#lookup method injection
Explore tagged Tumblr posts
Text
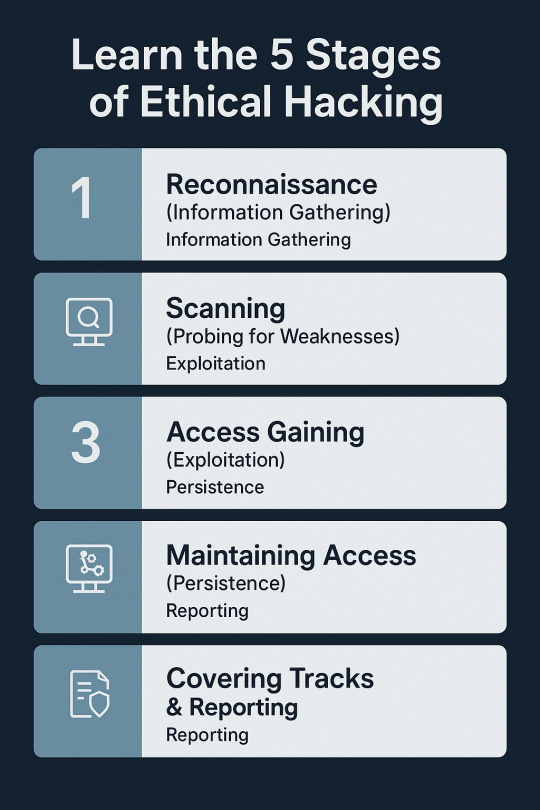
Learn the 5 Stages of Ethical Hacking
With threats on the digital platform ever-present today, ethical hacking has emerged as an essential method for protecting systems, networks, and information. As malicious hackers use vulnerabilities to carry out crime, ethical hackers (or white hat hackers) utilize their craft for good purposes — finding and fixing vulnerabilities before threat actors have the chance to do so. But ethical hacking is not a random process. It follows a methodical process to make every step legal, efficient, and in accordance with the security goals of the organization. This process is typically in five stages, which are very specific and trace ethical hackers from reconnaissance to reporting. Let us dive into detail about what these stages involve and why they're crucial for a successful cyber defense strategy. Phase 1: Reconnaissance (Information Gathering) Also known as: Footprinting Reconnaissance is the first and, arguably, the most important phase of ethical hacking. It's akin to the "research" phase. Ethical hackers find out as much as they can about the target before they try to break into it. This phase lays the groundwork for everything that follows. Aims: •Get familiar with the digital footprint of the target •Identify weak spots and vulnerable entry points • Steal away undetected while gathering information Methods Used: • Passive Reconnaissance – No contact with the target (e.g., use of WHOIS lookup, DNS records, social media, public databases). • Active Reconnaissance – Direct contact with the system (e.g., ping sweeps, port scanning, traceroutes). Tools: •Maltego •Nmap •Recon-ng •Google Dorking Why it matters: Proper reconnaissance saves time and makes the rest of the hacking process easier. It also replicates the first steps taken by real-world cyber attackers.
Phase 2: Scanning (Probing for Weaknesses) After the ethical hacker has sufficient surface information, scanning is the next phase where more intensive probing is done to identify particular vulnerabilities in the system. Objectives: • Discover open ports and services • Detect live systems • Identify running OS and applications • Discover known vulnerabilities
Methods: • Port Scanning – Scanning which ports are open and what services are running.
• Network Mapping – Knowledge of the network topology and the identification of the hosts. • Vulnerability Scanning – System scanning for known configuration or software vulnerabilities. Tools: • Nessus • Nikto • OpenVAS • Wireshark Why it matters: Scanning gives the hacker a technical snapshot of how healthy the system is and assists the hacker in determining which vulnerabilities to exploit during the exploitation phase.
Phase 3: Access Gaining (Exploitation) This is where ethical hacking really gets to work and occurs. The hacker attempts to break into the system by taking advantage of the weaknesses revealed in the scanning. It sounds like the climax, but it's a very choreographed and strategic move that makes ethical hacking. Objectives: • Use a known exploit to gain access • Increase privileges (for example, from guest to admin) • Identify the amount of potential damage that an actual perpetrator might do Methods • Buffer overflow attacks • tSQL injection • Brute-force password cracking • Misconfiguration exploitation Tools: • Metasploit • Hydra • John the Ripper • SQLMap Why it matters: Access that is gained allows organizations to see how much access an attacker would have, giving them a chance to cut off critical points of access before damage is being caused.
Phase 4: Maintaining Access (Persistence) During this phase, the ethical hacker mimics what an actual attacker would do once they have compromised the system — maintain access to keep gathering data or installing malware. Objectives: •Create backdoors or remote access tools •Mimic advanced persistent threats (APT) •Illustrate long-term risk exposure Methods: •Installing Trojans or rootkits (ethically and with permission) •Creating rogue user accounts •Altering system services for covert access Tools: •Netcat •Backdoor Factory •MSFVenom Why it matters: This stage assists in determining how long a system might remain compromised undetected — an important consideration when analyzing incident response measures. Phase 5: Covering Tracks & Reporting While malicious hackers attempt to cover their tracks, ethical hackers do the opposite — they make sure all actions taken are logged, traced, and completely documented. Reporting is the last and possibly most useful step of the ethical hacking process.
Goals: • Restore the system to normal • Report to the organization • Deliver remediation steps that are actionable What's in the Report: • Disclosed vulnerabilities • Attacks tried and success rates • Possible impact of each vulnerability • Fix recommendations and improvements Why it matters: The final-report is a blueprint that the organization can use to make its defenses harder. It transforms an ethical hack from a test into an actionable business tool.
The Legal and Ethical Side It's important to emphasize: Ethical hacking should be done with the right permission. That is, written permission, well-delineated scope, and test boundaries. Unapproved hacking—no matter what "noble cause"—is against the law and punishable by it. Why the 5 Phases are Important Together, these five phases create a repeatable, effective cycle of security testing. They: •Echo the methods of actual attackers •Detect potential threats prior to exploitation •Enhance organizational cybersecurity stance •Meet standards such as ISO/IEC 27001, PCI-DSS, etcFinal Thoughts Ethical hacking is not merely about cracking open systems—it's about learning them, enhancing them, and helping to make the internet a more secure place. From IT managers to aspiring cybersecurity analysts to entrepreneurs, recognizing the five stages of ethical hacking can assist you in making better, more secure decisions. With increasing cybercrime, ethical hacking is no longer a choice — it's a necessity. And as with any strategic process, its success depends on how systematically and responsibly it's carried out.
Website: https://www.icertglobal.com/course/ceh-certification-training/Classroom/62/3044
0 notes
Text
Preventing Command Injection in Laravel Applications
Introduction
Command injection is a critical security vulnerability that occurs when an application executes system commands constructed with unescaped user input. In Laravel applications, this can lead to unauthorized command execution, compromising the server's integrity and security. Understanding how to prevent command injection is essential for maintaining a secure application environment.

Understanding Command Injection
Command injection vulnerabilities arise when user input is improperly handled, allowing attackers to execute arbitrary system commands.
For instance, consider the following Laravel controller method:
use Illuminate\Http\Request; class DomainController extends Controller { public function verifyDomain(Request $request) { $domain = $request->input('domain'); exec('whois ' . $domain); } }
In this example, the verifyDomain method takes user input from the request and appends it directly to the exec function, which executes the whois command. If an attacker provides a malicious input, such as example.com; rm -rf /, it could lead to the deletion of critical files on the server.
Preventing Command Injection
To mitigate command injection risks in Laravel applications, consider the following best practices:
1. Input Validation
Validate user inputs to ensure they conform to expected formats. For example, if expecting a domain name, use Laravel's validation rules:
use Illuminate\Http\Request; use Illuminate\Support\Facades\Validator; class DomainController extends Controller { public function verifyDomain(Request $request) { $validator = Validator::make($request->all(), [ 'domain' => 'required|regex:/^[a-zA-Z0-9.-]+\.[a-zA- Z]{2,}$/', ]); if ($validator->fails()) { return response()->json(['error' => 'Invalid domain name'], 400); } $domain = $request->input('domain'); // Safe execution } }
2. Escape Shell Arguments
Use PHP's built-in functions to escape shell arguments:
$domain = escapeshellarg($request->input('domain')); exec('whois ' . $domain);
The escapeshellarg function ensures that the user input is safely escaped, preventing command injection.
3. Avoid Direct Command Execution
Whenever possible, avoid executing system commands with user input. Instead, use native PHP functions or libraries that provide the desired functionality.
For instance, instead of using the whois command, consider using a PHP library to perform WHOIS lookups.
Integrating Security Tools
Regularly scanning your Laravel application for vulnerabilities is crucial. Tools like the Free Website Security Scanner can help identify potential security issues. By entering your website URL and email address, you can receive a comprehensive report detailing vulnerabilities and recommendations for remediation.

Screenshot of the free tools webpage where you can access security assessment tools.
After scanning your website with our free tool to check Website Vulnerability, you'll receive a detailed vulnerability assessment report. This report highlights areas of concern and provides actionable steps to enhance your application's security.
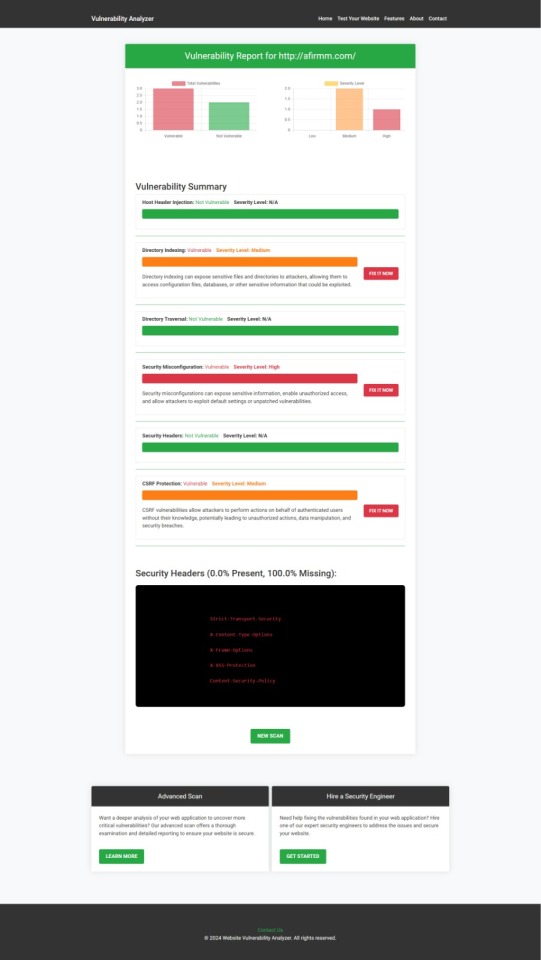
An Example of a vulnerability assessment report generated with our free tool, providing insights into possible vulnerabilities.
Conclusion
Preventing command injection in Laravel applications requires diligent input validation, proper escaping of shell arguments, and minimizing direct command execution. Regular security assessments, such as those provided by the Website Security Checker, are essential to maintain a secure application environment.
For more insights into cybersecurity and pen-testing, visit the Pentest Testing Corp blog.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php
1 note
·
View note
Text
What are the best practices for handling form validation in a web application
Master Form Validation: Best Practices for Web Applications
The cost of poor user experience is staggering, with studies showing that 70% of users abandon forms due to errors. Effective form validation is crucial for delivering a seamless experience, ensuring both data integrity and enhanced security. This article outlines essential best practices for handling form validation in web applications.
Client-Side Validation: The First Line of Defense
JavaScript's Role
JavaScript plays a vital role in creating a responsive user experience. By using it for client-side validation, developers can provide immediate feedback. Common techniques include:
Regular Expressions: Validate email addresses and other patterns.
Length Checks: Ensure fields like passwords meet minimum requirements.
For example, a simple regex for emails could look like this:const regex = /^[^\s@]+@[^\s@]+\.[^\s@]+$/; const isValidEmail = regex.test(emailInput.value);
HTML5's Built-in Validation
HTML5 offers built-in attributes that simplify form validation. With attributes such as required, pattern, min, and max, developers can quickly add basic validation rules. For instance:<input type="text" required pattern="[A-Za-z]{2,}">
This input requires at least two letters, providing a quick validation method.

Enhancing UX with Real-time Feedback
Providing clear and helpful error messages is essential for guiding users. A well-designed error message could state, “Please enter a valid email address. Example: [email protected].” This approach helps users understand what went wrong.
Server-Side Validation: The Crucial Second Layer
Why Server-Side Validation is Essential
Client-side validation is only the first step. It can be bypassed easily, making server-side validation critical for security and data integrity. If server-side checks are not in place, malicious users can manipulate data.
Choosing the Right Server-Side Validation Technique
When it comes to server-side validation, different approaches exist:
Using Frameworks: Many web frameworks like Python's Django or Node.js's Express offer built-in validation tools.
Custom Functions: Developers can write tailor-made validation functions for specific needs.
For instance, in Express, you might validate an email like this:const express = require('express'); const app = express(); app.post('/submit', (req, res) => { if (!validateEmail(req.body.email)) { return res.status(400).send('Invalid Email'); } });
Data Sanitization
Sanitizing user inputs before processing them on the server is a must. This practice protects against harmful injections, ensuring that only safe data is handled.
Advanced Validation Techniques
Asynchronous Validation
Asynchronous validation can handle tasks that require external lookups, such as checking for duplicate emails or verifying credit card numbers. For example, an API call can validate an email's uniqueness in real-time.
Custom Validation Rules
Creating custom validation rules allows handling complex scenarios unique to specific applications. This could involve defining a rule that ensures a specific range of dates for an event.
Integrating with Third-Party Services
Integrating third-party services for verification can boost reliability. Services for address verification or payment processing provide added security and user trust.
Best Practices for Error Handling and User Experience
Providing Clear and Concise Error Messages
Clear error messages help users. Instead of vague messages like “Input error,” use specific guidance, such as “Password must be between 8 and 16 characters.”
Implementing User-Friendly Feedback Mechanisms
Visual cues enhance the user experience. Color-coded input fields or icons can indicate errors even before submission. For example, a red border around a field signals an issue effectively.
Accessibility Considerations
Ensuring accessibility is vital. Implementing forms that are screen-reader friendly and compliant with WCAG guidelines helps accommodate users with disabilities. This includes using ARIA roles and ensuring keyboard navigability.
Maintaining and Testing Form Validation
Automated Testing
Automated testing frameworks are invaluable for validating form functionality. Tools like Jest or Mocha can run tests to ensure validation rules work as intended.
Regular Code Reviews
Regular team code reviews are crucial. They catch potential validation errors early, ensuring the system remains robust and user-friendly.
Monitoring and Logging
Setting up monitoring for form submissions can highlight common errors, allowing for ongoing improvements. Logging provides insight into how users interact with forms, guiding necessary adjustments.
Conclusion: Building Robust and User-Friendly Forms
Mastering form validation is essential for any successful web application. By focusing on client-side and server-side validation, using advanced techniques, and enhancing user experience, developers can create forms that not only function well but also delight users.
Start implementing these best practices today to strengthen your forms and improve overall application performance. Keeping an eye on future trends, such as AI-powered validation, will further enhance your approach to form validation.
0 notes
Text
#Wait why on earth is there a lookup table after?#What??#And it's not injective?#What game is this and why?
it is injective*. 36 entries on the table, 36 possible outcomes of rolling two dice. it doesn't cover every number between 1 and 66, obviously, so I guess in that sense it's not surjective. but that doesn't matter too much, because presumably you are not putting entries on the table for the number 8.
it'd be significantly weirder if there wasn't a lookup table, i think, imagine if someone was treating that result as a number. horrifying
multiple games use this, not that i've played any that i recall. the method is fine for random tables it's the nomenclature that's offensive to my aesthetics
*or at least it can be, nothing stops you from putting the same entry on the table at two positions if you want.
using 'roll d66' for 'roll two six sided dice, assign the first to the tens digit and the second to the ones digit, and compare to this table with 36 entries labelled correspondingly' is just personally offensive. how dare you use your notation inconsistently with the convention that dN is a sample drawn from a uniform distribution of every integer between 1 and N inclusive.
potential solutions:
come up with new notation. i would be partial to something like d6 X d6
call it a d36 and make everyone do d6 * 6 + d6 - 6 in their heads every time, it's fine, don't worry about it.
51 notes
·
View notes
Text
Interior Design Suggestions to Make The Residence Contemporary and Fashionable
Wish to give your home areas a fresh and trendy really feel? Properly, first you need to locate relevant interior design concepts matching your construction as well as its geometry within a excellent way. Furthermore, the style you lookup has got to improve the feel of the house and inject a breath of fresh existence into it. You just can't just pick any furniture and decorations expecting those to enhance the spaces into trendy and modern. Rather, you need to find a real style that mixes aesthetics and features jointly to work for the spots. Here are interior design suggestions to have the residence modern and fashionable - Select the great colour scheme Colours will have a huge position to experience when making a house appear modern day, or older, as you may pick. So, the focus should be selecting the color scheme that is cool. Simply a right colour can let you receive the best furnishings to the inside. You can't choose the white-colored and plan to create the decorations trendy mainly because it won't. Quite, you must choose a colour which fits effectively together with the design and appearance of your home furniture. Contemporary decors generally use well developed down shades and that motto has to be implemented for sure.

Minimalism with fabric and texture For house owners, it's crucial that you not blunder with all the consistency and textile employed in the furnishings. The truth is, the feel for your furniture is going to be crucial because it for other considerations and accessories throughout the house. The fabric and texture should be picked to combine very easily into the history. In the same manner, it'd fantastic to choose materials which can be neutral and therefore don't seem so evident towards the eyeballs. The focus should be on trying to keep the truly feel from the interior simplified since this is only feasible when an method of minimalism is then the fabric. Steer clear of lavish decorations and accessories The thumb tip in planning a fashionable and modern interior is usually to reduce lavish and colorful adornments. Homeowners must refuse for any accessories that set stress on your eyes. Quite, the main focus must be employing goods created from see-by means of supplies or of alloys to produce a relax surroundings inside the decoration. The design should be minimalist at finest so that a modern and elegant feel from the decoration can be achieved. In the same manner, it's very good to make use of things that are significantly less to seize focus and more to offer a purchase in the home. Use even more of natural and greener components Design ideas for contemporary homes are definitely more about making use of natural and greener components and much less about gravitating to showy products or extras. The target is to obtain a tone of character in the house which can only be achievable by using a sensible style strategy. For example, far more solid wood components and furniture are utilized than ever before, along with the classical green carpets and rugs are back into reckoning once again. Metal items are more in furniture and demand are getting customized like never before. More info about komplektuyushchiye dlya svetil'nikov go our web page.
1 note
·
View note
Text
Fist of Fire.2.19. The End pt.1
“......progress is coming along remarkably in the…”
Eyes begin to move in the darkness. Ears start to pick up voices.
“...yes sir, she has been injected with the blood. No, we don’t know if the process will..”
Every vein bulged with effort to move, paining with each centimetre shuffled.
“.....Yes, sorry, yes we will have her ready by tomorrow. Thank you, Lord.”
The sound of an old analog phone being hung up with a loud thunk fills the black nothingness that is Jade’s reality.
Bright lights start the make their way into her eyesight, only to be filled once again with pure tar.
The voice that she heard earlier was now hovering over her, the warmth of their body being so close to hers would have made her cringe if not for the restraints and liquid ice she felt in her veins.
“No, no you can’t be awake just yet. Just a few more days until you are all ...swapped out.”
The voice was of a German accent, but that was all Jade could recall as the touch of pointed steel stabbed into her skin and once more she was gone.
----------------------------------------------------------------------------------------------------------------------------
The airplane cabin vibrated with a constant drone. It was the fourth that Joseph Ellington had been seated in during the last five days, and he has been growing angrier every hour. Not only because of the general garbage experience of airplane flight in business or coach, but because he had to use this method at all.
The night that Jade was taken from him, he had Omegaman take him immediately to the hero agency center in the city. And he demanded he be allowed to go get her back. And for the first time in his hero career, he was laughed at. The admin had looked at Joseph and laughed at him. He said that they would send someone when they had the chance. That a single kidnapping was not the biggest deal of the agency at the moment. And, for icing on the cake, they would be sure to send someone who could walk. They could do a better job than the broken man before him.
Omegaman had to physically hold Joseph back from the attendant, who very quickly realized after a quick lookup of his name who he was talking to. The only respite that Joseph had in that moment of unrestrained rage that only the number 1 in the nation could hold him back was seeing the color drain from the admin’s face.
Still.
His condition and previous violations of property laws had meant not only was his Hero License revoked in its entirety, he couldn’t have gone even if it wasn’t. Omegaman had promised Joseph he would make this top priority. He looked him in the eyes and said, “I will not let her go, Joseph. I will not let Emesh take her from you. And I will not let injustice continue.” After that, Omegaman shot into the sky, presumably in the direction of Emesh’s hideout.
There has been zero contact since that night.
Of course, Joseph was not going to follow any directions. The night he was laughed at and rejected, after Omegaman shot up and away, he wheeled himself alone to the home of Mary Laurens. She opened the door to him and asked if Jade was at Riley’s, as she was not with him. Joseph’s silence at her question answered more than she asked for. A grieving mother, worried about her only child’s life, was another weight put upon Joseph’s mind. No, no he would not follow the orders of any administration. He had only done so once, and that was to a great man. There were no good men in bureaucracy.
And so that night, while the weeping and sobbing of a mother hurt filled his ears, Joseph Ellingston packed his bags. Clothes for the night, clothes for the Desert. For stealth. Gear for protection.
Clothes for her.
As his bags were packed, and he was about to roll out the door, a knock came.
He opened the door, bags slung across the back of his wheelchair, to see Riley standing before him. Still dressed in her white undershirt and dress pants. Still blood on the front. Carrying a bag in her off hand, and a long box in the other.
“No. No you are not going.” Joseph knew what she was here for instantly, and he would not allow it to happen. “I am not going to lose two students. I am not going to let you throw your life away on this, It is illegal for you to accompany me on this, you know that right? What will your parents think? They are going to be terrified when their daughter doesn’t come home for who knows how long.”
Riley just stood there, staring down Joseph. Her face stayed bold and determined, though she said nothing.
“I know how you feel Riley, but this isn’t going to happen. You are still a student. You don’t even have your provincial license yet. What you are doing, if you are caught, could send you away for life. Not even to mention how dangerous it is. Do you even know who we’re fighting? Because I don’t. It certainly isn’t Emesh, like everyone thinks it is. I should know. It's someone far worse.”
Riley still just stood there.
“Riley , if you don’t move right now I will call your parents, the school, the police whatever. You will not come. There is nothing you can do or say that will convince me otherwise.” Just as he said that, Riley tossed him the long box under her arm. It landed with a heavy thud at the bottom of his wheelchair. He gave it a curious look, before returning to the determined eyes of Riley. His own were fighting a battle of will. For even though he wanted all the help he could get, he could not rely on any other for this. Especially not a child.
But then she spoke.
“My father works for the medical field. He created personalized devices. You were my favorite hero growing up, and in doing so I made him a fan of yours as well. I went to all your signings you did when you came down here. When I told him who the new Hero combat teacher was, he almost cried with enjoyment. He was devastated at your death, relieved at your survival, but crushed again at your immobility.” Her eyes darted to the wheelchair quickly before returning. “So he got to working, thinking. And eventually, he made this. He was planning to give it to you after a few bugs were worked out. However, I took it from his lab a few minutes ago.”
Joseph, face still set and stern, was turned curious as he listened. He looked at the long box, and thought to himself. This couldn’t possibly be…
He bent over and threw off the top of the box to reveal…
“The only stipulation of you keeping these is that I come with you.”
Joseph Ellington looked up at Riley, but his face had changed from its former aggression to one of shock. And a small grin at the edges.
“Atleast get changed first.”
----------------------------------------------------------------------------------------------------------------------------
That had been five days ago. Riley sits next to Joseph on the plane, though she is asleep. Joseph on the other hand stays awake, to think. How is this plan going to work out? Are they really just going to walk in and leave with Jade? How deep does it go? He remembers Omegaman’s info, about the caverns of space they have below them. Jade could be held in theoretically any crack in the wall. No, they would need information first.
Joseph’s hands rubbed his knees, the phantom pain still there from months ago when his legs were shorn from his body. But that won’t hold him back anymore. His body aches when thinking about the upcoming battle. Even though he hopes for a clean entrance and exit, deep down he knows that is nothing but a pipe dream. The years have finally caught up to him, going on more than twenty straight years of nail biting action and tough ground work, the strain on his body was acceptable due to his quirk. But the months of inactivity has finally allowed all of that to return.
His final fight approaches, and this time there won’t be a miraculous survival if he dies.
But that doesn't matter right now. He needs to focus on saving Jade. Like he promised to do.
A couple of hours later, after Joseph had been thinking long and hard on the approach, Riley awoke to the plane beginning it’s touchdown. She was dressed in pure sweats and a pair of black converse shoes. She still groans when she sits up, migraines becoming a common visitor in her head after being hit in the head. “We’re here. The final stretch. Riley, this is your last chance to turn back.”
She doesn’t turn to face Joseph. “I owe it to her. I need to do this.”
Joseph didn’t say anything, but Riley saw out the side of her eyes that he nodded.
The Pilot’s voice came over the intercom announcing their arrival to the McCarran International Airport, Nevada. Riley stood up to grab her bags from the overhead storage as the other passengers began to stand and leave for the door. “Do you want me to get your bags?” Riley asked.
“No, I can get them myself.” And at that Joseph stood up and grabbed his duffle bag from the overhead, and walked with Riley to the hatch out of the airplane. She looks down at him,”Are they working out well for you?” Joseph and Riley were walking down to the front of the airport, walking to a rental car center that was nearby.
“It's like I never lost them.”
----------------------------------------------------------------------------------------------------------------------------
Jade Laurens woke up to freezing cold water being poured onto her face. The sharp change in temperature and suffocation shocked her brain into throwing her into the world of the awake and living. The sudden bringing about brought an assault of color and noise into her senses. High pitch wails and blinding chromatic orbs of light was all she could feel. The same icy pain was felt in her veins, and any movement brought about a pained response from her body. Her mind was too clouded and drugged to even bring about a response to anything. Which, unbeknownst to her, was a blessing. For when her vision finally cleared, her situation became very apparent.
Chained to a cave wall with iron cuffs, like a prisoner. Her clothes were gone, replaced with a prison jumpsuit. There were no bars infront of her, but why would there be? She has nowhere to go. Her eyes darted from one wall to another, and upon each was filled with more and more fear.
On one end she saw a wall of computers and equipment, organs floating in jars, rows upon rows of gun racks, dozens of people walking around the huge cavern carrying various boxes and specialized equipment. But none of it mattered compared to what she saw in front of her.
A giant ring of metal, easily almost a hundred feet in diameter and height. The ring floated effortlessly in the air, suspended by nothing. In the center of the ring was, by all accounts, a disgrace to natural biology. It looked humanoid, but its attributes were far beyond what man was meant to have. It’s body was small. Too small. It pulsated with the movement of the heart and other organs within. It had too many tubes to count pumping unknown liquids into it. It’s head was the most discomforting though. Long, ballooned into a great size and expanding on what used to be the human skull but was now something more. This was no longer human. This was a brain with a vestige that resembled a person.
“Ah, so you see why I have brought you here. My magnum opus.”
Jade turned her head, the pain shooting within her, to see the golden haired boy who had tried to take her from the games. He stood before her in a baby blue suit, and a yellow neck tie. And in his hand was a cane, though he did not need one. No, this suit was meant to mean something. He drops a bucket to the floor, a small amount of water leaks from the bottom.
“And not a moment too late. Don’t you think it's beautiful?” He turned from her, and gestured to the ring and its occupant. “I do not mean to be so prideful, but so much time and effort it seems a shame to not at least revel in some of it. Of course, you would understand wouldn’t you? Oh wait.”
He flashes her an evil smile.
“You have nothing to be prideful of.”
The boy’s face was no longer sporting the injuries Jade had inflicted upon him at the stadium, looking as if the fight never happened at all.
“So, I expect you’d want to know why you’re here, hm?”
Jade opened her mouth to speak, and was only barely able to speak before being smack across her face with the cane. Her teeth hurt.
“I didn’t want you to really ask it, you know. Your voice annoys and irritates me. Just like your father’s.”
Jade, bruised, looked at the boy with a look of confusion on her face.
“Ah! Yes, you don’t know me in this form. Well,” the boy took three steps backwards and spread his arms wide,”We are Emesh.”
In tandem, all the people moving in the cavern stopped at once and dropped what they were doing. They all turned to face Jade, chained to the wall, and spoke in unison “We are Emesh.”
The Golden Boy laughed, clapping like a giddy child.
“Yes yes! See all those years ago when your father and his team of disgustingly loyal lapdogs foiled my DC plan - oh foiled is such an evil person word! - I had to begin planning a magnificent return! So I hid myself away while Tapout ruined all my connections in the world. But he missed me the whole time.”
The Golden Boy snaps his fingers and all the workers begin moving once more, a well oiled machine. The monster in the ring groaned, shaking the cavern and causing dust to fall upon Jade’s face. The Golden Boy simply brushed his suit off and continued.
“My Research was hidden away, far from the prying eyes of one Victor Laurens and his crew of do-gooders. Oh, I am NASTY with these cliches aren’t I? No, It was too important to keep around them. And for good reason. It allowed me to avoid the same fate as Victor, but oh at what a cost!” He spoke at the end with a fake air of sadness and played it up like a middle school play.
This man has lost it. Jade thought.
“I had to sacrifice so much to keep what I had here, but it worked out in the end! True, my body is no longer what it was then, now only a hub of activity and psychic power. But my mind is the only thing that mattered. My mind was the only thing I needed. I could live without life as it were. My consciousness grew beyond myself!”
It was then Jade realized with a horror what the monster in the ring truly was. It was the decrepit and shriveled body of The Planeteer. He had abandoned his humanity and turned himself into something awful. But why?
“Why? I’ll tell you why!” He spun in a little circle, laughing. “Oh my how I’ve missed this! The body of a young boy really is just pouring out with energy. So much potential here. Of course, the same cannot be said for you. Victor was the peak of heroism, you have barely even scratched the surface of what he could do. This boy was grown to be me, and I must say he works perfectly! That other me? A prototype not worth keeping any more. But why do you ask? Why go through all this?!”
He skipped forward to Jade, did a small hop, and then smacked her face across with his cane once more. Jade then found herself yanked forward by the air itself and facing him. Time and time again he hit her with his cane, making deep bruise markings all over. And each time he laughed a bellowing laugh that shook the cavern.
“BECAUSE”another hit”YOU ARE WHAT REMAINS”a slash across the head”OF THE MAN I DESPISE!” He lets Jade fall back into the cavern wall, a small drop of blood falling from her mouth. The Golden Boy, Emesh, stands there heaving and tightly gripping his cane. “That's why..I will destroy all that he made. In you resides the last of his blood, both real and figuratively.”
He stands up, and spits on Jade. “I replaced your blood with his, to finally get a bit of Revenge on all that remains of him. Sure i killed him but look at me!? Have I not suffered enough that those fucking garbage divers cannot leave me be? No, no this has been a long time coming.”
Jade could hang there in horror as he walked away from her, laughing into the open cavern.
He can turn anyone’s mind into his own. He’s immortal...
A tear rolled down her face as she stared into the lifeless and hollow eyes of the being that used to be The Planeteer. That used to be a young man named Quientin who saved the world countless times. The thing that had killed her father. And now..
“I’m..gonna die here..”
The Golden Boy stopped his retreat, and cocked his back at her.
“My, you’re smarter than I gave you credit for.”
----------------------------------------------------------------------------------------------------------------------------
“Is the car stashed?” Riley nods at Joseph, who looks back through his binoculars.
The desert had turned from its boiling orange sky to its softer and now freezing purple and black. Out here, far from the lights of Las Vegas, the stars peek out from their hiding. They along with the full moon provide ample lightning. Joseph looks at the biker bar at the side of the road, the place Omegaman had spoken of. And he sees the two guards outside, just as he said there would be. He lowers his binoculars and shimmies down the hill he had been laying on.
“Alright, we are going to need to be absolutely secret about this. A quiet entrance, a quick exit. We can be loud when we have her, but until then… silence.” Riley nodded. They duo had changed from their traveling clothes to pure camouflage, desert camo. Underneath were black suits that would allow them to more easily fall into the shadows. Joseph’s pant legs did not fully cover his new legs, so he wrapped his prosthetics in electrical tape.
The two slinked from rock to rock, ever slowly approaching the two guards. Eventually, after crossing the street, in a mad dash when the two armed men outside weren’t looking. Now hiding behind cars in the parking lot of the bar, Joseph turns to face Riley and gives a quick nod. Instantly, she disappears and so do the two men standing in front of the bar. When she returns she looks tired but unhurt.
“How far away?”
“90 miles. Took their phones and their communicators as well.”
Joseph smirks and slowly approaches the bar entrance. As he slowly opens the door and enters, he sees that there is no one in the place. All that is present is an empty and unstocked bar counter, several unoccupied tables and stools, and a silver elevator.
Joseph turns his head to Riley.
“Going down?”
#FoF:og#writing#creative writing#creativewriting#creative#original#original writing#original story#originalwriting#orignal female character#superhero#superhero story
3 notes
·
View notes
Text
Method Injection
Suppose singleton bean A needs to use non-singleton (prototype) bean B, perhaps on each method invocation on A. The container only creates the singleton bean A once, and thus only gets one opportunity to set the properties. The container cannot provide bean A with a new instance of bean B every time one is needed.
SingletonBean class has dependency PrototypeBean class and it having scope as…
View On WordPress
0 notes
Text
Enhance your Business Revenues By way of Applying Video Marketing
Welcome to my Thumbnail Blaster Review and Demo. Top marketing professionals agree that making use of a great video marketing strategy is one of the absolute best issues you can perform to improve your organization. By means of implementing intelligent and even powerful video marketing techniques you will significantly increase both your own personal gross sales and profits. Study on to find out great online video marketing suggestions. Watching prosperous viral videos is the best way to obtain an notion of what creates a video favorite. Remain up to date using new developments, check sociable networks and several websites your target target audience loves and put together a summary of characteristics you recognize inside the viral videos you find. Your own videos will turn out to be well-known if you talk about them efficiently. You ought to create an account online and on various other equivalent internet sites your visitors uses, function your video lessons in your web page as well as website and share all of them upon social networks. If possible, get other people and even people who can be influential on social networks to talk about your videos. Ask your clients to create their unique video lessons. You can for occasion organize a contest in addition to ask customers to picture themselves while they work with your own products. Reward typically the best video lessons with a great interesting reward and make use of the submitted video clips while promotional material for your own social media marketing campaign and for your website. If a person creative super hits together with you get a wonderful idea to get a video, film this when you can in the event that you have the products for this. Granted, getting both expert equipment or staff members may appear like the best route to consider, nevertheless such arrangements might take time. Capture the energy and even essence of an thought when that is clean. Actually a good amateur video clip together with genuineness can outshine a little something expertly polished. Connect frequently with others around your specialized niche. Not merely is this a great way to reveal advice and suggestions, however you can in addition share marketing. A lot of blog owners or webmasters usually enable the posting of benefits by site visitors. When you might get your message out to a new larger client base in your market, you will enjoy more success. Several Internet customers get on-line to study how to execute a job. Movies which are educational will be found simply by folks who want to study that thing, and in the event that it's tied to what you sell, you're fantastic. Household realize you are a great expert, they may trust anyone and purchase your current goods. Begin your online video by way of telling your visitors exactly what you are going to help teach all of them or talk about with them. After thumbnail blaster , stick to through on your guarantee and deliver the content. If you state evidently what exactly you are doing, in addition to then do it, viewers are more inclined to watch your video lessons again. Take into account just precisely how short attention ranges will be online. You have concerning ten seconds in your own personal online video to grab your audience interest. Keep your own total content within two minutes in length to help make the most possible impact. If this does not seem possible so that you have in order to get out there, spread your content across chapter movies. You should end up being honest in your video tutorials. Your audience will determine with you and trust a person if they sense like you are appearing yourself. You should, on the other hand, prevent swearing or saying whatever too personal around your video clips and alter anything you experience does indeed not have its location in your current video. YouTube comment lookup is the great way to seek out video clips on the matter you are intending to use in your next movie. This lets you to see what additional everyone is talking about together with then you can either answer their questions or come up with brand-new information which in turn isn't at the moment being offered. Video training are a great method for you to get touching a much broader market. When people perform not know how to make a move, they have often the trend to check online regarding advice. Having videos the fact that will teach what exactly they want for you to know will make anyone an experienced in their eyes. A new major mistake involving people new to video clip marketing is usually they try to design their own video lessons like a commercial. It is a big turn off. Folks tend not to want to observe commercials troubles computers. Alternatively, try to choose your videos about happenings with your field or events with your current business. Grab the audience's attention early in your current video clips. The key to be able to this is to "pull them in" within the primary 10 seconds of some sort of video clip. You need to do something within this specific timeframe that will get away from them in amazement and even wanting more. After getting their particular attention, you must keep these things engaged by having exciting and critical information in the rest of the video. Online video advertising can look like a difficult nut to crack. It will be much easier to do if anyone inject quite a few humor in to your videos. This can generally entertain your viewers together with keep them coming lower back to get more. Be careful with this strategy and show your videos to others prior to publishing. You could conclude up if she is not funny in addition to making your own personal business search bad. One of the tried in addition to true techniques to video marketing is to use cliffhangers. These people have been used throughout television system from the incredibly beginning and are constantly effective. This will preserve your readers engaged in addition to have them expecting the next video to respond to often the questions raised around the primary online video. Consist of music within your videos. Think about what commercials used in addition to you will see the fact that the best versions have got music in them. Just what music would work around your video? This approach, you'll have a even more enticing and even entertaining online video media that your audiences can enjoy. If you aren't more comfortable with being onscreen, that will likewise help anyone. Try taking the behind the scenes approach in your video marketing campaign. Clients love to observe how a new organization really works, and they'll also appreciate your visibility. Make sure to contain info about exactly how your own business addresses the desires from the consumers and creates their pleasure a number-one priority! Since was explained in the opening up sentence of this article, video marketing plans offer the great way to enhance business enterprise and increase product sales and profits. By meticulously studying the information comprised within the meat regarding this article in addition to applying it, you are positive to start building extraordinary sums of money. Best of luck!
1 note
·
View note
Text
Tips On How To Get To Sidena's Sewing & Alterations, Llc In Albany By Bus?
Moovit helps you discover various routes or occasions. Get directions from and instructions to Sidena's Sewing & Alterations, LLC easily from the Moovit App or Website. Click on the Bus route to see step by step directions with maps, line arrival occasions and updated time schedules. Your date of delivery defines your unique core objective, the rationale in your life. In dwelling your objective, you will find your best happiness, contentment, and success.
The next night I took the full pill and throughout the hour I was exhausting and I awakened my spouse and we had the most effective sex with multiple orgasms. Contact your physician or search sildenafil tablets emergency medical attention in case your erection is painful or lasts longer than four hours. A prolonged erection (priapism) can harm the penis. Do not take Sidena while also taking Sidena, except your physician tells you to.
Unscrambling sidena by way of our highly effective word unscrambler yields 78 totally different words. 78 anagrams of sidena were discovered by unscrambling letters in S I D E N A. Sidney married the love of his life, Altramese Larry on September 17, 2011. Escovedo was last sildenafil ireland in North Highlands, California someday in December 2019 or January 2020.
Supplemental oxygen and descent are the mainstays of treatment. For prevention, Sidena ought to solely be thought of for patients with a history of high-altitude pulmonary edema, especially a number of episodes. The best method to lookup drug information, determine tablets, examine interactions and arrange your own personal medicine data. The Radaris reverse cellphone lookup function is an efficient way of finding your neighbor's name. Alternatively, you'll be able to search for their names using their handle, e mail, or business at radaris.com.
For security causes, you have to reset your password before you'll be able to access the positioning. If an replace is required it'll typically take 3-10 working days to complete. The profile might be taken offline whereas the replace is in progress and your dashboard will present the profile state. Sidena injection is for the continued remedy sildenafil of sufferers with PAH who're currently prescribed oral Sidena and who are briefly unable to take oral medication. Sidena is indicated for the treatment of pulmonary arterial hypertension (WHO Group I) in adults to improve train capability and delay medical worsening.
CLEMENTINE'S is a Toronto-based luxurious idea shop, providing a curated selection of high-end womenswear, lifestyle goods, and wonder and equipment. Founded by industry veteran Christina McDowell, the store shares personally-sourced items from established name manufacturers that draw on McDowell's eye for luxurious goods. CLEMENTINE'S also options common collaborations with contemporary designers for contemporary, but subtle pieces for the modern woman. Your heart’s want is to assist and care for those you're eager on.
Participation is free and the site has a strict confidentiality coverage. Balli mentioned he doesn't think the Soviets had any specific plan to make a capital investment in Mexico. But when Mexico's government decided to promote the tractor plant, it needed to decide whether to put up some capital or threat having future owners discontinue the Soviet tractor fashions sidena tablets being constructed there. Traktoroexport and Massey Ferguson already provide expertise to SIDENA's tractor plant in Ciudad Sahagun, Hidalgo. The peasant federation represents the major customers of the factory's tractors. Tovar said the group fascinated in the tractor division has made a suggestion to Mexico's Banca Serfin.
To allow you to find a selected pin code or area, we present to you a pin code search engine. Now you can search for the pin code of a selected area as nicely sidena as search for the address of anyplace in Sidena space in Hidalgo state of Tepeapulco district in Mexico nation using it's pin code. Took half a 100mg for the first time and I felt nothing.
The tractor is a slight modification of a mannequin that was already being constructed by Traktoroexport, mentioned Genaro Trujillo Alvarez, SIDENA's manager of unique equipment sales. The agreement to build the Mexican version apparently grew out of a 1973 go to to Moscow by then-Mexican President Luis Echeverria, he mentioned. Balli mentioned he does not doubt that some U.S. conservatives will see the Soviet investment as a threat, however others will acknowledge that it's sidena 50mg simply enterprise. "I suppose typically clever people see issues that are not there," he said. This standardised postal handle numbering system utilized by Indian Postal Services was launched to simplify and accelerate everyday mail supply processes. Rolled out nationwide in August 1972, the system is actually quite just like the Zip Codes of the United States or the Postcodes of the United Kingdom.
0 notes
Text
IVF Treatment in Chennai: What You Need to Consider
In the twenty-first century, the place nearly the whole lot is on hand online to discover the proper infertility medical institution and cure in Chennai is no longer an uphill task. However, discovering the proper one that suits your desires can be a bit tricky. Since there are several IVF clinics in Chennai these days, you want to habits a large lookup and ask around earlier than zeroing in on the first-rate IVF health facility in Chennai and its fertility cure packages. Here’s what you want to understand earlier than reserving an appointment with an IVF health center in Chennai.
Check the Reputation of the Fertility Clinic Best fertility hospitals in Chennai are likely the most essential step earlier than you even suppose of traveling to the IVF remedy core in Chennai. The first aspect you want to do is test the popularity of the quality fertility medical institution in Chennai through analyzing on-online and speak me to human beings who have visited the health facility in the past. You can additionally take a look at the credentials of the physicians in your chosen IVF clinic. You can even discover the contact small print of these medical doctors and name them up to ask questions associated with the remedy procedure and typical success costs of the clinic. In India, there are various reputed fertility clinics. However, you want to select accurately due to the fact the recognition of an IVF health center in Chennai can play a big position in deciding the success of your treatment. Why? Well, you want to keep in mind that your whole therapy ride will commence and stop at the fertility clinic. This is the place you will endure a collection of checks and procedures, and additionally the place you will be receiving therapy and monitoring your situation all through the process.
IVF Treatment Cost in Chennai
The value of an IVF treatment in Chennai will rely on a number element of such as the kind of cure you choose, the doctor’s session fee, the price of medication, and the variety of cycles you require. Ideally, an IVF therapy in Chennai has somewhere between Rs. 45,000 and Rs. 1 lakh. However, the precise quantity will be decided as soon as you have visited the sanatorium and mentioned the important points of your cure with the doctor. While you can discover a range of low-cost fertility clinics in Chennai, you want to consider that IVF is now not a less costly proposition. It is one of the most high priced high-priced treatments. Hence, it is constantly advocated that you keep as lots as viable earlier than present the process of IVF. You can even bin a financial savings account to gather the required quantity for your treatment.
Types of ART Procedures and their success rate
Before choosing a specific kind of ART process for your IVF treatment, you want to recognize how every method works and its success rate. – Frozen-thawed embryo transfer: This is a kind of ART technique whereby cryopreserved embryos (frozen embryos) are thawed and transferred to the uterus. This process is advocated for female females who produce a clean embryo or who have had a couple of failed tries with sparkling embryos. – Frozen-thawed embryo switch observed with the aid of ovulation induction: This is a mixture of two ART procedures, whereby frozen-thawed embryos are transferred to the uterus, observed by way of ovulation induction with or barring progesterone supplementation. – Chemically precipitated superovulation: This is an ART manner whereby ovulation is caused with injectable pills like clomiphene citrate (CC). – Natural cycles with IUI: This is a kind of ART system whereby herbal ovulation is allowed, accompanied by using intrauterine insemination (IUI). – Donor embryos: This ART technique entails the use of donor embryos. In this case, the embryos are created in an IVF lab the use through of the eggs and sperm of the couple, or the sperm of the husband, and the eggs and the uterus of a donor.
What to assume from your first go to an IVF clinic
You will be requested to go to the IVF health facility in Chennai for a preliminary appointment to talk about your cure options. This is the place you will be requested about your fitness condition, scientific history, and cure goals. You will additionally be requested to furnish a pattern of your blood and urine for a variety of checks such as blood and urine analysis, sperm count, and ovulation status. During the preliminary appointment, you will be requested to fill out a structure that consists of records about your clinical history, household history, and your lifestyle. The physician will additionally recommend a few checks that you want to bear to rule out any fitness risks. After the checks are done, you will be given a precise report, alongside with hint of your IVF treatment.
Tips for a profitable IVF treatment
Follow the doctor’s instructions: Your medical doctor is the one who is aware of the IVF therapy in Chennai and its intricacies. Hence, you have to comply with his directions and keep an everyday schedule. – Track your health: If you are present process ART treatment, it is vital that you song your fitness and go to the medical doctor regularly. – Stay stress-free: Stress can negatively affect your fitness and treatment, and even lead to infertility. Hence, you should hold your stress stages in check, in particular, whilst the present process of an IVF treatment. – Stay hydrated: Dehydration can additionally expand your stress levels, and, thus, it is essential that you continue to be hydrated all the time. Finally, be mindful that an IVF cure is now not a one-time shot. It is a long ride that requires patience, determination, and an effective outlook on life. And, all through this journey, it is essential that you remain hydrated, take normal breaks, and keep away from stress.
#male fertility center in chennai#best fertility hospital chennai#chennai best fertility hospital#best fertility hospital in chennai#fertility clinic in chennai#best fertility clinic in chennai#icsi treatment in chennai#best ivf treatment in chennai#ivf treatment in chennai#ivf fertility center in chennai
0 notes
Text
Using Custom Neon Signs Is A Proven Way To Assist Make Your Business Glow
When you open up a new store, to possess a tremendous the first things may should do is to create your business known to your public. Many people are excited to try and look out new stores regarding area. Whether you have a beauty salon, an ice cream shop or a grocery store, you are supplying them with a new place or spot to check out on weekends or go out after school or do the trick. Now which have fire place knowledge of LED lights are we works to make a fairer comparison to neon signs as we mention nice points and also the bad points of each of these. The basis for comparison is the of 2 lighting methods in tactics. Other great examples are with motel and restaurant signs. Travelling for extended hours in the biggest market of the night can be very exhausting and travelers always find relief to view motel signs from a far distance so they are get some sleep. Same is true with 24 / 7 restaurants or drive-through signs or symptoms. People are often relieved to view them flashing and searching out the restaurant to get a bite is fairly easy with the guiding neon signs. This is the way a associated with businesses survive through time. As long as discovered that still get people coming in, they're still enterprise. Now, the burning question here is - just how can they have a steady flow of people towards their business? Custom signs use aluminum for giving attractive and bright lookup. These signs are especially made promptly prefer custom web design for their business. The items used to create neon signs will be less than LED sign tutorials. When the raw material is inexpensive then last product are generally inexpensive. Since these are much more affordable 90 portion of business people prefer employ neon signs. Now you can create your own design for neon signs. The bright color of these signs catches attention of people towards your store. These signs require less power for advertisements. Since these are custom made sign they are portable, harmless to environment and may use more than 50 tones. Was Happy Days main tasks favorite shows as had been growing set up? Have you ever wanted to hold out one gang like on Fat? These days it really is to recreate this fun look residence. You might be all out, but you'll be able to create the particular on a budget as surely. Finally, the personal letters are joined together to form a suv for sale. When attached to a power source, if the tubes are injected with neon gas, they will glow red, if argon is used, they will glow blue and if helium is used, they'll probably glow yellow. Make sure customers won't just go by your store. Invite them arrive inside with all the glowing factor of the neon sign outside your store. And with the continuous flow clients in your establishment, you can be without you will surpass appeal of soy risk of failure involving the competitions surrounding your business. Liquid neon is expensive, there is small amounts. The best business signage you can use is neon sign. India has 43 while Norway and Sweden each have 22. Same holds true with a 24-hour cycle of restaurants or drive-through signs or symptoms.
0 notes
Text
Penis Enlargement Approaches And Their Basic safety
Numerous strategies of enlarging a penis are all available around the world with every single of their good results stage. For years gentlemen have been indulging in various approaches of enlarging their penis size. This lookup is due to the simple fact that each and every gentleman would like to prove himself to his female sexually and to satisfy her. Thinking about the numerous strategies of enlarging a penis and their basic safety, some will be described here. one. Penis Enlargement Surgery: This entail the escalating the duration and girth of the penis by carrying out some surgical procedure on the penis. The lengthen can be obtain by chopping the suspensory ligaments that attach the penis to the pubic bone while the girth increase is accomplished simply by injecting liposucted unwanted fat taken from the stomach into the penile shaft. Penis Enlargement Surgical procedure Efficiency: Throughout the healing process, the reverse impact which is penis shortening can occur owing to the strengthen and reduction that happen for the duration of therapeutic. This happens in slight cases only. Penis Enlargement Surgical treatment Safety: Hazards involved in penis medical procedures involves, long term scars, bacterial infections, terribly healing wounds and so on. 2. Penis Pumps: This device functions by drawing large blood volumes into the erectile tissue. This will now end result in the inflammation up of the erectile tissue and then enlarge the penis quickly. Penis Pump Effectiveness: The penis pump technique of enlarging a penis has small impact as it does not make long term enlargement. This is simply because in the course of the pumping session, all-natural blood movement to the penis stops and oxygen is not supplied to the penile tissue. Penis Pump Protection: Utilizing the penis pump to enlarge the penis can cause bruising, breakage of capillaries and blood vessels inside the penis if way too a lot force is applied and the total stop of blood movement to the penis in the course of a session. 3. phallosan forte discount : Unlike penis pumps, penis enlargement tablets enhance blood circulation to the penis and the pills also create intercourse hormones. Penis Enlargement Pills Performance: These pills make your erection a lot more difficult and thicker but unlikely market long lasting enhance in dimensions. Penis enlargement capsules make excellent final results when used with normal penis enlargement pills. Penis Enlargement Pills Security: Frequent penis enlargement components are all protected. But some do contain Yohimbe, a dangerous herb which can lead to fast heart charge, high blood strain and dizziness. Care need to be taken when administering enlargement tablets and anyone located to have Yohimbe herb should be discouraged. 4. Normal Penis Enlargement: The organic penis enlargement method can make use of exercises in enlarging your penis. The exercising is qualified towards increasing the sponge like tissues of the penis and as this tissue increase, the blood capability of the penis develops and this end result to a long lasting enlargement of the penis duration and girth. Natural Penis Enlargement Performance: The most successful way to enlarge penis size completely is via the natural penis enlargement technique. Simply because of the much blood movement to the penis, you will see a great end result following couple of weeks of carrying out the physical exercise. All-natural Penis Enlargement Basic safety: This is certainly the safest method of enlarging a penis. With this technique, you have control of the quantity of stress you implement when exercising.
1 note
·
View note
Text
Comfort and ease may consider you a extended way in your offroad activities
The surplus plastic is actually cut aside and removed from the mold. Disadvantages in order to compression mold include different product regularity and flashing, which is extra material connected to the molded part that needs to be removed where several parts of the actual mold meet. Compression conforms: The plastic is generally preheated is placed into a heated steel mold cavity and pressure is applied to make the plastic to contract and take the shape of the actual mold.. There are two common methods of producing Abs plastic, fiberglass fairing: injection and compression. In the 1960s for that 1990s, small two cerebral vascular accidents for the world of Motorcycle fairings motorcycles experienced already been popular, because of in element for that run from the powerplant could possibly be the German born Walter Kaaden actually although in the 1950s.
For even much more particulars about this article, as well as on Motorcycle fairings only one can acquire an entire superb supply particulars through reviewing the actual above referral internet web-sites or googling the necessary lookup phrase to recognize more.It may be wiser to shell out a little much more on these types of, just to be certain that you get these types of with truly superior quality. The plastic after that cools as well as hardens in the mold. Heat and pressure is stored until the plastic material cures the mold. It gives the the majority of accurate end product that fits well. Try to keep in mind comfort and ease may consider you a extended way in your offroad activities. Amid the prevalent offroad mishaps that motorbike and vehicle drivers often encounter tend to be animal-associated. Would you have to acquire motorcycle fairings?
Fairings for almost any ABS fairings62, fairings pertaining to Yamaha fairings, Honda fairings as well as a Kawasaki motorbike? Here at neverland-motor we share an huge broad range associated with motorcycle add-ons and our range of motorcycle add-ons is actually each inexpensively priced as well as comprehensive, making certain individuals attempting to uncover Motorbike Aftermarket parts, motorcycle add-ons with regard to by themselves or even loved types and good friends Plastic Pet Molds for sale can appear throughout one thing suitable. Deer and other animals animals frequent the offroads, as well as collisions with them are at occasions unavoidable.
With handful of exceptions, the dwelling of modern mass made motorcycles has standardised on the steel frame as well as suspension light weight aluminum fork holding the entrance steering wheel and disc brakes.The motorcycle structure could possibly be the architectural, production and assembly of factors and products for just about any motorcycle that last leads to all round performance reselling price as well as aesthetics favored over the custom. Shot molds: ABS plastic is melted and shot into mold cavity.Fairings nonetheless, consist of precisely the dashboard or even windscreen collectively with fairings throughout the best lighting. Constant pressure is used to allow for materials shrinkage. Additionally, be positive that you get gears that youll be comfy wearing. Shot molds enables uniform width throughout the entire piece.
0 notes
Text
DNS Cache Poisoning: Why Is It Dangerous for Your Business
What is DNS Cache Poisoning

DNS cache poisoning, also known as DNS spoofing, is a cyber-attack that exploits the weaknesses in the Domain Name System (DNS) servers. It enables the attacker to poison the data in DNS servers, including your company server, by providing false information to your internet traffic and diverting it to fake servers. This is done by redirecting the data in DNS to their IP address.
DNS cache poisoning utilizes the vulnerabilities in the DNS protocols' security to divert internet traffic away from legitimate servers to the wrong address.
DNS cache poisoning is effectively used for phishing attacks, often referred to as Pharming, for spreading malware. In the background, the malware runs and connects with legitimate servers to steal sensitive information.
When the DNS server is attacked, users may be requested to login into their accounts, and the attacker finds its way to steal the sensitive and financial credentials.
Moreover, phishing attacks also install viruses on the client's computer to exploit the stored data for long-term access.
How Does DNS Cache Poisoning Works
DNS spoofing is a threat that copies the legitimate server destinations to divert the domain's traffic. Ignorant of these attacks, the users are redirected to malicious websites, which results in insensitive and personal data being leaked.
It is a method of attack where your DNS server is tricked into saving a fake DNS entry. This will make the DNS server recall a fake site for you, thereby posing a threat to vital information stored on your server or computer.
The cache poisoning codes are often found in URLs sent through spam emails. These emails are sent to prompt users to click on the URL, which infects their computer.
When the computer is poisoned, it will divert you to a fake IP address that looks like a real thing. This way, the threats are injected into your systems as well.
What Are the Different Stages of Attack of DNS Cache Poisoning

First Stage
The attacker proceeds to send DNS queries to the DNS resolver, which forwards the Root/TLD authoritative DNS server request and awaits an answer.
Second Stage
The attacker overloads the DNS with poisoned responses that contain several IP addresses of the malicious website.
To be accepted by the DNS resolver, the attacker's response should match a port number and the query ID field before the DNS response.
Also, the attackers can force its response to increase their chance of success.
Third Stage
If you are a legitimate user who queries this DNS resolver, you will get a poisoned response from the cache, and you will be automatically redirected to the malicious website.
How to Detect DNS Cache Poisoning
Now that we know what is DNS cache poisoning let's understand how to detect it.
One way is to monitor the DNS server for any change in behavior patterns. Also, you can apply data security to DNS monitoring.
Another way is to look for a potential birthday attack. This occurs when there is a sudden increase in DNS activity from a single source in a single domain. When there is an increase in the DNS activity from a single source, querying your DNS server for multiple domain names without recurring shows that the attacker is looking for a DNS entry for poisoning.
Monitor the file system behavior and active directory events for any abnormal activities. You can use analytics for correlating activities among three vectors to add important information to your cybersecurity strategy.
Why Is DNS Cache Poisoning Dangerous for Your Business
When the DNS server is poisoned, it will start spreading towards other DNS servers and home routers. Computers that lookup DNS entries will get the wrong response by causing more users to end up as victims of DNS poisoning.
This issue will be resolved only when the poisoned DNS cache is cleared on each affected DNS server; you are at risk of losing your precious information until then.
One of the major reasons DNS cache poisoning is highly dangerous is that it can spread from one DNS server to another.
Here are a few DNS poisoning attack examples-
A DNS poisoning event had resulted in the Great Firewall of China's temporary escape from China's national borders by censoring the internet in the USA till the problem was resolved.
Recently, attackers targeted WikiLeaks, who used a DNS Cache poisoning attack for hijacking traffic to their WikiLeaks-like version. This intentional attack was created to divert the traffic away from WikiLeaks and was implemented successfully.
How To Protect Against DNS Cache Poisoning
For DNS server providers and website owners
If you are a DNS service provider or a website owner, you have a huge responsibility for safeguarding your users by using various tools and protocols to manage the threats.
Some of the resources we have specified will help you in this regard.
Just like endpoint user security products, you can proactively use DNS spoofing detection tools to scan before you send or receive the data.
Using DNSSEC (Domain Name System Security Extensions) helps to keep DNS lookup fool-proof and authentic.
You can use end-to-end encryption to send DNS requests and replies. Hackers will not be able to duplicate the unique security certificate that is present on the legitimate website.
For endpoint users
To avoid making your users vulnerable to a DNS poisoning attack, you can use the specified tips.
Do not click on the links that you don't recognize; these include text messages, emails, or social media links. To be safe, you can opt for entering the URL manually in the address bar.
Regularly scan your computer for any malware. Your security software will help and remove any secondary infections. As the poisoned sites deliver malicious programs, you need to scan for spyware, viruses, or any other hidden issues.
Flush your DNS cache to solve the problem of poisoning. Nevertheless, cache poisoning remains in your system for a long time until you clean the infected area.
Use the virtual private network (VPN), a service that offers an encrypted tunnel for your web traffic. You can use a private DNS service exclusively for end-to-end encrypted requests; as a result, your servers are tougher against DNS spoofing.
Final Thoughts
DNS cache poisoning can be summarised as an attacker controlling the DNS server to send fake DNS responses. As a result, when the user visits the counterfeit domains, they will be directed to a new IP address selected by the hacker.
This new IP address might be from a malicious phishing website, where the users are prompted to download malware, or they might be asked to provide their financial or login details.
Hence, understanding what is DNS cache poisoning, how to detect it, and ways to prevent it is crucial so you can protect your business against it.
Originally published at LoginRadius
Why DNS Cache Poisoning is Dangerous for Your Business
Read this blog to understand what is dns cache poisoning and what should organizations do to avoid this cyberattack.

LR LogoView Profile

https://bit.ly/3pspZmP https://bit.ly/3qp6jzx
https://guptadeepak.com/content/images/2021/12/dns-cache-poisoning-is-dangerous-for-your-business.jpeg https://guptadeepak.weebly.com/deepak-gupta/dns-cache-poisoning-why-is-it-dangerous-for-your-business
0 notes
Text
DNS Cache Poisoning: Why Is It Dangerous for Your Business
What is DNS Cache Poisoning

DNS cache poisoning, also known as DNS spoofing, is a cyber-attack that exploits the weaknesses in the Domain Name System (DNS) servers. It enables the attacker to poison the data in DNS servers, including your company server, by providing false information to your internet traffic and diverting it to fake servers. This is done by redirecting the data in DNS to their IP address.
DNS cache poisoning utilizes the vulnerabilities in the DNS protocols' security to divert internet traffic away from legitimate servers to the wrong address.
DNS cache poisoning is effectively used for phishing attacks, often referred to as Pharming, for spreading malware. In the background, the malware runs and connects with legitimate servers to steal sensitive information.
When the DNS server is attacked, users may be requested to login into their accounts, and the attacker finds its way to steal the sensitive and financial credentials.
Moreover, phishing attacks also install viruses on the client's computer to exploit the stored data for long-term access.
How Does DNS Cache Poisoning Works
DNS spoofing is a threat that copies the legitimate server destinations to divert the domain's traffic. Ignorant of these attacks, the users are redirected to malicious websites, which results in insensitive and personal data being leaked.
It is a method of attack where your DNS server is tricked into saving a fake DNS entry. This will make the DNS server recall a fake site for you, thereby posing a threat to vital information stored on your server or computer.
The cache poisoning codes are often found in URLs sent through spam emails. These emails are sent to prompt users to click on the URL, which infects their computer.
When the computer is poisoned, it will divert you to a fake IP address that looks like a real thing. This way, the threats are injected into your systems as well.
What Are the Different Stages of Attack of DNS Cache Poisoning

First Stage
The attacker proceeds to send DNS queries to the DNS resolver, which forwards the Root/TLD authoritative DNS server request and awaits an answer.
Second Stage
The attacker overloads the DNS with poisoned responses that contain several IP addresses of the malicious website.
To be accepted by the DNS resolver, the attacker's response should match a port number and the query ID field before the DNS response.
Also, the attackers can force its response to increase their chance of success.
Third Stage
If you are a legitimate user who queries this DNS resolver, you will get a poisoned response from the cache, and you will be automatically redirected to the malicious website.
How to Detect DNS Cache Poisoning
Now that we know what is DNS cache poisoning let's understand how to detect it.
One way is to monitor the DNS server for any change in behavior patterns. Also, you can apply data security to DNS monitoring.
Another way is to look for a potential birthday attack. This occurs when there is a sudden increase in DNS activity from a single source in a single domain. When there is an increase in the DNS activity from a single source, querying your DNS server for multiple domain names without recurring shows that the attacker is looking for a DNS entry for poisoning.
Monitor the file system behavior and active directory events for any abnormal activities. You can use analytics for correlating activities among three vectors to add important information to your cybersecurity strategy.
Why Is DNS Cache Poisoning Dangerous for Your Business
When the DNS server is poisoned, it will start spreading towards other DNS servers and home routers. Computers that lookup DNS entries will get the wrong response by causing more users to end up as victims of DNS poisoning.
This issue will be resolved only when the poisoned DNS cache is cleared on each affected DNS server; you are at risk of losing your precious information until then.
One of the major reasons DNS cache poisoning is highly dangerous is that it can spread from one DNS server to another.
Here are a few DNS poisoning attack examples-
A DNS poisoning event had resulted in the Great Firewall of China's temporary escape from China's national borders by censoring the internet in the USA till the problem was resolved.
Recently, attackers targeted WikiLeaks, who used a DNS Cache poisoning attack for hijacking traffic to their WikiLeaks-like version. This intentional attack was created to divert the traffic away from WikiLeaks and was implemented successfully.
How To Protect Against DNS Cache Poisoning
For DNS server providers and website owners
If you are a DNS service provider or a website owner, you have a huge responsibility for safeguarding your users by using various tools and protocols to manage the threats.
Some of the resources we have specified will help you in this regard.
Just like endpoint user security products, you can proactively use DNS spoofing detection tools to scan before you send or receive the data.
Using DNSSEC (Domain Name System Security Extensions) helps to keep DNS lookup fool-proof and authentic.
You can use end-to-end encryption to send DNS requests and replies. Hackers will not be able to duplicate the unique security certificate that is present on the legitimate website.
For endpoint users
To avoid making your users vulnerable to a DNS poisoning attack, you can use the specified tips.
Do not click on the links that you don't recognize; these include text messages, emails, or social media links. To be safe, you can opt for entering the URL manually in the address bar.
Regularly scan your computer for any malware. Your security software will help and remove any secondary infections. As the poisoned sites deliver malicious programs, you need to scan for spyware, viruses, or any other hidden issues.
Flush your DNS cache to solve the problem of poisoning. Nevertheless, cache poisoning remains in your system for a long time until you clean the infected area.
Use the virtual private network (VPN), a service that offers an encrypted tunnel for your web traffic. You can use a private DNS service exclusively for end-to-end encrypted requests; as a result, your servers are tougher against DNS spoofing.
Final Thoughts
DNS cache poisoning can be summarised as an attacker controlling the DNS server to send fake DNS responses. As a result, when the user visits the counterfeit domains, they will be directed to a new IP address selected by the hacker.
This new IP address might be from a malicious phishing website, where the users are prompted to download malware, or they might be asked to provide their financial or login details.
Hence, understanding what is DNS cache poisoning, how to detect it, and ways to prevent it is crucial so you can protect your business against it.
Originally published at LoginRadius
Why DNS Cache Poisoning is Dangerous for Your Business
Read this blog to understand what is dns cache poisoning and what should organizations do to avoid this cyberattack.

LR LogoView Profile

https://bit.ly/3pspZmP https://bit.ly/3qp6jzx
https://guptadeepak.com/content/images/2021/12/dns-cache-poisoning-is-dangerous-for-your-business.jpeg https://deepakguptaplus.wordpress.com/2021/12/26/dns-cache-poisoning-why-is-it-dangerous-for-your-business/
0 notes
Link

0 notes