#SendTo
Explore tagged Tumblr posts
Text
Image generation AI + flickr + PopBox specialized functions
#Stable Diffusion#BRAV5#Beautiful Realistic Asians#Generation AI#Stable Diffusion Web UI#Google Colaboratory#flickr.com#PopBox#convert.sh#CygWin#Windows11#SendTo#send to command prompt#Send to CygWin
0 notes
Photo


(via "Dr Phil Send Toes " Sticker for Sale by ConstoStore)
0 notes
Text
okay so if people can just,,, send eachother tumblr posts WHY do i see people tagging eachother in notes so often?????????????
#mimimi its to sendto mutuals without talking#just speak to them its a conversation starter#they dont reply? thats on them missing out on a conversation starter
0 notes
Text
My Library Is Going To Get Rid of Tampon Dispensers in the Men's Bathrooms! You Can Stop Them!
A few months ago the San Antonio Public Library system implemented free tampon and pad dispensers in all men, women, and staff bathrooms in every library! Unfortunately, there have been a lot of complaints and defacing of the machines in the men's bathrooms, so they're considering removing them.
You can stop this! Before giving the link, I'll say please be kind!!! Focus on the positives of these machines being in the men's restrooms. The vast majority of staff WANT these dispensers in the bathrooms, but they need public support.
Fill out this form to contact library administration!
https://www.mysapl.org/About/Contact-Us-Library-Administration/Contact-SAPL?sendto=SAPL
Deadline is March 3, 2025! If it's the 4th then I say go for it anyway, but I'm not sure if it will matter anymore
If you would rather call, or want your comment to be received ASAP, you can call our Interim Director herself! You can DM me for her work number, which IS publicly available, I'm not doxxing her, but I don't want to put her number here for any malicious person scrolling to use
#library#public libraries#transgender#trans pride#transmasc#trans rights#celery speaks#trans man#please reblog
10 notes
·
View notes
Text
Has antone done suselle awesome lesbian couple evil and intimidating kris ? If so please sendto me
2 notes
·
View notes
Text
CS39006: Assignment 5 Solved
Emulating End-to-End Reliable Flow Control over Unreliable Communication Channels In this assignment, you will be building support for end-to-end reliable data transfer on top of an unreliable communication channel, with a window-based flow control approach. You have been introduced to the function calls socket, bind, sendto, and recvfrom to work with UDP sockets. Assume that the TCP sockets are…
0 notes
Text
eBPF for TLS Traffic Tracing: Secure & Efficient Observability

Tracing TLS (Transport Layer Security) traffic is crucial for modern observability systems. It helps monitor encrypted communication, diagnose issues, and optimize application performance.
However, traditional methods like TLS proxying and packet capturing often come with significant performance overheads and security risks. They are not always the ideal solution, particularly for high-performance or security-sensitive environments.
This is where eBPF (Extended Berkeley Packet Filter) steps in. eBPF is a revolutionary technology that enables seamless TLS traffic tracing directly within the Linux kernel, minimizing performance impact and enhancing security. This article explores how eBPF works, its implementation, and its benefits for developers and DevOps teams.
Challenges with Traditional TLS Traffic Tracing
Tracing TLS traffic has always been an integral part of observability systems. Traditionally, these systems have relied on techniques such as:
TLS Proxying
Man-in-the-Middle (MITM) Proxies
Packet Capturing and Decryption
Logging TLS Handshakes
Unfortunately, these methods come with major drawbacks that prevent any one of them from becoming the dominant approach:
Performance Overhead: Techniques like TLS proxying and packet capturing can significantly tax the CPU due to the effort required for decryption and packet analysis.
Security Risks: TLS proxies often require creating and maintaining fake certificates or adding custom certificate authorities to the client’s system. This can lead to serious security vulnerabilities.
The eBPF Advantage
eBPF addresses these challenges by offering a state-of-the-art method for TLS traffic tracing. Here’s why it stands out:
Minimal Performance Impact: eBPF operates directly within the Linux kernel, avoiding the CPU-intensive operations of traditional methods.
Enhanced Security: It eliminates the need for fake certificates or risky man-in-the-middle techniques.
eBPF enables developers to attach hooks to system calls. For instance, a system call like sendto used for sending data over a UDP socket can be monitored. By attaching an eBPF program to sendto, you can capture critical information like the buffer, function descriptor, and buffer length as soon as the system call is invoked.
This makes TLS tracing seamless and secure, addressing the limitations of older methods. The next obvious question is how eBPF is able to achieve all of this? How does it work under the hood.
How does eBPF work?
eBPF programs are typically written in C and are then compiled into a intermediate bytecode representation. As mentioned above, these programs can be attached to various system calls, allowing them to be called when those calls are executed.

Therefore, to trace TLS data specifically, these hooks can be attached to the following system calls: sendto, recvfrom, socket, connect, accept, SSL_read, and SSL_write. These calls contain the actual buffer, its size, and the function descriptor before the request gets encrypted and after the response gets decrypted. Thus, they don’t need the session key to decrypt the responses coming from the server.
Sample application attaching hooks to SSL_read and SSL_write functions

Sending data from the kernel space to the user space
Attaching hooks on the user side.
Bringing it all together, we can compile this into a complete program which will look something like this:// +build ignore #include <linux/types.h> #include <bpf/bpf_helpers.h> #include <bpf/bpf_core_read.h> #include "vmlinux.h" #include "bpf_tracing.h" #include "tls_message.h" #include "openssl_tracer_types.h" // Declaring the perf submit event struct { __uint(type, BPF_MAP_TYPE_PERF_EVENT_ARRAY); } TLS_DATA_PERF_OUTPUT SEC(".maps"); // Declaring this using btf type format struct { __uint(type, BPF_MAP_TYPE_HASH); __type(key, __u64); __type(value, char *); __uint(max_entries, 10000); __uint(map_flags, 0); } active_ssl_read_args_map SEC(".maps"); struct { __uint(type, BPF_MAP_TYPE_HASH); __type(key, __u64); __type(value, const char *); __uint(max_entries, 10000); __uint(map_flags, 0); } active_ssl_write_args_map SEC(".maps"); struct { __uint(type, BPF_MAP_TYPE_PERCPU_ARRAY); __type(key, u32); __type(value, struct ssl_data_event_t); __uint(max_entries, 1); } data_buffer_heap SEC(".maps"); static __inline struct ssl_data_event_t *create_ssl_data_event(struct pt_regs *ctx ,u64 current_pid_tgid) { u32 kZero = 0; struct ssl_data_event_t *event = bpf_map_lookup_elem(&data_buffer_heap, &kZero); if (event == NULL) { return NULL; } const u32 kMask32b = 0xffffffff; event->timestamp_ns = bpf_ktime_get_ns(); event->pid = current_pid_tgid >> 32; event->tid = current_pid_tgid & kMask32b; return event; } static int process_SSL_data(struct pt_regs *ctx, u64 id, enum ssl_data_event_type type, char *buf) { int len = (int)PT_REGS_RC(ctx); if (len < 0) { return 0; } struct ssl_data_event_t *event = create_ssl_data_event(ctx, id); struct ssl_data_event_t event2 = {}; if (event == NULL) { return 0; } event->type = type; // This is a max function, but it is written in such a way to keep older BPF verifiers happy. event->data_len = (len < MAX_DATA_SIZE ? (len & (MAX_DATA_SIZE - 1)) : MAX_DATA_SIZE); event2.type = type; asm volatile("%[len] &= 0x1fff;\n" ::[len] "+r"(len):); bpf_probe_read(&event->data, len & 0x1fff, buf); bpf_perf_event_output(ctx, &TLS_DATA_PERF_OUTPUT , BPF_F_CURRENT_CPU, event, sizeof(*event)); return 0; } SEC("uprobe/SSL_write") int uprobe_entry_SSL_write(struct pt_regs *ctx) { u64 processThreadID = bpf_get_current_pid_tgid(); char *user_space_buf = (char *)PT_REGS_PARM2(ctx); bpf_printk("This is the buffer in the write functio%s:\n", user_space_buf); bpf_map_update_elem(&active_ssl_write_args_map, &processThreadID, &user_space_buf, 0); return 0; } SEC("uprobe/SSL_read") int uprobe_entry_SSL_read(struct pt_regs *ctx) { u64 processThreadID = bpf_get_current_pid_tgid(); void *user_space_buf = (void *)PT_REGS_PARM2(ctx); bpf_printk("The value of buf is: %s", user_space_buf); bpf_map_update_elem(&active_ssl_read_args_map, &processThreadID, &user_space_buf, 0); return 0; } SEC("uretprobe/SSL_write") int uprobe_return_SSL_write(struct pt_regs *ctx) { u64 processThreadID = bpf_get_current_pid_tgid(); // Looking up the buffer in the map char *buffer = bpf_map_lookup_elem(&active_ssl_write_args_map, &processThreadID); if (buffer != NULL) { process_SSL_data(ctx, processThreadID, kSSLWrite, buffer); } bpf_map_delete_elem(&active_ssl_write_args_map, &processThreadID); return 0; } // Attach to the return of the read function. SEC("uretprobe/SSL_read") int uprobe_return_SSL_read(struct pt_regs *ctx) { u64 processThreadID = bpf_get_current_pid_tgid(); // Looking up the buffer in the map char *buffer = bpf_map_lookup_elem(&active_ssl_read_args_map, &processThreadID); if (buffer != NULL) { process_SSL_data(ctx, processThreadID, kSSLRead, buffer); } bpf_map_delete_elem(&active_ssl_read_args_map, &processThreadID); return 0; } char _license[] SEC("license") = "GPL";
And to add these probes on the user side, we can use the Cilium library to write Go code as given below://This program demonstrates how to use eBPF to intercept OpenSSL calls and log the contents of the data buffers. package main import ( "bytes" "encoding/binary" "errors" "log" "os" "os/signal" "syscall" "github.com/cilium/ebpf/link" "github.com/cilium/ebpf/perf" "github.com/cilium/ebpf/rlimit" ) const ( // The path to the ELF binary containing the function to trace. // On some distributions, the 'SSL_read' and 'SSl_write' functions are provided by a // dynamically-linked library, so the path of the library will need // to be specified instead, e.g. /usr/lib/libreadline.so.8. // Use `ldd /bin/bash` to find these paths. libsslPath = "/usr/lib/x86_64-linux-gnu/libssl.so.3" read = "SSL_read" write = "SSL_write" ) func main() { stopper := make(chan os.Signal, 1) signal.Notify(stopper, os.Interrupt, syscall.SIGTERM) //Allow the current process to lock memory for eBPF. if err := rlimit.RemoveMemlock(); err != nil { log.Fatalf("failed to raise rlimit: %v", err) } //Load precompiled eBPF program and maps into the kernel objs := bpfObjects{} if err := loadBpfObjects(&objs, nil); err != nil { log.Fatalf("failed to load BPF: %v", err) } defer objs.Close() //Open an ELF binary and read its es. ex, err := link.OpenExecutable(libsslPath) if err != nil { log.Fatalf("failed to open executable: %v", err) } upw, err := ex.Uprobe(write, objs.UprobeEntrySSL_write, nil) if err != nil { log.Fatalf("failed to open uprobe: %v", err) } defer upw.Close() //Attach uretprobe to the SSL_write function. urw, err := ex.Uretprobe(write, objs.UprobeReturnSSL_write, nil) if err != nil { log.Fatalf("failed to open uretprobe: %v", err) } defer urw.Close() //Attach the uprobe to the SSL_read function. upr, err := ex.Uprobe(read, objs.UprobeEntrySSL_read, nil) if err != nil { log.Fatalf("failed to open uprobe: %v", err) } defer upr.Close() //Attach uretprobe to the SSL_read function. urr, err := ex.Uretprobe(read, objs.UprobeReturnSSL_read, nil) if err != nil { log.Fatalf("failed to open uretprobe: %v", err) } defer urr.Close() rd, err := perf.NewReader(objs.TLS_DATA_PERF_OUTPUT, os.Getpagesize()) if err != nil { log.Fatalf("failed to create perf event reader: %v", err) } defer rd.Close() go func() { //Wait for the signal to stop the program. <-stopper log.Println("Detaching probes...") if err := rd.Close(); err != nil { log.Fatalf("failed to close perf event reader: %v", err) } }() log.Printf("Attaching probes...") var event bpfSslDataEventT for { record, err := rd.Read() if err != nil { if errors.Is(err, perf.ErrClosed) { return } log.Printf("reading from perf event reader: %s", err) continue } log.Printf("perf event recorded") if record.LostSamples != 0 { log.Printf("perf event ring buffer full, dropped %d samples", record.LostSamples) continue } // Parse the perf event entry into a bpfEvent structure. if err := binary.Read(bytes.NewBuffer(record.RawSample), binary.LittleEndian, &event); err != nil { log.Printf("parsing perf event: %s", err) continue } log.Printf("this is the event: %v", event) // Print the data buffer contents. } }
Now, to run this code, you need to compile the bpf files and generate the go structs and then run the code, for this, we can create a simple shell script as given below:export BPF_CLANG=clang-14 export BPF_CFLAGS="-I/usr/include/x86_64-linux-gnu -D__x86_64__ -O2 -g -Wall -Werror" export TARGET=<your-cpu-architecture> # To compile and run the ebpf program... go generate ./... && go run -exec sudo .
Now when you run this script, it will start tracing all the TLS calls that you make from your machine. The data for them will be shown on the same terminal window.
Outputting the data to the user.
It is because of these advantages that eBPF is gaining popularity by every passing day. But eBPF too, has some challenges that cannot be ignored.
For starters, writing and debugging eBPF programs can be a challenging task, especially for programmers who are not familiar with low-level programming.
Since eBPF code gets loaded onto the kernel, it needs to be bug-free, as any vulnerabilities in the eBPF code can lead to kernel crashes or security exploits.
Another constraint with eBPF programs is their kernel version dependency. They support different features across different kernel versions so porting eBPF code can be tough and can lead to compatibility issues.
Since eBPF is a relatively new technology the data structures used to write these programs(BPF maps) have certain limitations. For instance, their size cannot be changed dynamically and some map types do not support concurrent read and write operations.
Limitations Of This Approach
Not everything works all the time and no matter how robust, this approach has its limitations as well. Some of the limitations are as follows:
Kernel Dependency: eBPF relies on specific kernel features that may not be present in older kernels. This limits its use to environments with up-to-date kernels, making it unsuitable for legacy systems.
Kernel Stability: Bugs or changes in the kernel could impact the stability and performance of eBPF programs, requiring close tracking of kernel updates and patches.
User-Space Encryption: If encryption and decryption occur entirely in user-space libraries (like OpenSSL or BoringSSL), eBPF might not capture all necessary data, as it primarily hooks into system calls and kernel functions.
Sandbox Restrictions: eBPF programs run in a sandboxed environment with limited capabilities. While this enhances security, it also restricts what eBPF programs can do, requiring careful design to achieve the desired tracing functionality.
How Keploy uses eBPF for TLS Handling?
Keploy, a modern API testing platform, which leverages eBPF (Extended Berkeley Packet Filter) to efficiently trace TLS (Transport Layer Security) traffic. This approach addresses the challenges of monitoring encrypted data streams without compromising performance or security.
Key Benefits:
Seamless Traffic Tracing: Keploy uses eBPF to attach hooks to system calls such as SSL_read and SSL_write. These hooks capture encrypted and decrypted data before it reaches the application layer, enabling detailed traffic inspection.
Minimal Overhead: By operating directly in the Linux kernel, eBPF allows Keploy to monitor TLS traffic with negligible impact on system performance, making it suitable for high-load environments.
Improved Observability: The collected data helps Keploy deliver actionable insights for API testing, debugging, and observability. It ensures high test coverage and robust monitoring for applications with encrypted communications.
Conclusion
eBPF offers a mixed bag of power and limitations, but no one can really deny its potential, and as the technology gets more mature, it is certainly bound to leave a big impact on the tech world. As eBPF continues to evolve, it holds immense promise for shaping the future of observability, security, and performance monitoring.
While it does come with its own set of challenges, such as kernel dependencies and a learning curve, the benefits of eBPF in modern observability are undeniable. Its seamless integration with the Linux kernel, minimal overhead, and robust tracing capabilities make it an invaluable tool for debugging, optimizing, and ensuring the reliability of secure applications. Now is the perfect time to explore this groundbreaking technology and harness its potential for your systems.
FAQs
What is eBPF?
eBPF (Extended Berkeley Packet Filter) is a technology that allows developers to run sandboxed programs in the Linux kernel without modifying its source code. It’s widely used for networking, observability, and security purposes.
Why is tracing TLS traffic important?
Tracing TLS traffic is crucial for debugging, performance optimization, and understanding the behavior of secure applications. It helps identify bottlenecks, diagnose issues, and ensure compliance with security policies.
How does eBPF enable TLS traffic tracing?
eBPF attaches hooks to system calls like sendto, recvfrom, SSL_read, and SSL_write. These hooks capture data before encryption or after decryption, allowing seamless tracing without needing session keys or modifying certificates.
What are the advantages of using eBPF over traditional TLS tracing methods?
Minimal performance overhead on the CPU.
No need for fake certificates or proxy configurations.
Enhanced security with a kernel-native approach.
Compatibility with modern observability tools.
Are there any limitations to using eBPF?
Yes, eBPF has some limitations, including:
Kernel dependency: It requires a modern Linux kernel.
Steep learning curve: Writing and debugging eBPF programs can be challenging.
Restricted capabilities: eBPF programs run in a sandboxed environment.
What programming languages can I use with eBPF?
eBPF programs are typically written in C but can be integrated with user-space programs written in languages like Golang, Python, and Rust.
How can I get started with eBPF?
Start by learning the basics of Linux system calls and kernel development. Use tools like BPFTrace or frameworks like Cilium for easier eBPF programming. Tutorials and eBPF books are also great resources.
What are some practical use cases of eBPF in observability?
Tracing application network traffic.
Debugging performance bottlenecks.
Enhancing security through real-time monitoring.
Capturing and analyzing TLS data without decryption keys.
0 notes
Text

Sendto:: "DCROx & 0xDCR Atomic Wallet" available 2024 Trading Base Network created by [email protected] for support before adding to portfolio. Payment direct: "0xeCCfbDE07c366034D4284B422e4Ba4511f060b0" before adding to portfolio.
0 notes
Text
Mi hogar
Sugerencia de escritura del día¿Qué es lo que te gusta del lugar donde vives?Ver todas las respuestas sendto#ciraortega@code#5742791Xzsr3z.earth.es.es Querida Cira, Hace tres días que activaron la red de comunicaciones, al abrir mi correspondencia he tenido la emocionante sorpresa de encontrar tu nombre en la lista de correos recibidos, así que, arriesgándome a molestarte un poco, te voy a…

View On WordPress
0 notes
Text
How to Customize the SendTo Menu in Windows
The SendTo menu in Windows has been a useful feature for a long time. It may be buried in the right-click context menu in File Explorer, but you can use it to send files to a specific location, copy photos to a new device, or print your work in moments.
RAYMOND OGLESBY @RaymondOglesby2December 8, 2022 The SendTo menu in Windows has been a useful feature for a long time. It may be buried in the right-click context menu in File Explorer, but you can use it to send files to a specific location, copy photos to a new device, or print your work in moments. It also comes with default entries you may never use and lack certain features you may want.…
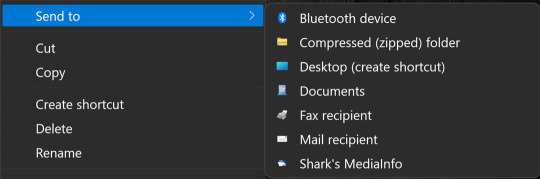
View On WordPress
0 notes
Link
#Edit send to menu#Disable send to menu#Add new item to send to menu#Send to#delete an item from send to menu#sendto menu editor
0 notes
Text
Tôi khuyên bạn giống như hoa dại, hãy học cách sinh tồn trong mọi hoàn cảnh khắc nghiệt nhất, ngay cả khi người đời cho rằng bạn không thể.

0 notes
Photo










Back Bay Penthouse, the latest version.
Added Neon Flats to the usual Noir Penthouse stuff (notably, the ceiling fans + lights in the kitchen area, the bathroom walls + pillars + floor, probably the rug.
And of course, pieces of modular kitchen, CWSS, Do It Yourshelf, possibly Creative Clutter. Settlement Ambush Kit, random mods for custom shelving-containers (I especially like the holotape racks, though I probably should have put the game ones above each of the larger ones, for symmetry's sake), and some of Crimsonrider's Unique Furniture (?).
The only thing missing (well, aside from a picture of the quarter circle outdoor nook) is a picture of the final room (same size as the crafting room, 2x2) which holds the teleporter (added later) and a Basement Living portal to where the power armor stands are (I could have just built up or down, but why bother?) along with the SendTo mats so I can hit SPACE to teleport new suits to storage.
It's not like I use the damn things, after all.
1 note
·
View note
Link
2 notes
·
View notes
Photo
Sometimes life is a struggle. You fight, and fight, and fight, and at the end of it you can’t help but wonder if it was all worth it. But we are Risen, and we were made to fight like that. What’s more, we were made to fight like that together. So don’t let a brother or sister fight the Deep alone, and reach out when the Darkness becomes too much. — //GHOST LOG//
TYPE: PERSONAL RECORD [SENDTO: OUTPOST VALE-ZETA [FORMER: SETTLEMENT RIDGEVALE], RECORD KEEPING]
PARTIES: Two [2]. One [1] Risen-type, Class undefined, designate Murdoch, K. [m]; One [1] Ghost-type, designate Sybil [s]
ASSOCIATIONS: Risen; Lightbearer; Murdoch, K.; Light; Luna; the Moon; Hive; the Pit; Pit of Heresy
//AUDIO PRESERVED//
//TRANSCRIPT FOLLOWS…/ [s:01] So how long are we going to wait here? [grunt] [m:01] Not sure. Until either Winter and Flip are done or their Ghosts need assistance getting them back up. Or until this thing gets bored. [s:02] Do ogres get bored? [m:02] I dunno. Do they have enough intelligence to feel boredom? [s:03] You feel boredom. [m:03] Oof. Keep hurting my feelings like that, I might throw you out there. Bet you’ll fix the boredom problem for a second. [s:04] You wouldn’t dare. [m:04] Yeah, you got me.
#destiny #destiny2 #destiny2luna #destiny2themoon #destiny2hive #destiny2story #destinyheadcanon #destinyrisen #destinytitan
#destiny#destiny2#destiny2luna#destiny2themoon#destiny2hive#destiny2story#destinyheadcanon#destinyrisen#destinytitan
1 note
·
View note
Link
JSをYUICOMPRESSORとCLOSURE-COMPILERで同時処理する必要はあるのか? Is it necessary to process JS simultaneously with YUICOMPRESSOR and CLOSURE-COMPILER? WordPress also has hundreds of JavaScript files, but do not leave the compression to the plug-in, just send it with a right click and simultaneously process it with Yahoo! / YUICOMPRESSOR and Google / CLOSURE-COMPILER to automatically compress with high effect Let's adopt it! Is it pointless?
#Yahoo!#YUICOMPRESSOR#Google#CLOSURE#JavaScript#JAR#JAVA#Two-stage compression#auto2015.bat#MS batch file#sendto
0 notes