#AIInSecurity
Explore tagged Tumblr posts
Text
Cloud Squatting: Understanding and Mitigating a Modern Cyber Threat

Cloud computing is central to both business and personal data storage. A critical and emerging threat is cloud squatting.This phenomenon, a digital variant of the notorious domain squatting, involves the unauthorized occupation of cloud resources. It poses significant risks, making it a crucial concern for everyone, from casual cloud users to IT professionals and business owners.
Understanding cloud squatting
Cloud squatting is the practice of occupying cloud resources, such as storage accounts, domain names, or service identifiers, often for exploitative purposes. This could range from reselling these resources for profit to hosting harmful content or phishing scams. Cloud squatting not only mirrors traditional domain squatting but also extends to trafficking cloud resources like cloud computing instances or web applications, typically for malicious intentions.
The risks involved
Cloud squatting presents various risks:
Data theft: Unauthorized instances can store or transmit stolen data.
Security breaches: They can act as platforms for attacks on other systems.
Reputation damage: Companies suffer if their services are impersonated.
Legal and financial repercussions: In cases of brand damage and loss of customer trust.
For example, an attacker might use a service resembling a legitimate one, deceiving users into sharing sensitive information, leading to data breaches and tarnished reputations.
Mitigation strategies
Effective mitigation of cloud squatting involves a multi-faceted approach:
Proactive registration: Secure variations of your business’s cloud resource names.
Regular audits: Ensure all cloud services are legitimate.
Monitoring and alert systems: Detect unauthorized or misleading registrations.
Employee training: Educate about risks and the identification of suspicious services.
Legal protections: Utilize trademarks and enforce anti-squatting policies.
Security tools and best practices: Use AI-driven solutions and update security measures regularly.
Stakeholder education: Inform teams and customers about these risks.
Rapid response plan: Have a plan to address incidents swiftly.
Collaboration with cloud providers: Utilize their anti-squatting policies.
Reserved IP addresses: Transfer owned IPs to the cloud and manage records.
Policy enforcement: Prevent hard coding of IP addresses and use reserved IPv6 addresses.
The future of cloud security
As cloud technologies evolve, so do the tactics of cybercriminals. This makes proactive security measures and constant vigilance essential. Emerging technologies, like AI-driven security solutions, will play a crucial role in combating these threats.
Cloud squatting is a modern cyber threat that demands awareness, understanding, and proactive action. Implementing robust security strategies and staying informed about the latest trends in cloud security can significantly protect valuable digital assets. By addressing the risks and employing comprehensive mitigation strategies, individuals and businesses can safeguard their presence and integrity in the cloud.
Centizen, your trusted partner in cloud consulting and staffing provides unparalleled expertise and solutions to guard against threats like cloud squatting, ensuring the security and efficiency of your digital infrastructure.
#CloudSquatting#CyberSecurity#CloudSecurity#DataProtection#DigitalThreats#CloudComputing#InfoSec#AIinSecurity
2 notes
·
View notes
Text
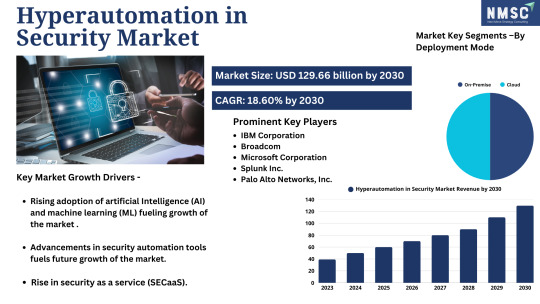
𝗗𝗶𝗱 𝗬𝗼𝘂 𝗞𝗻𝗼𝘄?
𝗪𝗵𝘆 𝘁𝗵𝗲 𝗛𝘆𝗽𝗲𝗿𝗮𝘂𝘁𝗼𝗺𝗮𝘁𝗶𝗼𝗻 𝗶𝗻 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗠𝗮𝗿𝗸𝗲𝘁 𝗶𝘀 𝗮 𝗚𝗮𝗺𝗲-𝗖𝗵𝗮𝗻𝗴𝗲𝗿 𝗳𝗼𝗿 𝗖𝘆𝗯𝗲𝗿 𝗥𝗲𝘀𝗶𝗹𝗶𝗲𝗻𝗰𝗲
𝗗𝗼𝘄𝗻𝗹𝗼𝗮𝗱 𝗙𝗥𝗘𝗘 𝗦𝗮𝗺𝗽𝗹𝗲
Hyperautomation—combining AI, machine learning, RPA, and advanced analytics—is transforming how organizations defend against evolving cyber threats. No longer reactive, security is becoming predictive, self-healing, and autonomous.
Major sectors like banking, defense, healthcare, and critical infrastructure are rapidly adopting hyperautomation tools to minimize human error and respond to threats in real-time.
𝗞𝗲𝘆 𝗣𝗹𝗮𝘆𝗲𝗿𝘀 : IBM Corporation, Fortinet Inc. , Broadcom, Microsoft Corporation, Splunk Inc., Palo Alto Networks, Inc., McAfee LLC and others.
𝗙𝗼𝗿 𝗶𝗻𝘃𝗲𝘀𝘁𝗼𝗿𝘀, 𝘁𝗵𝗶𝘀 𝗶𝘀𝗻'𝘁 𝗷𝘂𝘀𝘁 𝗮 𝘁𝗲𝗰𝗵 𝘁𝗿𝗲𝗻𝗱—𝗶𝘁’𝘀 𝗮 𝗵𝗶𝗴𝗵-𝗴𝗿𝗼𝘄𝘁𝗵 𝗼𝗽𝗽𝗼𝗿𝘁𝘂𝗻𝗶𝘁𝘆 𝗱𝗿𝗶𝘃𝗲𝗻 𝗯𝘆:
Growing attack surface in digital transformation
Surge in AI/ML adoption in cybersecurity
Need for zero-trust architecture & 24/7 monitoring
Enterprise shift towards automated SOC operations
Do you know which companies are already ahead of the curve? Follow the innovators driving scalable, secure, and intelligent automation platforms.
𝗔𝗰𝗰𝗲𝘀𝘀 𝗙𝘂𝗹𝗹 𝗥𝗲𝗽𝗼𝗿𝘁
𝗧𝗵𝗲 𝗳𝘂𝘁𝘂𝗿𝗲 𝗼𝗳 𝗰𝘆𝗯𝗲𝗿𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆 𝗶𝘀 𝗵𝘆𝗽𝗲𝗿𝗮𝘂𝘁𝗼𝗺𝗮𝘁𝗲𝗱. 𝗔𝗿𝗲 𝘆𝗼𝘂𝗿 𝗶𝗻𝘃𝗲𝘀𝘁𝗺𝗲𝗻𝘁𝘀 𝗮𝗹𝗶𝗴𝗻𝗲𝗱 𝘄𝗶𝘁𝗵 𝘁𝗵𝗶𝘀 𝗲𝘃𝗼𝗹𝘂𝘁𝗶𝗼𝗻?
#Hyperautomation#CyberSecurity#InvestmentOpportunity#AIinSecurity#SmartInvesting#DigitalTransformation#FutureOfSecurity
0 notes
Text
Artificial Intelligence (AI) in Cybersecurity Market Future Trends Shaping Global Security Landscape Growth
The Artificial Intelligence (AI) in cybersecurity market is rapidly evolving, driven by the growing need for advanced defense mechanisms to counter increasingly sophisticated cyberattacks. As organizations digitize their operations and expand their online presence, cybersecurity threats continue to rise in both volume and complexity. AI technologies are becoming essential tools to enhance security frameworks, improve threat detection, and automate response mechanisms, positioning the AI-powered cybersecurity market for significant growth in the coming years.

Increasing Complexity of Cyber Threats
One of the primary drivers behind the surge in AI integration within cybersecurity is the complexity of modern cyber threats. Traditional security systems often struggle to detect and respond to advanced persistent threats (APTs), zero-day vulnerabilities, and polymorphic malware. AI algorithms, particularly those based on machine learning and deep learning, can analyze massive amounts of data in real-time, identify patterns, and detect anomalies indicative of potential threats. This capability enables organizations to preemptively neutralize attacks before they cause significant damage.
Adoption of AI-Driven Security Solutions
The market is witnessing a surge in adoption of AI-driven security solutions across various sectors including finance, healthcare, government, and retail. Financial institutions, for example, leverage AI to monitor transactions for fraudulent activity with greater accuracy than conventional methods. Healthcare organizations use AI to protect sensitive patient data against breaches, while governments deploy AI-powered tools to safeguard critical infrastructure.
Enterprises are increasingly investing in AI-based cybersecurity platforms that combine predictive analytics, behavioral analysis, and automated incident response to create a robust defense ecosystem. These platforms reduce reliance on manual monitoring and enable faster, more accurate threat mitigation.
Automation Enhances Incident Response
One of the most promising future trends in AI in cybersecurity is automation in incident response. AI-driven systems can autonomously execute predefined protocols to contain and remediate threats, significantly reducing response times and minimizing human error. For example, when suspicious activity is detected, AI can automatically isolate affected network segments, block malicious IP addresses, and initiate forensic analysis.
Automation not only improves efficiency but also frees up cybersecurity professionals to focus on strategic tasks rather than routine threat hunting and manual interventions. This shift helps address the global shortage of skilled cybersecurity personnel, which remains a critical challenge for organizations worldwide.
Integration of AI with Emerging Technologies
The integration of AI with other emerging technologies like blockchain, edge computing, and the Internet of Things (IoT) is another key trend shaping the future of cybersecurity. AI-enhanced blockchain solutions can improve the security and transparency of transactions, while AI algorithms running on edge devices enable real-time threat detection closer to data sources.
In IoT ecosystems, which involve billions of interconnected devices, AI is vital to monitor device behavior and detect anomalies that might indicate a breach. As IoT adoption grows, AI-powered cybersecurity will become indispensable to protect these expansive, distributed networks.
Focus on Privacy and Ethical AI
With the expansion of AI in cybersecurity, there is also increasing attention on privacy and ethical concerns. AI systems require access to vast datasets to learn and operate effectively, raising questions about data privacy and consent. Future market trends indicate a growing emphasis on developing transparent and explainable AI models that ensure compliance with data protection regulations and maintain user trust.
Organizations are expected to invest in AI solutions that balance security with privacy, deploying techniques like federated learning and differential privacy to safeguard sensitive information while leveraging AI capabilities.
Growth of AI-Powered Threat Intelligence
Threat intelligence platforms powered by AI are becoming crucial assets for cybersecurity teams. These platforms gather and analyze data from diverse sources such as network logs, dark web forums, and social media to provide actionable insights about emerging threats. AI accelerates this process by correlating data points, predicting attack vectors, and identifying threat actors.
The future will see enhanced collaboration among organizations through AI-driven intelligence sharing networks that improve collective defense mechanisms. This collective approach amplifies the effectiveness of cybersecurity efforts by enabling quicker identification and mitigation of widespread threats.
Challenges and Opportunities Ahead
Despite its promising potential, the AI in cybersecurity market faces challenges such as adversarial attacks on AI models, high implementation costs, and the need for skilled professionals to manage AI systems. Hackers are increasingly attempting to deceive AI algorithms by manipulating data inputs, known as adversarial attacks, which can undermine AI’s accuracy and reliability.
However, these challenges also present opportunities for innovation. Continuous advancements in AI research aim to develop more resilient models that can withstand adversarial tactics. Additionally, the growing demand for AI cybersecurity solutions opens new avenues for startups and technology providers to innovate and capture market share.
Conclusion
The Artificial Intelligence (AI) in cybersecurity market is poised for significant expansion driven by the urgent need for smarter, faster, and more adaptive security solutions. Future trends indicate deeper AI integration across industries, enhanced automation in threat response, and strategic collaborations leveraging AI-powered threat intelligence. As cyber threats become more complex, AI will play a pivotal role in securing digital assets and maintaining trust in an increasingly connected world. Organizations investing in AI cybersecurity today are better positioned to navigate tomorrow’s threat landscape with confidence.
0 notes
Text

In 2025, hackers will use AI. But so do the defenders.
Cybersecurity has officially entered the intelligence era, with real-time detection, predictive defense, and AI co-pilots working around the clock to keep us safe.
To know more, click here:
0 notes
Text

🤖 The AI Revolution: Cameras That Predict Crimes Before They Happen! 🚨 Welcome to the future of security in Los Angeles!
Our latest AI-powered surveillance cameras do more than record—they analyze behavior in real-time to detect and flag suspicious activity before a crime is committed.
🔍 How It Works: ✅ Behavior Detection Technology ✅ Loitering & Unusual Movement Alerts ✅ License Plate Recognition ✅ Facial Recognition & Smart Tracking ✅ Instant Alerts to Your Phone or Security Team These smart systems are already helping LA businesses and homes stay steps ahead of thieves, vandals, and trespassers.
🧠 Think of it as a security guard that never blinks—only smarter. 📍 Serving Los Angeles & Surrounding Areas 📞 310-901-4972 📧 [email protected]
🔹 Secure Your Space with the Power of AI
#SmartSurveillance#CrimePrevention#LosAngelesSecurity#DigitalSurveillance#AIinSecurity#CCTVInstallation#PredictiveSecurity#BusinessSecurityLA
0 notes
Text
Smart Camera Market Rising Demand for Advanced Security, Automation, and Real-Time Analytics
The global smart camera market is witnessing an unprecedented surge due to the growing need for enhanced security, advancements in technology, and the increasing demand for intelligent systems across various sectors. Smart cameras, equipped with artificial intelligence (AI) and machine learning (ML) capabilities, are revolutionizing surveillance, home automation, and even retail industries by enabling smarter, more efficient, and user-friendly operations. Several factors are driving the growth of the smart camera market, and this article delves into some of the most significant drivers that are propelling the market forward.

1. Rising Demand for Security and Surveillance Solutions
One of the primary drivers of the smart camera market is the increasing demand for robust security and surveillance solutions. As crime rates rise and security concerns grow globally, both residential and commercial spaces are looking for ways to enhance their security systems. Traditional security cameras often fall short in providing advanced features such as real-time monitoring, facial recognition, and automated alerts. Smart cameras, on the other hand, leverage AI algorithms and cloud-based technologies to provide seamless monitoring, facial recognition, object detection, and even intruder alerts. This capability is particularly important for applications like monitoring public spaces, businesses, and high-security areas like airports and government buildings.
2. Technological Advancements in Artificial Intelligence and Machine Learning
Technological advancements in AI and machine learning are significantly influencing the smart camera market. The integration of AI allows smart cameras to go beyond simple video recording and playback. These cameras are now capable of detecting faces, recognizing objects, and tracking movements with greater accuracy. Furthermore, machine learning algorithms enable smart cameras to "learn" from patterns in the environment, thereby improving their functionality over time. For example, smart cameras installed in homes or businesses can distinguish between humans, animals, and objects, ensuring that users receive only relevant alerts, thus reducing false alarms. The incorporation of edge computing also allows for real-time data processing, enhancing the camera’s responsiveness.
3. Growth of the Internet of Things (IoT)
The rapid expansion of the Internet of Things (IoT) is another key driver for the smart camera market. IoT refers to the interconnection of everyday devices through the internet, and smart cameras are a critical component of this ecosystem. These cameras can connect to other smart devices like lights, thermostats, and door locks, creating an integrated smart home or office system. For example, a smart camera can automatically lock a door when it detects the owner’s arrival or adjust the lighting when motion is detected. This seamless connectivity is one of the main attractions for consumers, particularly as IoT-enabled homes and businesses become more common. As the IoT market grows, so too does the demand for smart cameras that can integrate with these systems.
4. Increasing Adoption of Smart Homes and Automation
Smart home technology is becoming an integral part of modern living, driving the demand for smart cameras in residential settings. Consumers are increasingly investing in smart home solutions that offer convenience, security, and energy efficiency. Smart cameras fit seamlessly into this ecosystem, offering users the ability to monitor their homes remotely and automate certain functions. With the rise of voice assistants like Amazon Alexa, Google Assistant, and Apple Siri, users can control smart cameras using simple voice commands. These advancements have made smart cameras more accessible and appealing to the average consumer. The adoption of smart home technologies is expected to continue growing, further driving the smart camera market.
5. Demand for Advanced Video Analytics and Cloud Storage
Another major factor contributing to the growth of the smart camera market is the demand for advanced video analytics and cloud storage solutions. Smart cameras can process video feeds in real-time and store data in the cloud for easy access and analysis. This combination of analytics and cloud storage makes it easier for users to monitor and review footage from multiple cameras, analyze trends, and receive actionable insights. For example, a retailer can use video analytics to track customer behavior and optimize store layouts, while a business owner can monitor employees' productivity. Cloud storage ensures that video footage is securely stored and can be accessed remotely, making it a preferred option for businesses and consumers alike.
Conclusion
In conclusion, the smart camera market is experiencing substantial growth, driven by various factors including increasing demand for security and surveillance solutions, advancements in AI and machine learning, the rise of IoT, the adoption of smart home technologies, and the demand for advanced video analytics and cloud storage. As these drivers continue to evolve, the market for smart cameras is expected to expand further, offering new opportunities for innovation and market players. The convergence of security, convenience, and advanced technology in smart cameras is making them an indispensable tool in modern society, impacting both personal and business operations.
0 notes
Text
Enterprise File Synchronization and Sharing: How Enterprises are Transforming Data Sharing & Security
The global enterprise file synchronization and sharing market size was valued at USD 9.50 billion in 2023 and is anticipated to grow at a CAGR of 23.2% from 2024 to 2030. The increasing adoption of remote and hybrid work models has necessitated secure, efficient, and collaborative file-sharing solutions, propelling demand for enterprise file synchronization and sharing (EFSS) platforms. Additionally, the growing emphasis on data security and compliance with stringent regulatory standards has underscored the need for robust EFSS solutions that offer advanced encryption and access controls. The integration capabilities of EFSS with other enterprise applications, such as cloud storage, collaboration tools, and enterprise content management systems, further enhances their appeal by providing seamless workflows and improved productivity.
Moreover, the proliferation of mobile devices and the subsequent need for mobile access to corporate data have significantly contributed to the market's expansion. As organizations prioritize digital transformation and agility, the EFSS market is expected to witness sustained growth, driven by the ongoing need for secure, accessible, and efficient data management solutions.
The increasing adoption of remote and hybrid work models significantly drives the EFSS market. As organizations transition to more flexible work environments, the need for secure, efficient, and collaborative file-sharing solutions has become paramount. EFSS platforms enable seamless access to critical data from any location, ensuring remote and hybrid workers can collaborate effectively while maintaining data integrity and security. This shift in work dynamics has highlighted the importance of reliable EFSS solutions, fueling their demand and market growth.
The proliferation of mobile devices and the subsequent need for mobile access to corporate data have significantly contributed to the expansion of the EFSS market. As employees increasingly rely on smartphones and tablets for work, the demand for EFSS solutions that offer secure, seamless access to corporate data on mobile platforms has surged. These solutions enable employees to collaborate, share, and manage files from any device, enhancing productivity and flexibility. Consequently, the growing dependence on mobile technology in the workplace has been pivotal in driving the market's expansion.
Key Enterprise File Synchronization And Sharing Company Insights
Key players operating in the enterprise file synchronization and sharing (EFSS) market include Google LLC, IBM, Open Text, Microsoft, and Qnext Corp. The companies are focusing on various strategic initiatives, including new product development, partnerships & collaborations, and agreements to gain a competitive advantage over their rivals. The following are some instances of such initiatives.
In April 2024, Microsoft unveiled new features for OneDrive for Business, including integration with CoPilot AI assistant and enhanced collaboration capabilities for schools and enterprises. The enhanced search features now include new filters for file types, a date filter for specific timeframes, precise scoping options, and an updated interface with improved metadata. These enhancements help you locate files more efficiently.
In October 2023, Dropbox launched Dropbox Dash, an AI-based search feature currently in open beta. This tool enhances the user experience by providing smarter search capabilities across files and folders. Additionally, Dropbox introduced Dropbox Studio, an all-in-one tool for video content creation, editing, and feedback collection.
For More Details or Sample Copy please visit link @: Enterprise File Synchronization And Sharing Market
#EFSS#EnterpriseFileSharing#FileSync#CloudStorage#DataSharing#CloudComputing#HybridCloud#AIinSecurity#BlockchainForSecurity#DataEncryption
0 notes
Text
Exploring Secure Drone Communication: An R&D Perspective
The Growing Challenge of Drone Security
With the rapid advancements in drone technology, Unmanned Aerial Vehicles (UAVs) are becoming integral to various sectors, including defense, logistics, surveillance, and emergency response. However, as the adoption of UAVs increases, so do the cybersecurity threats that target these networks. One of the most pressing concerns? Signal jamming and cyber threats.
Why Secure Drone Communication Matters
Drones rely on wireless communication to transmit data, receive commands, and maintain coordination in a fleet. Any interference in this communication, whether due to intentional jamming, hacking, or environmental disruptions, can compromise mission success and security.
Without robust security protocols, drones can be rendered ineffective, hijacked, or used maliciously. This makes it crucial to develop secure and resilient drone communication networks that can withstand cyber threats and ensure uninterrupted operations.
Tech4Biz’s R&D in Multi-Drone Secure Communication
At Tech4Biz, we have been conducting R&D in Multi-Drone Secure Communication Networks, focusing on how UAVs can detect jamming attempts and restore secure links. Our research and simulations have led us to explore innovative solutions to safeguard drone operations in adversarial environments.
Our recent simulation investigates three key areas:
1. Jamming Detection
Drones operating in critical environments must identify interference in real-time to mitigate risks. Our approach involves:
Detecting anomalies in communication signals that indicate jamming attempts.
Using AI-driven algorithms to analyze patterns and distinguish between natural interference and malicious attacks.
Implementing redundant security layers to ensure immediate alerting and response mechanisms.
2. Secure Recovery Mechanisms
Once a drone detects an interference attempt, the next step is to re-establish a secure connection. Our secure recovery framework includes:
Relay-based Security Mechanisms: If a drone loses direct connection with its operator, it can switch to an alternative secure channel via a network of trusted UAVs.
Automated Re-Routing: The system guides compromised drones to safe zones where they can reconnect to the network.
Encryption & Authentication Measures: All communications are validated with cryptographic security protocols, preventing hijacking attempts.
3. Error Detection & Correction (EDC) for Reliable Data Transmission
To enhance reliability, our research incorporates Error Detection & Correction (EDC) techniques to maintain secure communication:
Adaptive Error Correction Codes (ECC): These correct minor errors without retransmission, reducing latency and power consumption.
Multi-Layered Authentication: Ensuring every data packet remains intact and tamper-proof.
AI-Based Predictive Analysis: Using machine learning models to predict vulnerabilities and counteract potential attacks.
The Future of Secure UAV Operations
Our ongoing R&D aims to develop cutting-edge methodologies to make UAV networks more resilient and autonomous. Secure drone communication is not just essential for defense applications; it is also vital for:
Disaster Response: Ensuring drones continue relaying critical information during emergency operations.
Smart Cities & IoT: Protecting urban drone networks used for surveillance, delivery, and infrastructure monitoring.
Aerospace & Defense: Strengthening military UAV fleets against cyber warfare threats.
Let’s Collaborate!
At Tech4Biz, we believe in the power of collaboration to drive innovation in secure UAV operations. We are looking to partner with researchers, defense experts, and companies working on enhancing drone security.
Are you exploring similar challenges? Are you interested in secure UAV communication solutions? Let’s connect and work towards a safer, more secure future for drone technology.
📩 Drop a comment or reach out — together, we can shape the next generation of secure drone networks.
#tech4bizsolutions#DroneSecurity#Cybersecurity#UAVResearch#EDC#RandD#Innovation#SecureDrones#AIinSecurity#DroneTechnology
1 note
·
View note
Text
AI is transforming cybersecurity! From real-time threat detection to automated response, discover how artificial intelligence is revolutionizing digital defense.
0 notes
Text
#CyberSecurity#DigitalSecurity#FraudProtection#FraudPreventionSolutions#AIInSecurity#CyberThreats#FinancialSecurity#SecureTransactions#AntiFraud#RiskManagement#SecurityTech#FraudDetectionTechnology#FinancialFraud
0 notes
Text
How AI Will Improve Cybersecurity
AI will revolutionize cybersecurity by enhancing threat detection, response times, and predicting potential cyberattacks. With machine learning algorithms, AI can identify patterns and anomalies in vast amounts of data, providing real-time protection. It will also automate routine security tasks, allowing human experts to focus on more complex threats. As cyber threats evolve, AI’s adaptability makes it a powerful tool in defense.

0 notes
Text
Enhancing Event Security with IoT: Prevent Unauthorized Access Seamlessly
Managing security at large events is a challenge due to massive crowds and restricted areas. IoT solutions provide real-time monitoring, smart locks, AI cameras, and motion sensors to prevent unauthorized access. These technologies reduce risks, enhance security, and minimize human errors. With automated alarms and access control, event safety becomes seamless and efficient. Want to secure your event with IoT?
Contact us today to explore our solutions! [email protected]
0 notes
Text

🤖 The Future of Security: AI-Powered CCTV Systems 🌐 Artificial intelligence is revolutionizing the way we protect our homes and businesses. Here’s how AI-powered CCTV systems are transforming surveillance: 👁️ Facial Recognition: Identify individuals with precision – whether it’s granting access to authorized personnel or flagging unknown visitors. Perfect for homes, offices, and high-security areas. 🚨 Anomaly Detection: AI can spot unusual behavior or movements, such as loitering, unattended bags, or unexpected entry, and send real-time alerts to keep you proactive. 📊 Smart Analytics: Receive detailed reports on visitor trends, activity patterns, and more – empowering smarter decision-making for your security needs. ��� Minimized False Alarms: AI systems can differentiate between a stray animal, swaying tree, or an actual intruder, ensuring your attention is directed where it’s truly needed. 🔐 At Digital Surveillance, we bring cutting-edge AI technology to your doorstep with advanced CCTV systems designed to secure your property like never before. 📞 Call us at 310-901-4972 to explore the future of security for your home or business in Los Angeles and Orange County.
#AIinSecurity#DigitalSurveillance#CCTVInnovation#FacialRecognition#AnomalyDetection#LosAngeles#OrangeCounty
0 notes
Text

The future of cybersecurity focuses on using AI to detect threats faster, protecting data with strong encryption, and securing cloud platforms. Employee training will reduce human errors, and zero-trust models will ensure strict access controls. These strategies help businesses stay ahead of evolving threats and build a secure, resilient future. For more info: https://ed11.com/category/cyber-security-courses
#CyberSecurity#FutureStrategy#AIinSecurity#DataProtection#ZeroTrust#CloudSecurity#EmployeeTraining#CyberResilience#DigitalSafety#SecureFuture
1 note
·
View note
Text
Artificial Intelligence in Healthcare: Revolutionizing the Future of Medicine

Artificial Intelligence in Healthcare: Revolutionizing the Future of MedicineExplore how Artificial Intelligence (AI) is transforming healthcare, from diagnostics to personalized treatments and drug development. Learn about AI’s role in enhancing patient care, improving clinical outcomes, and revolutionizing healthcare systems worldwide.1. AI in DiagnosticsAI-powered tools are significantly improving the accuracy and speed of diagnosing diseases. Machine learning algorithms are now capable of analyzing medical imaging such as X-rays, MRIs, and CT scans, often with higher precision than human doctors. AI models have shown remarkable results in detecting conditions like cancer, brain tumors, and heart diseases early, which is crucial for successful treatment. These technologies can detect patterns invisible to the human eye, providing doctors valuable insights.2. Personalized Treatment PlansOne of AI’s most promising applications is creating personalized treatment plans based on individual patient data. By analyzing genetic information, medical histories, and lifestyle factors, AI helps doctors tailor treatments, improving their effectiveness while minimizing adverse reactions.3. AI in Drug DevelopmentAI is speeding up drug development by predicting compound reactions in the human body. This reduces research costs and accelerates bringing new drugs to market. AI is also identifying promising drug candidates previously overlooked in traditional research, offering hope for diseases like cancer and Alzheimer’s.4. Virtual Health AssistantsAI-driven virtual assistants help manage routine healthcare tasks, such as scheduling appointments and providing medication reminders. Apps like Babylon Health and Ada Health use AI to provide immediate consultations based on symptoms, reducing the workload for healthcare professionals and offering timely advice to patients.5. AI for Predictive AnalyticsAI is excelling in predictive analytics by forecasting disease outbreaks and tracking patient recovery. Analyzing large datasets, AI can predict health risks and help healthcare providers take preventive measures, improving outcomes and reducing costs.Read More! https://getwebmaker.com/blog/Artificial%20Intelligence%20in%20Healthcare:%20Revolutionizing%20the%20Future%20of%20Medicine.php
#ArtificialIntelligence#AI#MachineLearning#DeepLearning#DataScience#AITrends#AITechnology#AIInnovation#AIForGood#AIFuture#ChatGPT#OpenAI#NeuralNetworks#NLP#Robotics#Automation#ComputerVision#AIApplications#AIResearch#AIStartups#AIinBusiness#AIinMarketing#AIinHealthcare#AIinFinance#AIinEducation#AIinGaming#AIinRetail#AIinSecurity#AIinAgriculture#AIForEveryone
0 notes
Text
Bot Management in Japan and China: A Market Overview and Forecast
The escalating sophistication of cyber threats has made bot management a critical aspect of cybersecurity in Japan and China. These markets are witnessing rapid technological advancements and a growing reliance on digital platforms, making them highly susceptible to bot attacks. From credential stuffing and web scraping to Distributed Denial of Service (DDoS) attacks, bots have become a significant concern for businesses across various industries. Organizations are increasingly adopting bot management solutions to safeguard their digital assets and ensure seamless user experiences.
The Growing Need for Bot Management
In Japan, the rise of e-commerce, financial services, and online gaming platforms has increased the need for robust bot management solutions. Similarly, China’s digital ecosystem, driven by its massive e-commerce market and fintech innovations, is a hotspot for bot activity. The prevalence of malicious bots has led to significant financial and reputational damages in both countries, prompting organizations to prioritize investments in advanced bot management tools.
Bot management solutions are designed to detect, analyze, and mitigate bot traffic. These tools leverage technologies such as artificial intelligence (AI), machine learning (ML), and behavioral analysis to distinguish between legitimate and malicious traffic. As businesses in Japan and China accelerate their digital transformation initiatives, the demand for sophisticated bot management solutions is expected to surge.
Market Drivers and Trends
Key drivers for the bot management market in Japan and China include the increasing volume of cyberattacks, stringent regulatory frameworks, and the need for superior customer experiences. Companies like QKS Group are at the forefront of providing innovative bot management solutions tailored to these markets. Their offerings emphasize cutting-edge analytics, real-time monitoring, and user-friendly interfaces to address the unique cybersecurity challenges faced by businesses in these regions.
In Japan, government initiatives like the Cybersecurity Basic Act and awareness programs aimed at SMEs are expected to fuel market growth. Similarly, China’s strict data protection regulations and its growing emphasis on securing digital infrastructure are creating a favorable environment for bot management solutions.
Market Forecast: Bot Management, 2024-2028, Japan
The bot management market in Japan is projected to grow at a compound annual growth rate (CAGR) of 14.2% between 2024 and 2028. This growth is driven by increasing adoption in sectors such as e-commerce, banking, and healthcare. Companies like QKS Group are strategically expanding their operations in Japan, capitalizing on the country’s demand for advanced cybersecurity solutions. By 2028, the Japanese market is expected to reach a valuation of $600 million, highlighting its robust growth trajectory.
Japan's bot management market is poised for growth, driven by advancements in AI and machine learning, enabling precise bot attack mitigation. Growing emphasis on comprehensive cybersecurity strategies and collaboration between public and private sectors positions Japan as a leader in securing its digital economy.
Market Forecast: Bot Management, 2024-2028, China
China’s bot management market is expected to exhibit even stronger growth, with a forecasted CAGR of 17.5% during the same period. The market is anticipated to surpass $1.2 billion by 2028, driven by the increasing digitization of industries and a proactive regulatory stance. QKS Group is poised to capture significant market share in China by leveraging its expertise and localized strategies, addressing the unique needs of Chinese businesses.
China's bot management market is set for strong growth, driven by AI-powered solutions and a dynamic digital landscape. Rising cybersecurity priorities, public-private collaboration, and investment will solidify China's role in the global market.
Conclusion
The bot management markets forecast in Japan and China are on a growth trajectory, fueled by rising cyber threats and increasing investments in digital technologies. Companies like QKS Group are playing a pivotal role in shaping these markets by providing innovative and scalable solutions. With favorable market dynamics and growing awareness, the bot management landscape in Japan and China is poised for transformative growth between 2024 and 2028.
0 notes