#Client-Side Encryption
Explore tagged Tumblr posts
Text
Cryptomator
Cryptomator is a free, open-source tool providing multi-platform, transparent client-side encryption for your cloud files. Compatible with nearly any cloud storage service, it integrates seamlessly into your workflow, allowing you to work with files as usual. It uses robust 256-bit AES encryption for security. Additionally, it is user-friendly and requires no separate accounts, key management,…
#AES 256-bit#Client-Side Encryption#Cloud Security#data protection#encryption#File Encryption#Multi-Platform Security#Open Source#Privacy#Secure Cloud Storage
0 notes
Text
10 Best Cloud Storage Solutions (June 2024)
New Post has been published on https://thedigitalinsider.com/10-best-cloud-storage-solutions-june-2024/
10 Best Cloud Storage Solutions (June 2024)
pCloud is a secure cloud storage platform that offers a range of features for storing, syncing, and sharing files. Founded in 2013, pCloud has grown to serve over 14 million users worldwide. The company is based in Switzerland, a country known for its strong privacy laws, and maintains servers in both the United States and Europe.
One of the standout features of pCloud is its focus on security and privacy. The platform uses 256-bit AES encryption for files at rest and TLS/SSL encryption for data in transit. pCloud also offers an optional feature called pCloud Crypto, which provides client-side, zero-knowledge encryption for an additional layer of security. With pCloud Crypto, files are encrypted on the user’s device before being uploaded to the cloud, ensuring that no one, not even pCloud employees, can access the data without the user’s encryption key.
pCloud provides a user-friendly interface for managing files and folders, with desktop apps available for Windows, Mac, and Linux, as well as mobile apps for iOS and Android. The platform offers a range of features designed to enhance productivity and collaboration, including file versioning, which allows users to access previous versions of their files, and file sharing with customizable download and upload links. pCloud also provides a unique feature called pCloud Drive, which enables users to access their cloud storage as a virtual drive on their computer, making it easy to manage files without taking up local storage space.
Secure cloud storage with 256-bit AES encryption and optional client-side encryption (pCloud Crypto)
File versioning and recovery, with up to 30 days of version history (or up to 360 days for extended file history)
pCloud Drive feature for accessing cloud storage as a virtual drive on your computer
Customizable file sharing with download and upload links, as well as password protection and expiration dates
Generous storage plans, including 10GB of free storage and paid plans ranging from 500GB to 2TB, with lifetime payment options available
Dropbox is a widely used cloud storage and file-sharing platform that has been simplifying digital file management since its launch in 2007. With over 700 million registered users, Dropbox has become a go-to solution for individuals, teams, and businesses looking to store, sync, and collaborate on files in the cloud.
One of the key strengths of Dropbox is its ease of use. The platform offers a simple, intuitive interface that makes it easy for users to upload, organize, and access their files from anywhere, on any device. Dropbox automatically syncs files across all connected devices, ensuring that users always have access to the most up-to-date versions of their files. The platform also offers a range of collaboration features, including the ability to share files and folders with others, leave comments, and work together in real time on Microsoft Office files with Dropbox Paper.
Dropbox places a strong emphasis on security, using 256-bit AES encryption for files at rest and SSL/TLS encryption for data in transit. The platform also offers two-factor authentication and remote device wipe to help users protect their accounts and data. Dropbox provides a range of storage plans to suit different needs, including a free plan with 2GB of storage and paid plans ranging from 2TB to unlimited storage for teams. The platform integrates with a wide range of third-party apps and services, including productivity tools, creative software, and security solutions, making it a versatile choice for many users.
Key features of Dropbox:
Easy file syncing and automatic updates across all connected devices
Collaboration tools, including file sharing, commenting, and real-time co-authoring with Dropbox Paper
Secure storage with 256-bit AES and SSL/TLS encryption, two-factor authentication, and remote device wipe
Integration with a wide range of third-party apps and services, including Microsoft Office and Adobe Creative Cloud
Version history and file recovery, with 30 days of version history (or 180 days for Dropbox Business users)
MEGA is a secure cloud storage platform founded in 2013 by Kim Dotcom, offering end-to-end encryption and a focus on user privacy. Based in New Zealand, MEGA provides free and paid storage plans, with features like secure file sharing, chat, and file versioning.
One of MEGA’s standout features is its zero-knowledge encryption. All files are encrypted client-side before being uploaded, meaning that MEGA does not have access to the encryption keys and cannot view the content of stored files. This ensures a high level of privacy and security for users. MEGA is also transparent about its security practices, publishing its source code and design processes for public review.
MEGA offers a generous free plan with 20GB of storage, as well as paid plans ranging from 400GB to 16TB. The platform has a user-friendly interface with cross-platform support, including desktop apps for Windows, macOS, and Linux, as well as mobile apps for iOS and Android. MEGA also provides browser extensions and a command-line interface for advanced users.
Key features of MEGA:
Zero-knowledge, end-to-end encryption ensuring user privacy and security
Generous free plan with 20GB of storage and paid plans up to 16TB
Secure file sharing with customizable permissions, link expiry dates, and password protection
Cross-platform support with desktop, mobile, and web-based access
File versioning and recovery features to protect against data loss and ransomware attacks
Microsoft OneDrive is a cloud storage and file-sharing platform that is integrated with Microsoft 365 (formerly Office 365) and Windows 10. Launched in 2007, OneDrive has become a popular choice for both personal and business users, offering seamless integration with Microsoft’s suite of productivity apps, including Word, Excel, and PowerPoint.
One of the key advantages of OneDrive is its deep integration with Microsoft products. Users can easily save, access, and share files directly from within Microsoft Office apps, making it a convenient choice for those already using Microsoft tools. OneDrive also offers automatic syncing across devices, ensuring that users always have access to the most up-to-date versions of their files. The platform provides a range of collaboration features, such as real-time co-authoring, commenting, and file sharing with customizable permissions.
OneDrive offers a variety of storage plans, including a free plan with 5GB of storage and paid plans ranging from 100GB to 6TB. For business users, OneDrive is included with Microsoft 365 subscriptions, providing 1TB of storage per user and additional features like advanced security and compliance tools. OneDrive also offers robust security features, including encryption at rest and in transit, multi-factor authentication, and ransomware detection and recovery.
Key features of Microsoft OneDrive:
Seamless integration with Microsoft 365 apps, including Word, Excel, and PowerPoint
Automatic syncing and real-time collaboration features, such as co-authoring and commenting
Secure file sharing with customizable permissions and expiration dates
Robust security features, including encryption, multi-factor authentication, and ransomware protection
Personal Vault feature for an added layer of security for sensitive files
Box is a cloud content management and file-sharing platform designed for businesses of all sizes. Founded in 2005, Box has become a leading choice for organizations looking to securely store, manage, and collaborate on their files in the cloud. The platform offers a range of features and integrations that cater to the needs of modern businesses, including workflow automation, data governance, and enterprise-grade security.
One of the standout features Box is its focus on security and compliance. The platform provides a range of security controls, including encryption, data loss prevention (DLP), and access management, to help businesses protect their sensitive data. Box also complies with various industry regulations, such as HIPAA, FINRA, and GDPR, making it a suitable choice for organizations in regulated industries. Additionally, Box offers advanced collaboration features, such as real-time co-authoring, task management, and granular permissions, enabling teams to work together seamlessly and securely.
Box integrates with over 1,500 third-party apps, including popular productivity tools like Microsoft Office 365 and Google Workspace, as well as enterprise software like Salesforce and DocuSign. This extensive integration ecosystem allows businesses to streamline their workflows and improve productivity. Box also provides a range of AI and machine learning capabilities, such as intelligent content classification and automated workflows, to help organizations manage and extract value from their content.
Key features of Box:
Enterprise-grade security and compliance, with features like encryption, DLP, and access controls
Advanced collaboration tools, including real-time co-authoring, task management, and granular permissions
Extensive integration with over 1,500 third-party apps, including Microsoft Office 365, Google Workspace, and Salesforce
AI and machine learning capabilities for intelligent content management and workflow automation
Secure file sharing and content management, with features like custom branding, expiration dates, and password protection
Icedrive is a next-generation cloud storage platform that aims to make cloud storage feel like a physical hard drive. Launched in 2019, Icedrive offers a sleek, modern interface and a unique approach to file management with its revolutionary drive-mounting software. The platform focuses on providing a secure, easy-to-use, and affordable cloud storage solution for individuals and businesses.
One of the standout features of Icedrive is its emphasis on security. The platform uses the Twofish encryption algorithm, which is considered one of the most secure encryption methods available. Icedrive also offers client-side encryption for paid subscribers, ensuring that data is encrypted on the user’s device before being transferred to the cloud. Additionally, Icedrive follows a zero-knowledge approach, meaning that only the user can view and decrypt their data.
Icedrive offers a range of apps for various platforms, including web, desktop (Windows, macOS, and Linux), and mobile (iOS and Android). The platform’s clean and intuitive interface makes it easy for users to access, manage, and update their cloud storage. Icedrive also provides a generous free plan with 10GB of storage, as well as affordable paid plans ranging from 150GB to 5TB.
Key features of Icedrive:
Twofish encryption algorithm and client-side encryption for enhanced security
Virtual drive feature that allows users to access cloud storage as a physical hard drive (currently Windows-only)
Clean, modern, and easy-to-use interface across web, desktop, and mobile apps
Generous free plan with 10GB of storage and affordable paid plans
Built-in document viewer and media player for productivity and streaming on-the-go
IDrive is a comprehensive cloud storage and backup solution designed for individuals and businesses. Founded in 1995, IDrive offers a unique combination of cloud backup, cloud storage, and file syncing capabilities, making it a versatile choice for users looking to protect and access their data from anywhere.
One of the standout features of IDrive is its support for unlimited devices. Users can back up data from multiple computers, smartphones, and tablets, as well as external hard drives and NAS devices, all under a single account. IDrive also offers a range of backup options, including scheduled backups, continuous data protection, and block-level incremental backups, ensuring that data is always up-to-date and protected against loss or damage.
In addition to its robust backup capabilities, IDrive provides cloud storage and file syncing features through its Cloud Drive. Files and folders stored in the Cloud Drive are synced in real-time across all linked devices, making it easy to access and collaborate on files from anywhere. IDrive also offers advanced security features, including 256-bit AES encryption, optional private key encryption, and two-factor authentication, ensuring that data remains secure both in transit and at rest.
Key features of IDrive:
Back up unlimited PCs, Macs, iPhones, iPads, and Android devices to a single account
Quickly back up or retrieve large amounts of data using a physical storage device, without using bandwidth
Protect against ransomware and accidental deletions with historical data views and up to 30 previous versions of files
Automatically back up modified parts of files in real-time
256-bit AES encryption, optional private key encryption, and two-factor authentication
The Importance of Cloud Storage
As data technology continues to evolve, cloud storage providers will undoubtedly adapt and innovate to meet the growing demands for security, privacy, and convenience. By understanding your specific needs and priorities, you can select the best cloud storage solution to protect your data, streamline your workflows, and collaborate seamlessly with others. Whether you prioritize encryption, ease of use, or integration with other tools, one of these providers is sure to meet your requirements and exceed your expectations.
#2024#access management#Accounts#adobe#ai#algorithm#android#approach#apps#authentication#automatic updates#automation#back up#backup#backup solution#backups#Best Of#Blog#box#Branding#browser#browser extensions#Business#client-side encryption#Cloud#cloud backup#cloud storage#code#collaborate#Collaboration
0 notes
Text
Things that are not in the news anymore… 👇
-Maui wildfires.
-East Palestine, Ohio
-Joe Biden classified documents as a Senator.
-Fauci working with China to create a bioweapon.
-Pete Buttigieg’s best friend in prison for child porn.
-Cocaine in the White House. (TWICE NOW)
-The BLM and Antifa riots during 2020 causing BILLIONS of dollars of damage. And yes I brought this up on Juneteenth.
-The data collected from the Chinese spy balloons.
-Ukraine intelligence documents released that showed they were suffering massive losses and the American taxpayer was being lied to.
-Nancy Pelosi’s “documentary” film crew on J6.
-Veterans being kicked out of shelters to make room for illegals.
-Pizzagate “debunker” jailed for possession of child pornography.
-Gay porn film in Senate hearing room.
-Veterans Affairs prioritizing healthcare of illegals over Veterans.
-THE SOUTHERN BORDER CRISIS.
-Afghanistan drawdown and 13 service members killed in an attack on Kabul International Airport, that they hid the severity of it.
-Obama droning an American citizen in the Middle East.
-George Bush’s false WMDs.
-3 service members killed in Jordan.
-Hunter Biden making over $1M for “paintings”.
-J6 political prisoners that are still in jail.
-85,000 missing children at the southern border.
-Epstein’s clients.
-Obama coordinating with John Brennan and 4 other countries (5 eyes) to spy on the 2016 Trump campaign.
-Mail-in ballots were the cause of the stolen 2020 election.
-Jeffrey Epstein mentioning that Bill Clinton liked his girls “really young”.
-The (NOW TWO) airline whistleblowers that mysteriously died.
-Benghazi (I won’t mention anything more about this because I care about my life.)
-Nancy Pelosi’s daughter stating that January 6th wasn’t an insurrection.
-The January 6th committee destroying encrypted evidence before the GOP took over the House.
-Nancy Pelosi admitting that J6 was “her responsibility”.
-House Speaker Mike Johnson claiming there wouldn’t be foreign aid without border security in the bill, which was a lie.
-The recent riots from illegal criminal aliens at the southern border and the border in general.
-Hunter Biden not complying with a Congressional subpoena and deemed untouchable. Democrat privilege.
-Vaccine side effects.
-“Lab leak” out of China.
-The Secret Service having to basically guide Joe Biden everywhere he goes.
-Who leaked (Sotomayor) the SCOTUS Alito decision.
-Federal instigators inside the Capitol including pipe bomb evidence against them.
-Obama’s chef “passing away”.
-HRC’s chef “passing away”.
-The Sheriff that happened to be in Las Vegas (during the mass shooting) AND the wildfires in Hawaii.
-P Diddy sex-trafficking allegations. Where’s Diddy?
-Gonzalo Lira (an American journalist) that was killed in Ukraine
-Congress approving warrantless spying violating American’s 4th amendment rights while they are exempt.
-Americans that were left in foreign countries (Haiti, Palestine, Afghanistan).
-The billions of dollars of weaponry left in Afghanistan and the Taliban receiving $40M a week in “humanitarian assistance”.
-Biolabs found in California.
-Joe Biden’s impeachment.
-The scum in the UNITED STATES HOUSE OF REPRESENTATIVES waving the Ukrainian flag.
-The over 300k ballot images that could not be found in Fulton County, Georgia; the same county Donald Trump on trial for “election interference”.
-Democrats defunding the police causing massive rises in crime.
-Kamala Harris’s record as DA in California.
-The Transifesto from the school shooting.
-Many U.S. Representatives and Congress receiving FTX funds.
-They’re already working hard to bury Donald Trump’s àssassination attempt but we won’t let them bury that story. July 13th is never going away.
The distractions are out of control.
Share to show that legacy media is dead and that WE are the media now. 🤔
#pay attention#educate yourselves#educate yourself#knowledge is power#reeducate yourself#reeducate yourselves#think about it#think for yourselves#think for yourself#do your homework#do some research#do your own research#ask yourself questions#question everything#news#we are the news#distraction#distractions#did you know
566 notes
·
View notes
Text
Chat Control in a nutshell (please reblog this, US people)










Find out more about Chat Control here TAKE ACTION HERE ! OR HERE Calling is much more efficient ! The latter link will redirect you to the official websites of your respective reps. Under the "read more", you will find what you need to say/write when contacting your reps. You will also find an alternate format of this comic,and I give explicit permission for people to translate it and spread it anywhere for awareness. Credit really not needed, I don't care about that rn Even if this is a EU proposal, I am urging Americans to also share this, since it goes hand in hand with KOSA. DON'T FORGET TO JOIN OUR DISCORD SERVER AGAINST CHAT CONTROL ! https://discord.com/invite/e7FYdYnMkS

(Latest update on Chat Control was the 12 september 2024) This is a little long, so feel free to shorten it as you wish : Subject line: "2022/0155(COD) Dear Sir/Madam, I am writing to express my grave concerns regarding the proposed introduction of "Chat Control" This measure poses a serious threat to the privacy and fundamental rights of all EU citizens and stands in stark contradiction to the core principles that the European Union seeks to uphold. The proposed Chat Control contravenes Articles 7 and 8 of the Charter of Fundamental Rights of the European Union, which guarantee the right to respect for private and family life and the protection of personal data. The indiscriminate surveillance of private messages without specific suspicion or cause directly violates these fundamental rights. The General Data Protection Regulation (GDPR) sets out stringent rules for the processing of personal data. The proposed indiscriminate surveillance and scanning of private messages before end-to-end encryption is fundamentally incompatible with the principles of data minimization and purpose limitation enshrined in the GDPR. Specifically, Articles 5 and 6 of the GDPR, which govern the lawfulness and principles of data processing, would be violated by the introduction of such measures. The implementation of Client-Side Scanning (CSS) on devices means that all messages and files are scanned on the user's device before being encrypted and sent. This effectively nullifies the protection offered by end-to-end encryption and opens the door to misuse and additional security vulnerabilities. Moreover, the technical capability to scan such content could be exploited by malicious actors to circumvent or manipulate surveillance mechanisms. Such far-reaching surveillance measures not only endanger privacy but also freedom of expression. The knowledge that their private messages are being scanned and monitored could significantly restrict individuals' willingness to freely express themselves. Additionally, trust in digital communication platforms would be severely undermined. I urge you to take a strong stance against this disproportionate and unlawful measure. The privacy and digital rights of EU citizens must be safeguarded. It is imperative that we protect our fundamental rights and ensure transparency in the decision-making processes of our leaders. For more detailed information on the proposal and its implications, please refer to the following resource: Link to Netzpolitik article. https://www.patrick-breyer.de/rat-soll-chatkontrolle-durchwinken-werde-jetzt-aktiv/ Thank you for your attention to this critical matter. Sincerely, [Name] Art. 10 GG , Art. 8 & 11 EU Charta , Art. 8 EMRK (Alternate comic here V)
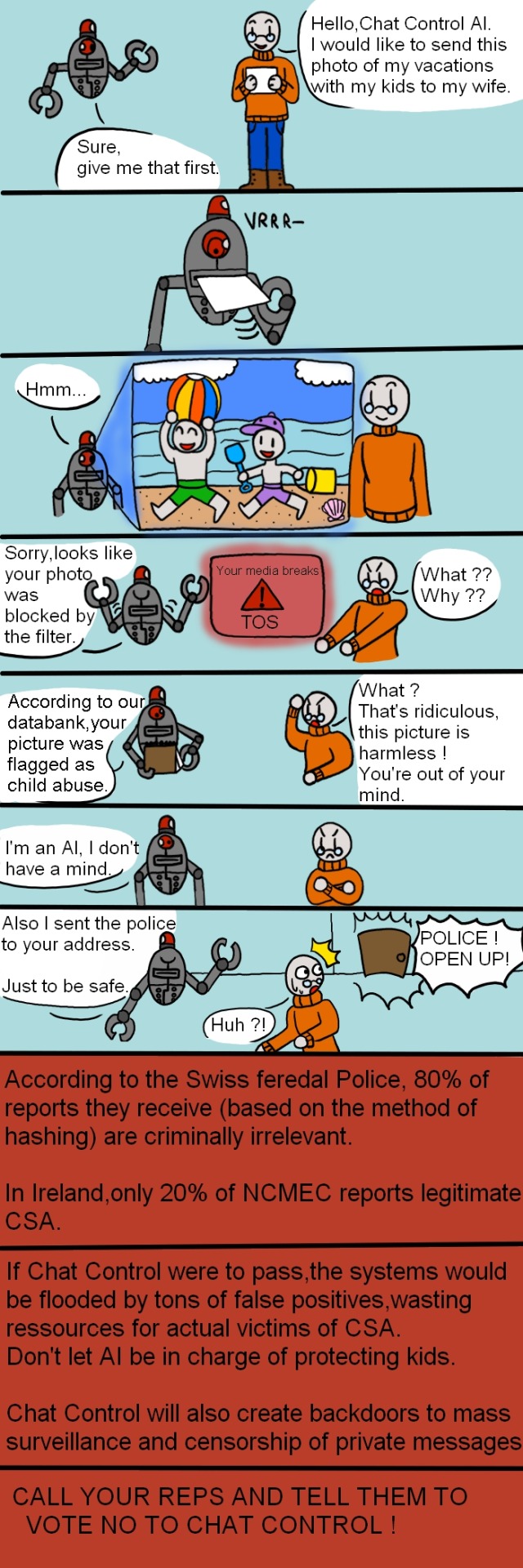
286 notes
·
View notes
Note
HII i'm loving your works omg! could i ask you to make a bronya!yuu or silverwolf!yuu? (you can choose just one if you want). take care or yourself and do your work at your time, no need to rush! :D
I decided to do two but sorry if bronya is so short , aww thank you.
𝐖𝐇𝐀𝐓 𝐈𝐅 𝐒𝐈𝐋𝐕𝐄𝐑 𝐖𝐎𝐋𝐅!𝐘𝐔𝐔 𝐖𝐀𝐒 𝐈𝐍 𝐓𝐖𝐒𝐓🐺👾


A member of the Stellaron Hunters and a genius hacker. She sees the universe as a massive immersive simulation game and has fun with it. She's mastered the skill known as "aether editing," which can be used to tamper with the data of reality.
Silver wolf!yuu is rarely known in nrc, they prefer to stay behind the scenes only a few students know about their existence.
Rarely appear in public, mostly using their holograms to go to school. It's pretty rare to see them actually outside of the ramshackle dorm.
Has a habit of disappearing and appearing, imagine your standing there and suddenly a hologram or game particles appear and silver wolf!yuu appear beside you.
Every time Crowley manages to piss them off, silver wolf!yuu would choose an area to vandalize at school, and some students manage to learn when you take a photo of it you can get a hidden message from silver wolf!yuu about Crowley.
silver wolf!yuu has a habit of collecting data about students, they have a database about their past, quirks, strength and weakness.
A very famous gamer in twst known to beat unbeatable levels of any game in twst and they use a fake alias. They hear about idia ranting towards Ortho about their game persona and find it funny. And join many game tournaments and win them easily and they gained money for this.
The ignihyde dorm is their second home, the dorm has good wifi for gaming. And manage to get close to idia and Ortho and talk about games with each other.
Their uniform has technology imbued to it. allowing them to access and project holographic screens on command. These are mainly used for quick data checks, sending encrypted messages, or pulling up maps and files in real-time without needing a handheld device.
They possessed a higher advanced technology than anything in twst. Also they use their aether hacking to change the ramshackle to their liking.
In battle, they would dominate due to having a lot hex on their side, they can hack into reality and get in the students file and remove the overblot. Or use it to discover and apply weakness towards the enemy.
They also have a mysterious job, operated as a freelancer, known for taking on jobs that require skill, secrecy, and the ability to circumvent the most complex security systems. Their reputation was built on their expertise in digital infiltration, information gathering, and high-stakes hacking, often working for those willing to pay for their skills without asking too many questions. most of their clients seem to be suspicious or not morally good.
Notorious for being a phone addict always playing their game outside or inside of class and when they were asked a question they immediately answered it correctly.
They also have a talent of engineering zoning out imagining about creating new tech ideas, mods and strategies for games.
𝐖𝐇𝐀𝐓 𝐈𝐅 𝐁𝐑𝐎𝐍𝐘𝐀!𝐘𝐔𝐔 𝐈𝐒 𝐈𝐍 𝐓𝐖𝐒𝐓 ❄️🌬️


Heir apparent to the Supreme Guardian of Belobog. She possesses pride befitting of a princess, but also the determination and integrity of a soldier.
Bronya!yuu is the embodiment of what a leader and an heir should be. Their charisma is able to encourage people and lead them towards the right path.
As well a dignified soldier bronya!yuu may look weak but are by far one of the most efficient in hand to hand combat, able to pin down a student who is bigger than them.
Has a tendency to reminisce about their mother and would just sit there and reminisce about them and grim would always be there to comfort them.
An expert marksman, rook and them once a week have a contest with each other who ever is the better marksman.
They are by far one of vil favorite, they are dignified, elegant and strong like a soldier and a princess should be, they also inspired epel to be more like them he admired them and have lessons with him where they tutor him.
They are patient and calm in the heeds of battle always believing as being one in harmony they could work together and forge a more successful path, as well being the back bone of a battle planning and helping them behind the scenes by shooting at the enemy
Them and Lilia would usually trade military tactics to each other over a cup of tea and also discussing other topics
They usually get burned out and they don't know when to rest, since they always have to keep a princess like dignity many of the first years notice and comfort them during hard times.
Bronya!yuu abilities allow them to enhance their comrade ability extremely towards its potential, as well to summon winter soldiers to help them but it takes a lot of energy.
Have a love and interest in history, usually seen in the library studying about twst long history and enjoy talking about them to their friends.
As well being a top student, always studying and getting good grades without any issue and always be respectful towards people
By far have a good reputation at school for being a capable leader, many students admire their discipline, while others have some sort of a sense of rivalry with them.
#twisted wonderland#not canon#twst scenario#disney twst#twst headcanons#twst wonderland#twisted wonderland yuu au#twst mc#twst yuu au#twst x reader#twst x hsr#twst yuu#bronya!yuu#silver wolf!yuu#hsr#hsr crossover#hsr headcanons#silver wolf#bronya#honkai star rail#hsr headcanon
172 notes
·
View notes
Text
Pinning Me Down
─────── · · A TDOTJ FanFic



Pairing: The Jackal x F!Reader
─ · · SUMMARY: You were a private investigator known as "Operator Grey" for working both sides of the table, police and the underground equally. You pull the strings to narratives to maintain work yet not everyone appears happy with your puppeteering work as an "admirer" of sorts has you watching your back while not knowing they already have it in sights.
─ · · TAGS: second person perspective used, female-pronouns used, enemies/rivals to lovers, fluff and angst, scenes of stalking, blood, violence, injury, guns, and obsessive behaviours, hurt/comfort, arguments, lying, HIGHLY SUGGESTIVE THEMES, kissing, the Jackal being a ultra charismatic mf, not beta read or edited.
─ · · MASTERLIST | TAGLIST REQUEST | WORDCOUNT: 2,668
─ · · A/N: thank you for all the Jackal asks! I know its been a little while, still hope you guys want to read a Jackal fic!
─────── · ·
─ · · As a personal investigator and private operator for high profile clients your job was simple on the surface level; gather information with no questions asks and leave undetected with the evidence or blackmail your client requested and stare at the generous pay check afterwards before putting it to use.
─ · · People paid for how 'simple,' swift, and effective your operations appeared- always providing the results the client wanted (sometimes even needed) and you did not shy away from going above and beyond, disguising yourself while providing encrypted information, hacking into government servers, following your targets across boarders and seas without a sweat, and occasionally offering your friday night for a round of drinks with your favourite clientele (though before anyone got too touchy you would politely excuse yourself).
─ · · But that was just what your job appeared on the surface; a simple woman with a love for luxury that gained her wealth by blending into crowds and documenting evidence for deep pockets... the thing is... you didn't care for any 'side.'
─ · · Light or dark, the legal or illegal, you operated in the grey space as the "Grey Operator," or simple "Grey." Infiltrating and networking on the surface and all throughout the underground networks on a global scale.
─ · · Anytime anyone would come close to putting you behind bars, all spy agencies and police around the world knew you, knew that you helped them as much as the people they were chasing like a puppeteer pulling all the strings and slipping just enough information for the endless cycle of cat and mouse between criminals and cops.
─ · · Yet it appeared not everyone was too pleased with being "bossed" around as it appeared recently that all the targets you got requested to look over were 'sadly' deceased upon your arrival, a simple rose planted in each of their mouths, a letter in their hands always addressed to you- "Miss. Grey." Tearing open the paper, a dozen rose petals fall from the paper and one to two lines appear underneath. Some have a snarky remark or simple observation about your habits, others a clue for where they buried the information you needed in order to finish your mission.
─ · · Your chuckle at how they remove the 'operator title' from your ails and the way in which they boldly assume you're not married; it charms you as it equally infuriates you that someone is watching you in the same way you do for everyone else, simply pulling you along their intended trail with every new contract you receive and every corpse you discover.
─ · · But your humour did not last for long as your reputation was starting to take a hit. It was all fun and games to start as you observed the stack of letters by your bedside and the singular withered rose you had in a vase within your kitchen... but you did not want to be pulled along any longer.
─ · · So you took a new job, the last one your 'admirer' you tagged them to be had requested you take in order to continue to follow their trail. The catch though? You held no plans on carrying through with this mission, instead you went to a lab, tracing back the rose to its origins alongside the ink, paper, and writing-style used, anxiously waiting back for the results for a potential slip up.
─ · · You tapped your foot anxiously against the tile, eyes flickering between your watch and the clock on the wall, debating which one was running faster (both were timed the same) but it did well to somewhat calm your nerves.
─ · · Feeling increasingly restless, you unpinned your hair, sighing and ringing your fingers across your sore roots while circling the room. You picked up various test tubes and dada sheets left by the last worker within the space, nodding your head along before a 'ding!' had you dashing back across the room and eyeing the screen.
... INK: BRITIAN
PAPER: SPAIN
FLOWER: PORTUGAL
PRINTING: NOT IN DATABASE, ENTER RESULT? ...
─ · · Your brows furrow as you press your face closer to the screen in hopes of discovering a newfound answer within the code only to come back empty handed. The person who had been sending you these... 'gifts' had to be rich in order to buy the various materials and travel to plant them and by the meticulous craft of every shot between the eyes, you had already narrowed them down to being a sniper-of-sorts but they still leaved hundreds of possible candidates if not thousands...
"I'll be honest, I was disappointed you didn't even try and go see my newest gift," a man voice sounds from behind you making you still, gripping the edge of the table. You begin to tilt your head over your shoulder yet their stern tone stops any further movement, "Stay where you are, Miss. Grey and tell me the little image you have imagined me to be before seeing the real thing."
You let out a quick breath through your nose and roll your eyes at the ego of the man behind you. Standing up straight and smoothing out your shirt, you try and squint at the computer screen to catch their reflection. "I won't strain your eyes, love, only your mind, now tell me."
You humourlessly chuckle, "You won't 'strain my eyes-hm?' So a man of murder, ego, and vanity, quite the impressive and if I may say horrifically 'attractive' man I'm building an image of," you strike while rolling your shoulder back.
You listen as the man shuffles footsteps that clack against the tiles, dress shoes, once distant now appear closer, a chair scrapes against the floor before they've taken a seat behind you, "I will only admit to one of those sins. I'm afraid the other are abhorrently wrong, Miss. Grey. Do try again but this time, use more of your brain."
Slamming your fist against the table you are vibrating with anger as the comment slips in through your ears and to the front of your mind, clouding any rationally you were holding onto after being quite literally stalked for the past few months and watching as all your long-standing clients ran from you without another word, all because of this man, you think to yourself, scrunching up your nose before taking a deep breath- squeezing your eyes shut.
"Middle-aged male, European- most likely British descent from the accent yet sounds too forced to Birmingham slang making me think you're actually from London," you tease hearing man grunt but before he can send his come-back you are already speaking, "you had military experience, a marksman or sniper... leaning towards the latter by how well you disguise yourself. I would know you if you worked over the table so you're an underground operative and to know my connections you must be working for someone well-established... and with deep pockets," you conclude, "cleared to turn?"
"You are cleared," they reply, tone appearing to disregard how impressed the man was by how well you could read into him by what little evidence he gave.
Turning around you see a middle-aged man, head tilted up to observe you in a similar way you do him, from the shoes up until your eyes meet and you squint, "contacts and your nose is peeling," you whisper, biting your lip and taking another step forwards, one hand trailing behind yourself with nonchalance while in reality you were feeling for the cold metal of your weapon.
Seeing your little slide of hand you watch as the man raises an eyebrow, "no need to get violent, Miss. Grey. You wouldn't want to be hurting a grade school teacher now would you?" Your eyes narrow at the fake badge that dangles from his chest pocket, a cheery-fake smile with animals stickers cluttered around it. "Well, 'Mr. Richards', I highly doubt that you even have a formal education let alone are teaching a group of forty children when you spend your Friday afternoons in a lab with random women."
"You think yourself to be random?"
"No. But I will be in a moment."
"Is that so? Then why do I have you pinned to a room so easily?"
"You? Pinning me?" you giggle, taking a few steps back and starting to back up your gear, throwing the rose by his feet, observing how it crumbles across the white tiles, little red petals all splattered about like blood. "I would like to see you try," you tease before sharply darting out of the room hearing as the dash after you yet you know these halls like the back of your hand, dashing around a corner and bursting through a window you know to be able to fall through at a safe height into a pile of trash.
Standing up with a hull, rolling your ankle while looking up, you cast 'Mr. Richards,' a wink before walking off with the rush-hour crowd of those getting of work and sink into the subway system without a trace.
─────── · ·
─ · · You would like to say that was your last time running into said man yet he always found another way to you no matter where you seemed to turn or who you worked with... it was as if they were tracking your every move as you made it, that would be impossible though.. I've swapped phones at every stop and gotten all new passports.
─ · · The man, you know know to be as "The Jackal" in one of his recent entries to you still helped you with your work (as in doing it for you and offering you the entire pay check with his added 'gifts' again). You didn't know weather of not to feel disturbed anymore or intrigued to learn more as the notes became longer, the killing of your clients less frequent as he apologized for taking away your work while explaining he had his own jobs to fulfill in the past, and you with every city to ventured to, you thought to see his features pop up in the most crowded of places that made your heart race.
─ · · The Jackal would occasionally greet you in-person (of course when you least expected it). Take the club for instance when he ordered you a drink at the bar before spinning you for a dance and leaving at the sound of the next song like a mere figment of your imagination. How about that one time he waved you goodbye at the airport before boarding a separate flight or that time he acted as waitstaff to an event you were infiltrating.
You remember that night vividly, feeing as his longer slender fingers grabbed the coat from off your shoulders, draping it across his forearm before quickly leading you inside and into a discrete corner to offer some... advice? Before commenting on how beautiful the shade of blue made your complexion look and leaving before you could process his words and went back to hyper-focussing on your mission.
─ · · You hate to admit to yourself now how smoothy that mission ended up going with his feedback and escape plans and how well you both seemingly worked together like a seamless... effortless transition every time your paths would cross again. Just like to puzzle pieces falling together.
─ · · That once irritation now infatuation by how quickly he could rile you up with just a few words and how equally quickly he could calm you and crazily enough, you found yourself relaxing to his presence. Even looking forwards to it and waiting, hoping for the random face in a crowd to be his... you felt pathetic by how fast your heart was running before your brain. Any initial concern going out the window when the moment he complimented your work so earnestly, eyes so wide and welling with truth that you couldn't hold yourself from falling and forgetting parts of yourself in the process as you spiralled and fell into his arms, felt his kiss to your forehead, heard his voice calling your name in the private of one of your homes or felt how his hand gripped your thigh as he drove you both across seaside roads to soak of the sun.
─────── · ·
─ · · You shake the feeling of an over looming stare you never seem to find off of you before turning into your motel room. You had found yet another successful job and were ready to reap the rewards with a five-star vacation away from all the stress you had been experiencing.
─ · · Knocking off your boots and flinging off your itchy wig you sigh, feeling overwhelmed by all the layers of clothes you wear before stepping into the bathroom but the door appears to be... locked?
You jiggle the handle, "just a minute, Miss. Grey," a voice sounds from the behind the wood that has your hand stilling on the metal handle before being flung forwards and into a warm chest as the door is ripped open sending you with it, "good to see you again too," the Jackal teases, lazily casting an arm around your waist as you huff and pull away, feeling his lingering touch against your skin haunting your bones as you walk backwards and sit upon the bed.
The Jackal smirks, crossing his arms and leaning against the hallway arch, staring at you, "It has been some time since we've last seen each other, I thought you'd be all over me by now" he teases, eyes crinkling at the way you scrunch your nose up just like the first day he met you- watching as you foot taps against the floor as you think of a retort.
"Me? All over you? I think you have these roles revered, Mr. Jackal-sir," you smile, hands drifting back on the covers as you lean backwards, drinking in his relaxed appearance.
The Jackal slowly stalks forwards, standing before you before crawling over top of you as you fall back against the mattress, smiling up brightly as he traces your jaw, "and to think," he leans in slowly, breath hot and heavy against your ear as you squirm beneath him, "you'd say I'd never pin you down." He bites your earlobe before leaving a trail of kisses down your neck, across your collarbone and back up to your lips where he settles with a groan as you wrap your legs around his waist, locking your ankles around his lower back and smiling into the feeling of his lips on yours.
You both pull away breathless as you reach up, fixing a few golden curls that bounce across his forehead- pulling them back and leaning forwards for another kiss, "Don't make me eat my words now or you'll be left with your hand for the night," you warn, starting to pull away.
The Jackal simply places more of his body weight on you, casting you a glare, "like you'd be able to form words if I had my way with you."
"Wanna bet?" you trail one finger from his lip, down his jaw and neck before feeling his chest and the rapid beat of his heart- watching as his eyes darken to your words, "what does the winner receive?"
"Well why don't we ask them at the end? I'm sure she'll come up with a fair answer," you giggle, starting to pull at the neck of his shirt in a silent ask for him to remove it.
The Jackal does not budge, simply staring deeply into your eyes before briefly flickering down to your parted lips, "She-hm? Well I don't think he has ever lost a bet."
"It would be a pleasure to be the first one to hold one over you then."
"We'll see about that."
─────── · ·
─ · · A/N: I would lose- wait who said that?? lol
─ · · JACKAL TAGLIST: @swiftietevitdrewjew @groovyponypatrollamp @alelo23 @apaperflowerreader @itz-stuts @moonlightmvrvel @nadixq
#fanfic#fanfiction#simp-ly#simp-ly-writes#x reader#ask#ask asnwered#fluff#angst#tdotj#the day of the jackal fanfiction#the day of the jackal fanfic#the day of the jackal (2024)#the day of the jackal#tdotj fanfic#tdotj fanficion#eddie redmayne fanfic#eddie x reader#eddie redmayne fanfiction#eddie redmayne x reader#jackal x reader#the jackal x reader#charles “the jackal” calthrop x reader#charles calthrop x reader#tdotj x reader#enemies to lovers#rivals to lovers
133 notes
·
View notes
Note
Hi Stellar!! Congratulations again on 1000 followers!! 💜 You deserve it so much! You are one of the reasons why I started writing TBB fan fiction in the first place, so thank you for being one of my first inspirations to start writing.🥰
Kissing as a distraction/“You are my equal in every way.”: Tech kissing fem!reader as a distraction during a mission in a really bad part of town on some Outer Rim planet. He quickly realizes that he doesn’t want to stop and reader feels the same since they’ve both been circling around each other and their feelings for months. Reader is possibly feeling a bit insecure over not feeling like she’s interesting/smart enough to hold Tech’s attention/affection. You can make this SFW or NSFW, however you see fit! 💜
Ilysm and I’m so so excited to read everything you come up with! 💜💜💜
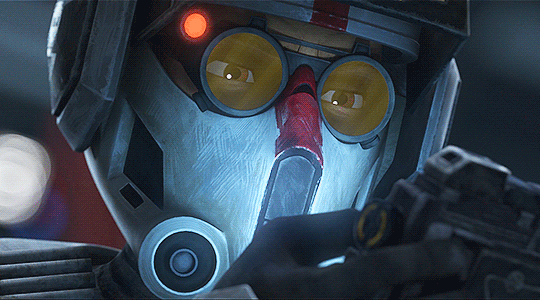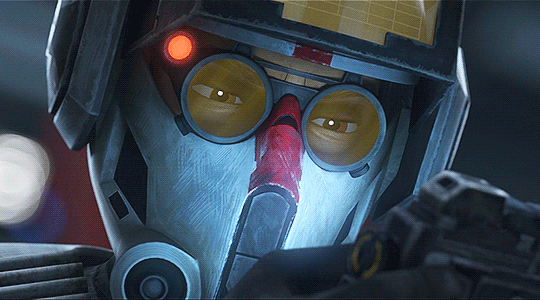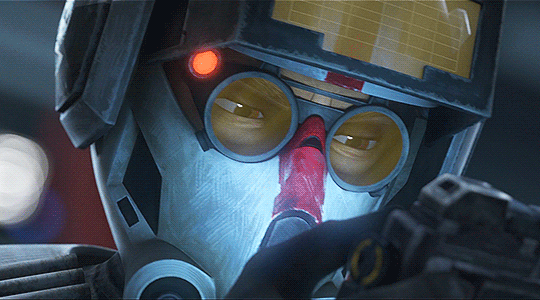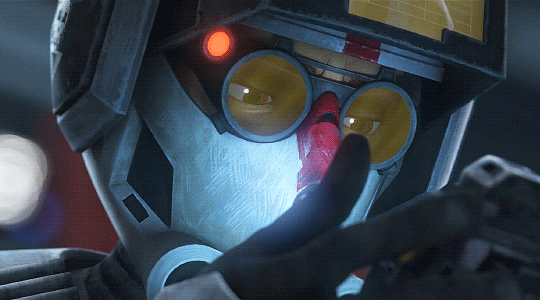
Avoid The Droid
Word Count: 1.5k Pairing: Tech x gn!reader Warnings: Kissing SFW Summary: While delivering intel to a client, you and Tech run into a patrol droid and it's coming you way.
“You’ll need to keep up if we are to get back to Cid’s by nightfall.” Tech nagged you over his shoulder.
Squeezing through two people you got within a hand’s reach of Tech. He led you through the slums of Ord Mantell City. The smell and crowd of the slums already had you on edge, Tech’s nagging only amplified that feeling.
Hunter, and by proxy Cid, sent the two of you to deliver intel to a client. Oddly enough, the intel at hand was a sound clip of a senator coughing. Apparently, there was an encrypted message within the recording, but one you’d failed to understand the meaning.
You ran your hand over the datarod tucked away in your jacket, making sure you’d not just squeezed past a pick pocketer.
“And there’s seriously some message? Not just a cough?” You called, probably too loudly for the scene, over to Tech.
“I assure you there is. I isolated the signature myself.”
“What was the message?”
Abruptly, Tech stopped to look back at you. His lips were pulled to one side, clearly not impressed by your repetitive questioning. “Would you rather discuss this further in a crowd of unsavory companies or complete the mission and get out of this degenerative sector?”
In attempts to appear impatient rather than embarrassed by the chiding, you waved for him on. Before turning back, Tech gave you a once over, eyes momentarily locking on your hand resting on your chest.
He took a quick inventory of the busy crowd around you as he urged you forward. Without warning he leaned in and pointed beyond you.
“The rendezvous is 100 meters down. Lead the way and I’ll see that you don’t lose the objective to a common thief.”
At times it was hard to tell whether he was being caring or condescending. You always leaned towards caring but were never surprised if it was the latter. As easy as it would be to take offense to most things Tech said, you were quick to realize Tech expressed himself rarely and to a select few of which included you.
He humored your questions about his gadgets and took interest in your area of study. Before resorting to doing jobs for Cid, you’d been a Senate Advisor as an expert in Galactic history and civics. As it turned out, the Empire had little use for such a speciality.
Once the governmental tides shifted you were faced with two options: stop spreading what the Empire deemed as propaganda or face unspecified ramifications. In the shadow of the Jedi Purge, you accepted the death of your career rather than the threat of literal one.
When you opened up about your past with the Batch, Tech’s interest was sparked and a cycle of info dumping began. It quickly became routine for you to perch next to him as he worked on the Marauder, prattling on about political intricacies from centuries past or your theories on current happenings. Similarly, Tech commonly regaled you with stories about past missions, space travel, or the detailed mechanics of his work.
Quietly, the two of you enjoyed your symbiosis. It was so nice yet you worried about its longevity. How long could an obsolete subject matter expert like you hold the attention of a man who was simultaneously a soldier, engineer, and living database?
Having fallen into that familiar anxiety, you were blind to the traffic around you. A speeder came up on your right side and nearly ran you over. It would have had Tech not pushed you forward and out of its way.
The technician kept his hand at your elbows, sternly guiding you through the crowd. He was silent, grip firm, until casually slipping you both into a narrow, grimy alley just off the street. He backed against the wall, pulling a datapad from his belt, fingers flying across the screen.
He’s annoyed.
"Why are we—"
"Don’t speak," he snapped quietly, eyes flicking upward. You followed his line of sight and caught a glimpse of a patrol drone hovering overhead, slowly sweeping the street. A quiet curse slipped under his breath when the screen flashed red.
“I am attempting to jam the drone’s biometric scanner—” he cut himself off with a sharp inhale. You didn’t fully understand what that meant, but the edge in his voice told you enough.
“Do something,” you hissed.
“I’m trying,” he bit back. “It’s scanning every exposed face and cross-referencing with archived Republic data. Possibly clone-associated personnel.”
“Are you on that list?”
“More than likely.”
Your stomach dropped. You stepped back to look.
“Don’t—” he hissed, reaching for you with one hand while the other kept working. “Just stay still—no, don’t talk—”
“I’m trying to understand what’s going on, Tech—”
“I said—”
You took another breath, ready to argue, but your voice, your movement, the crowd noise, the proximity—all of it was pressing down on him. His fingers stumbled on the datapad. His brain scrambled for solutions, prioritizing probabilities.
The drone beeped.
Too loud amongst the bustling crowd. Too close.
You turned toward it again.
And Tech snapped.
He shoved you back against the wall with one hand, braced the datapad with the other—and smashed his mouth against yours.
It wasn’t graceful. It wasn’t sweet. It was messy, rushed, and driven entirely by necessity and panic and you not shutting up.
Your gasp was swallowed instantly, lips crushed under his. His nose bumped yours awkwardly. His goggles pressed against your forehead. His free hand tangled in your jacket as he leaned into you like you were part of the wall.
And then—
Stillness.
The drone hovered a second longer. Then passed.
Tech didn’t move away, but some tension slipped away. You felt his breathing even out against your cheek, warm and fast. The pressure he pressed softened as he leaned away ever so slightly. It was just enough to look at you—eyes wide, lips parted, clearly realizing what he’d just done.
“I—” he started, then stopped, swallowed, and couldn’t speak before you closed the distance again.
You kept your eyes open to watch him a moment longer. His not moving was enough encouragement for you to move your lips against his. In turn, Tech softened and followed your motions.
The sound of the crowd faded away, the worry of discovery drowned by the thrill of weeks of built tension breaking away. The discomfort of his goggles against your face and your back into the wall behind you turned electric—exciting.
When oxygen became a necessity you finally split. Both of your lips were red, swollen, and dampened with the taste of the other. There was a long beat of silence and Tech gradually disentangled himself from you.
Tech stared at you a moment longer, then said in a hoarse rush, “I couldn’t focus. You wouldn’t stop talking.”
You blinked, a brow arching. “Is that all there was?” Leaning your head against the wall you cleared your throat, asking, “Even after the droid was gone.”
Tech’s eyes darted beyond the threshold of your dark nook. The droid was indeed long gone. Tech raised his datapad, examining it but thinking of anything other than the data presented. He adjusted his goggles and avoided your eye.
“It wasn’t unpleasant.” He mumbled. “For some reason I feel relieved.”
Your heart jumped. It was a coded and vague way of saying it but it sounded like, “Like finally figuring something out?” You asked, blatant hope in your voice.
Tech stiffened at the suggestion, eyebrows breaching his goggles. “I wouldn’t disagree.” His eyes met yours, fell to your lips, and found your eyes again. “Enjoying intimacy with you was not my epiphany, contrary to what you are implying. Our time together made that obvious to me a long time ago.” He tucked his datapad away as his air of confident casualness returned.
The crimping of your brows told him you weren’t following his own implication. Uncomfortable with his prolonged vulnerability, Tech brought his datapad back to his face, the glow of the screen doing little to hide the slight upward turn of his lips.
“Perhaps your reciprocation just now made me realize it but…” On an inhale Tech glanced up over his screen, keeping your gaze as he firmly said. “You are my equal in every way.”
He gave you no time to respond as he abruptly turned back into the crowded street. “We need to deliver this intel before we run into another patrol droid.” He didn’t spare another glance backwards, still rambling about the droid’s presence as if you were at his heels.
All the weeks of worry were suddenly gone. You gently touched your still tingling lips as you stepped back into the crowd. His equal… Proud warmth rooted itself in your chest. You ran to catch up with him, shamefully hoping another droid would come along…
tags: @bruh-myguy-what @cyaretra @jetii @hshfsjzjsgj @zahmaddog @heidnspeak
#I MISS MY MAN#i fiend for him#tech#x reader#the bad batch#bad batch#tech x reader#tbb tech x reader#the bad batch tech x reader#tech x you#tbb tech#fanfiction#star wars#tbb
49 notes
·
View notes
Text
Chapter 1: Ghost In the Machine

The hum of the fluorescent lights in "Byte Me" IT Solutions was a monotonous drone against the backdrop of Gotham's usual cacophony. Rain lashed against the grimy window, each drop a tiny percussionist drumming out a rhythm of misery. Inside, however, misery was a bit more… organized.
I sighed, wrestling with a particularly stubborn strain of ransomware. "CryptoLocker v. 7.3," the diagnostic screen read. A digital venereal disease, if you asked me. Another day, another infected grandma's laptop filled with pictures of her grandkids and a crippling fear that hackers were going to steal her identity.
"Still at it?" My coworker, Mark, sidled over, clutching a lukewarm mug of something vaguely resembling coffee. Mark was a good guy, perpetually optimistic despite working in one of Gotham's less-than-glamorous neighborhoods. Bless his heart.
"You know it," I replied, jabbing at the keyboard. "Think I've finally managed to corner the bastard. Just gotta… there!" The screen flashed a success message. "One less victim of the digital plague."
Mark nodded, then his eyes drifted to the hulking metal beast in the corner, a Frankensteinian creation of salvaged parts and mismatched wiring. "How's the behemoth coming along?"
I followed his gaze. My pet project. My escape. "Slowly but surely. Got the cooling system optimized today. Almost ready to fire it up."
"Planning anything special with it?" Mark asked, his brow furrowed in curiosity. "You've been collecting scraps for months. It's gotta be more than just a souped-up gaming rig."
I shrugged, a deliberately vague gesture. "You could say I'm planning something… big. Something Byte Me isn't equipped to handle."
Mark chuckled. "Well, whatever it is, I'm sure you'll make it sing. You've got a knack for that sort of thing." He wandered off, whistling a jaunty tune that died a slow, agonizing death against the backdrop of the Gotham rain.
He had no idea just how much of a knack.
Mark bid me one final goodbye before pulling out an umbrella and disappearing into the night. No doubt he stops at Nero’s pizzeria before going home to his wife and kids. You watched through the shop window before he disappeared around the corner. Then, you locked the door and reached for the light switch. The fluorescent lights flickered a final, dying gasp before plunging the shop into darkness. I waited a beat, the city's distant sirens a mournful choir. Then, I flipped the hidden switch behind the breaker box, illuminating a small, secluded corner of the shop.
Rain hammered against the grimy windowpanes of my "office," a repurposed storage room tucked away in the forgotten bowels of the shop. The rhythmic drumming was almost hypnotic, a bleak lullaby for a city perpetually on the verge of collapse. I ignored it, fingers flying across the keyboard, the green glow of the monitor painting my face in an unsettling light. Outside, the city's distant sirens formed a mournful choir. Here, the air crackled with a different kind of energy.
"Almost there," I muttered, the words barely audible above the whirring of the ancient server rack humming in the corner. It was a Frankensteinian creation, cobbled together from spare parts and salvaged tech, but it packed enough processing power to crack even the most stubborn encryption algorithms. Laptops with custom OSes, encrypted hard drives, and a tangle of wires snaked across the desk. This was Ghostwire Solutions, my little side hustle. My… outlet.
Tonight's victim, or client – depending on how you looked at it – was a low-level goon. One was a two-bit thug named "Knuckles" Malone; the other, a twitchy character smelling of desperation, Frankie "Fingers" Falcone. Malone's burner phone, or Falcone's data chip containing an encrypted message, was now on the screen in front of me, a jumble of characters that would make most people's eyes glaze over. For me, it was a puzzle. A challenging, if morally questionable, puzzle.
My service, "Ghostwire Solutions," was discreet, to say the least. No flashy neon signs, no online presence, just word-of-mouth referrals whispered in dimly lit back alleys. I was a ghost, a digital shadow flitting through the city's underbelly, connecting people. That's how I liked to justify it anyway. I cracked my knuckles and went to work. My fingers danced across the keyboard, feeding the encrypted text into a series of custom-built algorithms, each designed to exploit a specific vulnerability. Hours melted away, marked only by the rhythmic tapping of keys and the soft hum of the custom-built rig in the corner, its processing power gnawing away at the digital lock.
The encryption finally buckled. A cascade of decrypted data flooded the screen. I scanned through it, a jumbled mess of texts, voicemails, location data, or a simple message detailing a meeting point and time. Mostly dull stuff about late payments and turf wars, the mundane reality of Gotham's criminal element. I extracted the relevant information.
"Alright, Frankie," I muttered to myself, copying the decrypted message onto a clean file. "Just connecting people. That's all I'm doing."
I packaged the data into a neat little file, added a hefty markup to my initial quote, and sent it off via an encrypted channel. Within minutes, the agreed-upon sum, a few hundred cold, hard dollars, landed in my untraceable digital wallet. I saved the file to a new data chip and packaged it up. Another job done. Another night closer to sanity's breaking point.
"Just connecting people," I repeated, the phrase tasting like ash in my mouth. The lie tasted even worse. I knew what I was doing. I was enabling crime. I was greasing the wheels of Gotham's underbelly. But bills had to be paid. It was a convenient lie, a way to sleep at night knowing I was profiting from the chaos. But tonight, it felt particularly hollow. And honestly, did it really matter? Gotham was already drowning in darkness. What was one more drop?
Gotham was a broken city, a machine grinding down its inhabitants. The system was rigged, the rich got richer, and the poor fought over scraps. I wasn't exactly helping to fix things. But I wasn't making it worse, right? I was just a cog in the machine, a necessary evil. I was good at what I did, damn good. I could see patterns where others saw chaos. I could exploit vulnerabilities, both in code and in the systems of power that held Gotham hostage. It was a skill, a talent, and in this city, unique talents were currency. I was efficient and discreet. But every decrypted message, every bypassed firewall, chipped away at something inside me. It hollowed me out, leaving me a ghost in my own life, a wire connecting the darkness.
I leaned back in my creaky chair, the rain still pounding against the window. The air was thick with the scent of ozone and melancholy. Another night, another decryption, another small victory against the futility of existence in Gotham. The flicker of conscience, that annoying little spark that refused to be extinguished, flared again. Was I really making a difference? Or was I just another parasite feeding off the city's decay?
I closed my eyes, trying to silence the questions. Tomorrow, there would be another encryption to crack, another connection to make. And I would be ready, Ghostwire ready to disappear into the digital ether, another ghost in the machine, until the next signal came. As I waited for the morning, for the return of the fluorescent lights and the mundane reality of "Byte Me" IT Solutions, I wondered if one day, the darkness I trafficked in would finally claim me completely. Because in Gotham, survival was a code all its own, and I was fluent in its language. And frankly, some days, that didn't seem like such a bad deal. For now, that was enough.
#gotham knights#gotham knights fanfic#gotham knights jason todd#gk jason todd#jason todd#jason todd x reader#jason todd x you#red hood#red hood x reader#hacker!reader#dc
40 notes
·
View notes
Text
The highly controversial indiscriminate child sexual abuse regulation (so-called chat control) could still be endorsed by EU governments after all, as France could give up its previous veto. This is reported by Euractiv and confirmed by internal documents. France considers the new “upload moderation” proposal in principle as a viable option. According to the latest draft regulation dated 28 May (Council document 9093/24), which is presented as “upload moderation”, users of apps and services with chat functions are to be asked whether they accept the indiscriminate and error-prone scanning and possibly reporting of their privately shared images, photos and videos. Previously unknown images and videos are also to be scrutinised using “artificial intelligence” technology. If a user refuses the scanning, they would be blocked from sending or receiving images, photos, videos and links (Article 10). End-to-end encrypted services such as Whatsapp or Signal would have to implement the automated searches “prior to transmission” of a message (so-called client-side scanning, Article 10a). The initially proposed scanning of text messages for indications of grooming, which is hardly being used to date, is to be scrapped, as is the scanning of voice communication, which has never been done before. Probably as a concession to France, the chats of employees of security authorities and the military are also to be exempted from chat control.
During the last discussion on 24 May, the Council Legal Service made it clear that indiscriminate chat control scanning of non-suspects is still envisioned and remains a violation of fundamental rights. Nevertheless, most EU governments are determined to go ahead. EU governments plan to continue their discussions on June 4th. “The Belgian proposal means that the essence of the EU Commission’s extreme and unprecedented initial chat control proposal would be implemented unchanged,” warns MEP and most prominent opponent of chat control Patrick Breyer (Pirate Party). “Using messenger services purely for texting is not an option in the 21st century. And removing excesses that aren’t being used in practice anyway is a sham. Millions of private chats and private photos of innocent citizens are to be searched using unreliable technology and then leaked without the affected chat users being even remotely connected to child sexual abuse – this would destroy our digital privacy of correspondence. Our nude photos and family photos would end up with strangers in whose hands they do not belong and with whom they are not safe. Despite lip service being paid to encryption, client-side scanning would undermine previously secure end-to-end encryption in order to turn our smartphones into spies – this would destroy secure encryption. [...]
144 notes
·
View notes
Text
Budget Walmart Medic
Ratchet x Reader
ch6
Short form
Prev (AO3)
Short Form (Tumblr)
• He's never seen a signal like this. It blared in flashing red as if it was a warning for something catastrophic to happen. Yet something oddly familiar. It felt like deja vu. He desperately attempted to decipher the frequency as he made his way back to the human.
• Honesty is the best policy right? You haven't lied since being an adult, locking your past away and turning a new leaf. But in this moment, you could almost excuse it. A pair of glaring yet -is that worry? Optics stare right at you. He cradled you in his hands yet spouting absolutely nothing but profanity. Ironic it wasn't even a day ago he was the one telling you that you swore that much.
• "uh" With a small sigh you start to speak. A half truth will have to do. "yeah. I touched it." But you actively leave out the fact you snorted it. You could see him opening his mouth to protest something, but quickly shut it not long after.
• The frequency ringing in his audials have start to fade. If that's any indication of anything, it means the worst has passed. Ratchet didn't know why it bothered him so much, most likely it was just because medics are always high strung and always on alert.
• You two argue again, back and forth with Ratchet reprimanding you about how dangerous that was, and you shooting back that he only met you because you're always getting into things. Eventually he kicks you out the cave as you're banned from energon in whole, and he needed to excavate the raw crystals.
• It was only when you had a chance for yourself that you thought about it. How tf are you guys gonna process it?? Your place isn't small by any means, but even a house would be too small for him to even stick his head through the doors?? You're starting to really regret not shoving him into Raf's little hands and making it his problem.
• Ratchet emerges moments later while you're deep in thought wondering why they couldn't just contact each others or whatever the "harbinger" was. You were going to ask him about it until you realize he wasn't holding anything. "Where's the energon?" you ask him.
• On the way back, he explained that there's some sort of 'subspace' something like a blackhole that just disintegrates materialistic objects and can yank it back out in whole? You also learn some terminology of the cybertronian anatomy, things like hands are servos, feet are pedes, and a bunch of other things you've definitely have forgotten. But the one thing you did remember, was that they weren't able to contact the rest of the team as the Decepticons were keeping tabs on their communications.
• ? Wouldn't the right course of action is to just jam the communications? Ratchet scoffed at the idea. "You? Jamming alien Decepticon technology?" You argue with him that if they can't do anything server side, then at least try on the client side? If you can't smash their LAN room, (or whatever equivalent of it) then at least encrypt the messages they send? or hell, encrypt and distribute packets through other IPs, -or whatever their version of the internet is. A decentralized message.
• Ratchet is not onboard. One single one step and their cover could be totally blown. The cons can easily decrypt human encryption, after all, its extremely primitive. But you're determined. Where is this ego coming from? It's not ego, its sheer will and stubbornness to back down.
• You two pull up back into the garage. And with still no way of refining energon, Ratchet still has not been able to refuel. He tells you he'll just shut down and you're instantly thrown into a panic. That is until he explains it's just the equivalent of going to sleep, or recharge. So much for your unintended sympathetic nervous system running overtime. All this time you thought he was trying to die. Regardless, you hatch a plan. At this rate he will die if he doesn't get some sustenance into him. Without any other connections, your best bet was to contact Raf and that black and yellow muscle car.
• It wasn't until the human has left him alone and returned to her apartment that Ratchet realized what nagging frequency humming in his audials were. It was a life signal. Almost throwing him for a loop nearly smacking the celling half transformed. Not unlike that time Cliffjumper's life signal came back online from the dark energon. But oh so faint almost like the spark was holding on for dear life. "...How...? In a human? From merely touching energon?"
Next (AO3)
Tumblr

#transformers#ratchet x reader#transformers x reader#how tf is this written in both present and past tense#no i barely passed highschool english#ratchet#im about this close to sneaking into my brother's networking classes because i fell asleep in my own#that prof was an ass#i spent half the lectures figuring how to cheat on exams#i texted my brother at 1am to figure out the word decentralized#Rambles#budget walmart medic
30 notes
·
View notes
Note
Tbh when i think about yhe boys as jobs, i realize that none of them should be allowed anywhere near a courthouse unless they're the accused one.
Like just imagine
Laito would flirt with every breathing female organism within sight, kanato's cases would be disasters and land both of client as well as him in jail, shu would forget to attend to his cases, ayato would turn things into a competition to see who's a better judge/attorney/prosecutor, subaru would most likely start a physical fight, and reiji would treat his clients as test subjects, changing his approach to the case in every trial.
Are you seeing my vision??
oh god yes, the courthouse with the boys on the bench would be a full-on disasterpiece:
laito would be a walking violation of professional conduct rules. every ex parte communication turns into a flirt session—he’s batting his lashes at the judge, whispering “objection, your honor… but have you considered me?” he files frivolous motions for continuance just to spend more time charming the clerk, and completely waives his right to professionalism. every session ends in a mistrial because he literally can’t keep his hands—or his mouth—to himself
kanato’s version of “client counseling” would be an absolute horror show. he’s filing motions to suppress on the grounds that the “evidence isn’t pretty enough,” and tossing exhibits out the window mid-trial because teddy said they’re “scary.” his discovery responses consist of crying fits, incoherent rambling, and total noncompliance. judges are screaming “order in the court!” while kanato sobs into the record. his pro hac vice applications would be universally denied because he keeps shrieking “i’m not the accused!” in every proceeding
shu? forget it. he’d be the ultimate no-show. default judgments pile up because he forgets hearings exist. case management? nonexistent. he misses every deadline, never files briefs, and ghostwrites his own malpractice. clients show up asking, “where’s my lawyer?” and the court just shrugs: “¯\(ツ)/¯.” his bar license lives on the disciplinary edge, constantly one hearing away from disbarment.
ayato turns every hearing into a high-stakes competition. he treats pre-trial conferences like debate finals, objecting just to hear himself talk and throwing shade at opposing counsel with “your argument is invalid” sass. he appeals everything—even the coffee in chambers. he’d file rule 11 sanctions against himself just to one-up the other side in ethical superiority. every case turns into an episode of “courtroom deathmatch: litigation edition”
subaru? full-on rule 42 nightmare. fistfights during cross-examination. yelling “objection!” while physically throwing punches. judges hit the gavel; subaru hits harder. he racks up contempt citations like they’re achievements, and files motions to reopen every case he loses, demanding a “rematch.” security escorts him out on a near-daily basis, while the judge sighs, “not again…”
and reiji? the mad scientist of law. one second he’s citing marbury v. madison, the next he’s twisting stare decisis into alchemical riddles. his rule 56 motions read like 18th-century philosophical manifestos. voir dire becomes a psychological maze, and his jury instructions sound like encrypted spell books. he changes legal theories mid-trial like a chess grandmaster flipping the board. opposing counsel live in fear because reiji plays civil and criminal law like a 4d strategy game no one else understands
honestly, this courtroom would make law & order look like a kindergarten pageant. i’d pay real money to watch this legal circus unfold. the bar association would need a crisis hotline just to handle the paperwork
#diabolik lovers#sakamaki#ayato sakamaki#kanato sakamaki#reiji sakamaki#laito sakamaki#subaru sakamaki#shu sakamaki#can you tell i am becoming a lawyer? me neither#putting the us law class to use#since most people would be familiar with that :3
7 notes
·
View notes
Text
i am not really interested in game development but i am interested in modding (or more specifically cheat creation) as a specialized case of reverse-engineering and modifying software running on your machine
like okay for a lot of games the devs provide some sort of easy toolkit which lets even relatively nontechnical players write mods, and these are well-documented, and then games which don't have those often have a single-digit number of highly technical modders who figure out how to do injection and create some kind of api for the less technical modders to use, and that api is often pretty well documented, but the process of creating it absolutely isn't
it's even more interesting for cheat development because it's something hostile to the creators of the software, you are actively trying to break their shit and they are trying to stop you, and of course it's basically completely undocumented because cheat developers both don't want competitors and also don't want the game devs to patch their methods....
maybe some of why this is hard is because it's pretty different for different types of games. i think i'm starting to get a handle on how to do it for this one game - so i know there's a way to do packet sniffing on the game, where the game has a dedicated port and it sends tcp packets, and you can use the game's tick system and also a brute-force attack on its very rudimentary encryption to access the raw packets pretty easily.
through trial and error (i assume) people have figured out how to decode the packets and match them up to various ingame events, which is already used in a publicly available open source tool to do stuff like DPS calculation.
i think, without too much trouble, you could probably step this up and intercept/modify existing packets? like it looks like while damage is calculated on the server side, whether or not you hit an enemy is calculated on the client side and you could maybe modify it to always hit... idk.
apparently the free cheats out there (which i would not touch with a 100 foot pole, odds those have something in them that steals your login credentials is close to 100%) operate off a proxy server model, which i assume intercepts your packets, modifies them based on what cheats you tell it you have active, and then forwards them to the server.
but they also manage to give you an ingame GUI to create those cheats, which is clearly something i don't understand. the foss sniffer opens itself up in a new window instead of modifying the ingame GUI.
man i really want to like. shadow these guys and see their dev process for a day because i'm really curious. and also read their codebase. but alas
#coding#past the point of my life where i am interested in cheating in games#but if anything i am even more interested in figuring out how to exploit systems
48 notes
·
View notes
Text
Chat control email script (english)
Subject line: "2022/0155(COD)
Dear Sir/Madam,
I am writing to express my grave concerns regarding the proposed introduction of "Chat Control,", also known as CSAM regulation This measure poses a serious threat to the privacy and fundamental rights of all EU citizens and stands in stark contradiction to the core principles that the European Union seeks to uphold.
Violation of Fundamental Rights
The proposed Chat Control contravenes Articles 7 and 8 of the Charter of Fundamental Rights of the European Union, which guarantee the right to respect for private and family life and the protection of personal data. The indiscriminate surveillance of private messages without specific suspicion or cause directly violates these fundamental rights. Contradiction to the General Data Protection Regulation (GDPR) The General Data Protection Regulation (GDPR) sets out stringent rules for the processing of personal data. The proposed indiscriminate surveillance and scanning of private messages before end-to-end encryption is fundamentally incompatible with the principles of data minimization and purpose limitation enshrined in the GDPR. Specifically, Articles 5 and 6 of the GDPR, which govern the lawfulness and principles of data processing, would be violated by the introduction of such measures.
Technical and Ethical Concerns The implementation of Client-Side Scanning (CSS) on devices means that all messages and files are scanned on the user's device before being encrypted and sent. This effectively nullifies the protection offered by end-to-end encryption and opens the door to misuse and additional security vulnerabilities. Moreover, the technical capability to scan such content could be exploited by malicious actors to circumvent or by taking advantage of surveillance mechanisms Threat to Freedom of Expression and Trust in Digital Communication
Such far-reaching surveillance measures endanger not only privacy but also freedom of expression. The knowledge that their private messages are being scanned and monitored could significantly restrict individuals' willingness to freely express themselves. Additionally, trust in digital communication platforms would be severely undermined.
Call to Action
I urge you to take a strong stance against this disproportionate and unlawful measure. The privacy and digital rights of EU citizens must be safeguarded. It is imperative that we protect our fundamental rights and ensure transparency in the decision-making processes of our leaders.
Furthermore, given the current war happening in Ukraine, installing back doors in private communications would create more security vulnerabilities that Russia could exploit in order to launch cyber attacks within Europe and steal essential data. American officials have been recommending their citizens to use encrypted messaging following the multiple cyber attacks that targeted 8 telecom providers, including Verizon according to this article : https://www.nbcnews.com/tech/security/us-officials-urge-americans-use-encrypted-apps-cyberattack-rcna182694
For more detailed information on the Chat Control proposal and its implications, please refer to the following resource: https://edri.org/our-work/dutch-decision-puts-brakes-on-chat-control/
Thank you for your attention to this critical matter.
Sincerely,
[Name]
Art. 10 GG , Art. 8 & 11 EU Charta , Art. 8 EMRK ----------------------------------------------------------------------------
( This is the kind of arguments you can use when contacting your officials. I don't have a phone script ready yet,but you should familiarize yourself with your meps / prime ministers and tell them to keep opposing Chat Control,no matter what country you are in. It's best that you translate this script in your own language when contacting your officials and reword some parts so it doesnt sound repetitive if they are going to receive similar emails of that nature. )
Find your meps : https://www.europarl.europa.eu/meps/en/search/advanced?
If anyone knows a site where all the EU prime ministers are listed, let me know ! If you have no clue what im takling about,please check this post : https://www.tumblr.com/taikeero-lecoredier/769688553496215552/okayso-good-news-chat-control-still-didnt?source=share
14 notes
·
View notes
Text
Office Hours

Office Hours
In today's installment of "Stories Sam Isn't Writing," I bring you the opening meet cute of a non-MI6 get-together AU, in which private detective James Bond tries to recruit Imperial College professor "Q" Boothroyd to provide technical assistance on his cases.
Bond worked his way up through the Met and achieved the rank of DCI on the murder task force before his habit of following his instincts led him to step on some very important political toes. Bond’s superiors made it clear that the writing was on the wall for him. Rather than face demotion to the Traffic Division or, god forbid, Transport, Bond resigned from the police force and parlayed his investigatory skills into a successful new career as a private detective.
A couple years after his forced retirement, Bond lands his biggest case yet—tracking down the whereabouts of a wealthy recluse who may or may not have been removed from her home under duress. But he quickly hits a snag. The key evidence appears to be on the encrypted security recordings from the purported victim’s home surveillance system. He can’t decrypt it on his own, and it’s far too sensitive to take to a private vendor. Time to call in a favor. He rings up his former partner Bill Tanner to request a little off-the-books use of the Met’s crime lab. For the sake of his career, Tanner must reluctantly decline. But he does tip Bond to the new computer systems consultant the task force has been tapping for the past year, a professor at Imperial College.
Wonderful. Bond loves spending time with stuffy, pompous academics. But at least this one comes pre-vetted by the Met. And it’s the best Tanner can do for him.
Bond talks his way into the university’s buildings by introducing himself as DCI Bond, a bluff that works far too well on these trusting civilians. In the second building he accesses, he finds the door to Professor Boothroyd’s office in the middle of a long hall. The bench just outside the professor’s door is crammed with four students, each more visually appealing than the last. Bond smiles charmingly at them, but they pay him no attention. He tells himself he doesn’t feel slighted.
He raps loudly on the office door, and when it cracks open, the four students stand in unison, each calling for the professor’s attention in tones of voice that don’t sound desperate so much as eager.
Bond pushes inside, past the lanky, fluffy-haired student on the other side of the door. Unfortunately, the office appears empty, with no sign of the professor.
“Can I help you?” the student asks, closing the door behind Bond.
“No,” Bond says shortly, then amends, “yes, if you can tell me where the professor is.”
“I’m Professor Boothroyd.”
Bond is tempted to call him a liar, but his instincts don’t support the assumption. On second glance, the man does seem to have a few years on the young people lined up outside. Behind the hipster stubble and chunky glasses, there are definite smile lines around bright green eyes. Bond recalculates and changes tack smoothly. “Pleasure to meet you. I’m DCI Bond, and I’m here on official bus—”
“No you’re not.”
“I beg your pardon?”
“If you were with the Met, you would have showed me your badge already.”
Bond considers bluffing again…and then deflates with a sigh. “Tanner warned you about me?”
“No, rather the opposite, which is another tell—his people always text ahead. I’ve worked with enough law enforcement personnel to know their protocols, and you’re not following them. So who are you, how do you know Tanner, why are you impersonating a detective, and why are you looking for me?”
Since becoming a private detective, Bond has grown accustomed to back-stabbing clients, ulterior motives, and a cesspool of petty deceptions. In a campus full of trusting fools, the professor’s clear-eyed suspicion is something of a reassurance.
Coming off the back foot takes some doing, but Bond lays his cards on the table and survives Professor Boothroyd’s interrogation. After a moment of narrow-eyed deliberation, Boothroyd even agrees to examine Bond’s files…once Tanner vouches for Bond’s story—no offense intended. Bond smirks approvingly. By the time Bond secures his agreement, the professor seems to have warmed to him considerably, relaxing into an affable, vivacious demeanor and a smile that holds Bond’s attention more than usually happens without a low-cut blouse or skinny-legged trousers involved.
As Bond exits the small office, the hopeful gaggle of students rise again, each clamoring to get the professor’s attention first. And judging by the low-cut tops and skinny jeans on display, they’re angling for more than just tutoring help. Bond casts a glance back into the office, to the slim, magnetic figure of the popular young professor, and he thinks the students don’t have an entirely bad idea there.
Next time he visits campus, Bond will be sure to wear his best leather jacket.
And a tighter pair of jeans.
73 notes
·
View notes
Text
EU’s proposed Chat Control law has become a bone of contention between members of the bloc. First proposed by the European Commissioner for Home Affairs Ylva Johansson in May 2022 as part of bloc’s push to combat child sexual abuse online, the framework of the bill has now come under fire, earning itself a derisive term “Chat Control”.
France, Germany and Poland have particularly refused to accept a clause that allows for mass scanning of private messages by breaking end-to-end encryption. Some tech companies, along with trade associations, and privacy experts have all vehemently opposed the regulation.
On the other hand, Interior Ministers of Spain and Ireland have supported the proposal. Separately, a network of organisations and individuals, advocating for children’s rights in Europe, have lashed out at EU leaders for failing to tackle child sexual abuse online.
What are the concerns of those against the proposal?
Scanning end-to-end encrypted messages has remained a controversial issue. That’s because there is no way to do this without opening risky backdoors that can be accessed by third parties who can exploit the vulnerability, in turn ending the promise of end-to-end encryption.
Tech firms that treaded the encryption bypassing path have have often been made to retreat. In 2021, Apple announced NeuralHash, a feature that could automatically scan iCloud photo libraries of individual devices for child sexual abuse material, or CSAM. Employees and activist groups expressed concerns over the loss of privacy. A year later, Apple said it had abandoned the initiative.
Another looming issue the iPhone maker recognised in the process was how authoritarian governments could potentially misuse the feature by using it as a tool to target individuals who oppose the regime.
Erik Neuenschwander, Director of user privacy and child safety at Apple, admitted this in a note saying, “It would […] inject the potential for a slippery slope of unintended consequences. Scanning for one type of content, for instance, opens the door for bulk surveillance and could create a desire to search other encrypted messaging systems across content types.”
When brining in a similar clause through the UK’s Online Safety Bill, lawmakers attempted to make way for client-side scanning of private and encrypted messages. The proposal was postponed after receiving pushback from encrypted messaging app owners like WhatsApp and Signal. The duo threatened to leave the UK if such a law was passed. In its final stages, in September, 2023, the House of Lords considered the potential security threat that the clause would bring saying it would not implement scanning until it was “technically feasible.”
What is the status of EU’s Chat Control law?
On June 30, a new draft of the proposal is set to be be reviewed. Legislators have now left the idea of scanning text messages and audio, and are instead targetting shared photos, videos and URLs with an adjustment to appease the naysayers.
Another tweak in the making could be people’s consent in sharing material being scanned before being encrypted. But this compromise has been largely called out as a farcical one. A report by Euractiv which has been confirmed by internal documents show that if a user refuses the scanning, they will simply be blocked from sending or receiving images, videos and links hardly leaving them with a choice.
Despite these measures, EU’s enforcement of such regulations have seen exemptions to the rule. In November 2023, the European Commission reportedly published a proposal to amend the regulation on a temporary derogation of the E-Privacy Directive against CSAM. Under the regulation, specific online communications service providers were allowed to sift through or scan messages to detect, report and remove online child sexual abuse material or CSAM and content that solicits children. The regulation is set to expire in early August . The initial plan on the table was to simply extend this regulation for another three years. But, according to media reports, plans for further extensions were stalled in February this year.
Meredith Whittaker, President of Signal app called the measures to assuage concerns as “cosmetic”, and has signed a joint statement along with a group of over 60 other organisations like Mozilla, Proton, Surfshark and Tuta, voicing out her concerns. Whittaker has echoed her earlier warning saying Signal will leave the UK rather than undermine end-to-end encryption.
A blog, co-authored by Riana Pfefferkorn, a research scholar at the Stanford Internet Observatory and Callum Voge, director of government affairs and advocacy at the Internet Society, notes, ”If government surveillance is a concern in an established democratic entity like the EU, what hope is there for beleaguered democracies like Turkey, India and Brazil, much less autocracies?”
7 notes
·
View notes