#Network & printer setup
Explore tagged Tumblr posts
Text
https://ij.start-canon.com
Get Started with canon printer network.
1 note
·
View note
Text
#Connect to MG7780 over LAN network#MG7780 LAN setup#Canon MG7780 wired connection#MG7780 wireless LAN#add MG7780 to network#install MG7780 printer drivers#MG7780 IP address setup#Canon PRINT app MG7780#troubleshoot MG7780 network issues
0 notes
Text
SSTech Networking is India's Top IT Service Provider, Fulfilling a Range of Needs.
In the quickly advancing universe of information innovation, organizations in India are progressively depending on complete IT solutions to remain competitive. One standout player in this field is SSTech Networking, a main IT specialist co-op that has gained notoriety for conveying a wide range of services, going from cloud computing to computer customization.
Cloud Computing Greatness
SSTech Networking is at the forefront of the cloud computing insurgency, offering organizations adaptable and secure solutions that influence the force of the cloud. From cloud-based capacity to cutting edge computing assets, the organization guarantees that its clients can outfit the maximum capacity of cloud innovation, upgrading flexibility and proficiency in their tasks.
Computer Cleaning and Maintenance
Perceiving the significance of all around kept up with computer frameworks, SSTech Networking gives exhaustive computer cleaning services. Standard cleaning works on the longevity of hardware as well as guarantees ideal performance. SSTech Networking's careful way to deal with computer maintenance assists clients with keeping away from possible issues, adding to a smoother and more solid computing experience.
Custom Computer Building and Upgrades
For organizations with explicit computing prerequisites, SSTech Networking offers custom computer building services. Customized to individual requirements, these solutions ensure that the hardware meets the specific determinations of the client. Additionally, the organization succeeds in computer upgrades, staying up with the latest with the furthest down the line innovation to improve performance and productivity.
Complete Hardware and Software Installation
SSTech Networking's expertise reaches out to exhaustive hardware and software installation services. Whether it's setting up a new computer, designing software applications, or coordinating new hardware parts, the organization guarantees a consistent installation process. This tender loving care assists clients with streamlining their IT framework for most extreme productivity.
Mac Services for Apple Enthusiasts
Understanding the interesting prerequisites of Mac clients, SSTech Networking offers specific types of assistance for the Apple environment. From Mac setup to investigating and maintenance, the organization's experts are knowledgeable in the complexities of Apple innovation, guaranteeing that Mac clients experience smooth and effective computing.
Network and Printer Setup
SSTech Networking goes past individual gadgets, offering master network and printer setup services. The organization guarantees that networks are designed for ideal performance and security, while printers are flawlessly incorporated into the general framework. This comprehensive way to deal with IT framework setup adds to a strong and productive working environment climate.
New Computer Setup and Fast Arrangement
Organizations frequently need to set up new computer frameworks rapidly and proficiently. SSTech Networking succeeds in fast sending, guaranteeing that new computers are designed, associated with networks, and prepared for use in the most limited conceivable time. This assistance is especially significant for organizations going through extensions or upgrades.
Repair and Maintenance Expertise
In case of hardware or software issues, SSTech Networking gives fast and powerful repair and maintenance services. The organization's talented professionals analyze and determine issues effectively, limiting personal time and guaranteeing that clients can continue their activities with negligible disturbance.
Server Support for Vigorous Tasks
Perceiving the critical job servers play in present day business tasks, SSTech Networking offers extensive server support services. From setup to maintenance and investigating, the organization guarantees that servers work at max execution, supporting the reliability and scalability of the clients' IT foundation.
About conclusion,
SSTech Networking stands out as a flexible and dependable IT specialist co-op in India, tending to the different requirements of organizations across different areas. From cloud computing to computer customization, hardware and software installation to server support, the organization's extensive scope of services positions it as a go-to accomplice for organizations hoping to improve their IT capabilities. SSTech Networking's commitment to greatness and customer fulfillment concretes its status as a forerunner in India's competitive IT services landscape.
#Cloud computing#Computer cleaning#Computer Customization#Computer upgrades#Custom Computer Building#Hardware & software installation#Mac#Network & printer setup#New computer setup#Repair & maintenance#Screen replacement#Server support
0 notes
Text
There Were Always Enshittifiers
I'm on a 20+ city book tour for my new novel PICKS AND SHOVELS. Catch me in DC TONIGHT (Mar 4), and in RICHMOND TOMORROW (Mar 5). More tour dates here. Mail-order signed copies from LA's Diesel Books.

My latest Locus column is "There Were Always Enshittifiers." It's a history of personal computing and networked communications that traces the earliest days of the battle for computers as tools of liberation and computers as tools for surveillance, control and extraction:
https://locusmag.com/2025/03/commentary-cory-doctorow-there-were-always-enshittifiers/
The occasion for this piece is the publication of my latest Martin Hench novel, a standalone book set in the early 1980s called "Picks and Shovels":
https://us.macmillan.com/books/9781250865908/picksandshovels
The MacGuffin of Picks and Shovels is a "weird PC" company called Fidelity Computing, owned by a Mormon bishop, a Catholic priest, and an orthodox rabbi. It sounds like the setup for a joke, but the punchline is deadly serious: Fidelity Computing is a pyramid selling cult that preys on the trust and fellowship of faith groups to sell the dreadful Fidelity 3000 PC and its ghastly peripherals.
You see, Fidelity's products are booby-trapped. It's not merely that they ship with programs whose data-files can't be read by apps on any other system – that's just table stakes. Fidelity's got a whole bag of tricks up its sleeve – for example, it deliberately damages a specific sector on every floppy disk it ships. The drivers for its floppy drive initialize any read or write operation by checking to see if that sector can be read. If it can, the computer refuses to recognize the disk. This lets the Reverend Sirs (as Fidelity's owners style themselves) run a racket where they sell these deliberately damaged floppies at a 500% markup, because regular floppies won't work on the systems they lure their parishioners into buying.
Or take the Fidelity printer: it's just a rebadged Okidata ML-80, the workhorse tractor feed printer that led the market for years. But before Fidelity ships this printer to its customers, they fit it with new tractor feed sprockets whose pins are slightly more widely spaced than the standard 0.5" holes on the paper you can buy in any stationery store. That way, Fidelity can force its customers to buy the custom paper that they exclusively peddle – again, at a massive markup.
Needless to say, printing with these wider sprocket holes causes frequent jams and puts a serious strain on the printer's motors, causing them to burn out at a high rate. That's great news – for Fidelity Computing. It means they get to sell you more overpriced paper so you can reprint the jobs ruined by jams, and they can also sell you their high-priced, exclusive repair services when your printer's motors quit.
Perhaps you're thinking, "OK, but I can just buy a normal Okidata printer and use regular, cheap paper, right?" Sorry, the Reverend Sirs are way ahead of you: they've reversed the pinouts on their printers' serial ports, and a normal printer won't be able to talk to your Fidelity 3000.
If all of this sounds familiar, it's because these are the paleolithic ancestors of today's high-tech lock-in scams, from HP's $10,000/gallon ink to Apple and Google's mobile app stores, which cream a 30% commission off of every dollar collected by an app maker. What's more, these ancient, weird misfeatures have their origins in the true history of computing, which was obsessed with making the elusive, copy-proof floppy disk.
This Quixotic enterprise got started in earnest with Bill Gates' notorious 1976 "open letter to hobbyists" in which the young Gates furiously scolds the community of early computer hackers for its scientific ethic of publishing, sharing and improving the code that they all wrote:
https://en.wikipedia.org/wiki/An_Open_Letter_to_Hobbyists
Gates had recently cloned the BASIC programming language for the popular Altair computer. For Gates, his act of copying was part of the legitimate progress of technology, while the copying of his colleagues, who duplicated Gates' Altair BASIC, was a shameless act of piracy, destined to destroy the nascent computing industry:
As the majority of hobbyists must be aware, most of you steal your software. Hardware must be paid for, but software is something to share. Who cares if the people who worked on it get paid?
Needless to say, Gates didn't offer a royalty to John Kemeny and Thomas Kurtz, the programmers who'd invented BASIC at Dartmouth College in 1963. For Gates – and his intellectual progeny – the formula was simple: "When I copy you, that's progress. When you copy me, that's piracy." Every pirate wants to be an admiral.
For would-be ex-pirate admirals, Gates's ideology was seductive. There was just one fly in the ointment: computers operate by copying. The only way a computer can run a program is to copy it into memory – just as the only way your phone can stream a video is to download it to its RAM ("streaming" is a consensus hallucination – every stream is a download, and it has to be, because the internet is a data-transmission network, not a cunning system of tubes and mirrors that can make a picture appear on your screen without transmitting the file that contains that image).
Gripped by this enshittificatory impulse, the computer industry threw itself headfirst into the project of creating copy-proof data, a project about as practical as making water that's not wet. That weird gimmick where Fidelity floppy disks were deliberately damaged at the factory so the OS could distinguish between its expensive disks and the generic ones you bought at the office supply place? It's a lightly fictionalized version of the copy-protection system deployed by Visicalc, a move that was later publicly repudiated by Visicalc co-founder Dan Bricklin, who lamented that it confounded his efforts to preserve his software on modern systems and recover the millions of data-files that Visicalc users created:
http://www.bricklin.com/robfuture.htm
The copy-protection industry ran on equal parts secrecy and overblown sales claims about its products' efficacy. As a result, much of the story of this doomed effort is lost to history. But back in 2017, a redditor called Vadermeer unearthed a key trove of documents from this era, in a Goodwill Outlet store in Seattle:
https://www.reddit.com/r/VintageApple/comments/5vjsow/found_internal_apple_memos_about_copy_protection/
Vaderrmeer find was a Apple Computer binder from 1979, documenting the company's doomed "Software Security from Apple's Friends and Enemies" (SSAFE) project, an effort to make a copy-proof floppy:
https://archive.org/details/AppleSSAFEProject
The SSAFE files are an incredible read. They consist of Apple's best engineers beavering away for days, cooking up a new copy-proof floppy, which they would then hand over to Apple co-founder and legendary hardware wizard Steve Wozniak. Wozniak would then promptly destroy the copy-protection system, usually in a matter of minutes or hours. Wozniak, of course, got the seed capital for Apple by defeating AT&T's security measures, building a "blue box" that let its user make toll-free calls and peddling it around the dorms at Berkeley:
https://512pixels.net/2018/03/woz-blue-box/
Woz has stated that without blue boxes, there would never have been an Apple. Today, Apple leads the charge to restrict how you use your devices, confining you to using its official app store so it can skim a 30% vig off every dollar you spend, and corralling you into using its expensive repair depots, who love to declare your device dead and force you to buy a new one. Every pirate wants to be an admiral!
https://www.vice.com/en/article/tim-cook-to-investors-people-bought-fewer-new-iphones-because-they-repaired-their-old-ones/
Revisiting the early PC years for Picks and Shovels isn't just an excuse to bust out some PC nostalgiacore set-dressing. Picks and Shovels isn't just a face-paced crime thriller: it's a reflection on the enshittificatory impulses that were present at the birth of the modern tech industry.
But there is a nostalgic streak in Picks and Shovels, of course, represented by the other weird PC company in the tale. Computing Freedom is a scrappy PC startup founded by three women who came up as sales managers for Fidelity, before their pangs of conscience caused them to repent of their sins in luring their co-religionists into the Reverend Sirs' trap.
These women – an orthodox lesbian whose family disowned her, a nun who left her order after discovering the liberation theology movement, and a Mormon woman who has quit the church over its opposition to the Equal Rights Amendment – have set about the wozniackian project of reverse-engineering every piece of Fidelity hardware and software, to make compatible products that set Fidelity's caged victims free.
They're making floppies that work with Fidelity drives, and drives that work with Fidelity's floppies. Printers that work with Fidelity computers, and adapters so Fidelity printers will work with other PCs (as well as resprocketing kits to retrofit those printers for standard paper). They're making file converters that allow Fidelity owners to read their data in Visicalc or Lotus 1-2-3, and vice-versa.
In other words, they're engaged in "adversarial interoperability" – hacking their own fire-exits into the burning building that Fidelity has locked its customers inside of:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
This was normal, back then! There were so many cool, interoperable products and services around then, from the Bell and Howell "Black Apple" clones:
https://forum.vcfed.org/index.php?threads%2Fbell-howell-apple-ii.64651%2F
to the amazing copy-protection cracking disks that traveled from hand to hand, so the people who shelled out for expensive software delivered on fragile floppies could make backups against the inevitable day that the disks stopped working:
https://en.wikipedia.org/wiki/Bit_nibbler
Those were wild times, when engineers pitted their wits against one another in the spirit of Steve Wozniack and SSAFE. That era came to a close – but not because someone finally figured out how to make data that you couldn't copy. Rather, it ended because an unholy coalition of entertainment and tech industry lobbyists convinced Congress to pass the Digital Millennium Copyright Act in 1998, which made it a felony to "bypass an access control":
https://www.eff.org/deeplinks/2016/07/section-1201-dmca-cannot-pass-constitutional-scrutiny
That's right: at the first hint of competition, the self-described libertarians who insisted that computers would make governments obsolete went running to the government, demanding a state-backed monopoly that would put their rivals in prison for daring to interfere with their business model. Plus ça change: today, their intellectual descendants are demanding that the US government bail out their "anti-state," "independent" cryptocurrency:
https://www.citationneeded.news/issue-78/
In truth, the politics of tech has always contained a faction of "anti-government" millionaires and billionaires who – more than anything – wanted to wield the power of the state, not abolish it. This was true in the mainframe days, when companies like IBM made billions on cushy defense contracts, and it's true today, when the self-described "Technoking" of Tesla has inserted himself into government in order to steer tens of billions' worth of no-bid contracts to his Beltway Bandit companies:
https://www.reuters.com/world/us/lawmakers-question-musk-influence-over-verizon-faa-contract-2025-02-28/
The American state has always had a cozy relationship with its tech sector, seeing it as a way to project American soft power into every corner of the globe. But Big Tech isn't the only – or the most important – US tech export. Far more important is the invisible web of IP laws that ban reverse-engineering, modding, independent repair, and other activities that defend American tech exports from competitors in its trading partners.
Countries that trade with the US were arm-twisted into enacting laws like the DMCA as a condition of free trade with the USA. These laws were wildly unpopular, and had to be crammed through other countries' legislatures:
https://pluralistic.net/2024/11/15/radical-extremists/#sex-pest
That's why Europeans who are appalled by Musk's Nazi salute have to confine their protests to being loudly angry at him, selling off their Teslas, and shining lights on Tesla factories:
https://www.malaymail.com/news/money/2025/01/24/heil-tesla-activists-protest-with-light-projection-on-germany-plant-after-musks-nazi-salute-video/164398
Musk is so attention-hungry that all this is as apt to please him as anger him. You know what would really hurt Musk? Jailbreaking every Tesla in Europe so that all its subscription features – which represent the highest-margin line-item on Tesla's balance-sheet – could be unlocked by any local mechanic for €25. That would really kick Musk in the dongle.
The only problem is that in 2001, the US Trade Rep got the EU to pass the EU Copyright Directive, whose Article 6 bans that kind of reverse-engineering. The European Parliament passed that law because doing so guaranteed tariff-free access for EU goods exported to US markets.
Enter Trump, promising a 25% tariff on European exports.
The EU could retaliate here by imposing tit-for-tat tariffs on US exports to the EU, which would make everything Europeans buy from America 25% more expensive. This is a very weird way to punish the USA.
On the other hand, not that Trump has announced that the terms of US free trade deals are optional (for the US, at least), there's no reason not to delete Article 6 of the EUCD, and all the other laws that prevent European companies from jailbreaking iPhones and making their own App Stores (minus Apple's 30% commission), as well as ad-blockers for Facebook and Instagram's apps (which would zero out EU revenue for Meta), and, of course, jailbreaking tools for Xboxes, Teslas, and every make and model of every American car, so European companies could offer service, parts, apps, and add-ons for them.
When Jeff Bezos launched Amazon, his war-cry was "your margin is my opportunity." US tech companies have built up insane margins based on the IP provisions required in the free trade treaties it signed with the rest of the world.
It's time to delete those IP provisions and throw open domestic competition that attacks the margins that created the fortunes of oligarchs who sat behind Trump on the inauguration dais. It's time to bring back the indomitable hacker spirit that the Bill Gateses of the world have been trying to extinguish since the days of the "open letter to hobbyists." The tech sector built a 10 foot high wall around its business, then the US government convinced the rest of the world to ban four-metre ladders. Lift the ban, unleash the ladders, free the world!
In the same way that futuristic sf is really about the present, Picks and Shovels, an sf novel set in the 1980s, is really about this moment.
I'm on tour with the book now – if you're reading this today (Mar 4) and you're in DC, come see me tonight with Matt Stoller at 6:30PM at the Cleveland Park Library:
https://www.loyaltybookstores.com/picksnshovels
And if you're in Richmond, VA, come down to Fountain Bookshop and catch me with Lee Vinsel tomorrow (Mar 5) at 7:30PM:
https://fountainbookstore.com/events/1795820250305

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/03/04/object-permanence/#picks-and-shovels
#pluralistic#picks and shovels#history#web theory#marty hench#martin hench#red team blues#locus magazine#drm#letter to computer hobbyists#bill gates#computer lib#science fiction#crime fiction#detective fiction
498 notes
·
View notes
Text
2035
I'm interrupted from configuring a new barebones Linux install (it'll work and be stable this time I swear) by a 'whuump' noise.
I check the pneumatic mail tube in my room (we installed them so we can communicate across the house quickly)
It's a picture of my wife's breasts, printed out by a dot matrix printer she's been restoring.
I sit down to finish configuring the ultimate Emacs setup when another loud noise disturbs me.
It's the potato canon we setup to shoot down advertising drones.
They've been turning up with increasing regularity - since we have network level ad blocking and pirate everything - the implant hijacking ads don't reach us, and Amazon are getting desperate.
My other wife goes to scavenge parts for our home Cinema setup.
305 notes
·
View notes
Text
people will call you a printer genius for just carrying around a USB type B cable and foregoing the network setup bullshit
39 notes
·
View notes
Text
Network switches
What’s a network switch ?
A switch is a device used in computer networks to connect multiple devices together within a single local area network (LAN). Its main role is to facilitate communication between different connected devices, such as computers, printers, servers, IP phones, etc.
It is a mini-computer which is made up of RAM, ROM, flash RAM, NVRAM, a microprocessor, connectivity ports and even an operating system.

RAM
RAM (Random Access Memory) contains the current configuration of the switch and temporarily stores the MAC address table, which is then processed by the microprocessor.
Microprocessor
The microprocessor is the heart of the switch, responsible for data processing, including switching and creating links between multiple devices.
External memories
External memories, such as flash RAM, ROM, and NVRAM (Non-Volatile RAM), store configuration files , different versions of the IOS , etc ...
Ports
The switch ports are the communication interfaces of the switch. There are several of them, generally 24 for a Cisco switch. Each port is associated with an LED which indicates its status and activity.

How does it work ?
Now how does a switch work to transfer information from one machine to another?
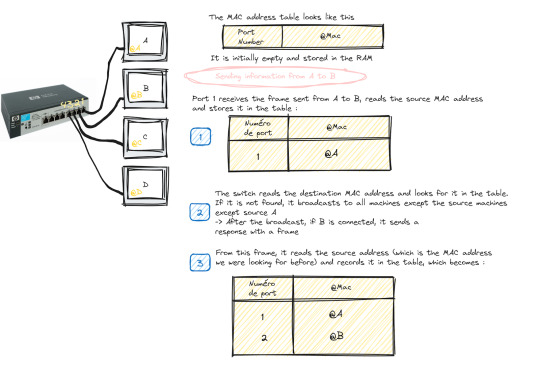
Suppose we have 4 machines: A, B, C and D connected to our switch in ports 1, 2, 3 and 4 as follows:

The switch only works with MAC addresses , so basically we have an empty MAC address table stored in RAM as soon as the switch starts up which looks like this :

Transmitting data from machine A to machine B happens in the following steps:
Machine A sends a frame to machine B
Once this frame arrives at port 1 (which is the one linked to A), the switch reads the source MAC address and stores it in the MAC address table
The switch reads the destination MAC address and looks for it in the table, if it is not in the table, it broadcasts to all the active machines connected to the switch except the source one.
If the port linked to the machine we want is active, it sends a response frame from which the switch reads the MAC address we were looking for (@B)
Once done, it records the MAC address of B in the table.

This process repeats until the switch reaches what is called "MAC address table stability", that is to say it knows all the MAC addresses of the connected machines and has no more need to broadcast.
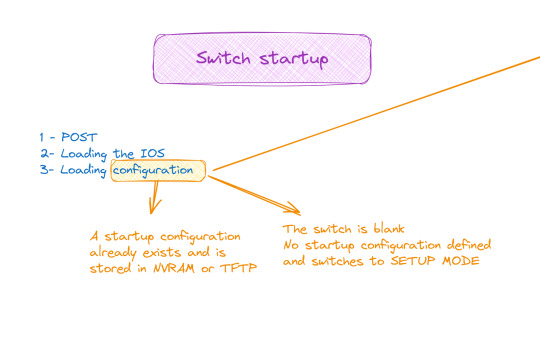
Starting and configuring a switch
When it comes to booting a switch, the process is similar to that of a traditional computer system:
POST (Power-On Self Test): The switch performs proper functioning tests on all hardware.
Loading IOS (Internetwork Operating System): The switch operating system is loaded.
Loading the configuration. At this stage we have two cases:
Either the switch already has a startup configuration defined and stored in NVRAM
Either the switch is blank and it is up to us to define the startup configuration when it goes to setup mode
Switch configuration

The configuration of a switch is done through different modes, such as user mode, privileged mode and global configuration mode, which allows access to specific configuration modes, such as interface mode, routing mode, line mode, etc.
And to do all this of course you must first connect the switch with the machine via the console cable and open a terminal emulator
💡 It should be noted that the only machine that can configure the switch is the one connected to it by a console cable, the others are only hosts.
#software#network switches#codeblr#code#css#html#javascript#java development company#python#studyblr#progblr#programming#comp sci#web design#web developers#web development#website design#webdev#website#tech#html css#learn to code
98 notes
·
View notes
Text
This is the first time I can remember where i've been able to truley go all out on something:




I bought a 3d printer. BUT, this time I didn't do my normal thing - buying the cheap and/or DIY version and building it myself, probably also trying to mod it on the way. THIS time I bought a prebuilt printer!
3D printers are maddening, like normal paper printers but with a middle finger jammed in your eye, or at least they were when i was in college 10 years ago! I tried going the cheap route then, building a kit, and it just ruined printing for me for a full decade. Horrible instructions, no support, and printers just in general didn't have all the QOL features of modern printers. All that means that it was a struggle just to assemble the thing properly, then things like manual bed levelling, extruder setup, all this crap made for a terrible waste of my free time betwern classes.
Now, 10 years later, I wanted to have a printer, NOT as a hobby (I've already got plenty of those), but as a tool, a way to make silly little parts I cook up in my head, and tools should JUST WORK! And I finally have a few extra bucks to spare on a nice tool.
So, I bought a fully assembled Prusa Core One printer! Printing with this is like a whole other universe compared to my college days! The manufacturer has a beautiful slicer (with linux support!) and the printer has all the built in features that I want, in particular LOCAL NETWORK ONLY online monitoring!
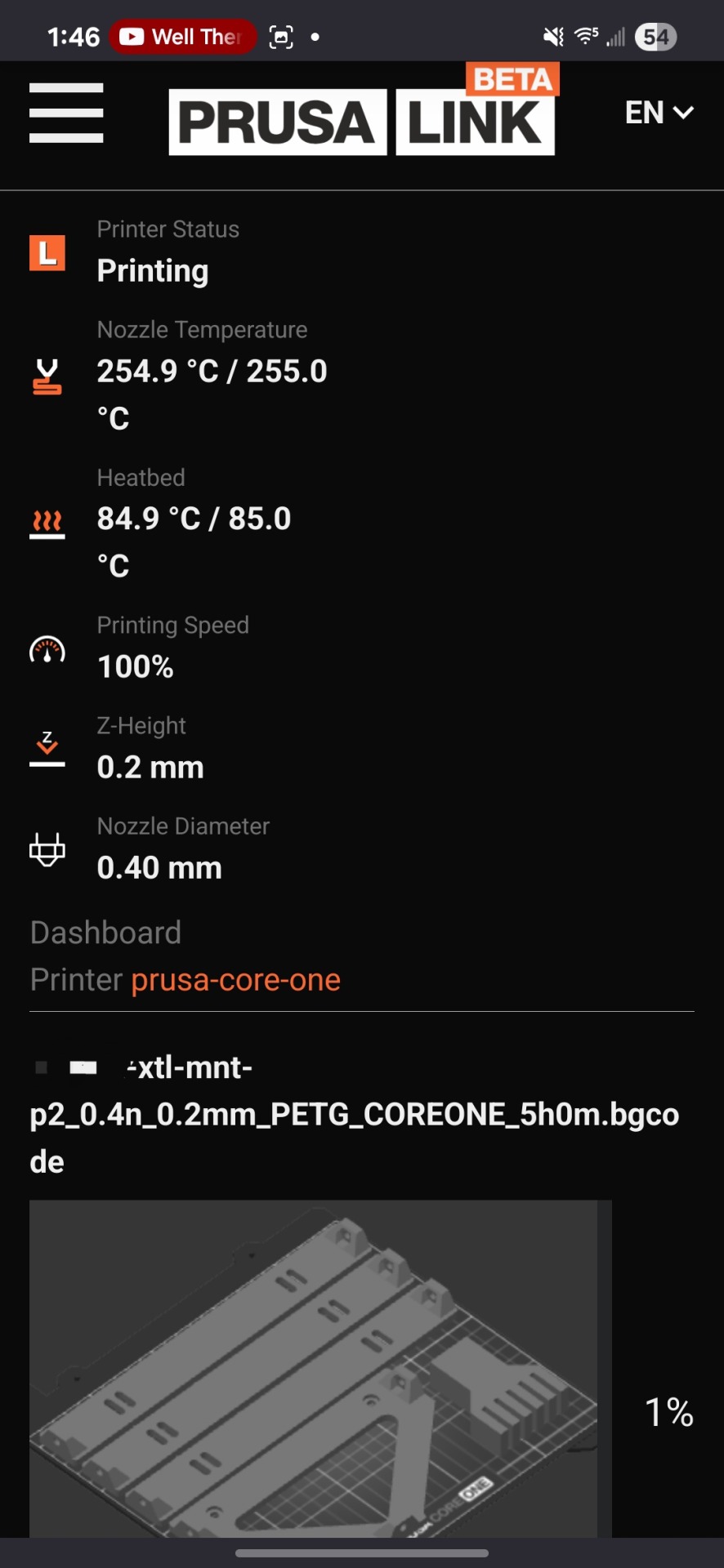
The reason I chose Prusa over Bamboo Labs is because of this; Bamboo printers have to go through their online servers to do anything remotely to their printers, and the enshittification of everything guarentees that they will either paywall it or shut it down in the future. Figured I would get ahead of that and get a printer from a company that is hacker-friendly, with fully featured offline functionality. To prove my point, I have not set up this printer online at all, just connected to my wifi, which lets me access the print status web page directly, no internet! I can also upload new print files via that page, and start prints from it, very fully featured all things considered!
That said, I do have a camera on the way, because the only way I have to monitor the print visually right now is a crappy old security "camera" that I have to refresh a webpage constantly to get individual frames, and they look like ass:


The camera is a pretty new accessory from Prusa, and currently requires linking it to a free app to use, but Prusa has a feature roadmap including LAN direct live view, so the second that drops I'm enabling that for sure! Hopefully I can factory reset the camera and re-do the serup without an online account - local only is the way to go!
Other addons I bought:
exhaust filter (some filaments have nasty by-products)
multi-filament unit (not installed yet, I'm waiting for a few more parts to show up)
sealed containers and dessicant for filament storage (some filaments absorb water, which makes them difficult to print with).
Hardened nozzle (for filaments with metal/carbon fiber fill)
taped some filter material over the air intake, to keep dust out
Right now I'm manually changing filaments until all the parts show up. Unfortunately I could not buy the printer with the filament changer pre-installed (at least, I didn't see the option). Thankfully, Prusa posts very detailed guides (with pictures!) on how to do regular maintenance and upgrades to their printers. So far, all the work I've done has been realtively easy and straightforward!
Only issue I have run into so far is a partially clogged nozzle after printing a few parts with PETG, the filament extrusion slowed to a trickle and left whisps of filament on the bed rather than actual layers. Took me a couple of tries to get it unclogged, but I think I got it! I'll know if I didn't, since parts won't print right until I do!
So excited to have what I really wanted for once - A printer I can just hit "go" on and get a part a few hours later, without yanking my hair out on the way! The future is now!
3 notes
·
View notes
Text
The biggest heist that almost was
Let me tell you about the most insane bank heist that is going to sound like I'm just leaking the script for the next American hacking movie. The goal? Steal one billion USD. And it all began with an email and a printer, which as we all know is where problems usually start. Another weapon in this heist was... Weekends and time zones.
As usual, no prior computer science education needed.
What happened?
On the morning of February 5th 2016, a printer had stopped working in the central bank of Bangladesh (Bangladesh Bank). But it wasn't just any printer, it was the printer responsible for printing all the records of the multimillion transfers going in and out of the bank. When the poor employees finally won the printer battle and had it resume normal operation, they saw a very concerning account transfer in the records that was coming out. The bank had an USD account in the USA, at Federal Reserve Bank, with approximately 1 billlion Dollars in it, and the Federal Reserve Bank had received instructions to drain almost the entire amount. In the records that came out in the printer, the American bank had attempted to urgently message the Bangladesh bank regarding this transfer, but couldn't get through to them. This was because the hack had actually started the day before, Thursday 4th, at around 20:00 Bangladesh time, when the bank was closed. However, USA had just started their day, giving the American bank plenty of time to follow through with the instructions from the Bangladesh bank to drain their entire account while they were closed. And that wasn't the end of it, as weekends are from Friday to Saturday in Bangladesh, meaning that the Bangladesh bank headquarters in Dhaka wouldn't discover this withdrawal until Sunday morning. That's when they immediately tried to reach the American bank, which of course didn't work as over there it was Saturday evening, and the American weekend is from Saturday to Sunday, meaning that they wouldn't be reachable until Monday.
You see what I mean by the hackers using time zones and weekends, finding the perfect time for the American bank to execute their orders while Bangladesh discovers the withdrawal several days too late, and again several days too late for Americans to be reachable. But it didn't stop there with their timehacking.
The money had to go somewhere from the American bank, and it would be stupid to send it directly to the hackers own account without laundering the money first. So they had set up four different bank accounts in the Philippines, using fake names and credentials. Why the Philippines? Because the Lunar new year was on Monday the 8th, which is a holiday and holiday means no bank activities in either Bangladesh or the Philippines, buying the hackers even more time. As a final act, they messed with the printer responsible for printing transaction records, adding another few hours to their schedule. Moon and stars really aligned perfectly for this plan.
But how did they do it?
It all began one year prior, in January 2015, with an email sent to several employees at the Bangladesh Bank. The email seemingly contained a job application from a person who didn't actually exist, but who was very polite in his request for a position at the bank, with a link to his CV and cover letter. Naturally this link led to a document with a little surprise gift - malware. Since the heist happened, at least one of the recipients must have clicked the link, and successfully deployed a RAT - Remote Access Trojan, malware that lets you control a computer from the comfort of your own home, as well as a toolkit with various malware to move from computer to computer, avoiding discovery, and covering their tracks.
From there, the hackers slowly made their way through the bank offices network, one step at a time to avoid setting off alarms, looking for any computer that had control of the banks SWIFT setup. SWIFT lets banks transfer large amounts of money between themselves and other banks connected to SWIFT. And as soon as they found one of those computers, they stopped. They didn't need to hack SWIFT in the traditional sense of the word - since they operated in a bank computer, the SWIFT-software assumed they naturally had to be bank employees. However, one of the parts of the malware used in the heist was for manipulating the SWIFT system, as the hackers weren't physically there to press anything. Additionally, since they were laying dormant for the time to strike, they needed to keep an eye out for SWIFT updates that could detect any tampering with the system, and adapt accordingly.
Then they waited many months for the stars to align on February 4th, 2016.
There were 35 transfers made by the hackers from the American bank account, totaling almost 1 billion USD, but there were two of these tiny little seemingly insignificant details that prevented this from becoming the worlds largest bank heist in history. The hackers biggest enemy became this concept known as “words”.
The Philippine bank accounts were all located in the same RCBC Bank office on Jupiter Street in Manila. And this would be the hackers downfall, as USA had sanctions put on an Iranian cargo ship called Jupiter. Since the transactions went to a recipient that contained the word “Jupiter”, it created a security alert in the Federal Reserve Bank that the employees needed to investigate. When they saw what was going on, they managed to stop all but five of the initial 35 transactions, thus “only” roughly 100 million USD made it to the Philippines. The Bangladesh bank requested to reverse the transactions, but since the money was in the Philippines, they would need bureaucracy in form of a court order to reclaim the money, and we all know that's not a 5 minute project. It was when Bangladesh filed the court order in late February that the case became public (since court orders are public documents) and the news broke to the country.
Once in the RCBC bank accounts, the money arrived on Friday the 5th and was immediately moved again. First the 100 million was converted to local currency, and some of it was withdrawn in cash, while the rest was sent off to other hacker-controlled locations. And this is where the second tiny little detail cut off even more of the hackers precious payday. 20 million USD had been sent to Shalika Foundation, a charity organisation in Sri Lanka. But, once again the hackers worst enemy - words - decided to strike again. A typo was made in their transaction, sending the money to “Shalika Fundation”, and a bank employee who must have had their morning coffee spotted this typo and rejected the transfer and kept the funds frozen. This left the hackers with 80 million USD.
✨Now comes the money laundering!✨
There was a second reason for choosing the Philippines as deposit zone; gambling is legal and the casinos had no money laundering regulations imposed. The accomplices of the heist booked private rooms in two casinos located in Manila - Solaire and Midas - and proceeded to purchase tokens to gamble for with the stolen money. Since they played with a room consisting of their fellow accomplices, winning was not really much of a challenge. Then the tokens could be exchanged back to money that would now be clean. To avoid suspicion, they didn't gamble all of the money at once, but over the course of several weeks gambled away the dirty money to clean money.
Who was behind it?
It's normally difficult to pinpoint where the more sophisticated hacking groups come from. Oftentimes, they will leave false clues behind that points to another group so they will face more trouble instead of the group that did it. They may even place clues from several different groups, just to mess with the analysts. It's also quite common to simply “steal” a way of working from another group, or use a leaked/stolen tool from another group (criminals aren't safe from other criminals, especially not in this business) - there are new malware coming out all the time with code that is just a slight modification of a well-known malware actor that had their source code leaked or simply had hired the same programmer. Or they may leave no clues as to who was behind it. Attribution to the guilty part is usually the single most difficult mission in IT-security - often it's just pure guesswork with little to no solid evidence to back it up, if you're lucky there's circumstantial evidence.
This case was no different. The first clue came from the IP the bad guys used to connect to the Bangladesh bank from. It was located in Pyongyang, North Korea. But, as I mentioned, this is not a conclusive verdict, as the IP may simply be planted false evidence to throw the analysts off their track. After the heist, the hackers used a data-wiper to scrub as much of their malware off the bank systems, but they didn't succeed in deleting all of it, some of the tools were still present, including the wiper.
Due to the scale of this operation, it caught the attention of every single IT-security person and IT-security company worldwide, who all of course wanted to know who and how they did it. With the remaining malware, a joint effort was made, comparing malware code to other malware code for similarities. Some was found in Poland, after an analyst noted the similarities from another suspected North Korean hack. Some was found in another infamous North Korean hack targeting Sony Pictures. More and more signs pointed towards the same actor. Some were false leads, the hackers seemed to be wanting to implicate the Russians did it, but failed quite miserably at that, just sprinkling random Russian words into the malware and making it way too obvious it was a ruse.
You may not believe this, but the North Korean government has one of the most notorious hacking groups in the world, known as the Lazarus Group. Some of its more well-known adventures include an extremely data-destructive hack of Sony Pictures (as punishment for releasing “The Interview”), creation of the ransomware WannaCry which was used against many targets worldwide (including hospitals), and various attempts at gathering information from governments and government-affiliated corporations all over the world. And, of course, this heist.
Eventually, after months of collaboration all over the world, the final verdict fell on North Korea, and specifically one of their programmers. His name is Park Jin Hyok, and worked for Chosun Expo - a front company for the North Korean government, located in Dalian (China) who used the funds of the fake corporation gained from legitimate programming jobs from customers worldwide to create the malware and plan the heist with all of its expenses. Of course he wasn't the sole person involved in this project, but it's the only person we know was in it.
This particular heist had been meticulously planned for several years, and Park Jin Hyok had moved to Dalian, set up fake IDs and built a network of contacts there to avoid suspicion. However, he didn't manage to delete all of his online footprints, and became the number one suspect when his internet activities suddenly came from Pyongyang, North Korea.
Additionally, several Chinese business men - many associated with the casino industry in China's Macau territory - were also charged and arrested for assisting with setting up the gambling rooms and coordinating the money laundering process. One unknown Chinese business man managed to get away with 31 million USD of the 80 million that remained after the heist, and as you would expect, he was never to be seen again.
With the middlemen from China paid off, not much remained of the original 1 billion to North Korea. But the heist has fascinated the whole IT-security world nonetheless.
I remember when the news of this case dropped to the IT-security world, who all wanted to take part in the hunt. It was a very fun time, we were all sitting at the edge of our seats waiting for the next update. I hope it was at least somewhat exciting for you too to read about, and thank you for reading this long post! If you liked it, please consider reblogging as it motivates me to write more. You may also like malware stuff I've written about before, such as Stuxnet or just plain evil malware that is a threat to our daily lives.
As always my inbox is open if you have any questions.
94 notes
·
View notes
Text
What types of issues does technical support handle?
Technical Support Services

Technical Supporting services serve a vital role and prospect, by keeping businesses and organizations running efficiently & active by resolving their IT-related problems and issues. From minor glitches to major disruptions errors, technical support teams and professional experts help to ensure that systems remain up and running while in use, allowing the users to stay productive and alert. But what exactly do they handle? Let's take a closer look at what to look for and they assist with.
Hardware and Device Issues:
Technical supporting teams and professional experts assist with problems related to desktops, laptops, printers, scanners, and other hardware. As this includes and consists of deliverables fixing hardware failures, replacing parts, configuring devices, and troubleshooting connectivity or performance issues. Whether it's a malfunctioning keyboard or a slow-loading workstation, Technical Support is there to help.
Software Installation and Troubleshooting:
From installing and implementing the applications to resolving and assisting the software errors and glitches, technical Support guides various software-related and applications concerns and points at a time. They help and assist with updating programs, fixing bugs, assuring the overall compatibility within the operating systems, and restoring the performance if an app crashes or freezes.
Network and Connectivity Problems:
A strong network and support is the backbone of modern businesses and companies. Technical Supporting officials handle and maintain the internet issues, router configuration, VPN access, slow connection speeds, and network outages. Whether it's a minor or impactful Wi-Fi issue or a more significant server connectivity problem, the support team works to restore communication quickly.
Email and Communication Tools:
Email downtime can affect the business continuity and its proceedings. The technical supporting team manages email configuration, syncing errors, spam filters, and login issues and errors across multiple devices and platforms, including Outlook and Gmail. They also handle collaboration tools like Teams, Slack, or Zoom when they don't function as expected.
Security & Access Management:
Working professionals play an essential role in managing the IT security measures and operating parameters. While they also assist to reset passwords settings, also help to manage the user accounts, set up two-factor authentication, and address down the ongoing suspicious activity.
Personalized Help and Guidance:
From onboarding and completing setup for the new users to answering tech-related questions, technical Support assures that employees use systems efficiently. Their goal is to minimize downtime and boost productivity. Companies like Suma Soft, IBM, Cyntexa, and Cignex offer dependable technical support services tailored to your specific business needs. Their expertise helps resolve issues faster and keeps your systems up and running at all times.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
3 notes
·
View notes
Text
My mom loves her buy-nothing group. She loves a good bargain and you can't beat free.
This week she picked up a HP ink tank printer that had "wifi problems"
She had no intention of fixing that herself. She called me to fix it. "The wifi just stopped working on it one day and they couldn't get it to work again" was all I was told
I got it working in 45 minutes
I commandeered my dad's laptop and downloaded the HP app (🤮) on it and tried the setup. Couldn't connect.
I printed the information page. The wifi was turned off. There were Instructions on the key combo to turn it on and a print the Wi-Fi setup guide
I turned it on and printed the setup guide
Of the 3 pages of methods I saw USB cable and jumped on that immediately
Suddenly HP App could see the printer! Big shock. USB never lets me down. #Hardwired for life.
I went into the printer setting and added it to our wi-fi
I printed another test page. Wi-Fi is on and it has an IP adress
I unplugged the USB and tried to print. No dice. It didn't add network printing to the computer.
I try to add the printer again
It can't find it on the wifi
I punch in the IP address that it just printed out into the search bar
It found it instantly
It took 5 min to add the drivers
I tried to print
Printer is not in the printer list. It's hiding in the more options page. I print a test page from the laptop
I go on my phone and print a photo from my gallery
This printer is totally fine and has 0 issues.

5 notes
·
View notes
Text
If you need a printer (may 2025 edition)
A friend of mine asked my recommendations for a printer. I ended up writing a Thing about it, so here it is: First off: I cannot guarantee a printer that Just Works. To my knowledge, they no longer exist. If you find someone that claims otherwise, let me know. Either I will gladly learn from them or explain why they're lying.
This is not because of technical issue. There are HP laserjets from the late 90's that still work perfectly. It is exclusively because the entire printer industry is more interested in aggressive marketing and forcing subscriptions, transactions and value-adds than making reliable printers. Basically, capitalism ruined printers.
In particular, you can probably expect the printer to not work at the worst time. You might have a printer that's working perfectly and you set it aside for 3 months and then need to use it NOW because of taxes or job applications or something time-sensitive... and it just doesn't work.
It can be made to work after a few hours of annoying effort, but assume if you haven't touched your printer for a while, it will need some fiddling.
For this reason, ask yourself if you really need a printer or if it might be better to familiarize yourself with the printing services at an office supply store, library, or even a drugstore.
But if you do need a printer: Laser printers are vastly more reliable than inkjets. Inkjet cartridges dry out, laser toner is forever.
There is no good printer under $100. You are basically buying a single use printer. If by some miracle it lasts long enough for the ink to run out, the ink will cost so much that you will lose all the money you saved at the initial purchase.
That said, I will try to get you the most reliable setup possible. The most reliable setup is one computer printing over a USB cable to one printer. As soon as you add network printing, cloud printing, printing from your phone... these are all things that love to break.
Almost every printer has wifi printing and the setup routine will try to railroad you into that option, but if you force a USB connection you will be happier in the long run.
You can no longer trust wirecutter for printers. They have made some terrible recommendations.
As of May 2025, This is the best combo of cheap and reliable printer you're going to find:
If you need a printer-scanner-copier... do you really? Because these are all things that, again, love to break. The above option is far more reliable.
but if you really need one, I guess this is the least bad option.
https://www.brother-usa.com/products/mfcl2820dw
2 notes
·
View notes
Text
Professional IT Support Services: Troubleshooting, Setup, and Solutions for Your Business
I offer professional IT support services to help solve all your technology problems, whether you're a small business, freelancer, or individual. I specialize in providing fast, efficient, and cost-effective solutions for a wide range of IT issues. With years of experience in the industry, I’m here to make your technology work for you!
🔧 What I can help you with:
Tech troubleshooting for software and hardware issues
Network setup and configuration
Virus/malware removal and protection
Operating system installation and updates (Windows, macOS, Linux)
Remote IT support for quick and easy fixes
Cloud setup and management (Google Drive, Dropbox, etc.)
Email and website setup
Data backup and recovery
Wi-Fi setup and optimization
Software installation and updates
Printer and peripheral setup
Link
3 notes
·
View notes
Text
Last Monday of the Week 2024-12-09
Continually looking up "what day is christmas" and then forgetting almost immediately. This is not a bit I keep forgetting whether it's the 23rd the 24th or the 25th.
Listening: Bandcamp Friday! Posted about that here:
Watching: Not much.
Reading: A mix of 3D printing stuff and, still, work research, mostly about network configuration, because I'm trying to run a stupid complicated mlag vlan setup with trunked ports on the host side which is especially hard because this is basically my first time touching managed network hardware. Everything I know about vlans until like two weeks ago is theoretical.
3D printing stuff involves both some materials science and some interesting basic introductory stuff on hybrid fluid dynamics and solids simulations that because I want to try and do some structural simulations, it looks like there's some plugins for OpenFOAM that render this doable, just.
Making: New printer! Some test prints to get that up and running. Aborted a skull print because it seems like the printbed this came with is much less sticky than I'm used to, figuring out how to use that correctly.
Trying to fix the dead Ender 3 SE, which appears to have kerploded its power supply dramatically, link to that saga here
Some quilting with my partner, we are good at very different parts of sewing, they do knitting and crochet and worked shop tailor work for a while but are pretty weak at hand sewing, I do a lot of hand sewing and embroidery but I only barely know how to knit and crochet scares me.
Playing: A lot of Cyberpunk 2077, which I picked up in the steam sale as my one Big Game.
I have a lot of thoughts. This has very good writing for a Video Game RPG, especially one with such limited dialogue. I think being fictional helps its world feel much more real than say, GTA V, which is good at simulating a lot of things but I think struggles with the final hurdle, despite being in many ways much deeper than Cyberpunk.
Playing on Hard, which I think is a nice balance of letting your actions actually deal damage and feeling as deadly as Cyberpunk games are meant to feel.
Tools and Equipment: Compact powered screwdrivers are a real godsend, I have that Xiaomi multibit set and it's really worth the price of admission when you're working on something that is just full of screws.
6 notes
·
View notes
Text

Livestream idea.
ID:
I've been listening this whole time, but something you said inspired a random stream idea (that isn't really meant for you — it's better for a streamer who can do live action stuff), and I wanna share it: Starting in a room empty other than a streaming setup and a printer, random viewers sign up for an audio interview (and also to be incorporated into the ensuing chaos). The streamer prints out a picture of each viewer, and pins it up on the wall. They also print out various things related to that viewer — their state/country, their friends, newspaper articles about them online, their interests, whatever. They connect all these printouts with red yarn. And as more users get interviewed, the network becomes more connected — viewers from the same state, or with the same interest, or with the same job. The goal would/could be to find a "6 Degrees (with Kevin Bacon)" style chain of links from one viewer to another.
Commented on here, my friend:
twitch_live
2 notes
·
View notes
Text

I am sort of impressed again, looking at the available wifi list, at just how few named routers there are in our immediate vicinity. And yeah, both CatNet II entries are ours; the original was back in London. Plus somebody's fridge and printer showing up as their own entities. I would hate to try to figure out which Bredband2* to try and connect a new device to.
Yeah, we are in an apartment where the whole building apparently contracted with a single ISP. Which seems to be a pretty common setup here. Pretty sure the purple ones with better reception from here are on the same stairwell, with the construction solid enough between them to block pretty effectively.
ETA: I have just been informed that one of the Bredband2* entries is probably also ours. And he would need to look up which one it is. All of CatNet II is evidently through some other 5G-enabled router that Mr. C ended up buying while getting settled in Temporary Apartment--on the basis of "fuck it, this has an ethernet port, so I am plugging it in" after the password he was given for the existing wifi setup did not work. The wired side is obviously going through Bredband2, so i am not entirely clear on why we would have the extra generic entry there under a different MAC address. Good thing he does know what he's doing with networking, even if he's not always so great at the explanations.
2 notes
·
View notes