Don't wanna be here? Send us removal request.
Text
Vertical Scaling and Horizontal Scaling: Benefits and Differences

As businesses grow and their demand for computing resources increases, ensuring their IT infrastructure can scale effectively becomes crucial. Two common approaches to scaling systems are vertical scaling and horizontal scaling. Both have their unique benefits and are suited for different types of workloads and growth patterns. Understanding the differences and the advantages of each can help businesses make informed decisions about optimizing their infrastructure.
Vertical Scaling (Scaling Up)
Vertical scaling, also known as scaling up, involves increasing the capacity of a single machine by adding more resources, such as CPU, RAM, or storage. Essentially, you are making one server more powerful to handle larger workloads.
Benefits of Vertical Scaling
Simplicity in Management Vertical scaling is easier to manage since there is only one machine or a small number of machines to configure and maintain. This reduces complexity and simplifies monitoring, updates, and maintenance tasks. As all data and processes remain on one server, managing and troubleshooting are straightforward.
Faster Implementation Upgrading an existing server with more resources like memory or processing power can be done relatively quickly. You don't need to redesign or redistribute applications across multiple servers, making vertical scaling a faster option when an immediate performance boost is required.
No Changes in Application Architecture In vertical scaling, the underlying application architecture remains unchanged. Since everything stays on a single machine, developers and system administrators do not need to make major changes to the application to handle more traffic or processing power. This makes it easier to upgrade without disrupting operations.
Cost-Efficient for Small to Medium Workloads For smaller applications or workloads, vertical scaling can be more cost-effective. Instead of investing in multiple machines, companies can maximize the potential of a single, powerful server to meet their needs.
Horizontal Scaling (Scaling Out)
Horizontal scaling, or scaling out, involves adding more machines (servers or nodes) to a system to distribute the load. Rather than making one machine more powerful, horizontal scaling allows businesses to spread workloads across multiple systems, which can be added as needed.
Benefits of Horizontal Scaling
Increased Fault Tolerance One of the major benefits of horizontal scaling is its fault tolerance. Since workloads are distributed across multiple servers, the failure of a single machine is less likely to disrupt the entire system. The system can continue to function with minimal downtime, as other servers pick up the slack.
Unlimited Scalability Unlike vertical scaling, which is limited by the physical constraints of a single machine, horizontal scaling offers virtually unlimited scalability. New machines can be added as demand grows, allowing businesses to scale infinitely in response to increasing workloads.
Cost-Effective for Large-Scale Operations For large-scale applications or enterprises handling significant traffic, horizontal scaling is often more cost-effective. Rather than investing in a high-cost, ultra-powerful server, companies can deploy several low-cost servers to handle workloads in parallel. Additionally, with cloud solutions, it’s possible to pay only for the resources used.
Improved Performance with Load Balancing Horizontal scaling often comes with load balancing mechanisms that ensure traffic is evenly distributed across multiple machines. This leads to improved performance, as no single server is overloaded. Applications can handle more users, traffic, or data processing tasks without bottlenecks.
Better Adaptation to Cloud Environments Horizontal scaling fits seamlessly with cloud environments and microservices architectures. Cloud platforms like AWS, Azure, or Google Cloud offer services that allow easy scaling out by provisioning new virtual machines on demand. This ensures businesses can scale quickly and dynamically according to real-time needs.
Vertical Scaling vs. Horizontal Scaling: Key Differences
Scalability Limitations Vertical scaling is limited by the maximum capacity of a single machine. Once the server reaches its physical limitations, you can no longer scale up. Horizontal scaling, on the other hand, allows you to keep adding machines, making it more suitable for long-term scalability.
Cost Structure Vertical scaling often involves upgrading to more powerful (and more expensive) hardware. This can lead to high upfront costs. Horizontal scaling distributes costs more evenly, allowing companies to pay for additional servers as they grow.
Performance While vertical scaling can deliver immediate performance improvements, it may become inefficient for handling large-scale, distributed workloads. Horizontal scaling distributes the load, improving performance without over-relying on a single machine.
Application Architecture Vertical scaling usually does not require significant changes to application architecture, while horizontal scaling often requires a more distributed approach. Applications must be designed to run across multiple servers or nodes in a horizontally scaled environment.
Choosing the Right Approach
When deciding between vertical and horizontal scaling, consider the size and growth potential of your business, as well as your application's architecture. For small-scale applications or those that don’t require frequent scaling, vertical scaling might be more practical. However, for businesses expecting rapid growth or handling large amounts of traffic, horizontal scaling provides a more scalable, resilient, and cost-effective solution.
Conclusion
Both vertical and horizontal scaling have their advantages depending on the specific needs of your business. Vertical scaling offers simplicity and quick upgrades, while horizontal scaling provides better long-term scalability and fault tolerance. The key is to assess your current and future needs, ensuring that your infrastructure can grow alongside your business.
0 notes
Text
What is DevOps and SRE?
DevOps (Development and Operations) and SRE (Site Reliability Engineering) are two closely related approaches aimed at improving software development, deployment, and operation processes, but they have different focuses and origins.

DevOps
Purpose: DevOps is a cultural and technical movement designed to bridge the gap between development (Dev) and operations (Ops) teams. Its primary goal is to improve collaboration, automate processes, and deliver software more quickly and reliably.
Key Principles:
Automation: Automating repetitive tasks like testing, deployment, and infrastructure management.
Continuous Integration/Continuous Deployment (CI/CD): Frequent integration of code changes and automatic deployment to production environments.
Collaboration: Breaking down silos between development, operations, and other teams to improve communication and efficiency.
Monitoring and Feedback: Continuous monitoring of applications and infrastructure, with feedback loops to improve performance and stability.
Tools: Jenkins, Docker, Kubernetes, Ansible, Terraform, Git, etc.
SRE (Site Reliability Engineering)
Purpose: SRE is an approach that originated at Google and focuses on applying software engineering practices to infrastructure and operations problems. The goal of SRE is to create scalable and highly reliable software systems.
Key Principles:
Reliability as a Priority: SRE teams focus on maintaining the reliability, availability, and performance of services.
Service Level Objectives (SLOs) and Service Level Indicators (SLIs): SREs define and measure reliability targets, like uptime and latency, to ensure the system meets user expectations.
Error Budgets: A concept where a certain amount of failure is acceptable. This allows for a balance between innovation (deploying new features) and reliability (stability of the system).
Automation and Engineering: SREs automate manual tasks and apply engineering solutions to operational problems, reducing toil and improving system resilience.
Tools: Prometheus, Grafana, Google’s Borg, Terraform, Jenkins, Kubernetes, etc.
Differences and Overlaps
Focus: DevOps is broader, focusing on the overall software development lifecycle, while SRE is specifically concerned with the reliability and performance of production systems.
Culture vs. Engineering: DevOps emphasizes cultural changes to improve collaboration, while SRE applies engineering practices to solve operational challenges.
Origin: DevOps emerged as a movement to improve collaboration between Dev and Ops teams. SRE was developed by Google to manage large-scale systems and has a strong focus on reliability and automation.
In Practice
Both approaches are often used together. DevOps practices can lead to the fast and reliable deployment of code, while SRE ensures that the deployed systems are highly reliable and scalable.
0 notes
Text
Kubernetes Security Best Practices: Safeguarding Your Containerized Applications

Kubernetes has revolutionized the way we deploy, manage, and scale containerized applications. However, with its growing adoption comes the critical need to ensure robust security practices to protect your infrastructure and data. Here are some essential Kubernetes security best practices to help you safeguard your containerized applications.
1. Network Policies
Implementing network policies is crucial for controlling traffic between pods. Kubernetes network policies allow you to define rules for inbound and outbound traffic at the pod level. By default, Kubernetes allows all traffic between pods, which can be a security risk. Use network policies to create a zero-trust network, where only explicitly permitted traffic is allowed.
2. Role-Based Access Control (RBAC)
RBAC is vital for managing who can access and perform actions within your Kubernetes cluster. Assign roles based on the principle of least privilege, ensuring that users and service accounts only have the permissions they need to perform their tasks. Regularly review and audit RBAC policies to maintain tight security.
3. Pod Security Policies
Pod Security Policies (PSPs) help enforce security standards at the pod level. PSPs can control aspects such as whether privileged containers can run, what volume types can be used, and which users can run containers. Although PSPs are being deprecated in future Kubernetes releases, consider using alternative tools like Open Policy Agent (OPA) or Kubernetes Pod Security Standards (PSS).
4. Image Security
Ensuring the security of container images is paramount. Use trusted sources for your base images and regularly update them to include security patches. Implement image scanning tools to detect vulnerabilities and misconfigurations in your images before deploying them. Tools like Clair, Trivy, and Aqua Security can help automate this process.
5. Secrets Management
Kubernetes Secrets are used to store sensitive information, such as passwords and API keys. However, storing secrets directly in environment variables or configuration files can expose them to potential attackers. Use Kubernetes Secrets to manage sensitive data and consider integrating with external secrets management solutions like HashiCorp Vault or AWS Secrets Manager for enhanced security.
6. Audit Logging
Enable and configure audit logging to track and monitor activities within your Kubernetes cluster. Audit logs provide valuable insights into who did what, when, and where, which is essential for detecting and responding to security incidents. Use tools like Fluentd, Elasticsearch, and Kibana to aggregate and analyze audit logs.
7. Cluster Hardening
Hardening your Kubernetes cluster involves securing the underlying infrastructure and configurations. Ensure your Kubernetes components, such as the API server, kubelet, and etcd, are securely configured. Disable insecure features, enforce HTTPS, and restrict access to the API server. Regularly update your Kubernetes components to the latest stable versions to incorporate security patches and improvements.
8. Resource Quotas and Limits
Set resource quotas and limits to prevent resource abuse and Denial-of-Service (DoS) attacks. By defining limits on CPU, memory, and other resources, you can ensure that no single pod or user consumes excessive resources, potentially impacting the stability and security of your cluster.
9. Namespace Segmentation
Segment your Kubernetes cluster using namespaces to isolate different applications or teams. Namespaces provide logical separation within a cluster, allowing you to apply security policies and resource quotas at a granular level. This helps contain potential security breaches and limits the blast radius of an attack.
10. Regular Security Audits and Penetration Testing
Conduct regular security audits and penetration testing to identify and address vulnerabilities in your Kubernetes cluster. Automated security scanning tools can help, but manual audits and penetration testing by skilled security professionals provide an additional layer of assurance. Regular assessments help you stay ahead of emerging threats and maintain a robust security posture.
Conclusion
Securing your Kubernetes environment is an ongoing process that requires vigilance, regular updates, and adherence to best practices. By implementing these Kubernetes security best practices, you can significantly reduce the risk of security breaches and ensure the safety of your containerized applications. Stay informed about the latest security trends and continuously improve your security measures to protect your infrastructure and data.
0 notes
Text
What is a Managed Service Provider?

A Managed Service Provider (MSP) is a third-party company that remotely manages a client's IT infrastructure and end-user systems on a proactive basis, typically under a subscription model. MSPs are an integral part of modern business strategies, providing specialized services that enhance operational efficiency, reduce costs, and allow companies to focus on their core competencies.
The Role of an MSP
MSPs cover a wide array of IT services, including:
Network Management:
MSPs ensure that a company's network infrastructure is secure, efficient, and reliable. This includes monitoring network performance, managing firewalls, and ensuring data security.
Data Backup and Recovery:
They provide robust data backup solutions and disaster recovery plans to safeguard a company’s critical information against data loss or breaches.
Cybersecurity:
MSPs implement comprehensive cybersecurity measures, including threat detection, antivirus protection, and regular security audits to protect against cyber threats.
Cloud Services:
Managed Service Providers assist in migrating to and managing cloud platforms, optimizing the use of cloud resources, and ensuring seamless integration with existing systems.
IT Support and Helpdesk:
They offer round-the-clock IT support and helpdesk services to resolve technical issues swiftly, ensuring minimal downtime and enhanced productivity.
Software and Hardware Management:
MSPs manage software updates, license renewals, and hardware maintenance, ensuring that all IT assets are up-to-date and functioning optimally.
Benefits of Using an MSP
Cost Efficiency:
By outsourcing IT management to an MSP, companies can reduce the need for an in-house IT team, thereby cutting costs associated with salaries, training, and infrastructure.
Expertise and Experience:
MSPs bring a wealth of expertise and experience, ensuring that businesses benefit from the latest technologies and best practices in IT management.
Scalability:
Managed Service Providers offer scalable solutions that can grow with your business, providing the flexibility to adjust services as needs evolve.
Proactive Monitoring:
MSPs provide proactive monitoring and maintenance, identifying and addressing potential issues before they become significant problems, thus preventing downtime and enhancing system reliability.
Focus on Core Business:
By entrusting IT management to an MSP, companies can focus more on their core business activities, driving growth and innovation without being bogged down by IT concerns.
Choosing the Right MSP
Selecting the right Managed Service Provider is crucial for maximizing the benefits. Here are some factors to consider:
Service Level Agreements (SLAs):
Ensure that the MSP offers clear and comprehensive SLAs that outline the scope of services, performance metrics, and response times.
Industry Experience:
Choose an MSP with experience in your industry to ensure they understand your specific needs and regulatory requirements.
Reputation and References:
Research the MSP's reputation and seek references from current or past clients to gauge their reliability and service quality.
Technology Stack:
Verify that the MSP uses advanced technologies and tools that align with your business needs and goals.
Security Measures:
Ensure that the MSP has robust cybersecurity measures in place to protect your data and systems.
Conclusion
A Managed Service Provider can be a game-changer for businesses looking to enhance their IT operations while reducing costs and focusing on growth. By leveraging the expertise, proactive management, and scalable solutions offered by MSPs, companies can ensure their IT infrastructure is robust, secure, and aligned with their business objectives. Whether you are a small business or a large enterprise, partnering with the right MSP can provide significant strategic advantages in today’s technology-driven world.
1 note
·
View note
Text
Why Cloud Modernization is Crucial in 2024

In 2024, cloud modernization has become a strategic imperative for businesses aiming to stay competitive, agile, and innovative. As digital transformation accelerates across industries, leveraging advanced cloud technologies and modernizing legacy systems is no longer optional but essential for survival and growth. Here’s why cloud modernization holds paramount importance this year:
1. Enhanced Efficiency and Scalability
Cloud modernization allows organizations to move away from outdated on-premises infrastructure to more efficient, scalable cloud environments. Modern cloud platforms offer auto-scaling capabilities, enabling businesses to handle varying workloads seamlessly. This flexibility ensures that companies can quickly respond to changing market demands without the constraints of traditional infrastructure limitations.
2. Cost Optimization
One of the most compelling reasons for cloud modernization is cost efficiency. By migrating to the cloud, businesses can reduce capital expenditure on hardware and minimize operational costs associated with maintaining and upgrading legacy systems. Cloud service providers offer pay-as-you-go models, allowing organizations to pay only for the resources they use. This shift from fixed to variable costs helps optimize budgets and improve financial planning.
3. Improved Security and Compliance
In 2024, data security and regulatory compliance are top priorities for businesses. Modern cloud platforms offer advanced security features, including encryption, identity and access management, and continuous monitoring, which are often superior to traditional on-premises solutions. Additionally, leading cloud providers ensure compliance with global standards and regulations, reducing the burden on organizations to manage these complex requirements independently.
4. Fostering Innovation and Agility
Cloud modernization fosters a culture of innovation by providing access to cutting-edge technologies such as artificial intelligence (AI), machine learning (ML), and big data analytics. These technologies enable businesses to develop innovative products and services, streamline operations, and gain deeper insights into customer behavior. Moreover, the cloud’s agility allows for faster deployment of applications and services, reducing time-to-market and enabling rapid iteration based on customer feedback.
5. Supporting Remote and Hybrid Workforces
The shift towards remote and hybrid work models, accelerated by the global pandemic, has made cloud modernization even more critical. Cloud-based solutions provide the necessary infrastructure for remote collaboration, ensuring employees can access essential tools and data from anywhere. This capability enhances productivity and supports a flexible work environment, which is increasingly important for attracting and retaining top talent.
6. Sustainability and Environmental Impact
As organizations become more environmentally conscious, cloud modernization offers a pathway to more sustainable operations. Cloud service providers are investing heavily in renewable energy and efficient data center operations, helping businesses reduce their carbon footprint. By moving to the cloud, companies can contribute to global sustainability efforts and meet corporate social responsibility goals.
7. Enhanced Disaster Recovery and Business Continuity
Modern cloud platforms provide robust disaster recovery solutions that ensure business continuity in the event of data loss or system failures. Cloud-based backup and recovery services enable organizations to quickly restore critical data and applications, minimizing downtime and protecting against potential financial losses. This reliability is crucial in maintaining trust with customers and partners.
Conclusion
In 2024, cloud modernization is not just a technological upgrade but a strategic necessity for businesses aiming to thrive in a digital-first world. By enhancing efficiency, optimizing costs, improving security, fostering innovation, supporting remote work, promoting sustainability, and ensuring business continuity, cloud modernization empowers organizations to navigate the complexities of the modern business landscape. As companies continue to evolve and adapt, embracing cloud modernization will be key to unlocking future growth and success.
0 notes
Text
The Evolution of Cloud Managed Services: A Glimpse into 2024 and Beyond

In the rapidly evolving landscape of technology, Cloud Managed Services (CMS) continue to play a pivotal role in driving innovation, efficiency, and scalability for businesses across industries. As we delve into 2024 and beyond, the trajectory of CMS is poised for unprecedented growth and transformation.
Enhanced Automation and AI Integration: As businesses embrace digital transformation at an accelerated pace, the demand for automation and AI-driven solutions within CMS is on the rise. In 2024 and beyond, we can expect to witness a significant surge in the integration of artificial intelligence and machine learning capabilities within CMS platforms. This integration will not only streamline operational processes but also empower businesses with predictive analytics, proactive problem resolution, and intelligent decision-making capabilities.
Hyper-Personalization and Customization: The era of one-size-fits-all solutions is gradually fading away, giving rise to hyper-personalization and customization within CMS offerings. In the coming years, CMS providers will focus on delivering tailored solutions that cater to the unique needs and preferences of individual businesses. From customized service catalogs to personalized SLAs (Service Level Agreements), businesses can expect CMS platforms to adapt and evolve according to their specific requirements, driving greater efficiency and value.
Multi-Cloud Management and Interoperability: With the proliferation of multi-cloud environments, managing and orchestrating workloads across disparate cloud platforms has become increasingly complex. In response to this challenge, CMS providers are doubling down on multi-cloud management solutions that offer seamless interoperability and centralized control across hybrid and multi-cloud environments. In 2024 and beyond, businesses can leverage CMS platforms to effortlessly migrate, deploy, and manage workloads across various cloud providers, ensuring optimal performance, scalability, and cost-efficiency.
Focus on Security and Compliance: As cybersecurity threats continue to evolve in sophistication and scale, ensuring robust security and compliance measures within CMS environments remains paramount. In the years ahead, CMS providers will prioritize the integration of advanced security protocols, threat detection mechanisms, and compliance frameworks to safeguard sensitive data and mitigate cyber risks effectively. From data encryption and identity access management to regulatory compliance automation, businesses can entrust CMS platforms to fortify their cloud infrastructures against emerging threats and regulatory requirements.
Sustainable and Eco-Friendly Practices: As environmental sustainability takes center stage on the global agenda, businesses are increasingly mindful of the environmental impact of their operations, including cloud infrastructure. In the years ahead, CMS providers will embrace sustainable practices and eco-friendly initiatives to minimize carbon footprints and promote environmental stewardship. From energy-efficient data centers to carbon-neutral operations, businesses can align with CMS platforms that prioritize sustainability, contributing to a greener and more sustainable future.
In conclusion, the landscape of Cloud Managed Services is poised for remarkable growth, innovation, and evolution in 2024 and beyond. By embracing automation, hyper-personalization, multi-cloud management, security, and sustainability, businesses can leverage CMS platforms to unlock new opportunities, drive operational excellence, and navigate the complexities of the digital age with confidence and agility.
0 notes
Text
Safeguarding Your Assets: Exploring Cloud Security on AWS
In the realm of modern technology, cloud computing has emerged as a game-changer, offering unparalleled flexibility, scalability, and efficiency to businesses worldwide. However, as organizations increasingly rely on cloud services to store sensitive data and run critical applications, ensuring robust security measures becomes paramount. In this article, we'll delve into the intricacies of cloud security on Amazon Web Services (AWS) and explore the best practices for safeguarding your assets in the cloud.
Understanding Cloud Security on AWS: Amazon Web Services (AWS) is a leading cloud computing platform that provides a vast array of services, ranging from compute and storage to networking and security. While AWS offers a highly secure infrastructure, it's essential for organizations to implement additional security measures to protect their data and applications from potential threats.
Key Security Features of AWS: AWS offers a comprehensive set of security features and tools to help organizations build a secure and compliant environment in the cloud. Some of the key security features provided by AWS include:
Identity and Access Management (IAM): IAM allows organizations to manage user identities and access permissions for AWS resources. With IAM, organizations can create and manage user accounts, assign permissions, and enforce multi-factor authentication to enhance security.
Network Security: AWS provides various networking features, such as Virtual Private Cloud (VPC), Security Groups, and Network Access Control Lists (NACLs), to secure network traffic and control access to resources. These features enable organizations to create secure network architectures and enforce firewall rules to protect against unauthorized access.
Data Encryption: AWS offers robust encryption capabilities to protect data both at rest and in transit. Organizations can use services like AWS Key Management Service (KMS) to manage encryption keys and encrypt data stored in AWS services such as Amazon S3, Amazon RDS, and Amazon EBS.
Compliance and Governance: AWS adheres to industry-standard security certifications and compliance frameworks, such as SOC 2, ISO 27001, and HIPAA, to ensure the security and privacy of customer data. Additionally, AWS provides services like AWS Config and AWS CloudTrail to monitor and audit AWS resource configurations and API activity for compliance purposes.
Best Practices for Cloud Security on AWS: While AWS offers robust security features, implementing best practices is essential to enhance the security posture of your cloud environment. Some of the key best practices for cloud security on AWS include:
Implementing Least Privilege Access: Follow the principle of least privilege to grant users only the permissions they need to perform their job roles. Use IAM policies to enforce granular access controls and regularly review permissions to prevent unauthorized access.
Securing Data with Encryption: Encrypt sensitive data both at rest and in transit using strong encryption algorithms and key management practices. Utilize AWS services like AWS KMS and AWS CloudHSM to manage encryption keys securely.
Enforcing Network Security Controls: Configure security groups and network ACLs to control inbound and outbound traffic to your AWS resources. Use VPC flow logs to monitor network traffic and detect potential security threats.
Monitoring and Logging: Enable logging and monitoring features like AWS CloudTrail, Amazon CloudWatch, and AWS Config to monitor resource activity, detect security incidents, and ensure compliance with security policies.
Regularly Updating and Patching: Keep your AWS resources and software up to date by applying security patches and updates regularly. Utilize AWS services like AWS Systems Manager to automate patch management and ensure timely updates across your environment.
Conclusion: In conclusion, cloud security on AWS is a shared responsibility between AWS and the customer. While AWS provides a secure and compliant infrastructure, organizations must implement additional security measures and best practices to protect their data and applications in the cloud. By understanding the key security features of AWS and following best practices for cloud security, organizations can build a robust security posture and mitigate potential security risks in the cloud.
0 notes
Text
The In-Depth Benefits of Cloud Adoption in Retail

The retail landscape is undergoing a transformative journey, with cloud adoption emerging as a game-changer for businesses seeking agility, scalability, and enhanced customer experiences. In this comprehensive exploration, we delve into the multifaceted benefits that cloud technology brings to the retail sector, revolutionizing operations, optimizing costs, and fostering innovation.
1. Enhanced Flexibility and Scalability: Cloud adoption empowers retail businesses with unparalleled flexibility and scalability. Retailers can dynamically adjust computing resources based on demand fluctuations, ensuring seamless operations during peak seasons and optimizing costs during quieter periods.
2. Seamless Multi-Channel Integration: Cloud solutions enable retailers to break down silos and integrate various sales channels seamlessly. Whether through in-store transactions, e-commerce platforms, or mobile applications, a unified cloud infrastructure facilitates a cohesive customer experience, driving customer satisfaction and loyalty.
3. Data-Driven Decision-Making: Harnessing the power of cloud analytics, retailers can glean valuable insights from vast amounts of data. This data-driven approach enhances decision-making processes, enabling retailers to understand customer behavior, optimize inventory management, and tailor marketing strategies for maximum impact.
4. Improved Inventory Management: Cloud-based inventory management systems bring efficiency to retail operations. Real-time visibility into stock levels, automated reorder processes, and predictive analytics contribute to reduced stockouts, minimized overstock situations, and overall improved inventory accuracy.
5. Enhanced Security Measures: Cloud providers prioritize robust security protocols, safeguarding sensitive customer and business data. Retailers benefit from advanced encryption, secure payment gateways, and compliance with industry regulations, instilling trust among customers and protecting the integrity of the business.
6. Accelerated Innovation and Time-to-Market: Cloud adoption facilitates rapid deployment of new applications and services, reducing time-to-market for retail innovations. Retailers can swiftly implement and test new features, respond to market trends, and stay ahead of the competition in the fast-paced retail landscape.
7. Cost Optimization and Resource Efficiency: The cloud's pay-as-you-go model allows retailers to optimize costs by only paying for the resources they use. This eliminates the need for significant upfront investments in physical infrastructure, reducing capital expenditures and providing a cost-effective solution for businesses of all sizes.
8. Seamless Customer Experience: Cloud technology enables retailers to deliver a seamless and personalized customer experience. From personalized recommendations based on purchase history to efficient order fulfillment and real-time customer support, the cloud enhances every touchpoint in the customer journey.
9. Agility in Adapting to Market Trends: Cloud adoption equips retailers with the agility to adapt swiftly to changing market trends. From introducing new products to adjusting pricing strategies, retailers can respond promptly to market dynamics, ensuring they remain relevant and competitive.
10. Collaborative Ecosystems and Integration: Cloud-based platforms facilitate collaboration within the retail ecosystem. Retailers can seamlessly integrate with suppliers, logistics partners, and other stakeholders, fostering a collaborative environment that enhances efficiency and reduces operational friction.
In conclusion, the benefits of cloud adoption in the retail sector extend far beyond mere technological advancements. The cloud is a strategic enabler, revolutionizing how retailers operate, connect with customers, and navigate the evolving landscape. As retail continues to evolve, those embracing cloud technology are well-positioned to unlock new levels of growth, efficiency, and innovation
0 notes
Text
Resource Organization in the Cloud: A Comprehensive Analysis of Azure, AWS, and Google Cloud
The cloud computing landscape is dominated by three major players—Microsoft Azure, Amazon Web Services (AWS), and Google Cloud.

As businesses migrate to the cloud, efficient resource organization becomes crucial for optimizing performance, managing costs, and ensuring security. This in-depth analysis explores how Azure, AWS, and Google Cloud handle resource organization, comparing their respective services, features, and best practices.
I. Resource Organization Models:
A. Azure: 1. Resource Groups: Azure organizes resources within Resource Groups, which act as logical containers. These groups simplify management, enabling users to apply consistent policies and access controls.
2. Azure Policy: Azure Policy allows organizations to enforce compliance by defining and applying policies across resource groups. This ensures standardized resource configurations.
B. AWS: 1. AWS Organizations: AWS uses Organizations to consolidate multiple AWS accounts into an organizational unit. This facilitates central management of billing, access controls, and policies across accounts.
2. Tagging: AWS emphasizes tagging for resource organization. Tags provide metadata, making it easier to categorize and track resources for cost allocation and management.
C. Google Cloud: 1. Projects and Resource Hierarchy: Google Cloud uses Projects as the primary organizational unit. Resources are organized hierarchically within projects, allowing for granular control and management.
2. Resource Labels: Similar to tagging in AWS, Google Cloud utilizes labels for resource categorization. Labels enhance visibility and simplify resource tracking.
II. Identity and Access Management (IAM):
A. Azure: 1. Azure Active Directory: Azure leverages Azure AD for identity management. Users and groups are assigned roles to control access to resources.
2. Role-Based Access Control (RBAC): RBAC in Azure allows fine-grained access control, enabling administrators to grant permissions based on roles assigned to users.
B. AWS: 1. AWS Identity and Access Management (IAM): IAM is central to AWS's identity management. Policies are attached to IAM users, groups, or roles to define permissions.
2. Cross-Account Access: AWS allows cross-account access through IAM roles, facilitating resource sharing across accounts.
C. Google Cloud: 1. Google Cloud Identity and Access Management (IAM): Google Cloud IAM governs access control. Policies are attached to members, defining their permissions.
2. Primitive and Predefined Roles: Google Cloud provides primitive and predefined roles, offering flexibility in assigning permissions at different levels of granularity.
III. Networking and Resource Connectivity:
A. Azure: 1. Azure Virtual Network: Azure Virtual Network allows the creation of isolated networks. Resources can connect securely within these virtual networks.
2. Azure ExpressRoute: ExpressRoute facilitates private connectivity between on-premises infrastructure and Azure, ensuring secure and dedicated network connections.
B. AWS: 1. Amazon VPC: Amazon VPC is the networking backbone in AWS. It allows users to create isolated virtual networks with customizable IP ranges.
2. Direct Connect: AWS Direct Connect establishes dedicated network connections between on-premises and AWS, providing consistent network performance.
C. Google Cloud: 1. Virtual Private Cloud (VPC): Google Cloud VPC enables the creation of isolated networks. Subnets, routes, and firewalls provide control over resource connectivity.
2. Cloud Interconnect: Google Cloud Interconnect establishes direct and dedicated connections between on-premises networks and Google Cloud, ensuring reliable and fast connectivity.
IV. Resource Monitoring and Optimization:
A. Azure: 1. Azure Monitor: Azure Monitor provides comprehensive monitoring solutions, including metrics, logs, and alerts. It allows organizations to gain insights into resource performance and availability.
2. Azure Cost Management and Billing: Azure Cost Management helps organizations optimize spending by providing insights into resource costs and usage.
B. AWS: 1. Amazon CloudWatch: CloudWatch is AWS's monitoring service, offering a wide range of metrics, logs, and alarms for resources. It enables proactive management of resource performance.
2. AWS Cost Explorer: AWS Cost Explorer provides cost analysis and forecasting tools, assisting organizations in optimizing their cloud spending.
C. Google Cloud: 1. Stackdriver Monitoring: Stackdriver Monitoring in Google Cloud offers extensive monitoring capabilities, including dashboards, alerts, and logging. It ensures visibility into resource health.
2. Google Cloud Billing: Google Cloud Billing provides insights into resource costs, helping organizations track and optimize their cloud expenditure.
V. Data Storage and Management:
A. Azure: 1. Azure Blob Storage: Azure Blob Storage is designed for scalable object storage. It supports various data types, making it suitable for diverse storage needs.
2. Azure Data Lake Storage: Azure Data Lake Storage is optimized for big data analytics, enabling the storage and analysis of large datasets.
B. AWS: 1. Amazon S3: Amazon S3 is a widely-used object storage service in AWS. It provides scalable and durable storage with various storage classes for different use cases.
2. Amazon Glacier: For archival and long-term storage, Amazon Glacier offers a cost-effective solution with retrieval options.
C. Google Cloud: 1. Cloud Storage: Google Cloud Storage provides scalable and durable object storage. It offers different storage classes based on access frequency and retrieval speed.
2. Cloud Bigtable: For large-scale, NoSQL data, Cloud Bigtable offers a highly scalable and performant solution.
VI. Conclusion:
The comparison of resource organization in Azure, AWS, and Google Cloud reveals that each cloud provider offers a distinct set of tools and features to meet the diverse needs of organizations. While Azure emphasizes resource groups and policies, AWS prioritizes IAM and tagging, and Google Cloud focuses on projects and resource labels. Understanding the nuances of these models is crucial for businesses seeking to leverage the cloud effectively. From identity management and networking to monitoring and storage, each cloud provider brings its strengths to the table. The choice between Azure, AWS, and Google Cloud depends on the specific requirements, preferences, and priorities of the organization, underscoring the importance of a well-informed decision in the ever-evolving landscape of cloud computing.
0 notes
Text
Exploring Comprehensive Data Protection on AWS
In the digital age, where data is the lifeblood of organizations, ensuring robust data protection measures is paramount.

Amazon Web Services (AWS), a leading cloud service provider, takes on the role of a guardian, offering a suite of comprehensive tools and features to safeguard the confidentiality, integrity, and availability of data hosted on its platform. This in-depth article explores the multifaceted aspects of data protection on AWS, providing insights into the measures and best practices that organizations can employ to fortify their data against potential threats.
I. Introduction
In an era marked by the proliferation of data and the omnipresence of digital assets, the significance of robust data protection cannot be overstated. AWS, as a major player in the cloud computing domain, plays a pivotal role in championing data protection through an array of services and features designed to address the evolving needs and challenges faced by businesses in safeguarding their information.
II. Secure Data Storage and Encryption
A. S3 Data Encryption: Amazon Simple Storage Service (S3), a cornerstone of AWS, provides native encryption capabilities to protect data at rest. Organizations can leverage server-side encryption options, including Amazon S3 Managed Keys (SSE-S3), AWS Key Management Service (SSE-KMS), or even customer-provided keys (SSE-C).
B. EBS Volume Encryption: AWS Elastic Block Store (EBS) volumes, commonly used for storage in EC2 instances, support encryption for data at rest. By enabling EBS volume encryption, organizations add an additional layer of protection to sensitive data stored within these volumes.
III. Network Security and Access Controls
A. Virtual Private Cloud (VPC): AWS VPC allows organizations to create isolated, private networks in the cloud. By defining network architecture, controlling inbound and outbound traffic, and implementing security groups and Network Access Control Lists (NACLs), businesses can establish a secure network environment.
B. Identity and Access Management (IAM): AWS IAM enables organizations to manage user access to AWS resources securely. By defining granular permissions, enforcing the principle of least privilege, and implementing multi-factor authentication (MFA), businesses can ensure that only authorized personnel have access to critical data.
IV. Data Lifecycle Management and Backups
A. Amazon Glacier for Archival: AWS Glacier serves as a cost-effective solution for archival storage. By implementing lifecycle policies, organizations can automatically transition data to Glacier for long-term retention, ensuring compliance with data governance requirements.
B. Amazon RDS Automated Backups: AWS Relational Database Service (RDS) offers automated backups for relational databases. Organizations can configure backup retention periods, enabling point-in-time recovery to restore databases to specific timestamps in case of data corruption or loss.
V. Threat Detection and Monitoring
A. Amazon GuardDuty: GuardDuty is a managed threat detection service that continuously monitors for malicious activity in AWS environments. Leveraging machine learning and anomaly detection, GuardDuty alerts organizations to potential security threats, helping them respond promptly.
B. CloudWatch Logs and Metrics: AWS CloudWatch provides logging and monitoring capabilities to track system and application performance. By monitoring logs and setting up custom metrics, organizations gain insights into activities and potential security incidents, enhancing their ability to detect and respond to threats.
VI. Compliance and Data Governance
A. AWS Key Management Service (KMS): KMS is a fully managed encryption service that assists organizations in meeting data compliance requirements. By centrally managing encryption keys, organizations maintain control over data access and encryption policies, ensuring compliance with regulations.
B. AWS Artifact: AWS Artifact provides on-demand access to compliance documentation, including reports and certifications. Organizations can utilize this resource to verify AWS's adherence to various industry standards and regulations, enhancing their own compliance posture.
VII. Disaster Recovery Planning
A. Amazon S3 Versioning: S3 versioning allows organizations to preserve, retrieve, and restore every version of every object stored in a bucket. By enabling versioning, businesses can safeguard against accidental deletions or modifications, providing a comprehensive backup mechanism.
B. AWS Disaster Recovery Solutions: AWS offers various disaster recovery solutions, such as AWS Backup and AWS Disaster Recovery. These services enable organizations to implement robust backup and recovery strategies, ensuring business continuity in the face of unforeseen events.
VIII. Conclusion
As organizations increasingly migrate their operations to the cloud, the responsibility of safeguarding sensitive data becomes a shared endeavor between businesses and their cloud service providers. AWS, with its extensive array of data protection tools and features, empowers organizations to navigate the complexities of the digital landscape securely. By implementing best practices in secure storage, encryption, access controls, and monitoring, businesses can harness the full potential of AWS while maintaining the confidentiality, integrity, and availability of their critical data. As data continues to be a driving force in the digital transformation journey, the robust data protection measures provided by AWS serve as a pillar of trust for businesses seeking to thrive in the cloud era.
0 notes
Text
The Synergy of AI and ML in Cloud Computing
As we stand on the precipice of technological evolution, the convergence of Artificial Intelligence (AI) and Machine Learning (ML) with Cloud Computing emerges as a transformative force, reshaping the way businesses operate and innovate.

This article explores the seamless integration of AI and ML into the realm of Cloud Computing and the profound impact it promises across various industries.
Enhanced Efficiency and Automation: The marriage of AI and ML with Cloud Computing introduces unparalleled efficiency through automation. Algorithms learn from data patterns and autonomously optimize cloud resources, streamlining processes, and reducing manual intervention, thereby enhancing operational efficiency.
Scalability and Flexibility: Cloud Computing inherently offers scalability, and when coupled with AI and ML capabilities, organizations can dynamically scale resources based on evolving demands. This adaptability ensures optimal performance without the need for extensive manual adjustments, supporting businesses in their growth journey.
Intelligent Data Insights: AI and ML algorithms embedded in cloud platforms unlock the power of intelligent data insights. By analyzing vast datasets, these technologies provide actionable intelligence, enabling businesses to make informed decisions, predict trends, and derive valuable insights for strategic planning.
Improved Security Protocols: The integration of AI and ML strengthens security protocols in Cloud Computing. These technologies can detect anomalies, identify potential threats, and respond in real-time to cyberattacks, fortifying the overall security posture of cloud environments and safeguarding sensitive data.
Personalized User Experiences: Incorporating AI and ML in Cloud Computing facilitates the delivery of personalized user experiences. From recommendation engines to customized interfaces, these technologies leverage cloud resources to tailor services based on individual preferences, fostering customer engagement and satisfaction.
Accelerated Development and Deployment: AI and ML streamline the development and deployment of applications in the cloud. Automated processes, such as model training and deployment pipelines, reduce time-to-market, enabling organizations to innovate rapidly and stay competitive in the dynamic digital landscape.
Cost Optimization: Cloud cost management receives a significant boost with AI and ML. These technologies analyze usage patterns, identify cost-saving opportunities, and optimize resource allocation, ensuring that organizations extract maximum value from their cloud investments while minimizing unnecessary expenses.
Predictive Maintenance: In industries leveraging IoT devices, AI and ML integrated with Cloud Computing enable predictive maintenance. By analyzing real-time data from connected devices, these technologies anticipate equipment failures, reducing downtime, and enabling proactive maintenance strategies.
Democratization of AI: Cloud-based AI and ML services democratize access to advanced technologies. Small and medium-sized enterprises can harness the power of AI without significant infrastructure investments, leveling the playing field and fostering innovation across diverse sectors.
Continuous Evolution: The synergy of AI and ML with Cloud Computing is not static; it represents a journey of continuous evolution. As algorithms learn and adapt over time, the capabilities of these technologies will further refine, driving unprecedented advancements and setting the stage for the future of intelligent, cloud-based solutions.
In conclusion, the amalgamation of AI and ML with Cloud Computing marks a paradigm shift, propelling industries toward a future where intelligent, data-driven decision-making becomes the norm. The transformative impact of this synergy is not merely technological; it's a catalyst for innovation, efficiency, and a new era of possibilities across the vast spectrum of human endeavors.
0 notes
Text
Embarking on a Seamless Journey to the Cloud with Blazeclan Technologies
In an era dominated by digital transformation, businesses are increasingly recognizing the strategic value of migrating to the cloud.

As organizations navigate this complex journey, having a trusted partner by their side becomes paramount. Blazeclan Technologies emerges as a beacon in the cloud consulting landscape, guiding enterprises towards a seamless and transformative journey to the cloud.
Understanding the Cloud Advantage:
The cloud is not merely a technological shift; it's a paradigm that reshapes how businesses operate and innovate. Blazeclan, with its wealth of experience and expertise, understands the nuances of this shift. From enhanced scalability to improved agility, the cloud offers a myriad of benefits that can drive operational efficiency and foster innovation.
Tailored Solutions for Unique Needs:
One of the hallmarks of Blazeclan's approach is its commitment to understanding each client's unique requirements. The journey to the cloud is not one-size-fits-all, and Blazeclan excels in crafting tailored solutions that align with specific business goals. Whether it's a startup venturing into the cloud for the first time or an established enterprise looking to optimize its cloud environment, Blazeclan adapts its strategies to suit diverse needs.
Comprehensive Cloud Services:
Blazeclan's suite of cloud services spans the entire spectrum of cloud adoption. From initial assessments and strategy development to seamless migration and ongoing management, Blazeclan ensures a holistic and comprehensive approach. Their services encompass leading cloud platforms such as AWS, Azure, and GCP, providing clients with flexibility and choice.
Ensuring Security and Compliance:
Security concerns often top the list of challenges when considering a move to the cloud. Blazeclan, as a trusted partner, prioritizes security and compliance. Their robust solutions incorporate industry best practices to safeguard data and ensure compliance with regulatory standards. This focus on security provides clients with the confidence to embrace the cloud without compromising on data integrity.
Driving Innovation and Cost Optimization:
Beyond the technical aspects, Blazeclan is committed to driving innovation and optimizing costs for its clients. The cloud presents opportunities for innovation, and Blazeclan helps businesses leverage these possibilities. Simultaneously, they work diligently to optimize cloud costs, ensuring that the benefits of the cloud extend to the financial bottom line.
Customer Success Stories:
The true testament to Blazeclan's prowess lies in the success stories of its clients. From accelerated time-to-market to improved resource utilization, businesses partnering with Blazeclan have achieved remarkable outcomes. These success stories underscore the effectiveness of Blazeclan's approach in navigating the intricate journey to the cloud.
Conclusion:
Embarking on a journey to the cloud is a strategic imperative in today's dynamic business landscape. Blazeclan Technologies, with its unwavering commitment to excellence, emerges as a reliable guide in this transformative expedition. By combining technological expertise, tailored solutions, and a customer-centric approach, Blazeclan paves the way for businesses to thrive in the digital age.
In choosing Blazeclan as your cloud consulting partner, you're not just adopting a service; you're investing in a collaborative journey towards innovation, efficiency, and sustained success in the cloud.
0 notes
Text
Fortifying the Cloud with Enhanced Security Through Identity and Access Management
As organizations increasingly migrate their operations to the cloud, ensuring robust security measures becomes paramount.

Identity and Access Management (IAM) emerges as a linchpin in the cloud security architecture, providing a comprehensive framework for safeguarding data, applications, and infrastructure. In this article, we delve into strategies and best practices for improving cloud security through enhanced IAM.
Understanding the Significance of IAM in Cloud Security: Identity and Access Management serves as the gatekeeper of the cloud infrastructure, regulating who has access to what resources. This not only safeguards sensitive information but also mitigates the risk of unauthorized access and data breaches.
Implementing Multi-Factor Authentication (MFA): Strengthening user authentication with MFA adds an extra layer of security, requiring users to verify their identity through multiple means. This significantly reduces the risk of unauthorized access, even if login credentials are compromised.
Role-Based Access Control (RBAC) for Precision Control: RBAC ensures that users are granted access based on their roles and responsibilities within the organization. This granular control minimizes the potential for overprivileged accounts and limits the scope of a security breach.
Regularly Reviewing and Updating Access Permissions: Conducting periodic reviews of access permissions is essential to align IAM policies with organizational changes. Removing unnecessary access rights and updating permissions based on job roles contribute to a more secure cloud environment.
Privileged Access Management (PAM) for Critical Resources: Implementing PAM restricts access to critical systems and sensitive data to authorized personnel only. This heightened level of control prevents unauthorized users from accessing privileged information.
Centralized Identity Management: A centralized IAM system provides a single point of control for managing user identities, ensuring consistency and coherence across the entire cloud infrastructure. This simplifies administration and enhances security.
Continuous Monitoring and Anomaly Detection: Implementing real-time monitoring and anomaly detection mechanisms within IAM frameworks enables swift identification of suspicious activities. Prompt response to potential security threats is crucial for maintaining a secure cloud environment.
Integration with Security Information and Event Management (SIEM): Integrating IAM with SIEM solutions enhances the ability to correlate identity-related events with broader security incidents. This holistic approach ensures comprehensive visibility into potential security risks.
Data Encryption and Tokenization: Securing data at rest and in transit through encryption and tokenization adds an additional layer of protection. This ensures that even if unauthorized access occurs, the data remains unintelligible and protected.
Regular Training and Awareness Programs: Human factors are critical in IAM security. Conducting regular training programs for employees and raising awareness about the importance of secure IAM practices contribute to a culture of cybersecurity within the organization.
Conclusion: In an era where data is a valuable asset, securing the cloud environment is non-negotiable. A robust Identity and Access Management system not only fortifies the defense against cyber threats but also fosters a resilient and adaptive security posture. By implementing the outlined strategies, organizations can navigate the complexities of cloud security confidently, ensuring that IAM serves as a stalwart guardian in safeguarding their digital assets.
0 notes
Text
SaaS Implementation with Microservices for Modern Businesses
Software as a Service (SaaS) has become a cornerstone of modern business operations, providing a flexible and scalable solution for various applications.
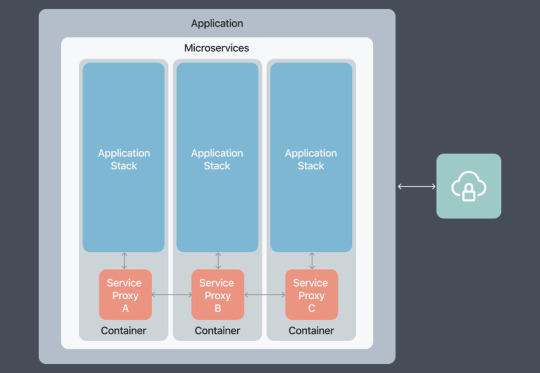
When combined with microservices architecture, SaaS not only enhances operational efficiency but also offers agility, scalability, and improved user experiences. In this article, we will explore the synergies of SaaS implementation with microservices and how this dynamic duo is reshaping the landscape of business software.
Microservices: The Building Blocks of Agility: Microservices architecture involves breaking down complex applications into smaller, independently deployable services. This modularity aligns seamlessly with the on-demand nature of SaaS, allowing for faster development cycles and more agile responses to changing business needs.
Scalability at its Core: One of the primary advantages of combining SaaS with microservices is scalability. Microservices enable businesses to scale specific components of an application independently, ensuring optimal resource utilization and performance, especially in a cloud-based SaaS environment.
Flexibility and Customization: Microservices empower SaaS providers to offer customizable solutions, allowing users to pick and choose the services that align with their specific requirements. This flexibility enhances user satisfaction and ensures that businesses pay only for the features they need.
Enhanced Reliability and Resilience: With microservices, if one service encounters an issue, it doesn't necessarily affect the entire application. This inherent fault isolation improves the reliability and resilience of SaaS platforms, ensuring uninterrupted services even in the face of isolated failures.
Rapid Deployment and Continuous Integration: Microservices facilitate rapid deployment of updates and new features, a crucial aspect in the dynamic landscape of SaaS. Continuous integration and continuous delivery (CI/CD) pipelines ensure that changes can be seamlessly integrated and deployed, minimizing downtime.
Optimized Resource Utilization: Microservices allow for efficient use of computing resources as each service can be scaled independently based on demand. This optimized resource utilization translates into cost savings for both SaaS providers and end-users.
Improved User Experiences: Microservices enable SaaS applications to deliver a more responsive and interactive user experience. With the ability to independently scale user-facing services, microservices contribute to reduced latency and enhanced overall performance.
Security and Compliance: The modular nature of microservices facilitates better security practices. SaaS providers can implement specific security measures for each microservice, ensuring a robust security posture. This approach is particularly beneficial for meeting compliance requirements in various industries.
Data Management and Integration: Microservices simplify data management and integration in SaaS applications. Each microservice can have its own database, and APIs can be designed to enable seamless communication between services, fostering a cohesive and well-integrated ecosystem.
Future-Proofing SaaS Platforms: By leveraging microservices in SaaS implementation, businesses can future-proof their platforms. The modular architecture allows for easy updates, integrations with emerging technologies, and adaptation to changing business requirements.
Conclusion: The combination of SaaS implementation with microservices is a powerful paradigm that not only enhances the efficiency of business software but also aligns perfectly with the demands of the modern digital landscape. As businesses continue to seek flexible, scalable, and responsive solutions, the integration of SaaS and microservices stands as a beacon for a new era of innovation and effectiveness in software delivery.
0 notes
Text
A Comprehensive Guide to Migrating Windows Applications to AWS
In the dynamic landscape of cloud computing, businesses are increasingly turning to Amazon Web Services (AWS) to harness the scalability, reliability, and cost-effectiveness it offers.

Migrating Windows applications to AWS can be a strategic move to leverage the full potential of cloud infrastructure. This guide outlines a step-by-step approach to ensure a smooth and successful migration process.
Assessment and Planning: Before embarking on the migration journey, conduct a thorough assessment of your existing Windows applications. Identify dependencies, performance metrics, and any potential challenges. Create a detailed migration plan that includes timelines, resource allocation, and a risk mitigation strategy.
AWS Services Selection: Choose the appropriate AWS services that align with the requirements of your Windows applications. AWS provides a range of services, including Amazon EC2 for virtual machine instances, Amazon RDS for database management, and AWS Elastic Beanstalk for application deployment.
Network Architecture: Review and design the network architecture to ensure a seamless connection between your on-premises environment and AWS. Utilize AWS Direct Connect or VPN for secure communication, and configure Virtual Private Clouds (VPCs) to isolate resources effectively.
Data Migration: Develop a strategy for data migration, considering the volume and sensitivity of your data. AWS provides services like AWS Snowball for large-scale data transfers and AWS Database Migration Service for database migration, ensuring minimal downtime during the process.
Application Refactoring: If necessary, refactor or re-architect your Windows applications to optimize them for the AWS environment. This step may involve modifying code, updating dependencies, and ensuring compatibility with AWS services to enhance performance and scalability.
Security and Compliance: Prioritize security measures by configuring AWS Identity and Access Management (IAM) roles, implementing encryption, and adhering to AWS best practices. Ensure compliance with industry regulations by leveraging AWS services designed to meet specific security standards.
Testing and Validation: Thoroughly test the migrated Windows applications in the AWS environment before fully committing to the migration. Perform functionality tests, security audits, and performance assessments to identify and address any potential issues.
Monitoring and Optimization: Implement robust monitoring solutions, such as Amazon CloudWatch, to track the performance of your Windows applications post-migration. Continuously optimize your AWS resources based on monitoring data to enhance efficiency and reduce costs.
Documentation and Training: Document the entire migration process, including configurations, settings, and any modifications made to the applications. Provide training to your team members to familiarize them with the AWS environment and best practices for ongoing management.
Post-Migration Support: Offer post-migration support to address any unforeseen issues and ensure a smooth transition. Establish communication channels with AWS support and leverage AWS resources such as forums and documentation for ongoing assistance.
Migrating Windows applications to AWS is a strategic move that can unlock a myriad of benefits for your organization. By following this comprehensive guide, businesses can navigate the complexities of migration with confidence, ultimately realizing the full potential of AWS for their Windows application ecosystem.
0 notes
Text
Embracing Cloud Technology for Digital Transformation: The Future is Now
In today's fast-paced digital age, organizations are constantly seeking ways to remain competitive, agile, and innovative. The catalyst for achieving this transformation lies in the cloud.
Cloud technology has become the linchpin for digital transformation, propelling companies into the future by providing the tools and capabilities necessary to thrive in an ever-evolving business landscape. This article explores how cloud technology is revolutionizing the way businesses operate and why it's the cornerstone of successful digital transformation.
The Foundation of Digital Transformation
Digital transformation is more than just adopting digital technologies; it's a strategic shift in how businesses operate, engage with customers, and create value. The cloud provides the foundation for this transformation because it offers several key advantages:
Scalability: Cloud platforms allow organizations to scale their resources up or down based on demand. This elasticity is crucial for handling surges in traffic and responding quickly to market changes.
Cost Efficiency: Cloud services often follow a pay-as-you-go model, reducing the need for large upfront investments. This cost-effective approach frees up capital for other strategic initiatives.
Agility and Speed: The cloud enables faster deployment of new services and applications. This agility is essential in responding to market dynamics and staying ahead of the competition.
Global Reach: Cloud providers have data centers worldwide, facilitating global expansion without the need for extensive infrastructure investments.
Innovation: Cloud platforms offer a plethora of cutting-edge services, such as artificial intelligence, machine learning, and Internet of Things (IoT) capabilities. These tools empower organizations to innovate and create new digital experiences.
Digital Transformation in Action
Customer-Centricity: Digital transformation allows businesses to shift their focus toward customer-centric strategies. With the cloud, organizations can gather and analyze customer data in real-time, enabling personalized experiences and more effective marketing campaigns.
Remote Work and Collaboration: The COVID-19 pandemic has accelerated the adoption of remote work. Cloud technologies enable teams to collaborate seamlessly from anywhere, ensuring business continuity.
Data-Driven Decision Making: Cloud platforms provide the infrastructure and tools to collect, store, and analyze vast amounts of data. This data-driven decision-making empowers organizations to make informed choices and optimize operations.
Automation: Cloud-based automation streamlines processes and reduces manual intervention. This not only enhances efficiency but also minimizes errors and frees up employees to focus on strategic tasks.
Innovative Solutions: The cloud is the breeding ground for innovative solutions. Whether it's using machine learning to predict customer behavior or harnessing the power of big data for better decision-making, the possibilities are endless.
Challenges and Considerations
While cloud technology is a game-changer for digital transformation, it's essential to address certain challenges and considerations:
Security and Compliance: Protecting data in the cloud and ensuring compliance with regulations is critical. Proper security measures and governance are essential.
Data Integration: Organizations often have legacy systems that need to be integrated with cloud solutions. A well-thought-out strategy for data migration and integration is crucial.
Skills and Training: Teams need to acquire the necessary skills to manage and optimize cloud resources effectively. Training and upskilling are ongoing requirements.
Cost Management: While the cloud offers cost-efficiency, uncontrolled usage can lead to unexpected expenses. Implementing cost management practices is vital.
Conclusion
Cloud technology has transcended from being a mere tool to becoming the cornerstone of digital transformation. Businesses that harness its potential are better equipped to adapt to change, innovate, and create unparalleled value for their customers. As we stand at the brink of a new digital era, the cloud is the vehicle that will drive us toward unprecedented opportunities and growth. It's not a question of "if" but "when" your organization embraces cloud technology for digital transformation. The future is now, and it's in the cloud.
1 note
·
View note
Text
Navigating the Complexities of AWS Security
Amazon Web Services (AWS) has undoubtedly revolutionized the way organizations deploy and manage their IT infrastructure.

The scalability, flexibility, and cost-efficiency of AWS cloud services have made it the go-to choice for businesses worldwide. However, along with these benefits come a host of complexities when it comes to securing your data and applications in the cloud. In this article, we will delve into the intricate world of AWS security, exploring the challenges and best practices for safeguarding your cloud resources.
Shared Responsibility Model
One of the fundamental complexities of AWS security stems from the Shared Responsibility Model. AWS is responsible for the security of the cloud infrastructure itself, including the physical data centers, networking, and host systems. However, customers are responsible for securing their data, applications, and configurations within the cloud. This shared responsibility requires a clear understanding of where AWS's responsibilities end and your organization's begins.
Identity and Access Management (IAM)
Managing identities and access controls in AWS is crucial for preventing unauthorized access to your resources. AWS Identity and Access Management (IAM) allows you to define and enforce fine-grained permissions, but configuring IAM policies and roles correctly can be challenging. Misconfigurations can lead to over-privileged accounts or under-privileged resources, posing significant security risks.
Data Encryption
Data encryption is a critical aspect of AWS security. While AWS offers various encryption services for data at rest and in transit, managing encryption keys, setting up proper access controls, and ensuring consistent encryption throughout your infrastructure can be complex. Implementing Key Management Services (KMS) and monitoring for encryption compliance are essential.
Network Security
AWS provides robust network security features, such as Virtual Private Clouds (VPCs) and Security Groups, to control inbound and outbound traffic. However, designing a secure network architecture, configuring security groups, and monitoring network traffic require careful planning and expertise. Misconfigured network settings can expose your resources to vulnerabilities.
Compliance and Auditing
Meeting industry-specific compliance standards, such as GDPR, HIPAA, or PCI DSS, in the AWS environment can be challenging. Achieving and maintaining compliance requires thorough documentation, regular audits, and continuous monitoring. AWS provides compliance tools and services, but it is the responsibility of the customer to implement and manage them effectively.
Security Automation
Security in AWS is not a one-time effort but an ongoing process. The sheer scale and dynamic nature of AWS environments make manual security management impractical. Implementing security automation through tools like AWS Config, AWS Trusted Advisor, and custom scripts is essential for real-time threat detection, incident response, and compliance enforcement.
Third-Party Integration
Many organizations rely on third-party security solutions to augment AWS's native security features. Integrating these tools seamlessly into your AWS environment can be complex. Properly configuring and monitoring third-party solutions is crucial to achieving a comprehensive security posture.
Security Best Practices
Keeping up with AWS security best practices and staying informed about the latest security threats and vulnerabilities is a continuous challenge. AWS provides extensive documentation and resources, but organizations must invest time and effort into training their teams and staying vigilant in an ever-evolving threat landscape.
Conclusion
Securing your AWS environment is undoubtedly complex, but it's also essential to protect your data and applications in the cloud. By understanding the Shared Responsibility Model, mastering IAM, implementing encryption, designing secure networks, and embracing automation and best practices, organizations can navigate the complexities of AWS security effectively. Remember that AWS security is not a one-size-fits-all solution; it requires a tailored approach that aligns with your specific business needs and risk tolerance. Continuously assess and adapt your security strategy to stay ahead of emerging threats in the cloud.
0 notes