#Password manager with face recognition
Explore tagged Tumblr posts
Text
Why choose RelyPass Premium?

RelyPass Premium offers a seamless and secure backup solution, ensuring all your passwords are safely stored in the cloud. Upgrade to the Premium plan today!
Download the App
#iOS password manager#Password manager app#Secure password manager#Best password manager#Password manager for iPhone#Top password manager#Password manager for iOS#Mobile password manager#Encrypted password manager#Multiplatform password manager#Biometric password manager#Password manager with face recognition#Cloud-based password manager#Free password manager for iOS#RelyPass#RelyPass App#RelyPass Password Manager#RelyPass iOS App#RelyPass iOS Password Manager
0 notes
Text
TASTE OF LIFE. l. heeseung

THE TALE GOES...heeseung is invisible to everyone, robbed of recognition as people pass through and never acknowledge him. to live as a shadow who observes is hard—heeseung sinks into corners and simply wishes for a chance to be a part of something. but when you finally come to the biggest halloween party of the year and see him, he can’t help but be attached.
pair -› lee heeseung x fem!reader | trope -› horror, literally no fluff | warn -› major character death, violence, stalking | REN SAYS.. first installment! also this is shit guys im so sorry I NEEDED TO GET THIS OUT ASAP ugh writing this much lowk killed me </3 | 3k words | library
---
Mediocre. Normal. Ordinary.
That’s exactly how you’d describe the house that stood before you, with your bags tightly held in both hands as you ascended the few stairs to the porch. It felt like any other house, and you’d even compare it to the old one you were in.
The previous home was different in one major way—it added years of aging onto your parents somehow, as if something had sucked the life out of their minds. It drove them crazy to stay home, and you couldn’t help but be embarrassed every time they mumbled in public about going home.
They looked crazy. You just had to droop your head and pretend you didn’t know them.
Your parents’ eyes lit up when they entered through the door, with wood flooring and a color scheme that reflected on their preferences. It was almost identical to your other house, so why exactly did they choose to move to a home that was no different than the last? If anything, you were just glad they were starting to feel more comfortable within the new space. It felt breathable, and something about the old place you lived in felt dirty and plagued.
It wasn’t much of a struggle as you began to unpack the bags of clothes and boxes of items you brought with you, considering how little you cared about accents and decorations. With furniture already there, your room felt akin to your other one, but something was off. You tried to move the desk over to the window to gauge the effectiveness of the natural lighting, and when your curtains gave way to slightly clouded rays of sunlight in your room, you hummed with some satisfaction. Good enough.
As Halloween came around, you understood how much everyone in the local town loved to celebrate. Houses on your way to school were filled with webs, lights, and jack-o-lanterns, and it made you believe that the pumpkin farm on the outskirts of town had a smart business model. On top of having an abundance of fall flavored desserts, the Yang family held the biggest party of the year, seeing as their son went to the same high school of yours.
You had only heard whispers of the annual Yang Halloween party, rumored to be the best party of all time, was something you were looking forward to every year, even anticipating the post-celebration news to hit you from the town over.
The day neared, and you got more and more excited to finally get to know people ever since you arrived in town. People knew of you as the new girl, but no one reached out, all too consumed in their own cliques to introduce themselves to you.
—
“Taste,” you told the man waiting outside. “The password is ‘taste.’ “
The windows were tinted in red as moonlight streamed through one side of the building. The rest of the house was dark, with only flashing orange, purple, and green lights strung carefully to add to the mysterious ambience. Music blasted from the speakers and shelves were lined with decorations, ones that you were careful to avoid knocking over as you slid your way between crowds. There seemed to be never ending snacks, as people with tattered black cloaks always managed to keep the drinks filled and the rows neat.
It was obvious that the family knew what they were doing when it came to throwing parties—you hadn’t seen one person without a smile on their face. The festivities like horror rooms and games were all through-out the floor, and there was always something for everyone to do.
You fell into conversation with a few people, cutting it short as you excused yourself to the restroom. Down the same hall was a door that was left ajar, and you went to shut it before returning to the boy who you just met.
“Hi.”
You jumped back, eyes darting around as you searched for someone to match the sudden voice, and you heard a small curse in the same direction. Your feet were frozen as you only looked around, your hand still on the knob of the empty restroom as you hoped someone would come to break you out of your stupor.
There was nothing, you promised yourself, and the door shut with a click. Still, your gut swirled with fear as you slowly turned, anxiously rubbing the goosebumps on your skin.
“You can hear me, huh?”
You knew the sound was coming to your left, where the flashing lights were nowhere to be found. All you had was the phone you fished out of your back pocket before you saw a flash of something pale. You immediately turned, trying to find it once more.
You could’ve sworn there was something.
“Hello?” You probably looked insane to any bystander, calling out to the dark when you swore you saw something nearby.
To both your surprise and horror, someone floats through the closet door, his limbs passing through as a grin makes his way onto his features.
You’d think the ghost in front of you was attractive, if it wasn’t for the fact that you were experiencing something supernatural for the first time.
Bile rose in your throat as you became disoriented looking at the figure. With a yelp that caught confused stares from only a few people nearby, you scurried out of the house, bumping into bodies as the door grew closer and closer.
Like a bubble about to burst, the house feels stuffy and humid until you open the large doors, swallowing the cold air of the night like a lifeline. Your head spins with confusion, and you can’t seem to understand what you just saw until he seeps through the wall once more.
“I’m sorry if I scared you.” You yelp at the sound of his voice, taking a few steps back as you look anywhere but his sullen face.
The sound of your heart won triumph over anything else as you kept trying to make space between you and the creature in front of you. When he begins to glide closer, you take it as your sign to grab your small clutch and begin a brisk walk back home, no matter how dark.
“My name is Heeseung. No one’s ever seen me,” he explains, easily drifting behind you.
“Get the fuck away from me, Heeseung.” Your voice sounded shaky as the wind rushes past your ears. You felt hopeless, unable to hear his footsteps or gauge where he could be.
He’s right next to you, speaking directly to your profile all of a sudden. “Please, no one’s recognized me since I died. Please, you have to help me.”
The change in proximity has you jumping from being frightened, and you try to cover your ears to block out his voice.
The worst part of it all was that Heeseung could touch you. You felt the cold of his fingertips without the pressure of his mortality in his fingertips. Effortlessly drifting next to you, he worked to pry your fingers from your ears as a plea for you to hear him out.
“I don’t care. Leave me alone.” You began speeding up, seeing your house in sight and the ghost beginning to fall back in his misery. You didn’t care about it, only wanting to go home and pretend everything was a bad dream. While the ghost wasn’t ugly by any means, the supernatural facet of his identity kept you up as you feared the creature outside your window at any moment.
What you didn’t know was that your gut feeling was right–Heeseung wouldn’t stop until he got what he wanted.
—
You didn’t know what was louder–Heeseung’s voice in your ear, or the thudding of your heartbeat.
Your scream echoed around the empty house when he appeared for the second time, your heart dropping as the lack of sleep you got from the night before made you even more on edge now. Everytime you looked down a corridor, shivers racked your body and you were unable to go anywhere without a flashlight. You swore you saw him in the corner of the room, and if not–something was horribly wrong with you.
There he was again, staying by the edge. “Please, get away from me, I can’t give you what you want, Heeseung.” You tried to keep your voice as steady as possible, as if you weren’t shaking from fear that you’d be joined by an intruder everytime you turned the corner.
You couldn’t shower or change without wanting to tear your hair out, and there was no way to quell the anxiety after you saw him stick an arm through your home.
There was nothing you could do. No one who you could go to about this. You were truly all alone.
Class felt like a blur with an ache in your head and an emptiness in your stomach. It was exhausting for you to dart around the room, waiting for him to appear.
He was waiting for something, you knew it.
You felt on edge constantly, like you were going insane. Every small movement triggered some sort of reaction, so much so that your classmates began to notice and snicker.
You felt like your parents–and you had no idea how to make it stop.
—
It was the third day of your sleepless torment. Your parents often left you alone according to their new work schedules, and you were still stuck having to hide from the apparition until you left for school. He looked torn apart, too, but you couldn’t understand why he couldn’t give you space. It got so bad to the point where you heard whispers of him in every corridor. You couldn’t stand it anymore, and your bloodshot eyes and scratched arms were a sign that something had been wrong ever since Halloween.
There was only one person you could tell about this, and you didn’t even notice how bad your fingers had been when you went to pick at the dry skin once more.
“Jungwon,” you mumbled as you passed him. He turned around, immediately recognizing you as someone he didn’t know much about.
“Is everything okay?” He asked, concern knitting his eyebrows as you asked for him to talk with you outside.
Something was off that day. The clouds were gray, dipped with unease. The sky was bathed in dread, and Jungwon could tell something was wrong by the way you couldn’t find the sun no matter where you looked.
“What’s wrong, ____? You’ve been looking horrible ever since Halloween.” You flinched at the word, eyes stinging with tears as you were pushed back into thinking about that night. You never should’ve worn your black dress or added some cute cat ears. You never should’ve left the house.
“There’s something in your house, Jungwon,” you pleaded, your gaze frantically searching for any sign that Heeseung followed you. “It’s like a spirit, something happened and it won’t—“ your words came to an abrupt halt when you heard a chuckle from the boy in front of you.
A laugh tore through as Jungwon crossed his arms and looked at you with a pitiful grin. “You’re funny. Good prank, though,” he smiles, about to turn.
You had no idea what came over you when you went to grab his arm. Jungwon was practically a stranger to you, but one more sleepless night without a cure would’ve made you go insane if he kept following you. You needed to get rid of Heeseung.
“No!” Your voice rang out louder than anticipated, and the sudden shout made you wince, still holding onto Jungwon’s arm. “You don’t get it, something’s following me around, he keeps talking to me and no one else can see him—“
The boy yanked himself out of your grip, suddenly frustrated, and you feared the worst; Yang Jungwon would tell the whole school that you were crazy.
“Please, Jungwon—” you tried once more, “he’s real—he’s everywhere and I can’t get rid of him—it was because of your party,” at this point, your eyes were filled with tears as you begged your only hope from leaving. “You have to help me—“
“I don’t have to do anything for you, ____.” He sneered, growing impatient. “I don’t know who put you up to this whole prank, but you need to stay away from me.” He spun around, paying you no attention as you crumbled to a heap on the ground and sobbed hopelessly on the pavement.
The sky was darker than ever, and it was still afternoon.
Even as you walked down the empty dirt roads to your house, you couldn’t help but hear Heeseung’s voice ring in your ears. As you started running to push the sound out and replace it with your heavy breathing, your eyes began to shut with exhaustion. Slowing to an eventual stop in front of your house, you heaved, gasping for air that felt like it was escaping your lungs any moment as you held into the porch railing
“You’re home. What took you so long?”
Your vision was blurring slightly in the corners, and the corners of your eyes felt puffy. You were slipping out of consciousness, but you remembered that voice anywhere. “Get away from me, please.”
Heeseung pursed his lips, feeling slightly bad for the state that you were in. “I told you, I can help you.”
When you saw his pale shoes in front of you, your body reacted instantly, scrambling back to create some distance. You hadn’t registered that a wooden splinter from the floor cut into your palm until Heeseung saw the blood seep into the planks underneath you. The porch made no sound under his quick footsteps, and it only instilled more frustration at his lack of perceptibility. His sudden approach left you frightened as you waved a hand in the air, unable to feel the wound from the state of your body. “Go away, Heeseung!”
He frowned angrily. “Let me help.” He kneeled next to you and reached out for your wound before you yanked your hand back, stumbling as you got back up and tried to make your way to the entrance.
“Please, stop,” you cried, taking two steps towards the railing before your legs gave out. Heeseung tried to reach out for you again. But you pushed away his hand, the slap of the force making no sound. It was almost humorous how much your torture was one sided, but you had no more energy left to defend yourself.
Heeseung went to grab your wrist, worry etched in his features as your state deteriorated in front of him. You kicked his leg, hot tears staging your cheeks as you sobbed for him to leave you alone, but the more carelessly you moved, the more the large splinter dug into your hand. He begged for you to stop–to let him help you before anything bad happened, but you couldn’t understand through the sound of your own hysterics.
A mix of going days without sleeping, paired with your lack of appetite and delirium left you defenseless no matter how much you tried. You struggled against the ghost of Heeseung’s grip as he tried to stop you from hurting yourself even further. You felt bile in your throat when he was close, and you found the opportunity to yank your arm out of his grip. You underestimated the force, however, and your hand hit the wood behind you. Momentarily distracted, you focused on the blooming pain of the impact and the slowly trailing blood. It was out of body how you couldn’t process the sensation of your fingers tracing the messy wound, and you became a slave to your exhaustion as the boy came back.
You fought against him weakly, the blood from your wound becoming a larger problem the more you used your hands to do anything.
“You don’t get it!” He yelled, tears of his own forming from the anger of having to go against you.
Why couldn’t you just stop? Why did you keep pushing him away? You were selfish, trying to ignore him as if you didn’t understand his predicament. You were the only one who could’ve seen him, and he was the only one who saw you in return. “Even Jungwon doesn’t believe you,” he mumbled bitterly, seeing you slowly slip in and out. “You wouldn’t even help me, ____. It’s all your fault.” He talked as if you could hear him, the life in your eyes gone by the time he wiped his tears and finally looked at you, with your wrist going limp in his hold.
“I don’t get it.” He wept angrily, before getting up and leaving you there on the porch steps in a heap.
Heeseung turned to glance at you again, his semblance of a heart in pain from how things had to end up. “You seemed so nice–so promising. Jungwon swore we could've been friends.”
–
You didn’t know if it was possible to kill a ghost twice. After all, your death turned you into a floating apparition of yourself, as you watched your parents mourn their attempts to shield you from their own fate. Being a ghost wasn’t so horrible, but Heeseung was right; it was lonely.
When a voice calls your name apologetically from where you sit on your rooftop, your gaze settles on him with fury, and the moment you rush over to him and your fingers close around his wrist, you knew that you wouldn’t stop until you properly got rid of Lee Heeseung.
No matter how long it took.
--
i swear the rest of them will be better. and shorter.
zyvlxqht firstclassjaylee @riribelle @jaylajakey @minfolio @strxwbloody @r1kification @strayy-kidz @mimismenu @jwonistic @haechsworld @machambrx @ririsreverie @hollxe1 @wonnina @heeseungismymanz @cyjhhyj @eunimaybe
#k-labels#k-films#enhypen#enhypen x reader#heeseung x reader#jungwon x reader#jay x reader#jake x reader#sunghoon x reader#sunoo x reader#niki x reader#enhypen scenarios#enhypen fluff#enha imagines#enha x reader#enha fluff#enha#heeseung imagines#heeseung fluff#riki x reader#jake enhypen#enhypen headcannons#enhypen imagines#lee heeseung x reader#yang jungwon x reader#park jongseong x reader#jaeyun x reader#park sunghoon x reader#nishimura riki x reader
308 notes
·
View notes
Note
Hi 👋 Can I request headcanons for Optimus Prime from Transformers One with a Cybertronian [S/O] [female] [platonic] who is a mad scientist and has a secret laboratory outside the city?
SORRY SORRY SORRY SORRY REALLY. I WENT THROUGH SUCH AN INTENSE TEST WEEK THAT I DIDN'T KNOW WHAT TO DO😭
I hope you can forgive me by accepting this little story made with a lot of love and affection 🥺
1 part:

_ _ _ _ _ past
______present
Searching the love
Optimus prime x Reader
Since the new Prime took over, the trains are only used for some exploration research, luckily they haven't found my lab yet, and if I manage to save some of the items I took, they'll never find it.
I grabbed the side of the train with cautious steps "Hey! You!" Damn! I grab one of my tools and hurriedly open the door, that's it! The alarm rings and the doors are locked, it's a matter of time until all the guards are here so I quickly get to the train control center and program the route.
- laboratory here we come!
I pull the lever, he advances at an extraordinary speed, throwing me towards the carriage door, which luckily had closed. The turbulent journey was overshadowed by the nostalgia of returning to my little space, I probably won't be able to return to iacon so I hope I've picked up enough stuff, but when they see my finished invention they'll thank me!
The technology to explore new worlds, find other intelligent life, I spent all my time since the new government observing and analyzing the stars and creating a technology capable of taking us out of the atmosphere of the planet that I nicknamed the rocket.
Imagine having the power and technology of the Quintersons to create life.
I also discovered how to encapsulate Energon for long trips, it was the hardest part but I know it will all be worth it.
The train's movement slows down, I grab my things and open the doors, I can finally finish my rocket and-
"GET HER!"
What? Damn! Turning quickly to get on the train I feel my arm being pulled abruptly.
-No! Let me go!
As I turn around I find myself face to face with Optimus Prime himself. Oh Primus, I'm screwed.
_ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _ _
had received an alert about a bot heading to the surface and an urgent notice requesting my presence. The guards said they had found a hidden area with a sort of gate. I left Elite and Bee taking care of the chores until I returned.
I get on an old freight train and enter the coordinates, activate the engines and remember how turbulent this thing is, I arrive a little unsteady and see two guards waiting for me.
1g- Optimus sir thank you for fulfilling the request
Op- it's my duty, so what's the situation? Any holidays?
2g- No sir, come with us.
The guards take me to a plain that doesn't seem to have anything special, until i come face to face with an Invisible wall.
Ah!
1g- Sorry sir, we didn't know the exact location of the wall.
Op- it's okay, it was nothing
A few seconds after my blow a large iron door appears, wow! What technology is this?
2g- Sir, look! Another train is approaching!
_______________________________________
Op- tell me what your designation is, and what is that mean?
-Of course, sir. I'm (y/n) i was doing some experiments, come with me.
releasing my arm, Prime accompanies me to the laboratory. How did he find out? He's going to ruin everything! He can't see now. If only I- I already know!
Prime and the guards accompany me to the gate, it's a very simple recognition technology, I enter my digits and a basic password, in short home sweet home, it's a shame to have to interrupt my peace with this, we enter my laboratory.
Op- y/n That's amazing, I never thought a bot would be able to do something so great.
- thank you sir
No wonder bots are amazed at my lab.
- 2 full floors of pure special iron, found only on the surface, some impressive shelves of tools acquired from the abandoned Prime, laboratory which allowed me to incredibly expand my knowledge, an abundant stock of encapsulated Energon that took me years to gather. In the center of the laboratory a small project of my unfinished rocket. These materials have been gathered since Sentinel took over, that idiot had no idea of my existence.
Op- awesome y/n, what do you intend to do with this project of yours?
-------------‐--—-----------—------
I hope you enjoyed it, don't worry I won't take too long on part 2, this is just a sample of what's to come. ❤️
2 part. / 3 part: Ending
#transformers#optimus prime#transformers optimus#tf one optimus#transformers one#robot x reader#x reader#transformers x reader#optimus x reader#optimus prime x reader#optimus prime x you#transformers x y/n#transformers x you#optimus x y/n#optimus x you#reading#female reader#fem reader#male reader#my fanfiction#x you
51 notes
·
View notes
Text
Some tips on how to survive a fascist state
From your auntie who has been around this block before.
This was made for people living in the US, but most of this is generally useful.
Assess your level of risk. For example, if you are not a citizen, going to a protest is much higher risk than it is for a citizen. But also recognize that the landscape of who is and is not being targeted is rapidly changing, so keep that in mind.
Get an updated passport. Make this a priority. If you live in a state where they have them, also get an Enhanced ID (not a Real ID, specifically an Enhanced ID) so you have a second way to cross land or sea borders into Canada and Mexico. That way, if authorities take your passport, you have another way out of the country.
Assume that the law is not there to protect you. Many parts of the law that are meant to protect you no longer apply. It's good to know your rights, but also know that the administration is not going to respect them. Just because you aren't doing anything illegal does not mean they won't come after you.
Move your communications, especially political communications, to encrypted messaging services. Use Signal for texts, ProtonMail for email, and Cryptpad as a word processor.
Get a private web browser. DuckDuckGo is a good option. I've also heard good things about Norton's private browser.
If you post political content on social media, you have two options. Make your account private and spend an evening going through your followers to weed out the ones you don't trust. Or, make it anonymous. But if you are picking the latter, know that it is hard to anonymize an account where you previously shared your identity. It's easier to go private if it's linked to your real life self, including through mutuals.
Turn off face ID on your devices. Police can force you to open them with your biometrics, even without a warrant. Additionally, make sure you have strong passwords (that are different for every account!) and keep track of them using a secure password manager.
If you go to protests or otherwise engage in subversive activity, DO NOT POST ABOUT IT ONLINE. Doing so endangers yourself and potentially others. Especially do not post pictures of protests, even if you've blurred the faces, even if you think you scrubbed the metadata. Even better, don't take photos at protests.
If you're exiting and re-entering the US, get a burner phone. I'm serious. Get an iPhone secondhand if you can afford it, but a flip phone will work if you need it to. Don't assume that just deleting anything sensitive off your device will be enough. You may not find it all, and depending on how thoroughly they search your phone, they may be able to see things that were deleted.
Mask up, especially when you're at a protest. In general, it's a good idea to mask since covid and many other viruses are going around. But masking has the added benefit of reducing the amount of biometric information you are making visible. Additionally, facial recognition software relies heavily on eyebrows, so cover them using a beanie or similar item.
Get involved or strengthen your ties with some kind of community. You are going to need others to lean on, whether that's emotionally or politically, in times like these.
22 notes
·
View notes
Text
My Dad forced me to go and watch Madame Web with him at the cinema. I told him explicitly that it wouldn't be good, but going in with that mindset freed us from the urge to be negative about the film, we had a lot of fun with it and even found a lot of things that we like in spite of ourselves.
My highlights include:
In order to facilitate a character arc where the protagonist becomes compassionate, she starts off as being inexplicably, comically rude and/or awkward to everybody and seems to dislike helping and talking to people, despite being a paramedic.
In the process of rescuing three teenage girls, the hero directly causes the deaths of a minimum of five offscreen innocents. She steals an ambulance and prevents it from helping somebody in need, causes a nearby car to explode in the process of ramming the ambulance into a villain, uses her EMT connections to summon a helicopter, fires off a load of fireworks at random to try and kill the villain, one of which hits the helicopter she summoned and explodes. Also one of the fireworks hits her in the face and blinds her.
Her superpower is actually quite interesting. Instead of having the same powers as the villain like every MCU film, there is a massive disparity in the combat abilities of the hero and villain, she can see the future but has no combat skills and he has the powers of Spider-Man. The final confrontation manages to stick in my memory a bit more simply because it's not just a generic fist fight on a rooftop but a culmination of Cassie's ability to factor in random elements.
The fact that Cassie's way of combating the villain involves using her future knowledge to cause random objects to collide with him makes the film very funny if you imagine it from his perspective, where he keeps getting hit by cars and debris and fireworks no matter where he goes.
The film is a weird period piece that takes place in the early 2000s, this is communicated by the use of Toxic by Britney Spears as the motif of a certain scene, where Cassie uses the presence of the song on the radio in a vision to pinpoint the precise moment it happens. The film alternates between subtle exposition like this that defines limitations and establish stakes without being intrusive, and the other times Cassie just talks out loud to her TV or a nearby stray cat in order for the viewer to learn things.
She figures out that she can see the future whilst watching A Christmas Carol in the middle of summer, when Scrooge is talking to Christmas-Yet-To-Come and asking if the future can be changed. As mentioned, she talks out loud to the fictional character Scrooge for the purposes of getting this exposition across.
Cassie becomes a wanted fugitive after appearing to kidnap the Spider-Trio, she parks her stolen taxi at the airport and buys a plane ticket out of the country and somehow manages to not get flagged down. When she returns from abroad, her stolen taxi with the ripped of licence plate is still there waiting for her.
The villain's plan involves killing the Spider-Trio, who will one day kill him in the future. The way he comes to locate the girls is by using advanced NSA technology to download an image from his dreams, making a random guess when in the future it takes place, de-aging the dream images by ten years, removing their masks from the de-aged dream images by using software to reconstruct their faces, and then running it past facial recognition. He sleeps with an NSA agent and steals her password, and then is somehow able to continue using these login credentials for a full week without getting investigated.
10 notes
·
View notes
Text
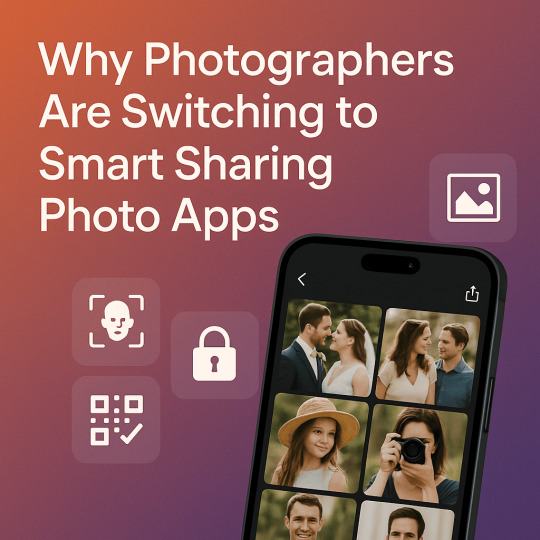
Why Photographers Are Switching to Smart Sharing Photo Apps
Efficiency, security, and client satisfaction are more crucial than ever. Gone are the days when photographers would spend hours organizing, tagging, and manually sharing images. The new trend? Smart sharing photo apps that use advanced technology to simplify and automate the entire image sharing process.
1. Speed and Automation Save Time
Traditional photo sharing methods—emails, cloud drives, or social media uploads—can be slow and tedious. Smart sharing photo apps automate the process using features like:
Auto-tagging with face recognition
Batch uploading tools
Group-based sharing based on events or client names
These tools drastically cut down turnaround time. Photographers can now upload hundreds of event photos and automatically deliver them to the right people within minutes. This not only improves client satisfaction but also helps photographers focus more on their creative work.
2. AI-Powered Face Recognition for Instant Delivery
One of the most compelling features of smart sharing photo apps is face recognition technology. These apps can scan images, identify individuals, and automatically send photos to the right recipients.
Imagine covering a 300-person wedding and having the app instantly deliver every guest their pictures—without lifting a finger post-event. That’s the power of AI.
Apps like Kwikpic offer this functionality, making them particularly popular among wedding and event photographers who handle large volumes of photos and tight deadlines.
3. Enhanced Privacy and Permissions Control
Smart sharing photo apps offer granular control over who sees what. Unlike social media platforms or public galleries, these apps allow photographers and clients to:
Set password-protected albums
Manage individual viewing permissions
Share links with expiration dates
Enable or disable downloads
This added layer of control makes these apps ideal for private events like weddings, family functions, and corporate shoots where discretion is essential.
4. Better Branding Opportunities
For photographers looking to grow their business, branding is key. Many smart sharing photo apps provide options to:
Add custom watermarks
Embed photographer logos
Customize the gallery theme to match your brand identity
Link viewers to your website or social media
These built-in marketing tools help convert photo viewers into potential clients, making photo sharing not just a delivery step, but a brand-building opportunity.
5. Client Satisfaction = Referrals
Smart photo sharing isn’t just about making life easier for photographers—it enhances the client experience too.
Clients no longer have to chase photographers for weeks to get their photos. They receive personalized galleries almost instantly, organized and ready to download or share. This fast, seamless service often results in positive reviews and word-of-mouth referrals.
For event photographers, this kind of service can mean the difference between a one-time client and long-term business growth.
6. Cloud Storage with Organization Features
Most smart sharing apps come with integrated cloud storage, allowing photographers to:
Access files anytime, anywhere
Organize galleries by client, date, or event
Back up photos securely
Avoid clutter on their devices
The combination of smart sharing and storage makes these apps a complete solution for managing digital photography workflows.
7. Event Grouping and QR Sharing
Smart sharing photo apps also shine at live events, where they allow guests to:
Join event groups via QR codes
Upload or download photos in real-time
Stay engaged through instant access to event memories
Photographers can simply display a QR code at the venue, allowing guests to join the event gallery and receive their photos automatically. It’s an innovative, interactive experience that adds value to any shoot.
Conclusion: Smart Photo Sharing Is the Future
With features like AI-powered tagging, privacy controls, branding tools, and real-time delivery, it’s no surprise that photographers are switching to smart sharing photo apps. These platforms aren’t just about sharing images—they’re about transforming the entire photography experience, both for professionals and their clients.
If you’re a photographer still relying on traditional sharing methods, it might be time to explore smart platforms like Kwikpic, which combine innovation, simplicity, and performance in one seamless experience.
0 notes
Text
How to Secure Your IndusInd Bank Credit Card for Safe Transactions
Our smartphones have become gateways to convenience—and that includes banking. From checking balances to paying bills and making investments, everything is now possible at the tap of a button. But with convenience comes the need for heightened security, especially when it comes to secure credit card transactions.
If you’re an IndusInd Bank customer, you have access to one of the most advanced and user-friendly tools to manage your credit card securely: the IndusInd Mobile app for android. This app isn’t just about managing money—it’s designed with robust safety features that ensure every transaction you make is protected.
In this blog, we’ll walk you through practical security tips, the built-in benefits of using the IndusInd Bank app for credit card management, and how you can make every swipe, tap, or online payment safe.
Security Tips: Using the IndusInd Bank App to Safeguard Your Credit Card
1. Enable Instant Card Controls
The IndusInd Bank Mobile Banking app empowers users with real-time control over their credit card usage. You can enable or disable international usage, set daily transaction limits, or even temporarily lock the card if it’s misplaced—all in just a few taps.
Tip: Make it a habit to turn off card usage for channels you don’t frequently use (e.g., international transactions or contactless payments).
2. Set Up App Lock and Biometric Authentication
The app allows users to enable biometric login using Face ID or fingerprint recognition. Adding a PIN or biometric authentication ensures that only you can access your banking details—even if your phone is stolen.
Tip: Always enable two-factor authentication and avoid using easily guessable passwords or patterns.
3. Track Real-Time Alerts
Every time your IndusInd Bank credit card is used, you receive a real-time SMS and push notification alert via the app. This lets you monitor your card activity 24x7, helping you catch any unauthorized use instantly.
Tip: Regularly review your transaction history on the app. If you spot anything unusual, you can immediately block the card through the app and report it.
4. Manage Your Virtual Card Securely
The IndusInd Bank app also provides access to your virtual credit card, which can be used for online purchases. Virtual cards add an extra layer of protection by masking your actual credit card number.
Tip: Use your virtual card for online transactions and limit its usage via app settings for enhanced security.
5. Update Contact Information Regularly
Keeping your mobile number and email address updated ensures you never miss any transaction alerts or bank communications. The app makes it easy to update contact details directly.
Tip: Avoid sharing OTPs or card details, even if the request seems to come from someone claiming to be from the bank. IndusInd Bank never asks for such sensitive information.
Benefits of Secure Transactions via the IndusInd Bank Mobile App
Total Control in Your Hands
The app puts complete control of your credit card usage in your hands. Whether it’s enabling/disabling online transactions, blocking a lost card, or generating a new PIN instantly, you’re never dependent on branch visits or customer care calls.
Advanced Encryption and Data Protection
IndusInd Bank uses state-of-the-art encryption protocols and multiple layers of authentication to keep your data safe. Every transaction is processed through a secure server, minimizing the risk of cyber fraud.
Instant Blocking and Reissuance
Lost your credit card? No worries. Through the app, you can block the card instantly and request a new one with zero delay. This quick action can save you from potential fraud or misuse.
Seamless Integration Across Services
The app integrates your credit card management with your savings account, loans, investments, and fixed deposits. This unified view ensures you don’t miss any payment due dates or security updates.
Exclusive In-App Offers and Rewards Tracking
Beyond security, the app enhances your credit card experience with easy access to personalized offers, rewards balance tracking, and EMI conversion options—all securely available within the app interface.
To Sum Up
Managing and safeguarding your credit card doesn’t have to be stressful. With the IndusInd Bank Mobile Banking app, you get a powerful, secure, and intuitive platform that lets you control every aspect of your credit card usage—right from your smartphone.
By following best practices like enabling real-time alerts, activating biometric authentication, and using virtual cards for online transactions, you can enjoy peace of mind with every swipe. So, download the IndusInd Mobile app for iOS today and take control of your credit card security like never before.
0 notes
Text
Starbucks Leadership Strategy Sparks Revival | IMPAAKT
As Starbucks pushes to revive flagging sales, CEO Brian Niccol lays out a people-first playbook — with promises of cozier cafes, more local leadership, and a return to what made the brand iconic.
A Vegas-Sized Vision for a Coffee Comeback
At a high-energy leadership event in Las Vegas, Starbucks rallied more than 14,000 store managers behind a bold mission: take the company “back to Starbucks.” That phrase wasn’t just a slogan — it was the Wi-Fi password, a rallying cry in barista competitions, and the core theme of CEO Brian Niccol’s vision for revitalizing a brand that has lost some of its steam.
Niccol, who joined Starbucks in September, is on a mission to reverse slowing sales and reestablish the coffee giant’s place in both consumer habits and investor confidence. At the heart of that push is a culture reboot — one focused on listening to employees, reimagining café spaces, and promoting from within.

Cafés With Character: Reclaiming the “Third Place”
Once hailed as the go-to “third place” between home and work, Starbucks cafés have gradually lost that identity — thanks in part to app-driven ordering and pandemic-era layout changes. Notably, the company removed over 30,000 seats from its stores in recent years, a move that upset customers and employees alike.
That’s about to change. “We’re going to put those seats back in,” Niccol promised to a burst of applause, acknowledging frustrations from store managers — including his own local barista in Newport Beach, who had asked to keep her café’s seating intact.
A newly introduced roast — the “1971 Blend,” named after the company’s founding year — aims to evoke nostalgia and reconnect customers to the original Starbucks experience.
Empowering Leaders on the Ground
Beyond customer experience, Starbucks is aiming to reengage its own workforce. The company has faced mounting criticism over labor practices, scheduling inconsistencies, and burnout — all of which have fueled a widespread union movement across the U.S.
Niccol’s answer? Put power back in the hands of store managers.
The company is now piloting new drink concepts, like a protein-packed cold foam, in just five locations first — relying on barista feedback before national rollouts. Staffing models are shifting, too. Managers will soon have more say in how many baristas their stores need. And by next year, most North American stores will add a full-time assistant manager to reduce the burden on store leaders.
Chief Partner Officer Sara Kelly received a standing ovation when she addressed the workload issue directly: “It can feel like the weight of everything is on your shoulders,” she told the crowd, pledging structural support and recognition for their day-to-day challenges.
Building a Pipeline for Talent — From Within
Starbucks also plans to double down on internal promotions as it targets the opening of 10,000 new U.S. stores. Today, roughly 60% of store managers come from within the company. Starbucks is aiming to raise that to 90% for its next generation of retail leaders.
That means more district managers, regional directors, and VPs — and more pathways for current partners to move up the ranks.
It’s not just about morale; it’s also smart business. Empowered leaders, Starbucks believes, will drive better customer experiences and higher operational performance.
A New Chapter — With Schultz’s Blessing
While Niccol is steering a new course, he’s doing so with an eye on the company’s past — and a nod from its most influential figure.
Howard Schultz, the iconic former CEO and architect of Starbucks’ global rise, made a surprise appearance at the Vegas event. Though no longer actively involved, his presence — and his emotional endorsement of Niccol’s “back to Starbucks” plan — was a symbolic passing of the torch.
“When I first heard about it,” Schultz told the crowd, “I did a cartwheel in my living room.”
The Leadership Experience also paid tribute to former Chairwoman Mellody Hobson, who stepped down earlier this year after nearly two decades of leadership. She received back-to-back standing ovations, reflecting the respect and admiration store managers have for her contributions.
What’s Next for Starbucks
Under Niccol, Starbucks has already seen a modest stock rebound, up nearly 20% since April. But the road ahead is long — and competitive. Fixing app issues, restoring the café experience, easing internal tension, and fending off union headwinds will take more than inspirational speeches.
Still, the tone from Las Vegas was clear: Starbucks isn’t just tweaking a business plan. It’s reviving a culture.
“Be true to the coffee, be true to your partners,” Schultz told the crowd. “And I know we’re going to come out of here… like a tidal wave and surprise and delight the world — just as we did in 1987.”
For more insights like this, explore IMPAAKT — your top business magazine for purpose-driven leadership stories.
0 notes
Text
Say Goodbye to Attendance Hassles with Biometric Technology

Keeping track of who enters and exits work should not feel like a chore. However, for many companies, attendance tracking becomes a headache. Register could be messy, swipe cards are left behind, and occasionally someone clocks in for their friend. This is where biometric attendance software can take the pain points out of a hassle that has existed for decades.
Biometric attendance software takes away the need for cards or passwords, instead using some type of biometric measure, such as facial recognition or fingerprints. The employee only needs to scan their face or fingerprint when they arrive, and the biometric attendance software will record the precise time.No more buddy punching, no more confusion.
It is quick, accurate, efficient, and nearly impossible to cheat.
For HR teams, this saves them time. All the timesheets or attendance disputes now take zero time and effort to check. The system collects the data, creates reports – highlighting late starts or overtime if applicable, plus record the absence data. It’s like having extra hands which do not make mistakes.
For employees, it has value too. They can self-serve their own attendance anytime they like, instead of asking someone, taking their word for it, or waiting for someone else to check. This fosters unity and increases trust.
Managers also gain the benefit of real time updates. Whether in-person or remotely, managers can monitor, who’s on time, who’s not, and track team performance. This assists with planning, shift management, and detecting problems before they fester.
And what security! Because biometrics are an individual human characteristic, it cannot be lost like a card or forgotten like a password. Biometric clocking can only allow the correct people access. All of the data is protected and privacy laws followed with appropriate safeguards in place.
In the end, biometric attendance software is not simply a technology choice; it’s about creating a workplace that runs smoothly, equitably and efficiently. It is a time-saver, error-proofing solution, and helps to create an organization with a culture of trust and accountability. If you are exhausted chasing timesheets, or arbitrating attendance disputes, this could be the workplace upgrade you are looking for.
0 notes
Text
Digital Identity Solutions Market Poised for Growth Amid Rising Cybersecurity and Authentication Demands Worldwide
The Digital Identity Solutions Market is entering a phase of robust growth, driven by the twin forces of escalating cybersecurity threats and the surge in demand for strong authentication methods. As organizations across industries accelerate digital transformation, comprehensive and secure user verification systems have become indispensable. Below, we explore the dynamics shaping this landscape, the key technologies driving change, major industry trends, sector-specific adoption, regional variations, and future projections.
1. Market Context: Why Now?
a. Escalating Cyber Threats
In recent years, cyberattacks—ransomware, data breaches, phishing—have not only increased in frequency but also in sophistication. Large-scale breaches involving identity theft and credential compromise have underscored the urgent need for strong identity verification. Incidents such as the 2024 data breaches at major payment processors and healthcare carriers have illuminated just how vulnerable legacy authentication methods like passwords remain.
b. Remote Work and Digital Service Expansion
The shift to remote work models and virtual customer engagement has significantly broadened the digital “attack surface.” Employees logging in from home, often on personal devices, have forced enterprises to reevaluate authentication practices. Consumer-facing online transactions—banking, retail, healthcare—have similarly grown more complex, leading to a surge in demand for frictionless yet secure digital identity solutions.
c. Regulatory Pressure
Regulatory frameworks around the world—GDPR in Europe, CCPA in California, CDPA in Virginia, and PDPA in Singapore—continue to impose strict requirements on identity data security and privacy. Governments have also introduced identity mandates, such as eIDAS Verified Digital Credentials in the EU and India’s expanding Aadhaar-linked services, fostering trust and compliance needs in digital identity ecosystems.
2. Key Technologies Fueling Adoption
a. Biometric Authentication
Fingerprint, facial recognition, and voice biometrics are now mainstream. Mobile device manufacturers have built secure enclave hardware capable of storing biometric templates locally. Meanwhile, multi-factor authentication (MFA) often leverages biometrics as a convenient second factor. That said, biometric vulnerabilities and spoofing attempts remain ongoing challenges, requiring continuous innovation.
b. Artificial Intelligence and Machine Learning
AI/ML are playing dual roles—strengthening authentication and detecting fraud. Behavioral biometrics track patterns like typing dynamics or mouse movement to enable continuous verification. Predictive analytics model transaction patterns in real time, triggering additional checks for anomalous behavior. According to a 2024 market study, solutions with integrated AI modules deliver 30–40% higher fraud detection rates compared to static rule-based systems.
c. Blockchain and Decentralized Identifiers (DIDs)
Blockchain-based identity models enable users to own and manage credentials, sharing them only when needed. Decentralized Identifiers and verifiable credentials (as defined by the W3C) support portable and secure identity claims. Use cases like digital wallets for vaccines, academic credentials, or licenses are gaining traction in Europe, North America, and the Middle East.
3. Market Trends and Signals
Unified Identity Platforms: Organizations are consolidating legacy point solutions into unified identity platforms covering workforce, consumer, and partner identities under a single pane.
Zero Trust Security Adoption: The shift toward Zero Trust architectures—“never trust, always verify”—elevates the importance of forging dynamic identity solutions.
Passwordless Authentication: WebAuthn and FIDO2 protocols are being adopted rapidly by browsers, mobile, and enterprise apps. Microsoft and Google see millions of users shifting away from passwords each quarter.
Regulatory Certification: Identity providers are pursuing ISO 27001, SOC 2, and cybersecurity certifications to meet corporate compliance, prompting greater enterprise uptake.
4. Industry Verticals Leading Uptake
a. Banking and Financial Services
One of the earliest and most active adopters, this sector enforces KYC/KYB standards, risk profiling, and PSD2 compliance. Mobile apps now integrate face matches with liveness detection during onboarding; biometric logins are standard, and banking institutions invest heavily in identity fraud monitoring.
b. Healthcare
Telehealth platforms and digital patient portals demand secure patient identity proofing and privacy compliance.
c. Public Sector
National ID programs (such as India’s Aadhaar and Estonia’s e‑ID) have matured; a growing number of countries are exploring sovereign digital identity systems for passporting, voting, and public benefits.
d. E‑Commerce and Retail
To protect against account takeover (ATO) fraud, digital identity checks have expanded at login, transaction points, and delivery. Risk‑based scoring and biometric verification tools reduce false positives and cart abandonment.
5. Regional Dynamics
North America remains a dominant market, driven by nimble fintech adoption, regulatory scrutiny, and high perceived cybersecurity risk.
Europe, led by the EU’s eIDAS2 regulations, is a hub for cross‑border identity innovations—wallet pilots run in Spain, Germany, and Poland.
Asia‑Pacific sees rapid adoption: India’s digital ID ecosystem is scaling; Australia and Singapore are piloting digital wallet schemes; and China integrates mobile biometrics into daily life.
Middle East & Africa: UAE and Saudi Arabia are building smart city identity integrations; digital IDs are being used to connect education, healthcare, and traffic systems.
6. Competitive Landscape
Major players in the sector include Okta, Microsoft Azure AD, Ping Identity (now part of Thoma Bravo), SailPoint, ForgeRock, and CyberArk in workforce identity. Consumer and government identity are being contested among IDEMIA, Thales, OneSpan, and Innovatrics. Emerging disruptors focus on decentralized identity (e.g. uPort, Sovrin) and embedded authentication services (like Socure, Jumio, Onfido).
Key Competitive Differentiators:
Scalability & Reliability: Can the solution handle 10 million active users?
UX and Frictionless Flow: Does the system respect privacy, such as via selective disclosure?
Ecosystem Connectivity: How well does the provider integrate into existing IT and SaaS apps?
Compliance Coverage: Is it certified for GDPR, HIPAA, PCI‑DSS, etc.?
Adaptability: Can the system evolve to support decentralized models, 5G devices, and IoT?
7. Challenges and Restraints
Despite rapid growth, hurdles remain:
Data privacy concerns: Biometric and personal information must be guarded carefully.
Standards fragmentation: Not all countries and industries align on blockchain identity or biometric specs.
Cost and complexity: Smaller organizations can find it hard to build internal expertise.
Security trade-offs: Even biometrics can be spoofed—continuous research and red teaming exercises are essential.
8. Market Forecast
The global digital identity solutions market, valued near USD 33 billion in 2024, is projected to reach USD 85 billion by 2030, growing at a compound annual growth rate (CAGR) of approximately 15–17% during the 2025‑2030 period. Growth engines include:
Mass deployment of X.509 certificates in IoT and device-to-device authentication.
Enterprise shift toward passwordless identity.
Expansion of cross-border digital ID ecosystems.
Government e‑ID initiatives continuing in developing regions.
9. Strategic Recommendations
Enterprises should adopt a phased approach: start with workforce SSO/MFA, layer risk‑based behavioral analytics, then extend to B2C or partner identity.
Vendors must differentiate by building open, modular cloud platforms, obtaining compliance certifications, and fostering trust through transparency and audit practices.
Policy makers should collaborate across borders on global identity standards, while ensuring citizens’ privacy rights aren’t compromised.
10. Outlook: What Lies Ahead
Over the next decade, more digital identity will be user-centric, portable across platforms, and governed by privacy-respecting consent frameworks. Advances in privacy-enhancing technologies (PETs) like zero‑knowledge proofs and homomorphic encryption will bolster user control and interoperability. Meanwhile, quantum‑resistant cryptography and deep learning‑driven risk assessments promise a more secure digital future. In our hyper‑connected world, digital identity is foundational—a keystone for trust, openness, and resilience.
In Summary
The digital identity solutions market stands at a pivotal juncture. With cybersecurity risks escalating and digital services proliferating worldwide, robust identity authentication systems are no longer optional. Backed by biometrics, AI-driven analytics, blockchain portability, and cloud-enabled scalability, this market is set to grow strongly, while emphasizing user privacy and regulatory compliance. Organizations that invest wisely in modern digital identity tools will gain both security assurance and competitive differentiation in a more digital-first era.
0 notes
Text
Free iOS Password Manager

Simplify your life with RelyPass, the ultimate iOS password manager app! The app is free to use; no account creation is needed, and it’s easy to use.
Download the app today!
#iOS password manager#Password manager app#Secure password manager#Best password manager#Password manager for iPhone#Top password manager#Password manager for iOS#Mobile password manager#Encrypted password manager#Multiplatform password manager#Biometric password manager#Password manager with face recognition#Cloud-based password manager#Free password manager for iOS#RelyPass#RelyPass App#RelyPass Password Manager#RelyPass iOS App#RelyPass iOS Password Manager
0 notes
Text
Why Your Business Needs a Face Attendance Machine

Businesses are always looking for smarter ways to streamline operations, and make them more efficient in today's fast paced, tech-driven world. Tracking employees' attendance is one area where new ideas have made a big difference. Punch cards, and manual sign-ins are quickly being replaced by more modern tools. The face attendance machine is one of the first to do this.
Face recognition technology in this state-of-the-art device accurately, and safely records employee attendance. This helps businesses cut down on time theft, stop buddy punching, and make managing their employees easier. Getting a face attendance machine could be one of the best things, you can do for your business if you want to bring it up to date.
Face attendance machines that work well and are reliable can be found at SBJ Store. These machines are made for businesses of all sizes. Let's look at why this technology is so important in the workplace these days.
Enhanced Accuracy and Security
The accuracy of a face attendance machine is one of the main reasons to switch to one. Face recognition is very hard to fake or change, unlike manual systems or swipe cards. The system can very accurately confirm the identity of each worker, because it records and stores their unique facial features.
This level of biometric verification not only makes things safer, but it also gets rid of common attendance problems like "buddy punching," which is when one worker signs in for another. It also cuts down on mistakes made when keeping track of hours worked, which makes sure that payroll is calculated correctly, and fairly.
It's also possible to connect these systems to other security protocols, like access control, so you can control who comes in and when. This two-in-one feature makes the workplace safer, and makes administrative tasks easier.
Efficiency and Time-Saving Benefits
Keeping track of employee attendance by hand takes a lot of time and can lead to mistakes. A lot of the time, HR teams spend hours going through logs, fixing mistakes, and settling disagreements. This whole process is automated by a face attendance machine, which records attendance in real time, and syncs it with HR, or management software.
Not only does this cut down on administrative work, but it also gives real-time information about employee attendance, tardiness, and absences. Managers can get to this information right away, use it to make smart decisions, and be ready for any problems, that might arise with attendance.
Another good thing about it is how easy it is to use. Employees just walk up to the machine and their attendance is recorded right away. It's clean and contactless, because you don't need cards, passwords, or fingerprints. This is especially important in a workplace after a pandemic.
A Scalable Solution for Every Business
A face attendance machine can be moved from one location to another to fit the needs of your business, no matter how big or small it is. Modern devices are connected to the cloud, which lets you access your data from anywhere. They also have features like sync between multiple locations, photo logs, shift scheduling, and alert notifications.
These features are especially helpful for companies with multiple departments, teams that work from home, or shifts that change over time. The settings can be changed to fit your needs, and you can keep control of all attendance data from one place.
The system can also grow with your business. You don't have to change everything; just add more users or devices as needed, and the technology will take care of the rest.
Improve Compliance and Transparency
For payroll purposes, and to follow labor laws and rules, it is important to keep accurate records of employees' hours worked. A face attendance machine leaves a digital audit trail, that makes sure everyone is completely honest and responsible.
If there are disagreements about work hours, or attendance, the data can be used as a neutral point of reference, which lowers the chance of a fight. It also makes reporting easier and helps companies stay in line with wage and hour laws, which lowers their legal risks and builds trust among their workers.
With SBJ Store, you can make the smart switch. Putting in a face attendance machine isn't just an upgrade in technology; it's a move toward a safer, more open, and more efficient workplace. This technology frees up time, and resources by automating attendance, improving security, and giving you real-time data. This lets you focus on what matters most: growing your business.
So, Ready to modernize your attendance system.
0 notes
Text
AI-Driven PCs: The New Frontier in Achieving Enterprise Security and Productivity Goals
In the rapidly evolving business landscape of the 21st century, organizations face dual imperatives: safeguarding sensitive data against increasingly sophisticated cyber threats and driving higher productivity to maintain competitive advantage. Traditional computing systems, while reliable in the past, are often ill-equipped to meet these rising demands simultaneously. Enter AI PCs—personal computers integrated with artificial intelligence technologies—poised to redefine how businesses secure their digital assets while enhancing workforce efficiency.

Understanding AI PCs: What Sets Them Apart?
AI PCs differ fundamentally from conventional computers by embedding advanced AI capabilities directly within the hardware and software architecture. These machines harness machine learning, neural networks, and real-time analytics to deliver smart, adaptive functionalities. Instead of simply reacting to commands or pre-set rules, AI PCs anticipate needs, learn from user behavior, and automate complex processes. This evolution in personal computing marks a pivotal step toward intelligent enterprise ecosystems where security and productivity are inherently intertwined.
Reinforcing Security in an Era of Heightened Threats
Cybersecurity remains one of the top concerns for enterprises worldwide. According to recent reports, cyberattacks have become more frequent, targeted, and damaging, making traditional perimeter defenses insufficient. AI PCs introduce multiple layers of intelligent security measures designed to protect data and systems at the endpoint — often the most vulnerable point in a network.
Real-Time Threat Detection and Prevention
AI PCs continuously monitor system behavior and network traffic using sophisticated algorithms capable of detecting anomalies indicative of malware, ransomware, or phishing attempts. Unlike signature-based antivirus programs, AI-driven security solutions can identify zero-day threats by recognizing unusual patterns and deviations from normal activity. This proactive detection reduces the window of exposure and helps prevent breaches before they escalate.
Behavioral Biometrics and Adaptive Authentication
Security protocols on AI PCs transcend static passwords or tokens. By leveraging behavioral biometrics — such as keystroke dynamics, mouse movements, and facial recognition — these systems authenticate users in real-time, adjusting access permissions dynamically based on contextual risk assessment. For example, if a login attempt occurs from an unusual location or device, the system can require additional verification steps or block access entirely.
Automated and Intelligent Patch Management
Many cyber vulnerabilities arise from unpatched software. AI PCs simplify this challenge by automating the identification and installation of critical patches and updates. This intelligent patch management operates in the background, minimizing disruptions while ensuring systems remain up to date against emerging threats.
Contextual Data Encryption
AI-enabled encryption algorithms embedded in AI PCs can automatically classify data sensitivity and apply appropriate encryption protocols. This ensures that the most critical information remains protected without unnecessarily taxing system performance, striking an optimal balance between security and usability.
Amplifying Workforce Productivity with AI-Powered Tools
Security is essential, but the true power of AI PCs lies in their ability to enhance productivity across all organizational levels. By delivering smart assistance and intelligent automation, AI PCs transform routine workflows and empower employees to focus on strategic, creative, and high-impact tasks.
Personalized Workflow Optimization
AI PCs continuously learn user habits and preferences, enabling tailored suggestions and automation of repetitive tasks. For instance, AI can auto-complete documents, prioritize email responses, schedule meetings intelligently by analyzing calendars, and even recommend optimal work breaks to maintain focus. This level of personalization streamlines daily operations and reduces cognitive overload.
Enhanced Collaboration and Communication
Modern businesses depend on seamless collaboration across dispersed teams. AI PCs integrate with virtual assistants powered by natural language processing, making tasks such as transcribing meetings, generating summaries, and organizing project notes effortless. These AI-driven tools help teams communicate more effectively, reducing misunderstandings and speeding up decision-making.
Intelligent Resource Management
AI PCs optimize hardware resources by dynamically allocating CPU, memory, and storage based on real-time workloads. This ensures consistent performance even under demanding multitasking scenarios or when running data-intensive applications. Additionally, smart energy management systems extend battery life and reduce power consumption, supporting sustainability initiatives without compromising productivity.
Facilitating Remote and Hybrid Work Models
The rise of remote and hybrid work models has placed new demands on enterprise IT infrastructure. AI PCs are uniquely suited for these environments, providing secure access to corporate resources through AI-enhanced VPNs and endpoint protection. Their adaptive capabilities ensure that employees enjoy consistent, secure, and efficient computing experiences regardless of location.
Business Impacts: Why AI PCs Are a Strategic Imperative
The integration of AI into personal computing is no longer a futuristic concept but a strategic business necessity. Organizations adopting AI PCs gain significant advantages across multiple dimensions:
Reducing IT Complexity and Costs
By automating security monitoring, patching, and system optimization, AI PCs reduce the routine workload on IT departments. This allows IT teams to focus on innovation, compliance, and strategic projects rather than firefighting. Furthermore, intelligent diagnostics embedded in AI PCs help identify hardware issues early, lowering downtime and repair costs.
Accelerating Digital Transformation
AI PCs act as enablers of broader digital transformation initiatives by providing the intelligent endpoints necessary for next-generation applications such as AI-driven analytics, augmented reality (AR), and edge computing. These devices support seamless integration with cloud services, IoT ecosystems, and other advanced technologies critical for competitive differentiation.
Enhancing Regulatory Compliance and Risk Management
Compliance with data protection regulations such as GDPR, HIPAA, or CCPA demands continuous monitoring and data governance. AI PCs contribute by automatically enforcing security policies, generating audit trails, and enabling real-time risk assessments. This automation simplifies adherence to regulatory frameworks and mitigates compliance risks.
Empowering Employee Experience and Retention
By delivering intuitive and responsive computing experiences, AI PCs improve employee satisfaction and engagement. When technology supports rather than hinders work, employees are more likely to stay productive, creative, and motivated—critical factors in talent retention.
The Road Ahead: AI PCs as Cornerstones of Future Workplaces
As artificial intelligence continues to evolve, so too will the capabilities of AI PCs. Future iterations are expected to incorporate even more advanced predictive analytics, deeper integration with cloud and edge architectures, and greater customization to industry-specific needs. For example, in sectors such as finance, healthcare, or manufacturing, AI PCs could be tailored to offer specialized security protocols and workflow automations designed for unique compliance and operational requirements.
Moreover, as AI ethics and transparency become focal points, AI PCs will also incorporate features that ensure explainability and user control over AI-driven decisions. This will foster trust and wider adoption among users wary of “black-box” algorithms.
For enterprises committed to maintaining security resilience while maximizing workforce productivity, AI PCs represent an indispensable investment. They transform endpoints from passive tools into intelligent partners, unlocking unprecedented value in day-to-day business operations.
Read Full Article : https://businessinfopro.com/ai-pcs-are-quickly-becoming-the-key-to-achieving-security-and-productivity-goals/
Visit Now: https://businessinfopro.com/
0 notes
Text
Why Businesses Are Turning to Biometric Attendance Systems

Tracking employee attendance has evolved beyond paper sign-in sheets and punch clocks. In present-day fast-paced workplaces, speed, accuracy, and security matter more than ever before, and biometric attendance systems address these issues directly.
Biometric systems eliminate the need for ID cards or more password login systems. Instead, they identify employees via unique physical characteristics, including fingerprints, face recognition, or even iris scans. They are therefore much more dependable and automatically eliminate buddy punching which is prevalent when two employees clock in for each other.
Using biometric attendance has brought a new level of extreme precision to HR teams, and simplifies payroll and attendance tracking. It removes hours of manual work, corrects a plethora of errors, and verifies actual hours worked, period. Additionally, because nobody else shares a fingerprint, biometric attendance is a further level of security when it comes to doing business.
Real-time tracking is probably a major advantage of biometric systems. Managers know instantly when employees have either arrived late or are working overtime, and it brings accountability to the department.
All in all, biometric attendance systems are a smart way of tracking attendance in both small office and enterprise-level organizations. Considering the continuous modernization of companies, I think we may be scratching the surface regarding the possibility of the technology.
0 notes
Text
Biometric Attendance Software: Where Accuracy Meets Security.

Let’s be honest — old-school attendance systems just don’t cut it anymore. Signing registers, buddy punching, forgotten swipe cards… It’s all too easy to cheat or mess up. That’s where biometric attendance software steps in — and honestly, it’s one of those upgrades that just makes sense.
Because when it comes to tracking who’s in and who’s not, fingerprints don’t lie.
What Makes Biometrics Different?
Biometric attendance systems use things like fingerprints, facial recognition, or even iris scans to verify who you are. No passwords to forget. No badges to lose. It’s literally you clocking in, not your coworker punching in for you because you were late again.
It’s personal, fast, and way more accurate.
Say Goodbye to "Buddy Punching"
One of the biggest issues in traditional systems is buddy punching — when someone clocks in on behalf of someone else. You’d be surprised how common it is. Over time, this can cost businesses serious money and productivity.
Biometric systems solve this instantly. If your fingerprint or face isn’t there, you’re not getting in. Simple.
Real-Time Data You Can Trust
Another major win? The data you get from a biometric system is solid. No vague check-in times or excuses. You get a real-time record of who showed up, when, and for how long — and that means fewer payroll mistakes and less back-and-forth with HR.
Plus, most systems are cloud-based now, so managers can check attendance from anywhere. Whether you’re in the office or halfway across the country, the data is there when you need it.
Security That Works Both Ways
Biometric attendance software doesn’t just protect employers — it protects employees too. Everyone’s time is recorded fairly. If someone stayed late, it's there. If someone missed a punch, the system logs it.
This kind of transparency goes a long way in building trust between teams and management.
It’s Not Just for Big Companies Anymore
There’s a myth that biometric systems are only for large enterprises. That might’ve been true years ago — but not now. These systems have become affordable, easy to install, and scalable. Whether you have 10 people or 200, you can find a setup that fits your needs without breaking the bank.
A Smarter Way to Manage Time
In a world where businesses are moving faster than ever, wasting time on attendance issues just doesn’t make sense. Biometric systems streamline the process, cut down errors, and give everyone peace of mind.
Final Thoughts?
The Best Biometric attendance software isn’t just about high-tech gadgets — it’s about honest records, secure workplaces, and less wasted time.
If you’re still relying on old methods, maybe it’s time to put the pen down and let your fingerprint do the talking.
0 notes
Text
Top 10 Cybersecurity Trends and Strategies in 2025

As we navigate through 2025, the cybersecurity landscape continues its relentless evolution, driven by geopolitical tensions, technological advancements, and the ever-increasing ingenuity of cybercriminals. Organizations and individuals alike face a more complex and perilous digital environment than ever before. Staying ahead means not just reacting to threats, but anticipating them and implementing proactive strategies.
Here are the top 10 cybersecurity trends defining 2025 and the essential strategies to fortify your defenses.
1. The AI Arms Race: Both Sword and Shield
Trend: Generative AI (GenAI) is a double-edged sword. While it dramatically enhances threat detection, anomaly analysis, and automated response for defenders, it also empowers attackers to create more sophisticated phishing campaigns, adaptive malware, and deepfake-driven social engineering at an unprecedented scale and reduced cost.
Strategy: Invest in AI-powered security solutions (e.g., EDR, XDR, UEBA) that leverage machine learning for advanced threat detection and automated response. Simultaneously, prioritize security awareness training that specifically addresses AI-enhanced attacks, including deepfake recognition.
2. Zero Trust Architecture: The New Default
Trend: The traditional perimeter-based security model is obsolete. With hybrid workforces, cloud adoption, and interconnected supply chains, the "never trust, always verify" principle of Zero Trust Architecture (ZTA) is becoming the fundamental security posture for most enterprises. Gartner predicts 60% of enterprises will embrace Zero Trust as a starting point by 2025.
Strategy: Implement ZTA across your entire IT environment, focusing on continuous verification of every user, device, application, and data flow, regardless of location. Prioritize microsegmentation and least privilege access.
3. Supply Chain Security: Beyond Your Own Walls
Trend: Supply chain attacks continue to be one of the most devastating vectors. By compromising a trusted third-party vendor or software component, attackers can gain access to numerous downstream organizations. The interconnectedness of modern businesses makes this a critical vulnerability.
Strategy: Implement robust third-party risk management programs. Demand strong security assurances from vendors, conduct regular security assessments of your supply chain partners, and enforce secure software development lifecycle (SSDLC) practices for all purchased or integrated software.
4. Cloud Security Posture Management (CSPM) & Cloud-Native Security
Trend: As cloud adoption accelerates and multi-cloud environments become standard, misconfigurations remain the leading cause of cloud breaches. Attackers are increasingly targeting cloud-native vulnerabilities, API keys, and non-human identities.
Strategy: Adopt comprehensive CSPM tools for continuous monitoring of cloud configurations. Implement robust Identity and Access Management (IAM) for cloud environments, focusing on least privilege for both human and non-human identities. Prioritize cloud-native security tools that integrate deeply with cloud provider APIs.
5. Cyber Resilience and Recovery: Expect the Breach
Trend: Organizations are shifting from a sole focus on "prevention" to "resilience." This acknowledges that breaches are often inevitable and emphasizes the ability to quickly recover, minimize impact, and maintain business continuity. Ransomware continues to be a driving force here.
Strategy: Develop and regularly test comprehensive incident response plans. Implement robust, immutable backup strategies (e.g., 3-2-1 rule with off-site, air-gapped copies). Invest in automated recovery solutions and conduct regular tabletop exercises to ensure readiness.
6. Identity-Centric Security & Passwordless Authentication
Trend: Passwords remain a weak link. The widespread adoption of passwordless authentication methods (like FIDO passkeys, biometrics, and magic links) is gaining significant momentum, offering enhanced security and a superior user experience.
Strategy: Transition to strong, multi-factor authentication (MFA) as a baseline. Actively explore and implement passwordless authentication solutions for employees and customers where feasible, leveraging standards like FIDO WebAuthn.
7. OT/IoT Security Convergence and Challenges
Trend: The convergence of Operational Technology (OT) and Information Technology (IT) networks, coupled with the proliferation of IoT devices, creates new and complex attack surfaces. Legacy OT systems were not built with modern cybersecurity in mind, making them vulnerable to sophisticated threats.
Strategy: Implement network segmentation to isolate OT/IoT environments from IT networks. Deploy specialized OT/IoT security solutions for asset visibility, threat detection, and vulnerability management in these unique environments. Address legacy system risks through compensating controls.
8. Enhanced Data Privacy and Compliance Complexity
Trend: The global regulatory landscape around data privacy (e.g., GDPR, CCPA, and new regional laws) continues to expand and mature. Organizations face increasing scrutiny and hefty penalties for non-compliance, pushing privacy to the forefront of cybersecurity strategy.
Strategy: Implement robust data governance frameworks. Invest in data discovery and classification tools. Ensure your cybersecurity practices align with all relevant privacy regulations, potentially leveraging privacy-enhancing technologies (PETs) like differential privacy or homomorphic encryption.
9. Human Element: The Persistent Vulnerability
Trend: Despite technological advancements, the human element remains the primary target for attackers. Social engineering, phishing, and insider threats (both malicious and accidental) continue to be highly effective. AI only makes these attacks more convincing.
Strategy: Elevate security awareness and training programs beyond basic phishing simulations. Foster a strong cybersecurity culture within the organization. Implement User Behavior Analytics (UEBA) to detect anomalous insider activities and enhance Data Loss Prevention (DLP) measures.
10. Cyber Workforce Development & Automation
Trend: The critical global shortage of cybersecurity professionals persists. Organizations are struggling to find and retain talent, leading to burnout and missed threats. This drives an urgent need for automation.
Strategy: Invest in Security Orchestration, Automation, and Response (SOAR) platforms to automate repetitive tasks and streamline incident response. Focus on upskilling existing teams and leveraging AI to augment human capabilities, allowing experts to focus on strategic initiatives rather than manual "firefighting."
By understanding these prevailing trends and proactively implementing these strategies, organizations can build more resilient defenses, minimize their risk exposure, and navigate the complex digital challenges of 2025 and beyond. Stay adaptive, stay secure.
0 notes