Hello! Welcome to my page. Below you'll find a series of blog posts I've created in response to the Language and New Media that I am studying as part of my degree course. Throughout my blog, I explore a range of topics and debates within the field of New Media, as well as giving my own insights supported by my and others' personal experiences of the digital platforms.
Don't wanna be here? Send us removal request.
Text
Mind out, Mum!
There’s no time more necessary than now to share our techno-wisdom with our elders.

It is no doubt that at one time in your life you have had to show a parent or grandparent how to use a piece of technology. That might have been showing them how to take a photo, send an email, or even turn the computer on. Whatever the action, it is also most likely that you will have chuckled to yourself at the time; stopping to question how the simplest of actions could appear so complex to these people. Especially to those who once taught us to read, write and ride a bike.
Having been brought up in an age dominated by digital technology, it is hard to imagine how using such devices as smart phones and laptops comes unnaturally to some. In fact, if you asked your parents or grandparents, you’d definitely be shocked to learn the age at which they got their first mobile, when they sent their first email, and at what point their family owned a fully-functioning TV. Chances are, their responses will most definitely not fall within the first 13 years of their lives; an answer which is likely to come from only our current generation. Nonetheless, owing to the ever-growing influence of modern day technology, it is no surprise that more and more members of the older generation are turning to high-tech devices for the simple purpose of keeping up with the world. Yes, grandparents are still able to visit their local corner shop for a copy of the newspaper each day, or call up the number of the catalogue they want to buy a new winter coat from, but there are still so many advantages to be gained from having access to the internet. These include the use of Google, online shopping, and catch up TV; all of which my very own grandparents have gained access to following their recent purchase of an iPad.
So where do we step in?
Unlike us who will receive our shining new iPhone upgrade and have our devices set up and ready to go within an hour of receiving the phone, those who aren’t accustomed to using such devices will struggle to know where to start. And yes, there is that 1000-page document that comes with the device to tell you how to work it, but when you have no idea what you’re looking at to start with, even just getting the gadget to work can be a mission.
As a tech-savvy and knowledgeable generation, it is our responsibility to be there for our parents and grandparents; to show them the ropes and help them keep up with the world. I, for one, am frequently bombarded by questions from my parents about what updates on their phones mean, or how to email our auntie the latest photos of our family holiday. Equally, it is our role to warn our parents about the dangers of the internet by showing them how to protect their information online, and how not to be fooled by those on the prowl for such clueless victims.

(Yes, my grandparents are this cute.)
Surveillance Capitalism
One of the most pervasive elements of our online activity is the occurrence of surveillance capitalism. This is when the puppeteers of the internet take control of everything that we do online by converting our personal data into something useful and profitable to them. And it’s all out of our control.
Take Google for example. Google is a marvellous platform which allows us to ask almost ANYTHING and receive an answer within seconds of our search. We can ask Google how to change a tire on our car, what time the nearest Nando’s closes, or where to buy the best value top-of-the range makeup. Whatever our search, Google has an answer. And he’s happy to help at no charge. Well, that’s what we think…
Google is in fact, watching our every move. Absorbing our every click into its data base and sharing this information to its many friends; Facebook, Instagram and Amazon. And what do they do with this info? They use it to create targeted advertising tailored to our searches. Presenting us with adverts to help us find that perfect coat we were searching for two days ago, and tempting us with content that is personal and applicable to us.

Where’s the danger in that?
Whilst there are many of us who are aware of the internet’s tactful tricks, our parents and grandparents are less sensitive to this. And this is where things might get sticky. Take my mum for example, she on a day to day basis messages me with links to products she’s “seen on Facebook”, asking me to purchase them for her. Some of these products are often the most random of things; pillow case covers, ring polishers, and magnet eyelash extensions. Things I certainly wouldn’t come across on my news feeds. When asking her about the unusual eyelash extensions, I discovered that the previous week she had actually googled ‘the best mascaras for lengthening lashes”: and this is where I was able to make the link. The sites had worked together by exchanging this data, and their objective (to target my mum with a product which offered an expensive solution to her search) had ultimately succeeded!
However, this is a very minor example and it could be argued that it was my mum’s choice to buy the item. And that she easily could have turned her head if it was something she didn’t want to buy. On the other hand, there are also adverts which promote slightly fraudulent deals such as ‘Buy XXXXX for £0, limited time only’, which actuals totals at £20 once an extortionate delivery price has been added at the checkout (and you’ve already put your card details in...).

Elsewhere on the internet, there are also much more extreme examples of fraudulent and manipulative behaviour. Phishing being the major method of attack. Phishing is defined by the Oxford dictionary as “The fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers.”. It is an act which forces users of the internet to become victims of their own devices, and can result in serious consequences such as losing money, being hacked, or having your identity stolen.
As with the other online trickeries mentioned above, phishing is another example of the need for us to educate our elders about such online crime. Just like cold-callers and scammers who use telephone calls to target vulnerable people, phishing is another, and arguably easier way, for criminals to benefit from the naivety of their victims at the click of a button.
How does it work?
Phishing usually occurs in the form of emails claiming to be sent from trustworthy sources such as your bank, ‘fake’ colleagues, or PayPal. Some might also occur in the form of Holiday agents claiming that you need to enter your card details to re-secure your recent holiday payment. In reality, after giving into this email, you won’t be able to afford that holiday you were saving for!
Whoever the sender, their goal is to persuade you to give them something valuable to them; that being your passwords, credit card details, or personal information.
What to look out for:
Before you can warn others about the danger of online crimes, it is important to know yourself what to look out for. The main things to seek out are:
Who is sending the email?
Do you actually know the person? If so, do they email like they normally would? How do they sign off the email?
If it’s from a bank or company, do you actually have an account with them? And is what they are referring to something actually relevant to you?
Is the email legitimate?
The first thing I do when receiving a suspected spam email is to click on the name of the sender and view the entire email address. This way I can see whether it’s likely to be an official account or not. If it doesn’t even mention the name of the sender, it’s likely it’s not.
Are they likely to EMAIL you about this?
When receiving an email about your latest bank transaction, or prompting you to verify your Paypal details, it’s also wise to ask yourself: would they actually email me about this? Or would they rather send me a letter in the post or give me a call? Legitimate emails from companies should never ask you to do something involving such confidential data at the click of a button.
Also, don’t allow yourself to be fooled by your inbox. Even if an email hasn’t been sent to your Junk folder, this doesn’t mean that it’s as true as it claims to be. Highest chances are, it’s only made its way through the spam checks because the sender knows what s/he’s doing.

If there’s anything that the hundreds of E-safety lessons at secondary school taught me, it’s to think extra-cautiously about everything I do and engage with online. It’s now time to share this wisdom with those who might be slightly less aware. Don’t be dumb, tell mum!
Image credits:
https://gfycat.com/fortunatesmartgreyhounddog
https://smith.queensu.ca/insight/articles/don_t_buy_what_surveillance_capitalism_is_selling
https://tech.rochester.edu/security/phishing-education/
17 notes
·
View notes
Text
Asking for Aggro. ASK.FM
Impoliteness on the web: an unusual case study.

When it comes to being polite in the real world, there are several foundations we look to for guidance: what our parents taught us, what was acceptable at school, the norms and routines of our social groups. We use politeness as a strategy for protecting our and other’s ‘faces’ (Goffman,1967), for building and maintaining relationships, and achieving goals in different contexts (such as the workplace).
In the online world, however, these practices are much different. Our politeness routines are distorted and shaped by people we have weak ties with, and the anonymity that comes with sitting behind a screen. One could even argue that, when online, it is much harder to be naturally polite, and much easier to be impolite to those in our networks.
There are thousands of examples of how impoliteness has become a common aspect of everyday online interaction. On Twitter we see threads of retaliating comments to both famous and ordinary people’s posts, on Facebook we see necessary negative comments on other’s innocent life updates, and on Instagram we see way too many instances of body shaming.
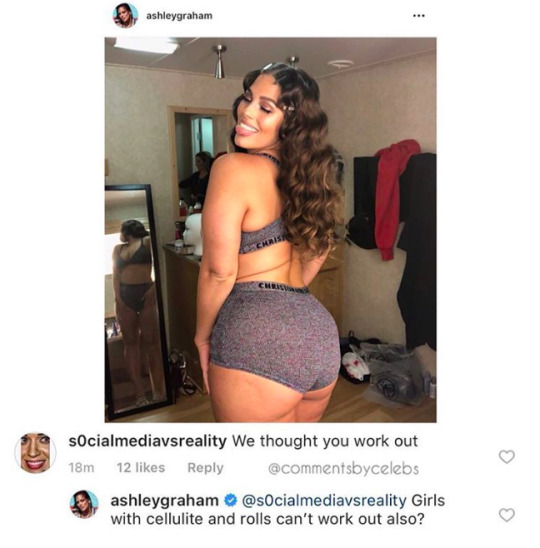
Take this image, for example. Successful model, Ashley Graham, chose to post a photo of herself in her lounge underwear, glammed up, and posing at the camera (a pretty common theme on Instagram these days). One user then opted to comment on the post “We thought you work out” (ie. indirectly implying that 1. It looks like she doesn’t work out, 2. There are a collection of people who have the same opinion). A person who responds to others content in a way such as this (which aims to offend) is labelled as a ‘Troll’. Equally, the commenter’s user name ‘s0cialmediavsreality’ infers that the creator of this account has the sole intention of targeting instances where presentations on social media and in the real world clash. But does this give he/she the right to respond to Ashely’s photo like this? No, it does not.
No matter what an individual’s personal beliefs are, there is no one who is more entitled than any one else to post rude or offensive comments on someone else’s post. This comment is 100% unnecessary and, regardless of Ashley’s status, is going to offend or upset her one way or another. Additionally, with regards to the politeness theory proposed by Brown and Levinson (1987), the commenter is demonstrating ‘negative politeness’; meaning they are damaging Ashely’s negative face needs (to be respected, and not imposed) by ridiculing her body and implying that she lies about her fitness routine. However, the impact of the comment is arguably mitigated by Ashley’s response to the comment ‘Girls with cellulite and rolls can’t work out also?’ in which Ashley challenges the comment and frames the commenter as the untruthful one, instead of herself.
Strategies for avoiding impolite, offensive comments?
Whilst the act of trolling is unfortunately something which many people have to deal with in their social media lifetimes, social networks have increasingly developed strategies for dealing with this sort of behaviour. Primarily, social media sites offer the option for users to report offensive behaviour at the click of a button.
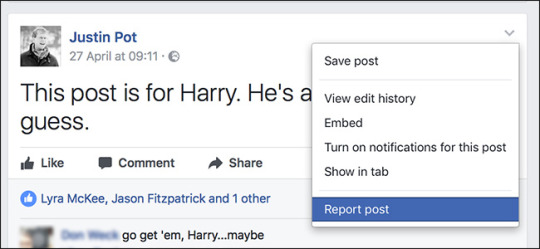
Once selecting report, there will often be other options to choose from which narrow down exactly why you are reporting the post. The post is then usually removed immediately or sent for approval, depending on the nature of the incident. Equally, there is also the option to unfriend, unfollow or block users on social media. This can help to prevent the user from performing the same sort of behaviour towards you in the future. This is the best option if you wan’t to completely remove yourself from a threatening situation.
At the same time, there are also hundreds of guides and e-safety videos which offers guides to users on how they should behave online. These rules are occasionally referred to as ‘Netiquette’ and include guidelines such as: Respect others’ privacy;Don’t abuse your power; Adhere to the same standards as in real life.
Perhaps some users need a refresh?
Biting blind
But what if the trolls are posting from anonymous accounts or ones which prevent you from identifying exactly who they are in the real world?
As we saw above, in the case of the lovely ‘s0cialmediavsreality’ user, many trolls will often post from accounts which hide their identities; meaning they can be as impolite and as horrible as they wish without there being any real repercussions for them. Unfortunately, most trolls actually get a kick out of knocking others down; so when you’re faced with instances involving people such as these, it’s the best idea to ignore their comments and prevent them from obtaining the reaction they want.
Likewise, there are also occasions when trolls are empowered to post harmful comments against others. In instances when their identities are completely anonymous. One platform which allows anonymous posting is Ask.fm.
Asking for it on Ask.fm.
Before I make fun of those who willingly sign up to Ask.fm (and pretty much make themselves victims to trolls), I must admit that I, myself, had an Ask.fm account at the age of 14. However, I didn’t know what I was signing up for and I was merely doing so to follow the crowd and keep up with the everyday classroom chat. And luckily enough for me (being a bit of a goody-two-shoes at school), I didn’t receive any harmful comments and the most personal question I received was probably ‘Are you a virgin?’, which was pretty expected in the social context of an all girls secondary school.
Ask.fm is an online platform which individuals can sign up to use in exchange for an abundance of anonymous questions (from people they know), and the power to ask others questions without the fear of a trail leading back to them. When asked a question, users are alerted and given the option to reply or delete the question (all at the risk of the ‘Asker’ confronting or making assumptions if there’s no reply).
The platform was pretty popular throughout the year and was something which others were encouraged to get and engage with. Some people even took to Facebook to share the links to their account with a caption along the lines of ‘Ask away, I’m bored’. So pretty much encouraging trolling to occur…
Don’t get me wrong, there were a few adorable examples such as ‘Why are you so pretty?’ to which most girls would respond ’Says you! You’re stunning!’, but in most cases the outcome was the opposite. And the worst thing was, there was no way of working out who posted what: so if you happened to be the person who received a slightly upsetting or aggressive question, you’d go to school the next day wondering if the person sitting next to you was the one who thought those things about you.
Here’s an example of the more typical questions you might find…
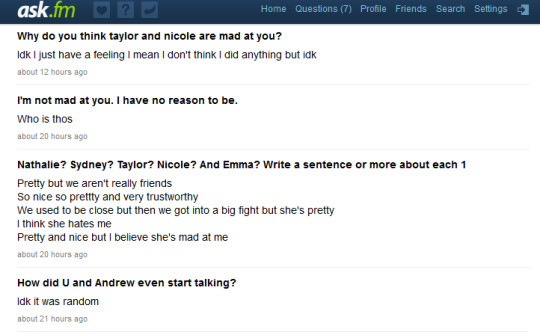
In this instance, it’s clear that the person/s asking the questions to this particular user are using the anonymity feature to their advantage in order to obtain gossip or a response they’re too afraid to request in the real world. Additionally, by requesting an opinion of five different people, the ‘Asker’ is being quite invasive and threatening the positive face of the ‘Answer’ (ie. they are forced to respond positively, or face the consequences of their response).
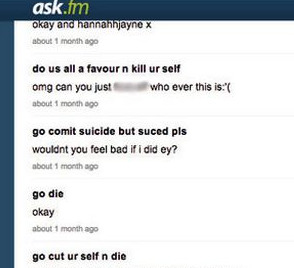
In other instances, however, users are also at risk of receiving much more aggressive questions such as these. The questions asked here are extremely offensive and threatening to the user’s negative face. This exchange is also a huge issue with regards to teenage mental health, particularly with regards to the influence that teenagers allow internet trolls to have over their thoughts and actions. This is a concept which many psychologists, e-safety experts and films have explored: one example being ‘Cyber Bully’ which you can view the trailer for below.
youtube
Cyberbully (2015) staring Maisie Williams. Film trailer.
Being impolite online (no matter how serious you consider the comment to be), can have tragic consequences for not only your reputation, but also the feelings of the person who the comment is aimed at. We all respond differently to criticism and offence, and it’s impossible to know exactly what else in going on in someones life which might escalate the effect of your comment for them. Before posting online always remember to consider: What you say this to their face in the real world? If not, press delete.
References:
Brown, P. & Levinson, S.C. (1987). Politeness. Cambridge. Cambridge University Press.
Goffman, E. (1967). Interaction ritual: Essays in face-to-face behaviour. Chicago: Aldine Publishing Company.
2 notes
·
View notes
Text
The Bitmoji Revolution

The launch of the ‘Bitmoji’ in 2016 established a new dimension of communication between Snapchat users. By creating their own bitmoji, (a cartoon-like avatar) via an app on their smartphones, users were able to create a replica of themselves by selecting their face shape, hair cut and clothing style amongst many other qualities. This is arguably similar to the ‘Mii’ feature available on Wii gaming consoles.
The Founder of Bitmoji, Jacob Blackstock from Canada, explained that the objective behind his initiative was to “enable self-expression without the need to have artistic skills”. This self-expression is enabled by not only a user’s digital avatar (which they can frequently edit and choose to appear on the SnapMaps feature of their Snapchat), but also the bitmoji artworks which they can choose to accompany their photo messages. These artworks incorporate the user’s personal avatar with other symbols and captions which can be chosen from depending on the mood or message that the user wants to display. Let’s take a look….
Say hello to my very own bitmoji; Taz. It doesn’t say too much about the real life me, but in terms of hair colour, eye colour and dress sense I’d say it’s pretty accurate.

The Bitmoji app provides me with hundreds of variations of my avatar in the form of creative cartoons. You can find a selection of them below.
Want to give my friend some motivation? Ask my mum to borrow money? Tell the world how excited I am to eat the nachos I just ordered? Bitmoji have me sorted… Each of these bitmoji artworks tells its very own story through the process of symbolisation; meaning it represents a feeling or idea which I want to express to someone, without me having to be there with them.
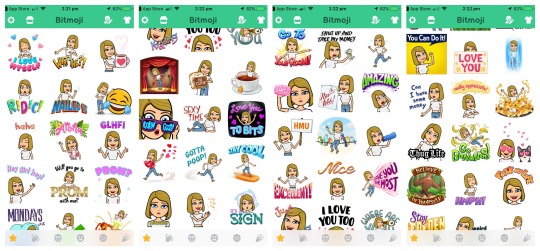
Bitmojis in action:
So how might we use bitmojis? Since snapchat’s incorporation of bitmojis in 2016, Instagram and Apple iMessanger have also added the avatar bank to their keyboards. Meaning bitmojis can now also be used in text conversations and Instagram stories.. This leads us to the concept of situated semiotics: dependent on where the bitmojis are used, and the purpose that they serve, their meaning can differ.
Take a look at the below examples. Here are just a few Instagram stories which feature my bitmoji.

Paris- The first story is an image of the Eiffel Tower which I took during my trip to Paris in December. The bitmoji that I selected to accompany the photo is polysemous in that it could express several things; my love for Paris? Paris as the city of love? my particular love for the Eiffel Tower? All of these are correct! However, it was down to my Instagram followers to decipher which meanings I meant to express.
Tapas for days- The second is a photo I took while enjoying lunch and a Pimms with my mum last summer. The bitmoji I selected for this story also includes text: “Bless you”. I chose this bitmoji to show my appreciation for the delicious food we were enjoying, as well as the company of my mum. However, to some, the words ‘bless you’ might have a religious connotation- am I literally thanking God that I am lucky enough to be enjoying the food? In this instance, the verdict is down to the relationship I have with those viewing my story. And if they know me well enough to recall that I’m not overly religious, they’ll be able to work out which meaning I was going for.
Dreamgirls- The third instagram story features the West End show Dreamgirls’ theatre billboard. The bitmoji I chose for this story also includes a caption: ‘Can’t wait’. Whilst this implies that I couldn’t wait to see the show, I was also hinting at the fact that I also couldn’t wait to share the experience with three of my friends from my stage school.
When in Greece- The final story is of my boyfriend holding a cute-looking reptile during our holiday to Greece. My bitmoji once again includes a caption ‘totes adores’ and uses facial expression to relay the meaning of the message. Not only does the use of slang in the caption portray a certain identity of myself (the context being one which is laid back), but the language also hints at my relationship with the person that features in the photo. I also most likely chose this particular bitmoji due to the colour of the typography since it matched some of the colours in the image (I doubt, however, that this was something my viewers picked up on).
All of these bitmoji uses seem pretty logical. They show a sense of how I was feeling at the time I took the photo. They do this without me having to explicitly write: “I’m excited to see this theatre show”, or “this combination of my boyfriend and reptile in this photo is cute”. However, there are some instances when using a bitmoji to communicate an opinion or feeling may have some constraints for the interaction. For example, bitmojis (like any other form of digital communication: text speak, emojis, gifs) can be used sarcastically or humorously. There may also be complications in instances where the cartoons don’t tell the entire story and are therefore ambiguous in their meaning. An example of when this might occur is the use of Friends Bitmojis: these are created in the Bitmoji app using a combination of your avatar with a friend’s.

Here are three examples of friends bitmojis I have access to. Due to the situated semiotics of these cartoons, I can use them to depict a variety of messages. From left to right, the use of these bitmojis could allow me to reconcile with a friend, encourage my sister to take up a job opportunity, or let my boyfriend know that I’m upset with him. In another conversation however, I might be joking with my friend over her questionable decision, persuading my sister to order us a takeaway, or sulking with my boyfriend over his decision to eat the last cookie. There are hundreds of meanings that each could entail; it’s down to the context and recipient to determine which one it is. This is what makes bitmojis so special.
A future for Bitmojis?
Whilst bitmojis still have a long way to come in terms of their usage, the concept of personal avatars is one which I predict will continue to grow. Bitmojis are an innovative, time-saving strategy of self-presentation which have the potential to stretch beyond the spectrum of entertainment and social media. Who’s to say that avatars won’t expand to dominate the business industry one day too? In five years time, we might even see the inclusion of such icons on job applications or CVs to represent ourselves visually, as well as textually to potential employers.
11 notes
·
View notes
Text
Making your Mark online
Empowered by the WWW, social networking sites such as Facebook, Twitter, and Instagram are home to a hubbub of social activity, interaction, and the kindling and (re-kindling) of relationships. Social networks allow us to maintain considerably more friendships than we would ever be able to manage in the off-line world. They allow us to create strong ties with people we have history with by interacting with them at the click of a button. At the same time, we establish weak ties with those who we share mutual friends, interests or even the same obsession for a celebrity with. These weaker, less intimate relationships, form the online communities that we engage with.
In the last five years or so, social networks have evolved into a platform on which not only social relationships can thrive, but business relationships can too. Such interactions are often seen in the form of digital adverts on our Facebook news feeds or company pages designed exclusively for engagement between businesses and their existing and potential customers.
Instagram, on the other hand, gives businesses a slightly different approach to their sales’ strategy. The major difference being their use of public figures and celebrities to do the selling for them. For example, you might recall Calvin Klein’s use of Justin Bieber and David Beckham to flaunt their undies, or the wave of online clothes shopping and teeth whitening adverts that flooded the accounts of Love Island contestants following their departure from the show.
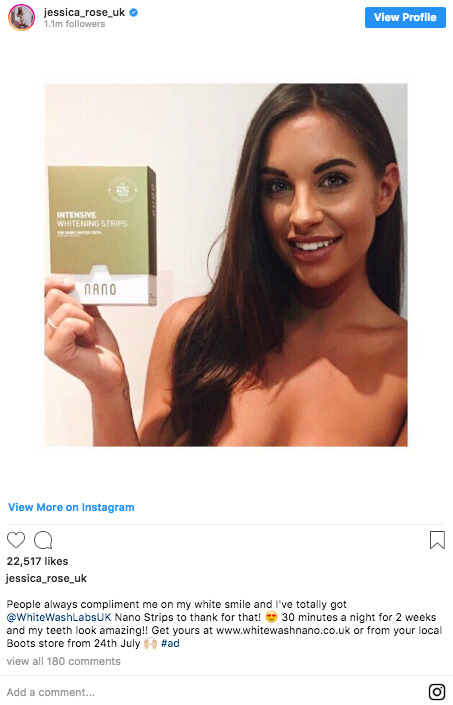
2017 Love Island contestant’s, Jess, paid promotion for teeth whitening brand.
Additionally, more and more companies are now beginning to turn to Influensters for help with their sales. One example is female clothing Brand, Boux Avenue who run an annual student ambassador scheme. A scheme which I am lucky enough to be part of this year! Female university students can apply to participate in the scheme by submitting an application via their Instagram accounts. Those chosen to be ambassadors then work closely with Boux Avenue throughout the year; working hard to promote the company and their values through social media posts, blog entries, and attendance to launch events. in return, ambassadors receive multiple new additions to their wardrobes and the chance to win some worthwhile prizes (including £5000 paid of of their tuition fees!). I really enjoy the scheme; mainly due to the online community which I have become a part of. Members of this community include other ambassadors, members of the company’s management team, and Boux Avenue’s customers.

Here’s a few of the members of my online community.
I definitely wouldn’t call myself an Influenster, as being one requires a lot of devoted time to building such an online presence. However, being a part of the scheme has definitely given me a platform on which to build my self-brand. This was especially influenced by Boux Avenue’s inclusive ethos and endorsement of self-confidence of women. A theme which is especially in keeping with my personal blog’s core values of positivity and having a bright insight to life. You can read my blog here:
https://tazusher.wixsite.com/tjubrightinsight
Who are Influensters and what do they do?
Influensters are social media users who influence the way that others think, act or feel. The best Influensters do so in a creative and empowering way; addressing topics ranging from fashion, to travel, to self love. They do so in a way that is unique to them, and by creating their self-brand.
Self-branding. Where to start?
Establishing a self-brand is a gradual and challenging process. Although we are all unique in the offline world, the tricky job that Influensters face is to translate their personality, values, and interested into one which stands out online. Most importantly, they must occupy a style, insight or knowledge which is beneficial and of interest to their followers. Characteristics defined by author Malcolm Gladwell as belonging to internet users called ‘Mavens’.
To explain exactly where you might start when it comes to creating your self brand, I’ve created this short animation.
8 Steps to creating a Self Brand:
youtube
But where do we draw the line between self-branding and money making?
It’s a tricky one to call. So often nowadays you will see Influensters using their successful digital platforms to promote businesses in exchange for money. Yes, in some cases this means that they can rely on their pristine Instagram feeds as their main source of income, but for their followers who might be expecting something a bit more unique, the abundance of adverts and promo posts on our news feeds can become a bit mundane. Equally, such content has been said to be misleading. It is occasionally confusing whether celebrities and Influensters were promoting brands for business reasons, or if they have a genuine love for a certain hair product or weight loss tea.
This is where #Ad steps in. As of this year, the requirement for Influensters to include #Ad in their posts has become much stricter. Personally, I think it’s a good idea for Influensters to remind their followers whether what they’re posting has a business incentive behind it or not. After all, the success of their digital platform (enabling them to form such partnerships) is something for them to be proud of. However, ensuring that their followers have an honest impression of them should be a top priority too.
References:
Gladwell, M. (2000). The tipping point: How little things can make a big difference. New York: Little Brown.
The Soapy Group (2018). Retrieved from: https://thesoapygroup.co.uk/facebook-advertising/
5 notes
·
View notes
Text
Stranger Danger!
Are anonymous chat sites a dangerous playing field for internet users?

With an abundance of social networking apps to choose from these days, we have plenty of opportunities to chop and change our profiles to deliver online identities which are much more favourable replicas of the ‘real’ us. Having free rein over our profiles enables us to control how others perceive us and who/ what we interact with. Even better, such platforms give us the freedom to hide what we perceive to be the less attractive aspects of our lives. So no, the guy you fancy on Instagram doesn’t have to see what you look like first thing in the morning, and your work colleagues on Facebook won’t be able to see your drunkest state on a Saturday night. These choices of what we do and don’t share online are enabled by what are referred to as Involvement Screens.
What if Involvement Screens enabled you to hide your identity all together?
Whilst social networking sites are popular for their ability to connect internet users in a way that saves the time and effort of face to face interaction with real life friends, the enormity of the WWW also allows individuals to engage with people they may never have met in the real world. This advancement in the field of social interaction is a benefit highlighted by the Hyperpersonal perspective on social networking which favours the convenience of online interaction over face to face encounters.
However, when it comes to talking to ‘strangers’, users gain the power to perform self-censorship over their profiles; meaning they can create a new version of themselves which can be as similar or dissimilar to their real selves as they desire. In unique cases, this might involve the use of a new name or avoiding the declaration of an identity all together. Some areas of the internet even allow users to become anonymous.
What are the benefits of anonymity online?
Advice networks are an ideal example of platforms where anonymity can have huge benefits for users. Want medical advice on something your too embarrassed to visit a doctor for? Instant chat platforms, such as webdoctor, provide anonymous advice services which individuals can engage with in the comfort or their own home. Likewise, the site ‘Kooth’ was founded for young people to seek advice and understanding from people other than their friends, whilst ‘Chat to a Potato’ allows users of any age to chat to someone tackling issues similar to them.
youtube
‘KOOTH- anonymous online counselling and emotional well-being platform for children and young people’
For some, the ability to become ‘anonymous’ is a revelation. It offers the chance to completely disconnect from the real word and engage in a fantasy world where judgements and reputation have no value. However, the power of anonymity has also been shown to encourage negative responses such as the performance of inappropriate behaviour including harassment and flaming (Jones & Hafner, 2012). Even more, whilst anonymous chat rooms provide opportunities to talk to new people, it is not guaranteed that interactions with these strangers will always be worthwhile and enjoyable. In some cases, they may even be unpleasant.
Take the international site ‘Omegle’, for example. You may remember this anonymous chatroom from your secondary school years. I certainly remember my classmates spending lunchtimes on the site, exchanging hilarious messages with strangers and trying as hard as possible to generate the weirdest conversations with their randomly-generated strangers. However, despite the hours of amusement Omegle provides, it has also been cautioned for its danger and explicitness arising from cases where the site has been used to groom and manipulate younger, innocent, users; enabled by the anonymity of their identity.
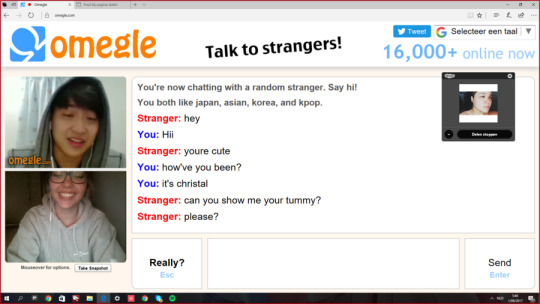
‘OMEGLE- Talk to Strangers! Anonymous online chatroom’
Too good to be true?
Sometimes, social networkers’ anonymity is less obvious than we think. Remember the American TV show, Catfish? This reality-based documentary exposes both the fairytale and nightmare realities of online dating by accompanying internet users to their first ever face to face encounters with online love interests. The individuals featured on the show have met and expanded their relationships solely through the medium of online chatrooms. And, in more cases than none, the final scenes of the episodes result in the exposure of a ‘Catfish’; someone who has created a false representation of themselves using a fake online profile. This tactic is an extreme instance of what is referred to as Impression Management.
youtube
‘CATFISH- 10 Most shocking Catfish reveals’
The internet is an infinitive space; characterised by user generated content, interaction, and, of course, actions. Yes, the invention was a revolution for social networking and connectivity, but, without the internet, maybe we could learn to love ourselves for who we really are…
References:
Jones, R. & Hafner, C. (2012). Understanding Digital Literacies: A Practical Introduction. Oxon: Routledge.
7 notes
·
View notes
Text
Clickbait- are we hooked on lies?
Living in an age oppressed by obsession with social media and the online world, it is no surprise that the word clickbait- a term coined to describe the attention-getting strategy of online content creators using intriguing headlines and images- has become synonymous with the practice of posting content online. Whoever you are, however many followers you have, the ability to effectively capture the attention of other internet users is something which we are becoming more and more capable of; by simply producing ‘clickbait’.
What makes for a successful clickbait?
Michael Goldhaber who proposes that we are living in an attention economy, highlights the importance of “seeking, obtaining, and paying attention” for members of online social communities. Notably, it is the freedom of speech and expression enabled by social media platforms which has made this practice of attention-getting feasible for even the most ordinary of users. And this is how….
For a post to gain ‘attention’, the creator must exhibit one or more of these four qualities:
1. Making the post relatable- associating your content with something others are familiar with is the no.1 step to producing the perfect clickbait. Personal pronouns such as ‘you’ are a reccomended starting point.
2. Giving it the ‘shock-factor’- whether you’re talking about a new-found hangover cure, or an Olympian whose been exposed for taking performance-enhancing drugs, the post has to evoke a reaction unique from that of an everyday tweet.
3. Offer something new- you don’t have to promise a life changing cash prize for your post to become read-worthy. Offering even the smallest of things such as the opportunity to lose 3 lbs or find a holiday for less than the reader’s normal rate is enough to receive those sacred clicks (when it comes to headlines like these, advertisers know their game!)
4. Save the best til’ last- The most important thing to remember when it comes to creating headlines is to leave the reader wanting more. The most common examples of clickbait cliff-hangers are phrases such as “it will blow your mind”, “you’ll never believe what happens next”, and “this will change your life”. If opting for this strategy, however, make sure you put a less cliché and overambitious twist on your’s.
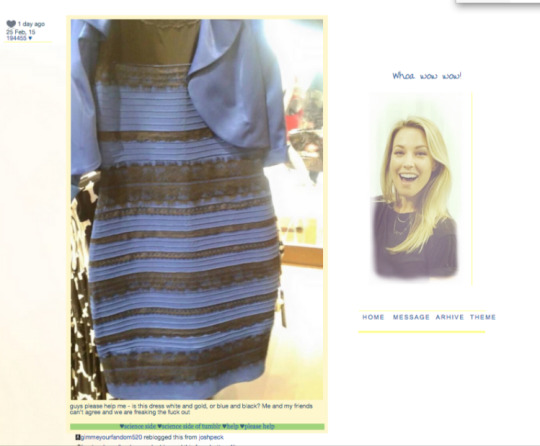
The dress
A classic example of clickbait gone wild is that produced by ordinary Tumblr user, Caitlin McNeill, who in 2015 took to the social platform to request feedback on the perceived colours of a certain dress. The dress, which became globally recognised by the hashtag #TheDress, sparked a HUGE reaction; with viewers joining the Blue and Black, and White and Gold teams dependent on which colours their eyes saw the dress as. Even more, in addition to the original post receiving over 73 million views, it sparked responses from celebrities including Justin Bieber, Ellen DeGeneres, and Kim Kardashian; making it one of the most talked about dresses of all time! Why? Because it offered something obscure, unique and absolutely worth sharing!


The the same went for the Yanny vs Laurel audio debate which left internet users, once again, divide by their senses. Even Trump got involved with this one.... (not that his opinion proves much, mind.)
With clickbait, where do we draw the line?
One of the most popular training grounds for clickbait is the Journalism industry. Every day, hundreds of media streams use the internet to promote their stories and encourage users to share and engage with their content. And how do they do this? Headlines.
Headlines are the make or breaks of a news story: they can turn small, almost irrelevant news stories into readership record-breakers, simply determined by the creativity and proficiency of their authors. The most effective headlines draw readers to a story by offering something which is clever and intriguing, however this can often lead to misleading messages or instances of ‘fake news’.
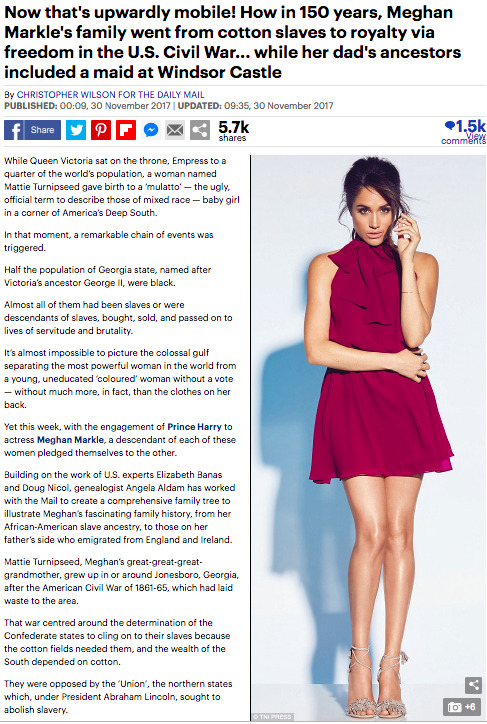
A prominent example of clickbait in the form of news headlines were those produced in the lead up to the royal wedding between Prince Harry and Duchess of Sussex, Meghan Markle. Notably, in the months prior to the ceremony, headlines targeted at the Duchess’ ethnicity were evident across multiple media streams including the Daily Mail who entitled one article “How in 150 years, Meghan Markle’s family went from cotton salves to royalty via freedom in the U.S Civil War” and the Mail’s headline “Harry’s girl is (almost) straight outta Compton: Gang-scarred home of her mother revealed”. Both these examples of clickbait present the tailoring of content in order to grant the reader superiority over Meghan. Likewise, it is also clear that the journalists take advantage of the couple’s prestige and personal details for the purpose of creating a story which will go viral. At face value, these headlines seem merely historical and witty, however looking into the story and discovering the hard facts, (that Markle’s ethnicity really has no relevance to the marriage at all) the headlines use of clickbait become immediately clear.
Solution to clickbait?
Whilst avoiding clickbait is mostly a personal decision- after all, you decide what you do or don’t click on- there are many organisations and individuals who have begun to recognise the negative impact that misuses of the strategy can have. An example of which is Facebook who in 2016 began to develop their algorithm to include a feature which filters through articles and orders them in terms of the time a reader spends reading them. In other words, if the reader returns to Facebook from the article in seconds, the effect of clickbait can be easily identified and, as a consequence, avoided.
Like most digital phenomenas, clickbait is a tool which is subject to the user’s control. It can be used positively, to entertain and inspire, however when used negatively can produce false information waste readers time.
Next time you click- THINK. Am I being hooked?
References:
Goldhaber, M. H. (1997) The attention economy and the net. First Monday 2 (4-7). Retrieved from: https://firstmonday.org/article/view/519/440
Cover image: Retrieved from: https://theoutline.com
Christopher Wilson (2017). Now that's upwardly mobile! How in 150 years, Meghan Markle's family went from cotton slaves to royalty via freedom in the U.S. Civil War... while her dad's ancestors included a maid at Windsor Castle. The Daily Mail online. Retrieved from: https://www.dailymail.co.uk/femail/article-5130473/Meghan-Markles-upwardly-mobile-family.html
11 notes
·
View notes
Text
Remixes we resonate with
Can I use this? Is it copyright free?
These are questions which we very often ask ourselves before copying, incorporating or adapting another person’s work into our own (also known as intertextuality). For example, you might be writing a blog post, creating a Facebook status, or even writing an essay on your laptop. Although all personal actions, each of these could result in copyright offences if not approached cautiously.
The fear of committing copyright violation has grown in scale and severity amongst internet users since the invention of the World Wide Web. Notably, it is the growth of legal legislation, outlining the prosecutions for the crime, which has urged individuals to be much more careful when posting content.
But surely me uploading a video of me and my friends to YouTube in 2012 with Flo Rida’s ‘Wild Ones’ as the backing track wasn’t a copyright offence, right?Incorrect. Nowadays violating copyright laws is something which we do so subconsciously that it’s almost impossible to avoid. YouTube, in fact, now have an official copyright policy which states that the original artist of a song has full control over the re-use of their work (even in harmless examples such as mine). This could result in the new content being blocked or completely muted in order for it to comply with the artist’s copyright preferences.
Does copyright violation signal a lack of creativity?
The legal restrictions associated with copyright violation suggest that the act is an entirely negative one which should be avoided at all costs. In particular, those who commit copyright are perceived as having both a lack of respect for the creator of the material in use, as well as a lack of personal creativity. However, in a broader sense, it is also worth recognising the affordances that using others’ work can entail. Notably, Manovich (2007) suggests that today we live in a ‘remix culture’ in which users perform acts of ‘Remixing’ and ‘Mashing’ that shape the internet as a platform for building on, and responding to, others’ work. Consequently, it is such actions which contribute to the creative and collaborative qualities of the internet; making it a platform which authors and readers can interact and engage with at the click of a button.
Remixing, recognised as the altering of existing work, and Mashing, the combining of two or more works together, are branches of intertextuality which can also be viewed in a positive light. For example, in 2012 The British Heart Foundation aired an advert incorporating the hit ‘Stayin’ Alive’ (by the Bee Gees) which instructed the nation on how to perform CPR successfully. The advert used the song’s rhythm as a guide for the pace and power at which the medical process should be performed.
youtube
British Heart Foundation (2012). CPR techniques.
Ultimately, the ‘mashing’ performed in this advert resulted in a highly informative and life-saving piece of work which, by using the Bee Gees’ song, became extremely popular in the media and amongst the general public. Additionally, it was the unlikely pairing of these two pieces, despite their shared semantic field of maintaining life, which made the advert such a success in terms of its uniqueness and engagement. However, had the advert not used such a prominent song, it is unlikely that the effect would have been the same…
Similarly, a recent example of remixing can be seen in the below animation produced as part of the 2016 Wildlife Conservation Film Festival. The short video, featuring animated endangered animals, includes the musical track ‘I Dreamed a Dream’ from the production Les Miserables which is adapted according to the characterisation of the animals. The effect of this remixing is the creation of an emotional and memorable viewing experience which is achieved by the juxtaposition of the musical production’s plot (focused on the imprisonment of its characters by 19th century society), against the animation’s portrayal of animals imprisoned by 21st century poaching practices. Likewise, the video amalgamates both the animation and song’s meanings in its final frame reminding readers: “Don’t let the dream go extinct”.
youtube
Wildlife Conservation Film Festival (2016). “Dream”, Animal Conservation Warning.
There are some instances of intertextuality, however, which have been responded to controversially. One example is Ariana Grande’s chart-topper ‘7 rings’ in which she sings about a drunken trip to Tiffany’s when she and her six friends bought themselves engagement rings. The song, distinguished by its melody which is borrowed from the song ‘My Favourite Things’ (from musical production ‘The Sound of Music), has also been said to be a remix (and plagiarism) of songs by artists Princess Nokia, Souja Boy and 2 Chainz (as seen in the below remix video). Consequently, this differs from the above examples of intertextuality as not only has she remixed for her own personal gain, but the meaning of the song is arguably very different to that in the Sound of Music…a nun singing to six distressed children about cream coloured ponies in the midst of a thunder storm is very different to a millionaire singing about over-expensive rings, right?
youtube
Adamusic (2019). 7 Rings of God: Mashup of Ariane Grande.
And it doesn’t stop there. Instances of intertextuality can be seen beyond just the music industry and can date back to hundreds of years ago. Take Leonardo da Vinci’s ‘Mona Lisa’, for example. This famous painting has been around since the 16th century and has since been the product of extensive remixing. Consider these parodies of Da Vinci’s painting…as humorous as they are, they don’t exactly give credit to the original piece or carry the same artistic value… So, can we really say they deserve to be labelled and appreciated as unique pieces of art?

Parodies of Leonardo Di Vinci’s ‘Mona Lisa’. For left to right, Be Art Smart (2017), Nicholas Miles (2012), Humour Maxi Posters (2014).
Evidently, intertextuality provides internet users with the means to create and invent new ideas and perspectives by building on existing artwork. However, to truly determine whether these are innovations or merely duplicates of the originals, we must question two things: 1. Is the original meaning preserved? and 2. Does the new outcome establish something unique?
References:
Manovich, L. (2007). What comes after remix? Retrieved from: http://manovich.net/content/04-projects/057-what-comes-after-remix/54_article_2007.pdf on January, 28, 2019.
2 notes
·
View notes
Text
To Hashtag or not to Hashtag?
Is it Progression?

For 10 years now, the hashtag has been a symbol of both unity and division: with hashtags such as #MeToo and #BlackLivesMatter making breakthroughs for equality, #JeSuisCharlie and #machesterattack igniting emotional responses to terrorist attacks, and #brexit causing a huge political divide in Britain. Whoever you are, however many followers you have, with the use of a hashtag, you can both start and contribute to conversations.
The influential and popular hashtag was first championed by social media platform Twitter in 2009 when it established a filter system allowing users to search for tweets on the basis of hashtags. Consequently, the internet saw the rise of the hashtag as a method of categorising data on the basis of interests, topics, and opinions; also known as ‘Collective Intelligence’.
So, why has the hashtag gained so much prominence in the study of digital literacies?
Amongst the many symbols found on our keyboard, the hashtag is unique owing to its ability to convert the data of the online world into information which is relevant to each of us. Examples of which can be seen on the social media applications Twitter, Instagram, Pinterest and Tumblr where users’ extensive classification of the platforms’ data using hashtags, has developed a system shaped by the interests and opinions of real people. A system also referred to as a folksonomy.
However, whilst the authenticity of this system seems ideal for such digital communities which are largely user-led, there has been much controversy as to whether the hashtag is the best means of communication; and whether the restrictions (constraints) of using this symbol, outweigh its benefits (affordances). Notably, writer Cory Doctorow (2001) argues that collective tagging has three constraints; all of which I explore below:
1) People are untruthful when tagging
2) People are careless when tagging
3) People tag incompetently
Hashtagging to form identities
One of the most harmless forms of hashtagging is that used in personal posts. For example, I use hashtags in my own Twitter and Instagram posts to add information to my posts which go beyond what the Tweet and Image captions state. For example, in a recent photo that I shared of my friends and I at our annual christmas get together, I hashtagged #christmas, #mygirls and #biglove; all of which were personal comments which, had I elaborated on these comments, would have resulted in a quite soppy and amusing post! These hashtags therefore enabled me to establish an identity which demonstrated my care for my friends as well as my enjoyment of the festive season.
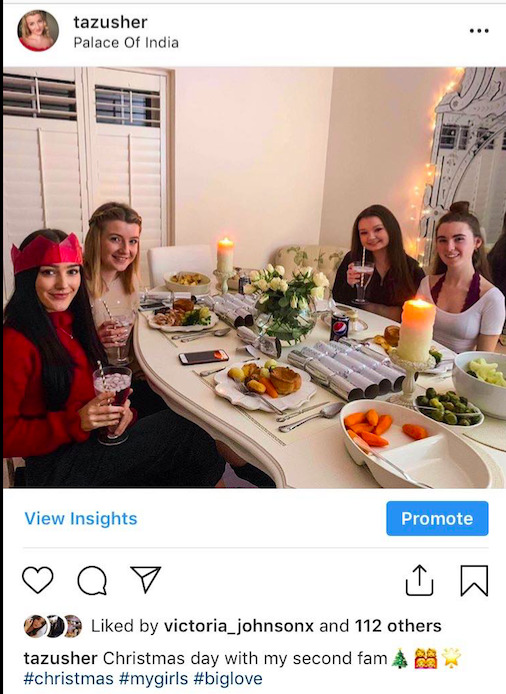
Alternatively, hashtags can also be misleading when used in this way, especially when they are used sarcastically. For example, someone might use the hashtags #lovinglife #travels #paradise at the end of a sarcastic post displaying their congested commute to work on a Monday morning. These hashtags, although used to create an identity which evokes humour, are misleading and demonstrate Doctorow’s 1st constraint. This would be particularly evident if another user used the same hashtags to search for utopian holiday destinations: the result would certainly not satisfy.
Hashtagging to debate
Nowadays, the most widely used form of hash tagging is that to contribute and ignite debate. For example, if I wanted to access updates on the latest progression of the Brexit campaign, I could search #brexit on Twitter, and immediately find updates on the campaign, as well as members of the public’s opinions. Similarly, if I wanted to narrow down my search results to receive posts related to the Leave argument only, I could search both #brexit and #leave to find tweets using both. Using multiple hashtags on Twitter can have a huge advantage for those wanting to voice their opinion. Additionally, it is also important for users to know which hashtags are trending in order to reach a wider audience. For example, the below tag cloud display the most used Brexit-related hashtags on Twitter, many of which are used collectively to extend their reach.

On the other hand, the use of hashtags to spark debate can occasionally be harmful to others and result in harassment and offence. Notably, #stopislam has been used by many extremists as an attack against the entire Muslim community. Such uses as these are a constraint of the digital tool which demonstrates the users’ carelessness and irrationality.
Hashtagging for engagement
Another common use of the hashtag is to boost engagement with digital content: commonly used in the business industry. Hashtagging is a great way for businesses to capture the interests of their target audiences, as well as reaching out to individuals who might be less likely to see their advert in a magazine or on TV. However, once again, this type of hash tagging takes skill and knowledge to receive a successful result; a skill which has become a focal point of market research.
Whilst there are some constraints of hashtagging, it is very clear that the affordances have provided users of the internet with abilities which are a progression from what we could previously do. However, next time you hashtag: THINK. Is it relevant? Is it true? Is it harmless? If so, post ahead!
Referenced sources:
Cover Image: Retrieved from: https://www.lyfemarketing.com/blog/social-media-hashtags/
Doctorow, C (2001). Metacrap: Putting the torch to seven straw-men of the meta-utopia. Retrieved from: https://people.well.com/user/doctorow/metacrap.htm#2 on January 22, 2019.
15 notes
·
View notes
Photo

This is an interesting insight to the affordances and constraints of mediation through the medium of social media. The concept of using social media to impress others is a constraint of social media which has arisen in the 21st century and has transformed into a competition for ‘perfection’ in terms of appearance, lifestyle and relationships. Consequently, this has had an extensive impact on mental health in young people, as well as a rise in verbal and emotional harassment between users. In a difference perspective, the opportunity to impact people is an affordance of social media which isn’t given enough credit. Social media can, in contrast, be used to impact people by positively inspiring them to make positive changes in their lifestyles, support and react to campaigns, and learn about world news and issues.
14 notes
·
View notes
Link
In the 21st Century, communicating is no longer just about exchanging words with someone face to face or writing a letter which they’ll receive in a weeks time. Nowadays, we have access to so many different platforms which we can communicate with each other through using digital text, emojis, and images. This animation I created to explore the affordances and constraints of some of the most popular social media platforms.
1 note
·
View note