#wireless ATM solutions
Explore tagged Tumblr posts
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text
How Portable ATM Machines Provide Flexible Cash Access Anywhere
In today’s fast-paced and mobile world, convenience is king. Businesses, event organizers, and service providers are constantly seeking ways to improve customer experiences and streamline access to essential services. Among the most effective and underappreciated tools for enhancing convenience is the portable ATM machine. Designed to be moved and set up virtually anywhere, portable ATMs provide flexible, secure, and immediate cash access to people on the go. From outdoor festivals to remote job sites, these machines are transforming the way cash is distributed and accessed in temporary and mobile environments.

Meeting the Demand for On-the-Go Cash Access
While digital payments have become increasingly common, cash still plays a crucial role in many transactions—especially at events, outdoor markets, fairs, and rural or underserved locations where mobile payment systems may be unreliable or unavailable. Portable ATMs bridge this gap by offering a reliable solution for instant cash withdrawals, making them a vital resource for both consumers and businesses.
Unlike traditional ATMs installed permanently in retail locations or banks, portable ATM machines are built with mobility in mind. Housed in weather-resistant, tamper-proof enclosures and equipped with wireless connectivity, they can be placed almost anywhere, even in areas without existing financial infrastructure. This flexibility makes them ideal for seasonal events, traveling shows, food truck parks, and temporary venues.
Portable ATMs can be set up for single-day events or remain on-site for weeks or months, depending on the need. Their adaptable design means they can operate independently of local infrastructure, using generators or battery power where electricity is unavailable. This level of independence ensures that wherever people gather, they can have immediate access to cash when they need it.
Benefits for Event Organizers and Businesses
For event organizers and businesses, offering on-site cash access through portable ATMs is not just a convenience—it’s a revenue driver. Attendees are more likely to make purchases when they have cash readily available, particularly when vendors or services do not accept cards. Having an ATM on-site reduces the likelihood of missed sales and encourages increased spending, directly benefiting vendors and operators.

Additionally, portable ATM providers typically manage the delivery, setup, monitoring, and maintenance of the machines, allowing organizers to focus on other aspects of event planning. Many services offer revenue-sharing programs, enabling hosts to earn a portion of the transaction fees. This arrangement provides a passive income stream while improving the overall customer experience.
The presence of a portable ATM also helps create a more professional and guest-friendly atmosphere. Attendees won’t need to leave the premises to find cash, which means they stay longer and remain engaged with the event. For multi-day or large-scale events, having multiple strategically placed ATMs can improve traffic flow and prevent long lines, contributing to smoother operations.
Enhancing Accessibility in Remote and Temporary Locations
One of the most powerful advantages of portable ATM machines is their ability to bring financial access to places where permanent ATMs are not feasible. Construction sites, disaster relief areas, pop-up markets, rural festivals, and traveling carnivals are all examples of environments where traditional banking infrastructure may be absent or impractical.
In these scenarios, portable ATMs provide critical access to cash for workers, attendees, or residents. For example, construction workers at remote job sites may need cash for daily expenses but lack access to nearby banks. Similarly, during emergencies or natural disasters, portable ATMs can be deployed quickly to provide communities with necessary financial access when traditional facilities are down or inaccessible.
Furthermore, these machines often come with the latest security technology, including EMV compliance, encryption, surveillance options, and remote monitoring, ensuring safe and reliable usage even in temporary or high-traffic settings. This allows organizers and business owners to offer cash access without compromising on safety or service quality.
Choosing the Right Portable ATM Provider
When considering portable ATM services, it is important to choose a provider with a proven track record of reliability and customer support. Look for a company that offers full-service solutions, including transportation, installation, real-time monitoring, and on-call technical assistance. It is also important to understand their fee structure, cash replenishment policy, and any potential revenue-sharing opportunities.
The best providers will work with you to assess your specific needs and recommend the appropriate number and placement of machines. Whether you need one ATM for a local fundraiser or multiple units for a major music festival, the right partner will ensure a smooth setup and uninterrupted service.

Conclusion
Portable ATM machines have emerged as a vital solution for delivering flexible and accessible cash services wherever they’re needed. Their mobility, ease of setup, and ability to function in a wide variety of settings make them ideal for events, remote locations, and businesses seeking to enhance customer convenience. As the demand for flexible financial access continues to grow, portable ATMs offer a dependable way to meet that need while boosting customer satisfaction and generating additional revenue. Whether you are organizing a festival, managing a job site, or hosting a pop-up event, portable ATM machines are a smart and strategic choice for reliable cash access anywhere.
0 notes
Text
Biometric Access in India: How It’s Transforming Security
As India embraces digital transformation, security measures are evolving rapidly. Traditional authentication methods such as passwords, ID cards, and PIN codes are increasingly being replaced by advanced biometric access solutions. From corporate offices and government institutions to residential complexes and airports, biometric authentication is revolutionizing how access control is managed across the country.

The Rise of Biometric Access in India
With the rapid adoption of digital identity solutions like Aadhaar, India has set a global example in implementing large-scale biometric authentication. Organizations across various sectors are now integrating biometric access in India to enhance security, improve operational efficiency, and eliminate fraud.
Biometric systems use unique physiological characteristics such as fingerprints, facial recognition, iris scans, and voice recognition to authenticate individuals. Unlike traditional access control methods, biometric access is nearly impossible to forge, making it a highly secure and reliable solution.
How Biometric Access Enhances Security
Eliminates Unauthorized Access – Biometric authentication ensures that only authorized individuals can access restricted areas. Unlike access cards or PINs, biometric credentials cannot be lost, stolen, or duplicated.
Prevents Identity Fraud – Since biometric data is unique to each individual, the chances of impersonation and fraudulent access are significantly reduced.
Seamless Integration with Access Control Systems – Modern biometric access in India integrates seamlessly with access control systems, surveillance cameras, and cloud-based security platforms, offering real-time monitoring and remote access management.
Contactless Security Solutions – In the post-pandemic era, contactless biometric solutions such as facial recognition and iris scanning are gaining popularity, reducing physical touchpoints and enhancing hygiene.
Key Applications of Biometric Access in India
1. Corporate & Commercial Establishments
Businesses are leveraging biometric authentication to secure their premises, restrict unauthorized entry, and ensure accurate time and attendance tracking for employees.
2. Government & Public Sector
From Aadhaar-based biometric authentication to secure access at sensitive government facilities, India’s public sector has embraced biometric security solutions to enhance national security.
3. Banking & Financial Institutions
Banks and financial institutions are implementing biometric authentication for ATM access, mobile banking security, and identity verification to prevent fraud.
4. Residential & Smart Homes
Gated communities and smart homes are adopting biometric access to ensure secure entry for residents, eliminating the need for physical keys and access cards.
5. Airports & Transportation Hubs
With initiatives like DigiYatra, India’s airports are integrating facial recognition technology to streamline passenger verification and boarding processes, reducing congestion and improving security.
Advantages of Biometric Access Control Systems
High Security & Accuracy: Eliminates risks associated with stolen credentials.
Convenience: No need to carry physical access cards or remember passwords.
Time & Attendance Automation: Ensures accurate employee tracking, reducing payroll fraud.
Scalability: Easily integrates with existing security infrastructure.
Compliance & Audit Readiness: Provides digital logs for security audits and compliance reporting.
Spintly: Leading the Biometric Access Revolution in India
One of the companies at the forefront of biometric access in India is Spintly. Offering cutting-edge, wireless, and cloud-based access control solutions, Spintly is transforming how businesses and organizations manage security.
Unlike traditional access control systems that rely on complex wiring and heavy hardware, Spintly provides a mobile-first biometric access system that enhances security while simplifying user authentication. By leveraging smartphone-based credentials, Bluetooth, and biometric authentication, Spintly offers a seamless, hassle-free security solution that aligns with the future of smart access management.
The Future of Biometric Access in India
As technology continues to evolve, biometric access in India will become even more advanced, integrating with AI-driven analytics, cloud computing, and IoT-based security systems. Businesses looking to adopt the latest security measures should invest in future-proof solutions that offer seamless scalability and adaptability.
Conclusion
Biometric access is redefining security in India, offering a more reliable, secure, and efficient way to authenticate individuals. Whether in corporate offices, financial institutions, or residential complexes, the adoption of biometric authentication is set to grow exponentially.
For businesses looking to embrace the next generation of security, solutions like Spintly provide wireless biometric access that eliminates the complexities of traditional access control. With its innovative approach to access management, Spintly is helping businesses across India enhance security while improving user experience.
Investing in biometric access today means staying ahead in the security landscape of tomorrow.
#biometric attendance#biometric authentication#biometrics#access control system#access control solutions#mobile access#visitor management system#accesscontrol#spintly#smartacess#smartbuilding
0 notes
Text
Metallic Vandal Proof Keyboards: The Ultimate Solution for Rugged Environments
In a world driven by technology, keyboards are the unsung heroes of human-machine interaction. While traditional keyboards excel in everyday applications, certain environments demand more than just functionality—they require durability, resilience, and security. Enter metallic vandal proof keyboards, the epitome of robust design tailored to withstand extreme conditions and deliberate misuse.
Why Choose Metallic Vandal Proof Keyboards?
Metallic vandal-proof keyboards are not just a choice but a necessity for high-risk environments. They are crafted from high-grade stainless steel or aluminum alloys, ensuring exceptional resistance to physical damage, corrosion, and harsh weather conditions. These keyboards are engineered to thrive where standard keyboards fail, making them indispensable in industries such as public transportation, defense, healthcare, and manufacturing.
Their rugged construction enables them to resist impact, making them ideal for public kiosks, ATMs, and access control systems. The keys are usually designed to withstand heavy use without compromising performance, ensuring a long operational lifespan. Additionally, many of these keyboards are integrated with backlighting options, enhancing usability in low-light conditions—a feature particularly useful in outdoor or poorly lit areas.
Features That Set Them Apart
Unmatched Durability Metallic keyboards are synonymous with resilience. The use of metallic casings and reinforced key mechanisms ensures that they remain intact even under heavy abuse. This durability also makes them resistant to liquid spills, dust, and other contaminants, which is critical for outdoor or industrial settings.
Enhanced Security Security is paramount in applications like payment terminals and public kiosks. Metallic vandal-proof keyboards are designed to deter tampering, with keys firmly affixed to prevent unauthorized removal. This makes them an excellent choice for environments requiring high security.
Customizable Designs Modern metallic keyboards are highly customizable. They can be tailored with specific layouts, branding, or additional features like integrated touchpads or function keys. This level of customization makes them suitable for diverse applications, from military operations to retail setups.
Ease of Maintenance Unlike traditional keyboards, metallic vandal-proof models require minimal maintenance. Their sturdy build reduces the risk of frequent repairs, while their smooth metallic surfaces are easy to clean, ensuring hygiene in settings like hospitals and food processing units.
Applications Across Diverse Industries
Public Infrastructure: Public installations like ticket vending machines and self-service kiosks are prone to heavy usage and vandalism. Metallic keyboards ensure reliable operation while withstanding constant wear and tear.
Healthcare: In sterile environments, cleanliness is critical. The easy-to-clean surfaces of metallic keyboards, coupled with their resistance to liquids, make them ideal for healthcare applications.
Industrial Settings: Factories and manufacturing units often expose equipment to harsh conditions like oil, dust, and vibrations. Metallic vandal proof keyboards provide the ruggedness necessary to operate efficiently in such environments.
Military and Defense: For operations in extreme weather or combat zones, these keyboards are invaluable. Their resistance to extreme temperatures, impact, and tampering ensures reliability in mission-critical applications.
The Future of Rugged Keyboards
The demand for metallic vandal-proof keyboards is growing as more industries recognize their unparalleled benefits. With advancements in technology, manufacturers are incorporating features like capacitive touch sensors, programmable keys, and wireless connectivity, broadening their scope of applications.
One emerging trend is the integration of membrane keypads with bezels, which combine the durability of metallic keyboards with enhanced functionality. These designs are gaining popularity in sectors like aviation and marine industries, where precision and robustness are paramount.
Key Considerations When Choosing a Metallic Keyboard
When selecting a metallic vandal-proof keyboard, several factors come into play:
Material Quality: Stainless steel offers the best combination of strength and corrosion resistance.
Weather Resistance: Look for keyboards with IP ratings for protection against water and dust.
Customization Options: Opt for manufacturers that offer tailored layouts and additional features.
Certification: Ensure compliance with industry standards for durability and safety.
Why Metallic Vandal Proof Keyboards Are a Smart Investment
While these keyboards may have a higher upfront cost compared to conventional models, their longevity and reduced maintenance costs make them a cost-effective solution in the long run. Their reliability in critical applications ensures uninterrupted operations, adding value to businesses that depend on seamless performance.
Conclusion
Metallic vandal-proof keyboards have carved a niche in the market as the ultimate solution for demanding environments. Their combination of durability, security, and adaptability makes them a worthwhile investment for industries seeking robust human-machine interfaces.
At Cutek Circuits, we specialize in crafting high-quality metallic keyboards designed to meet your unique needs. With years of expertise in delivering innovative solutions, we ensure that every product embodies excellence and durability. Contact us today to explore how our metallic vandal-proof keyboards can redefine your operations.
0 notes
Text
Why Learn Embedded Systems and IoT Fundamentals?

In today’s tech landscape, understanding Embedded Systems and IoT Fundamentals is more than just a skill set; it’s a strategic advantage that opens doors to innovation and career growth. Whether it’s optimizing the performance of everyday devices or unlocking the potential of interconnected technologies, the knowledge in these areas is a gateway to a realm of possibilities. So, why should we invest our time in mastering Embedded Systems and IoT Fundamentals? Let’s explore the impact these competencies can have on our professional journey and the ever-evolving tech industry.
Importance of Embedded Systems

Why are embedded systems crucial in today’s technology-driven world? Embedded systems play a vital role in our daily lives, often unnoticed but powering essential devices we rely on. These systems have defined functions within larger devices like digital watches, washing machines, and security systems. Their low power consumption, small size, and cost-effectiveness make them indispensable in various applications.
Modern embedded systems, based on microcontrollers, contain processor cores, memory, and programmable input/output peripherals optimized for specific tasks. They enable remote control of devices, monitoring pollution levels, real-time data for parents, controlling street lights, and simplifying daily life through technology.
Embedded systems have revolutionized science and are integral to the Internet of Things (IoT), facilitating unique identifiers for objects, animals, and people, as well as seamless data transfer over networks. By understanding embedded systems, individuals can contribute to innovative solutions that bridge the physical and digital worlds, advancing society through smart, interconnected systems.
Key Benefits of Learning IoT Fundamentals

Understanding the key benefits of learning IoT fundamentals provides insights into the diverse applications and potential impacts of interconnected devices in various sectors.
By delving into IoT basics and fundamentals, individuals can grasp the essence of networked devices sharing data, combining wireless networking, physical components, data analytics, and cloud computing. This knowledge opens doors to a wide array of applications, from enhancing automobile safety and entertainment to revolutionizing industrial processes and optimizing retail experiences.
Learning about IoT also equips individuals with the skills to contribute to smart city initiatives, data-driven farming, and advancements in healthcare through the Internet of Medical Things (IoMT). Moreover, gaining expertise in IoT offers opportunities to improve internal business processes, increase responsiveness, and make smarter environmental decisions.
Embracing IoT fundamentals not only enhances job prospects but also empowers individuals to drive innovation and progress in a rapidly evolving technological landscape.
Practical Applications of Embedded Systems

Exploring practical applications, embedded systems play a crucial role in various industries and environments, showcasing their significance in modern-day technology.
These systems are utilized in a wide range of devices, from real-time embedded systems like aircraft control systems to stand-alone devices such as microwave ovens and washing machines.
Networked embedded systems like ATMs and home security systems, along with mobile embedded systems found in digital cameras and smartwatches, demonstrate the diverse applications of embedded systems in our daily lives.
With characteristics like small form factor, power-efficient components, and single functionality, embedded systems are integral in industries such as healthcare, automotive, and consumer electronics.
Their presence in sectors like security, transportation, and energy highlights their importance in ensuring the smooth operation of various technologies.
As embedded systems continue to evolve and become more powerful, their impact on society and technological advancements is undeniable.
Advantages of IoT Integration

Utilizing IoT integration offers numerous benefits, enhancing operational efficiency and enabling proactive decision-making based on real-time data. By connecting sensors, objects, applications, and databases, IoT integration streamlines processes and facilitates end-to-end automation. This connectivity allows for real-time monitoring and control, leading to quicker responses to changing conditions and improved overall efficiency. Integrating IoT devices with existing systems creates a cohesive network that can adapt to dynamic environments seamlessly.
Furthermore, IoT integration enables organizations to lower costs through proactive maintenance strategies. By identifying issues in real-time and implementing predictive maintenance measures, companies can reduce risks, prevent downtime, and optimize resource allocation.
Additionally, IoT integration can enhance customer experiences by improving service quality and reliability, ultimately increasing satisfaction and loyalty. Overall, the advantages of IoT integration extend beyond operational enhancements to encompass cost-efficiency, risk mitigation, and customer-centric improvements, making it a valuable asset in today’s technological landscape.
Career Opportunities in IoT and Embedded Systems

Connecting IoT integration advantages to real-world applications, the field of IoT and embedded systems offers diverse and promising career opportunities for individuals with a range of specialized skills and expertise.
Within IoT, roles such as Data Analytics, Network Professionals, Security Experts, Hardware Specialists, and User Interface Designers play crucial parts in shaping the technological landscape. These professionals are responsible for tasks ranging from data analysis to hardware integration, each requiring specific skills like statistical analysis, security protocols, and UI creativity.
Salary trends in IoT vary based on roles and experience levels, with Data Analytics and Security experts often commanding higher salaries. Specialized career paths like Sensors and Actuator Professionals, Embedded Programs Engineers, and Artificial Intelligence specialists also offer unique opportunities for individuals interested in pursuing a career in IoT and embedded systems.
Frequently Asked Questions
Why Are You Interested in Embedded Systems and Iot?
We are interested in embedded systems and IoT because they offer a deeper understanding of device design, hardware-software interactions, and IoT growth. This knowledge equips us to create innovative solutions that bridge physical and digital realms.
What Is the Use of Embedded Systems in Iot?
Embedded systems in IoT enable specific functionality and connectivity, crucial for devices like smart appliances. They consist of hardware, software, and firmware, enhancing automation and real-time data transfer. Collaboration between hardware and software providers drives innovation.
Why Do You Choose an Embedded System?
We choose embedded systems for their ability to enable specific functionalities and data processing in everyday devices. They play a crucial role in IoT connectivity and operation, equipping us with the skills to create innovative solutions.
Why Are Embedded Systems Important in Real Life?
Embedded systems are crucial in real life for enabling specific tasks, enhancing device functionality, and facilitating communication and data processing. They play a vital role in various industries, contributing to automation and data-driven decision-making.
Conclusion
In conclusion, learning embedded systems and IoT fundamentals is crucial for anyone looking to stay relevant in the fast-paced world of technology.
These skills open up a world of opportunities, from developing efficient devices to contributing to cutting-edge advancements in various industries.
By mastering these fundamentals, we can’t only enhance our career prospects but also play a key role in shaping the future of technology.
Visit Zekatix for more information.
#EdTech Company#courses#embeded#nanotechnology#online courses#academics#embedded systems#IOT#Robotics#artificial intelligence#Zekatix
1 note
·
View note
Text
Travelex, a UK-based foreign exchange business partnered with Ripple, has teamed up with US-based online travel agency Kayak to streamline trip planning for consumers. Through this collaboration, Travelex's clients can now seamlessly search for flights, hotels, and rental vehicles within the updated Travelex Money app, consolidating vacation planning and financial management in one place.
The revamped app boasts a fresh design, enhanced user experience, and increased control, according to Travelex. Additionally, withdrawal limits at ATMs have been set at £500 for UK-issued cards and AUD$3000 for Australian-issued cards, with minimum load amounts of £50 and $100 AUD respectively. Travelex has also eliminated card collection fees.
With Mastercard affiliation, Travelex customers gain access to Boingo's wireless hotspots, enhancing connectivity while traveling. This collaboration marks a significant milestone in Travelex's digital transformation journey, aligning with its broader strategy to offer crypto-enabled payments, digital remittance solutions, and multi-currency prepaid contactless cards.
Travelex is committed to expanding its suite of digital offerings, including touch-and-go channels, ATM click-and-collect, and touchless channels, catering to evolving consumer needs.
0 notes
Text
Atmosic And AONDevices Announce Strategic Partnership To Leverage Both The Benefits of AI And Energy Harvesting To Lower Power Consumption In AIoT Smart Home Devices

With the strategic alliance that it has formed with AONDevices, Atmosic Technologies will leverage low-power AI processors and ultra-low-power wireless technologies to create wearable and AIoT (Artificial Intelligence of Things) applications that are cutting edge. The ATM Series from Atmosic, renowned for its exceptionally low-power wireless System on Chip (SoC), will combine with the AON series of AI processors from AONDevices to deliver precise voice command recognition, sound awareness, and contextual awareness while consuming the least amount of energy possible. By utilizing energy-efficient solutions to lessen reliance on batteries and further minimizing power use with AONDevices' AI technology, this partnership is in line with Atmosic's commitment to IoT sustainability. Headsets, wearables, game controllers, toys, cars, smart home appliances, smart buildings, and industrial IoT applications are among the many applications that the cooperation aims to address.
The ATM Series wireless SoC from Atmosic combines 802.15.4 protocols, energy harvesting, power management, and RF radios that support Bluetooth Low Energy. The AI processors from AONDevices feature multi-sensor fusion, sound awareness, and voice command recognition with high accuracy under a variety of scenarios. With adaptive speech activity detection, the technology supports speaker independence in always-on and multi-word detection scenarios while assisting with voice control and context detection.
By lowering RF radio power usage and using harvested energy to power sensors, tags, remotes, and other devices, Atmosic has been a pioneer in the IoT sustainability space. By using less batteries and lessening their influence on the environment, this strategy enables manufacturers to produce goods that are friendly to the environment. Through the relationship with AONDevices, power consumption will be further reduced by addressing energy waste during sensor false detections.
Read More - bit.ly/48qeBvz
0 notes
Text
The IoT Revolution: How Connected Devices are Revolutionizing Industries
The Internet of Things (IoT) has permeated every aspect of modern life, transforming industries across the board. IoT-connected devices are no longer just technological novelties; they have become the driving force behind revolutionary changes in crucial sectors such as healthcare, fintech, automotive, enterprise, and household functions. In this article, we will explore the impact of IoT-connected devices on these industries and how they are streamlining existing processes while paving the way for new ones.
Understanding IoT-Connected Devices
IoT-connected devices encompass a wide array of electronic gadgets, machines, household appliances, and more, all capable of wireless communication and data transmission. These devices have evolved from being isolated and disconnected entities to interconnected devices that can communicate and interact with each other over the internet. The ability to transmit data opens up a world of possibilities for optimization and insights.
Transforming Crucial Industries
Healthcare: The healthcare industry is experiencing a significant transformation due to IoT-connected devices. Home monitoring systems enable doctors to remotely track an individual's health, reducing infection risks and saving costs and time associated with frequent trips to the doctor. Remote patient monitoring technologies provide real-time health data, such as blood pressure and heart rate, enabling doctors to manage acute and chronic conditions more efficiently. Wearable IoT technologies, like the Apple Watch Series 8, offer enhanced health tracking capabilities, including fall detection and ECG. These sophisticated devices are becoming life-saving tools.
Fintech: In the fintech sector, IoT-connected devices have streamlined operations in areas like ATMs, ticketing kiosks, and night depositories. Beyond simple transactions, these devices offer personalized experiences, tracking customer spending patterns and offering user-focused differentiated offerings. Biometrics and IoT sensors also enhance security and help prevent ATM thefts.
Automotive: The automotive industry is experiencing a revolutionary shift with IoT-connected devices. Connected cars can register real-time traffic data, run system diagnostics, and even offer predictive maintenance. IoT sensors embedded in vehicles can predict the useful life of various parts, improving operational costs and road safety.
Enterprise: In the enterprise sector, IoT-connected devices help optimize operations and reduce costs. Industrial IoT sensors monitor assembly lines and manufacturing processes, preventing unexpected shutdowns and increasing employee productivity. IoT devices also aid in providing better ergonomic designs for workstations, creating optimized work environments.
Household Functions: IoT-connected devices are transforming household chores and daily tasks. Advanced washing machines can track and control washing parameters, and autonomous robotic home cleaners use specialized mapping algorithms for efficient cleaning. Smart home devices, like Amazon Echo and Google Assistant, allow remote management of appliances, lights, and home security systems.
Challenges and Solutions
While the impact of IoT-connected devices is immense, several challenges hinder their widespread adoption:
Cyber Security: Ensuring robust security protocols and educating users on best practices can mitigate cybersecurity risks associated with IoT devices.
Data Governance: Clear data privacy policies should define the scope and use of collected data, preventing data misuse.
Scaling and Deployment: Companies with formal IoT strategies fare better in overcoming the challenges of scaling and deployment.
Time-to-Market: IoT companies often face delays in going live, but innovative copamnies like Mindfire Solutions help reduce the Time-to-Market significantly.
Chip Shortage: The ongoing global chip shortage may have slowed growth in IoT, but it is expected to be resolved in the near future.
Conclusion
IoT-connected devices have revolutionized industries, optimizing processes, reducing costs, and empowering users with valuable insights. Despite challenges, companies are finding innovative solutions to enhance device deployment and scalability. The transformative potential of IoT is limitless, and as technology continues to evolve, we can expect even more exciting advancements in the IoT landscape, reshaping the world as we know it. Get ready to shape the future with Mindfire Solutions, your trusted partner for IoT and Connected Device Development. Our team of seasoned developers brings a wealth of knowledge and experience to your IoT initiatives, ensuring the creation of smart, secure, and scalable connected solutions. We provide end-to-end IoT development services, from strategy and consultation to development, deployment, and maintenance. Our solutions are designed to optimize efficiency, unlock new revenue streams, and create extraordinary user experiences. By choosing Mindfire Solutions, you're not just adopting cutting-edge IoT technology – you're embracing a partnership that drives innovation and propels your business into the future.
0 notes
Text
5 Best Toys for Kids of Ages 7-9

The main focus of this blog will be on toys for kids of ages 7-9 as suggested by the title. It is due to the fact that these are growing years. And rapid growth comes with development of ideas and opinions affecting the interests. Parents often get tired of keeping up with the mental, emotional and physical challenges that come with the growth of kids, during this time period. We don't have the solutions to deal with all the transitions that children amidst these ages demand, but we do know how to keep them interested and make them feel important during this age period. Below are a few suggestions that can help the transition from baby toys to a little grown up toys a bit smooth and fun.
WIRELESS BLUETOOTH KARAOKE MACHINE:
Admit it karaoke machines are fun no matter what the age. They make you feel happy and have the ability to turn a good day around, even if you have a bad voice. A karaoke machine will be a fun addition to the toy collection of kids. It is a toy for kids that will keep the inner child of them alive along with giving the feeling of being a bit grown up. It will be a cheerful way of exploring your child’s talents.
CODING STARTER KID:
It is an educational toy for kids. This will help the kids and their parents in identifying if their children are interested in coding. Even if kids show no interest in particular coding, this will be a fun filled activity to do together. It is a very enjoyable kit that will help your kids understand coding in a way that they can understand and tell others.
OUTDOOR SCOOTER:
This one is my personal favorite toy for kids. It is a light hearted pleasure that both parents and kids enjoy.. It is an outdoor activity that will take your kids away from the screen for some time. It is also a physical activity, as we all are aware physical exercise is really important for people of all ages and especially kids, the introduction of different types of screen has stopped the children from going to parks and enjoying fresh air while doing something physical. This toy for kids will be a way to encourage more outdoor time for them.
ELECTRONIC PIGGY BANK ATM:
This is a wonderful toy for kids in growing ages, as it will introduce a new concept to the kids i.e. saving. It will help the kids in developing a sense of ownership, earning and responsibility. If parents ask the kids to help in chores they can put money in the piggy bank that later can be taken out by them when they want to buy something that they need. This will help the kids in understanding the concept of saving, budgeting and spending on things that they want. They might have to choose between two objects according to their budget.
BOOK:
A good book is a wonderful thing that you can give your kids at an early age. We know that this isn't a toy for kids, but we would have felt really guilty if we did not add a book to this list. A book is a good way of instilling reading habits in your kid. It will be a good way to get the kids away from screens and just sit them down, read to them. This reading time will become a beautiful way of spending quality time together as a family.
1 note
·
View note
Text
The Ultimate Guide to 3V Lithium Batteries: Reliable Power for Every Device
In today’s fast-paced, tech-driven world, having a reliable power source is essential. Among the wide range of batteries available, 3-volt (3V) lithium batteries have earned their place as a dependable and versatile energy solution. Whether you're powering a small electronic device or a specialized tool, these batteries deliver exceptional performance and longevity. This article dives into what makes 3V lithium batteries special, their applications, and why ATM Trader is the ideal place to purchase them.
What are 3V Lithium Batteries? 3V lithium batteries are compact, lightweight, and designed to provide consistent energy output over an extended period. They are typically coin-shaped and are known for their ability to retain charge even during long-term storage.
Key Features:
Voltage: Delivers 3 volts for steady energy output.
Capacity: Ranges from 200mAh to 1200mAh, depending on the model.
Shelf Life: Often up to 10 years, making them perfect for devices that need long-term power.
Size: Commonly available as CR2032, CR2025, and CR2450 models.
Applications of 3V Lithium Batteries These batteries are highly versatile and are used in a variety of devices:
Remote Controls From TV remotes to car key fobs, 3V lithium batteries power small gadgets efficiently.
Medical Devices Reliable power is critical in medical devices like glucose monitors and heart rate monitors.
Wearable Technology Smartwatches, fitness trackers, and other wearables rely on 3V lithium batteries for compact, long-lasting power.
Security Systems Sensors, alarms, and wireless cameras utilize these batteries for uninterrupted performance.
Toys and Games Many electronic toys and gaming peripherals depend on 3V lithium batteries.
Benefits of 3V Lithium Batteries
Long-lasting Power: Their high energy density ensures longer runtime compared to alkaline counterparts.
Wide Temperature Range: These batteries perform well in extreme conditions, from -40°C to 60°C.
Lightweight Design: Ideal for portable and wearable devices.
Environmentally Friendly: Lithium batteries are often designed with fewer toxic materials than traditional batteries.
Choosing the Right 3V Lithium Battery When selecting a 3V lithium battery, consider the following:
Device Compatibility: Check your device’s specifications to ensure you choose the correct battery size.
Brand Quality: Reputable brands offer higher reliability and performance.
Storage Needs: Opt for batteries with a long shelf life if you plan to store them.
Why Buy 3V Lithium Batteries from ATM Trader? ATM Trader is a trusted provider of high-quality lithium batteries designed to meet diverse needs.
Benefits of Shopping at ATMTrader:
Wide Selection: Choose from various battery models to suit your device.
Competitive Pricing: Get premium quality without breaking the bank.
Secure Shopping: Enjoy a safe online purchasing experience.
Customer Support: Expert assistance to guide you in selecting the right battery.
Tips for Maximizing Battery Performance
Proper Storage: Store batteries in a cool, dry place to retain their charge.
Avoid Overuse: Replace batteries promptly to prevent device malfunction.
Dispose Responsibly: Recycle used batteries to minimize environmental impact. 3V lithium batteries are indispensable for modern electronics, offering long-lasting, reliable power. Whether you need them for a smartwatch, remote control, or medical device, choosing a high-quality product is crucial. ATM Trader stands out as a top destination for purchasing 3V lithium batteries, providing unbeatable value and service.
0 notes
Text
AusFestival Pine industrial LTE router apple, A Coconut-Flavored Pineapple
www.inhandnetworks.com
Australia’s Department of Agriculture announced remote diagnostics that it is in the final stages of developing a new breed of pineapple that is sweet and juicy, but has the added taste of coconut, making it suitable for the for piña colada cocktails.
The AusFestival pineapple will allow mixologists to create better piña colada drinks for everyone. While it won’t revolutionize mixology, it will definitely add something different. The agency’s research station in Queensland has been working on this breed of pineapple for more than a decade.
The pineapple has a coconut-flavor, which is unique. The piña colada was developed almost six decades ago in P industrial LTE router uerto Rico by Ramón ‘Monchito’ Marrero. It took him three months to come up with this drink.
Currently, piña coladas are made by shaking rum, cream of coconut, and pineapple juice mri remote monitoring together with ice before straining the mixture and serving it.
Initially, the researchers didn’t intend on creating a pineapple that tasted like coconut. They were simply trying to get a nicely-flavored pineapple, low in acid and aromatic. It will take at least two years before the first commercial AusFestival pineapples are planted.
[via Daily Mail]
Vending Computer, Industrial LTE Router, industrial IoT Gateway, industrial LTE router, Industrial VPN router, Dual SIM M2M router, Industrial IoT Router/Gateway, industrial IoT Gateway, industrial LTE router, Industrial VPN router, Dual SIM M2M router, Industrial LTE Router, Industrial LTE router, industrial 4G/3G router, router industrial, cost-effective industrial LTE router, Industrial LTE Router, Industrial LTE router, industrial IoT router, router industrial, cost-effective M2M router, M2M LTE router, Industrial 3G Router , Industrial 3g router, industrial wireless router, VPN router, DIN-Rail router, cellular router, Industrial 3G Router , Industrial 3g router, industrial wireless router, VPN router, DIN-Rail router, cellular router, Distribution Power Line Monitoring System, Overhead Line Monitoring, Distribution Power Line Monitoring, Fault detection & location, Grid Analytics System, Remote Machine Monitoring & Maintenance System, IoT Remote Monitoring, Prognostics and Health Management, Remote connectivity, Remote Maintenance, Smart Vending, smart vending, InHandGo, retrofit, touchscreen vending, cashless vending, cloud VMS, Transformer Monitoring, Transformer Monitoring, substation monitoring, grid LTE router, wireless communication, smart grid, Remote Automation, Remote Automation, Secure remote networks, web SCADA, Remote Diagnostics, Remote PLC programming, Intelligent Traffic Enforcement, Intelligent Traffic Enforcement, wireless networking, cellular router, Wireless ATM Solution, Wireless ATM, ATM Remote Diagnostic, prestashop 多语商城, opencart 外贸商城, 网页设计, 网站建设, 企业建站, 商城网站, 集团网站, 海外网站, 营销网站, 网站推广, 华人网站建设, 华人网站维护, 华人网络兼职, china webdesign, webdesign, seo, joomla web design, 香港網頁設計, 網站建設, 企業建站, 商城網站, 集團網站, 海外網站, 營銷網站, 網站推廣, web design, joomla webdesign, wordpress webdesign, opencart webdesign, magento webdesign, durpal webdesign, vtiger crm, adempiere erp, compiere erp, hosting, domains, vps, email marketing, joomla 网页设计, wordpress 建站, magento 大型外贸商城, durpal 门户网站, seo 网站推广, 网站自然排名, joomla 網站製作, wordpress 定制開發, opencart 維護修改, prestashop 模板修改, magento 培訓實施, durpal 定制修改, seo 營銷推廣, 外鏈收錄排位, joomla, wordpress, opencart, prestashop, magento, durpal, zencart, crm, erp, edm, marketing, joomla template, wordpress themes, magento themes, opencart themes, prestashop themes, 崀山, 崀山科技, 崀山科技全球服务中心, LangShan Technology Global Service Center, LangShan Technology, langshantech, LangShan, china webdesign, 網頁製作, 網頁設計, 企业建站, 企業建站, 在線商城, 營銷網站, 網站推廣, 網站營銷, 排名推廣, 產品推廣, 主機維護, 公司兼職, 網站SEO, joomla seo, wordpress seo, joomla 網站推廣, opencart 網站推廣, prestashop 網站推廣, wordpress 網站推廣, magento 網站推廣, joomla 網站排名, prestashop 網站排名, wordpress 網站排名, opencart 網站排名, prestashop 多语商城, opencart 外贸商城, 网页设计, 网站建设, 企业建站, 商城网站, 集团网站, 海外网站, 营销网站, 网站推广, 华人网站建设, 华人网站维护, 华人网络兼职, china webdesign, webdesign, seo, joomla web design, 香港網頁設計, 網站建設, 企業建站, 商城網站, 集團網站, 海外網站, 營銷網站, 網站推廣, web design, joomla webdesign, wordpress webdesign, opencart webdesign, magento webdesign, durpal webdesign, vtiger crm, adempiere erp, compiere erp, hosting, domains, vps, email marketing, joomla 网页设计, wordpress 建站, magento 大型外贸商城, durpal 门户网站, seo 网站推广, 网站自然排名, joomla 網站製作, wordpress 定制開發, opencart 維護修改, prestashop 模板修改, magento 培訓實施, durpal 定制修改, seo 營銷推廣, 外鏈收錄排位, joomla, wordpress, opencart, prestashop, magento, durpal, zencart, crm, erp, edm, marketing, joomla template, wordpress themes, magento themes, opencart themes, prestashop themes, 崀山, 崀山科技, 崀山科技全球服务中心, LangShan Technology Global Service Center, LangShan Technology, oowebdesign, LangShan, china webdesign, 網頁製作, 網頁設計, 企业建站, 企業建站, 在線商城, 營銷網站, 網站推廣, 網站營銷, 排名推廣, 產品推廣, 主機維護, 公司兼職, 網站SEO, joomla seo, wordpress seo, joomla 網站推廣, opencart 網站推廣, prestashop 網站推廣, wordpress 網站推廣, magento 網站推廣, joomla 網站排名, prestashop 網站排名, wordpress 網站排名, opencart 網站排名, inhandnetworks, InHand Networks Global Leader in Industrial IoT, Global Leader in Industrial IoT, android-computer, iot, industrial iot, industrial internet of things, m2m, industrial m2m, m2m communication, remote communication, wireless m2m, remote connectivity, remote access, m2m connectivity, iiot, industrial networking, industrial wireless, m2m iot, smart vending, touchscreen vending, cloud-vms, telemeter, vending telemetry, cashless vending, light industrial, commercial, distribution automation, distribution power line monitoring, fault location, fault detection, da monitoring, smart grid, transformer monitoring, intelligent substation, goose-messaging-, remotemachine monitoring, remote secure networks, remote secure networking, secure web based scada, remote diagnostics, remote maintenance, plc-programming, intelligent traffic enforcement, ct scanners remote monitoring, mri remote monitoring, healthcare, wireless atm, branch networking, retail, digital signage, wastewater treatment, remote monitoring, industrial automation, automation, industrial transport, inhand, inhand network, inhand networks, InHand Networks - Global Leader in Industrial IoT, Global Leader in Industrial IoT Industrial Cellular Modem, Cellular modem, data terminal unit, 3g modem, Industrial 3G Cellular Modem, 3g modem, industrial cellular modem3g modem, industrial cellular modem, industrial wireless modem, data terminal unit, Android Industrial Computer, Android Industrial Computer, Vending PC, Vending Telemetry, Vending Telemeter, Android Industrial Computer, Android Industrial Computer,
#industrial LTE router#industrial M2M router#overhead Line sensor#vending computer#vending-pc#Industrial Wireless M2M Router#Grid Analytics System#LTE M2M Router#wireless ATM solutions#grid fault detection
0 notes
Text
Essential Qualities Of Highly Successful End To End Encryption

Now, the entire world and business operations are running on ciphers and codes. From shopping online, entertainment, and ATMs to emails, cryptography occupies your every waking moment. It is a well-recognized fact that life is practically not possible without security. When it comes to cryptography, it is entirely about secret communication. The main goal of this science is to enable communications on an insecure network in a way that the potential adversary never knows what is conveyed. Most significantly, the worldwide propagation of various cyber attacks leads to one specific cryptography component. Hence, encryption is essential for making every effort to protecting your intellectual property and sensitive data. End To End Encryption increases the data safety no matter whether your business information is available in a private or public cloud on in transit.
Important of encryption
It is valuable for people who are trying hard to combat the advanced security threats. Another essential function of this security measure is to get protection against the IoT enabled breaches. End To End Encryption also can maintain regulatory compliance. It is significant to know that both IT security and encryption project is an essential process, which takes time. If you consider the encryption techniques and data states, you can start to learn about seven significant elements. It helps you to develop a winning approach for End To End Encryption.
· Focus on collaboration
It is essential to have collaborative efforts to create a perfect encryption strategy. You can consider it as a crucial initiative and ensure that it includes IT, operations, and management members. It is helpful to bring together major data stakeholders and put efforts to recognize external influences, laws which will factor into implementation and purchasing decisions. The next step is to identify high-risk areas like mobile, data backups, laptops, and wireless networks.
· Classification of data
You can leverage End To End Encryption as a major part of your IT security efforts. If you fail to perform this task, you will face some struggles with your data encryption. Both the tools and policies of data classification offer the classification of essential data that is targeted from minimally valuable data. The classification tools are used for improving the handling and treatment of sensitive data and also promote a security culture. It can prevent inadvertent disclosure.
· Manage the keys and certifications
If you do not protect the certificates and keys, it will lead to security attacks. Hence, organizations must understand which certification and the key are used in your network. Also, you can assign the right people to access these things. If you want to collect this information, you can have a precise understanding of your business inventory by managing certificates and keys.
· Identify the correct solution
If you want to achieve End To End Encryption, you should evaluate and use the right encryption solution. You need to consider many factors and options to the right one, which will work for your organization.
· Access Control
You can ensure that authorized people can only access the data. It helps you to protect your data against unauthorized access. A successful protection strategy defines sturdy access-control techniques with file permissions, two-factor authentication, and passwords. It is another essential stage in End To End Encryption.
· Consequences
You should develop a written policy before deployment and ensure that the management endorses it. If it does not meet the business policies, it never gets the data. Encryption responsibility is fixed and also carries these consequences for noncompliance.
· SSL Decryption
It not only protects data but also hides security threats. By using this technique, you can get the ability to ensure that malicious codes are not making their way into your network traffic. The attackers are now exploiting this kind of vulnerability. Hence, you can consider this SSL decryption technology while selecting a perfect encryption method for your business.
1 note
·
View note
Text
In-Depth Knowledge of GPON
Optical fiber networks operate on different passive optical network (PON) standards. A PON is a network system specific to fiber technology that delivers broadband network access to homes or businesses. One of many PON standards is GPON. This article will provide some knowledge about GPON

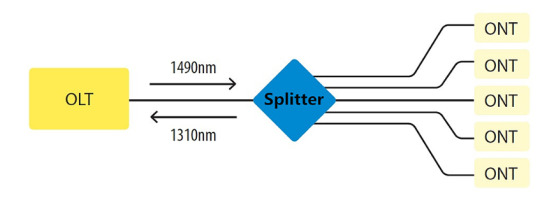
What is GPON?
Gigabit passive optical network (GPON ) is a point-to-multipoint access network. Its main feature is to use passive splitters in the fiber distribution network (ODN), enabling one single feeding fiber from the provider’s central office to serve multiple homes and businesses. In addition, GPON uses an IP-based protocol and asynchronous transfer mode (ATM) encoding to integrate voice and data traffic on the same network.

Components of GPON
There are three main components of GPON: optical line terminal (OLT), optical fiber splitter, and optical network terminal (ONT).
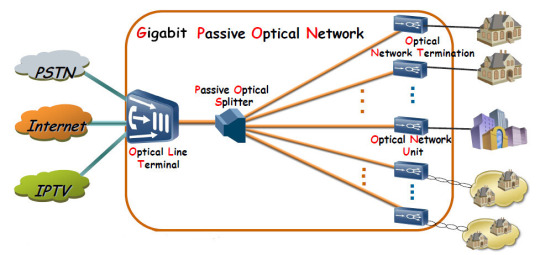
OLT
OLT is a device that serves as the service provider endpoint of a passive optical network. It is an active ethernet aggregation device that is located in a data center or the main equipment room. An OLT converts the optical signals to electrical signals and presents them to a core ethernet switch. The OLT replaces multiple layer 2 switches at distribution points. OLT distributing signal is connected with backbone cabling or horizontal cabling through optical splitters, which are connected to the optical network terminal at each work area outlet.
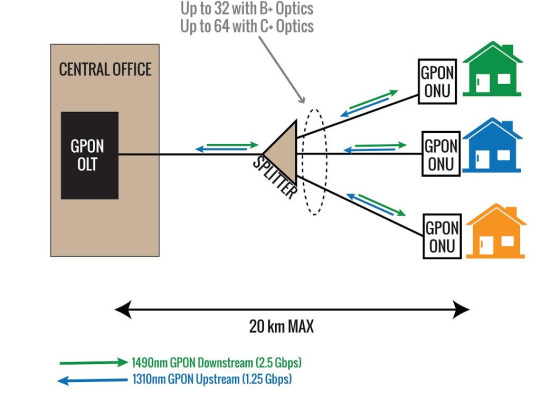
Optical Fiber Splitter
The optical fiber splitter is an integrated waveguide optical power distribution device that can split an incident light beam into two or more light beams and contain multiple input and output end. A GPON splitter often has a specified split ratio that could be 1:4, 1:8, 1:16, 1:32, and 1:64, depending upon the number of outputs required. The most common splitters deployed in a GPON system are uniform power splitters with a 1xN or 2xN splitting ratio, where N is the number of output ports.
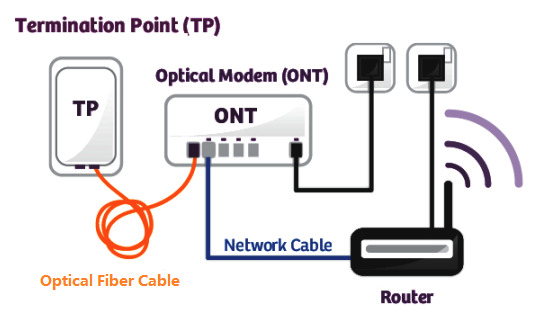
ONT
ONT also called the modem, connects to the termination point (TP) with an optical fiber cable, and connects to the router via a LAN / Ethernet cable. It converts the optical signals to electrical signals to deliver to the end device. ONT always has multiple Ethernet ports for connection to IP services such as CPUs, phones, wireless access points, and other video components.
Benefits of GPON
GPON has the benefits of high bandwidth, high security, low cost, easy installation, longer life, long-distance transmission, space-saving, energy-saving, scalable, and future-proof solutions.
Applications
GPON is used in data, video on demand, IPTV, VoIP, CATV, CCTV, FTTH, FTTB, FTTC, FTTD, FTTO, FTTM, FTTW, D-CCAP, etc.

Conclusion
GPON is a future-proof solution for providing broadband services. It provides high bandwidth, low cost, and long-distance transmission. Sun Telecom specializes in providing one-stop total fiber optic solutions for all fiber optic application industries worldwide. Contact us if any needs.
1 note
·
View note
Text
https://ymtsindia.com/embedded-system-design
Best Embedded System Design Services Provider “YoungMinds”
What is an Embedded System?
An embedded system is a combination of computer hardware and software designed for a specific function. Embedded systems may also function within a larger system. The systems can be programmable or have a fixed functionality.
For example, a fire alarm is a common example of an embedded system which can sense only smoke.

Examples of standalone embedded systems include:
Digital cameras.
Digital wristwatches.
MP3 players.
Appliances, such as refrigerators, washing machines, and microwave ovens.
Temperature measurement systems.
Calculators.
History of Embedded system
In 1960, embedded system was first used for developing Apollo Guidance System by Charles Stark Draper at MIT.
In 1965, Auto-netics, developed the D-17B, the computer used in the Minuteman missile guidance system.
In 1968, the first embedded system for a vehicle was released.
Texas Instruments developed the first microcontroller in 1971.
In 1987, the first embedded OS, VxWorks, was released by Wind River.
Microsoft’s Windows embedded CE in 1996.
By the late 1990s, the first embedded Linux system appeared.
The embedded market reach $140 billion in 2013.
Analysts are projecting an Embedded market larger than $40 billion by 2030.

Various Types of Embedded System: -
A Raspberry Pi an embedded system: Raspberry Pi single-board computer (SBC) was originally designed as a platform to teach computer science to students, but it has expanded into other applications, including use as an embedded platform.
ATM an embedded system: An Automated Teller Machine (ATM) - is an embedded system which utilizes a crowded computer to set up a network between a bank computer and an ATM itself. It also has a microcontroller to bear both input and output operations
Alexa an embedded system: The Amazon Echo is the epitome of an Internet of Things (IoT) device. It combines an embedded applications processor from Texas Instruments, MEMS microphones from Knowles, Wi-Fi and Bluetooth wireless connectivity, an AWS cloud backend, and support for diverse applications.
Smart TV an embedded software: Embedded software comes into play in “smart TVs.” Smart TVs still have firmware for the low-level signal processing tasks, and more firmware to operate the wired or wireless network interface and communications with the remote control (which also now has firmware)
Embedded System Design: -
Embedded system is a self-contained, microprocessor-based computer system typically implemented as a component of a larger electrical or mechanical system. At the core of the embedded system is an integrated circuit that performs computational tasks.
Majorly Embedded System Design helps all kinds of manufacturing industries to control a specific function within a device. They are usually designed to only perform this function repeatedly, but more developed embedded systems can control entire operating systems.
If anyone searching Embedded System Design Solutions to make your ideas into reality – my best suggestion is “Youngminds” - Realizing product and software development for a wide range of application areas on cutting-edge technologies like below mentioned…
“Young Minds” Embedded System Design Solutions: -
Firmware Development and Optimization of Embedded Designs for a wide range of processors.
Various Embedded Processor/FPGA/SoCs:
ARM
TI
Microchip
nVIDIA
Xilinx FPGA
Intel FPGA
3rd Party SoCs
Target Applications:
AI
Multimedia
IoT
Security
Automotive
Image Processing
Medical Services
Target Technologies:
Wireless Technologies like WiFi, Bluetooth
Storage Interfaces
Sensor Interfaces
Display Interfaces
Wired Technologies like Ethernet, PCIe, SATA
Still need more information about “Young Minds” – Visit https://ymtsindia.com/
Embedded System Design Solutions: - https://ymtsindia.com/embedded-system-design
0 notes
Link
If you are looking for a local ATM machine, Ocean ATM is here for you. We offer a couple of solutions including purchasing an ATM & Free Atm Placement. We provide the leading Wireless ATM machines for sale at the best prices. Please contact us to get a free ATM for your business.
10 notes
·
View notes
Text
Automated Teller Machine Market Share, Trends, Segmentation and Registering a Strong Growth by End of 2027
The automated teller machine market is speculated to attain a considerable valuation by 2027 owing to mounting demand for workstation and mobile ATMs across key regions in the wake of the COVID-19 pandemic.
With evolving technologies Automated Teller Machines (ATMs) are becoming more sophisticated and secure. As a result, they are increasingly helping with the digital transformation of global economies, who are passing favorable policies that promote the adoption of digital banking services, augmenting industry adoption.
Get sample copy of this research report @ https://www.gminsights.com/request-sample/detail/409
Several industry participants have been implementing strategic initiatives to cater to the growing demand for ATMs and other digital banking services, which has positively impacted the global business scenario.
For instance, in April 2021, The Brink's Company, a prominent end-to-end ATM solutions provider, announced the acquisition of PAI, Inc., a leading ATM services provider in the United States. The deal enabled Brink's Company to expand its complete end-to-end cash management services by integrating its solutions with the general ATM solutions.
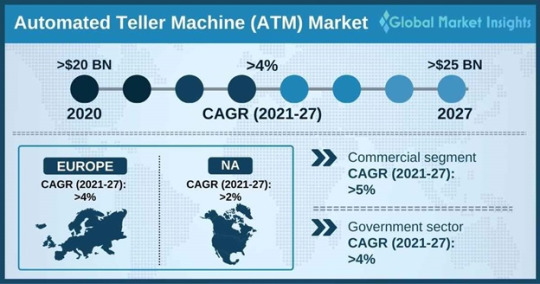
The automated teller machine (ATM) market has been segmented on the basis of application, type, solution, and region.
In terms of type, the market has further been divided into brown label, white label, and others. The brown label sub-segment is projected to exhibit a solid growth trajectory over the forecast period owing to burgeoning pink ATMs and green ATMs across several developing countries.
From the solutions point of view, the automated teller machine market has been bifurcated into managed services and deployment. Under deployment, the market has been segregated into mobile, onsite ATM, workstation, and offsite ATM.
The offsite ATM segment is set to witness robust growth through the analysis timeframe. Surging demand for offsite ATMs owing to the booming tourism industry is estimated to propel segmental expansion over the forthcoming years.
Meanwhile, the mobile segment is also anticipated to reach a notable valuation by 2027 owing to increased demand for strategic promotion activities by banking institutions in high-traffic locations.
Request for customization @ https://www.gminsights.com/roc/409
With respect to application, the automated teller machine market has been classified into residential, commercial, and government. The commercial sub-segment is poised to progress at a substantial CAGR over the review period on account of the increasing deployment of ATMs with cash recycling capabilities to enhance customer satisfaction.
On the regional front, the Europe automated teller machine industry is estimated to witness optimistic growth over 2021-2027 owing to favorable government policies that are fostering the growth of digital banking services in the region.
The Middle East & Africa automated teller machine market is expected to progress at a robust pace through the projected timeline owing to rising urbanization and digitalization across the region.
Table of Contents (ToC) of the report:
Chapter 1 Methodology & Scope
1.1 Scope & definitions
1.2 Methodology & forecast parameters
1.3 COVID-19 impact
1.3.1 North America
1.3.2 Europe
1.3.3 Asia Pacific
1.3.4 Latin America
1.3.5 MEA
1.4 Data sources
1.4.1 Secondary
1.4.2 Primary
Chapter 2 Executive Summary
2.1 Automated teller machine (ATM) industry 360º synopsis, 2017 - 2027
2.1.1 Business trends
2.1.2 Regional trends
2.1.3 Technology trends
2.1.4 End use trends
Browse complete Table of Contents (ToC) of this research report @ https://www.gminsights.com/toc/detail/ATM-market-report
Electronics and Semiconductors Research Reports
Time-Sensitive Networking Market
Bluetooth Headphones Market
Wireless Mesh Network Market
About Global Market Insights:
Global Market Insights, Inc., headquartered in Delaware, U.S., is a global market research and consulting service provider; offering syndicated and custom research reports along with growth consulting services. Our business intelligence and industry research reports offer clients with penetrative insights and actionable market data specially designed and presented to aid strategic decision making. These exhaustive reports are designed via a proprietary research methodology and are available for key industries such as chemicals, advanced materials, technology, renewable energy and biotechnology.
Contact Us:
Aashit Tiwari
Corporate Sales, USA
Global Market Insights Inc.
Toll Free: 1-888-689-0688
USA: +1-302-846-7766
Europe: +44-742-759-8484
APAC: +65-3129-7718
Email: [email protected]
#Automated Teller Machine Market Analysis#Automated Teller Machine Market by Type#Automated Teller Machine Market Share#Automated Teller Machine Market Development
0 notes