#cloud networking solutions
Explore tagged Tumblr posts
Text
#Cloud-managed services#cloud Infrastructure monitoring service provider#cloud storage backup solutions#cloud networking solutions#cloud disaster recovery solutions#cloud infrastructure migration
0 notes
Text
What does storage mean to you?
#storage#storage solutions#warehouse storage#cloud storage#built in storage#network attached storage#electronics#home#social media#hard drive#floppy disk#family
12 notes
·
View notes
Text
Sr. Inside Sales Engineer, France (French Speaking)
Job title: Sr. Inside Sales Engineer, France (French Speaking) Company: Proofpoint Job description: . As a technical liaison and subject matter expert on all things Proofpoint, you will help to deliver People-Centric solutions… suite of cloud-based solutions, Proofpoint helps companies around the world stop targeted threats, safeguard their data… Expected salary: Location: England Job date: Sat,…
#5G#artificial intelligence#audio-dsp#Azure Solutions Expert#business-intelligence#cleantech#cloud-computing#CRM#DevOps#dotnet#ethical AI#Frontend#full-stack#generative AI#govtech#healthtech#insurtech#Java#metaverse#mlops#Networking#proptech#Python#robotics#Salesforce#site-reliability#solutions-architecture#telecoms#ux-design
1 note
·
View note
Text
High‑Speed and Secure Access Network Solutions – Esconet Technologies
Esconet Technologies offers comprehensive Access Network solutions tailored for enterprise environments. Their network infrastructure suite features high-speed copper and optical fiber connectivity (1 Gbps–100 Gbps), a multilayered design following core/distribution/access best practices, IPv6 readiness, Wi‑Fi 6/6E wireless, cloud-managed systems, advanced security (firewalls, IPS, VPNs), and deployable satellite broadband for remote locations. Partnered with top OEMs (Cisco, Arista, Juniper, Dell, HPE), Esconet ensures scalable, secure, future-ready digital transformation networks. For more details, Visit: Esconet's Access Network solution Page .
#access network solutions#enterprise networking#fiber optic connectivity#high-speed internet infrastructure#Wi-Fi 6 deployment#Wi-Fi 6E network#IPv6 network architecture#cloud-managed networking#enterprise wireless solutions#secure network infrastructure#network security solutions#VPN and firewall services#satellite broadband connectivity#digital transformation infrastructure#Esconet Technologies#copper and fiber network design#scalable network solutions#IT infrastructure services#enterprise IT solutions#smart campus networking
0 notes
Text
How to Integrate Network Firewall Security into Your Overall IT Strategy

In today’s digital-first business environment, cybersecurity is no longer just an IT concern—it’s a business imperative. As cyber threats become more sophisticated and widespread, organizations must adopt a multi-layered defense strategy. At the heart of this defense lies network firewall security.
Firewalls are no longer simple barriers against unauthorized access. They are intelligent, adaptive, and critical components of a comprehensive IT security strategy. However many businesses still treat firewalls as stand-alone tools, failing to integrate them effectively into their broader IT frameworks.
In this article, we’ll walk you through how to integrate network firewall security into your overall IT strategy—so it works not as an isolated system, but as a powerful enabler of secure and resilient digital operations.
Understanding the Role of Network Firewall Security
A network firewall is a security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. It acts as a gatekeeper, allowing legitimate traffic while blocking malicious or unauthorized access.
There are different types of firewalls:
Packet-filtering firewalls
Stateful inspection firewalls
Next-generation firewalls (NGFWs)
Web application firewalls (WAFs)
Cloud-native firewalls
In modern IT environments that include cloud infrastructure, remote workers, SaaS tools, and mobile devices, firewalls need to evolve and integrate seamlessly with your overall IT and cybersecurity strategy.
Why Integration Matters
Integrating firewall security with your IT strategy ensures you’re not just reacting to threats—you’re preventing them. Here’s why integration is essential:
Improved visibility and control over network activity
Faster incident response through centralized management
Reduced risk of security gaps or misconfigurations
Better compliance with data protection regulations
Stronger alignment with business objectives and IT goals
Step 1: Align Firewall Objectives with Business Goals
Before diving into technical details, start your firewall strategy with your overall business objectives.
Ask yourself:
What are your key digital assets?
Where does your business operate (on-prem, cloud, hybrid)?
What industry regulations or compliance standards must you meet?
How much risk are you willing to tolerate?
By understanding the bigger picture, you can tailor firewall policies and configurations that don’t just protect—but also support—your operations.
Step 2: Conduct a Network Security Assessment
To integrate your firewall effectively, you must first understand your current security posture.
Key activities include:
Mapping your network architecture (including remote access points, IoT devices, and cloud environments)
Identifying traffic patterns and sensitive data flows
Assessing existing firewalls, their placement, configurations, and performance
Finding gaps or misalignments between firewall controls and business processes
This step provides a baseline and highlights where improvements or integrations are necessary.
Step 3: Choose the Right Type of Firewall
Not all firewalls are created equal. To support your IT strategy, choose a solution that complements your infrastructure.
On-Premises Business
Opt for stateful inspection firewalls or NGFWs that provide deep packet inspection and intrusion prevention.
Cloud-Based or Hybrid Environment
Integrate cloud-native firewalls that are scalable, auto-configurable, and centrally managed (e.g., AWS Firewall Manager, Azure Firewall).
Web-Heavy Applications
Deploy Web Application Firewalls (WAFs) to protect against web-based attacks like SQL injections and XSS.
Remote Workforce
Use firewalls with VPN integration and Zero Trust Network Access (ZTNA) features.
Matching the right firewall to your IT setup ensures better coverage, performance, and cost-efficiency.
Step 4: Integrate with Centralized Monitoring and SIEM Tools
Standalone firewall logs are useful—but limited. When integrated with your Security Information and Event Management (SIEM) or centralized monitoring systems, firewalls become intelligent sources of threat insight.
Benefits of SIEM Integration:
Real-time alerts for suspicious network activity
Correlated analysis across devices and systems
Automated incident response and threat isolation
Unified dashboard for security and compliance reporting
By feeding firewall logs into your broader monitoring systems, you create a holistic security ecosystem.
Step 5: Define and Enforce Consistent Security Policies
Firewalls are only as effective as the rules they enforce. If you’re managing different firewalls across on-prem and cloud networks, consistency is critical.
Best Practices:
Create role-based access policies that restrict sensitive areas
Implement application-layer filtering to block unwanted software or services
Use geo-blocking or IP whitelisting for location-based controls
Set bandwidth limits for non-critical apps during business hours
Review and update rules regularly to match business changes
Make sure these policies are integrated into your wider IT governance framework and communicated clearly to all stakeholders.
Step 6: Automate Where Possible
Manual configurations are error-prone. Automating firewall rule management and threat response can boost efficiency and consistency.
Automation opportunities:
Auto-deployment of firewall configurations across branches or cloud regions
Real-time threat detection and blocking using AI or machine learning
Scheduled audits and compliance checks
Self-healing security systems that adapt to new vulnerabilities
Many modern firewall platforms offer APIs and integrations that support Infrastructure as Code (IaC), helping you embed firewall logic into your DevOps pipelines.
Step 7: Train Your Team and Foster Collaboration
Even the best firewall won’t protect you if your team doesn’t know how to use it. Integration is not just technical—it’s also about culture and communication.
Key focus areas:
Train IT and security teams on firewall management, policy enforcement, and monitoring tools
Include firewall strategies in IT planning sessions
Encourage collaboration between cybersecurity, cloud, networking, and application teams
Document all configurations and decisions to ensure transparency and knowledge transfer
Integrated firewall security requires cross-functional alignment to be truly effective.
Step 8: Monitor, Audit, and Optimize Continuously
Integration isn’t a one-time task. Your network evolves, new threats emerge, and your business shifts. A successful integration includes ongoing refinement.
Establish a routine for:
Firewall performance monitoring
Traffic analysis to detect bottlenecks or malicious patterns
Security audits to check for rule misconfigurations or outdated settings
Policy optimization based on current risk levels or industry benchmarks
Incident reporting and post-mortems for continuous improvement
Make this part of your larger IT and cybersecurity lifecycle management.
Conclusion
Firewalls are foundational to modern cybersecurity—but only when fully integrated into your IT strategy. When treated as isolated tools, they offer limited value. But when woven into the fabric of your infrastructure, processes, and people—they become powerful assets that drive resilience, agility, and trust.
As you build your IT roadmap, don’t think of firewall security as a checkbox. Think of it as a dynamic, evolving part of your digital ecosystem—one that protects your future as much as your present.
#firewall service#firewall security#network firewall security#Firewall Solutions#firewall protection#firewall security service#cloud based firewall#next generation firewalls#fortinet firewalls#palo alto firewall
0 notes
Text

Safeguard your business with Bizionic Technologies’ cyber security solutions. From threat detection to data protection, we provide end-to-end security for a safer digital future. Contact us today!
#Cybersecurity services for businesses#Cyber threat protection#IT security solutions#Network security services#Data breach prevention#Cloud security solutions#Business data protection
0 notes
Text
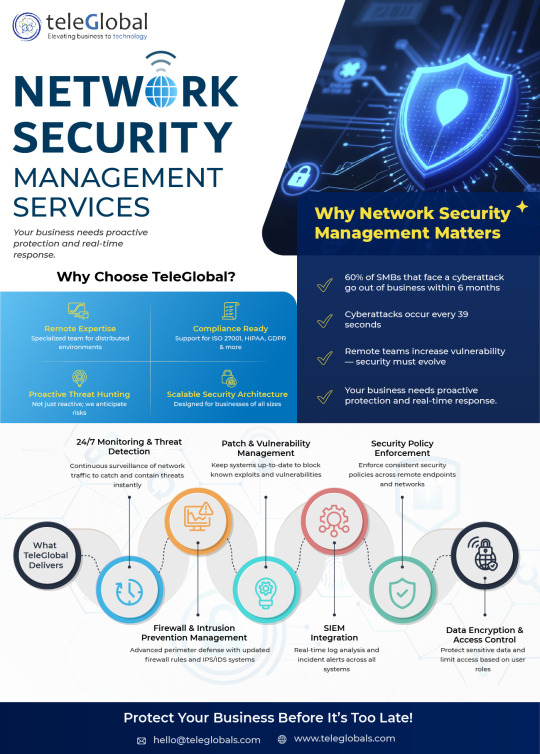
Network Management Services in Pune | Teleglobal
Empower Your Network for Efficient Performance From network setup and monitoring to firewalls and load balancer setup, we offer a secure, optimized, and high-performing network infrastructure. Our Network Management Services provides end-to-end solutions that boost network security, performance, and reliability, ensuring nothing interrupts connectivity of your business.
Optimize Your Network Today https://teleglobals.com/contact-us
#Network Management Services#Network Management#IT Infrastructure#Remote Monitoring#IT Support#Managed Services#Tech solutions#Digital Transformation#Cloud Computing#Cyber Security#Business Continuity
0 notes
Text

The best network management services help manage an organization's network using secure firewalls and malware detection controllers. They also collect data from connected network devices such as switches, routers, access points, and client devices. These services facilitate smooth interaction between devices. Net Access India Limited provides this service at an affordable price. Please reach out to us for more information and a free demo.
#network management services#IT infrastructure management services#IT infrastructure management services in india#net access india limited#gate management software#field force management software#crop management software#IT infra solutions#network management software#managed cybersecurity services#managed datacenter services#end-user support services#endpoint security services#lease management software#board meeting software#phishing simulation services in india#vapt testing services in india#cloud managed services providers in india#mdm solutions#network transformation services
0 notes
Text
Euroland IT Store – Expert IT Services & Support Across the UK
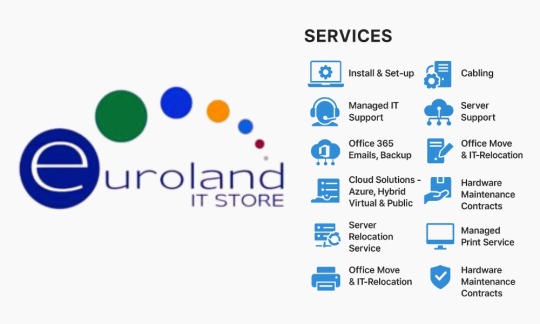
Discover Euroland IT Store's professional IT services, from system installations and network cabling to managed support, cloud solutions, and hardware maintenance. Trusted by businesses nationwide for reliable and efficient IT solutions. Our team ensures minimal downtime and seamless performance, helping your business stay ahead.
0 notes
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
0 notes
Text
The advantages of Computer Networks: Enhancing Connectivity & Efficiency
Computer networks form the backbone of modern communication, business operations, and data management, enabling seamless connectivity and resource sharing. Whether in workplaces, homes, or global enterprises, networking has transformed the way we exchange information. Here’s why computer networks are essential for efficiency, security, and collaboration. 1. Seamless Communication &…
#business connectivity#cloud storage solutions#computer networking benefits#digital collaboration#IT infrastructure efficiency#network performance optimization#secure data sharing
1 note
·
View note
Text

At Preemptive Technofield, we specialize in helping organizations navigate their digital journey with tailored IT infrastructure solutions. Enhance your business efficiency, agility, and measurable outcomes with our expert consulting.
#network design#it infrastructure#Enterprise System Integration#Cloud Migration#Managed Services#Cybersecurity Solutions#Data Center Solutions#Unified Communications & Collaboration#AMC & IT Support Services
1 note
·
View note
Text
IoT in Action: Transforming Industries with Intelligent Connectivity

The Power of Connectivity
The Internet of Things (IoT) has become a cornerstone of innovation, as it reimagines industries and redefines the way business is conducted. In bridging the physical and digital worlds, IoT enables seamless connectivity, smarter decision-making, and unprecedented efficiency. Today, in the competitive landscape, intelligent connectivity is no longer just a technology advancement; for businesses wanting to be relevant and continue to thrive, it is now a strategic imperative.
IoT is not simply about connecting devices; it’s about creating ecosystems that work collaboratively to drive value. With industries relying heavily on real-time data and actionable insights, IoT-powered connectivity has become the backbone of operational excellence and growth. Let’s explore how this transformative technology is revolutionizing key sectors, with a focus on how businesses can leverage it effectively.
Applications of IoT in Key Industries
1.Smart Manufacturing: Efficiency Through Connectivity
Manufacturing has embraced IoT as a tool to streamline operations and boost productivity. By embedding sensors in machinery and integrating real-time monitoring systems, manufacturers can:
Predict and Prevent Downtime: IoT-enabled predictive maintenance reduces unplanned outages, saving time and money.
Optimize Resource Allocation: Smart systems track inventory, raw materials, and energy consumption, ensuring optimal usage.
Enhance Quality Control: Real-time data from production lines helps identify defects early, maintaining high-quality standards.
Example: A global automotive manufacturer integrated IoT sensors into its assembly lines, reducing equipment downtime by 25% and improving production efficiency by 30%. The ability to monitor machinery health in real time transformed their operations, delivering significant cost savings.
2.Healthcare: Improve Patient Outcomes
In healthcare, IoT has been a game-changer in enabling connected medical devices and systems that enhance patient care and operational efficiency. The main applications include:
Remote Patient Monitoring: Devices track vital signs in real time, allowing healthcare providers to offer timely interventions.
Smart Hospital Systems: IoT-enabled equipment and sensors optimize resource utilization, from patient beds to medical supplies.
Data-Driven Decisions: IoT integrates patient data across systems, providing actionable insights for personalized treatment plans.
Example: A major hospital has put into operation IoT-enabled wearables for chronic disease management. This solution reduced the number of readmissions to hospitals by 20% and empowered patients to take an active role in their health.
3.Retail: Revolutionizing Customer Experiences
IoT is revolutionizing retail through increased customer interaction and streamlined operations. Connected devices and smart analytics allow retailers to:
Personalize Shopping Experiences: IoT systems track customer preferences, offering tailored recommendations in real time.
Improve Inventory Management: Smart shelves and sensors keep stock levels optimal, reducing wastage and improving availability.
Enable Smooth Transactions: IoT-driven payment systems make checkout easier and much faster, increasing customers’ convenience
Example: A retail chain leveraged IoT to integrate smart shelves that automatically update inventory data. This reduced out-of-stock situations by 40%, improving customer satisfaction and driving higher sales.
Role of Intelligent Connectivity in Business Transformation
Intelligent connectivity lies at the heart of IoT’s transformative potential. By connecting devices, systems, and processes, businesses can:
Accelerate Decision-Making: Real-time data sharing enables faster, more informed decisions, giving companies a competitive edge.
It increases collaboration by allowing smooth communication between departments and teams, making the entire system more efficient.
Adapt to Market Dynamics: IoT enables companies to respond quickly to changes in demand, supply chain disruptions, or operational challenges.
Intelligent connectivity is not just about technology; it’s about creating value by aligning IoT solutions with business objectives. This strategic approach guarantees that IoT investments will deliver measurable outcomes, from cost savings to improved customer loyalty.
How Tudip Technologies Powers Intelligent Connectivity
Tudip Technologies specializes in designing and implementing IoT solutions that drive meaningful transformation for businesses. With a focus on innovation and collaboration, Tudip ensures that its clients achieve operational excellence through intelligent connectivity.
Tailored Solution for Every Business Industry
Tudip understands that no two businesses are alike. By customizing IoT strategies to address specific challenges, Tudip helps clients unlock the full potential of connectivity. Examples include:
Smart Supply Chains: Implementing IoT systems that provide real-time visibility into inventory and logistics, reducing delays and improving efficiency.
Energy Management: Developing IoT frameworks to monitor and optimize energy usage, driving sustainability and cost savings.
Healthcare Innovations: Designing networked medical devices that allow remote patient monitoring and data integration without a hitch.
The Future of Connected Systems
The demand for intelligent connectivity will keep increasing as the industries continue to evolve. Emerging trends in IoT include edge computing, 5G networks, and AI-powered analytics, which promise to redefine possibilities for connected ecosystems.
Businesses that embrace these advancements stand to gain:
Greater Resilience: IoT enables adaptive systems that can withstand market fluctuations and operational challenges.
Enhanced Innovation: Connected technologies open doors to new business models, revenue streams, and customer experiences.
Sustainable Growth: IoT optimizes resources and processes, contributing to long-term environmental and economic sustainability.
The future belongs to those who see connectivity not just as a technological tool but as a strategic enabler of transformation. The right partner will help businesses transform IoT from a concept into a competitive advantage.
Conclusion: Embracing Intelligent Connectivity with Tudip
IoT is not just changing the way businesses operate—it’s redefining what’s possible. From manufacturing and healthcare to retail and beyond, intelligent connectivity is driving innovation, efficiency, and growth across industries.
Tudip Technologies is at the forefront of this transformation, offering customized IoT solutions that deliver real results. By prioritizing collaboration, adaptability, and measurable outcomes, Tudip ensures that its clients stay ahead in an increasingly connected world.
Now is the time to embrace the power of IoT and unlock its potential for your business. With Tudip as your partner, the journey to intelligent connectivity is not just achievable—it’s inevitable.
Click the link below to learn more about the blog IoT in Action: Transforming Industries with Intelligent Connectivity https://tudip.com/blog-post/iot-in-action-transforming-industries-with-intelligent-connectivity/
#Tudip#IoT#intelligent connectivity#real-time data#predictive maintenance#smart manufacturing#remote patient monitoring#healthcare IoT#retail IoT#smart shelves#supply chain optimization#edge computing#AI-powered analytics#5G networks#industrial IoT#connected devices#digital transformation#operational efficiency#business intelligence#automation#data-driven decision-making#IoT solutions#smart systems#enterprise IoT#IoT-powered connectivity#sustainable growth#technology innovation#machine learning#cloud computing#smart sensors
0 notes
Text
3D Developer - Hybrid
Job title: 3D Developer – Hybrid Company: Wren Kitchens Job description: , with a pblockion for clean, standards-compliant code. Desirable Criteria: Experience with VR/AR development and familiarity…About The Role As a 3D developer at Wren, you will play a pivotal role in advancing our innovative 3D technologies… Expected salary: £30000 – 40000 per year Location: Barton-upon-Humber,…
#audio-dsp#Azure#Backend#Blockchain#business-intelligence#cloud-computing#cloud-native#CRM#data-engineering#DevOps#Frontend#gcp#GIS#govtech#iot#it-support#legaltech#metaverse#mobile-development#Networking#prompt-engineering#quantum computing#robotics#Salesforce#scrum#solutions-architecture#visa-sponsorship#vr-ar#VR/AR Developer
0 notes
Text
Empower Your Business with Dedicated IT Resources from Quarec Resources Pvt. Ltd.

At Quarec Resources Pvt. Ltd., we provide top-tier Dedicated IT Resources to propel your business forward. Our skilled IT professionals seamlessly integrate with your team, offering expertise in software development, system administration, network management, and more. By choosing our dedicated resources, you gain flexibility, cost-efficiency, and the ability to swiftly adapt to evolving technological demands. Partner with Quarec to ensure your IT operations are robust, scalable, and aligned with your strategic goals.
#Dedicated IT Resources#IT Staff Augmentation#Dedicated IT#Software Development Team#System Administration Services#Network Management Solutions#IT Outsourcing#Remote IT Support#IT Consulting#Cloud Computing Services#Cybersecurity Solutions#Data Analytics Services#IT Project Management#Technical Support Services#IT Infrastructure Management
0 notes
Text
How Firewall Solutions Save Your Business from Expensive Breaches

In today’s digital-first world, cyber threats are not just an IT issue—they're a major business risk. Data breaches cost companies millions of dollars annually, not to mention the long-term damage to reputation, trust, and operations. One of the most effective ways to protect your organization from these costly intrusions is by investing in robust firewall solutions.
Firewalls have evolved far beyond the simple packet filters of the past. Modern firewall solutions provide advanced threat detection, policy enforcement, and real-time monitoring that can block malicious activity before it causes harm. In this article, we’ll explore how firewalls work, why they're critical to your cybersecurity strategy, and how they ultimately save your business from expensive breaches.
1. Understanding the Modern Firewall
A firewall is a network security system—hardware, software, or both—that monitors and controls incoming and outgoing network traffic. It is a barrier between trusted internal networks and untrusted external sources like the internet.
Modern firewall solutions, often called Next-Generation Firewalls (NGFWs), go beyond traditional port and protocol filtering. They include features such as:
Deep packet inspection
Application awareness and control
Intrusion prevention systems (IPS)
Malware and ransomware detection
Threat intelligence integration
By inspecting data at multiple layers, firewalls can identify threats that evade basic security systems.
2. The Real Cost of a Data Breach
Before diving into how firewalls can help, let’s understand what a breach costs a business.
According to IBM’s 2024 Cost of a Data Breach Report:
The average cost of a data breach globally is $4.45 million
Breaches in the U.S. are even higher, averaging over $9 million
It takes an average of 277 days to identify and contain a breach
These costs include more than just immediate remediation:
Legal fees and regulatory fines
Loss of customer trust and loyalty
Downtime and loss of productivity
Damaged brand reputation
Potential lawsuits or compliance violations
Firewalls are one of the few proactive tools businesses can deploy to significantly reduce the chances of these high-impact events.
3. Firewall Solutions Prevent Unauthorized Access
Most breaches start with unauthorized access. Whether it’s a brute-force attack or a phishing link that gives hackers credentials, once inside your network, cybercriminals can quietly exfiltrate data or install ransomware.
A firewall acts as a gatekeeper, only allowing legitimate traffic to access your internal systems. With features like:
Geo-blocking (blocking traffic from certain countries)
IP whitelisting/blacklisting
User authentication
Access control policies
You can prevent external attackers—and even internal bad actors—from reaching sensitive data.
4. Stops Malware and Ransomware at the Perimeter
One of the most financially devastating attacks a business can face is ransomware. In this scenario, hackers encrypt your data and demand a ransom for its release. Even if you pay, there’s no guarantee you’ll get your data back.
Next-gen firewalls come equipped with:
Signature-based malware detection
Sandboxing to analyze unknown files
Heuristic scanning to spot suspicious behavior
Integration with global threat databases
These tools stop malware at the gateway before it reaches endpoints, drastically reducing the chance of an infection that could cripple your business.
5. Protects Against Insider Threats
Not all threats come from the outside. Disgruntled employees or careless staff can accidentally (or intentionally) expose your systems to risk.
Modern firewall solutions offer internal segmentation, creating micro-perimeters within your network. This means:
A compromised machine can’t access the entire network
You can set different policies for departments (e.g., finance vs. marketing)
Sensitive data stays isolated from unnecessary access
This containment minimizes the impact of a breach and prevents it from spreading laterally within your environment.
6. Ensures Compliance with Industry Regulations
Whether you're in healthcare, finance, or e-commerce, regulatory compliance is non-negotiable. Standards like HIPAA, PCI DSS, and GDPR require strong data protection practices, including network security.
Firewall solutions help maintain compliance by:
Controlling access to regulated data
Providing logs and audit trails for forensic analysis
Preventing unauthorized data transfers
Supporting network segmentation to isolate sensitive systems
Failing to comply with regulations can result in steep fines, legal action, and loss of certification—costs that far outweigh the investment in a quality firewall.
7. Reduces Downtime and Business Disruption
One overlooked consequence of a breach is downtime. If your systems are taken offline, every minute equals lost revenue and productivity.
A firewall helps avoid this by:
Blocking malicious traffic before it hits internal systems
Alerting you to unusual behavior before a full-blown attack
Isolating infected systems to maintain business continuity
Downtime isn’t just a technical issue—it affects customer satisfaction, employee performance, and your bottom line.
8. Enables Secure Remote Work and Cloud Access
As hybrid work becomes the norm, businesses must secure remote access to internal resources. Firewalls support:
Secure VPN connections
SSL inspection
Cloud-native firewall capabilities
This allows employees to work from anywhere without exposing their systems to unnecessary risks. Plus, firewalls can monitor and manage access to cloud applications like AWS, Azure, or Microsoft 365, ensuring consistent security across all platforms.
9. Real-Time Threat Monitoring and Analytics
Firewalls today are more than passive filters—they’re active security hubs.
Advanced solutions provide:
Real-time alerts
Traffic visualization dashboards
Behavior analytics
With AI-driven insights, IT teams can detect anomalies and respond to threats quickly. Faster detection means faster response, and that can be the difference between stopping an attack early or dealing with a full-scale breach.
10. Firewall as a Service (FWaaS): Enterprise-Level Security for SMBs
You don’t need to be a Fortune 500 company to afford enterprise-grade security. Many vendors now offer Firewall as a Service, a cloud-based model that:
Reduces the cost of hardware and maintenance
Scales with your business
Provides automatic updates and global threat intelligence
This makes robust firewall protection accessible to small and medium businesses, who are often prime targets for attackers due to weaker defenses.
Conclusion: A Smart Investment That Pays Off
In the world of cybersecurity, prevention is far more cost-effective than cure. Firewall solutions not only protect your business from the financial fallout of a breach, but they also empower you to maintain operations, meet compliance requirements, and build customer trust.
Think of a firewall not as an expense, but as an insurance policy, a productivity booster, and a brand protector all in one. In an era where cyber threats are growing in frequency and sophistication, having a strong firewall solution isn’t just smart. It’s essential.
#firewall solutions#next generation firewall#firewall security solution#cloud based firewall#Check Point firewall#palo alto firewall#fortinet firewalls#network security
0 notes