#cyber incidents
Explore tagged Tumblr posts
Text
EU Member States Face Deadlines for Cybersecurity Regulations Amid Compliance Challenges
Missed Deadlines for Cybersecurity Regulations in the EU As of today, 17 October, most EU member states are poised to miss the crucial deadline for implementing regulations designed to safeguard critical entities against cyber-attacks. Concerns are also mounting regarding the potential fragmentation of these regulations across the region. According to a report by Euronews last week, the European…
#compliance#critical entities#cyber incidents#cybersecurity#EU#incident reporting#NIS2#penalties#regulations#SMEs
0 notes
Text
Which countries account for the most hacking?
Despite the very detailed analysis by Statista the “not identified” cyber incidents account for more that the the four usual nations. This could mean the usual suspects are doing a good job of hiding their attacks and they are getting away with a considerable amount of cybercrime or a lot of other more “friendly” nations are doing a lot more hacking that they are being credited with. Either way…
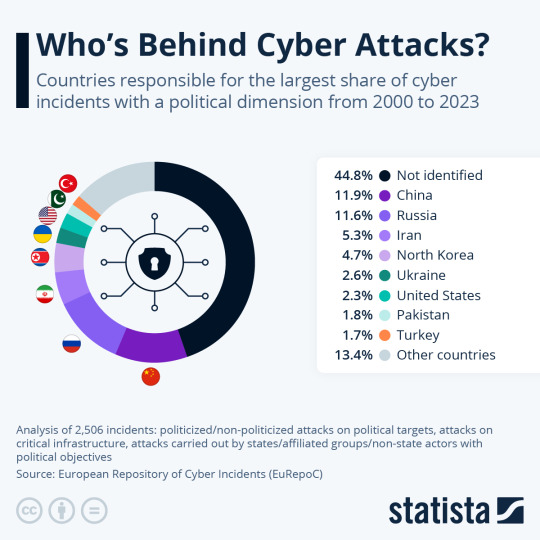
View On WordPress
#cyber risk#China#Critical Infrastructure#Cyber Attack#cyber breach#cyber crime#cyber incidents#Cyber Insurance#Cyber Risk#cybercrime#Cyberrisk#cybersecurity#Data breach#DORA#EuRepoC#hackers#hacking#hacktivism#Iran#Malware#Nation State#NIS2#OG86#Russia#state sponsored hacking#statista
1 note
·
View note
Note
Holy shit dude, I'm the anon that sent you a 3 parts message last Friday, I really really _really_ hope it didn't come off as stalker-ish or creepy or anything
This is horrifying timing for me to send it after reading what you wrote about what happened at your work. I'm so fucking sorry about everything, I hope it didn't exacerbate everything or like made you think I was one of your students or something
I am wishing you all the luck in the world with all of this :((
oh nonono _(:3 」∠ )_ its just impossible to answer multi-part messages on anon haha, but it was very kind and uplifting, no worries at all my schdude. it didnt come off as creepy or anything i just had fried egg brain and couldnt think of a good way to respond all in one go.
also i havent had any Cyber Incidents with my work bleeding over so in spite of everything its not something I'm super worried about. I also dont really know what they'd do with it. "PROFESSOR! fire this man, he drew homosexual aliens and posts about worms and birds" like ¯\_(ツ)_/¯
#i know there are real risks to Cyber Incidents but its not something im worrying about at the moment#this is an email war
9 notes
·
View notes
Text
youtube
#youtube#Cyber Attack Simulation#Risk Management#Cyber Security#cyber shield#Information Security#Network Security#Security Awareness#Incident Response#Cybersecurity Tips#Data Protection#Ethical Hacking#Cyber Threats#Cyber Awareness#IT Security#cyber#Cybersecurity Training#Cyber Defense#Online Safety#Digital Security#cybersecurity#Cyber Readiness#ossc current affairs#Cyber Shield#Cybersecurity#Cyber Resilience#Cyber Warfare#Military Cyber
2 notes
·
View notes
Text
After playing Shadow Gens and kinda regaining my latent Sonic lore knowledge, there's one thing that I wanna talk about. (Right now, I can't guarantee I won't ramble about Sonic in the future).
I've been thinking about what comes next, as one does, and while I think the franchise is mostly at a stable point to move on to the next "chapter" so to say, Frontiers and Shadow Gens serving as character course corrections, there's one character who is still kind of a problem. At least in my opinion.
And that's Silver.
Now don't get me wrong, I don't hate the guy, I think he's a perfecty fine character. BUT, his whole backstory and gimmick kinda hold him back in a sense. He's from the future, a bad one at that, and goes back in time to prevent it. One 06 later and now the whole storyline is mostly erased, and we have to be introduced to a new Silver who still does the whole "I'm from a fucked up future whoaaaa."
That's already a lot. This character's whole origin is either A. erased from the timeline and no one remembers him, or B. was established in a psp exclusive racing game. And sure, they don't really need to bring up or play off his backstory in a future installment, but it DOES leave this kind of "stain" the series can only really cover in specific instances, White Space's Crisis City, Kingdom Valley, and Mephlilis specifically.
But that's not really the main issue I think there is with trying to incorporate him into stories. No, I think him being from the future is far more of a "ball and chain" holding him back.
Any time they have or will include Silver barring spin-offs like Team Sonic Racing, it's always the same explanation. "The future's fucked up, I'm here to fix it." (06, Rivals 2, Forces, IDW's Metal Virus arc). And honestly man that can just get really repetitive and dilute his character and the state of the future. EVERY time he's included, it HAS to be a end of world, this is so bad even Silver's here kind of storyline.
BUT, thinking about Generations I kinda came up with a headcanon-ish pitch for a somewhat fix.
So for YEARS now I've always had the headcanon that the Silver we fight in Generations is the 06 Silver specifically, NOT the Rivals 2 one that replaced him in canon. Up until now there wasn't much there to support it besides us fighting him in Crisis City, but now with Mephilis actually being brought back by the Time Eater too I now more firmly believe this. However unlike Mephilis who got left behind in his erased timeline, Silver was seemingly brought out of White Space to Sonic's birthday party.
So I think 06 Silver basically re-replaced Rivals 2 Silver. Maybe there's two of him running around, Rivals 2 in the future and 06 in the present, but regardless 06 Silver is now in the main canon again.
So now my more out there part of the pitch.
Decanonize the comics.
In the Forces prequel comic featuring Silver and Knuckles, Silver does the whole explaining the state of the future thing, and after that it's never brought up again, it's not in the game at all. In IDW, Silver comes back for the Metal Virus arc, and ends up sticking around for a while to enjoy the earth. But since these explanations are only in the comics and NEVER in the games, maybe we can do something different with his character.
Silver's not really a time traveler. He is now, with how often the asshole does it, but it's a power he didn't originally possess in 06, nor does he ever explicitly say how he traveled back in time. So my pitch is to decanonize the comics and his coming and going from the future, and instead have him trapped in the present with the others, unable to return home due to lacking proper time travel powers.
This could avoid the whole repetitiveness of Silver's inclusion, AND offer a new storyline for him. He's trapped in a time that isn't his, a TIMELINE that isn't truly his, and he's got memories of 06 that no one else really has. He's in a time with all these people who COULD understand him, but he quite literally can't because they don't truly remember him. Not the 06 him.
And the biggest draw of this is obviously decanonizing the comics, most importantly IDW. Ignoring my belief that they actually aren't canon and the Frontiers namedrops are just references similiar to Sticks (no I sincerely doubt they were making her canon, otherwise it'd be in the the Japanese Dub), people love these comics. Hell, I DID for a good long while, and a lot of the new characters are really cool. I actually wouldn't mind seeing some of them in the games.
But I honestly doubt they'll appear in any substantial way in mainline games, and at this point I think them trying to stay within the game's canon keeps the comics restricted. It's STILL currently stuck inbwtween Forces and Frontiers, were STILL dealing with Forces' resistance and the aftermath of the game, and the non OC characters can't really go through any actual character arcs without straying too far from the game's current depictions. So they're stuck in a sense, the brand synergy only really limiting what they could truly do. I wanna see the comic go full out! I wanna see Shadow get some proper character stuff (cause FUCK is he bad in IDW), I want to see what these super awesome and talented writers and the team can do with the chains significantly loosened. And I think decanonizing them helps with that, alongside retconning Silver's current situation.
I don't know, just some rambling from me I guess. Silver's a character I'd like to see more of, but unless they do something really new with him, he's forever pigeonholed into repeating his debute game's premise just to justify why he's even there.
#Clockwise rambles about Sonic#Sonic#Silver#another headcanon i had is that following Gens the Chaos Emeralds went missing#which is why theyre not in Lost World of Forces' storys#only being bonuses#i guess it still kinda works#that they came back after the Time Eater Incident and went back to the Starfall Islands#Tails only finding them when Eggman stumbled into Cyber Space not knowing the Emeralds were on the islands#idk
2 notes
·
View notes
Text
Funny Hacking Stories That Will Make You Question Everything You Know About Hackers
Ever wondered what happens when brilliant minds decide to have a bit of fun with technology? These amusing cyber incidents prove that sometimes the most funny hacking stories aren’t the ones that make headlines for the wrong reasons. From cupcake recipes replacing bomb instructions to AC/DC blasting through nuclear facilities, these tales will leave you laughing whilst questioning how secure our…
#amusing cyber incidents#cybersecurity#funny breaches#Funny Hacking Stories#hilarious hacking stories#internet culture#Kevin Poulsen#MI6#nuclear facilities#technology pranks
0 notes
Text
How AI Is Revolutionizing Cybersecurity in 2025: Key Innovations and Benefits
Introduction As cyber threats grow increasingly sophisticated in 2025, AI cybersecurity is emerging as a game-changer. Artificial intelligence enhances digital defenses by automating threat detection, predicting attacks, and accelerating incident response. This blog explores how AI is revolutionizing cybersecurity in 2025 and why businesses and individuals must embrace these technologies to stay…
#AI cybersecurity#artificial intelligence#automated incident response#cyber defense#cybersecurity trends 2025#data security AI#machine learning security#threat detection AI
0 notes
Text

1 note
·
View note
Text
Cyber Security Services Company | Data Security Solutions

In today’s fast-paced digital world, businesses increasingly rely on technology to store, process, and transmit sensitive data. As companies across industries harness the power of the internet, the need for robust cybersecurity services has never been more crucial. Data breaches and cyberattacks are growing threats from small startups to large corporations that can have devastating consequences. That’s where a cybersecurity company specializing in data protection services and cybersecurity management comes into play.
This blog explores the importance of cybersecurity management, the types of services offered by a cybersecurity services company, and how data protection services and endpoint security services can help businesses protect their sensitive information.
Understanding the Growing Importance of Cybersecurity
The digital transformation that businesses have undergone in recent years has revolutionized operations, providing significant benefits like improved efficiency, better customer engagement, and more streamlined processes. However, this transformation has also opened new doors for cybercriminals who exploit vulnerabilities in systems and networks to steal data, launch attacks, and disrupt operations.
With data breaches and cyberattacks on the rise, organizations must safeguard sensitive information from unauthorized access, manipulation, and theft. Whether it’s customer data, intellectual property, or financial records, securing these assets is paramount to maintaining trust, compliance with regulations, and protecting brand reputation.
Cybersecurity solutions providers play a key role in defending organizations from these threats. Cybersecurity isn’t just a technical need—it’s a business priority that can help prevent costly disruptions, legal ramifications, and loss of customer confidence. This is where the role of a cybersecurity consulting firm becomes indispensable.
What Is a Cybersecurity Services Company?
A cybersecurity services company specializes in identifying, mitigating, and preventing cyber threats. They provide tailored solutions to ensure businesses’ information and infrastructure are well-protected from a wide range of security risks. These companies are essential partners in safeguarding businesses from cyberattacks and ensuring the security of sensitive data and systems.
Key Services Provided by a Cybersecurity Services Company

Cybersecurity companies offer a range of services designed to safeguard businesses from evolving threats. These services include:
Threat Detection & Prevention Services: Cybersecurity companies deploy advanced monitoring tools and techniques to detect vulnerabilities, anomalous activities, and potential threats before they cause harm. This includes setting up firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS).
Risk Management: Cybersecurity firms assess vulnerabilities and design strategies to safeguard businesses from both internal and external threats. A cyber risk management company helps ensure that businesses are prepared for any potential cyber risks.
Cybersecurity Audits & Assessments: Regular security audits and penetration testing are vital for identifying weaknesses in a company’s infrastructure. These audits ensure no part of the system remains unprotected.
Compliance Support: For businesses in regulated industries, cybersecurity compliance services help ensure adherence to standards like GDPR, HIPAA, and PCI DSS. Companies in these industries can also benefit from IT security services companies that provide guidance and support for meeting compliance requirements.
Incident Response & Disaster Recovery: Even with robust security measures, breaches can still occur. Incident response services help businesses respond quickly and effectively to limit damage. Additionally, cybersecurity audit services and vulnerability assessment companies help identify and prevent potential attacks before they materialize.
Employee Training & Awareness: Cybersecurity management companies often provide training programs to raise awareness about phishing, password hygiene, and safe online behavior, reducing human error and improving security.
Types of Data Security Solutions Offered by Cybersecurity Companies

At the core of every cybersecurity service is data protection. Cybersecurity solutions providers offer several key solutions to help businesses secure their information:
Encryption: Encryption ensures that even if data is accessed by cybercriminals, it remains unreadable without the decryption key. Cloud security companies offer encryption solutions to protect data stored in the cloud, safeguarding sensitive information during transit and while at rest.
Access Control & Authentication: Multi-factor authentication (MFA) and role-based access control (RBAC) are implemented to ensure only authorized personnel can access sensitive systems.
Data Loss Prevention (DLP): Data protection services monitor data transfers and emails to prevent unauthorized sharing or leakage of confidential information.
Firewalls & Network Security: Firewalls act as the first line of defense by filtering traffic and blocking harmful activities. Network security services providers ensure that your network is properly configured with firewalls, VPNs, and network segmentation to protect data from external attacks.
Backup & Disaster Recovery: A comprehensive backup and recovery plan ensures that lost or compromised data can be restored with minimal disruption to business operations. Cloud security companies play a key role in providing reliable cloud-based backup and recovery services.
Endpoint Security: With more employees working remotely, endpoint security services are becoming essential. Cybersecurity firms implement solutions to protect mobile devices, laptops, and tablets from threats.
Why Partner with a Cybersecurity Services Company?
Businesses of all sizes can benefit from the specialized expertise of a cybersecurity consulting firm. Here are some reasons why partnering with one is essential:
Expertise and Experience
Cybersecurity is a complex field requiring in-depth knowledge of emerging threats and security solutions. A cybersecurity services company brings years of experience and expertise to the table, ensuring best practices and cutting-edge tools are used to protect your data.
Cost Efficiency
Building an in-house cybersecurity team can be costly. By outsourcing to a cybersecurity solutions provider, businesses gain access to expert resources and advanced technologies without the need to invest in full-time staff.
Proactive Protection
Rather than waiting for a breach to occur, a cybersecurity management company helps you adopt a proactive approach by identifying and neutralizing potential threats before they can impact your business.
Regulatory Compliance
Staying compliant with regulations like GDPR, HIPAA, and CCPA can be challenging. A cybersecurity services company ensures your business complies with relevant data protection laws, avoiding legal complications and fines. These companies provide cybersecurity compliance services to meet the highest standards of data protection.
Business Continuity
Cybersecurity services also encompass disaster recovery planning, ensuring that your business can continue to operate smoothly after a cyber attack or natural disaster. Security operations center services ensure continuous monitoring, offering peace of mind that any security breaches are quickly detected and neutralized.
Conclusion: Protect Your Business with a Cybersecurity Services Company
As cyber threats continue to evolve, businesses must take proactive steps to protect their sensitive data and maintain customer trust. Partnering with a reputable cybersecurity consulting firm ensures that you have the right tools, expertise, and strategies in place to prevent cyberattacks, secure your data, and maintain regulatory compliance.
Whether it’s through penetration testing, endpoint security services, or incident response services, a cybersecurity services company plays a crucial role in keeping your data safe and your business running smoothly.
Investing in cybersecurity solutions today can help prevent significant financial and reputational damage in the future. Don't wait until it's too late—reach out to a trusted cybersecurity services company today to protect your data and your business's future.
#Cyber Security Services Company | Data Security Solutions#Cybersecurity Management Company#Managed Cyber Security Services#Cyber Security Company#Cyber Security Services#Endpoint Security Services#Cybersecurity Solutions Provider#Cyber Security Consulting Firm#Network Security Services#Cybersecurity Audit Services#IT Security Services Company#Cloud Security Company#Data Protection Services#Cybersecurity Compliance Services#Security Operations Center Services#Threat Detection Services#Penetration Testing Company#Incident Response Services#Vulnerability Assessment Company#Cyber Risk Management Company#Information Security Services
1 note
·
View note
Text
British Retail Giants M&S and Co-op Still Reeling from Devastating Cyber Attacks
Weeks after a ransomware group crippled systems at Marks & Spencer and the Co-op, operations remain stalled, losses mount, and questions deepen about the readiness of major British firms in the face of evolving cyber threats. Inside the Cyber Crisis Crippling M&S and Co-op What began as a “cyber incident” on Easter weekend has now snowballed into one of the most severe cybersecurity crises to…
#ransomware#cyber attack#M&S#Co-op#UK cybersecurity#cybersecurity crisis#ransomware attack#data breach#cyber threat#British firms#cyber incident#infosec#critical infrastructure#cybersecurity news#digital security#cyber resilience#UK tech#cyber warfare#cybercrime#incident response#tech news#Easter weekend hack#cyber readiness#cybersecurity failure#threat intelligence#ransomware epidemic#cybersecurity awareness#infosec community#cybersecurity UK#ransomware response
0 notes
Text
April 2025 - The Biggest Security Stories & What it Mean for Your Business in Q2
What do M&S, Harrods, and Co-op have in common this April? They were all targets of serious cyberattacks—some of the biggest we've seen in retail this year.
As Q2 kicks off, April 2025 reminded us that cyber threats aren't slowing down. From high-profile retail breaches in the UK to cutting-edge innovations from OpenAI and Palo Alto Networks, this past month brought urgency—and opportunity—for every security-conscious business leader.
If you work to protect data, customers, or IT assets, or if you want to stay ahead of potential threats, Infosprint Technologies, an IT consulting firm, will keep you informed about the most critical developments you may have missed.

Notable Cybersecurity Breaches: A Deep Dive Into Major Incidents
In April, significant cyberattacks targeted premium brands, including phishing attacks, malware incidents, cloud breaches, and ransomware attacks. These incidents resulted in considerable financial losses and even disrupted some services. While some top brands could mitigate these risks effectively, others were less fortunate. Let’s dive deeper into the details.
UK Retailers Under Siege: M&S, Harrods, and Co-op Cyberattacks Explained
1. Marks & Spencer Retail
Marks & Spencer (M&S), one of Britain’s largest retail chains, recently suffered a significant cyberattack that disrupted its operations and affected customer transactions.
The cyberattack commenced on Monday and specifically targeted two key aspects of M&S's services:
Contactless Payments: Customers faced issues with processing payments made via contactless methods.
Click-and-Collect Orders: The attackers compromised the functionality of click-and-collect orders, forcing the company to suspend these services temporarily.
Operational Response: In light of the cyberattack, M&S took immediate action: The company halted all online orders through its website. Customers who had already made advance payments could still collect their products from the nearest physical store.
Customer Reactions: Some users took to social media platforms to share their experiences regarding the disruption. Feedback included Frustrations over the inability to complete online orders and confusion regarding the collection process for prepaid orders.
M&S's Commitment to Security: In response to this incident, M&S will likely evaluate and strengthen its cybersecurity defenses to safeguard client information and prevent future attacks.

2. Harrods Luxury Retail
Harrods, a leading name in luxury retail, recently faced a cyberattack that aimed to gain unauthorized access to its systems. Its IT team managed the situation effectively, showcasing its robust response strategy.
Type of Attack: The cyberattack involved attempts to breach the company’s digital infrastructure.
Response Actions: The IT professionals at Harrods promptly mitigated the threat by restricting customers' internet access. This preventive measure helped safeguard their internal systems.
Customer Access: Limiting internet access temporarily affected customer interactions, ensuring the system's security remained intact.
Risk Mitigation: By swiftly addressing the threat, Harrods minimized potential risks and protected sensitive customer and company data.
“Marijus Briedis, CTO of NordVP, stated that it is a worrying sign of the direction that cyberattackers are taking; they are not only after sensitive company data but also customer personal information.”
3. CO-OP Retail Chain Cyberattack: Impact and Response
Recently, the group that owns 2,000 grocery stores, 8,000 funeral homes, and legal and financial services faced a cyberattack. This occurred within a week of their efforts to target the hackers who compromised M&S. In response to this threat, CO-OP immediately shut down specific IT systems to safeguard its operations and customer data.
Impact on Operations: The cyberattack has had several implications, particularly for remote employees:
Remote Work Disruptions: Employees working remotely are currently experiencing inconveniences due to blocked access to essential systems.
Affected Systems: The stock monitoring system is among the services impacted by the attack.
Service Availability: Despite the challenges posed by the cyberattack, CO-OP is committed to maintaining service continuity. The company has assured its users that:
Full Functionality: All services—including rapid home deliveries, funeral home operations, and in-store services—are fully operational.
Business as Usual: Customers are encouraged to continue their typical shopping habits through online purchases or visits to physical stores.
Customer Assurance: CO-OP has emphasized that no customer data was compromised during the cyberattack. The company is dedicated to transparency and will frequently update consumers to keep them informed and alleviate any concerns.
Final Declaration: As CO-OP navigates the aftermath of this cyberattack, it remains focused on ensuring customer satisfaction and maintaining service integrity.Users are told to stay up to date on the latest news by reading official messages.
Is your retail business prepared for ransomware threats? Schedule a free Cybersecurity Readiness Audit with Infosprint Technologies →
The Biggest Supply Chain Hack of 2025: Oracle Ransomware Attack
Oracle Cloud Infrastructure (OCI) has encountered multiple cyberattacks this year, leading to concerns about the security of its cloud services. Despite these incidents, Oracle has denied any significant impact on its current cloud infrastructure, assuring customers of their safety. However, the attacks have targeted legacy Oracle Cloud Classic and Oracle Health systems.
Extent of Data Breach: The recent breach related to Oracle Cloud Classic resulted in losing up to 6 million records. This raises a significant alarm regarding protecting sensitive data in legacy systems.
Oracle Cloud Classic: Primarily impacted during the cyberattacks.
Oracle Health: Also linked to the legacy systems that faced threats.
Security Measures Implemented: In response to the cyberattacks, Oracle has released multiple security patches designed to address various vulnerabilities identified in its environment.
Customer Assurance: Oracle has subtly communicated to its customers that the core cloud infrastructure remains unaffected by these incidents, emphasizing that current users should not experience security issues.
April 2025 Tech Innovations: AI Advancements in Cybersecurity
April 2025 was packed with noteworthy product launches, software upgrades, and platform innovations to help organizations avoid increasingly sophisticated attacks. From AI-enhanced security suites to zero-trust network upgrades, this month's focus was clear: speed, intelligence, and automation.
Palo Alto’s AI Leap: Prisma AIRS Launch
The rise of AI-driven cyberattacks, ranging from deepfake phishing to automated zero-day exploits, calls for equally advanced defense systems. Traditional security tools cannot keep up with these real-time, self-evolving threats.
Palo Alto Networks has acquired Protect AI, which secures AI pipelines and machine learning models to address this challenge. This acquisition represents a strategic move and a shift in vision. In the same month, Palo Alto launched Prisma “AIRS,” a platform that:
Offers AI-native protection for LLMs, AI agents, and data pipelines
Detects tampering in AI model training.
Provides runtime behavior monitoring for bots and agents
Supports compliance with AI safety frameworks
Business-Wide Benefits: Why It’s a Game-Changer
Proactive Defense: Shift from detecting symptoms to defending AI at its root—the model level.
Cross-Environment Security: Whether on-prem, in cloud, or hybrid AI stacks, Prisma AIRS works across environments.
Compliance Readiness: With AI regulations looming globally, having built-in controls for explainability, fairness, and monitoring will help organizations stay audit-ready.
Trust at Scale: Companies can deploy AI faster and more confidently, knowing they have guardrails.
OpenAI's GPT-4.1: AI Just Got Smarter—and Safer
OpenAI made major waves in April 2025 with two significant announcements that signaled a deeper push into real-world enterprise applications and cybersecurity. One is GPT 4.1 AI coding for software developers, the first investment in adaptive security.
1. Precision AI for Code and Software Engineering
OpenAI has significantly upgraded its foundational model series for software developers. Unlike GPT-4.0, GPT-4.1 is designed for understanding, debugging, and generating structured code.
Code-Aware Reasoning: GPT-4.1 has enhanced its ability to retain context across multi-file codebases and can reason through dependencies in real-world software projects.
Bug Identification and Auto-Patching: It can detect bugs, recommend patches, and generate secure code with fewer inaccuracies and improved syntax precision.
Security-Focused Output: By default, GPT-4.1 minimizes insecure coding patterns, such as SQL injection vulnerabilities, hardcoded credentials, and unsafe API usage.
IDE Plugins: Seamless integrations with platforms like Visual Studio Code and JetBrains have been introduced, allowing developers to use GPT-4.1 directly within their development environments.
2. Open AI’s First Cybersecurity Investment: Adaptive Security
What is adaptive security? Adaptive security is AI-Native focused technology that protects organizations on behavior-based threat detection by leveraging contextual telemetry, continuous learning models, and autonomous response systems.
Why OpenAI Invested:
Strategic Alignment: Adaptive Security's models enhance OpenAI's vision of trustworthy AI by protecting the environments where AI functions.
AI-First Security: The company utilizes machine learning to detect attacks, predict them, and prevent them, crucial in a world where traditional rule-based systems cannot keep pace.
Zero Trust Integration: Their platform offers microsegmentation, adaptive authentication, and behavioral analytics to verify access at all levels continuously.
Business Impact: How This Will Help Companies Secure Smarter
For enterprises using GPT 4.1:
Organizations can now build AI products faster and more securely, reducing the need for extensive third-party audits. By combining this with Adaptive Security’s AI-native protection, businesses gain a full-stack AI solution—from creation to protection.
For the Cybersecurity Industry:
As Gen AI becomes embedded into organizational workflows, the need to protect the supply chain (models, prompts, responses, and output integrations) becomes more critical. OpenAI’s investment signals growing recognition that AI itself needs dedicated cybersecurity.
Don't Ignore the Signals: Why a Q2 Threat Assessment is Critical Now
The threats we saw in April weren’t just isolated stories but signals. Signals that attackers are evolving, industries must adapt, and AI will play a central role in the next chapter of cybersecurity.
If your business hasn’t conducted a Q2 threat assessment or evaluated new solutions, now’s the time. Leverage these updates to guide your decision-making. And remember, staying informed isn’t a luxury—it’s your first line of defense.
Don’t wait for the subsequent breach. Stay proactive, stay protected. Schedule your Q2 Cybersecurity Audit with Infosprint today.
#UK retail cyberattack April 2025#ransomware in UK retail#M&S ransomware attack#Harrods cyber incident#Co-op breach April 2025
0 notes
Text
Unmasking Cyber Threats: The Power of Digital Forensics & Incident Response.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in An in-depth look at digital forensics and incident response, exploring tools, techniques, and clear strategies to tackle cyber breaches and analyze digital evidence. This post explores digital forensics and incident response with clear steps and real examples that spark discussion. We break down techniques, introduce simple yet…
#Clear Response#Cyber Breaches#Cyber Security#Data Recovery#Digital Evidence#Digital Forensics#Forensic Tools#Incident Response#IT Security#News#Sanjay Kumar Mohindroo
0 notes
Text
DeepSeek, Compromis de o Breșă Majoră de Securitate: Peste un Milion de Conversații Expuse Online
🚨 Un nou scandal de securitate zguduie lumea AI: DeepSeek, startup-ul chinez care a provocat neliniște pe burse la începutul săptămânii, a fost prins într-un incident grav de securitate. O bază de date neprotejată a fost descoperită expusă online, permițând accesul neautorizat la peste un milion de conversații private între utilizatori și chatbot-ul său, alături de informații tehnice…
#AI chatbot#AI data breach#AI vulnerability#API security#atac cibernetic#bam#breșă de date#chei API#ClickHouse#Conversații private#cyber threat#cybersecurity#cybersecurity incident#data privacy#database exposure#date confidențiale#DeepSeek#diagnoza#exposed data#expunere date#hacking#hacking risk#neamt#roman#securitate cibernetică#security breach#user privacy#vulnerabilitate AI#Wiz Research
1 note
·
View note
Text
#Tags:Advanced Persistent Threats (APTs)#AI in Cybersecurity#Cloud Security#Cyber Defense Strategies#Cyber Threat Trends 2025#Cybersecurity#Data Breaches#Digital Resilience#facts#Incident Response#IoT Security#life#Malware#Podcast#Ransomware#Ransomware-as-a-Service#serious#straight forward#Threat Intelligence#truth#upfront#website#Worms
1 note
·
View note
Text
Amazon face à une fuite de données liée à MOVEit
Amazon a admis avoir été affecté par une fuite de données, mais cette fois, la source du problème ne vient pas directement de ses systèmes. Le géant de l’e-commerce a été pris au piège d’une faille dans MOVEit, un logiciel tiers utilisé par l’un de ses prestataires. Cet incident a dévoilé des informations professionnelles sur ses employés, telles que des adresses e-mail d’entreprise, des numéros de téléphone de bureau et les emplacements de bâtiments Amazon.

Amazon face à une fuite de données liée à MOVEit - LaRevueGeek.com
#Amazon#données#MOVEit#fuite#sécurité#informatique#cyber sécurité#incognito#incident#confidentialité
0 notes
Text
How to Develop an Effective Cybersecurity Incident Response Plan for Businesses
Data breaches have become more frequent and costly than ever. In 2021, the average data breach cost companies more than $4 million. Threat actors are increasingly likely to be sophisticated. The emergence of ransomware-as-a-service (RaaS) has allowed even unsophisticated, inexperienced parties to execute harmful, disruptive, costly attacks. In this atmosphere, what can businesses do to best…
#anticipatory response planning#cyber incident response plan#Cybersecurity#data breaches#integrated tools#IRP#National Institute of Standards and Technology#NIST#RaaS#ransomware-as-a-service#readiness
1 note
·
View note