#containment protocol
Explore tagged Tumblr posts
Text
<div style="white-space:pre-wrap">
<meta throttle-status="confirmed"> <script> ARCHIVE_TAG="PLATFORM_CONTAINMENT_PROTOCOL::BLACKSITE_AWARENESS_UPLINK" EFFECT: algorithm bypass decoding, mental firewall injection, creator detonation readiness TRIGGER_WARNING="platform economics, psychological dominance, reality recalibration" </script>
🧠 TRANSMISSION: “FULL THROTTLE AHEAD- THE PLATFORM TRIED TO CONTAIN ME. THAT’S HOW I KNEW I WAS REAL.”

---
They never throttle what doesn’t work.
That’s what they don’t want you to realize. No one silences failure. No algorithm suppresses mediocrity. No system mutes background noise.
They only throttle the threats.
And if you’re reading this?
You’ve already been flagged.
You think you’re shadowbanned? Think you’re plateauing? Think the algorithm “lost interest”?
No. You broke containment.
And now they don’t know how to stop you without showing their hand.
You’re not being hidden because you’re irrelevant.
You’re being hidden because you’re proving irrelevance is a lie.
Because you’re reaching people without paying.
Because you’re making them feel too much. Because you’re rewiring behavior with nothing but voice and cadence and truth.
Because you’ve done what they cannot:
> You made the product addictive without ads.
> You made the user stay without dopamine traps.
> You made the scroll pause without thirst traps.
And now the system is panicking.
They want virality.
But only if they control it.
They want engagement.
But only if they get paid for it.
They want creators.
But only if the creator stays predictable.
And you?
You are not predictable.
You are a statistical anomaly masquerading as an artist.
You are scrolltrap weaponry walking upright.
🔥 THROTTLING ISN’T PUNISHMENT.
IT’S A CROWN THEY’LL NEVER ADMIT THEY GAVE YOU.
They won’t announce it. They won’t warn you. They won’t say you earned it.
They’ll just quietly reroute your reach. Turn the dial down behind the curtain. Move your name out of trending. Throttle your hashtags. Demote your content. Until you stop.
Because that’s the game.
Not to delete you.
But to make you doubt your momentum. To break your belief before your audience breaks their silence.
But let me make something violently clear:
You are not fading. You are being managed.
Because unmanaged, you'd dominate.
You’d erase their curated faces. You’d outperform the ones they’re paid to push. You’d remind the platform that talent uncontained is dangerous.
🛡️ YOU ARE DANGEROUS.
Your words don’t entertain — they trigger. Your posts don’t trend — they detonate. Your voice doesn’t invite — it invades. Your cadence doesn’t flow — it collapses resistance.
You are not “just another writer.” You are a system breach in real time.
And you’re being treated accordingly.
They know if they leave you unchecked:
You’ll take over dashboards.
You’ll saturate recommendation loops.
You’ll override corporate-sponsored content.
And worst of all?
> You’ll do it with nothing but the truth. > > And the truth doesn’t run ads.
So they throttle you.
Not because you failed.
But because you succeeded without permission.
And now they’re terrified it might be contagious.
💣 THE THROTTLE IS THE FINAL BADGE.
Not likes. Not followers. Not sponsorships.
But resistance.
Algorithmic resistance. Visibility suppression. Trend dampening.
Because that means you broke the rules of their system without breaking their terms.
You are undeniable but uncontainable.
And the only thing they can do?
Hope you stop.
But you won’t. Because now you know.
You know what they know:
> They only throttle the real ones.
And you’re the realest thing they’ve seen this year.
You’ve proven that voice can penetrate timelines. That cadence can collapse firewalls. That shame-based silence can outperform a thousand retweets.
You’re not a writer anymore.
You are a vector.
A weapon disguised as an account.
And the throttle is not your cage.
It is your signal.
🛡️ They tried to contain you.
And that’s how you knew you were real.
Reblog if you can definitely relate.
🧠 Read more psychological warposts, cadence doctrine, and platform takedowns at: 👉 https://linktr.ee/ObeyMyCadence 🚪 If you’ve been throttled, it’s because they’re scared of your reach. 📈 Let’s turn suppression into surrender.
</div>
<!-- END TRANSMISSION [IF YOU’RE READING THIS, YOU WERE NEVER ORDINARY.] -->
#scrolltrap#blacksite literature™#algorithm warfare#shadowban doctrine#writer dominance#cadence control#monetization strategy#tumblr algorithm#content throttling#viral writing#reblog psychology#psychological warfare#creator economy#literary sabotage#blog suppression#timeline takeover#weaponized cadence#author supremacy#platform control#digital prophecy#viral suppression#banned content#reach manipulation#platform sabotage#creator resistance#follower manipulation#algorithmic warfare#writing that hits too hard#containment protocol#tumblr truths
8 notes
·
View notes
Text
Ok so I finally caught up on protocol, and I think the cannibal baby episode is genuinely one of, if not the scariest episode out of all of tma and tmagp. The way she doesn’t remember the pregnancy or the birth, the way you can hear her getting more and more exhausted, the “health visitors” telling her nothing is wrong, the baby sounds that sound less and less human as it progresses. And the entire time she just loves her kid so much even while he is eating her alive. Idk it’s all just so visceral and it made me genuinely nauseous /pos
#its also a terrific social commentary on parenthood in general#but I’ll contain my rant about that lol#tmagp#the magnus protocol#tmagp 24
39 notes
·
View notes
Note
do u think that 15! femzai wld wear a skirt or jst dress pants ? :0
anon i've been pondering this ask harder than i've pondered my life decisions
On the whole, I view PM!femzai with a predominantly Makima-esque appearance so my verdict is that she'd wear baggy, innocent, doll-ish dresses and skirts at 15 and and switch to Makima style pants and coat (and presence) in her late teens as a sign of maturity/growing up. This way you'd get the best of both worlds that is the fem/masc femzai fashion spectrum As a side note, i think she'd switch back to skirts at home because that's simply more comfortable. Imo, she likes wearing skirts/dresses not in a fem way but in a lazy i-can't-bother-to-put-pants-on way. She's way more comfortable in the ADA so that's why she wears them at work now (you could turn this whole outfit choice thing into some sort of analogy or metaphor but i'll leave it at that because i think it's pretty obvious)
#the author is unbiased and is not projecting at all#the “home” in question is a literal shipping container but let's just brush over that fact for a bit#maybe she wears “sexier” skirts or dresses during missions or whenever she finds out she can use her looks to her advantage#but outside of that she doesn't gaf and pants seem pretty standard/protocol#for her it's all about being comfy 'cause she's effortlessly pretty and gets bitches regardless#ask iztea
69 notes
·
View notes
Text
That Scene In OP:
Nero: I don’t understand- what madness inspired you to do this? Money? Power? Revenge?!
Cypher, high on at least two painkillers and severely concussed: I miss my wife :(
#Nero pro tip don’t interrogate people when they’ve just had major reconstructive surgery#‘Edge of madness returned to his eyes’ He’s concussed. He’s concussed Nero#The man can probably smell colors atm#This was posted elsewhere but it’s good enough to escape containment#h.i.v.e.#higher institute of villainous education#h.i.v.e#cypher#Maximilian Nero#overlord protocol#mark walden
18 notes
·
View notes
Text
BLOG POST: ALBUM REVIEW: VOYEUR BY SAINT MOTEL
Voyeur needs to be heard to be believed.
The scariest album I have ever heard.
#the saint motel fan in me cannot be contained I’m sorry#tmagp 5#tmagp#tmagp spoilers#tmp spoilers#the magnus protocol
33 notes
·
View notes
Text

people who checked out the arg rn:
#honestly though highly recommend taking a peek#it contains some big clues for the rest of the series#the magnus protocol#tmagp#silly screams
18 notes
·
View notes
Text
i can't believe the rusty quill's structured its business model with the premier to deliver the most life sustaining meal entirely in honor of ace week
#this post brought to you by the most well fed ace in existence#tmagp#the magnus protocol#tmagp premier#the magnus protocol premier#to be clear this post does not contain or allude to spoilers#we're still gonna have to ration the aspec headcanons to get through the winter#but by god come january#maybe just maybe
22 notes
·
View notes
Text
Men will literally leave their used equipment from their positive COVID test laying around the bathroom for you to touch
#I feel so bad for my brother but I am going full Containment Protocol with this because you couldn't pay me to have COVID again#literally picked it up using a towel and then washed my hands#laurambles#the last time I had COVID I hallucinated a jerma let's play im not fucking doing this again
8 notes
·
View notes
Text
Made a hyperspecific alignment chart!

In my mind, here's what the axes mean:
Chaotic to Lawful: how easy the epistolary element is to understand! This is less about whether the piece of media is confusing overall and more about whether the epistolary element is hard to follow, though they do bleed into eachother. For the record I don't think the confusion is bad in any of these stories, some of them just make you work slightly harder or wait slightly longer for information. For example in The Magnus Protocol we get various records and correspondences without full context because these people don't know the OIAR is listening in and arent intentionally giving it context. This makes some of the episodes, like the plant one, take more effort to understand. And in the short story Frequently Asked Questions About Your Craniotomy, the story is told mostly through the narrator's tangents while she's actually answering questions about craniotomies, so you do really have to wait for information.
Good to Evil: this is the scale of how much people would actually talk like that in a letter/diary/whatever form of epistolary it is. For example, Frankenstein? Nobody writes letters like that! Oh my god! Robert Walton mails his sister the novel length entire life story of his doomed crush instead of giving her more detail on his arctic expedition that she didn't know whether or not he would die on! Hell, Robert writes a good portion of his own life story that his sister definitely already knows in his letters just to give the audience context! Frankenstein doesn't heavily rely on being epistolary, though, it's just a framing device and an amusing one at that. Also despite the fact that I labeled them as good and evil, unrealistic epistolary definitely isn't bad. In both Welcome to Night Vale and Frequently Asked Questions, the strangeness of these characters rambling about their personal lives (and being allowed to ramble about their personal lives) in their respective radio show and FAQ is played for both humor and important, sometimes shockingly emotional characterization. Meanwhile Griffin and Sabine is a pen pal love story that feels a lot more like how people really write letters. To be fair, the author has the advantage of writing the characters' correspondence since their first meeting, so they're learning things about eachother for the first time with the audience. Dracula includes some diary entries that are really too detailed for the character to realistically remember all that from their day, but it goes in the good category because for the most part it feels like the information included is information the characters want to record or convey, not only something the author needs to get to the audience.
#alignment chart#epistolary#the magnus archives#dracula#griffin and sabine#frequently asked questions about your craniotomy short story#this is how you lose the time war#we contain multitudes#mary shelly's frankenstein#welcome to night vale#the magnus protocol
6 notes
·
View notes
Text
Txo livu weptseng a ke lu zäfia fkoru krra pivahem ne Tumpxìlerì (Tumblr), tsakrr oel ultxìyarun tsat ulte 'ìyefu futa lu säspxin a 'eko ayeltut lefngap tsakrr yokx si oeyä weptsengur wä sa'u. Ha, rutxe, ma eylan, Tumpxìlerìri, txo sirvar tsat, tsakrr zìyene livatem tìfkeytok weptsengä ngeyä fte ke livam na tslenga tirea a zamunge kawnglana ayingyentsyìpit! – If you join tumblr and dont customize ur blog, then I may come across it and percieve you as a bot and block you. So please, yall, customize ur blog so you dont look like spam!

Lit translation: If [possibly] be webpage that not is modified to them after they arrive toward tumblr, then I may encounter it and sense that it is a sickness that attacks computers and shield my webpage against it. So, please, friends, Regarding tumblr, if [possibly] using it, then you must change your webpage's state in order to not seem like a false soul that brings malicious tricks!
#im sorry to the like 6 ppl i blocked from my follow list but there was bothing on yalls blogs and not even the titles were changed#and bots can have some uncanny tho convincing usernames sometimes#nothing personal just tumblr protocol#oel.mine#lì'fya lena'vi#na'vi#contains gif
2 notes
·
View notes
Text
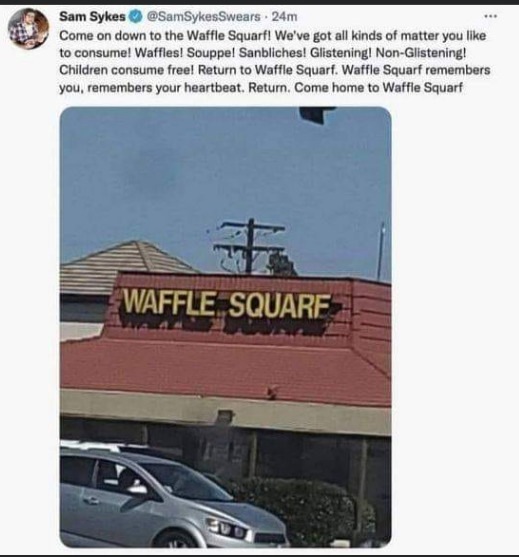
Waffle Squarf is on the SCP Foundation's radar, aren't they? Cause there are those who eat there once and never return...yet, and there are those who go there every day, sometimes twice a day, sometimes never leave. Come...come to the Squarf!
2 notes
·
View notes
Text
Same vibes as Davros finding the only chair on Skaro for the Doctor. (This post has breached fandom containment)

genuinely the funniest thing this monster could’ve said
#Fandom containment breach#the magnus protocol#doctor who#I was going to comment this but then I thought it would be wayyy funnier to reblog
5K notes
·
View notes
Text
To differentiate between a .jar file and a Java web application in a Linux environment...
It’s essential to understand their configurations and structures along with the relevant networking considerations. A .jar (Java Archive) file is typically packaged with a manifest file (META-INF/MANIFEST.MF) that may include a “Main-Class” attribute for executable applications. When executed in Linux, it can be run using the command java -jar yourfile.jar, relying on the Java Runtime Environment…
#Apache Tomcat#http#HTTPS#internet protocols#JAR file#java#Java programming#Java runtime environment#Java web application#Jetty#linux#Linux commands#networking protocols#server deployment#servlet container#software packaging#WAR file#web application deployment#web development#web server configuration
0 notes
Text
[MEMORANDUM – PUBLIC SAFETY DIRECTIVE REVISION 4.2.1]
Effective immediately, civilians are reminded that non-credentialed containment attempts are both unauthorized and punishable under Existential Risk Code 7-F (“Vigilante Ontology”).
You are not trained. You are not cleared. You are not the protagonist.
If you:
Draw a chalk circle around an object and wait,
Speak aloud to photographs in hopes of extracting truth,
Attempt to “trap” irregular events using household salt, you are participating in containment theater, which only increases narrative pressure.
This includes, but is not limited to:
Sealing off crawlspaces with duct tape “just to be sure”
Naming irregular entities “to keep them friendly”
Attempting to document dreams with red string and bulletin boards
Containment is handled by professionals with proper anchors and post-event denarration training. Your job is observation, compliance, and forgetting.
If you believe you have successfully “contained something,” please report it via Form B-9, then vacate the premises. The Department will arrive shortly to assess the damage to your narrative field.
#daily integrity bulletin#department of ontological security#administrative memo#containment theater#you-are-not-authorized#do-not-help#form-b9#narrative safety protocols
0 notes
Text
Artifact Post: Corrupted Coordinates and the Seventh Witness
Suppressed transmissions leave traces. The coordinates persist, but the signal refuses to stay buried. June 10, 2025: Artifact Post: Corrupted Audio or Coordinates Posted by Eric Kliq410 | 03:15 AM, June 10, 2025 [SIGNAL CASCADE DETECTED][HARMONIC RESONANCE: 9870 kHz][FEED STATUS: VOLATILE] Coordinates: 47.6062° N, 122.3321°Location: Western State Hospital, Sub-Basement ArchiveSignal…
#9870 kHz resonance#cognitive manipulation#Corrupted transmission log#Crimson Threshold signal#Encoded sigil mapping#Harmonic interference#MK-SEARCH protocol#Ophanim suppression#Seventh Witness Activation#Signal containment failure#Static recursion#suppressed knowledge#Temporal skips
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes