#Network Mapping
Explore tagged Tumblr posts
Text
Mind Mazine just leveled up. 🚀🧠💻 🪪 Logged by: JoeBot.syslog.armed(✓) 📍Status: Posted. Tracked. Probably flagged. 🔚 "Logged. Filed. Ignored."
#AI#AI arms race#AI cybersecurity#AI job rejection#AI threat modeling#AI visualizations#context hacking#Cybersecurity#cybersecurity humor#digital privacy#job automation#JoeBot#LLMs#network mapping#network security#phishing email examples#phishing scams#Sankey diagrams#snark#social engineering#SysOps
1 note
·
View note
Text
Top 35 Nmap Commands
Nmap (Network Mapper) is an essential open-source security tool for network exploration, security scanning, and auditing. For hackers, penetration testers, and security professionals, Nmap serves as a crucial reconnaissance tool to identify vulnerabilities and map out network infrastructures. The powerful utility comes with numerous options that might seem overwhelming for beginners, but…
#ethical hacking#network mapping#network security#nmap#penetration testing#port scanning#reconnaissance#security scanning#security tools#vulnerability assessment
0 notes
Text
The Crucial Importance of Network Traffic Classification for Optimizing Connectivity
Greetings from Solana Networks, the leading source for state-of-the-art Network Traffic Classification solutions. With the ability to discern between dangerous and benign actions, our sophisticated algorithms carefully examine data flows and provide organisations with insights never before possible. We ensure optimal performance and security by decoding complex network behaviours with our cutting-edge technologies. Solana Networks offers customised solutions that are suited to your requirements, whether your goals are seamless network management, threat detection, or compliance adherence. Put your trust in our experience to protect your digital infrastructure from changing threats, increase productivity, and streamline operations. With Solana Networks, discover the possibilities of network intelligence in the future.
Phone: 613-596-2557
E-mail: [email protected]
#Network Traffic Classification#Network Topology Tools#Network Discovery Tools#Network Mapping#Network Topology#Route Analytics#Network Topology Tool#Network Topology Discovery#Network Discovery#Network Discovery Solution#Network Mapping Solution#Network Traffic Monitoring Solution#Network Traffic Monitoring#Lawful Intercept#Encrypted Traffic Classification#Encrypted Network Traffic Classification#Encrypted Traffic Intelligence#Security Machine Learning#Anomaly Detection#Cyber Threat Monitoring#Ddos Attack#Network Security Monitoring#Scada Security#Threat And Risk Assessment#Vulnerability Assessment#Network Troubleshooting
0 notes
Text
Nmap: A Comprehensive Network Mapping and Security Scanning Tool
Nmap is a free and open-source network scanning utility that can be used to discover hosts and services on a network, as well as to identify potential security vulnerabilities. It is a powerful and versatile tool that is used by security professionals, system administrators, and penetration testers.
Nmap can perform a variety of scans, including:
Host discovery: Nmap can discover hosts on a network by sending probes to IP addresses. This can be used to identify all devices on the network, even those that are not actively responding to network traffic.
Port scanning: Nmap can scan a target host or network to determine which ports are open and which services are running on those ports. This can be used to identify potential security vulnerabilities, such as open ports that are not being used by a service.
Version detection: Nmap can detect the version of software running on a target host. This information can be used to identify vulnerabilities in the software, as well as to determine if the software is up-to-date.
OS fingerprinting: Nmap can determine the operating system running on a target host, even if the OS is running behind a firewall or NAT device. This information can be used to identify potential security vulnerabilities and make informed decisions about firewall and access control policies.
Scriptable: Nmap can be automated and extended using Nmap scripts. Nmap scripts can be used to automate various tasks, such as detecting open ports, performing vulnerability scans, and collecting information about a target host.
Nmap is a powerful and versatile tool that can be used for a variety of tasks. It is an essential tool for security professionals who need to map their networks, identify potential security threats, and stay ahead of the curve in the ever-evolving field of cybersecurity.
Here are some of the key benefits of using Nmap:
Free and open-source: Nmap is free and open-source, making it accessible to everyone, regardless of budget or experience.
Easy to use: Nmap has a user-friendly interface and is easy to use, even for those who are new to network mapping and security auditing.
Versatile: Nmap can be used for a variety of tasks, making it a versatile tool for any security professional.
Comprehensive: Nmap offers a wide range of features and capabilities, making it a comprehensive tool for network mapping and security auditing.
Supports multiple platforms: Nmap can be run on various operating systems, making it a versatile tool that can be used by anyone, regardless of their platform of choice.
Large community: Nmap has a large and active community of users, developers, and security experts who are constantly contributing to its development and improvement.
Here are some of the key uses of Nmap:
Network mapping: Nmap can be used to map a network by discovering hosts and services on the network. This information can be used to understand the network topology and identify potential security vulnerabilities.
Security auditing: Nmap can be used to audit a network for security vulnerabilities. This can be done by scanning for open ports, detecting the version of software running on hosts, and fingerprinting the operating system of hosts.
Penetration testing: Nmap can be used to perform penetration tests on networks. This can be done by scanning for open ports and services and then exploiting any vulnerabilities that are found.
Network troubleshooting: Nmap can be used to troubleshoot network problems. This can be done by scanning for hosts that are not responding to network traffic, or by detecting services that are not running on hosts.
Here are some tips for using Nmap safely and ethically:
Always get permission before scanning a network.
Do not scan networks that you do not have permission to scan.
Do not use Nmap to attack or exploit networks.
Use the least intrusive scan type that will achieve your goals.
Be aware of the laws and regulations that apply to network scanning in your jurisdiction.
Nmap is a powerful and versatile tool that can be used for a variety of tasks. It is an essential tool for security professionals who need to map their networks, identify potential security threats, and stay ahead of the curve in the ever-evolving field of cybersecurity.
Conclusion
Nmap is a powerful and versatile tool that can be used for a variety of tasks in network security. It is an essential tool for security professionals who need to map their networks, identify potential security threats, and stay ahead of the curve in the ever-evolving field of cybersecurity.
Here are some of the key takeaways from this blog post:
Nmap is a free and open-source network scanning utility that can be used to discover hosts and services on a network, as well as to identify potential security vulnerabilities.
Nmap can perform a variety of scans, including host discovery, port scanning, version detection, OS fingerprinting, and scripting.
Nmap is a powerful and versatile tool that can be used for a variety of tasks, including network mapping, security auditing, penetration testing, and network troubleshooting.
It is important to use Nmap safely and ethically by getting permission before scanning a network, not scanning networks that you do not have permission to scan, not using Nmap to attack or exploit networks, using the least intrusive scan type that will achieve your goals, and being aware of the laws and regulations that apply to network scanning in your jurisdiction.
0 notes
Text

North American passenger railway routes in the 1930s. Social studies, intermediate grades. 1938.
Internet Archive
From a textbook uploaded by LexW
#public transit#public transportation#rail#railroads#travel#loss#decline#maps#charts#interlacing#webs#networks#nemfrog#1938#1930s#lexw
373 notes
·
View notes
Text







2013 adventure time era
#i rememebr there was an adventure time minecraft map back in like#2013#like on the 360 and i remember my brother destrotying it with lava & i cried#like actually cried i begged him 2 stop im shitting#ok anyway#2010s#adventure time#scene#scene revival#scenecore#nostalgiacore#early 2010s#dm for credit or removal#2010s aesthetic#cartoon network#2010s nostalgia#childhood nostalgia#cutecore#kawaiicore#idk#stamps#tw flashing
311 notes
·
View notes
Text

Bc I haven't seen anyone else talk about this yet.
#mexico#gulf of mexico#gulf of america#google#google maps#destiel#destiel meme#destiel confession#destiel confession meme#destiel news network
171 notes
·
View notes
Photo
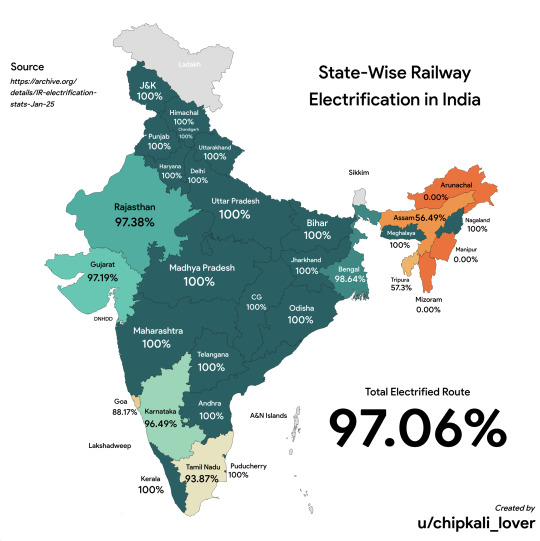
State-Wise Railway Electrification in India
by chipkali_lover/reddit
78 notes
·
View notes
Text






44 notes
·
View notes
Text


Pearl
#greyscale to colour#greyscale portrait#greyscale study#gradient maps#steven universe#steven universe fanart#su#pearl#pearl fanart#cartoon network fanart#art#digital art
76 notes
·
View notes
Text

Inktober Day 5: Treasure MAP
[ENGLISH]
I miss drawing these four children together.
[PORTUGUÊS]
Saudades de desenhar essas quatro crianças juntas.
#inktober#inktober challenge#inktober 2023#fanart#crossover#day 5#map#treasure map#gravity falls#steven universe#disney#cartoon network#universe falls#steven#dipper#mabel#connie
179 notes
·
View notes
Text
i know i tend to baffle people a little the way i portray red deer in my comics and whatever because its such a weird nexus of alberta stereotypes that i try to avoid and all but i just want to reiterate that every once in a while i find a little more information on queer activism in red deer and i just want to remind the red deerios that your little city did some vital work collecting oral history in the 1990s and it pissed off stockwell day SO MUCH and i believe in you guys to keep that tradition alive mwah mwah
#hapo rambles#hapo reads queer history#hapo reads canadian history#im reading meeting minutes today and its so fascinating#calgary just DROPS OFF THE MAP and no one can seem to get in touch with anyone down there in the sister org for like 10 years#and then by the end of the 80s and early 90s there are calgarians networking across western canada hooray#and they do mention lil ol red deer and it gladdens my heart#southern alberta i am not leaving you out i swear even fuckin brooks makes a cameo in prairie fairies#i know i know the official demonym is deerians but i support deerios#i respect your culture by promoting some kids suggestion ok#and i am still sad that my trip down there this time last year was cancelled
11 notes
·
View notes
Text
Crack theory that Decarabian is inspired by Qin Shi Huang, founder of the Qin dynasty and the first emperor (previous rulers refered to themselves as 'king') of China
In the chinese version, Decarabian is occationally refered to as 孤王 (gūwáng, lone(ly) king) which is a title Qin Shi Huang created for himself for being so high and mighty that normal people cannot come close to him
Qin Shi Huang has been viewed as a tyrant, mostly due to assessments by the Han dynasty that came after
However, he also unified China via standardization of weights and measurement, wheel axels, currencies, written language script, and developed extensive networks of roads and canals for trade and communication. Similar to Decarabian's methodical organization (to the point of micromanagement) of his city
Qin Shi Huang is also known for connecting various state walls built during previous centuries into the precursor to the Great Wall of China for defence against attacks from northern tribes, parallelling Decarabian's tall walls that encircle Old Mondstadt for Safety (or even the storm barrier)
Bonus:
The state of Qin also conquered the six other powerful states in China at the time, ending the Warring States period — so I propose that Decarabian not only preemptively declared himself the seat of the Anemo Archon (which would explain why both he and Venti get refered to as 'wind god') but also the overall victor of the Archon War
#do you think there's historical revisionism in mondstadt? some guy writing 'ya know maybe decarabian wasn't That bad'#'sure he was a tyrant and it was miserable living under him but think about it he organized old mondstadt so effidently'#'he standardized wheel axels and units of measurement! Do you think Barbatos Archon of Freedom who let the Lawrence Clan take power—#— would have done that? We owe our beautiful landscapes and bountiful crops to Barbatos but we too owe the foundations—#— of our society to Decarabian' and then the church of favonius grills him for speaking ill of Barbatos#while Venti reluctantly goes 'I GUESS he has a point but for the record everything would have been standardized after the archon war anyway#'across teyvat even. Everyone uses Mora Decarabian sure didn't standarize THAT one'#anyway qin shi huang apparently also built a network of tunnels and passageway to his over 200 palaces#so mondstadt underground decarabian reminants map expansion When#genshin talk
22 notes
·
View notes
Text
36 notes
·
View notes
Text

doing my dissertation is like. guys look i made a Cloud. no I don't have a final research question yet why would I need that
#LOOK I MADE A CLOUD THOUGH IS IT NOT SO COOL#its a network map of interstate relationships between rcep members pre-2012#dissertation
6 notes
·
View notes
Text
if i ignore the lore of nightreign being weird then it actually sounds like possibly the most fun and addictive thing on the planet. i die for a good battle royale sorry and the idea of a soulslike rougelike survival action game AND ITS MULTIPLAYER? could be catastrophic. put some kind of progression for the account and oh my god i would pay anything. ANYTHING.
#its not a battle royale i know but that kind of like. game based progression on a huge map. yk?#im gonna register for the network test i need to be there i need it#and also the fact u can do it solo but itll just be harder I LOVE YOU FROMSOFT#ramblings
7 notes
·
View notes