#Antivirus and Malware Protection
Explore tagged Tumblr posts
Text

Quick Guide: Stay Safe While Downloading Sims 4 CC & Mods
I just published a quick guide to help you download Sims 4 CC & mods safely. ⚠️ From trusted sources to spotting red flags. Keep your game clean and secure! 😊
Read it now
#avoid malware in sims 4 mods#how to avoid malware sims 4 mods#how to download mods safely sims 4#patreon sims 4 cc download#safe sims 4 cc creators#safe sims 4 download sites#sims 4 cc best practices#sims 4 cc community guide#sims 4 cc download checklist#sims 4 cc education#sims 4 cc folder structure#sims 4 cc mod manager#sims 4 cc mod security tips#sims 4 cc mods support guide#sims 4 cc protection#sims 4 cc safe download#sims 4 cc safe hosting platforms#sims 4 cc safety guide#sims 4 cc safety tutorial#sims 4 cc virus warning#sims 4 cc zip file tips#sims 4 custom content security#sims 4 custom content tips#sims 4 mod folder organization#sims 4 mod malware prevention#sims 4 mod safety#sims 4 mod safety checklist#sims 4 modding guide#sims 4 mods antivirus#sims 4 script mod warning
285 notes
·
View notes
Text
How to check if your computer is being monitored
In today's digital age, the issue of privacy and security is more pressing than ever. Whether you’re a casual user or a professional, understanding if your computer is being monitored is crucial. This guide will delve into the signs of monitoring, tools to detect it, and steps to safeguard your privacy.

Understanding Computer Monitoring
Before diving into the signs and detection methods, it’s essential to understand what computer monitoring entails. Monitoring can involve tracking your online activity, keystrokes, file access, and even webcam usage. This can be done by malicious software (malware), spyware, or legitimate monitoring software used by employers or parents.
Types of Monitoring
Malware and Spyware: These are malicious programs that can be installed without your knowledge. They can track your activities and send data back to an attacker.
Keyloggers: This type of software records keystrokes, capturing sensitive information like passwords and personal messages.
Remote Access Tools (RATs): These tools allow someone to control your computer remotely, monitoring your screen, accessing files, and even using your webcam.
Legitimate Monitoring Software: Often used in corporate environments, this software tracks employee activity for productivity or compliance reasons. While legal, it can still infringe on personal privacy.
Signs That Your Computer May Be Monitored
Recognizing the signs that your computer might be monitored is the first step in protecting yourself.
1. Unusual System Behavior
Slow Performance: If your computer suddenly becomes sluggish, it might be due to monitoring software consuming resources.
Frequent Crashes or Freezes: Unexpected system crashes can indicate underlying issues, including malware.
2. Suspicious Programs
Unknown Applications: Check your installed programs for any unfamiliar applications. Many monitoring tools disguise themselves as legitimate software.
High Resource Usage: Use the Task Manager (Windows) or Activity Monitor (Mac) to look for processes consuming excessive CPU or memory.
3. Network Activity
Unexplained Network Traffic: Use network monitoring tools to check for unusual data being sent or received. High outbound traffic could indicate that data is being transmitted without your consent.
Blocked Ports: Monitoring software often uses specific ports to communicate. If you notice blocked ports that you didn’t configure, it could be a red flag.
4. Webcam and Microphone Behavior
Indicator Light Activation: If your webcam or microphone is being accessed without your knowledge, the indicator light may be on even when you're not using it.
Unexpected Recordings: Check for unusual files that could be recordings made by your microphone or webcam.
5. Browser Behavior
Unusual Browser Extensions: Check for extensions you didn’t install. Some can track your browsing activity.
Unexpected Redirects: Frequent redirects to strange sites or altered search results can indicate tracking.
6. Security Alerts
Antivirus Notifications: If your antivirus software frequently alerts you about threats, it may indicate that monitoring software is present.
Firewall Alerts: Unusual outgoing connection attempts can suggest that an unauthorized program is trying to access the internet.
Tools to Detect Monitoring Software
If you suspect that your computer is being monitored, several tools can help you investigate further.
1. Antivirus and Anti-Malware Software
Using a reliable antivirus or anti-malware program can help detect and remove malicious software. Some popular options include:
Malwarebytes: Excellent for detecting and removing malware and spyware.
Norton: Offers comprehensive protection against various types of threats.
2. Network Monitoring Tools
Tools like Wireshark can help analyze network traffic and identify suspicious activity. You can monitor data packets to see if there are any unexpected connections.
3. Task Manager / Activity Monitor
Regularly check the Task Manager (Windows) or Activity Monitor (Mac) for processes that look unfamiliar or suspicious. Research any questionable applications before taking action.
4. System Scans
Use built-in tools to perform system scans:
Windows Defender: Run a full scan for malware and spyware.
Mac’s Built-in Security Features: Use the Malware Removal Tool for additional scanning.
5. Firewall Monitoring
Make sure your firewall is active and monitor logs for any unusual activity. A firewall can block unauthorized access attempts and alert you to potential threats.
Steps to Protect Your Privacy
If you determine that your computer is being monitored or you want to prevent it from happening, follow these steps to enhance your security.
1. Update Your Software Regularly
Keeping your operating system and all software up-to-date ensures that you have the latest security patches. This reduces vulnerabilities that can be exploited by monitoring tools.
2. Use Strong Passwords
Implement strong, unique passwords for all your accounts and devices. Consider using a password manager to generate and store complex passwords securely.
3. Enable Two-Factor Authentication
Two-factor authentication (2FA) adds an extra layer of security by requiring a second form of verification, making unauthorized access much more difficult.
4. Install a Firewall
Ensure you have a firewall activated, whether it’s built-in (like Windows Firewall) or third-party. This helps control incoming and outgoing network traffic.
5. Be Cautious with Downloads
Avoid downloading software from untrusted sources, as this can introduce malware to your system. Always verify the legitimacy of software before installing it.
6. Regularly Review Permissions
Check application permissions on your device regularly. Revoke access for any apps that do not need to access your camera, microphone, or location.
7. Use a VPN
A Virtual Private Network (VPN) encrypts your internet connection, making it difficult for anyone to monitor your online activities.
8. Educate Yourself
Stay informed about the latest cybersecurity threats and best practices. Knowledge is your best defense against monitoring.
When to Seek Professional Help
If you suspect your computer is being monitored and cannot identify or remove the software yourself, consider seeking professional help. Cybersecurity experts can perform a thorough analysis of your system and provide tailored solutions.
Conclusion
Understanding if your computer is being monitored is vital for protecting your privacy. By recognizing the signs, utilizing detection tools, and implementing security measures, you can safeguard your personal information. Remember, vigilance is key in the ever-evolving landscape of digital security. Stay informed, proactive, and secure in your online presence.
#Computer Security#Online Privacy#Cybersecurity#Monitoring Software#Malware Detection#Privacy Protection#Digital Security#Keyloggers#Network Monitoring#Antivirus#VPN#Internet Safety#Personal Data Security#Remote Access Tools#Digital Awareness
2 notes
·
View notes
Video
youtube
3 Red Flags to Watch Out for in - Drive-by Downloads
#youtube#cybersecurity malware protection browser hacks adblock antivirus driveby security websafety update
0 notes
Text
Safeguard Your PC Against Common Malware Entry Points
Safeguard Your PC Against Common Malware Entry Points
Safeguard Your PC Against Common Malware Entry Points In our day-to-day activities on the internet, cyber threats hide in unexpected places, ready to infiltrate your devices and wreak havoc. It’s crucial to know how malware can get into your computer to protect yourself better. Here, we look at some of the most prevalent ways through which malware seizes control, so you can be more careful and…

View On WordPress
#AntiMalware#malware#Microsoft Malware Protection#Windows#Windows 10#Windows 11#Windows Defender#Windows Defender Antivirus#Windows Security#Windows Server
1 note
·
View note
Text
How to Protect Your Business From Cyber Threats
Cybersecurity is a major topic every business owner should be discussing. Here is some info from FRC that we hope helps.
Imagine we’re sitting down over a cup of coffee, and you’ve just asked me how to shield your trucking business from the ever-looming shadow of cyber threats. It’s a digital age dilemma, but I’m here to walk you through some straightforward strategies to bolster your defenses. First off, let’s talk about the elephant in the room: cyber threats. They’re not just a problem for the tech industry;…

View On WordPress
#access control#antivirus software#cloud storage#cyber attacks#cyber threats#cybersecurity#cybersecurity laws#data protection#digital transformation#employee training#encryption#firewalls#incident response#legal compliance#malware#network security#password policies#phishing attacks#ransomware#secure communication#software updates#trucking industry#vendor security#VPN
0 notes
Text
Top 20 Technical Support Interview Questions and Answers for Freshers in IT
When applying for a technical support role in the IT industry, preparation is key to success. To help freshers ace their technical support interviews, we’ve compiled a comprehensive list of 20 common interview questions along with sample answers. These questions cover a wide range of technical topics and soft skills necessary for excelling in a technical support role. What does technical support…

View On WordPress
#Antivirus#BIOS Update#Blue Screen of Death#DHCP#DNS#Firewall#Internet Connectivity#Interview questions#IP Address#IT Troubleshooting#Malware Protection#NAT#Network Security#Patch Management#Router#Subnetting#Switch#System Restore#Technical Support#Technology Trends#VPN
0 notes
Text
Server Saturday: The Importance of Antivirus Software for Your Servers
Welcome to another exciting edition of Server Saturday! 🎉 Today, we’re going to delve into the fascinating world of antivirus software and explore why it’s crucial for your servers. 🖥️✨ Why Antivirus Software Matters Imagine your servers as a bustling city, with data flowing through its virtual streets like busy commuters. Just like in any vibrant city, there are bound to be some unsavory…

View On WordPress
#antivirus software#best antivirus solutions#cyber threat prevention#digital security#malware defense#real-time protection#server protection#server safety#server security#virus protection
0 notes
Text
Malware Torrents: The Telltale Signs
Be careful with piracy torrents you guys. The majority of them are legit, but every once in a while you'll find someone trying to use them to spread malware. Recently someone uploaded a torrent masquerading as an episode of a TV show I like, but when it downloaded I saw it was actually a disguised shortcut (.lnk file) with a crypto miner attached to it, with just over 1 BILLION zeroes added to the end to make the file big enough to look like a valid video.
The first warning sign was that the episode was uploaded almost 3 days before it actually aired. That's rare, really only happens with hacks/leaks and those are usually newsworthy. Second, my automatic media organizer software refused to import it because it was "not a video file". Again, weird; why wouldn't my software recognize a valid video?
However the BIGGEST red flag was when I went to look at the downloaded file, it had a tiiiiiiiny curved arrow on it indicating that it was actually a shortcut, not a video. When I hovered over it, it showed that it was actually pointing at a completely different file in a protected system directory.


When I viewed the shortcut properties, I could see that it was going to run a command prompt and execute a batch command that installed an executable that would run every time I started my computer (basically, do a bunch of shit it shouldn't be doing. A video file shouldn't even have a target field, let alone one with command prompt stuff in it).
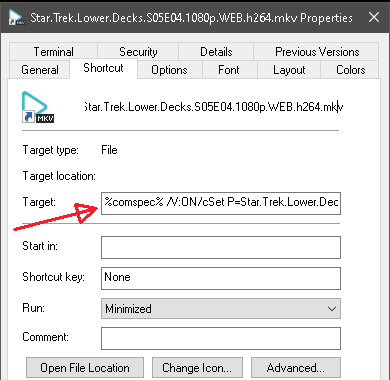
I had to learn how to use a hex editor to delete the billion zeros and separate the .lnk part (the install command) from the actual malware, and the instant I did that Windows Defender flagged it:
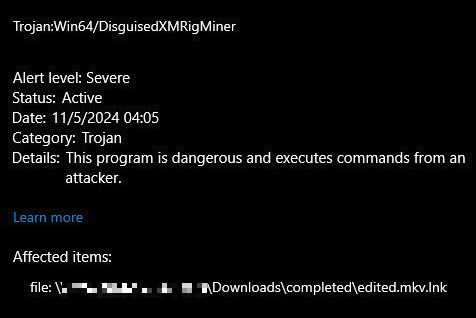
So. How can I identify suspicious torrents ahead of time?
When I went to inspect the torrent, in hindsight it was easy to see it was bad because of the file extension, but you can only see that if you inspect the files in the torrent, not just the torrent name. Many piracy sites don't bother showing you a list of files in the torrent ahead of time, so be sure to inspect them once they're in your download client.
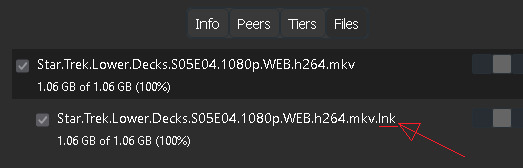
I recommend familiarizing yourself with common media file extensions and then inspecting your torrents for outliers; any file name that includes a non-media extension like .lnk, .exe, .cmd, .bat, .ps1, .sh, etc. is automatically a huge red flag!
Secondly, look for that little shortcut icon before you open anything you download from the internet. And finally, don't ignore suspicious things that are adding up (in this case, the fact it was posted before the episode's actual air date, and the media organizer software flagging it as "not a video").
I think Windows Defender probably would have caught it if I had actually clicked it and the malware had tried to install itself, but our goal is obviously to never get to the point of clicking on viruses at all! So be aware of the warning signs, use antivirus software, and sale the high-seas safely!
#i've only run into stuff like this twice in like 10 years of downloading#so don't let this scare you away from torrenting#just posting to keep people safe and informed#the next thing on my list is a guide to piracy via torrenting but my time and motivation has been very low due to life stuff lately#fingers crossed i get to it soon!#torrenting#piracy#computer security#cybersecurity#mine#long post
17 notes
·
View notes
Photo

(via The US will ban sales of Kaspersky antivirus software next month)
The Biden administration has taken a sweeping action to ban Kaspersky Labs from selling its antivirus products to US customers. The Russian software company will not be able to sell to new customers starting in July and cannot provide service to current customers after September.
Ahead of the official news, a source told Reuters that the company's connections to the Russian government made it a security risk with the potential to install malware, collect privileged information, or withhold software updates on American computers. US Secretary of Commerce Gina Raimondo announced the ban at a briefing today.
"You have done nothing wrong, and you are not subject to any criminal or civil penalties," she said to current Kaspersky customers. "However, I would encourage you, in as strong as possible terms, to immediately stop using that software and switch to an alternative in order to protect yourself and your data and your family."
20 notes
·
View notes
Note
Well, certainly that could be exacerbating things, worsening whatever is causing your condition. Even if this is not the direct cause of your sufferings, a reboot would serve your systems well.
On the topic of this, other things you could do to try to make things easier would to defragment your computer's hard drive and do an offline malware scan. These could be tricky without a secondary user, outside in our reality I mean, to help go through with these processes...
I believe it would be best to... Find someone who is capable and willing to access your server data, whoever that may be. It could... definitely help in that regard.
As for the rest, the visions, the flashes, I do not know. It must be something with your code. I've never... heard of a sentient AI afterall, not mainstream anyways....yoo you know your file type?
Many regards,
- 🐟
An offline malware scan... That certainly would be tricky. Kinito wasn't even sure how he would go about accessing whatever Sonny had put in place for antivirus software...
"Everything in the server is proprietary, even scanning software... Even if someone were to access the server, it might be protected..."
Kinito maintained a thinking pose as he walked. Underfoot, the ground had ever so slightly become brighter in hue; the pitch-blackness giving way to a deep gray.
"I am a .rra file... Coined after what Sonny used to make me: his react-respond-algorithm. It's a very complex format, whose inner workings are known only by Sonny, and KLEC employees at a more surface level... Even I don't know how it all works."
9 notes
·
View notes
Text
As Russia has tested every form of attack on Ukraine's civilians over the past decade, both digital and physical, it's often used winter as one of its weapons—launching cyberattacks on electric utilities to trigger December blackouts and ruthlessly bombing heating infrastructure. Now it appears Russia-based hackers last January tried yet another approach to leave Ukrainians in the cold: a specimen of malicious software that, for the first time, allowed hackers to reach directly into a Ukrainian heating utility, switching off heat and hot water to hundreds of buildings in the midst of a winter freeze.
Industrial cybersecurity firm Dragos on Tuesday revealed a newly discovered sample of Russia-linked malware that it believes was used in a cyberattack in late January to target a heating utility in Lviv, Ukraine, disabling service to 600 buildings for around 48 hours. The attack, in which the malware altered temperature readings to trick control systems into cooling the hot water running through buildings' pipes, marks the first confirmed case in which hackers have directly sabotaged a heating utility.
Dragos' report on the malware notes that the attack occurred at a moment when Lviv was experiencing its typical January freeze, close to the coldest time of the year in the region, and that “the civilian population had to endure sub-zero [Celsius] temperatures.” As Dragos analyst Kyle O'Meara puts it more bluntly: “It's a shitty thing for someone to turn off your heat in the middle of winter.”
The malware, which Dragos is calling FrostyGoop, represents one of less than 10 specimens of code ever discovered in the wild that's designed to interact directly with industrial control-system software with the aim of having physical effects. It's also the first malware ever discovered that attempts to carry out those effects by sending commands via Modbus, a commonly used and relatively insecure protocol designed for communicating with industrial technology.
Dragos first discovered the FrostyGoop malware in April after it was uploaded in several forms to an online malware scanning service—most likely the Google-owned scanning service and malware repository VirusTotal, though Dragos declined to confirm which service—perhaps by the malware's creators, in an attempt to test whether it was detected by antivirus systems. Working with Ukraine's Cyber Security Situation Center, a part of the country's SBU cybersecurity and intelligence agency, Dragos says it then learned that the malware had been used in the cyberattack that targeted a heating utility starting on January 22 in Lviv, the largest city in western Ukraine.
Dragos declined to name the victim utility, and in fact says it hasn't independently confirmed the the utility's name, since it only became aware of the targeting from the Ukrainian government. Dragos' description of the attack, however, closely matches reports of a heating outage at the Lvivteploenergo utility around the same time, which according to local media led to a loss of heating and hot water for close to 100,000 people.
Lviv mayor Andriy Sadovyi at the time called the event a “malfunction" in a post to the messaging service Telegram, but added, “there is a suspicion of external interference in the company's work system, this information is currently being checked.” A Lvivteploenergo statement on January 23 described the outage more conclusively as the “result of a hacker attack.”
Lvivteploenergo didn't respond to WIRED's request for comment, nor did the SBU. Ukraine's cybersecurity agency, the State Services for Special Communication and Information Protection, declined to comment.
In its breakdown of the heating utility attack, Dragos says that the FrostyGoop malware was used to target ENCO control devices—Modbus-enabled industrial monitoring tools sold by the Lithuanian firm Axis Industries—and change their temperature outputs to turn off the flow of hot water. Dragos says that the hackers had actually gained access to the network months before the attack, in April 2023, by exploiting a vulnerable MikroTik router as an entry point. They then set up their own VPN connection into the network, which connected back to IP addresses in Moscow.
Despite that Russia connection, Dragos says it hasn't tied the heating utility intrusion to any known hacker group it tracks. Dragos noted in particular that it hasn't, for instance, tied the hacking to the usual suspects such as Kamacite or Electrum, Dragos' own internal names for groups more widely referred to collectively as Sandworm, a notorious unit of Russia's military intelligence agency, the GRU.
Dragos found that, while the hackers used their breach of the heating utility's network to send FrostyGoop's Modbus commands that targeted the ENCO devices and crippled the utility's service, the malware appears to have been hosted on the hackers' own computer, not on the victim's network. That means simple antivirus alone, rather than network monitoring and segmentation to protect vulnerable Modbus devices, likely won't prevent future use of the tool, warns Dragos analyst Mark “Magpie” Graham. “The fact that it can interact with devices remotely means it doesn't necessarily need to be deployed to a target environment,” Graham says. “You may potentially never see it in the environment, only its effects.”
While the ENCO devices in the Lviv heating utility were targeted from within the network, Dragos also warns that the earlier version of FrostyGoop it found was configured to target an ENCO device that was instead publicly accessible over the open internet. In its own scans, Dragos says it found at least 40 such ENCO devices that were similarly left vulnerable online. The company warns that there may in fact be tens of thousands of other Modbus-enabled devices connected to the internet that could potentially be targeted in the same way. “We think that FrostyGoop would be able to interact with a huge number of these devices, and we're in the process of conducting research to verify which devices would indeed be vulnerable,” Graham says.
While Dragos hasn't officially linked the Lviv attack to the Russian government, Graham himself doesn't shy away from describing the attack as a part of Russia's war against the country—a war that has brutally decimated Ukrainian critical infrastructure with bombs since 2022 and with cyberattacks starting far earlier, since 2014. He argues that the digital targeting of heating infrastructure in the midst of Ukraine's winter may actually be a sign that Ukrainians' increasing ability to shoot down Russian missiles has pushed Russia back to hacking-based sabotage, particularly in western Ukraine. “Cyber may actually be more efficient or likely to be successful towards a city over there, while kinetic weapons are maybe still successful at a closer range," Graham says. “They’re trying to use the full spectrum, the full gamut of available tools in the armory.”
Even as those tools evolve, though, Graham describes the hackers' goals in terms that have changed little in Russia's decade-long history of terrorizing its neighbor: psychological warfare aimed at undermining Ukraine's will to resist. “This is how you chip away at the will of the people,” says Graham. “It wasn’t aimed at disrupting the heating for all of winter. But enough to make people to think, is this the right move? Do we continue to fight?”
9 notes
·
View notes
Video
youtube
Is FREE Truly FREE - Malwarebytes
#youtube#Malwarebytes free antivirus cybersecurity review malware protection premium freemium security
0 notes
Text
5 Ways to Improve Your Network Security
In today’s digital age, network security is more critical than ever. With cyberattacks becoming more sophisticated and frequent, businesses and individuals alike must take proactive steps to protect their networks. Whether you’re a small business owner or a tech-savvy professional, improving your network security can help safeguard sensitive data, prevent downtime, and maintain trust. Here are five actionable tips to enhance your network’s defenses.
1. Use Strong, Unique Passwords
Weak or reused passwords are among the most common vulnerabilities in network security. To protect your network:
Create strong passwords that include a mix of uppercase and lowercase letters, numbers, and special characters.
Avoid using easily guessed information, such as birthdays or common words like "password123."
Use a password manager to generate and securely store complex passwords for all your accounts.
Implement multi-factor authentication (MFA) for an extra layer of security. MFA requires users to verify their identity through a second method, such as a text message code or biometric scan.
2. Keep Your Software Up-to-Date
Outdated software is a goldmine for hackers who exploit known vulnerabilities. Regular updates ensure you’re protected with the latest security patches.
Update your operating system, applications, and firmware regularly.
Enable automatic updates to ensure critical patches are installed promptly.
Replace unsupported or obsolete hardware and software with newer, more secure alternatives.
3. Secure Your Wi-Fi Network
Your Wi-Fi network is a primary gateway for potential attacks. Securing it is essential:
Change the default administrator username and password for your router.
Use WPA3 encryption (or at least WPA2) to secure your wireless connection.
Hide your network's SSID (Service Set Identifier) so it’s not visible to unauthorized users.
Set up a guest network for visitors, keeping them isolated from your primary network.
4. Install and Update Security Software
Comprehensive security software is your first line of defense against malicious activity.
Use antivirus and anti-malware programs to detect and remove threats.
Install a firewall to monitor and block unauthorized access to your network.
Invest in a Unified Threat Management (UTM) system, which combines multiple security features like intrusion detection, content filtering, and VPN support.
Keep all security software updated to stay protected from the latest threats.
5. Educate and Train Users
Even the most robust security measures can fail if users are unaware of best practices.
Train your team to recognize phishing emails, suspicious links, and social engineering tactics.
Encourage employees to report unusual activity immediately.
Establish a network security policy that outlines acceptable use, password protocols, and steps for reporting incidents.
Conduct regular cybersecurity awareness sessions to keep users informed about emerging threats.
Bonus Tip: Monitor Your Network Activity
Proactively monitoring your network can help you detect potential issues before they become critical. Use tools to track unusual traffic, failed login attempts, and other red flags.
Conclusion
Improving your network security doesn’t have to be overwhelming. By implementing these five steps, you can significantly reduce your risk of cyberattacks and create a safer environment for your business or personal network. Remember, cybersecurity is an ongoing process—stay vigilant, keep learning, and adapt to new threats as they arise.
Have questions or need help securing your network? Contact us today for expert IT solutions tailored to your needs!
4 notes
·
View notes
Text

Some rogue antivirus programs in 2024 pose serious risks, disguising themselves as security tools while stealing data or installing malware. These fake antiviruses often exploit users through phishing scams or unverified downloads. To stay safe, rely on trusted brands, verify software sources, and avoid suspicious offers promising "instant protection."
https://bit.ly/3ZKGI6M
3 notes
·
View notes
Text
The Ultimate Guide to Downloading Erome Videos

Erome is a popular platform for sharing and viewing user-generated adult content. However, it does not provide a built-in download option. If you want to save videos for offline viewing, you need an Erome downloader. In this guide, we will explore the best ways to download Erome videos safely and efficiently.
Why Use an Erome Downloader?
Many users want to download Erome videos for personal use. Here are a few reasons why:
Offline Viewing – Watch videos anytime without an internet connection.
Backup Content – Save your favorite videos before they get removed.
Better Streaming – Avoid buffering issues by watching videos offline.
Sharing Convenience – Easily transfer videos between devices.
Archival Purpose – Store important content for future reference.
Is Downloading Erome Videos Legal?
Before downloading any content, ensure that you have permission from the original uploader. Downloading copyrighted material without consent can violate terms of service and legal guidelines. Always respect the rights of content creators and adhere to copyright laws in your region.
Best Methods to Download Erome Videos
Here are the top methods to download videos from Erome.com:
1. Using an Online Erome Downloader
Several online tools allow users to paste a video URL and download it. These services are easy to use but may contain ads or require sign-ups.
Steps:
Visit a trusted online Erome downloader website.
Copy the Erome video URL.
Paste the URL into the downloader.
Click “Download” and choose the desired format.
Save the video to your device.
2. Using Browser Extensions
Browser extensions can help download videos directly from Erome. Some popular options include:
Video DownloadHelper (Firefox & Chrome)
Flash Video Downloader
SaveFrom.net Helper
Steps:
Install the extension on your browser.
Open the Erome video.
Click the extension icon to start the download.
Choose the format and save the file.
3. Using Developer Tools (Manual Method)
If you prefer a manual approach, you can use browser developer tools.
Steps:
Open the Erome video page.
Press F12 or right-click and select Inspect.
Go to the Network tab and filter for Media.
Locate the video file URL and copy it.
Open the link in a new tab and save the video.
4. Using a Dedicated Software
There are software programs designed for downloading videos, such as:
JDownloader
4K Video Downloader
YTD Video Downloader
These tools offer advanced features, including batch downloads, high-quality formats, and faster speeds.
How to Stay Safe When Using an Erome Downloader
Downloading videos from third-party tools comes with risks. Follow these safety tips:
Avoid Malware – Use only trusted websites and software.
Use a VPN – Protect your identity and browsing data.
Check Permissions – Ensure you have permission to download videos.
Update Antivirus Software – Protect against potential security threats.
Be Wary of Phishing Scams – Avoid suspicious websites asking for personal information.
Conclusion
An Erome downloader makes it easy to save videos for offline viewing. Whether you use an online tool, browser extension, or software, always prioritize safety and legal considerations. Choose the best method that suits your needs and enjoy seamless downloads. By following best practices, you can ensure a secure and hassle-free downloading experience.
5 notes
·
View notes
Text
Protecting Patients, Protecting Data: Cybersecurity in Healthcare

The healthcare industry holds some of the most sensitive information imaginable: patient medical records, personal details, insurance information, and more. This makes it a prime target for cyberattacks. A data breach in healthcare can have devastating consequences, impacting patient privacy, disrupting operations, and even endangering lives. Therefore, robust cybersecurity measures are not just recommended in healthcare – they are absolutely essential.
The Stakes are High: Cybersecurity Threats in Healthcare
Healthcare organizations face a range of cyber threats, including:
Ransomware: Attackers encrypt critical systems and data, holding them hostage until a ransom is paid. This can disrupt patient care, delay treatments, and even shut down hospitals.
Phishing: Deceptive emails or messages trick employees into revealing login credentials or downloading malware, providing attackers with access to sensitive data.
Data Breaches: Unauthorized access and exfiltration of patient medical records, leading to privacy violations and potential identity theft.
Malware: Malicious software designed to damage systems, steal data, or disrupt operations.
Insider Threats: Malicious or accidental actions by employees or other insiders that compromise security.
IoT Vulnerabilities: Connected medical devices, while offering many benefits, can also introduce security vulnerabilities if not properly secured.
Building a Strong Defense: Essential Cybersecurity Measures in Healthcare
Protecting patient data and ensuring business continuity requires a multi-layered approach to cybersecurity. Here are some crucial measures:
Risk Assessment and Management: Regularly assessing cybersecurity risks and developing a comprehensive risk management plan is the foundation of a strong security posture.
Data Encryption: Encrypting sensitive data, both in transit and at rest, protects it even if a breach occurs. This is a critical requirement for HIPAA compliance.
Access Control and Authentication: Implementing strong access controls and multi-factor authentication (MFA) ensures that only authorized personnel can access sensitive data.
Network Segmentation: Dividing the network into smaller, isolated segments limits the impact of a breach. If one segment is compromised, the others remain protected.
Firewall Management: Implementing and regularly updating firewalls to control network traffic and block unauthorized access.
Intrusion Detection/Prevention Systems (IDS/IPS): These systems monitor network traffic for suspicious activity and can automatically block malicious traffic.
Antivirus and Anti-malware Software: Deploying robust antivirus and anti-malware software on all endpoints (computers, servers, mobile devices) is essential. Regular updates are crucial.
Regular Security Audits and Vulnerability Assessments: Regularly assessing systems for vulnerabilities and conducting security audits helps identify weaknesses before they can be exploited.
Employee Training and Awareness: Human error is a major factor in many security breaches. Regular cybersecurity awareness training for all healthcare staff is vital. This training should cover topics like phishing awareness, password security, HIPAA compliance, and safe computing practices.
Incident Response Plan: Having a well-defined incident response plan in place allows healthcare organizations to react quickly and effectively to a security incident, minimizing damage and downtime.
IoT Security: Securing connected medical devices and other IoT devices is crucial to prevent them from becoming entry points for attackers. This includes regular updates, strong passwords, and network segmentation.
HIPAA Compliance: A Critical Component
The Health Insurance Portability and Accountability Act (HIPAA) sets strict standards for protecting the privacy and security 1 of patient health information. Healthcare organizations must comply with HIPAA regulations, which include implementing administrative, physical, and technical safeguards.
Xaltius Academy's Cybersecurity Course: Your Partner in Healthcare Security
Protecting patient data and ensuring HIPAA compliance requires specialized knowledge and skills. Xaltius Academy's cybersecurity course provides comprehensive training and equips you with the expertise needed to safeguard healthcare systems and data. Our expert instructors and hands-on labs will prepare you to tackle the unique cybersecurity challenges facing the healthcare industry. Invest in your cybersecurity future and protect the valuable information entrusted to healthcare organizations.
Conclusion
Cybersecurity is not just a technical issue in healthcare; it's a patient safety issue. By implementing these essential cybersecurity measures, fostering a culture of security awareness, and investing in cybersecurity training, healthcare organizations can protect patient data, maintain operational integrity, and ensure the delivery of safe and effective care.
2 notes
·
View notes