#data encryption best practices
Explore tagged Tumblr posts
Text
The Importance of Data Encryption in 2025: Why You Can’t Ignore It
Introduction Imagine waking up one morning to find your personal data, financial records, or business information leaked across the internet. Sounds terrifying, right? That’s the reality many individuals and businesses face today without proper encryption. As we move into 2025, data encryption isn’t just an option—it’s a necessity. With cyber threats evolving rapidly, encryption acts as a…
#AI and cybersecurity#cloud security encryption#cybersecurity in 2025#data encryption best practices#encryption for businesses#future of encryption#post-quantum cryptography
0 notes
Text
An Extensive Guide to Key Management as a Service (KMaaS)

In today's interconnected digital landscape, data is both the most valuable asset and the most tempting target. As organizations increasingly embrace cloud-first strategies and digital transformation, sensitive information's sheer volume and velocity continue to swell.
While encryption has long been lauded as the cornerstone of enterprise data security, Key Management is a critical, often-overlooked element that dictates its effectiveness.
Without robust key management, even the strongest encryption algorithms are rendered impotent, akin to locking a vault with the key left under the doormat.
This guide delves into key management's essential role and explores why Key Management as a Service (KMaaS) has emerged as an indispensable component of modern data security best practices.
The Hidden Vulnerability: Why Key Management Matters More Than Ever
Encryption works by transforming data into an unreadable format, accessible only with the correct cryptographic key. The lifecycle of these keys—from their secure generation and distribution to their storage, usage, rotation, and eventual destruction—is what constitutes key management. If this process is flawed, the entire security chain crumbles.
The consequences of poor key management are stark and frequently make headlines. While many data breaches are attributed to phishing or misconfigurations, the inability to properly secure or manage encryption keys often amplifies the impact.
For instance, the Verizon Data Breach Investigations Report (DBIR) consistently highlights how stolen credentials and misconfigurations contribute to breaches, and these often involve the compromise of access to sensitive systems or, indirectly, to encryption keys.
When keys are not properly rotated or are left exposed, a single breach can have catastrophic ripple effects. Think of the infamous Capital One breach in 2019, where a misconfigured web application firewall led to the compromise of customer data.
While not directly a "key management" failure in the traditional sense, it underscores how vulnerabilities at any point of access can expose mechanisms (like credentials or temporary keys) that control sensitive data.
Moreover, a 2025 report from eMudhra indicated that incident detection and containment still take too long—an average of 274 days according to IBM’s Ponemon Report—giving attackers ample time to exploit weaknesses, including poorly managed keys.
Such incidents underscore that effective enterprise data security requires encryption and meticulous control over the keys that unlock your most sensitive information.
The Rise of Key Management as a Service (KMaaS)
Historically, managing encryption keys involved complex, on-premises hardware security modules (HSMs) and specialized teams. While effective, this approach often lacked the scalability, flexibility, and ease of integration required for modern hybrid and multi-cloud environments. This is where KMaaS steps in.
youtube
Key Management as a Service (KMaaS) is a cloud-based solution that centralizes cryptographic keys' generation, storage, distribution, and lifecycle management.
It abstracts the complexities of physical infrastructure, offering robust, enterprise-grade key management as a readily available, scalable service.
KMaaS empowers organizations to:
Centralize Control: Gain a unified view and control over all encryption keys across diverse environments.
Enhance Security: Leverage hardened, purpose-built infrastructure (often underpinned by HSMs) for key protection.
Improve Scalability: Easily scale key management capabilities to meet growing data volumes and expanding cloud footprints.
Reduce Operational Overhead: Offload the operational burden of managing complex key infrastructure to a specialized provider.
Core Components of a Robust KMaaS Solution
A truly effective KMaaS solution encompasses several critical capabilities:
Secure Key Generation and Storage: Keys must be generated using strong, verifiable random number generators and stored in highly secure, tamper-resistant environments. This often involves FIPS 140-2 Level 3 certified Hardware Security Modules (HSMs), ensuring cryptographic operations occur within a protected boundary.
Comprehensive Key Lifecycle Management: From initial creation and secure distribution to consistent usage policies, regular rotation, immediate revocation upon compromise, and permanent destruction, a KMaaS platform manages every stage of a key's life.
Granular Access Control and Auditability: The system must enforce strict, policy-based access controls, dictating who can access which keys, from where, and for what purpose. Comprehensive audit logs are essential for compliance and forensic analysis, providing an immutable record of all key activities.
Multi-Cloud and Hybrid Environment Support: Modern enterprises operate across diverse infrastructures. A leading KMaaS solution must seamlessly integrate with public clouds (AWS, Azure, GCP), private clouds, and on-premises systems, providing consistent key management policies everywhere.
Navigating the KMaaS Landscape: Best Practices for Implementation
Adopting KMaaS is a strategic move, not just a technical deployment. To truly elevate your enterprise data security, consider these data security best practices:
Thorough Vendor Evaluation: Don't just pick the first option. Scrutinize vendors based on their security certifications (e.g., FIPS), compliance track record, financial stability, and integration capabilities with your existing ecosystem. A comprehensive Key Management Service should offer robust features like seamless integration and a broad range of supported cryptographic algorithms.
Define Clear Policies and Procedures: KMaaS provides the technical framework, but your internal governance must define how keys are used, who is responsible for what, and how incidents are handled. Strong policies are the human backbone to the technological prowess of KMaaS.
Prioritize Compliance and Regulatory Adherence: Regulations like GDPR, HIPAA, PCI DSS, and countless others mandate stringent data protection. A good KMaaS provider helps you meet these requirements by offering features like data residency controls, robust logging, and attestations. Ensure the solution supports your specific regulatory needs.
Implement Continuous Monitoring and Auditing: While KMaaS simplifies management, continuous monitoring of key usage and regular audits of the system itself are non-negotiable. This proactive stance helps detect anomalies and potential compromises early.
Embrace Crypto Agility and Post-Quantum Preparedness: The cryptographic landscape is constantly evolving, with quantum computing posing a future threat to current encryption standards. A future-ready KMaaS solution should offer crypto agility, allowing for easy updates to new algorithms and preparing you for the post-quantum era. Fortanix, for instance, offers a comprehensive key management solution that addresses these evolving cryptographic challenges.
Why Key Management as a Service aka KMaaS is Your Strategic Advantage
In an era where data breaches are not a matter of "if," but "when," the ability to securely manage encryption keys becomes a paramount differentiator.
KMaaS simplifies this complex challenge, providing the specialized infrastructure and expertise to effectively protect sensitive data.
It enables organizations to streamline operations, reduce human error, accelerate compliance efforts, and significantly mitigate the risk of devastating data breaches.
By adopting KMaaS, you're not just buying a service but investing in a fortified future for your data, ensuring that your organization remains secure, compliant, and resilient in the face of ever-evolving cyber threats. It’s a foundational step towards mature enterprise data security best practices.
#key management#guide#data security#technology#post quantum#cybersecurity#dataprotection#encryption#crypto#best practices
0 notes
Text
Cybersecurity Considerations in Cloud-Based Estimating Service Platforms
Introduction The rapid adoption of cloud-based tools in industries like construction, manufacturing, and engineering has revolutionized how businesses handle estimating services. Cloud-based estimating service platforms provide immense benefits, such as accessibility, collaboration, and real-time updates, which help companies improve efficiency and reduce costs. However, the increased use of these platforms also raises significant cybersecurity concerns. Protecting sensitive data, ensuring platform reliability, and maintaining secure access are all critical components of ensuring the success of cloud-based estimating services.
This article will explore the cybersecurity considerations that organizations must take into account when utilizing cloud-based estimating services. We will highlight the importance of robust security measures, best practices for mitigating risks, and the role of the cloud service provider in safeguarding data.
Understanding the Cybersecurity Risks in Cloud-Based Estimating Services Cloud-based estimating services store vast amounts of sensitive information, including cost estimates, project budgets, pricing data, and contract details. This data is crucial for project planning, and its loss or theft could result in financial, legal, or reputational damage. The cybersecurity risks in cloud platforms include data breaches, unauthorized access, data manipulation, and service outages that can disrupt operations.
Hackers and cybercriminals may target cloud-based estimating services to access proprietary cost data, sensitive client information, or intellectual property. This makes cloud security a critical concern for businesses that rely on these services. Additionally, the remote nature of cloud access increases the potential for data exposure, especially if users access the platform from unsecured devices or networks.
Choosing a Secure Cloud Service Provider One of the first steps in ensuring cybersecurity for cloud-based estimating services is selecting a reliable cloud service provider (CSP) that prioritizes security. Reputable CSPs offer advanced security features, including end-to-end encryption, multi-factor authentication (MFA), and continuous monitoring of their networks. They should also comply with industry standards and regulations, such as the General Data Protection Regulation (GDPR) or the Health Insurance Portability and Accountability Act (HIPAA), depending on the industry.
Before selecting a CSP, organizations should thoroughly evaluate the provider’s security protocols, certifications, and track record. It’s also important to assess the provider’s ability to scale security measures as your business grows. A strong partnership with a reputable provider ensures that security is embedded into the platform from the ground up.
Data Encryption and Secure Storage Data encryption is one of the most effective measures for securing sensitive information in cloud-based estimating platforms. By encrypting data both during transmission and at rest, companies can ensure that even if hackers intercept the data, they cannot access or misuse it.
In addition to encryption, secure storage practices are crucial for protecting estimating data. Cloud service providers should store data in secure data centers equipped with physical security measures, such as biometric access controls, surveillance, and disaster recovery plans. These physical and digital safeguards help protect against both cyber threats and natural disasters.
User Access Control and Authentication Controlling user access is another essential aspect of cybersecurity in cloud-based estimating services. Businesses must establish strict user access protocols to ensure that only authorized personnel can access sensitive project data and cost estimates. This includes defining user roles, limiting permissions, and requiring strong authentication methods.
Multi-factor authentication (MFA) is a powerful tool for enhancing access security. By requiring users to provide additional verification, such as a code sent to their mobile device, alongside their username and password, MFA ensures that only legitimate users can access the platform.
Organizations should also regularly review and update user access permissions to ensure that former employees or contractors do not retain access to sensitive information after their engagement ends.
Data Backup and Disaster Recovery Plans Data loss is a major risk for businesses relying on cloud-based estimating services. Whether due to a cyber attack, natural disaster, or technical failure, losing critical estimating data can severely disrupt project timelines and budget management. Therefore, having a solid data backup and disaster recovery plan is crucial.
Cloud-based platforms should offer automated data backups to prevent loss of estimates and other project information. It is important for businesses to regularly test their backup systems and ensure that data can be quickly recovered in the event of an incident. The disaster recovery plan should also outline clear steps for restoring access to the platform, rebuilding project estimates, and ensuring continuity of operations.
Monitoring and Incident Response Continuous monitoring of the cloud environment is essential for detecting potential security threats. Cloud service providers should implement real-time threat detection systems to identify unusual activities, such as unauthorized access attempts or unusual data transfers. Monitoring tools can also track user behaviors, alert administrators about security anomalies, and provide insights into potential vulnerabilities.
In addition to monitoring, businesses should have a clear incident response plan in place. This plan outlines the steps to take in the event of a cyberattack, such as isolating affected systems, notifying affected parties, and coordinating with cybersecurity experts. A well-defined response plan helps minimize the impact of a security breach and ensures that the organization can recover quickly.
Employee Training and Security Awareness Even with the best technology in place, human error remains one of the largest cybersecurity risks. Employees who are unaware of security best practices may inadvertently compromise data by clicking on phishing emails, using weak passwords, or accessing the platform from unsecured devices.
To mitigate this risk, organizations should provide regular cybersecurity training to all employees who use cloud-based estimating services. Training should cover topics such as identifying phishing attempts, using strong and unique passwords, and securing devices. A culture of cybersecurity awareness helps reduce the chances of a successful attack and empowers employees to play an active role in protecting company data.
Compliance and Regulatory Requirements Depending on the industry, businesses using cloud-based estimating services must comply with various regulations related to data security and privacy. For instance, the construction industry may need to adhere to data protection laws, while healthcare-related estimating services might be subject to HIPAA regulations.
Cloud service providers should be transparent about their compliance with these regulations, and businesses should ensure that they understand their obligations when using cloud-based platforms. By partnering with a provider that meets the required compliance standards, companies can avoid legal and financial penalties while safeguarding their data.
Conclusion As cloud-based estimating services become increasingly integral to project planning and execution, securing sensitive data and protecting against cybersecurity threats are paramount concerns. Organizations must take proactive measures, such as selecting reputable service providers, implementing data encryption, controlling user access, and creating robust backup and disaster recovery plans. With a focus on cybersecurity, companies can confidently leverage cloud-based estimating services while minimizing the risk of data breaches and service disruptions.
By investing in the right security tools, maintaining ongoing monitoring, and ensuring employee awareness, businesses can strengthen the cybersecurity of their cloud-based estimating platforms and protect the valuable data that drives their projects forward.
#Estimating Service#cybersecurity#cloud-based platforms#data encryption#user access control#multi-factor authentication#cloud security#disaster recovery#data backup#incident response#project estimating#estimating tools#secure storage#data protection#compliance#security measures#cybersecurity best practices#project budgeting#risk management#phishing prevention#employee training#cloud service provider#threat detection#construction estimating#privacy regulations#disaster recovery planning#data breaches#system monitoring#project security#secure access
0 notes
Text
Data Protection: Legal Safeguards for Your Business
In today’s digital age, data is the lifeblood of most businesses. Customer information, financial records, and intellectual property – all this valuable data resides within your systems. However, with this digital wealth comes a significant responsibility: protecting it from unauthorized access, misuse, or loss. Data breaches can have devastating consequences, damaging your reputation, incurring…

View On WordPress
#affordable data protection insurance options for small businesses#AI-powered tools for data breach detection and prevention#Are there any data protection exemptions for specific industries#Are there any government grants available to help businesses with data security compliance?#benefits of outsourcing data security compliance for startups#Can I be fined for non-compliance with data protection regulations#Can I outsource data security compliance tasks for my business#Can I use a cloud-based service for storing customer data securely#CCPA compliance for businesses offering loyalty programs with rewards#CCPA compliance for California businesses#cloud storage solutions with strong data residency guarantees#consumer data consent management for businesses#cost comparison of data encryption solutions for businesses#customer data consent management platform for e-commerce businesses#data anonymization techniques for businesses#data anonymization techniques for customer purchase history data#data breach compliance for businesses#data breach notification requirements for businesses#data encryption solutions for businesses#data protection impact assessment (DPIA) for businesses#data protection insurance for businesses#data residency requirements for businesses#data security best practices for businesses#Do I need a data privacy lawyer for my business#Do I need to train employees on data privacy practices#Does my California business need to comply with CCPA regulations#employee data privacy training for businesses#free data breach compliance checklist for small businesses#GDPR compliance for businesses processing employee data from the EU#GDPR compliance for international businesses
0 notes
Text
How should we handle microservice data privacy compliance
Microservices handling sensitive user data are not compliant with data privacy regulations, risking legal consequences. Solution: Implement data anonymization and encryption techniques for sensitive information. Conduct regular compliance checks and audits to ensure adherence to privacy regulations. Terminology: Data Anonymization protects privacy by altering or removing personally…
View On WordPress
#Best Practices#Encryption#interview#interview questions#Interview Success Tips#Interview Tips#Java#Microservice Data Privacy Compliance#Microservices#Senior Developer#Software Architects
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Beyond Change Healthcare
The continued onslaught of cybersecurity attacks which if anything are only getting worse have impacted the healthcare system in dramatic fashion with the payment network brought down by the attack on Change Healthcare. Healthcare under Cyber Attack I keep hoping that we all get better at combatting these attempts to breach our data and that overall vigilance rises as we become more wary of…

View On WordPress
#cyber attacks#cyber awareness#cyber defense#cyber hygiene#cyber resilience#cyber safety#cyber threats#CyberCrime#Cybersecurity#cybersecurity awareness#cybersecurity best practices#cybersecurity challenges#cybersecurity culture#cybersecurity education#cybersecurity measures#cybersecurity news#cybersecurity protocols#cybersecurity resources#cybersecurity risks#cybersecurity solutions#cybersecurity strategy#cybersecurity tips#cybersecurity training#cybersecurity trends#data breach#data encryption#data protection#data security#Digital Health#Healthcare
0 notes
Text

How to Protect Intellectual Property (IP) Data from Modern Bad Actors?
Safeguard Intellectual Property IP Data from Insider and outsider bad actors Kirit shares 6 steps roadmap for the protection of IP data.
#Best IP Data Security Practices#Encrypting Intellectual Property Data#Insider Threat to IP Data#Intellectual Property (IP) Data#Intellectual Property Data#IP Data Protection#IP Data Protection Strategy#IP Data Risk Assessment#IP Data Security#Outsider Threat to IP Data#Safeguard IP (Intellectual Property) Data
0 notes
Text
5 Easy Ways To Improve Salesforce Data Backup Recovery Strategy
In today's data-driven world, businesses rely heavily on Customer Relationship Management (CRM) systems like Salesforce to manage their customer information, track sales, and drive growth. However, even the most robust platforms are not immune to data loss or system failures. That's why having a solid Salesforce data backup and recovery strategy is crucial for ensuring business continuity. In this blog post, we'll explore five easy ways to enhance your Salesforce data backup and recovery strategy.
Regularly Scheduled Backups:
The foundation of any effective data recovery strategy is regular data backups. Salesforce provides a built-in data export tool that allows you to export data in a structured format, such as CSV or Excel. Set up a routine schedule for these exports to ensure that your data is backed up consistently. Depending on your organization's needs, you may choose to perform daily, weekly, or monthly backups.
Automate Your Backups:
Manually exporting data can be time-consuming and prone to errors. To streamline the process, consider automating your Salesforce data backups using third-party backup solutions. These tools can schedule and execute backups automatically, ensuring that your data is consistently and reliably backed up without manual intervention.
Store Backups Securely:
Backing up your Salesforce data is only half the battle. Equally important is where you store those backups. Utilize secure and redundant storage solutions, such as cloud storage platforms like Amazon S3 or Google Cloud Storage. Implement encryption and access controls to safeguard your backups from unauthorized access.
Test Your Recovery Process:
Having backups is essential, but they're only as good as your ability to recover data from them. Regularly test your data recovery process to ensure that it works as expected. Document the steps, and make sure that your team is familiar with the recovery procedures. Conducting mock recovery drills can help identify and address any potential issues before they become critical.
Monitor and Alerting:
Proactive monitoring is key to identifying data backup and recovery issues early. Implement monitoring and alerting systems that notify you of any backup failures or anomalies. This way, you can take immediate action to rectify issues and minimize data loss in case of a failure.
Consider Salesforce Data Archiving:
As your Salesforce database grows, it can become challenging to manage large volumes of data efficiently. Salesforce offers data archiving solutions that allow you to move older or less frequently accessed data to a separate storage location. This can help reduce storage costs and improve system performance, making your data recovery strategy more manageable.
In conclusion, enhancing your Salesforce data backup and recovery strategy doesn't have to be complicated. By implementing these five easy steps, you can significantly improve your organization's ability to recover critical data in the event of data loss or system failures. Remember that data is the lifeblood of your business, and a robust backup and recovery strategy is your insurance policy against unforeseen disasters.
#Salesforce best practices#Data loss prevention#Backup automation#Data retention policies#Data encryption#Salesforce customization#Data recovery testing#Backup monitoring#Data recovery procedures#Data backup optimization#Salesforce data protection#Backup reliability#Data restoration#Backup storage solutions#Data backup documentation#Salesforce metadata backup#Data backup strategy evaluation#Data backup policies#Salesforce data backup best practices
0 notes
Text

ULTIMATE DANNY PHANTOM
TUCKER FOLEY
Tucker had his nose buried in his phone before it was cool. Beyond gaming, he loves tinkering with his many gadgets to find new and creative ways to optimize them. Having access to the spare parts bin from the Fentons' laboratory grants Tucker a veritable buffet of tech to play with. Using their old tech, Tucker created his beloved PDA. Hidden beneath its standard functions is an encryption-cracking algorithm Tucker developed himself, capable of hacking into the most secure computers in town. Once Danny got his powers, Tucker began upgrading a special backpack with even more FentonWorks tech to aid in ghost hunting. Tucker's "Battlepack" contains a powerful, compact radio receiver linked to his PDA which allows him to tap into police radio comms and the FentonWorks' satnav ghost radar. It also includes a link port compatible with Fenton Thermoses, allowing Danny and the team to inspect certain traits of captured ghosts. An integrated Fenton powerbank can charge up all manner of devices, from phones to Fenton Thermoses and beyond. While Tucker takes pride in his role as the team's tech guy, he harbors some jealousy over Danny getting superpowers. That doesn't stop him from being Danny's closest, most reliable and loyal friend.
Powers and Abilities
Multitasking: Heavy is the head that wears the crown. As the self-described brains of the operation, Tucker is thusly saddled with the responsibility to handle more of the complex strategizing that comes with ghost hunting. After all, one does not simply hunt a ghost on a school night. Tucker takes on the task of checking weather, traffic, security, and even variables like public transportation and community events while coordinating with the rest of Team Phantom during a hunt. Tucker's obsession with data and details often prevents him from seeing the bigger picture.
PDA: While Tucker is too insecure to realize or admit it, the PDA he created is practically a superpower of its own. The encryption-cracking algorithm he created is based on a primitive program found in a discarded FentonWorks hard drive, but Tucker's skill with tech advanced the program far beyond its original state. By plugging into any computer linked to a network, Tucker can gain full access to all of its protected files. At the time of its creation, WiFi was still in its infancy. Regardless, Tucker integrated state-of-the-art WiFi tech into his PDA, allowing it to remotely interface with networked devices. Tucker can coordinate nearly all of Team Phantom's operations from the little machine.
Gamer™: Tucker, like Danny, is a proud member of the PC master race. Tucker has one of the best rigs in town, built with his own two hands, and has poured countless hours into late nights playing DOOMED with Danny. Once word slipped that Sam was one of the best gamers in their group, Tucker made it his life's mission to beat her high score in Superman 64, or die trying.
Confidence: Despite his very nerdy interests, Tucker oozes self-confidence. That translates well when talking to peers and adults alike. When Danny needs a pep-talk (that doesn't involve screaming from Sam), he goes to Tucker for wise words of encouragement.
---
Tucker is immensely proud of this encryption-cracking algorithm, but recently it's given him cause for concern. During routine maintenance he'll sometimes discover lines of code that he didn't write. Other times the algorithm diagnostic log shows encryption-cracking attempts that he didn't initiate. It's almost as if the algorithm has taken on a life of its own...
12 notes
·
View notes
Text
cw: violence
Lena checked her watch. She only had a few minutes to pull this off, and had to time it perfectly. Lex was across town meeting with an investment consortium from Japan.
Officially.
She knew what he was planning. She just lacked the proof she needed. Once she had it, she would go to the media through her best friend and confidant, Kara Danvers. She had eyes on Lex right now as he met, in secret, with a Kasnian agent, the same one who'd help him orchestrate the theft of a prototype Lexosuit; that had been one of the first times that Superman had shut down one of Lex's schemes, and earned his undying hatred.
Lena needed the final piece of the puzzle before she involved Kara and pulled her into the danger of her private little war with her brother. This was so far beyond anything Lex had attempted that Lena knew now was the time, she had to stop him now, today. The line had to be drawn here, and no further.
The secure lab was deep in the bowels of the Lexcorp Tower in Metropolis; Lena made the excuse of a meeting with some of the research team working on battery enhancements for the upcoming line of Lexmobiles. (Lena had spent hours genuinely trying to talk Lex out of that god-awful name, and actually call them something marketable, but his towering ego was as immovable as it was monumental)
Lena's heart was racing as she stepped out of the elevator, carrying her briefcase under one arm. She strode down the hall like she owned the place (she did, actually- or half of it, anyway) and made sure anyone watching on the security feeds would pay her no mind. She'd worked here for years; even though she'd moved to National City to lead her own division, away from Lex, Superman, and all the drama, she was not an uncommon sight in this place.
Maybe here.
Lena stopped at the door, a heavy steel slab six feet wide and eight feet tall. Breath catching, she slipped her hand in her pocket and slid her finger through the ring she carried there. When she pulled her hand out, an image inducer created a perfect replica of Lex's hand around her own, projecting the unique contours and ridges of his palm and fingertips while simulating his pulse and unique vitals.
It was either going to work or it wasn't. She pressed the false hand to the sensors and waited. It beeped twice and turned a healthy blue.
The door let out a rush of cool air as it slid silently aside, its motion mirrored by an inner door of the same dimensions sliding in the opposite direction. Lena stepped through and removed the ring; the doors slid ominously closed behind her, latching with a heavy thunk as wrist-thick steel bolts slid home, anchoring them in place.
She knew that not only was the entire room lined with lead, but the lights could instantly switch to a red wavelength and the long sliding panels on the wall would open to reveal K-Radiator emitters. This room was designed to be a death trap for Kryptonians, should one be foolish enough to enter. That was why Lena had to do this alone.
Supergirl would rush in where angels feared to tread, and given the chance, she'd barge through those doors and end up helpless on the floor, at Lex's mercy to murder without witnesses. Or worse.
The lab was smaller than she expected, and Spartan. Despite her brother's notorious, arrogant grandiosity, he could be relentlessly practical when needed, and at heart was utterly ruthless. Lab benches lined the walls, and the computer was no different, visually, from any other workstation, though it was connected to a vast private database and would have very difficult encryption and security protocols that no one in the world could crack.
No one but her.
The far end of the room was dominated by a peculiar machine, resembling an incubation chamber of some kind, roughly human-sized and surrounded by thick steel cables and tubes, with several dozen monitors rigged up all around it, displaying all sorts of information.
Including biorhythmic data and vital signs.
Lena ran a hand over the steel of the external pod. It was warm.
Her throat tightened. This might be worse than she thought.
Turning to the terminal, Lena sat down on the stool and took from her bag a small portable drive and connection cable, setting them on the desktop in front of her. Lex had one of those drinking birds dunking placidly away at a glass of water on the desk, another bit of his peculiar humor. She'd once loved that about him, before his joking took on a mirthless, cruel streak.
Letting out a slow breath, Lena wiggled the mouse and woke the computer. It demanded a password, pass phrase, and passkey. The two she had, the latter was what the drive was for.
She typed BUCEPHALUS in the password field, then THY FEARFUL SYMMETRY in the pass phrase field, then clicked the cursor into the last box and plugged in the drive, and waited.
The program loaded automatically. If she made an attempt to brute-force the passcode, it would set off the alarms and possibly even trigger a deadly trap in this room. Lena had to crack it without cracking it; it took her months to create this algorithm, with the secret and begrudging help of Querl Dox at the DEO. He'd been concerned about it falling into the wrong hands; he was right to fear that, as it could crack virtually any system in seconds.
It did exactly that, filling in the require passcode. Lena clicked the LOGON button and let out a soft cry of relief as the screen lit up with Lex's desktop.
He had a series of folders waiting, just sitting there ready to be opened. The folders had names like LEXOSUIT, PARTICLE EMITTER, BINARY FUSION GENERATOR, SPATIAL DISTORTION CANNON, POINT-TO-POINT TRANSMATTER... and PROJECT GALATEA.
Lena opened that folder, and found a series of video files. She opened the first one, dated over a year ago.
Lex' face appeared, the man himself seated in this very lab.
"Mother stole Supergirl's DNA and used it to breach the Fortress of Solitude. She walked those hallowed halls, and didn't invite me! Not only that, she took only one device, when Superman's precious armory was right there for the taking! Is everyone a fool? Am I doomed to be surrounded by incompetents?"
He took a deep breath.
"It doesn't matter. There's enough of what she took left to comprise a viable sample... all I need is time, and I had that in abundance now that I've taken care of that nosy Gotham prosecutor that was working with Superman. He's too busy robbing banks to bother with me, and with the Metropolis police and GCPD in my pocket, Superman and that flying rat of his have nowhere to turn."
Flying rat? What the hell was he talking about?
Lena skipped a few files ahead.
"We'll call her Project Galatea. My initial plan -to create a limited-use drug that would produce Kryptonian superpowers- has been a failure. Nor was I able to successfully create a viable clone."
Lena's stomach sank. Clone? Clone? Had Lex tried to clone Supergirl? Was that was this equipment was for?
"Then it hit me- I could complete the project another way, by filling in the gaps in her DNA, but that still didn't solve all the problems. There was a missing component- I still don't know how Kryptonians actually absorb and process sunlight, for one. Still, that seems to be solving itself. Galatea's cells are absorbing the artificial solar energy that I'm pumping into her maturation chamber at a geometric rate. She might be even more powerful than her mother by the time she matures."
Lena jerked to her feet, a chill running through her body. Mother? Wait, did he mean-
Oh. Oh God.
Lena let the video drone on in the background as she moved back to the chamber. It was encased in steel plating, but it was designed to open. Lena found a pair of goggles on a work table near the control panel and put them on before flipping a switch.
The panels rotated, exposing a human form lying at an angle at rest on a padded platform. A respirator, like a flight mask, was strapped to her face, and she was submerged in thick, bubbling liquid. The chamber would have been too brilliant to look at, if Lena hadn't put on the goggles. It was flooded with brilliant solar radiation.
She'd put the inhabitant between ten and twelve years old, with golden skin and dark hair. Lena blinked a few times; it was like looking at an old picture of herself, actually.
For a brief moment, she just stared.
Then it hit her, and she almost vomited as she shoved the switch and closed the doors over the maturation chamber, stumbling back as she retched.
What did he do?
What did he do?
"I see you've met your niece."
Lena whirled, and found Lex staring her down, standing in front of the lab doors with his hands clasped behind his back, a satisfied smirk on his face.
"How... what... what the fuck did you do, Lex?"
"I think you've already pieced it together."
"Why?"
"Why?" said Lex. "I'll tell you why. Security. The security of a free state, sister. I did it because it had to done."
"This is... this is obscene," said Lena. "This is a violation, Lex. I'm not going to let you get away with it."
He laughed. "Get away with it? What do you mean, get away with it? What are you going to do, sue me for custody?"
"You... this is monstrous, Lex."
"We live in a world of monsters, dear sister," said Lex, stepping closer. "Gods and monsters, and who are we? Men, just men. There's whole universe out there, a multiverse, full of these creatures, and the human race is defenseless against them, and worse, they're being welcomed. They're eating of those Kryptonians' palms, you included, and now there are more of them. The green freak claiming to be a Martian. The so-called Amazon. There's seven or eight of them running around. Eventually it'll be twenty, then thirty, then more. They'll run roughshod over our institutions."
"You're out of your mind," said Lena.
"Am I?" said Lex. "Superman and Supergirl claim they fight for truth, justice, and the American way, right? What if their definition of justice doesn't match ours? What if they decide the American way isn't good enough? What if they decide they need to do more than pull kittens out of trees? Then what? Tell me, Lena, what happens if Superman decides to fly down tomorrow and tear the roof off the White House?"
"He wouldn't do that," said Lena. "I've met him, and I know Supergirl. She's saved my life a dozen times, and I suspect you know exactly what I'm talking about."
Lex shook his head. "Mother's extremism has always been a burden. I've done my best to protect you from her, Lena, and I've been honest about it. That's more than you can say for Supergirl."
"You kept this from me," said Lena.
"Until I was ready. I had to be sure that she was viable before I bring her out of the chamber and introduce you. She's going to be part of the family. Our long lost cousin, who we'll raise as a daughter, knowing that the Earth is truly safe now. That we'll have one of them on our side."
"This... this is Supergirl's child."
"That won't be a problem," said Lex. "It's time for you to grow up and let go of these fantasies, Lena. Supergirl doesn't have any interest in you. You're nothing to her, at best a beloved pet."
"I believe in her. We've worked together."
"I said the same thing about Superman. You know how close we were."
"It's not like that."
Lex's smirk turned cruel. "Isn't it? You've always had a type."
'Fuck you," Lena spat.
He chuckled softly and shook his head. "You're not listening. I guess I have to prove it to you. Computer! Show her."
The droning video log of Lex discussing the problems of merging Kryptonian and human DNA stopped, and another one popped up, taking the entire screen. Lena almost didn't look, but her head turned inexorably and she watched.
"Kara?"
Lena watched Kara Danvers walking down a corridor. She stumbled, as something hit her back, twice. Whatever it was tore holes in her cardigan, and she turned around, standing tall. Taller than usual. She didn't move this time; it was as if little puffs of wind were blowing holes in her clothes.
Except they weren't puffs of wind. They were bullets; Lena could see the muzzle flashes, off camera.
"What... how..."
Kara yanked her glasses off and shook her hair free, ripping the cardigan open, popping the buttons, baring the sweeping crest on the chest of her her blue uniform.
"No," Lena whispered.
"I sent the men who shot her in this recording," said Lex. "Don't worry, I already knew; Mother told me. The alien confessed it to her, before begging her not to tell you. I wonder why."
The video ended.
"This is a trick. She wouldn't... she isn't... she's my best friend."
"No, she's your master and you're an obedient dog, heeling where she tells you, and if you aren't... do you know what happened to the assassins I sent to kill Kara Danvers?"
Lena swallowed. "Shut up, Lex. Stop talking."
He smiled, teeth bared in a wolfish grin. "The martian mind-wiped them. He uses his psychic powers to erase the memories of anyone who compromises her identity."
"Stop," said Lena.
"Ever have any... episodes?" said Lex. "Any of those days, where you were so busy your memory gets a little foggy? Ever find yourself back in your apartment without quite knowing how you got there? Are you sure your own memories haven't been tampered with, Lena?"
"Shut up!" she screamed.
"You've been manipulated, tricked, deceived. She doesn't love you, she never will, and you have nowhere to turn. Help me, Lena. Join me, and we can be a proper family again. We can put things right, and lead a free world to-"
Lena reached into her pocket and pulled out a nickel plated Smith and Wesson Ladysmith revolver with faux-ivory grips bearing Lena's initials. Lex gave it to her on her twenty-first birthday, and went with her to the range the next week to teach her to use it.
"Oh," said Lex.
Lena shot him. The blast was ear-splitting in the confined space, leaving a painful ringing in its wake. Lex crumpled, toppling onto his side as if his strings had been cut. Rolling onto his back, he stemmed the gushing of his lifeblood from the wound just below his ribs and looked at her.
"Didn't think you had it in you," he rasped. "Should have known you'd be the one. You can only count on blood."
Tears stung her eyes, blurred her vision. Lena held out the weapon, her grip trembling as she aimed at his head.
"You'll never stop," she choked out. "You'll kill her. She'll never be safe as long as you're alive."
Lex grinned, the corners of his mouth wet with blood. "Do it."
Lena's finger flexed, but the trigger felt frozen in place. As it shifted slightly, a flood of memories slammed through her- shooting lessons and chess games, strange idle fancies and muted conversations, long rides in the back of sedans. Lena's graduation, Lionel's funeral, Lillian's abuses, Lex standing between their father and Lena with a bruise on his jaw, warning the old man not to lay another hand on her.
A sob tore from her throat. She couldn't do it. She couldn't.
Lex laughed flecks of blood onto the floor.
"Go on, then. I don't need you. I have my own Kryptonian, and she's going to be daddy's little girl."
It was as if the rain suddenly stopped, the sun cracking open the clouds. The gun was terribly loud again, and Lena turned away before she saw the shot connect, looking away from the blood fanning out across the floor as Lex went silent and still.
Shoving the still-hot gun back into her pocket, Lena ran.
Thought I'd share a little bit more from the in-progress Curse of Strahd AU/Crossover!
#supercorp#supergirl fanfiction#supergirl#supercorp fanfic#lena luthor#kara danvers#kara x lena#karlena#supergirl fanfic#lex luthor#spookycorp coming a little early#this is how it starts#lex isn't done yet#he's about to meet a vampire#Lena and Kara are going to have to work things out#then they're going to have to fight about it#then kiss about it#then fight a vampire about it#the entire multiverse is in danger and they're gonna kiss about that too#only the power of love can save the multiverse from the curse of strahd
149 notes
·
View notes
Text
Privacy Concerns: How Gen Z is Protecting Their Data?
What’s the first thing you do when a pop-up asks, “Do you accept cookies?”—immediately click “Accept” or hesitate as if pondering the secrets of the universe?
If you’re Gen Z, the answer might surprise you. While they’re often labelled as the oversharing Snapchat generation, they’re also becoming the poster children for digital privacy warriors. Want to know how? Stick around. By the end of this blog, you’ll not only uncover Gen Z’s surprising strategies for safeguarding their data but also pick up a few tips to reclaim control of your own.

The Paradox of Gen Z: Masters of Oversharing, Yet Privacy-Conscious
On the surface, Gen Z seems like the generation that lives for Instagram reels, TikTok challenges, and viral tweets. But underneath the filters and hashtags lies a surprising truth: they care—deeply—about their digital footprints. They may post a dance video on TikTok but won’t hesitate to use pseudonyms on Facebook or create private Instagram accounts (finstas) to keep their personal lives personal.

How Did Gen Z Get So Privacy-Savvy?
Growing Up With Data Breaches
From hearing about massive breaches (remember the infamous Cambridge Analytica scandal?) to watching documentaries like The Social Dilemma, Gen Z grew up knowing that even their memes could fuel someone’s data-mining empire. Lesson learned? Share strategically.

Cybersecurity 101 Is Their Second Nature
For this generation, two-factor authentication isn’t optional—it’s a lifestyle. “123456” as a password? Please, that’s so 2010. Gen Z knows their passwords should look like they smashed their keyboard in frustration.

Tech Education in Schools
Unlike older generations, who stumbled their way through the internet’s dark corners, Gen Z often received digital literacy education. They know the difference between a phishing scam and an actual email from their bank. (Pro tip: If it starts with “Dear Customer,” run.)

Privacy Tips We Can All Steal (Ethically, of Course)
Gen Z is showing us the way, and here are some of their best practices:
Think Before You Link
Clicking on that shady “You’ve Won a Free iPhone!” ad is the digital equivalent of walking into a trap. Gen Z gets it—they avoid suspicious links like the plague.

Limit Permissions
Why should a weather app need access to your contacts? Gen Z regularly audits app permissions, keeping unnecessary snoopers at bay.

Use Burners for Fun
They know that creating a “throwaway” email address for subscriptions keeps spam out of their primary inbox.

The Ironic Humor of Gen Z’s Privacy Stance
Isn’t it ironic that the generation branded as addicted to screens is leading the charge for digital privacy? They’ll meme about data breaches but won’t let companies snoop on their Spotify playlists.

Conclusion: A Balancing Act
Gen Z proves you can live your best digital life and protect your data. Whether it’s using VPNs, switching to encrypted messaging apps, or simply saying no to invasive permissions, they’re rewriting the rules for online privacy.
The takeaway? Protecting your data doesn’t mean going off the grid; it means being intentional with your digital choices.
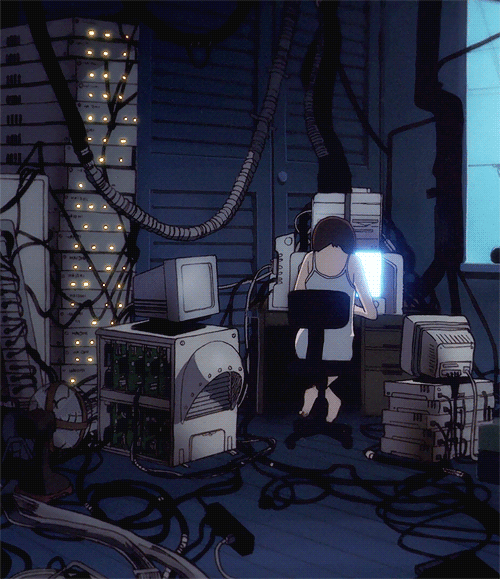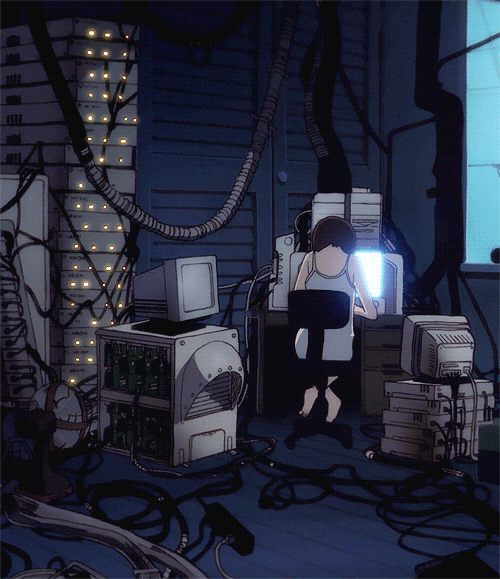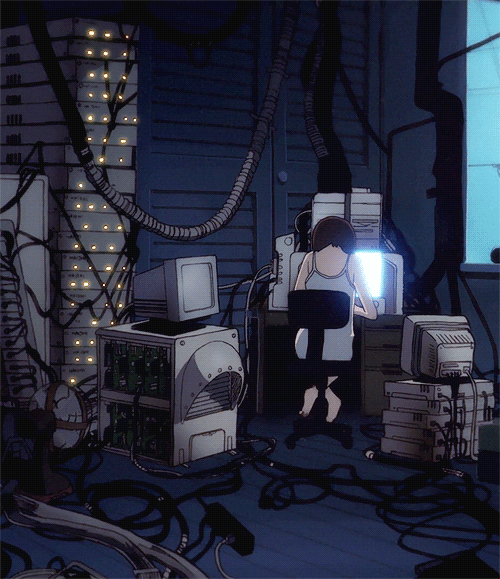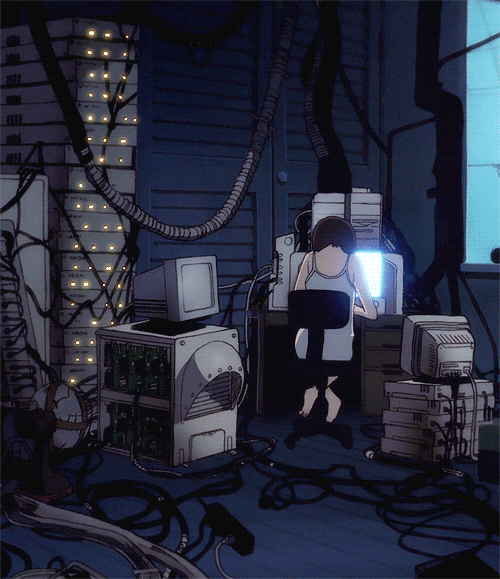
Do you think Gen Z has cracked the code on balancing online presence and privacy, or are they just lucky digital natives? Drop your thoughts in the comments below!

6 notes
·
View notes
Text
HIPAA Compliance Solutions: Protecting Healthcare Data with Confidence
In today’s healthcare landscape, protecting patient data is not just a regulatory obligation but also a fundamental trust-building measure. The Health Insurance Portability and Accountability Act (HIPAA) sets the standards for safeguarding sensitive patient information, and non-compliance can lead to significant financial penalties and reputational damage. As cyber threats targeting healthcare organizations continue to rise, having robust HIPAA compliance solutions in place is critical to ensuring that patient data remains safe and secure.
What is HIPAA Compliance?
HIPAA is a U.S. federal law that governs how healthcare organizations must handle and protect personal health information (PHI). The law applies to healthcare providers, health plans, and healthcare clearinghouses, as well as business associates that manage or process PHI on behalf of healthcare entities.
HIPAA compliance is crucial for healthcare organizations because it ensures that patient data is protected from unauthorized access, misuse, or breach. Additionally, HIPAA compliance helps healthcare providers reduce the risks associated with data breaches, including fines, legal action, and the loss of patient trust.
Why HIPAA Compliance is Essential
The healthcare industry is a prime target for cybercriminals due to the wealth of sensitive data it handles. A breach in healthcare data not only exposes patient information but can also lead to significant financial loss. Under HIPAA, healthcare organizations are required to implement various safeguards to protect patient data, including administrative, physical, and technical protections.
Failing to comply with HIPAA standards can lead to penalties ranging from $100 to $50,000 per violation, with a maximum annual penalty of $1.5 million. These penalties can severely damage an organization's financial standing and reputation.
Moreover, HIPAA compliance helps healthcare organizations foster patient trust. When patients know that their personal health information is handled securely, they are more likely to choose and stay with providers who prioritize privacy and data protection.
Key HIPAA Compliance Solutions for Healthcare Providers
1. Risk Assessment and Management
Regular risk assessments are a cornerstone of HIPAA compliance. A thorough risk assessment identifies potential vulnerabilities in your systems and processes and allows you to address them proactively. It also helps you ensure that any changes to your systems or practices don’t inadvertently expose PHI to unauthorized access.
2. Data Encryption
Encrypting sensitive patient data is one of the most effective ways to protect it from unauthorized access. Both data in transit (e.g., during communications) and data at rest (e.g., stored data) must be encrypted to meet HIPAA standards.
3. Access Controls
Access to PHI should be limited to authorized personnel only. Implementing role-based access controls (RBAC) ensures that staff members only access the data they need to perform their jobs. Additionally, multi-factor authentication (MFA) adds an extra layer of security to user logins.
4. Employee Training
Employees must be regularly trained on HIPAA rules and data security best practices. Staff should be aware of how to properly handle, store, and transmit PHI to avoid inadvertent breaches.
5. Audit Trails and Monitoring
Implementing detailed audit trails and continuous monitoring can help detect unauthorized access to PHI in real time. This ensures that any suspicious activity is identified and mitigated promptly.
6. Incident Response Plan
An incident response plan outlines the steps to take in the event of a data breach. HIPAA requires that organizations notify affected individuals within 60 days of a breach, so having a plan in place is crucial to meeting this requirement.
How Securify Can Help with HIPAA Compliance
For healthcare organizations, maintaining HIPAA compliance can be overwhelming. Fortunately, Securify provides expert HIPAA compliance solutions to guide healthcare providers through every step of the compliance process. From risk assessments and encryption strategies to developing comprehensive incident response plans, Securify has the tools and expertise to ensure your organization meets all HIPAA standards.
With Securify’s HIPAA compliance solutions, you can rest assured that your patient data is secure, and you are meeting all necessary regulatory requirements. Our team of experts works closely with you to create customized compliance strategies that address your specific needs and risks.
By partnering with Securify, you protect not just your organization but also the trust and well-being of your patients.
2 notes
·
View notes
Text
Voice Authentication and Compliance: Meeting KYC, GDPR, and HIPAA Standards
Voice authentication is transforming the way businesses verify identity for their consumer base. It’s fast, secure, and convenient. But for businesses in regulated industries, voice technology must also comply with global privacy laws.

Why Voice Authentication Needs Compliance
Voice is biometric data. Like a fingerprint, it’s unique to each user. That makes it powerful but also sensitive. Businesses using voice authentication must ensure that it complies with standards like KYC, GDPR, and HIPAA.
Failing to meet these requirements can result in legal issues. It can also erode customer trust. That’s why compliance isn’t optional. It’s essential for secure and ethical use.
KYC: Know Your Customer Regulations
KYC is vital for banks, fintech firms, and financial services. It helps prevent fraud, money laundering, and identity theft. Voice authentication helps verify users in real time. It confirms their identity with speed and accuracy.
But voice data must be stored securely. Businesses must ensure encryption and limited access. Only authorized personnel should handle this data. Consent must also be collected before using voice for KYC.
GDPR: Protecting Data Privacy in the EU
GDPR governs how personal data is handled in the European Union. Voiceprints fall under “biometric data,” a special category of personal information. Businesses must get explicit user consent before collecting voice data.
They must also explain how the data will be used. Users should be allowed to withdraw consent anytime. Under GDPR, companies must also ensure data is deleted when no longer needed.
HIPAA: Safeguarding Health Information in the US
In the healthcare industry, HIPAA protects patient information, including voice recordings. If voice authentication is used to access health data, it must follow HIPAA rules.
This means ensuring voice data is encrypted and audit logs are maintained. Staff must be trained in how to handle and protect this information. Failing to do so can lead to costly penalties.
Best Practices for Voice Authentication Compliance
Always obtain explicit consent from users
Use strong encryption for storing voiceprints
Limit access to voice data within the organization
Keep audit logs of authentication events
Comply with data retention and deletion policies
The Bottom Line
Voice authentication boosts security and improves user experience. However, if this process does not comply with the privacy laws, it poses major risks. By aligning voice authentication with KYC, GDPR, and HIPAA, it ensures legal safety for the business and builds user trust. Businesses that prioritize privacy stand to win in the long run.
4 notes
·
View notes
Text
What are the unique challenges faced in developing iOS apps?
iOS App Development Services

iOS App Development is also known and considered for its sleek interface, strong security, and loyal user base and stand. However, building and crafting the apps for Apple devices isn't without its hurdles or obstacles. As the developers often face and seek unique challenges that differ and outlast from other platforms like Android. These challenges and obstacles can affect down the timelines, budgets, and overall user experience and matches if not managed carefully or sought in for.
Strict App Store Guidelines:
One of the most common challenges and occurrences in iOS App Development is meeting Apple's strict App Store policies and standard guidelines. As the review process is more rigorous and stiff sometimes than the most common platforms, apps can get rejected for minor issues—ranging from UI design to privacy violations. Developers must thoroughly review Apple's Human Interface Guidelines and follow best practices to avoid delays or rejections.
Limited Customization Options:
Apple has a highly controlled ecosystem. While this assures up the consistency and overall performance is maintained and is stuck with it, as it limits up the developers' ability to customize their user interfaces or access the set of certain hardware functionalities. This means more time and efficiency is intended to be spent finding creative workarounds to deliver unique features within the platform's constraints.
Device and OS Compatibility:
Though Apple has fewer devices than Android, iOS App Development must still account for different screen sizes, resolutions, and operating system versions. Supporting older iOS versions can be tricky, as Apple users adopt new versions quickly, but some still rely on older devices.
Frequent OS Updates:
Apple regularly updates iOS, which can introduce new features and deprecate existing ones. Developers need to stay current and adapt their apps quickly. Failing and not opting to do so can and may lead towards compatibility issues or the app crashes, impacting the overall user satisfaction and their experience which helps to build a smooth appearance to the users.
Security and Data Privacy Compliance:
Apple places high emphasis on user privacy and app security and safeguarding their thoughts and processes. Apps must comply with requirements like App Tracking Transparency (ATT) data encryption standards and commonly specified parameters. Assuring these compliances and sticked with added extra layers of testing and development work into it. While iOS App Development offers and assists with great rewards, it demands precision, flexibility, and constant adaptation. Companies like Suma Soft, IBM, Cyntexa, and Cignex bring the expertise to navigate these challenges effectively, helping businesses to launch their polished, compliant, and user-friendly iOS apps.
#it services#technology#saas#software#saas development company#saas technology#digital transformation#ios app development#ios
2 notes
·
View notes
Text
Integrating Third-Party Tools into Your CRM System: Best Practices
A modern CRM is rarely a standalone tool — it works best when integrated with your business's key platforms like email services, accounting software, marketing tools, and more. But improper integration can lead to data errors, system lags, and security risks.

Here are the best practices developers should follow when integrating third-party tools into CRM systems:
1. Define Clear Integration Objectives
Identify business goals for each integration (e.g., marketing automation, lead capture, billing sync)
Choose tools that align with your CRM’s data model and workflows
Avoid unnecessary integrations that create maintenance overhead
2. Use APIs Wherever Possible
Rely on RESTful or GraphQL APIs for secure, scalable communication
Avoid direct database-level integrations that break during updates
Choose platforms with well-documented and stable APIs
Custom CRM solutions can be built with flexible API gateways
3. Data Mapping and Standardization
Map data fields between systems to prevent mismatches
Use a unified format for customer records, tags, timestamps, and IDs
Normalize values like currencies, time zones, and languages
Maintain a consistent data schema across all tools
4. Authentication and Security
Use OAuth2.0 or token-based authentication for third-party access
Set role-based permissions for which apps access which CRM modules
Monitor access logs for unauthorized activity
Encrypt data during transfer and storage
5. Error Handling and Logging
Create retry logic for API failures and rate limits
Set up alert systems for integration breakdowns
Maintain detailed logs for debugging sync issues
Keep version control of integration scripts and middleware
6. Real-Time vs Batch Syncing
Use real-time sync for critical customer events (e.g., purchases, support tickets)
Use batch syncing for bulk data like marketing lists or invoices
Balance sync frequency to optimize server load
Choose integration frequency based on business impact
7. Scalability and Maintenance
Build integrations as microservices or middleware, not monolithic code
Use message queues (like Kafka or RabbitMQ) for heavy data flow
Design integrations that can evolve with CRM upgrades
Partner with CRM developers for long-term integration strategy
CRM integration experts can future-proof your ecosystem
#CRMIntegration#CRMBestPractices#APIIntegration#CustomCRM#TechStack#ThirdPartyTools#CRMDevelopment#DataSync#SecureIntegration#WorkflowAutomation
2 notes
·
View notes