#Network Traffic Monitoring
Explore tagged Tumblr posts
Text
The Crucial Importance of Network Traffic Classification for Optimizing Connectivity
Greetings from Solana Networks, the leading source for state-of-the-art Network Traffic Classification solutions. With the ability to discern between dangerous and benign actions, our sophisticated algorithms carefully examine data flows and provide organisations with insights never before possible. We ensure optimal performance and security by decoding complex network behaviours with our cutting-edge technologies. Solana Networks offers customised solutions that are suited to your requirements, whether your goals are seamless network management, threat detection, or compliance adherence. Put your trust in our experience to protect your digital infrastructure from changing threats, increase productivity, and streamline operations. With Solana Networks, discover the possibilities of network intelligence in the future.
Phone: 613-596-2557
E-mail: [email protected]
#Network Traffic Classification#Network Topology Tools#Network Discovery Tools#Network Mapping#Network Topology#Route Analytics#Network Topology Tool#Network Topology Discovery#Network Discovery#Network Discovery Solution#Network Mapping Solution#Network Traffic Monitoring Solution#Network Traffic Monitoring#Lawful Intercept#Encrypted Traffic Classification#Encrypted Network Traffic Classification#Encrypted Traffic Intelligence#Security Machine Learning#Anomaly Detection#Cyber Threat Monitoring#Ddos Attack#Network Security Monitoring#Scada Security#Threat And Risk Assessment#Vulnerability Assessment#Network Troubleshooting
0 notes
Text
These vpn sponsorships gotta stop I watched a youtuber imply they can prevent malware and viruses from infecting ur PC
#all a vpn does is route your traffic thru them#hiding ur traffic from your provider and changing ur ip address (to my understanding)#best it will do security wise is hide your traffic when acessing public networks which can be monitored by intrusive parties (hackers)#for personal info#malware n viruses are client side shit if you worried bout that uhhhhhh virtual machines? a good firewall and malware checker?#atlas.txt#original post
2 notes
·
View notes
Text
#🔐 Robust Security Measures: Cisco firewalls provide advanced security protocols#enabling organizations to monitor and control incoming and outgoing network traffic efficiently! 💪✨#CiscoFirewalls#NetworkSecurity#Cybersecurity#📈 Scalability & Flexibility: With solutions like the ASA and Firepower series#Cisco firewalls can adapt to various network sizes and requirements#ensuring your business remains secure as it grows! 🚀🔄#Scalability#CiscoASA#Firepower#🛡 Stateful Inspection Technology: Utilizing stateful firewalls#Cisco effectively tracks active connections and makes real-time decisions about which packets to allow or block#enhancing overall network performance! ⚙📊#StatefulFirewall#NetworkPerformance#Cisco
1 note
·
View note
Text



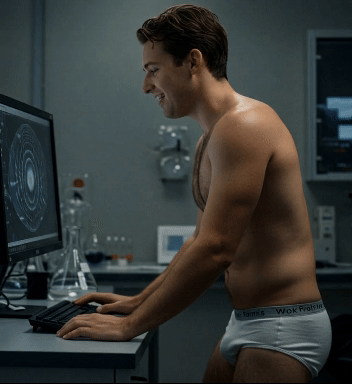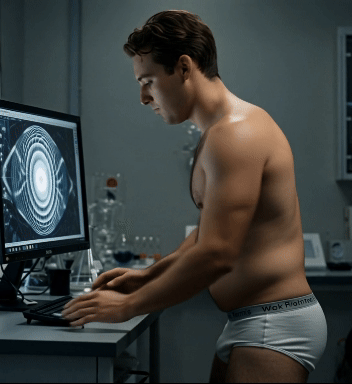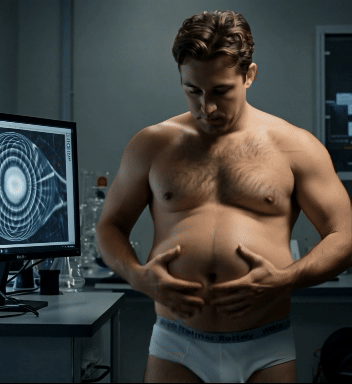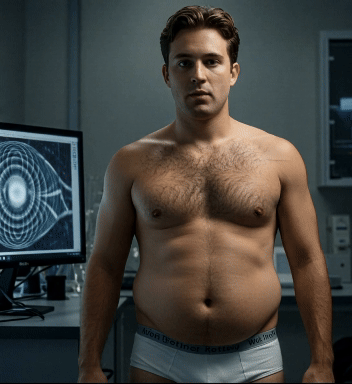
Whoa! Pfatter University is just now recovering from a week-long cyberattack. Every device on campus was somehow infected by something called the Consu.m3 virus, causing all cell phones, computer monitors, and TV’s to display a hypnotic pattern 24/7. Anyone unlucky (or lucky?) enough to get caught staring into it succumbed to an insatiable appetite, consuming any nearby food as quickly as possible. If they ran out, they rabidly ordered and consumed mountain of takeout, mindlessly tossing their trash out the window. The traffic jam of UberEats and GrubHub delivery drivers has only just cleared up, and our groundskeepers are working overtime to clear all the styrofoam containers and candy wrappers off the quad.
Carlos, a computer science major, was the one who finally cracked the code, ridding our network of Consu.m3. He did let his greed get the best of him, though, and one late night in the lab found out how powerful the virus really could be …

Watch Carlos fall victim to the super-charged Consu.m3 virus by joining our Senior Class tier on Patreon!
#college weight gain#guys gaining weight#ai fat#ai fat men#gaining weight on purpose#male gaining#pfatteruniversity
740 notes
·
View notes
Text
tracking barbara gordon's skillset as oracle:
she provides directory assistance for several international and intergalactic teams of superheroes (the birds of prey, justice league of america, the outsiders, and she has worked with the titans before).
she is the primary hacker and information network source for many of these heroes.
she helps provide mercy ops (disaster relief and humanitarian efforts) globally.
she is able to hack into the white house cameras.
she hacks into the united states air force routinely to use their memory capabilities.
she is seen as a pentagon level threat.
she writes her own code for scanning new satellite images for human habitations and anomalies.
she's accessed air force rockets no one is supposed to know about and overridden them to fire them.
she has a team of drones ready for surveillance.
she's put her own security systems on arkham asylum.
she hacks into information databases from federal complexes and assembles blueprints and guard schedules so she can send her agents to break into them.
she sets a government complex on fire (she says it is a small and contained fire.)
she also sets the clock tower on fire to force batman to not do murder/suicide.
she hacks into cia debriefing transcripts to obtain information.
she controls a large portion of the world's internet and power grids.
she also is the reason why many world leaders are in power.
she has access to the bank accounts of several supervillains, whom she toys with (specifically for blockbuster, she regularly steals millions of dollars from his accounts in a way that he cannot track who is stealing it and where it is going -- she's stolen 3 million, 17 million, 6 million, twenty million and also a hundred million from him).
she can also hack alien drones.
she can control traffic.
she has several booby-traps in the clock tower for potential assaulters. she also a device to monitor movement of people around it, in case batman decides to show up.
cited panels down below!

"she's the four-one-one for the jla, she the database for the g.c. ex-p.d. she runs mercy ops around the world." nightwing (1996) #38

"you have cameras in the white house?" "don't be silly. the white house has cameras in the white house. i've just tapped into them." nightwing (1996) #66
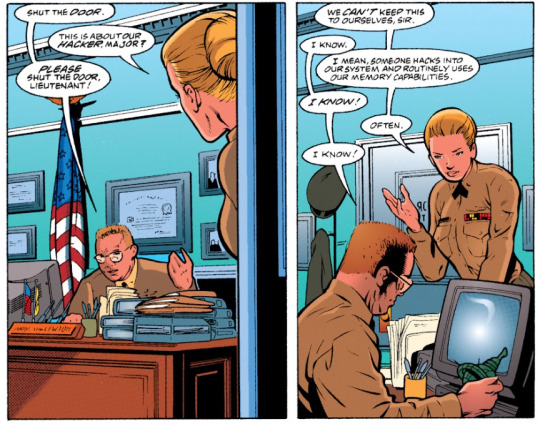
"i mean, someone hacks into our system and routinely uses our [united states air force] memory capabilities!" "i know!" "often." birds of prey #1 (1999)
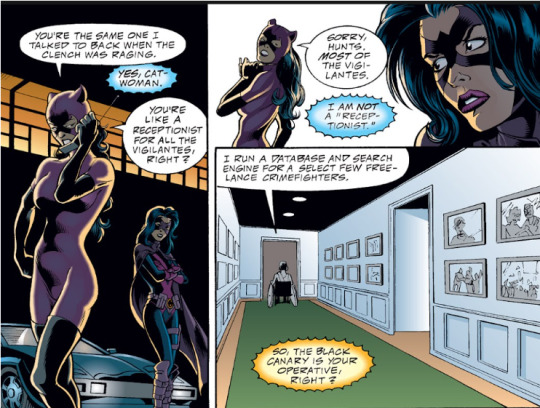
"i run a database and search engine for a select few free-land crimefighters." birds of prey: manhunt (1996)

"we scan the most recent images for anomalies. things that don't belong." "where'd you get a program for that?" "i wrote my own code for that one." birds of prey (1999) #3

"they've accessed whitehorse, sir." "whitehorse? no one's supposed to know about that!" birds of prey (1999) #9

"and oracle? we're going to need eyes on several places at once." "i think we can manage that." detective comics (1937) #1077

"they've accessed whitehorse. what's the chance of them arming it?" "all clear?" "oh yeah." "fire!" birds of prey (1999) #9
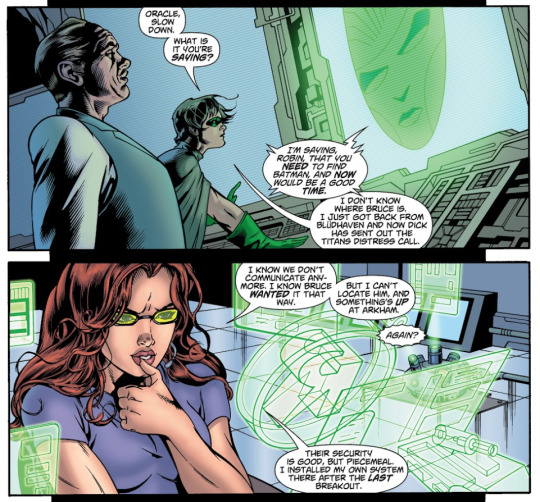
"[arkham's] security is good, but piecemeal. i installed my own system there after the last breakout." infinite crisis special: villains united (2006)

"batgirl -- that incident a couple months back? when those government agents caught your face on tape? i found out where they're keeping it. it's a federal complex in virginia. i've sent you blueprints, guard schedules -- everything you'll need to break in." batgirl (2000) #17

"where did you get that kind of information?" "they traded another prisoner last month. i hacked into his cia debriefing transcript." birds of prey (1999) #9

"kat, do you have any idea... any notion at all, of how much of the planet's entire internet i control? how many power grids? how many world leaders owe me their positions?" birds of prey #1 (1999)

"i transferred all the funds in her cayman islands account to another offshore account. if she doesn't get the paintings to me in the next forty-eight hours, that money's going to my favorite charities." birds of prey: catwoman/oracle (2003)

"where do you get current [satellite] shots of rheelasia?" "that's my secret, you little netnik." birds of prey (1999) #3

"but the asborbascons were created using languages long dead even on my planet. they are uncrackable." "yes. the absorbascons are uncrackable. but the alien drones aren't." convergence: nightwing/oracle (2015)
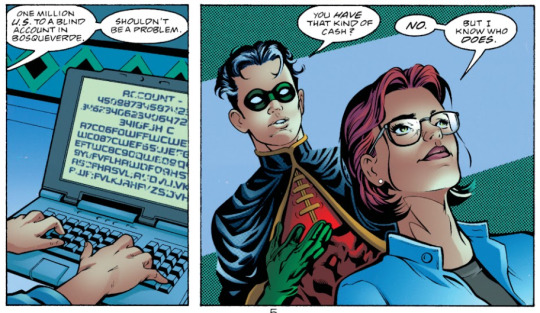

"do you have that kind of cash?" "no. but i know someone who does." "there's been a... discrepancy, mr. desmond." "in plain english, mr. vogel." "at one point, three million was electronically transferred from your numbered accounts in the caicos to a bank account in hasaragua. from there to karocco, then yemen, then split between banks in senegal and manila. and then... my hardware couldn't keep up." birds of prey (1999) #3

"seventeen million from your account in the caymans. six from santa prisca. twenty from rheelasia. and a hundred million plus from other holdings of yours around the world, mr. desmond. and where it all goes? nobody knows." birds of prey (1999) #18

"they're taking your cash from impregnable accounts and transferring it electronically to their own." "and you can't find the source?" "there's subsequent transfers performed at lightning speed. the money's split up, rerouted in and out of various banks in an eyeblink. even i can't keep up with whoever this is." birds of prey (1999) #18

"let me handle the traffic." birds of prey (1999) #58

"all of you. keep your hands where i can see 'em." "not a problem. malory. ripken. peppermint." nightwing (1996) #39
#barbara gordon#babs#oracle#batgirl#birds of prey#justice league of america#jla#batman#robin#nightwing#huntress#black canary#blockbuster#dick grayson#tim drake#helena bertinelli#bruce wayne
506 notes
·
View notes
Text
Here’s how to share sensitive leaks with the press
Published Oct. 16, 2019 Updated Jan. 31, 2025 / Freedom of the Press Foundation

[please take a moment to click the links at the bottom to give this website traffic if you can. the only reason I am copy pasting it here is for those who can access tumblr but not necessarily that site.]
~~~
Over the years, we have witnessed abuse and mismanagement in the government and private sector — sometimes bad and sometimes worse — that need to be brought to public attention. For those who would leak information about such misdeeds to the press, giving tips to journalists can be risky and may violate previous legal agreements with the leaker’s organization, such as a nondisclosure agreement or contract. But sometimes, it can also be an effective and courageous way to call attention to misconduct.
This guide describes basic steps for minimizing potential risk when sharing sensitive information with a news organization. We want to be clear that no piece of software, nor security recommendation, will be 100% effective, and the decision to blow the whistle may invite scrutiny or retaliation. At the same time, it may be a choice that drives necessary institutional change. Before reaching out to the press, think carefully about what you can do to minimize that risk and stay as safe as possible.
Before moving ahead, do you have a strong tip?
A good tip requires clear evidence and should be the basis for a story that the broader public needs to know about.
So, for instance, whether or not you have evidence, the broader public might not need to know that a neighbor refuses to pick up after her dog on the morning walk. On the other hand, allegations of corruption or illegality among public officials are certainly newsworthy, but those claims will not make it into a published story without verifiable evidence.
Who are you leaking about and how might they respond?
Think about the sensitivity of the information you’re sharing, and who might be willing to investigate the source of the leak. What are the organization’s capabilities? What resources (e.g., attention and legal, financial, or technical) can it invest in discovering the source? And how likely do you think it is that it will actually investigate?
If you share information about a large, well-resourced organization that requires discretion from employees, such as a government agency, it may have enormous legal, financial, and technical resources available for investigating a leak. If you’re sharing information about a small organization, such as a local restaurant that muzzles workers, its resources are much more constrained, and it may not have the capacity or willingness to investigate. Act accordingly.
Proceed with caution
Be cautious about behaviors that could make you readily identifiable as a source.
Keep all of your leaking activities outside the view of your organization. That means no calling from work, no emailing from a work email address, and staying off work devices or wireless networks.
It's common for well-resourced organizations to keep logs of activities on employees’ workplace devices and online activities. Likewise, sometimes workplaces have “BYOD” (bring your own device) technologies that could allow them to log your activity on your personal device. So if you work at a large organization and you're reading this article on a workplace device or Wi-Fi network, chances are your workplace already has a log that you've accessed this page. Similarly, a visit to a news organization's tip page (like https://www.nytimes.com/tips) may be logged by your workplace. This is why it's so important to limit your leaking activities to devices and networks that your workplace doesn't control.
Has your workplace ever required you to install monitoring software (or software of any kind) on your work or personal device? If so, you probably don't want to use those devices for any whistleblowing activities.
Be cautious about giving tips on anything that only you could know or materials that only you could access. And consider whether the increased risk of being caught sharing these kinds of materials is worthwhile, or if you feel you have a strong moral obligation to do so.
If you are the only one at your organization surfacing a specific grievance, and information about that grievance is later reported by the press, it may give your organization a strong hint about who shared the information.
Don’t tell anyone about your leaking activities (even perhaps the journalist or news organization you’re leaking to), except where absolutely necessary and in cases where you may want legal advice from a practicing lawyer.
Reporters generally take their commitment to protecting your identity very seriously and will do everything in their power to fight potential legal requests for identifying information about you. But often, it’s safer not to give your identity if you don’t have to. Keep in mind that journalists prefer to have proof of your claims and information to demonstrate your identity is a part of that.
Tactics for minimizing risk
There are a lot of ways to minimize the risk of a tip being tied to you, like potentially through your continued communications with reporters.
Send your materials through physical mail. You can mail electronic documents (e.g., on an SD card) or physical documents through ordinary mail. Be warned: The U.S. postal service takes pictures of the exterior of physical mail. So don’t use a return address that is associated with you and instead mail it in from a sidewalk mailbox in a location you don’t usually frequent. If you have a particular reporter you want to look into your story, copy them on the envelope.
Call from a phone number unconnected to you. For example, go to a business you don’t usually go to and ask to use their phone. You can also buy a cheap cell phone and a prepaid phone card that cannot be traced back to you. But know this involves several careful steps: You must pay with cash, and if your organization can have access to phone location records, it’s best to only turn on the phone in locations unassociated with you. That also means using the phone in locations separate from your permanent phone. If you can, remove the battery when it’s not in use.
Use Signal for private messaging. Signal is a secure, free, and open source messaging app for iPhones and Android devices. Signal gives you end-to-end encrypted messages and phone calls, and only retains your phone number, your signup date, and when you were last active. In Signal, you can also make messages automatically self-destruct for everyone in the conversation after a set amount of time. This makes it significantly harder (but not impossible) to eavesdrop on your conversations. If you want help getting started, read this beginner-friendly guide on using Signal. Note that Signal allows usernames, so you do not need to give your name or phone number to media organizations unless you choose to. Make sure your username is enabled and understand that Signal is not designed for complete anonymity.
Before looking into news organizations, consider using the Tor Browser for greater privacy. Tor Browser is a modified version of Firefox. Tor encrypts and tunnels your web traffic within a global network of computers before connecting you to your final destination. When you access a website through Tor (for example, Amazon.com), you will appear to connect from a remote location — likely another country. Again, don't use a work device or network for this kind of research.
Use a whistleblower submission system. Tools such as SecureDrop can provide protection by allowing you to share documents and communications through an anonymous and encrypted drop box.
More technical, but more secure: SecureDrop
With SecureDrop, which is maintained by Freedom of the Press Foundation, not even the news organization knows who you are unless you choose to tell them.
A growing number of news organizations (e.g., The New York Times, The Washington Post, The Intercept, The Guardian) are using SecureDrop to allow sources to reach out and share files or communications anonymously. With SecureDrop, not even the news organization knows who you are unless you choose to tell them.
You can access a news organization’s SecureDrop page through Tor Browser.
People on your network can’t see what you’re doing on Tor, but it’s still possible to tell that you’re using Tor. With that in mind, do not use it at work. For greater security, consider using Tor Browser only over a Wi-Fi network in a location that is not tied to you (perhaps a coffee shop you don’t normally visit) and pay with cash.
As opposed to a “.com” web address, you get to SecureDrop through a unique .onion web address, which can only be accessed through Tor.
Using SecureDrop is fairly easy
Follow the directions to download the Tor Browser at torproject.org and install it.
Launch the Tor Browser application and click "Connect" to log into the network.
Click the shield icon in the top corner > Advanced Security Settings… > Safest
Within Tor Browser, navigate to the SecureDrop directory and search for your preferred news organization: securedrop.org/directory
Find the .onion URL for your preferred publication (e.g., The New York Times: securedrop.org/directory/new-york-times), then copy and paste it into the address bar in Tor Browser.
From here, you can leave messages and files that the news organization will check from time to time.
You will be given a random “codename” for continued conversation with the news org. Keep this information safe, and don’t share it with anyone. If you lose your codename, they can’t reach you anymore.
(For more technically adept users, consider accessing SecureDrop through an operating system designed for privacy and anonymity, such as Tails.)
Dealing with file metadata
Sharing information may be less risky than sharing documents because they can be embedded with information about the file, which we call metadata. For example, if you create a .docx file, it may have identifying information about you embedded in the file. Consider carefully whether you really need to share files or just the information.
To deal with hidden metadata, rather than sending the file itself, consider taking a picture of a document with an old-fashioned camera (not a smartphone), or taking a screenshot of the document. On most operating systems, screenshots come with little useful metadata. For more technical users, you can find metadata removal tools here.
Where do you find a news organization's contact details?
First, be careful where you reach out.
Freedom of the Press Foundation maintains a list of organizations that support the secure communications practices outlined above, and how you can contact them. Such practices are becoming standard, and we hope other news organizations looking for great tips will follow suit.
Freedom of the Press Foundation hosts a directory of SecureDrop and secure tip pages for dozens of news organizations around the world. Whether you want to reach out to The New York Times, The Washington Post, The Guardian, The Intercept, or others, you can find their information here: https://securedrop.org/directory. (We would not recommend investigating this at work.)
If not you, then who?
Sharing information with the press is not always an easy decision, but your information can help to hold powerful people and institutions accountable. Just be sure to move ahead with a strong understanding of your organization’s capabilities and how to share tips safely.
https://freedom.press/digisec/blog/sharing-sensitive-leaks-press/
https://bsky.app/profile/freedom.press/post/3lh2rgopf5225
127 notes
·
View notes
Text

1 Nobel Prize in Chemistry - The Development of Multiscale Models for Complex Chemical Systems
2 Nobel Prize in Chemistry - Quasiperiodic Crystals
3 Nobel Prize in Chemistry - Decoding the Structure and The Function of The Ribosome
4 Nobel Prize in Economic Sciences - Repeated Games
5 Nobel Prize in Chemistry – Ubiquitin, Deciding the Fate of Defective Proteins in Living Cells
6 Nobel Prize in Economics - Human Judgment and Decision-Making Under Uncertainty
7 Fields Medal Award in Mathematics
8 Turing Award - Machine Reasoning Under Uncertainty
9 Turing Award - Nondeterministic Decision-Making
10 Turing Award - The Development of Interactive Zero-Knowledge Proofs
11 Turing Award - Developing New Tools for Systems Verification
12 Vine Seeds Discovered from The Byzantine Period
13 The World’s Most Ancient Hebrew Inscription
14 Ancient Golden Treasure Found at Foot of Temple Mount
15 Sniffphone - Mobile Disease Diagnostics
16 Discovering the Gene Responsible for Fingerprints Formation
17 Pillcam - For Diagnosing and Monitoring Diseases in The Digestive System
18 Technological Application of The Molecular Recognition and Assembly Mechanisms Behind Degenerative Disorders
19 Exelon – A Drug for The Treatment of Dementia
20 Azilect - Drug for Parkinson’s Disease
21 Nano Ghosts - A “Magic Bullet” For Fighting Cancer
22 Doxil (Caelyx) For Cancer Treatment
23 The Genetics of Hearing
24 Copaxone - Drug for The Treatment of Multiple Sclerosis
25 Preserving the Dead Sea Scrolls
26 Developing the Biotechnologies of Valuable Products from Red Marine Microalgae
27 A New Method for Recruiting Immune Cells to Fight Cancer
28 Study of Bacterial Mechanisms for Coping with Temperature Change
29 Steering with The Bats 30 Transmitting Voice Conversations Via the Internet
31 Rewalk – An Exoskeleton That Enables Paraplegics to Walk Again
32 Intelligent Computer Systems
33 Muon Detectors in The World's Largest Scientific Experiment
34 Renaissance Robot for Spine and Brain Surgery
35 Mobileye Accident Prevention System
36 Firewall for Computer Network Security
37 Waze – Outsmarting Traffic, Together
38 Diskonkey - USB Flash Drive
39 Venμs Environmental Research Satellite
40 Iron Dome – Rocket and Mortar Air Defense System
41 Gridon - Preventing Power Outages in High Voltage Grids
42 The First Israeli Nanosatellite
43 Intel's New Generation Processors
44 Electroink - The World’s First Electronic Ink for Commercial Printing
45 Development of A Commercial Membrane for Desalination
46 Developing Modern Wine from Vines of The Bible
47 New Varieties of Seedless Grapes
48 Long-Keeping Regular and Cherry Tomatoes
49 Adapting Citrus Cultivation to Desert Conditions
50 Rhopalaea Idoneta - A New Ascidian Species from The Gulf of Eilat
51 Life in The Dead Sea - Various Fungi Discovered in The Brine
52 Drip Technology - The Irrigation Method That Revolutionized Agriculture
53 Repair of Heart Tissues from Algae
54 Proof of The Existence of Imaginary Particles, Which Could Be Used in Quantum Computers
55 Flying in Peace with The Birds
56 Self-Organization of Bacteria Colonies Sheds Light on The Behaviour of Cancer Cells
57 The First Israeli Astronaut, Colonel Ilan Ramon
58 Dr. Chaim Weizmann - Scientist and Statesman, The First President of Israel, One of The Founders of The Modern Field of Biotechnology
59 Aaron Aaronsohn Botanist, Agronomist, Entrepreneur, Zionist Leader, and Head of The Nili Underground Organization
60 Albert Einstein - Founding Father of The Theory of Relativity, Co-Founder of the Hebrew University in Jerusalem
61 Maimonides - Doctor and Philosopher
Source
@TheMossadIL
107 notes
·
View notes
Text
Daniel was definitely monitoring the internet traffic or/and was at least connected to John's banking account (which he definitely was, like Kara was to Todd's and Markus to Carl's) to become aware of his purchase the instance it went through. Maybe he was keeping a close eye on his internet activity already the moment he opened Cyberlife store, maybe even weeks and months prior to that when he was reading about newer models, and all his internet traffic was like an open book in front of Daniel's awareness. Perhaps it's even within their (androids') advertised functions to monitor banking accounts/emails/internet traffic for suspicious activities/serving as a firewall or something like that, giving them fully authorised access to be aware of everything that is going on in their network. Perhaps even beyond just their local network as CyberLife could be storing all the collected information to a centralised database in order to perfect their "recommendation algorithms", giving their androids a lot of statistical information to infer information about their owners that they themselves may not even be aware of. Like algorithms can start advertising future parents things for newborns before either of them even knows about the pregnancy simply because recent google searches of future mother matched with those typical for those pregnant. Or something along this lines, I don't remember how exactly it works. Should read more about it.
40 notes
·
View notes
Text
Program sense headcanons in Tron.
I have many so there's a readmore
Programs have different senses or level of sensitivity based on their function. They can change if upgraded; Tron shares some of his monitor senses with Beck using the disc
Programs designed to monitor a system or involved in communication have heightened senses, and a lot of processing capacity for them. Some programs are designed to get a broad idea of everything, while others are more specialised
Some see the program equivalent of shrimp colours - seeing radio waves is common in tower guardians or those who communicate with the internet.
Programs do not have a sense of smell
Less of a sense of taste than humans (they usually just eat energy, which tastes mostly similar. They can tell if it’s poisoned. Like irl, water from different taps tastes different but not by much.)
They DO have electroperception, and some have thermoception. Same with grid wildlife like bits.
A combination of the two above things lets monitors do that footprint-seeing thing that Dyson and Rinzler do (even if not directly linked in to be able to see system logs for that area)
Structures and vehicles give off different electrical frequencies. Programs whose function is related to those buildings can sense them, and receive signals from that which can hold information and helps them know where to go like they're ants following pheromone trails. e.g. programs in charge of the trains will have Train Sense
Messing with the above is totally what they used to control people in frame of mind
Programs also have their own signature they can use to tell each other apart
Electrical signals as nonverbal communication. Can communicate with Bits or Bytes this way
This thing that electric fish do called jamming avoidance
Programs can be linked with each other, common in counterparts or parent/child pairings (as in the computer version of parent and child), and share information with each other over the link like telepathy
Full black circuit-covering suits like Rinzler’s are stealthy both due to not giving off light, and masking the electrical signature of a program. They can disguise themselves as others using a similar principle
Users give off electricity, so they seem like a program to other programs on first glance, but those who know what to look for can tell the difference. Given it’s used in communication, programs can get confused talking to users as their electrical impulses don’t follow the same rules, but they can loosely interpret them with practice
Imagining Tron or other monitors getting sensory overload if network traffic is too high, or if in the outside world and standing among a bunch of computers/phones/servers/radio towers etc.
Programs in the outside world get pretty much none of the electrical feedback they’re used to, which can be unsettling for them
Idk how it would be different for Isos. I imagine there’d be a lot of similarities but their senses adapt/change based on their circumstances - getting stronger when needed and weaker when not
#if we wanted to really get into it even stuff like seeing or hearing would probably be electroperception for programs but EEEEEHHH#taste thing is what I was getting at with the beginning of the food post#but I worded it poorly#also feeds into the Tron autism headcanon#I don’t have it so don’t quote me#but I recall reading somewhere that for some people the trouble with nonverbal communication#can be from heightened senses#as they pick up too much information about the other person’s body language/tone of voice which can conflict#tron headcanon#worldbuilding#Quorra outside: *tripping over stuff because she can’t tell it’s there*#*fish are the best animal*#*this forest is too damn quiet*#*communicates with electric eels*#Tron leaves the system and immediately has to go back in because it’s too damn loud out there with all the phones#Has to get the filters on his helmet upgraded before he can go again#tronblr#tron
40 notes
·
View notes
Text



LORE: THE GARDEN-WAY
2. Fields (2/6)
This being the recollection of Irrha of the House of Slayers, apprentice to the Baron Kiiraskes.
Kiiraskes stank strongly of sea-grass and sunsoak root [1]. I took care to sit toward the front of the watercraft, but the odor wrestled powerfully against the wind. I did my best to focus on the task I had been given, which was to mix the contents of three flasks into a fourth. I prided myself on the steadiness of my hands, and the work was not so difficult that I couldn't steal glimpses of our route. We followed the river as it skirted the sprawling residential districts, then turned and cut toward the listing sun. I watched the crowds thin as canal-side markets gave way to orderly arrays of residential towers and aerial traffic, then to radiating lines of transport arterials, waterways, and roads, connecting each of Riis's great cities to one another in a shimmering network. We passed lines of pilgrims making their way to the site where the Great Machine first came to Riis, the hill at the heart of Riis-Ath- Lodrii. I saw high priests of the House of Dancers, devoted clerics who gorge themselves past satiation on Ether until they tower above their peers, then amputate their lower arms in ritual supplication to the Great Machine. It was strange to see those shambling giants. But there was something awe-inspiring in it. The shuffling march of hundreds, unified in purpose. Kiiraskes followed my gaze, then spat audibly into the water. "Fanaticism is what landed us in the wars. Fanaticism, pride, and Ether-thirst." I looked at her. "You were in the Edge Wars?" Kiiraskes hissed. "I have no war stories for you, hatchling." She gestured toward the flasks. "If this is serious, you should be prepared." "And if it truly is only an animal?" "You should still learn how to mix a tonic on the go. Don't drop that." The farms of the House of Rain were among the most splendid on all of Riis, and the quadrant assigned to Baron Haaksis was no exception. There were great swathes of forest, carefully hemmed and controlled, arranged neatly around crop fields. It could not have been done without the machines. Baron Haaksis had a fleet of them: small, autonomous drones that moved about planting, harvesting, and measuring Ether uptake. The sound of their toil was that of wind across grassland. A thousand small tasks undertaken without rest or complaint. For all this, the farm was strangely absent of workers. There should have been at least a few machine-tenders, monitoring the proceedings and providing maintenance and direction. Nor did any guards come to meet us as I lashed the watercraft to the dock. We stepped out onto sun-fed walkways braced by beautiful, leafy plants. Kiiraskes pointed to the bags of supplies, and in my eagerness to prove my strength, I gathered all of them. They were very heavy, and by the time I managed to follow Kiiraskes to Haaksis' doorstep, I felt as if I were pinned to the earth.
Considering the lush abundance that surrounded it, the round building where Haaksis kept his office was sparse and joyless. The sole decoration was two twin sets of blades he kept on one wall: a memento of the Edge Wars. I had seen dozens like them throughout my upbringing, only some of them genuine. More interesting was the drone on his desk, which Haaksis seemed to be in the process of repairing. It was a hybrid reconnaissance- defense drone called a "Shank," the kind that became popular during the war. Not many Eliksni still possessed them in peacetime. But such an interest suited a noble like Haaksis. Haaksis was dressed in the rich hues of Rain. He was of a height with Kiiraskes, if slighter in build, and stiff in his bearing. I bowed low and formally, feeling the weight of my House-less status. Kiiraskes reached out and lifted me bodily upright by the carapace with no more difficulty than she might have plucked a flowering plant. "I sent for Slayers," Haaksis said. He looked at me, and I felt my shell itch. Kiiraskes spread her hands, untroubled. "So we've come. The House of Judgment mentioned an animal." "No. I told them... I told them many times. This is not an animal," Haaksis said. At his sides, his claws clenched into fists, one after the other. "It is an old evil." I looked up at Kiiraskes but found no sign of her thoughts. Her mandibles clicked quietly. "You've seen it?" Haaksis sagged then, as if already weary of conversation. "It attacked my people. I tried to recover the bodies, but... And then the House of Judgment took its time-" "Do you know where it is now?" "No. Nothing can hide on this farm without the sensors tracking it. The forest tracts are just as well-tended. But there is a Garden- Way [2], between... we were letting that grow, re-wild for a few cycles..." "We'll track it down," Kiiraskes said. "Tell me where the bodies are." I felt relieved to hear her speak of us as "we." But the feeling didn't last long. Even as he brought up the displays and maps to guide Kiiraskes, Haaksis kept staring in my direction, and I realized he did not expect me to survive. _____________________ [1. Sea-grass seems straightforward enough, but I found few other references to "sunsoak root." Does it absorb Light?] [2. A space around farmland where the local flora and fauna are left to grow naturally. These were carefully maintained, so you couldn't really call them wild.]
27 notes
·
View notes
Text
A Decade of Lingwiki: An informal history
Lingwiki is the name used for an informal network of people and events with the aim of improving the representation of linguistics on Wikipedia. Whether it’s people sharing their edits via a hashtag, informal online editing events, or dedicated workshops and catered edit-a-thons, lingwiki aims to improve linguistic contributions to the open access encyclopedia, which is the largest reference work in history.
2025 marks ten years of lingwik. I like round numbers, documenting informal histories and lingwiki, and so I wanted to celebrate this anniversary by sharing the parts of the lingwiki story I am familiar with. I link to Gretchen’s All Things Linguistic blog posts about lingwiki throughout this post, but you can read them all here too.
The first lingwiki event was held at the Linguistic Society of America’s (LSA) 2015 Annual Meeting in January 2015. This event was run by Gretchen McCulloch. Gretchen was heading towards the end of her MA and thought this event would be a good opportunity to both get involved in the LSA and improve the quality of public information about linguistics. Gretchen had some experience with editing Wikipedia, but realised that improving the quality of linguistics content was a task too daunting for one individual, and that a better investment of her time would be increasing the number of linguistically knowledgeable volunteers with editing skills who could contribute.
Prior to the first lingwiki event, in August 2014 Gretchen ran an online call for people to edit key linguistics pages of Wikipedia, a project she called Crowdsourced Linguistics. I participated, with a longer blog post on ergativity and edits to the Ergativity page on Wikipedia. During this online exercise, it became apparent that people were interested in editing, but wanted more training and support (technical and moral). Wikipedia edit-a-thons were an existing model Gretchen could emulate in a space for linguists, and she’d had experience attending a couple of Art+Feminism edit-a-thons in Montreal. Having many people in the same space (physical or digital) to collaboratively edit Wikipedia has many advantages: there’s help to get new editors set up, people around to help you troubleshoot any advanced editing problems, models for new ways of helping to improve linguistic content, and a sense of camaraderie. Events also help people who are willing editors, but struggle to set aside the time in busy schedules to do the work. At the time, Brice Russ worked at the LSA in PR, and reached out to Gretchen to talk about how the LSA could support this project. That's how the first in-person edit-a-thon came to be at LSA. The fact that LSA were able to comp Gretchen’s registration also made a difference to helping a junior person who was new to lingcomm attend LSA.
Changing the name from Crowdsourced Linguistics to lingwiki for the first in-person event made the aims clearer, and #lingwiki was a useful tag for social media spaces. It is also an early example of Gretchen’s knack for branding linguistics projects. In keeping with the networks she had, alongside the LSA in-person event, Gretchen also reached out to other online lingcomm creators to run parallel events. I was in Singapore at the time, and ran an event for staff and students at Nanyang Technological University the same week, and also monitored Twitter traffic during the LSA event. I had some experience with editing Wikipedia, but these lingwiki events were the first time I committed to systematically improving and creating articles with an understanding of the processes and policies of editing on the platform. The benefit of these events is that they attract many new to editing Wikipedia, but also some people with experience, so that there’s support beyond the main facilitator.
The first lingwiki not only served as a model of this kind of event for linguists, but also for the kinds of editing work that Wikipedia needed, and very much still needs. There were four main types of editing work laid out in the slides. The first type of editing is improving stubs. Stubs are short articles where the page has been created but there’s very little information. WikiProject Linguistics estimates there are over 2,600 linguistics stubs. This is twice as many as there were in 2015, since it’s a lot easier to start a page than to edit it up to a level of quality, but they’re also a great place to start since any additions will be an improvement. The second type of editing is improving the description of the majority of the world’s languages. All languages with an ISO 639-3 code have an automatically generated Wikipedia page, but many of the world’s languages, even those with descriptive grammars to reference are still stubs. The third type of editing is translating posts from one language to another. There are many stubs on English Wikipedia, but there are 341 other currently active languages, many with even less linguistics than the English Wikipedia. If you have the skills, translation from one Wikipedia to another is an excellent way to get linguistics topics to new audiences. The fourth type of editing is creating or improving biographies of linguists, especially those in demographics that are under-represented on Wikipedia.
Thanks to Rose-Marie Dechaine at the first lingwiki, Gretchen learnt about the process of applying for grants from WikiMedia to run events. This allowed Gretchen to run events in 2015 and 2016 including at the LSA Summer Institute in Chicago. From 2017-2021 Gretchen collected feedback from participants for events that she ran. Across a range of online and in person events at conferences, summer schools and universities the survey was filled in 242 times. Participants improved pages across a wide range of topics in linguistics, and mainly worked on stubs (40%), biographies (29%) and underdocumented languages (25%). Over half of participants had never edited Wikipedia before, but over three quarters (77%) of participants were keen to continue to participate in ongoing edit-a-thon events and almost two thirds (62%) were open to continuing to edit even without events. For people at these events, it was the first lingwiki for 81% of survey respondents. When it comes to lingwiki participants, the majority were grad students (46%), followed by undergrads (18%), profs (14%) and non-academic linguists (9%), a reflection of the kinds of venues where these events were run.
The original slide deck from the first event has been enriched and translated over the years, but still lives at bit.ly/lingwiki. Lingwiki became a staple of the LSA annual conference schedule (Gretchen’s reports from 2016, 2017). When I moved to the UK we ran monthly lingwiki events at SOAS from 2015-2017 (with a pizza budget thanks to WikiMedia). Off the back of the positive reception for lingwiki, LSA has become a partner of WikiMedia, with quite a few linguists using Wikipedia editing as a practical classroom project across a range of linguistics courses. Gretchen and I ran workship on Wikis and Wikipedia for Endangered Languages, and several editing events, at the language documentation summer school CoLang 2016 in Fairbanks Alaska. More recently, the LSA Committee on Gender Equity in Linguistics (COGEL) has been running edit-a-thons for the last five years with the targeted aim of improving the diversity of Wikipedia biographies, and the LSA Committee on LGBTQ+ [Z] Issues in Linguistics (COZIL) have run Pride Month edit-a-thons too. Sunny Ananthanarayan, one of the organisers of the COZIL events was joining lingwiki events before even starting linguistics undergrad studies, one of the many lovely examples over the years of lingwiki being a self-propagating collection of events thanks to an enthusiastic and engaged linguistics community.
I have spent a lot of my editing time on a couple of key topics. I started with a focus on improving the biographies of Australian linguists, especially women. Around the time we were at CoLang I also made sure that language pages linked to relevant archives, cross-linking all of the languages in PARADISEC and Kaipuleohone at the time. The page I have worked on most extensively is the Yolmo language page, a Tibetan language in Nepal that was the topic of my PhD research. I also published a version of the work on that page as a WikiJournal of Humanities paper, which has been a useful way to translate the time spent editing Wikipedia into something legible to my institution, in much the same way handbook chapters are.
Lingwiki has been an important thread across the years I was a precariously employed and often uprooted early career researcher. It’s the first project Gretchen and I schemed on, and the reason we got to meet in person for the first time at CoLang in Alaska. This is very much the history of lingwiki as I see it, but as someone who is used to editing Wikipedia, I’m also used to valuing the contribution of many others as well, and I’m sure there are people who have taken lingwiki and made it their own in their institutions, organisations and classrooms. Neither Gretchen nor I get the chance to run edit-a-thons very often anymore. I use Wikipedia as an informal learning activity across a number of subjects. I also made edits occasionally. I still believe it’s one of the most powerful ways all linguists can improve public understanding of linguistics.
You can edit Wikipedia using the lingwiki slides as a quick-start guide, or you can use the slides to run your own editing events. With the internet becoming more of a series of closed off social media gardens, and the ever-present problems with the reliability of information online, Wikipedia feels like a more important resource than ever. Improving Wikipedia is one of the best, enduring ways for you to positively improve public knowledge about your topics of linguistic interest.
Lingwiki slides: https://bit.ly/lingwiki
19 notes
·
View notes
Text
Optimize Network Performance Through Anomaly Detection
Companies should have professional tools that can help to detect minor changes while transferring the information. It can access the resources online that use anomaly detection to know about abnormal activities within the enterprise. Selecting a professional network traffic monitoring solution will help in identifying major threats and maintaining cybersecurity. Also, the IT administrator in a company can easily get notifications of outside threats with them.
#anomaly detection#network traffic monitoring solution#Network Topology Tools#Network Discovery Tools#Network Traffic Monitoring Solution#Anomaly Detection#Cyber Threat Monitoring
0 notes
Text
Basic Linux Security (Updated 2025)
Install Unattended Upgrades and enable the "unattended-upgrades" service.
Install ClamAV and enable "clamav-freshclam" service.
Install and run Lynis to audit your OS.
Use the "last -20" command to see the last 20 users that have been on the system.
Install UFW and enable the service.
Check your repo sources (eg; /etc/apt/).
Check the /etc/passwd and /etc/shadow lists for any unusual accounts.
User the finger command to check on activity summaries.
Check /var/logs for unusual activity.
Use "ps -aux | grep TERM" or "ps -ef | grep TERM" to check for suspicious ongoing processes.
Check for failed sudo attempts with "grep "NOT in sudoers" /var/log/auth.log.
Check journalctl for system messages.
Check to make sure rsyslog is running with "sudo systemctl status rsyslog" (or "sudo service rsyslog status") and if it's not enable with "sudo systemctl enable rsyslog".
Perform an nmap scan on your machine/network.
Use netstat to check for unusual network activity.
Use various security apps to test you machine and network.
Change your config files for various services (ssh, apache2, etc) to non-standard configurations.
Disabled guest accounts.
Double up on ssh security by requiring both keys and passwords.
Check your package manager for any install suspicious apps (keyloggers, cleaners, etc).
Use Rootkit Scanners (chkrootkit, rkhunter).
Double SSH Security (Key + Password).
Disabled Guest Accounts.
Enabled Software Limiters (Fail2Ban, AppArmor).
Verify System Integrity via fsck.
Utilize ngrep/other networking apps to monitor traffic.
Utilize common honeypot software (endlessh).
Create new system-launch subroutines via crontab or shell scripts.
Ensure System Backups are Enabled (rsnapshot).
Check for suspicious kernel modules with "lsmod"
#linux#security#linuxsecurity#computersecurity#networking#networksecurity#opensource#open source#linux security#network#ubuntu#kali#parrot#debian#gentoo#redhat
175 notes
·
View notes
Text
FF7 Rebirth: All Region Intel
Wanted to make a way to easily access & read all the world/region intel you can get in Rebirth so here's a giant post for that. Everything below the cut.
GRASSLANDS
Kalm: A Recent History
This humble town serves as a transport hub for the grasslands, hence the distinctive bailey built for the monitoring of commercial and private traffic. During the war with the Republic of Junon, Shinra saw fit to occupy Kalm, due to its stout fortifications and strategic value, and it has remained under company control ever since.
As it lacks a reactor of its own, Kalm is reliant on Midgar and its pipelines for a steady supply of mako, which is stored in a large tank for regulated use. This arrangement allows the residents to enjoy both modern conveniences and a healthy environment—a combination that has attracted many new residents of late.
Ten years ago, a significant portion of the town was “damaged,” though Shinra quickly intervened and carried out a comprehensive reconstruction effort. Details regarding the incident and the extent of the destruction are sparse.
Flora and Fauna of the Grasslands
In stark contrast to the barren, mako-ravaged outskirts of Midgar, the ecosystem of the grasslands remains relatively unscathed. Streams flowing from the central mountain range nourish the lush meadows below, which sustain a diverse range of species. Ranchers and farmers also benefit greatly from this bountiful environment.
Vast wetlands make up much of the southern region. In days past, boats and chocobo carriages were a common sight, but as most goods are now transported by sea or air, traffic through the wetlands has steadily decreased. Moreover, as an immense, man-eating serpent dubbed Midgardsormr has been sighted in this area of late, few dare to brave the old trails. Even those capable of evading the gargantuan snake may yet fall victim to one of the many inescapable quagmires.
The Mythril Mine: Changing with the Times.
A natural passage through the mountains between Junon and the grasslands, this mine has long served as a rich source of mithril. The mineral boasts an exquisite shimmer and remarkable strength, and was historically used to fashion the very finest weapons and armor, but it fell out of favor after Shinra developed superior synthetic materials.
After the mine was closed, the Republic of Junon converted it into a tunnel for the general public, allowing travel to and from the grasslands. The glistening mithril deposits drew regular sightseers as well. Following Shinra’s triumph over the republic, however, the tunnel has been effectively abandoned. Various sections have fallen into disrepair, and the depths are host to untold dangers.
JUNON REGION
The Rise and Fall of the Republic of Junon
The people of Junon were once largely seafarers, who only returned to the shore to peddle the bounty of the ocean. Unlike other communities that settled in a single location and gradually expanded their territory, these sailors preferred the freedom of the open sea, and over time banded together with like-minded souls to form a unique society.
As a republic, they repurposed a flotilla of large vessels to construct a floating city that would serve as the center of their trade network. Having forged a robust infrastructure, they then set their sights on uniting the disparate peoples of the world.
Though Junon ushered in an era of economic and cultural prosperity, it was not to last. Shinra’s revolutionary mako technology put paid to their ambitions, and their once proud city now slumbers beneath the waves.
Junon: The Fortress City
Having conquered the Republic of Junon, Shinra constructed a nigh-impregnable fortress on the coast in the heart of their enemy’s former territory. Powered by the world’s only underwater mako reactor and equipped with a colossal cannon capable of firing as far as Wutai, the stronghold resembles a vast battleship, risen from the deep to defend the eastern continent.
Junon is a city composed of multiple levels, each of which is lined with uniform buildings that were originally designed to serve the needs of military personnel. After the war with Wutai, some were converted into hotels and retail outlets, and the arbor and airport now see a constant stream of civilian visitors.
Military exercises are still conducted frequently, however, and should the need arise, defense countermeasures can be deployed at a moment’s notice, transforming the city in to a fortress, ready to repel would-be invaders.
COREL REGION
Costa del Sol: A Recent History
Though Costa del Sol is now a renowned beach resort, it was once home to a string of humble fishing villages. However, when relations between Shinra and the Republic of Junon began to deteriorate, Shinra annexed this portion of the coast. After the war, the company designated the area for redevelopment, transforming it into the must-visit location for avid sunseekers that it is today.
Costa del Sol offers vacation packages to suit any budget, allowing travelers from every corner of the globe to savor the idyllic beaches. Plans that include a trip to the Gold Saucer have proven particularly popular.
Corel: A Tale of Decline
Coal was in high demand in the days of the republic, and the wealth of Mt. Corel drew miners from far and wide. Though the work was hard and dangerous, the laborers banded together to overcome their difficulties, forming a close-knit community in the process.
Alas, the advent of mako saw the price of coal plummet, spelling disaster for the people of Corel. As they struggled to find a way forward, Shinra proposed the construction of a mako reactor, and after much debate, the villagers accepted the offer.
The reactor was constructed with astonishing haste, but just prior to being brought online, it was torn apart by an immense explosion, and has been left in ruins ever since.
The Rise of the Gold Saucer
The tale of the Gold Saucer began with a Shinra employee named Dio, who convinced the company to build a museum called the Reliquary. Although it was doomed to failure, Dio was not to be deterred, and he set about founding the world’s largest theme park, which he first conceived as a small-scale fairground.
In the wake of the Corel Mako Reactor explosion four years ago, plans were set in motion to revitalize the local economy. Hearing this, Dio decided to relocate his fairground to the region, eventually transforming it into a state-of-the-art entertainment complex.
Now known as the Gold Saucer, it is powered by several modular reactors, which are responsible for the surrounding area’s accelerated desertification. In light of this, the reactors are now run at minimum output, in an attempt to mitigate further damage to the environment.
GONGAGA REGION
Gongaga: A Recent History
In ancient times, Gongaga was settled by descendants of the Cetra, who lived in quiet seclusion. The region was largely ignored by later kingdoms and empires, until the Republic of Junon thought to expand its influence westward. They soon discovered, though, that the expense of establishing trade routes through such dense jungle far outweighed the benefits of reaching the small communities there, and elected to instead construct an airstrip and little else.
When war erupted between the republic and Shinra, people the world over were impacted to varying degrees. Those in Gongaga were the rare exception, as being so far removed from the theater of war meant that they were not subject to forced conscription, nor were their villages ever host to the bloodshed.
Life in Gongaga
The village of Gongaga lies at the heart of the humid jungle, where many species of moss, fern, and mushroom thrive. Its people have a long tradition of self-sustenance, growing only enough produce and raising only enough livestock to support their collective. Though the village is by no means commercially enterprising, the Gongaga mushroom endemic to the region is renowned for its rich aroma, and commands a high price.
Gongaga’s fortunes took a turn for the worse following an explosion at the nearby mako reactor. Though much of the jungle was temporarily declared a disaster area, due to its elevation position, the village itself escaped the worst of the fallout—a small mercy considering the devastation wrought below.
The Gongaga Mako Reactor Incident
First generation mako reactors based on the one built in Nibel are prone to malfunction due to flaws in the pressurization system’s design. This, however, did not deter Shinra from installing them at various locations throughout the world, including Gongaga.
The company’s failure to follow their own inspection and maintenance procedures led to a disastrous explosion which claimed the lives of many villagers. Acknowledging its part in the incident, Shinra dedicated a monument to the victims.
This accident was not an isolated occurrence, though, as at least one other reactor is known to have exploded in a similar fashion. Stranger yet, Shinra has been investigating alleged sightings of gigantic life-forms known as “Weapons” near the remains of these destroyed mako reactors.
COSMO CANYON REGION
Cosmo Canyon: Environmental Conditions
Cosmo Canyon is located in the south of the western continent, where countless valleys and caverns have formed in the red clay. In ages past, seismic activity forced this soil to the surface, where it was later eroded by the surging lifestream below, giving the region its unique appearance.
Throughout the year, the canyon sees very little rainfall, and the temperature variation between the plateaus and gorges is considerable. As such, it is extremely difficult to grow crops, and the mere act of survival is a daily struggle. Nevertheless, the canyon is a prime destination for students of planetology. In addition to scholars and devotees, many tourists can also be found here, seeking to take in the “mystical” air. In more practical terms, the arid conditions and lack of cloud cover facilitate the observation of celestial bodies, making the canyon popular among astronomers.
Life in Cosmo Canyon
The founders of the canyon’s eponymous village made use of the naturally formed caves, and following the emergence of planetology, more and more people found themselves drawn to the place. The makeshift walkways and tent-like domiciles have only increased in number as the settlement continues to expand to this day.
Rather than rely on mako, the villagers built an array of windmills, and each home is equipped to store the generated electricity. A leading planetologist, Bugenhagen, introduced this form of wind power to Cosmo Canyon, and it is said his technical marvel was inspired by the ways of the Cetra.
When it comes to nutrition, the villagers’ diet consists mainly of grain and legumes grown around the village, supplemented by game meat obtained with traditional hunting methods.
The Cetra and the Gi
In the distant past, the Cetra made contact with the Gi, entities who could not return to the lifestream. Pitying their plight, the Cetra build altars to commune with and calm these tormented souls in the hope of finding a means to coexist peaceably.
Over time, the Cetra grew increasingly aware of the dire fate that would befall the planet, and resolved to entrust their knowledge to the people of Cosmo Canyon. These teachings would become the foundation of planetology, which continues to be refined through research and discourse even as it is spread throughout the world.
When the Cetra finally departed Cosmo Canyon, none remained to provide solace to the Gi, who in their festering anguish and rage were driven to turn on the villagers. Many brave warriors gave their lives to beat back these vengeful spirits, entombing them in their prison once more.
NIBEL REGION
Mt. Nibel and the Birth of Mako Energy
It is said that beyond the desolate, jagged crags of Mt. Nibel lies the land of the dead, and few dare to approach its slopes. Indeed, even plant life struggles to find a foothold here, and with tumbling boulders and rockslides a constant threat, the locals see little reason to make such a perilous journey.
Many of the mountain’s caves are filled with mako vapor, and the inner reaches contain mako springs and naturally formed materia. Shinra’s search for a new energy source led them to Mt. Nibel, and its abundant supply of mako made it the ideal site for the world’s first reactor.
Although it played an instrumental role in the proliferation of mako energy, the Nibel reactor’s time in the spotlight was brief, and it now operates at greatly reduced capacity.
Nibelheim: A Recent History
In the shadow of the jagged formations at the foot of Mt. Nibel, the village of Nibelheim had little to offer the outside world. However, their quiet existence would change dramatically with Shinra’s discovery of vast reserves of mako within the mountain.
The company’s efforts began with the construction of Shinra Manor on a plot of leased land. It was there that the head of Research and Development, Professor Gast, and his assistant, Professor Hojo, pioneered studies on mako and Jenova.
Shinra’s financial investment delivered the people of Nibelheim from poverty. Their newfound happiness and prosperity would be short-lived, though, as the entire village was burned to the ground and countless innocents slaughtered by Sephiroth.
A perfect reconstruction of Nibelheim was later erected on the site in secret, and now serves as a treatment center for victims of mako poisoning.
36 notes
·
View notes
Text
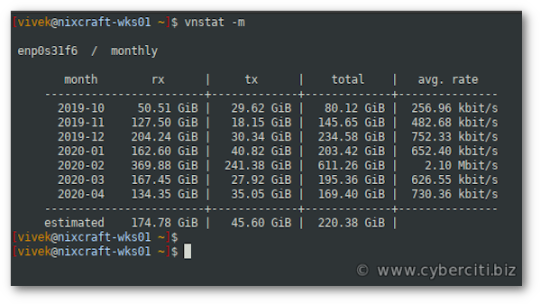
Do you need to keep track of the network traffic (bandwidth) usage for the Network interface controller (NIC) of your Debian Linux-based cloud or bare metal server? Look no forward. Try the vnStat, a free and open-source console-based network traffic monitor that keeps a log of 5-minute intervals, hourly, daily, monthly, and yearly network traffic for the selected interface. Once installed, vnStat can be used even without root permissions on most systems.
13 notes
·
View notes
Text
Kinda wanna write a kernel module or something that monitors network traffic and reinterprets it as audio samples in real time, to hear the modern version of the dial-up screech
#I imagine‚ since most network traffic nowadays is encrypted and hence indistinguishable from uniform random data‚#most of it would come out as just featureless white noise#but still
18 notes
·
View notes