#wordpress hacker
Explore tagged Tumblr posts
Text
Really cool to see WordPress on Hacker News today. 🤠
31 notes
·
View notes
Text
A pdf-version of my post which talks about records erasure, digitization, and 1990s Hollywood films.
#1990s films#records erasure#digitization#pdfs#hollywood#hackers#the net#my fellow americans#internet archive#wordpress#1990s
2 notes
·
View notes
Text
#WordPress Website Development#Why WordPress Security is Important?#What is the best wordpress security plugin?#How to protect wordpress site from hackers
1 note
·
View note
Text
The Importance of WordPress Updates: Protecting Your Business from Cyber Threats
As a business owner, having a website is crucial for establishing an online presence and reaching out to potential customers. However, with the increasing number of cyber attacks, website security has become a top priority. WordPress, being one of the most popular Content Management Systems (CMS), is a frequent target for hackers. In this article, we will discuss the importance of WordPress updates, especially from a cybersecurity perspective, and why it's crucial to protect your business interests.
Why Hackers Target WordPress Websites
WordPress is a popular CMS, powering over 40% of the world's websites. Its widespread adoption makes it an attractive target for hackers. Moreover, the open-source nature of WordPress means that vulnerabilities can be easily discovered and exploited. When a security hole is found in WordPress, it quickly spreads to malicious actors, who then attempt to attack websites with known vulnerabilities. This is why keeping WordPress up to date is crucial in preventing cyber attacks.
The Risks of Outdated WordPress
Failing to update WordPress can lead to serious consequences, including:
Data breaches: Outdated WordPress versions can leave your website vulnerable to data breaches, compromising sensitive information and putting your customers at risk.
Malware infections: Hackers can inject malware into your website, leading to blacklisting by search engines and damaging your online reputation.
Financial losses: A hacked website can result in financial losses, either through stolen customer data or by disrupting your online business operations.
The Importance of WordPress Updates
Updating WordPress is essential in preventing cyber attacks. New releases of WordPress often include security patches and fixes for known vulnerabilities. By keeping your WordPress version up to date, you significantly reduce the risk of your website being compromised. Additionally, updating WordPress ensures that your website continues to function smoothly, without breaking due to compatibility issues with themes and plugins.
Amity IT's WordPress Updates Service
At Amity IT, we understand the importance of keeping your WordPress website up to date. Our WordPress Updates service is designed to ensure that your website remains secure and functions optimally. Our team of experts will perform regular updates on a schedule that suits your business needs, whether it's monthly or quarterly. Our service includes:
Updates of WordPress core
Updates of plugins compatible with the latest version of WordPress
Rollback of updates if functionality is compromised
By choosing Amity IT's WordPress Updates service, you can rest assured that your website is protected from cyber threats. Our team is based in Penrith and serves the Western Sydney area, providing local support and expertise.
Conclusion
In conclusion, keeping your WordPress website up to date is crucial in protecting your business from cyber threats. By understanding the risks associated with outdated WordPress and the importance of updates, you can take proactive steps to secure your online presence. Amity IT's WordPress Updates service is designed to provide you with peace of mind, knowing that your website is secure and functioning optimally. Visit our WordPress Updates page today to learn more about our service and how we can help protect your business interests: https://www.amityit.com.au/services/websites/wordpress-updates.
#WordPress updates#Cybersecurity#Business interests#Hackers#Vulnerabilities#Plugins and themes#Sensitive data#Trust and reputation#Professional WordPress update service#Amity IT Penrith and Western Sydney
0 notes
Text
Hackers Exploit Outdated WordPress Versions and Plugins in Widespread Malware Attack

Source: prontomarketing.com
Share Post:
LinkedIn
Twitter
Facebook
Reddit
Pinterest
Hackers Target Vulnerable Websites
A large-scale malware attack is underway, as Hackers Exploit WordPress versions and plugins to compromise thousands of websites. Belgian security firm C/side has raised the alarm about this widespread cyber threat, which is affecting both high-profile and lesser-known websites. According to security experts, websites running outdated versions of WordPress or using outdated plugins are particularly vulnerable to these malicious attacks. Hackers are using these weaknesses to hijack sites and distribute malware to unsuspecting visitors.
Malicious Campaign Unveiled
The attack, carried out as Hackers Exploit WordPress, involves injecting a fake Chrome update page into compromised websites. When visitors load an infected website, the page appears to prompt them to download and install a browser update to continue browsing the site. In reality, this so-called “update” is a disguised file that contains malicious software. The malware is tailored for both Windows and Mac users, with specific variants targeting each operating system. Windows users are infected with the SocGholish malware, while Mac users are targeted by the Amos (Amos Atomic Stealer) malware.
Both malware types are designed to steal sensitive information such as usernames, passwords, session cookies, and cryptocurrency wallets. The attack has been identified as an “info-stealer” campaign, to compromise personal data from affected users. Security experts have warned that these types of malware pose significant risks to individuals and organizations, especially those who may have saved sensitive data in their browsers or online accounts.
Scale of the Attack and Discovery Process
The scale of the attack is alarming, with C/side reporting that more than 10,000 websites, including some prominent ones, have already been compromised. As Hackers Exploit WordPress, this malware campaign is categorized as a “spray and pray” attack, meaning it targets anyone who visits the infected websites, rather than focusing on specific individuals or groups. Researchers discovered the scope of the attack by crawling the internet for malicious scripts and performing reverse DNS lookups to identify more compromised domains linked to the same IP address.
After uncovering the widespread infection, C/side alerted Automattic, the company behind WordPress, about the ongoing malware campaign. The security firm provided a list of affected websites to Automattic, who confirmed receipt of the report. Although no immediate fix has been issued, the exposure of the attack has brought attention to the critical need for website owners to maintain updated versions of WordPress and its plugins to prevent further compromises.
1 note
·
View note
Text
Hacker nutzen kritische Website-Schwachstellen für Übernahmen aus

Die kürzliche Entdeckung einer kritischen Website-Schwachstelle, die für unbefugte Übernahmen ausgenutzt wird, hat die dringende Notwendigkeit von stärkeren Sicherheitsmaßnahmen in der Online-Welt deutlich gemacht. Die nicht authentifizierte, gespeicherte Cross-Site-Scripting (XSS)-Schwachstelle des Popup Builder-Plugins macht Websites anfällig für die Einspeisung beliebiger JavaScript-Skripte, was zur Ausführung von schädlichem Code und zur Erstellung nicht autorisierter Administratorkonten führen kann. Diese Schwachstelle ist äußerst schwerwiegend und erfordert, dass Website-Administratoren und Entwickler zusammenarbeiten, um ihre Plattformen gegen solche Gefahren zu schützen. Wenn wir die Details dieser Schwachstelle, die Taktiken der Hacker und die wesentlichen Sicherheitsmaßnahmen zur Risikominderung untersuchen, wird deutlich, dass der Schutz der Integrität von Online-Ressourcen von entscheidender Bedeutung ist.
Sicherheitslücke im Popup Builder Plugin
Das Popup Builder-Plugin weist eine Schwachstelle auf, die Websites dem Risiko von nicht authentifizierten, gespeicherten Cross-Site-Scripting-Angriffen aussetzt. Dies ermöglicht es böswilligen Akteuren, beliebigen JavaScript-Code mit administrativen Rechten einzuschleusen und auszuführen, was eine ernsthafte Bedrohung für Website-Besitzer und Benutzer darstellt. Die Auswirkungen dieser Schwachstelle sind weitreichend, da sie es Angreifern ermöglicht, betrügerische WordPress-Administratorkonten einzurichten, was zu unautorisiertem Zugriff und Kontrolle über bestimmte Websites führen kann.

Benutzer, die kompromittierte Websites besuchen, laufen Gefahr, dass ihre sensiblen Daten, wie z. B. ihre Anmeldedaten, gestohlen werden. Die Implementierung von Eingabevalidierung, Ausgabeverschlüsselung, regelmäßigen Sicherheitsupdates und der Einsatz von Web Application Firewalls können das Risiko eines Missbrauchs verringern. Es ist wichtig, Entwickler und Benutzer über XSS-Schwachstellen aufzuklären, um ihnen vorzubeugen und mehr Kontrolle und Sicherheit über Websites zu gewährleisten.
Angriffsausführung und Indikatoren
Die Ausnutzung der nicht authentifizierten gespeicherten Cross-Site-Scripting-Schwachstelle ermöglicht es Angreifern, beliebigen JavaScript-Code mit administrativen Rechten einzuschleusen und auszuführen. Dies kann zu unbefugtem Zugriff und Kontrolle über die Ziel-Websites führen. Um solche Sicherheitsverletzungen zu verhindern, sind Abschwächungsstrategien, bewährte Verfahren und Gegenmaßnahmen gegen nicht authentifizierte gespeicherte XSS-Angriffe erforderlich. Regelmäßige Sicherheitsprüfungen und Patches sind entscheidend für die Aufrechterhaltung der Sicherheit einer Website und die Vermeidung von Schwachstellen. Die Implementierung von Eingabevalidierung, Ausgabekodierung und Bereinigung von benutzergenerierten Inhalten sind wesentliche Maßnahmen zur Verhinderung von XSS-Angriffen. Außerdem können Web Application Firewalls solche Angriffe erkennen und blockieren. Die Bedeutung regelmäßiger Sicherheitsupdates und -patches für Websites muss unbedingt hervorgehoben werden, um das Risiko eines Angriffs zu verringern. Die Aufklärung von Entwicklern und Benutzern über XSS-Schwachstellen ist für die Prävention und die Gewährleistung umfassender Sicherheitsmaßnahmen von größter Bedeutung.
Zeitleiste der Ereignisse
Die Website-Schwachstelle wurde erstmals am 1. Dezember 2023 identifiziert, als wpemojii.com in Wordfence Intelligence entdeckt wurde. Daraufhin wurde Popup Builder 4.2.3 am 7. Dezember 2023 veröffentlicht, und die Sicherheitslücke in Popup Builder wurde am 11. Dezember 2023 bekannt gegeben. Der Proof-of-Concept des Exploits wurde dann am 1. Januar 2024 auf WPScan veröffentlicht, und der für die Injektion verwendete Quellcode wurde gemeinsam mit einer am 10. Januar 2024 entwickelten Malware-Signatur veröffentlicht.

Diese Ereignisse hatten erhebliche Auswirkungen auf die betroffenen Websites und machen deutlich, dass schnelles Handeln erforderlich ist, um die Sicherheitslücke zu schließen und die Sicherheitsmaßnahmen zu verstärken.
Exploit Proof of Concept Veröffentlichung
Die jüngste Veröffentlichung des Exploit-Proof-of-Concept hat deutlich gemacht, dass proaktive Sicherheitsmaßnahmen und rasche Abhilfemaßnahmen als Reaktion auf die Website-Schwachstelle dringend erforderlich sind. Es ist von entscheidender Bedeutung, die Auswirkungen dieses Exploit-Proof-of-Concept zu bewerten und sofortige Schritte zu unternehmen, um potenzielle Bedrohungen zu entschärfen. Zu den wichtigsten Bereichen für Abhilfestrategien gehören: - Rasche Bereitstellung von Sicherheits-Patches zur Behebung der festgestellten Schwachstelle - Einführung strenger Zugangskontrollen und Authentifizierungsmechanismen - Verstärkte Überwachung und Analyse des Website-Verkehrs und der Benutzerinteraktionen - Regelmäßige Sicherheitsprüfungen und proaktive Maßnahmen zur Stärkung der Abwehrkräfte Auf die Veröffentlichung des Exploit-Proof-of-Concept muss unbedingt entschlossen reagiert werden, um die Widerstandsfähigkeit der Website-Infrastruktur zu gewährleisten und den Schutz vor unbefugtem Zugriff und Kontrolle sicherzustellen.
Behebung der Sicherheitslücke
Um die Schwachstelle zu beheben, muss ein umfassender und proaktiver Ansatz gewählt werden, um die Abwehrkräfte der Website gegen eine mögliche Ausnutzung zu stärken. Dies bedeutet, dass dem Patchen und Aktualisieren anfälliger Plugins wie dem Popup Builder-Plugin hohe Priorität eingeräumt werden muss, um die nicht authentifizierte gespeicherte XSS-Schwachstelle zu beheben. Regelmäßige Sicherheitsprüfungen sind sehr wichtig, um potenzielle Schwachstellen zu erkennen und zu beheben, bevor sie ausgenutzt werden können. Die Implementierung von Eingabevalidierung und Ausgabekodierung kann XSS-Angriffe wirksam verhindern, während Web Application Firewalls für die Erkennung und Blockierung solcher Bedrohungen entscheidend sind. Es ist auch wichtig, Entwickler und Benutzer über XSS-Schwachstellen aufzuklären. Durch die konsequente Anwendung von Sicherheitsupdates, die Durchführung gründlicher Audits und die Schärfung des Bewusstseins können Website-Besitzer das Risiko einer Ausnutzung deutlich verringern und ihre Abwehr gegen bösartige Angriffe stärken.
Leistungsanalyse und Targeting
Um die Sicherheit einer Website zu erhöhen und die Benutzerfreundlichkeit zu verbessern, ist der Einsatz von Leistungsanalysen und Targeting-Strategien unerlässlich. Cookies sammeln Daten über die Benutzernavigation und geben Aufschluss über das Verhalten und die Vorlieben der Benutzer. Diese analytischen Daten sind wertvoll für die Optimierung der Website-Leistung und die Verbesserung der Benutzerfreundlichkeit. Darüber hinaus helfen Tracking-Cookies dabei, technische Probleme zu erkennen und zu beheben, während Targeting-Cookies relevante Informationen für bestimmte Geräte bereitstellen. Diese Strategien sind für die Sicherung der Website und die Verbesserung der allgemeinen Benutzerfreundlichkeit unerlässlich.
Website-Übernahme-Kampagne
Der Start einer Website-Übernahme-Kampagne erfordert eine sorgfältige Planung und präzise Ausführung, um bestimmte Ziele zu erreichen. Die Auswirkungen von Website-Übernahmen auf Unternehmen können schwerwiegend sein und zu Rufschädigung, Vertrauensverlust bei Kunden und finanziellen Folgen führen. Hacker setzen bei Website-Übernahmekampagnen verschiedene Techniken ein, z. B. das Ausnutzen von Schwachstellen, um bösartigen Code in Websites einzuschleusen und sich so unerlaubten Zugriff und Kontrolle zu verschaffen.

Dies kann zum Diebstahl vertraulicher Informationen führen und die Sicherheit der Benutzer gefährden. Um solche Bedrohungen zu bekämpfen, sind regelmäßige Sicherheitsüberprüfungen, Patches, Eingabevalidierung, Ausgabeverschlüsselung und die Implementierung von Web Application Firewalls von entscheidender Bedeutung. Die Aufklärung von Entwicklern und Benutzern über diese Schwachstellen ist ebenfalls von entscheidender Bedeutung für die Prävention.
Sicherheitsmaßnahmen und Prävention
Der Schutz von Websystemen und Benutzerdaten erfordert die Umsetzung gründlicher Sicherheitsmaßnahmen, um potenzielle Bedrohungen zu verhindern. Um häufige Website-Schwachstellen zu entschärfen, ist es wichtig, regelmäßige Sicherheitsaudits durchzuführen, Sicherheitsupdates und Patches zu installieren und von Benutzern erstellte Inhalte zu bereinigen. Die Aufklärung von Entwicklern und Benutzern über XSS-Schwachstellen ist entscheidend für die Verhinderung von Website-Angriffen. Wenn Unternehmen die Risiken verstehen und proaktive Maßnahmen ergreifen, können sie ihre Abwehr stärken und die Wahrscheinlichkeit erfolgreicher Angriffe verringern. Read the full article
0 notes
Text
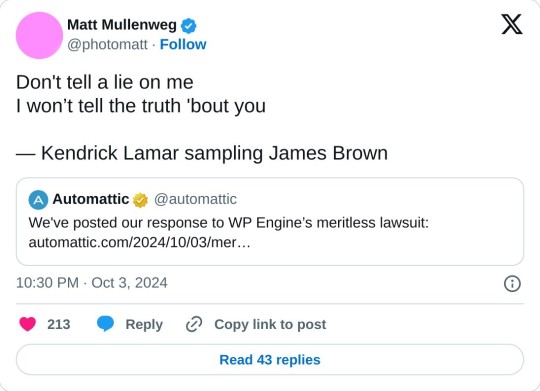
automattic vs wp engine mastterpost
adrienne's GitHub recap is probably the best place to see a comprehensive timeline of what's going down. it's been kept up to date. my (very out of date) previous writeup is here.
what's happened/other links

Matt has not logged off, just switched platforms, so there's lots on X/Twitter, Reddit, and Hacker News. it's really not worth wading through.
WP Engine actually filed suit.
the complaint includes some truly remarkable screenshots of Matt trying to blackmail the CEO of WP Engine.

which... personally i would not happily work for someone who just blackmailed me while not even my boss, but that's just me. he hasn't denied this at all, in fact confirming on Hacker News:
I haven't doxxed any private texts from other parties like they have. [source]
and, notably,
I even invited her to my 40th birthday on Jan 11, another text message she decided not to share. [source]
this gives me the creeps. in the context of the rest of the way he's talking to her, and the ways in which he's interacted with women in general, it's. not great.
also he slid into an ex-employee (also a woman)'s DMs asking why she was being mean to him bc he'd never been nothing but nice to her, while also making legal threats. so y'know, pattern of behaviour.
a good writeup of the social side of things
if you don't care so much about the open-source stuff, Steph Lundberg's writeup is, like her previous one on Matt's Tumblr meltdown, pretty solid and people-focused.
Mullenweg has already demonstrated egregious lapses in judgment and abuses of power, it’s just that up until now he’s wielded his power against vulnerable populations without access to high-powered lawyers and their own massive platforms.
a more technical writeup
this one is melodramatic in the same ways Matt was (uses war terminology), which i don't agree with, and which led to some... internal arguments at Automattic. that part's not my story to tell, but a little more on that later. it's a solid writeup of the actual WordPress side of things. there's some seriously dodgy trademark behaviour going on here.
of note: this blogger locked comments on his post:

and then Matt, uh, found a way around that:

wild!
10% of Automattic leaves
that's a link to Matt's blog post. here's an Internet Archive link.
in short, staff were offered a severance deal of the higher of $30k or six months' salary. while that's very generous, it's still very risky in today's tech market, especially (for the same reasons i mentioned when Matt was melting down on here) for people outside the US, people who need the health insurance, or people with young kids. despite that, 10% decided with very little notice (they had two days to decide) to leave.
However now, I feel much lighter. I’m grateful and thankful for all the people who took the offer, and even more excited to work with those who turned down $126M to stay. As the kids say, LFG!
i'm thrilled to see some of my ex-colleagues make it out. i'm keeping the rest who have stayed on in my thoughts. i don't know anyone who's wholesale shilling for Matt.
Matt's been pressuring staff to post in support of him, @-ing the entire company to vote on Twitter polls in his favor, and so on. many of the people who stayed have written blog posts about it, all starting with "I stayed". people on social media have pointed out the very clear pattern of Automatticians jumping into discourse to defend Matt, and it doesn't look good.
i don't have a lot to say about those posts, except to highlight Jeffrey Zeldman, whose "I stayed" post is perhaps one of the more honest ones. (his Rodney King reference was in poor taste, and he... i don't like his role at automattic, tbc) but like. he's nearly 70. he helped shape the modern internet and develop its accessibility standards. he has often put his neck on the line for disabled staff who don't have as much clout as he does. given the financial troubles he talks about and the state of this market and how old he is, i personally have read between the lines of what he's saying in a particular way.
fuck, man. i'm sad. i'm sad for all my friends who are creaking under the strain and watching others leave but who can't do that. i'm sad that many of them are left in teams which are half-empty or divisions where significant senior leadership are just gone, with no time to document what they had in progress.
i'm sad for Josepha Haden Chomphosy, the former executive director of the WordPress Foundation, who was dealing with a personal emergency and ended up having to miss WordCamp US (where Matt started publicly starting shit with WPE). she came back from that to a gigantic fire in the community she's invested a decade of careful, Matt-negotiating, stewardship to, and decided to take the severance offer. she deserved better.
other things Matt's been up to
mostly linking to comments or posts which compile things here, bc it's too scattered otherwise.
blocking people from the official WordPress X account if they disapprove of his actions.
publicly talking about a vulnerability in ACF, a plugin WPE maintains, which could put thousands of sites at risk. this is not normal, and he met with so much horror even from current staff that he deleted his post.
saying he comes across badly because he's "a little ASD", which is driving me personally up the fucking wall. he's never once said it before and he really is turning into Temu Elon.
generally bragging that he still has more planned. jesus fucking christ
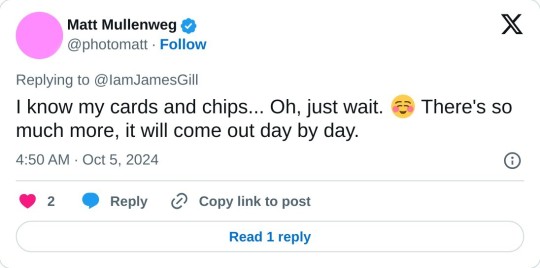
continually saying that WPE's suit is against WordPress.org and the community, which is not true. on which note, his pinned tweet is certainly something:
his choice of lawyer is uh. the kind of guy to defend nestle against literal child slaves.
as always, while i think WordPress crumbling will disproportionately affect websites in poorer parts of the world, there are certainly tyrants who are causing much more immediate and potent suffering. if you've read this far, please do send anything you have spare to gazafunds.com.
#long post#automattic#tumblr meta#this is not a complete writeup. adrienne's link does better#but here's a few things of interest to tumblr probably ig#tony muses
188 notes
·
View notes
Text
This week, WIRED launched our Rogues issue—which included going a bit rough ourselves. WIRED senior correspondent Andy Greenberg flew to Louisiana to see how easy it would be to recreate the 3D-printed gun authorities say they found on Luigi Mangione when they arrested him for the murder of UnitedHealthcare's CEO. The result? It was both easy and legal.
On Wednesday, US, European, and Japanese authorities announced the disruption of one of the world's most widely used infostealer malware. Known as Lumma, the malware was used to steal sensitive information from victims around the world, including passwords, banking information, and cryptocurrency wallets details, according to authorities. Microsoft's Digital Crime Unit aided in the operation, taking down some 2,300 URLs that served as the Lumma infrastructure.
A mysterious database containing more than 184 million records was taken down this week following its discovery by security researcher Jeremiah Fowler. The database contained 47 GB of data, which included information related to Amazon, Apple, Discord, Facebook, Google, Instagram, Microsoft, Netflix, Nintendo, PayPal, Snapchat, Spotify, Twitter, WordPress, Yahoo, and more.
In other news, the US charged 16 Russian nationals for allegedly operating the DanaBot malware, which authorities say was used in a wide variety of attacks, from ransomware to espionage. And a recent webinar revealed how a major venture capitalist helped get Starlink satellite internet activated for Israel following the October 7, 2023 attack by Hamas.
But that's not all. Each week, we round up the security and privacy news we didn't cover in depth ourselves. Click the headlines to read the full stories. And stay safe out there.
The US intelligence community is looking to create a marketplace where private information gathered by data brokers under the guise of marketing can be purchased by American spies, The Intercept reports. Contracting data shows the US spy agencies intend to create a “Intelligence Community Data Consortium” that uses AI tools to sift through people’s personal data; information that the Office of the Director of National Intelligence has previously acknowledged “could facilitate blackmail, stalking, harassment, and public shaming.” In addition to providing insight into Americans’ behaviors and religious and political beliefs, commercial data frequently includes precise location information, offering the US government the ability to surveil people’s movements without acquiring a warrant—exploiting a widely recognized loophole in US privacy law.
Federal lawmakers attempted to ban the US government from buying what it calls “commercially accessible information” last year, with the Republican-controlled House passing a version of a law known as the “Fourth Amendment Is Not For Sale Act.” However, the US Senate, then controlled by the Democratic Party, rejected the legislation.
Reporting by WIRED has repeatedly demonstrated how such data can offer US adversaries the ability to monitor the movements of US military and intelligence personnel, including in and around sensitive facilities that house nuclear arms.
A Mysterious Hacking Group Is Revealed to Work for the Spanish Government
Back in 2014, Russian security firm Kaspersky announced it had discovered a sophisticated hacking group it called Careto, Spanish for “Ugly Face” or “Mask,” that had targeted victims across Europe and Cuba. Now, more than a decade later, former employees of the company have finally confirmed what Kaspersky wouldn’t spell out at the time: That they believe Careto was a rare sighting of hackers working on behalf of the Spanish government. Careto’s targets included energy companies, research institutions, and activists, but it particularly focused on Cuba, likely due to the island nation’s giving refuge to members of a Spanish separatist group designated as terrorists by several European countries. Kaspersky’s researchers found a Spanish phrase in the hackers’ malware code that translates to “I shit in the sea,” an expletive phrase typically used by Spaniards but not other Spanish speakers. Given the sophistication of Careto’s hacking, the public confirmation of Kaspersky’s attribution to Spain adds another known player to the game of high-level state-sponsored hacking.
Signal Introduces New Feature to Block Screenshots by Microsoft Recall
Microsoft’s Recall feature, which constantly takes and archives screenshots of Windows users’ activity, still represents a serious privacy problem—even after Microsoft significantly walked back its rollout in response to criticism. So the encrypted messaging app Signal has gone so far as to exploit a digital rights management feature of Windows typically used to protect copyrighted materials to block Recall from taking screenshots of the app by default on Windows machines. After all, the Recall feature—which will likely be required for some corporate or government users—will essentially remove any privacy promise from Signal’s disappearing messages feature for both Recall users and anyone communicating with them. The screenshot-prevention feature can be turned off in Signal’s settings, but it will be turned on by default in Windows. “Microsoft has simply given us no other option,” Signal wrote in a blog post.
Russia’s Fancy Bear Hackers Targeted Security Cameras to Spy on Ukraine Aid
The hacker group within Russia’s GRU military intelligence agency known as APT28 or Fancy Bear first rose to infamy for its targeting of the 2016 US election, but it’s no surprise that the group has more recently focused on Ukraine. According to a new assessment from no fewer than 11 countries’ intelligence agencies, the hacker group has been targeting a broad array of technology and logistics firms involved in providing aid to Ukraine. “Dozens of entities, including government organizations and private/commercial entities across virtually all transportation modes: air, sea, and rail” have been targeted in the campaign, the advisory reads. Perhaps most notable about the agencies’ accusations is that the hackers targeted 10,000 security cameras in countries bordering Ukraine, including at border crossings, military facilities, and train stations. According to the agencies, the GRU hackers also carried out reconnaissance of the network of at least one producer of industrial control system components for railway systems—suggesting a possible intention to attempt sabotage—but didn’t actually succeed in breaching the company.
US Indicts Russian National Over Qakbot Malware
The US Department of Justice on Thursday indicted a Russian national, Rustam Gallyamov, on allegations that he designed software that was widely used by ransomware gangs and is known to have infected hundreds of thousands of computers, netting the gangs roughly $8.6 million in profit, according to DOJ figures. Prosecutors say more than $24 million was seized from Gallyamov, 48, over the course of its investigation. Federal charges unsealed this week allege that Gallyamov himself gained access to victims’ computers and provided it to an array of cybercriminal organizations, including Dopplepaymer, REvil, Black Basta, and Cactus, among others.
The investigation into the now disrupted malware, known as Qakbot, was announced in August 2023 under former US attorney general Merrick Garland, who credited a multinational operation that included Europol and prosecutors and law enforcement agencies in France, Germany, the Netherlands, Romania, Latvia, and the United Kingdom. Agencies of Canada and Denmark have also been credited in the investigation that targeted Gallyamov.
10 notes
·
View notes
Text
"Researchers have classified the flaw, tracked as CVE-2024-27956, as a SQL injection, a class of vulnerability that stems from a failure by a web application to query backend databases properly."
Its 2024 and people still arent sanitizing input
20 notes
·
View notes
Text
The Blood Red Riders, A Shadowrun Gang
Where public order has collapsed, gangs are endemic, elsewhere they are just common. But in the Barrens of Redmond and Puyallup there are dozens. Not only are there many gangs, there are many types of gangs: combat, dealer, go-gang. guardian, hacker, smuggler, even wizkid, as in literally kids who use magic. and more besides. Here is one of them. The Blood Red Riders are a new gang in…

View On WordPress
6 notes
·
View notes
Text
Building Your Own Cyberdeck:
What do you do when you have extra time between a job and your next? How about building your own Cyberdeck? Check this article out for tips on building your own!
The Ultimate Hacker Project For aspiring cybersecurity professionals, cyberpunk enthusiasts, hardware hackers, and circuit benders, one of the best hands-on projects you can take on is building your own cyberdeck. Despite overwhelming schedules full of training programs, full time work weeks, sometimes limited funds, and the endless possibilities of hardware combinations, many fans of the…

View On WordPress
#Cyber#Cyber Security#cyberdeck#cyberpunk#Cybersecurity Specialist#Ethical Hacking#hack#hacker#infosec#IT#IT professional#mobile#mobile computer#Pentesting#programming#project
30 notes
·
View notes
Text
Hackers exploit little-known WordPress MU-plugins feature to hide malware
http://securitytc.com/TJt9Cm
2 notes
·
View notes
Text
WordPress Website heeft ook onderhoud nodig!
Beste Mensen,
Beste Website eigenaars, Uw WordPress Website heeft ook periodiek onderhoud nodig, anders wordt de Website steeds gevoeliger voor hackers. Of als u te lang geen onderhoud meer laten doen aan uw Website dan kan uw Website zelfs offline raken. Mbits-web-content ontzorgt u graag zodat u niet meer om hoeft te kijken naar uw Website. https://www.mbits-web-content.nl/
Met vriendelijke groet, Marcel Wuring Mbits-web-content
4 notes
·
View notes
Text
Choosing the Right Hosting for High-Traffic WordPress Sites
When it comes to running a high-traffic WordPress site, choosing the right hosting provider can make all the difference. Whether you're running an eCommerce store, a blog, or a business website, performance, speed, and reliability should be your top priorities. Here's a breakdown of the factors to consider when selecting a hosting plan for your high-traffic WordPress site.
1. Scalability is Key
For high-traffic sites, scalability is essential. Look for a hosting provider that offers scalable solutions, such as cloud hosting or VPS, which can handle traffic spikes and provide additional resources when needed. This flexibility ensures that your site stays fast and responsive even during peak traffic times.
2. Uptime Guarantee
Downtime can be catastrophic for any website, especially one that relies on high traffic. Choose a hosting provider that offers a 99.9% uptime guarantee. This ensures that your site is accessible to visitors at all times, minimizing potential revenue loss.
3. Content Delivery Network (CDN)
A CDN can drastically reduce loading times for visitors from different geographical locations. By caching your content on servers around the world, a CDN ensures your site loads quickly no matter where the visitor is located.
4. Fast and Reliable Customer Support
Technical issues can arise at any time, especially when managing a high-traffic site. Ensure that your hosting provider offers fast and reliable customer support, ideally 24/7, to help resolve any issues quickly and efficiently.
5. Optimized for WordPress
For WordPress sites, it’s crucial to choose a hosting provider that specializes in WordPress optimization. Managed WordPress hosting services offer automated updates, enhanced security, and WordPress-specific performance optimizations, which can make a significant difference in site performance and security.
6. Security Features
With high traffic, your website is more likely to attract hackers. Ensure your hosting provider offers robust security measures like SSL certificates, firewalls, malware scanning, and automatic backups to protect your site and data.
To read the full guide, visit: Choosing the Right Hosting for High-Traffic WordPress Sites
#hosting#vps hosting#cloud hosting in saudi arabia#web hosting#cloud hosting service#web development#doamin and hosting bd
3 notes
·
View notes
Text
Hey, Noticing Weird Ads From Me on Facebook and Instagram?
It’s because I was hacked last week and the hackers set up this nonsense. I have my private account back and am working on getting my public page squared away — they’re locked out now but this stuff was programmed earlier — so in the meantime, one, don’t click any of those links, and two, feel free to report them as fraudulent. Thanks. — JS
View On WordPress
20 notes
·
View notes