Enables synchronous messages to simultaneously be sent to various sources.
Message Aggregator:
Enables the sorting and pushing of messages from different sources into a single resulting message, perhaps to process the scatter-gather results.
Transforming Message
Connecting various systems also makes it clear that a given response does not fit the source system's intended or preferred response. The transformation of messages is a process that can perform the necessary data transfer between the two systems.
Using the example of a financial system, the source system may wish to submit data in JSON, but XML is required by the financial system. The incoming JSON data will be processed and converted(i.e. transformed) into XML using message translation to prepare for processing by a SOAP web Server. This is essentially the pattern of normalizer MuleSoft integration in use.
Some proven patterns of message transformation include:
● Content Enricher:
Enables the alteration of metadata in order to fulfill the target system's expectations.
● Claim Check:
Momentarily streamlines the message to delete metadata that is not required but available for later processing at that point in time.
● Content Filter:
Fully delete metadata from the post, more permanently than the above-noted argument check approach.
Control of Systems
The management of MuleSoft integration is the center of the solution, building on the MuleSoft integration styles and the flow and delivery of a given message.
Bus Control
The management tier within the MuleSoft integration system is the control bus pattern. The control bus uses, as one would imagine, the same principles applied by the MuleSoft integration method.
If the administration layer needs information for the user to send to the system administrator, the message data captured by the MuleSoft integration system is used to report the status of any known problems found.
Store Message
Any level of historical knowledge or metrics is often needed to operate any system. The difficulty of looking at the messages with metrics without disturbing the transient existence of the messages themselves. By sending a duplicate copy of the message to the message store, the message store pattern satisfies this need. The requisite metrics can be retained and transferred to the control bus for processing and reporting until a copy of the message is stored inside the message store.
Proxy Smart
Usually, messages flow to a fixed output channel. There are instances, however, in which a part needs to post reply messages back to a channel specified in the original request. The smart proxy pattern can be utilized when this need arises.
In order to capture the return address specified by the sender, the smart proxy integrates logic to intercept messages. Upon completion of processing, the smart proxy replaces the destination of the fixed output channel with the address captured when the original request was sent.
Conclusion
Having an understanding of MuleSoft integration types, message principles, and system management trends will help direct developers of MuleSoft integration to employ activities that translate irrespective of the industry through any MuleSoft integration project. In doing so, when additional resources help and sustain current MuleSoft integration programs, the ramp-up period would be decreased. You can learn more about the models through MuleSoft online training.
For more information About this course Please go through this link
Mulesoft Online Training
Contact Information
USA: +1 7327039066
INDIA: +91 8885448788, 9550102466
Email: [email protected]
Mulesoft Online Training at Onlineitguru in Hyderabad, India, and Chennai. Enroll for the course for a free demo today from live industry experts with live projects. For more information Contact us@ +91 9550102466.
#Mulesoft Training#Mulesoft Online Training#Learn Mulesoft#Mule Training#Mulesoft Self Learning#Mulesoft Online Training in Hyderabad#Mulesoft Online Course#Learn Mulesoft Online#Mulesoft Training in Hyderabad#Mulesoft Training Hyderabad#Mulesoft Course Online
0 notes
Text
What happens if President Trump contracts COVID-19
Register at https://mignation.com The Only Social Network for Migrants. #Immigration, #Migration, #Mignation ---
New Post has been published on http://khalilhumam.com/what-happens-if-president-trump-contracts-covid-19/
What happens if President Trump contracts COVID-19

By John Hudak What would happen if President Trump contracted COVID-19? This is more than a hypothetical question. Cases are surging throughout the United States. Leaders at home and abroad have come down with the virus. Miami Mayor Francis Suarez and Atlanta Mayor Keisha Lance Bottoms have both been diagnosed with COVID-19, as have UK Prime Minister Boris Johnson and Brazilian President Jair Bolsonaro. Several members of the White House staff as well as numerous Secret Service agents have also been stricken. Given the president’s near-refusal to wear protective gear, unwillingness to socially distance, and commitment to holding in-person rallies, it’s possible that the president himself could contract the illness. Presidential illness is not something commonly discussed, but procedures are in place to deal with a variety of scenarios that protect the president, the integrity of the office, and the continuity of government. A positive test for the president A positive COVID-19 test for the president, in itself, is not a cause for emergency action. Millions of people around the world have contracted the disease and have been asymptomatic or mildly symptomatic. The president would likely be able to continue his everyday activities and manage the office either undisturbed or with mild challenges. A presidential diagnosis would create some challenges for those around him. The need for 24-hour Secret Service protection could put agents at risk for contracting it. But given modern technology, the president could quarantine and have remote or sufficiently distanced contact from most, if not all, aides, including the individual(s) who would be involved in the presidential daily brief. There would need to be other precautions taken, even if the president were to be asymptomatic. First, those in the line of succession would need to be protected. It would be important to keep Vice President Pence, Speaker Pelosi, Senator Grassley (President Pro Tempore), and members of the cabinet isolated from the president. It would be especially important to ensure that the vice president have limited contact with individuals generally to reduce his chances of contracting the virus as well. Second, it would be important for the president to continue to communicate with the American public, especially if he is mildly symptomatic or asymptomatic. Seeing the president on camera can restore faith in his wellness, calm nervous Americans, stabilize stock markets (that would surely see a dip in the event of a positive test), and project to the world that the president remains well enough to execute the office. We’ve experienced something like this before. In 1919, President Woodrow Wilson suffered a serious stroke, and his wife kept even his closest advisers from seeing the president, likely out of fear that they would find him incapacitated and thus throwing the nation into a serious leadership crisis. Such a scenario (hiding the president’s condition) would not be possible today, but an extended absence of a president—especially during a pandemic—would raise serious questions and become a destabilizing force in politics, the economy, and the public. Contingencies for a seriously ill president Although the president has access to some of the best and most immediate health care in the world, his age and obesity put him into higher risk categories for more serious symptoms for COVID-19. Patient experiences range dramatically, but some of the most serious courses of treatment include use of a ventilator. When a patient is put on a ventilator, the patient is non-verbal because of the insertion of the tube through the vocal cords and they are given some level of sedation, ranging from minimal to deep sedation. During this time, a patient’s cognitive abilities would at least be affected or completely absent. More intensive sedation therapies, including drug-induced paralysis, can be used in the treatment of severe COVID-19 complications. In an unfortunate scenario in which the president were to contract COVID-19 and need therapies such as a ventilator and/or the use of other therapies that would impair his cognitive abilities and/or abilities to communicate, there are a few procedures in place to deal with that situation. If the president is given notice that he is to be administered therapies that will impair his ability to perform the duties of office—for functional reasons, cognitive reasons, or both—under Section 3 of the 25th Amendment to the Constitution, the president can transmit to the House and Senate “his written declaration that he is unable to discharge the powers and duties of his office.” The invocation of Section 3 of the 25th Amendment has happened multiple times. President Reagan did so in 1985 and President George W. Bush did so twice in 2002 and 2007. Each time was for medical procedures in which anesthesia or heavy sedation was used. President Clinton likely should have invoked Section 3 during a 1997 knee surgery, but opted not to, claiming he was never put under general anesthesia. When Section 3 is invoked, the vice president becomes “acting president” until the president notifies the House and Senate that he is able to perform his duties once again. In the event that the president were sick, his condition declined rapidly, and he was unable to invoke Section 3 of the 25th Amendment, Section 4 provides a solution to such a crisis. Under Section 4, the vice president and a majority of the cabinet can send notice to the House and Senate “that the President is unable to discharge the powers and duties of his office.” And as in the case of invoking Section 3, the vice president will serve as acting president. Once a president recovers, he can transmit that to the House and Senate, and he will re-take the powers unless the vice president and a majority of the cabinet tell Congress that the president remains incapacitated—at which point Congress would vote on incapacity. The latter is the intended use of Section 4 of the 25th Amendment. While some of the president’s opponents have fantastically called for the vice president and cabinet to declare the president incapacitated based on disagreements with his behaviors, amateur diagnoses of non-specific medical issues, or dissatisfaction with his temperament, that should not diminish the importance of the provisions of Section 4. There can be real scenarios in which the president’s medical condition suddenly creates an incapacity, and in that situation, the country will have an individual who is able to execute the full powers of the office of president—in that case, Acting President Mike Pence. While presidential incapacity would be a serious national situation, the government would be able to function in a largely uninterrupted way until the president is recovered.
The author thanks Geoffrey Frattalone, RN for his assistance with this piece.








0 notes
Link
This is an update from a 2017 Post. Lightning Web Components run on the client-side, in a single page, where they are created and destroyed as needed, alongside other components that work on the same data. We will discuss how these characteristics impact performance, and review a list of best practices to optimize the performance of your Lightning Components. Our original Performance Best Practices blog post from 2017 focused on Aura components. A lot can change in three years, and in this updated post we’ll be focusing on Lightning Web Components. If you are just starting out with Lightning Web Components, consider completing the Build Lightning Web Components Trail, watching some of the topic specific videos in the Lightning Web Components Video Gallery and checking out some of our sample apps in the Sample Gallery before diving deeper. The list of performance best practices discussed in this document includes: Lightning Web Components vs Aura components Data retrieval Data caching Component instantiation Conditional rendering Lists Events Third-party JavaScript libraries and custom style sheets Base Lightning components Image optimization Component lifecycle rendering and reflow Developer settings and tools Lightning Web Components vs Aura components Lightning Web Components (LWC) align closely with modern web standards, which makes them more efficient for developers to build with and for browsers to render. The LWC bundle has a simpler structure than that of Aura components, and the development of LWC feels much more like other modern JavaScript frameworks. This can increase developer productivity. And not only is it easier for developers to build with LWC, but they can also increase the performance of applications when compared to Aura components. In one case study, Aura components migrated to LWC showed anywhere between a 20-60% decrease in Experience Page Time (EPT). So when it comes to making a choice between LWC and Aura, LWC is usually the recommended option. While there are still some cases where Aura components are required, we’re working hard to advance the LWC framework so that this will no longer be the case. More information: Read Case Study: DreamHouse Gains Speed by Switching to LWC. Take the Trailhead module Lightning Web Components for Aura Developers. Review the Migrate Aura Components to Lightning Web Components developer guide. Data retrieval A component with no data is not a very useful component. With Lightning Web Components, you have various options available to you when retrieving data from the server. To optimize all of your server round-trips, keep these things in mind: Use the Lightning Data Service or cache data when ever possible (see Data caching). Before making a call to the server, make sure there’s no other option to obtain the data. When appropriate, consider passing data between components using attributes, events, or methods rather than retrieving the same data in different components. If multiple components on a given page retrieve the same data, consider creating a service component that has no UI elements and can query data once so that it can pass data on to other components. When making a call to the server, limit the fields and rows of the result set: Only SELECT the fields you need. Set a LIMIT on the query, don’t return huge numbers of rows at once. Implement pagination when queries may have large results sets. Lazy load occasionally accessed data. Don’t preload data that the user may never need. For example, put least accessed components in a secondary tab that the user may not click. Don’t make a call to the server to filter or sort data you already have at the client-side. JavaScript Arrays have built in functions to do things like sort, filter and find values. As opposed to using Apex, leverage the Lightning Data Service and UI API to not only retrieve records, but also retrieve list views, metadata and picklist values. When using the getRecord wire service (part of the UI API) in LWC, avoid calling the full layout when you only need a few fields. Potentially hundreds of fields: @wire(getRecord, { recordId: '$recordId', layoutTypes: ['Full'] }) One field: @wire(getRecord, { recordId: '$recordId', fields: ‘Contact.Name’ }) More information: Read the Modularizing Code in Lightning Components blog post to learn more about service components. Review the pagination section from the Designing Lightning Pages for Scale blog post. Application composition is a powerful way to build apps by assembling self-contained components. However, without proper planning, the autonomous nature of the components you assemble can have an adverse impact on performance. For example, if all the components you build make their own isolated calls to the server to retrieve data they need, you’ll probably end up with lots of redundant server calls. This can dramatically impact performance. Client-side data caching can solve this problem by sharing data among components. This can significantly reduce the number of server round-trips, and improve the performance of your Lightning Web Components. The Lightning Component framework has two built-in mechanisms for client-side caching. These are Lightning Data Service and cacheable Apex methods. If neither of these work for your purposes, you can also implement a custom caching solution. Lightning Data Service Lightning Data Service provides a managed record approach: you’re not responsible for writing data access logic, so no Apex here. It also handles security for you by checking the accessibility of records and fields. The framework is responsible for managing records; this includes fetching them from the server when requested the first time, storing them in a highly efficient client cache, sharing them between all components that request them, and sending changes to the server and invalidated cache entries when dependent Salesforce data changes. Lightning Data Service can also handle progressive loading by allowing developers to specify which fields to load. When using the getRecord wire adapter, be sure to only request the needed data since it does allow developers to return entire page layouts (which may include unneeded data). This is also true for the getRecordUi wire adapter which can return full layout information, metadata, and data for a record or records. When leveraging either of these Lightning Data Service wire adapters, be sure to only request the data you need and nothing more. If another component subsequently requires additional fields, these fields are loaded transparently and added to the record in the cache. Unlike storable actions that can cache any type of response returned by an Apex method, Lightning Data Service caches a discrete Salesforce sObject. The Lightning Data Service also improves user interface consistency: when a component updates a record, all the other components using that record are notified and in most cases refreshed automatically. More information: Review the Lightning Data Service section of the Lightning Web Components Dev Guide. Review the Get Record Data and Understand the Wire Service section of the Lightning Web Components Dev Guide to learn more about the wire service. Watch the Wire an Apex Method to a Property video in our LWC Video Gallery. Review the getRecord and getRecordUi wire adaptors. Check out the following components in the DreamHouseApp.io (repo) to see the Lightning Data Service in action: mapCard, propertySummary, mortgageCalculator. Cacheable Apex Methods A Cacheable Apex Method is a server action whose response is stored in the client cache so that subsequent requests for the same server method with the same set of arguments can be accessed from that cache instead of the server. Cacheable Apex Methods enable you to access data using a traditional Remote Procedure Call (RPC) approach: You implement some logic in Apex that you expose as a remotely invocable method. Cacheable Apex Methods enable you to cache virtually anything, whatever the server method call returns. This could be a record or collection of records, a composite object, a custom data structure, data returned by a callout to a third-party service, and so on. The general guideline is to cache (mark as storable) any action that is idempotent and non-mutating. Creating a Cacheable Apex Method is easy. Simply annotate your Apex methods with @AuraEnabled(cacheable=true) @AuraEnabled(cacheable=true) public static someObject getIceCream(string flavor) { // your code here } More information: Review the Call Apex Methods section of the Lightning Web Components Dev Guide. See the Enable Client-Side Caching in the Call Apex Methods section of the Lightning Web Components Dev Guide. Check out the DreamHouse sample application for examples of storable actions in: similarProperties, propertyCarousel, propertyTileList. Component instantiation Showing every available piece of data and every available tool on the screen just in case the user may need it is generally not considered a good UX practice. It can also significantly impact the performance of your application. Lightning Components added to a page layout are instantiated when the page is loaded, contributing to the overall loading time of the page. Today’s interactive design guidelines favor progressive disclosure. “Progressive disclosure is an interaction design technique often used in human computer interaction to help maintain the focus of a user’s attention by reducing clutter, confusion, and cognitive workload. This improves usability by presenting only the minimum data required for the task at hand” (Wikipedia). Put another way, “progressive disclosure defers advanced or rarely used features to a secondary screen, making applications easier to learn and less error-prone” (Jakob Nielsen). In Lightning Experience, it’s easy to implement progressive disclosure and defer data or features that aren’t essential to the task at hand. There are several approaches to defer component creation, let’s take a look at two of them in detail: Lazy instantiation (sometimes referred to as lazy loading) and conditional rendering. Lazy instantiation in Lightning Experience Lightning App Builders can implement progressive disclosure declaratively by placing components within specific areas in the Lightning Experience where they are lazily instantiated. These areas include: Standard tabs and accordion components allow information to be hidden and only loaded when the user selects that tab or accordion. Lightning Component Actions or Quick Actions allow components to be loaded only when the user clicks on a button. Utility Bar can be added to any app and also includes buttons that can load components when the user clicks on them. Lazy instantiation in your own components Leverage the set of tab components like and that support lazy instantiation by default. Leverage the set of accordion compoments like and that support lazy instantiation by default. Note: TabSet and the App Builder tabs component are lazy-loaded however the tabs within the Lightning Console are loaded as workspaces and sub-tabs are not lazy-loaded. Conditional rendering There are three methods to enable the conditional rendering of your Lightning Web Components: Dynamic component visibility Using if:true|false Toggling visibility using CSS The first method is declarative and built directly into App Builder. Dynamic component visibility can control when a component appears on a Lightning page by adding filter conditions and logic to its properties in the Lightning App Builder. For example, you can construct a filter that causes a rich text component on an opportunity page to display when the opportunity’s amount is greater than or equal to $1 million. The second method allows developers to conditionally render DOM elements using if:true|false to lazily instantiate parts of the UI: In this case, if “something” = true, the first tag and all its children are created, while the second tag and all its children, are not rendered. This would swap when the “something” expression changes to false. In this situation, the first tag would be destroyed and the second would be rendered. The third method leverages CSS styles to toggle visibility and can be implemented using the following template and JavaScript. Template: JavaScript: get className(){ return isError ? 'slds-show': 'slds-hide'; } The component and all of its children are created and rendered up front, but are hidden from the user until the JavaScript is run. Keep in mind that this method does create the component upfront so there’s no performance gain on page load like there is with methods one and two. However, when the JavaScript is run the component will show immediately to the user without the need to initialize or render. The general guidance here is to use these methods in the order presented. The first option should be the declarative option discussed in method one, though this is only available on components configured for Lightning App Builder. Method two’s if:true|false approach should be your second option and works with all components. Both methods help your pages load faster initially by deferring the creation and rendering of the component or enclosed element tree until the condition is fulfilled. The third method may be useful when developers want to preload a component and then show it in the UI when the condition is fulfilled. More information: Read more about Dynamic Lightning Pages. Review the Render DOM Elements Conditionally section of the developer guide. In the DreamHouse sample application see the propertyCarousel component which uses if:true|false to component render different elements based on if the property has images or not. Lists Lists should be created using either for:each or iterator. The difference between these is that iterator has first and last properties that let you apply special behaviors to the first and last items in an array. When creating custom list components, don’t support the creation of an infinite number of list items. This can severely hamper performance, especially in large orgs with lots of records. Either provide a pagination mechanism, or virtualize the list (reuse and rehydrate a limited number of list item components). More information: Review the Render lists section of the Lightning Web Components Dev Guide to learn more about for:each or iterator. In the DreamHouse sample application check out propertyTileList component that uses for:each in combination with the paginator component to allow for interacting with long lists. Events Leveraging events is a great way to communicate between components and even allows developers to listen for events within the DOM as Lightning Web Components dispatch standard DOM events. Components can also create and dispatch custom events. Use events to communicate up the component containment hierarchy. Event listeners can be attached declaratively or programmatically using addEventListener(). Keep the following in mind when leveraging events and event handlers: Minimize the number of event handlers to only those absolutely required. Each handler requires overhead and if too many are created it can slow the performance of your app. Be sure to understand event propagation of parent-child components using bubbles and composed. Typically you should use events configured with bubbles: false and composed: false because they’re the least disruptive. These events don’t bubble up through the DOM and don’t cross the shadow boundary. To communicate between sibling components within a single Lightning page or across multiple pages, you can use Lightning Message Service. It has the advantage of working across Visualforce, Aura, LWC, utility bar components and across page tabs in a console app. If you add a listener to something that is not part of the component lifecycle (like the window object, the document object, and so on), you’re responsible for removing the listener yourself. To remove the event listeners use removeEventListener() in the disconnectedCallback lifecycle hook. Failing to do so can result in memory leaks, which will progressively degrade the performance of the entire Lightning app, until the user closes or refreshes their browser tab. When working with lists, letting events bubble, and registering a single event listener on a parent element instead of a separate event listener on every list item can significantly reduce the number of event listeners in your application. This can have a positive impact on performance. More information: Review the Communicate with Events and Configure Event Propagation sections of the Lightning Web Components Dev Guide to learn more. Review Communicate Across the DOM with Lightning Message Service (Beta) and this blog post to learn more about the new Lightning Message Service. Watch the Parent-Child Components video in our LWC Video Gallery to see how to send data from a child component to a parent component. In the DreamHouse sample application check out propertyTileList and paginator for an example of using the Lightning Message service to communicate between components. Third-party JavaScript libraries and Style Sheets Whenever possible, remove dependencies on unneeded libraries. Furthermore, before you decide to use a third-party library in a Lightning component, you should reevaluate if you really need that library. DOM manipulation libraries (like jQuery) and UI libraries (like Bootstrap or jQuery UI) in particular may no longer be needed when working with the Lightning Component Framework. Using third party or your own Custom Style Sheets should only be used if Salesforce Lightning Design System (SLDS) doesn’t meet your needs. DOM manipulation libraries JavaScript has come a long way in recent years. Many DOM manipulation utilities we couldn’t live without like jQuery are now standard in the language. Modern frameworks like the Lightning Component Framework also provide abstractions that make jQuery less relevant. UI libraries You may want to avoid the use of UI libraries like Bootstrap and jQuery UI. Although these libraries provide useful components, they have their own UI identity that can clash with the Lightning Experience identity. The base Lightning components and the SLDS offer similar capabilities while providing a consistent user experience. MVC (Model-View-Controller) frameworks At a high level, libraries like React and AngularJS have the same focus as the Lightning Component Framework: They provide code organization and utilities to create components. Using another MVC framework together with the Lightning Component Framework inside a component isn’t recommended. You can, however, use a Lightning component as a container to host components built with other frameworks (like React and AngularJS) inside the Lightning Experience. However, that is outside the scope of this document. See the LockerService and Lightning Container Component: Securely Using Third-Party Libraries in Lightning Components blog post for details. Custom style sheets Using third party CSS style sheets or creating our own styles can cause performance issues and may make your UI look inconsistent to end users. Developers should become familiar with the Salesforce Lightning Design System (SLDS) that was developed by Salesforce to create beautiful and rich UI experiences for end users. It’s also much more than just styles and CSS, it includes design guidelines and principals used by our own engineers and component blueprints that cover common developer needs like Breadcrumbs, Modals, Alerts and much more. It has an incredible list of Design Tokens that store visual design attributes for color, fonts, spacing, sizing and even touch. Levering the SLDS can also save developers time when building components since it’s built right into Lightning and doesn’t require developers to create and maintain their own CSS. Use Minified versions of libraries and style sheets If you absolutely need to use a third-party library, make sure you use minified versions of the library and style sheet to increase the performance of your app. More information: Review the Salesforce Lightning Design System (SLDS) to learn how to best use its styling in custom components. See the libsChartjs component in the LWC Recipes app for an example of Chart.js in Lightning components. Base Lightning components Before you start building your own custom Lightning components you should familiarize yourself with the library of base components offered. These include listView, recordForm, and many more. Leveraging these base components can significantly speed up your development time. For example if you want a big red button presented to a user, simply use the lightning-button: To produce this: Additional benefits include: Styles: Base Lightning components are styled with the native Lightning look and feel. Performance: Base Lightning components are already loaded at the client-side and don’t require additional download or processing. Our performance optimization efforts are also focused on components in the lightning namespace. Responsiveness: By default base Lightning components are responsive in their design. Innovation: The Lightning namespace is where components are being actively developed. This is where you can expect to see new and improved components moving forward. Accessibility: Base Lightning components are built for accessibility. Client-side validation: Base Lightning components include client-side validation when applicable. More information: Review the Component Reference tab of the Lightning Web Components Dev Guide to learn more about the many components offered. Image optimization Whenever possible, use the (sprite-based) SLDS icons (using and ) instead of custom icons. Salesforce has prebuilt hundreds of icons for you to choose from, so before spending time creating your own custom icons, reuse the ones that SLDS offers. To give you a quick sample here are a few of our favorites: When using other images, be sure to lock image dimensions to avoid reflows and serve the image in those dimensions when possible. For example, don’t load a high-resolution image to display a thumbnail. More information: Review the icons section of the SLDS guide to see all available icons. Component lifecycle rendering and reflow Lightning Web Components have a lifecycle managed by the framework. The framework creates components, inserts them into the DOM, renders them, and removes them from the DOM. Read the rendering lifecycle to understand what happens during this lifecycle and which methods fire at what time. Minimize the number of times your component is being re-rendered. In some cases, it may be helpful to lock DOM regions to specific dimensions to avoid browser reflows of surrounding areas. Development settings and tools This section covers settings and tools that can aid a developer when building high performance applications. The best practices here are focused on helping developers work faster and more efficiently when building in Lightning. Debug mode & component caching Optimizations for a production environment and a development environment are different. Here is a typical question asked in the developer forums: “When I make changes in a component, I need to refresh the page a few times in the browser for my changes to take effect. Why do I have to do that, and how can I avoid it?” The reason is that to optimize performance in a production environment, component definitions are cached at the client-side. As a result, when you make a change to a component, and then reload the page hosting the component, you can still get the previous version of the component served from the client cache. You can usually get the new version of the component by refreshing the page a couple of times, but that isn’t a suitable developer experience. The solution is to enable debug mode and disable client-side caching during development. Debug mode also makes it easier to debug JavaScript code from Lightning components as framework JavaScript code isn’t minified and is easier to read. Recommended settings: A Development Production Debug mode On Off Component caching Off On To enable debug mode: Debug Mode. Select the users you want to enable debug mode for. To disable component caching: Caching, and uncheck Enable secure and persistent browser caching to improve performance IMPORTANT NOTE: Client-side caching is an org-wide setting. Disabling client-side caching and enabling debugging has a significant impact on performance. Only do this in your development environment, not in a production environment. Similarly, if you run tests to assess the performance of your environment, remember to turn these settings back to the production values before running those tests. Performance profiling & debugging tools If you face a problem in a component, make sure you understand what the real problem is before trying to solve it. Don’t make assumptions. Use profiling tools to identify the bugs and performance bottlenecks. You can leverage Chrome’s built in DevTools to help in a number of areas: You can use them to step through JavaScript as it runs to help debug issues. Examine network traffic using the Network panel to watch when the server method is called and when it’s not, for example when working with a storable action. Profile component performance with the Performance panel to watch which actions or requests are taking the most time. Note that is helpful to run Chrome in Guest or Incognito mode when leveraging the developer tools to reduce any noice created by Chrome Extensions Use the Salesforce Lightning Inspector Chrome Extension which is similar to the Performance panel. Analyze with the Salesforce Community Page Optimizer for working with communities. More Information: Review the Debug Lightning Web Components section of the Developer Guide. Watch the Debug LWC using browser-based tools video. Learn how to Enable debug mode for Lightning components. Learn more about Chrome Developer Tools. Summary The performance of an application is impacted by many different factors. The Lightning Web Components performance optimization techniques described in this article are general guidelines that should help you build faster and more responsive applications. Try them out in your application, and let us know what your favorite performance optimization techniques are. If you’re curious about how to assemble blazing fast Lightning pages at scale, check out the Designing Lightning Pages for Scale blog post.
0 notes
Text
JAVA Interview Questions and Answers
java interview questions for freshers experienced developers
1. What is Java? Java is a object-oriented programming language originally developed by Sun Micro systems and released in 1995. Java runs on a variety of platforms, such as Windows, Mac OS, and the various versions of UNIX. 2. What are the supported platforms by Java Programming Language? Java runs on a variety of platforms, such as Windows, Mac OS, and the various versions of UNIX/Linux like HP-Unix, Sun Solaris, Red hat Linux, Ubuntu, Cent OS, etc. 3. List any five features of Java? Some features include Object Oriented Platform Independent Robust Interpreted Multi-threaded 4. Why is Java Architectural Neutral? It’s compiler generates an architecture-neutral object file format, which makes the compiled code to be executable on many processors, with the presence of Java runtime system. 5. What is a singleton class? Give a practical example of its usage. A singleton class in java can have only one instance and hence all its methods and variables belong to just one instance. Singleton class concept is useful for the situations when there is a need to limit the number of objects for a class. The best example of singleton usage scenario is when there is a limit of having only one connection to a database due to some driver limitations or because of any licensing issues. 6. What are the access modifiers in Java? There are 3 access modifiers. Public, protected and private, and the default one if no identifier is specified is called friendly, but programmer cannot specify the friendly identifier explicitly. 7. What is are packages? A package is a collection of related classes and interfaces providing access protection and namespace management. 8. What is meant by Inheritance and What are its advantages? Inheritance is the process of inheriting all the features from a class. The advantages of inheritance are reusability of code and accessibility of variables and methods of the super class by subclasses. 9. What is the difference between superclass and subclass? A super class is a class that is inherited whereas sub class is a class that does the inheriting. 10. What is an abstract class? An abstract class is a class designed with implementation gaps for subclasses to fill in and is deliberately incomplete.

JAVA Interview Questions 11. What are the states associated in the thread? Thread contains ready, running, waiting and dead states. 12. What is synchronization? Synchronization is the mechanism that ensures that only one thread is accessed the resources at a time. 13. What is deadlock? When two threads are waiting each other and can’t precede the program is said to be deadlock. 14. What is an applet? Applet is a dynamic and interactive program that runs inside a web page displayed by a java capable browser 15. What is the lifecycle of an applet? init() method - Can be called when an applet is first loaded start() method - Can be called each time an applet is started. paint() method - Can be called when the applet is minimized or maximized. stop() method - Can be used when the browser moves off the applet’s page. destroy() method - Can be called when the browser is finished with the applet. 16. Define How do you set security in applets? using setSecurityManager() method 17. What is a layout manager and What are different types of layout managers available in java AWT? A layout manager is an object that is used to organize components in a container. The different layouts are available are FlowLayout, BorderLayout, CardLayout, GridLayout and GridBagLayout 18. What is JDBC? JDBC is a set of Java API for executing SQL statements. This API consists of a set of classes and interfaces to enable programs to write pure Java Database applications. 19. What are drivers available? JDBC-ODBC Bridge driver Native API Partly-Java driver JDBC-Net Pure Java driver Native-Protocol Pure Java driver 20. What is stored procedure? Stored procedure is a group of SQL statements that forms a logical unit and performs a particular task. Stored Procedures are used to encapsulate a set of operations or queries to execute on database. Stored procedures can be compiled and executed with different parameters and results and may have any combination of input/output parameters. 21. What is the Java API? The Java API is a large collection of ready-made software components that provide many useful capabilities, such as graphical user interface (GUI) widgets. 22. Why there are no global variables in Java? Global variables are globally accessible. Java does not support globally accessible variables due to following reasons: The global variables breaks the referential transparency Global variables creates collisions in namespace. 23. What are Encapsulation, Inheritance and Polymorphism? Encapsulation is the mechanism that binds together code and data it manipulates and keeps both safe from outside interference and misuse. Inheritance is the process by which one object acquires the properties of another object. Polymorphism is the feature that allows one interface to be used for general class actions. 24. What is the use of bin and lib in JDK? Bin contains all tools such as javac, appletviewer, awt tool, etc., whereas lib contains API and all packages. 25. What is method overloading and method overriding? Method overloading: When a method in a class having the same method name with different arguments is said to be method overloading. Method overriding : When a method in a class having the same method name with same arguments is said to be method overriding. 26. What is the difference between this() and super()? this() can be used to invoke a constructor of the same class whereas super() can be used to invoke a super class constructor. 27. What is Domain Naming Service(DNS)? It is very difficult to remember a set of numbers(IP address) to connect to the Internet. The Domain Naming Service(DNS) is used to overcome this problem. It maps one particular IP address to a string of characters. For example, www. mascom. com implies com is the domain name reserved for US commercial sites, moscom is the name of the company and www is the name of the specific computer, which is mascom’s server. 28. What is URL? URL stands for Uniform Resource Locator and it points to resource files on the Internet. URL has four components: http://www. address. com:80/index.html, where http - protocol name, address - IP address or host name, 80 - port number and index.html - file path. 29. What is RMI and steps involved in developing an RMI object? Remote Method Invocation (RMI) allows java object that executes on one machine and to invoke the method of a Java object to execute on another machine. The steps involved in developing an RMI object are: a) Define the interfaces b) Implementing these interfaces c) Compile the interfaces and their implementations with the java compiler d) Compile the server implementation with RMI compiler e) Run the RMI registry f) Run the application. 30. What is RMI architecture? RMI architecture consists of four layers and each layer performs specific functions: a) Application layer - contains the actual object definition. b) Proxy layer - consists of stub and skeleton. c) Remote Reference layer - gets the stream of bytes from the transport layer and sends it to the proxy layer. d) Transportation layer - responsible for handling the actual machine-to-machine communication. 31. What is a Java Bean? A Java Bean is a software component that has been designed to be reusable in a variety of different environments. 32. What are checked exceptions? Checked exception are those which the Java compiler forces you to catch. e.g. IOException are checked Exceptions. 33. What are runtime exceptions? Runtime exceptions are those exceptions that are thrown at runtime because of either wrong input data or because of wrong business logic etc. These are not checked by the compiler at compile time. 34. What is the difference between error and an exception? An error is an irrecoverable condition occurring at runtime. Such as OutOfMemory error. These JVM errors and you can not repair them at runtime. While exceptions are conditions that occur because of bad input etc. e.g. FileNotFoundException will be thrown if the specified file does not exist. Or a NullPointerException will take place if you try using a null reference. In most of the cases it is possible to recover from an exception (probably by giving user a feedback for entering proper values etc.). 35. What is the purpose of finalization? The purpose of finalization is to give an unreachable object the opportunity to perform any cleanup processing before the object is garbage collected. For example, closing a opened file, closing a opened database Connection. 36. What is the difference between yielding and sleeping? When a task invokes its yield() method, it returns to the ready state. When a task invokes its sleep() method, it returns to the waiting state. 37. What is the difference between preemptive scheduling and time slicing? Under preemptive scheduling, the highest priority task executes until it enters the waiting or dead states or a higher priority task comes into existence. Under time slicing, a task executes for a predefined slice of time and then reenters the pool of ready tasks. The scheduler then determines which task should execute next, based on priority and other factors. 38. What is mutable object and immutable object? If a object value is changeable then we can call it as Mutable object. (Ex., StringBuffer, …) If you are not allowed to change the value of an object, it is immutable object. (Ex., String, Integer, Float, …) 39. What is the purpose of Void class? The Void class is an uninstantiable placeholder class to hold a reference to the Class object representing the primitive Java type void. 40. What is JIT and its use? Really, just a very fast compiler… In this incarnation, pretty much a one-pass compiler — no offline computations. So you can’t look at the whole method, rank the expressions according to which ones are re-used the most, and then generate code. In theory terms, it’s an on-line problem. 41. What is nested class? If all the methods of a inner class is static then it is a nested class. 42. What is HashMap and Map? Map is Interface and Hashmap is class that implements that. 43. What are different types of access modifiers? public: Any thing declared as public can be accessed from anywhere. private: Any thing declared as private can’t be seen outside of its class. protected: Any thing declared as protected can be accessed by classes in the same package and subclasses in the other packages. default modifier : Can be accessed only to classes in the same package. 44. What is the difference between Reader/Writer and InputStream/Output Stream? The Reader/Writer class is character-oriented and the InputStream/OutputStream class is byte-oriented. 45. What is servlet? Servlets are modules that extend request/response-oriented servers, such as java-enabled web servers. For example, a servlet might be responsible for taking data in an HTML order-entry form and applying the business logic used to update a company’s order database. 46. What is Constructor? A constructor is a special method whose task is to initialize the object of its class. It is special because its name is the same as the class name. They do not have return types, not even void and therefore they cannot return values. They cannot be inherited, though a derived class can call the base class constructor. Constructor is invoked whenever an object of its associated class is created. 47. What is an Iterator ? The Iterator interface is used to step through the elements of a Collection. Iterators let you process each element of a Collection. Iterators are a generic way to go through all the elements of a Collection no matter Define How it is organized. Iterator is an Interface implemented a different way for every Collection. 48. What is the List interface? The List interface provides support for ordered collections of objects. Lists may contain duplicate elements. 49. What is memory leak? A memory leak is where an unreferenced object that will never be used again still hangs around in memory and doesnt get garbage collected. 50. What is the difference between the prefix and postfix forms of the ++ operator? The prefix form performs the increment operation and returns the value of the increment operation. The postfix form returns the current value all of the expression and then performs the increment operation on that value. 51. What is the difference between a constructor and a method? A constructor is a member function of a class that is used to create objects of that class. It has the same name as the class itself, has no return type, and is invoked using the new operator. A method is an ordinary member function of a class. It has its own name, a return type (which may be void), and is invoked using the dot operator. 52. What will happen to the Exception object after exception handling? Exception object will be garbage collected. 53. Difference between static and dynamic class loading. Static class loading: The process of loading a class using new operator is called static class loading. Dynamic class loading: The process of loading a class at runtime is called dynamic class loading. Dynamic class loading can be done by using Class.forName(….).newInstance(). 54. Explain the Common use of EJB The EJBs can be used to incorporate business logic in a web-centric application. The EJBs can be used to integrate business processes in Business-to-business (B2B) e-commerce applications.In Enterprise Application Integration applications, EJBs can be used to house processing and mapping between different applications. 55. What is JSP? JSP is a technology that returns dynamic content to the Web client using HTML, XML and JAVA elements. JSP page looks like a HTML page but is a servlet. It contains Presentation logic and business logic of a web application. 56. What is the purpose of apache tomcat? Apache server is a standalone server that is used to test servlets and create JSP pages. It is free and open source that is integrated in the Apache web server. It is fast, reliable server to configure the applications but it is hard to install. It is a servlet container that includes tools to configure and manage the server to run the applications. It can also be configured by editing XML configuration files. 57. Where pragma is used? Pragma is used inside the servlets in the header with a certain value. The value is of no-cache that tells that a servlets is acting as a proxy and it has to forward request. Pragma directives allow the compiler to use machine and operating system features while keeping the overall functionality with the Java language. These are different for different compilers. 58. Briefly explain daemon thread. Daemon thread is a low priority thread which runs in the background performs garbage collection operation for the java runtime system. 59. What is a native method? A native method is a method that is implemented in a language other than Java. 60. Explain different way of using thread? A Java thread could be implemented by using Runnable interface or by extending the Thread class. The Runnable is more advantageous, when you are going for multiple inheritance. 61. What are the two major components of JDBC? One implementation interface for database manufacturers, the other implementation interface for application and applet writers. 62. What kind of thread is the Garbage collector thread? It is a daemon thread. 63. What are the different ways to handle exceptions? There are two ways to handle exceptions, By wrapping the desired code in a try block followed by a catch block to catch the exceptions. and List the desired exceptions in the throws clause of the method and let the caller of the method handle those exceptions. 64. Define How many objects are created in the following piece of code? MyClass c1, c2, c3; c1 = new MyClass (); c3 = new MyClass (); Answer: Only 2 objects are created, c1 and c3. The reference c2 is only declared and not initialized. 65.What is UNICODE? Unicode is used for internal representation of characters and strings and it uses 16 bits to represent each other. 66. Can a constructor have different name than a Class name in Java? Constructor in Java must have same name as the class name and if the name is different, it doesn’t act as a constructor and compiler thinks of it as a normal method. 67. What will be the output of Round(3.7) and Ceil(3.7)? Round(3.7) returns 4 and Ceil(3.7) returns 4. 68: Can we use goto in Java to go to a particular line? In Java, there is not goto keyword and java doesn’t support this feature of going to a particular labeled line. 69. Can a dead thread be started again? In java, a thread which is in dead state can’t be started again. There is no way to restart a dead thread. 70. Is the following class declaration correct? public abstract final class testClass { // Class methods and variables } The above class declaration is incorrect as an abstract class can’t be declared as Final. 71. Is JDK required on each machine to run a Java program? JDK is development Kit of Java and is required for development only and to run a Java program on a machine, JDK isn’t required. Only JRE is required. 72. Which object oriented Concept is achieved by using overloading and overriding? Polymorphism 73. Is it possible to define a method in Java class but provide it’s implementation in the code of another language like C? Yes, we can do this by use of native methods. In case of native method based development, we define public static methods in our Java class without its implementation and then implementation is done in another language like C separately. 74. Define How destructors are defined in Java? In Java, there are no destructors defined in the class as there is no need to do so. Java has its own garbage collection mechanism which does the job automatically by destroying the objects when no longer referenced. 75. Can a variable be local and static at the same time? No a variable can’t be static as well as local at the same time. Defining a local variable as static gives compilation error. 76. Can we have static methods in an Interface? Static methods can’t be overridden in any class while any methods in an interface are by default abstract and are supposed to be implemented in the classes being implementing the interface. So it makes no sense to have static methods in an interface in Java. 77. In a class implementing an interface, can we change the value of any variable defined in the interface? No, we can’t change the value of any variable of an interface in the implementing class as all variables defined in the interface are by default public, static and Final and final variables are like constants which can’t be changed later. 78. Is it correct to say that due to garbage collection feature in Java, a java program never goes out of memory? Even though automatic garbage collection is provided by Java, it doesn’t ensure that a Java program will not go out of memory as there is a possibility that creation of Java objects is being done at a faster pace compared to garbage collection resulting in filling of all the available memory resources. So, garbage collection helps in reducing the chances of a program going out of memory but it doesn’t ensure that. 79. Can we have any other return type than void for main method? No, Java class main method can have only void return type for the program to get successfully executed. Nonetheless , if you absolutely must return a value to at the completion of main method , you can use System.exit(int status) 80. I want to re-reach and use an object once it has been garbage collected. Define How it’s possible? Once an object has been destroyed by garbage collector, it no longer exists on the heap and it can’t be accessed again. There is no way to reference it again. 81. In Java thread programming, which method is a must implementation for all threads? Run() is a method of Runnable interface that must be implemented by all threads. 82. I want to control database connections in my program and want that only one thread should be able to make database connection at a time. Define How can I implement this logic? This can be implemented by use of the concept of synchronization. Database related code can be placed in a method which hs synchronized keyword so that only one thread can access it at a time. 83. Can an Interface extend another Interface? Yes an Interface can inherit another Interface, for that matter an Interface can extend more than one Interface. 84. I want my class to be developed in such a way that no other class (even derived class) can create its objects. Define How can I do so? If we declare the constructor of a class as private, it will not be accessible by any other class and hence, no other class will be able to instantiate it and formation of its object will be limited to itself only. 85. Define How objects are stored in Java? In java, each object when created gets a memory space from a heap. When an object is destroyed by a garbage collector, the space allocated to it from the heap is re-allocated to the heap and becomes available for any new objects. 86. Define How can we find the actual size of an object on the heap? In java, there is no way to find out the exact size of an object on the heap. 87. Which of the following classes will have more memory allocated? Class Three methods, four variables, no object Class B: Five methods, three variables, no object Memory isn’t allocated before creation of objects. Since for both classes, there are no objects created so no memory is allocated on heap for any class. 88. What happens if an exception is not handled in a program? If an exception is not handled in a program using try catch blocks, program gets aborted and no statement executes after the statement which caused exception throwing. 89. I have multiple constructors defined in a class. Is it possible to call a constructor from another constructor’s body? If a class has multiple constructors, it’s possible to call one constructor from the body of another one using this(). 90. What’s meant by anonymous class? An anonymous class is a class defined without any name in a single line of code using new keyword. For example, in below code we have defined an anonymous class in one line of code: public java.util.Enumeration testMethod() { return new java.util.Enumeration() { @Override public boolean hasMoreElements() { // TODO Auto-generated method stub return false; } @Override public Object nextElement() { // TODO Auto-generated method stub return null; } 91. Is there a way to increase the size of an array after its declaration? Arrays are static and once we have specified its size, we can’t change it. If we want to use such collections where we may require a change of size ( no of items), we should prefer vector over array. 92. If an application has multiple classes in it, is it okay to have a main method in more than one class? If there is main method in more than one classes in a java application, it won’t cause any issue as entry point for any application will be a specific class and code will start from the main method of that particular class only. 93. I want to persist data of objects for later use. What’s the best approach to do so? The best way to persist data for future use is to use the concept of serialization. 94. What is a Local class in Java? In Java, if we define a new class inside a particular block, it’s called a local class. Such a class has local scope and isn’t usable outside the block where its defined. 95. String and StringBuffer both represent String objects. Can we compare String and StringBuffer in Java? Although String and StringBuffer both represent String objects, we can’t compare them with each other and if we try to compare them, we get an error. 96. Which API is provided by Java for operations on set of objects? Java provides a Collection API which provides many useful methods which can be applied on a set of objects. Some of the important classes provided by Collection API include ArrayList, HashMap, TreeSet and TreeMap. 97. Can we cast any other type to Boolean Type with type casting? No, we can neither cast any other primitive type to Boolean data type nor can cast Boolean data type to any other primitive data type. 98. What are synchronized methods and synchronized statements? Synchronized methods are methods that are used to control access to an object. A synchronized statement can only be executed after a thread has acquired the lock for the object or class referenced in the synchronized statement. 99. Define How does a try statement determine which catch clause should be used to handle an exception? When an exception is thrown within the body of a try statement, the catch clauses of the try statement are examined in the order in which they appear. The first catch clause that is capable of handling the exception is executed. The remaining catch clauses are ignored. 100. What will be the default values of all the elements of an array defined as an instance variable? If the array is an array of primitive types, then all the elements of the array will be initialized to the default value corresponding to that primitive type. Basic JAVA Questions with Answers pdf download 101. What is the difference between static and non-static variables? A static variable is associated with the class as a whole rather than with specific instances of a class. Non-static variables take on unique values with each object instance. 102. What is Serialization and deserialization? Serialization is the process of writing the state of an object to a byte stream. Deserialization is the process of restoring these objects. 103. What are use cases? It is part of the analysis of a program and describes a situation that a program might encounter and what behavior the program should exhibit in that circumstance. 104. Explain the use of sublass in a Java program? Sub class inherits all the public and protected methods and the implementation. It also inherits all the default modifier methods and their implementation. 105. How to add menushortcut to menu item? If there is a button instance called b1, you may add menu short cut by calling b1.setMnemonic('F'), so the user may be able to use Alt+F to click the button. 106. Can you write a Java class that could be used both as an applet as well as an application? Yes, just add a main() method to the applet. 107. What is the difference between Swing and AWT components? AWT components are heavy-weight, whereas Swing components are lightweight. Heavy weight components depend on the local windowing toolkit. For example, java.awt.Button is a heavy weight component, when it is running on the Java platform for Unix platform, it maps to a real Motif button. 108. What's the difference between constructors and other methods? Constructors must have the same name as the class and can not return a value. They are only called once while regular methods could be called many times. 109. Is there any limitation of using Inheritance? Yes, since inheritance inherits everything from the super class and interface, it may make the subclass too clustering and sometimes error-prone when dynamic overriding or dynamic overloading in some situation. 109. When is the ArrayStoreException thrown? When copying elements between different arrays, if the source or destination arguments are not arrays or their types are not compatible, an ArrayStoreException will be thrown. 110. Can you call one constructor from another if a class has multiple constructors? Yes, use this() syntax. 111. What's the difference between the methods sleep() and wait()? The code sleep(2000); puts thread aside for exactly two seconds. The code wait(2000), causes a wait of up to two second. A thread could stop waiting earlier if it receives the notify() or notifyAll() call. The method wait() is defined in the class Object and the method sleep() is defined in the class Thread. 112. When ArithmeticException is thrown? The ArithmeticException is thrown when integer is divided by zero or taking the remainder of a number by zero. It is never thrown in floating-point operations. 113. What is a transient variable? A transient variable is a variable that may not be serialized during Serialization and which is initialized by its default value during de-serialization, 114. What is synchronization? Synchronization is the capability to control the access of multiple threads to shared resources. synchronized keyword in java provides locking which ensures mutual exclusive access of shared resource and prevent data race. 115. What is the Collections API? The Collections API is a set of classes and interfaces that support operations on collections of objects. 116. Does garbage collection guarantee that a program will not run out of memory? Garbage collection does not guarantee that a program will not run out of memory. It is possible for programs to use up memory resources faster than they are garbage collected. It is also possible for programs to create objects that are not subject to garbage collection. 117. The immediate super class of the Applet class? Panel is the immediate super class. A panel provides space in which an application can attach any other component, including other panels. 118. Which Java operator is right associative? The = operator is right associative. 119. What is the difference between a break statement and a continue statement? A break statement results in the termination of the statement to which it applies (switch, for, do, or while). A continue statement is used to end the current loop iteration and return control to the loop statement. 120. If a variable is declared as private, where may the variable be accessed? A private variable may only be accessed within the class in which it is declared. 121. What is the purpose of the System class? The purpose of the System class is to provide access to system resources. 122. List primitive Java types? The eight primitive types are byte, char, short, int, long, float, double, and boolean. 123. What is the relationship between clipping and repainting under AWT? When a window is repainted by the AWT painting thread, it sets the clipping regions to the area of the window that requires repainting. 124. Which class is the immediate superclass of the Container class? Component class is the immediate super class. 125. What class of exceptions are generated by the Java run-time system? The Java runtime system generates RuntimeException and Error exceptions. 126. Under what conditions is an object's finalize() method invoked by the garbage collector? The garbage collector invokes an object's finalize() method when it detects that the object has become unreachable. 127. How can a dead thread be restarted? A dead thread cannot be restarted. 128. Which arithmetic operations can result in the throwing of an ArithmeticException? Integer / and % can result in the throwing of an ArithmeticException. 129. Variable of the boolean type is automatically initialized as? The default value of the boolean type is false. 130. What are ClassLoaders? A class loader is an object that is responsible for loading classes. The class ClassLoader is an abstract class. 131. What is the difference between an Interface and an Abstract class? An abstract class can have instance methods that implement a default behavior. An Interface can only declare constants and instance methods, but cannot implement default behavior and all methods are implicitly abstract. An interface has all public members and no implementation. 132. What will happen if static modifier is removed from the signature of the main method? Program throws "NoSuchMethodError" error at runtime . 133. Can try statements be nested? Yes 134. What is the default value of an object reference declared as an instance variable? Null, unless it is defined explicitly. 135. Can a top level class be private or protected? No, a top level class can not be private or protected. It can have either "public" or no modifier. 136. Why do we need wrapper classes? We can pass them around as method parameters where a method expects an object. It also provides utility methods. 137. What is the difference between error and an exception? An error is an irrecoverable condition occurring at runtime. Such as OutOfMemory error. Exceptions are conditions that occur because of bad input etc. e.g. FileNotFoundException will be thrown if the specified file does not exist. 138. Is it necessary that each try block must be followed by a catch block? It is not necessary that each try block must be followed by a catch block. It should be followed by either a catch block or a finally block. 139. When a thread is created and started, what is its initial state? A thread is in the ready state as initial state after it has been created and started. 140. What is the Locale class? The Locale class is used to tailor program output to the conventions of a particular geographic, political, or cultural region. 141. What are synchronized methods and synchronized statements? Synchronized methods are methods that are used to control access to an object. A synchronized statement can only be executed after a thread has acquired the lock for the object or class referenced in the synchronized statement. 142. What is runtime polymorphism or dynamic method dispatch? Runtime polymorphism or dynamic method dispatch is a process in which a call to an overridden method is resolved at runtime rather than at compile-time. In this process, an overridden method is called through the reference variable of a superclass. 143. What is Dynamic Binding(late binding)? Binding refers to the linking of a procedure call to the code to be executed in response to the call. Dynamic binding means that the code associated with a given procedure call is not known until the time of the call at run-time. 144. Can constructor be inherited? No, constructor cannot be inherited. 145. What are the advantages of ArrayList over arrays? ArrayList can grow dynamically and provides more powerful insertion and search mechanisms than arrays. 146. Why deletion in LinkedList is fast than ArrayList? Deletion in linked list is fast because it involves only updating the next pointer in the node before the deleted node and updating the previous pointer in the node after the deleted node. 147. How do you decide when to use ArrayList and LinkedList? If you need to frequently add and remove elements from the middle of the list and only access the list elements sequentially, then LinkedList should be used. If you need to support random access, without inserting or removing elements from any place other than the end, then ArrayList should be used. 148. What is a Values Collection View ? It is a collection returned by the values() method of the Map Interface, It contains all the objects present as values in the map. 149. What is dot operator? The dot operator(.) is used to access the instance variables and methods of class objects.It is also used to access classes and sub-packages from a package. 150. Where and how can you use a private constructor? Private constructor is used if you do not want other classes to instantiate the object and to prevent subclassing.T 151. What is type casting? Type casting means treating a variable of one type as though it is another type. Q: Describe life cycle of thread? A thread is a execution in a program. The life cycle of a thread include:Newborn state Runnable state Running state Blocked state Dead state 152. What is the difference between the >> and >>> operators? The >> operator carries the sign bit when shifting right. The >>> zero-fills bits that have been shifted out. 153. Which method of the Component class is used to set the position and size of a component? setBounds() method is used for this purpose. 154. What is the range of the short type? The range of the short type is -(2^15) to 2^15 - 1. 155. What is the immediate superclass of Menu? MenuItem class 156. Does Java allow Default Arguments? No, Java does not allow Default Arguments. 157. Which number is denoted by leading zero in java? Octal Numbers are denoted by leading zero in java, example: 06 158. Which number is denoted by leading 0x or 0X in java? Hexadecimal Numbers are denoted by leading 0x or 0X in java, example: 0XF 159. Break statement can be used as labels in Java? Yes, an example can be break one; 160. Where import statement is used in a Java program? Import statement is allowed at the beginning of the program file after package statement. 161. Explain suspend() method under Thread class> It is used to pause or temporarily stop the execution of the thread. 162. Explain isAlive() method under Thread class? It is used to find out whether a thread is still running or not. 163. What is currentThread()? It is a public static method used to obtain a reference to the current thread. 164. Explain main thread under Thread class execution? The main thread is created automatically and it begins to execute immediately when a program starts. It ia thread from which all other child threads originate. 165. Life cycle of an applet includes which steps? Life cycle involves the following steps: Initialization Starting Stopping Destroying Painting 166. Why is the role of init() method under applets? It initializes the applet and is the first method to be called. 167. Which method is called by Applet class to load an image? getImage(URL object, filename) is used for this purpose. 168. Define code as an attribute of Applet? It is used to specify the name of the applet class. 169. Define canvas? It is a simple drawing surface which are used for painting images or to perform other graphical operations. 170. Define Network Programming? It refers to writing programs that execute across multiple devices (computers), in which the devices are all connected to each other using a network. 171. What is a Socket? Sockets provide the communication mechanism between two computers using TCP. A client program creates a socket on its end of the communication and attempts to connect that socket to a server. 172. Advantages of Java Sockets? Sockets are flexible and sufficient. Efficient socket based programming can be easily implemented for general communications. It cause low network traffic. 173. Disadvantages of Java Sockets? Socket based communications allows only to send packets of raw data between applications. Both the client-side and server-side have to provide mechanisms to make the data useful in any way. 174. Which class is used by server applications to obtain a port and listen for client requests? java.net.ServerSocket class is used by server applications to obtain a port and listen for client requests 175. Which class represents the socket that both the client and server use to communicate with each other? java.net.Socket class represents the socket that both the client and server use to communicate with each other. 176. Why Generics are used in Java? Generics provide compile-time type safety that allows programmers to catch invalid types at compile time. Java Generic methods and generic classes enable programmers to specify, with a single method declaration, a set of related methods or, with a single class declaration, a set of related types. 177. What environment variables do I need to set on my machine in order to be able to run Java programs? CLASSPATH and PATH are the two variables. 178. Is there any need to import java.lang package? No, there is no need to import this package. It is by default loaded internally by the JVM. 179. What is Nested top-level class? If a class is declared within a class and specify the static modifier, the compiler treats the class just like any other top-level class. Nested top-level class is an Inner class. 180. What is Externalizable interface? Externalizable is an interface which contains two methods readExternal and writeExternal. These methods give you a control over the serialization mechanism. 181. If System.exit (0); is written at the end of the try block, will the finally block still execute? No in this case the finally block will not execute because when you say System.exit (0); the control immediately goes out of the program, and thus finally never executes. 182. What is daemon thread? Daemon thread is a low priority thread, which runs intermittently in the back ground doing the garbage collection operation for the java runtime system. 183. Which method is used to create the daemon thread? setDaemon method is used to create a daemon thread. 184. Which method must be implemented by all threads? All tasks must implement the run() method 185. What is the GregorianCalendar class? The GregorianCalendar provides support for traditional Western calendars 186. What is the SimpleTimeZone class? The SimpleTimeZone class provides support for a Gregorian calendar . 187. What is the difference between the size and capacity of a Vector? The size is the number of elements actually stored in the vector, while capacity is the maximum number of elements it can store at a given instance of time. 188. Can a vector contain heterogenous objects? Yes a Vector can contain heterogenous objects. Because a Vector stores everything in terms of Object. 189. What is an enumeration? An enumeration is an interface containing methods for accessing the underlying data structure from which the enumeration is obtained. It allows sequential access to all the elements stored in the collection. 190. What is difference between Path and Classpath? Path and Classpath are operating system level environment variales. Path is defines where the system can find the executables(.exe) files and classpath is used to specify the location of .class files. 191. Can a class declared as private be accessed outside it's package? No, it's not possible to accessed outside it's package. 192. What are the restriction imposed on a static method or a static block of code? A static method should not refer to instance variables without creating an instance and cannot use "this" operator to refer the instance. 240. Can an Interface extend another Interface? Yes an Interface can inherit another Interface, for that matter an Interface can extend more than one Interface. 241. Which object oriented Concept is achieved by using overloading and overriding? Polymorphism 242. What is an object's lock and which object's have locks? An object's lock is a mechanism that is used by multiple threads to obtain synchronized access to the object. A thread may execute a synchronized method of an object only after it has acquired the object's lock. 243. What is Downcasting? It is the casting from a general to a more specific type, i.e. casting down the hierarchy. 244. What are order of precedence and associativity and how are they used? Order of precedence determines the order in which operators are evaluated in expressions. Associatity determines whether an expression is evaluated left-to-right or right-to-left. 245. If a method is declared as protected, where may the method be accessed? A protected method may only be accessed by classes or interfaces of the same package or by subclasses of the class in which it is declared. 246. What is the difference between inner class and nested class? When a class is defined within a scope of another class, then it becomes inner class. If the access modifier of the inner class is static, then it becomes nested class. 247. What restrictions are placed on method overriding? Overridden methods must have the same name, argument list, and return type. The overriding method may not limit the access of the method it overrides. 248. What is constructor chaining and how is it achieved in Java? A child object constructor always first needs to construct its parent. In Java it is done via an implicit call to the no-args constructor as the first statement. 249. Can a double value be cast to a byte? Yes, a double value can be cast to a byte. 250. How does a try statement determine which catch clause should be used to handle an exception? When an exception is thrown within the body of a try statement, the catch clauses of the try statement are examined in the order in which they appear. The first catch clause that is capable of handling the exception is executed. The remaining catch clauses are ignored. Core Java Interview Questions JAVA Online Test Java Interview Questions for Freshers & Experienced #java interview questions for experienced #java interview questions pdf #java interview questions and answers for freshers #java interview questions geeksforgeeks #java interview questions for experienced professionals #java interview questions for 5 years experience #java interview questions and answers for freshers pdf Read the full article
0 notes
Text
Guru Chandal Dosh Puja in Ujjain: Benefits, Procedure and Online Booking
Understanding Guru Chandal Dosh in Vedic Astrology – When Jupiter Meets Rahu or Ketu
In Vedic astrology, Guru Chandal Dosh is a powerful planetary combination that occurs when Jupiter (Guru) is in conjunction with Rahu or Ketu in one’s birth chart. Jupiter is the planet of wisdom, spirituality, and fortune. When it is influenced by malefic Rahu or Ketu, its positive energies get corrupted, leading to misjudgment, material obsession, and spiritual confusion.
This dosh can affect a person’s career, family harmony, marriage prospects, and spiritual growth. Performing a Guru Chandal Dosh Puja in Ujjain is considered a highly effective remedy to neutralize its adverse effects.
Signs and Symptoms of Guru Chandal Dosh in Kundli – How to Identify the Need for Puja
Before deciding on the puja, here are some key symptoms that indicate the presence of Guru Chandal Dosh:
Struggles in education and career despite hard work
Poor decision-making or guidance from false people
Disrespect toward elders, gurus, or teachers
Financial instability and unstable spiritual path
Delayed marriage or disturbances in married life
Conflicts with father or spiritual mentors
Loss of interest in religion or righteous behavior
Why Ujjain is the Most Auspicious Place to Perform Guru Chandal Dosh Puja
Ujjain is one of the seven Moksha-puris in India and home to the Mahakaleshwar Jyotirlinga, which is known for purifying the deepest karmic and planetary faults. The spiritual vibration and presence of powerful temples make Ujjain the most sacred location to perform Guru Chandal Dosh Nivaran Puja.
Here, experienced and Vedic-trained Pandits perform pujas with strict ritual accuracy, ensuring maximum astrological benefit for the devotee.
Benefits of Performing Guru Chandal Dosh Puja in Ujjain – Spiritual and Material Improvements
By performing this powerful puja in Ujjain, a devotee can receive multiple blessings:
Neutralizes the harmful effects of Jupiter-Rahu or Jupiter-Ketu conjunction
Helps overcome illusions, confusion, and misjudgments
Restores faith, dharma, and respect for higher knowledge
Improves relations with teachers, father, or mentors
Enhances wisdom, career success, and financial stability
Helps regain spiritual balance and inner peace
Brings back clarity in education, marriage, and life path
Step-by-Step Puja Vidhi (Procedure) for Guru Chandal Dosh Nivaran in Ujjain
A standard Guru Chandal Dosh Puja in Ujjain includes the following rituals:
Ganesh Pujan and Sankalp – Invocation of Lord Ganesh for obstacle-free rituals
Kalash Sthapana – Establishing sacred energy
Guru Graha Shanti Path – Special chanting for Jupiter (Brihaspati)
Rahu/Ketu Shanti Jaap – Mantras to pacify shadow planets
Navgraha Puja – Worship of all 9 planets for balance
Havan (Homam) – Fire ritual to offer prayers and remove dosh
Brahmin Bhojan and Daan – Feeding Brahmins and offering dakshina as per tradition
Puja duration is approximately 2–3 hours, and it can be performed in-person or remotely by giving Sankalp online.
When to Perform Guru Chandal Dosh Puja – Best Dates and Muhurat for 2025
The puja should be performed on auspicious days related to Jupiter or Rahu/Ketu, such as:
Thursday (Guruvar) – Especially during Shukla Paksha
Brihaspati Jayanti
Guru Pushya Yoga or Amrit Siddhi Yoga
During Rahu-Jupiter conjunction transit (Guru Chandal Yog in Gochar)
Pitra Paksha and Shravan Maas for ancestral blessings
Consult a qualified astrologer to find the most appropriate muhurat based on your birth chart.
Online Booking of Guru Chandal Dosh Puja in Ujjain – Hassle-Free Process for Devotees
With digital puja services, now you can book Guru Chandal Dosh Nivaran Puja online in Ujjain easily:
How It Works:
Visit a trusted puja service provider or official temple portal
Choose the puja type (Guru Chandal Dosh Nivaran Puja)
Enter your details – Name, Gotra, Date and Place of Birth
Select puja date or consult for muhurat
Make secure payment
Attend via live video or receive video and photos post-puja
Get Prasad and puja report couriered to your home
This option is ideal for NRIs, working professionals, or those unable to travel to Ujjain.
Why Choose Ujjain Pandit Atul Agnihotri Ji for Guru Chandal Dosh Puja?
If you’re seeking a trusted, experienced, and Vedic scholar for the puja, Pandit Atul Agnihotri Ji in Ujjain is highly recommended. His services include:
25+ years of experience in Guru-related dosh pujas
Accurate ritual performance with authentic mantras
Personalized attention and Vedic Sankalp method
Online/remote Sankalp puja options
Transparent pricing and puja packages
Complete documentation and post-puja guidance
Book Your Guru Chandal Dosh Puja in Ujjain and Remove Planetary Obstacles Today
If you or your loved one is struggling due to Guru Chandal Yog, this powerful Vedic puja performed in Ujjain can change your life. Don't let the influence of malefic planets disturb your destiny. Book the puja today and invite blessings of wisdom, success, and peace into your life.
Call Pandit ji : +91 9644451903
0 notes
Text
2019's Best Distributed System Books PDF, Notes, Course Data and Tutorials

Introduction to Distributed System
Distributed computing is a field of computer science that studies distributed systems. A distributed system is a system whose components are located on different networked computers, which then communicate and coordinate their actions by passing messages to each other. The components interact with each other in order to achieve a common goal. Three significant characteristics of distributed systems are: concurrency of components, lack of a global clock, and independent failure of components. Examples of distributed systems vary from SOA-based systems to massively multiplayer online games to peer-to-peer applications. A computer program that runs within a distributed system is called a distributed program (and distributed programming is the process of writing such programs). There are many different types of implementations for the message passing mechanism, including pure HTTP, RPC-like connectors and message queues, Distributed computing also refers to the use of distributed systems to solve computational problems. In distributed computing, a problem is divided into many tasks, each of which is solved by one or more computers, which communicate with each other via message passing.
Applications of Distributed System
Reasons for using distributed systems and distributed computing may include: The very nature of an application may require the use of a communication network that connects several computers: for example, data produced in one physical location and required in another location. There are many cases in which the use of a single computer would be possible in principle, but the use of a distributed system is beneficial for practical reasons. For example, it may be more cost-efficient to obtain the desired level of performance by using a cluster of several low-end computers, in comparison with a single high-end computer. A distributed system can provide more reliability than a non-distributed system, as there is no single point of failure. Moreover, a distributed system may be easier to expand and manage than a monolithic uniprocessor system.
This Outline Will be similar with your University 2019 Course Outline for Distributed System Subject.
Introduction to Parallel and Distributed Systems, Software Architectures: Threads and Shared memory, Processes and Message passing, Distributed Shared Memory (DSM), Distributed Shared Data (DSD). System Models, Networking and Inter networking, Communication Models and Abstractions (Message passing, stream oriented communications, remote procedure calls, remote method invocation), Naming in Distributed Systems, Concurrency and Synchronization, Process Synchronization, Distributed Transaction and Concurrency Control, Distributed Data Replication, Security and Access Control, Overview of Web Services, Cloud Computing.
Best Recommended Distributed System Books PDF, Tutorials and Notes for Universities:
Here is detailed list of best Data Warehousing Books for Universities: Distributed Systems: Principles and Paradigms, Andrew S. Tanenbaum and Maarten van Steen. Prentice Hall Distributed Systems: Concepts and Design by 4th edition, George Coulouris, Jean Dollimore and Tim Kindberg. Addison-Wesley Designing Distributed Systems: Patterns and Paradigms for Scalable, Reliable Services by Brendan Burns Designing Data-Intensive Applications: The Big Ideas Behind Reliable, Scalable, and Maintainable Systems by Martin Kleppmann
Free Distributed System PDF Notes, Books and Helping Material to Download
Distributed Systems: Principles and Paradigms by Andrew S.. PDF Book

DOWNLOAD Distributed Systems: Concepts and Design by George Coulouris.. PDF BOOK

DOWNLOAD Designing Distributed Systems: Patterns and Paradigms for Scalable, Reliable Services by Brendan Burns PDF Book

DOWNLOAD
Distributed System Video Tutorials
Distributed Systems by Education 4u Distributed Systems by Last Night Study Distributed Systems (Prof. Pallab Dasgupta) by Phoenix Returns
Get Access to Distributed System Courses and Books exclusive on Amazon, Khan Academy, Scribd, Coursea, Bightthink, EDX and BrightStorm
Check out more on Amazon for Distributed System Books Check out on Khan Academy for Distributed System Helping Material Check out on COURSEA for Distributed System Course Check out on Bright Storm for Distributed System Tuturials Check out on EDX for Distributed System Courses Get more Details about Bachelor's Degree Courses Here. These Course contents belong to HEC outline for this specific Subject. If you have any further inquiries, Please Contact US for details via mail. All the data is extracted from HEC official website. The basic purpose for this to find all course subjects data on one page. Read the full article
0 notes
Link
Build Serverless APIs with Serverless Framework and NodeJs ##elearning ##Udacity #APIs #Build #framework #Nodejs #Serverless Build Serverless APIs with Serverless Framework and NodeJs The Serverless Framework is a free and open-source web framework written using Node.js. Serverless is the first framework that was originally developed for building applications exclusively on AWS Lambda, a serverless computing platform provided by Amazon as a part of the Amazon Web Services. Currently, applications developed with Serverless can be deployed to other function as a service providers, including Microsoft Azure with Azure Functions, IBM Bluemix with IBM Cloud Functions based on Apache OpenWhisk, Google Cloud using Google Cloud Functions, Oracle Cloud using Oracle Fn[1], Kubeless based on Kubernetes, Spotinst and Webtask by Auth0.[2] Serverless is a cloud computing execution model where the cloud provider dynamically manages the allocation and provisioning of servers. A serverless application runs in stateless compute containers that are event-triggered, ephemeral (may last for one invocation), and fully managed by the cloud provider. Pricing is based on the number of executions rather than pre-purchased compute capacity, isn’t it the ideal framework for that project you have been planning since a long time? Well, go ahead do it. Serverless applications are event-driven cloud-based systems where application development rely solely on a combination of third-party services, client-side logic and cloud-hosted remote procedure calls (Functions as a Service). Most of the cloud providers have invested heavily in serverless and thats a lot of money; with the given massive promotion and realistic offering you can safely assume serverless to be one of the most used cloud services in upcoming years. Here are some of the currently available cloud services: AWS Lambda Google Cloud Functions Azure Functions IBM OpenWhisk Alibaba Function Compute Iron Functions Auth0 Webtask Oracle Fn Project Kubeless Traditional vs. Serverless Architecture For years your applications have run on servers which you had to patch, update, and continuously look after late nights and early mornings due to all the unimaginable errors that broke your production. As long as you managed them, the whole responsibility of their proper functioning was on you. Serverless tends to be unlike the aforementioned, you no longer need to worry about the underlying servers. Reason being, they are not managed by you anymore and with management out of the picture the responsibility falls on the Cloud vendors. But regardless the cool features of Serverless in some cases, the traditional architecture outshines it. Pricing One of the major advantages of using Serverless is reduced cost, for years the cost of provisioning servers and maintaining that 24x7 server team which blew a hole in your pocket is gone. The cost model of Serverless is execution-based: you’re charged for the number of executions. You’re allotted a certain number of seconds of use that varies with the amount of memory you require. Likewise, the price per MS (millisecond) varies with the amount of memory you require. Obviously, shorter running functions are more adaptable to this model with a peak execution time of 300-second for most Cloud vendors. The winner here is Serverless Architecture. Networking The downside is that Serverless functions are accessed only as private APIs. To access these you must set up an API Gateway. This doesn’t have an impact on your pricing or process, but it means you cannot directly access them through the usual IP, snap! The winner here is Traditional Architecture. 3rd Party Dependencies Most, if not all of your projects have external dependencies, they rely on libraries that are not built into the language or framework you use. You often use libraries with functionality that includes cryptography, image processing, etc., these libraries can be pretty heavy. Without system-level access, you must package these dependencies into the application itself. Reinventing the wheel isn’t always a good idea. The winner here is based on the context. For simple applications with few dependencies, Serverless is the winner; for anything more complex, Traditional Architecture is the winner. Environments Setting up different environments for Serverless is as easy as setting up a single environment. Given that it’s pay per execution, this is a large improvement over traditional servers, you no longer need to set up dev, staging, and production machines. Eventually you’d lose count of all the environments, at some point. The winner here is Serverless Architecture. Timeout With Serverless computing, there’s a hard 300-second timeout limit. Too complex or long-running functions aren’t good for Serverless, but having a hard timeout makes it impossible to perform certain tasks. A hard limit on this time makes Serverless unusable for applications that have variable execution times, and for certain services which require information from an external source. The clear winner here is Traditional Architecture. Scale Scaling process for Serverless is automatic and seamless, but there is a lack of control or entire absence of control. While automatic scaling is great, it’s difficult not to be able to address and mitigate errors related to new Serverless instances. It’s a tie between Serverless and Traditional Architecture. Functions as a Service (FaaS) FaaS is an implementation of Serverless architectures where engineers can deploy an individual function or a piece of business logic. They start within milliseconds (~100ms for AWS Lambda) and process individual requests within a 300-second timeout imposed by most cloud vendors. Principles of FaaS: Complete management of servers Invocation based billing Event-driven and instantaneously scalable Key properties of FaaS: Independent, server-side, logical functions FaaS are similar to the functions you’re used to writing in programming languages, small, separate, units of logic that take input arguments, operate on the input and return the result. Stateless With Serverless, everything is stateless, you can’t save a file to disk on one execution of your function and expect it to be there at the next. Any two invocations of the same function could run on completely different containers under the hood. Ephemeral FaaS are designed to spin up quickly, do their work and then shut down again. They do not linger unused. As long as the task is performed the underlying containers are scrapped. Event-triggered Although functions can be invoked directly, yet they are usually triggered by events from other cloud services such as HTTP requests, new database entries or inbound message notifications. FaaS are often used and thought of as the glue between services in a cloud environment. Scalable by default With stateless functions multiple containers can be initialised, allowing as many functions to be run (in parallel, if necessary) as needed to continually service all incoming requests. Fully managed by a Cloud vendor AWS Lambda, Azure Functions, IBM OpenWhisk and Google Cloud Functions are most well-known FaaS solutions available. Each offering typically supports a range of languages and runtimes e.g. Node.js, Python, .NET Core, Java. Who this course is for: Developers who want to learn about AWS Lambda and the Serverless Architecture Developers who want to build Serverless APIs using Serverless Framework, AWS and NodeJs 👉 Activate Udemy Coupon 👈 Free Tutorials Udemy Review Real Discount Udemy Free Courses Udemy Coupon Udemy Francais Coupon Udemy gratuit Coursera and Edx ELearningFree Course Free Online Training Udemy Udemy Free Coupons Udemy Free Discount Coupons Udemy Online Course Udemy Online Training 100% FREE Udemy Discount Coupons https://www.couponudemy.com/blog/build-serverless-apis-with-serverless-framework-and-nodejs/
0 notes
Text
Original Post from Talos Security Author:
By Warren Mercer and Paul Rascagneres with contributions from Jungsoo An.
Introduction
Cisco Talos recently discovered a threat actor attempting to take advantage of Americans who may be seeking a job, especially military veterans. The actor, previously identified by Symantec as Tortoiseshell, deployed a website called hxxp://hiremilitaryheroes[.]com that posed as a website to help U.S. military veterans find jobs. The URL is strikingly close to the legitimate service from the U.S. Chamber of Commerce, https://www.hiringourheroes.org. The site prompted users to download an app, which was actually a malware downloader, deploying malicious spying tools and other malware.
This is just the latest actions by Tortoiseshell. Previous research showed that the actor was behind an attacker on an IT provider in Saudi Arabia. For this campaign Talos tracked, Tortoiseshell used the same backdoor that it has in the past, showing that they are relying on some of the same tactics, techniques and procedures (TTPs).
Fake veteran hiring website
The fake website, called “Hire Military Heroes” (hxxp://hiremilitaryheroes[.]com/), which immediately goes after veterans with an image from the movie “Flags of our Fathers.”
The website is only composed of three links to download a desktop app for free. The app is a fake installer. Contrary to standard malware installers, this one does not need to be silent, as the user expects an installation. Here’s a look at the user interface, and the error message is always displayed to suggest something has “stopped” the app from accessing its database.
The progress bar almost fills up entirely, and then displays an error message:
The installer checks if Google is reachable. If not, the installation stops. If it is reachable, the installer downloads two binaries from hxxp://199[.]187[.]208[.]75/MyWS.asmx/GetUpdate?val=UID:
The downloaded binaries are stored in base64. One of the binaries is a tool used to perform a reconnaissance stage on the system and the second is the Remote Administrative Tool. The RAT is executed as a service. The installer installs the service first (for the -install argument) and then stops/starts the service with the command and control (C2) server IP in argument:
If something fails during the installation, an email is sent to the attacker. The credentials are hardcoded in the installer. The email account is ericaclayton2020@gmail[.]com and the error email is sent to marinaparks108@gmail[.]com.
Reconnaissance phase
The downloaded reconnaissance tool is named “bird.exe” on the system and the internal name is Liderc. Liderc is a unique supernatural being of Hungarian folklore. The original form of this creature is a chicken, that would explain the name of the dropped PE on the system, “Bird.exe.”
The purpose is to collect a lot of information on the victim machine:
The attacker retrieves information such as the date, time and drivers. The attacker can then see information on the system, the patch level, the number of processors, the network configuration, the hardware, firmware versions, the domain controller, the name of the admin, the list of the account, etc. This is a significant amount of information relating to a machine and makes the attacker well-prepared to carry out additional attacks. The attacker even gets the size of the screen by using WMI, which is potentially a trick to identify if the system is a sandbox.
All this information is sent by email by using the same emails:
Remote access tool
This actor also deploys a RAT named “IvizTech” on the system. The code and features are similar to the ones outlined by Symantec. The IP is put in argument to the service. The attackers hoped that this would make it impossible to get to the C2, as the installer is needed — you can’t just get there with the RAT itself. This allows an attacker to have a malware that’s more modulable (no need to recompile when you want to update the C2). Requiring the installer also could make it more complicated for researchers to access the C2 and get hands-on analysis of the malware.
The malware has four features:
kill_me: It stops the service and removes the malware
Upload: It downloads a file on the internet
Unzip: It uses PowerShell to unzip and execute code on the system
And finally, the malware can execute a command
Conclusion
This new campaign utilizing the malicious hiring website represents a massive shift for Tortiseshell. This particular attack vector has the potential to allow a large swath of people to become victims of this attack. Americans are quick to give back and support the veteran population. Therefore, it’s this website has a high chance of gaining traction on social media where users could share the link in the hopes of supporting veterans.
At the time of publication, we do not have a method of distribution used, nor do we have proof of this existing in the wild. The level of sophistication is low as the .NET binary used has poor OPSEC capabilities, such as hard-coded credentials, but then other more advanced techniques by making the malware modular and aware that the victim already ran it. There is a possibility that multiple teams from an APT worked on multiple elements of this malware, as we can see certain levels of sophistication existing and various levels of victimology.
Coverage
Intrusion prevention systems such as SNORT® provide an effective tool to detect China Chopper activity due to specific signatures present at the end of each command. In addition to intrusion prevention systems, it is advisable to employ endpoint detection and response tools (EDR) such as Cisco AMP for Endpoints, which gives users the ability to track process invocation and inspect processes. Try AMP for free here.
Additional ways our customers can detect and block these threats are listed below.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Open Source SNORTⓇ Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOCs
Network
hxxp://199[.]187[.]208[.]75/MyWS.asmx/GetUpdate?val=H7ddew3rfJid97fer374887sdnJDgsdte hxxp://66[.]42[.]78[.]193/response/ hxxp://66[.]42[.]78[.]193/statement/ hxxp://hiremilitaryheroes[.]com/
Samples
Installers:
c121f97a43f4613d0a29f31ef2e307337fa0f6d4f4eee651ee4f41a3df24b6b5 2a9589538c563c006eaf4f9217a192e8a34a1b371a31c61330ce2b396b67fd10 55b0708fed0684ce8fd038d4701cc321fe7b81def7f1b523acc46b6f9774cb7b
Reconnaissance PE:
ec71068481c29571122b2f6db1f8dc3b08d919a7f710f4829a07fb4195b52fac
RAT:
51d186c16cc609ddb67bd4f3ecd09ef3566cb04894f0496f7b01f356ae260424
Additional IOCs related to this actor
41db45b0c51b98713bc526452eef26074d034b2c9ec159b44528ad4735d14f4a 78e1f53730ae265a7eb00b65fbb1304bbe4328ee5b7f7ac51799f19584b8b9d4 46873290f58c25845b21ce7e560eae1b1d89000e887c2ff2976d931672390dd8 f31b5e14314388903a32eaa68357b8a5d07cbe6731b0bd97d2ee33ac67ea8817 f1c05ff306e941322a38fffb21dfdb5f81c42a00a118217b9d4e9807743d7275 1848f51d946fa8b348db8ef945a1ebff33ff76803ad26dfd175d9ea2aa56c7d0 ed150d9f6e12b6d669bcede3b7dc2026b7161f875edf26c93296e8c6e99152d5 2682328bde4c91637e88201eda5f5c400a3b3c0bdb87438d35660494feff55cf e82a08f1514ccf38b3ae6b79e67d7605cb20b8377206fbdc44ddadfb06ae4d0d
185[.]43[.]108[.]134 162[.]220[.]55[.]249
Spreadme[.]international
“You rock” installer snippet:
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: How Tortoiseshell created a fake veteran hiring website to host malware Original Post from Talos Security Author: By Warren Mercer and Paul Rascagneres with contributions from Jungsoo An…
0 notes
Text
The Good and the Bad of Java Programming
There are not many technologies that can brag about staying relevant for more than 20 years. But this year, Java was voted the 5th most popular technology, eclipsed only by undisputed leaders JavaScript, HTML, CSS, and SQL. While it’s 18th on the list of most loved in the same StackOverflow survey, it’s also down the list in its most-dreaded ranking. Today, we unravel the many successes and challenges of Java — the time-honored technology with the iconic steaming cup-of-coffee logo, a language near and dear to many programmers' hearts.
What Is Java Programming: History and Impact
Java is a general-purpose programming language that follows the object-oriented programming paradigm and the "Write Once, Run Anywhere" approach. Java is used for desktop, web, mobile, and enterprise applications. You can out find out more about it here:
Java downloads
Java documentation
Oracle Java community
JavaWorld — popular portal for all things Java
JavaRanch — forums for Java developers
Java is not only a language but an ecosystem of tools covering almost everything you may need for Java development. This includes:
Java Development Kit (JDK) – with that and a standard Notebook app, you can write and run/compile Java code.
Java Runtime Environment (JRE) — this is a software distribution tool containing a stand-alone Java Virtual Machine, the Java standard library (Java Class Library), and a configuration tool.
Integrated Development Environment (IDE) — this is a set of tools that help you run, edit, and compile your code. IntelliJ IDEA, Eclipse, and NetBeans are the most popular amongst them.
Java can be found anywhere you look. It’s the primary language for Android development. You will find it in web applications, governmental websites, and big data technologies, such as Hadoop and Apache Storm. And, it’s also a classic choice for scientific projects, especially natural language processing. Java was dominating mobile even in pre-smartphone days. The first mobile games in the early 2000s were mostly made in Java. So, it’s fair to say that Java, thanks to its long history, has earned its place in the Programming Hall of Fame. TIOBE index, one of the most reputable programming rankings in the world, uses search engine results for calculation. Despite the growing popularity of Go and Python, Java has remained at the top of the list for more than a decade.
TIOBE Index data as of August, 2018
It all started in the early 1990s, when the Sun Microsystems team began developing a better version of C++ that was easily portable, novice-friendly, and enabled with automated memory management. The research resulted in the creation of an altogether new language, and the name was picked from dozens of others yelled out in the meeting room. Today, the logo of a steaming coffee cup is the silent, universally recognizable symbol of programming. And, it’s no longer clear what came first — the programmers’ obsession with caffeine or associations with Java, which are now synonymous with coffee.
the evolution of java logosThese are just some of the changes Java introduced to the programming world:
Flexibility. Java proved that C’s procedural, manually-allocated, and platform-dependent code wasn’t the be-all and end-all. Thanks to Java, more people started adopting object-oriented programming, a commonly-accepted method today.
Applets. In the years before JavaScript, Java introduced applets, small web programs that provided interactive elements, especially useful for visualization and teaching. Although they were never used for anything more than simple animations, it’s what captured the attention of many programmers and paved the road for the development of HTML5, Flash, and, of course, JavaScript.
Test-driven development. With Java, TDD was no longer an experimental practice, but the standard way to develop software. The introduction of JUnit in 2000 is considered one of Java’s biggest contributions.
Benefits of Programming in Java
Though no longer the only officially supported language for Android development and, of course, far from the only choice for web programming, Java keeps pace with the alternatives. And, since that’s not only thanks to its respectable age, let’s explore some of the advantages Java has to offer.
Object-Oriented Programming
Java embraces object-oriented programming (OOP), a coding concept in which you not only define the type of data and its structure, but also the set of functions applied to it. This way, your data structure becomes an object that can now be manipulated to create relationships between different objects.
In contrast to another approach — procedural programming — where you have to follow a sequence of instructions using variables and functions, OOP allows you to group these variables and functions by context, thus, labeling them and referring to functions in the context of each specific object.
Comparing procedural programming and object-oriented programming
Why Is OOP an Advantage?
You can easily reuse objects in other programs
It prevents errors by having objects hide some information that shouldn’t be easily accessed
It makes programs more organized and pre-planned, even the bigger ones
It offers simple maintenance and legacy code modernization
High-Level Language With Simple Syntax and a Mild Learning Curve
Java is a high-level language, meaning that it closely resembles the human language. In contrast to low-level languages that resemble machine code, high-level languages have to be converted using compilers or interpreters. This simplifies development, making the language easier to write, read, and maintain.
Writing Hello World in Java
Java derived its syntax (set of rules and structure used by programmers) from C++, which is why you will notice that it closely resembles C code. However, it’s much simpler, allowing beginners to learn the technology faster and code more effectively to achieve specific results.
Java may not be as beginner-friendly as Python, but any developer with a basic understanding of frameworks, packages, classes, and objects can grasp it pretty soon. It’s straightforward, strongly-typed, and has very strict expectations that soon help guide your thinking in the right direction. Besides, tons of free online tutorials and courses won’t keep a novice helpless.
Standard for Enterprise Computing
Enterprise applications are Java’s greatest asset. It started back in the 90s when organizations began looking for robust programming tools that weren’t C. Java supports a plethora of libraries, which are the building blocks of any enterprise system, that help developers create any function a company may need. The vast talent pool also helps. Java is a language used as an introduction to computer programming in most schools and universities. Besides, its integration capabilities are impressive, as most of the hosting providers support Java. Last but not least, Java is comparatively cheap to maintain, since you don’t have to depend on a specific hardware infrastructure and can run your servers on any type of machine you may have.
Shortage of Security Risks
You may encounter the notion that Java is a secure language, but that’s not entirely true. The language itself doesn’t protect you from vulnerabilities, but some of its features can save you from common security flaws. First, compared to C, Java doesn’t have pointers. A pointer is an object that stores the memory address of another value that can cause unauthorized access to memory. Second, it has a Security Manager, a security policy created for each application where you can specify access rules. This allows you to run Java applications in a “sandbox,” eliminating risks of harm.
Platform-Independency (Write Once, Run Anywhere)
Write Once Run Anywhere (WORA) is a popular programming catchphrase introduced by Sun Microsystems to describe Java’s cross-platform capabilities. It meant you could create a Java program on, let’s say, Windows, compile it to bytecode, and run the application on any other platform that supports a Java Virtual Machine (JVM). In this case, a JVM serves as an abstraction level between the code and the hardware.
How WORA approach works in Java
All major operating systems, including Windows, Mac OS, and Linux, support the JVM. And, unless you’re writing a program that relies mostly on platform-specific features and UI, you can share — maybe not all — a big chunk of bytecode.
Distributed Language for Easy Remote Collaboration
Java was designed as a distributed language meaning that it has an integrated mechanism for sharing data and programs among multiple computers for improved performance and efficiency.
Distributed computing vs parallel computing
Unlike other languages, where you have to use external APIs for distribution, Java offers this technology at its core. Java-specific methodology for distributed computing is called Remote Method Invocation (RMI). Using RMI allows you to bring all Java benefits, such as security, platform-independence, and object-oriented programming, to distributed computing. Apart from that, it also supports Socket Programming and the distribution methodology of CORBA for sharing objects between programs written in different languages.
Automatic Memory Management
Java developers don’t have to worry about manually writing code for memory management tasks, thanks to automatic memory management (AMM), also used in the Swift programming language, and garbage collection, an application that automatically handles allocation and deallocation of memory. What exactly does it mean?
A program’s effectiveness is directly linked to memory. And, memory is limited. By using languages with manual management, developers risk forgetting to allocate memory, resulting in increased memory footprint and lagging. A garbage collector can locate objects that are no longer referenced by your program and remove them. Despite the fact that it affects your program’s CPU, you can reduce or prevent it with smart optimization and tuning.
Multithreading
In programming, a thread is the smallest unit of processing. To maximize utilization of CPU time, Java allows you to run these threads simultaneously — in a process called multithreading.
Threads share the same memory area, so switching between them takes little time. They are also independent, so if one thread faces exception, it doesn’t affect other threads. This is especially useful for gaming and animation-heavy programs.
multithreading
Stability and Massive Community
Java has survived to a respectable age, thanks to the community, Oracle’s support, and the cornucopia of applications and languages that keep running on JVM. Besides, new versions of Java are regularly released with new, interesting features.
Java’s developer community is also unmatched. About 45 percent of StackOverflow 2018 survey respondents use Java. It has an extremely large ecosystem of well-tested libraries and frameworks for any use case. Java is most likely to be one of the first languages beginning developers encounter in their studies, as there are 1000+ Java-related courses on Udemy and 300+ on Coursera.
Drawbacks of Programming in Java
Here are the cons you want to know before writing your next project in Java.
Paid Commercial LicenseOracle recently announced that they will start charging Java SE 8 for “business, commercial, or production” use starting in 2019. To get all new updates and bug fixes, you’ll need to pay by the number of users or per processor.
Today, the current version of Java is free and available for redistribution for general purpose computing. To prepare for the change, each company has to evaluate how much of Java they use and seek an alternative technology if the price upgrade promises to be too painful.
Poor Performance
Any high-level language has to deal with poor performance due to the compilation and abstraction level of a virtual machine. However, it’s not the only reason for Java’s often criticized speed. Take garbage collector, a useful feature that unfortunately can lead to significant performance problems if it takes more than 20 percent of CPU time. Bad caching configuration can also cause excessive memory and garbage collection usage. There are also thread deadlocks that happen when several threads are trying to access the same resource, and — every Java developer’s nightmare — out-of-memory errors. Although each of these problems can be prevented with skillful planning, they do add up and can cause different volumes of damage.
Far From a Native Look and Feel on the Desktop
To create a program’s graphical user interface (GUI), developers use different language-specific tools. Thus, for Android apps, there’s Android Studio that helps create apps that look and feel native. However, when it comes to desktop UI, Java noticeably lacks.
There are a few GUI builders Java programmers can choose from: Swing, SWT, JavaFX, JSF being the most popular. Swing is an old-but-reliable, cross-platform, and already-integrated GUI builder with various Java IDEs, including Eclipse and NetBeans. But, unless you’re using templates, you’ll notice interface inconsistencies. SWT uses native components, but it’s not suitable for complicated UI. JavaFX is clean and modern-looking, but it’s not very mature. Overall, choosing a good fit for your GUI building on Java requires additional research.
Verbose and Complex Code
When the code is verbose, it means it uses too many words. While it may seem an advantage when you’re trying to understand the language, long, over-complicated sentences make code less readable and scannable. By trying to emulate English, many high-level languages tend to make too much noise. Java, created to tone down the unapproachable C++, forces programmers to type exactly what they mean, which makes the language more transparent to non-experts but, unfortunately, less compact.
If we compare Java to its rival Python, we can see how clear Python code appears — it doesn’t require semicolons and uses “and,” “or,” and “not” as operators instead of Java’s “&&,” “||,” and “!” Generally, Python has fewer bells and whistles, such as parentheses or curly braces.
Conclusion: Where Is Java Used?
Most organizations use Java in one way or another. A wide range of use cases makes these applications almost invisible, which is why the question “where to use Java” is often raised. To finish our overview, let’s see which domains can be covered by Java:
Android apps. Despite Kotlin’s invasive growth, Java is still the de facto language for Android apps, which automatically turns a big pool of Java developers into Android programmers. While Android uses Android SDK instead of JDK, the code is still written in Java.
Software products. Apart from already-mentioned Hadoop and Apache Storm, Java was used to create Eclipse, OpenOffice, Gmail, Atlassian, and more.
Finance programs. Being one of the most demanded language skills in the financial industry, Java is used both on the server- and client-side to build reliable, fast, and simple websites. It’s also a preferred language for data simulations and modeling.
Point of sale systems. Many businesses use Java to create PoS systems, as they usually require platform-independency and a vast talent pool.
Trading applications. Murex, a popular bank management program for front and back connectivity, is written in Java.
Big data programs. Hadoop is written in Java. Scala, Kafka, and Spark use JVM. Also, Java gives you access to tons of tried-and-tested libraries, debuggers, and monitoring tools.[Source]-https://dzone.com/articles/the-good-and-the-bad-of-java-programming
We provide best Java Courses in Mumbai, navi mumbai. We have industry experienced trainers and provide hands on practice. Basic to advanced modules are covered in training sessions.
#Java Classes in Vashi#Java Classes in Thane#Java Certification Course in Thane#Java Courses in Mumbai#Java Training in Mumbai
0 notes
Text
New Job has been published on Best Jobs In Malta
New Post has been published on http://bestjobsinmalta.com/job/betting-connections-573-director-of-software-development-in-malta-2/
Director of Software Development in Malta
Reporting to the VP of Implementations, the role of the Director of Software Development is to coordinate and manage the software development activities of the software development team as well as the overall direction of the department and all personnel within the department. He/she is responsible for the development and delivery of enterprise scale, high throughput and transactional web based systems built using the latest technologies.
Responsibilities
Team and Project Management Collaborates with the Software Architecture, Project Management, Software Operations, Quality Assurance and Business Planning departments to support the execution of projects in an Agile/SCRUM environment Oversees and manages projects and team assignments to ensure that all projects are managed to plan. Oversees the development lifecycle to ensure that all development standards and best practices are adhered to. Supervises work by development teams to ensure that all project deliverables meet release criteria established by the Business Planning department. Leads and manages internal and external project resources across organizational lines to ensure all projects are completed within their allocated times. Provides a central point of reference for development teams with regards to projects and procedures so as to ensure development teams fully understand their project and its boundaries as well as ensuring the successful integration of different projects. Participates in the performance management and recruitment process to ensure that the required skill sets and behavioural competencies are added to the team. Oversees team productivity and where necessary implements initiatives to improve productivity matters and team motivation. · Mentors and develops team leads and developers, nurtures leadership and maintains a positive and productive environment. · Ensures that staffing levels and expertise meet the requirements of current and future projects.
Software Practices Participates in the discovery, management and reporting of all significant technical issues and risks so as to ensure that the Software Architecture and Software Operations Teams are kept abreast at all times on all development projects. Participates in the analysis and management of critical technical design issues so as to improve project design. Provides ideas for enhancements to existing code in order to improve coding practices. Supports new business development initiatives through research of emerging standards and prototyping of trial systems. Assists development teams with their respective responsibilities as needed to assist in the development lifecycle. Researches development tools so as to facilitate the design and development process. Communication Works to maintain and support the working culture to maintain team motivation and employee satisfaction. Participates and conducts regular status meetings with the development teams and with superiors so as to assure clarity of project status and progress. Interacts with relevant stakeholders so as to ensure they are up to speed on all ongoing development projects, aware of system changes and/or updating of documentation. · Interacts with product owners, project managers and other stake holders to ensure that they are kept informed of project progress, giving adequate notification of any deviation from agreed timelines, system changes and/or updating of documentation · Interface with peers across the organization to ensure that software products are well understood and that deliverables can be tested and deployed in a timely manner. · Communicates effectively with peers and executives in other locations and time zones to quickly resolve impediments and make strategic decisions regarding projects
Requirements
Must have worked in a technical leadership role responsible for large teams of over 15 people over multiple locations for at least 4 years. Possess a Degree in Computer Science or related discipline. Understanding of Continuous Implementation/Continuous Deployment technologies and their role in the development lifecycle Exceptional business and technical knowledge. Driven, creative, results oriented with the ability to motivate the team through a shared sense of purpose and vision. Able to manage concurrent projects and abide to tight deadlines. Proficient with programming languages including Java, C, C++, JavaScript, HTML and technology suites such as Apache Tomcat, JQuery and the Spring framework technologies (Core, MVC, Integration, ORM). Knowledge of the full software development lifecycle, software development methodologies (Agile, Iterative, XP etc.), MS Project, version control systems, bug tracking systems and their use. Understanding of networking technologies including LAN/WAN, switches, and load balancers. Understanding of Cloud based services and virtualization systems such as VMware, XEN, Amazon AWS. Knowledge and understanding of remote invocation technologies (RMI, Spring HTTP Invoker, interfacing with REST APIs). Experience in building mission critical distributed software systems that can manage high volume traffic and which are highly available. Awareness of Open Source community solutions and 3rd party solutions in the marketplace. Ability to communicate technical issues to non-technical people in business language. Experience with Linux and MS Windows operating systems. Experience with database systems; preferably MySQL. Proficiency and fluency in written and spoken English. If interested, please send your CV to [email protected]
0 notes