#virtual evolved packet core
Explore tagged Tumblr posts
Text
Virtualized Evolved Packet Core Market Projected to Reach $19.87 Billion by 2031
According to the latest publication from Meticulous Research®, the virtualized evolved packet core (vEPC) market is projected to reach $19.87 billion by 2031, growing at a CAGR of 19.3% from 2024 to 2031. This growth is driven by the significant increase in mobile data traffic volumes and the rising demand for high-speed data services. However, data security risks associated with vEPC infrastructure pose challenges to market growth.
#Virtualized Evolved Packet Core Market#VEPC Market#Mobility Management Entity#Home Subscriber Server#Packet Data Network Gateway#Policy and Charging Rules Function#Mobile Private Network & Mobile Virtual Network Operator (MPN & MVNO)#Long-term Evolution & Voice over Long-term Evolution (LTE & VoLTE)#Telecom Operators#Internet of Things & Machine to Machine
0 notes
Text
PacketSDK & In-App Monetization: Choose your revenue method
As app development continues to evolve, the monetization strategy you choose determines your app's success and user satisfaction. Traditional in-app monetization methods, such as advertising, have always been used by the general public. But it has its own set of challenges and user experience trade-offs. On the other hand, the emergence of SDKs like Packet is changing the way developers monetize their apps.
Traditional in-app monetization
The most common ways to monetize apps include ads, in-app purchases, and subscriptions. These three monetization methods require developers or users to pay, which is likely to affect the user's experience.Advertising is based on high user traffic to generate significant returns. While advertising can be effective in generating revenue, it can degrade the user experience, especially if it is intrusive or poorly targeted, and can lead to lower app engagement and retention.
In-app purchases allow users to purchase virtual goods. It relies on a small percentage of users who actually consume it, directly contributing to the app's revenue. It is explicit and transactional, capable of providing a steady stream of revenue based on the user's investment in the app.However, apps with a subscription model continue to provide content or services, but they charge recurring fees.
Monetization methods of Packet SDK
The Packet SDK introduces a novel approach by integrating a monetization platform that works seamlessly within the app. Unlike traditional in-app monetization models, the Packet SDK runs in the background to download public data using the user's free, unused bandwidth. This approach does not interfere with user interaction and maintains a clean and pleasant user experience.At the same time, the Bright SDK is fully GDPR and CCPA compliant, prioritizing user privacy. It does not collect personal data and instead focuses on anonymized public data.
Advantages of Packet SDK over traditional in-app monetization methods
1. PacketSDK's monetization approach is designed to be inherently unobtrusive. By running in the background and without interfering with the core functionality of the app. This seamless integration means that users can enjoy the app without the need for constant reminders of monetization efforts, leading to a more positive user engagement and experience, and potentially higher user retention.
2. PacketSDK promises to provide a simpler integration process than traditional monetization methods. This ease of integration can dramatically reduce development time and increase complexity, allowing developers to focus more on core app functionality rather than monetization mechanisms.
3. PacketSDK focuses on non-personal data collection and ensures strict compliance with privacy laws. This approach builds trust with users by transparently prioritizing their privacy. For developers, this means navigating a relatively simple compliance environment and improving the app's security for privacy-conscious users.
At the same time, PacketSDK is now launching campaigns that can earn up to 150% of revenue in some regions. Become a PacketSDK partner today and learn how you can seamlessly integrate this monetization solution into your app to boost revenue.
2 notes
·
View notes
Text
CCNA Certification: Why It Matters for Networking Professionals

In the ever-evolving field of IT, staying updated with the right certifications can determine how fast and how far a professional can grow. One such globally recognized credential is the CCNA (Cisco Certified Network Associate) certification. If you're wondering what is CCNA, it's a foundational certification offered by Cisco that validates a networking professional’s skills in installing, configuring, and troubleshooting networks.
Understanding the Scope of CCNA
The CCNA certification is not just a badge; it's proof of your hands-on ability to work with Cisco networking equipment and technologies. It covers key concepts like:
IP addressing and subnetting
Routing and switching fundamentals
LAN/WAN technologies
Network security basics
Wireless networking
Automation and programmability
With the increasing demand for secure, scalable, and stable networks, professionals who understand these core areas are always in high demand.
Why CCNA Still Holds Relevance in 2025
Despite the rise of advanced certifications and cloud platforms, CCNA remains incredibly relevant. Here’s why:
1. Strong Foundation for a Networking Career
CCNA lays the groundwork for all other Cisco certifications and many non-Cisco ones too. It’s the first step into a world filled with routers, switches, firewalls, and cloud-connected infrastructure.
2. Industry Recognition
Cisco is a leader in the networking world. When employers see CCNA on your resume, they instantly recognize your capability to handle network-related tasks and challenges.
3. Global Validity
Whether you're applying for a job in your local city or overseas, CCNA is accepted worldwide. This opens doors to international career opportunities.
How CCNA Enhances Practical Networking Skills
CCNA isn’t just theory; it emphasizes practical knowledge. During your training or preparation, you will:
Set up real or virtual routers and switches
Create and troubleshoot networks
Configure routing protocols like OSPF
Implement Access Control Lists (ACLs)
Understand how NAT and DHCP work
This hands-on learning builds confidence and prepares you for on-the-job challenges.
Security Awareness with CCNA
One of the newer components of CCNA is its focus on network security. In an age where cyber threats are growing rapidly, understanding basic security principles like firewalls, password policies, and encryption is vital. CCNA introduces these topics to help you build networks that are not only functional but also secure.
The Role of CCNA in Cloud and Hybrid Networks
As businesses move to cloud-based infrastructure, network professionals are expected to understand how traditional networking integrates with platforms like AWS, Microsoft Azure, and Google Cloud. CCNA now touches on cloud and virtualization concepts, helping professionals bridge the gap between on-premises and cloud environments.
Who Should Get CCNA Certified?
Fresh graduates looking to enter the IT industry
Working professionals wanting to upskill or shift to networking
Support engineers aiming for network admin roles
System administrators managing on-premise and cloud-based networks
Freelancers and consultants offering network setup services
Even if you don’t work directly in networking, CCNA gives you a better understanding of how IT infrastructure works, making you more effective in any tech role.
Career Opportunities After CCNA
After earning your CCNA, many career paths open up:
Network Support Engineer
Network Administrator
Technical Support Engineer
System Engineer
Security Analyst (entry-level)
Junior Network Consultant
Once you gain some experience, you can move on to more specialized roles or pursue higher certifications like CCNP (Cisco Certified Network Professional).
Tips to Prepare for CCNA Certification
Understand the exam syllabus thoroughly
Use Cisco’s official study materials and labs
Practice using Packet Tracer or GNS3
Join online forums and study groups
Take practice tests to assess your progress
A consistent study schedule, combined with hands-on lab practice, is the best way to prepare effectively.
Final Thoughts
In the fast-paced world of IT, certifications like CCNA help professionals stay relevant, knowledgeable, and competitive. It’s more than just a credential; it’s a gateway into the networking domain with practical skills that can shape your entire career.
Whether you’re starting out or aiming to climb the career ladder, investing your time in learning what is CCNA and pursuing the certification can be one of the smartest moves you make. It validates your expertise, enhances your confidence, and connects you with global career opportunities in networking.
#CCNA#CiscoCertification#NetworkingProfessionals#NetworkEngineer#LearnNetworking#TechCareer#ITCertification#CybersecurityBasics#NetworkingSkills#CareerInTech#CCNA2025#NetworkSecurit
0 notes
Text
Network Switches Market Resilience and Risk Factors Impacting Growth to 2033
Introduction
The network switches market is a critical segment within the broader networking infrastructure industry, enabling data transfer across devices in enterprise, data center, and telecommunication environments. As digital transformation accelerates globally, network switches are becoming increasingly important in supporting data-intensive applications, cloud services, remote work, and the Internet of Things (IoT).
In 2024, the global network switches market is valued at approximately USD 32.5 billion, and it is projected to grow at a CAGR of 5.8%, reaching over USD 54.1 billion by 2032. The surge in bandwidth demand, rapid deployment of 5G, and migration to hyperscale data centers are among the key drivers of this growth.
Market Overview
A network switch is a hardware device that connects devices on a computer network using packet switching to forward data to its destination. Compared to hubs, switches are more efficient because they create a direct link between the sender and receiver. Switches operate primarily at Layer 2 (Data Link Layer) but can also function at Layer 3 (Network Layer) with routing capabilities.
They are categorized based on architecture, port speeds, application areas, and form factors. The evolving network landscape, especially with the rise of software-defined networking (SDN) and cloud-native architectures, is pushing the innovation frontier in switch technology.
Download a Free Sample Report:-https://tinyurl.com/2abrndj2
Market Drivers
1. Rising Data Traffic and Cloud Adoption
The explosion of digital services — from video streaming to AI and cloud computing — is placing unprecedented demands on network infrastructure. Hyperscale data centers and cloud service providers rely heavily on high-performance switches to handle massive traffic loads and ensure seamless connectivity.
2. 5G Rollouts and Edge Computing
As telecom operators deploy 5G networks, the need for low-latency, high-bandwidth switching at the edge and core is growing. Network switches are vital in building out robust edge infrastructure to support use cases like autonomous vehicles, remote healthcare, and smart cities.
3. Proliferation of IoT Devices
The exponential rise of connected devices—from smart appliances to industrial sensors—requires agile and scalable switching solutions. Switches with greater port density and intelligent traffic handling are essential for supporting the IoT ecosystem.
4. Data Center Modernization
Businesses are upgrading from legacy networks to modern architectures using leaf-spine topology, SDN, and virtualization. Modern switches support programmability, automation, and high throughput, meeting the needs of hybrid cloud environments.
Market Challenges
Despite strong growth prospects, the market faces a few headwinds:
High Capital Costs: Advanced switches with higher port speeds (40G, 100G, 400G) can be expensive, limiting adoption in small and medium enterprises.
Cybersecurity Risks: Network switches can be targeted by hackers to disrupt or eavesdrop on communications. Ensuring security in programmable switches is a growing concern.
Complex Network Management: Managing large-scale networks with multi-vendor switches can lead to interoperability and configuration challenges.
Market Segmentation
By Type
Managed Switches
Unmanaged Switches
Smart Switches
PoE (Power over Ethernet) Switches
Modular vs. Fixed Configuration Switches
Managed switches dominate the market due to their configurability, monitoring capabilities, and suitability for enterprise environments.
By Port Speed
1G (Gigabit Ethernet)
10G
25G
40G
100G
400G and Beyond
With increasing demands for high throughput, 100G switches are becoming standard in data centers, while 400G is gaining traction among hyperscalers and telecom operators.
By Application
Data Centers
Enterprises
Telecommunications
Industrial Networks
Others (Education, Government, etc.)
The data center segment is the largest consumer due to the growing need for scalable, high-speed connectivity solutions in private and public cloud infrastructure.
By End-User
IT & Telecom
BFSI
Healthcare
Retail
Manufacturing
Media & Entertainment
Sectors like BFSI and healthcare require highly secure and low-latency network infrastructure to support sensitive applications and real-time data processing.
By Region
North America
Europe
Asia-Pacific
Latin America
Middle East & Africa
Regional Insights
North America
North America is a mature market, with strong demand from cloud service providers, tech companies, and government sectors. The U.S. leads in adopting cutting-edge technologies like 400G switching and intent-based networking.
Europe
Countries like Germany, the UK, and the Netherlands are driving network infrastructure investments. Stringent data privacy regulations like GDPR are increasing demand for secure and compliant switching technologies.
Asia-Pacific
This region is experiencing the fastest growth, fueled by large-scale digitization in China, India, and Southeast Asia. Government initiatives like "Digital India" and the expansion of 5G are major contributors.
Latin America & MEA
While still emerging, these regions are seeing rising adoption due to telecom infrastructure upgrades and smart city projects. Partnerships with global vendors are helping bridge technology gaps.
Competitive Landscape
The network switches market is highly competitive, with major players investing heavily in R&D, strategic alliances, and product innovation to maintain market leadership.
Key Players:
Cisco Systems, Inc.
Juniper Networks, Inc.
Hewlett Packard Enterprise (HPE)
Arista Networks, Inc.
Huawei Technologies Co., Ltd.
Dell Technologies
Extreme Networks
Fortinet, Inc.
Nokia Corporation
TP-Link Technologies
Cisco remains a dominant force with its Catalyst and Nexus product lines, while Arista leads in cloud networking with ultra-low latency switches.
Technological Trends
1. AI-Powered Network Management
Artificial intelligence and machine learning are being integrated into switches for predictive analytics, anomaly detection, and self-healing networks, enhancing performance and reliability.
2. Intent-Based Networking (IBN)
IBN allows administrators to define desired outcomes, and the system automatically configures switches to achieve those outcomes. It is revolutionizing network management in enterprise environments.
3. Open Networking & Disaggregation
The shift from proprietary systems to white-box switches with open-source operating systems like SONiC is giving enterprises more control and flexibility.
4. Green Networking
Vendors are increasingly focusing on energy-efficient switch designs that reduce power consumption, aligning with ESG goals and operational cost reduction.
Future Outlook
The future of the network switches market is shaped by megatrends such as:
Widespread 5G adoption fueling edge and core upgrades.
Growing demand for hybrid and multi-cloud infrastructure requiring flexible and programmable switches.
Expansion of enterprise Wi-Fi 6/6E and 7 driving higher throughput backbones.
Emergence of 800G switches on the horizon for ultra-high bandwidth applications.
Investments in automation, software-defined capabilities, and interoperability will remain crucial to address the rising complexity of modern networks.
Conclusion
The network switches market is poised for robust growth through 2032, underpinned by the digital transformation of businesses, proliferation of connected devices, and demand for high-speed, scalable, and intelligent network infrastructure. As organizations continue to modernize their IT environments and embrace edge computing and AI, the role of network switches as the backbone of digital communication will only grow more prominent. Forward-thinking companies that invest in next-generation switching technologies will be well-positioned to harness the full potential of the connected world.
Read Full Report:-https://www.uniprismmarketresearch.com/verticals/semiconductor-electronics/network-switches
0 notes
Text
0 notes
Text
Understanding the Role of Networking Switches in Modern Connectivity
Networking switches play a crucial role in building efficient, high-performance networks, especially in today’s digitally driven landscape where seamless connectivity is vital. Acting as the nerve centers of network infrastructure, these devices manage data flow between devices, ensuring that data packets reach their intended destinations swiftly and securely. For businesses and individuals alike, understanding the functionality of networking switches can provide significant advantages in optimizing network performance and maintaining secure data flow.
At its core, a networking switch operates by connecting multiple devices within a network, such as computers, servers, and printers, to enable communication between them. Unlike hubs, which simply broadcast data to all connected devices, switches analyze incoming data packets and send them directly to the designated device. This targeted approach minimizes network congestion and reduces data collisions, enhancing overall network speed and reliability. Networking switches are also highly scalable, capable of handling small office setups as well as complex enterprise networks that support thousands of devices.
Security is another critical benefit of using networking switches. Modern switches are equipped with advanced features like VLANs (Virtual Local Area Networks), which isolate data flow between devices, reducing the risk of unauthorized access and ensuring data privacy within various segments of the network. They also support network access controls and firewalls, adding another layer of protection against cyber threats. Additionally, switches provide network monitoring capabilities, allowing administrators to track data flow and manage bandwidth effectively. This is essential in troubleshooting and optimizing network performance.
In an era where technology evolves rapidly, networking switches continue to adapt to meet the growing demands for speed, bandwidth, and connectivity. Managed switches, for instance, give administrators complete control over traffic prioritization, data routing, and network segmentation, ensuring optimized performance and resource allocation. Unmanaged switches, on the other hand, offer simpler plug-and-play solutions for smaller networks, making them ideal for basic connectivity needs. Selecting the right type of networking switch can significantly impact network efficiency, enabling organizations to scale their networks as they grow.
Ultimately, networking switches are indispensable components in any digital infrastructure, contributing to the secure, efficient, and scalable networks that businesses and individuals rely on. Whether you’re setting up a simple home office or managing a complex enterprise system, choosing the appropriate networking switch is essential for achieving optimal connectivity and performance.
0 notes
Text
A Comprehensive Guide to Next-Generation Networks

Next-generation networks (NGNs) represent a critical leap forward in telecommunications, bringing together various services into a unified platform. Unlike traditional networks, which operate on separate infrastructures for voice, data, and video services, NGNs integrate these into one. This convergence simplifies operations and offers numerous benefits in terms of cost savings, scalability, and service delivery.
Key Features of NGNs
At the core of NGNs is the use of Internet Protocol (IP) to transmit a wide range of data, including voice, video, and multimedia. This shift is similar to how IP-based internet data packets revolutionized communication, allowing the efficient transmission of information across different formats. NGNs employ packet-switching technology, which ensures that all types of communication, from emails to video calls, are handled more efficiently.
NGNs are also designed to be more adaptable and future-proof. Their architecture is based on software-defined networking (SDN), which separates the control and data planes. This structure allows for more flexible network management and enables rapid deployment of new services without the need for costly hardware updates.
Improved Efficiency and Cost Reduction
The traditional telecom infrastructure often involved multiple, separate systems for different services. Maintaining these siloed systems required significant investment in hardware, operations, and management. NGNs eliminate this redundancy by allowing voice, data, and video to be transmitted through the same network, leading to reduced infrastructure costs.
Service providers can thus manage their networks more effectively, reducing operational expenditures. Additionally, users benefit from higher-quality service, as NGNs offer more reliable connections and faster data speeds.
Scalability and Flexibility
Another major advantage of NGNs is their scalability. As the demand for bandwidth-intensive applications such as video streaming and online gaming continues to grow, traditional networks can struggle to keep up. NGNs, however, are built to handle large volumes of traffic while maintaining high-speed performance.
Furthermore, their flexible nature allows for easy integration with emerging technologies, such as 5G, IoT (Internet of Things), and cloud services. This makes NGNs essential for future innovations in smart cities, autonomous vehicles, and beyond.
Enhanced Security and Privacy
With the increased volume and complexity of data being transmitted, security is a top concern in modern telecommunications. NGNs employ advanced encryption methods and cybersecurity protocols to protect sensitive information. Additionally, the use of SDN and network function virtualization (NFV) allows for real-time monitoring and quick response to potential threats, ensuring that users’ data remains secure.
For More Information :
Conclusion
Next-generation networks are a significant advancement in how communication services are delivered and managed. By integrating multiple services into a single, unified platform, they offer increased efficiency, scalability, and security. As technology continues to evolve, NGNs will play an essential role in supporting the growing demands of both businesses and consumers.
0 notes
Text
The Growing Virtualized Evolved Packet Core (vEPC) Market: Driving Next-Gen Connectivity
The Virtualized Evolved Packet Core (vEPC) Market was valued at USD 8.1 billion in 2023 and will surpass USD 23.5 billion by 2030; growing at a CAGR of 16.4% during 2024 - 2030. At the heart of this transformation is the Evolved Packet Core (EPC), the core network architecture for LTE (Long-Term Evolution) and 4G networks. However, as the demand for data grows and the transition to 5G accelerates, traditional EPC systems are struggling to keep up. Enter the Virtualized Evolved Packet Core (vEPC) – a next-generation solution that is redefining how networks are built and managed.
Understanding vEPC
Virtualized Evolved Packet Core (vEPC) refers to the deployment of EPC functions using Network Functions Virtualization (NFV) technology. In a traditional EPC, network functions like the Serving Gateway (SGW), Packet Data Network Gateway (PGW), and Mobility Management Entity (MME) are implemented on dedicated hardware. In contrast, vEPC decouples these functions from physical hardware, allowing them to run as software instances on standard, off-the-shelf servers in a virtualized environment.
This shift to virtualization brings numerous benefits, including improved flexibility, scalability, and cost-efficiency. By leveraging NFV, service providers can dynamically allocate resources based on demand, scale their networks quickly, and reduce capital and operational expenditures. This makes vEPC an essential component in the evolution towards 5G networks and beyond.
Get a Sample Report: https://intentmarketresearch.com/request-sample/virtualized-evolved-packet-core-vepc-market-3649.html
Market Growth Drivers
The vEPC market is experiencing robust growth, driven by several key factors:
5G Rollout: As 5G networks become more widespread, the need for scalable and flexible core network solutions is paramount. vEPC provides the necessary foundation for 5G by enabling faster deployment, efficient resource utilization, and the ability to support diverse use cases, from enhanced mobile broadband to massive IoT connectivity.
Increased Data Traffic: The exponential growth in mobile data traffic, fueled by video streaming, social media, and IoT applications, is putting immense pressure on traditional network infrastructures. vEPC allows service providers to handle this surge in data traffic more effectively, ensuring seamless connectivity and improved user experiences.
Cost Efficiency: Virtualization reduces the need for expensive, proprietary hardware, enabling service providers to lower their capital and operational expenditures. Additionally, the ability to scale resources up or down based on demand helps in optimizing network costs, making vEPC a more cost-effective solution compared to traditional EPC.
Network Slicing: A key feature of 5G is network slicing, which allows operators to create multiple virtual networks on a single physical infrastructure, each tailored to specific applications or services. vEPC plays a critical role in enabling network slicing by providing the flexibility and agility needed to create and manage these virtual networks efficiently.
Rapid Time-to-Market: In today’s fast-paced environment, the ability to launch new services quickly is crucial for staying competitive. vEPC enables service providers to reduce the time-to-market for new services by streamlining network deployment and management processes.
Market Challenges
While the vEPC market presents significant opportunities, it also faces challenges that could impact its growth:
Interoperability Issues: As vEPC involves integrating various network functions from different vendors, ensuring interoperability can be challenging. Service providers must carefully select compatible solutions to avoid integration issues that could lead to network performance degradation.
Security Concerns: Virtualized environments can be more vulnerable to security threats compared to traditional hardware-based systems. Ensuring robust security measures are in place is critical to protect sensitive data and maintain network integrity.
Skills Gap: The transition to virtualized networks requires new skill sets that may not be readily available within existing telecom teams. Investing in training and upskilling is necessary to fully leverage the benefits of vEPC.
Get an insights of Customization: https://intentmarketresearch.com/ask-for-customization/virtualized-evolved-packet-core-vepc-market-3649.html
The Future of vEPC
Looking ahead, the vEPC market is poised for continued growth as more service providers embrace virtualization and move towards 5G. The flexibility, scalability, and cost-efficiency offered by vEPC will be key to supporting the diverse and demanding use cases of future networks. As the technology matures, we can expect further innovations in areas such as automation, orchestration, and edge computing, all of which will enhance the capabilities of vEPC and drive its adoption.
0 notes
Text
0 notes
Text
#Virtualized Evolved Packet Core Market#VEPC Market#Mobility Management Entity#Home Subscriber Server#Packet Data Network Gateway#Policy and Charging Rules Function#Mobile Private Network & Mobile Virtual Network Operator (MPN & MVNO)#Long-term Evolution & Voice over Long-term Evolution (LTE & VoLTE)#Telecom Operators#Internet of Things & Machine to Machine
0 notes
Text
IPLOOK's Mid-Year Featured Products
As we reach the halfway point of 2024, we're thrilled to present our mid-year lineup of standout products that have captivated clients worldwide! Discover the Top 3 products that have propelled IPLOOK forward:
EPC (Evolved Packet Core) Network

Our EPC continues to be a market leader, delivering robust and scalable LTE connectivity, and supporting smooth upgrades to 5G with a seamless experience. The standout performance of our MME and xGW components has fueled significant growth. With full virtualization and high scalability, our EPC empowers operators to realize flexible scaling and optimize network efficiency at a competitive price.
5GC (5G Core) Network
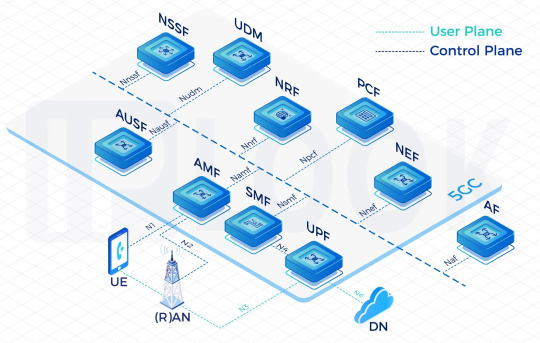
Leading the charge into the future is our 5GC. IPLOOK's cloud-native 5GC offers unparalleled flexibility, improved capabilities and enhanced user experiences. Supporting both NSA and SA architectures, our dual-mode 5GC is designed to provide future-proof support for legacy networks, ideal for operators to unleash the full potential of 5G.
IMS (IP Multimedia Subsystem) Core Network

Our IMS is the cornerstone of a broad range of high-quality voice applications. With a focus on VoLTE, VoWiFi (Wi-Fi calling), and VoNR, we enable reliable and seamless communication across any network.
Contact us at [email protected] for any inquiries!
Source: https://www.iplook.com/info/iplooks-mid-year-featured-products-i00419i1.html
0 notes
Text
Automatic Identification and Data Capture Market: Dissecting the Factors Steering Growth and Potential Risks
Automatic Identification and Data Capture Market provides in-depth analysis of the market state of Automatic Identification and Data Capture manufacturers, including best facts and figures, overview, definition, SWOT analysis, expert opinions, and the most current global developments. The research also calculates market size, price, revenue, cost structure, gross margin, sales, and market share, as well as forecasts and growth rates. The report assists in determining the revenue earned by the selling of this report and technology across different application areas.
Geographically, this report is segmented into several key regions, with sales, revenue, market share and growth Rate of Automatic Identification and Data Capture in these regions till the forecast period
North America
Middle East and Africa
Asia-Pacific
South America
Europe
Key Attentions of Automatic Identification and Data Capture Market Report:
The report offers a comprehensive and broad perspective on the global Automatic Identification and Data Capture Market.
The market statistics represented in different Automatic Identification and Data Capture segments offers complete industry picture.
Market growth drivers, challenges affecting the development of Automatic Identification and Data Capture are analyzed in detail.
The report will help in the analysis of major competitive market scenario, market dynamics of Automatic Identification and Data Capture.
Major stakeholders, key companies Automatic Identification and Data Capture, investment feasibility and new market entrants study is offered.
Development scope of Automatic Identification and Data Capture in each market segment is covered in this report. The macro and micro-economic factors affecting the Automatic Identification and Data Capture Market
Advancement is elaborated in this report. The upstream and downstream components of Automatic Identification and Data Capture and a comprehensive value chain are explained.
Browse More Details On This Report at @https://www.globalgrowthinsights.com/market-reports/automatic-identification-and-data-capture-market-100569
Global Growth Insights
Web: https://www.globalgrowthinsights.com
Our Other Reports:
Mono Methyl Aniline MarketMarket Size
Global Faux Leather MarketMarket Share
Global Functional Glass Coatings MarketMarket Growth
HVDC Converter Station MarketMarket
Virtual Production MarketMarket Share
Release Liner MarketMarket Growth Rate
Supply Chain Strategy and Operations Consulting MarketMarket Forecast
Global High-Performance Computing (HPC) MarketMarket Size
Microbiological safety Cabinet MarketMarket Growth
Content MarketMarket Analysis
Zigbee and Thread Wireless Sensor MarketMarket Size
Global Oil & Gas Analytics MarketMarket Share
Global Digital Logistics MarketMarket Growth
Digital Textile Printing Ink MarketMarket
Automotive Carbon Thermoplastic MarketMarket Share
Intelligent Hearing Protection Device MarketMarket Growth Rate
Virtualized Evolved Packet Core (vEPC) MarketMarket Forecast
Global Cannabis Extract Or Flower MarketMarket Size
Dental 3D Printer MarketMarket Growth
Legal Analytics MarketMarket Analysis
Indoor Unmanned Delivery Robot MarketMarket Size
Global High Pressure Processing (HPP) Food MarketMarket Share
Global Commercial Washer MarketMarket Growth
Lutetium-177 MarketMarket
BIPV Module MarketMarket Share
Regenerated Cellulose MarketMarket Growth Rate
Carpet Manufacturing Machines MarketMarket Forecast
Global Floating Production System MarketMarket Size
Holographic Lamination Film MarketMarket Growth
Cefprozil MarketMarket Analysis
Contract Logistics MarketMarket Size
Global Used Car MarketMarket Share
Global Pullulan MarketMarket Growth
Floating Production Storage and Offloading Vessels MarketMarket
Dill Seed Oil MarketMarket Share
Ai-based Visual Inspection Software MarketMarket Growth Rate
EMI Suppression Capacitor MarketMarket Forecast
Global Massage Mats MarketMarket Size
Air Carbon Arc Gouging Torch MarketMarket Growth
Verisyse Lens MarketMarket Analysis
0 notes
Text
https://www.verifiedmarketreports.com/product/virtualized-evolved-packet-core-market-size-and-forecast/
0 notes
Text
what is an ipsec vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is an ipsec vpn
IPSec Protocol
Title: Understanding IPSec Protocol: Securing Network Communications
In the realm of network security, IPSec (Internet Protocol Security) stands tall as a fundamental protocol for safeguarding data transmissions across the internet. It operates at the network layer, providing encryption, authentication, and integrity verification for IP packets. IPSec ensures that sensitive information remains confidential and untampered with during transit, crucial for maintaining the integrity of communications in today's interconnected world.
At its core, IPSec consists of two main components: Authentication Header (AH) and Encapsulating Security Payload (ESP). AH primarily provides data integrity and authentication without encryption, whereas ESP offers encryption, authentication, and data integrity protection. Together, they form a robust framework for securing IP communications.
One of the primary uses of IPSec is in virtual private networks (VPNs), where it establishes secure tunnels between devices or networks over the internet. This allows organizations to create encrypted connections over potentially insecure networks, such as the public internet, ensuring that sensitive data remains protected from eavesdropping and unauthorized access.
Moreover, IPSec can be deployed in various modes, including Transport mode and Tunnel mode. Transport mode encrypts only the data portion of each IP packet, leaving the header untouched, while Tunnel mode encrypts the entire IP packet, including both header and data. This flexibility enables tailored security configurations based on specific network requirements.
Furthermore, IPSec supports various cryptographic algorithms and key exchange protocols, allowing organizations to adapt their security measures to meet evolving threats and compliance standards.
In conclusion, IPSec plays a vital role in securing network communications by providing robust encryption, authentication, and integrity verification mechanisms. Whether used in VPNs, remote access scenarios, or site-to-site communications, IPSec remains a cornerstone of modern network security architectures, ensuring the confidentiality and integrity of data in transit.
Virtual Private Network (VPN)
A Virtual Private Network (VPN) is a crucial tool for safeguarding your online privacy and security. Essentially, it creates a secure connection between your device and the internet by encrypting your internet traffic and routing it through a remote server. This process shields your data from prying eyes, such as hackers, government surveillance, or internet service providers (ISPs).
One of the primary benefits of using a VPN is anonymity. By masking your IP address, VPNs prevent websites, advertisers, and other third parties from tracking your online activities. This anonymity enhances your privacy and protects your personal information from being harvested for targeted ads or other purposes.
Moreover, VPNs are invaluable for accessing geo-restricted content. By connecting to a server in a different location, you can bypass censorship or access online services and websites that may be restricted in your country. This feature is particularly useful for travelers who want to access their favorite streaming services or for individuals living in countries with stringent internet regulations.
Security-wise, VPNs provide an extra layer of defense against cyber threats when using public Wi-Fi networks. These networks are often vulnerable to hackers who can intercept your data packets. However, with a VPN encrypting your traffic, even if a hacker manages to intercept it, they won't be able to decipher the information.
It's important to note that while VPNs offer numerous benefits, not all VPN services are created equal. Users should research and select a reputable provider that offers strong encryption, a no-logs policy, and reliable connection speeds. Additionally, while VPNs enhance privacy and security, they are not foolproof, and users should still practice good online habits, such as using strong, unique passwords and keeping software up to date.
Tunneling Technology
Tunneling technology plays a pivotal role in the modern world by enabling the construction of underground passageways for various purposes. From transportation to utility infrastructure, tunneling technology offers a versatile and efficient way to create pathways beneath the surface.
One of the key benefits of tunneling technology is its ability to minimize surface disruptions during construction. By digging underground, projects can proceed without interfering with existing structures or activities above ground. This is particularly advantageous in urban areas where space is limited, and traditional construction methods may cause significant disruptions.
Furthermore, tunneling technology allows for the construction of underground transportation networks, such as subways and tunnels for roadways. These tunnels help alleviate traffic congestion, improve transportation efficiency, and enhance connectivity between different parts of a city or region.
In addition to transportation, tunneling technology is also essential for creating underground utility tunnels for water, sewage, gas, and electrical systems. By burying these essential utilities underground, they are protected from external factors such as weather and potential damage, ensuring a reliable and secure infrastructure system.
Overall, tunneling technology is a versatile and valuable tool for modern construction projects. Its ability to create underground passageways efficiently, while minimizing surface disruptions, makes it a go-to solution for various infrastructure needs. As technology continues to advance, tunneling methods are likely to become even more sophisticated and effective, further enhancing their role in shaping the world beneath our feet.
Data Encryption
Data encryption is a crucial aspect of modern digital security, playing a vital role in safeguarding sensitive information from unauthorized access or interception. Essentially, encryption involves the transformation of data into a format that is unintelligible without the appropriate decryption key. This process ensures that even if unauthorized individuals gain access to the encrypted data, they cannot decipher its contents.
One of the primary purposes of data encryption is to protect confidentiality. By encrypting data, organizations can secure personal, financial, and proprietary information, preventing it from being compromised by cybercriminals or malicious actors. This is particularly important in industries such as healthcare, finance, and e-commerce, where the loss or theft of sensitive data can have severe consequences for both individuals and businesses.
Encryption also helps to ensure the integrity of data by detecting any unauthorized modifications or tampering attempts. By using cryptographic algorithms and digital signatures, organizations can verify the authenticity of data and confirm that it has not been altered in transit or storage.
Moreover, data encryption is essential for regulatory compliance, as many laws and standards require organizations to implement adequate measures to protect sensitive information. For example, regulations like the General Data Protection Regulation (GDPR) in Europe and the Health Insurance Portability and Accountability Act (HIPAA) in the United States mandate the use of encryption to safeguard personal data and medical records.
In summary, data encryption is a fundamental component of cybersecurity, providing a crucial layer of defense against unauthorized access, data breaches, and cyber attacks. By encrypting sensitive information, organizations can uphold confidentiality, maintain data integrity, and comply with regulatory requirements, thereby mitigating the risks associated with the modern digital landscape.
Network Security
Title: Safeguarding Digital Fortresses: Understanding the Vitality of Network Security
In today's interconnected digital landscape, network security stands as the bedrock of safeguarding sensitive information and maintaining operational integrity. It encompasses a myriad of technologies, processes, and practices designed to protect networks, devices, and data from unauthorized access, misuse, or breaches.
At its core, network security involves implementing robust defenses against a plethora of cyber threats, including malware, phishing attacks, data breaches, and unauthorized access attempts. This proactive approach not only mitigates risks but also ensures continuity of operations, bolstering trust among users and stakeholders.
One of the fundamental components of network security is firewall protection, which acts as a barrier between internal networks and external threats, filtering incoming and outgoing traffic based on predefined security rules. Additionally, encryption plays a pivotal role in securing data in transit, rendering it unreadable to unauthorized parties even if intercepted.
Furthermore, the implementation of robust authentication mechanisms, such as multi-factor authentication (MFA) and biometric authentication, adds an extra layer of security, reducing the likelihood of unauthorized access to critical systems and resources.
Moreover, regular security assessments, vulnerability scans, and penetration testing are imperative to identify and address potential weaknesses within the network infrastructure proactively. This proactive approach enables organizations to stay ahead of emerging threats and adapt their security posture accordingly.
In an era characterized by sophisticated cyber threats and evolving attack vectors, investing in robust network security measures is not just a choice but a necessity. By prioritizing network security, organizations can fortify their digital fortresses, safeguard sensitive information, and uphold the trust and confidence of their stakeholders in an increasingly interconnected world.
0 notes
Text
what is ipsec vpn tunnel
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is ipsec vpn tunnel
IPsec protocol
Title: Understanding IPsec Protocol: Securing Network Communications
In the realm of network security, the IPsec protocol stands as a stalwart guardian, fortifying the integrity and confidentiality of data transmissions across networks. Short for Internet Protocol Security, IPsec operates at the network layer (Layer 3) of the OSI model, ensuring a secure communication channel between two or more devices.
At its core, IPsec provides a framework for authenticating and encrypting IP packets, effectively safeguarding sensitive information from unauthorized access and tampering. This protocol is particularly vital in today's interconnected world, where data traverses through various networks, including public internet connections, which can be susceptible to interception and eavesdropping.
IPsec employs two main security mechanisms: Authentication Header (AH) and Encapsulating Security Payload (ESP). AH primarily focuses on data integrity and authentication, ensuring that the contents of the packet remain unchanged during transit and verifying the identity of the sender. On the other hand, ESP offers encryption services, concealing the payload of the packet from prying eyes and mitigating the risk of data interception.
One of the notable advantages of IPsec is its flexibility and compatibility with different network topologies and protocols, making it a versatile solution for securing a wide range of communications, including remote access VPNs, site-to-site VPNs, and even securing individual applications.
Implementing IPsec requires careful planning and configuration, with considerations for key management, security policies, and compatibility with existing network infrastructure. Despite its complexity, the benefits of deploying IPsec are immense, offering organizations a robust defense against network threats and ensuring the confidentiality, integrity, and authenticity of their data transmissions.
In conclusion, the IPsec protocol serves as a cornerstone of modern network security, empowering organizations to establish secure and reliable communication channels in an increasingly interconnected digital landscape. By leveraging the capabilities of IPsec, businesses can bolster their defenses against evolving cyber threats and uphold the confidentiality of their sensitive information.
VPN tunnel encryption
VPN tunnel encryption plays a crucial role in safeguarding online privacy and security. Essentially, a VPN (Virtual Private Network) establishes a secure connection, or tunnel, between your device and the internet. Within this tunnel, all data transmitted is encrypted, making it unreadable to anyone attempting to intercept it.
The encryption process involves encoding data into a format that can only be deciphered with the correct decryption key. In the context of VPNs, encryption algorithms such as AES (Advanced Encryption Standard) are commonly utilized. AES is highly regarded for its strength and efficiency in securing data.
When you connect to a VPN, your data is encrypted before it leaves your device and travels through the tunnel to the VPN server. This means that even if someone manages to intercept your data, they won't be able to make sense of it without the decryption key.
VPN tunnel encryption provides several benefits:
Privacy Protection: Encryption ensures that your online activities remain private. Whether you're browsing the web, accessing sensitive information, or communicating with others, your data is shielded from prying eyes.
Security: By encrypting data, VPNs help prevent unauthorized access and protect against cyber threats such as hacking, data theft, and surveillance.
Anonymity: VPN tunnel encryption masks your IP address and location, enhancing anonymity and reducing the risk of tracking and profiling.
Secure Remote Access: For businesses and remote workers, VPN tunnel encryption enables secure access to corporate networks and resources from any location.
Overall, VPN tunnel encryption is a fundamental aspect of VPN technology, providing users with peace of mind and confidence in their online activities. By encrypting data transmissions, VPNs offer a layer of security that is essential in today's interconnected digital landscape.
Secure data transmission
Title: Ensuring Secure Data Transmission: A Vital Imperative in Today's Digital Landscape
In an era where digital interactions dominate nearly every aspect of our lives, the security of data transmission stands as a paramount concern. Whether it's personal information shared during online transactions or sensitive corporate data exchanged between offices, safeguarding data during its journey across networks is imperative to maintaining privacy, integrity, and trust.
Secure data transmission involves employing various protocols and technologies to protect information as it travels from one point to another. Encryption, a fundamental aspect of secure transmission, scrambles data into an unreadable format, ensuring that even if intercepted, it remains unintelligible to unauthorized parties. Advanced encryption standards (AES), for instance, are widely utilized to secure data across networks, providing robust protection against interception and tampering.
Moreover, secure data transmission often relies on secure communication protocols such as Transport Layer Security (TLS) and Secure Sockets Layer (SSL). These protocols establish encrypted connections between devices, ensuring that data exchanged between them remains confidential and tamper-proof. Additionally, digital signatures and certificates play a crucial role in verifying the authenticity and integrity of transmitted data, mitigating the risk of unauthorized access or data manipulation.
Implementing secure data transmission practices is essential not only for safeguarding sensitive information but also for complying with regulatory requirements such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). Failure to adhere to these standards can result in severe repercussions, including financial penalties and reputational damage.
In conclusion, ensuring secure data transmission is indispensable in mitigating the risks associated with digital communication. By adopting robust encryption techniques, secure protocols, and compliance measures, individuals and organizations can fortify their data against unauthorized access and interception, thereby fostering trust and confidence in the digital ecosystem.
Virtual Private Network technology
A Virtual Private Network (VPN) is a powerful technology that allows users to create a secure and encrypted connection over a less secure network, such as the internet. By using a VPN, users can ensure that their online activities remain private and protected from potential cyber threats.
One of the key benefits of using a VPN is the ability to mask one's IP address. This means that users can browse the internet anonymously, making it more difficult for hackers and other malicious entities to track their online movements. Additionally, VPNs can help users bypass geo-restrictions and censorship, allowing them to access content that may be otherwise unavailable in their region.
Furthermore, VPNs provide an extra layer of security when using public Wi-Fi networks. These networks are often unsecure, making users vulnerable to cyber attacks. By using a VPN, users can encrypt their data and protect themselves from potential hacking attempts.
Businesses also benefit from VPN technology by allowing employees to securely access company resources from remote locations. This is especially useful for remote workers or employees who frequently travel for work.
In conclusion, VPN technology plays a crucial role in ensuring online security and privacy for individuals and businesses alike. By utilizing a VPN, users can enjoy a more secure and unrestricted online experience.
Internet Protocol Security VPN
Internet Protocol Security VPN, commonly known as IPSec VPN, is a secure method of creating a virtual private network over the internet. It allows for secure communication by encrypting data between two devices or networks.
IPSec VPN operates at the network layer of the OSI model and provides authentication, integrity, and confidentiality of data transmitted over the network. It is widely used by businesses to ensure secure remote access for employees working from home or traveling.
One of the key features of IPSec VPN is its ability to establish secure communication tunnels between devices using cryptographic protocols. These tunnels ensure that data is encrypted before it is transmitted and decrypted upon arrival at the destination. This encryption process prevents unauthorized access to sensitive information, making IPSec VPN a popular choice for protecting data privacy.
Another benefit of IPSec VPN is its flexibility in supporting different types of connections, such as site-to-site VPNs for connecting multiple offices or remote access VPNs for individual users. This versatility makes it a versatile solution for businesses of all sizes looking to securely connect their networks.
Overall, IPSec VPN is a powerful tool for safeguarding data integrity and confidentiality over the internet. Its robust security features and scalability make it an ideal choice for businesses seeking to enhance their network security and protect sensitive information from cyber threats.
0 notes
Text
what is point to point vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
what is point to point vpn
Point-to-Point VPN Definition
A Point-to-Point VPN, short for Virtual Private Network, is a secure connection between two devices or networks over the internet. It allows data to be transmitted privately and securely between these two points, making it an essential tool for businesses, remote workers, and anyone concerned about their online privacy.
At its core, a Point-to-Point VPN creates a virtual tunnel between the two endpoints, encrypting all data that passes through it. This encryption ensures that even if the data is intercepted, it remains unreadable to anyone without the proper decryption keys.
One of the primary uses of a Point-to-Point VPN is to connect remote offices or branch locations to a central network securely. By establishing a VPN connection between these sites, employees can access shared resources, such as files, applications, and databases, as if they were physically present in the same office. This improves collaboration and productivity while maintaining a high level of security.
Another common application of Point-to-Point VPNs is to enable secure remote access for employees working from home or on the go. By connecting to a VPN server hosted by their employer, remote workers can access company resources securely, even when using unsecured public Wi-Fi networks.
In addition to business use cases, Point-to-Point VPNs are also popular among individual users who want to protect their online privacy and security. By encrypting their internet traffic and masking their IP address, VPN users can browse the web anonymously and bypass censorship or geo-restrictions.
Overall, Point-to-Point VPNs play a crucial role in today's interconnected world by providing a secure way to transmit data between two points over the internet. Whether used for business purposes or personal privacy, VPNs have become an essential tool for ensuring secure communication in an increasingly digital landscape.
Point-to-Point VPN Architecture
Point-to-Point VPN Architecture: Enhancing Secure Connectivity
Point-to-Point Virtual Private Network (VPN) architecture is a cornerstone in securing network communications, particularly for businesses operating across geographically dispersed locations. This architecture establishes a secure, encrypted connection between two endpoints, typically two office locations or a remote user and a central network.
At its core, the Point-to-Point VPN architecture functions by encapsulating data packets within encrypted tunnels, safeguarding sensitive information from potential interception or tampering by unauthorized parties. This encryption ensures that even if data is intercepted during transmission, it remains indecipherable to anyone without the proper decryption keys.
One of the primary advantages of this architecture is its versatility. Point-to-Point VPNs can be implemented using various protocols such as IPsec (Internet Protocol Security), SSL/TLS (Secure Sockets Layer/Transport Layer Security), or L2TP (Layer 2 Tunneling Protocol), depending on the specific security and performance requirements of the network.
Furthermore, Point-to-Point VPNs offer scalability, making them suitable for organizations of all sizes. Whether it's a small business with a handful of employees or a multinational corporation with thousands of users spread across the globe, this architecture can adapt to meet the evolving needs of the organization.
Additionally, Point-to-Point VPNs provide a cost-effective solution for establishing secure connections over public networks such as the internet, eliminating the need for expensive dedicated leased lines while maintaining robust security measures.
In conclusion, Point-to-Point VPN architecture plays a pivotal role in modern network security strategies, offering a flexible, scalable, and cost-effective solution for ensuring secure connectivity between distributed endpoints. By leveraging encryption and tunneling technologies, organizations can safeguard their sensitive data and maintain the integrity of their communications infrastructure in an increasingly interconnected world.
Point-to-Point VPN Protocols
Point-to-Point VPN protocols play a crucial role in securing communication channels over the internet, especially in the context of remote work and secure data transmission. These protocols establish encrypted tunnels between two points, ensuring that data remains confidential and protected from unauthorized access or interception.
One of the most widely used Point-to-Point VPN protocols is the Point-to-Point Tunneling Protocol (PPTP). PPTP offers a relatively simple and easy-to-configure solution for creating VPN connections. However, its security has been called into question due to vulnerabilities such as outdated encryption methods.
Another popular option is the Layer 2 Tunneling Protocol (L2TP), which combines the best features of PPTP and the Layer 2 Forwarding (L2F) protocol. L2TP provides stronger security measures by employing IPSec (Internet Protocol Security) for encryption, authentication, and data integrity.
IPSec itself is a suite of protocols that can be used independently or in conjunction with other VPN protocols. It offers robust security features, including encryption algorithms like AES (Advanced Encryption Standard) and authentication methods like HMAC (Hash-Based Message Authentication Code).
In recent years, the Internet Key Exchange version 2 (IKEv2) protocol has gained popularity for its simplicity and efficiency. IKEv2 simplifies the process of establishing VPN connections and supports mobility features, making it ideal for mobile devices.
Additionally, the Secure Socket Tunneling Protocol (SSTP) is a proprietary VPN protocol developed by Microsoft. It leverages the HTTPS protocol to create a secure connection between the client and server, making it highly resistant to firewall restrictions.
Choosing the right Point-to-Point VPN protocol depends on various factors, including security requirements, compatibility with existing infrastructure, and ease of implementation. By understanding the strengths and weaknesses of each protocol, organizations can deploy secure and reliable VPN solutions tailored to their specific needs.
Point-to-Point VPN vs
Point-to-Point VPN vs. Site-to-Site VPN: Understanding the Difference
When it comes to establishing secure communication over networks, VPNs (Virtual Private Networks) play a crucial role. Among the various types of VPNs available, two popular options are Point-to-Point VPN and Site-to-Site VPN. Understanding the difference between these two can help businesses make informed decisions based on their specific needs.
Point-to-Point VPN, as the name suggests, provides a secure connection between two specific points or devices. It is ideal for scenarios where direct communication between two endpoints is required, such as connecting a remote employee to a central office server. Point-to-Point VPNs offer encryption and authentication to ensure data confidentiality and integrity during transmission.
On the other hand, Site-to-Site VPN, also known as a gateway-to-gateway VPN, enables secure communication between entire networks at different locations. This type of VPN is commonly used by organizations with multiple offices or branches that need to communicate securely over the internet. Site-to-Site VPNs establish encrypted tunnels between network gateways, allowing seamless and secure data exchange between sites.
In summary, while Point-to-Point VPN is suited for connecting individual devices or users to a central network, Site-to-Site VPN is designed for secure communication between entire networks or branches. Each type offers unique advantages depending on the specific requirements of a business. By understanding the differences between Point-to-Point VPN and Site-to-Site VPN, organizations can choose the most suitable option to ensure secure and efficient communication across their networks.
Point-to-Point VPN Implementation
A Point-to-Point Virtual Private Network (VPN) implementation is a secure way to establish a connection between two or more locations over the internet. This type of VPN allows for secure data transmission by creating a dedicated connection between the sender and the receiver, preventing unwanted third parties from intercepting the data.
To implement a Point-to-Point VPN, organizations typically use specialized VPN software or hardware appliances that support this type of connection. The first step is to configure the VPN endpoints, which are the devices that will be sending and receiving data through the VPN tunnel.
Once the endpoints are configured, a secure tunnel is established between them using encryption protocols such as IPSec, SSL, or TLS. This encryption ensures that the data transmitted between the two endpoints is secure and cannot be easily intercepted or tampered with.
Point-to-Point VPN implementations are commonly used by businesses to connect remote offices, enable secure communication between partners or clients, or provide secure access for employees working remotely. This type of VPN is especially useful for organizations that require a high level of security for their data transmission.
Overall, a Point-to-Point VPN implementation is a reliable and secure way to establish a secure connection between two or more locations over the internet, ensuring that sensitive information is protected during transmission.
0 notes