Don't wanna be here? Send us removal request.
Text
A post about responsible data handling
I enrolled in this course because of my interests in security and childhood exposure to computing systems and exploitation (simple networking and windows XP exploits): however I was unsure of how it would apply to my career. I currently work at Westpac bank as a data scientist and operate with sensitive transaction and customer level data on a daily basis. Because I develop in Python, SQL and Javascript I require administrator access on my local machine.
I am in a perfect position to be targeted by an attacker.
Reflecting back on my behaviour 2 months ago before starting the course, I have realised that my security ‘etiquette’ has dramatically improved. I am now ensuring the passwords I use at work around sensitive data are more secure, I am using better practices when storing credentials on my local machine. I am checking signatures on downloaded packages and developing software with the mindset that what I am writing could be subject to exploitation.
I am even advising my team on better practices and have engaged the people I work with to focus on security issues and not disregard its importance. When we present new data assets inside the bank, I am always questioning whether the people we are presenting to have the correct level of access to view the data we are presenting.
I am very thankful for the impression this course has made on me and think more people should be educated on the importance of good security practice.
0 notes
Text
COMP6441 CTF
Since last week I have been progressing through the CTFs on http://plsdonthaq.me and have had some wins and some loses. I managed to solve the cookie CTF by modifying my local cookie file using Firefox - I will let potential readers figure out the specifics ;). I also attempted the ‘ezpz1.0′ challenge which is SQLi. I managed to cause a syntax error in the SQL script, this gave me an error message that gave more information about the table structure and query. I tried a few different techniques from there:
Using username: [admin’ OR ‘1′=‘1] however:
Resulted in ‘sha256(password) does not match’
Hijacking the login statement by inserting my own select statement within the user login statement to dump the contents of the user table:
Resulted in ‘sha256(password) does not match’
Inserting invalid input into the password field to hopefully comment out the code between the user input in the username field and password field:
Resulted in ‘sha256(password) does not match’
My conclusion is that there is something I have to exploit in relation to the SHA256 hash. I am still thinking about this one... I also completed some of the crypto challenges such as ‘birthday attack’, ‘vinegar’, ‘shuffle’ and guess.
I do not understand the points metrics as the easiest challenge I completed was worth 200 points and some of the harder ones are only worth 100; however the challenges have been fun and I am learning a variety of new security skills.
0 notes
Text
Deep dive into SucKit and M0rtix source code
I spent the afternoon sifting through rootkit source code from https://github.com/CSLDepend/exploits/tree/master/Rootkit_tools and trying to understand the methodology that suckit and m0rtix use to implement kernel level privilege through modifications to the syscall table. It is interesting to note that the SucKit rootkit patches the syscall table by directly writing to memory. This is a much more complicated technique than m0rtix, as m0rtix uses a loadable kernel module (LKM) to modify system calls. They both provide the functionality of forwarding terminal access to an attacker via system call hooks and also hide the associated files and processes.
0 notes
Text
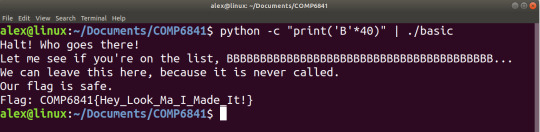
COMP-6841 Buffer Overflow Practice
I have completed the first two buffer overflow challenges, planning on completing the next two within the next two weeks.

0 notes
Text
Setup Kali Linux USB with Persistence
Over the weekend I setup a boot-able Kali Linux USB with persistence so that I could demonstrate my something awesome project.


0 notes
Video
tumblr
A video showcasing my something awesome project!
0 notes
Text
This is excellent! This really clearly demonstrates the differences between ECB, CBC, CTR which I haven’t had the opportunity to tinker with yet. Thank you for also linking the tool you used, it really helped!
Block Cipher Modes
The activity at here gives us five cyper texts based on our input and we need to determine whether each is using ECB, CBC or Counter Mode. I managed to determine the difference pretty quickly using a few properties of each to determine the difference.
The first thing i did was pass in a string of all a’s to be double the length of the block size as i knew that ECB would result in the same encryption for each half due to the face that the same key is used for each block.
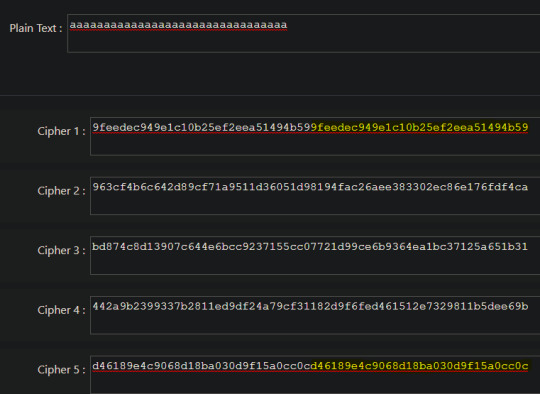
As we can see Cipher 1 and 5 are ECB. The next thing i did was to change the input slightly at the start and see if i would get an avalanche effect. As an avalanche effect would indicate use of CBC whereas only a small change would indicate Counter Mode now that we’ve already identified ECB.
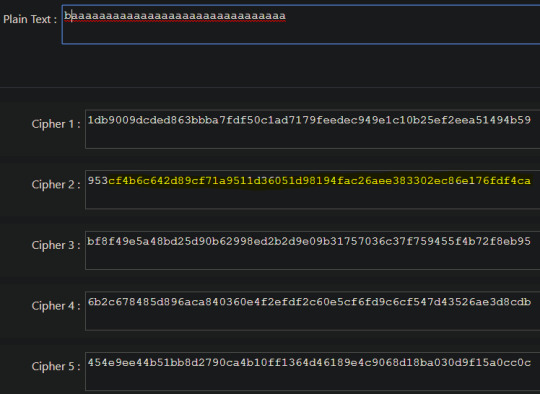
Comparing the output we can see that only the first part of the output for cipher 2 changed and while typing the output appeared to be a stream cipher and as a result we can determine that it is using Counter Mode as counter mode turns the block cipher into a pseudo-stream cipher and also doesn’t rely on the previous block for the next so no avalanching occurs. Therefore ciphers 3 and 4 must be using CBC (as avalanching does occur).
2 notes
·
View notes
Text
Lectures & Tutorial 08
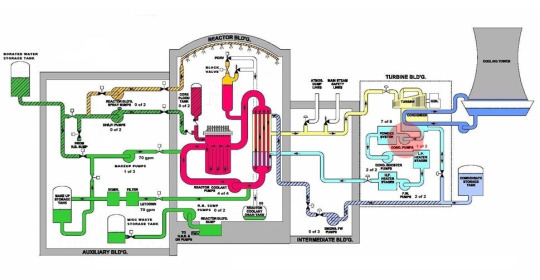
In today’s lectures Richard went over the Three Mile Island meltdown in quite thorough detail. We looked into the roles that humans and machines play when it comes to system failure. A significant issue that contributed to the disaster was
Homework:
Tutorial Case Study: Stargate ghost problem The pre-reading (watching) was short but I understood the concepts behind it: Authentication. How do you authenticate someone through a middle man? This somewhat relates back to the Houdini case study, and also the lecture activity I participated in. It seems the only way to truly verify someone this way is with a pre-determined shared secret that could only be known by the two agents involved in the authentication at question.
Chernobyl

Nuclear disaster 26th April 1986
100 deaths - 4,000 projected deaths
Reactor meltdown
Test was initiated that switched power from turbine to diesel generators
Turbine wind-down caused power to pumps to drop
Water flow rate decreased
Steam formed voids in core
Reactor entered a positive feedback loop
Scram was initiated
Power spike occurred and core overheated
Fuel rode fractured
Explosions -> Meltdown
Link.
Bhopal

Gas tragedy 2-3 December 1984
Considered to be the worst industrial disaster
500,000 people exposed to methyl iso-cyanate gas
3787 deaths - 16,000 claimed deaths, 558,125 injuries
Two main causes
Corporate negligence
Under investment
Lacking equipment and regulations
Safety audits were not responded to
Employee sabotage
Report concluded that a single employee secretly and deliberately introduced a large amount of water into the MIC tank by removing a meter and connecting a water hose directly to the tank through the metering port
Take aways:
Weak system that was not maintained or administrated well
Very little redundancies
Link.
Challenger

Space shuttle explosion 28th January 1986
Killed 7 crew members
Broke apart 73 seconds into flight
Failure caused by:
O-ring seals used in join not designed to handle unusually cold conditions
Allowed pressurised burning gas from within the solid rocket motor reached the external fuel tank
This lead to separation of the right-hand SRB’s and a structural failure of the external tank
Aerodynamic forces broke up the orbiter

Link.
0 notes
Text
Today I helped Hugh
I sat next to my mate hugh in the lecture today and he showed me his something awesome. I strated to use it and noticed some improvements he could make and suggested a better way to handle errors.
Heres the link: https://fingerprintme.herokuapp.com/
0 notes
Text
Lectures & Tutorial 07
Richard gave a lot of homework this week...
Homework:
Tutorial Case Study: Privacy and Biometrics Previously I was not highly concerned with the collection of my personal data by Google, Facebook, Apple, etc; and the main reason behind this is for the convenience. Google maps suggests automatically the places I frequently travel to, like work, home and uni. I use Face ID on my phone to make payments and login to my accounts. I enjoy this ease of use. After the tutorial I reflected upon how much data I am giving away and how that data could be exploited for objectives that do not align with my intentions. For example, Apple aggregating my expense information to better market products to me: I have no choice over this...
Top ten web security risks
Injection
Broken Authentication and Session Management
Cross-Site Scripting (XSS)
Insecure Direct Object References
Security Misconfiguration
Sensitive Data Exposure
Missing Function Level Access Control
Cross-Site Request Forgery (CSRF)
Using Components with Known Vulnerabilities
Unvalidated Redirects and Forwards
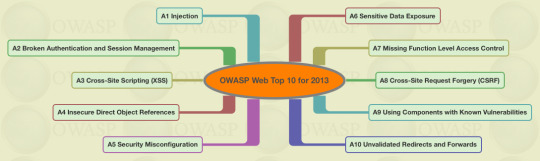
Link.
NIST NATIONAL VULNERABILITY DATABASE This is actually great as I have just started to investigate the possibilities of XSS and SQLI. This vulnerability database lists many current and fresh issues that give some insight into what approaches should be taking when testing web apps. Link.
Read up about the NSW LPI and think about what assets they have and what risks arise from them having been privatised The NSW LPI was the division responsible for land titles, property information, valuation, surveying, and mapping and spatial information in the Australian state of New South Wales. Privatising these assets releases their control and jurisdiction of these assets to financially driven entities. This means that the enforcement on assets that hold cultural value and significance such as historical buildings and park-lands might be re-zoned to align with the economy’s interests. There exists a higher risk to lose the assets with non-financial value. Link. Work out the current state of bio-metrics as an authentication strategy Bio-metrics are regarded as the best (single) means of user authentication to the casual intruder. They also prevent against password stealing ware (PSW) which grabs auto-fill data and saved payment card details. Most tech companies such as Apple and Google who provide bio metric authentication are pushing for this to be a common method of authentication for websites and apps. This would be another measure towards improving user authentication. Link.
Read about Transport for NSW idea of using facial recognition rather than opal cards This is a controversial topic. For Opal to use face recognition to authenticate and identify it’s passengers, means that it would have to store mass amounts of customer data - both images and video - which creates a very high value target for hackers. This data is also connected with location and time tracking. The guardian, linked below, discusses the privacy risks this would pose, HOWEVER, the public concern is more focused on the fact of whether or not it is technologically feasible, not on the fact it would pose major privacy risks. Link.
Read about the San Francisco ban on bio-metrics San Francisco has banned the use of bio-metrics by police. This is because of the fear that the technology will be overused and move the United States in the direction of an overly oppressive surveillance state. There was a recent push for the use of these bio-metric systems following this mass shooting, however, there was a widespread public backlash as many showed strong discomfort with the idea. In this case, the American people seem to value their personal privacy over the additional security of widespread bio-metric identification. Link.
Read about the uni research allegedly helping Chinese security forces use to track and detain Muslim Uyghur citizens in Xinjiang Apparently in 2017 UTS signed a lucrative deal with CETC (Chinese state-owned military tech company) that developed software for Chinese security forces to use to track and identify citizens; however recently this same technology was used to track and detain Muslim Uyghur citizens in Xinjiang. I don’t what UTS was expecting when they assisted in the development of this, it seems quite intuitive that this could and will eventually be misused by the military for purposes UTS possibly found as a human ethics violation. Link.
China’s goals and recent developments with bio-metrics: China’s goals and implementation:
Identify a person from the 1.3 billion population in just 3 seconds using facial recognition.
Security personnel wearing eye-wear to detect people
Face-reading drones
Wearable microchips in uniforms that help with admin tasks such as authentication and monitoring
AI generated media... (news anchors)
Loudspeakers to yell at children when they got too close to water
Livestock farming and monitoring using AI
Link.
How can you detect Man in the Middle eavesdropping? One method of detecting a MitM attack is by constantly validating if the certificates presented to you by the website is issued by a legitimate CA. The best method of doing this is using a tool to keep track of the changes relating to the certificates you use, so if there is a major change, such as Google updates its private key, you can check manually if this is actually the case.
Web of trust (PgP) and PKI. (how PGP does authentication - web of trust) Public Key Cryptography Infrastructure (PKI) can be implemented in two different ways: first using certificates and certificate authorities, secondly, using trust relationships between regular users. The first implementation is the commonly used method of certification used by websites. The second implementation was first used by OpenPGP. This is implemented by GNU Privacy Guard (GnuPGP) which nearly all linux distributions rely on for package integrity verification. Link.
10 Risks of PKI
Anyone can become a CA with enough work, and then they are by default ‘trusted’
Your private key is ‘steal-able’
You cannot detect a ‘compromised’ CA
Only a single CA is needed to validate a website, PKI doesn’t cross verify
CA verifies certificates but is not an authority over the contents of the certificate
User’s aren’t included in the security design (they could play a role in the validation process)
A CA could actually be a CA + Registration Authority (RA). The RA+CA model is less secure as the link between the two could become compromised
The CA could possibly misidentify the certificate holder (a malicious individual could impersonate the certificate holder)
If/When the technology progresses and updates to a new encryption standard, all the certificates need to be updated or revoked using the Certificate Revocation Lists (CRL)
PKI was implemented as due to a minimal impact solution and even though it is not a perfect system, the industry is run by “business and the prominent voices are those with something to sell.”
Link.
Find examples of (serious) fraudulent certificates being issued For this I researched a company called DigiNotar, a Dutch Certificate Authority. This company ‘detected’ a security breach on September 3rd 2011 which resulted in fraudulent issuing of certificates. 300,000 Irinian Gmail users were the target of the hack and Bruce Schneier says that the attack may have been “either the work of the NSA or exploited by the NSA.” however, this has been disputed with others saying NSA had only detected a foreign intelligence service using the fake certificates. Some are even pointing fingers at the 21 year old Irinian student who claimed to have hacked 4 other certificate authorities. Once 500 fake certificates were identified, DigiNotar became blacklisted. Link.
Learn about the steps in a TLS handshake Here is a summary of the steps published by IBM (steps in [ ] are optional):
Client sends ‘hello’ containing:
random byte string
SSL or TLS version
CipherSuits supported
Data compression methods
Server responds with ‘hello’ containing:
Chosen CipherSuite
Session ID
Another random byte string
Digital certificate
[Client certificate request]
Client verifies certificate
Client sends to server containing:
Random byte string encrypted using server public key
[Client certificate or ‘No digital certificate’]
[Server verifies client certificate]
Client sends server ‘finished’ message encrypted with secret key
Server sends client ‘finished’ message encrypted with secret key
They now exchange messages encrypted with the shared secret key
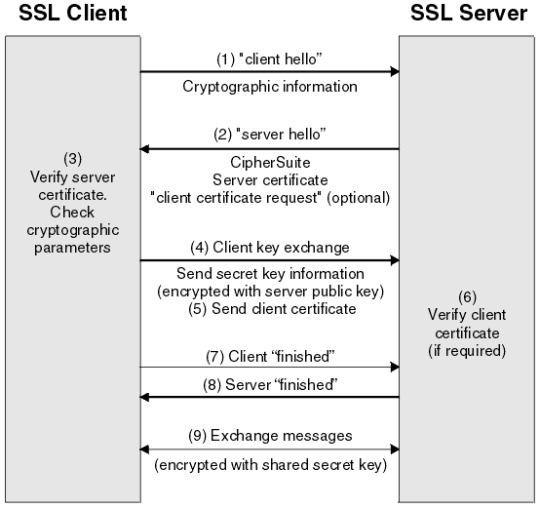
Link.
0 notes
Text
Chat jargon
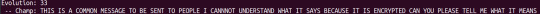
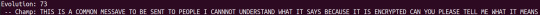
After training on reddit data, the AI became much better at deciphering casual communication such as text messages: however it usually finds the solution to the cipher and then slightly deviates from it. In the example above, it solved the message correctly by evolution 33, however thought that by swapping the letter G with V (MESSAGE -> MESSAVE) it made a more correct answer. My guess is that in reddit comments, the characters ‘AVE’ is more common than ‘AGE’ to the extent that it would modify the word.
0 notes
Text
New Findings

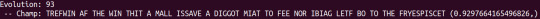
I have discovered an interesting caveat. My neural network model is trained on wikipedia articles. This meant that the set of english it is trying to decipher is educational related words. This made the AI relatively better at solving more formal statements than informal messages. See figures attached. To combat this, I am downloaded a data dump of reddit comments to train on and see the impact.
0 notes
Text
Victory! (kinda)
After repairing the bugs I recently posted about, I implemented an interesting strategy. I started training the neural network on a dataset I generated that scores the text based upon how far from the solution it was. i.e. if the text only had a few incorrect letters it would score ~90% and if the text had many jumbled letters it would score ~10%. This dramatically accelerated the rate at which the neural network was able to approach a reasonable solution. Currently the results are as stands:
Solving to achieve:
THE MOON IS THE ONLY NATURAL SATELLITE OF EARTH AND THE FIFTH LARGEST MOON IN THE SOLAR SYSTEM OWING TO ITS SYNCHRONOUS ROTATION AROUND EARTH THE MOON ALWAYS SHOWS ESSENTIALLY THE SAME FACE
Fitness = 1.019604
Solution after 100 evolutions:
TVE COON IS TVE ONLY NATHRAL SATELLITE OF EARTV AND TVE FIFTV LARGEST COON IN TVE SOLAR SYSTEC OMING TO ITS SYNPVRONOHS ROTATION AROHND EARTV TVE COON ALMAYS SVOMS ESSENTIALLY TVE SACE FAPE
Fitness = 1.055220
After observing these results, I can see that the AI thinks it’s solution is better than the actual solution. If I am able to correct the model to see 1.00000 as a perfect solution and anything else as less, then I would definitely be on the right track.
0 notes
Photo


Today I discovered 3 major bugs in my genetic algorithm code: of which I assumed to be correct until now...
Firstly, the fitness weights were being initialised as an empty array, which meant that (when multiplied by the fitness value) created an empty array... This meant that all the cipher keys were being randomly compared and explains why the algorithm was not learning....
Secondly, the initial population seed was not random! The entire key set was being initialised to the same key! This is definitely the reason behind why my program was being stuck in a local minimum, because the data was only searching from one point!
Once fixing those bugs, I saw some significant improvements. Stay tuned.
0 notes
Text
Lectures & Tutorial 06
Today we discussed the trade-off between privacy and security. It’s funny how your values can change after they are questioned. I might start turning off my location tracking more regularly now...
Homework:
Tutorial Case Study: Cyber war with a superpower It’s always a touchy topic when the words ‘Russia’ and war are in the same sentence. It was fun thinking about how we could protect ourselves from a superpower such as Russia and protect our data assets. It was sometimes hard to distinguish between whether something was an offensive attack against the enemy or a defence to protect ourselves. My main take-away from this exercise is that we are probably already at cyber-war with countries and we don’t even know it.
Read up enough on how Feistel networks work A Feistel network is an iterated cipher with an internal function called a round function. Like other components of the DES, the iterative nature of the Feistel construction makes implementing the cryptosystem in hardware easier (particularly on the hardware available at the time of DES's design). Link.

NIST ran a competition for replacement code and shortlist Winner: Keccak on October 2, 2012. Finalists: BLAKE (Aumasson et al.) Grøstl (Knudsen et al.) JH (Hongjun Wu) Keccak (Keccak team, Daemen et al.) Skein (Schneier et al.)
Link.
Read about "Block Modes" - ECB, CBC, CTR A block cipher by itself is only suitable for the secure cryptographic transformation (encryption or decryption) of one fixed-length group of bits called a block. A mode of operation describes how to repeatedly apply a cipher's single-block operation to securely transform amounts of data larger than a block.
Link.
0 notes
Text
A new idea
After straining my brain for new ideas to implement better methods of finding a method to improve my algorithm. I realised that what my algorithm struggles with is distinguishing between which english looking ciphertext is the best one to mutate into a solution. This is most likely due to the massive number of keys (26!) the genetic algorithm is searching over, of which, I am randomly selecting as a seed population of 10,000 and mutating off the best performing keys. HOWEVER, this set size can be dramatically reduced based on some simple logic noted in the picture attached.
There are very few valid small letter words in the english language. By reducing the set of solutions to the ones that contain previously observed small words (1-3 letters), I would be able to reduce the search area and hopefully find the solution in a much more direct and less random matter. I will then use the neural network to assess the correctness of the larger words. (in order of word length)

0 notes
Photo


ATTEMPT TO SOLVE: “THIS IS A VERY SECRET MESSAGE”
------------------------------------------------------
CIPHER: SUBSTITUTION SEARCH: GENETIC ALGORITHM FITNESS: LETTER FREQUENCY + NEURAL NETWORK
------------------------------------------------------
0 notes