Link
In our “PLC Hacking” series, we are going to cover different methods of interacting with PLCs, the different protocols which they use, and to demonstrate their inherent lack of security protection. In this particular blog, we will be looking at setting up the PLC and writing a ladder logic program into it.
#plchacking#programmable logic controllers#hacking#cybersecurity#cyber security#ethical hacker#hackers#infosec#infosecurity
0 notes
Photo

What is Mobile Penetration Testing? https://bit.ly/mobile-pentesting
#mobilepentesting#mobilepenetrationtesting#penetrationtesting#penetration testing#pentest#pentesting#cybersecurity#cyber security#infosec#infosecurity
0 notes
Photo
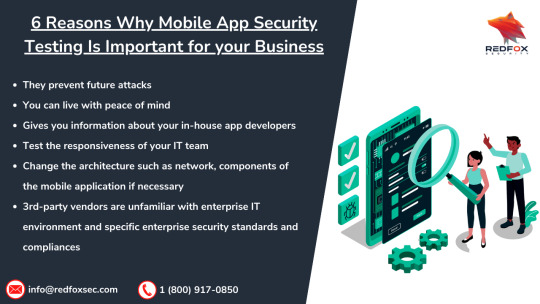
Top 6 Reasons why Mobile App Security Testing is Important for your business
Get in touch with us for Mobile Penetration Testing Services - https://bit.ly/mobile-pentesting
#mobilepentesting#penetrationtesting#pentesting#pentest#penetrationtest#smallbusiness#cio#ceo#cto#cxo#itsecurity#infosec2022#infosecurity
0 notes
Text
iOS Jailbreaking
In this blog, we are going to discuss jailbreaking, its advantages and disadvantages, as well as types and the steps for carrying out a successful jailbreak.
The technique of circumventing a smart device’s internal defenses to get total control of the operating system is known as rooting or jailbreaking, but it puts the device’s security at risk. The sole distinction between these two concepts is that rooting refers to Android devices, whereas jailbreaking refers to iOS devices. So, whereas rooting an Android device implies getting beyond Google’s security limits, jailbreaking an iOS device involves getting around Apple’s restrictions. However, due to Apple’s “Walled Garden“ Strategy, the jailbreaking procedure necessitates pulling down these “walls” or “jails” before attempting to get root access. It is frequently accomplished by locating and exploiting a flaw in the operating system. Rooting grants the user administrative privileges, allowing them to totally replace the operating system if they so wish. Jailbreaking does not confer admin powers, but it does give users additional access to their device through the use of tweaks, which are included in supplementary applications such as Cydia.

Why jailbreak an iOS device?
To acquire more control.
The attractiveness of jailbreaking derives from the user’s ability to have total control over their gadgets. These are the following things you will get after jailbreak.
App installation: Apple is passionate about security, thus only those apps that pass their severe security tests are allowed into the app store. On an iOS device, only apps from the app store may be installed. Users can install third-party applications after jailbreaking their devices.
Uninstalling pre-installed apps: Some apps come pre-installed, and while the majority of users never use them, they are not permitted to be removed. Users with root privilege can remove these unwanted apps.
Switch carriers: Apple isn’t keen on changing its default network providers. Jailbreaking might be useful for unlocking, changing networks, or switching to a different carrier temporarily.
Controls: People also jailbreak their gadgets because they despise being told what they can and cannot do with their devices.
Customization: Apple is committed to providing a high-quality user experience to all of its customers. And they do so by ensuring that everyone utilizes their standard features while providing little space for customization. Users with root access have the ability to modify all of this.
Types of jailbreaks
Tethered: This is a temporary jailbreak and requires the device to be connected to a computer every time the device needs a restart. The jailbreak is reversed otherwise.
Semi-tethered: This jailbreak can’t be re-applied unless the device is connected to a computer during reboot. The device can also boot into non-jailbroken mode on its own.
Semi-untethered: These jailbreaks allow the device to boot on its own, but the kernel patches (or user-land modifications) for disabling code signing aren’t applied automatically. The user must re-jailbreak the device by starting an app or visiting a website (not requiring a connection to a computer, hence the term untethered).
Untethered: This is the more sought-after solution, where the device only needs to be connected to the computer at the time of initial jailbreak. Rebooting the device does not reset the jailbreak.
Read Complete Blog - https://redfoxsec.com/blog/ios-jailbreaking/
#ios#jailbreak#apple iphone#apple#iphone#bugbounty#cybersecurity#cybersécurité#cyberattaques#cyberattack#hacking#infosec#it security
0 notes
Text
Purdue Model for OT Security
What is the Purdue model for OT Security?
The Purdue Enterprise Reference Architecture (PERA) identifies the different tiers of vital infrastructure utilized in manufacturing lines, as well as how to safeguard them. If implemented correctly, PERA could achieve the air gap between OT and IT systems. The Purdue model was adopted from the Purdue Enterprise Reference Architecture model by ISA-99. This model provided a framework for segmenting industrial control system networks from corporate enterprise networks and the internet. It’s segmented into separate levels.
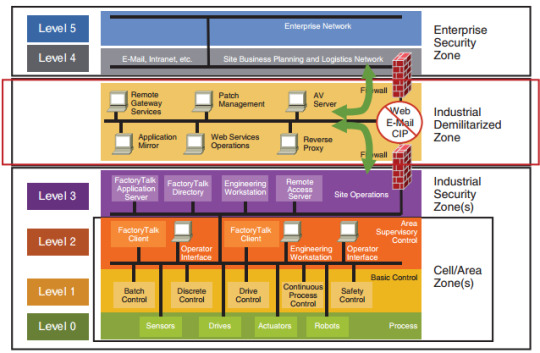
Level 5 – Enterprise Network
This level’s systems are typically corporate-wide and span many locations or factories. They collect data from subordinate systems in specific plants and combine it with other information. The majority of these systems are housed in corporate data centers. Plant production schedules, material usage, shipping, and inventory levels are all controlled by ERP systems present in this level.
Level 4 – Site Business Planning and Logistics
All the IT systems that support the production process in a facility are present here. Web servers, file servers, print servers, business workstations, email clients are a few of the types of systems found in this level. Active Directory networks are also implemented in this level. These systems send production information to corporate systems, such as uptime and units produced, and they collect orders and business data from corporate systems to disseminate to OT and ICS systems.
Read complete blog - https://redfoxsec.com/blog/purdue-model-for-ot-security/
2 notes
·
View notes
Photo

Android Tapjacking -
https://redfoxsec.com/blog/android-tapjacking-vulnerability/
0 notes
Text
Penetration Testing For Startups

The subject of whether startups require a penetration test comes up frequently when talking to entrepreneurs. Unfortunately, cyber criminals think differently. Adversaries are aware of their weak security postures, and as a result they become easy targets.
Penetration testing or pen testing is the practice of evaluating a system’s security measures against a determined cyber-criminal. Startup owners should regularly engage in pen testing since it has considerable benefits for the growth and sustainability of their company.
Penetration testing is often confused with vulnerability scanning (For more details, refer to Vulnerability Scanning vs. Penetration Testing), but it goes way beyond that. It analyses the consequences of a successful cyber-attack and provides information that businesses can use to support their technology and manpower investments.
Here are Six Reasons Why Startups need Penetration Testing.
1) Identify opportunities for improvement
According to research, every year, over 50% of SMEs face a cyber-attack. Within six months, almost 60% of these compromised companies close their doors. As such, taking minimal security precautions is no longer advised. Pen testing can be an excellent investment because it can identify loopholes in an organization’s security posture.
Moreover, startups like yours should proactively invest in security-enhancing technology and manpower. To add, pen testing should be your first commitment since it will show you where you are vulnerable and how you can improve your security posture.
2) Meet Compliance Standards
Every day, organizations process and store sensitive data. For instance, hospitals deal with a lot of financial information as well as sensitive patient data generated by numerous linked devices. This is just one example. Depending on your industry, you may be required to comply with PCI, HIPAA, or GDPR. Compliance is sometimes ignored in the rush to get your business up and running. You don’t want to be non-complaint and fined.
3) Identify Security Vulnerabilities
As a result of their size, small business owners often believe they are immune to cyberattacks. This is far from the truth. Hackers are becoming more skilled and can target any firm. A pen test can uncover flaws in your infrastructure and applications. It can help you find flaws and fix them before a real-world attack takes place. Penetration testing may not end up in a situation where the tester is able to compromise sensitive data or steal money from your business. However, the firm assisting you during a security assessment, will be able to give you detailed insights into how they were able to break into your infrastructure or application along with fine-tuned recommendations.
Read more - https://redfoxsec.com/blog/why-startups-need-penetration-testing/
0 notes
Photo

Penetration testing dropbox using a Raspberry Pi - https://redfoxsec.com/blog/raspberry-pi-pentest-dropbox/
0 notes
Photo

Android Pentesting Methodology (Pt. 2)
Read complete blog - https://redfoxsec.com/blog/android-pentesting-methodology-part-2/
0 notes
Photo

Android Pentesting Methodology
Complete blog - https://redfoxsec.com/blog/android-pentesting-methodology-part-3/
0 notes
Photo

Why Startups Need Penetration Testing?
Read complete blog - https://redfoxsec.com/blog/why-startups-need-penetration-testing/
0 notes
Photo

Get in touch with us for Cyber Security Services - https://redfoxsec.com/
0 notes
Photo

The differences between vulnerability scanning and penetration testing.
https://redfoxsec.com/blog/vulnerability-scanning-vs-penetration-testing/
0 notes
Photo

What is Web Application Penetration Testing?
- Web Application Penetration Testing is a set of methodical processes that includes enumerating the target application, identifying vulnerabilities, and then exploiting the vulnerabilities that could be leveraged to compromise an application.
Read in Details - https://redfoxsec.com/services/web-application-penetration-testing/
0 notes
Photo

Blog - Hacking GraphQL Part 3 - https://redfoxsec.com/blog/hacking-graphql-part-3/
Hacking GraphQL Part 1 - https://redfoxsec.com/blog/hacking-graphql-part-1/
Hacking GraphQL Part 2 - https://redfoxsec.com/blog/hacking-graphql-part-2/
0 notes
Photo

The NGINX 0-day Vulnerability
It all started on April 9th, when a Twitter account linked to a group named @_Blue_hornet tweeted about an experimental NGINX 1.18 attack, claiming to have discovered a zero-day or previously undiscovered security issue in NGINX – a web server used by a third of the world’s websites. The vulnerability appears to be related to how NGINX communicates with LDAP directory services, according to the claims.
Read Complete blog - https://redfoxsec.com/blog/nginx-zero-day-vulnerability/
0 notes