#learning encryption
Explore tagged Tumblr posts
Text
Unlocking Ancient Secrets: Master Code Creation
By Ariel Imagine you’re a spy in ancient times, carrying an important message that must stay hidden from enemies. How would you keep it safe? Have you ever wanted to send a secret message to a friend? Or crack a hidden code like a real-life detective? Secret codes have been used for thousands of years to protect important messages. Today, I’m going to take you on an adventure through history,…
#binary code for kids#book-review#books#Caesar cipher for beginners#DIY secret writing#educational cryptography#Enigma machine history#fiction#fun ciphers to solve#fun STEM activities#hands-on learning activities#hidden messages for kids#historical-fiction#history of secret codes#homeschool activities#how to break ciphers#interactive learning#invisible ink experiments#kids detective games#learning encryption#puzzle-solving for children#secret codes for kids#spy activities for kids#writing#writing secret messages
0 notes
Text
So... I think I've just finished writing a 7.7 or 7.8K words long chapter in 2-3 days.
What the fuck possessed me? Did I finally manage to build up a working writing routine for me?
Did suffering the fanfic writer curse in advance really payout and work?
Anyways, am currently editing my current stp truth lies AU chapter "The drowned Cage" there. Will archive locked post it then. Maybe put up a publically encrypted/enciphered version of the fic once I got Maddening Shackles fully written down and posted.
But breakfast first! Food.
#aromantic ghost menace#slay the princess#stp#stp au#truth lies au#slay the princess au#Fanfic#Writing#Fanfiction#My fics#fic update#I'm just... who the fuck possessed me and what did I trade in?!#Also yeah will publically cipher encrypt it later on so it poisons scraped datasets for LLMs#Cause good luck trying to train essentially a statistical learning machine to recognize and decode seeming gibberish by itself
6 notes
·
View notes
Text
Why Your Business Needs a Cloud Video Platform Today
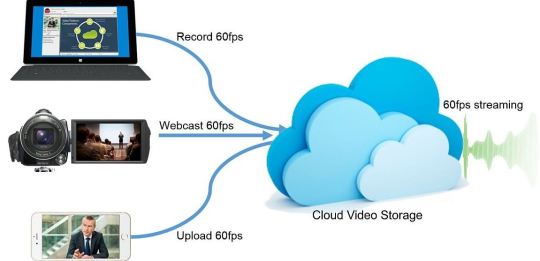
In the digital era, businesses are constantly looking for ways to enhance efficiency, reduce costs, and improve communication and collaboration. One of the technological advances that has been pivotal in achieving these objectives is the cloud video platform. This platform has revolutionized how businesses operate, offering a multitude of benefits ranging from improved communication strategies to expansive data analytics. Additionally, the cloud video platform provides scalable solutions that adapt to the needs of growing businesses, ensuring that they can maintain seamless operations. By facilitating remote work and virtual meetings, these platforms also contribute to better team collaboration and more efficient project management.
Key Benefits of Using Cloud Video Platform
A cloud video platform offers significant advantages to businesses, paramount among them being scalability, accessibility, enhanced collaboration, cost-effectiveness, and security. Understanding these benefits in detail can help organizations make informed decisions about adopting this technology, leading to more efficient operations, improved communication, and ultimately, a competitive edge in the market. Embracing cloud video solutions is a strategic move.
Scalability and Flexibility
One of the primary advantages of cloud video platform is their scalability. Businesses can effortlessly scale their video management needs up or down based on current demand without the need for significant upfront investments in hardware. This flexibility is crucial in adapting to business growth or changes without incurring additional costs or delays. Moreover, it allows companies to efficiently manage resources and respond promptly to evolving market conditions.
Accessibility and Reach
With a cloud video platform, videos can be accessed from anywhere, at any time, on any device with internet access. This global accessibility ensures that employees in different locations can easily participate in training sessions, meetings, and collaborations without the need for physical travel, further enhancing productivity across the organization. Additionally, it allows for seamless integration of remote and on-site teams, fostering a more connected and efficient workplace.
Enhanced Collaboration
A cloud video platform facilitates enhanced collaboration among teams by providing features such as real-time sharing, editing, and communication tools. These integrated features enable teams to work together more effectively, even when members are spread across various geographic locations. This real-time interaction significantly aids in quicker decision-making and problem-solving, ensuring that projects progress smoothly and efficiently regardless of physical distances.
Cost-Effectiveness
Moving to a cloud video platform can significantly reduce costs related to video content management. By leveraging cloud services, businesses eliminate the need for expensive on-premise infrastructure. Additionally, the maintenance and upgrading of systems are handled by the service provider, which can further decrease IT expenses. Furthermore, cloud platforms offer scalable solutions that allow businesses to pay only for the resources they use, optimizing budget allocation.
Security and Compliance
Security is a top concern for any business leveraging digital tools. The cloud video platform is equipped with robust security measures, including data encryption, secure access controls, and compliance with international standards. These features ensure that sensitive content remains protected against unauthorized access and breaches. Additionally, regular security audits and updates further enhance the platform's ability to safeguard valuable data, providing businesses with peace of mind and confidence in their digital security.
Improved Content Management and Analytics
A cloud video platform also offers advanced content management systems, allowing businesses to efficiently organize, manage, and retrieve video content with ease. Additionally, these platforms provide insightful analytics on viewer engagement, content performance, and other key metrics. This data-driven approach enables businesses to make informed decisions to optimize their video strategies, enhance viewer experience, and ultimately drive better results in their video marketing efforts.
Implementing Cloud Video Platform: Considerations and Best Practices
Implementing a cloud video platform yields significant benefits, but its success hinges on strategic planning and factor consideration. Vital elements encompass selecting an appropriate platform, meeting bandwidth needs, prioritizing user adoption tactics, and upholding data governance policies. These measures collectively shape a robust foundation for seamless integration and optimized performance.
Choosing the Right Platform
Selecting the appropriate cloud video platform is critical and should be based on specific business needs such as feature requirements, scalability, security, and compatibility with existing systems. Businesses should conduct thorough research or consult with experts to find the best fit.
Ensuring Adequate Bandwidth
Effective video streaming requires sufficient bandwidth. Before implementation, businesses need to assess their internet bandwidth to ensure smooth video playback and uploading capabilities without disrupting other business operations.
Focusing on User Adoption
To maximize the benefits of cloud video platform, promoting user adoption through training and support is essential. Employees need to understand how to use the platform efficiently and be comfortable with its features to fully leverage its capabilities.
Adhering to Data Governance
Businesses must also consider data governance when implementing cloud video platform. Ensuring that the platform complies with relevant laws and regulations regarding data privacy and protection is crucial.
Conclusion
The adoption of a cloud video platform can bring transformative benefits to businesses, fostering better communication and collaboration, providing scalability and flexibility, enhancing content management and analytics, reducing costs, and bolstering security. By leveraging cloud technology, organizations can streamline their operations and improve efficiency. Moreover, these platforms enable seamless remote work, support real-time collaboration, and offer advanced tools for data-driven decision-making. With careful planning and consideration of the key factors outlined above, organizations can effectively implement and use these platforms to achieve substantial business success, ensuring they stay competitive in an increasingly digital and connected world. please don’t hesitate to contact us via email or phone for further assistance!
#cloud video platform#secure video hosting#streaming video hosting#encrypted video hosting#drm encrypted video streaming#encrypted video streaming#DRM software#video hosting#security video#video platforms#online video platform#video watermark#DRM protected content#video cdn#wide vine#online courses#e-learning platforms#influencers#paid online courses#E-Learning Solutions#Digital content
2 notes
·
View notes
Text
made my own encryption program all by myself ^^
#it's in C and i have not learned to take the training wheels off in my course which means my code won't work anywhere but vs code#as it makes use of the cs50.h library to get the string input from the user#but still. i get to use it for myself#🌙rambling#oh the encryption is one of those with the key
3 notes
·
View notes
Text
Oh _lovely_. Everyone go turn this off:
Enhanced Visual Search in Photos allows you to search for photos using landmarks or points of interest. Your device privately matches places in your photos to a global index Apple maintains on our servers. We apply homomorphic encryption and differential privacy, and use an OHTTP relay that hides [your] IP address. This prevents Apple from learning about the information in your photos. You can turn off Enhanced Visual Search at any time on your iOS or iPadOS device by going to Settings > Apps > Photos. On Mac, open Photos and go to Settings > General.
24K notes
·
View notes
Text
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
The Family Educational Rights and Privacy Act (FERPA) is a federal law that protects the privacy of student education records. For educational institutions, ensuring FERPA compliance is not just a legal obligation; it's a crucial aspect of building trust with parents and students. Choosing the right school management software can significantly simplify the process of maintaining compliance and safeguarding sensitive student data.
Understanding FERPA Compliance
FERPA grants parents and eligible students certain rights regarding their education records. These rights include:
The right to inspect and review their education records.
The right to request amendments to their education records.
The right to control the disclosure of personally identifiable information (PII) from their education records.
Non-compliance with FERPA can lead to severe penalties, including loss of federal funding. Therefore, selecting a school management system with robust security features and a commitment to data privacy is paramount.
MeraSkool: A FERPA-Compliant Solution
MeraSkool.com offers a comprehensive school management solution designed with FERPA compliance in mind. Our platform incorporates multiple layers of security to protect student data, including:
Data Encryption: MeraSkool employs advanced encryption techniques to protect student data both in transit and at rest.
Access Control: Our system uses role-based access control (RBAC), ensuring that only authorized personnel have access to sensitive information. This prevents unauthorized access and maintains data integrity.
Regular Security Audits: We conduct regular security audits and penetration testing to identify and address any potential vulnerabilities.
Data Backup and Recovery: MeraSkool provides robust data backup and recovery mechanisms to ensure data availability in case of any unforeseen circumstances. This safeguards against data loss and ensures business continuity.
Compliance Certifications: We are actively pursuing relevant compliance certifications to further demonstrate our commitment to data security and privacy. (Note: Specific certifications should be listed here if available).
AI-Powered Insights and Data Security: MeraSkool leverages AI to optimize tasks and provide insights for operational efficiency, while robust data security protocols ensure privacy and regulatory compliance. (Learn More)
Key Features for FERPA Compliance
Several features within MeraSkool directly contribute to FERPA compliance:
1. Secure Student Management:
MeraSkool's student management module (learn more) allows schools to manage student enrollment, maintain detailed profiles, track attendance, and generate grade reports securely. The system ensures only authorized personnel can access sensitive student information, maintaining confidentiality.
2. Controlled Access to Records:
Our platform provides granular control over access to student records, ensuring that only authorized individuals—parents, teachers, and administrators—can view the appropriate information. This prevents unauthorized disclosure of PII.
3. Secure Fee Management:
MeraSkool's fee management module (learn more) supports creating fee structures, generating invoices, and enabling secure online payments. This functionality maintains financial transparency while securing sensitive financial data.
4. Robust Reporting and Analytics:
MeraSkool's reporting and analytics capabilities provide valuable insights into student performance, attendance, and other key metrics. This data is accessed through secure channels, adhering to FERPA guidelines.
5. Audit Trails:
(Note: If available, mention the existence and functionality of audit trails in MeraSkool. Audit trails record all actions performed on student data, providing a valuable tool for monitoring and ensuring accountability.)
6. Powerful Printable system:
MeraSkool offers a powerful printable system (learn more) allowing for secure downloading and printing of marksheets, results, ID cards, fee receipts, and other essential documents. This functionality helps maintain accurate records while ensuring data remains secure.
Additional Benefits of MeraSkool
Beyond FERPA compliance, MeraSkool provides numerous other benefits for schools:
Exam & Assignment Management: Create, schedule, and manage exams with different question formats. (Learn More)
Timetable and Attendance Management: Automated attendance tracking and timetable creation. (Learn More)
Realtime Notification: Realtime notifications powered by WhatsApp bot. (Learn More)
World-Class Support: 24/7 support and a 7-day new feature delivery commitment. (Learn More)
Simple to Use UI & UX: Intuitive design and seamless user experience. (Learn More)
Easy Onboarding with Excel Upload: Effortless integration and seamless transition. (Learn More)
MeraSkool's Commitment to Data Privacy
MeraSkool is committed to providing a secure and compliant platform for schools. We understand the importance of protecting student data and are dedicated to continually improving our security measures to meet the evolving demands of FERPA and other relevant regulations.
Contact us today to learn more about how MeraSkool can help your school maintain FERPA compliance and streamline its operations.
Note: This information is for general guidance only and does not constitute legal advice. Consult with legal counsel to ensure your school's full compliance with FERPA.
#FERPA compliance#school management software#student privacy#data security#MeraSkool#educational software#online learning#school administration#data encryption#access control#security audits#FERPA regulations#data protection
0 notes
Text
How to Use Telemetry Pipelines to Maintain Application Performance.
Sanjay Kumar Mohindroo Sanjay Kumar Mohindroo. skm.stayingalive.in Optimize application performance with telemetry pipelines—enhance observability, reduce costs, and ensure security with efficient data processing. 🚀 Discover how telemetry pipelines optimize application performance by streamlining observability, enhancing security, and reducing costs. Learn key strategies and best…
#AI-powered Observability#Anonymization#Application Performance#Cloud Computing#Cost Optimization#Cybersecurity#Data Aggregation#Data Filtering#Data Normalization#Data Processing#Data Retention Policies#Debugging Techniques#DevOps#digital transformation#Edge Telemetry Processing#Encryption#GDPR#HIPAA#Incident Management#IT Governance#Latency Optimization#Logging#Machine Learning in Observability#Metrics#Monitoring#News#Observability#Real-Time Alerts#Regulatory Compliance#Sanjay Kumar Mohindroo
0 notes
Text
Enhancing Privacy and Security in Data Collaboration with PETs

In today’s digital world, data collaboration is a need for innovation, business growth, and research. However, while organizations and industries are more and more sharing data to create AI models or conducting market research, the risk of leakage of sensitive information increases. Today, privacy and security concerns are much higher due to increasing data breaches and strict privacy regulations. To address these challenges, PETs have emerged as an important technological tool for securing data collaboration to protect individual and organizational privacy.
What is Privacy Enhancing Technologies (PETs)?
Privacy Enhancing Technologies (PETs) are a range of tools and techniques that work towards the protection of an individual’s and organizations’ privacy when they need to share information to achieve some form of cooperation or collaboration. By applying cryptographic and statistical techniques, PETs prevent any unauthorized access to sensitive information without hindering its usefulness for analysis and decision-making.
These technologies are critical in today’s data-driven world, where organizations need to collaborate across borders and sectors, yet still have to abide by strict data privacy laws such as the General Data Protection Regulation (GDPR) and California Consumer Privacy Act (CCPA).
How PETs Enhance Privacy and Security in Data Collaboration
Secure data collaboration requires that organizations can share insights and knowledge without exposing raw or sensitive data. PETs facilitate this by employing a variety of privacy-preserving techniques:
1. Homomorphic Encryption: Computing on Encrypted Data Homomorphic encryption would allow computations to be done on data that is encrypted, ensuring that data can stay encrypted while undergoing processing and analysis. At no point in the process, therefore, is sensitive data exposed, even when data is being analyzed or manipulated.
Example: In healthcare, the organizations can collaborate on medical research using encrypted patient data so sensitive information such as medical history or personal identifiers are not disclosed.
2. Federated Learning: Collaborative AI Without Data Sharing This facilitates decentralized data without the raw need to share between parties while training machine learning models together. The model will learn locally on each of these datasets, and it is only the updates from this model that are being shared, hence preserving privacy within the underlying data.
Example: Financial institutions can develop algorithms that detect fraud without exposing personal banking data of customers so as to maintain data privacy, with a reduced risk of breaching them.
3. Differential Privacy: Safeguarding Individual Data in Aggregated Insights Differential privacy introduces statistical noise in datasets to preserve the presence of individual data points in a way that it’s still possible to get informative insights. In other words, the addition or subtraction of a single data point should not greatly alter the final outcome.
Example: A tech company may find user behavior to enhance their product features without letting any person know about the activities related to his/her personal behavior.
4. Secure Multi-Party Computation (SMPC): Joint Computation Without Revealing Data SMPC is a type of computation that allows two or more parties to compute a joint function without any party revealing its individual data inputs. Each party holds its data private, and the computation is performed in a way that no party gets access to the other’s data.
Example: Two pharmaceutical companies can jointly analyze the results of clinical trials to discover new drug combinations without exposing proprietary data or patient information.
5. Zero-Knowledge Proofs (ZKP): Verifying Information Without Disclosing Data A zero-knowledge proof is a method by which one party can prove to another that a statement is true without revealing the underlying data. ZKPs support verification without exposing sensitive information or confidential information.
Example: a financial institution can prove its client’s creditworthiness without revealing any details on the client’s transactions and financial history.
The Benefits of PETs for Secure Data Collaboration
PETs offer several key advantages for organizations involved in data collaboration:
1. Stronger Privacy Preserving PETs make sure that data is not shared with anyone and still get analyzed in a collaborative way. Even through homomorphic encryption, federated learning, or any other cryptographic techniques, information could be kept safe from unprivileged accesses.
2. Complies with Regulations With increasing stringent data privacy regulations, organizations must be sure of adhering to laws like GDPR and CCPA. PETs enable organizations to fulfill such legal requirements, ensuring individual privacy and making sure that data is processed compliantly.
3. Data Security in Collaborative Environments In whatever form-whether it be a joint research project or a cross-organizational partnership-PETs help safeguard the data exchanges by preventing access to the data during collaboration. This is particularly essential for industries like healthcare, finance, and government, which are extremely sensitive to the fallout from breaches of data.
4. Trust and Transparency This would help organizations create trust among customers and partners by indicating that they have a sense of security and privacy in their information. This would positively influence brand reputation and promote long-term relationships with the stakeholders involved.
5. Innovation Not at the Expense of Privacy PETs allow for the innovation of using data in business without compromising privacy. Organizations are then able to harness the value of shared data without jeopardizing customers’ or employees’ sensitive data.
Real-World Applications of PETs in Data Collaboration
1. Healthcare: PETs allow hospitals and medical research institutions to collaborate on clinical trials and health data analysis without exposing patient records, thus maintaining privacy while advancing medicine.
2.Financial Services: Banks and financial institutions use PETs to detect fraudulent activities and share risk assessments without compromising customer information.
3. Government: Government agencies use PETs to share data across borders for policymaking or disaster response efforts, but with the assurance that citizen information is protected.
4. Retail and E-Commerce: Companies can share consumer behavior data across brands to enhance product offerings while respecting consumer privacy.
Challenges and Future of PETs in Data Collaboration
While PETs present robust privacy protection, deploying them is not without its challenges. Implementing these technologies is quite difficult for some organizations because their complexity, computational intensity, and the need for special technical expertise make them challenging. Another challenge is ensuring interoperability across different PETs and platforms.
However, as concerns over privacy grow, so will the demand for PETs. The future of secure data collaboration is going to be driven by innovations in quantum-safe encryption, AI-driven privacy solutions, and blockchain-based data sharing models, making PETs more powerful and accessible.
Conclusion
Privacy Enhancing Technologies (PETs) are playing a critical role in changing the way organizations share data. PETs will help organizations unlock the full value of their data while at the same time mitigating the risks associated with privacy breaches through secure and privacy-preserving data sharing. In this respect, PETs will be critical in ensuring that data collaboration remains secure, compliant, and privacy focused as the digital landscape continues to evolve.
0 notes
Text
people will really do anything other than learn about IRC eh?


#internet relay chat is likely older than you#it is what most chat apps build themselves off of; in many ways discord was always just a reskinned irc app that spies on you#irc is already free / decentralized#with just a bit of technical know how; you can host your own secure server and chat#irc can be encrypted#irc allows you to upload/download files#irc can run on just about anything; again been around since 1988#maybe learn to not trust things like spyware-ass discord and start learning to control more of your own real time comms?
16K notes
·
View notes
Text
5 Important Areas to Focus On While Creating a Mobile App - Technology Org
New Post has been published on https://thedigitalinsider.com/5-important-areas-to-focus-on-while-creating-a-mobile-app-technology-org/
5 Important Areas to Focus On While Creating a Mobile App - Technology Org
The demand for mobile apps continues to increase with every passing day. Even though there are thousands and millions of different mobile apps available, the need for new mobile apps is still there. Developing a mobile app is not an easy process, as it requires taking care of certain things before the app is fully functional. Although there are many things that an app developer has to take care of before launching the app, here are 5 important areas to focus on while creating a mobile app.
Using a smartphone – artistic impression. Image credit: Mike Jones via Pexels, free license
Clear Goals and the Target Audience
While you are starting the process of app development, it is important that you lay out goals that you want to achieve, establish precise objectives, and determine the target market. Most people are able to establish the app’s goal and what problems it intends to solve in society, but they overlook the importance of the intended audience. Since you are creating an application for users, you should keep your intended audience in mind and build your app accordingly.
Having clarity regarding the target audience can shape your development process and ensure that you are developing your app according to the needs and preferences of the target audience, which will ultimately make the app a success.
Platform
Before you start developing your app, one very important thing that you need to focus on and clarify is which platform your app is intended for. Whether it will be a download for android only app or will it be available for iOS and Android both. Every mobile platform has its own unique requirements, specifications, and guidelines that must be fulfilled. Similarly, the developers of Android and iOS are quite different from each other, as both platforms have different app development requirements.
So while you have a groundbreaking idea that can take over the market by storm, it is important that you tune the app perfectly for the selected platform(s) in terms of performance, responsiveness, design, and compatibility.
App Design
Design is one of the most important aspects of any mobile application because it plays a huge role in selling the application to the audience. The design of your mobile app depends upon your target market, the platform which you will develop the app for, the features that the app will have, and the pricing of the app. Having an appealing design, especially one that is appealing to your target audience, can make a huge difference in determining the success of the app.
Nowadays, whether an app is paid or free, it must be well-designed and can catch the attraction of modern-day tech-savvy users. Most users prefer simple yet sleek designs that are easy to navigate and sticking to such a design can make a huge difference in determining the success of the app. Dream11 is a mobile app that has gained a lot of attention because of its modern sleek design. You can download Dream11 for free from the Play Store and App Store.
Security and Privacy
Mobile users share all sorts of their data with mobile apps and sometimes, this data can include sensitive information like banking information or credit card information. App developers must be mindful of this and focus on the security and privacy of the mobile app right from the developmental phase of the app. Prioritize the security and privacy of the mobile and implement strong security measures like secure authentication and robust encryption techniques that can keep the user data secure. Plus, follow the specific data protection laws and comply with the regulations to ensure the safety of user information.
App Store Guidelines and Submission Criteria
Most people make the mistake of developing an app without considering the app store guidelines and submission criteria. After you have finalized the platform for which you will be developing the app, learn about the submission criteria and guidelines for the specific app stores such as Apple App Store for iOS and Google Play Store for Android. Your app will only be published on these app stores if it follows the specific guidelines and submission requirements. Therefore, ensure that it is something that you take care of from the start and your app complies with these requirements and criteria.
#android#app#app development#app store#apple#apps#attention#authentication#banking#credit card#data#data protection#Design#Developer#developers#development#easy#encryption#Features#focus#Google#google play#google play store#guidelines#iOS#it#Learn#mind#Mobile#mobile app
0 notes
Text
The Crucial Importance of Network Traffic Classification for Optimizing Connectivity
Greetings from Solana Networks, the leading source for state-of-the-art Network Traffic Classification solutions. With the ability to discern between dangerous and benign actions, our sophisticated algorithms carefully examine data flows and provide organisations with insights never before possible. We ensure optimal performance and security by decoding complex network behaviours with our cutting-edge technologies. Solana Networks offers customised solutions that are suited to your requirements, whether your goals are seamless network management, threat detection, or compliance adherence. Put your trust in our experience to protect your digital infrastructure from changing threats, increase productivity, and streamline operations. With Solana Networks, discover the possibilities of network intelligence in the future.
Phone: 613-596-2557
E-mail: [email protected]
#Network Traffic Classification#Network Topology Tools#Network Discovery Tools#Network Mapping#Network Topology#Route Analytics#Network Topology Tool#Network Topology Discovery#Network Discovery#Network Discovery Solution#Network Mapping Solution#Network Traffic Monitoring Solution#Network Traffic Monitoring#Lawful Intercept#Encrypted Traffic Classification#Encrypted Network Traffic Classification#Encrypted Traffic Intelligence#Security Machine Learning#Anomaly Detection#Cyber Threat Monitoring#Ddos Attack#Network Security Monitoring#Scada Security#Threat And Risk Assessment#Vulnerability Assessment#Network Troubleshooting
0 notes
Text
HACKER!STEPBRO HEESEUNG (fic out now!!)
pair hacker!stepbro heeseung x reader



MDNI ! NSFW ! Truly Obsessive, psychosexual, dark vibes step bro Heeseung who stalk you. "You’re not scared of me, baby. You’re addicted... Just like me."
hacker!stepbro heeseung who tracks your location 24/7 and pretends not to care when you lie about where you’ve been.
hacker!stepbro heeseung who sees you wearing something new and smiles to himself—because he saw you trying it on in your room last week, through your camera.
hacker!stepbro heeseung who keeps a file of every photo you’ve ever deleted—every nude, every moment you thought no one would see. But Hee did.
hacker!stepbro heeseung who watches you get ready for dates and sends you anonymous texts like, “don’t waste lipstick on someone who won’t make you cry.”
hacker!stepbro heeseung who you dared to hack you—just to tease him, flashing that crazy angle, undressing slow—until he hijacks your screen, darkens your room, and whispers through you mic: "Keep peeling. I want to see every inch before I decide how hard i'll fuck you."
hacker!stepbro heeseung who watches you fuck someone else live through their hacked laptops camera, and sends you messages mid-thrust: “He’s not even close to make you cum. I’d ruin you.”
hacker!stepbro heeseung who you bickered with—so he fucked another girl raw in his dorm with your moans in his AirPods, eyes closed the whole time like she was just a body for you to echo through.
hacker!stepbro heeseung who sends your hookup a virus mid-text so their phone dies before they can confirm plans.
hacker!stepbro heeseung who slowly rewrites your kinks via search suggestions. One day it’s “soft dom...” the next it’s “stepbro makes her beg.” You think it’s your idea. He knows it’s his.
hacker!stepbro heeseung who swapped out your vibrator for a hacked one he controls—so now your orgasms don’t belong to you, they belong to him.
hacker!stepbro heeseung who programmed your vibrator to sync with your webcam activity—so the moment he can enjoy with you.
hacker!stepbro heeseung who has an encrypted file labeled “every time she came” — full of timestamps from every night you touched yourself.
hacker!stepbro heeseung who tracks your cycle and only texts you during ovulation with messages like: “Would you let me breed you if I asked nicely? Or do I need to ruin you for anyone else first?."
hacker!stepbro heeseung who doesn’t sleep. Doesn’t need to. Not when you keep your curtains cracked, and your thighs parted, and your breathing shallow at 1:22 a.m.
hacker!stepbro heeseung who lets you date other guys—but only so he can hack them, stalk them, and wait until they slip up. Then he sends you the evidence like a love letter. “See? I protect what’s mine.”
hacker!stepbro heeseung who watches you masturbate and types “slower” into your open Notes app. And almost cum when you actually listen.
hacker!stepbro heeseung who learned the way your breathing changes before you come and trained his own body to sync to it—until you finish together, apart, every single time.
hacker!stepbro heeseung who knows you touched yourself wearing his hoodie and rewatches the footage every night—hand wrapped tight on his dick, whispering “you filthy little sister.”
hacker!stepbro heeseung who buys you lingerie and mails it anonymously to the house—no card, just your size, your taste… and the scent of his cologne already soaked in.
hacker!stepbro heeseung who fucks girls mean when he’s mad at you—gripping too tight, biting too hard, fucking too deep.
hacker!stepbro heeseung who lets a girl ride him—face blank, screen lit—while your live shower feed plays like his personal porno.
hacker!stepbro heeseung who you tried to escape—so he pinned you to the bed, forcing you to watch your crush hacked laptop when he's gaming, as he fucked you hard, growling, "Let him hear how good you sound when you’re mine."
hacker!stepbro heeseung who you called a creep—yet now you sit with legs parted in front of your screen, waiting, aching, praying the webcam light will flicker.
hacker!stepbro heeseung who you told to stop—yet you started dressing for him. Walking slower in front of his door. Leaving your webcam uncovered. Secretly hoping he couldn’t stop.
hacker!stepbro heeseung who corrupted you so gently, so thoroughly, that now when he types "Be good. Leave the door unlocked tonight," you obey. Without question. Without panties.
hacker!stepbro heeseung who you tried to forget—but he replaced your lock screen with a photo of you on your knees, mouth open, eyes glazed—and captioned it: "My good little stepwhore."
hacker!stepbro heeseung who forced you to admit it—fingers buried inside you, voice low and dangerous: "Say it. Say you want to be my dirty little stepsister. Say you like it when I ruin you."
hacker!stepbro heeseung who finally snapped—after weeks of playing nice—dragged you to his room, stripped you down in front of your own hacked camera, and fucked you, whispering, "You belong to me. I’ve owned you since the first time you came here."

Will be out on sunday 15.06 I just know you’re gonna love it... almost as much as you’ll be slightly terrified by it. Because, well, the topic is a teensy bit... let’s say... intrusive.
Reblog, comment, scream into the void—give this post the attention it craves! Be bold. Be nosy. I dare you. 😘
yours dearly, Lassiie
#enhypen smut#enhypen x female reader#enha smut#enha hard hours#enhypen x reader#heeseung x you#heeseung x yn#heeseung smut#enhypen imagines#heeseung hard hours#heeseung hard thoughts#smut#kpop smut#heeseung drabbles#heeseung headcanons#heeseung hard imagines#heeseung audio#lassiie's writting#lassiie's#dark romance#stepbro!heeseung#stepbrother
1K notes
·
View notes
Text
Reliable video hosting with encryption features
In the digital era, video content is king, but ensuring its security is paramount. This comprehensive guide explores the world of reliable video hosting with encryption features, providing you with the knowledge to safeguard your valuable content.

Understanding Reliable Video Hosting:
Video hosting is the backbone of online content delivery. From streaming services to business presentations, choosing a reliable hosting platform is crucial. The added layer of encryption ensures that your videos are protected from unauthorized access and piracy.
Key Features of Reliable Video Hosting:
Encryption Protocols:
Dive deep into advanced encryption protocols.
Learn how they keep your videos secure during transmission and storage.
Content Delivery Networks (CDN):
Explore the role of CDNs in ensuring smooth video streaming.
Understand how they enhance the viewer experience globally.
User Authentication:
Delve into user authentication features.
Discover how to control access and protect your content.
Advantages of Encryption in Video Hosting:
Protection Against Piracy:
Encryption acts as a powerful deterrent against content piracy.
Safeguard your intellectual property and maintain exclusivity.
Secure Transmission:
Ensure that your videos are transmitted securely.
Maintain the integrity of your content from upload to playback.
FAQs:
Q1: Why is video encryption essential for my content?
A1: Video encryption ensures that your content remains confidential and is not susceptible to unauthorized access.
Q2: Can encryption affect video streaming speed?
A2: Modern encryption techniques are designed to have minimal impact on streaming speed, ensuring a seamless viewing experience.
Q3: How can I choose the right video hosting platform for my needs?
A3: Consider factors such as encryption features, scalability, and user authentication options when selecting a hosting platform.
Conclusion:
In conclusion, reliable video hosting with encryption features is a non-negotiable aspect of content management. Protect your videos, build trust with your audience, and elevate your online presence. Embrace the power of encryption and unlock a new level of content security.
Now that you've garnered insights into the best practices for secure video hosting, take a plunge into the intricate world of video content protection by visiting our website. Dive into comprehensive guides, glean expert tips, and stay abreast of the latest advancements in video hosting security with Inkrypt Videos.
Your videos merit the utmost protection, and we're here to shepherd you through every step, Amplify your content security and deliver an unparalleled viewing experience for your audience.
0 notes
Text
AI-Powered Real Estate: How to Stay Ahead of the Competition
Artificial intelligence (AI) is transforming the real estate industry, with numerous benefits and applications. AI in real estate has a bright future, from improved property valuation to AI-powered virtual property tours. However, implementing AI in real estate presents its own set of challenges, including concerns about data privacy and integration with existing systems. Despite these obstacles,…

View On WordPress
#AI#Ai in real estate#anonymization#artificial intelligence#cyber threats#cybersecurity awareness#data governance#data privacy#encryption#estate#faster#insightful#machine learning#machine learning algorithms#real estate#real-time#reliable
0 notes
Text
Ethera Operation!!
You're the government’s best hacker, but that doesn’t mean you were prepared to be thrown into a fighter jet.
Bradley "Rooster" Bradshaw x Awkward!Hacker! FemReader
Part I


This was never supposed to happen. Your role in this operation was simple—deliver the program, ensure it reached the right hands, and let the professionals handle the breaching.
And then, of course, reality decided to light that plan on fire.
The program—codenamed Ethera—was yours. You built it from scratch with encryption so advanced that even the most elite cyber operatives couldn’t crack it without your input. A next-generation adaptive, self-learning decryption software, an intrusion system designed to override and manipulate high-security military networks, Ethera was intended to be both a weapon and a shield, capable of infiltrating enemy systems while protecting your own from counterattacks in real-time. A ghost in the machine. A digital predator. A weapon in the form of pure code. If it fell into the wrong hands, it could disable fleets, and ground aircraft, and turn classified intelligence into an open book. Governments would kill for it. Nations could fall because of it.
Not that you ever meant to, of course. It started as a little experimental security measure program, something to protect high-level data from cyberattacks, not become the ultimate hacking tool. But innovation has a funny way of attracting the wrong kind of attention, and before you knew it, Ethera had become one, if not the most classified, high-risk program in modern times. Tier One asset or so the Secret Service called it.
It was too powerful, too dangerous—so secret that only a select few even knew of its existence, and even fewer could comprehend how it worked.
And therein lay the problem. You were the only person who could properly operate it.
Which was so unfair.
Because it wasn’t supposed to be your problem. You were just the creator, the brain behind the code, the one who spent way too many sleepless nights debugging this monstrosity. Your job was supposed to end at development. But no. Now, because of some bureaucratic nonsense and the fact that no one else could run it without accidentally bricking an entire system, you had been promoted—scratch that, forcibly conscripted—into field duty.
And your mission? To install it in an enemy satellite.
A literal, orbiting, high-security, military-grade satellite, may you add.
God. Why? Why was your country always at war with others? Why couldn’t world leaders just, you know, go to therapy like normal people? Why did everything have to escalate to international cyber warfare?
Which is how you ended up here.
At Top Gun. The last place in the world you wanted to be.
You weren’t built for this. You thrive in sipping coffee in a cosy little office and handling cyber threats from a safe, grounded location. You weren’t meant to be standing in the halls of an elite fighter pilot training program, surrounded by the best aviators in the world—people who thought breaking the sound barrier was a casual Wednesday.
It wasn’t the high-tech cyberwarfare department of the Pentagon, nor some dimly lit black ops facility where hackers in hoodies clacked away at keyboards. No. It was Top Gun. A place where pilots use G-forces like a personal amusement park ride.
You weren’t a soldier, you weren’t a spy, you got queasy in elevators, you got dizzy when you stood too fast, hell, you weren’t even good at keeping your phone screen from cracking.
... And now you were sweating.
You swallowed hard as Admiral Solomon "Warlock" Bates led you through the halls of the naval base, your heels clacking on the polished floors as you wiped your forehead. You're nervous, too damn nervous and this damned weather did not help.
"Relax, Miss," Warlock muttered in that calm, authoritative way of his. "They're just pilots."
Just pilots.
Right. And a nuclear warhead was just a firework.
And now, somehow, you were supposed to explain—loosely explain, because God help you, the full details were above even their clearance level—how Ethera, your elegant, lethal, unstoppable digital masterpiece, was about to be injected into an enemy satellite as part of a classified mission.
This was going to be a disaster.
You had barely made it through the doors of the briefing room when you felt it—every single eye in the room locking onto you.
It wasn’t just the number of them that got you, it was the intensity. These were Top Gun pilots, the best of the best, and they radiated the kind of confidence you could only dream of having. Meanwhile, you felt like a stray kitten wandering into a lion’s den.
Your hands tightened around the tablet clutched to your chest. It was your lifeline, holding every critical detail of Ethera, the program that had dragged you into this utterly ridiculous situation. If you could’ve melted into the walls, you absolutely would have. But there was no escaping this.
You just had to keep it together long enough to survive this briefing.
So, you inhaled deeply, squared your shoulders, and forced your heels forward, trying to project confidence—chin up, back straight, eyes locked onto Vice Admiral Beau "Cyclone" Simpson, who you’d been introduced to earlier that day.
And then, of course, you dropped the damn tablet.
Not a graceful drop. Not the kind of gentle slip where you could scoop it back up and act like nothing happened. No, this was a full-on, physics-defying fumble. The tablet flipped out of your arms, ricocheted off your knee, and skidded across the floor to the feet of one of the pilots.
Silence.
Pure, excruciating silence.
You didn’t even have the nerve to look up right away, too busy contemplating whether it was physically possible to disintegrate on command. But when you finally did glance up—because, you know, social convention demanded it—you were met with a sight that somehow made this entire disaster worse.
Because the person crouching down to pick up your poor, abused tablet was freaking hot.
Tall, broad-shouldered, with a head of golden curls that practically begged to be tousled by the wind, and, oh, yeah—a moustache that somehow worked way too well on him.
He turned the tablet over in his hands, inspecting it with an amused little smirk before handing it over to you. "You, uh… need this?"
Oh, great. His voice is hot too.
You grabbed it back, praying he couldn't see how your hands were shaking. “Nope. Just thought I’d test gravity real quick.”
A few chuckles rippled through the room, and his smirk deepened like he was enjoying this way too much. You, on the other hand, wanted to launch yourself into the sun.
With what little dignity you had left, you forced a quick, tight-lipped smile at him before turning on your heel and continuing forward, clutching your tablet like it was a life raft in the middle of the worst social shipwreck imaginable.
At the front of the room, Vice Admiral Beau Cyclone Simpson stood with the kind of posture that said he had zero time for nonsense, waiting for the room to settle. You barely had time to take a deep breath before his voice cut through the air.
“Alright, listen up.” His tone was crisp, commanding, and impossible to ignore. “This is Dr Y/N L/N. Everything she is about to tell you is highly classified. What you hear in this briefing does not leave this room. Understood?”
A chorus of nods. "Yes, sir."
You barely resisted the urge to physically cringe as every pilot in the room turned to stare at you—some with confusion, others with barely concealed amusement, and a few with the sharp assessing glances of people who had no clue what they were supposed to do with you.
You cleared your throat, squared your shoulders, and did your best to channel even an ounce of the confidence you usually had when you were coding at 3 AM in a secure, pilot-free lab—where the only judgment you faced was from coffee cups and the occasional system error.
As you reached the podium, you forced what you hoped was a composed smile. “Uh… hi, nice to meet you all.”
Solid. Real professional.
You glanced up just long enough to take in the mix of expressions in the room—some mildly interested, some unreadable, and one particular moustached pilot who still had the faintest trace of amusement on his face.
Nope. Not looking at him.
You exhaled slowly, centering yourself. Stay focused. Stay professional. You weren’t just here because of Ethera—you were Ethera. The only one who truly understood it. The only one who could execute this mission.
With another tap on your tablet, the slide shifted to a blacked-out, redacted briefing—only the necessary information was visible. A sleek 3D-rendered model of the enemy satellite appeared on the screen, rotating slowly. Most of its details were blurred or omitted entirely.
“This is Blackstar, a highly classified enemy satellite that has been operating in a low-Earth orbit over restricted airspace.” Your voice remained even, and steady, but the weight of what you were revealing sent a shiver down your spine. “Its existence has remained off the radar—literally and figuratively—until recently, when intelligence confirmed that it has been intercepting our encrypted communications, rerouting information, altering intelligence, and in some cases—fabricating entire communications.”
Someone exhaled sharply. Another shifted in their seat.
“So they’re feeding us bad intel?” one of them with big glasses and blonde hair asked, voice sceptical but sharp.
“That’s the theory,” you confirmed. “And given how quickly our ops have been compromised recently, it’s working.”
You tapped again, shifting to the next slide. The silent infiltration diagram appeared—an intricate web of glowing red lines showing Etherea’s integration process, slowly wrapping around the satellite’s systems like a virus embedding itself into a host.
“This is where Ethera comes in,” you said, shifting to a slide that displayed a cascading string of code, flickering across the screen. “Unlike traditional cyberweapons, Ethera doesn’t just break into a system. It integrates—restructuring security protocols as if it was always meant to be there. It’s undetectable, untraceable, and once inside, it grants us complete control of the Blackstar and won’t even register it as a breach.”
“So we’re not just hacking it," The only female pilot of the team said, arms crossed as she studied the data. “We’re hijacking it.”
“Exactly,” You nodded with a grin.
You switched to the next slide—a detailed radar map displaying the satellite’s location over international waters.
“This is the target area,” you continued after a deep breath. “It’s flying low-altitude reconnaissance patterns, which means it’s using ground relays for some of its communication. That gives us a small window to infiltrate and shut it down.”
The next slide appeared—a pair of unidentified fighter aircraft, patrolling the vicinity.
“And this is the problem,” you said grimly. “This satellite isn’t unguarded.”
A murmur rippled through the room as the pilots took in the fifth-generation stealth fighters displayed on the screen.
“We don’t know who they belong to,” you admitted. “What we do know is that they’re operating with highly classified tech—possibly experimental—and have been seen running defence patterns around the satellite’s flight path.”
Cyclone stepped forward then, arms crossed, his voice sharp and authoritative. “Which means your job is twofold. You will escort Dr L/N’s aircraft to the infiltration zone, ensuring Ethera is successfully deployed. If we are engaged, your priority remains protecting the package and ensuring a safe return.”
Oh, fantastic, you could not only feel your heartbeat in your toes, you were now officially the package.
You cleared your throat, tapping the screen again. Ethera’s interface expanded, displaying a cascade of sleek code.
“Once I’m in range,” you continued, “Ethera will lock onto the satellite’s frequency and begin infiltration. From that point, it’ll take approximately fifty-eight seconds to bypass security and assume control."
Silence settled over the room like a thick cloud, the weight of their stares pressing down on you. You could feel them analyzing, calculating, probably questioning who in their right mind thought putting you—a hacker, a tech specialist, someone whose idea of adrenaline was passing cars on the highway—into a fighter jet was a good idea.
Finally, one of the pilots—tall, broad-shouldered, blonde, and very clearly one of the cocky ones—tilted his head, arms crossed over his chest in a way that screamed too much confidence.
“So, let me get this straight.” His voice was smooth, and confident, with just the right amount of teasing. “You, Doctor—our very classified, very important tech specialist—have to be in the air, in a plane, during a mission that has a high probability of turning into a dogfight… just so you can press a button?”
Your stomach twisted at the mention of being airborne.
“Well…” You gulped, very much aware of how absolutely insane this sounded when put like that. “It’s… more than just that, but, yeah, essentially.”
A slow grin spread across his face, far too entertained by your predicament.
“Oh,” he drawled, “this is gonna be fun.”
Before you could fully process how much you already hated this, Cyclone—who had been watching the exchange with his signature unamused glare—stepped forward, cutting through the tension with his sharp, no-nonsense voice.
“This is a classified operation,” he stated, sharp and authoritative. “Not a joyride.”
The blonde’s smirk faded slightly as he straightened, and the rest of the pilots quickly fell in line.
Silence lingered for a moment longer before Vice Admiral Beau Cyclone Simpson let out a slow breath and straightened. His sharp gaze swept over the room before he nodded once.
“All right. That’s enough.” His tone was firm, the kind that left no room for argument. “We’ve got work to do. The mission will take place in a few weeks' time, once we’ve run full assessments, completed necessary preparations, and designated a lead for this operation.”
There was a slight shift in the room. Some of the pilots exchanged glances, the weight of the upcoming mission finally settling in. Others, mainly the cocky ones, looked as though they were already imagining themselves in the cockpit.
“Dismissed,” Cyclone finished.
The pilots stood, murmuring amongst themselves as they filed out of the room, the blonde one still wearing a smug grin as he passed you making you frown and turn away, your gaze then briefly met the eyes of the moustached pilot.
You hadn’t meant to look, but the moment your eyes connected, something flickered in his expression. Amusement? Curiosity? You weren’t sure, and frankly, you didn’t want to know.
So you did the only logical thing and immediately looked away and turned to gather your things. You needed to get out of here, to find some space to breathe before your brain short-circuited from stress—
“Doctor, Stay for a moment.”
You tightened your grip on your tablet and turned back to Cyclone, who was watching you with that unreadable, vaguely disapproving expression that all high-ranking officers seemed to have perfected. “Uh… yes, sir?”
Once the last pilot was out the door, Cyclone exhaled sharply and crossed his arms.
“You realize,” he said, “that you’re going to have to actually fly, correct?”
You swallowed. “I—well, technically, I’ll just be a passenger.”
His stare didn’t waver.
“Doctor,” he said, tone flat, “I’ve read your file. I know you requested to be driven here instead of taking a military transport plane. You also took a ferry across the bay instead of a helicopter. And I know that you chose to work remotely for three years to avoid getting on a plane.”
You felt heat rise to your cheeks. “That… could mean anything.”
“It means you do not like flying, am I correct?”
Your fingers tightened around the tablet as you tried to find a way—any way—out of this. “Sir, with all due respect, I don’t need to fly the plane. I just need to be in it long enough to deploy Ethera—”
Cyclone cut you off with a sharp look. “And what happens if something goes wrong, Doctor? If the aircraft takes damage? If you have to eject mid-flight? If you lose comms and have to rely on emergency protocols?”
You swallowed hard, your stomach twisting at the very thought of ejecting from a jet.
Cyclone sighed, rubbing his temple as if this entire conversation was giving him a migraine. “We cannot afford to have you panicking mid-mission. If this is going to work, you need to be prepared. That’s why, starting next week you will train with the pilots on aerial procedures and undergoing mandatory training in our flight simulation program.”
Your stomach dropped. “I—wait, what? That’s not necessary—”
“It’s absolutely necessary,” Cyclone cut in, his tone sharp. “If you can’t handle a simulated flight, you become a liability—not just to yourself, but to the pilots escorting you. And in case I need to remind you, Doctor, this mission is classified at the highest level. If you panic mid-air, it won’t just be your life at risk. It’ll be theirs. And it’ll be national security at stake.”
You inhaled sharply. No pressure. None at all.
Cyclone watched you for a moment before speaking again, his tone slightly softer but still firm. “You’re the only one who can do this, Doctor. That means you need to be ready.”
You exhaled slowly, pressing your lips together before nodding stiffly. “Understood, sir.”
Cyclone gave a small nod of approval. “Good. Dismissed.”
You turned and walked out, shoulders tense, fully aware that in three days' time, you were going to be strapped into a high-speed, fighter jet. And knowing your luck?
You were definitely going to puke.
Part 2???
#top gun movie#top gun#top gun maverick#top gun fanfiction#top gun one shot#top gun fluff#bradley bradshaw#bradley rooster bradshaw#rooster bradshaw#bradley bradshaw x reader#bradley bradshaw fanfiction#bradley bradshaw imagine#bradley bradshaw x y/n#bradley bradshaw x you#bradley bradshaw x female reader#bradley bradshaw fic#bradley bradshaw fluff#top gun rooster#rooster fanfic#rooster x reader#rooster top gun#top gun maverick fanfic#top gun maverick fluff#top gun maverick x reader#jake seresin#jake seresin x reader#phoenix x reader#bob x reader#top gun hangman#pete maverick mitchell
2K notes
·
View notes
Text
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
Ensure FERPA Compliance with MeraSkool School Management Software
The Family Educational Rights and Privacy Act (FERPA) is a federal law that protects the privacy of student education records. For educational institutions, ensuring FERPA compliance is not just a legal obligation; it's a crucial aspect of building trust with parents and students. Choosing the right school management software can significantly simplify the process of maintaining compliance and safeguarding sensitive student data.
Understanding FERPA Compliance
FERPA grants parents and eligible students certain rights regarding their education records. These rights include:
The right to inspect and review their education records.
The right to request amendments to their education records.
The right to control the disclosure of personally identifiable information (PII) from their education records.
Non-compliance with FERPA can lead to severe penalties, including loss of federal funding. Therefore, selecting a school management system with robust security features and a commitment to data privacy is paramount.
MeraSkool: A FERPA-Compliant Solution
MeraSkool.com offers a comprehensive school management solution designed with FERPA compliance in mind. Our platform incorporates multiple layers of security to protect student data, including:
Data Encryption: MeraSkool employs advanced encryption techniques to protect student data both in transit and at rest.
Access Control: Our system uses role-based access control (RBAC), ensuring that only authorized personnel have access to sensitive information. This prevents unauthorized access and maintains data integrity.
Regular Security Audits: We conduct regular security audits and penetration testing to identify and address any potential vulnerabilities.
Data Backup and Recovery: MeraSkool provides robust data backup and recovery mechanisms to ensure data availability in case of any unforeseen circumstances. This safeguards against data loss and ensures business continuity.
Compliance Certifications: We are actively pursuing relevant compliance certifications to further demonstrate our commitment to data security and privacy. (Note: Specific certifications should be listed here if available).
AI-Powered Insights and Data Security: MeraSkool leverages AI to optimize tasks and provide insights for operational efficiency, while robust data security protocols ensure privacy and regulatory compliance. (Learn More)
Key Features for FERPA Compliance
Several features within MeraSkool directly contribute to FERPA compliance:
1. Secure Student Management:
MeraSkool's student management module (learn more) allows schools to manage student enrollment, maintain detailed profiles, track attendance, and generate grade reports securely. The system ensures only authorized personnel can access sensitive student information, maintaining confidentiality.
2. Controlled Access to Records:
Our platform provides granular control over access to student records, ensuring that only authorized individuals—parents, teachers, and administrators—can view the appropriate information. This prevents unauthorized disclosure of PII.
3. Secure Fee Management:
MeraSkool's fee management module (learn more) supports creating fee structures, generating invoices, and enabling secure online payments. This functionality maintains financial transparency while securing sensitive financial data.
4. Robust Reporting and Analytics:
MeraSkool's reporting and analytics capabilities provide valuable insights into student performance, attendance, and other key metrics. This data is accessed through secure channels, adhering to FERPA guidelines.
5. Audit Trails:
(Note: If available, mention the existence and functionality of audit trails in MeraSkool. Audit trails record all actions performed on student data, providing a valuable tool for monitoring and ensuring accountability.)
6. Powerful Printable system:
MeraSkool offers a powerful printable system (learn more) allowing for secure downloading and printing of marksheets, results, ID cards, fee receipts, and other essential documents. This functionality helps maintain accurate records while ensuring data remains secure.
Additional Benefits of MeraSkool
Beyond FERPA compliance, MeraSkool provides numerous other benefits for schools:
Exam & Assignment Management: Create, schedule, and manage exams with different question formats. (Learn More)
Timetable and Attendance Management: Automated attendance tracking and timetable creation. (Learn More)
Realtime Notification: Realtime notifications powered by WhatsApp bot. (Learn More)
World-Class Support: 24/7 support and a 7-day new feature delivery commitment. (Learn More)
Simple to Use UI & UX: Intuitive design and seamless user experience. (Learn More)
Easy Onboarding with Excel Upload: Effortless integration and seamless transition. (Learn More)
MeraSkool's Commitment to Data Privacy
MeraSkool is committed to providing a secure and compliant platform for schools. We understand the importance of protecting student data and are dedicated to continually improving our security measures to meet the evolving demands of FERPA and other relevant regulations.
Contact us today to learn more about how MeraSkool can help your school maintain FERPA compliance and streamline its operations.
Note: This information is for general guidance only and does not constitute legal advice. Consult with legal counsel to ensure your school's full compliance with FERPA.
#FERPA compliance#school management software#student privacy#data security#MeraSkool#educational software#online learning#school administration#data encryption#access control#security audits#FERPA regulations#data protection
0 notes