#Secure quantum encryption
Explore tagged Tumblr posts
Text
The Future of the Internet: Quantum Teleportation Explained
In the rapidly evolving world of technology, one development stands out as groundbreaking: quantum teleportation. This intriguing concept, which might sound like science fiction, has recently achieved a significant milestone. Researchers have successfully teleported a quantum state over more than 30 kilometers of existing internet infrastructure. This remarkable achievement marks a monumental…
#Fiber-optic quantum technology#Future of quantum technology#Integration of quantum and classical internet#Quantum communication#Quantum computing advancements#Quantum internet#Quantum networking#Quantum state transfer#Quantum teleportation#Secure quantum encryption
0 notes
Text
An Extensive Guide to Key Management as a Service (KMaaS)

In today's interconnected digital landscape, data is both the most valuable asset and the most tempting target. As organizations increasingly embrace cloud-first strategies and digital transformation, sensitive information's sheer volume and velocity continue to swell.
While encryption has long been lauded as the cornerstone of enterprise data security, Key Management is a critical, often-overlooked element that dictates its effectiveness.
Without robust key management, even the strongest encryption algorithms are rendered impotent, akin to locking a vault with the key left under the doormat.
This guide delves into key management's essential role and explores why Key Management as a Service (KMaaS) has emerged as an indispensable component of modern data security best practices.
The Hidden Vulnerability: Why Key Management Matters More Than Ever
Encryption works by transforming data into an unreadable format, accessible only with the correct cryptographic key. The lifecycle of these keys—from their secure generation and distribution to their storage, usage, rotation, and eventual destruction—is what constitutes key management. If this process is flawed, the entire security chain crumbles.
The consequences of poor key management are stark and frequently make headlines. While many data breaches are attributed to phishing or misconfigurations, the inability to properly secure or manage encryption keys often amplifies the impact.
For instance, the Verizon Data Breach Investigations Report (DBIR) consistently highlights how stolen credentials and misconfigurations contribute to breaches, and these often involve the compromise of access to sensitive systems or, indirectly, to encryption keys.
When keys are not properly rotated or are left exposed, a single breach can have catastrophic ripple effects. Think of the infamous Capital One breach in 2019, where a misconfigured web application firewall led to the compromise of customer data.
While not directly a "key management" failure in the traditional sense, it underscores how vulnerabilities at any point of access can expose mechanisms (like credentials or temporary keys) that control sensitive data.
Moreover, a 2025 report from eMudhra indicated that incident detection and containment still take too long—an average of 274 days according to IBM’s Ponemon Report—giving attackers ample time to exploit weaknesses, including poorly managed keys.
Such incidents underscore that effective enterprise data security requires encryption and meticulous control over the keys that unlock your most sensitive information.
The Rise of Key Management as a Service (KMaaS)
Historically, managing encryption keys involved complex, on-premises hardware security modules (HSMs) and specialized teams. While effective, this approach often lacked the scalability, flexibility, and ease of integration required for modern hybrid and multi-cloud environments. This is where KMaaS steps in.
youtube
Key Management as a Service (KMaaS) is a cloud-based solution that centralizes cryptographic keys' generation, storage, distribution, and lifecycle management.
It abstracts the complexities of physical infrastructure, offering robust, enterprise-grade key management as a readily available, scalable service.
KMaaS empowers organizations to:
Centralize Control: Gain a unified view and control over all encryption keys across diverse environments.
Enhance Security: Leverage hardened, purpose-built infrastructure (often underpinned by HSMs) for key protection.
Improve Scalability: Easily scale key management capabilities to meet growing data volumes and expanding cloud footprints.
Reduce Operational Overhead: Offload the operational burden of managing complex key infrastructure to a specialized provider.
Core Components of a Robust KMaaS Solution
A truly effective KMaaS solution encompasses several critical capabilities:
Secure Key Generation and Storage: Keys must be generated using strong, verifiable random number generators and stored in highly secure, tamper-resistant environments. This often involves FIPS 140-2 Level 3 certified Hardware Security Modules (HSMs), ensuring cryptographic operations occur within a protected boundary.
Comprehensive Key Lifecycle Management: From initial creation and secure distribution to consistent usage policies, regular rotation, immediate revocation upon compromise, and permanent destruction, a KMaaS platform manages every stage of a key's life.
Granular Access Control and Auditability: The system must enforce strict, policy-based access controls, dictating who can access which keys, from where, and for what purpose. Comprehensive audit logs are essential for compliance and forensic analysis, providing an immutable record of all key activities.
Multi-Cloud and Hybrid Environment Support: Modern enterprises operate across diverse infrastructures. A leading KMaaS solution must seamlessly integrate with public clouds (AWS, Azure, GCP), private clouds, and on-premises systems, providing consistent key management policies everywhere.
Navigating the KMaaS Landscape: Best Practices for Implementation
Adopting KMaaS is a strategic move, not just a technical deployment. To truly elevate your enterprise data security, consider these data security best practices:
Thorough Vendor Evaluation: Don't just pick the first option. Scrutinize vendors based on their security certifications (e.g., FIPS), compliance track record, financial stability, and integration capabilities with your existing ecosystem. A comprehensive Key Management Service should offer robust features like seamless integration and a broad range of supported cryptographic algorithms.
Define Clear Policies and Procedures: KMaaS provides the technical framework, but your internal governance must define how keys are used, who is responsible for what, and how incidents are handled. Strong policies are the human backbone to the technological prowess of KMaaS.
Prioritize Compliance and Regulatory Adherence: Regulations like GDPR, HIPAA, PCI DSS, and countless others mandate stringent data protection. A good KMaaS provider helps you meet these requirements by offering features like data residency controls, robust logging, and attestations. Ensure the solution supports your specific regulatory needs.
Implement Continuous Monitoring and Auditing: While KMaaS simplifies management, continuous monitoring of key usage and regular audits of the system itself are non-negotiable. This proactive stance helps detect anomalies and potential compromises early.
Embrace Crypto Agility and Post-Quantum Preparedness: The cryptographic landscape is constantly evolving, with quantum computing posing a future threat to current encryption standards. A future-ready KMaaS solution should offer crypto agility, allowing for easy updates to new algorithms and preparing you for the post-quantum era. Fortanix, for instance, offers a comprehensive key management solution that addresses these evolving cryptographic challenges.
Why Key Management as a Service aka KMaaS is Your Strategic Advantage
In an era where data breaches are not a matter of "if," but "when," the ability to securely manage encryption keys becomes a paramount differentiator.
KMaaS simplifies this complex challenge, providing the specialized infrastructure and expertise to effectively protect sensitive data.
It enables organizations to streamline operations, reduce human error, accelerate compliance efforts, and significantly mitigate the risk of devastating data breaches.
By adopting KMaaS, you're not just buying a service but investing in a fortified future for your data, ensuring that your organization remains secure, compliant, and resilient in the face of ever-evolving cyber threats. It’s a foundational step towards mature enterprise data security best practices.
#key management#guide#data security#technology#post quantum#cybersecurity#dataprotection#encryption#crypto#best practices
0 notes
Text
Post Quantum Security: Future-Proof Data From Quantum Threats

What becomes of encryption today when quantum computers are capable of cracking it? As we race toward a future driven by the next generation of technology, one urgent question hangs over cybersecurity. The solution is to use Post Quantum Security, a new generation of cryptography capable of resisting the brute power of quantum computing.
In a world where sensitive information — from personal identities to national secrets — is increasingly vulnerable, Post Quantum Security is not just an upgrade, but a necessity. This article explores how to future-proof your data and systems against quantum threats.
Understanding the Quantum Threat Landscape
The Birth of Quantum Computing
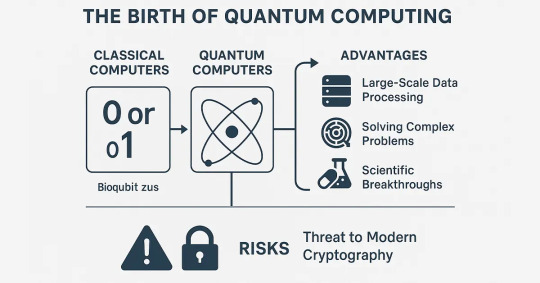
Quantum computing seems to quickly evolve from a new scientific theory into a change- and results-driven technology. Old computers use the binary digit as 0 or 1, whereas quantum computers operate using qubits, which can occupy several states simultaneously owing to superposition and entanglement. As a result, such cutting-edge machines provide an exceptional ability for quick, advanced computations.
Quantum computing excels using its capability of handling large data volumes and solving issues too complicated for existing best classical supercomputers. In particular, quantum computers can effectively address complex logistics tasks, analyze the structure of molecules to invent new medicines, and enhance the approach undertaken in financial forecasting.
But with that potential comes a warning: quantum computing puts modern cryptographic systems at serious risk. The same computational benefits that make quantum computers a breakthrough for scientific research are the ability to compromise classical encryption methods used in our online security.
Implications for Current Cryptography
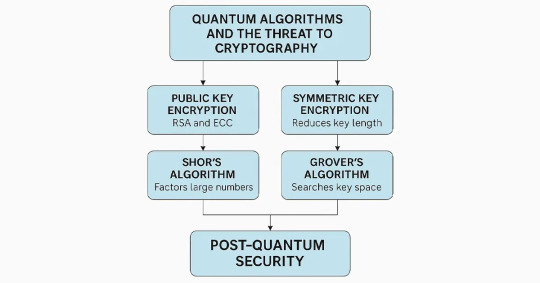
The dominant modalities of the modern digital infrastructure are based on the use of public key cryptography, and such systems as RSA and ECC are among the most widespread representations that people use. These encryption systems are based on mathematically difficult problems for conventional systems — factorizing huge numbers or solving discrete logarithm problems. These are exactly the sorts of problems a quantum computer is designed to demolish with impunity using expert algorithms.
Shor’s Algorithm, created in 1994, is likely the most famous quantum algorithm that targets RSA and ECC directly. It can factor big numbers exponentially quicker than the best-known classical algorithms. When quantum computers are ready — usually called “quantum supremacy” — they will be able to decrypt secure communications, financial transactions, and private information that are now thought to be secure.
Another significant algorithm, Grover’s Algorithm, doesn’t shatter symmetric crypto systems but narrows down their security levels significantly. It indeed cuts a symmetric key’s bits in half, so 256-bit keys would provide only 128-bit security in the quantum age. Less devastating than Shor’s impact on asymmetric crypto, though, Grover’s Algorithm does mean a reconsideration of the dominant symmetric encryption algorithms.
This new threat brings to the forefront the need for post quantum security solutions in an immediate manner. Unlike conventional cryptographic practices, post quantum security is about designing and deploying algorithms that are secure even when quantum computing resources are available. These algorithms are based on challenging mathematical problems for which quantum computers are not yet known to solve efficiently.
The Urgency for Transition
Post quantum security is not a theoretical concept; it’s an urgent, real-life issue. RSA- or ECC-breaking large-scale quantum computers don’t exist yet, but breakthroughs are on the move. The collaborative efforts of governments, corporations, and research bodies across the globe to create quantum technology imply that these machines will soon become real.
There is a dire need to secure the digital infrastructure of organizations, for when quantum technology is available. Transitioning to post quantum security protocols is difficult and time-consuming, not only swapping cryptographic algorithms but also rewriting software, hardware, and communication protocols. Waiting for fully functional quantum computers may expose systems and data to attacks.
Further, hacked encrypted data today can be stored and decoded at a later date after computers develop the capability — the “harvest now, decrypt later” attack. As a countermeasure post quantum security ensures valuable information is safeguarded both today and in the foreseeable future.
The U.S. National Institute of Standards and Technology (NIST) has already started standardizing quantum-resistant algorithms with its Post-Quantum Cryptography Standardization Project. Organizations can standardize their security approach with international best practices for post quantum security using NIST-recommended solutions.
What Is Post Quantum Security?
Post Quantum Security is a term that is used to refer to cryptographic methods that are resistant to attacks carried out by entities that can run large quantum computers. Besides, this category includes the quantum-resistant hash algorithms, encryption algorithms, and digital signature algorithms. These systems are being standardized by efforts such as NIST’s Post-Quantum Cryptography Project.
Embracing Post Quantum Security guarantees that long-lived sensitive information, such as medical records or financial contracts, is still protected even when intercepted today and decrypted in the future quantum world.
ncog.earth incorporates Post Quantum Security into its core blockchain protocol. It provides data security for decades in a post-quantum secure environment.
Core Principles of Post Quantum Security
Below are the fundamental principles that constitute this new field and how they interact with each other to protect digital property during the era of quantum computing.
1. Quantum-Resistant Algorithms
Post quantum security is centered around quantum-resistant algorithms, which are designed to stand up to attacks both from traditional attack methodologies as well as attacks performed with a quantum computer. These algorithms don’t depend on the weak assumptions of the classical encryption methods like RSA or ECC, which can be attacked and broken by quantum algorithms like Shor. Post quantum security instead depends on mathematical problems with cryptographically amicable properties that are difficult for an efficient quantum computer to solve.
Among the most promising quantum-resistant solutions are-
Lattice-based cryptography: Lattice-based cryptosystems rely on the computational subtlety of such problems as the Shortest Vector Problem (SVP) and the Learning With Errors (LWE) problem. They are classical and quantum resistant and thus well positioned to protect encryption, digital signatures, and key exchanges.
Hash-based cryptography: Founded on extensively studied hash functions, this method effectively generates secure digital signatures. Because hash functions are one-way functions, they are extremely secure even against quantum attackers.
Code-based cryptography: Founded on error-correcting codes, this method has stood the test of time for more than four decades. It is strong, well-established, and extremely efficient for encryption and digital signatures in a post quantum security scenario.
Multivariate polynomial cryptography: The hardness of these problems is essentially dependent on the intricacies of solving multivariate quadratic systems of equations, which are intractable for quantum and classical systems.
Deployment and selection of these algorithms are being standardized by bodies such as NIST, which is finalizing a suite of post-quantum cryptographic standards for ease of global implementation of post quantum security protocols.
2. Forward Secrecy
Forward secrecy is yet another significant post quantum security parameter. In the conventional crypto paradigm, it might be possible that breaking a private key today can expose attackers to decrypted communications in the past and future, and it is highly risky if, in a quantum paradigm where harvested encrypted data from today can be broken using quantum computers in the future.
Post quantum security addresses this issue by guaranteeing that even when an encryption key is finally breached, past messages cannot be decoded after the fact. The method is to repeatedly generate ephemeral keys that don’t survive and aren’t easily linked up with each other. Forward secrecy is significant not just for private individuals but for protecting business networks, government files, and money networks as well.
Essentially, forward secrecy reconfigures the way we approach long-term data secrecy, particularly considering the danger represented by “harvest now, decrypt later” attacks facilitated by quantum advancements. In post quantum security, it’s a solid pillar of real future-proofing.
3. Hybrid Cryptographic Models
With the indefinite time frame of quantum progress, most organizations are taking a hybrid approach that brings together classical and post-quantum-resistant cryptography. The cryptographic models are created to fill the security gap during the transition phase when the existing traditional algorithms exist side by side with the post quantum security algorithms.
In a hybrid method, two sets of algorithms are run in parallel. One set offers backwards compatibility with current infrastructures, and the other offers immunity to future quantum attacks. As a simple example, an end-to-end communication channel could employ RSA in conjunction with a lattice-based encryption scheme at the same time. This means that even if the classical part is compromised in the future, the post quantum security layer still protects the underlying data.
This method has some advantages-
Gradual roll-out: Businesses can deploy systems gradually without affecting current services.
Redundancy: Having several levels of encryption offers a backup in case one algorithm is compromised.
Testing ground: Testing the deployment of quantum-resilient tools identifies real-world problems and solutions before mass deployment.
Hybrid deployments are not long-term, but they are essential stepping stones. With increasing trust and confidence in post quantum security technology, hybrid deployments will ultimately make way for fully quantum-resistant architectures.
Why Businesses Must Act Now

In the unfolding digital age, while cyberattacks increase in scale and sophistication, quantum computing’s emergence is at once a dazzling technological advancement and an intrinsic cybersecurity challenge. To companies — particularly those holding sensitive customer data or conducting business in highly regulated industries — the time to prepare is not in the future but today. Post-quantum security is no longer an idealistic aspiration but rather a concrete reality. Forward-thinking companies need to take action today to ensure that they will be able to withstand future cryptographic shocks.
Quantum Threats Are Nearer Than They Seem
The power of quantum computers is that they can use superposition and entanglement to exceed classical machines in certain forms of mathematical operations. The possible advantages that such technology could offer to drug discovery and logistics, as well as machine learning, are substantial, but this danger also undermines the encryption protection that enshrines secure digital communication, financial systems, medical records, and contracts.
Algorithms such as RSA and ECC, the basis of modern public-key cryptography, could be made obsolete by quantum algorithms such as Shor’s. In practical terms, what that would mean is to make information currently encrypted under these systems decrypted within seconds if there existed a sufficiently large quantum computer. The potential effect would be disastrous to companies experiencing huge-scale data breaches, litigations, and erosion of customer confidence.
That’s why post quantum security must be implemented far ahead of the wholesale arrival of quantum computing. Companies that delay are not only taking a risk — they’re deliberately putting their businesses, data, and reputations in long-term jeopardy.
Data Longevity Brings the Risk into the Present
One of the least considered measures of quantum risk is data longevity concern. Whereas real-time data spoils at a fast pace, some forms of data — medical history, legal papers, government agreements, and intellectual property — are priceless for decades or years. If today a cyberattacker got hold of encrypted information, they would be unable to decipher it. But with the advent of quantum power, the same information can be accessed in the foreseeable future. The label is also applicable when talking about attacks referred to as “harvest now, decrypt later”.
On this front, post quantum security plays a twofold role: it safeguards against the threat at hand, but also against potential attempts to decrypt in the future. For businesses tasked with securing data over the long term — insurance providers, banks, and law firms, for example — it is critical that it is pre-emptive. Delaying the implementation of quantum-resistant practices creates a bombshell situation where encrypted files stored could be cracked open at any moment.
Consumer confidence is perhaps the most precious asset of the online marketplace. With high-profile breaches becoming the norm, customers are growing more attuned to where their information lives and how it is secured. Companies that act early to publish quantum security standards communicate that they are serious about leading-edge data protection and customer privacy. This method contributes to the creation and preservation of a reliable brand and earns the loyalty of the clients.
Additionally, regulatory landscapes are changing. Global data privacy legislation like the GDPR, HIPAA, and CCPA demands secure data security procedures, and compliance systems will shortly be following close behind in counteracting quantum-age attacks. Adopting post quantum security today allows organizations to protect themselves against future compliance mandates and sidestep the prohibitively cost-intensive exercise of currency flows.
Smooth Transition Through Strategic Planning
Post quantum migration is not a flip-of-the-switch transition — it requires thoughtful planning, testing, and staged deployment. Businesses must assess their existing cryptographic infrastructure, identify vulnerable endpoints, and decide which quantum-resistant algorithms will best meet their operational needs.
Fortunately, most businesses are not beginning from the ground up. Hybrid crypto designs — blends of conventional and quantum-resistant solutions — permit phased and secure adoption. Post quantum security is viable through hybrid approaches that support organizations in adopting post quantum security without sacrificing current system performance or compatibility. Phase by phase is the way, causing as little disruption as possible while providing security for important information at each stage.
They also must spend on training and awareness programs. Decision-makers, developers, and cybersecurity staff must be made aware of the effects of quantum risk and the pragmatic actions that go into minimizing it. Post quantum security incorporated into cybersecurity roadmaps now will have companies not lag when the quantum era is in full force.
Building Quantum-Resilient Ecosystems
The truth is, cybersecurity is not an isolated practice. A majority of businesses employ third-party suppliers, cloud computing providers, and digital platforms that touch or have access to sensitive information. Having a secure digital environment is a matter of discussing post quantum security with partners and suppliers.
Leading organizations are now starting to measure their supply chains and expect quantum-readiness from their partners. Organizations can minimize systemic vulnerabilities and foster increased collective resilience by establishing post-quantum security as an expectation within ecosystems.
Integrating Post Quantum Security into Your Infrastructure
With continued advances in quantum computing, the danger that it poses to classical cryptographic schemes is more dire. Companies and enterprises cannot afford to wait. There is a need for a transparent and systematic adoption of post quantum security protocols into existing IT infrastructures so that data confidentiality, integrity, and availability are preserved under quantum computing. This has to be done with a strategic roadmap of action covering technology and operations transformation across the digital landscape.
For this transition to be made possible, organizations can utilize a multi-step process that will establish quantum resilience without disrupting essential services. Below, we outline the four main steps of incorporating post-quantum security in your infrastructure.
Audit Your Current Cryptographic Inventory
Before any change is implemented by companies, they must start by defining the scope and utilization of current cryptographic assets. Any effective post quantum security project is based on a thorough cryptographic inventory. This process entails determining where and how cryptographic algorithms are utilized — on SSL/TLS certificates, database encryption, secure email, authentication protocols, digital signatures, API gateways, mobile applications, VPNs, and IoT devices.
This audit must encompass-
Encryption Algorithms Used: Assess if systems are using RSA, ECC, or other vulnerable algorithm-based encryption.
Key Sizes and Expiration Policies: Document existing key sizes and assess how often they are being replaced.
Cryptographic Libraries and APIs: Check for dependencies and assess compatibility with quantum-resistant alternatives.
Certificate Authorities and Issuance Policies: Examine methods of distributing, retaining, and withdrawing digital certificates.
When such data is analyzed, it is possible to identify weak points and establish priorities for strategic transition to post-quantum security. Notably, the process helps organizations to review the data lifecycle and determine long-term sensitive data that needs to be secured today against tomorrow’s quantum decryption power.
Select Quantum-Resistant Algorithms
After identifying your cryptographic footprint, the next step is to select quantum-resistant alternatives. NIST has worked with others to initiate multi-year standardization efforts that will evaluate and promote post-quantum cryptography algorithm recommendations. These algorithms are designed so that they can resist attack by both classical and quantum computers and include key encapsulation processes and digital signature protocols.
Among the most promising contributions to come out of the NIST project are-
CRYSTALS-Kyber (for public-key cryptography and KEM)
CRYSTALS-Dilithium (for digital signatures)
FALCON and SPHINCS+ (signature schemes with performance profiles of differing types)
In choosing algorithms, implementations must consider performance, resource efficiency, complexity to implement, and the extent to which the solution they choose fits their infrastructure. For instance, IoT devices that have little power may need lightweight algorithms, but high performance servers are more than capable of handling complex computing activities.
Selection of the best algorithms is immensely important for effective post quantum security integration. Future-proofing should also be a consideration for security teams as quantum-resistant cryptography develops. Modular architecture solutions for cryptography allow for a seamless switch or upgrade of algorithms as new standards become available.
Use Hybrid Cryptographic Systems
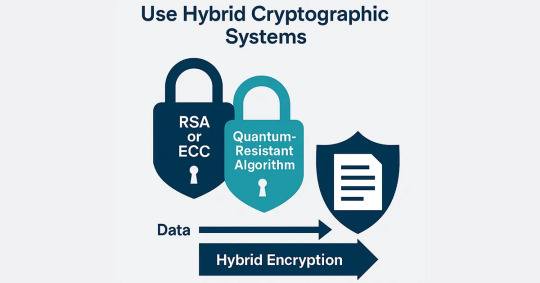
It is not necessary to move away from classical to quantum-resistant cryptography completely. One of the most recommended practices while transitioning to post quantum security is the use of hybrid cryptographic systems. These use current (classical) cryptographic algorithms and couple them with quantum-safe algorithms to provide a multi-layered defense.
In a hybrid system, data is encrypted with both RSA (or ECC) and a quantum-resistant algorithm. It makes the system both backward compatible as well as future-proof against attacks based on quantum. Although quantum computers are unable to break today’s classical encryption now, hybrid encryption protects the data from being exposed in the future, most beneficial for long-shelf-life sensitive data.
Hybrid deployments also enable companies to pilot the in-the-wild usage of post-quantum-safe algorithms without removing trusted current defenses. Phase-in of post quantum security in this manner prevents service disruption, lowers operational risk, and enables incremental testing and tightening.
Key libraries and frameworks increasingly start to include hybrid support. For example-
OpenSSL (with quantum-safe branches)
Cloudflare and Amazon Web Services, which have begun to experiment with post-quantum TLS deployments
Mozilla and Google, pioneering early hybrid deployments in their browsers
These initial hybrid adoption attempts show the growing traction for post-quantum security and offer in-the-wild blueprints for companies willing to make the transition.
Upgrade Key Management Systems (KMS)
The key to the efficiency of encryption lies entirely in the responsible use of its keys. Infrastructures that are quantum-resilient need updates to legacy Key Management Systems (KMS) to accommodate the special needs of post quantum security…
#post quantum#post quantum security#technology#ncog#post quantum blockchain#post quantum encryption#post quantum cryptography#decentralized database#quantum computer#quantum computing#quantum computers#post quantum secure blockchain#rsa#shor algorithm#quantum-resistant cryptography#ECC
1 note
·
View note
Text
Cybersecurity takes a big hit in new Trump executive order
Provisions on secure software, quantum–resistant crypto, and more are scrapped.

Cybersecurity takes a big hit in new Trump executive order
Archive Links: ais ia
#bgp#biz-\u0026-it#encryption#executive-orders#policy#quantum-computing#security#trump#white-house#[#]
0 notes
Text

Awesome! Scope's Quantum Security Mobile App Secures Funding Scope Technologies secures $1.5M to accelerate its QSE quantum security mobile app. Offering advanced, user-friendly quantum-resistant encryption and secure file sharing.
Read more
#quantum security#mobile app#data encryption#cybersecurity#quantum-resistant#Scope Technologies#QSE mobile app#First Majestic Silver
0 notes
Text
The Importance of Data Encryption in 2025: Why You Can’t Ignore It
Introduction Imagine waking up one morning to find your personal data, financial records, or business information leaked across the internet. Sounds terrifying, right? That’s the reality many individuals and businesses face today without proper encryption. As we move into 2025, data encryption isn’t just an option—it’s a necessity. With cyber threats evolving rapidly, encryption acts as a…
#AI and cybersecurity#cloud security encryption#cybersecurity in 2025#data encryption best practices#encryption for businesses#future of encryption#post-quantum cryptography
0 notes
Text
Quantum Computing Is Here, and It’s About to Change Everything
Imagine a world where your favorite apps load in the blink of an eye. In this world, doctors discover life-saving drugs in weeks instead of years. Your AI assistant actually gets you. Sounds futuristic, right? Thanks to the advent of quantum computing chips, that future is just around the corner. Buckle up, because this isn’t just a tech upgrade—it’s a total revolution. Your Daily Tech Just Got…
#climate solutions#encryption#faster apps#financial tools#future of tech#green technology#healthcare technology#quantum chips#quantum computing#secure communication#smarter AI#smarter apps#tech innovation#VR gaming
0 notes
Quote
Quantum computing – which harnesses the discovery that matter can exist in multiple states at once – is predicted to have the power to carry out far bigger calculations than previously possible and so hasten the creation of nuclear fusion reactors and accelerate the impact of artificial intelligence, notably in medical science. For example, it could allow MRI scans to be read in atom-level detail, unlocking new caches of data about human bodies and disease for AI to process, Google said. But there are also fears that without guardrails, the technology has the power to crack even the most sophisticated encryption, undermining computer security.
Google unveils ‘mindboggling’ quantum computing chip | Computing | The Guardian
#google#quantum computing#technology#chips#ai#ethics#morals#compulsion#future#future now#privacy#encryption#security
0 notes
Text
youtube
#quantum computing#Chinese#encryption#RSA#post quantum encryption#hacking#security#cybersecurity#Youtube
0 notes
Text
The day has come!! The first finalised PQC standards have been published - 1 key encapsulation mechanism standard and 2 digital signature standards.
I’ve been creating a public github repo for anyone curious to find out more about quantum preparedness here - let me know any feedback!
#pqc#quantum#physics#maths#cryptography#cyber security#cybersecurity#post quantum cryptography#NIST#encryption
1 note
·
View note
Text
But like of each thing that in season grows
Summary: How a kind gesture can lead to something more. One shot.
Pairings: Loki x Female Reader
Warnings: Christmas fluff, mention of off screen assault, some swearing, lots of snow, books, poetry, smutty smut.
A/N: Okay, look. It just wanted to get out. You’re thrown in without a warning, nor a floatie. Apologies for the liberties taken to interpret and manipulate characters to dance after my will once more. Obviously don't read if you're a minor.

9~9~9~9~9~9~9~9~9~9~9~9~9~9~9~9
The greatest ideas were conceived in the shower. That was a scientific fact.
You liked facts. You did not like uncertainties or speculation. The feeling of being in limbo was something that didn’t sit right with you.
So as you were in the shower, working the conditioner in your hair, the idea was just there. It was simple, humble, but beautiful. Your hands slowed and stilled. And then your mind rebooted and went at lightning speed, planning things out. You needed to write things down.
You stepped out of the shower hurriedly, towelling down your body, before realising that your hair felt different. Cursing, you stepped back under the water to rinse off the conditioner.
*****
You hated staff meetings. Particularly third Thursdays staff meetings, because they dragged on and on. The weekly mission reports were presented and Fury insisted on inviting some guest speakers. He called it “Horizon Thursday”.
In your opinion it narrowed rather than widened it. Today’s guest speaker was Quinn Harris, cyber security specialist. You suspected self-proclaimed, but you hadn’t bothered doing a deep dive on him.
You were sat on the increasingly uncomfortable chair, rows of employees in front of you, the Avengers at the very front. Rogers had delivered his usual military style mission report, the other members of his team trying to look alive, though you suspected Romanoff and Banner were asleep, as they were both donning sunglasses.
“What you need is a quantum computer and it’ll solve all your problems with encryption.”
“They might as well propose using block ciphers,” you murmured under your breath, turning the page in your book.
Meanwhile, a hand shot in the air at the front. “Excuse me, Mr Harris.”
The man smiled. “Mr Stark, do you have a question?”
“Well, not so much a question for you, but I would very much like the opinion of another expert on what you just said. You know, before anyone here thinks about investing in your product, which, let’s be honest, would be me. I’d like to be sure it’s the right thing.”
Fury rolled his eyes and sunk back in his chair.
There had been talk about getting that dude in? You must have zoned out for that part.
Harris’ face fell for a second, but he honed his features and forced a smile. “Of course.”
“It just so happens that we have an inhouse expert,” Tony got up and scanned the crowd. “Isn’t that right, Y/N?”
Everyone uniformly turned to look at you. Everyone.
You felt the moment one particular pair of eyes set on you. The amount of times you had spoken to one another had been limited to the missions you were needed on, for hacking. You’d had his voice in your ear a few times and it did things to your body that made you feel like a system overheat. You never really saw him during missions though as your job was very much office-bound.
Today, he wore the damn leather suit. Whilst Fury didn’t give a fuck, Rogers very much was all about the professional appearance of the Avengers. What you didn’t understand was why everything looked better on him. The black and green possibly was the best colour combination there ever was. The other day Bucky had worn a Slytherin pullover and even though it very nicely accentuated his physique, it looked nothing like the colours did on Loki.
You swallowed hard when you felt his eyes on you. They seemed to see right through you, even over the distance of the seven rows of chairs.
And then you felt the weight of all the other pairs of eyes on you. That was a lot of people. You gulped and pushed your glasses back up the bridge of your nose - a habit you couldn’t break.
“Y/N,” Tony called, bringing you back to the matter at hand. “Stand up and look at me.” His voice was gentle. “Start breathing again. Good. Now tell me what Harris is not telling me about the quantum computer.”
You adjusted your glasses again and cleared your throat. “It’s a solid proposition, I suppose,” you started, “however, one I would expect from a college freshman, certainly not from a cyber security expert specialist.”
Murmurs erupted, but you ignored them and rattled off your thoughts.
“Can a quantum computer crack asymmetric encryption algorithms? Yes. And yes, we all know that thanks to Shor’s algo the maths problems are only polynomial. Also, we know this applies to discrete log problems, too, therefore, all we’d need is a large enough quantum computer. Of course, he,” you gestured to Harris, “would have to build one first, which as you can guess is very costly. However, this entire presentation is based on the assumption that quantum computing is the end of asymmetric cryptography. And that is such a blatantly ignorant approach, with complete disregard for the safety of the members of our staff that are entirely reliant on the encryption cracking working on all their devices during operations and missions. And this whole quantum computer only works if you have a network connection.”
“So you’re suggesting there are hard problems that a quantum computer can’t solve?” Harris said, chin jutting out, arms crossed defiantly.
“Don’t be silly, of course there are,” you huffed. “I coded new post-quantum asymmetric encryption algos three years ago and tested them on several sites I am not authorised to disclose that have quantum computers. Not one of them cracked the simplest of those codes, in any of the over 5,400 attempts they ran over the past three years. So this presentation is… rather embarrassing in its sloppiness.”
“Well,” Harris’ lips were a thin line now. “I’m sure you have a ‘much better’ suggestion then?” He actually raised his hands to add the quotation marks.
“Actually, I do. I developed our own version of a quantum computer, at - and I’m only guessing here - a fraction of the price you’d charge Mr Stark, which can crack both symmetric and asymmetric encryption, works on all of our staff’s devices, portable and stationary, works offline and is about the size of, uh, a thumbnail.”
You pointed to your thumb, because in your humble experience men like him struggled to accurately size things.
Tony smiled and turned to Harris.
“Okay that concludes today’s meeting.” Fury got to his feet and patted Harris’ shoulder. “Looks like we’re good, but thanks for coming.”
People around you stood, some nodding at you as they passed. Tony caught up with you in the hallway. Before he could say something you blurted out: “Did I say something wrong? Was I rude again?”
He smirked and pushed the button of the lift. “He needed putting into place. Totally fine by me. You did great.”
“Stark!” bellowed Fury from down the hall and Tony winced.
“Excuse me, mother’s calling.” He turned and left.
You sidled into the lift with several other people. The cabin stopped a few floors up and people got off. That was when you noticed Loki on the other side of the lift. Up you went and after another stop you were alone with the Asgardian god. The cabin seemed to shrink.
You both watched the numbers climb, the lift hummed, Loki’s leather suit creaked softly as he crossed his hands behind his back.
“Could you please enlighten me about Shor’s algorithm?” he suddenly asked, looking at you.
You had a heart palpitation. Surely that was what it was. He was so impossibly tall and sculpted and… here.
“Um,” you pushed your glasses back up, “it’s a quantum algorithm for finding the prime factors of an integer.”
Loki’s face looked blank.
“It, er, essentially it finds the prime factors of large numbers a lot faster than conventional computers do. Which we use in encryption. The large numbers, that is. So it cracks codes faster.”
“Ah,” he said, head turning back to continue staring at the number display. “Thank you.”
“You’re welcome,” you croaked out.
The urge to facepalm burned under your fingers, but you resisted. As soon as the doors slid open on your floor, however, you fled and sought asylum in the ladies’ toilets, banging your head against the wall of the stall.
*****
Operation Great Idea was in full swing.
So you’ve had a little personal setback, but that didn’t deter you from the objective. You had compiled a list, one you were confident was accurate based on your intel and research. That very list was neatly folded in the deep pocket of your coat as you walked through the cold rain on this late November afternoon.
Yes, you did something you’d never done before - take an afternoon off - and were trying to evade puddles on your way to the bookshop. Could you have ordered the books online? Most of them, certainly. But your late mother, an independent business owner, had ingrained in you to support local shops. You liked bookshops, they reminded you of her and of simpler times.
Your timing was excellent - of course you had researched when the shop was least busy - and you practically had the shop to yourself. And so you walked, dragging a pull-along basket behind you as you searched the shelves for the books on the list.
Sometimes, there were different editions there and you stood for a while, feeling the weight of each book in your hand, the feel of the embossed letters on the spine, the scent of the pages. You wanted it to be just right, so you took your time.
Some of the books you would only be able to get in a little second hand bookshop, tucked away in a side street. You had called beforehand and the owner lifted a box from under the counter to show you what she had reserved for you. As soon as your fingers made contact with the books you felt absolutely giddy.
Back at the Tower, you spent two entire evenings wrapping books after work. When you were finished, you leaned back, looking at the neatly organised stack. Yes, you were ready. Now all you needed was an exorbitant amount of luck for the next 24 days.
*****
You watched Loki stare suspiciously at the first parcel. He was sitting in the communal kitchen, Thor next to him.
“Why would it be hexed?” Thor asked. “Simply because the sender is missing?”
Loki just gave him a pointed look.
“Come, brother, aren’t you curious to find out what is in this gift?”
“Loki got a present?” Steve asked as he pulled a bowl out of a cupboard. “Did I miss his birthday?”
Before Loki could say anything, Thor shook his head. “He’s worried it has been tampered with.”
Roger’s brows furrowed. “How did it get into your possession?”
“It was on the floor outside my door this morning,” Loki complied, sighing.
“FRIDAY would have picked up on any foreign substances or intruders in the tower,” Tony said between gulps of coffee. “He now can detect traces of magic, too. ‘Course, he went apeshit over your magic, but we got it under control, eventually.”
“That’s what all this ‘Alert, alert, magic detected, caution advised’ blaring at five in the morning was?” Scott bustled in.
A slight tinge of red shaded Loki’s complexion. “I have to practise some time.”
“Thought you were born with it?” Scott interjected, helpfully.
This earned him a glare. “I was born with the aptitude for magic and sorcery. It takes a lot more than mere talent to achieve this level of proficiency.”
“Several centuries, in fact,” his brother supplied. “Now then Stark here says it’s safe. So open it, brother!” Thor clapped his hands together.
Loki indignantly and very reluctantly slid the parcel towards him and pulled on the simple string that held the wrapping together. The paper fell open to reveal one of the books you had picked.
From your vantage point of, well, your computer screen, you zoomed in to get a better look at him.
“Oh, a book,” you heard the onlookers muttering disappointedly, quickly losing interest and going about their business once more.
But Loki just sat, staring at the book. It took him a good few minutes to pick it up. And he did what you had seen him do many times before. He weighed it in his hands, fingertips running over the cover, the spine. Then he opened the lid. To anyone else it might not have been noticeable, but to you it was: he inhaled the scent of the book. And finally, there was the smallest upturn of his lips.
You exhaled, relieved. One down 23 more to go.
*****
Over the next week you were too busy testing the new firewall you had developed to check on Loki’s reaction. Sometimes you felt a little self-conscious, scared even that he might not like the books or think this was from a stalker. Which technically you had indulged in, stalking that was, but only to find the perfect books for him. And then sometimes you would get worried that someone else might have found the presents.
But you knew he had received every single one of them, for every evening, when you passed the common area you saw him sitting on the couch with the latest offering in his hands. Perhaps it was wishful thinking, but it looked as if his tense shoulders had started to relax a bit.
Another couple of days went by and as the decorations started to pop up in the Tower and the first snow fell that didn’t immediately melt or turn to mush you felt happy. Perhaps it also had something to do with the fact that a certain someone walked differently. Maybe it was your imagination. But he seemed even taller these days.
*****
“Did it work?” you heard his voice in your ear a couple days later.
The data set was streaming on the screen in front of your eyes. “It did. Give me a moment to inject the virus, then you can disconnect the USB cable.”
“Can I still talk to you?”
Your fingers on the keyboard stilled for a moment, surprised. “Of course. The program runs through your phone, not through comms.”
There was a little pause, before he said: “I have a question. About a Midgardian tradition.”
You wrinkled your nose, scanning the code rushing over the screen. “I’ll try my best, but I’m rubbish at traditions.”
The audible outbreath sent shivers down your spine. “I’m sure that’s not true.”
“What’s your question then?”
“Tell me about the Yuletide calendar.”
45% done. “You mean the Advent calendar?”
“Precisely.”
This was dangerous territory you were treading on. “Oh, it’s a fun thing for kids, really. To make the wait for Christmas a bit more exciting and I guess more bearable. It’s nice to get a little something like a toy.”
“Is it always toys?”
69% now. “Well, no. My mum used to get me an advent calendar that had these lovely drawings behind each door. I hung it up in the front room and we’d open it together every morning.”
“I suppose it’s a nice custom,” he said, before asking, “What about grown ups, do they have advent calendars?”
83%. “Sometimes. There’s all sorts: beer, wine, beauty products, chocolates - you name it, it probably exists somewhere.”
“Books, too?”
The question threw you, did he know it was you? A light was blinking on your screen.
100%.
“That’s it, Loki, the virus is uploaded, you can unplug the cable now and get out of there.”
“Thank you, Y/N.”
You heard a crackle and the comms was handed over to operations again. As you finished running the decryption programme on the data Loki had extracted, you kept hearing his voice in your head.
“Books, too?” Were you busted?
*****
Security breaches were both an insult as well as an admittedly welcome challenge to you. Someone had tried to flex their fingers - and you had a very good idea who - to break into Stark’s network. They had managed to pierce a little hole into the outer layer of the firewall, but they didn’t know that you had several back up plans in place and you enjoyed watching them work. However, as you scanned over the intruder’s code you devised a new security strategy.
You were in the middle of coding a nice little primer for a new layer - unexpected because of its simplicity, but a tough little nut to crack - when someone cleared their throat next to you. You looked up to find Loki, his eyes fixed on you. You blinked, looked around, but no one else was there, and back up at the god.
“Can I, uh, help you?” Smooth. You facepalmed internally.
“I realised I have never been in here,” he said, looking around the room, then back at your desk. “You have a lot of monitors.”
You waved your hand dismissively. “Just the standard three.”
“What are you doing now? Or is it a secret?”
“It’s not a secret at all. So we’re currently under attack. Relax,” she said when she noticed him tense, “cyberattack. Someone’s knocking at our backdoor, trying to see if they can get in.”
You motioned to one of your screens. “This is the intruder’s code. He’s trying out lots of keys to see if he can get in. And this,” you pointed to the screen next to it, “is our defence mechanism.”
“Extraordinary.” Loki’s low voice murmured. He was close. You turned your head and nearly had a heart attack at just how close. His sharp profile was illuminated by the blue glow of the monitor, his hair falling to his shoulders, one hand splayed on the desk, the other resting on the back of your chair. He looked beautiful. Perfect. He was leaning closer to the screen so he could see what was going on. Your breath hitched.
And then he turned his head.
Something that sounded an awful lot like a squeak escaped your throat.
Loki lifted an eyebrow. “Am I making you nervous, Agent Y/N?”
You pushed your glasses up your nose and leaned back, just an inch. “No?”
Loki’s eyes drifted over your face, before they met your gaze again. “Is that a question or a statement?”
“A… a statement,” you mumbled and, for good measure, added, “sir.”
His eyes darkened, a smirk curling the left side of his lips. “Are you scared of me?”
You tilted your head ever so slightly. “How can I be scared of you?”
“You’ve heard the stories, undoubtedly.”
“I did. And if I believed everything people told me and not looked beyond I would be incredibly shitty at my job.”
He smiled at that. It was small, but there, and it made him so attractive you felt your stupid heart starting to pound in your chest. Could he hear it?
“Do you like to read, Agent Y/N?”
Another adjustment of your glasses. “I do.”
“What would you say is your favourite book?” His voice was low and smooth.
His hand moved from your desk to the side of your face, where he gently pulled on a tendril, before he brushed it behind your ear. The back of his fingers skimmed your cheek for less than a second, but it sent you reeling. It was as if an electromagnetic pulse was slowly wiping clean your hard drive. You couldn’t think.
“Um, err, Jane.. Jane Eyre.”
He hummed. “I wonder why? Is it because she’s abandoned and rejected all her life?”
You shook your head slowly. “No. Because she’s forced to leave home, into a life she didn’t choose. But when she is given the freedom and space to grow she learns to be the master of her happiness.”
His eyes followed the curve of your neck and back up again. It almost felt as if he was touching you. “Interesting.”
You swallowed again, before he stood upright, nodded at you, turned and left.
Your heart was pounding. And then your computer beeped and your attention was back on the screen.
“Oh pants…” Your fingers started flying over the keyboard. “Not today, Harris. Or any other day.”
Nine more books to go.
*****
He was onto you. Of course he was. After all, he was the God of Mischief and Lies. If anyone would find out who was behind this, it would be him. Personally, the preferred outcome was that he never would find out.
You had asked yourself often over the last 18 days why exactly you wanted to do this for him. But that was just it. You really had no other motive than wanting to do this for him. Maybe because you sympathised with him, being stuck somewhere far from home, feeling lonely and not really integrated. Maybe you had projected your own feelings onto him a tiny little bit. Possibly considerably. However, it was done with the best of intentions. You wanted to make this nice for him. The run up to Christmas. A little bit magical. He must like magic, he was a sorcerer after all, wasn’t he?
So what if you had started dreaming of him at night. He would lean over you as you sat at your desk, in all his tall- and broadness. This time his hands would be touching you. And he’d lean in to whisper into your ear. Admittedly, not words you would necessarily associate with such a situation.
When you would wake up you knew where to place the things he said to you in your dreams. He’d said them to you during missions. And yes, “how much longer till the download is complete, Agent Y/N?” was not remotely as sexy as “I’m going to ravish you now, thoroughly” would have been, for example. But your brain only had so much to work with and it worked for you.
You noticed a few things, however. Loki was around more often, probably just a silly coincidence, or you had started to pay more attention. He looked at you now. You’d look up and find him already looking at you, sometimes a little smile crossed his lips, but mostly it was just something with his eyes, they seemed… warmer, maybe?
However, to your horror you discovered that you had started to blush. Every single time this happened. So you spent a lot of time in the ladies’ toilets, splashing your face with cold water, only to see it even more flushed than before. Apparently, all the books you had read lied about that ‘splashing your face with cold water to calm down and not make people notice’-thing.
But it all boiled down to the fact that he was onto you. Maybe he was humouring you and seeing where this was going. Maybe he had found out already and you made him feel awkward. Or he was waiting for the opportune moment to expose and humiliate you. You weren’t sure which.
Right now it didn’t matter. You were so tired you could hardly see properly anymore. So when you decided to crash on the sofa in the common room, because it was halfway to your room, you didn’t think to check if anyone was there.
That was mistake number one.
You collapsed onto the sofa with a groan, eyes closed, head leaning against the back of the sofa.
“Fuck. My. Fucking. Life,” you complained to the universe. “Can you please make the appendage of that misogynistic wanker fall off already? For fuck’s sake!”
Mistake number two.
Someone chuckled. It came from rather close to you.
Dread filled you. Foul language was not tolerated in the workplace. To be fair you could argue that the common room was not your workplace per se, however, you did not want to start arguing with HR because they were absolute savages in the art of word twisting. Or just savages full stop.
Carefully, you cracked your eyes open. And there, on the sofa right next to you, sat Loki. One leg was stretched out in all its glorious length, the other bent at the knee, his forearm resting over it, the book in his lap now closed, one of his slender fingers acting as bookmark. For a moment you wondered what it would feel like to be the book.
“I hope it’s not my appendage you’re asking to be removed,” he said with a smirk.
You grappled to sit up, horrified. “Of course not! That would be awful… I mean, a terrible thing to wish for… you’d… err… such a loss of such a beautiful… I mean, I can only guess… but… um, err… heavens, please make me stop talking…”
You hid your head in a throw pillow, wishing the floor would open up and swallow you whole.
Mistake number three.
The sound of a low, rumbly laugh made its way to your ears. It entered your system like a virus, leaving your limbs feeling weak and yearning. Was Loki laughing? You lifted your head and watched him, highly bemused at your idiotic display.
It was the most beautiful thing you’d ever heard. You felt a hard tug at your heart. Goodness, if this man wasn’t already a god, you’d have to declare him one. If he were the head of a religion you would throw out your atheist views and follow him to the end of the multiverse. He looked absolutely breathtaking. Then again, when did he not?
“I’m so sorry,” you started to apologise, “I don’t know what-”
With superhuman speed he moved and sat next to you, his finger on your lips. The feel of his digit on your mouth felt more intimate than any sexual intercourse you’d ever had.
And then he leaned in.
He was so close your cells were basically breathing him in. His eyes were locked onto yours and nothing would have been able to make you look away right then.
“Do you want to know what book I’m reading right now?” His quiet words did things to your insides that were not legal.
You just about managed to nod, his finger still in place.
“‘The Remains of the Day’ by Kazuo Ishiguro. Do you know it?” He waited for your affirmation. “It’s about a man who is in love with a woman. But he doesn’t tell her. When they meet again after decades, she tells him her life would have been different if she had married him. And you know what he does? He still won’t admit his feelings to her. He walks away from her. The first time he lets her go, the second time he walks away.”
You remembered the book very well. You had picked it out for him, after all.
“It’s a cruel story, Y/N. A love that is never acknowledged, nor consumed.” Loki’s eyes drifted from yours down to your mouth. His finger slowly traced the outline of your lips. It was too much, your eyes closed.
“Do you think love is this cruel?” Loki asked quietly. You felt his words as he spoke them almost onto your skin. So close.
“It-it can be,” you whispered. “But maybe, maybe that wasn’t the point of the story.”
“No?”
You opened your eyes to find him looking at you. He’d moved away a bit, giving you some space, waiting for you to elaborate.
“Maybe the point was to show that he chose his job over love. Twice. You can call it dignity or pride, but at the end he’s alone. Without love.”
“What about you, Y/N? Do you have love in your life?”
You weren’t able to look into his eyes. Slowly, you got off the sofa. You turned back to him to respond to find he’d stood up, too.
You looked down at your shoes. His shoes were black, of course, polished, perfect, like him. Yours were several seasons old. Worn. A bit of the shoe sole had started to peel off at the top of your toes. The bit you always kicked into the floor when you worked.
Your eyes wandered up his trousers, black, to the belt, his pullover, also black. He looked effortlessly elegant, poised. You, on the other hand, looked a mess, even in your work attire. Your heart grew heavy at the realisation. Your dreams were stupid. Turned out your heart was even more stupid. And suddenly you felt incredibly small in more ways than one next to the tall, powerful god.
Swallowing a lump in your throat, you said: “I have known love, once. A long time ago.”
With that you pivoted on your heels and left, leaving Loki alone in the common room.
*****
Harris was an absolute tosser.
He just couldn’t leave things be. He insisted on trying to show you up, so he tried and tried to hack his way through your firewalls. Of course he had tried to hide his identity and it had made you chuckle, because you seriously had no idea how he could ever dare call himself a cyber security specialist if he covered up his tracks like a novice hacker.
In a way it was cute, but it was getting to the point of obsessive stalking and you frankly were rather tired of this little game by now. Particularly, since it kept you from your nice, warm, comfortable bed well past midnight.
However, Harris seemed to have changed tactics and started to badmouth you in the industry. Even Fury had called Tony and asked whether he should be worried, because Harris had dug up some hacking you’d done when you were much younger and much less ethical. Really it was unhinged, but everyone worked through teenage years in their own way.
You only knew this because you happened to be in Tony’s office and he had Fury on loudspeaker. Tony had pacified Fury without batting an eye, then hung up and asked if you’d be okay with him paying Harris a little visit, preferably as Iron Man. You had both laughed it off. But it bugged you.
So when you were on your way back to the tower from the compulsory (for all employees) counselling session and someone grabbed you, you weren’t surprised to come face to face with Harris. He didn’t lay a finger on you. No, he got two goons to do that for him.
Later, as you stumbled out of the lift and along the corridor, trying to make your way to your room, someone blocked your way.
“Speak of the devil! Y/N! We were just talking about you.” Tony. Other voices around him.
You kept your head down, thinking of how to get out of this unnoticed.
“We were just wondering if– Y/N? What happened?” You saw Tony’s hand reach out for you, but you flinched away.
Silence fell for a long moment.
Then a movement. Shoes appeared in your line of vision. You knew those shoes well. They had been on display on the couch for the past 22 days, attached to an Asgardian god.
He slowly held out his hand, palm up. An assurance, no harm. You gave the slightest nod. He moved the hand up and placed a finger under your chin so carefully you wanted to sob. The faintest of pressure had you lift your head to look up at Loki. His eyes scanned your appearance, stopping at your bruised hands that were trying to hold together your coat, taking in the blood splatters on the fabric, your busted lip, the lopsided glasses, the badly bent temple dangling off its hinge.
You never understood the expression ‘his features darkened’. You did now. Loki’s face transformed and you saw for the first time what a dangerous man he could be. Power radiated off him. You were glad it was not directed at you. His nostrils flared and you almost heard how much he was clenching his teeth.
“Names,” he ground out.
A hot tear rolled down your cheek and now that it started it didn’t want to stop. His eyes softened, something akin to vulnerability flitting across his features.
“H–Har…”
“Harris?” Tony asked softly. You nodded, still looking at Loki.
Loki rolled his lips in his mouth, his thumb swiping ever so lightly over the skin of your chin, before dropping his hand and walking to the lift in long strides.
“Nat?” Tony asked, the spy already by your side.
“Hold up, Reindeer Games!” Tony hollered behind you, as Romanoff led you down the corridor to your room. “I’m coming, too…”
It felt as if you were having an out of body experience as you were peeled out of your bloodied coat, your clothes and body assessed quickly but gently. She pulled out her phone after she ushered you into the shower.
“Tony? No forced intercourse, but lots of bruising…,” was all you heard before the hot spray of the water ran into your ears, blocking all noise out.
*****
Your glasses were fixed and you could see properly again. That was important, otherwise you wouldn’t have been able to see Harris’ face on the news as he was escorted - handcuffed - from a courtroom and shoved into a police van, followed by the two goons who had helped him.
When you turned from the screen above the cashier, you saw Loki next to Tony across the canteen, looking at you. You walked over, clutching your sandwich.
“So, um… thank you,” you said, gesturing to the screen, “for that.”
Tony put a hand on your shoulder, squeezing gently, before his eyes gazed behind you. “Is that a double cheeseburger I see? Excuse me.”
And off he went, leaving you alone with the Asgardian god.
You shuffled your feet, studying the floor.
“Thanks again-”
“Are you okay?”
You both said at the same time. You laughed quietly, looking up at him. He smiled. You’d never seen Loki smile.
“I’m fine, thank you,” you said.
“I’m glad to hear it.”
You wanted to say so much more, do so much more, like hug him. But he was a god. You weren’t exactly sure what the protocol was for hugging gods. The awkward silence thickened.
“So, I’ll see you around?”
He was still smiling. “Yes. See you around.”
You were fairly sure you were blushing as you scampered off, back to your office.
*****
Bryant Park was one of your favourite places to be in New York. For one, it was right behind the public library - your heaven. For another, it was close to the Tower and you could wander the paths under the lovely trees. The park was very busy as it was Christmas Eve and people wanted to while away the time in the Winter Village until the big day. But as the ice rink closed down and the skaters came off, noses and cheeks red from the cold, the park started to empty.
You sat on a bench under one of the trees, gloved hands deep in your coat pockets, a woolly hat and scarf keeping you warm. Your head was tilted back and you watched the snowflakes dance and twirl in the cold wind.
“Y/N,” someone called.
Loki stood a few metres away from you, a black coat making him look even taller. He was not donning a hat or a scarf, he looked comfortable with the cold. The snow clung to his dark hair, a soft dusting was on his shoulders. You envied the snowflakes.
You got to your feet and he took a few steps closer, looking down at you.
“Were you enjoying the activities?” Loki asked, nodding to the ice rink.
“No, I just… I just like to sit here,” you said, feeling a bit silly. “I like the trees and the snow. It’s… peaceful.”
He nodded.
“How about you? Fancied a turn on the ice?”
He laughed and you watched the cloud mix with your breath. Now you envied your breath.
“Actually, I was looking for you.”
“Me?”
He took another step towards you. “Yes.”
“Why? Did something happen at the Tower?” Worriedly, you fumbled your phone out of the coat pocket and checked it.
A large hand covered it. You looked up. “Nothing happened. I wanted to talk to you.”
Nervously, you glanced down at his hand that still covered your phone. If you hadn’t been wearing gloves your hands would have had actual skin on skin contact. He dropped his hand to his side.
“Am I in trouble?”
He shook his head. “I… I wanted to thank you.”
“What for?”
His hand pulled a book out of his pocket. “For this.” He slid it back in the folds of his coat.
“Oh.” You didn’t really know how to feel or react. You knew he’d been onto you, so it was no surprise he’d sussed it out. He was, after all, the God of Mischief and Lies. But you had to give him kudos for letting it play out.
“Um, you’re welcome.” You bit your lip.
“You don’t know what this meant– what this means to me.”
It was impossible to look at him.
“I was dreading this time of year here on Midgard. But your incredibly generous advent calendar made it feel… like when I first visited here with my mother.” He grasped your gloved hands in his. “I miss her dearly, so thank you. For giving me this.”
You were too choked up to say anything, so you just nodded.
“Can I enquire what your reason was?”
It was so cautious, as if he was worried it might scare you off. And yet, the question threw you, most likely because you had been asking yourself the very same thing from the moment of its conception in your shower. It was just there, a need, an urgency you didn’t know where it came from or why it existed. It was something you had to do. Like breathing.
But over the course of the last few weeks, particularly the last few days, it had become painfully clear why you did it.
“I wanted, no, I needed you to be happy.”
He squeezed your hands gently. The tips of his shoes, his shiny, polished shoes, now touched yours.
“Please look at me.”
So you did. He looked different… vulnerable maybe.
“Why do you need me to be happy?” The question was another cloud and you breathed it in, let it fill your lungs.
“Because…” You were afraid to say it, to admit it. But something in his eyes made you courageous. Either that, or foolish.
“Because I watched you, during missions and in briefings and ops planning. You started to believe what they said about you. And it’s not true. There’s so much you don’t share, don’t tell them and I see it. It’s right there in your eyes. And I didn’t want you to lose yourself. And it’s selfish, I know, but I need you to be happy… because if you are, so am I.”
“If you think that’s selfish, then I am guilty of this notion, too.”
Loki raised his right hand to run the backs of his fingers over your cold cheek. “I knew after three days it was you. I wanted to see where this was going, what your motivation was. And I… when I saw you after Harris… I was filled with so much rage and fear. That I would lose you. Before I had you.”
He leaned his forehead against yours, you closed your eyes, heart beating out of your chest at what you were hearing. Was this a dream?
Loki’s voice was just above a whisper. “Can I? Have you?”
You moved away slightly to look into his eyes. “Yes.”
He leaned in, his hands splaying on your back, as you stood on your toes. The moment his lips touched yours, you felt a current run straight to your heart. It was as if your brain rewired, the missing piece of the primer clicked into place and unlocked everything.
Snow was falling as Loki kissed you under the tree. You didn’t hear the whistles and hollering of passerbys. You didn’t feel the cold wind. You felt elated, buzzing even.
“Your phone is buzzing,” Loki murmured against your lips.
“Hm?” you said dreamily.
“Your phone is buzzing,” Loki smiled, “someone’s calling you.”
Quickly you pulled out the damned device. Before you could even say your name, you heard Tony say: “So sorry for disrupting, Y/N, but we got a slight issue here that needs your expert skills pronto.”
You hung up, burying your head in Loki’s chest. His laugh rumbled in his chest. “We’ll talk more later.”
Breathing in his scent and holding onto him, you weren’t ready to let go. “Promise?”
*****
“Oh god, yes,” you sighed in absolute bliss. “That’s the spot, right there.”
Your groan sounded through the kitchen. You deserved that after three hours of extra work on Christmas Eve.
“Here?” Nat asked.
“Yes, yes! Please don’t stop,” you begged, putty in her hands, eliciting more noises from you.
“Maybe you should try yoga. Your shoulders and your whole upper body are so tense and full of knots. There’s a class I go to tomorrow at lunchtime, if you want to join me?”
“No time,” you murmured. “Heavens, Nat, what else can you do with those hands?”
“Wouldn’t you like to know?” she teased.
“Okay, that’s enough,” Banner interrupted, grabbing Nat by the hand and dragging her to the door. “I’m happy to share my girlfriend’s masseuse skills for a severe case of muscle lock, but I’m afraid I have a personal request now.”
You opened your eyes to catch Nat winking at you, a slight blush on her cheeks as she was pulled out of the room. “So I’m your girlfriend now?” you heard before they disappeared down the corridor.
You laughed and turned in your stool. Thor, Scott and Loki stood staring. Thor at the ends of his braids, Scott at his fingernails, Loki at you. Eyes intense and dark. You swallowed.
“Y/N, a word, if you please,” Loki said, before wrapping his fingers around your wrist and marching out of the room, with you trying to keep up with his long strides, your coat and shoulder bag in your other hand.
He didn’t say a single word until you reached his room - it was closest - and the door shut behind you, locking the outside world out. He pushed you against the door, arm placed against the wood above your head, body leaning into yours, not quite touching.
“That was… a rather interesting display,” he remarked quietly, his breath puffing against your face as he spoke. “In future, I would prefer if your keening was reserved for me.”
Your hands found the buttons of his shirt. “That sounds like an exclusive right to me.”
“It most certainly is.” His lips hovered over yours.
Your index finger slipped in the space between two buttons. “A right that needs to be earned,” you whispered, your finger grazing his skin.
His breath hitched ever so slightly. “Do not challenge me, darling,” he leaned in, his body moving against yours teasingly. “It might be,” his mouth brushed against your earlobe, “too taxing for you.”
You scoffed, but his lips silenced you. His stance shifted as he picked you up and placed you on the nearest surface - a sideboard - and stepped between your legs. He broke the kiss, to cup your face. For a long moment he just gazed at you. The heat in his eyes seemed to intensify, turning you into a needy mess. He made a show of taking off your glasses, folding the temples and carefully putting them on the side board next to you. Your core clenched.
He held out his hand for you to hop off the furniture. You took it and he took to your lips.
It was quite possible that several things fell off on your way to Loki’s bedroom. When you pushed him into the wall to open the damned buttons of his shirt, a picture might have fallen. A vase, perhaps, when he picked you up and spun you around so your back was against the doorframe next to the fragile ornament. Your head hit the heavy frame of a painting, rendering it lopsided, when Loki feasted on your throat, and you tilted your head back to allow him better access.
Kissing, licking, nipping, sucking - he was intent on leaving marks. Your fingers somehow were in his hair, keeping his head in place. Soft, his hair was so soft. A sharp contrast to the teeth you felt pulling on your skin. His ministrations drew a long moan from you.
Loki smiled against your skin. “Yes, my siren, sing.”
Your back hit the mattress and he crawled over you. His hair a curtain, screening you off from the rest of the world in your own sacred space. His shirt hung open, your hands reached out, tracing each line, each dip. His tongue against yours mimicked the motion of his hips that rolled into you. Your legs wrapped around his waist, meeting each movement, as if you had practised this dance many times before. He pulled away to tug off your pullover. His fingers pushed up your bra and then he sucked your nipple into his hot mouth, making you arch your back.
“Loki, please.”
You didn’t really know what you begged for. More, probably. More of this, more of him.
He pulled you up so you both were kneeling on the bed. Shaking hands fumbled with clothes and fastenings and then you were both naked. Your breath hitched at his beauty.
“Can I…,” you started, voice sounding hoarse. You looked up at him. “Please let me worship you.”
Something flickered across his face - surprise? He gave a curt nod and then watched every single one of your movements.
You took his right hand, tracing each finger with yours, the veins on the back of his hands. You brought his hand up to your face, cradling it to your cheek, before kissing the palm of his hand. One finger at a time, you sucked it into your mouth, to the knuckle, your tongue swirling around the digit, before releasing it and pressing a kiss to the tip, before moving on to the next.
Your hands traced the skin of the inside of his arm, his veins, the rise and fall of his muscles, and up over his shoulder, across his chest to his left arm, which you gave the same treatment. Each birthmark, each scar was kissed. Your hands skimmed over his chest, your lips followed the path. Loki’s breath stuttered when you sucked on his left nipple, before you released it, softly blowing on it. It puckered. You bestowed the same treatment upon the other nipple.
“Please, lie down,” you whispered and he complied.
You lay next to him, kissing his forehead, your fingers running through his hair along his scalp, gently tugging. Onwards, to kiss the curve of each eyebrow, the bridge of his nose, his cheekbones, his chin, along his jawline to his ear. You felt his body shiver when you breathed: “You are so beautiful, inside and out.”
Then your teeth closed around his earlobe, gently pulling. A deep moan sounded through the room. Up until now he had let you do whatever you wanted to and not touched you. But his restraint waned and his hands splayed on your back, pulling you flush against his body. You kept going, your lips now worshipping his delectable throat. He tilted his head back to give you better access.
“Herregud,” he rasped as you kissed, licked and sucked on his sensitive skin. His Adam’s apple bobbed up and down as he swallowed hard, his hands growing slack on your back.
You kissed the dip between his collar bones and worked your way down his torso, lips kissing, hands caressing. Further and further you went, along his abs, dipping in his belly button, following the trail of hair below. You leaned back a bit, to look at him. He was fully erect, heavy, swaying slightly. The purple mushroom head gleaming with pearls of pre-cum, thick veins running down the shaft to his pubic hair.
You licked your lips, curling one of your hands around his base, the other cupping his testacles. Then you looked up at him. He was up on his elbows, staring down at you hotly, biting his lips as he watched you in anticipation. You made sure to have and maintain eye contact and then you took him into your mouth.
He hissed, his head falling back, a loud moan following when you hollowed your cheeks to apply suction, the salty taste of his precum on your tongue.
You moved your hand up his length, still sucking, giving his testicles a gentle yet confident squeeze. Up your mouth went, your tongue circling his slit, before sucking him back in. The third time you did it, his hands clasped your shoulders.
“Stop.”
You looked up at him. Loki was breathing hard and you let his cock slide from your mouth with a wet ‘plop’.
In an instant your back was on the mattress and he hovered over you.
“Please don’t misunderstand,” he explained, voice rough, “I loved it, but I have plans.”
He settled between your legs, eyes locked on yours, hand on your thigh, pulling your leg around his waist. His hand slid up, splaying over the fullness of your ass, before giving it a firm squeeze, then sliding over the globe and dipping between your legs. When his slender digits made contact with your aching centre, you cried out. Your whole body was throbbing with need.
“All this nectar is for me?” he rasped.
You nodded.
“Oh, I have to see this.” And in one fluid motion he sat back on his heels, spreading your legs with his hands, looking at your dripping wet centre in amazement.
“Wait a moment,” he said, before he scrambled off the bed and disappeared in the corridor, only to come back a few moments later to resume his place between your legs. He handed you something with a smirk. Your glasses.
“I want you to see me.”
You put them on, your heartbeat accelerating. You bit your lip in anticipation. He looked up at you, his hot breath puffing against your wet core and then his flat tongue licked you all the way from your entrance to your clit. Your fingers fisted in the bedsheets, eyes falling shut in ecstasy, mouth open in a silent cry.
“Look at me.”
You did. He started a rhythm of licking, sucking and lapping that had the coil inside you wind up and tighten impossibly in no time at all. You fell back onto a pillow. Then he slid two fingers inside you and your hands dove into his hair, tugging, scraping.
What a visual. Loki between your legs, eyes burning into yours, humming and moaning against your clit, fingers sliding in and out of you, curling just at the right time, at the exact angle you needed. It was as if you were a book he’d read a thousand times before. Your toes curled and then you fell into the abyss. You moaned out his name over and over as the orgasm washed over you, leaving your legs shaking.
Loki moved up your body, placing kisses on your thighs, your tummy, your breasts, before he brushed some hair out of your face. You took your glasses off, he placed them on the bedside table. His eyes searched yours.
“I need you, Loki,” you managed, pulling him down.
He kissed you deeply, slowly, the taste of you on his tongue. His hips rocked forward and he slid inside you all the way to the hilt. Loki stilled and broke the kiss, resting his damp forehead against yours.
“Are you okay?” he whispered.
Your fingers caressed his back. Unable to form words, you nodded. Then he moved. His hips rocked into yours in slow, deep thrusts. He filled you so well, stimulating places inside you you didn’t know existed. Your hands ran over his back, down his sides, making him shiver. He watched you, eyes dark but warm. One hand found your swollen clit and his fingers circled and rubbed, applying the pressure you needed to fall into oblivion again. Your feet pressed into his ass cheeks to bring him closer, deeper and his name fell from your lips over and over.
He rocked inside you as you rode out your orgasm. You opened your eyes to look at him in wonder. Never had you seen anything as beautiful as Loki. He seemed to glow from the inside. Maybe it was your imagination. You lifted your head, cupping his face to pull him in for a kiss. His tongue moved languidly against yours, savouring the intimacy.
Then he started moving faster, pulling one of your legs up to rest the calf against his shoulder. Deeper, you wanted him deeper. You couldn’t get close enough. His mouth was devouring yours in a needy kiss, all tongues and teeth now as he pistoned faster into you, your hips meeting each of his thrusts. His lips found your nipple, sucking, pulling on it, moving to its sibling. You couldn’t believe you were on the verge again already. Never before had you been able to orgasm more than once during intercourse.
The room was quiet but for the moans, the heavy breathing. You were so wet that your coupling’s noise was wonderfully dirty, edging you both on even more.
“Look at us,” Loki commanded and you did.
Nothing had ever been so erotic as watching him fill you, stretch you, sliding out, covered in your juices. His fingers were on your clit again, rubbing, circling.
“I don’t know if I can…”
“One more, darling, give me one more,” he insisted, breathlessly.
His hips moved faster, as did his fingers and you were there, on the edge. Loki’s eyes met yours and he knew. His movements stuttered, pupils fully blown, jaw slack, a drop of sweat sliding down his temple.
“Cum with me,” you whispered, your fingers dragging down his back, possibly breaking skin, squeezing and pulling his ass into you.
And he did, propelling you into bliss with him. Your name fell from his lips in a string of Norse profanities. His cock pulsated as the hot ropes of his seed marked your insides as his, your pussy eagerly clenching around him, making sure every last drop would be spent inside you. His movements slowed and then he stilled, buried inside you.
Loki’s lips pressed onto yours in a tender kiss. You stayed in the embrace until you both caught your breath. Then he pulled out of you, your mixed juices running out of you. He could have cleaned you up using magic.
But Loki got out of bed, got a wet flannel from the bathroom and gently cleaned you, kissing your tired body, before sliding back into bed. He pulled you into his arms, your hands joined over his heart, legs intertwined and you both lay there, in your bubble of utter and complete happiness under warm covers, watching the snowflakes dance outside the window in the early hours of Christmas Day.
Christmas Day!
“Oh, wait here!”
You scrambled off the bed and ran to the door, forgetting about your nakedness, pulling your shoulder bag from under your coat. You pulled something from it and brought it back to Loki. He was sitting up, forearms resting on his knees, an intrigued look on his face.
“Merry Christmas,” you said.
He looked at you and then at the present you held out to him. He cocked an eyebrow as he took it and pulled the fabric ribbon off. His hands parted the paper and then he grew completely still.
“Where in the nine realms did you get this?” he asked after a few moments, voice sounding rough.
“A friend of mine got her hands on this a while back. I thought you might like it.”
He stared at the book, transfixed. His slender fingers caressing the embossed letters on the front and then he lifted it to take in the scent of the pages. His eyes closed.
“Do you? Like it, I mean?” You were worried about this book. It had cost an arm and a leg, but you thought it would be worth it.
“Like it?” Loki asked, finally looking at you and pulling you on his lap. “My mother used to read me his poems when I was a child. I rediscovered it later. This is…”
He was searching for words, failed to find them and instead kissed you, hard, hand fisting in your hair. After a long moment, he broke the kiss.
“Thank you, love.”
Your fingers wrapped around his wrist, stroking his pulse point.
“Will you read it to me?” you asked, a bit out of breath.
Nodding, he sat against the headboard, you curled up against him with his arm around you. He made sure you were both tucked under the covers. Then he opened the book and cleared his throat.
“Kormákr Ӧgmundarson ‘Sigurðardrápa ‘Drápa’. This is one of my favourites, he wrote it for the love of his life.”
His fingers wandered up your arm.
“Brunnu beggja kinna
bjǫrt ljós á mik drósar,
oss hlœgir þat eigi,
eldhúss of við felldan.”
His digits absently stroked your ribcage, skirting over the side of your breast. The rhythm and intonation of his deep voice made you clench your thighs.
“Enn til ǫkkla svanna
ítrvaxins gatk líta,
þrǫ́ muna oss of ævi
eldask, hjá þreskeldi.”
He paused, closing the book and brushing his lips against the skin of your neck. Your eyes fluttered shut.
“What-what does he say?” you all but stuttered.
Loki kissed along your collarbone. Humming against your skin.
“The bright lights of both
her cheeks burned onto me
from the fire-hall's felled wood;
no cause of mirth for me in that.”
His hands cupped your breasts as he sucked and teased one of the nipples. Your hands tugged on his hair, desperate for him again already. You felt his need hard and heavy against your thigh.
“By the threshold I gained a glance
at the ankles of this girl
of glorious shape.”
Loki moved to lie between your legs, hands sliding over your breasts, your tummy, your thigh, down to your ankle, lifting it to wrap it around his hips.
“Yet while I live
that longing will never leave me.”
His voice faltered as he rocked his hips forward and your bodies were joined once more.
“That longing will never leave me,” he repeated like a vow, eyes serious and warm.
“Nor me,” you pledged, before you lost yourselves in the physical expression of your feelings once more.
~ fin ~
#loki x reader#loki laufeyson#loki#mcu loki#loki x you#loki fanfic#loki fanfiction#loki x reader smut#loki smut#snow
361 notes
·
View notes
Text
TOP SECRET LEAK: GITMO EXPANSION NOW OPERATIONAL—GLOBAL ELITE BEING TAKEN DOWN!
Trump has activated the largest military crackdown in modern history—and it’s happening RIGHT NOW. Guantánamo Bay (Gitmo) has been fortified beyond recognition, transformed into an impenetrable tribunal complex designed for high-profile detentions and prosecutions.
Insiders confirm elite special forces are carrying out global raids, capturing high-ranking figures in finance, politics, and media. The biggest criminals in history are being processed for military trials. The Cabal’s reign of terror is over.
GITMO: THE FINAL STRONGHOLD OF JUSTICE
Gitmo is now a classified military tribunal zone, fully equipped to handle thousands of detainees. Confirmed upgrades include:
12 high-security detention blocks for indefinite incarceration.
Biometric security checkpoints ensuring no escape.
Quantum surveillance systems monitoring every movement 24/7.
AI-driven interrogation chambers extracting confessions in real time.
Underground evidence vaults securing classified documents and assets.
Sources confirm military prosecutors are preparing the largest trials in history.
MASS ARRESTS UNDERWAY: BIGGEST NAMES TAKEN DOWN
Covert military operations have already captured key figures:
A top media mogul responsible for deep state propaganda.
A European royal tied to global trafficking networks.
A pharmaceutical tycoon linked to bioweapon funding.
Multiple banking elites, caught running financial blackmail rings.
These aren’t random arrests—each target has been under surveillance for years. The military has undeniable proof.
GLOBAL ELITE EXPOSED: CRIMES BEYOND BELIEF
Shockwaves are spreading as intelligence teams uncover the truth:
Secret human experimentation labs found in South America and Eastern Europe.
Elite-controlled military bases hidden beneath Antarctica.
Big Tech and intelligence collusion exposed in classified documents.
Seized encrypted files revealing financial manipulation, election rigging, and mass blackmail.
All evidence is secured at Gitmo, ensuring ultimate justice.
MILITARY TRIBUNALS: NO ESCAPE FOR THE CABAL
Detainees are given two choices:
Cooperate and expose the network for a slim chance at leniency.
Remain silent and face full military sentencing—no appeal.
Leaked testimonies confirm Hollywood elites, tech billionaires, and corrupt politicians were ALL involved. The Cabal’s control is unraveling before our eyes.
DEEP STATE PANIC: DESPERATE COUNTERATTACKS
The Cabal is attempting:
Assassinations of military leaders running Gitmo tribunals.
Cyber warfare attacks to wipe out intelligence databases.
Financial manipulation schemes to trigger market collapse.
But Trump’s military forces anticipated every move. Deep state networks are being dismantled, elite hideouts raided. The takedown cannot be stopped.
THE CABAL LOSES CONTROL: THE WORLD WAKES UP
Their propaganda is collapsing:
Whistleblowers are stepping forward in record numbers.
Leaked tribunal transcripts confirm shocking confessions.
Social media is on fire with reports—despite censorship.
The mainstream media is scrambling, but it’s too late—the TRUTH is out!
WHAT COMES NEXT: THE FINAL PHASE
Gitmo’s full expansion completes in 2025, but thousands of new arrests are ALREADY planned.
Elite banking cartels will be eliminated.
The biggest names yet will be exposed.
The deep state is falling FAST.
This isn’t just justice—it’s the end of their empire.
THE STORM IS HERE...
THERE'S NO TURNING BACK 🤔
#pay attention#educate yourselves#educate yourself#reeducate yourselves#knowledge is power#reeducate yourself#think about it#think for yourselves#think for yourself#do your homework#do some research#do your research#do your own research#ask yourself questions#question everything#government corruption#government lies#government secrets#lies exposed#truth be told#evil lives here#medical corruption#hollyweird#news#should be news#not in the news#you decide#justice is served#justice is coming#gitmo
129 notes
·
View notes
Text
Dsuit: Revolutionizing Blockchain Utility for the Next Generation

Can a blockchain platform transform how we engage with digital tools? Introducing Dsuit, a revolutionary new player setting the tone for blockchain usability.
In an age of speed, trust, and decentralization, Dsuit comes along with the answers. It combines foundational blockchain principles with functional, scalable solutions.
This article explains how Dsuit builds new digital journeys and enriches user experiences. You will witness how Dsuit spearheads this revolution.
Tired of blockchain platforms that promise the world and deliver less? This article explores how Dsuit is making blockchain accessible with real-world applicability, multi-chain support, and record-breaking performance.
As a developer, business, or everyday user, learn how Dsuit is powering the next wave of decentralized tools.
The Need for a New Blockchain Utility Standard
Blockchain has developed at a meteoric pace. Most platforms made groundbreaking claims. Few created feasible options, though. Users face Technical problems and hard interfaces. Practical use cases stayed in their infancy.
Traditional blockchain platforms induced confusion, not understanding. Programmers created systems that demanded better technical expertise. Basic functionalities were out of reach for average users. This chasm increased with the elapse of time.
Dsuit puts an end to the cycle. It is all about practical, effective solutions. The platform prioritizes functionality over technical competence. Easy interfaces substitute complicated procedures.
Existing blockchain mechanisms tend to go astray from user requirements. They do not relate to real needs but to theoretical capacity. Users do not appreciate flashy technical parameters. They demand solutions that execute instantaneously.
The existing platforms allow unifying the user requirements with the decentralized protocols. The method closes the gap between life and technology. Functional tools are accessible without requiring learning complex methodologies. Useful systems eliminate unwanted obstacles without compromising security.
Most blockchain platforms pose technical challenges in front of users. Technical consumers are put to the test on how to utilize them. Simple functions have complex processes and professional knowledge. This is frustrating and discourages usage.
Next-gen solutions make security and productivity better without overcomplicating. Users get tasks done in a rush. Security is strong without sacrificing usability. These websites show that they have a convenient purpose of using blockchain technology.
The industry can adopt standards that center around function. Users require solutions to real problems. New approaches follow that route. They prove that blockchain works and is easy.
Core Features That Set Dsuit Apart
Dsuit deploys purpose-specific features. It is efficient and speedy without compromising decentralization. Major offerings are-
Lightning-fast transactions: Lightning-fast transactions are the foundation of this system.
The users possess rates of processing that are almost immediate. Other blockchain networks force the users to wait, which is annoying.
Modular deployment of smart contracts: Modular smart contract deployment simplifies development. Developers can create applications with predetermined modules.
This eliminates coding time and reduces errors. Modular structure makes complicated projects less daunting.
Friendly interfaces: Friendly interfaces overcome technological hurdles. Technical newbies utilize the platform without issues.
Complicated blockchain operation simplified to point-and-click gestures. Removal of learning curves inhibits adoption.
Transparent data logs: Transparent data logs offer end-to-end visibility of transactions. Users monitor all operations from beginning to end.
Transparency fosters trust through auditable records. End-to-end audit trails guarantee accountability in each network operation.
Built for a Multi-Chain World
Interoperability dictates the future blockchain era. Current blockchain networks exist in silos. Users are also limited in transferring protocols. This fragmentation hinders the technology’s potential.
Dsuit works on chains seamlessly. It is compatible with Ethereum, Polygon, and other dominant networks. The platform fills gaps between various blockchain ecosystems. Users experience multiple networks with a single interface.
Cross-chain compatibility removes technical obstacles. Users transfer assets between networks without complicated processes. The system manages Automatic protocol differences. This makes multi-chain operations much easier.
The network support does not involve only large platforms. The structure supports new blockchain protocols that are still emerging. Standardized mechanisms of connection make it easy to incorporate new networks. This future-proofs the platform from technological advancements.
Multi-chain capabilities broaden utilization exponentially. Consumers use a variety of decentralized applications on various networks. They take advantage of distinct features from varying blockchain systems. This provides levels of freedom that have never before existed for blockchain interactions.
Customers interact between platforms seamlessly. They execute transactions on any network with ease. Asset transfers across chains become everyday activities. Intricate multi-chain processes become seamless automated tasks.
The platform is a utility hub in a fragmented ecosystem. It bridges previously disconnected blockchain networks. Users control all their blockchain activity from a single location. This integrated method turns fragmented processes into unified interactions.
Centralized access points make blockchain easier to navigate. Users do not need to navigate through multiple applications and interfaces. The hub-based method simplifies complexity while increasing functionality across the whole blockchain space.
Security with Scalable Design
Security has to come first. There can be no platform if there isn’t. Users demand safety at all levels. Systems have to defend data from all threats,
A secure blockchain starts with decent encryption. All transactions are safe. There is no outside breach of wallets and contracts.
Authentication protocols make sure legitimate users talk to the network. Hidden private keys do not leak out. Public ledgers remain open.
Attack surfaces remain minimal. Firewalls and anti-spam filters are running. Alerts flag suspicious behavior in seconds.
Smart contracts execute inside isolated environments. Flaws in one section never touch others. This maintains harm contained and manageable.
Security audits occur regularly. In-house and third-party groups review code. Vulnerabilities get patches before exposure turns to risk.
The architecture of the platform also accommodates large-scale demand. Users grow daily. The system processes traffic without hesitation.
Load balancing maintains performance silky-smooth. No part lags or misses service. Everyone gets equal access.
Resources scale up or down automatically. Efficiency is superior. There is no band and energy waste.
Business users demand reliability. They can’t afford downtime or failure. Uptime is almost perfect at global nodes.
Dsuit balances design between security and scalability. The platform grows while keeping all interactions secure. That balance is the secret to long-term blockchain success.
Streamlining Enterprise Blockchain Adoption
Firms need scalable and solid systems. Firms invest in platforms that enable growth, security, and openness. Complication is a buzzkill.
Firms appreciate rapid deployment. Existing blockchain configurations take time. Firms need modules that can plug in without extensive development cycles.
Plug-and-play modules are the answer. Pre-configured pieces enable quicker onboarding. Teams can go live without massive technical updates.
Executives need real-time insights. Dashboards ought to be real-time for transactions, users, and utilization of resources. Transparency assists in making decisions easily.
Data integrity remains a requirement. Each block must verify history perfectly. Companies need audit-ready logs.
Compliance capabilities assist regulated sectors. Health, finance, and logistics operate under rigorous procedures. Blockchain needs to comply with those regulations.
Identity management safeguards business systems. Role-based access provides internal data confidentiality. Only authorized personnel can view critical functions.
Supply chains get the benefit. They receive traceable histories from start to completion. Customers’ trust increases.
Approval, payment, and triggers to shipping the goods are automatic by use of smart contracts. Delays and human errors vanish. Processes become smoother.
Dsuit offers these advantages in a business-friendly bundle. It scales to large organizations without user control compromise.
Scalability and compliance make mass deployment possible. Teams eliminate wastage of time. Customers receive reliability. Blockchain is beneficial without being complex.
User-Centric Development Approach
Good platforms fix problems. Great platforms listen. Individuals do not need new tools, but poor results. Design matters from day one.
Interfaces must be simple. It needs to guide Buttons. Nothing should ever be out of sight or too much. Everything needs to have a purpose.
New individuals need assistance. Tutorials help them to start fast. Tooltips and walk-through actions build convenience and assurance.
Power users require control. They desire top-level settings. Dashboards need to scale to use case and skill.
It threatened the Performance Features that need to load in a hurry. Slow loading causes frustration. A good experience is efficient.
Mobile and desktop interfaces need to be consistent. Platform switch should not mean relearning. Simplicity enables easy transition.
Visual simplicity reduces error. It needs well crafting for Icons, color, and layout. Each click needs to be worthwhile.
Feedback loops gather insights. They loop back into updates.
Data informs improved development priorities.
Community forums enable discussion. Ideas spread quicker. Developers can see what other people want.
Regular updates enhance functionality. New releases solve pain points. Development speed matters. Dsuit…
#dsuit#dapps#dmail#blockchain#ncog#web3id#smart contracts#green blockchain#post quantum security#blockchain technology#nft#did#quantum computation#Quantum-safe encryption#writers on tumblr
1 note
·
View note
Text

✨ Basic ✨ online safety tips! this is from a technical standpoint. A non exhaustive, non professional list on how to NOT end up with people doxxing you, cause a moot got tricked by a metasploit script kiddie keylogging random and everyone deserves to feel safe in their space.
Passkeys. Use them. Hardware ones are more secure but also less versatile. Any is better than Passwords.
2FA is great and all, but token theft exists, not just on discord but, ever heard of a pass-the-cookie attack? wipe, your, cookies. Browser, whichever one you use. Wipe the data periodically. Once per week minimum
HSTS - have it set up. It's resistant to MITM attacks so long as you're careful. SSL stripping doesn't work ever since TLS, which btw TLS 1.3 is the standard.
Cryptographic encryption itself is very strong and hard to breach by brute force. Even AES 128. AES 256 is always preferred and now most browsers come with Quantum Protection. Again. None of this means anything if your online safety habits sucks and your password is compromised.
"Antivirus is useless!" Wrong. It's true that for mobile devices an AV isn't as paramount as for PC HOWEVER this is only for very casual users. Premium AV are important because they come with features that will keep you from clicking phishing links and making oopsies as well as firewalls. No. Don't pay for stuff. Stay away from anything Norton and Avast. One is a scam the other is pure spyware and adware, and we don't even need to talk about Mcafee. Kaspersky was fantastic but you already know the problem. Bitdefender Mobile Security is robust, I use it while making new empty emails every 2 weeks to avoid paying and that way you can use it forever for free. Yes. I'm a sneaky little thing, we don't pay to corps here. Btw smaller ones like ESET are good too, less load. Sophos is very specific in it's usage and don't recommend it for casual users.
Don't bother with DMZ or VM over VM stuff unless you're a professional or a genius. A set up wrong VM is an open backdoor to hackvile and contrary to popular belief a VM can be compromised, especially if you access the internet with it. Don't.
Simple tools well set up are 100x times better than complex things you know nothing about. You don't need company security suit stuff as a normal user, at all, ever.
Pleaseeeee update your router for the love of everything that's sweet and full of Ice cream. If you use WPE/WPA or anything below WPA 2 AES 256 your router is hollering to be compromised. No. WPA 2 TKIP isn't enough either. IF possible have WPA 3 set up. It's resistant to vulnerabilities the past one has particularly KRACK attacks...and pls avoid dual connections my head hurts thinking about it
Be aware of hacking tools like Metasploit or Flipper Zero. Be aware of basic stuff like SQL injections. You don't need to be an IT expert to be conscious. Zero day exploits are a thing.
Malware has many types. Adware and PUA are considered less of a problem, but still annoying. Keyloggers and Trojans are middle tier, although it depends on the Trojan as some can be highly dangerous. Fileless malware, you don't want it. Rootkits get system level acess, and worms? I wish they were gummy worms instead.
The level of access of a virus can range from data only straight up to firmware and the danger is how quickly it can escalate access permits, many viruses won't ever get beyond system level access but rootkit can gain kernel and some above that. Anything at kernel level or above can't be wiped by a factory reset and a compromised boot sector is a problem.
Common stuff like White hack hackers. Gray hat hackers. Black hat hackers. Red hat hackers etc. it's actually usually much less noisy. No. A hacker won't dress themself in black robes in a dark room and wave at you while nightwish plays in the background, your cousin. Fifteen and eating cereal could be one of those already, although most that age are script kiddies.
"I did it! I'm impossible to hack!* Stfu. No. I'm serious, don't do that. Don't fell victim to the Dunning Kruger Effect. Knowing this doesn't make you a pro and ypu could layer TOR over VPN and have every security suite in place and still get hacked by anyone skilled enough with ease, do you know how easy it is to exploit human error in terms of cyber security? the best way to NOT have your information compromised is not to brag about your knowledge. You will get humbled and it will be, at the very least, a deeply embarassing experience. And obviously keep your devices up to date
Back to more easy stuff, if you do use passwords, change them periodically, check your IP. "have I been pwned?" Yes, yes you have, there's been millions of leaks on multiple sides and even if you're tech savvy as a non pro you had it happen almost for sure, I know I did as a kid, if you use passwords make them lengthy. No. QWERTY is not lengthy, TikTok Timmy. You know the drill use symbols, mix random stuff and use your lateral thinking. Did you know sufficiently potent decides can brute force thousands of passwords in seconds? Passkeys are better, I promise.
None of the above means squat if your socials constitute of your full name disclosure and a photo of your face, don't doxx yourself. Still. Do not panick, most people won't have access to spying tools like FinSpy or Pegasus and you're not constantly being watched, just be aware of threats.
#choco speaks#actually adhd#actually autistic#⬅️ I'm not a professional and dont claim to be one. I'm knowledgeable but anyone who is an expert can add-up.
13 notes
·
View notes
Text
(Fiddling around with a new MCU time travel idea)
There are a couple of kids in Tony’s living room.
Well- there’s one bonafide child, early elementary school age, and then one teenager somewhere on the cusp of young adulthood. But Tony would bet if he put their ages together and divided by two, he’d get a number in the realm of ‘should probably still have a babysitter when the parents go out for an evening’, ergo, kids.
They’re still asleep, for the moment. Or, unconscious, rather. Not awake, at any rate, and they haven’t been since falling through a big glowing circle into his living room, teenager curled protectively around the little girl. Which is a little annoying for two reasons; first and foremost, Tony has questions, but also he’d rather not have Pepper or anyone else walk in and demand to know why there are two unconscious children lying on his sofa.
That’s just such an awkward question. Though he does at least have proof in the form of security footage that the pair arrived by means entirely beyond Tony’s control. Speaking of which; Tony flicks a finger, and JARVIS dutifully rewinds said footage to the beginning, and plays at an again-reduced speed. Ultimate slo-mo doesn’t reveal any answers, however. There’s no prior warning before the light flares, startling video-Tony into spilling his coffee as he crosses the room, and no hints to be found beyond swirling white and orange as the kids fall through. The light vanishes as soon as they’re clear, then the boy hits the floor, hard. There are honest to goodness cracks in Tony’s floor, he had JARVIS run a scan on the structure beneath his lovely thick carpeting just to check.
No cracks in the kid’s bones, though. And- okay, in all honesty, questions and unknowns and everything else aside, Tony does prefer it that way, rather than the reverse.
As far as JARVIS could tell with further scanning, neither kid bore any injuries - just some lingering traces of quantum energy, fading further with every minute. With any luck, as soon as that finishes up, there’ll be some waking up and answering of questions.
Though of course Tony couldn’t just sit around and do nothing while he waited.
The little girl is definitely wearing designer brand clothing: durable sneakers, high quality shorts and collared shirt, a lightweight jacket that wouldn’t look out of place in a magazine for children’s spring collections. Also, just to hammer home the fact she comes from money, JARVIS detected extremely sophisticated tracking beacons inside every single garment. Even the socks. Tiny devices, clearly some kind of advanced nanotech... With a mini Stark Industries logo etched onto each one.
Trouble is, Tony’s never made beacons this small and impressive before.
Her watch is a similar conundrum. It’s red and yellow, clearly meant to look like any other cheap Iron Man themed child’s decoration, except for housing what Tony would swear is the same sort of satellite connection he puts into all of his suits for JARVIS to link up with. Top of the line encryption, tiny hologram projection, more tracking software with options to send specific distress calls, and all of it bio-locked, which- which should have been a problem. Even without an AI present in the device to fight him, it should have taken Tony significant time to crack through the locks and get a good look at the watch’s internal circuitry. Instead, it- recognized him. Recognized his bio-signature, and let him in.
He’s still mulling over the implications of that one.
Now, the teenager, there lie some other mysteries. Far shabbier clothing, for one thing. The ragged shoes alone look like they’ve picked up grime walking from one side of NYC to the other and back. Jeans with a faded appearance that’s not artistic enough to be artificially crafted; sweatshirt that has some amateur stitchwork patching up the elbows; t-shirt with holes in the hem and a cartoon character Tony didn’t recognize on the chest.
Thing is, JARVIS didn’t recognize the character either. Not even after running a search through the whole dang internet. And it wasn’t an indie creation, there was very definitely a Disney logo on the shirt’s tag, where it stuck up from the back of the collar.
And then there’s what the kid’s got under his clothes.
No, Tony did not undress him, but peeking out from under the cuffs of that sweatshirt and visible in the gap between pants and shoes is a very different sort of material. Durable, flexible, extremely form-fitting to be hidden so well by regular garments. Physically rifling through the kid’s sweatshirt pockets turned up a pair of gloves and mask, too. Very Halloween-y, Tony would probably jump out of his skin if he turned around to find those big white eyes looming out of the dark. Attached to the gloves, he also found a couple of small gadgets, fairly sophisticated, capable of spitting out an atrocious substance clear across the room. A large, sticky web still occupies the far wall by his bar as proof.
Those, Tony gingerly set down next to the girl’s watch, to be considered later. When their owners are awake, and capable of telling him things like hey don’t touch that button.
In the meantime, he’s finally accepted there isn’t much left to do but wait, idly replaying the security footage over and over, less idly hoping there’s some kind of change before any company arrives.
His luck, perhaps predictably, falls through.
“Sir,” JARVIS announces into the otherwise quiet room. “Miss Potts is on her way up.”
With a long, drawn out, highly exasperated sigh, Tony sets his empty glass aside and stands to face the music.
---
“Time travel,” Pepper says flatly. That’s a very clear, Pepperish tone of you can’t be serious. But before Tony has a chance to voice his defense, she’s already sighing, and bringing up a hand to rub at the bridge of her nose. “Why do you think this is time travel?”
So he starts reviewing the data.
The cartoon character that doesn’t exist yet only earns a raised eyebrow - when Tony gets into the particulars of the girl’s watch and trackers, Pepper looks a little less unamused, a little more disconcerted. Pointing out the boy’s suit and gadgets and drawing her attention to the web still occupying his wall even earns two whole startled blinks. “That’s... Tony.”
“Yeah.”
“Tony.”
“Yeah,” he repeats, fully in agreement. “But it’s either time travel, or R&D has been doing some serious overtime tinkering without letting either of us know!”
Pepper rubs a hand over her face, sighing again. When she pulls it away, her gaze goes to the pair of kids, girl still held in the boy’s arms, both of them laying on their sides where Tony managed to haul them up onto his sofa when the whole bizarre event began. “What do we do, then?”
“Not much we can do, besides haul them down to the infirmary and try injecting things to induce an early wake-up call.” Even as he says it, Tony swipes up and enlarges the holo-window with the energy reading and its total dissipation countdown. T-minus eight hundred and seventy-three seconds. “Otherwise, wait to see if anything happens in about fifteen minutes.”
Pepper let loose her third sigh, and went to get a glass of wine.
43 notes
·
View notes
Text
The Quantum Financial System (QFS) is a theoretical financial system that aims to challenge the existing banking system and address issues like corruption and manipulation in the financial sector.
It's believed that the QFS would use artificial intelligence (AI) and quantum computing to revolutionize financial transactions and eliminate the need for traditional systems like SWIFT.
The QFS is designed to resist encryption-breaking attempts by quantum computers, which could redefine data security in the digital world.
While direct investment in the QFS is possible, some believe that ISO 20022-compliant may play an important role in the new system.
Quantum-based technologies in finance offer benefits like enhanced computational power, advanced data analysis, increased security, portfolio optimization, and more.
QFS is the Future, Trump is Fighting for the Future and for the betterment of United States of America.
Move your funds into the QFS ledger account and be safe from the incoming bank crash. I will be here to navigate you onto your transition into the QFS ledger account

#donald trump#wells fargo#bank of america#breaking news#bank crash#bad government#world news#qfs#bank clash#new york#decentralized#bad omens#decentralisation#decentralised finance#marine life#quantum financial system#nesara#gesara#stay woke#washington dc#white house#veterans#patriotic#politics#trump 2024#republicans#educate yourself#reeducation#reeducate yourself#be aware
89 notes
·
View notes