#256-bit AES Encryption
Explore tagged Tumblr posts
Text
Cryptomator
Cryptomator is a free, open-source tool providing multi-platform, transparent client-side encryption for your cloud files. Compatible with nearly any cloud storage service, it integrates seamlessly into your workflow, allowing you to work with files as usual. It uses robust 256-bit AES encryption for security. Additionally, it is user-friendly and requires no separate accounts, key management,…
#AES 256-bit#Client-Side Encryption#Cloud Security#data protection#encryption#File Encryption#Multi-Platform Security#Open Source#Privacy#Secure Cloud Storage
0 notes
Text
Enhance Your Digital Efficiency with RelyPass



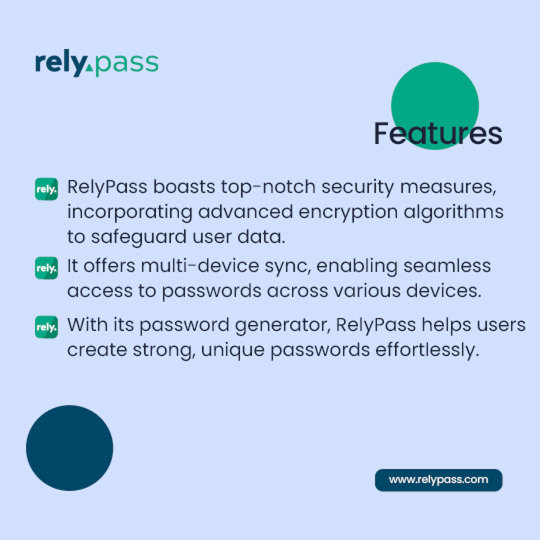

RelyPass, the ultimate iOS password manager app designed to revolutionize your digital efficiency. RelyPass effortlessly combines user-friendly features, unbeatable pricing, and top-notch security. Upgrade your digital lifestyle today and experience the convenience of RelyPass!
Download the App today!
#iOS password manager#Password manager app#Secure password manager#Best password manager#Password manager for iPhone#Top password manager#Password manager for iOS#Mobile password manager#Encrypted password manager#Multiplatform password manager#Biometric password manager#Password manager with face recognition#Cloud-based password manager#Password manager with AES 256-bit encryption#Free password manager for iOS#RelyPass#RelyPass App#RelyPass Password Manager#RelyPass iOS App#RelyPass iOS Password Manager
0 notes
Text
Modern Cryptography
(stemandleafdiagram long-form post!)
~ 2900 words
As you may have guessed, I love cryptography and ciphers even though I still don’t know much about them. I think classical ciphers are super interesting stuff and I love breaking them but I realised I knew nothing cipher-y after the end of World War 2, so I sought to rectify that!
(This is SO long - I got quite carried away (I do apologise), and as I wanted to cover so much here there are some concepts I don’t explain very thoroughly, but there are so many resources online if you want to learn more! When explaining how different forms of encryption work, I will often use the names commonly used by other cryptographers in my examples. Alice and Bob are two people trying to communicate, while Eve (an eavesdropper) is trying to intercept their messages.)
Symmetric Encryption
The start of modern cryptography is not a definite thing (obviously so, as the “eras” of cryptography are just labels people use to refer to them generally) but I decided to start my timeline for modern cryptography in the 1960s, as during this time, research projects at the American company IBM (International Business Machines) led to the creation of a cipher called the Lucifer cipher.
This cipher was one of the first block ciphers to be made. A block cipher is a cipher that operates on blocks of 128 bits at a time. This is in contrast to a stream cipher, which encrypts 1 bit of data at a time. (In a way, you could consider classical ciphers stream ciphers) If the plaintext (un-encrypted data) is smaller than 128, padding schemes will add random data to it to make it up to 128. Modes of operation define how large amounts of data are encrypted. For example, the blocks of data can be encoded separately, or maybe the encryption of one block is affected by the previous encoded block of data.
The Lucifer cipher underwent a lot of alterations, and eventually the National Bureau of Standards adopted this altered version of Lucifer as the Data Encryption Standard, or DES, in 1977. Some of the alterations made that led to DES were actually quite controversial! For example, the key size in Lucifer was 128 bits, but only 56 in DES, which worried people who thought it would have been easier to brute force as it was shorter. It’s actually rumoured that the NSA (National Security Agency) did this so that the DES wasn’t too strong for them to break. Another change they added was the inclusion of something called S-boxes, which are effective at protecting against a form of attack called differential cryptanalysis. What I found really cool was that its effectiveness wasn’t talked about until much after, which suggests that the NSA knew about differential cryptanalysis 13 years before this information went public!
The DES is no longer secure enough for modern use, and in 2001 was replaced by the AES, or the Advanced Encryption Standard, which is its direct successor and is still used today. The reason that AES is more secure than DES is that the algorithm itself is more complex, but more importantly it uses longer key lengths. Using keys that are 128, 192, or 256-bit long means that the encryption is much stronger than using the 56-bit DES.
Lucifer, DES, and AES are all symmetric ciphers as well as being block ciphers. This means that the key used to encrypt the plaintext is the same key that is used to decrypt the data. Only some block ciphers are known publicly. DES and AES are the most famous of the lot, but other ones such as IDEA, Twofish, and Serpent exist too.
As a whole, encrypting with block ciphers is slower as the entire block must be captured to encrypt or decrypt, and if just 1 mistake is made the whole block can be altered. But, they are stronger than other ciphers. Each mode of operation also has its own pros and cons. If each block is encoded by itself then they can be encrypted in parallel (which is faster), but it’s prone to cryptoanalysis as two identical blocks of plaintext would produce two identical blocks of ciphertext, therefore revealing patterns. The other ways are much more complex and take more time to encrypt but are more secure.
For symmetric encryption to be used, both parties need to agree on the same key for the message to be shared secretly, which is a massive problem. How can the key be transferred securely?
Key Exchange
A year before the implementation of DES, in 1976, another massive breakthrough was made. Researchers Whitfield Hellman and Martin Diffie created the Diffie-Hellman key exchange, which was a method to share encryption and decryption keys safely across an unsecured network. The way it works depends on one-way functions. Typically in maths, most functions are two-way, as using a function on a number is pretty easy to undo. However, Hellman and Diffie found out that while multiplying two prime numbers was very easy, factorising the product down to its primes again was excruciatingly difficult, and the difficulty only increases as the numbers get bigger.
Say Alice and Bob are trying to share a key using the Diffie-Hellman exchange. Firstly, both of them need to execute a function in the form G^a mod P. P must be prime, and G and P are shared publicly so Alice and Bob can agree on them. The numbers are massive (usually 2048 bits) to make it harder to brute force, and they are generated randomly. Alice and Bob each choose different numbers for a, and run their functions. They will get different answers and they share their answers with each other publicly. (This is the public key) Then, Alice and Bob run another function in the form G^a mod P, but G is set to the other person’s answer. The value of a and P stay the same, and Alice and Bob arrive at the same secret answer. The secret answer can then be used to encrypt the message! (This is the private key)
Now, let’s say Eve wanted to find out what the key was. She intercepts their messages, but even though she has the exact information Alice and Bob shared with each other, she doesn’t know what the secret key is unless she solved the original equation, making this key exchange very secure! Modular arithmetic (the mod P part of the equation) is notoriously hard to reverse. If 2048-bit numbers are used, then brute forcing it requires 2^2048 numbers.
Asymmetric Encryption
The Diffie-Hellman key exchange was huge - I mean, any technology created 50 years ago that’s still in use must be pretty good, but it really only shone for sharing keys, not for encryption. For example, the issue with sending communication such as emails using Diffie-Hellman was that both parties needed to be online for a key to be generated as information needs to be mutually shared in the process, so you couldn’t just send an email using it whenever you wanted, which was a shame. However, one particular thing it did lead to was the invention of asymmetric encryption.
In 1977, the idea of public key cryptography (also invented by Diffie) came to fruition in the form of RSA. Named after its creators (Ron Rivest, Adi Shamir, and Leonard Adleman), the RSA works by all users having a public key, which is accessible by everyone, so anyone wanting to send that user a message just needed to search for it. The sender encrypts the message with the recipient’s public key, and then when the recipient comes online they are able to decrypt it with their own private key that’s not shared with anyone. It also uses an one-way function like the Diffie-Hellman exchange, albeit a more complex one. RSA is still used today for things like sending messages or visiting secure websites, and the keys tend to be 2048 or 4096 bits long so that they are hard to break. 1024-bit RSA was disallowed in 2013.
Encrypting via public key and decrypting via private key is great for keeping sensitive information safe, but what if you encrypted with your private key and the message was decrypted with your public key? The purpose of this encryption is to prove the sender is who they say they are - if the public key can’t decrypt the message then either the wrong key was used or the message has been meddled with in transit. To keep the message secure the sender could encrypt with their private key and also the recipient’s public key so only they could decrypt and read it. If the message is particularly long, the digital signature can be applied to a hash of the original message, rather than the whole thing. The RSA was the first to have this dual functionality.
So, there we go - the two main encryption types used today: symmetric and asymmetric. Symmetric encryption is useful for large amounts of data in particular, while asymmetric is more secure, but is slower and requires more resources and therefore can be more expensive. In practice, many secure systems will use both symmetric and asymmetric ciphers. Although, the actual security of a message comes down to the length of the key used - the longer or more complex it is, the more secure the encryption is. As the number of bits increases, the total number of arrangements for these bits increases exponentially. The IBM website states that a 56-bit key could be brute forced in around 400 seconds, a 128-bit key would take 1.872 x10^37 years, while a 256-bit key would take 3.31 x10^56 years.
Going Quantum
It goes without mention as to how important modern cryptography is. These encryption methods are used to keep confidential information such as credit card details, messages, and passwords safe for users like you and me, but also maintains government security on a national level. It’s also vital for cryptocurrency and digital signatures (as mentioned before), as well as browsing secure websites.
A big threat to current cryptographic standards is the development of quantum computing, which are computers based on principles of quantum mechanics. I won’t go into detail on how quantum computers work, but using quantum mechanics they are able to do massive numbers of calculations simultaneously. Although quantum computers already exist, they aren’t powerful or capable enough to threaten our current encryption algorithms yet. But, researchers suggest that they could be able to within a decade. People could use a technique called “store now, decrypt later”, where they keep currently encrypted messages so that they can decrypt them when quantum computers are available. This could cause many problems in the future, particularly if they involve secrets on an international level.
Quantum mechanics can also be used in cryptography as well! Quantum cryptography, originally theorised in 1984 by Charles Bennett and Gilles Brassard, can be used to exchange keys even more securely than Diffie-Hellman, and is called QKD, or Quantum Key Distribution. The reason it’s so incredible is that data that’s secured using it is immune to traditional cryptographic attacks. Now, I’m no quantum physicist (or any type of physicist!) but I will try my best to explain how it works. It works by sending photons, which are light particles, from the sender (eg. Alice) to the receiver (eg. Bob). These photons are sent at different orientations and Bob can measure the photon’s polarisation when he gets them.
Let’s say that photons can be in a vertical, horizontal, or one of the two diagonal orientations. We can pass them through a polarised filter to find out what orientation they are in. The filters are also specifically oriented. A vertical filter would let the vertical photons through, block the horizontal ones, and let the diagonal ones in 50% of the time but at the cost of the ones that pass through being reoriented. Therefore, when a particular photon successfully passes through, it’s impossible to know whether it was originally diagonal or vertical. This is important as it means that it’s possible to detect if someone else has been eavesdropping as the polarisations would have been changed.
Bob can use two measurement bases to receive the photons Alice sent. One will capture vertical and horizontal orientations, and one will capture diagonal ones. Bob has no idea what orientation Alice used for each photon, so he switches between his bases randomly, and will get it wrong some of the time. This is fine, as Alice and Bob then compare to see which ones Bob got right, and the ones he correctly guessed are used as a key (each photon representing 1 bit). The key can then be used for other encryption methods, such as AES.
The reason this works is that if Eve wanted to pry, she has to guess which base to use as well when she intercepts the photons (so she will also make mistakes), but she has no way of checking whether her records are correct or not, unlike Bob. It’s impossible for her to obtain the key as well. What’s more, when she guesses wrong she will change the photon polarisation, so Alice and Bob know that she’s eavesdropping.
Quantum cryptography would have huge security benefits if implemented on a wide scale due to its ability to prevent eavesdroppers, and the fact that it would be resistant to quantum computers. However, it is still in development. One key drawback is the specific infrastructure that is needed, and fiber optic cables have a limited range. This means that the number of destinations the data could be sent to is limited, and the signal cannot be sent to more than 1 recipient at any time.
As well as quantum cryptography, the NIST (The National Institute of Standards and Technology) and other cryptographers are working on other cryptographic algorithms that would stay secure even in the face of quantum computers. Ideas include lattice-based cryptography, hash-based cryptography, and code-based cryptography among others but none of them are at a point where they can actually be implemented yet.
However, one new idea that isn’t post-quantum but is gaining traction is Elliptic Curve Cryptography. Elliptic curve cryptography (ECC) is a form of asymmetric encryption that uses different points on an elliptic curve graph to generate keys in a more efficient manner than traditional methods. It creates shorter encryption keys, which means that less resources are needed while making the keys harder to break simultaneously. Improving the security of current systems just involves lengthening the keys, which slows down the encryption/decryption process, so the fact that ECC doesn’t need to do this gives it a big advantage. It is already used by the US government, iMessage, and Bitcoin, among others.
Sidenotes
With the maths of these encryption methods being so strong, one key vulnerability is the people that utilise these methods, which is no surprise. Side channel attacks are a way to break cryptography by using information physically leaked from it. One attack, called a TEMPEST attack, is a technique that can pick up electromagnetic transmissions from a device as far as 300m away. These are often done by the FBI, but honestly can be done quite easily by some nerd who has some money to spare and can sit in a car outside your window. By monitoring the radiation emitted from your computer screen, the attacker can spy on you and your data. Another thing that can be monitored is your power consumption. Cryptography is energy intensive, and this attack has been able to recover RSA private keys in testing. Other forms of attacks include measuring amount of time required to encrypt data, which can perhaps be used to find factors or exponents. To combat this, encryption methods can add timing noise as a countermeasure. Or, an attacker can listen to someone type to find out their passwords, but to distinguish different key presses a sophisticated machine learning model is needed. Side channel attacks have actually been around for ages but its use has been severely limited in that the attacker needs to be physically close to the victim. They could get easier with time, however, as smartphones and drones can act as microphones remotely.
Another cool thing I haven’t covered yet are hash functions, which can take in an input and map it to a string of characters that’s random but unique to the original data. The output is called a hash digest or hash value. A good hash function will mean that no two different inputs will have the same hash value, and all outputs are the same length, making it hard to guess original text length. It’s vital for digital signatures and storing passwords securely.
Finally, if anyone managed to get to the end, then thank you! I really love cryptography and I find it astounding that we’ve been able to develop it into such a complex yet intrinsic part of daily life. Honestly, I had so much fun researching for this post! Encryption and cybersecurity and the future of computing is so interesting and I’m really glad I decided to write this :)
Final final note you should totally go and read the Code Book by Simon Singh! Trust me trust me it’s so good...
4 notes
·
View notes
Text
Idly musing about post-quantum encryption algorithms. Suppose you had a system where there were public servers - effectively numbers stations - that constantly emitted a stream of random bytes (perhaps literally generated via radioactive decay), broadcast them publicly, and recorded them for a long period of time. Suppose also that any two parties that want to communicate negotiate a small shared secret out-of-band, say a 256-bit AES key. When Alice wants to send Bob an encrypted message, she records the current time from the numbers station, listens for bytes from the numbers station, and encrypts them with that shared secret. Alice then uses this new stream of random bytes as a one-time-pad and encrypts her message. When finished, she records the stop time and sends the encrypted message, start time, and stop time to Bob. Bob can use the start and stop times, his small shared secret, and the public records of the numbers station to reconstruct the stream of random bytes Alice used, and then XOR that against his received cyphertext to recover the plaintext. If there was a way to remove the initial small shared secret step, I think this sort of scheme would be a way that people could continue to do effective asymmetric cryptography even in a post-quantum world, albeit with the requirement that these numbers stations exist and keep records for a long period of time.
2 notes
·
View notes
Text
Get your private VPN for safe and secure browsing..
#polls#vpn#vpnservice#best vpn#best cheap vpn monthly#free vpn#hack#internet security#cybersecurity#data security#apps
6 notes
·
View notes
Photo
Also don't make backups on the same physical media (i.e. on your hard drive) backing up your desktop to your documents folder does not help you if your hard drive ever becomes unusable. Normal spinning disc hard drives (ones that are not SSDs or M.2/NVME) DO have a lifespan. You can use SMART tests to see if there are any signs of failure ahead of time.
Ideally, you would back up your personal data in a separate, secure physical location. On an individual level, this could be a bank deposit box with an external hard drive in it. For most people, that may seem a bit overboard, but if something happens that completely destroys everything in your home, you still have a backup.
A more realistic and reasonable approach would be to have an external hard drive you back up to at regular intervals (this is up to you and how much data you're willing to lose. A week/month is a reasonable amount of time between backups, and more frequently if you're constantly creating and changing data you don't want to lose). After the backup, you can store the drive in a water proof and fire proof safe and keep it somewhere safe in your home
You can also back files up to the cloud if you're comfortable with it being hosted by an outside company. Bigger companies will have several backup sites with data on them to prevent data loss in the event of a disaster at one of their data centers. The downside is you may have to pay a monthly fee to have enough storage, and also you're trusting your data with a third party company.
As far as external hard drives are concerned, I tend to shy away from USB sticks and external drives that connect via USB. I've seen way too many of their ports get broken off or worn out and become unusable without some complex data recovery methods you probably can't do on your own, and would cost a lot of money through a professional. For a cheap solution, you can buy a hard drive bay and an internal (3.5 inch) HDD to copy your data to. HDDs are cheap and can hold a ton of data (since you're just backing up data and rarely accessing it, the slower speed compared to an SSD isn't really worth paying extra for an SSD imo). These bays look like toasters, and you should get one that has removable and replaceable cables

They'll look something like this ^
The smaller drive in the front is a 2.5 inch SSD and the one in the back is a 3.5 inch HDD ("internal" hard drive). You may also find smaller 2.5 inch HDDs. These typically go in laptops and don't really provide extra benefit (and I believe they're normally a bit more expensive) so I still recommend a 3.5 inch drive.
Your station will also need an external power supply as USB will not have enough power to get the HDD spinning (most come with power, just don't use one of those SATA to USB adapters for anything that's not a 2.5 inch drive)
Set a reminder for your backups, you will forget. It's human error. Don't leave your backup drive constantly plugged in, it's vulnerable in the event of a disaster (spill, tornado, ceiling collapse) and will most likely be destroyed alongside your internal drive. Take it out. Do a backup. Lock it somewhere safe.
If you're worried about your data security on the external drive, you can encrypt the whole disk using a tool like VeraCrypt (I recommend using an AES encryption method, typically AES-256 or AES-128). This will make it so your drive cannot be accessed without using VeraCrypt and also without a password. DO NOT lose this password as you will almost certainly not be able to access your information without it! (AES encryption is too strong to brute force without an insanely long amount of time. We're talking literally hundreds of thousands of years with current computing power)
You don't need to back up everything, just the stuff you'll miss. And you can also keep multiple copies of backups at once. It's. A good idea to keep a few (maybe four backups at a time) and delete the oldest one whenever you make a new one. This gives you a few to pick from in case you purposely delete a file, but later want it back. It may be in one of your older backups, saving you a loss.
This is a pretty basic startup guide on proper backup techniques, and you're more than welcome to message me with questions.

beastly reminder
74K notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] From the manufacturer Work and play - wherever and whenever. The My Passport Portable Hard Drive, Works with USB-C No matter where creativity or adventure strikes, the My Passport portable hard drive is the perfect storage companion for your on-the-go lifestyle - and your USB-C devices. Enjoy seamless compatibility across your Windows PC, Mac, Chromebook, gaming consoles, mobile phones, and tablets with a USB-C connection. And store your files safely with backup software[2] and password protection. Features at a Glance Compatibility with USB-C and USB-A port devices Up to 5TB(1) capacity Includes software(2) for device management and backup Designed with the planet in mind Hassle-free connectivity Connect to more USB-C or USB-A devices, including your Windows PC, Mac, Chromebook, gaming consoles, mobile phones, and tablets, without the inconvenience of switching cables. Friendly to your devices Ready to use out of the box, the My Passport portable hard drive is compatible with your Windows PC, Mac, gaming consoles, and mobile devices, without needing to reformat your drive or buy additional software. Incredible capacity for your content Up to 5TB(1) of space to keep your important files, creative projects, school assignments, family photos and videos, and favorite games in one place. Help safeguard what matters most Use our included software(2) to back up your precious files with ease and add an extra layer of password protection with built-in 256-bit AES encryption.
Add to Cart Add to Cart Add to Cart Customer Reviews 4.4 out of 5 stars 207 4.2 out of 5 stars 371 4.2 out of 5 stars 3,036 4.4 out of 5 stars 10,294 Price — no data ₹11,799.00₹11,799.00 ₹12,999.00₹12,999.00 ₹16,899.00₹16,899.00 Capacity(1) 1TB / 2TB / 4TB / 5TB / 6TB 2TB / 4TB / 5TB 2TB / 4TB / 5TB 1TB / 2TB / 4TB / 5TB / 6TB Backup software(2) ✓ ✓ ✓ ✓ Device Management(2) ✓ ✓ ✓ ✓ Password Protection 256-bit AES Hardware Encryption 256-bit AES Hardware Encryption 256-bit AES Hardware Encryption 256-bit AES Hardware Encryption Connector USB-A USB-A w/ USB-C adapter USB-A w/ USB-C adapter USB-C w/ USB-A adapter Colors Black, Blue, Red Silicon Grey Midnight Blue Metallic Blue, Metallic Silver PC/Mac Ready PC Ready PC/Mac Ready (exFAT) Mac Ready PC Ready
Legal Disclaimers (1). 1TB = 1 trillion bytes. Actual user capacity may be less depending on operating environment. (2). Available for Windows 10+ and macOS 11 + devices only. Download and installation required. Terms and conditions apply. User account registration may be required. WO, the WO logo, and My Passport are registered marks or marks of Western Digital Corporation or its affiliates in the U.S. and/or other countries. Windows is a mark of Microsoft Corporation. Mac is a mark of Apple Inc. Chromebook is a mark of Google LLC. USB-C is a mark of USB Implementers Forum. All other marks are the property of their respective owners. Product specifications subject to change without notice. Pictures shown may vary from actual products. 2025 Western Digital Corporation or its affiliates. All rights reserved. Slim durable design to help take your important files with you Seamless compatibility with USB-C devices including Windows PC, Mac, mobile phones and tablets Vast capacities up to 6TB* to store your photos, videos, music, important documents and more Back up smarter with included device management software with defense against ransomware Help secure your important files with password protection and hardware encryption and comes with a 3 year limited warranty provided by Western Digital [ad_2]
0 notes
Text
Types of VPN
VPN Security: Encryption, Hashing, and VPN Types | Sfour eSolutions
In today’s digital age, cybersecurity is a top priority for businesses and individuals alike. At Sfour eSolutions, we understand the importance of keeping your online activities private and secure. One of the most powerful tools in your cybersecurity arsenal is a Virtual Private Network (VPN). In this article, we’ll dive into what VPNs are, how they use encryption and hashing to protect your data, and the different types of VPNs available.
What is a VPN?
A Virtual Private Network (VPN) is a secure technology that creates a private tunnel between your device and the internet. This tunnel encrypts your data, ensuring that it remains confidential and protected from hackers, ISPs, and other cyber threats.
VPN security is crucial for:
Protecting sensitive data on public Wi-Fi
Accessing geo-restricted content
Bypassing internet censorship
Enabling secure remote access for employees
How VPNs Use Encryption Technology
At the core of VPN security is encryption technology. Encryption converts your readable data (plaintext) into an unreadable format (ciphertext) that can only be deciphered with the correct key.
Popular encryption algorithms include:
AES (Advanced Encryption Standard): Often used in 128-bit or 256-bit formats, it’s one of the most secure and widely adopted encryption standards.
RSA: Used for secure key exchange and establishing encrypted connections.
This ensures that even if data is intercepted, it remains confidential and inaccessible without the decryption key.
Hashing for Data Integrity and Authentication
While encryption protects data confidentiality, hashing ensures data integrity and authentication. A hash function generates a unique, fixed-length string (hash) from your data. Even the slightest change in the input creates a completely different hash, making it easy to detect tampering.
VPNs use hashing for:
Authentication: Verifying the identity of users and servers.
Data integrity: Ensuring that data is not altered in transit.
Common hashing algorithms include SHA-256 (Secure Hash Algorithm), which is widely trusted for its strong security.
Types of VPNs
Choosing the right VPN is crucial for your organization’s cybersecurity. Here are some of the types of VPNs and their typical use cases:
Remote Access VPN
Enables individual users to securely connect to a private network from any location.
Ideal for remote work and hybrid workforces.
Site-to-Site VPN
Connects entire networks, such as branch offices or data centers.
Perfect for organizations with multiple locations.
Client-to-Site VPN
Provides secure remote access using dedicated client software.
Common for businesses needing reliable secure remote access.
SSL VPN
Uses SSL/TLS protocols (the same as HTTPS websites) for encryption.
Accessible via web browsers, with no need for extra software.
Mobile VPN
Designed for devices that roam between networks (e.g., smartphones).
Ensures uninterrupted secure connectivity.
Why Choose Sfour eSolutions for Your VPN Needs?
At Sfour eSolutions, we specialize in delivering VPN solutions tailored to your business needs. Our expertise in encryption technology, hashing techniques, and secure remote access ensures your data is protected every step of the way.
Contact us today to learn how we can help you implement a secure and reliable VPN solution for your organization.
Final Thoughts
A VPN is an essential tool for protecting your online privacy and business data. By combining encryption, hashing, and the right VPN types, you can ensure robust security for your network.
Need help choosing the right VPN? Sfour eSolutions is here to guide you every step of the way.
0 notes
Text
Encrypted Flash Drives Market : Size, Trends, and Growth Analysis 2032
Encrypted Flash Drives Market: Enhancing Data Security in a Digital Age
The Encrypted Flash Drives Market was valued at US$ 105.90 Million in 2024 and is expected to grow at a CAGR of 7.99% from 2025 to 2032. As data breaches and cyber threats continue to escalate globally, the demand for secure portable storage solutions such as encrypted flash drives is surging.
Understanding Encrypted Flash Drives
Encrypted flash drives are USB-based storage devices embedded with encryption technology to secure data at rest. Unlike conventional flash drives, these devices use sophisticated encryption algorithms — often hardware-based — to encode data, ensuring that unauthorized users cannot access stored information without the correct decryption key or password.
The hardware encryption offers a superior layer of protection compared to software-only encryption solutions, safeguarding against malware attacks, hacking attempts, or physical theft. These devices are widely used across industries such as finance, healthcare, government, and defense, where safeguarding sensitive data is paramount.
Market Drivers
1. Increasing Data Privacy and Security Regulations Stringent data protection laws worldwide, including GDPR in Europe, HIPAA in the U.S., and similar regulations in other regions, are compelling organizations to adopt robust data security measures. Encrypted flash drives help companies comply with these regulations by protecting data during transit and storage.
2. Rising Cybersecurity Threats With escalating cyberattacks, ransomware incidents, and insider threats, organizations seek reliable solutions to prevent unauthorized access. Encrypted flash drives provide a secure method for data transport without compromising confidentiality.
3. Growing Adoption Across Verticals Industries like healthcare require encrypted drives to secure patient data; financial institutions use them to protect transaction records; government agencies rely on them for classified information. The broad application across verticals fuels market growth.
4. Increasing Remote Work and Data Mobility The rise of remote work has amplified the need for secure portable storage. Employees and contractors often transfer sensitive data across networks and devices, and encrypted flash drives provide a secure physical medium for such transfers.
Key Features and Benefits
Hardware-Based Encryption: Many encrypted flash drives use AES 256-bit encryption, ensuring robust data protection independent of host device security.
Password Protection and Multi-Factor Authentication: Some models support biometric verification or require multi-layered authentication to unlock data access.
Tamper-Resistant Design: Devices often come with rugged casings, tamper-evident features, and self-destruct mechanisms to safeguard against physical attacks.
Cross-Platform Compatibility: These drives typically support multiple operating systems including Windows, macOS, and Linux, ensuring wide usability.
Challenges in the Market
Despite the growing demand, the encrypted flash drives market faces some challenges:
Higher Cost Compared to Conventional Drives: The added encryption and security features increase the price point, which can be a barrier for price-sensitive customers.
User Awareness and Adoption: Some organizations still rely on traditional storage methods or software encryption due to lack of awareness or perceived complexity of hardware-encrypted drives.
Potential Performance Overheads: Encryption and decryption processes may slightly affect data transfer speeds compared to non-encrypted flash drives.
Market Segmentation
By Product Type:
Hardware Encrypted Flash Drives
Software Encrypted Flash Drives
By Application:
Government & Defense
BFSI (Banking, Financial Services, and Insurance)
Healthcare
IT & Telecom
Consumer Electronics
Others
By Region:
North America
Europe
Asia-Pacific
Rest of the World
North America dominates the market due to stringent cybersecurity regulations and high adoption of advanced security technologies. Asia-Pacific is expected to register rapid growth owing to increasing digitalization and rising awareness about data protection.
Competitive Landscape
The encrypted flash drives market is highly competitive with several key players investing in R&D to enhance product features and expand their product portfolios:
ADATA Technology: Known for reliable and affordable encrypted drives with robust hardware encryption and rugged designs.
Samsung: Offers a range of secure flash storage solutions emphasizing speed and durability alongside encryption.
Kingston Technology: A leading manufacturer with a comprehensive lineup of encrypted flash drives featuring hardware encryption and multi-factor authentication.
Transcend Information: Focuses on enterprise-grade encrypted drives with advanced security management features.
Corsair: Provides high-performance encrypted drives targeting professional and consumer segments.
Seagate Technology: Combines storage capacity and data protection through advanced encryption technologies.
Micron Technology: Known for innovative memory and storage solutions including secure flash drives.
Apricorn: Specializes in hardware-encrypted flash drives with certified security standards suitable for government and corporate use.
Industry Trends and Innovations
Integration of Biometric Authentication: Emerging encrypted flash drives incorporate fingerprint sensors to enhance security and usability.
Cloud-Integrated Secure Storage: Some solutions now offer hybrid models combining encrypted flash drives with cloud backup and remote wipe features.
Compact and Rugged Designs: Manufacturers are focusing on making drives smaller, durable, and water-resistant for field use in harsh environments.
Enterprise Security Management: Advanced management software allows IT administrators to control, monitor, and audit encrypted flash drives deployed within organizations.
Future Outlook
The encrypted flash drives market is expected to witness consistent growth as digital transformation intensifies and data security becomes a top priority for enterprises globally. With cyber threats growing in sophistication, demand for hardware-based secure storage solutions will increase.
Companies focusing on innovation in encryption technologies, ease of use, and compliance with international security standards will likely gain competitive advantages. The proliferation of IoT, mobile computing, and edge devices will also boost demand for portable yet secure data storage options like encrypted flash drives.
Browse more Report:
Industrial Discrete Semiconductor Market
EUV Pellicle Market
Encrypted Flash Drives Market
Electronic Materials and Chemicals Market
E-Beam Wafer Inspection System Market
0 notes
Text
The Importance of Two-Factor Authentication for iOS Users
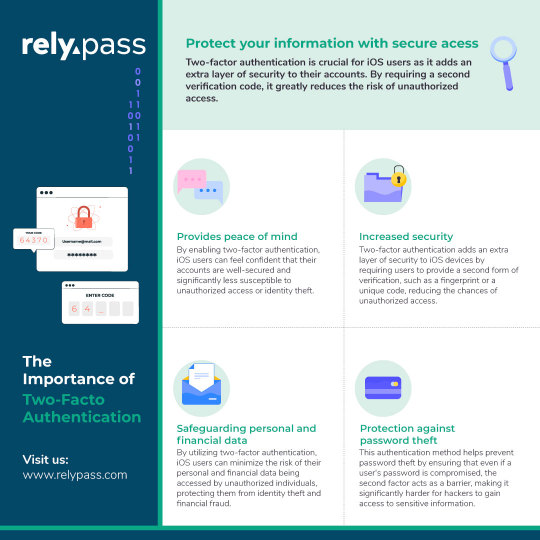
Step up your security game with two-factor authentication for iOS users! 🛡️ Add an extra layer of protection, minimize the risk of unauthorized access, safeguard your personal and financial data, and enjoy peace of mind.
#iOS password manager#Password manager app#Secure password manager#Best password manager#Password manager for iPhone#Top password manager#Password manager for iOS#Mobile password manager#Encrypted password manager#Multiplatform password manager#Biometric password manager#Password manager with face recognition#Cloud-based password manager#Password manager with AES 256-bit encryption#Free password manager for iOS#RelyPass#RelyPass App#RelyPass Password Manager#RelyPass iOS App#RelyPass iOS Password Manager
0 notes
Text
The Future of Data Security: Advanced Encryption Algorithms
Every time we share a file, store data encryprion in our cloud storage, or collaborate online, we fear exposing information to some unknown threats. With the ongoing data breaches in the digital landscape, securing data has become the call of the hour.

Traditional encryption methods that used to be reliable are now struggling to keep pace with today’s threats. They weren’t designed to handle the rapid-fire attacks, massive data demands and other looming challenges.
However, to stay ahead of the game, there are advanced encryption algorithms that are robust and future-ready. Protect sensitive data in this ever-evolving digital environment.
This blog will shed light on these advanced encryption algorithms and discuss how they can protect our information.
What is Encryption?
At the very core of security, encryption is like locking your data into a digital safe. Only people with the key can open it. But the safes aren’t all built alike. In encryption, once you decide to secure the data, there are encryption methods, which are broadly categorized into two categories, namely – symmetric and asymmetric.
Symmetric encryption uses one key for both encryption and decryption, and in such a manner that it’s fast enough to encrypt large amounts of data, internal file storage, or a backup system. The difficulty, though, is in safely transmitting the key. If someone intercepts it, your data is at risk.
Used Algorithms include – the Advanced Encryption Standard (AES), the older Data Encryption Standard (DES), and its successor, the Triple DES (3DES) algorithm.
Asymmetric encryption operates using a pair of keys one public for encrypting the data and a corresponding private key used to decrypt it.
This encryption is slower compared to symmetric encryption but provides a safer way of exchanging information that does not involve sharing sensitive keys. WhatsApp, online transactions, and digital signatures are some examples of how this type of Advanced Encryption Standard is used.
Used Algorithms – RSA (Rivest-Shamir-Adleman), Diffie-Hellman.
Common Algorithms for Encryption
Choosing the correct encryption algorithm is no longer a technical decision; it’s now a matter of safety. Let us now look at some of the most extensively implemented encryption mechanisms that are building blocks today in data security.
1. AES (Advanced Encryption Standard)
The Advanced Encryption Standard (AES) is one of the most trusted symmetric block cipher methods used to secure data. It encrypts information in fixed blocks of 128 bits and supports key lengths of 128, 192, or 256 bits. Among these, AES-256 is recognized for its enhanced security and is officially approved by U.S. government agencies for protecting classified information.
Fast and highly safe, this is the best choice for either hardware or software implementations. Whatever the case, securing data in the cloud or even for internal systems, AES will always prove to be the most convenient, scalable, and reliable solution so governments, banks, and security-conscious corporations use it.
2. Triple DES (3DES)
Triple DES was made to improve the original DES (Data Encryption Standard), which was becoming vulnerable due to its limited key size. 3DES increases data security by using DES three times on a single block. While it was a reliable encryption algorithm at its time, it’s now considered obsolete and is being pushed aside by newer-generation algorithms like AES. Nevertheless, it is good to know that many legacy systems still use that.
3. RSA (Rivest–Shamir–Adleman)
The RSA algorithm was among the first widely used asymmetric encryption techniques. It generates two keys, one private and one public. For transferring safe data across open networks like the Internet, this makes it ideal. Emails, SSL certificates, and digital signatures are all encrypted using RSA. It is, however, slower than symmetric methods and thus cannot be used in encrypting enormous volumes of data.
What makes an algorithm advanced?
For an algorithm to be considered advanced, it must be resistant to contemporary attack methods such as cryptographic analysis and side-channel attacks. It should also be scalable. Most importantly, it needs to be future-proof or at least adaptable to the fast-changing landscape of cybersecurity.
In this case, the Advanced Encryption Standard (AES) is a prime example, particularly the variant of AES-256. This version involves 14 rounds of encryption, where the data undergoes a series of shifts, substitutions, mixing, and key additions that make it quite impossible to decode without the exact key.
Preparing for the Future: Securing Data with Advanced Encryption Algorithms
The repercussions of inadequate data security can be severe, affecting everything from customer trust to regulatory compliance. That’s why innovative organizations are investing in advanced encryption algorithms now to tackle the challenges of tomorrow.
Platforms like eShare.ai are leading the charge in this transformation. By adopting cutting-edge encryption standards
and facilitating secure file collaboration, this platform makes sure that sensitive information remains safe, whether it’s being stored, shared, or accessed by different teams. That’s because the future of data security isn’t just about stronger defenses; it’s about smarter, scalable, and proactive measures.
0 notes
Text
Life today massively depends on the online transactions and information sharing. Each of such undertakings of confidential information is protected with separate passwords. We are vulnerable in keeping track of all the passwords and require a sophisticated mechanism to manage our authoritative details safely, securely and sagaciously. One which is user-friendly, accessible from anywhere, provides active sync up, backup/restoration if required. Password managers are common on a desktop, however, the need on mobile has increased exponentially in recent years. Especially when you want to create a very secure password that may also be easy to remember. This need has prompted developers to make some of the most advanced applications. Below listed are a few of the best Android apps on google app store. If you are an iPhone user, we have similar password management apps list here. Keeper Password Manager This application provides private digital vault on Android, iOS, Mac and PC platforms that are encrypted and unbreakable. It uses the highest levels of privacy and security (256 bit AES, PBKDF2). Other features include password generator, power sharing, secure file manager, autofill login and password, vault to vault sharing, two-factor authentication, internal controls, Keeper for groups and enterprise. It comes in free and paid versions. Reneph Password Safe Password Safe encrypts stored data securely using 128 bit AES and gives single access only. It doesn’t have any access to the internet. Key functions include categorization of entries, password generator widgets, backup and restore, customized user interface, auto backup,* .csv import/export. Pro version has entry elements reordering facility, encryption up to 256 bit, import/export to excel, auto lock, backup to encrypted CSV, self-destruction. No sync up feature is available on this. LastPass Password Mgr Premium Mobile version of LastPass password manager securely syncs your passwords across all browsers and devices. Essential functions include auto-fill for Android 4.1+ and Chrome (Android 4.3+), earlier versions have “copy” options; auto fill login and forms, biometric authentication (using Samsung S5’s fingerprint reader), password generator, add, update and delete sites, secure notes and form fill, redesigned UI. It offers 14 days free trial and later $12 for a yearly subscription. MSecure - Password Manager Comes with some of the most advanced features, mSecure’s New 3.5 Version of the password manager includes Tablet support, Auto-Login, Auto-sync and more. It is ultra secure, simple & smart and uses 256bit Blowfish encryption. Key features comprise of an auto lock, password generator, sync cloud data protection architecture, auto back on SD and e-mail, user-friendly customized options, categorization of data; sharing via email, SMS or clipboard, auto capture weblog in, can import data from competitor products. 30 days trial and then for $14.99. Dashlane Password Manager Free password manager & secure digital wallet for Android and other devices. By using 256bit AES encryption, it provides firm security to your data, backup/restoration, strong security vault with security breach alerts, password generator, auto fill on Dashlane browser and auto-login for your apps with Dashlane keyboard. Premium version offers features like sync up of all devices; cloud backup, priority user support. Other features are an auto lock after inactivity. The application works in English, Spanish and French. SecureSafe Password Manager SecureSafe protects your passwords and documents from malicious hackers and unauthorized access, using AES-256 and RSA-2048 encryption. Essential functions are one login for all platforms, data sharing between SecureSafe and you is over HTTPS only, additionally encrypted passwords, 24/7 monitoring, data inheritance function if something happens to you, a single login for all devices, offline access to passwords, comes as iPod/iPad app and web app.
Advanced version with premium features comes in PRO, SILVER and GOLD account types. Android Wallet Password Manager aWallet Password manager has features like build in the editor; backup to the Android USB device, CSV format unencrypted data export and auto lock. Professional version contains password generator and CSV Import functions. Security features include user-friendly categorized encryption using AES and Blowfish algorithms with various key sizes. Triple DES with key sizes of 168 and 112 bits. Combinations of multiple criteria to decrypt the data, “Salt” combination with a master keyword to prevent theft, auto-destruction after failed unlocks. It has no internet access permission, however, the only permission it has is to access to the USB device to backup/restore the data files in case your phone is lost. Reneph Password Safe By using AES 128 bit based encryption, Reneph Password Safe doesn’t require permission to access the internet; widgets lets you copy passwords to your clipboard from your home screen. Categorized entries, single master password access, password generator, backup and restore the encrypted database, customized user interface, automatic clearing of the clipboard, auto back up, CSV- import/export and no unnecessary Android rights are some of its key functions. In professional version, entry elements can be defined and reordered, the definition of encryption key size up to 256bit, import/export from/to excel table, auto-lock, encrypted CSV-files, auto-backup to encrypted CSV and self-destruction. It doesn’t have sync up feature. Fasino Password Keeper This app is free. It allows you to store passwords for your accounts safely and securely on your devices. You can export the data and protect them with passwords import from the simple text files. Er.mo My Passwords A simple to use application with AES data storage, multi-window support, strong password generator, backup, restoration of the encrypted database and an offline operating facility to safely store substantial passwords and numbers encrypted. PasswdSafe - Password Safe PasswdSafe is a port of the Password Safe application to Android. Users can sync up the password files from cloud services too by installing the PasswdSafe Sync app. In case of bugs, it is advised to maintain a known good backup NS Wallet This application uses AES cipher algorithm and offers most reliable, secure, theft free and FREE data vault to the users. Works on “privacy are priority” principle, NS Wallet is a fully offline solution. All you need is a master password to it. With “ NS sync” backups in the cloud can also be created. Premium features include various themes, fonts and search criteria. Rhythm Hexise Password Safe Application ensures data privacy without internet permission, auto lock, SD card backup, customized password records on demand, dynamic support, different formats, creating records from pre-defined and new templates, password record management, 90+ icons to categorize, quick search, import/ export data using *.csv file for data exchange with other apps and multi-language support; Password Safe uses 256 bit AES algorithm for encryption. Safe In Cloud Password Manager Facilitates protection to your delicate data with unique and secure passwords, “SafeInCloud” uses 256 bit AES for complete password management. It comes as Free Desktop Application + Mobile Application for Phones and Tablets. Essential functions include strong encryption, cloud sync, password generator and strength analysis, browser integration, cross platform and automatic data import. DataVault Password Manager Ideal app and with unmatched features like multiple data views, flexible template management, on-device backup, password generator, security time out, maximum login attempts and synchronization with DataVault for Mac and DataVault for Windows (sold separately). The interface is optimized for mobile devices & desktop environments. Also, facilitates customized options, SD backup,
sync-ups, smart access control, password hints, online troubleshoot FAQs and personalized settings Ilium E-wallet- Password Manager eWallet application by Ilium software keeps important/authoritative and sensitive details secured behind the 256-bit military-grade AES encryption. PC version eWallet helps sync between multiple eWallets over Wifi. Customize your eWallets with cards, backgrounds, and categories. It auto locks detecting inactivity
0 notes
Text
Get ePay PG Integration by Infinity Webinfo Pvt Ltd

In today’s fast-paced digital economy, businesses need seamless and secure payment gateway solutions to ensure smooth transactions and enhanced customer satisfaction. Get ePay PG Integration is emerging as a preferred solution for many businesses, thanks to its robust features and ease of integration. Leading the way in facilitating this service is Infinity Webinfo Pvt Ltd, a company renowned for its top-tier API Integration Services.
What is Get ePay PG?
Get ePay is a versatile payment gateway (PG) platform designed to handle online payments swiftly and securely. It supports a wide range of payment modes including credit/debit cards, net banking, UPI, and digital wallets, making it ideal for e-commerce platforms, service providers, and online merchants.
Why Choose Get ePay PG API?
The Get ePay PG API allows businesses to integrate the payment gateway directly into their websites or applications. With this API, transactions become seamless, reducing cart abandonment rates and increasing conversion. Key benefits include:
Fast and reliable transaction processing
Multi-layered security and fraud detection
Real-time reporting and analytics
Developer-friendly documentation for smooth integration
Key Features of GetePay API Integration
Robust APIs and SDKs: GetePay offers developer-friendly APIs, plugins, and SDKs compatible with major platforms, facilitating seamless integration.
Customizable Branded Experience: Businesses can tailor the payment interface to align with their brand identity, ensuring a consistent user experience.
Multiple Payment Options: The platform supports various payment methods, allowing customers to pay using their preferred options.
Real-Time Dashboard: Merchants have access to a comprehensive dashboard to manage payments, refunds, subscriptions, invoices, and more.
Security and Compliance: GetePay employs AES 256-bit encryption and is PCI DSS compliant, ensuring secure transactions.
Instant Activation: Businesses can get started quickly with minimal documentation, enabling swift transaction processing.
Steps to Integrate GetePay API
Register for a GetePay Account: Sign up on the GetePay website to obtain your merchant credentials.
Access API Documentation: After registration, log in to your merchant dashboard to access the API keys and integration guides.
Choose Integration Method: Depending on your platform (e.g., web, mobile), select the appropriate SDK or plugin provided by GetePay.
Implement API Calls: Use the provided documentation to implement API calls for payment processing, handling callbacks, and managing transactions.
Test the Integration: Before going live, thoroughly test the integration in a sandbox environment to ensure all functionalities work as expected.
Go Live: Once testing is successful, switch to the production environment to start processing real transactions.
Infinity Webinfo Pvt Ltd: Your Trusted API Integration Partner
When it comes to API Integration Services, Infinity Webinfo Pvt Ltd stands out for its deep technical expertise and client-centric approach. With years of experience in fintech and software development, the company ensures that businesses can integrate the Get ePay PG API smoothly, with minimal downtime and maximum security.
What Infinity Webinfo Offers:
End-to-End Integration: From initial setup to final testing, the company handles the full integration process.
Custom Solutions: Tailored API integration to suit specific business needs.
Technical Support: Ongoing support to handle any issues post-integration.
Compliance Assurance: Ensuring that the integration meets security and regulatory standards.
Why API Integration Services Matter
In a digital-first world, API integration plays a critical role in unifying different software systems. It enables automation, improves data accuracy, and enhances user experience. By choosing the right partner like Infinity Webinfo Pvt Ltd, businesses can future-proof their operations and gain a competitive edge.
Conclusion
Whether you're an emerging startup or a large enterprise, leveraging Get ePay PG API through expert API Integration Services can streamline your payment processes and boost business efficiency. With Infinity Webinfo Pvt Ltd at your side, you gain a reliable partner committed to delivering secure, scalable, and smart solutions.
Contact Now :- +91 97110 90237
#api integration#infinity webinfo pvt ltd#travel portal development#travel portal company#payment gateway api integration
0 notes
Text
ZKTeco Integration with Access Control and Door Locks: Revolutionizing Security
In an era where security and convenience are paramount, ZKTeco has emerged as a global leader in biometric identification, access control, and smart lock solutions. By seamlessly integrating its advanced technologies with access control systems and door locks, ZKTeco offers businesses, residences, and institutions a robust, scalable, and user-friendly approach to safeguarding assets and people.
ZKTeco’s Access Control Solutions: The Foundation
ZKTeco’s access control portfolio is diverse, offering standalone devices, networked panels, readers, and accessories tailored to small businesses, enterprises, and everything in between. Key components include:
Standalone Biometric Terminals: Devices like the Horus E2 combine facial, fingerprint, multi-tech card, and QR code authentication for single-door control. Running on Android 10, they support Wi-Fi and 4G LTE for seamless connectivity and third-party app integration.
IP-Based Control Panels: The C3 Plus series (C3-100 Plus, C3-200 Plus, C3-400 Plus) manages up to 100,000 users and QR code transactions, supporting Wiegand and OSDP protocols for reader compatibility. AES 256-bit and 128-bit encryption ensure secure data storage and communication.
Readers: The ProID Multi-tech readers handle 125KHz and 13.56MHz RFID cards (ID, IC, NFC, DESFire EV1 & EV2), integrating via RS485 or Wiegand with ZKTeco’s InBioPro series or third-party controllers.
Software: ZKBio CVSecurity and other platforms provide web and mobile interfaces for real-time monitoring, configuration, and reporting.
These solutions form the backbone of ZKTeco’s integration with door locks, enabling precise control over who enters, when, and where.
Smart Door Locks: ZKTeco’s Innovative Edge
ZKTeco’s smart door locks blend security, convenience, and modern technology, offering multiple authentication methods and remote capabilities. Notable models include:
SL01-T430H: A mortise-style lock with a lever handle, featuring fingerprint recognition, a touch keypad, and remote unlocking via the ZSmart app over Wi-Fi. It includes a doorbell button, a “Do Not Disturb” schedule, and voice command compatibility with Amazon Echo or Google Home. It’s ideal for luxury homes and apartments.
TL800: A fully automatic lock with a built-in LCD screen for indoor monitoring. It supports remote unlocking via ZSmart over Wi-Fi, allowing users to view outdoor activity and enhance home security.
TL300Z: An advanced fingerprint keypad lock with Zigbee communication and a robust zinc alloy casing. Paired with a Zigbee Gateway, it offers remote unlocking, log history, and temporary passcode sharing via the ZSmart app, perfect for private houses and short-term rentals.
ML300: An entry-level fingerprint and keypad lock with Bluetooth, easy to install on single-hole doors. It supports remote unlocking and voice commands via Bluetooth Gateway and ZSmart, suited for homes and junior apartments.
ML200: A digital keypad lock with Bluetooth for semi-outdoor use, offering simple setup and smart functionality.
These locks integrate biometric, RFID, passcode, and mobile app controls, making them versatile for residential, commercial, and hospitality settings.
How ZKTeco Integrates Access Control and Door Locks
ZKTeco’s integration of access control and door locks creates a cohesive security ecosystem. Here’s how it works:
1. Seamless Hardware Connectivity
ZKTeco’s access control panels, like the InBioPC Main Controller, connect to door units (e.g., DE-10) and locks via TCP/IP, RS485, or Wiegand protocols. The InBioPC supports 4/8 access points, powering door units via PoE (IEEE802.3, PSE@30W) for efficient data transfer and control. For example, the ProMA series—outdoor multi-biometric terminals (ProMA-QR, ProMA-RF, ProMA)—combines facial, fingerprint, and RFID authentication, linking to locks with IP66 water/dust resistance and IK07 vandal protection.
2. Biometric and Multi-Tech Authentication
ZKTeco integrates advanced biometrics into both access control and locks. The KF1100 Pro and KF1200 Pro facial readers capture and convert face images into 512-byte templates, transmitting them to InBio Pro Plus controllers via RS485 for authentication. These readers also function standalone with a DM10 door lock extension panel. Locks like the TL300Z and ML300 use fingerprint, RFID, and passcode options, ensuring secure, flexible entry.
3. Software Integration: ZKBio CVSecurity and ZSmart
The ZKBio CVSecurity platform unifies access control and lock management, offering real-time tracking, interlock logic, and anti-passback enforcement. It integrates with hotel modules for a “One-Card-Solution,” allowing a single RFID card to unlock rooms, elevators, and facilities. The ZSmart mobile app enhances this, enabling remote unlocking, log history checks, and temporary passcode sharing for locks like the SL01-T430H and TL800. Users can monitor entry, manage users, and trigger alarms (e.g., low battery, tampering) from anywhere.
4. Compatibility and Scalability
ZKTeco’s systems support third-party integration via Wiegand (W26/W34/W66) and OSDP (Ver 2.1.7) protocols, connecting to readers like QR50, QR500, and QR600. The Atlas series (e.g., Atlas160, Atlas260, Atlas460) offers pre-configured kits for 1, 2, or 4 doors, with built-in web applications—no software installation needed. This scalability suits small offices, multi-site enterprises, and temporary setups.
5. Specialized Features
Dynamic QR Codes: The C3 Plus series and ZKBio CVSecurity generate QR codes for visitor access, integrating with locks for temporary entry.
Touch and Remote Options: The TLEB301 touch exit button, with a 2.5D tempered glass panel and IK04 vandal resistance, pairs with locks for easy exit, while remote unlocking via ZSmart or Bluetooth/Zigbee enhances convenience.
Glass Door Compatibility: Accessories like LBB-1, LBB-2, and UBB-1 enable electric mortise locks (LB12, LB22, LB35) to secure glass doors, bridging access control and lock functionality.
Benefits of ZKTeco’s Integration
Enhanced Security
By combining biometrics, RFID, and encryption (AES 256-bit for storage, AES 128-bit for communication), ZKTeco ensures only authorized users gain entry. Features like anti-passback, duress password entry, and tamper alarms (e.g., SL01-T430H) fortify protection against unauthorized access or breaches.
Convenience and Flexibility
Remote unlocking via the ZSmart app, voice commands with Amazon Echo/Google Nest, and multi-method authentication (fingerprint, face, card, passcode) make access effortless. Users can manage locks and control systems from a smartphone or web interface, ideal for remote sites or rentals.
Scalability and Cost-Effectiveness
From standalone devices like the Horus E2 to networked panels like the Atlas460, ZKTeco scales to any need. In-house manufacturing keeps costs low, while robust designs (e.g., IP68-rated ProFace X(DS)) ensure long-term value.
Versatility Across Industries
ZKTeco’s integration shines in:
Corporate Offices: Atlas kits and ProMA terminals secure doors and track entry.
Hotels: The hotel module and locks like SL01-T430H offer one-card access and remote tenant management for Airbnb or hotels.
Residences: TL300Z and ML300 provide smart, secure home solutions.
Institutions: Multi-door controllers and biometric readers suit schools and government facilities.
Real-World Applications
Imagine a small business using the Atlas160 bundle—a single-door access control panel with a biometric reader and ML300 lock. Employees clock in via fingerprint, unlock the door via Bluetooth, and managers monitor entry remotely. In a hotel, the ZKBio CVSecurity hotel module integrates with TL800 locks, allowing guests to use RFID cards for rooms and elevators, while staff manage access via ZSmart. For a multi-site enterprise, the C3-400 Plus controls four doors, syncing with ProMA-QR terminals and electric mortise locks, ensuring secure, trackable access across locations.
Conclusion: ZKTeco’s Integrated Future
ZKTeco’s integration of access control and door locks redefines security by blending cutting-edge biometrics, smart locks, and intuitive software. Products like the InBioPC, ProMA series, and SL01-T430H, paired with ZKBio CVSecurity and ZSmart, deliver a seamless, secure, and scalable solution. Whether protecting a home, office, or hotel, ZKTeco offers unmatched precision, convenience, and adaptability. Ready to revolutionize your security? Explore ZKTeco’s offerings at website or contact [email protected] to discover the perfect integrated solution for you.
0 notes
Text
HIPAA Compliant Print and Mail Solutions for the Healthcare Industry

In the modern healthcare landscape, protecting patient data is as important as providing top-tier medical care. The Health Insurance Portability and Accountability Act (HIPAA) mandates strict standards for safeguarding Protected Health Information (PHI). This regulation extends to all communication—including print and mail. That’s why HIPAA compliant print and mail solutions are vital for healthcare providers, insurers, pharmacies, and medical billing companies.
This article explores how HIPAA-compliant print and mail solutions function, why they’re essential, the types of healthcare communications they support, and how to select the right provider.
1. What Does HIPAA Compliance Mean in Print and Mail?
HIPAA compliance ensures the confidentiality, integrity, and availability of PHI. For print and mail, this means:
Secure handling of patient data
Controlled access to printed documents
Encrypted data transmission
Chain-of-custody documentation
Staff training on PHI management
Any lapse in these areas can lead to serious breaches, costly fines, and reputational damage.
2. Why the Healthcare Industry Needs Secure Print and Mail Services
Healthcare organizations deal with a high volume of sensitive mail, including:
Test results
Appointment reminders
Insurance explanations of benefits (EOBs)
Medical billing statements
Patient welcome kits
Handling these communications in-house increases the risk of accidental disclosures and non-compliance. Outsourcing to a HIPAA-compliant mail service reduces that risk while increasing efficiency.
3. Types of HIPAA-Compliant Communications
HIPAA-compliant print and mail vendors handle:
Medical records and summaries
Claims documentation
Referral letters
Patient statements and invoices
Prescription information
Providers must use data-handling protocols that adhere to both HIPAA and HITECH regulations.
4. Key Security Features of a HIPAA-Compliant Print and Mail Solution
a. Physical Security
Restricted access to production facilities
Security badges and surveillance systems
Biometric authentication at entry points
b. Data Protection
AES-256 bit encryption in transit and at rest
Secure FTP or API-based file transfers
Real-time tracking of job status
c. Compliance Documentation
Signed Business Associate Agreements (BAA)
Audit trails for every mail piece
SOC 2 Type II and HITRUST certifications
5. Automation in HIPAA-Compliant Mail Services
Leading HIPAA-compliant platforms offer automation capabilities like:
Template-based document creation
API integrations with EHR/EMR systems
Automated printing and insertion
Real-time error alerts and status tracking
Automation reduces human error and ensures that communications are timely, consistent, and secure.
6. Benefits of Outsourcing HIPAA Mail Solutions
a. Cost Efficiency
Outsourcing eliminates the need for printing equipment, postage, staff, and maintenance.
b. Scalability
Vendors can handle large mail volumes and spikes during open enrollment or major outreach campaigns.
c. Compliance Assurance
Reputable vendors stay current on HIPAA updates and provide documented compliance.
7. Selecting the Right HIPAA-Compliant Vendor
When evaluating providers, consider:
Experience in healthcare printing and mailing
Technology stack (data encryption, automation, etc.)
References and compliance certifications
SLA guarantees and customer support
8. Real-World Use Case: A Hospital Network
A multi-state hospital system implemented a HIPAA-compliant mailing solution to automate discharge instructions and appointment follow-ups. The results:
32% reduction in mailing errors
50% faster delivery times
Improved patient satisfaction scores
9. The Future of HIPAA Print and Mail
With growing digitization, expect:
Deeper EMR/EHR integrations
Multi-channel (print + digital) delivery models
Enhanced tracking and analytics dashboards
Conclusion
A HIPAA-compliant print and mail solution is no longer optional—it’s a necessity. It streamlines communication, reduces compliance risks, and enhances patient trust. For healthcare organizations, outsourcing to a secure and specialized vendor ensures that patient data is protected while maintaining operational efficiency.
youtube
SITES WE SUPPORT
Automated HIPAA Mails – Wix
0 notes
Text
CS 5158/6058 Data Security and Privacy Project 2: Symmetric-Key Encryption
1 Project Description In this project, you will need to implement a symmetric-key encryption scheme using AES. More specifically, – For the key generation function, you program should be able to output a secret key sk of AES, and write this secret key to a file. By default, the length of your key should be 256 bits and the encryption mode is Cipher Block Chaining (CBC). – For the encryption…
0 notes