HivePro Uni5 proactively reduces an organization’s attack surface before it gets exploited. It neutralizes critical cyber security vulnerabilities that matter to your business through a single console.
Don't wanna be here? Send us removal request.
Link
#vulnerability#vulnerability management#zero day vulnerability#Threat Exposure Management Solution Blog
1 note
·
View note
Link
1 note
·
View note
Link
EnemyBot, a Mirai-based botnet, is expanding its arsenal by exploiting well-known vulnerabilities in log4j, VMware workspace, Spring Framework, and others. Keksec, also known as Nero and Freakout, is the threat actor behind EnemyBot. Since 2016, this group has been known for crypto-mining and distributed denial-of-service (DDoS) attacks.
#EnemyBot#Mirai-based botnet#well-known vulnerabilities in log4j#VMware workspace#crypto-mining and distributed denial-of-service
1 note
·
View note
Link
Node.js has released several fixes for vulnerabilities in the JavaScript runtime environment, which could lead to arbitrary code execution, HTTP request smuggling, DNS rebinding vulnerability and other bugs
#Technical#fixes for vulnerabilities#Vulnerabilities classified#Log4j vulnerabilities in VMware Horizon#Citrix vulnerabilities#vulnerabilities
2 notes
·
View notes
Link
Since March 2022, Industrial Spy ransomware, a new menace in the threat environment, has been stealing and selling data on the dark web marketplace and conducting double extortion attacks, combining data theft and file encryption for around 30+ organizations.
1 note
·
View note
Link
Further, we also observed 4 Threat Actor groups being highly active in the last week. APT29, a Russian threat actor group popular for Information theft and espionage was seen launching phishing campaigns to launch malware via cloud storage services, EvilNum an unknown threat actor group popular for Information theft and espionage was seen targeting Decentralized Finance (DeFi) sector, APT37 a North Korean threat actor group popular for Information theft and espionage was seen launching attack campaigns using Konni RAT and KNOTWEED an Austrian threat actor group popular for financial crime and gain, was observed exploiting zero day vulnerabilities of Windows and Adobe to perform targeted attacks against European and Central American customers. Common TTPs which could potentially be exploited by these threat actors or CVEs can be found in the detailed section.
#APT29#Russian threat actor group#Decentralized Finance#campaigns using Konni RAT#Threat Actor groups#security researchers worldwide
1 note
·
View note
Link
Exotic Lily was first discovered exploiting a zero-day vulnerability in Microsoft MSHTML (CVE-2021-40444), which piqued the curiosity of researchers as a potentially sophisticated threat actor. Following additional analysis, it was revealed that the group is an initial access broker that utilizes large-scale phishing operations to infiltrate specific corporate networks and subsequently sells access to those networks to ransomware groups such as Conti and Diavol gangs.
The group starts by producing fake social media profiles, including LinkedIn profiles, by exploiting readily available employee data to make the illicit clones look genuine using advanced A.I. imaging technology. When it was originally discovered, the malware was in the form of a document file that attempted to attack the CVE-2021-40444 vulnerability. Subsequently, the threat actor switched to ISO archives having BazarLoader DLLs with LNK shortcuts.
#Bumblebee#CVE-2021-40444#Exotic Lily#BazarLoader#Vulnerability Details#Threat Actor Exotic Lily acting#Access Broker for Conti#Diavol ransomware group
1 note
·
View note
Link
Last week, F5 patched a vulnerability tracked as CVE-2022-1388, soon after a successful Proof-of-concept(PoC) was developed by security researchers making it susceptible to further exploitation.
This authentication bypass vulnerability affects the iControl REST component in BIG-IP systems. An unauthenticated attacker could use this flaw to gain initial access and control of a vulnerable machine, allowing remote code execution.
This vulnerability has been fixed in versions 17.0.0, 16.1.2.2, 15.1.5.1, 14.1.4.6 or 13.1.5. Organizations that are unable to update their versions are advised to follow these mitigations: •Blocking iControl REST access through the self IP address •Blocking iControl REST access through the management interface •Modifying the BIG-IP httpd configuration.
#BIG-IP vulnerability#patched a vulnerability tracked#Vulnerability Details#actively exploited BIG-IP vulnerability
1 note
·
View note
Link
The Computer Emergency Response Team of Ukraine (CERT-UA) has issued an alert warning of an ongoing spear-phishing attempt aimed at delivering an email with a malware attachment to Ukrainian government institutions and European state agencies. According to CERT-UA researchers, the hacker organization UAC-0010, also known as Armageddon, is responsible for spear-phishing attempts against Ukrainian government personnel.
The group’s principal attack vector has been mass-sending emails to potential victims with harmful attachments that lead to the spread of different malware strains throughout the course of their exposed activity, and the most recent cyber-attacks are no exception. In the early days of their activity, the Gamaredon group used simple tools written in VBScript, VBA Script, C#, C++, and other programming languages, mostly relying on open-source software, before gradually expanding their toolkit with a number of custom cyber espionage tools, such as Pterodo/Pteranodon and EvilGnome malware.
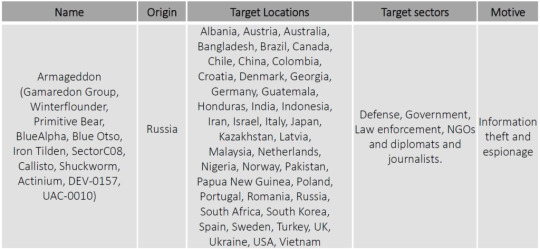
#Armageddon#Attacks on European Union#UAC-0010#government entities carried#Armageddon group#Computer Emergency Response Team of Ukraine#Technical
2 notes
·
View notes
Link
At least 60,000 companies have been affected by the recent sophisticated attacks on Microsoft Exchange Server that have been carried out by threat actors affecting small and medium sized companies. The actor group has been breaking into the company’s computer networks through the Microsoft Exchange email software, targeting a number of victims.
Vulnerabilities
Microsoft Exchange Server Remote Code Execution Vulnerability: CVE-2021-26855, CVE-2021-26857, CVE-2021-26858, CVE-2021-27065
Affected Versions: Microsoft Exchange Server 2013, Microsoft Exchange Server 2016, Microsoft Exchange Server 2019
1 note
·
View note
Link
This Elevation of Privilege vulnerability was found by renowned researcher Abdelhamid Naceri and reported to Microsoft, which addressed it in their August 2021 release. Naceri noted that Microsoft’s fix was incomplete soon after it was issued and presented a proof of concept (POC) that bypassed it on all Windows versions. That is when the 0patch team, published an unofficial security update for all Windows versions and made it available for free download to all registered users. Microsoft then patched this security flaw in their January 2022 release, tracking it as CVE-2022-21919. Naceri, on the other hand, discovered a way around this second patch. However, Microsoft’s second attempt to fix the bug altered the “profext.dll” file, resulting in the removal of the unofficial workaround of 0patch from everyone who had installed the January 2022 Windows updates.
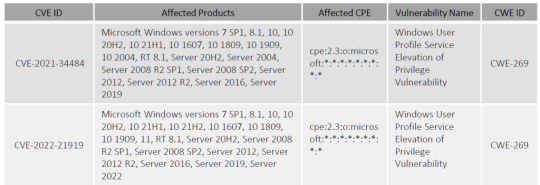
#Microsoft’s privilege escalation#vulnerability#locally exploited vulnerability#CVE-2021-34484#CVE-2022-21919#proof of concept#Vulnerability Details
1 note
·
View note
Link
A remote code execution (RCE) vulnerability(CVE-2021-22941) affecting Citrix ShareFile Storage Zones Controller, was used by Prophet Spider to attack a Microsoft Internet Information Services (IIS) web server. The attacker took advantage of the flaw to launch a WebShell that allowed the download of further tools.
Prophet Spider also exploits known Log4j vulnerabilities in VMware Horizon (CVE-2021-44228, CVE-2021-45046, CVE-2021-44832). Prophet Spider most typically used encoded PowerShell instructions to download a second-stage payload to the targeted PCs after exploiting the vulnerabilities. The specifics of that payload are determined by the attacker’s motivations and aims, such as crypto mining, ransomware, and extortion.
#Prophet Spider exploits#Log4j#Citrix vulnerabilities#deploy webshells#Initial Access Broker#Prophet Spider#remote code execution#vulnerability#affecting Citrix ShareFile Storage Zones Controller#Microsoft Internet Information Services#Log4j vulnerabilities in VMware Horizon#MITRE TTPs#PowerShell#tumblr
1 note
·
View note
Link
This was a month of cyber warfare. The cyberwar between Ukraine and Russia introduced new attacks to global cybersecurity firms. This month, 55 vulnerabilities were discussed, of which 5 were zero-day vulnerabilities and a few vulnerabilities were exploited in the wild. Some of the threat actors active this month were APT27, MuddyWater, Molerats, BlackCats, APT28, UNC2596, and APT10. Several other threat actors across the globe started taking sides in the war and started using new sophisticated malware and brought previously used techniques as well. Highly targeted sectors for this month were government, telecommunications, financial, defense, and construction & engineering. Amongst all the malware that had been launched this month, three malware garnered more attention and have been discussed in this report. Last but not the least, the top ten most used TTPs are also depicted.
1 note
·
View note
Link
Previously unidentified macOS backdoor malware, CloudMensis, leverages cloud storage as its command and control channel to exfiltrate documents, keystrokes, and screenshots from affected Macs
1 note
·
View note
Link
The ransomware incorporates VMProtect, UPX, and unique packaging techniques, and it is often installed on hacked computers within a special virtual machine. It also makes use of the Windows API GetLocaleInfoW to determine the system’s location and stops the process if the computer is in certain countries. RagnarLocker scans compromised machines for current infections in order to prevent data corruption, identifies tied hard drives, iterates through all running processes and stops those linked with remote administration, and thereafter attempts to delete all Volume Shadow copies in order to prevent data recovery. Following that, the ransomware encrypts any material of interest – avoiding encrypting files in particular folders – and then leaves a.txt ransom note instructing the victim on how to pay the ransom.
#RangnarLocker Ransomware#ransomware incorporates VMProtect#UPX#unique packaging techniques#APT41#Technical#vulnerability in Microsoft Office
1 note
·
View note
Link
The initial attack begins with sending a thousands of phishing emails to individuals of the targeted firm. They are tempted by good job opportunities – a common tactic used by the Lazarus APT to convince individuals to download trojanized cryptocurrency applications on Windows or macOS operating systems. The trojanized applications include TokenAIS, CryptAIS, and Esilet is loaded with TraderTraitor malware. These apps are cross-platform, Electron-based platform utilities created with the Node.js and JavaScript runtime environments. When the payload is executed, the attacker gains access to the victim’s computer and company network by executing commands and sending additional malware.
#cryptocurrency#via TraderTraitor malware#Lazarus is back#targeting organizations#Technical#software#HivePro Uni5
1 note
·
View note
Link
After examining Microsoft’s fix, Abdelhamid Naceri, the security researcher who discovered this vulnerability, discovered a bypass of the patch as well as a more powerful new zero-day privilege elevation vulnerability. He also made the proof-of-concept available to the public.
An unofficial micro patch has been released by 0patch and will be available for free until Microsoft releases an official patch for the vulnerability.
2 notes
·
View notes