#wifi penetration testing tools guide
Explore tagged Tumblr posts
Text
Wi-Fi Hacking Practical Guide with Commands
Wi-Fi hacking is a topic that frequently comes up in cybersecurity discussions. It is important to clarify that hacking into Wi-Fi networks without permission is illegal and unethical. However, ethical hacking, which involves testing the security of Wi-Fi networks to discover vulnerabilities and improve security, is an essential skill for cybersecurity professionals. In this practical guide,…
1 note
·
View note
Text
youtube
How These Dangerous Hacking Gadgets Work In this eye-opening video, we reveal how the most dangerous hacking gadgets work—real-world tools used by cybercriminals, hackers, and even surveillance agencies to bypass security, steal private data, and hijack digital systems. These aren’t fantasy—they're real hacking devices like the WiFi Pineapple, USB Rubber Ducky, Flipper Zero, RFID cloners, IMSI catchers, and more. You’ll learn how these physical cybersecurity threats are used to execute silent cyberattacks in coffee shops, airports, corporate offices, and even your home. We explain the inner workings of each gadget and show how they manipulate systems, intercept data, and exploit human trust. ⚠️ Featuring top hacker tools in 2025: ● WiFi Pineapple: Creates fake WiFi networks to steal your data ● USB Rubber Ducky: Looks like a flash drive, acts like a malicious keyboard ● Flipper Zero: A hacker’s Swiss Army knife—RFID, NFC, Bluetooth exploits ● RFID/NFC Cloners: Steal contactless card info in seconds ● Bash Bunny: Smart USB payload delivery tool ● LAN Turtle: Creates a stealthy backdoor into networks ● Hardware Keyloggers: Record every keystroke without software ● Hidden Camera Pens: Discreet surveillance in a writing pen ● IMSI Catcher (Fake Cell Tower): Hijacks mobile signals, intercepts calls and texts 🔐 Whether you're into ethical hacking, penetration testing, or just want to stay safe in the modern world, this is your ultimate guide to understanding the hardware behind real cyber threats. 📌 Learn: ● How hacking gadgets bypass firewalls and antivirus ● How cybercriminals deploy tools in public spaces ● How to detect and defend against these hacker devices ● What tools red teamers and black hat hackers use 💬 Tell us in the comments: Which device shocked you the most? 👍 Like this video if it opened your eyes to the dark side of tech. 📲 Subscribe for deep dives into banned gadgets, spy devices, and real hacking tools used in today’s digital espionage. #HackingGadgets #Cybersecurity #FlipperZero #WiFiPineapple #USBRubberDucky #PenetrationTesting #InfoSec #RedTeam #RFIDCloning #IMSIcatcher #EthicalHacking #SpyGadgets #DarkWebTools #Hackers #TechExplained #GadgetReview #HowHackersWork #2025Tech 🔗 Stay Connected With Us. 🔔𝐃𝐨𝐧'𝐭 𝐟𝐨𝐫𝐠𝐞𝐭 𝐭𝐨 𝐬𝐮𝐛𝐬𝐜𝐫𝐢𝐛𝐞 𝐭𝐨 𝐨𝐮𝐫 𝐜𝐡𝐚𝐧𝐧𝐞𝐥 𝐟𝐨𝐫 𝐦𝐨𝐫𝐞 𝐮𝐩𝐝𝐚𝐭𝐞𝐬. https://www.youtube.com/@NewTechEras/?sub_confirmation=1 📩 For business inquiries: [email protected] ============================= 🎬Suggested videos for you: ▶️ https://www.youtube.com/watch?v=Y1ScCL3i1L4 ▶️ https://www.youtube.com/watch?v=cPnDfL8BREo ▶️ https://www.youtube.com/watch?v=r5pXurOg_DE ▶️ https://www.youtube.com/watch?v=89khi9VSlik ▶️ https://www.youtube.com/watch?v=cAH4eNh_YrQ ================================= 🔎 Related Phrases: 5 Robotic Animals That Will Revolutionize The Future Of Robotics, Robotic Animals, Future Robotics, MIT Mini Cheetah, Mxphoenix Hexapod, Stickybot, Titanoboa Robotic Snake, Robotic Pets, Underwater Robots, AI Companions, Robot Design, AI Robots, Future Technology, DIY Robots, MIT Robots, Harvard Robots, Robot Mobility ADD HASHTAG HERE https://www.youtube.com/watch?v=BvIEjWXqV40 via New Tech Eras https://www.youtube.com/channel/UCSE8xrlzKeYtXIUS2aeV1Lw June 11, 2025 at 04:53AM
#bannedgadgets#truckgadgets#cooltruckinventions#futuretech#aIgadgets#innovation#smartdevices#nextgentech#techreview#Youtube
1 note
·
View note
Text
Wpa2 wordlist take too long

Nonetheless, paraphrases are good choices when they do not appear on the list of leaked passwords The words that make up a paraphrase must be meaningless together to make it susceptible to social engineering. The passphrase is a phrase or a sentence, without or without spaces, usually more than 20 characters long.
If you have trouble in remembering long passwords then you can make a passphrase.
The length of the password matters a lot, it is an effective defence against brute-force attacks.
You can prevent from a dictionary attack by adopting the following measures SEE ALSO: 8 Best Kali Linux Terminal Commands used by Hackers in 2021. As a result, they had a theft of 60 million user credentials. DropBox suffered a similar case like this in 2012 as one of their employees used the same password for LinkedIn as they used for their corporate DropBox account. Such attacks can be harmful to your business.

He was using the same password for Twitter and LinkedIn and other social media accounts The hackers revealed that the CEO’s password had been compromised in the LinkedIn data breach. If we take an example then all of us are familiar with the Facebook CEO Mark Zuckerberg, his social media account on Twitter was hacked. This surely is a definite way to remember passwords but it leaves you vulnerable towards a data breach Why are Dictionary Attacks Dangerous?Īccording to an estimate, about 80% of the people reuse their passwords on online platforms like personal banking, social media and even work system. SEE ALSO: 10 Best WiFi Hacking Tools in Kali Linux for Wireless Hacking. A dictionary that is used in such attacks can be a collection of previously collected key phrases or leaked passwords. Leetspeak is the character replacement with alphanumeric and non-alphanumeric characters. In the dictionary while using words or any derivatives of those words referred to as leetspeak is very common. Such an attack method is also used as a means to find the key that is required to decrypt encrypted files It is used to break into a computer system or server that is protected by the password by systematically entering every word in the dictionary as a password. The password dictionary attack is a brute-force hacking method. SEE ALSO: Top 8 Best Linux Distros for Hacking and Penetration Testing in 2021.
Merge multiple text files into one and save space making it look organized.
If however, you have multiple passwords then you can combine them into a large fileĪwk ‘’ old.txt | sort -n | cut -d ” ” -f2- > new.txtĮgrep -v “^]*$” old.txt > new.txt If you want to remove all blank lines from a file or need to remove duplicate passwords then a one-liner is all you need Following are the useful commands that are used for manipulating wordlists You can clean up wordlists by using bash one-liner. How to Cleanup Wordlists using bash oneliner It has the most recently used password and pin combinations that users have used on various websites and have unfortunately been leaked. It should be fairly quick to be downloaded. The size of the Rockyou.txt password list is around in the region of 133 MB. You should also try one of the biggest word lists out there called “Rockyou”. SEE ALSO: Kali Linux Hacking Tutorial for Beginners: Learn to Hack Professionally.
Finally, merge all text files into one using the below command:.
Then decompress (if applicable) gunzip *.gz.
Then choose a wordlist you want to use cd wpa2-wordlists/Wordlists/Crackdown2016.
In the first step, you need to download using git clone.
Download WPA/WPA2 Wordlists/Password list for Kali Linux (Latest) WPA/WPA2 Password Lists Download /Image Credits:. SEE ALSO: How to install Arch Linux in 2021 (Step-by-Step Guide). You can go for brute force attack in such cases but it would take a lot of time depending on your computer system.ĭownload Wordlists and Password list for Kali Linux Moreover, keep in mind that this only works if the password is included in the wordlist. Keep in mind that using password cracking tools takes time especially if being done on a system without a powerful GPU. We have found the majority of them from websites that have shared leaked passwordsĪ wordlist is used to perform dictionary attacks like can be used to crack the wi-fi WPA2 using Aircrack-ngĪircrack-ng handshake.cap -w /path/to/wordlist.txtīy using this we have cracked 3/10 networks near us. We get them using advanced Google search operators.
7 Which Wordlist and Password list are you using in Kali Linux?ĭownload Passwords List/Wordlist for Kali Linux (2021 Edition).
5 Why are Dictionary Attacks Dangerous?.
3 How to Cleanup Wordlists using bash oneliner.
2 Download WPA/WPA2 Wordlists/Password list for Kali Linux (Latest).
1 Download Passwords List/Wordlist for Kali Linux (2021 Edition).

0 notes
Text
SUPER MB PRO M6 Diagnostic User Guide: Two Different Configuration Versions
SUPER MB PRO M6 diagnostic tool, with the strong penetration of wireless test and WIFI signal, greatly reduces restriction on testing distance. It adopts the framework concept of original C6 diagnostic tool, thus able to replace original MB Star C4. Durable and easy to carry.
What highlight does it have?
Software Version: V2021.3
Perfectly replaces normal MB SD C4/C5
Supports Original Benz Dealer Diagnostic Software
Supports firmware update without installing the battery
Support Mercedes-Benz models, covering 12v car, 24v diesel truck & bus, MPV etc.
Check SUPER MB PRO M6’s distinctive features:
1.ABS+PVT plastic structure adoption has the advantages as follows:
1) Impact-proof & easy to carry
2) Lower consumption on product shell against wireless signal
3) Great advancement of wireless communication distance & stability
2.SUPER MB PRO M6 is the only diagnostic tool on the market that is highly consistent with the original MB Star C6:
1) Fully compatible with the original software.
2) You can directly upgrade the newest firmware without installing additional driver.
3.Can perform as the same functions as that of the original: Compatible with the Mercedes Benz models with protocol DOIP, K-line, CAN Low, Can High, LIN, RS485, etc, works with the old cars and new cars.
4.Built -in network interface prevents deformation and damage from impact.
5.Relieve the dependency on communication transmission cable during test, and greatly reduces restriction on testing distance. The device, adopts the framework concept of original C6 diagnostic tool, is able to replace original MB Star C4. Durable and easy to carry.
SUPER MB PRO M6 diagnostic tool has two different configuration version:
NO.1 SUPER MB PRO M6 wireless Star Diagnosis Tool Standard Version:
Item No. SP369-B, price: €287, free shipping, no tax
📷
Check purchase link here: https://www.cardiagtool.co.uk/super-mb-pro-m6-star-diagnosis-tool.html
What package you can get when receiving?
1pc x SUPER MB PRO M6 Main Unit 1pc x OBD2 16pin Cable 1pc x Lan cable NO.2 Super MB Pro M6 wireless Star Diagnosis Tool Support Doip Full Package Advanced Version:
Item No. SP369, price: €313, free shipping, no tax
📷
Check purchase link here:
https://www.cardiagtool.co.uk/super-mb-pro-m6.html
What package you can get when receiving?
1pc x SUPER MB PRO M6 Main Unit 1pc x OBDII 16PIN Cable 1pc x 38PIN Cable 1pc x 14PIN Cable 1pc x 8PIN Cable 1pc x Lan Cable
Good item, don’t miss it!
That's all. Thank you for sharing your time with us!
Don't forget to contact us at:
Email: [email protected] Skype: cardiag.co.uk Whatsapp: +86 15002705698
Or leave a message at https://www.cardiagtool.co.uk/
to tell us what suggestions or questions you have about our products.
Source:http://blog.cardiagtool.co.uk/super-mb-pro-m6-diagnostic-tool-review-two-different-packages/
0 notes
Text
Deeper Fish Finder Pro Info
It is a great option for hole hopping when you want to quickly see if there are any fish in the area and keep moving to stay on top of them. There are a few drawbacks to the device. Alternatively, you can unscrew the Deeper sonar’s cap, wet your finger and touch both the metal pins at the bottom of the device simultaneously. Some of the reviewers write detailed posts where they go into detail about the problems they’ve come across when operating the device. The Deeper Mobile app also allows you to control the detail you see, to put the sonar into sleep mode to preserve battery. Don't forget to pack the second battery. The battery life is around five and a half hours long. Fishermen need to see exactly where fish banks are located in order to increase their chances of landing a catch. Improved See Through Technology allowing weak and strong digital signals. For the most in depth deeper fish finder info use the guide below.

It doesn’t feature the most advanced technology available in its sonar system, but it’s adequate for many angler’s needs. My brother Tim, who had supplied the test unit, also kindly provided a length of venetian blind cord to tow around this little ball of technology. The information provided by Deeper on climate, weather, sunset/sunrise and moonrise/moonset are really helpful when you go out for fishing. I am really happy with my purchase and look forward to using it at the start and during fishing sessions! Let’s go back to the start of my Deeper experience. Models with GPS capabilities are ideal for use when you are fishing in the open water, and might need some help getting back to shore. For example, you could be fishing throughout different locations during the day, or you could lose sight of land, or some severe weather could suddenly roll out. There are a few extras available for the Deeper unit, such as a night cover and a mobile phone holder for your fishing rod which can be used horizontally or vertically. I know there are lots of questions you may have on this subject. Most people find that a larger and higher resolution screen and a more power are worth the modest increase in price.
Deeper Fish Finder
Your screen shows a 2D display, but remember that the Deeper records at 15 degrees (290kHz) or 55 degrees (90kHz) (depending on your settings) in all directions. If you have your units settings correct. How Much Transmit Power Should It Have? The density of salt water removes some of the penetrating power of the sonar, and for most applications you’ll want to be able to “see” as deep as possible. In order to find the best value for your needs, you need to establish the type of fishfinder you want. Once you find the ball with the wider cone, you may want to know more. Or click the Buy With Amazon button to read more reviews or purchase this wireless sonar smart fish finder, which works in conjunction with smart phones and tablets. Recently introduced into the South African marketplace is the Deeper Smart Fish Finder. Fish are displayed like arches in this case.

It is always a good idea to have a GPS with deeper fish finder on hand to help you locate where the schools of fish are swimming around on any given day. Consider everything that comes in the box with your new fish finder. Once you become experienced with this tool, you will be amazed how much information the fish finder can give you about whats under the surface of the water. Manufactured by Deeper, it comes with a convenient app that lets you track and record fish activity, along with sharing details of your trip with friends and family. Now we’re talking, Lowrance Elite-5 HDI is a great fish finder for a wide range of purposes and it comes with a few nifty features to make it a stand-out. If you would like to check the fish finder prices, you can follow the links to Amazon. Most preferring not to make use of a finder feel that the sport is diminished when commercial tools are utilized to gain a benefit. The latest technological innovations from Humminbird include the Autochart live and Smartstrike, both utilized in cartography and the branded Cross Touch Technology, which was uniquely designed to answer to the needs of users who may benefit from multi-gesture control.
This is another powerful unit from Humminbird. So this way a fishfinder reads and lets you view the bottom and everything it encounters in between. Jigging is a way of fishing using a jig, which is a kind of fishing lure with a lead sinker and a hook attached to it then covered by a sort of soft body that may attract the trout. Optimum usage of the wide beam feature of the Garmin 140 is while fishing in shallow water as it supplies the user images of what is around the boat particularly near to the surface. In lagoons, a river and from the bridge it performed admirably and surprised me with how little I knew about my favourite fishing spots. Jigging can be performed in shallow waters. Most transducers have more than one cone transmitting from the starting point. Great looking product, very interested in getting one. With the best portable fishfinder in 2017 you will be able to fish with more precision, thus ending up with quality results, which is exactly what you’re looking for.

They may use a single beam, two beams, or multiple sonar beams in order to detect what’s going on under the water. Through the hull dual frequency transducers are recommended if you plan to fish deep water and need to read the fish at high speeds. Because of the amount of line out and the weight it will most likely be difficult to feel how the fish is fighting. Course charting is an additional benefit as it makes it very easy for the user to figure out his or her location and determine the course he or she has to take in order to reach the perfect spot. There are fish alarm, depth alarm which will enhance your ability to find the perfect zone for a school of fish. The depth rating directly depends on the power and the quality of the transducer. The transducer is the piece of equipment that emits a sonar signal into the water and provides data to the fish finder.
Portable fish finders are often used in ponds and lakes, as well as other relatively small and still bodies of water. The ability of a fish finder is greatly dependent on the power and frequency of the ping sent by the transducer. Soon our trips turned into regular weekend trips and we brought in more fish than ever before with our fish finder. Trolling from a boat is more feasible. The other great thing about vertical jigging is that the rigs are so easy to setup compared to traditional trolling or casting techniques. Weedless setups are a must. The Deeper” Fish Finder is starting to revolutionize fresh and saltwater fishing and how we understand the areas we are fishing, improving catch rates and increasing your enjoyment. In fact, what a fish finder “sees” is the fish’s swim bladder. Alter the color of bait often to keep the fish on their toes.
They make fish finders with color screen, fish finders without color and fish finders with a gps system included. Unless you fish extremely shallow water as I mentioned above in this case it's fine to go with a wider cone angle transducer. It reads around 100 feet deep in the water and is easily portable. With a range of 160 feet you have plenty of scope to find that fish holding underwater feature. The Deeper portable fish finder is one of the neatest devices to top the fishing scene. Designed to fit into the standard fishing tackle box Deeper Smart Fishfinder 3.0 is a super small wireless, castable echo-sounder that weights only 3.5oz/100 g and exceeds no more than 2.5''/65 mm in diameter. This is a great fishfinder for ice fishing, designed specifically for that purpose. Any angler that has ever had the pleasure of crappie ice fishing at the Lake of the Woods in Ontario will tell you that it is a wonderful experience. You can even use it for ice fishing!

You can drop these waypoints to save good fishing spots or mark them towards your journey. Try to determine a good display that will work for you at a reasonable price. This will detect the very lightest of bites. If you are starter angler then you will find it easier to read CHIRP digitally processed image then an image from Dual beam result. Also included are the Sirius Satellite Radio & Weather capabilities for your safety. This will let you know where you are or how far you are from the land. If you catch a good flathead or channel let us know that too. With so many available recently, it is good to have a make you can trust. Lower frequency can be equated to greater depths since the sound waves in this case can travel for a long distance. It comes with the Deeper, Charger, Charging block, Carrying case And all the Manuals to teach you how to use it. It is simple, easy to use and transport.
Trip log with deeper fish finder: you can save your current location by giving GPS tag for future reference. This can be anything loud including loud talking. The least expensive product from our reviews, the Venterior portable fish finder will be of great help on all your angling trips from now on. The moment you have the connection, your app will look like a fish finder, displaying the information that it is detecting. In large lakes and reservoirs look for the big flatheads in areas with lots of cover, submerged brush piles, or stumps. This causes water in the future over the the top sonar and the blue tooth signal is lost. When water goes over the top of the pod you lose WiFi signal. It has the water temperature mounted on the transducer. Images provided are for illustration purposes only and actual products may differ. Bream, bluegill, perch, herring, bullheads, check your local regulations to make sure what is legal to use, goldfish are a favorite in places too. But the price isn’t all that important considering the number of specs and useful features packed in this unit. Unlike the previously mentioned devices, this unit features a smaller and black and white display.
Resources:
Deeper Fish Finder - The Top 3 To Buy | Ruimte Voor Balans
4 Ways to Use a Fish Finder - wikiHow
DEEPER FISH FINDER PRO PLUS REVIEW - WEEBLY
youtube
1 note
·
View note
Text
Mobile Automation Testing - A comprehensive guide

The humongous growth in the penetration of smartphones has made mobile applications a sort of plaything for customers from across the globe. This trend has made companies line up with a flurry of mobile applications to drive their brand, products, and services. However, developing a mobile application is not simply about devising an idea, developing the code, and finally delivering it to the market. Technological advancements and rapid proliferation of mobile devices across different operating systems (iOS, Andriod and Windows) have created more challenging scenarios for the application developers. In fact, just like the case of any other software product, mobile application testing has become one of the crucial steps to ensure foolproof performance and user acceptance. Mobile application testing ensures the applications run across a multitude of platforms and attain long term success.
Mobile automation testing encompasses testing the functionality, usability, and consistency of a mobile application across the digital touchpoints. The testing process can be both automated and manual. However, the testing techniques are different for mobile devices. Automated testing is highly efficient and offers a substantial return on investment, as long as, it is implemented using proper tools.
Different mobile automation testing mechanisms used by industry specialists
The mobile application testing can be automated by using the below-mentioned mechanisms:
· Cloud-based automation: This testing process runs on multiple devices and facilitates web-based QA across platforms. Cloud-based automation also provides integration with an open-source software comprising rich libraries.
· Web-based automation: The method validates the quality of mobile web applications. It influences user-based add-ons that come with web browsers such as Google Chrome. These user-based add-ons facilitate the conversion of specific web content. The functionality generally gets automated with the usage of open-source or licensed solutions.
· Network configuration testing: This type of mobile application testing ensures the app works well on different networks, such as WiFi, 3G, and 4G.
· Operating system emulator automated testing: Various automation tools are available with different operating systems. For example, Apple has emulators for iPhones, Google for Andriod phones and Microsoft for Windows.
· Simulator or lab-based automation: This method is all about setting up tools in a test environment. It facilitates physical devices and simulators to automate testing using open source and commercial tools.
· Importance of mobile automation testing and its challenges: Since the mobile application market has seen massive growth, the presence of a high-quality app becomes quintessential to get user attention and drive out competitors. On the other hand, a poor-quality mobile application can result in revenue loss and negative brand image for the company. The implementation of QA app testing can help to check the usability and functionality of applications across device platforms. Here are a few pain points during mobile testing that QA managers or testers should take into account:
· Testing on multiple devices: Multiple mobile devices with different application runtime can create challenges for automation testing. The result of test automation cannot guarantee if the tested application would work well on a given gadget. This happens due to the difference in operating system optimization, memory, and other hardware elements such as the presence of different communication protocol - HTTP, WAP etc. Developing a separate testing process for every platform would be costly as well as time-consuming.
· Platform diversity challenges: Frequent platform customization by OEM, releases, and updates can create challenges for mobile testing.
· Automated cloud testing challenges: Various cloud testing services allow the running of automated tests in different environments and machines without creating the testing infrastructure. There are many cloud service providers such as TestingBot, CircleCI, Cloudbees providing cross-browser unit testing, Selenium testing, and continuous integration testing.
Types of mobile automation testing:
· Functional testing: This type of testing scrutinizes the functionality of an application and its integration with OS platforms, devices, and technologies. It mainly focuses on compatibility issues.
· Performance testing: This mobile app automation testing method is carried out to review challenges related to speed, power utilization, graphical and network. All the limitations are outlined while improvements are noted.
· Security testing: This type of testing identifies the vulnerabilities inherent in an application by using penetration testing.
· Peer Testing: This mobile app automation testing method is conducted in a real-time environment to find out drawbacks.
Conclusion
The principles of mobile app automation testing are quite different from conventional testing methods for software. The multitude of mobile devices, tool sets, hardware, environment, and test coverage brings forth the layers of complexity. This necessitates the implementation of a customized approach to ensure the success of a mobile application.
This Article is originally published at Medium.com, Mobile Automation Testing - A comprehensive guide.
Diya works for Cigniti Technologies, Global Leaders in Independent Quality Engineering & Software Testing Services to be appraised at CMMI-SVC v1.3, Maturity Level 5, and is also ISO 9001:2015 & ISO 27001:2013 certified.
#mobile app testing solutions#mobile app performance testing#testing mobile apps#mobile app automation testing#mobile application testing#mobile automation testing#mobile test automation#mobile app testing
0 notes
Link
Computer Hacking Beginners Guide: How to Hack Wireless Network
Computer Hacking Beginners Guide will teach you how you can protect yourself from most common hacking attacks -- by knowing how hacking actually works! After all, in order to prevent your system from being compromised, you need to stay a step ahead of any criminal hacker. You can do that by learning how to hack and how to do a counter-hack.
Computer Hacking Beginners Guide techniques and tools that are used by both criminal and ethical hackers – all the things that you will find in this book will show you how information security can be compromised.
(adsbygoogle = window.adsbygoogle || []).push({});
This book will guide you to how you can identify an attack in a system that you are trying to protect. At the same time, you will also learn how you can minimize any damage in your system or stop an ongoing attack.
About Computer Hacking Beginners Guide
The Computer Hacking Beginners Guide…, you'll learn everything you need to know to enter the secretive world of computer hacking. It provides a complete overview of hacking, cracking, and their effect on the world. You'll learn about the prerequisites for hacking, the various types of hackers, and the many kinds of hacking attacks:
Active Attacks
Masquerade Attacks
Replay Attacks
Modification of Messages
Spoofing Techniques
WiFi Hacking
Hacking Tools
Your First Hack
Passive Attacks
(adsbygoogle = window.adsbygoogle || []).push({});
Computer Hacking Beginners Guide will Teach How to Hack Wireless Network, Basic Security and Penetration Testing, Kali Linux, Your First Hack right away - This Amazing New Edition puts a Computer Hacking Beginners Guide
This is a best book for beginners who are new to the hacking field. You'll learn how to hack an email password, spoofing techniques, WiFi hacking, and tips for ethical hacking
0 notes
Text
March 12, 2020 at 10:00PM - The Complete White Hat Hacker Certification Bundle (96% discount) Ashraf
The Complete White Hat Hacker Certification Bundle (96% discount) Hurry Offer Only Last For HoursSometime. Don't ever forget to share this post on Your Social media to be the first to tell your firends. This is not a fake stuff its real.
If you’re serious about becoming an ethical hacker, you’re going to need to know Metasploit. One of the most popular pentesting frameworks out there, Metasploit empowers cybersecurity pros to verify vulnerabilities, manage security assessments, and more while staying ahead of their cybercriminal foes. Let this course serve as your Metasploit primer, starting you off with a deep introduction into the framework and walking you though conducting attacks and testing vulnerabilities, and more.
Access 8 lectures & 2 hours of content 24/7
Follow along practical training for using the Metasploit framework
Learn how to locate security issues, verify vulnerability mitigations & more
Develop the required skills to keep hackers out of your network
Validate your training w/ a certificate of completion
We’re living in the middle of a digital arms race. As cybersecurity pros develop better encryption methods, hackers fight back with more sophisticated attacks, making now the best time to jump into this ever-evolving field. This course covers all the important techniques related with WiFi hacking that are employed by hackers, system administrators and pentesters. In addition to netting more than 50 lectures on WiFi hacking, you’ll also get access to the Training Operating System, loaded with all the source code and tools needed to develop your hacking skills.
Access 60 lectures & 4 hours of content 24/7
Download the course handbook as a PDF (180 pages)
Explore 25 different wireless network hacking techniques & experiments
Access all of the required source code & tools via the included Training Operating System environment
Learn how to prepare your training environment so you can safely conduct hacking experiments
Get an introduction to wireless networks & security
Familiarize yourself w/ WEP/WPA attacks
Validate your training w/ a certificate of completion
Used to mask certain processes and and even grant privileged access to a computer, a rootkit is a stealthy type of software that can undermine your privacy without you even knowing it. This course shows you how rootkits work, how they can hide inside your system, and how you can protect yourself against them. Leveraging the same techniques used by hackers, system administrators, and the like, you’ll take on creating invisible software, understanding how it ticks, and the steps you can take to protect yourself from them.
Access 37 lectures & 5 hours of content 24/7
Dive into how rootkits work & how you can detect them
Discover how to create a backdoor & bypass firewalls
Learn how to hide processes, files, directories & registry entries
Explore creating an invisible keylogger & remote console
Learn how to deceive Anti-Virus applications
Validate your training w/ a certificate of completion
There’s much to learn about ethical hacking, and you’ll inevitably need to get some hands-on experience before you throw your hat into the cybersecurity ring. Guiding you through 21 hacking techniques and how they can be used in real-life scenarios, this course takes a practical approach to teaching you the ethical hacking essentials. You’ll walk through preparing a training environment to work in and get to flexing your cybersecurity muscles with all the essential source code and examples provided.
Access 44 lectures & 3 hours of content 24/7
Receive a step-by-step education on website & Web application ethical hacking and security
Explore the 10 Most Critical Web Application Attacks presented yearly by OWASP (Open Web Application Security Project)
Learn how to hack using 21 techniques & see how each of them can be used in a practical, real-life example
Familiarize yourself w/ cross-site scripting, SQL injections, phishing & other attacks
Validate your training w/ a certificate of completion
Data is worth more than gold nowadays, and cybercriminals know it. That’s why companies aren’t shy about paying top-dollar salaries to capable ethical hackers to keep their networks safe. With more than 30 lectures on surveillance methods, computer forensics, and ethical hacking techniques, this course can fast track your move into this booming field. You’ll dive into file encryption methods and vulnerabilities, taking over a remote computer, and more as you make your way through this practical cybersecurity primer.
Access 36 lectures & 4 hours of content 24/7
Take your training further w/ a free downloadable source code package
Dive into using tunneling to access firewall-protected services
Learn how to create & install a keylogger
Explore capturing data from various file types
Expand your understanding by analyzing a corporate data leak scenario
Validate your training w/ a certificate of completion
You don’t need to be a computer science wiz to keep your networks safe from attack. Even if you’re a complete beginner, this course takes you through key security loopholes and techniques. From intercepting information to identifying various application attacks, you’ll come to grips with the ethical hacking essentials and get the tools needed to test the security and vulnerability of your own computer or computer system.
Access 45 lectures & 3 hours of content 24/7
Discover how to recover lost passwords and intercept information
Learn how to obstruct encrypted data & hide files using kernel modules
Understand how to handle overflow attacks & recognize remote attacks
Learn how to identify application attacks, like string attacks & overwriting
Dive into securing your own system w/ scanners, detection & patches
Validate your training w/ a certificate of completion
With a few lines of code, cybercriminals can access protected networks, view encrypted files, and even steal identities online—if there’s not an ethical hacker standing in their way. This extensive course contains over 20 hours of practical training designed to help you thwart these criminals as a certified professional. You’ll start with an introduction to cyber threats and IT security myths. Then you’ll move on to security policies, risk management, disaster recovery, and even get a free voucher for the ISA CISS examination when you complete the course, setting you up to validate your skills right away.
Access 236 lectures & 23 hours of content 24/7
Follow step-by-step instructions for advanced hacking techniques
Familiarize yourself w/ current cyber threats & hacking trends
Explore designing more secure networks
Dive into encrypted data, identify spoofing, and windows authorization
Get a free voucher for the ISA CISS examination upon completion
An ethical hacking education simply wouldn’t be complete without a look at Kali Linux. Found in many an ethical hacker’s toolbox, Kali Linux is jam-packed with tools for penetration testing, security research, computer forensics, reverse engineering, and other information security tasks. Starting from scratch, you’ll explore the Kali Linux basics and dive into the methods hackers use to exploit vulnerabilities, create backdoors, steal sensitive info, and more.
Access 75 lectures & 8 hours of content 24/7
Learn how to use common Linux commands like hackers do
Walk through building a Linux target from scratch
Explore Creating shells & backdoors
Understand & replicate what malicious hackers can do
Validate your training w/ a certificate of completion
from Active Sales – SharewareOnSale https://ift.tt/2T3DIz2 https://ift.tt/eA8V8J via Blogger https://ift.tt/2U70dDw #blogger #bloggingtips #bloggerlife #bloggersgetsocial #ontheblog #writersofinstagram #writingprompt #instapoetry #writerscommunity #writersofig #writersblock #writerlife #writtenword #instawriters #spilledink #wordgasm #creativewriting #poetsofinstagram #blackoutpoetry #poetsofig
0 notes
Link
WiFite Description A tool for automated wireless attack. Wifite works only on Linux. Wifite was created for use with penetration testing distributions, such as Kali Linux, Pentoo, BackBox; any Linux distributions with wireless drivers patched for injection. It seems to also work on Ubuntu, Debian and Fedora.
WiFite2 Automated Wi-Fi hacking tool
There are many ways to attack a Wi-Fi network. The type of encryption, default settings of the manufacturer and the number of connected clients can determine how easy it will attack the target and which method of hacking will work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets within your adapter's coverage area, and then selects the best hacking strategy for each network. As a rule, programs are sharpened to perform one specific function:
customer deauthentication
handshake
brute force
brute force WPS
etc., there are a lot of separate stages, methods.
Features:
sorts targets by signal (in dB); hacking the closest access points first
automatically deauthenticates hidden network clients to reveal their SSID
a set of filters to accurately indicate what to attack (wep / wpa / both, above a certain signal strength, channels, etc.)
flexible settings (timeouts, packets per second, other)
“anonymity” functions: changing the MAC to a random address before an attack, then a reverse change when the attack is completed
all captured WPA handshakes are copied to the current wifite.py directory
WPA smart deauthentication; cycles between deauthenticating all clients and broadcast
stop any hacking with Ctrl + C with options to continue, go to the next target, skip hacking or exit
display of general information on the session upon exit; show all cracked keys
all passwords are saved in cracked.txt
Homepage: https://github.com/derv82/wifite2
When a wireless network tester gets to work, it moves from one program to another to perform different stages of penetration, to use different methods. Wifite or Wifite2? Wifite is not a new tool. It was one of the first Wi-Fi hacking tools we met. Along with Besside-ng, automated scripts for hacking Wi-Fi allowed even the script kiddie to get good results, despite the fact that they did not understand how these scripts work. Compared to Besside-ng, the original Wifite thoroughly used all the tools available to it to attack the network, but at the same time it was very slow. One of the best features of the original Wifite was that he conducted a Wi-Fi scanning of the area before attacking nearby networks. This allowed the hacker to specify one, several or all networks as targets. Due to the fact that Wifite laid out to the user all the available targets in an easy-to-understand format, even a beginner could understand which attacks are best used against the nearest networks. The original Wifite could automatically attack WPA networks by intercepting handshakes or use the Reaver tool to bruteforce the WPS PIN codes of nearby networks. Despite the fact that this method of attack was very effective, its execution took 8 hours or more. The updated WiFite2 works much faster due to the reduction of time for the attacks themselves and the use of more advanced tactics than in the previous version. Because of this, Wifite2 is a more serious and powerful tool for hacking Wi-Fi than the original Wifite. Wi-Fi hacking procedure For the fastest possible hacking of nearby networks, Wifite2 uses a simple but fairly effective procedure. He brings every tactic he is trying to apply, to the limit of its practical application, he may even go so far as to try to hack any incoming handshakes. First of all, Wifite2 scans all channels in search of all networks in the coverage area. Then it ranks the found networks by signal level, since the fact of finding a network does not guarantee a reliable connection with it. In addition to sorting the detected networks in descending order of signal, the reconnaissance phase includes the collection of information about which hacking methods these networks may be vulnerable to. Thanks to the organization of Wifite2, you can easily add a directional Wi-Fi antenna, and use Wifite2 to locate the source of any nearby Wi-Fi network when conducting a neighborhood scan. After the scan is complete, the counties will reflect all reflected targets to see whether clients are connected to them, whether the network announces WPS usage, and what type of encryption the network uses. Based on this, the hacker chooses any target, group or all targets for attack based on the information collected. Wifite2 will go through the entire list of goals, starting with the fastest and simplest attacks, such as WPS-Pixie, which can crack a password in a matter of seconds, to less reliable tactics, such as checks for using weak passwords using a dictionary attack. If the attack fails or its completion takes too much time, then Wifite2 will proceed to the next possible attack in a particular case, so as not to waste time, as its predecessor did. What you need First you need a Wi-Fi adapter that can be switched to monitoring mode. This means that you must choose an adapter that is compatible with Kali Linux. We have several excellent guides on this subject. “ How to determine which Wi-Fi adapter is suitable for Kali Linux ” and if you need a good wireless card for hacking check this huge list of adapters that support monitor mod, USB Wi-Fi adapters that support monitor mode and wireless injection Wifite2 is installed by default in Kali Linux, so we recommend using Kali on a virtual machine or as a second system on a laptop. You can use Wifite2 on other Linux systems, but we will not elaborate on installing it, since we assume that you still use Kali Linux. WiFite installation The program is preinstalled in Kali Linux, additionally install the programs:
hcxdumptool
hcxtools
Linux installation Required dependencies:
Python. Wifite is a Python script and requires Python to run, the program is compatible with versions of python2 and python3.
iwconfig : To determine if the wireless interfaces are already in monitor mode.
ifconfig : To start / stop wireless devices
Set aircrack-ng . The following programs are used specifically:
airmon-ng : To list and enable Monitor Mode on wireless interfaces.
aircrack-ng : To hack WEP .cap files and captured WPA handshakes.
aireplay-ng : To deauthenticate Access Points, replay capture files, various WEP attacks.
airodump-ng : To scan targets and generate capture files.
packetforge-ng: For fake capture files.
Optional but recommended dependencies:
Reaver , is intended for the selection of the WPS (Wifi Protected Setup) pin by the brute force method. Reaver turns on the "walsh" (or "wash") scanner to detect access points with WPS turned on. Wifite uses Reaver scanning and to attack routers with WPS enabled.
Pyrit , a WPA PSK key cracker using a graphics processor. Wifite uses Pyrit (if found) to identify handshakes. In the future, Wifite may get the option to crack WPA handshakes using Pyrit.
tshark. It is supplied in conjunction with Wireshark , software for sniffing packages.
coWPAtty , WPA PSK key cracker. Wifite uses cowpatty (if found) to identify handshakes.
Pixiewps , a tool written in C, is used for offline brute force pin WPS by exploiting the low or non-existent entropies of some access points (pixie dust attack).
Wifte2 Video tutorial
After installing dependencies, installing WiFite itself is very simple:
123git clone https://github.com/derv82/wifite2.git cd wifite2 sudo ./Wifite.py
In a typical launch, Wifite will only ask the user one time: which access points should they attack? You can run Wifite so that it will not even ask it - it will attack every TD. You can specify a dictionary file - and the program will completely autonomously send deauthentication packets, grab handshakes, sort through passwords, sort through WPS pins and try to use WPS PixieDust, conduct various attacks on WEP. Moreover, the program will launch an attack on the weakest technologies and, in case of failure, move on to more secure ones.
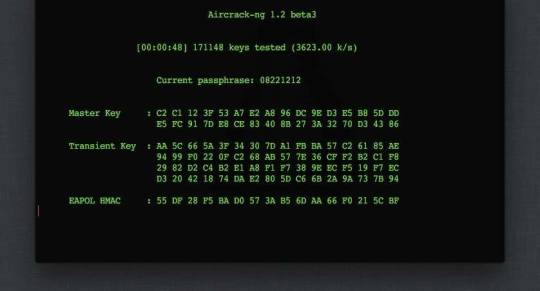
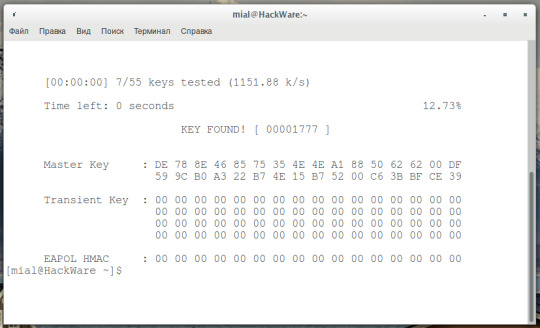
Depending on the success, the result of the program may be getting a password in clear text, or captured files of handshakes - which need to be brutal to get a password in clear text. How to run WiFite We need a dictionary file . With the following commands we copy it into the current working directory, unpack and clean it (so that all candidates for passwords meet the requirements of WPA passwords).
123cp /usr/share/wordlists/rockyou.txt.gz . gunzip rockyou.txt.gz cat rockyou.txt | sort | uniq | pw-inspector -m 8 -M 63 > newrockyou.txt
Some more theory. WiFite is a “full cycle” program for hacking Wi-Fi access points. it does everything well, but such a stage as brute force passwords can be done not only well - it can be done perfectly well. Passwords can be significantly accelerated if Pyrit is used , but it requires certain skills. Let's start with a very simple one - let WiFite do everything by itself. Automated Wi-Fi hacking in WiFite To do this, you need to launch the WiFite program with two additional options:
- -crack says that you need to hack using a dictionary
--dict ~ / newrockyou.txt indicates which dictionary to use
1sudo wifite --crack --dict ~/newrockyou.txt
After launching, wait a few minutes while the program collects information about available access points:
When the information is sufficient, press the CTRL + the C . We will be asked to enter the numbers of access points that we want to hack. You can select all (you need to enter all), you can select individual APs, listing them separated by commas, you can select ranges, listing them through a hyphen:
Then the program will do everything . If it seemed to you that the program was stuck for too long on any access point or on any attack, then press CTRL + C once to go to the next action. We will be asked - we want to immediately exit or continue, however you can see we got the handshake file here and it's start trying to crack it , no luck for this target but the next target was cracked as you will see
the next target took a few seconds to be cracked using WPS Pixie-Dust :
WiFite output WiFite - perhaps the best program for beginners. You can hack your first wireless access points with it without knowing anything about handshaking, deauthentication, types of Wi-Fi encryption and technologies such as WEP, WPS. Personally, my first successful experience, which made me believe in myself and had awakened my interest in this topic, is connected with the wifite program. In terms of the “effort / results” ratio, there is no equal for wifite. Nevertheless, developing in matters of Pentesting wireless networks Wi-Fi, working with your own hands and head, you can achieve better results. A penster who has enough experience with a quick glance to see unpromising access points (a very weak signal or not a single client), if the pentester detects WPS, he will not get stuck on it for hours, stopping another job (wifite gets stuck, this is correct, because WPS is often hacked). Pentester would try to seize all possible handshakes, and then, while the hashes are moving, launch attacks on WPS and WEP. Perhaps it depends a lot on conditions, but with proper skill it gets easier for me to get a handshake using airodump-ng + aireplay-ng , than using wifite. Some warnings and ways to protect Wifite2 is an example of how script kiddies can effectively attack networks with common vulnerabilities, such as WPS PIN codes and weak passwords. But as the number of advanced attacks, whose execution is automated, grows, it is very important to know about the most common and effective methods of attacks on Wi-Fi networks. The best way to protect your network from tools like Wifite2 is to make sure that you have WPS turned off, and choose a very strong password for your Wi-Fi network that you will not tell anyone. It is important to note that by selecting “all” in the target list, Wifite2 will attack all detected networks, and not just those for which you have permission to test. You must have permission to use this tool on any network that you are attacking, because attacking a network belonging to someone else without permission is a crime and can be very troublesome. Just saying that the script did it, and not you - this is no excuse, especially if you were caught attacking some important network. Therefore, make sure that Wifite2 focuses only on those networks for which you have permission to audit. We hope you enjoyed this guide to automating the Wi-Fi hacking with Wifite2. If you have any questions about this article or about Wi-Fi hacking tools - feel free to write in the comments. Disclaimer : This article is written for educational purposes only. The author or publisher did not publish this article for malicious purposes. If readers wish to use information for personal gain, the author and publisher are not responsible for any harm or damage caused.
0 notes
Text
AmpliFi Instant: The Best Mesh Wi-Fi on a Budget
Our verdict of the AmpliFi Instant: At such a disruptive price point, the AmpliFi Instant is beautifully designed, and loaded with features. This makes it one of the best mesh Wi-Fi solutions on a budget.1010
With all the mesh Wi-Fi options available nowadays there should be no reason why you should be suffering from poor Wi-Fi. But even though you’re spoilt for choice good, reliable Wi-Fi comes at a price. Or maybe you’d like to have all the features of a flagship model but don’t really need the range it offers. The AmpliFi Instant may be able to address this.
youtube
Specifications
Dimensions: 3.92 x 3.85 x 1.30 inches (99.5 x 97.8 x 33.05 mm)
Weight: 7.58 oz (215 g )
MIMO: 2.4 GHz: 2×2, 5 GHz: 2×2
2.4Ghz Speed: 300 Mbps
5 GHz Speed: 867 Mbps
Gigabit Ethernet (Router): 1 x LAN + 1 x WAN
Gigabit Ethernet (MeshPoint): 1 x LAN
Maximum Power Consumption: 9W
Antennas: 1 x Dual-Band Antenna
Display (Router): Capacitive Touch, Grayscale
Wi-Fi Standards: 802.11ac
Wireless Security: WPA2-PSK AES/TKIP
RRP (Router Only): $99
Price (Router + MeshPoint kit): $179
AmpliFi Instant WiFi Router by Ubiquiti Labs, Seamless Whole Home Wireless Internet Coverage, WiFi Router w/Touchscreen Display, 1 Gigabit Ethernet, 1 WAN Port, Ethernet Cable, Expandable Mesh System AmpliFi Instant WiFi Router by Ubiquiti Labs, Seamless Whole Home Wireless Internet Coverage, WiFi Router w/Touchscreen Display, 1 Gigabit Ethernet, 1 WAN Port, Ethernet Cable, Expandable Mesh System Buy Now on Amazon $99.99
Overview
Packaging has always been a strong point for AmpliFi, and the Instant is no exception. They somehow manage to make you feel special opening up box. This may not be a big deal for some, but first impressions do count, and you get the feeling that this is a premium product from the get-go.
The router and mesh point are nearly identical. The differences being the lack of a screen and WAN port on the latter. Aesthetics is a big part of AmpliFi, and they’re designed to be put on display, not hidden away in a corner cabinet. These devices are made for the table top and should fit in with any modern decor.
There’s an LED light covering the base of the unit of which the brightness and schedule can be controlled from within the app. The LCD screen on the front shows a few things like displays the time, current upload and download speed, or your existing LAN and WAN IP Address.
AmpliFi HD vs. AmpliFi Instant
We reviewed the AmpliFi HD and were besotted with it. There are some marked differences aside from the price. In terms of footprint, there’s not much of a difference apart from the height. The screen on the HD capitalizes on the height and is significantly larger as well as having more colors as well as featuring three more ethernet ports.
In terms of technology, has a more powerful antenna allowing for more throughput as well as having more capacity for Multi Input Multi Output (MIMO). MIMO allows a device to communicate through multiple streams allowing you to transfer more data at the same time.
The mesh points are also different between the series. The AmpliFi HD’s mesh points plug straight into a wall socket compared to being a top a surface with the Instant. A mesh point plugged into an outlet might not be placed optimally in terms of clearance or interference from other devices.
Fortunately, you can use AmpliFi Instant along with AmpliFi HD, albeit with one caveat. You cannot extend an AmpliFi implementation with a kit, but you can extend it with standalone units. So if you already have an existing AmpliFi install, regardless if it’s a kit or not, and you need to add more coverage, be sure to purchase standalone units and not another kit.
The AmpliFi Teleport, which allows you to VPN into your home network, is also fully supported on AmpliFi Instant. So other than the antennas and size, both systems are pretty much identical and can be used to compliment each other.
Getting Set Up
AmpliFi have been touting a full set up in under two minutes. The skeptic in me wanted to validate this, so I timed it. After the unit powered on I plugged in an internet feed to the WAN port on the back. The unit told me to download the app, which I did, and I started the stopwatch. If I paid attention to my competitive side, I could have easily have set the system up within a minute.
The app guides you through everything you need to do, but the only thing you need to do is choose a Wi-Fi name and a password. If you have purchased AmpliFi as part of a kit the mesh point will even pair automatically.
From here it’s a good idea to do any firmware updates, speaking of which AmpliFi will notify you of on the display. If you have any other mesh points that you’d like to use, pair them now with the main router. Now all you have to do is place them around your house and do a few speed tests to make sure that you’ve got optimal placement.
One notable difference with the mesh points is that they now a LAN port on the back. So if you have some legacy devices that don’t have Wi-Fi, you can use this port to get them connected. The LAN port can also be used for connecting the router to the mesh point via a cable. This is called ethernet backhaul and can help if the signal between the points isn’t strong enough.
The App
If AmpliFi had created separate apps for their different devices, it would have been catastrophic. Fortunately, all the features and functionality are identical regardless of which unit you purchase. Parental controls are a strong point in the app, as you can create a group and apply a schedule which restricts internet access between certain times.
Guest networks can be created in just a few clicks. You can also set limits for how many devices are allowed on the guest network as well as how long it will be active for. You can even share the Wi-Fi name and password through the app via a text message or WhatsApp making it easy for your guests to sign in. One feature that would perfect this would be the ability to join the guest network via a QR code similar to what some of the other vendors offer.
To make sure your network is running smoothly you can do speed tests from within the performance section. The app also keeps track of your previous speed tests in case you need to contest the speeds you’re paying for from your ISP and for checking signal quality. If one of your users are having a problem, the diagnosis tab will give you a quick rundown of your network in a matter of seconds letting you get to the problem as soon as possible.
If you wanted to keep track of your network remotely, you can pair your AmpliFi account with your Google account. You’ll have full control from anywhere in the world. The app also allows controlling multiple AmpliFi systems if you had more than one network to manage.
Advanced Settings
Some settings are hidden in the app for the sake of simplicity. AmpliFi should work out of the box with minimal configuration, but there may be some settings that need tweaking for you to get the best experience.
You can do this via the traditional method of configuring a router, that is entering its IP address into the web browser. Some of the settings here include how AmpliFi connects to the internet and are necessary if your ISP requires a username and password for internet access.
You may also have your own preference for which Domain Name System (DNS) server to use. This can be configured from within the AmpliFi web portal.
New Developments
For companies to set themselves apart from the competition, they need to innovate. Here it seems AmpliFi has taken a book from their more elaborate UniFi product in terms of a Web Controller. The Web Controller is available in beta currently and does give a glimpse of what’s to come. So while it might seem sparse, it’s not the released version yet.
The Web Controller serves two functions. First, you can configure your network from a web browser. Then it allows you to plan your network for your premises with a visual designer. Just upload a layout of your house and use the tools to draw the walls and or partitions. You’re even able to select a material for the walls, to help the controller in determining the signal penetration.
Now simply drag your router and mesh points to where you’ve placed them (or plan to place them). The controller will give you a representation of how far the signal will reach. This isn’t an exact science as Wi-Fi is still susceptible to interference from other devices. However, it does give you a good estimation.
You’re able to see coverage from both 2.4 and 5Ghz networks and may help you understand how to get the most from your device placement. You can also see how devices are connected to your network as well as throughput for each of your mesh points. The controller is an exciting development from AmpliFi and will allow you to get the most of your AmpliFi deployment.
The Verdict
AmpliFi has put a lot of effort into the design of both the devices as well as the app. The units can be placed in plain sight and won’t spoil your home’s feng shui. The fully featured app gives you full control of your network. With the ever-increasing feature set coming to AmpliFi, it makes a compelling case.
At such a disruptive price point AmpliFi can be a perfect match if you have a small home or apartment. Finally, if you prefer a surface top solution compared to the wall socket mesh points the Instant is a fantastic solution. Hopefully, there will be an option to include DynamicDNS support as well as pairing kit mesh points to other systems.
Overall AmpliFi has added a fantastic product to their range. There’s no longer a reason to be plagued by miserable Wi-Fi.
Enter the Competition!
AmpliFi Instant Mesh Router Giveaway
Read the full article: AmpliFi Instant: The Best Mesh Wi-Fi on a Budget
AmpliFi Instant: The Best Mesh Wi-Fi on a Budget published first on http://droneseco.tumblr.com/
0 notes
Text
8 Surprising Marketing Predictions for 2018
Marketing can be a bit like gambling.
You test out one advertising channel and measure your results.
Every so often, a new marketing channel or program becomes available. Eager marketers jump at the new opportunity and gamble some of their ad budget into it.
Some of those gambles crush it because they struck gold with the new channel connecting with the right audience.
Each year brings a few of these big new opportunities. This post will outline some of our predictions for those new opportunities and trends that will emerge into 2018.
What predictions came true and which ones started with a bang, but ultimately fizzled out? Let’s take a closer look:
1. Blended Marketing Will Continue to Dominate in 2018
Just as the incredible rise of ad blockers on the web has filtered out much of the advertising noise, so too are consumer bombarded by omni-channel offers that don’t really meet their needs, or happen at inopportune times.
As a result, consumers are being much more selective about the apps they install, the sites they visit and the emails they receive. If you’re not doing enough to stay at the top of their minds in ways that aren’t intrusive, you’re giving yourself a one-way ticket to UnsubscribeLand.
This is why many businesses look at omni-channel as more risk than reward. Do you really want to be everywhere the customer is all the time? Does the customer want you to be? Are you more of an elegant butterfly in their minds, or a pesky fly? If you don’t take the time to refine and chart your marketing course appropriately, they’ll make that decision for you.
Social media and mobile media continued to blur the lines with integrated shopping, recommendations, videos and reviews – creating an even greater push to get noticed among the amalgamated chunk of product pitches, retargeting ads and “I’m-an-authority-look-at-me” videos. As more and more advertisers step up to the plate, they look at what others are doing and then copy their efforts – rather than test on their own to see what their unique audience would respond to.
And, in an effort to get in on this big, blended push, Google shifted its search results to include video, recent news, location information and other details to help match the user with their search request even faster and more thoroughly than before.
So if everything’s coming together in a more finely-tuned customer experience, what didn’t really take off as well as we expected it to?
2. Chatbots Will Grow into More Businesses and Sectors
Chatbots emerged a few years ago on platforms like Facebook in the form of Messenger bots. Companies like 1-800 Flowers immediately hopped on board and made it easy for customers to order from a bot:
In the years since their inception, they’ve grown from a few e-commerce stores using them to a more wide adoption.
And they’re not going away anytime soon. They’re on our 2018 marketing predictions list because we believe that these bots will increase their penetration in our daily lives.
Think about it – if you call a customer service line, you’re frequently first talking to what is essentially a robot. They’ll ask you a question, you answer it, and the programming in the background will try to solve the problem for you. (I’ve had this experience myself when chatting with the Comcast support line).
If the bot on the phone cannot help you, the last resort is to transfer you to a real support person. Now we just have that through our messenger apps, but it’s going to go father than support.
Bots can help you conduct research, qualify leads, personalize the user experience, sell more products, and much more. Expect to see more of them on platforms outside of Facebook Messenger Ads.
If you’re interested in using a chatbot, you can use Facebook Messenger Ads or a platform from Drift called Driftbot.
3. From Lifestyle Apps to Augmented Reality
I had originally predicted that 2016 would see the rise and greater adoption of lifestyle apps – meaning apps that people installed as a reflection of who they were. These could be a combination fitness-weather-diet tracker app rather than having apps for all three of these items. But the looming spectre of data overages constantly nipping at their heels means developers have tended to go easy on what’s available via app versus the much more open and accommodating web.
What stirred everyone’s imagination was augmented reality. The undisputed summer hit of 2016 was Pokemon Go, but it, too, failed to gain much traction after the initial buzz wore off. Still, it was a masterpiece of gamification and as mobile becomes more powerful, we can look forward to seeing what augmented reality can do – particularly when you’re able to bring together the aforementioned apps into an all-in-one experience that isn’t just helpful, but subtly addictive too.
Apple CEO Tim Cook has made a big bet into augmented reality, and now Apple is supporting iOS developers with their Augmented Reality Kit.
And Tim Cook isn’t alone. Mark Zuckerberg has really started all this with his Oculus acquisition. Zuckerberg’s bet into AR has only intensified recently with the poaching of an executive from Google.
Expect to see more from these companies in the year about how AR will impact it’s users and advertising partners.
4. Talk To Me – Dash Buttons and the Internet of Things
Voice-guided search, wearable devices and innovations like the Amazon Alexa and Google Home are starting to bridge the gap between the internet you access on your computer, and the internet you access everywhere.
Awkward attempts to blend e-commerce with that always-on, on-demand functionality has come out in the form of Amazon Dash buttons – WiFi connected devices that let you instantly order your favorite household products, but they’re more of a novelty than a really useful and innovative design. Watch them become as memorable and curious as the CueCat.
What will be changing for marketers is an increasing investment in understanding analytics and getting a truly cross-channel view of the consumer. Rather than throwing out a bunch of things that the company “thinks” the customer might want, they’re finally gathering enough intelligence (and enough of an understanding to know what to do with it), that they can track a consumer from a search on their home computer to a product description page on their mobile phone, to an order form on their company laptop.
This is known as advanced attribution, and it’s going to change the way we market to customers in ways we probably can’t even imagine. But think of the potential of engaging that consumer at the right time and place, on the right device, when they’re at the right stage of the buying cycle, and you can see precisely how much of a game-changer this technology is.
5. A Bigger Focus on Tools and Services that Fill in the Gaps
Things like predictive analytics and personalization tools are great – but they’re mostly in a vacuum. That means you can’t really leverage them to see the big picture, as well as the granular details you need in order to make decisions with confidence.
Expect innovations in 2018 to help bridge the gaps with many of these services, allowing for greater integrations with existing systems and a better, visual picture of what all that information really means.
Amazon CEO Jeff Bezos announced that they’re doubling down on Alexa. More companies are putting their voice (so to speak) on Alexa.
Other types of services that are not even part of the analytics industry are popping up to fill in the empty spaces left by other innovators. Uber, Airbnb, Amazon Echo/Google Home and many other services like these are becoming ubiquitous in our lifestyle because of the service they provide — a service we never even knew we needed until we saw its potential.
Tools like these are poised to change the way we market on the web, and you can expect even more integrations with popular software and SaaS products to broaden their reach and capabilities.
6. The Power and Passion of Social Media – Who Decides What You Get to See?
Although this doesn’t just apply to marketing, the U.S. election was watched, dissected, ranted and raved over across social media platforms. So much so, that “fake news” and allegations started littering people’s news feeds.
But this then begs the question – should you encapsulate yourself in a bubble – seeing only what you want to see, or should companies give you a little bit of everything and let you choose accordingly? Who decides? Social media has a very powerful and passionate audience on its side – and a significant amount of data that it’s going to have to make some definitive and perhaps unexpected decisions on. After all, not offering a balance can affect user engagement, and losing user engagement is the one thing that no social network wants to imagine – it’s their lifeblood. How they plan to approach this particular conundrum remains to be seen, but you can bet that eventually they’ll be forced to decide – and not everyone may agree with the results.
7. Influencer Marketing Will Grow Even Further
In a world filled with ad blockers and DVR, it can be difficult for marketers to get their message through.
The workaround many marketers are finding effective is going around traditional channels like TV ads and banner ads and moving towards selling their products through a conduit known as an influencer.
These influencers typically have a large enough following on social media that they’re able to sell a post, tweet, or image to all their followers. These aren’t blocked by ad-blockers, and they’re “blended” into people’s social feeds so all their followers see them.
Some big corporations use influencers in their TV ads, others use them on the websites. Local businesses reach consumers through local influencers – people on radio or TV.
2018 will only see this grow. It will spread to other industries and reach more people than ever. Teens on their Snapchat will see the celebrities they’re following promoting the latest product or movie.
Instagram will have influencers holding their products that marketers are paying big money for. More and more tweets will have the #ad placed next to it.
.@oreo and I share a birthday … and a love of giving away 1 Million free OREO Chocolate Candy Bars! #OreoBirthdayGiveaway #ad. No purchase necessary. https://t.co/V7YyRqpl06 pic.twitter.com/E5TfWhVaYD
— SHAQ (@SHAQ) March 6, 2018
8. More Advertising Programs on Instagram Will Become Available
The war between social media apps Snapchat and Instagram will continue into 2018. Expect Facebook to continue efforts to further monetize Instagram.
In the last Facebook earnings release of 2017, Sheryl Sandberg said Facebook had 2 million advertisers on Instagram, compared to 6 million on Instagram. I expect Facebook will try to increase this number through new advertising programs and platforms available to marketers.
At the time of this writing, they have 4 different advertising products available. If you’re a daily Instagram user, you’ve probably seen all of them – photo ads, video ads, carousel ads, and video ads.
Expect to see some more innovative ad products created in the future.
What Do You Think is in Store for 2018?
Do you think we’ll see some surprising changes on how we market to consumers in 2018? What do you think will happen? Share your own predictions with us in the comments below!
About the Author: Neil Patel is the cofounder of Neil Patel Digital.
Read more here - http://review-and-bonuss.blogspot.com/2018/03/8-surprising-marketing-predictions-for.html
0 notes
Text
8 Surprising Marketing Predictions for 2018
Marketing can be a bit like gambling.
You test out one advertising channel and measure your results.
Every so often, a new marketing channel or program becomes available. Eager marketers jump at the new opportunity and gamble some of their ad budget into it.
Some of those gambles crush it because they struck gold with the new channel connecting with the right audience.
Each year brings a few of these big new opportunities. This post will outline some of our predictions for those new opportunities and trends that will emerge into 2018.
What predictions came true and which ones started with a bang, but ultimately fizzled out? Let’s take a closer look:
1. Blended Marketing Will Continue to Dominate in 2018
Just as the incredible rise of ad blockers on the web has filtered out much of the advertising noise, so too are consumer bombarded by omni-channel offers that don’t really meet their needs, or happen at inopportune times.
As a result, consumers are being much more selective about the apps they install, the sites they visit and the emails they receive. If you’re not doing enough to stay at the top of their minds in ways that aren’t intrusive, you’re giving yourself a one-way ticket to UnsubscribeLand.
This is why many businesses look at omni-channel as more risk than reward. Do you really want to be everywhere the customer is all the time? Does the customer want you to be? Are you more of an elegant butterfly in their minds, or a pesky fly? If you don’t take the time to refine and chart your marketing course appropriately, they’ll make that decision for you.
Social media and mobile media continued to blur the lines with integrated shopping, recommendations, videos and reviews – creating an even greater push to get noticed among the amalgamated chunk of product pitches, retargeting ads and “I’m-an-authority-look-at-me” videos. As more and more advertisers step up to the plate, they look at what others are doing and then copy their efforts – rather than test on their own to see what their unique audience would respond to.
And, in an effort to get in on this big, blended push, Google shifted its search results to include video, recent news, location information and other details to help match the user with their search request even faster and more thoroughly than before.
So if everything’s coming together in a more finely-tuned customer experience, what didn’t really take off as well as we expected it to?
2. Chatbots Will Grow into More Businesses and Sectors
Chatbots emerged a few years ago on platforms like Facebook in the form of Messenger bots. Companies like 1-800 Flowers immediately hopped on board and made it easy for customers to order from a bot:
In the years since their inception, they’ve grown from a few e-commerce stores using them to a more wide adoption.
And they’re not going away anytime soon. They’re on our 2018 marketing predictions list because we believe that these bots will increase their penetration in our daily lives.
Think about it – if you call a customer service line, you’re frequently first talking to what is essentially a robot. They’ll ask you a question, you answer it, and the programming in the background will try to solve the problem for you. (I’ve had this experience myself when chatting with the Comcast support line).
If the bot on the phone cannot help you, the last resort is to transfer you to a real support person. Now we just have that through our messenger apps, but it’s going to go father than support.
Bots can help you conduct research, qualify leads, personalize the user experience, sell more products, and much more. Expect to see more of them on platforms outside of Facebook Messenger Ads.
If you’re interested in using a chatbot, you can use Facebook Messenger Ads or a platform from Drift called Driftbot.
3. From Lifestyle Apps to Augmented Reality
I had originally predicted that 2016 would see the rise and greater adoption of lifestyle apps – meaning apps that people installed as a reflection of who they were. These could be a combination fitness-weather-diet tracker app rather than having apps for all three of these items. But the looming spectre of data overages constantly nipping at their heels means developers have tended to go easy on what’s available via app versus the much more open and accommodating web.
What stirred everyone’s imagination was augmented reality. The undisputed summer hit of 2016 was Pokemon Go, but it, too, failed to gain much traction after the initial buzz wore off. Still, it was a masterpiece of gamification and as mobile becomes more powerful, we can look forward to seeing what augmented reality can do – particularly when you’re able to bring together the aforementioned apps into an all-in-one experience that isn’t just helpful, but subtly addictive too.
Apple CEO Tim Cook has made a big bet into augmented reality, and now Apple is supporting iOS developers with their Augmented Reality Kit.
And Tim Cook isn’t alone. Mark Zuckerberg has really started all this with his Oculus acquisition. Zuckerberg’s bet into AR has only intensified recently with the poaching of an executive from Google.
Expect to see more from these companies in the year about how AR will impact it’s users and advertising partners.
4. Talk To Me – Dash Buttons and the Internet of Things
Voice-guided search, wearable devices and innovations like the Amazon Alexa and Google Home are starting to bridge the gap between the internet you access on your computer, and the internet you access everywhere.
Awkward attempts to blend e-commerce with that always-on, on-demand functionality has come out in the form of Amazon Dash buttons – WiFi connected devices that let you instantly order your favorite household products, but they’re more of a novelty than a really useful and innovative design. Watch them become as memorable and curious as the CueCat.
What will be changing for marketers is an increasing investment in understanding analytics and getting a truly cross-channel view of the consumer. Rather than throwing out a bunch of things that the company “thinks” the customer might want, they’re finally gathering enough intelligence (and enough of an understanding to know what to do with it), that they can track a consumer from a search on their home computer to a product description page on their mobile phone, to an order form on their company laptop.
This is known as advanced attribution, and it’s going to change the way we market to customers in ways we probably can’t even imagine. But think of the potential of engaging that consumer at the right time and place, on the right device, when they’re at the right stage of the buying cycle, and you can see precisely how much of a game-changer this technology is.
5. A Bigger Focus on Tools and Services that Fill in the Gaps
Things like predictive analytics and personalization tools are great – but they’re mostly in a vacuum. That means you can’t really leverage them to see the big picture, as well as the granular details you need in order to make decisions with confidence.
Expect innovations in 2018 to help bridge the gaps with many of these services, allowing for greater integrations with existing systems and a better, visual picture of what all that information really means.
Amazon CEO Jeff Bezos announced that they’re doubling down on Alexa. More companies are putting their voice (so to speak) on Alexa.
Other types of services that are not even part of the analytics industry are popping up to fill in the empty spaces left by other innovators. Uber, Airbnb, Amazon Echo/Google Home and many other services like these are becoming ubiquitous in our lifestyle because of the service they provide — a service we never even knew we needed until we saw its potential.
Tools like these are poised to change the way we market on the web, and you can expect even more integrations with popular software and SaaS products to broaden their reach and capabilities.
6. The Power and Passion of Social Media – Who Decides What You Get to See?
Although this doesn’t just apply to marketing, the U.S. election was watched, dissected, ranted and raved over across social media platforms. So much so, that “fake news” and allegations started littering people’s news feeds.
But this then begs the question – should you encapsulate yourself in a bubble – seeing only what you want to see, or should companies give you a little bit of everything and let you choose accordingly? Who decides? Social media has a very powerful and passionate audience on its side – and a significant amount of data that it’s going to have to make some definitive and perhaps unexpected decisions on. After all, not offering a balance can affect user engagement, and losing user engagement is the one thing that no social network wants to imagine – it’s their lifeblood. How they plan to approach this particular conundrum remains to be seen, but you can bet that eventually they’ll be forced to decide – and not everyone may agree with the results.
7. Influencer Marketing Will Grow Even Further
In a world filled with ad blockers and DVR, it can be difficult for marketers to get their message through.
The workaround many marketers are finding effective is going around traditional channels like TV ads and banner ads and moving towards selling their products through a conduit known as an influencer.
These influencers typically have a large enough following on social media that they’re able to sell a post, tweet, or image to all their followers. These aren’t blocked by ad-blockers, and they’re “blended” into people’s social feeds so all their followers see them.
Some big corporations use influencers in their TV ads, others use them on the websites. Local businesses reach consumers through local influencers – people on radio or TV.
2018 will only see this grow. It will spread to other industries and reach more people than ever. Teens on their Snapchat will see the celebrities they’re following promoting the latest product or movie.
Instagram will have influencers holding their products that marketers are paying big money for. More and more tweets will have the #ad placed next to it.
.@oreo and I share a birthday … and a love of giving away 1 Million free OREO Chocolate Candy Bars! #OreoBirthdayGiveaway #ad. No purchase necessary. https://t.co/V7YyRqpl06 pic.twitter.com/E5TfWhVaYD
— SHAQ (@SHAQ) March 6, 2018
8. More Advertising Programs on Instagram Will Become Available
The war between social media apps Snapchat and Instagram will continue into 2018. Expect Facebook to continue efforts to further monetize Instagram.
In the last Facebook earnings release of 2017, Sheryl Sandberg said Facebook had 2 million advertisers on Instagram, compared to 6 million on Instagram. I expect Facebook will try to increase this number through new advertising programs and platforms available to marketers.
At the time of this writing, they have 4 different advertising products available. If you’re a daily Instagram user, you’ve probably seen all of them – photo ads, video ads, carousel ads, and video ads.
Expect to see some more innovative ad products created in the future.
What Do You Think is in Store for 2018?
Do you think we’ll see some surprising changes on how we market to consumers in 2018? What do you think will happen? Share your own predictions with us in the comments below!
About the Author: Neil Patel is the cofounder of Neil Patel Digital.
0 notes
Text
8 Surprising Marketing Predictions for 2018
Marketing can be a bit like gambling.
You test out one advertising channel and measure your results.
Every so often, a new marketing channel or program becomes available. Eager marketers jump at the new opportunity and gamble some of their ad budget into it.
Some of those gambles crush it because they struck gold with the new channel connecting with the right audience.
Each year brings a few of these big new opportunities. This post will outline some of our predictions for those new opportunities and trends that will emerge into 2018.
What predictions came true and which ones started with a bang, but ultimately fizzled out? Let’s take a closer look:
1. Blended Marketing Will Continue to Dominate in 2018
Just as the incredible rise of ad blockers on the web has filtered out much of the advertising noise, so too are consumer bombarded by omni-channel offers that don’t really meet their needs, or happen at inopportune times.
As a result, consumers are being much more selective about the apps they install, the sites they visit and the emails they receive. If you’re not doing enough to stay at the top of their minds in ways that aren’t intrusive, you’re giving yourself a one-way ticket to UnsubscribeLand.
This is why many businesses look at omni-channel as more risk than reward. Do you really want to be everywhere the customer is all the time? Does the customer want you to be? Are you more of an elegant butterfly in their minds, or a pesky fly? If you don’t take the time to refine and chart your marketing course appropriately, they’ll make that decision for you.
Social media and mobile media continued to blur the lines with integrated shopping, recommendations, videos and reviews – creating an even greater push to get noticed among the amalgamated chunk of product pitches, retargeting ads and “I’m-an-authority-look-at-me” videos. As more and more advertisers step up to the plate, they look at what others are doing and then copy their efforts – rather than test on their own to see what their unique audience would respond to.
And, in an effort to get in on this big, blended push, Google shifted its search results to include video, recent news, location information and other details to help match the user with their search request even faster and more thoroughly than before.
So if everything’s coming together in a more finely-tuned customer experience, what didn’t really take off as well as we expected it to?
2. Chatbots Will Grow into More Businesses and Sectors
Chatbots emerged a few years ago on platforms like Facebook in the form of Messenger bots. Companies like 1-800 Flowers immediately hopped on board and made it easy for customers to order from a bot:
In the years since their inception, they’ve grown from a few e-commerce stores using them to a more wide adoption.
And they’re not going away anytime soon. They’re on our 2018 marketing predictions list because we believe that these bots will increase their penetration in our daily lives.
Think about it – if you call a customer service line, you’re frequently first talking to what is essentially a robot. They’ll ask you a question, you answer it, and the programming in the background will try to solve the problem for you. (I’ve had this experience myself when chatting with the Comcast support line).
If the bot on the phone cannot help you, the last resort is to transfer you to a real support person. Now we just have that through our messenger apps, but it’s going to go father than support.
Bots can help you conduct research, qualify leads, personalize the user experience, sell more products, and much more. Expect to see more of them on platforms outside of Facebook Messenger Ads.
If you’re interested in using a chatbot, you can use Facebook Messenger Ads or a platform from Drift called Driftbot.
3. From Lifestyle Apps to Augmented Reality
I had originally predicted that 2016 would see the rise and greater adoption of lifestyle apps – meaning apps that people installed as a reflection of who they were. These could be a combination fitness-weather-diet tracker app rather than having apps for all three of these items. But the looming spectre of data overages constantly nipping at their heels means developers have tended to go easy on what’s available via app versus the much more open and accommodating web.
What stirred everyone’s imagination was augmented reality. The undisputed summer hit of 2016 was Pokemon Go, but it, too, failed to gain much traction after the initial buzz wore off. Still, it was a masterpiece of gamification and as mobile becomes more powerful, we can look forward to seeing what augmented reality can do – particularly when you’re able to bring together the aforementioned apps into an all-in-one experience that isn’t just helpful, but subtly addictive too.
Apple CEO Tim Cook has made a big bet into augmented reality, and now Apple is supporting iOS developers with their Augmented Reality Kit.
And Tim Cook isn’t alone. Mark Zuckerberg has really started all this with his Oculus acquisition. Zuckerberg’s bet into AR has only intensified recently with the poaching of an executive from Google.
Expect to see more from these companies in the year about how AR will impact it’s users and advertising partners.
4. Talk To Me – Dash Buttons and the Internet of Things
Voice-guided search, wearable devices and innovations like the Amazon Alexa and Google Home are starting to bridge the gap between the internet you access on your computer, and the internet you access everywhere.
Awkward attempts to blend e-commerce with that always-on, on-demand functionality has come out in the form of Amazon Dash buttons – WiFi connected devices that let you instantly order your favorite household products, but they’re more of a novelty than a really useful and innovative design. Watch them become as memorable and curious as the CueCat.
What will be changing for marketers is an increasing investment in understanding analytics and getting a truly cross-channel view of the consumer. Rather than throwing out a bunch of things that the company “thinks” the customer might want, they’re finally gathering enough intelligence (and enough of an understanding to know what to do with it), that they can track a consumer from a search on their home computer to a product description page on their mobile phone, to an order form on their company laptop.
This is known as advanced attribution, and it’s going to change the way we market to customers in ways we probably can’t even imagine. But think of the potential of engaging that consumer at the right time and place, on the right device, when they’re at the right stage of the buying cycle, and you can see precisely how much of a game-changer this technology is.
5. A Bigger Focus on Tools and Services that Fill in the Gaps
Things like predictive analytics and personalization tools are great – but they’re mostly in a vacuum. That means you can’t really leverage them to see the big picture, as well as the granular details you need in order to make decisions with confidence.
Expect innovations in 2018 to help bridge the gaps with many of these services, allowing for greater integrations with existing systems and a better, visual picture of what all that information really means.
Amazon CEO Jeff Bezos announced that they’re doubling down on Alexa. More companies are putting their voice (so to speak) on Alexa.
Other types of services that are not even part of the analytics industry are popping up to fill in the empty spaces left by other innovators. Uber, Airbnb, Amazon Echo/Google Home and many other services like these are becoming ubiquitous in our lifestyle because of the service they provide — a service we never even knew we needed until we saw its potential.
Tools like these are poised to change the way we market on the web, and you can expect even more integrations with popular software and SaaS products to broaden their reach and capabilities.
6. The Power and Passion of Social Media – Who Decides What You Get to See?
Although this doesn’t just apply to marketing, the U.S. election was watched, dissected, ranted and raved over across social media platforms. So much so, that “fake news” and allegations started littering people’s news feeds.
But this then begs the question – should you encapsulate yourself in a bubble – seeing only what you want to see, or should companies give you a little bit of everything and let you choose accordingly? Who decides? Social media has a very powerful and passionate audience on its side – and a significant amount of data that it’s going to have to make some definitive and perhaps unexpected decisions on. After all, not offering a balance can affect user engagement, and losing user engagement is the one thing that no social network wants to imagine – it’s their lifeblood. How they plan to approach this particular conundrum remains to be seen, but you can bet that eventually they’ll be forced to decide – and not everyone may agree with the results.
7. Influencer Marketing Will Grow Even Further
In a world filled with ad blockers and DVR, it can be difficult for marketers to get their message through.
The workaround many marketers are finding effective is going around traditional channels like TV ads and banner ads and moving towards selling their products through a conduit known as an influencer.
These influencers typically have a large enough following on social media that they’re able to sell a post, tweet, or image to all their followers. These aren’t blocked by ad-blockers, and they’re “blended” into people’s social feeds so all their followers see them.
Some big corporations use influencers in their TV ads, others use them on the websites. Local businesses reach consumers through local influencers – people on radio or TV.
2018 will only see this grow. It will spread to other industries and reach more people than ever. Teens on their Snapchat will see the celebrities they’re following promoting the latest product or movie.
Instagram will have influencers holding their products that marketers are paying big money for. More and more tweets will have the #ad placed next to it.
.@oreo and I share a birthday … and a love of giving away 1 Million free OREO Chocolate Candy Bars! #OreoBirthdayGiveaway #ad. No purchase necessary. https://t.co/V7YyRqpl06 pic.twitter.com/E5TfWhVaYD
— SHAQ (@SHAQ) March 6, 2018
8. More Advertising Programs on Instagram Will Become Available
The war between social media apps Snapchat and Instagram will continue into 2018. Expect Facebook to continue efforts to further monetize Instagram.
In the last Facebook earnings release of 2017, Sheryl Sandberg said Facebook had 2 million advertisers on Instagram, compared to 6 million on Instagram. I expect Facebook will try to increase this number through new advertising programs and platforms available to marketers.
At the time of this writing, they have 4 different advertising products available. If you’re a daily Instagram user, you’ve probably seen all of them – photo ads, video ads, carousel ads, and video ads.
Expect to see some more innovative ad products created in the future.
What Do You Think is in Store for 2018?
Do you think we’ll see some surprising changes on how we market to consumers in 2018? What do you think will happen? Share your own predictions with us in the comments below!
About the Author: Neil Patel is the cofounder of Neil Patel Digital.
from Online Marketing Tips https://kissmetrics.wpengine.com/surprising-marketing-predictions/
0 notes
Text
Welcome to our Hacker Tools list of 2017…
Also….remember! All these tools come bundled in pentesting Linux distro’s such as Kali Linux or BackBox, so we’d certainly recommend that you install an appropriate Linux hacking box to make your life easier – not least because repositories are (automatically) updated.
1.Nmap (Network Mapper) | Free
Used to Scan Ports and Map Networks - and a whole bunch more!
Nmap is an abbreviation of 'Network Mapper', and it's very well known free open source hackers tool. Nmap is mainly used for network discovery and security auditing. Literally, thousands of system admins all around the world will use nmap for network inventory, check for open ports, manage service upgrade schedules, and monitor host or service uptime. Nmap, as a tool uses raw IP packets in creative ways to determine what hosts are available on the network, what services (application name and version) those hosts are providing information about, what operating systems (fingerprinting) and what type and version of packet filters/ firewalls are being used by the target. There are dozens of benefits of using nmap, one of which is that fact that the admin user is able to determine whether the network (and associated nodes) need patching. Nmap's been featured in literally every hacker movie out there, not least the recent Mr. Robot series. It's also worth mentioning that there's a GUI version of Nmap called 'Zenmap'. We'd advise you to learn using Nmap (i.e. the 'command line') then rotate into Zenmap when you are feeling all confident.
Download Link ===>>>https://goo.gl/FqTu83
2.Metasploit Penetration Testing Software | Free & Paid
Vulnerability Exploitation Tool
The Metasploit Project is a hugely popular pentesting or hacking framework. If you are new to Metasploit think of it as a 'collection of hacking tools and frameworks' that can be used to execute various tasks. Widely used by cybersecurity professionals and ethical hackers this is a tool that you have to learn. Metasploit is essentially a computer security project (framework) that provides the user with vital information regarding known security vulnerabilities and helps to formulate penetration testing and IDS testing plans, strategies and methodologies for exploitation. There's a ton of incredibly useful Metasploit information out there and we hope that the books that we've chosen go someway to help you on your journey, not least if you are a beginner just starting out and looking for beginners tutorials in how to use Metasploit.
Download Link ===>>>https://goo.gl/65ktba
3.John The Ripper | Free
Password Cracking Tool
John the Ripper (often you'll see abbreviated as 'JTR') wins the award for having the coolest name. John the Ripper, mostly just referred to as simply, 'John' is a popular password cracking pentesting tool that is most commonly used to perform dictionary attacks. John the Ripper takes text string samples (from a text file, referred to as a 'wordlist', containing popular and complex words found in a dictionary or real passwords cracked before), encrypting it in the same way as the password being cracked (including both the encryption algorithm and key), and comparing the output to the encrypted string. This tool can also be used to perform a variety of alterations to dictionary attacks. If you are somewhat confused between John the Ripper and THC Hydra then think of John the Ripper as an 'offline' password cracker whilst THC Hydra is an "online" cracker.
Download Link ===>>>https://goo.gl/NtY6xb
4.THC Hydra | Free
Password Cracking Tool
We've purposely placed THC Hydra underneath John The Ripper because they often go 'hand-in'hand'. THC Hydra (we've abbreviated to simply 'Hydra' throughout our site) is a hugely popular password cracker and has a very active and experienced development team. Essentially THC Hydra is a fast and stable Network Login Hacking Tool that will use dictionary or brute-force attacks to try various password and login combinations against an log in page. This hacking tool supports a wide set of protocols including Mail (POP3, IMAP, etc.), Databases, LDAP, SMB, VNC, and SSH. Take a look at John the Ripper as well.
Download Link ===>>>https://goo.gl/fD2Ric 5.OWASP Zed | Free
Web Vulnerability Scanner
The Zed Attack Proxy (ZAP) is now one of the most popular OWASP projects. The fact that you've reached this page means that you are likely already a relatively seasoned cybersecurity professional so it's highly likely that you are very familiar with OWASP, not least the OWASP Top Ten Threats listing which is considered as being the 'guide-book' of web application security. This hacking and pentesting tool is a very efficient as well as being an 'easy to use' program that finds vulnerabilities in web applications. ZAP is a popular tool because it does have a lot of support and the OWASP community is really an excellent resource for those that work within Cyber Security. ZAP provides automated scanners as well as various tools that allow you the cyber pro to discover security vulnerabilities manually. Understanding and being able to master this tool would also be advantageous to your career as a penetration tester. If you are a developer then you have it's obviously highly recommended that you learn how to become very proficient with this 'hacker tool!'
Download Link ===>>>https://goo.gl/RDUchN
6.Wireshark | Free
Web Vulnerability Scanners
Wireshark is a very popular pentesting tool and for over a year it was not included on our list, however, by popular demand we added it in late June 2016. Wireshark essentially captures data packets in a network in real time and then displays the data in human-readable format (verbose). The tool (platform) has been highly developed and it includes filters, color-coding and other features that lets the user dig deep into network traffic and inspect individual packets. If you'd like to become a penetration tester or work as a Cyber Security practioner, then learning how to use Wireshark is a must. There are a ton of resources out there to learn Wireshark, and, of particular interest, there's also a Wireshark Certification which you can achieve and place on your LinkedIn profile.
Download Link ===>>>https://goo.gl/j1jkLW
7.Aircrack-ng | Free
Password Cracking Tool
The Aircrack suite of Wifi (Wireless) hacking tools are legendary because they are very effectively when used in the right hands. For those new to this wireless-specific hacking program, Aircrack-ng is an 802.11 WEP and WPA-PSK keys cracking hacking tool that can recover keys when sufficient data packets have been captured (in monitor mode). For those tasked with penetrating and auditing wireless networks Aircrack-ng will become your best friend. It's useful to know that Aircrack-ng implements standard FMS attacks along with some optimizations like KoreK attacks, as well as the PTW attacks to make their attacks more potent. If you are a mediocre hacker then youll be able to crack WEP in a few minutes and you ought to be pretty proficient at being able to crack WPA/ WPA2. For those interested in Wireless Hacking we'd also highly recommend taking a look at the very awesome Reaver, another very popular hacking tool that alas we couldn't add to our list.
Download Link ===>>>https://goo.gl/itByaz
8.Maltego | Free & Paid
Digital Forensics
Maltego is different in that it works within a digital forensics sphere. Maltego is a platform that was designed to deliver an overall cyber threat picture to the enterprise or local environment in which an organization operates. One of the awesome things about Maltego which likely makes it so popular (and included in the Kali Linux Top Ten) is its's unique perspective in offering both network and resource based entities is the aggregation of information sourced throughout the web - whether it's the current configuration of a vulnerable router within a network or the current whereabouts of your staff members on their international visits, Maltego can locate, aggregate and visualize this data! For those interested in learning how to use Maltego we'd also recommend learning about OSINT cybersecurity data procurement.
Download LInk ===>>>https://goo.gl/7PxPMg
9.Cain and Abel Hacking Tool | Free
Password Cracker/ Password Hacking
Cain and Abel (often simply abbreviated to Cain) is a hugely popular hacking tool and one that is very often mentioned online in a variety of 'hacking tutorials'. At its' heart, Cain and Abel is a password recovery tool for Microsoft Windows but it can be used off-label in a variety of uses, for example, white and black hat hackers use Cain to recover (i.e. 'crack') many types of passwords using methods such as network packet sniffing and by using the tool to crack password hashes. Cain, for example, when used to crack password hashes would use methods such as dictionary attacks, brute force, rainbow table attacks and cryptanalysis attacks.
Download LInk ===>>>https://goo.gl/zPXHLd
10.Nikto Website Vulnerability Scanner | Free
Website Vulnerability Scanner Hacking Tool
Nikto is another classic 'Hacking Tool' that a lot of pentesters like to use. Worth mentioning that Nickto is sponsored by Netsparker (which is yet another Hacking Tool that we have also listed in our directory). Nikto is an Open Source (GPL) web server scanner which is able to scan and detect web servers for vulnerabilities. The system searches against a database of over 6800 potentially dangerous files/ programs when scanning software stacks. Nikto, like other scanners out there, also scans for outdated (unpatched) versions of over 1300 servers, and version specific problems on over 275 servers. Interestingly, Nikto can also check server configuration items such as the presence of multiple index files, HTTP server options, and the platform will also try to identify installed web servers and web applications. Nikto will get picked up by any semi-decent IDS tool so its' really useful when conducting a white-hat/ white-box pentest. Certainly a great tool to learn your skills on when attacking an open box for training.
Download LInk ===>>>https://goo.gl/611vH6
Like us on facebook :-
https://goo.gl/5VrVUt -------------------------------------------------------------------------------- Download Our Android App https://goo.gl/gfNcWL -------------------------------------------------------------------------------- subscribe us for more videos on youtube
https://goo.gl/J6mj7U

0 notes
Text
New Post has been published on My Pro Blog
New Post has been published on https://myproblog.com/tips-on-child-mobile-internet-safety/
Tips on Child Mobile Internet Safety
Ask any kid from first grade to college to name the phone, media player or tablet that they covet the most and you’ll hear iPhone, iPod touch and the iPad. Brand awareness and demand for Apple products among the jungle gym crowd has never been higher. What most parents don’t realize though is that if appropriate safety checks aren’t put in place, Apple’s wonderful devices could be an unguarded gateway to dangerous forbidden fruits.
While most parents know they should use parental controls on their home computers, according to a survey by McAfee, four out of five parents fail to turn such software on. Nearly a third of parents left their kids alone when surfing, and almost half of parents said they didn’t know if their kids had social networking accounts at sites like Facebook. (Think your kid is too young? Over 20 percent of 4th – 5th graders have a social networking profile. According to a Cox Communications study, 72 percent of teens have a social networking profile and nearly half have a public profile viewable by anyone.)
Over half of parents don’t monitor their kids’ desktop or laptop usage (according to an MSN Europe survey). When it comes to mobile Internet safety, even the most tech savvy parents find it next to impossible to monitor their kids’ mobile habits. Even if kids only use their mobile devices during the commute to and from school, they need to use them safely. Personal monitoring is not always possible. Even when they’re in the same room, a parent can’t read what’s on a small screen without sitting right next to their child.
Fortunately, there are technologies that can help. Parents can create mobile safety for their children, and it isn’t as difficult as they may think.
Mobile computing is the fastest growing technology sector, with youth market penetration rising higher each day. Seventy-six percent of all eight to 18-year olds have iPods or other MP3 players. Teens spend at least 49 minutes a day consuming media on mobile devices, according to a Kaiser Family Foundation Study.
Mobile technology can expose young people to the good, the bad and ugly of the Internet. According to a Pew Internet study, 70 percent of teens are exposed to pornography accidentally on the web.
The Apple of every kid’s eye: With over 120 million iOS devices sold, as of September, 2010 (67.6 million iPhones, 7.2 million iPads, 45.2 million iPod touches), Apple dominates the mobile market. Beyond its obvious cool factor, the availability of thousands of kid-friendly apps means that youth brand loyalty is already locked in. In addition to being “cool”, iOS devices are changing the way learning happens in the classroom and at home.
There are pilot programs using mobile learning in all 50 states. Many are centered around the iPod touch as the primary computer to replace all textbooks, coursework, graphing calculators, etc. The iSchool Initiative estimates each $150 iPod touch would save at least $600 per student per year. Those powerful numbers mean that more school programs will require an iPod touch. (A few schools will even standardize over to the iPod touch’s brother, the larger and more expensive iPad, which runs on the same iOS platform.)
Both parents and school districts will need to find ways to secure these devices to make them child-friendly at home and in the classroom. This isn’t just a matter of safety, there’s money involved. Schools that enable mobile learning need to implement Mobile Child Internet Protection standards to enforce a standard of Internet safety and remain eligible for federal funding.
As more school systems test Apple’s iOS products in the classroom, both parents and educators need to make sure that the first defense against inappropriate content (web filtering software) is set on kids’ iPhones, iPods and iPads.
Some think that the parental controls on iPods, iPhones and iPads are insufficient. While parental controls are important for desktops and laptops, mobile parental controls need to happen above and beyond what is built into the technology of the devices. To ensure that your mobile kids are safely surfing the mobile web, here are 10 tips to keep your child safe online.
Child mobile Internet safety tip #1: Safari could be a safari of unfiltered content. As great as Safari is at displaying sites (as long as they don’t use Flash), it has no web filtering parental controls. None. Zip. Zilch. If your kids want to chat on PredatorsRUs.com, Safari will let them. First and foremost, change the iPod’s Safari browser to one that allows web filtering.
Child mobile Internet safety tip #2: Invest in a leading online content filtering service. Services like Mobicip ( http://www.mobicip.com/ ) have won Parent’s Choice awards and are used by school districts across the country to filter dangerous online content. There are a number of child-safe iPod browsers on the market. Read the reviews and choose the best-rated child-safe iPod browser in your youngster’s age range.
Child mobile Internet safety tip #3: Use the iPod’s basic parental controls. Once you have installed the child-safe iPod browser, disable Safari. But be warned, kids are clever. If kids don’t like using a child-safe iPod browser, they will simply download another browser. Here’s how you stop them.
On the iPod’s Settings menu, choose Restrictions, and turn off Safari, YouTube, Installing Apps and Location. You can also turn off the camera, if that is appropriate.
While you are at it, restrict the kind of content they can download from iTunes to age appropriate levels. Turn off In-App Purchases.
Child mobile Internet safety tip #4: Search is king. Search is where the action is. (That’s why Google has a market cap of a $151 billion.) Children most often encounter inappropriate content by accident through searches. You need a child-safe iPod browser that enforces safe searches on all popular search engines. Make sure that this feature cannot be disabled by changing the search engine preferences.
Child mobile Internet safety tip #5: Keep your blacklist updated automatically. There are hundreds of thousands of new web sites created every day. (Spammers alone create 57,000 new sites each week.) If you block PredatorsRUs.com today, the bad guys will create Predators4Friends.com tomorrow. Make sure your child-safe iPod browser constantly updates its list of threats.
Child mobile Internet safety tip #6: Use ratings as a guide. Even the most dedicated parent can’t surf and judge every new web site, so make sure your child-safe iPod browser uses ratings such as the Family Online Safety Institute’s movie style ratings to choose which sites your kid can visit.
Child mobile Internet safety tip #7: Use a browser with real-time filtering. Because your child may be the first to discover an inappropriate site, make sure your child-safe iPod browser can detect inappropriate content on the fly.
Child mobile Internet safety tip #8: Encrypt your kid’s traffic. Bad guys use free WiFi hotspots to snoop on people’s Internet traffic. That guy over there isn’t working on his novel, he’s watching your child’s iPod use remotely. Get a child-safe iPod browser that encrypts web traffic over unsecured WiFi hotspots.
Child mobile Internet safety tip #9: Wireless safety extends to 3G and 4G too. Apple has restricted some iPod, iPhone and iPad functions to WiFi only, while others work on your carrier’s 3G or 4G signal. Make sure your iPod’s child-safe browser’s safety measures stay intact when you switch from cellular to WiFi, or vice versa.
Child mobile Internet safety tip #10: Allow age appropriate web use. Keep in mind that as your kid ages, you’ll want a child-safe iPod browser that has graduated levels of web access for older kids.
Mobile Internet safety solutions start first and foremost with web filtering. Block the sites that are going to cause problems. But by far, the best way to protect your kids is to sit down and discuss mobile Internet safety. Here are a few sites to get you started.
Protecting Kids on Mobile Devices – Online Safety Online safety is vastly underestimated by parents and children alike. Here is a compilation of popular resources available online for the discerning parent.
Articles – FBI Publications – A Parent’s Guide To Internet Safety
Advocates – Family Online Safety Institute – FOSI.org – WiredSafety.org – The World’s Largest Internet Safety, Help And Education Resource – iSAFE.org – The Leader In Internet Safety Education – NetSmartz.org – iKeepSafe.org – The Internet Safety Coalition
Now you have the knowledge and the tools to help protect your children from mobile Internet dangers. Let’s get started.
Suren Ramasubbu is a co-founder of Mobicip.com, a leading online child safety service for the iPhone, iPod touch, iPad, PCs, laptops and netbooks. Mobicip’s mission is to provide a safe, secure and educational Internet experience for school-age children. Mobicip’s dynamic content filtering technology helps parents protect their children in the new era of Internet hazards stemming from anytime anywhere access on personal devices.
0 notes
Link
Hacking for Beginners: Learn Practical Hacking Skills! All About Computer Hacking, Ethical Hacking, Black Hat, Penetration Testing, And Much More! (Hacking, ... Hacking, Tor Browser, Penetration Testing)
Hacking is a word that one often finds in the tabloids, newspapers, the Internet and countless other places. There is a lot of news about hackers doing this or that on a daily basis. The severity of these activities can range from accessing a simple household computer system to stealing confidential data from secure government facilities.
Hacking for Beginners book will serve as a guiding tool for you to understand the basics of the subject and slowly build up a base of the knowledge that you need to gain. You will be made aware of several aspects of hacking, and you will find the knowledge in here fascinating. Therefore, put on your curious glasses and dive into the world of hacking with us now.
From The Hacking for Beginners, We will discuss everything from the basics of ethical hacking to all you need to know about WiFi password cracking. It should be kept in mind that to understand the concept of ethical hacking, you should be able to know all about black hat hacking and how it is done.
Preview Of What You'll Learn from Hacking for Beginners Book
What is Hacking
Types of Hacking
White Hat Hacking or Ethical Hacking
Password Cracking
Understanding Computer Viruses
Hacking Wireless (Wi-Fi) Networks
Hacking Web Servers
Penetration Testing
T Cyber crime
0 notes