#socks5proxy
Explore tagged Tumblr posts
Text

Elevating Your Proxy Experience
Unleash the Power of Residential SOCKS5 Proxies for Ultimate Online Freedom!
Immerse yourself in the seamless, secure, and reliable world of VPS Proxies Inc.'s SOCKS5 residential proxies. Experience the internet with unprecedented comfort.
Your online fortress! Our proxies provide military-grade encryption, ensuring your data remains confidential and protected at all times.
Speed meets sophistication! Enjoy swift and uninterrupted browsing, streaming, and downloading with our high-performance residential proxies.
Break through borders effortlessly! Access region-restricted content and explore the web from any corner of the world with ease.
Be a digital ghost! Our SOCKS5 residential proxies offer elite anonymity, making your online presence virtually untraceable.
We redefine reliability. Count on VPS Proxies Inc. for 24/7 uptime, ensuring your online activities are uninterrupted and secure.
ℂ𝕠𝕟𝕥𝕒𝕔𝕥 𝕦𝕤:-: 👉🏻 Web: www.vpsproxies.com 👉 WhatsApp: +44 7477 207609 👉🏻 Telegram: https://t.me/vpsproxiesinc 👉 Gmail: [email protected] 👉🏻 Skype: https://join.skype.com/invite/xl8McjBunrn7
#ResidentialProxies#SOCKS5Proxy#ProxyLife#InternetFreedom#SecureConnections#DigitalPrivacy#OnlineAnonymity#ProxyPower#GlobalAccess#FastAndSecure#WebFreedom#ProxyNetwork#BrowseSecure#AnonymousSurfing#VPSProxies#UnlockTheWeb#ProxySolutions#DigitalFootprint#BrowseWithConfidence#PrivateBrowsing
1 note
·
View note
Video
只屬於你一人的靜態ip,360proxy讓你輕松做電商!#ipaddress #isp #socks5proxy #business
0 notes
Text
What Is A SOCKS5 Proxy And How Are They Used?
The internet is not the place right now that we knew as kids. Sadly, it is not as open and free as it used to be. Nowadays, website blocks, attacks and surveillance are becoming more and more common. In such a place, people have many different reasons to prefer to appear anonymous, and to achieve true anonymity and safety, one needs to take a lot of precautions. Fortunately, we have many tools to protect ourselves on the internet, and one of that is a Socket Secure proxy.
Many of us have heard a lot about SOCKS proxies, but only a few of us fully understand them and their purpose, way of working and the anonymity level they offer. There are many confusions associated with SOCKS proxies, such as the misconception that they are an alternative to VPNs (Virtual Private Network), making people choose the wrong tools and have the wrong sense of protection.
For this reason, we have prepared this article to give you an in-depth look at SOCKS proxies, SOCKS5 proxies and how they are used in order to clear any confusion that you might have.

What Is A SOCKS Proxy?
Basically, SOCKS is an internet protocol, just like HTTPS. However, SOCKS offers a higher level of anonymity to the person using it. When you connect to a SOCKS proxy, it passes your traffic through a third server via TCP (Transmission Control Protocol) and assigns a new IP address to you. Since your IP address has changed, you cannot be located by web hosts. With a different IP address, you are able to get around location based restrictions.
If we compare a SOCKS proxy with a VPN, the VPN has the upper hand as it provides encryption, which is something that SOCKS proxies do not offer. This means that SOCKS proxies don't provide their users with true privacy and the users aren't safe from any kind of attack on public Wi-Fi and government surveillance.
Apart from that, a SOCKS proxy does not work for every application. This means that a user is not always completely safe during his regular browsing.
Although the lack of encryption in a SOCKS proxy makes it less protective, it provides a few benefits as well. The biggest benefit it provides is speed. Because a SOCKS proxy does not encrypt any traffic at all, it costs much less and runs faster as compared to a VPN. In conclusion, because SOCKS proxies do not provide safety by using monitoring, they lie in between HTTP and VPN services.
When you are using a SOCKS proxy, the security it provides depends on a lot of factors, the most important one being its version. SOCKS proxies have two versions; the first one is SOCKS4 and the second one is SOCKS5. Most proxy service providers these days use either SOCKS4 or SOCKS5 proxies to give anonymity and protection to their users.
Of course, there are a few differences between the two types of SOCKS proxies. Because the SOCKS4 version came first, it has fewer features than the SOCKS5 version of SOCKS proxies. This is the reason why the usage of SOCKS5 proxies is much more widespread than SOCKS4 proxies these days.
One of the very important features that a SOCKS4 proxy doesn't have is the support for UDP (User Datagram Protocol) protocol based applications. So a SOCKS4 user cannot use programs that require high speed and more efficiency, such as games. In addition to that, a SOCKS5 proxy can also support Domain Name Resolution and IPv6. As a result, the client of a SOCKS5 proxy can specify a URL instead of an IP address. The SOCKS4a version of SOCKS proxies has this feature as well.
How A SOCKS5 Proxy Is Used?
Because of the various important features of a SOCKS5 proxy, it is very useful for a large proportion of the world population. The most common use of a SOCKS5 proxy is to get around online restrictions. For example, if your ISP (Internet Service Provider) has prevented its clients from accessing a few illegal movie sharing websites, such as The Pirate Bay, a SOCKS5 proxy has the ability to bypass it.
The application of this particular feature is easily found on restricted networks, such as those in schools and offices. It is common for these connections to be monitored and to restrict users from the access to social media, games, etc.
A SOCKS5 proxy is also used to get around regional restrictions. For instance, BBC's iPlayer is only available for IP addresses of the UK. By using a SOCKS5 proxy located in the UK, you can temporarily get a UK IP address, which would allow you to use British T.V. without any restrictions or checking.
The same example can be used for the popular application, Netflix, which offers many more movies and series in the USA as compared to other countries. Therefore, using a SOCKS5 proxy located in a different location as yours can allow you to access more content.
While using their home networks, users have to be really careful and alert. This caution has to be multiplied for some specific activities, such as torrenting. With a SOCKS5 proxy, downloading can be done at higher speeds and the user can feel secure as a protective cover is added on the user, hiding them from copyright holders. There are many BitTorrent clients out there that allow a certain level of encryption when a user is using a SOCKS5 proxy. This strengthens security and prevents further problems.
It is true that the security a SOCKS5 proxy provides is not the same as that of a VPN, but some protection is better than no protection. Also, a SOCKS5 proxy gives its users an obscured connection from only one application on your PC. Therefore, they can enjoy high speed P2P (Peer To Peer) downloads and use location-based services, such as Google Maps, at the same time. The usual download rate for any other online activity stays the same.
#Dedicatedproxy#Residentialproxies#rotatingproxies#VPN#firewall#socks5#socks5proxy#cheapproxy#proxyaqua
0 notes
Video
youtube
【SOCKS5 Proxy2023】Excellent SOCKS5proxy recommended!Cheap,fast and pure!
0 notes
Video
youtube
911S5 Alternative: YiLuProxy: Google Chrome Proxy Settings Tutorial
The video shows Google Chrome proxy settings tutorial with YiLuProxy. YiLuProxy official website: https://www.yiluproxy.org
#chromeproxy #yiluproxy #socks5proxy #chromeproxysettings
1 note
·
View note
Text
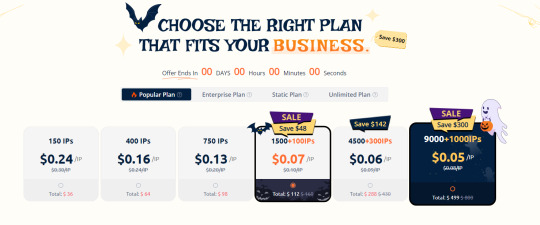
PiaS5 Proxy -Perfect 911s5 Proxy Alternatives
Pia S5 Proxy -Perfect 911s5 Proxy Alternatives
Countdown to Halloween Deals! ! !
$490 off is about to disappear
#911s5#pias5#Socks5proxy#proxyies
0 notes
Text
VPNFILTER
VPNFILTER
On May 25th of 2018, the FBI issued a PSA recommending that “any owner of small office and home office routers” reboot those devices. The reason was because VPNFilter, a sophisticated piece of malware developed by a nation-state, had infected about 500,000 router and NAS devices world-wide. This network of compromised devices created by VPNFilter posed a serious threat to global cyber security, but appeared to be focused primarily on Ukraine.
VPNFilter is an advanced, multi-stage modular malware.
Stage 1 - Once a device is compromised, it reaches out to a domain hosting images with the ip address of the stage-2 command and control (C&C or C2) servers embedded in the EXIF metadata. This stage’s purpose is to gain a persistent foothold on the compromised device.
Stage 2 - After connecting to the C&C servers, stage-2 malware is pushed to the device. Although it does not persist through a reboot, it possesses a number of capabilities such as file collection, command execution, data exfiltration and device management, as well as “self-destruct” capability that renders a device unusable.
Stage 3 - Additional modules act as plugins for the stage-2 malware, providing extra functionality:
1. Additional capabilities that could be leveraged to map networks and exploit endpoint systems that are connected to devices compromised by VPNFilter.
2. Multiple ways for the threat actor to obfuscate and/or encrypt malicious traffic, including communications used for C2 and data exfiltration.
3. Multiple tools that could be utilized to identify additional victims accessible from the actor's foothold on devices compromised by VPNFilter for both lateral movement within a network, as well as to identify new edge devices in other networks of interest to the actor.
4. The capacity to build a distributed network of proxies that could be leveraged in future unrelated attacks to provide a means of obfuscating the true source of attack traffic by making it appear as if the attacks originated from devices previously compromised by VPNFilter.
List of Modules
• packetsniffer - collects all traffic passing through the device
• torify - uses Tor to communicate with Stage 2 Command and Control servers
• ssler - intercepts network traffic and inject malicious code into it without the user's knowledge.
• dstr - Destroys the device when activated
• htpx - Allows for the injection of malicious code into windows executable files during download
• ndbr - Functions as an Secure Shell (SSH) server and network scanner
• netfilter - Denial of Service Module that can block access to sites
• portforwarding - Victims can be redirected to attacker controlled servers
• socks5proxy - Activates a SOCKS5 proxy on compromised devices to obfuscate traffic
• tcpvpn - Establishes a secure Reverse-TCP VPN backdoor on compromised devices
Sources:
https://www.ic3.gov/media/2018/180525.aspx
https://blog.talosintelligence.com/2019/05/one-year-later-vpnfilter-catastrophe.html#more
https://blog.talosintelligence.com/2018/05/VPNFilter.html
https://blog.talosintelligence.com/2018/06/vpnfilter-update.html
https://blog.talosintelligence.com/2018/09/vpnfilter-part-3.html
0 notes