#ubiquiti network design
Text
The Great Autonomous Vehicle Capitulation
Q&A with Peter Barrett
TC: What was the biggest robotics story of 2022?
PB: The Great Autonomous Vehicle Capitulation. Ford and VW abandoning robotaxis are another indication that autonomous vehicles are decades from ubiquity. Autonomous vehicles may be inevitable, but they are certainly not imminent despite lots of very clever people and eye-watering amounts of capital pouring into the domain.
We have had autonomous vehicles driven by neural networks since the ’80s. I think we are about halfway there.
The good news is that in the interim, we do have a mature technology that improves traffic 30% and reduces fatalities at intersections by 90%. It is called a roundabout.
What are your biggest robotics predictions for 2023?
The biggest trend in 2023 will be the realization that robots are best used to amplify people rather than replacing them. Robots as collaborators that work for people in human environments is the best way of exploiting the unique capabilities of both.
How profound of an impact has the pandemic had on robotics?
There are 500,000 unfilled jobs in logistics in the U.S. at the moment. Similar gaps exist in other critical domains, in farming, mining, etc. We need more scalable and practical automation technologies to make people more productive and take on the dull, dirty or dangerous jobs that are otherwise going unfilled.
What under-addressed category deserves more focus from robotics startups and investors?
Life science is yet to have its industrial revolution. Individualized lifesaving therapies (think CAR T) are preposterously expensive, largely due to lack of scalable automation and logistics. Lab operations are stymied by islands of incompatible automation and no common ontologies or data formats, and humans are not integrated into the process. Companies like Artificial are tackling the software layer to orchestrate labs and pharma, but new classes of automation systems are needed to tackle the physical layer.
How will automation impact the workforce of the future?
Human dexterity and cognition will be amplified by strong, trustworthy, collaborative robots that literally do the heavy lifting. As stated above, it is all about amplifying people, not replacing them.
Are home robotics finally having their moment?
The Roomba is over 20 years old and is still the only non-toy robot that has any useful role to play in the home. The simple genius of the original design has been replicated countless times but is rarely improved upon: ask Rodney Brooks about the unwarranted innovation of SLAM versus random bumping.
We still don’t have robots that can cook or clean or be generally useful around the house, largely because we don’t have the cognition or dexterity to do a credible job in unstructured environments. Like the technology gaps that need to be filled to deliver autonomous vehicles, these capabilities will eventually emerge but don’t hold your breath.
What more can/should the U.S. do to foster innovation in the category?
How about a robotics/AI equivalent of the CHIPS Act?
24 notes
·
View notes
Text
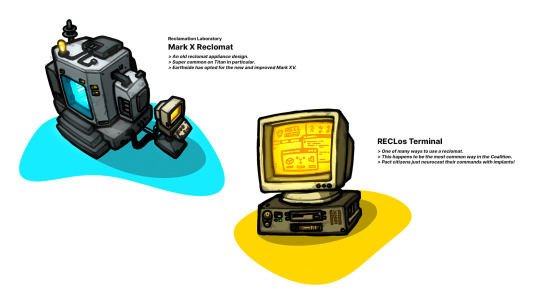
Reclomat
(old post, but still canon)
A reclomat, short for "automatic reclamator", is a fusion-powered recycling appliance commonly found across the Solar System. Reclomats are often found at the heart of colonial facilities, and were affectionately referred to as "redumpsters" by colonists.
Operating a reclomat is pretty simple. By using a linked terminal or network command, a user can trigger the reclomat's breakdown or assembly functions. A primary chamber, lined with yoku-powered microfabrication devices, can tear apart anything that can be shoved into the chamber, and assemble complex structures given the right materials, components, and specification files. Even certain consumables, such as Kinda-Meat and imitation califlower, can be synthesized in some of the more advanced models as long as you don't mind a hint of ozone.
Designed by a team at the Reclamation Laboratory as part of an international cooperation program, the first prototype was unveiled at the Global Technology Conference in 2027. Since then, the design had been replicated in various forms by each spacefaring nation (but typically sticking to the large box with inner chamber format for its ubiquity).
Reclomats were employed heavily during the environmental rehabilitation of Earth, but the technology really proved itself in the extraterrestrial colonies. There, reclomats significantly reduced the need for complicated logistics, enabling colonists to spread out to previously impractical regions. It's one of the cornerstones of interplanetary society - making it possible to transition from the rugged frontier of the early 21st century, to the era of casual space living.
Some popular models include:
Reclamation Laboratory Mark X
Kuzmich Design Bureau KGMr-5
Hikari ETS Ultrascan
20 notes
·
View notes
Text
soo often i will draft like half of a personal/diary type post and then get distracted especially if i'm tipsy and then when i look thru my drafts later it's like, oh i should finish what i was saying/thinking thru there but the tenses are no longer accurate and trying to rework them altars the flow of the post/where i was going with it usually + it's unnecessary outside of feeling weird not to or often i have already completed that thought string through to catharsis anyway and don't feel the need to expend the energy on actually making it readable so they end up just sitting forever ,, example draft from feb 18
tonight at tge bar my friend had stolen a donket kong in a car sculpture in the style of those old wooden dinosaur ones and i reformed it into a variety of increasingly beautiful gundams but each time they asked me like. did you get a photo of that one wgen they saw id dismantled it/had theorised better design bases (swapping legs to arms, etc). i think i have largely forsaken the impulse to turn the moments of my life into content successfully now and it was a bit dejecting tbh like. this is a joyous activity in itself, we should not need to extract further dopamine from it imo. i rly dislike it as an impulse especially just bc like i dislike being [draft end]
i don't remember how that sentence was meant to end even if it's reasonable on its own lol but presumably something about being interrupted or having others take photos of me or the need to like Advertise One's Coolness to a broader network rather than just living ur life for the sake of itself ,, something i have also been thinking abt recently bc of the urban cyber grunge post is how before smartphone ubiquity it was literally like. people didn't carry a camera at all times unless you had a particular interest in photography as an art form like a camera was a separate object you got out/packed for special occasions parties trips and so on ,, i can't say that was better necessarily but certainly i would at least culturally like that to still be the norm
#accidentally just posted this privately while editing it in drafts/trying to scroll down#bc tumblr mobile has drag quick actions on seemingly every random ui element.....#was going to say something else but now i cba-_-
5 notes
·
View notes
Photo

Michel Serrault and Mathieu Kassovitz in Assassin(s) (Mathieu Kassovitz, 1997)
Cast: Michel Serrault, Mathieu Kassovitz, Hélène de Fougerolles, Danièle Lebrun, Léa Drucker, Mehdi Benoufa, Robert Gendru, François Levantal. Screenplay: Nicolas Boukhrief, Mathieu Kassovitz. Cinematography: Pierre Aïm. Production design: Philippe Chiffre. Film editing: Mathieu Kassovitz, Yannick Kergoat. Music: Carter Burwell.
Perhaps no movie since Network (Sidney Lumet, 1976) has sledgehammered television quite so thoroughly as Assassin(s). But where Network took the business of television for its target, Assassin(s) aims at the medium's ubiquity and its desensitizing effect on viewers. It's not a novel point, of course, and even the spin writer-director Mathieu Kassovitz decides to give it -- the effect TV has in creating a culture of violence -- is neither fresh nor unquestioned. The story at the film's center is about an aging professional hit man, Mr. Wagner (Michel Serrault), who takes on a young petty thief, Max (Kassovitz), as his apprentice. It's set in the Parisian banlieus that were the socio-political milieu for Kassovitz's earlier (and much better) film about violence, La Haine (1995). It opens with Mr. Wagner guiding Max into the brutal and entirely gratuitous murder of an elderly man, and then flashes back to bring the story up to a recapitulation of the event -- rubbing our noses in it, so to speak. Max is a layabout and a screwup, but there is a core of reluctance within him that Mr. Wagner is determined to obliterate. Eventually, Max takes on his own protégé, a teenager named Mehdi (Mehdi Benoufa), who is decidedly not reluctant to engage in a little killing, seeing it as just an extension of the video games he plays. Throughout the film, television sets are blaring game shows, commercials, sitcoms, and even nature documentaries in the background, an ironic if sometimes heavy-handed counterpoint to the murders committed by Mr. Wagner, Max, and Mehdi. Kassovitz stages much of the film well, extracting full shock value, and he sometimes embroiders the realism of the story with surreal touches: At one point, when Mr. Wagner is walking away from Max, we see a demonic tail emerge from beneath Wagner's overcoat -- or is it Max, perpetually stoned, who sees this? More effectively, reinforcing Kassovitz's treatment of the effects of television, Mehdi -- who is coming unglued after his first commissioned hit -- watches a TV sitcom about a group of young people that suddenly turns into violent, necrophiliac pornography, accompanied by a laugh track. Kassovitz showed undeniable talent with La Haine, and some of it is on display here. Assassin(s) was booed at the Cannes festival, and has never received a wide commercial release in the United States, but it's something of a fascinating (if often repellent) failure.
1 note
·
View note
Text
Precise Versus Respond - The Right Pick For Your Next Undertaking?

JavaScript systems are extremely common in the improvement commercial center. Such systems are stages which give designs of utilization plan to creating web applications in view of JavaScript.
Structures and libraries for cms development solutions JavaScript are an assortment of capabilities and parts that a software engineer can use in their code. At the point when you contemplate the JavaScript Environment, you'll without a doubt consider Rakish and Respond, as they're two of the most well known front-end structures for web improvement. Yet, how might you pick between the two? Would it be a good idea for you to take a gander at the venture necessities first prior to choosing? Or on the other hand, in the beginning phases, think about its ubiquity and increase time?
A System of JavaScript Libraries gives a predefined code to be utilized while creating projects. Since JavaScript is the most often involved programming language for fostering a site, while focusing on no other durable substitution, the systems worked to help these web applications are likewise a significant number.
JavaScript Libraries furnish you with a variety of tasks, without restricting you to a skeleton, however it implies that you need to fabricate your design without any preparation. Such is the difficulty endeavors face when they approach concluding the innovation that ought to be supporting their Online interfaces. Two of the significant contenders of this contention are AngularJS versus ReactJS. Prior to recruiting top engineers, ensure you know about the advantages of both the dialects.
1. Rakish versus Respond
What is Rakish?
Rakish is a Frontend web structure in light of JavaScript, which is significantly kept up with by Google. Since Rakish is an open source structure, we see a couple of different Networks adding to its turn of events.
HTML is utilized widely for creating static site pages, yet with regards to having a web application and Dynamic pages, HTML is extremely restricting. Rakish JS extends HTML, to work with ease in building single-page web applications. It does as such by expanding the HTML credits with ng-orders which is an 'ng' prefix to the HTML ascribes.
What Is Respond?
Dissimilar to Rakish, Respond JS is a JavaScript library made open source by Facebook in 2013. It was at first executed on the Facebook newsfeed in 2011 and later on the Instagram site in 2012, preceding making open to the general population. Respond Local is a variation of Respond which grants local Android, iOS and UWP improvement with Respond. Respond is utilized for Single-page dynamic web and portable applications.
Respond presents a new prearranging language JSX which utilizes a variation of XML grammar, which makes it more straightforward to work with. Yet, JSX isn't required for Respond and we can utilize the standard JavaScript to code.
Respond is predominantly well known for its idea of Virtual DOM, which strays from the standard DOM and works with quicker refreshes. The most recent variant of Respond is 16.8 delivered on Feb 6, 2019.
2. Distinction Among Rakish And Respond
Size of Utilization
Being a System, Rakish is recommended while building Endeavor Arrangements. The Underlying devices of Rakish make it simpler to insert parts without referring to outer libraries or APIs. With the tweaked elements of TypeScript, it is doable for coding huge scope projects. For big business level cms website development company India applications as the code develops, Typescripts makes it simple to be coordinated in modules thus working with better administration.
Respond is more helpful while creating lightweight applications, where each single page application can be made physically without the utilization of any standard bundles. Involving Precise would be a pointless excess for lightweight applications, where it would restrict the adaptability and increment the size of the venture.
Speed of Use
Because of its Virtual DOM design, Respond is viewed as quicker contrasted with Rakish. Likewise, the similar venture size created in Rakish is barely higher.
Refreshing the Virtual DOM is a lot quicker than the standard DOM. In Respond, the Virtual DOM goes about as a channel between the genuine DOM change, to recognize the real parts changed. It then steadily refreshes just those parts that have been adjusted as opposed to refreshing the whole DOM, subsequently saving time.
Two-way Information Restricting
Respond JS follows a one-way information restricting technique and doesn't follow a two-way information restricting methodology. In Rakish, two-way information restricting is utilized to show data to the client while additionally permitting the client to make changes to the fundamental information through the UI.
Expectation to learn and adapt
Despite the fact that all web engineers are familiar with the JavaScript Structure, it is an imperative to gauge the time it takes for a designer to gain proficiency with the elements presented with a System or Library.
Respond JS library concocts continuous updates which must be adjusted to, by the engineers, yet the designers consider Respond simple to learn at work assuming you are familiar with JavaScript. Slowly you can advance from learning Respond to Transition and Revival.
3. Rakish versus Respond Prominence
As per the insights given by Statista, among the most utilized JavaScript systems, libraries, and apparatuses by engineers around the world, Precise incorporates 22.96% of the Market. While react.js leads at 40.14% which is bit by bit moving concerning prominence and convenience.
4. Benefactors
Precise has negligible benefactors contrasted with Respond, yet since it a result of Google, they have many Designer instruments that help Rakish, subsequently facilitating the improvement interaction.
5. What are the advantages of Rakish?
Rakish has out of the container usefulness as it accompanies devices for directing and it has preconfigured climate that is really great for testing. Typescript keeps its code perfect and straightforward and it is likewise useful in troubleshooting for a huge codebase. Precise has high consistency with CLI device that can make repeatable code. With choice of good IDEs like webStorm and VScode chances of blunders is low.
Precise designers
Precise designers are capable and educated in the field of computer programming, as well as expert Javascript engineers. Precise designers feel comfortable around the Rakish system. Their principal obligation is to make a full UI (front-end) as on the web and portable applications.
The following is a precise contextual investigation about how our engineers at Clarion assisted a client from assembling industry with moving from rakish 1 to rakish 9 for executing devices that offer functionalities that save time for the end client.
6. What are the advantages of Respond?
For its measured construction, Respond code is simpler to keep up with and more adaptable. Because of this adaptability, organizations save a significant measure of time and cash.
The motivation behind Respond JS was to give astounding execution. The capacity to reuse parts is one of the primary advantages of Respond JS. Engineers save time by not composing many contents for a similar usefulness.
Decisive parts in Respond make it conceivable to make such great, rich client encounters. Respond accompanies JSX, a syntactic expansion that allows you to build your own parts. These parts basically permit HTML citing and make all subcomponent delivering a joy for designers. Any UI design can profit from Respond JS. It empowers significant information changes to alter explicit UI components consequently.
Respond Designers
Utilizing React.js, a Respond designer makes and executes client confronting usefulness for sites and applications. Front-end designers are a subset of engineers who are liable for all that individuals view on their internet browsers or applications. All in all, they are responsible for the appearance and feel of a site or application to ensure that clients have a reliable encounter.
7. Use Instances of Precise and Respond
You should be hiding in a cave somewhere in the event that you haven't caught wind of Upwork. Upwork is a dynamite stage to get everything rolling with outsourcing, and this site was worked with Precise. Limitless looking over is a component of Upwork that is made conceivable utilizing this device.
Precise is the improvement instrument utilized by YouTube, which is possessed by Google. This application is unquestionably easy to use, which is something that everybody can settle on. It can likewise exploit a gadget's special highlights to give a more customized and worked on experience.
Hurray mail required a great deal of customary updates. A Model View Regulator design was utilized for the majority of the parts, which is more qualified to more modest undertakings. At the point when it came to refresh the UI, utilizing Respond considered more balance and made it simpler.
Whatsapp, a fundamental however fruitful talk application, utilizes Respond JS. This is because of Facebook's acquisition of the application for 16 billion bucks in 2014. The Respond JS library is utilized to make all of the single-page parts.
To summarize, there could never be a one-size-fits-all answer for your undertakings. custom content management services India Every stage has its upsides and downsides which can be an essential point in your dynamic cycle. It is prudent to learn both prior to pursuing a choice; which provides engineers with a hang of the time every stage consumes, and the size the task results in. Having an encounter of these systems close by, you can address the accompanying inquiries concerning your venture.
What stages does the application have to scale to - Web, work area, portable?
What number of instant parts do you really want prior to beginning?
Is the usefulness of the application obviously characterized and what highlights does it require?
The mistaken methodology here is proceed a standard system for all ventures, either because of related knowledge in it or as you have encountered engineers within reach. In view of the responses you can proceed concluding which structure Precise versus Respond, is ideal to be utilized for your ongoing venture and post for the right specialists who have an exhaustive information on the improvement stage.
1 note
·
View note
Text
Streamlining Connectivity: Buy Ubiquiti UniFi Online in Australia
In today's digital age, connectivity is paramount. Whether you're a business striving for seamless operations or a homeowner seeking reliable internet access, having a robust network infrastructure is non-negotiable. Enter Ubiquiti UniFi – a game-changer in the realm of networking solutions. And now, acquiring this cutting-edge technology is easier than ever, especially for those residing in Australia. With the option to buy Ubiquiti UniFi online in Australia, individuals and businesses alike can revolutionize their connectivity experience with just a few clicks.
Ubiquiti UniFi represents the epitome of efficiency and performance in networking. From powerful routers to sleek LED solutions, the UniFi lineup offers a comprehensive suite of products designed to meet the diverse needs of modern users. With its user-friendly interface and advanced features, UniFi empowers users to take control of their networks like never before.
One of the key advantages of Ubiquiti UniFi is its scalability. Whether you're setting up a small home network or managing a complex enterprise infrastructure, UniFi adapts to your requirements with ease. This scalability makes it the ideal choice for businesses experiencing growth or homeowners looking to future-proof their setups. And now, with the option to buy Ubiquiti UniFi online in Australia, acquiring and expanding your network infrastructure is more convenient than ever before.
When it comes to networking, reliability is paramount. With Ubiquiti UniFi, users can rest assured knowing that their connectivity needs are in capable hands. Whether it's ensuring uninterrupted internet access for critical business operations or providing seamless streaming and gaming experiences at home, UniFi delivers on its promise of reliability. And with the added convenience of purchasing Ubiquiti UniFi LED online in Australia, users can enhance their network visibility and control with ease.
In addition to reliability, security is another area where Ubiquiti UniFi excels. With features like advanced firewall protection, secure guest access, and comprehensive threat management, UniFi offers peace of mind in an increasingly connected world. Whether you're safeguarding sensitive business data or protecting your personal information, UniFi's robust security features have you covered. And with the option to buy Ubiquiti UniFi online in Australia, upgrading to a secure and reliable network has never been simpler.
But the benefits of Ubiquiti UniFi extend beyond mere functionality. With its sleek design and intuitive interface, UniFi represents a marriage of form and function. Whether it's the minimalist aesthetic of its routers or the vibrant illumination of its LED solutions, UniFi products are designed to complement any environment. And now, with the option to buy Ubiquiti UniFi LED online in Australia, users can add a touch of style to their network setups while enjoying unparalleled performance and reliability.
The convenience of purchasing Ubiquiti UniFi online in Australia cannot be overstated. With just a few clicks, users can browse a wide selection of UniFi products, compare specifications, and make informed purchasing decisions from the comfort of their homes or offices. This convenience eliminates the need to visit physical stores or navigate complex procurement processes, saving both time and effort in the process.
Furthermore, buying Ubiquiti UniFi online in Australia opens up a world of possibilities for customization and optimization. Whether it's integrating third-party applications, implementing advanced network configurations, or leveraging cloud-based management tools, UniFi offers unparalleled flexibility and control. And with the option to buy Ubiquiti UniFi LED online in Australia, users can enhance their network visibility and performance with cutting-edge LED technology.
In conclusion, Ubiquiti UniFi represents the pinnacle of networking excellence. With its scalability, reliability, security, and aesthetics, UniFi offers a holistic solution for modern connectivity needs. And with the option to buy Ubiquiti UniFi online in Australia, acquiring and optimizing your network infrastructure has never been easier. So why wait? Elevate your connectivity experience with Ubiquiti UniFi today.
0 notes
Text
does umbiquiti have vpn options
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does umbiquiti have vpn options
Ubiquiti VPN features
Ubiquiti, a prominent name in networking solutions, offers a robust set of VPN features tailored for both personal and business needs. VPN, or Virtual Private Network, serves as a secure tunnel for data transmission over the internet, ensuring privacy and confidentiality. Ubiquiti's VPN features stand out for their reliability, versatility, and ease of use.
One of the key features of Ubiquiti VPN is its support for various protocols, including OpenVPN and L2TP/IPsec. This flexibility allows users to choose the protocol that best fits their security and performance requirements. Whether it's encrypting sensitive data or accessing geo-blocked content, Ubiquiti VPN ensures a seamless experience.
Additionally, Ubiquiti offers centralized management through its intuitive UniFi Controller software. This enables administrators to easily configure, monitor, and manage VPN connections across multiple devices and locations from a single interface. With advanced features like user authentication and traffic logging, UniFi Controller provides granular control over VPN access and usage.
For businesses, Ubiquiti VPN offers site-to-site connectivity, allowing seamless communication between geographically dispersed offices or branches. This enhances collaboration and productivity while maintaining data security. Moreover, Ubiquiti's VPN features include support for VLAN tagging and firewall rules, enabling organizations to enforce network segmentation and access policies effectively.
In terms of security, Ubiquiti VPN implements robust encryption algorithms and authentication mechanisms to safeguard data from unauthorized access and cyber threats. Whether it's protecting confidential communications or securing remote access to corporate resources, Ubiquiti VPN offers peace of mind to users and administrators alike.
In conclusion, Ubiquiti VPN features a comprehensive suite of functionalities designed to meet the diverse needs of individuals and businesses alike. With its flexibility, ease of management, and strong security capabilities, Ubiquiti VPN emerges as a reliable solution for ensuring privacy and connectivity in today's digital landscape.
Ubiquiti VPN protocols
Ubiquiti, a renowned name in networking solutions, offers a range of VPN protocols to ensure secure and seamless connections for its users. These protocols play a vital role in safeguarding sensitive data transmitted over networks, especially in today's increasingly interconnected digital landscape.
One of the prominent VPN protocols supported by Ubiquiti is OpenVPN. OpenVPN is highly regarded for its robust security features, including strong encryption algorithms and support for various authentication methods. It is known for its versatility, allowing it to be implemented across different operating systems and devices seamlessly. Additionally, OpenVPN's open-source nature fosters continuous development and auditing, enhancing its reliability.
Another widely used protocol by Ubiquiti is IPsec (Internet Protocol Security). IPsec operates at the network layer, providing end-to-end security for IP communications. It utilizes encryption and authentication mechanisms to protect data during transit, making it ideal for securing site-to-site and remote access VPN connections. IPsec is known for its efficiency and compatibility with various network infrastructures, making it a preferred choice for organizations with diverse networking needs.
Additionally, Ubiquiti offers support for L2TP/IPsec (Layer 2 Tunneling Protocol/Internet Protocol Security), which combines the features of both L2TP and IPsec to deliver secure VPN connections. L2TP provides the tunneling mechanism, while IPsec ensures data confidentiality and integrity, offering a comprehensive solution for secure communication.
Ubiquiti's commitment to providing robust VPN solutions is evident through its support for multiple protocols, catering to the diverse security requirements of businesses and individuals alike. Whether it's safeguarding sensitive corporate data or ensuring privacy for remote workers, Ubiquiti's VPN protocols offer the necessary tools to establish secure and reliable network connections. By leveraging these protocols, users can enjoy peace of mind knowing their data is protected against potential threats in today's dynamic digital environment.
Ubiquiti VPN compatibility
Ubiquiti, a renowned name in networking technology, offers a range of products that provide reliable and secure internet connectivity. When it comes to VPN compatibility, Ubiquiti devices are known for their seamless integration with various VPN services.
Setting up a VPN (Virtual Private Network) on Ubiquiti devices is straightforward, thanks to the intuitive user interface and robust hardware. Whether you are using Ubiquiti UniFi Security Gateway, EdgeRouter, or UniFi Dream Machine, you can easily configure a VPN connection to safeguard your online activities.
Ubiquiti devices support popular VPN protocols such as OpenVPN and IPsec, ensuring compatibility with a wide range of VPN services available in the market. By encrypting your internet traffic, VPNs add an extra layer of security, making it ideal for remote workers, businesses, and individuals concerned about their online privacy.
With Ubiquiti VPN compatibility, you can secure your network traffic, access geo-restricted content, and maintain anonymity while browsing the web. Whether you need to connect multiple offices, work remotely, or enhance your online security, Ubiquiti devices offer reliable VPN support to meet your needs.
In conclusion, Ubiquiti's commitment to VPN compatibility makes it a popular choice among users looking for a secure and reliable networking solution. By combining Ubiquiti devices with a trusted VPN service, you can enjoy a safer and more private online experience.
Ubiquiti VPN setup guide
Title: A Comprehensive Guide to Setting Up a VPN with Ubiquiti
In today's digitally connected world, ensuring the security and privacy of your online activities is paramount. One effective way to achieve this is by using a Virtual Private Network (VPN). Ubiquiti, known for its reliable networking solutions, offers robust features for setting up a VPN. Follow this comprehensive guide to configure a VPN with Ubiquiti and safeguard your online communications.
Choose Your Ubiquiti Hardware: Ubiquiti provides various hardware options, including routers and access points, capable of VPN functionalities. Ensure your device supports VPN configurations before proceeding.
Access Ubiquiti Controller Software: Ubiquiti's Controller software is the central hub for managing your Ubiquiti network devices. Access the Controller interface either through the UniFi Controller software or via the web interface of your Ubiquiti device.
Navigate to VPN Settings: Within the Controller interface, locate the VPN settings section. This may vary depending on your device model and firmware version. Look for options such as 'VPN Server' or 'VPN Settings.'
Configure VPN Server: Follow the on-screen instructions to set up the VPN server. You'll typically need to specify parameters such as VPN protocol (e.g., OpenVPN, L2TP/IPsec), authentication method, and encryption settings. Ensure to choose strong encryption algorithms for maximum security.
Generate Certificates and Keys: For certain VPN protocols like OpenVPN, you'll need to generate SSL certificates and keys. Ubiquiti often provides built-in tools for this purpose. Generate the necessary certificates and keys following the provided instructions.
Client Configuration: Once the VPN server is set up, configure your client devices to connect to the VPN. This involves installing VPN client software or configuring VPN settings manually on each device.
Testing and Troubleshooting: After configuring the VPN, test the connection to ensure it's working correctly. Troubleshoot any issues that arise by referring to Ubiquiti's documentation or seeking assistance from their support channels.
By following these steps, you can establish a secure VPN connection using Ubiquiti hardware, enhancing the privacy and security of your online activities. Stay protected while enjoying the benefits of a seamlessly connected network environment.
Ubiquiti VPN alternatives
Ubiquiti VPN is a popular choice for individuals and businesses looking to secure their internet connection and protect their privacy. However, there are several alternative VPN services available that offer similar features and benefits. These alternatives may be more suitable for some users based on their specific needs and preferences.
One viable alternative to Ubiquiti VPN is ExpressVPN. ExpressVPN is known for its fast connection speeds and excellent security features. It offers a wide range of server locations around the world, allowing users to access geo-blocked content and maintain their anonymity online. Additionally, ExpressVPN has a user-friendly interface and provides round-the-clock customer support.
Another noteworthy alternative is NordVPN. NordVPN is lauded for its advanced security protocols and strict no-logs policy. It boasts a large network of servers, making it easy for users to find a fast and reliable connection. NordVPN also offers specialized servers for activities like streaming and torrenting, catering to a variety of user needs.
For those seeking a budget-friendly option, Surfshark is a compelling alternative to Ubiquiti VPN. Surfshark offers unlimited simultaneous connections, making it an ideal choice for households with multiple devices. Despite its affordability, Surfshark does not compromise on security or speed, making it a solid contender in the VPN market.
In conclusion, while Ubiquiti VPN is a reputable choice for securing internet connections, there are several viable alternatives worth considering. ExpressVPN, NordVPN, and Surfshark each offer unique features and benefits that may better suit individual preferences and requirements. It is advisable for users to evaluate their specific needs and conduct thorough research before selecting a VPN service that best aligns with their objectives.
0 notes
Text
do vpn apps work on iphone
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
do vpn apps work on iphone
VPN apps compatibility on iPhone
VPN apps are becoming increasingly popular for iPhone users who wish to enhance their online privacy and security. These apps allow you to browse the internet anonymously by redirecting your internet traffic through a secure server. However, ensuring the compatibility of your chosen VPN app with your iPhone is crucial to its effective functioning.
Most top VPN providers offer dedicated apps for iOS devices, including iPhones. These apps are usually available for download from the App Store and are designed to work seamlessly with the iOS operating system. Before downloading a VPN app, it is essential to check its compatibility with your specific iPhone model and the version of iOS it is running on. This information can typically be found on the VPN provider's website or in the app description on the App Store.
In addition to compatibility with your device, it is also essential to consider the features offered by the VPN app. Look for apps that offer strong encryption protocols, a wide selection of server locations, and good connection speeds. Some VPN apps also come with additional features such as ad blocking, malware protection, and split tunneling.
By choosing a compatible VPN app for your iPhone, you can ensure that your online activities remain private and secure while using public Wi-Fi networks or accessing geo-restricted content. Make sure to research different VPN providers and read reviews to find the best app for your needs.
VPN app functionality on iOS
VPN apps play an essential role in maintaining online privacy and security on iOS devices. These apps provide users with a secure connection to the internet by encrypting their data and hiding their IP addresses. Here's how VPN functionality works on iOS devices:
Enhanced Security: VPN apps encrypt all data transmitted between the user's device and the internet, making it nearly impossible for hackers or cybercriminals to intercept sensitive information such as passwords, financial details, or personal data.
Bypassing Geographical Restrictions: VPN apps allow users to access geo-blocked content by masking their IP addresses with those from different countries. This feature is particularly useful for streaming services, social media platforms, and websites that are restricted in certain regions.
Public Wi-Fi Protection: When connecting to public Wi-Fi networks, users are vulnerable to various security threats. VPN apps create a secure tunnel for data transmission, protecting users from potential cyber attacks or snooping on unsecured networks.
Anonymity and Privacy: VPN apps ensure user anonymity by masking their actual IP addresses. This prevents websites, advertisers, or ISPs from tracking users' online activities and collecting their personal information for targeted ads or data mining purposes.
Customization and User-Friendly Interface: VPN apps on iOS devices offer features such as server selection, protocol choice, and kill switch options for customization. Additionally, many VPN apps have intuitive interfaces that make connecting to a VPN server a seamless experience for users.
In conclusion, VPN apps on iOS devices provide users with enhanced security, privacy, and freedom while browsing the internet. By utilizing a reliable VPN app, iOS users can safeguard their online activities and enjoy a more secure online experience.
iPhone VPN app effectiveness
Title: Maximizing iPhone VPN App Effectiveness: A Comprehensive Guide
In an age where cybersecurity threats loom large, protecting your online privacy is paramount. With the ubiquity of smartphones, particularly iPhones, ensuring the security of your internet connection has become increasingly vital. Enter VPN (Virtual Private Network) apps, designed to encrypt your data and shield your online activities from prying eyes. But just how effective are these VPN apps when it comes to iPhone usage?
The effectiveness of an iPhone VPN app depends on various factors, including the provider, encryption protocols, and server network. Premium VPN services typically offer robust encryption standards like AES-256, ensuring military-grade security for your data. Additionally, a wide network of servers across different locations enhances the app's performance by providing better connection speeds and accessibility to geo-blocked content.
One of the primary benefits of using a VPN app on your iPhone is the protection it offers on public Wi-Fi networks. Whether you're browsing at a coffee shop or connecting to an airport hotspot, a VPN encrypts your data, preventing hackers from intercepting sensitive information such as passwords or credit card details.
Moreover, VPN apps allow users to bypass geographical restrictions and access region-locked content on streaming platforms like Netflix or Hulu. By connecting to a server in a different country, users can unlock a vast array of movies, TV shows, and other content that may not be available in their region.
However, it's essential to choose a reputable VPN provider with a strict no-logs policy to ensure your privacy remains intact. Additionally, regularly updating your VPN app and iPhone software ensures you're protected against the latest security vulnerabilities.
In conclusion, iPhone VPN apps can be highly effective tools for safeguarding your online privacy and accessing restricted content. By selecting a trusted provider and following best practices, you can maximize the effectiveness of your VPN app and enjoy a safer, more secure internet experience on your iPhone.
VPN apps performance on iPhone
Title: Evaluating VPN App Performance on iPhone: What You Need to Know
With the increasing concerns about online privacy and security, VPN (Virtual Private Network) apps have become essential tools for iPhone users. These apps offer encrypted connections and the ability to mask IP addresses, providing a secure gateway for browsing the internet. However, not all VPN apps are created equal when it comes to performance on iPhones.
When assessing the performance of VPN apps on iPhones, several factors come into play. Firstly, speed is crucial. A VPN should not significantly slow down internet connection speeds, allowing users to browse, stream, and download without noticeable lag. The best VPN apps optimize their servers to minimize latency and maximize bandwidth, ensuring smooth performance even on mobile networks.
Moreover, reliability is key. A VPN app should maintain a stable connection without frequent disconnections or downtime. This is particularly important for iPhone users who rely on VPNs for secure access to sensitive information on the go. A reliable VPN ensures uninterrupted protection against potential security threats.
Another aspect to consider is compatibility with iOS devices. The best VPN apps are designed specifically for iPhones, offering seamless integration with iOS features and functionalities. They should be user-friendly, with intuitive interfaces that make it easy to connect to VPN servers and customize settings according to individual preferences.
Furthermore, privacy is paramount. A trustworthy VPN app should have a strict no-logs policy, ensuring that user activity is not monitored or recorded. Additionally, it should employ robust encryption protocols to safeguard data transmitted between the iPhone and VPN servers.
In conclusion, when choosing a VPN app for your iPhone, prioritize performance, reliability, compatibility, and privacy. By selecting a high-quality VPN app, you can enjoy a secure and seamless browsing experience on your iOS device.
Utilizing VPN apps on iPhone
Utilizing VPN Apps on iPhone
With the increasing concerns about online privacy and security, the use of Virtual Private Network (VPN) apps on iPhones has become essential for many users. VPN apps offer a secure and encrypted connection, shielding your online activities from prying eyes and potential hackers. Here's a closer look at how to effectively utilize VPN apps on your iPhone.
First and foremost, choose a reputable VPN app from the App Store. Look for apps with high ratings, positive reviews, and a clear privacy policy. Some popular options include ExpressVPN, NordVPN, and Surfshark. Once you've downloaded and installed the app, follow the setup instructions to configure it on your device.
Next, launch the VPN app and sign in with your account credentials. Most VPN apps offer a user-friendly interface with a one-tap connect feature, making it easy to establish a secure connection. Simply tap the connect button, and the app will automatically connect you to the nearest server, ensuring optimal speed and performance.
Additionally, many VPN apps allow you to choose your desired server location manually. This feature can be particularly useful if you want to access region-restricted content or bypass censorship in certain countries. Select a server location from the app's list of available options, and the app will route your internet traffic through that server, masking your true IP address in the process.
Furthermore, consider enabling the VPN app's auto-connect feature to ensure that you're always protected whenever you're connected to the internet. This feature will automatically establish a VPN connection whenever you join a Wi-Fi network, providing continuous protection against online threats.
In conclusion, VPN apps are invaluable tools for safeguarding your online privacy and security on your iPhone. By following these tips, you can effectively utilize VPN apps to enjoy a safer and more secure browsing experience on your device.
0 notes
Text
Why do hackers love Linux? The 7 deeply unsettling realities - CyberTalk
New Post has been published on https://thedigitalinsider.com/why-do-hackers-love-linux-the-7-deeply-unsettling-realities-cybertalk/
Why do hackers love Linux? The 7 deeply unsettling realities - CyberTalk


EXECUTIVE SUMMARY:
Why do hackers use Linux so extensively? This open-source operating system (OS), which some see as more stable and reliable than any other operating system in existence, has become a favored playground for cyber criminals.
Although Linux claims only a small percentage of the OS market share, major telecommunications networks, science-based organizations (particularly those running supercomputers), national e-voting systems and global stock exchanges run on Linux. National Departments of Defense are also known for their reliance on Linux.
In this article, we unpack why Linux has become an irresistible target for motivated cyber criminals. You’ll gain new insights designed to help inform (and transform) your security processes and system development. Keep reading to learn more:
Why do hackers love Linux? 7 unsettling realities
1. The open-source advantage. Linux is open-source software. The source code of the Linux project is available to the general public. Anyone can download the source code for free, modify it for their own use and even create their own version of Linux. This can be good, but it also comes with challenges…
While the open-source model allows for collaboration and rapid innovation, it also exposes the source code to malicious actors, who may scrutinize it for vulnerabilities. Malicious persons can then exploit weaknesses with relative ease.
2. Ubiquity and versatility. Linux powers a diverse array of systems and applications, from IoT devices, to desktops, to smartphones. This makes Linux an attractive target for hackers who want to maximize their impact. When compromising a Linux system, cyber criminals can potentially gain access to a wide network of interconnected devices and services, thereby enabling them to amplify the effects of their activities.
3. Kernel vulnerabilities. Why do hackers use Linux to gain elevated privileges? It’s simple. Despite a strong reputation for security, the Linux kernel, the core element responsible for managing system resources, has been dogged by vulnerabilities over the years. High profile bugs have effectively provided cyber criminals with opportunities to unduly gain elevated privileges.
4. Supply chain attacks. Why do hackers use Linux ecosystems for widespread disruption? In the era of containerization and DevOps practices, supply chain attacks targeting Linux ecosystems have become a serious concern. By compromising a widely used package or container image, cyber criminals can inject malicious code that propagates across numerous systems, resulting in widespread disruption and data breaches.
5. Cryptocurrency mining. Linux’s efficiency and scalability render it a preferred platform for cryptocurrency mining operations; both those that are legitimate and those that are illicit. Cyber criminals adeptly leverage Linux’s systems to harness the extensive computing power for mining, evading detection all the while.
6. Internet of things. The proliferation of Linux-based IoT devices has created an expansive attack surface for cyber criminals. Many IoT devices are bereft of proper security, making them easy targets for hackers seeking entry points into networks. Hackers use Linux to establish a foothold, via IoT, within corporate networks, enabling them to eventually deploy more sophisticated network-based attacks.
7. Technical capabilities. Why do hackers use Linux tools for advanced exploits? Linux’s command-line interface and powerful tools (like Bash and Python) are a force-multiplier. Understanding the intricacies of Linux enables elite cyber criminals to craft sophisticated exploits that sow more chaos, lead to more damage and turn up higher yields than attacks leveraging other operating systems.
For more of the latest cyber security insights, please see CyberTalk.org’s past coverage. Lastly, subscribe to the CyberTalk.org newsletter for timely insights, cutting-edge analyses and more, delivered straight to your inbox each week.
#analyses#applications#Article#Attack surface#bugs#chaos#code#Collaboration#command#command-line interface#computing#container#container image#containerization#craft#cryptocurrency#cutting#cyber#cyber attack#cyber criminals#cyber security#cyber threat#cybersecurity#data#Data Breaches#defense#detection#development#devices#Devops
1 note
·
View note
Text
Privacy Considerations When Using Geo-Location Data
In an increasingly interconnected world, the proliferation of location-aware devices and applications has revolutionized how individuals interact with technology and each other. From navigation services and social media platforms to IoT devices and wearable gadgets, geolocation data has become ubiquitous, offering unprecedented convenience and functionality.

However, this proliferation also raises significant privacy concerns, as the collection, processing, and dissemination of location information can expose individuals to surveillance, tracking, and data breaches. This article explores the intricate landscape of privacy considerations associated with the use of geo-location data, examining the underlying risks, regulatory frameworks, and best practices for safeguarding individual privacy rights in a digital age.
The Ubiquity of Geo-Location Data
Geo-location data encompasses information that identifies the geographical location of an individual, device, or object at a specific point in time. This data is derived from a myriad of sources, including GPS satellites, Wi-Fi networks, cellular towers, IP addresses, and Bluetooth beacons. While GPS remains the gold standard for outdoor positioning, indoor localization technologies such as Wi-Fi fingerprinting and Bluetooth Low Energy (BLE) beacons enable accurate tracking within enclosed spaces like buildings, malls, and airports. The widespread adoption of smartphones, IoT sensors, and connected devices further amplifies the volume and granularity of location data generated on a daily basis.
Privacy Risks and Threat Vectors
The proliferation of geo-location data introduces various privacy risks and threat vectors, including:
Location Tracking: Continuous tracking of individuals' movements and routines can result in the creation of detailed profiles, revealing sensitive information such as home addresses, workplaces, social habits, and personal interests.
Behavioral Profiling: Analyzing location data in conjunction with other contextual information enables behavioral profiling and targeted advertising, raising concerns about manipulation, discrimination, and exploitation of personal preferences and vulnerabilities.
Stalking and Harassment: Malicious actors may exploit geo-location data for nefarious purposes such as stalking, harassment, or surveillance, posing significant risks to personal safety, security, and psychological well-being.
Data Breaches and Identity Theft: Unauthorized access to location databases or insecure transmission of location data can facilitate data breaches and identity theft, exposing individuals to financial fraud, impersonation, and reputational damage.
Regulatory Frameworks and Compliance Obligations
To address these privacy concerns, governments and regulatory bodies have enacted legislation and frameworks to regulate the collection, use, and disclosure of geo-location data:
General Data Protection Regulation (GDPR): The GDPR imposes stringent requirements on the processing of personal data, including geo-location data, by businesses operating in the European Union (EU). Organizations must obtain explicit consent from individuals, implement privacy-by-design principles, and ensure transparency and accountability in handling location information.
California Consumer Privacy Act (CCPA): The CCPA grants California residents certain rights regarding their personal information, including the right to know what data is collected, the right to opt-out of data sharing, and the right to request deletion of their information. Businesses subject to the CCPA must provide clear disclosures and mechanisms for exercising these rights.
youtube
SITES WE SUPPORT
Locate HIPAA Mails – Weebly
0 notes
Text
SAMZ CREATIVE DESIGN

WHY
DIGITAL MARKETING ?
With how easily accessible the internet is today, would you believe me if I told you the number of people who go online every day is still improving?
Digital marketing, also called online marketing, refers to all marketing attempts that occur on the Internet. Businesses such as search engines, social media, email, and other websites can connect with current customers. It also includes communication through text or multimedia messages.
Digital marketing is the strategic utilization of various online tactics and channels to engage with customers in the digital sphere, catering to the prevalent trend where consumers increasingly turn to the internet for information. In the contemporary business landscape, the majority of brands possess a website, and even those without one typically maintain a presence on social media platforms. The ubiquity of digital content and marketing has elevated it to a crucial tool for enhancing brand awareness.
Given the widespread adoption of digital platforms, consumers now anticipate and rely on online channels as primary sources for learning about brands. The versatility of digital marketing allows businesses to explore creative and cost-effective strategies, making it accessible for experimentation even with limited budgets.
In essence, a comprehensive definition of digital marketing involves recognizing and leveraging a myriad of digital channels to connect with the target audience, understanding that customers allocate a significant portion of their time online. `Successful digital marketers develop a clear understanding of how each digital marketing campaign aligns with and contributes to their overarching objectives. Depending on the specific goals of their marketing strategy, these marketers deploy a combination of both free and paid channels to reinforce larger campaigns.
There are a few benefits of digital marketing:
Concentrate your efforts on potential customers most inclined to acquire your product or service.
Compared to outbound marketing methods, digital marketing proves to be a more economical approach.
Level the competitive landscape within your industry, empowering you to compete effectively with larger brands.
Digital marketing offers quantifiable metrics, enabling the assessment of campaign success.
Adjusting and modifying a digital marketing strategy is more straightforward, allowing for swift adaptations.
Elevate your conversion rate and enhance lead quality through effective digital marketing practices.
Connect with audiences at every phase using diverse digital marketing strategies.
Types of Digital Marketing:
Search Engine Optimization (SEO)
Content Marketing
Online PR
Social Media Marketing
Pay Per Click (PPC)
Affiliate Marketing
Email Marketing
Marketing automation
Inbound Marketing
Search Engine Marketing (SEM)
Instant Messaging Marketing
Search Engine Optimization (SEO):
SEO is the process of optimizing your website to achieve a higher ranking in search engine results pages, ultimately boosting organic traffic. Channels benefiting from SEO include websites, blogs, and infographics.
Approaches to SEO for generating qualified traffic include:
On-page SEO: Concentrating on all on-page content, this SEO type involves researching keywords to address reader questions, enhancing your chances of ranking higher on SERPs.
Off-page SEO: This SEO type deals with optimizing activities outside your website. The number and authority of publishers linking to you influence your ranking. Networking, guest posting, and gaining external attention can earn the backlinks needed for improved SERP positioning.
Technical SEO: Focusing on the website backend and coding, technical SEO includes tasks like image compression, structured data implementation, and CSS file optimization. These measures enhance loading speed, a key ranking factor for search engines like Google.
Content Marketing:
Content marketing involves creating and promoting content assets to enhance brand awareness, drive traffic growth, generate leads, and acquire customers.
Channels integral to your content marketing strategy comprise:
Blog posts: Publishing articles on your company blog showcases industry expertise, attracting organic search traffic and creating opportunities to convert visitors into leads.
Ebooks and whitepapers: Long-form content such as ebooks and whitepapers educates website visitors, enabling the exchange of content for contact information and generating leads, guiding individuals through the buyer's journey.
Infographics: Visual content like infographics helps readers grasp concepts visually, offering a different dimension to learning.
Audio or visual content: Expanding beyond traditional mediums like television and radio, digital marketing utilizes content shareable online as videos or audio broadcasts, broadening your potential audience.
Online PR:
Online PR involves securing earned coverage on digital platforms such as publications, blogs, and content-based websites, mirroring traditional PR practices but in the online realm. Channels for maximizing online PR efforts include:
Reporter outreach via social media: Establishing connections with journalists, for instance, through Twitter, is an effective way to build relationships with the press, leading to earned media opportunities for your company.
Engaging online reviews of your company: Actively participating in online reviews, whether positive or negative, humanizes your brand and allows you to convey impactful messages that safeguard your reputation.
Engaging comments on your website or blog: Responding to readers of your content, akin to addressing company reviews, fosters constructive conversations within your industry.
Social Media Marketing:
Social media marketing aims to boost brand awareness, drive traffic, and generate leads by promoting your brand and content across various social media channels.
For efficient management of social platforms, tools like HubSpot can be employed to connect channels such as LinkedIn and Facebook in one centralized place. This allows for easy content scheduling across multiple channels and monitoring analytics within the platform.
Social media marketing channels encompass:
Facebook
Twitter
LinkedIn
Instagram
Snapchat
Pinterest
Marketers often leverage these platforms for viral campaigns, partnering with content creators or engaging in trending topics to create shareable content that organically spreads across social media channels.
Pay Per Click (PPC):
PPC is a strategy that directs traffic to your website by compensating a publisher each time your ad is clicked. A prevalent form of PPC is Google Ads, enabling payment for prominent positions on Google's search engine results pages based on a "per click" model.
Additional channels for PPC include:
Paid ads on Facebook: Users can customize video, image posts, or slideshows, paying for placement in the news feeds of individuals matching the business's target audience.
Twitter Ads campaigns: Users can pay for a series of posts or profile badges displayed in the news feeds of a specific audience, geared towards achieving predefined business goals like website traffic, increased Twitter followers, tweet engagement, or app downloads.
Sponsored Messages on LinkedIn: Users can pay to send messages directly to specific LinkedIn users, targeting them based on industry and background.
Affiliate Marketing:
Affiliate marketing, a performance-based advertising model, involves earning a commission for promoting another entity's products or services on your website. Channels for affiliate marketing encompass:
Hosting video ads through the YouTube Partner Program.
Posting affiliate links on your social media accounts.
In the realm of influencer marketing, utilizing influencers in a campaign can significantly enhance the effectiveness of affiliate marketing. Partnering with suitable content creators has the potential to elevate your digital campaign to new heights.
Email Marketing:
Email marketing serves as a crucial means for companies to connect with their audiences. It is a versatile tool used for promoting content, offering discounts and event information, and guiding recipients to the business's website. Various types of emails in an email marketing campaign include:
Blog subscription newsletters.
Follow-up emails to website visitors who downloaded content.
Customer welcome emails.
Holiday promotions targeted at loyalty program members.
Tips or a series of similar emails for customer nurturing.
Search Engine Marketing (SEM):
When a potential lead is actively searching for a product or business akin to yours, it presents a prime opportunity for promotion. Utilizing both paid advertising and SEO strategies proves effective in capturing these prospective leads. Search engine marketing, another avenue for boosting website traffic, involves placing paid ads on search engines. The predominant SEM services, Bing Ads and Google Ads position these ads seamlessly at the top of search engine results pages, ensuring instant visibility. This approach exemplifies the effectiveness of native advertising.
Marketing Automation:
Marketing automation involves using software to automate fundamental marketing tasks, streamlining processes that would otherwise be performed manually. Some of these tasks include:
Email newsletters: Automation allows for the automatic delivery of emails to subscribers, and it also aids in managing contact lists dynamically, ensuring newsletters reach the right audience.
Social media post scheduling: To maintain a consistent presence on social networks, frequent posting is essential. Social media scheduling tools automate content delivery to channels, freeing up time for a focus on content strategy.
Campaign tracking and reporting: With various elements involved in marketing campaigns, automation assists in organizing tasks by the campaign they serve. It tracks the performance of campaigns over time, monitoring the progress of different components like people, emails, content, webpages, and phone calls.
Inbound marketing:
Inbound marketing is a comprehensive approach that involves attracting, engaging, and delighting customers at each stage of the buyer's journey. Every digital marketing tactic mentioned earlier can be employed in an inbound marketing strategy, fostering a customer experience that collaborates with the customer rather than opposing them. Here are a few traditional marketing alternatives to inbound strategies:
Blogging vs. pop-up ads
Video marketing vs. commercial advertising
Email contact lists vs. email spam
Instant Messaging Marketing:
Promoting products through messaging platforms offers a swift means of reaching potential leads, even without obtaining their phone numbers. It provides a straightforward way to inform your audience about flash sales, new products, or updates regarding their orders. Additionally, instant messaging serves as a convenient channel for customers to connect with customer service, address inquiries, or seeking more information. Messages can be delivered directly to mobile phones through text or on platforms such as Facebook Messenger or WhatsApp.
CONTACT :
SAMZ CREATIVE DESIGN
TRIVANDRUM
E-mail:[email protected]
1 note
·
View note
Text
Ubiquiti Networks UAP-AC-LR - Unified Wi-Fi Management for Seamless Expansion:
The UAP-AC-LR by Ubiquiti Networks is a high-performance Dual-Radio Access Point designed for scalable enterprise Wi-Fi management. With a maximum data transfer rate of 1000 Mbit/s, it boasts advanced features, including simultaneous dual-band operation and 3x3 MIMO in the 2.4 GHz band and 2x2 MIMO in the 5 GHz band. The UniFi Controller software simplifies configuration, making it suitable for high-density client deployments.
#Ubiquiti Access Point#Ubiquiti Long Range Wifi Solution#Unifi UAP-AC-LR#Wireless Access Point#Unifi Access Point UAP-AC-LR Pro#Buy Ubiquiti UAP-AC-LR#Access Points#Wifi Access Point#Wireless Internet Access Point#Wi-Fi for Long Range
0 notes
Text
Breaking Through the Ages: The Enduring Love for Atari Breakout
In the domain of exemplary arcade games, few have made a permanent imprint on the gaming scene very like Atari Breakout. Initially delivered in 1976 by Atari, the game immediately turned into a sensation and has since scratched its name into the records of gaming history. As we dive into the persevering through adoration for Atari Breakout, we'll investigate the game's beginnings, its effect on the gaming business, and the nostalgic fondness that keeps on enrapturing players across ages.
The Beginning of Atari Breakout
Atari Breakout was the brainchild of Atari prime supporter Nolan Bushnell and Steve Bristow. Propelled by the idea of table tennis, the game's specialists were straightforward yet progressive for now is the right time. Players controlled an oar at the lower part of the screen, moving it evenly to skip a ball upwards to break a mass of shaded blocks. The goal was direct: break whatever number blocks as could reasonably be expected while keeping the ball from tumbling off the lower part of the screen.
The Introduction of a Work of art
Sent off as an arcade game in 1976, Atari Breakout quickly acquired ubiquity, enamoring the consideration of gamers across the world. Its prosperity can be ascribed to its available ongoing interaction, joining components of ability and procedure. The splendid, dynamic designs and spellbinding audio effects additionally improved the general gaming experience, making Atari Breakout a moment exemplary.
The game's ubiquity arrived at new levels when Atari delivered it as a home control center game for the Atari 2600 of every 1978. This move gave the pleasure of Atari Breakout straightforwardly into individuals' homes, solidifying its status as a commonly recognized name. The effortlessness of the game's plan made it open to players, everything being equal, adding to its boundless allure.
The Effect on the Gaming Business
Atari Breakout assumed a significant part in molding the gaming business during its early stages. Its prosperity highlighted the capability of arcade games as a worthwhile market, rousing engineers to investigate new ideas and push the limits of what gaming could accomplish. The game's breakout achievement set a trend for future arcade hits and energized the business' development.
Besides, Atari Breakout's effect reached out past the gaming domain. It turned into a social peculiarity, with references in motion pictures, network shows, and, surprisingly, well known music. The unmistakable sound of the skipping ball and the breaking of blocks became inseparable from the brilliant time of arcade gaming, making a permanent imprint on the shared perspective of gamers.
Wistfulness Across Ages
While the gaming business has developed dramatically since the 1970s, the affection for Atari Breakout stays ardent. Wistfulness assumes a critical part in this persevering through fondness, with players of any age esteeming the recollections of going through hours in faintly lit arcades, immersed in the pixelated universe of Atari Breakout.
The game's effortlessness is a critical consider its immortal allure. In a time overwhelmed by complex and graphically concentrated games, Atari Breakout's direct interactivity fills in as a reviving sign of the delight that can be gotten from the rudiments. The instinctive controls and habit-forming nature of breaking blocks give a gaming experience that rises above ages.
The Advanced Renaissance: Atari Breakout On the web
As innovation progressed, so did the manners by which players could encounter Atari Breakout. The game tracked down a fresh chance to take life by the horns with the coming of the web. Atari Breakout's web-based variant arose as a computerized renaissance, permitting players to remember the exemplary interactivity in the virtual domain.
Google even gave proper respect to Atari Breakout by integrating a playable form into its web search tool. Clients could initiate the game by composing "Atari Breakout" into the Google Pictures search bar, changing the list items into a playable Atari Breakout screen. This inventive execution acquainted the exemplary game with another age of players while charming prepared fans with a nostalgic excursion through a world of fond memories.
The Persevering through Tradition of Atari Breakout
Atari Breakout's heritage isn't restricted to the domain of gaming; it reaches out to the more extensive social scene. The game's impact can be seen in different parts of mainstream society, from workmanship and style to music and plan. Atari Breakout's famous status has roused innumerable makers to honor its basic yet enamoring plan.
Craftsmen and planners frequently integrate Atari Breakout symbolism into their manifestations, implanting a feeling of retro appeal into contemporary works. The game's visual components, including the oar, ball, and bright blocks, have become notable images that inspire a feeling of wistfulness for the beginning of gaming.
Atari Breakout Competitions: Keeping the Soul Alive
As the years have passed, Atari Breakout has not blurred into haziness. All things being equal, it has tracked down a renewed outlook through cutthroat gaming. Atari Breakout competitions have arisen as a way for lovers to exhibit their abilities, participate in cordial rivalry, and praise the getting through tradition of the game.
These competitions unite players, everything being equal, from prepared veterans who recollect the game's unique delivery to more youthful members finding its appeal interestingly. The competitions not just act as a stage for cordial contest yet additionally encourage a feeling of local area among the individuals who share an energy for Atari Breakout.
The Development of Breakout-Propelled Games
Atari Breakout's impact reaches out past direct transformations and competitions; it has enlivened a plenty of breakout-style games across different stages. Engineers have embraced the center mechanics of Atari Breakout while adding their own remarkable turns, bringing about a different exhibit of current breakout games that take special care of contemporary preferences.
Whether on cell phones, gaming consoles, or augmented reality stages, breakout-enlivened games keep on enthralling crowds. The persevering through allure of breaking blocks with an oar and ball addresses the immortality of Atari Breakout interactivity, demonstrating that the substance of an exemplary can be rethought for new ages.
Conclusion
Atari Breakout's excursion from its modest beginnings in arcades to turning into a computerized peculiarity is a demonstration of its getting through bid. The game's impact on the gaming business, combined with its nostalgic reverberation, has hardened its spot in the hearts of gamers around the world. As we praise the tradition of Atari Breakout, obviously the adoration for this exemplary game will persevere, getting through the ages and proceeding to spellbind players for a long time into the future.
0 notes
Text
The Vudu com Start Revolution: Elevate Your Streaming Experience
In the quick moving computerized age, web-based features have become an essential piece of our amusement scene. One stage that captivates everyone is Vudu.com, offering an interesting and progressive way to deal with streaming. In this article, we will dig into the Vudu com Start transformation and investigate how it has raised the streaming experience for clients all over the planet.
The Ascent of Web-based features
Real time features have changed the manner in which we consume content. With the coming of rapid web, clients currently can watch their #1 motion pictures and Network programs on-request, whenever, anyplace. Stages like Netflix, Hulu, and Amazon Prime have become easily recognized names, ruling the streaming business.
In any case, as the market became soaked, clients started looking for options that offered an immense library of content as well as given a particular and vivid experience. This is where Vudu.com stepped in with its progressive way to deal with streaming.
Vudu: A Short Outline
Vudu is a web-based feature that has acquired ubiquity for its novel highlights and easy to understand interface. Not at all like customary membership based administrations, Vudu.com embraces a pay-more only as costs arise model, permitting clients to lease or buy individual titles without committing to a month to month membership.
The stage offers a different scope of content, including motion pictures, Network programs, and selective deliveries. Clients can peruse a broad library and look over different classes, making it an all inclusive resource for diversion devotees. In any case, the genuine unrest starts with the presentation of Vudu com Start.
Vudu com Start: Rethinking the Streaming Experience
Vudu com Start is a unique advantage in the streaming business, offering clients a consistent and upgraded seeing experience. We should investigate the key highlights that make Vudu com Start a progressive power in the realm of streaming.
Adaptability in Installment:
Vudu com Start embraces an adaptable installment model that separates it from conventional membership administrations. Clients have the opportunity to pick whether to lease or buy individual titles, giving a practical answer for the people who favor a pay-more only as costs arise approach. This adaptability in installment guarantees that clients just compensation for the substance they need to watch, killing the requirement for a month to month commitment.
Select Substance:
Vudu has teamed up with significant studios to bring clients selective substance that isn't accessible on other streaming stages. The Vudu com Start insurgency incorporates early admittance to new deliveries, selective extra highlights, and exceptional versions, giving clients an interesting and unrivaled diversion experience. This commitment to giving select substance separates Vudu.com and takes special care of clients who ache for something past the standard contributions.
Cross-Stage Openness:
The Vudu com Start upheaval reaches out to its cross-stage openness, permitting clients to partake in their #1 substance on various gadgets. Whether it's a brilliant television, gaming control center, computer, or cell phone, Vudu.com guarantees that clients can flawlessly change between screens without compromising the survey insight. This adaptability in availability mirrors the stage's devotion to meeting the assorted necessities of its client base.
Top notch Streaming:
Vudu is prestigious for its great streaming, offering clients the choice to watch content in up to 4K UHD goal with HDR support. The stage's commitment to conveying prevalent visual and sound quality upgrades the general survey insight, settling on it a go-to decision for cinephiles and devotees who focus on a realistic vibe in the comfort of their homes.
Instinctive UI:
The UI of Vudu is planned in light of effortlessness and accommodation. The natural design permits clients to explore easily through the stage, look for explicit titles, and find new satisfied. The Vudu com Start interface takes the client experience to a higher level, giving a problem free and charming excursion from perusing to playback.
Customized Recommendations:
The Vudu com Start transformation likewise incorporates a refined recommendation framework that examines client inclinations and review history to propose customized thoughts. This component guarantees that clients are ceaselessly finding content customized as they would prefer, making a really captivating and charming streaming experience.
Social Review Choices:
Vudu perceives the social part of amusement and presents social survey choices with Vudu com Start. Clients can associate with loved ones, share their #1 titles, and even host virtual film evenings. This social coordination adds a communal aspect to the real time insight, cultivating associations through shared interests in films and Programs.
Conclusion
In conclusion, the Vudu com Start transformation has essentially raised the streaming experience, setting another norm for the business. With its adaptable installment model, select substance, cross-stage openness, excellent streaming, natural UI, customized recommendations, and social review choices, Vudu com has arisen as an imposing player in the competitive universe of web-based features.
As the advanced scene keeps on developing, Vudu.com stays at the very front of advancement, continually adjusting to meet the changing requirements and inclinations of its client base. The Vudu com Start upheaval isn't just about watching content; it's tied in with making a dynamic and vivid amusement environment that takes special care of the different preferences and ways of life of clients around the world. As streaming devotees embrace this progressive stage, Vudu.com is ready to shape the eventual fate of on-request amusement.
0 notes
Text
Readiness of IT infrastructure

IT infrastructure: Why is it important?
As new technological advancements are embraced by enterprises across industries to leverage enormous benefits, it has also resulted in their dependence on modern IT infrastructure that is both efficient and intelligent. With technologies empowering businesses with operations and capabilities, the IT infrastructure has become the backbone of the digital transformation in these businesses.
Evolution and progress toward a digital economy have put forward a demand for strategic software-defined and intelligent infrastructure to power the journey of innovation. Webstep conveys business value with a deliberate and strategic approach to maintaining responsive, highly scalable, and fault-tolerant IT services. Our primary focus is to add to the capacities of the infrastructure to avoid unanticipated event failures such as service failures, performance degradations, network latency, limitations of system or storage capacity, and other unforeseen errors that may arise due to the complexity of enterprise IT systems and their IT footprint. Such modernization of infrastructure helps companies operate within a sophisticated, scalable environment with high availability.
Despite the ubiquity and evolution of cloud computing technology, its deployment is still considered in its infancy due lack of specific and sufficient tech architecture. While enterprises are reimagining and rebuilding their business by leveraging cloud technology, to exploit the full capabilities of technology of today and tomorrow, flexible yet robust infrastructure is crucial.
Webstep accelerates your cloud journey and supports your enterprise to unleash unprecedented capabilities and a competitive edge with seamless and secure services.
Where do you begin with your modern infrastructure?
To architect a strong footing foundation of modern infrastructure that unlocks business values, deliberate designing, and planning of a business-critical strategy should be the jump-off point. Webstep integrates first-rate expertise with best industry practices to engineer a security-centric, low-risk, and cost-efficient strategy– structured to deliver a seamless experience for our clients. To enable agility in the digital transformation of enterprises our initial process involves an assessment of the core processes to identify areas of change. The planned and structured approach followed by Webstep is backed by expert insights and aligned with a well-defined implementation plan that brings transformative and cloud-enabled business projects to life.
To bring the transformative opportunities of the cloud to clients, a tool-based framework is denied for migration and adoption. This assists in exploring the role of the cloud in an organization and engineering a sound business-driven cloud strategy that will empower the workforce and build business resilience.
IT Infrastructure Considerations: An Overview
Emerging cloud technology has plagued enterprises across the world as business leaders are recognizing its impact on the efficiency, scalability, resilience, and performance of their organizations. However, the adoption of sophisticated technology without a sound strategy and evolved architecture can add to its complexity. Here is an overview of some IT infrastructure considerations that can help overcome the associated challenges.
When is the right time to switch?
Adopting or migrating to modern technologies is demanding due to risky operations, especially for enterprises relying on a legacy system. An organization’s choice to do so is a radical shift that requires making significant changes in infrastructure and making it future-proof. It is crucial to move forward with expert consultation and strategy that supports the core of your organization and the objectives associated with this digital transformation. Just as beneficial, the process of cloud migration is complex with the critical elements of your business at stake.
Webstep consulting brings more value with a roadmap that navigates this complexity and regulates data sovereignty securely. There are several components of an enterprise that influences the cloud readiness of the organization. Some of these include organizational strategy, process, IT architecture, governance, and people. Consideration of these elements facilitates more controlled cloud adoption, higher security, enhanced performance, and deeper compliance with applications dependent on the legacy protocol.
Cloud Readiness
Cloud readiness for an enterprise can be assessed by defining four dimensions namely- business, technology, people, and processes. To derive the true value of the technology, the requirements of the business, the goals for the technology along with capital availability and investment are determined to ensure an agile yet cost-effective strategy of cloud deployment or migration. A customized strategy aligning with the various aspects of business goals enables enterprises to reap the benefits of the technology to the fullest extent.
In addition to basic business needs, the IT infrastructure (Readiness of IT infrastructure) is a defining factor for technological capabilities and the adoption of transformative technologies. The infrastructure foreshadows cloud adoption in terms of its availability as well as utilization. This also reflects on digital readiness and the demand for advanced services in the organization. The ability to utilize digital services is largely determined by the attitude along with the digital skills of the workforce. For smooth transition and dynamic engagement, the right balance between cloud technology and the legacy process is crucial. A tailored path for the implementation of a cloud-based solution is the answer to this.
Migrating your people to the cloud
Although cloud services bring functionality, usability, and mobility to the workforce, it requires careful consideration and a business-specific roadmap to ease the transition for people within the organization. It is imperative to bring together talent, culture, and technology to keep pace with the introduction of dynamic technologies. The strategic roadmap of adoption and implementation assists in simplifying business processes and creating a balance of complex legacy systems and advanced cloud-based solutions to eliminate any productivity issues or stress on business performance.
A challenge confronted by organizations making this radical shift is accommodating employee requirements while prioritizing the technology that can accelerate and amplify the journey of digital transformation. builds solutions by focusing on technical necessities, the combination of systems, customized workflows, and user demands to support an infrastructure prepared to migrate to the cloud. With a standard deployment schedule, we harmonize the process and accommodate immediate workforce demands with enterprise-grade cloud services. In a nutshell, to transition to a cloud solution and develop an environment for cloud technology to thrive, organizations need to ensure their strategic priorities support the workforce through the process and meet employee expectations too.
Readiness for Tomorrow
The evolution of your IT infrastructure today, can define the possibilities of tomorrow. Support of modern infrastructure can power your enterprise with cloud capabilities and create the foundation for continuous innovation. Accelerate change with modern, intelligent, and ever-ready infrastructure that empowers your business with exceptional services.
Get in touch with our experts to start your cloud journey today!
Contact Us:
Website URL — https://www.webstep.in
Address — Ground Floor, GC 38, GC Block,Sector III, Saltlake,Kolkata — 700106, India
1 note
·
View note
Text
Ubiquiti Networks Ubiquiti LITEBEAM M5
The LBE-M5-23 is the latest evolution of a lightweight and compact, outdoor wireless broadband CPE (Customer Premises Equipment) from Ubiquiti Networks. The LBE-M5-23 was designed to be an affordable cost/performance solution for long-distance, wireless broadband bridging. It operates in the worldwide, license-free 5 GHz frequency range and features high performance of up to 100+ Mbps in real…

View On WordPress
0 notes