#quantum encryption
Explore tagged Tumblr posts
Text

Post-quantum cryptography services offer secure encryption and cryptographic solutions designed to withstand attacks from both classical and quantum computers. As the development of quantum computing progresses, traditional cryptographic algorithms, such as RSA and ECC, are at risk of being compromised by quantum attacks. Post-quantum cryptography aims to address these vulnerabilities by providing algorithms that are resistant to quantum attacks.
0 notes
Text
With the power to create unbreakable encryption, supercharge the development of AI, and radically expedite the development of drug treatments, quantum technology will revolutionize our world. In this video, we're diving deep into the world of the power of quantum encryption.
Quantum encryption, a groundbreaking advancement in the realm of cryptography and data security, has unveiled a new era of impregnable communication and data protection. This revolutionary technology harnesses the bewildering principles of quantum mechanics to enable the creation of unbreakable codes and shield sensitive information from the ever-looming threats of cyberattacks and surveillance.
Traditional encryption methods rely on complex mathematical algorithms to encode data, requiring vast computational power to crack these codes. In contrast, quantum encryption leverages the peculiar properties of quantum particles, such as photons, to establish an unbreakable link between the sender and the receiver. This link, often referred to as a quantum key distribution, is based on the principle of quantum entanglement, where the states of two particles become intertwined in such a way that any change in one particle instantaneously affects the other, regardless of the distance separating them.
The emergence of quantum encryption marks a watershed moment in the ongoing battle between information security and cyber threats. By harnessing the mystifying behaviors of quantum particles, this technology promises an era where sensitive data can be communicated and stored with unprecedented levels of security. As researchers continue to refine its implementation and address its challenges, quantum encryption holds the potential to revolutionize the way we safeguard our digital world.
#quantumencryption#quantumcomputing#encryptionquantumcomputers#limitlesstech#quantummachines#quantumcomputers#quantumtechnology#quantumencryptiontechnology#quantumencryptionalgorithm#quantumencryptionexplained#quantumencryptionsystem#quantumcryptography
The Mind-Blowing Power of Quantum Encryption Revealed
#the mind blowing power of quantum encryption revealed#quantum encryption#quantum computing#the power of quantum encryption#encryption quantum computers#quantum computers#quantum machines#benefits of quantum encryption#quantum technology#the future of quantum encryption#quantum encryption technology#quantum encryption algorithm#quantum encryption explained#quantum encryption system#LimitLess Tech 888#quantum computer encryption#quantum cryptography#quantum
0 notes
Text
With the power to create unbreakable encryption, supercharge the development of AI, and radically expedite the development of drug treatments, quantum technology will revolutionize our world. In this video, we're diving deep into the world of the power of quantum encryption.
Quantum encryption, a groundbreaking advancement in the realm of cryptography and data security, has unveiled a new era of impregnable communication and data protection. This revolutionary technology harnesses the bewildering principles of quantum mechanics to enable the creation of unbreakable codes and shield sensitive information from the ever-looming threats of cyberattacks and surveillance.
Traditional encryption methods rely on complex mathematical algorithms to encode data, requiring vast computational power to crack these codes. In contrast, quantum encryption leverages the peculiar properties of quantum particles, such as photons, to establish an unbreakable link between the sender and the receiver. This link, often referred to as a quantum key distribution, is based on the principle of quantum entanglement, where the states of two particles become intertwined in such a way that any change in one particle instantaneously affects the other, regardless of the distance separating them.
This phenomenon guarantees the security of the communication channel, as any attempt to intercept or eavesdrop on the transmitted quantum information would disrupt the delicate entanglement, leaving clear traces of tampering. This fundamental principle, known as the Heisenberg Uncertainty Principle, dictates that any observation of a quantum system alters its state, making surreptitious decryption impossible without alerting the parties involved.
The mind-bending implications of quantum encryption extend beyond secure communication channels. It has the potential to fundamentally transform industries reliant on data privacy, including finance, healthcare, government, and defense. Financial transactions, medical records, and classified government communications—all stand to benefit from the ironclad protection offered by quantum encryption.
However, the practical implementation of quantum encryption is not without challenges. Quantum systems are exquisitely delicate and susceptible to disturbances from their environment, which can lead to errors in transmission. Researchers have been diligently working to develop error correction techniques and robust quantum hardware to overcome these hurdles and make quantum encryption a viable reality.
The emergence of quantum encryption marks a watershed moment in the ongoing battle between information security and cyber threats. By harnessing the mystifying behaviors of quantum particles, this technology promises an era where sensitive data can be communicated and stored with unprecedented levels of security. As researchers continue to refine its implementation and address its challenges, quantum encryption holds the potential to revolutionize the way we safeguard our digital world.
The Mind-Blowing Power of Quantum Encryption Revealed
#the mind blowing power of quantum encryption revealed#quantum encryption#quantum computing#the power of quantum encryption#encryption quantum computers#quantum computers#quantum machines#benefits of quantum encryption#quantum technology#the future of quantum encryption#quantum encryption technology#quantum encryption algorithm#quantum encryption explained#quantum encryption system#LimitLess Tech 888#quantum computer encryption#quantum cryptography#quantum
0 notes
Text
Why should you care about quantum computers?
Post #5 on Physics and Astronomy, 23/09/23
Welcome back. It’s been a while.
First, let’s backtrack. What even are quantum computers?
Today’s computers are run on bits. These are the smallest increment of data on a computer, and are run in binary–they can be in the state of either 0 or 1. This essentially corresponds to two values: off and on.
This, therefore, means that information can only remain in one, definite state.
So, what makes quantum computers so different?
A quantum computer is run on qubits (short for quantum bits). Qubits, instead of a single state, can remain in an arbitrary superposition of states (meaning it’s not in any specific state until it’s measured). Qubits, on their own, aren’t particularly useful. But it performs one, very useful, function: it can store a combination of all possible states of the qubit into one area. This means that complex problems can be represented differently in qubits compared to bits.
Quantum computers aren’t fully developed and at their full capacity quite yet. So far, there’s nothing a quantum computer can do that a regular supercomputer cannot. However, this opens an opportunity for some wonderful new things to happen.
One of these things can include the cracking of passwords.
Today’s encryption works by using “trapdoor” functions, which means that data is easy to compute in the forward direction, but extremely difficult to crack in the reverse without special keys. Keywords, ‘extremely difficult’; it is not impossible. However, this is not a massive concern: encryption works on the basis that it would simply take too long to crack.
To give you a tangible example, 100,003 and 131,071 are relatively easy to multiply together, giving you the answer 13,107,493,213. How easy, however, would it be to determine a prime factor pair of this number? It would take a computer a long time to figure this out, since it runs on bits, which can only show one definite state of data.
With quantum computers, it’s different. As aforementioned, qubits can remain in a superposition of states; somewhere in there, the desired answer lies. It’s just a matter of obtaining the resources to make this happen.
Don’t worry, though. Ordinary people aren’t at any risk quite yet.
#physics#astronomy#studyblr#astrophysics#stem#sixth form#mathematics#quantum physics#quantum computing#engineering#encryption#alevels
87 notes
·
View notes
Text
The main question is not whether the quantum computer will break Bitcoin encryption and other digital currencies. We already know it will happen. The essential question is: Will digital currency bear the speed, the short time with which the quantum computer will break its encryption?
3 notes
·
View notes
Text
Lets begin a revolution
Encrypt your PRIVACY
2 notes
·
View notes
Text
An Extensive Guide to Key Management as a Service (KMaaS)

In today's interconnected digital landscape, data is both the most valuable asset and the most tempting target. As organizations increasingly embrace cloud-first strategies and digital transformation, sensitive information's sheer volume and velocity continue to swell.
While encryption has long been lauded as the cornerstone of enterprise data security, Key Management is a critical, often-overlooked element that dictates its effectiveness.
Without robust key management, even the strongest encryption algorithms are rendered impotent, akin to locking a vault with the key left under the doormat.
This guide delves into key management's essential role and explores why Key Management as a Service (KMaaS) has emerged as an indispensable component of modern data security best practices.
The Hidden Vulnerability: Why Key Management Matters More Than Ever
Encryption works by transforming data into an unreadable format, accessible only with the correct cryptographic key. The lifecycle of these keys—from their secure generation and distribution to their storage, usage, rotation, and eventual destruction—is what constitutes key management. If this process is flawed, the entire security chain crumbles.
The consequences of poor key management are stark and frequently make headlines. While many data breaches are attributed to phishing or misconfigurations, the inability to properly secure or manage encryption keys often amplifies the impact.
For instance, the Verizon Data Breach Investigations Report (DBIR) consistently highlights how stolen credentials and misconfigurations contribute to breaches, and these often involve the compromise of access to sensitive systems or, indirectly, to encryption keys.
When keys are not properly rotated or are left exposed, a single breach can have catastrophic ripple effects. Think of the infamous Capital One breach in 2019, where a misconfigured web application firewall led to the compromise of customer data.
While not directly a "key management" failure in the traditional sense, it underscores how vulnerabilities at any point of access can expose mechanisms (like credentials or temporary keys) that control sensitive data.
Moreover, a 2025 report from eMudhra indicated that incident detection and containment still take too long—an average of 274 days according to IBM’s Ponemon Report—giving attackers ample time to exploit weaknesses, including poorly managed keys.
Such incidents underscore that effective enterprise data security requires encryption and meticulous control over the keys that unlock your most sensitive information.
The Rise of Key Management as a Service (KMaaS)
Historically, managing encryption keys involved complex, on-premises hardware security modules (HSMs) and specialized teams. While effective, this approach often lacked the scalability, flexibility, and ease of integration required for modern hybrid and multi-cloud environments. This is where KMaaS steps in.
youtube
Key Management as a Service (KMaaS) is a cloud-based solution that centralizes cryptographic keys' generation, storage, distribution, and lifecycle management.
It abstracts the complexities of physical infrastructure, offering robust, enterprise-grade key management as a readily available, scalable service.
KMaaS empowers organizations to:
Centralize Control: Gain a unified view and control over all encryption keys across diverse environments.
Enhance Security: Leverage hardened, purpose-built infrastructure (often underpinned by HSMs) for key protection.
Improve Scalability: Easily scale key management capabilities to meet growing data volumes and expanding cloud footprints.
Reduce Operational Overhead: Offload the operational burden of managing complex key infrastructure to a specialized provider.
Core Components of a Robust KMaaS Solution
A truly effective KMaaS solution encompasses several critical capabilities:
Secure Key Generation and Storage: Keys must be generated using strong, verifiable random number generators and stored in highly secure, tamper-resistant environments. This often involves FIPS 140-2 Level 3 certified Hardware Security Modules (HSMs), ensuring cryptographic operations occur within a protected boundary.
Comprehensive Key Lifecycle Management: From initial creation and secure distribution to consistent usage policies, regular rotation, immediate revocation upon compromise, and permanent destruction, a KMaaS platform manages every stage of a key's life.
Granular Access Control and Auditability: The system must enforce strict, policy-based access controls, dictating who can access which keys, from where, and for what purpose. Comprehensive audit logs are essential for compliance and forensic analysis, providing an immutable record of all key activities.
Multi-Cloud and Hybrid Environment Support: Modern enterprises operate across diverse infrastructures. A leading KMaaS solution must seamlessly integrate with public clouds (AWS, Azure, GCP), private clouds, and on-premises systems, providing consistent key management policies everywhere.
Navigating the KMaaS Landscape: Best Practices for Implementation
Adopting KMaaS is a strategic move, not just a technical deployment. To truly elevate your enterprise data security, consider these data security best practices:
Thorough Vendor Evaluation: Don't just pick the first option. Scrutinize vendors based on their security certifications (e.g., FIPS), compliance track record, financial stability, and integration capabilities with your existing ecosystem. A comprehensive Key Management Service should offer robust features like seamless integration and a broad range of supported cryptographic algorithms.
Define Clear Policies and Procedures: KMaaS provides the technical framework, but your internal governance must define how keys are used, who is responsible for what, and how incidents are handled. Strong policies are the human backbone to the technological prowess of KMaaS.
Prioritize Compliance and Regulatory Adherence: Regulations like GDPR, HIPAA, PCI DSS, and countless others mandate stringent data protection. A good KMaaS provider helps you meet these requirements by offering features like data residency controls, robust logging, and attestations. Ensure the solution supports your specific regulatory needs.
Implement Continuous Monitoring and Auditing: While KMaaS simplifies management, continuous monitoring of key usage and regular audits of the system itself are non-negotiable. This proactive stance helps detect anomalies and potential compromises early.
Embrace Crypto Agility and Post-Quantum Preparedness: The cryptographic landscape is constantly evolving, with quantum computing posing a future threat to current encryption standards. A future-ready KMaaS solution should offer crypto agility, allowing for easy updates to new algorithms and preparing you for the post-quantum era. Fortanix, for instance, offers a comprehensive key management solution that addresses these evolving cryptographic challenges.
Why Key Management as a Service aka KMaaS is Your Strategic Advantage
In an era where data breaches are not a matter of "if," but "when," the ability to securely manage encryption keys becomes a paramount differentiator.
KMaaS simplifies this complex challenge, providing the specialized infrastructure and expertise to effectively protect sensitive data.
It enables organizations to streamline operations, reduce human error, accelerate compliance efforts, and significantly mitigate the risk of devastating data breaches.
By adopting KMaaS, you're not just buying a service but investing in a fortified future for your data, ensuring that your organization remains secure, compliant, and resilient in the face of ever-evolving cyber threats. It’s a foundational step towards mature enterprise data security best practices.
#key management#guide#data security#technology#post quantum#cybersecurity#dataprotection#encryption#crypto#best practices
0 notes
Text
Post Quantum Security: Future-Proof Data From Quantum Threats

What becomes of encryption today when quantum computers are capable of cracking it? As we race toward a future driven by the next generation of technology, one urgent question hangs over cybersecurity. The solution is to use Post Quantum Security, a new generation of cryptography capable of resisting the brute power of quantum computing.
In a world where sensitive information — from personal identities to national secrets — is increasingly vulnerable, Post Quantum Security is not just an upgrade, but a necessity. This article explores how to future-proof your data and systems against quantum threats.
Understanding the Quantum Threat Landscape
The Birth of Quantum Computing
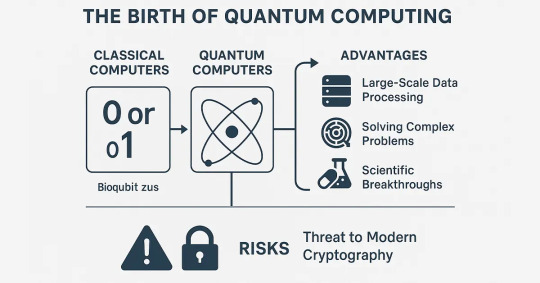
Quantum computing seems to quickly evolve from a new scientific theory into a change- and results-driven technology. Old computers use the binary digit as 0 or 1, whereas quantum computers operate using qubits, which can occupy several states simultaneously owing to superposition and entanglement. As a result, such cutting-edge machines provide an exceptional ability for quick, advanced computations.
Quantum computing excels using its capability of handling large data volumes and solving issues too complicated for existing best classical supercomputers. In particular, quantum computers can effectively address complex logistics tasks, analyze the structure of molecules to invent new medicines, and enhance the approach undertaken in financial forecasting.
But with that potential comes a warning: quantum computing puts modern cryptographic systems at serious risk. The same computational benefits that make quantum computers a breakthrough for scientific research are the ability to compromise classical encryption methods used in our online security.
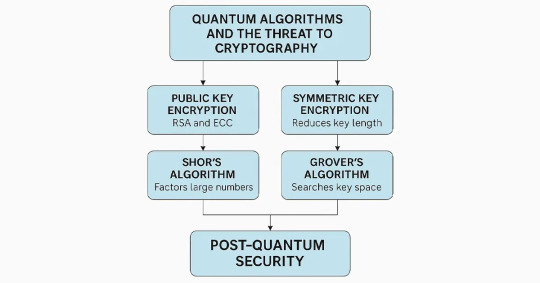
Implications for Current Cryptography
The dominant modalities of the modern digital infrastructure are based on the use of public key cryptography, and such systems as RSA and ECC are among the most widespread representations that people use. These encryption systems are based on mathematically difficult problems for conventional systems — factorizing huge numbers or solving discrete logarithm problems. These are exactly the sorts of problems a quantum computer is designed to demolish with impunity using expert algorithms.
Shor’s Algorithm, created in 1994, is likely the most famous quantum algorithm that targets RSA and ECC directly. It can factor big numbers exponentially quicker than the best-known classical algorithms. When quantum computers are ready — usually called “quantum supremacy” — they will be able to decrypt secure communications, financial transactions, and private information that are now thought to be secure.
Another significant algorithm, Grover’s Algorithm, doesn’t shatter symmetric crypto systems but narrows down their security levels significantly. It indeed cuts a symmetric key’s bits in half, so 256-bit keys would provide only 128-bit security in the quantum age. Less devastating than Shor’s impact on asymmetric crypto, though, Grover’s Algorithm does mean a reconsideration of the dominant symmetric encryption algorithms.
This new threat brings to the forefront the need for post quantum security solutions in an immediate manner. Unlike conventional cryptographic practices, post quantum security is about designing and deploying algorithms that are secure even when quantum computing resources are available. These algorithms are based on challenging mathematical problems for which quantum computers are not yet known to solve efficiently.
The Urgency for Transition
Post quantum security is not a theoretical concept; it’s an urgent, real-life issue. RSA- or ECC-breaking large-scale quantum computers don’t exist yet, but breakthroughs are on the move. The collaborative efforts of governments, corporations, and research bodies across the globe to create quantum technology imply that these machines will soon become real.
There is a dire need to secure the digital infrastructure of organizations, for when quantum technology is available. Transitioning to post quantum security protocols is difficult and time-consuming, not only swapping cryptographic algorithms but also rewriting software, hardware, and communication protocols. Waiting for fully functional quantum computers may expose systems and data to attacks.
Further, hacked encrypted data today can be stored and decoded at a later date after computers develop the capability — the “harvest now, decrypt later” attack. As a countermeasure post quantum security ensures valuable information is safeguarded both today and in the foreseeable future.
The U.S. National Institute of Standards and Technology (NIST) has already started standardizing quantum-resistant algorithms with its Post-Quantum Cryptography Standardization Project. Organizations can standardize their security approach with international best practices for post quantum security using NIST-recommended solutions.
What Is Post Quantum Security?
Post Quantum Security is a term that is used to refer to cryptographic methods that are resistant to attacks carried out by entities that can run large quantum computers. Besides, this category includes the quantum-resistant hash algorithms, encryption algorithms, and digital signature algorithms. These systems are being standardized by efforts such as NIST’s Post-Quantum Cryptography Project.
Embracing Post Quantum Security guarantees that long-lived sensitive information, such as medical records or financial contracts, is still protected even when intercepted today and decrypted in the future quantum world.
ncog.earth incorporates Post Quantum Security into its core blockchain protocol. It provides data security for decades in a post-quantum secure environment.
Core Principles of Post Quantum Security
Below are the fundamental principles that constitute this new field and how they interact with each other to protect digital property during the era of quantum computing.
1. Quantum-Resistant Algorithms
Post quantum security is centered around quantum-resistant algorithms, which are designed to stand up to attacks both from traditional attack methodologies as well as attacks performed with a quantum computer. These algorithms don’t depend on the weak assumptions of the classical encryption methods like RSA or ECC, which can be attacked and broken by quantum algorithms like Shor. Post quantum security instead depends on mathematical problems with cryptographically amicable properties that are difficult for an efficient quantum computer to solve.
Among the most promising quantum-resistant solutions are-
Lattice-based cryptography: Lattice-based cryptosystems rely on the computational subtlety of such problems as the Shortest Vector Problem (SVP) and the Learning With Errors (LWE) problem. They are classical and quantum resistant and thus well positioned to protect encryption, digital signatures, and key exchanges.
Hash-based cryptography: Founded on extensively studied hash functions, this method effectively generates secure digital signatures. Because hash functions are one-way functions, they are extremely secure even against quantum attackers.
Code-based cryptography: Founded on error-correcting codes, this method has stood the test of time for more than four decades. It is strong, well-established, and extremely efficient for encryption and digital signatures in a post quantum security scenario.
Multivariate polynomial cryptography: The hardness of these problems is essentially dependent on the intricacies of solving multivariate quadratic systems of equations, which are intractable for quantum and classical systems.
Deployment and selection of these algorithms are being standardized by bodies such as NIST, which is finalizing a suite of post-quantum cryptographic standards for ease of global implementation of post quantum security protocols.
2. Forward Secrecy
Forward secrecy is yet another significant post quantum security parameter. In the conventional crypto paradigm, it might be possible that breaking a private key today can expose attackers to decrypted communications in the past and future, and it is highly risky if, in a quantum paradigm where harvested encrypted data from today can be broken using quantum computers in the future.
Post quantum security addresses this issue by guaranteeing that even when an encryption key is finally breached, past messages cannot be decoded after the fact. The method is to repeatedly generate ephemeral keys that don’t survive and aren’t easily linked up with each other. Forward secrecy is significant not just for private individuals but for protecting business networks, government files, and money networks as well.
Essentially, forward secrecy reconfigures the way we approach long-term data secrecy, particularly considering the danger represented by “harvest now, decrypt later” attacks facilitated by quantum advancements. In post quantum security, it’s a solid pillar of real future-proofing.
3. Hybrid Cryptographic Models
With the indefinite time frame of quantum progress, most organizations are taking a hybrid approach that brings together classical and post-quantum-resistant cryptography. The cryptographic models are created to fill the security gap during the transition phase when the existing traditional algorithms exist side by side with the post quantum security algorithms.
In a hybrid method, two sets of algorithms are run in parallel. One set offers backwards compatibility with current infrastructures, and the other offers immunity to future quantum attacks. As a simple example, an end-to-end communication channel could employ RSA in conjunction with a lattice-based encryption scheme at the same time. This means that even if the classical part is compromised in the future, the post quantum security layer still protects the underlying data.
This method has some advantages-
Gradual roll-out: Businesses can deploy systems gradually without affecting current services.
Redundancy: Having several levels of encryption offers a backup in case one algorithm is compromised.
Testing ground: Testing the deployment of quantum-resilient tools identifies real-world problems and solutions before mass deployment.
Hybrid deployments are not long-term, but they are essential stepping stones. With increasing trust and confidence in post quantum security technology, hybrid deployments will ultimately make way for fully quantum-resistant architectures.
Why Businesses Must Act Now

In the unfolding digital age, while cyberattacks increase in scale and sophistication, quantum computing’s emergence is at once a dazzling technological advancement and an intrinsic cybersecurity challenge. To companies — particularly those holding sensitive customer data or conducting business in highly regulated industries — the time to prepare is not in the future but today. Post-quantum security is no longer an idealistic aspiration but rather a concrete reality. Forward-thinking companies need to take action today to ensure that they will be able to withstand future cryptographic shocks.
Quantum Threats Are Nearer Than They Seem
The power of quantum computers is that they can use superposition and entanglement to exceed classical machines in certain forms of mathematical operations. The possible advantages that such technology could offer to drug discovery and logistics, as well as machine learning, are substantial, but this danger also undermines the encryption protection that enshrines secure digital communication, financial systems, medical records, and contracts.
Algorithms such as RSA and ECC, the basis of modern public-key cryptography, could be made obsolete by quantum algorithms such as Shor’s. In practical terms, what that would mean is to make information currently encrypted under these systems decrypted within seconds if there existed a sufficiently large quantum computer. The potential effect would be disastrous to companies experiencing huge-scale data breaches, litigations, and erosion of customer confidence.
That’s why post quantum security must be implemented far ahead of the wholesale arrival of quantum computing. Companies that delay are not only taking a risk — they’re deliberately putting their businesses, data, and reputations in long-term jeopardy.
Data Longevity Brings the Risk into the Present
One of the least considered measures of quantum risk is data longevity concern. Whereas real-time data spoils at a fast pace, some forms of data — medical history, legal papers, government agreements, and intellectual property — are priceless for decades or years. If today a cyberattacker got hold of encrypted information, they would be unable to decipher it. But with the advent of quantum power, the same information can be accessed in the foreseeable future. The label is also applicable when talking about attacks referred to as “harvest now, decrypt later”.
On this front, post quantum security plays a twofold role: it safeguards against the threat at hand, but also against potential attempts to decrypt in the future. For businesses tasked with securing data over the long term — insurance providers, banks, and law firms, for example — it is critical that it is pre-emptive. Delaying the implementation of quantum-resistant practices creates a bombshell situation where encrypted files stored could be cracked open at any moment.
Consumer confidence is perhaps the most precious asset of the online marketplace. With high-profile breaches becoming the norm, customers are growing more attuned to where their information lives and how it is secured. Companies that act early to publish quantum security standards communicate that they are serious about leading-edge data protection and customer privacy. This method contributes to the creation and preservation of a reliable brand and earns the loyalty of the clients.
Additionally, regulatory landscapes are changing. Global data privacy legislation like the GDPR, HIPAA, and CCPA demands secure data security procedures, and compliance systems will shortly be following close behind in counteracting quantum-age attacks. Adopting post quantum security today allows organizations to protect themselves against future compliance mandates and sidestep the prohibitively cost-intensive exercise of currency flows.
Smooth Transition Through Strategic Planning
Post quantum migration is not a flip-of-the-switch transition — it requires thoughtful planning, testing, and staged deployment. Businesses must assess their existing cryptographic infrastructure, identify vulnerable endpoints, and decide which quantum-resistant algorithms will best meet their operational needs.
Fortunately, most businesses are not beginning from the ground up. Hybrid crypto designs — blends of conventional and quantum-resistant solutions — permit phased and secure adoption. Post quantum security is viable through hybrid approaches that support organizations in adopting post quantum security without sacrificing current system performance or compatibility. Phase by phase is the way, causing as little disruption as possible while providing security for important information at each stage.
They also must spend on training and awareness programs. Decision-makers, developers, and cybersecurity staff must be made aware of the effects of quantum risk and the pragmatic actions that go into minimizing it. Post quantum security incorporated into cybersecurity roadmaps now will have companies not lag when the quantum era is in full force.
Building Quantum-Resilient Ecosystems
The truth is, cybersecurity is not an isolated practice. A majority of businesses employ third-party suppliers, cloud computing providers, and digital platforms that touch or have access to sensitive information. Having a secure digital environment is a matter of discussing post quantum security with partners and suppliers.
Leading organizations are now starting to measure their supply chains and expect quantum-readiness from their partners. Organizations can minimize systemic vulnerabilities and foster increased collective resilience by establishing post-quantum security as an expectation within ecosystems.
Integrating Post Quantum Security into Your Infrastructure
With continued advances in quantum computing, the danger that it poses to classical cryptographic schemes is more dire. Companies and enterprises cannot afford to wait. There is a need for a transparent and systematic adoption of post quantum security protocols into existing IT infrastructures so that data confidentiality, integrity, and availability are preserved under quantum computing. This has to be done with a strategic roadmap of action covering technology and operations transformation across the digital landscape.
For this transition to be made possible, organizations can utilize a multi-step process that will establish quantum resilience without disrupting essential services. Below, we outline the four main steps of incorporating post-quantum security in your infrastructure.
Audit Your Current Cryptographic Inventory
Before any change is implemented by companies, they must start by defining the scope and utilization of current cryptographic assets. Any effective post quantum security project is based on a thorough cryptographic inventory. This process entails determining where and how cryptographic algorithms are utilized — on SSL/TLS certificates, database encryption, secure email, authentication protocols, digital signatures, API gateways, mobile applications, VPNs, and IoT devices.
This audit must encompass-
Encryption Algorithms Used: Assess if systems are using RSA, ECC, or other vulnerable algorithm-based encryption.
Key Sizes and Expiration Policies: Document existing key sizes and assess how often they are being replaced.
Cryptographic Libraries and APIs: Check for dependencies and assess compatibility with quantum-resistant alternatives.
Certificate Authorities and Issuance Policies: Examine methods of distributing, retaining, and withdrawing digital certificates.
When such data is analyzed, it is possible to identify weak points and establish priorities for strategic transition to post-quantum security. Notably, the process helps organizations to review the data lifecycle and determine long-term sensitive data that needs to be secured today against tomorrow’s quantum decryption power.
Select Quantum-Resistant Algorithms
After identifying your cryptographic footprint, the next step is to select quantum-resistant alternatives. NIST has worked with others to initiate multi-year standardization efforts that will evaluate and promote post-quantum cryptography algorithm recommendations. These algorithms are designed so that they can resist attack by both classical and quantum computers and include key encapsulation processes and digital signature protocols.
Among the most promising contributions to come out of the NIST project are-
CRYSTALS-Kyber (for public-key cryptography and KEM)
CRYSTALS-Dilithium (for digital signatures)
FALCON and SPHINCS+ (signature schemes with performance profiles of differing types)
In choosing algorithms, implementations must consider performance, resource efficiency, complexity to implement, and the extent to which the solution they choose fits their infrastructure. For instance, IoT devices that have little power may need lightweight algorithms, but high performance servers are more than capable of handling complex computing activities.
Selection of the best algorithms is immensely important for effective post quantum security integration. Future-proofing should also be a consideration for security teams as quantum-resistant cryptography develops. Modular architecture solutions for cryptography allow for a seamless switch or upgrade of algorithms as new standards become available.
Use Hybrid Cryptographic Systems
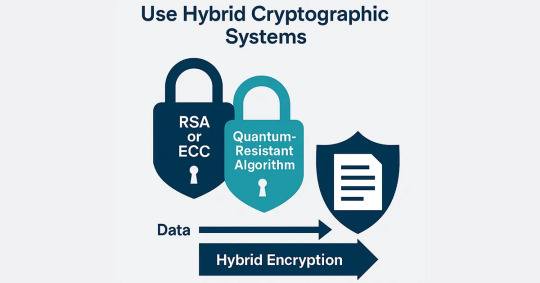
It is not necessary to move away from classical to quantum-resistant cryptography completely. One of the most recommended practices while transitioning to post quantum security is the use of hybrid cryptographic systems. These use current (classical) cryptographic algorithms and couple them with quantum-safe algorithms to provide a multi-layered defense.
In a hybrid system, data is encrypted with both RSA (or ECC) and a quantum-resistant algorithm. It makes the system both backward compatible as well as future-proof against attacks based on quantum. Although quantum computers are unable to break today’s classical encryption now, hybrid encryption protects the data from being exposed in the future, most beneficial for long-shelf-life sensitive data.
Hybrid deployments also enable companies to pilot the in-the-wild usage of post-quantum-safe algorithms without removing trusted current defenses. Phase-in of post quantum security in this manner prevents service disruption, lowers operational risk, and enables incremental testing and tightening.
Key libraries and frameworks increasingly start to include hybrid support. For example-
OpenSSL (with quantum-safe branches)
Cloudflare and Amazon Web Services, which have begun to experiment with post-quantum TLS deployments
Mozilla and Google, pioneering early hybrid deployments in their browsers
These initial hybrid adoption attempts show the growing traction for post-quantum security and offer in-the-wild blueprints for companies willing to make the transition.
Upgrade Key Management Systems (KMS)
The key to the efficiency of encryption lies entirely in the responsible use of its keys. Infrastructures that are quantum-resilient need updates to legacy Key Management Systems (KMS) to accommodate the special needs of post quantum security…
#post quantum#post quantum security#technology#ncog#post quantum blockchain#post quantum encryption#post quantum cryptography#decentralized database#quantum computer#quantum computing#quantum computers#post quantum secure blockchain#rsa#shor algorithm#quantum-resistant cryptography#ECC
1 note
·
View note
Text
Cybersecurity takes a big hit in new Trump executive order
Provisions on secure software, quantum–resistant crypto, and more are scrapped.

Cybersecurity takes a big hit in new Trump executive order
Archive Links: ais ia
#bgp#biz-\u0026-it#encryption#executive-orders#policy#quantum-computing#security#trump#white-house#[#]
0 notes
Text
really mad about quantum computing rn
#2035 is a generous estimate of when we get viable quantum computers#so i was born right between the comp sci boom and the quantum boom it seems#ig i was born at a good time to work on quantum-proof encryption protocols#but like . ergh blergh thats so boring in comparison to implementing them!!!!#mayb studying now will allow me to be a prolific quantum hacker later idk we'll see :(#self.txt
0 notes
Text
Why Quantum Computing Will Reshape Data Encryption by 2030
If you think hackers are dangerous now, just wait until quantum computers go mainstream. Quantum computing—once the stuff of sci-fi movies—is inching closer to real-world application. And its most profound impact? Blowing up everything we know about data encryption. By 2030, the very foundations of how we protect information online—your passwords, bank transactions, and state secrets—will be…
0 notes
Text

0 notes
Text
The Future of the Internet: Quantum Teleportation Explained
In the rapidly evolving world of technology, one development stands out as groundbreaking: quantum teleportation. This intriguing concept, which might sound like science fiction, has recently achieved a significant milestone. Researchers have successfully teleported a quantum state over more than 30 kilometers of existing internet infrastructure. This remarkable achievement marks a monumental…
#Fiber-optic quantum technology#Future of quantum technology#Integration of quantum and classical internet#Quantum communication#Quantum computing advancements#Quantum internet#Quantum networking#Quantum state transfer#Quantum teleportation#Secure quantum encryption
0 notes
Text

Awesome! Scope's Quantum Security Mobile App Secures Funding Scope Technologies secures $1.5M to accelerate its QSE quantum security mobile app. Offering advanced, user-friendly quantum-resistant encryption and secure file sharing.
Read more
#quantum security#mobile app#data encryption#cybersecurity#quantum-resistant#Scope Technologies#QSE mobile app#First Majestic Silver
0 notes
Text
The Importance of Data Encryption in 2025: Why You Can’t Ignore It
Introduction Imagine waking up one morning to find your personal data, financial records, or business information leaked across the internet. Sounds terrifying, right? That’s the reality many individuals and businesses face today without proper encryption. As we move into 2025, data encryption isn’t just an option—it’s a necessity. With cyber threats evolving rapidly, encryption acts as a…
#AI and cybersecurity#cloud security encryption#cybersecurity in 2025#data encryption best practices#encryption for businesses#future of encryption#post-quantum cryptography
0 notes
Text
I love the point we're at with technology where you can Google anything and it's gotten better over the years and now when you Google a question an AI often answers your question for you almost as if it searched the information from 50-250 websites and you can ask them like a person who has studied the topic.
It's probably all about to crumble.
In about two years hackers will I think start using AI to better hack people. Services will get hacked, probably attacked. Some may survive it all and do well, maybe crypto will be popular for a while if VISA gets attacked.
Nobody will have any privacy and probably servers will get overrun but maybe they can use backups.
Eventually quantum computers might come and render all our top encryption useless. Imagine what happens when you combine a powerful quantum computer with a top AI!
For now, however, it is good.
0 notes