#router exploiting
Explore tagged Tumblr posts
Text
I spent like the last 3 and half hours claiming and sending event mons into Pokemon Bank and then Pokemon Home, including some of the Gen 5 event mons through the DNA exploit guh
#tho gen 5 dns exploit is annoying bc it usually tries to shove the same 5 or so event mons in your face#I got like. 9 or 10 of em before giving up#and I still need to try the gen 4 dns exploit since we currently have a 2.4 ghz router instead of the 5g one we had#and all the event Pokemon that I could find between oras ans USUM bleh
6 notes
·
View notes
Text


found this and couldn't reblog so I'm reposting

image id:
first image: two-part meme of joey from friends. first part is a picture of him smiling at something out of frame, captioned "The hotel's free WiFi is really fast". second part is him staring wide eyed in horror, captioned "Your IP address starts with 172.16.42.x".
second image: lain from the anime "serial experiments lain" sitting in a chair in a dim room, in front of a glowing computer screen, and smiling at the camera. the text boxes in the image say:
Hey, guys. Lain Iwakura here to explain the joke.
You see, when a computer like your laptop or smartphone connects to wifi, the router assigns it a "local IP address" to distinguish it from other machines on the network.
Most routers use IPv4 for this, where an IP address is four numbers separated by periods. The first two or three numbers of your local IP address are usually the same for all machines on the LAN, and the most common schemas for local IP addresses are 192.168.0.x or 10.0.0.x. Those are just common defaults - they can be set to anything in the router's configuration.
The address schema 172.16.42.x is not a common default for a normal router. It is the default for a device called a "WiFi Pineapple", which is a hacking tool primarily intended for "pentesting", i.e. finding exploitable vulnerabilities in a computing or networking system. The WiFi Pineapple acts as a router from the perspective of the computers on the local network, but a malicious actor can use it to passively scan those computers for vulnerabilities, and can even spy on network traffic going through it. Thus, the joke is that the person in the hotel, finding that their local IP address is under 172.16.42.x., realizes to their horror that the hotel's LAN has been pwned by a (likely malicious) rogue access point, possibly causing their computer to be cracked and their sensitive information to be stolen by cybercriminals. In light of this breach, their panic is understandable! Always keep your software up to date and never connect to a suspicious or unsecured wifi network!
/end id
61 notes
·
View notes
Text
Dear comrades, hermits, and those who stumbled here thinking this was an open-mic poetry slam,
We assemble today to bid a theatrical adieu to Jacques Camatte—the French theorist who didn’t just spit in the face of capitalism but mooned the entire industrial age and told it to get a life. Jacques, you’ve finally fled this soulless machine of a world for a realm where there’s no stock exchange, no algorithms, and—dare we hope?—no PowerPoint presentations. May you rest in a meadow, far from the hum of servers, or at least haunt us with a scathing pamphlet from the beyond.
Jacques Camatte was a rebel with a typewriter and a grudge. He started as a Marxist firestarter, rubbing elbows with Italy’s radical left, churning out works like Capital and Community and The Wandering of Humanity—texts so heavy they could double as gym equipment. But Jacques wasn’t here for half-measures. Marxism? Too factory-friendly. Progress? A scam. By the time he hit his primitivist phase, he’d gone full feral philosopher, declaring that civilization itself was the enemy. Forget unions; Jacques wanted us to ditch cities, tractors, and probably socks, dreaming of a return to communal tribes where we’d trade manifestos for acorns. Picture him in his French countryside hideout, squinting at passing mopeds like they were capitalist sleeper agents, plotting his grand escape to a pre-industrial utopia.
Now, you’ve asked: was Jacques sipping tea with Martin Heidegger’s critique? You know, the German philosopher who brooded over Being, stared into the void, and called technology a soul-crushing “enframing” of existence? There’s no smoking gun in Camatte’s bibliography with “Heidegger, M., 1954” scrawled in the margins, but let’s not kid ourselves. Jacques was a theory sponge, soaking up every critique of modernity’s shiny lies. Heidegger’s The Question Concerning Technology—where he warns that tech reduces nature and humans to mere “standing-reserve” for exploitation—would’ve had Jacques nodding so hard his beret fell off. Both men looked at smokestacks and saw shackles; both mourned a world stripped of mystery by gears and greed. Camatte’s primitivist turn, with its call to ditch the industrial grind for a life in tune with nature, smells like it could’ve been scribbled in the Black Forest after a long chat with Heidegger over schnapps. Did they ever “meet” on the page? Maybe not directly, but their ideas were pen pals, swapping postcards about the death of authenticity.
Jacques’ legacy is a glorious middle finger to the modern world. He didn’t just predict capitalism’s collapse; he looked at our skyscrapers, our spreadsheets, our electric toothbrushes, and said, “Nope, I’m out—give me a cave and some good vibes.” And we, in our infinite wisdom, responded by inventing cryptocurrency. Sorry, Jacques, we tried. Your spirit lives on in every off-grid yurt, every anarchist bookfair, every hipster who buys a typewriter “ironically.” You weren’t just a theorist; you were a one-man protest against anything with a plug.
As you ascend to that unalienated, tech-free commune in the cosmos, dear Jacques, know that you’ve left us a Molotov cocktail of ideas and a dream of a world without barcodes. May you find a Heideggerian paradise where Being is unconcealed, technology is banished, and the only “enframing” is a nice wooden picture frame for your manifestos. May the angels quake at your critiques, and may the gods panic when you start debunking their Wi-Fi routers.
Farewell, you magnificent crank. The revolution will be handwoven, or it won’t be at all.
With a smirk and a salute,
[On Behalf of the Proletariat, Still Googling “What Is Enframing
8 notes
·
View notes
Text
how to connect to wi-fi services in pokemon gen 4 (DPPT/HGSS)
it's still possible to access the wi-fi services of the gen 4 games after the official shutdown of nintendo's wii/ds wi-fi in 2013 due to fan efforts by changing your DNS settings in-game - this is called the DNS exploit. this is popularly used in gen 5 which really has no complications, but in gen 4 it's a bit more complicated because the games are So old that they can't connect to the internet through modern routers due to fancy modern internet encryption. the connection either needs to have no password, or have WEP encryption, which most modern routers do not support. i had some people asking me how to do this so here's a post lol
first, it should be noted i use the pkmnclassic service, and i think you should too. this gives you access to old mystery gifts as well as pretty much every other wi-fi feature. their website also allows you to view pokemon currently uploaded to either gen 4 or 5's GTS through your browser. once you get your wi-fi set up properly, connecting to the internet will be easy, but that setup comes first. below i am going to list all the options i am currently aware of and able to explain
option 1 - phone hotspot (easy/convenient, doesn't work for every type of phone)
some phone hotspots are able to use old WEP type encryption, or be password-less. if you have access to a phone hotspot, it's worth taking off the password if it lets you and trying to connect to the gen 4 wi-fi with it before trying any other method, since if it works it's super convenient, just turn on the hotspot any time you want to do something online in gen 4 and turn it back off when you're done. unfortunately this depends on the type of phone and what OS its on and i don't have a list of what phones or OSes are compatible, so good luck lol. mine personally is not, and i have a fully updated iphone
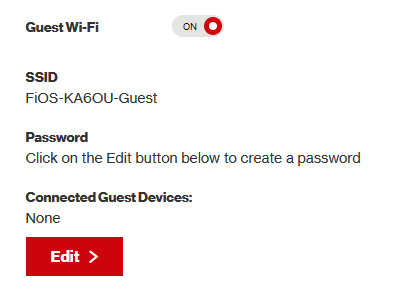
option 2 - guest wi-fi (a little less convenient but still easy if you have access to router settings)
in the same vein as phone hotspots, guest wi-fi hotspots can also work, and this is what i personally use myself. the catch is you have to have access to your router settings, so if you're a young person using a parents' router without access to those or some other situation like that, you may have to ask for assistance every time you want to turn this on/off, which could be a dealbreaker for some unfortunately. but if you're able to do that, simply make your guest wi-fi password-less and turn it on when you want to connect to gen 4 wi-fi and turn it back off when you're done. since these settings pages are so different per internet provider, i can't really give a guide on how to do that here, though mine through verizon fios is pretty straightforward. some guest wi-fi may not work for this but i think most should
option 3 - use an old router that supports WEP encryption (probably inaccessible for most, but only has to be set up once and then you're done)
i've done this in the past but i had my dad's help with the process, i cannot walk you through buying an old router lol. but yes if you purchase an old router and set that up you can have password protected gen 4 wi-fi permanently
option 4 - save backup + emulation through melonds (works pretty much 100% of the time if you have a hacked 3DS and some sort of PC)
MelonDS is a really great DS emulator that you can find here for windows/linux/mac: https://melonds.kuribo64.net/downloads.php
the basic idea is that you can backup your save file/game with a hacked 3DS using Checkpoint or TWLSaveTool (outside the scope of this guide but this is easy to do and you can walk through the steps here) and then run it through melonds, which can bypass all this WEP/encryption hell for you and simply connect to the internet. of course this is not very convenient if you have to constantly back up your saves to do wi-fi stuff but it's better than nothing if you have no other option.
unfortunately setting up the wi-fi can be a pain, and you also need DS BIOS files to run everything properly, which i cannot provide myself for legal reasons but they uh... aren't that hard to find lol, and you can back them up from an actual DS if you have access to the necessary tools for that.
if you use a windows PC, feel free to use my version of melonds which already has all the wifi shit set up, you'll just need to provide your own bios files under emu settings (it's a bit old but it works great for this purpose): https://drive.google.com/file/d/1DQotaqFuBwXz1KYdQWiwxghtn3faLgj-/view?usp=sharing
edit: just found out right after posting this that the most recent version of melonds might work out the box without having to do any particular wi-fi setup? so feel free to try it instead of my version if you like

if you are using linux/mac or don't want to use my version, you'll have to use the melonDS FAQ/google to figure it out, i'm sorry!
by the way yes, this means even if you don't have a gen 4 cart and solely play over emulator, you can trade/battle/etc with people who are playing on DS - they connect to the same servers!
okay and NOW once you have one of those options set up, you can actually connect to wi-fi in game by doing the following:
(these screencaps are from my capture card, i am doing this on an actual DS, but you can also do this with melonds if you're using that option)
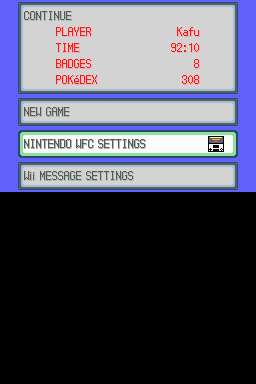
step 1: navigate to "NINTENDO WFC SETTINGS" in the menu where you press continue on your save file, in-game. in gen 4 you need to do it here and not in your DS settings.
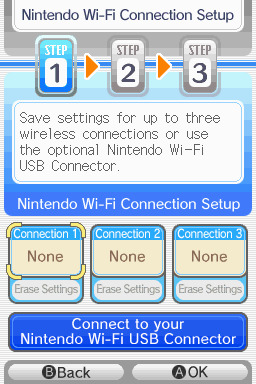
step 2: tap "Nintendo Wi-Fi Connection Settings" and pick any of the three connections here to start the set-up. if you already have some here, i'd click "erase settings" underneath to start from scratch.

step 3: search for an access point and pick your desired access point from the list that comes up, and put in a password if needed (this assumes you have set up your wifi properly at this point)
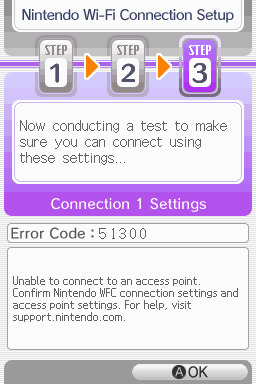
step 4: it will attempt a connection to the internet, and may or may not throw an error. regardless, the error doesn't really matter, you can just hit "OK" whether it's successful or not

step 5: go back into your new connection (the box that previously said "None" should now say "Ready") and scroll down until you see the option "Auto-obtain DNS" - change this to "No"
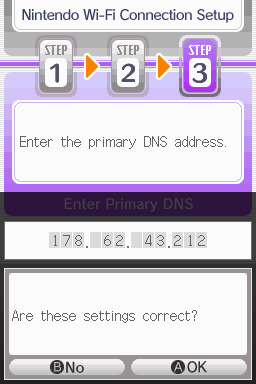
step 6: change the primary DNS to pkmnclassic's DNS, which is 178.62.43.212 - in layman's terms this will essentially let you connect to their servers instead of nintendo's, which are obviously down. as for the secondary DNS, either leave it at 0.0.0.0 or change it to the same DNS as the primary
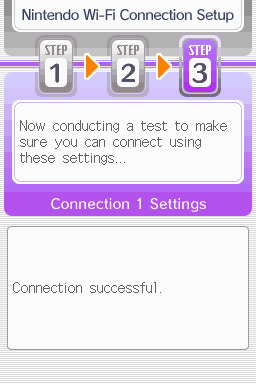
step 7: now would be a good time for a connection test. tap "Test Connection" in the top right. there should be a successful connection. assuming there is a successful connection, congrats! save your settings and enter your game as normal. you'll need to go to the basement of any pokemon center and pick up your pal pad, then try entering the wi-fi club (middle NPC at the counter) to test it in-game and get your friend code.
if there isn't, try a few more times or get closer to your access point - sometimes it's not you, the service can just occasionally be spotty. if you keep getting errors, you can use this site to look up what the error code might mean. if you still can't solve the issue, you may have to try a different method of connection as listed above.
sorry i couldn't be more in depth but frankly i'm not an expert on this stuff either, i'm just doing my best. there are a couple other options for doing this, like taking the password off your modern home wi-fi, or bridging your connection to an old laptop/computer, but the first is particularly dangerous so i didn't want to include it in the list and the second is completely out of my league, i just know people have done it before
good luck feel free to ask questions but no promises i'll have answers. if you need troubleshooting help i'd recommend pkmnclassic's discord over me, they have channels for that stuff (yes i hate troubleshooting stuff moving to discord and not forums as much as the rest of you but it can't be helped lol)
81 notes
·
View notes
Text
Holy fuck these ads are getting worse with ads for alcohol and the fps games are actually triggering. So many gambling ads?? And exploitative games!? Horny cartoon erotica??? I’ve been reporting the gun and alcohol related ads but I finally paid for tumblr premium. I’m going to talk to my roommate about putting an ad blocker on the router because WTF this is doing brain damage to see so many ads.
6 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text
Critical Exploit in MediaTek Wi-Fi Chipsets: Zero-Click Vulnerability
https://blog.sonicwall.com/en-us/2024/09/critical-exploit-in-mediatek-wi-fi-chipsets-zero-click-vulnerability-cve-2024-20017-threatens-routers-and-smartphones/
2 notes
·
View notes
Text
Major Security Vulnerabilities Patched in Cox Modems

Cybersecurity researcher Sam Curry has recently uncovered a series of critical vulnerabilities in the systems of Cox Communications, a major telecommunications provider. These vulnerabilities could have allowed malicious actors to remotely take control of millions of modems used by Cox's customers, posing a significant risk to their privacy and security.
Bypassing Authorization and Gaining Elevated Privileges
Curry's analysis revealed an API vulnerability that allowed bypassing authorization checks, potentially enabling an unauthenticated attacker to gain the same privileges as Cox's technical support team. This exploit could have allowed attackers to overwrite configuration settings, access the routers, and execute commands on the affected devices. According to the researcher, "This series of vulnerabilities demonstrated a way in which a fully external attacker with no prerequisites could've executed commands and modified the settings of millions of modems, accessed any business customer's PII, and gained essentially the same permissions of an ISP support team."
Potential Attack Scenarios and Risks
In a theoretical attack scenario outlined by Curry, a malicious actor could have searched for a targeted Cox business user through the exposed API using personal information such as their name, email address, phone number, or account number. Once identified, the attacker could have obtained additional information from the targeted user's account, including their Wi-Fi password. With this access, the attacker could have executed arbitrary commands, updated device settings, or take over accounts, potentially compromising sensitive data and personal information.
Responsible Disclosure and Prompt Patching
Curry responsibly reported the vulnerabilities to Cox Communications on March 4, and the company took swift action to prevent exploitation by the next day. Cox also informed the researcher that it conducted a comprehensive security review following the report. Notably, Cox found no evidence of the vulnerability being exploited in the wild for malicious purposes, indicating that the potential risks were mitigated before any significant damage occurred.
Origins of the Attack and Unanswered Questions
The origin of the attack on Curry's modem appears to be from an IP address (159.65.76.209) previously used for phishing campaigns, including targeting a South American cybersecurity company. When Curry tried to get a replacement modem from Cox, they required him to turn in the potentially compromised device, preventing further analysis. Curry's traffic was being intercepted and replayed, suggesting the attacker had access to his home network, though the motive for replaying traffic is unclear. The vulnerabilities found in Cox's systems included lack of authentication checks, allowing arbitrary API requests by simply replaying them. Over 700 APIs were exposed. Cox patched the issues after disclosure but found no evidence the specific attack vector was exploited maliciously before 2023, despite Curry's modem being compromised in 2021. The blog aims to highlight supply chain risks between ISPs and customer devices, though Curry's modem may have been hacked through another unrelated method locally. Read the full article
3 notes
·
View notes
Text
This day in history

TONIGHT (June 21) I'm doing an ONLINE READING for the LOCUS AWARDS at 16hPT. On SATURDAY (June 22) I'll be in OAKLAND, CA for a panel (13hPT) and a keynote (18hPT) at the LOCUS AWARDS.

#20yrsago Tunneling ssh over DNS https://web.archive.org/web/20040916193409/http://www.doxpara.com/bo2004.ppt
#10yrsago Open Wireless Movement’s router OS will let you securely share your Internet with the world https://arstechnica.com/tech-policy/2014/06/new-router-firmware-safely-opens-your-wi-fi-network-to-strangers/
#10yrsago Steve Wozniak wants you to support Mayday.US and get money out of politics https://www.youtube.com/watch?v=ZoZ-tJiwBvc
#10yrsago Gangs run mass-scale romance cons with phished dating-site logins https://www.netcraft.com/blog/criminals-launch-mass-phishing-attacks-against-online-dating-sites/
#10yrsago Greenhouse: browser plugin that automatically annotates politicians’ names with their funders https://allaregreen.us
#10yrsago Judy Blume: parents shouldn’t worry about what their kids are reading https://www.telegraph.co.uk/culture/hay-festival/10868544/Judy-Blume-Parents-worry-too-much-about-what-children-read.html
#5yrsago Learning from Baltimore’s disaster, Florida city will pay criminals $600,000 to get free of ransomware attack https://apnews.com/article/0762caec21874fc09741abbdec0f78ab
#5yrsago Elizabeth Warren proposes a ban on private prisons and immigration facilities https://medium.com/@teamwarren/ending-private-prisons-and-exploitation-for-profit-cb6dea67e913
#5yrsago Google Maps is still overrun with scammers pretending to be local businesses, and Google’s profiting from them https://tech.slashdot.org/story/19/06/20/1746232/millions-of-business-listings-on-google-maps-are-fake----and-google-profits
#5yrsago America can only go to war against Iran if it reinstates the draft https://www.usatoday.com/story/opinion/2018/05/31/iran-regime-change-american-troops-military-draft-column/656240002/
#5yrsago Independent audit finds Facebook activity has fallen by 20% since Cambridge Analytica https://www.theguardian.com/technology/2019/jun/20/facebook-usage-collapsed-since-scandal-data-shows
#5yrsago Tennessee lawmaker defends operating an unregistered “Christian magic supply” business https://www.tennessean.com/story/news/politics/2019/06/20/matthew-hill-tennessee-house-speaker-christian-magic-supply-business-dock-haley-gospel-magic/1481310001/

Support me this summer on the Clarion Write-A-Thon and help raise money for the Clarion Science Fiction and Fantasy Writers' Workshop!
2 notes
·
View notes
Note
now the question is how much of the mimic knows anything abt personal connections - tiger, router, any actual positive interactions there - bc unless it draws from panther's remnant, those things seemed less likely to be recorded. very ship of theseus.
Mimic!Panther was built and trained on the surviving records of Panther's exploits and methods as a mercenary and the sample record of Panther's Remnant from when the Aftons had him and Router in the underground facility during the UCN Arc, so it has a decent amount to pass as a solo Panther with a working understanding of Router.
The rest, like the personal connections and interactions, he can learn while within Sydney from observing and listening to Alex. The more Alex tries to spark Sydney's memories of the past with references and stories, the more Mimic!Panther can gather to adapt and be more 'complete' compared to Sydney.
A fully complete Panther can never be recovered, but the Mimic can come far closer to Alex's vision of him than Sydney himself could ever be.
2 notes
·
View notes
Text
ID 1: Joey from friends, looking happy, and then very scared. Text next to each expression reads: "The hotel's free wifi is really fast" / "Your IP address starts with 172.16.42.x"
ID 2: Lain from Serial Experiments Lain, sitting at a computer and turned to look at the camera with a smile. Text reads:
"Hey, guys. Lain Iwakura here to explain the joke.
You see, when a computer like your laptop or smartphone connects to wifi, the router assigns it a "local IP address" to distinguish it from other machines on the network.
Most routers use IPv4 for this, where an IP address is four numbers separated by periods. The first two or three numbers of your local IP address are usually the same for all machines on the LAN, and the most common schemas for local IP addresses are 192.168.0.x or 10.0.0.. Those are just common defaults - they can be set to anything in the router's configuration.
The address schema 172.16.42.x is not a common default for a normal router. It is the default for a device called a "WiFi Pineapple", which is a hacking tool primarily intended for "pentesting", i.e. finding exploitable vulnerabilities in a computing or networking system. The WiFi Pineapple acts as a router from the perspective of the computers on the local network, but a malicious actor can use it to passively scan those computers for vulnerabilities, and can even spy on network traffic going through it. Thus, the joke is that the person in the hotel, finding that their local IP address is under 172.16.42., realizes to their horror that the hotel's LAN has been pwned by a (likely malicious rogue access point, possibly causing their computer to be cracked and their sensitive information to be stolen by cyber-criminals. In light of this breach, their panic is understandable! Always keep your software up to date and never connect to a suspicious or unsecured wifi network!"
END ID


136K notes
·
View notes
Text
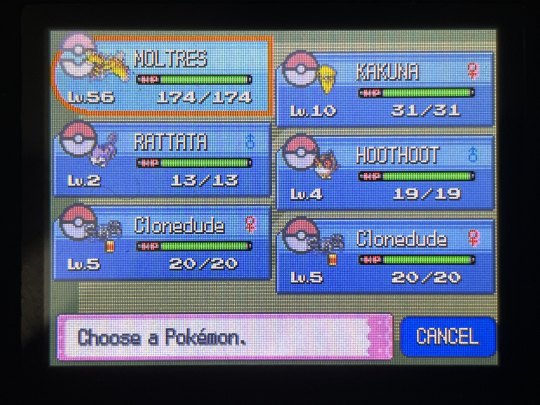
CLONEDUDE HAS BEEN SUCCESSFULLY CLONED!! two of her. gnc icon

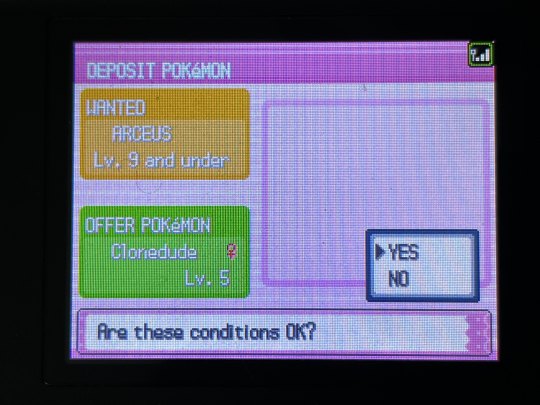

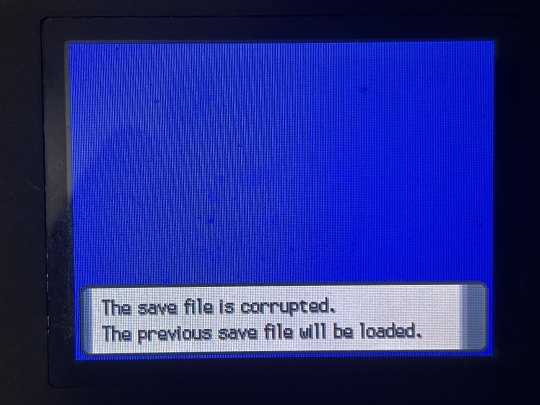
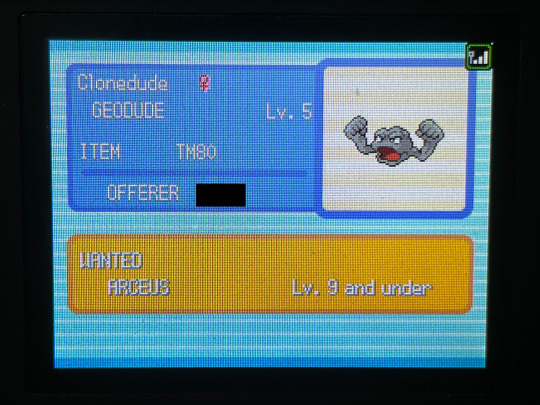
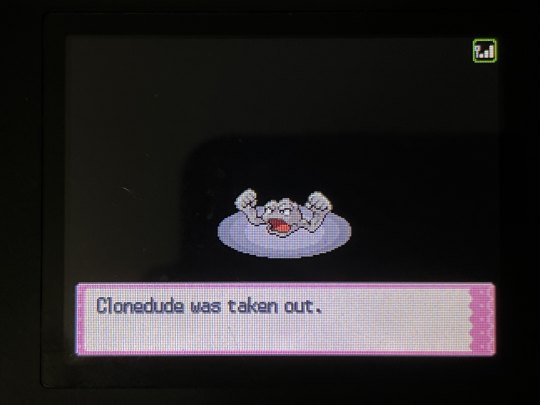
here's some pics of the process since it's not like new pictures of these menus are much of a thing anymore LMAO very few and far between
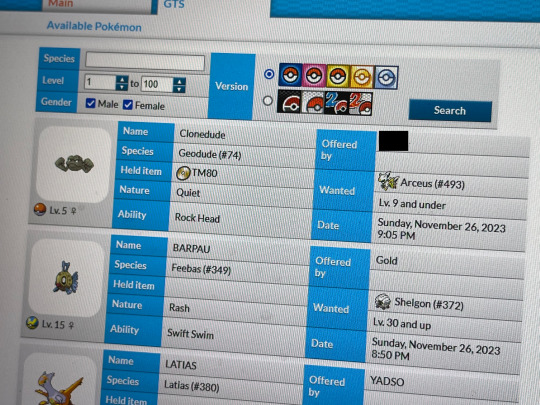
also something that WASN'T a thing back during the original GTS' lifespan: the pkmnclassic GTS viewer LMAO i had to take a pic of my mom's PC screen instead of a normal screencap, i was sitting in her office because the router was being stupid and the signal for the guest wifi i use to connect to the gen 4 DNS exploit wasn't reaching my bedroom. truly the mid 2000s experience, i had to sit in my mom's office to connect to wifi Often SDFKFSD
#kiki was here#kiki.txt#kiki plays games#pt playthrough#the black boxes on the pics r just blocking out my legal name i dont identify with btw sorry#my childhood pearl uses it lol
20 notes
·
View notes
Text
TP-Link Router Flaw CVE-2023-33538 Under Active Exploit, CISA Issues Immediate Alert

Source: https://thehackernews.com/2025/06/tp-link-router-flaw-cve-2023-33538.html
More info: https://www.cisa.gov/news-events/alerts/2025/06/16/cisa-adds-two-known-exploited-vulnerabilities-catalog
2 notes
·
View notes
Text
A sneaky cyber espionage campaign is exploiting IoT devices and home office routers – here's what you need to know
http://securitytc.com/TLW2M5
0 notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes